Designing an Interacting Particle System: Optimization of the Piecewise-Homogeneous Contact Process
|
|
|
- Morris Gilmore
- 5 years ago
- Views:
Transcription
1 2002 Conference on Information Sciences and Systems, Princeton University, March 20 22, 2002 Designing an Interacting Particle System: Optimization of the Piecewise-Homogeneous Contact Process Aaron B. Wagner and Venkat Anantharam Department of Electrical Engineering and Computer Sciences University of California Berkeley, CA USA Abstract We consider an optimization problem centered around a population-growth model similar to the onedimensional, finite contact process, but in which the reproduction rate varies spatially over the population. The objective is to choose the reproduction-rate-profile to maximize the time until the population is extinct. We first extend existing results about the contact process that describe the asymptotic growth of the extinction time with the population size to processes in which the reproduction rate is not constant but rather piecewise constant. We then formulate the optimization problem and characterize its solution in terms of statistics of the original contact process. We also examine the analogous problem for the simpler biased voter model, and obtain similar but more lucid results. I. ITRODUCTIO Interacting particle systems have been successfully employed to model such diverse phenomena as magnetism, population growth, and the propagation of information and opinions [, 2, 3]. The distinguishing features of these stochastic systems are that they model a large number of particles that live on a fixed lattice or graph, and that each particle is assigned a state that changes randomly at rates determined by the state of nearby particles. Here particles need not be atoms or molecules, but may represent such macroscopic entities as plants, computers, and people. Examples of interacting particle systems include the well-known Ising model, and also the contact process and voter model. This mathematical field of study is attracting the attention of engineers due to the emergence of large systems with locally-defined dynamics similar to interacting particle systems, such as packetswitched IP networks like the Internet, and more recently, wireless sensor networks. Traditionally, however, research on interacting particle systems has only answered analysis-type questions, such as determining the transient or steady-state behavior of a prescribed system. Our aim is to study these models with an engineering eye to answer design- and control-oriented questions, such as determining which system among a class of interacting particle systems has behavior that is closest to a specification, or what kind of control laws are appropriate for a particular interacting particle system. Answers to questions of this sort are required in order for interacting particle systems to impact the technologies mentioned above. With this general aim in mind, we consider a concrete optimization problem involving one particular interacting particle system, the contact process. The contact process is a Markov process used to model the spread of a population. We consider the finite, one-dimensional process, in which there are points in a line, each of which is in one of two states, occupied and vacant, at each time. An occupied point becomes vacant at rate, while a vacant point becomes occupied at rate λ times the number of occupied neighbors (0,, or 2), where λ, the reproduction rate, is a parameter. The idea is that on each occupied point lives a member of a population who survives for a random time that is exponentially distributed with mean, and who reproduces at the times of a Poisson process with rate 2λ, placing each offspring to its left (if the point is vacant) and to its right (if the point is vacant) with equal probability. This description makes it clear that the contact process can be viewed as a branching process with competition ; the progeny compete for space on the lattice. The process starts in the state in which every point is occupied. The state in which every point is vacant is absorbing, and it is reachable from every other state. Thus the primary question of interest is how long the process takes to reach this state. In the terminology of populations, the population eventually becomes extinct and we seek the distribution of the time it takes to do so. This analysis question was answered by Durrett and Liu [4] and Durrett and Schonmann [5] in the limit as tends to infinity. The answer is reproduced in the next section, following a more precise definition of the process. We consider an ensuing design question. Suppose the presence of the population is desirable and we wish to maximize its extinction time. To accomplish this, we vary λ from point to point. It is intuitively clear, and easy to prove using coupling techniques [2], that increasing the reproduction rate at a point increases the expected extinction time. We consider the problem of maximizing the extinction time subject to an upper bound on the average rate. In practice we expect to be large, so our precise objective is to maximize the asymptotic rate of growth of the extinction time with. This optimization problem has a natural description in terms of the population growth interpretation of the contact process. Consider a population that lives on a one-dimensional lattice, such as a row of bushes. We seek to maximize the longevity of this population by distributing a fixed quantity of fertilizer over the points. What then is the optimal strategy for distributing the fertilizer? The optimization problem arises in other contexts as well. Consider, for instance, the design of sensor networks. Suppose that in order to track a vehicle moving in the plane, we drop an array of radio-equipped sensors in a line near it. Each sensor detects a signal emitted by the vehicle and uses it to estimate the vehicle s bearing relative to the sensor. Periodically, the sensor broadcasts this information to a basestation, which uses the information received from all of the sensors to triangulate the position of the vehicle. The nodes broadcast asynchronously. Occasionally, the signal received by a sensor becomes too noisy for the sensor to make a meaningful estimate of the vehicle s bearing. We assume that once this occurs, the sensor is unable to reacquire the signal on its own. We assume, however, that a broadcast by one of the neighboring nodes contains enough information about the vehicle s position for the node to reacquire the signal and to continue tracking the vehicle. If we assume that a broadcast enables only one
2 of the node s neighbors to reacquire the signal, then we can model the randomness using a contact process, where the occupied points refer to the nodes that are tracking the vehicle. Eventually, then, the network will reach the state in which every node has lost the signal; the network designer seeks to maximize the time until this happens. Increasing a node s broadcast rate increases the power it consumes while it tracks the vehicle. etworks of this sort are power limited [7], so a rate constraint is natural. We arrive at our optimization problem. The most interesting feature of the homogeneous contact process is its phase transition: we will see that the extinction time is highly nonlinear in λ. There exists a constant, λ c, such that the process survives much longer if λ > λ c than if λ λ c. In our case, since we vary the λ-parameter over the process, we will see that different parts of the process can evolve in different phases. From a design standpoint, then, the contact process presents an unusual problem: the system has multiple phases, one of which is most desirable to us, and we would like as much of the process to operate in the preferred phase as the constraints allow. To clarify this point, we consider the same optimization problem for the simpler biased voter model. The finite biased voter model has a similar phase transition to the contact process but its simplicity allows us to more clearly expose how the phase transition affects the solution to the optimization problem. In the biased voter model, each point in {,..., } is viewed as a person who holds one of two opinions, say 0 and. A person with opinion 0 changes to opinion at rate λ times the number of neighbors with opinion, as in the contact process. But a person with opinion changes to opinion 0 at rate equal to the number of neighbors with opinion 0, whereas in the contact process the corresponding rate is regardless of the neighbors state. When determining the rates at the boundary points, and, we use the convention that persons 0 and + always have opinion 0. This process also has a single absorbing state, which is reachable from all other states, namely the state in which persons through all have opinion 0. We seek to maximize the hitting time to this state by varying λ from point to point, as with the contact process. Although we do not consider it here, the Ising model of magnetism also lends itself to an optimization problem of this kind. Consider fixed volumes of magnetic materials, with varying magnetic strengths. These materials are combined in some way, then magnetized to store one bit of information. If the total volume of the materials is one, how should one arrange the materials within, say, the unit cube to maximize the time until the magnetization is lost? The effect of design on two-dimensional site percolation has been studied by Carlson and Doyle [8, 9] in the context of power laws in complex systems. Robert, Carlson, and Doyle [0] consider, in the same context, the effect of design on a simple epidemic model in which infection spreads between three cells. Booth et al. [] consider the effect of design on two-dimensional continuum percolation in the context of the connectivity of wireless networks. The remainder of the paper is organized as follows. The next section contains the required background on the contact process, including the result due to Durrett and Liu [4] and Durrett and Schonmann [5] mentioned above. Section III contains our contact process results, and Section IV contains our voter model results. Some concluding remarks are made in Section V. II. BACKGROUD The finite, one-dimensional contact process of size and infection rate λ is defined as the Markov chain whose state space is This would be the case if they used directed antennae. 2 {,...,} and whose transition rates are q(a, A\{j}) =, if j A, q(a, A {j}) = λ A {j, j + }, if j / A, for A {,..., } and j {,..., }. Here denotes cardinality. For this process and all others defined in this paper, if B {,..., } with B A is not of the form A\{j} or A {j} for some integer j then q(a, B) = 0. One should interpret the state of the chain as the set of points that are currently occupied. This process is the finite analogue of the contact process on Z, which is the Markov process ξ t whose state space is the power set of Z and whose transition rates are given by () for A Z and j Z. It turns out that there exists a unique Markov process with these rates, although this is not clear a priori. See Liggett [] for a complete account. As in the finite case, the empty set is a trap for the infinite process. The process on Z differs, however, in that it can survive forever if the reproduction rate is sufficiently large. Specifically, the process exhibits the following phase transition [2]. Let ξt A denote the contact process on Z with initial state A Z. There exists λ c (0, ) such that if λ λ c then P (ξ {0} t for all t) = 0, but if λ > λ c then P (ξ {0} t for all t) > 0. Thus the behavior of the infinite process crucially depends on whether λ λ c or λ > λ c. If λ λ c, then the process started with a single occupied point becomes extinct with probability one, and we say that the process is subcritical if λ < λ c and critical if λ = λ c. If λ > λ c, then the process started with a single occupied point survives forever with positive probability, and we say that the process is supercritical. The exact value of λ c is not known rigorously, but simulations place it around.6 [3]. Loosely speaking, in the supercritical case, the population tends to spread because the tendency of its members to reproduce is stronger than their tendency to die. In the subcritical case, however, the population tends to contract because the tendency to reproduce is weaker than the tendency to die. See [, p. 283] for a mathematical formulation of this statement. Consider now the finite process of size, ζ t, with initial state {,..., }. Let σ be the extinction time of the process, i.e., () σ = inf{t 0 : ζ t = }. (2) The result due to Durrett and Liu [4] and Durrett and Schonmann [5], to which we alluded in the introduction, shows that the phase transition also appears in the finite process. Here and throughout, all logarithms have base e. Theorem ([4, 5]) If λ < λ c then as, σ log γ (λ) in probability. If λ > λ c then as, in probability. log σ γ2(λ) Here γ and γ 2 are deterministic functions of λ, which are defined using the infinite process. γ (λ) = lim t t γ 2(λ) = lim log P (ξ{0} t ) log P (τ < ), where τ = inf{t 0 : ξ {,...,} t = }. Both limits exist by subadditivity for all λ 0, but γ (λ) is positive if λ < λ c, while γ 2(λ)
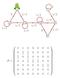
3 is positive if λ > λ c. o closed-form expression is known for either function. In words, Theorem says that if λ < λ c, then σ grows logarithmically with, whereas if λ > λ c, then σ grows exponentially with. When λ = λ c, Durrett, Schonmann, and Tanaka [6] show that σ grows polynomially with, but the correct power is unknown. We do not consider the critical process here. The intuition behind Theorem is the following. In the subcritical case, the tendency to reproduce is weaker than the tendency to die. Then for large, the extinction time is essentially the time it takes for all of the original members of the population to die out; reproduction can be neglected. That this gives logarithmic growth can be seen by inspecting the case λ = 0. Here σ is just the maximum of i.i.d. exponential random variables with mean one, so log σ / log in probability. In the supercritical case, the population tends to spread, so it becomes extinct only when all of the points die out simultaneously. The time that one must wait for events to occur simultaneously during parallel independent trails grows exponentially with. III. OPTIMIZATIO RESULTS We turn to the question posed in the introduction, namely how to vary the reproduction rate of the contact process to maximize the extinction time s asymptotic growth rate. To facilitate taking, we shall consider λ-profiles that are piecewise constant, defined as follows. We define a profile to be a triple (K, λ, α), where K is a natural number and λ and α are K-dimensional vectors with nonnegative elements (λ,..., λ K), and (α,..., α K) such that K αj =. We think of a profile as partitioning the unit interval into K partitions, the first of size α with reproduction rate λ, the second of size α 2 with reproduction rate λ 2, etc. The profile concept is useful because a profile induces an inhomogeneous contact process for each. To see how, fix, let β j = j i= αi for j =,..., K, define i j = β j, and let i 0 = 0. We will assume that is large enough that i j < i j+ for j = 0,..., K. Our inhomogeneous contact process is then the Markov chain whose state space is 2 {,...,}, and whose transition rates are q(a, A\{j}) =, if j A q(a, A {j}) = λ(j ) A {j } + λ(j + ) A {j + }, if j / A, for A {,..., } and j {,..., }. Here λ(j) = λ m where m satisfies i m < j i m if j {,..., }, and λ(0) = λ( + ) = 0. We term a process with transition rates given by (3) a piecewise-homogeneous contact process. We call a profile in which λ j < λ c for all j {,..., K} a subcritical profile, one in which λ j > λ c for all j {,..., K} a supercritical profile, and one in which λ j λ c for all j {,..., K} and λ j > λ c for some j {,..., K} a mixed profile. Before proceeding with the optimization problem, we must determine how the choice of the reproduction rates affects the growth rate of σ. The next three theorems generalize Theorem to piecewisehomogeneous contact processes. Consider a fixed profile and let σ be the extinction time of the piecewise-homogeneous process of size induced by this profile. Theorem 2 Let (K, λ, α) be a subcritical profile. Then in probability as. σ log γ (max(λ,..., λ K)) (3) C = {}, C 2 = {2}, C 3 = {3}, C 4 = {4, 5}, C 5 = {6}, C 6 = {7, 8}, C 7 = {9, 0}, D = {}, D 2 = {3}, D 3 = {6}, D 4 = {9, 0} Figure : A sample mixed profile. The supercritical partitions have their index placed above the line. The subcritical, below. The proof of this theorem and the subsequent ones can be found in the full version of this paper [2]. The intuition is that, in the subcritical case, the populations in each of the partitions tend to die out without spreading to the neighboring partitions, so the partitions essentially evolve independently, and σ is determined by the extinction times of the partitions with the maximum rate. In the supercritical case, the partitions interact significantly. Theorem 3 Let (K, λ, α) be a supercritical profile. Then log σ in probability as, and log E[σ ] K α jγ 2(λ j) α jγ 2(λ j). The idea here is that, if all of the partitions are supercritical, then any one of them, if left alive, will tend to spread to the others, so that the entire process dies out only when every partition dies out simultaneously. The time for the jth partition, evolving in isolation, to die out is exp(α jγ 2(λ j) + o()) by Theorem. Thus σ is ( K exp ). αjγ2(λj) + o() The exponent for mixed profiles is more difficult to determine, so we will only exhibit bounds on it that are tight enough to enable us to proceed with the optimization problem. Let F be the set of indices j such that i j separates sub- and supercritical partitions, F = {i {,..., K } : (λ i λ i+) < λ c < (λ i λ i+)}. ow M = F + is the number of aggregate partitions sets of partitions that are contiguous, entirely subcritical or supercritical, and maximal in that adding another partition either makes the set not contiguous or mixed sub- and supercritical. We denote these aggregate partitions by C j for j,..., M: C = {,..., inf F {K}} C j = {sup C j +,..., inf{i F : i > sup C j } {K}}. Let L be the number of aggregate partitions that are supercritical, so L = M/2 if λ > λ c, otherwise L = M/2. We call a C j consisting of supercritical partitions an island, and a C j consisting of subcritical partitions a sea. Let D j for j {,..., L} denote the islands, which are the C j s with even or odd indices depending on whether λ < λ c or λ > λ c, respectively. Figure shows an example. Theorem 4 Let (K, λ, α) be a mixed profile. Then P log σ < max α jγ 2(λ j) ɛ 0, i {,...,L} j D i L P log σ > α jγ 2(λ j) + ɛ 0, i= j D i
4 2 2 Figure 2: Two three-partition mixed profiles. for all ɛ > 0 as, and lim inf lim sup log E[σ ] log E[σ ] max i {,...,L} L i= 3 3 α jγ 2(λ j) j D i j D i α jγ 2(λ j). The difficulty leading to the incompleteness of this result is determining when the seas isolate the islands into separate processes. The lower and upper bounds in Theorem 4 correspond to two possible answers to this question, always and never. If the islands are isolated, the extinction time of the process is the extinction time of ( its longest-living island, giving an exponent of ) max i {,...,L} j D i α jγ 2(λ j). If the population can spread from one island to another, a process we call colonizing, then the process dies out only when all of the islands die out simultaneously. By the intuition following Theorem 3, this gives an exponent of ( L ) i= j D αjγ2(λj) i. We conjecture that the correct answer is sometimes ; whether a sea prevents two islands from colonizing depends on their sizes and reproduction rates. Consider the two profiles shown in Figure 2. In the first case, a wide subcritical partition separates two small supercritical ones. Our conjecture is that if all of the rates are sufficiently small, then the two supercritical partitions will not be able to colonize and σ will have exponent max(α γ 2(λ ), α 3γ 2(λ 3)). In the second case, a narrow subcritical partition separates two large supercritical ones. Our conjecture is that if all of the rates are sufficiently large, then the supercritical partitions will colonize, and σ will have exponent α γ 2(λ ) + α 3γ 2(λ 3). The full version of this paper contains a precise criterion for which of the two scenarios we expect to happen, shows how to extend the conjecture to more than three partitions, and contains some support for the conjecture. We also show in the full version of this paper that γ 2(λ) = 0 if λ λ c. Thus Theorem 4 asserts that ( K ) log σ P > α jγ 2(λ j) + ɛ 0, and lim sup log E[σ ] α jγ 2(λ j). (4) Also note that if there is a single island, then Theorem 4 gives the exact exponent. Theorems 2 and 4 together show that the piecewise-homogeneous process exhibits a similar phase transition to the homogeneous process, except that the relevant parameter is now the maximum of the K rates. That is, if all K rates are subcritical, then the extinction time grows logarithmically with, while if any of the rates are supercritical, then the extinction time grows exponentially with. In the context of our optimization problem, this shows that we can achieve exponential growth of σ with by making part of the process supercritical. This is significant since the constraint may prohibit us from making the entire process supercritical. Specifically, let λ 0 0 and η 0 be given. We interpret λ 0 as the nominal reproduction rate given to each point, and η as the additional reproduction rate that we may distribute over the population as desired. We seek a profile that maximizes the asymptotic growth rate of σ, subject to the constraint that λ j λ 0 for j =,..., K, and α jλ j λ 0 + η. (5) If λ 0 + η > 0, there are feasible profiles with supercritical partitions: simply make the supercritical partitions sufficiently small. By Theorem 4, it is then possible to achieve exponential growth of E[σ ] with. Since the case that λ 0 + η = 0 is not interesting, we shall seek to maximize lim inf (log E[σ ])/. This gives the following optimization problem. maximize over subject to lim inf (log E[σ ])/ K, λ, α K αjλj λ0 + η λ j λ 0 for j {,..., K}. Let R (λ 0, η) denote the supremum of lim inf(log E[σ ])/ over the set of feasible profiles. Let ˆγ λ 0 2 ( ) denote the concave hull of γ 2( ) on [λ 0, ), i.e., for x λ 0, { n } ˆγ λ 0 2 (x) = sup α jγ 2(λ j), where the supremum is over n, α, and λ such that λ j λ 0 for all j =,..., n, and n α jλ j = x. Theorem 5 R (λ 0, η) = ˆγ λ 0 2 (λ0 + η). Furthermore, R (λ 0, η) is achieved by a profile with K = 2. Here is the idea behind the proof. By (4), K lim inf (log E[σ ])/ α jγ 2(λ j) ˆγ λ 0 2 (λ 0 + η), which shows that R (λ 0, η) ˆγ λ 0 2 (λ0 + η). Carathéodory s Theorem [3, p. 55] and some continuity arguments that are supplied in the full version of this paper show that there exists α, α 2, λ, λ 2, such that min(λ, λ 2) λ 0, and α λ + α 2λ 2 λ 0 + η, α γ 2(λ ) + α 2γ 2(λ 2) = ˆγ λ 0 2 (λ 0 + η). Since a profile with K = 2 can have at most one supercritical island, Theorem 4 shows that for this profile, lim inf (log E[σ ])/ = αγ2(λ) + α2γ2(λ2) = ˆγλ 0 2 (λ 0 + η), which shows that R (λ 0, η) ˆγ λ 0 2 (λ0 + η) and that the optimum exponent is achieved by a profile with two rates. The intuition behind K = 2 is that we would like to make the entire process supercritical, but if λ 0 + η < λ c, then the constraint (6)
5 forbids us from doing so. The optimum growth rate is obtained, then, by making part of the process supercritical, and leaving the rest at λ 0. To understand this intuition better, suppose hypothetically that γ 2 is concave on (λ c, ). Then if λ 0 > λ c, so that the points are nominally supercritical, then ˆγ λ 0 2 = γ 2 on (λ 0, ) so R (λ 0, η) = γ 2(λ 0 + η), and an optimal profile would be a single partition with rate λ 0 + η. If λ 0 < λ c, there would exist λ > λ c such that ˆγ λ 0 2 (λ) = { γ2(λ ) λ λ 0 λ λ 0 if λ < λ γ 2(λ) if λ λ. In this case the points are nominally subcritical, so we must actively make them supercritical by increasing their rate. In doing so, we are confronted with a choice of allocating the rate to form a small supercritical region with a very high rate, or a large supercritical region with a relatively small rate. Evidently, λ plays a pivotal role in this trade-off: if λ 0 + η λ, then we would have ˆγ λ 0 2 (λ0 + η) = γ2(λ0 + η), and an optimal profile would be a single partition with rate λ 0 + η. If λ 0 + η < λ, then the optimal profile would consist of two partitions, one subcritical with rate λ 0 and one supercritical with rate λ. One might expect that γ 2 is concave on (λ c, ) since it is nondecreasing and O(log λ): if all points in {,..., } die out before reproducing, then τ {,...,} < so ( ) ( ) P τ {,...,} <, (8) + 2λ which gives γ 2(λ) log( + 2λ). But proving that γ 2 is concave on (λ c, ) is difficult, and in fact it might be false. Drawing upon conjectures from scaling theory, Durrett, Schonmann, and Tanaka [6] conjecture that lim λ λ c γ 2(λ) (λ λ c) α exists for some α >. If this is true, then γ 2 behaves as (λ λ c) α near λ c, and hence it is not concave on (λ c, ), since it is convex near λ c. Of course, it cannot be convex on the entire interval (λ c, ) due to (8). Since we are unable to resolve this conjecture, we cannot assert that the optimal exponent is achieved by profiles with at most one supercritical partition. To validate our intuition, therefore, we turn to the biased voter model. IV. BIASED VOTER MODEL RESULTS The finite, one-dimensional biased voter model of size is the the Markov chain whose state space is 2 {,...,} and whose transition rates are q(a, A\{j}) = (Z\A) {j, j + }, if j A q(a, A {j}) = λ A {j, j + }, if j / A, for A {,..., } and j {,..., }. Here one should interpret the state of the process as the set of persons that currently hold opinion. Due to the symmetry between the two opinions, the biased voter model is much simpler to analyze than the contact process. In particular, note that a point in state with two neighbors in state cannot change states, so if we start the process in state {,..., }, then the set of points in state is always contiguous, and we only need to keep track of the boundaries of this set. The boundaries, in fact, form independent random walks as long as the process is alive [4], and drift inward at rate and outward at rate λ. This fact simplifies the analysis and leads to nicer results, the first of which is the following analogue of Theorem, due to Durrett and Liu [4]. Consider the biased voter model of size, ζ t, with initial state {,..., }, and define σ as before by (2). (7) Theorem 6 ([4]) If λ < then as, σ 2( λ) in probability. If λ > then as, in probability. log σ log(λ) In the subcritical case, the boundaries drift inward at rate ( λ), and a weak law of large numbers argument shows that σ is /(2( λ)) + o(). In the supercritical case, the boundaries drift outward, and hence spend most of their time near and. But they make excursions toward the center, and the chance that the two boundaries meet in a short time interval is λ +o(). Standard arguments then show that σ is λ +o(). ote that for the biased voter model, λ c is simply, and unlike the contact process, the two limiting functions have simple expressions. Our definition of a profile remains the same, but now given the profile (K, λ, α), we consider the Markov chain with transitions rates q(a, A\{j}) = (Z\A) {j, j + } if j A q(a, A {j}) = λ(j ) A {j } + λ(j + ) A {j + } if j / A, for A {,..., } and j {,..., }. The analogue of Theorems 2 and 3 for the biased voter model is given by Theorem 7. Theorem 7 If (K, λ, α) is a profile such that λ j < for all j {,..., K}, then K σ α j 2( λ j) in probability as. If λ j > for all j {,..., K}, then log σ in probability as, and log E[σ ] K α j log(λ j) α j log(λ j). The intuition behind this result is the same as for the previous one. The only difference is that now the random walks that form the boundaries live in an inhomogeneous environment ; they drift at different rates in different partitions. Theorem 8 Theorem 4 holds for the biased voter model if we replace λ c with and γ 2(λ) with log λ. Determining the correct exponents for mixed sub- and supercritical profiles should be relatively easy for the biased voter model. We do not explore this here, however, because our interest in the biased voter model is its solution to the optimization problem, (6). Theorem 9 For the biased voter model, if λ 0 >, then R (λ 0, η) = log(λ 0 + η) is achieved by the profile (, λ 0 + η, ). If λ 0 <, let λ be the unique solution to λ0 = log λ λ that is greater than. If λ 0 + η > λ, then again R (λ 0, η) = log(λ 0 + η). If λ 0 + η < λ, then R (λ 0, η) = η/λ is achieved by the profile (2, (λ, λ 0), (α, α)), where α = η/(λ λ 0).
6 The proof is similar to the proof of Theorem 5 for the contact process. Using the approach that we sketched after that theorem, one can show that if f λ 0 (λ) is the concave hull of log on [λ 0, ), then R (λ 0, η) = f λ 0 (λ 0 + η) and is achieved by a profile with K = 2. The remainder of the result follows by observing that the expressions given for the optimal exponent are simply expressions for f λ 0, and the optimal profiles are the ones that achieve the hull. The intuition behind this result is the same as that following (7). If λ 0 >, or λ 0 < but λ 0 + η is large, then the concavity of log implies that the additional rate has the greatest effect when it is spread uniformly over the population. If λ 0 < and λ 0 + η is relatively small, then the trade-off between the size and rate of the supercritical partition becomes significant, and the optimal profile is to split the population into sub- and supercritical parts, and give the subcritical part rate λ 0, and the supercritical part rate λ. V. COCLUDIG REMARKS We considered a natural optimization problem based on the contact process as a first step toward a more general understanding of how to design and control interacting particle systems. This understanding is absent from the interacting particle systems literature, but it is required to put the theory to use in the design of practical systems. Our optimization problem highlighted how a phase transition, a common feature of many interacting particle systems, affects the design process. Many challenges remain. The theoretical challenges are to answer similar questions for more complicated models, such as the contact process in higher dimensions and the Ising model, and to address closed-loop control questions in place of the open-loop design problem considered here. A simple follow-up question to the one asked here is which profile minimizes the growth rate of the extinction time? If the conjecture that a sufficiently large subcritical partition between two supercritical partitions isolates them into independent processes is correct, then minimizing the hitting time would likely involve placing large amounts of rate in small regions that are separated by subcritical firebreaks. The practical challenges are related to modeling. One must determine if interacting particle-type models are appropriate for physical systems such as sensor networks and the Internet, and if so what the exact model should be. The potential benefit to this endeavor is the opportunity to use the rich set of tools that have been developed to study interacting particles to study these physical systems. REFERECES [] T. M. Liggett, Interacting Particle Systems, Springer, ew York, 985. [2] T. M. Liggett, Stochastic Interacting Systems: Contact, Voter, and Exclusion Processes, Springer, ew York, 999. [3] R. Durrett, Lecture otes on Particle Systems and Percolation, Wadsworth, Pacific Grove, 988. [4] R. Durrett and X.-F. Liu, The Contact Process on a Finite Set, The Annals of Probability, vol. 6, no. 3, 58 73, 988. [5] R. Durrett and R. H. Schonmann, The Contact Process on a Finite Set II, The Annals of Probability, vol. 6, no. 4, , 988. [6] R. Durrett, R. H. Schonmann, and. I. Tanaka, The Contact Process on a Finite Set III. The Critical Case, The Annals of Probability, vol. 7, no. 4, , 989. [7] J. M. Kahn, R. H. Katz, and K. S. J. Pister, Emerging Challenges: Mobile etworking for Smart Dust, J. of Commun. and etworks, vol. 2, no. 3, 88 96, [8] J. M. Carlson and J. Doyle, Highly Optimized Tolerance: A Mechanism for Power Laws in Designed Systems, Physical Review E, vol. 60, no. 2, 42 27, 999. [9] J. M. Carlson and J. Doyle, Highly Optimized Tolerance: Robustness and Design in Complex Systems, Physical Review Letters, vol. 84, no., , [0] C. Robert, J. M. Carlson, and J. Doyle, Highly Optimized Tolerance in Epidemic Models Incorporating Local Optimization and Regrowth, Physical Review E, vol. 63, no. 5, 05622, 200. [] L. Booth, J. Bruck, M. Franceschetti, and R. Meester, Covering Algorithms, Continuum Percolation, and the Geometry of Wireless etworks, Preprint. [2] A. B. Wagner and V. Anantharam, Designing a Contact Process: The Piecewise-Homogeneous Process on a Finite Set with Applications, In Preparation. [3] R. T. Rockafellar, Convex Analysis, Princeton University Press, Princeton, 970. ACKOWLEDGMETS This research was supported by DARPA Grants F and C-8062, by Grant from the Office of aval Research, and by Grant SBR and a Graduate Research Fellowship from the ational Science Foundation. The authors also wish to thank R. Durrett and R. Schonmann for helpful electronic mail correspondence.
Random graphs: Random geometric graphs
 Random graphs: Random geometric graphs Mathew Penrose (University of Bath) Oberwolfach workshop Stochastic analysis for Poisson point processes February 2013 athew Penrose (Bath), Oberwolfach February
Random graphs: Random geometric graphs Mathew Penrose (University of Bath) Oberwolfach workshop Stochastic analysis for Poisson point processes February 2013 athew Penrose (Bath), Oberwolfach February
Modern Discrete Probability Branching processes
 Modern Discrete Probability IV - Branching processes Review Sébastien Roch UW Madison Mathematics November 15, 2014 1 Basic definitions 2 3 4 Galton-Watson branching processes I Definition A Galton-Watson
Modern Discrete Probability IV - Branching processes Review Sébastien Roch UW Madison Mathematics November 15, 2014 1 Basic definitions 2 3 4 Galton-Watson branching processes I Definition A Galton-Watson
Erdős-Renyi random graphs basics
 Erdős-Renyi random graphs basics Nathanaël Berestycki U.B.C. - class on percolation We take n vertices and a number p = p(n) with < p < 1. Let G(n, p(n)) be the graph such that there is an edge between
Erdős-Renyi random graphs basics Nathanaël Berestycki U.B.C. - class on percolation We take n vertices and a number p = p(n) with < p < 1. Let G(n, p(n)) be the graph such that there is an edge between
BRANCHING PROCESSES 1. GALTON-WATSON PROCESSES
 BRANCHING PROCESSES 1. GALTON-WATSON PROCESSES Galton-Watson processes were introduced by Francis Galton in 1889 as a simple mathematical model for the propagation of family names. They were reinvented
BRANCHING PROCESSES 1. GALTON-WATSON PROCESSES Galton-Watson processes were introduced by Francis Galton in 1889 as a simple mathematical model for the propagation of family names. They were reinvented
Random Geometric Graphs
 Random Geometric Graphs Mathew D. Penrose University of Bath, UK Networks: stochastic models for populations and epidemics ICMS, Edinburgh September 2011 1 MODELS of RANDOM GRAPHS Erdos-Renyi G(n, p):
Random Geometric Graphs Mathew D. Penrose University of Bath, UK Networks: stochastic models for populations and epidemics ICMS, Edinburgh September 2011 1 MODELS of RANDOM GRAPHS Erdos-Renyi G(n, p):
4: The Pandemic process
 4: The Pandemic process David Aldous July 12, 2012 (repeat of previous slide) Background meeting model with rates ν. Model: Pandemic Initially one agent is infected. Whenever an infected agent meets another
4: The Pandemic process David Aldous July 12, 2012 (repeat of previous slide) Background meeting model with rates ν. Model: Pandemic Initially one agent is infected. Whenever an infected agent meets another
Latent voter model on random regular graphs
 Latent voter model on random regular graphs Shirshendu Chatterjee Cornell University (visiting Duke U.) Work in progress with Rick Durrett April 25, 2011 Outline Definition of voter model and duality with
Latent voter model on random regular graphs Shirshendu Chatterjee Cornell University (visiting Duke U.) Work in progress with Rick Durrett April 25, 2011 Outline Definition of voter model and duality with
arxiv: v1 [math.pr] 1 Jan 2013
![arxiv: v1 [math.pr] 1 Jan 2013 arxiv: v1 [math.pr] 1 Jan 2013](/thumbs/92/108996348.jpg) The role of dispersal in interacting patches subject to an Allee effect arxiv:1301.0125v1 [math.pr] 1 Jan 2013 1. Introduction N. Lanchier Abstract This article is concerned with a stochastic multi-patch
The role of dispersal in interacting patches subject to an Allee effect arxiv:1301.0125v1 [math.pr] 1 Jan 2013 1. Introduction N. Lanchier Abstract This article is concerned with a stochastic multi-patch
3. The Voter Model. David Aldous. June 20, 2012
 3. The Voter Model David Aldous June 20, 2012 We now move on to the voter model, which (compared to the averaging model) has a more substantial literature in the finite setting, so what s written here
3. The Voter Model David Aldous June 20, 2012 We now move on to the voter model, which (compared to the averaging model) has a more substantial literature in the finite setting, so what s written here
Any live cell with less than 2 live neighbours dies. Any live cell with 2 or 3 live neighbours lives on to the next step.
 2. Cellular automata, and the SIRS model In this Section we consider an important set of models used in computer simulations, which are called cellular automata (these are very similar to the so-called
2. Cellular automata, and the SIRS model In this Section we consider an important set of models used in computer simulations, which are called cellular automata (these are very similar to the so-called
Three Disguises of 1 x = e λx
 Three Disguises of 1 x = e λx Chathuri Karunarathna Mudiyanselage Rabi K.C. Winfried Just Department of Mathematics, Ohio University Mathematical Biology and Dynamical Systems Seminar Ohio University November
Three Disguises of 1 x = e λx Chathuri Karunarathna Mudiyanselage Rabi K.C. Winfried Just Department of Mathematics, Ohio University Mathematical Biology and Dynamical Systems Seminar Ohio University November
Lecture 9 Classification of States
 Lecture 9: Classification of States of 27 Course: M32K Intro to Stochastic Processes Term: Fall 204 Instructor: Gordan Zitkovic Lecture 9 Classification of States There will be a lot of definitions and
Lecture 9: Classification of States of 27 Course: M32K Intro to Stochastic Processes Term: Fall 204 Instructor: Gordan Zitkovic Lecture 9 Classification of States There will be a lot of definitions and
Revisiting the Contact Process
 Revisiting the Contact Process Maria Eulália Vares Universidade Federal do Rio de Janeiro World Meeting for Women in Mathematics - July 31, 2018 The classical contact process G = (V,E) graph, locally finite.
Revisiting the Contact Process Maria Eulália Vares Universidade Federal do Rio de Janeiro World Meeting for Women in Mathematics - July 31, 2018 The classical contact process G = (V,E) graph, locally finite.
Lecture 06 01/31/ Proofs for emergence of giant component
 M375T/M396C: Topics in Complex Networks Spring 2013 Lecture 06 01/31/13 Lecturer: Ravi Srinivasan Scribe: Tianran Geng 6.1 Proofs for emergence of giant component We now sketch the main ideas underlying
M375T/M396C: Topics in Complex Networks Spring 2013 Lecture 06 01/31/13 Lecturer: Ravi Srinivasan Scribe: Tianran Geng 6.1 Proofs for emergence of giant component We now sketch the main ideas underlying
Counting independent sets up to the tree threshold
 Counting independent sets up to the tree threshold Dror Weitz March 16, 2006 Abstract We consider the problem of approximately counting/sampling weighted independent sets of a graph G with activity λ,
Counting independent sets up to the tree threshold Dror Weitz March 16, 2006 Abstract We consider the problem of approximately counting/sampling weighted independent sets of a graph G with activity λ,
w i w j = w i k w k i 1/(β 1) κ β 1 β 2 n(β 2)/(β 1) wi 2 κ 2 i 2/(β 1) κ 2 β 1 β 3 n(β 3)/(β 1) (2.2.1) (β 2) 2 β 3 n 1/(β 1) = d
 38 2.2 Chung-Lu model This model is specified by a collection of weights w =(w 1,...,w n ) that represent the expected degree sequence. The probability of an edge between i to is w i w / k w k. They allow
38 2.2 Chung-Lu model This model is specified by a collection of weights w =(w 1,...,w n ) that represent the expected degree sequence. The probability of an edge between i to is w i w / k w k. They allow
Hitting Probabilities
 Stat25B: Probability Theory (Spring 23) Lecture: 2 Hitting Probabilities Lecturer: James W. Pitman Scribe: Brian Milch 2. Hitting probabilities Consider a Markov chain with a countable state space S and
Stat25B: Probability Theory (Spring 23) Lecture: 2 Hitting Probabilities Lecturer: James W. Pitman Scribe: Brian Milch 2. Hitting probabilities Consider a Markov chain with a countable state space S and
2. Transience and Recurrence
 Virtual Laboratories > 15. Markov Chains > 1 2 3 4 5 6 7 8 9 10 11 12 2. Transience and Recurrence The study of Markov chains, particularly the limiting behavior, depends critically on the random times
Virtual Laboratories > 15. Markov Chains > 1 2 3 4 5 6 7 8 9 10 11 12 2. Transience and Recurrence The study of Markov chains, particularly the limiting behavior, depends critically on the random times
1 Mechanistic and generative models of network structure
 1 Mechanistic and generative models of network structure There are many models of network structure, and these largely can be divided into two classes: mechanistic models and generative or probabilistic
1 Mechanistic and generative models of network structure There are many models of network structure, and these largely can be divided into two classes: mechanistic models and generative or probabilistic
EXISTENCE AND UNIQUENESS OF INFINITE COMPONENTS IN GENERIC RIGIDITY PERCOLATION 1. By Alexander E. Holroyd University of Cambridge
 The Annals of Applied Probability 1998, Vol. 8, No. 3, 944 973 EXISTENCE AND UNIQUENESS OF INFINITE COMPONENTS IN GENERIC RIGIDITY PERCOLATION 1 By Alexander E. Holroyd University of Cambridge We consider
The Annals of Applied Probability 1998, Vol. 8, No. 3, 944 973 EXISTENCE AND UNIQUENESS OF INFINITE COMPONENTS IN GENERIC RIGIDITY PERCOLATION 1 By Alexander E. Holroyd University of Cambridge We consider
WXML Final Report: Chinese Restaurant Process
 WXML Final Report: Chinese Restaurant Process Dr. Noah Forman, Gerandy Brito, Alex Forney, Yiruey Chou, Chengning Li Spring 2017 1 Introduction The Chinese Restaurant Process (CRP) generates random partitions
WXML Final Report: Chinese Restaurant Process Dr. Noah Forman, Gerandy Brito, Alex Forney, Yiruey Chou, Chengning Li Spring 2017 1 Introduction The Chinese Restaurant Process (CRP) generates random partitions
The first bound is the strongest, the other two bounds are often easier to state and compute. Proof: Applying Markov's inequality, for any >0 we have
 The first bound is the strongest, the other two bounds are often easier to state and compute Proof: Applying Markov's inequality, for any >0 we have Pr (1 + ) = Pr For any >0, we can set = ln 1+ (4.4.1):
The first bound is the strongest, the other two bounds are often easier to state and compute Proof: Applying Markov's inequality, for any >0 we have Pr (1 + ) = Pr For any >0, we can set = ln 1+ (4.4.1):
The parabolic Anderson model on Z d with time-dependent potential: Frank s works
 Weierstrass Institute for Applied Analysis and Stochastics The parabolic Anderson model on Z d with time-dependent potential: Frank s works Based on Frank s works 2006 2016 jointly with Dirk Erhard (Warwick),
Weierstrass Institute for Applied Analysis and Stochastics The parabolic Anderson model on Z d with time-dependent potential: Frank s works Based on Frank s works 2006 2016 jointly with Dirk Erhard (Warwick),
Epidemics in Complex Networks and Phase Transitions
 Master M2 Sciences de la Matière ENS de Lyon 2015-2016 Phase Transitions and Critical Phenomena Epidemics in Complex Networks and Phase Transitions Jordan Cambe January 13, 2016 Abstract Spreading phenomena
Master M2 Sciences de la Matière ENS de Lyon 2015-2016 Phase Transitions and Critical Phenomena Epidemics in Complex Networks and Phase Transitions Jordan Cambe January 13, 2016 Abstract Spreading phenomena
The tail does not determine the size of the giant
 The tail does not determine the size of the giant arxiv:1710.01208v2 [math.pr] 20 Jun 2018 Maria Deijfen Sebastian Rosengren Pieter Trapman June 2018 Abstract The size of the giant component in the configuration
The tail does not determine the size of the giant arxiv:1710.01208v2 [math.pr] 20 Jun 2018 Maria Deijfen Sebastian Rosengren Pieter Trapman June 2018 Abstract The size of the giant component in the configuration
RECENT RESULTS FOR SUPERCRITICAL CONTROLLED BRANCHING PROCESSES WITH CONTROL RANDOM FUNCTIONS
 Pliska Stud. Math. Bulgar. 16 (2004), 43-54 STUDIA MATHEMATICA BULGARICA RECENT RESULTS FOR SUPERCRITICAL CONTROLLED BRANCHING PROCESSES WITH CONTROL RANDOM FUNCTIONS Miguel González, Manuel Molina, Inés
Pliska Stud. Math. Bulgar. 16 (2004), 43-54 STUDIA MATHEMATICA BULGARICA RECENT RESULTS FOR SUPERCRITICAL CONTROLLED BRANCHING PROCESSES WITH CONTROL RANDOM FUNCTIONS Miguel González, Manuel Molina, Inés
Selecting Efficient Correlated Equilibria Through Distributed Learning. Jason R. Marden
 1 Selecting Efficient Correlated Equilibria Through Distributed Learning Jason R. Marden Abstract A learning rule is completely uncoupled if each player s behavior is conditioned only on his own realized
1 Selecting Efficient Correlated Equilibria Through Distributed Learning Jason R. Marden Abstract A learning rule is completely uncoupled if each player s behavior is conditioned only on his own realized
Markov Chains and Pandemics
 Markov Chains and Pandemics Caleb Dedmore and Brad Smith December 8, 2016 Page 1 of 16 Abstract Markov Chain Theory is a powerful tool used in statistical analysis to make predictions about future events
Markov Chains and Pandemics Caleb Dedmore and Brad Smith December 8, 2016 Page 1 of 16 Abstract Markov Chain Theory is a powerful tool used in statistical analysis to make predictions about future events
IN THIS paper we investigate the diagnosability of stochastic
 476 IEEE TRANSACTIONS ON AUTOMATIC CONTROL, VOL 50, NO 4, APRIL 2005 Diagnosability of Stochastic Discrete-Event Systems David Thorsley and Demosthenis Teneketzis, Fellow, IEEE Abstract We investigate
476 IEEE TRANSACTIONS ON AUTOMATIC CONTROL, VOL 50, NO 4, APRIL 2005 Diagnosability of Stochastic Discrete-Event Systems David Thorsley and Demosthenis Teneketzis, Fellow, IEEE Abstract We investigate
Ω = e E d {0, 1} θ(p) = P( C = ) So θ(p) is the probability that the origin belongs to an infinite cluster. It is trivial that.
 2 Percolation There is a vast literature on percolation. For the reader who wants more than we give here, there is an entire book: Percolation, by Geoffrey Grimmett. A good account of the recent spectacular
2 Percolation There is a vast literature on percolation. For the reader who wants more than we give here, there is an entire book: Percolation, by Geoffrey Grimmett. A good account of the recent spectacular
Evolutionary dynamics of cancer: A spatial model of cancer initiation
 Evolutionary dynamics of cancer: A spatial model of cancer initiation Jasmine Foo University of Minnesota School of Mathematics May 8, 2014 Collaborators Rick Durrett Kevin Leder Marc Ryser Next talk by
Evolutionary dynamics of cancer: A spatial model of cancer initiation Jasmine Foo University of Minnesota School of Mathematics May 8, 2014 Collaborators Rick Durrett Kevin Leder Marc Ryser Next talk by
Resistance Growth of Branching Random Networks
 Peking University Oct.25, 2018, Chengdu Joint work with Yueyun Hu (U. Paris 13) and Shen Lin (U. Paris 6), supported by NSFC Grant No. 11528101 (2016-2017) for Research Cooperation with Oversea Investigators
Peking University Oct.25, 2018, Chengdu Joint work with Yueyun Hu (U. Paris 13) and Shen Lin (U. Paris 6), supported by NSFC Grant No. 11528101 (2016-2017) for Research Cooperation with Oversea Investigators
Introduction to Probability
 LECTURE NOTES Course 6.041-6.431 M.I.T. FALL 2000 Introduction to Probability Dimitri P. Bertsekas and John N. Tsitsiklis Professors of Electrical Engineering and Computer Science Massachusetts Institute
LECTURE NOTES Course 6.041-6.431 M.I.T. FALL 2000 Introduction to Probability Dimitri P. Bertsekas and John N. Tsitsiklis Professors of Electrical Engineering and Computer Science Massachusetts Institute
Some rigorous results for the stacked contact process
 ALEA, Lat. Am. J.Probab. Math. Stat. 13 (1), 193 222(2016) Some rigorous results for the stacked contact process Nicolas Lanchier and Yuan Zhang School of Mathematical and Statistical Sciences, Arizona
ALEA, Lat. Am. J.Probab. Math. Stat. 13 (1), 193 222(2016) Some rigorous results for the stacked contact process Nicolas Lanchier and Yuan Zhang School of Mathematical and Statistical Sciences, Arizona
Stochastic Processes
 Stochastic Processes 8.445 MIT, fall 20 Mid Term Exam Solutions October 27, 20 Your Name: Alberto De Sole Exercise Max Grade Grade 5 5 2 5 5 3 5 5 4 5 5 5 5 5 6 5 5 Total 30 30 Problem :. True / False
Stochastic Processes 8.445 MIT, fall 20 Mid Term Exam Solutions October 27, 20 Your Name: Alberto De Sole Exercise Max Grade Grade 5 5 2 5 5 3 5 5 4 5 5 5 5 5 6 5 5 Total 30 30 Problem :. True / False
CONTACT PROCESS WITH DESTRUCTION OF CUBES AND HYPERPLANES: FOREST FIRES VERSUS TORNADOES
 J. Appl. Prob. 48, 352 365 (2011) Printed in England Applied Probability Trust 2011 CONTACT PROCESS WITH DESTRUCTION OF CUBES AND HYPERPLANES: FOREST FIRES VERSUS TORNADOES N. LANCHIER, Arizona State University
J. Appl. Prob. 48, 352 365 (2011) Printed in England Applied Probability Trust 2011 CONTACT PROCESS WITH DESTRUCTION OF CUBES AND HYPERPLANES: FOREST FIRES VERSUS TORNADOES N. LANCHIER, Arizona State University
6 Markov Chain Monte Carlo (MCMC)
 6 Markov Chain Monte Carlo (MCMC) The underlying idea in MCMC is to replace the iid samples of basic MC methods, with dependent samples from an ergodic Markov chain, whose limiting (stationary) distribution
6 Markov Chain Monte Carlo (MCMC) The underlying idea in MCMC is to replace the iid samples of basic MC methods, with dependent samples from an ergodic Markov chain, whose limiting (stationary) distribution
MATH 56A: STOCHASTIC PROCESSES CHAPTER 2
 MATH 56A: STOCHASTIC PROCESSES CHAPTER 2 2. Countable Markov Chains I started Chapter 2 which talks about Markov chains with a countably infinite number of states. I did my favorite example which is on
MATH 56A: STOCHASTIC PROCESSES CHAPTER 2 2. Countable Markov Chains I started Chapter 2 which talks about Markov chains with a countably infinite number of states. I did my favorite example which is on
Problems on Evolutionary dynamics
 Problems on Evolutionary dynamics Doctoral Programme in Physics José A. Cuesta Lausanne, June 10 13, 2014 Replication 1. Consider the Galton-Watson process defined by the offspring distribution p 0 =
Problems on Evolutionary dynamics Doctoral Programme in Physics José A. Cuesta Lausanne, June 10 13, 2014 Replication 1. Consider the Galton-Watson process defined by the offspring distribution p 0 =
Operations Research Letters. Instability of FIFO in a simple queueing system with arbitrarily low loads
 Operations Research Letters 37 (2009) 312 316 Contents lists available at ScienceDirect Operations Research Letters journal homepage: www.elsevier.com/locate/orl Instability of FIFO in a simple queueing
Operations Research Letters 37 (2009) 312 316 Contents lists available at ScienceDirect Operations Research Letters journal homepage: www.elsevier.com/locate/orl Instability of FIFO in a simple queueing
Stochastic modelling of epidemic spread
 Stochastic modelling of epidemic spread Julien Arino Centre for Research on Inner City Health St Michael s Hospital Toronto On leave from Department of Mathematics University of Manitoba Julien Arino@umanitoba.ca
Stochastic modelling of epidemic spread Julien Arino Centre for Research on Inner City Health St Michael s Hospital Toronto On leave from Department of Mathematics University of Manitoba Julien Arino@umanitoba.ca
Lecture 20 : Markov Chains
 CSCI 3560 Probability and Computing Instructor: Bogdan Chlebus Lecture 0 : Markov Chains We consider stochastic processes. A process represents a system that evolves through incremental changes called
CSCI 3560 Probability and Computing Instructor: Bogdan Chlebus Lecture 0 : Markov Chains We consider stochastic processes. A process represents a system that evolves through incremental changes called
Lecture 11: Introduction to Markov Chains. Copyright G. Caire (Sample Lectures) 321
 Lecture 11: Introduction to Markov Chains Copyright G. Caire (Sample Lectures) 321 Discrete-time random processes A sequence of RVs indexed by a variable n 2 {0, 1, 2,...} forms a discretetime random process
Lecture 11: Introduction to Markov Chains Copyright G. Caire (Sample Lectures) 321 Discrete-time random processes A sequence of RVs indexed by a variable n 2 {0, 1, 2,...} forms a discretetime random process
1/2 1/2 1/4 1/4 8 1/2 1/2 1/2 1/2 8 1/2 6 P =
 / 7 8 / / / /4 4 5 / /4 / 8 / 6 P = 0 0 0 0 0 0 0 0 0 0 4 0 0 0 0 0 0 0 0 4 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 Andrei Andreevich Markov (856 9) In Example. 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 P (n) = 0
/ 7 8 / / / /4 4 5 / /4 / 8 / 6 P = 0 0 0 0 0 0 0 0 0 0 4 0 0 0 0 0 0 0 0 4 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 Andrei Andreevich Markov (856 9) In Example. 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 P (n) = 0
Distributionally Robust Discrete Optimization with Entropic Value-at-Risk
 Distributionally Robust Discrete Optimization with Entropic Value-at-Risk Daniel Zhuoyu Long Department of SEEM, The Chinese University of Hong Kong, zylong@se.cuhk.edu.hk Jin Qi NUS Business School, National
Distributionally Robust Discrete Optimization with Entropic Value-at-Risk Daniel Zhuoyu Long Department of SEEM, The Chinese University of Hong Kong, zylong@se.cuhk.edu.hk Jin Qi NUS Business School, National
Random Geometric Graphs
 Random Geometric Graphs Mathew D. Penrose University of Bath, UK SAMBa Symposium (Talk 2) University of Bath November 2014 1 MODELS of RANDOM GRAPHS Erdos-Renyi G(n, p): start with the complete n-graph,
Random Geometric Graphs Mathew D. Penrose University of Bath, UK SAMBa Symposium (Talk 2) University of Bath November 2014 1 MODELS of RANDOM GRAPHS Erdos-Renyi G(n, p): start with the complete n-graph,
Application: Bucket Sort
 5.2.2. Application: Bucket Sort Bucket sort breaks the log) lower bound for standard comparison-based sorting, under certain assumptions on the input We want to sort a set of =2 integers chosen I+U@R from
5.2.2. Application: Bucket Sort Bucket sort breaks the log) lower bound for standard comparison-based sorting, under certain assumptions on the input We want to sort a set of =2 integers chosen I+U@R from
The range of tree-indexed random walk
 The range of tree-indexed random walk Jean-François Le Gall, Shen Lin Institut universitaire de France et Université Paris-Sud Orsay Erdös Centennial Conference July 2013 Jean-François Le Gall (Université
The range of tree-indexed random walk Jean-François Le Gall, Shen Lin Institut universitaire de France et Université Paris-Sud Orsay Erdös Centennial Conference July 2013 Jean-François Le Gall (Université
Lecture 5. If we interpret the index n 0 as time, then a Markov chain simply requires that the future depends only on the present and not on the past.
 1 Markov chain: definition Lecture 5 Definition 1.1 Markov chain] A sequence of random variables (X n ) n 0 taking values in a measurable state space (S, S) is called a (discrete time) Markov chain, if
1 Markov chain: definition Lecture 5 Definition 1.1 Markov chain] A sequence of random variables (X n ) n 0 taking values in a measurable state space (S, S) is called a (discrete time) Markov chain, if
MIXING TIMES OF RANDOM WALKS ON DYNAMIC CONFIGURATION MODELS
 MIXING TIMES OF RANDOM WALKS ON DYNAMIC CONFIGURATION MODELS Frank den Hollander Leiden University, The Netherlands New Results and Challenges with RWDRE, 11 13 January 2017, Heilbronn Institute for Mathematical
MIXING TIMES OF RANDOM WALKS ON DYNAMIC CONFIGURATION MODELS Frank den Hollander Leiden University, The Netherlands New Results and Challenges with RWDRE, 11 13 January 2017, Heilbronn Institute for Mathematical
Recap. Probability, stochastic processes, Markov chains. ELEC-C7210 Modeling and analysis of communication networks
 Recap Probability, stochastic processes, Markov chains ELEC-C7210 Modeling and analysis of communication networks 1 Recap: Probability theory important distributions Discrete distributions Geometric distribution
Recap Probability, stochastic processes, Markov chains ELEC-C7210 Modeling and analysis of communication networks 1 Recap: Probability theory important distributions Discrete distributions Geometric distribution
arxiv:math/ v1 [math.pr] 6 Jun 2003
![arxiv:math/ v1 [math.pr] 6 Jun 2003 arxiv:math/ v1 [math.pr] 6 Jun 2003](/thumbs/95/123545930.jpg) ECOLOGICAL SUCCESSION MODEL By Nicolas Lanchier Université de Rouen arxiv:math/0306113v1 [math.pr] 6 Jun 003 Abstract We introduce in this paper a new interacting particle system intended to model an example
ECOLOGICAL SUCCESSION MODEL By Nicolas Lanchier Université de Rouen arxiv:math/0306113v1 [math.pr] 6 Jun 003 Abstract We introduce in this paper a new interacting particle system intended to model an example
A mathematical model for a copolymer in an emulsion
 J Math Chem (2010) 48:83 94 DOI 10.1007/s10910-009-9564-y ORIGINAL PAPER A mathematical model for a copolymer in an emulsion F. den Hollander N. Pétrélis Received: 3 June 2007 / Accepted: 22 April 2009
J Math Chem (2010) 48:83 94 DOI 10.1007/s10910-009-9564-y ORIGINAL PAPER A mathematical model for a copolymer in an emulsion F. den Hollander N. Pétrélis Received: 3 June 2007 / Accepted: 22 April 2009
A TWO-SPECIES COMPETITION MODEL ON Z D
 A TWO-SPECIES COMPETITION MODEL ON Z D GEORGE KORDZAKHIA AND STEVEN P. LALLEY Abstract. We consider a two-type stochastic competition model on the integer lattice Z d. The model describes the space evolution
A TWO-SPECIES COMPETITION MODEL ON Z D GEORGE KORDZAKHIA AND STEVEN P. LALLEY Abstract. We consider a two-type stochastic competition model on the integer lattice Z d. The model describes the space evolution
Oberwolfach workshop on Combinatorics and Probability
 Apr 2009 Oberwolfach workshop on Combinatorics and Probability 1 Describes a sharp transition in the convergence of finite ergodic Markov chains to stationarity. Steady convergence it takes a while to
Apr 2009 Oberwolfach workshop on Combinatorics and Probability 1 Describes a sharp transition in the convergence of finite ergodic Markov chains to stationarity. Steady convergence it takes a while to
Limit shapes outside the percolation cone
 jointly with Tuca Auffinger and Mike Hochman Princeton University July 14, 2011 Definitions We consider first-passage percolation on the square lattice Z 2. x γ - We place i.i.d. non-negative passage times
jointly with Tuca Auffinger and Mike Hochman Princeton University July 14, 2011 Definitions We consider first-passage percolation on the square lattice Z 2. x γ - We place i.i.d. non-negative passage times
Stability of the two queue system
 Stability of the two queue system Iain M. MacPhee and Lisa J. Müller University of Durham Department of Mathematical Science Durham, DH1 3LE, UK (e-mail: i.m.macphee@durham.ac.uk, l.j.muller@durham.ac.uk)
Stability of the two queue system Iain M. MacPhee and Lisa J. Müller University of Durham Department of Mathematical Science Durham, DH1 3LE, UK (e-mail: i.m.macphee@durham.ac.uk, l.j.muller@durham.ac.uk)
On a Form of Coordinate Percolation
 On a Form of Coordinate Percolation Elizabeth R. Moseman and Peter Winkler July 31, 008 Abstract Let a i, b i, i = 0, 1,,... be drawn uniformly and independently from the unit interval, and let t be a
On a Form of Coordinate Percolation Elizabeth R. Moseman and Peter Winkler July 31, 008 Abstract Let a i, b i, i = 0, 1,,... be drawn uniformly and independently from the unit interval, and let t be a
Other properties of M M 1
 Other properties of M M 1 Přemysl Bejda premyslbejda@gmail.com 2012 Contents 1 Reflected Lévy Process 2 Time dependent properties of M M 1 3 Waiting times and queue disciplines in M M 1 Contents 1 Reflected
Other properties of M M 1 Přemysl Bejda premyslbejda@gmail.com 2012 Contents 1 Reflected Lévy Process 2 Time dependent properties of M M 1 3 Waiting times and queue disciplines in M M 1 Contents 1 Reflected
Asymptotics for Polling Models with Limited Service Policies
 Asymptotics for Polling Models with Limited Service Policies Woojin Chang School of Industrial and Systems Engineering Georgia Institute of Technology Atlanta, GA 30332-0205 USA Douglas G. Down Department
Asymptotics for Polling Models with Limited Service Policies Woojin Chang School of Industrial and Systems Engineering Georgia Institute of Technology Atlanta, GA 30332-0205 USA Douglas G. Down Department
PHYSICS 653 HOMEWORK 1 P.1. Problems 1: Random walks (additional problems)
 PHYSICS 653 HOMEWORK 1 P.1 Problems 1: Random walks (additional problems) 1-2. Generating function (Lec. 1.1/1.2, random walks) Not assigned 27. Note: any corrections noted in 23 have not been made. This
PHYSICS 653 HOMEWORK 1 P.1 Problems 1: Random walks (additional problems) 1-2. Generating function (Lec. 1.1/1.2, random walks) Not assigned 27. Note: any corrections noted in 23 have not been made. This
MIT Manufacturing Systems Analysis Lectures 6 9: Flow Lines
 2.852 Manufacturing Systems Analysis 1/165 Copyright 2010 c Stanley B. Gershwin. MIT 2.852 Manufacturing Systems Analysis Lectures 6 9: Flow Lines Models That Can Be Analyzed Exactly Stanley B. Gershwin
2.852 Manufacturing Systems Analysis 1/165 Copyright 2010 c Stanley B. Gershwin. MIT 2.852 Manufacturing Systems Analysis Lectures 6 9: Flow Lines Models That Can Be Analyzed Exactly Stanley B. Gershwin
EE 550: Notes on Markov chains, Travel Times, and Opportunistic Routing
 EE 550: Notes on Markov chains, Travel Times, and Opportunistic Routing Michael J. Neely University of Southern California http://www-bcf.usc.edu/ mjneely 1 Abstract This collection of notes provides a
EE 550: Notes on Markov chains, Travel Times, and Opportunistic Routing Michael J. Neely University of Southern California http://www-bcf.usc.edu/ mjneely 1 Abstract This collection of notes provides a
NGSS Example Bundles. Page 1 of 13
 High School Modified Domains Model Course III Life Sciences Bundle 4: Life Diversifies Over Time This is the fourth bundle of the High School Domains Model Course III Life Sciences. Each bundle has connections
High School Modified Domains Model Course III Life Sciences Bundle 4: Life Diversifies Over Time This is the fourth bundle of the High School Domains Model Course III Life Sciences. Each bundle has connections
A Control-Theoretic Perspective on the Design of Distributed Agreement Protocols, Part
 9. A Control-Theoretic Perspective on the Design of Distributed Agreement Protocols, Part Sandip Roy Ali Saberi Kristin Herlugson Abstract This is the second of a two-part paper describing a control-theoretic
9. A Control-Theoretic Perspective on the Design of Distributed Agreement Protocols, Part Sandip Roy Ali Saberi Kristin Herlugson Abstract This is the second of a two-part paper describing a control-theoretic
Simulated Annealing for Constrained Global Optimization
 Monte Carlo Methods for Computation and Optimization Final Presentation Simulated Annealing for Constrained Global Optimization H. Edwin Romeijn & Robert L.Smith (1994) Presented by Ariel Schwartz Objective
Monte Carlo Methods for Computation and Optimization Final Presentation Simulated Annealing for Constrained Global Optimization H. Edwin Romeijn & Robert L.Smith (1994) Presented by Ariel Schwartz Objective
Probability Models of Information Exchange on Networks Lecture 6
 Probability Models of Information Exchange on Networks Lecture 6 UC Berkeley Many Other Models There are many models of information exchange on networks. Q: Which model to chose? My answer good features
Probability Models of Information Exchange on Networks Lecture 6 UC Berkeley Many Other Models There are many models of information exchange on networks. Q: Which model to chose? My answer good features
arxiv: v2 [math.pr] 4 Sep 2017
![arxiv: v2 [math.pr] 4 Sep 2017 arxiv: v2 [math.pr] 4 Sep 2017](/thumbs/77/75891959.jpg) arxiv:1708.08576v2 [math.pr] 4 Sep 2017 On the Speed of an Excited Asymmetric Random Walk Mike Cinkoske, Joe Jackson, Claire Plunkett September 5, 2017 Abstract An excited random walk is a non-markovian
arxiv:1708.08576v2 [math.pr] 4 Sep 2017 On the Speed of an Excited Asymmetric Random Walk Mike Cinkoske, Joe Jackson, Claire Plunkett September 5, 2017 Abstract An excited random walk is a non-markovian
Worst-case design of structures using stopping rules in k-adaptive random sampling approach
 10 th World Congress on Structural and Multidisciplinary Optimization May 19-4, 013, Orlando, Florida, USA Worst-case design of structures using stopping rules in k-adaptive random sampling approach Makoto
10 th World Congress on Structural and Multidisciplinary Optimization May 19-4, 013, Orlando, Florida, USA Worst-case design of structures using stopping rules in k-adaptive random sampling approach Makoto
Introduction to self-similar growth-fragmentations
 Introduction to self-similar growth-fragmentations Quan Shi CIMAT, 11-15 December, 2017 Quan Shi Growth-Fragmentations CIMAT, 11-15 December, 2017 1 / 34 Literature Jean Bertoin, Compensated fragmentation
Introduction to self-similar growth-fragmentations Quan Shi CIMAT, 11-15 December, 2017 Quan Shi Growth-Fragmentations CIMAT, 11-15 December, 2017 1 / 34 Literature Jean Bertoin, Compensated fragmentation
IEOR 6711: Professor Whitt. Introduction to Markov Chains
 IEOR 6711: Professor Whitt Introduction to Markov Chains 1. Markov Mouse: The Closed Maze We start by considering how to model a mouse moving around in a maze. The maze is a closed space containing nine
IEOR 6711: Professor Whitt Introduction to Markov Chains 1. Markov Mouse: The Closed Maze We start by considering how to model a mouse moving around in a maze. The maze is a closed space containing nine
INSIDE ALGEBRA CORRELATED WITH CALIFORNIA S COMMON CORE STANDARDS HIGH SCHOOL ALGEBRA
 We CA Can COMMON Early Learning CORE STANDARDS Curriculum PreK Grades 8 12 INSIDE ALGEBRA CORRELATED WITH CALIFORNIA S COMMON CORE STANDARDS HIGH SCHOOL ALGEBRA May 2011 www.voyagersopris.com/insidealgebra
We CA Can COMMON Early Learning CORE STANDARDS Curriculum PreK Grades 8 12 INSIDE ALGEBRA CORRELATED WITH CALIFORNIA S COMMON CORE STANDARDS HIGH SCHOOL ALGEBRA May 2011 www.voyagersopris.com/insidealgebra
Markov Chains Handout for Stat 110
 Markov Chains Handout for Stat 0 Prof. Joe Blitzstein (Harvard Statistics Department) Introduction Markov chains were first introduced in 906 by Andrey Markov, with the goal of showing that the Law of
Markov Chains Handout for Stat 0 Prof. Joe Blitzstein (Harvard Statistics Department) Introduction Markov chains were first introduced in 906 by Andrey Markov, with the goal of showing that the Law of
Example: physical systems. If the state space. Example: speech recognition. Context can be. Example: epidemics. Suppose each infected
 4. Markov Chains A discrete time process {X n,n = 0,1,2,...} with discrete state space X n {0,1,2,...} is a Markov chain if it has the Markov property: P[X n+1 =j X n =i,x n 1 =i n 1,...,X 0 =i 0 ] = P[X
4. Markov Chains A discrete time process {X n,n = 0,1,2,...} with discrete state space X n {0,1,2,...} is a Markov chain if it has the Markov property: P[X n+1 =j X n =i,x n 1 =i n 1,...,X 0 =i 0 ] = P[X
On Distribution and Limits of Information Dissemination Latency and Speed In Mobile Cognitive Radio Networks
 This paper was presented as part of the Mini-Conference at IEEE INFOCOM 11 On Distribution and Limits of Information Dissemination Latency and Speed In Mobile Cognitive Radio Networks Lei Sun Wenye Wang
This paper was presented as part of the Mini-Conference at IEEE INFOCOM 11 On Distribution and Limits of Information Dissemination Latency and Speed In Mobile Cognitive Radio Networks Lei Sun Wenye Wang
arxiv:cond-mat/ v1 [cond-mat.other] 4 Aug 2004
![arxiv:cond-mat/ v1 [cond-mat.other] 4 Aug 2004 arxiv:cond-mat/ v1 [cond-mat.other] 4 Aug 2004](/thumbs/74/69831888.jpg) Conservation laws for the voter model in complex networks arxiv:cond-mat/0408101v1 [cond-mat.other] 4 Aug 2004 Krzysztof Suchecki, 1,2 Víctor M. Eguíluz, 1 and Maxi San Miguel 1 1 Instituto Mediterráneo
Conservation laws for the voter model in complex networks arxiv:cond-mat/0408101v1 [cond-mat.other] 4 Aug 2004 Krzysztof Suchecki, 1,2 Víctor M. Eguíluz, 1 and Maxi San Miguel 1 1 Instituto Mediterráneo
On Krause s Multi-Agent Consensus Model With State-Dependent Connectivity
 2586 IEEE TRANSACTIONS ON AUTOMATIC CONTROL, VOL. 54, NO. 11, NOVEMBER 2009 On Krause s Multi-Agent Consensus Model With State-Dependent Connectivity Vincent D. Blondel, Julien M. Hendrickx, and John N.
2586 IEEE TRANSACTIONS ON AUTOMATIC CONTROL, VOL. 54, NO. 11, NOVEMBER 2009 On Krause s Multi-Agent Consensus Model With State-Dependent Connectivity Vincent D. Blondel, Julien M. Hendrickx, and John N.
THE CONTACT PROCESS ON TREES
 THE CONTACT PROCESS ON TREES Robin Pemantle 1 Department of Mathematics Cornell University Ithaca, NY 14853 ABSTRACT: The contact process on an infinite homogeneous tree is shown to exhibit at least two
THE CONTACT PROCESS ON TREES Robin Pemantle 1 Department of Mathematics Cornell University Ithaca, NY 14853 ABSTRACT: The contact process on an infinite homogeneous tree is shown to exhibit at least two
Exact solution of site and bond percolation. on small-world networks. Abstract
 Exact solution of site and bond percolation on small-world networks Cristopher Moore 1,2 and M. E. J. Newman 2 1 Departments of Computer Science and Physics, University of New Mexico, Albuquerque, New
Exact solution of site and bond percolation on small-world networks Cristopher Moore 1,2 and M. E. J. Newman 2 1 Departments of Computer Science and Physics, University of New Mexico, Albuquerque, New
Finite Connections for Supercritical Bernoulli Bond Percolation in 2D
 Finite Connections for Supercritical Bernoulli Bond Percolation in 2D M. Campanino 1 D. Ioffe 2 O. Louidor 3 1 Università di Bologna (Italy) 2 Technion (Israel) 3 Courant (New York University) Courant
Finite Connections for Supercritical Bernoulli Bond Percolation in 2D M. Campanino 1 D. Ioffe 2 O. Louidor 3 1 Università di Bologna (Italy) 2 Technion (Israel) 3 Courant (New York University) Courant
Open Loop Optimal Control of Base Station Activation for Green Networks
 Open Loop Optimal Control of Base Station Activation for Green etworks Sreenath Ramanath, Veeraruna Kavitha,2 and Eitan Altman IRIA, Sophia-Antipolis, France, 2 Universite d Avignon, Avignon, France Abstract
Open Loop Optimal Control of Base Station Activation for Green etworks Sreenath Ramanath, Veeraruna Kavitha,2 and Eitan Altman IRIA, Sophia-Antipolis, France, 2 Universite d Avignon, Avignon, France Abstract
A New Approach to Estimating the Expected First Hitting Time of Evolutionary Algorithms
 A New Approach to Estimating the Expected First Hitting Time of Evolutionary Algorithms Yang Yu and Zhi-Hua Zhou National Laboratory for Novel Software Technology Nanjing University, Nanjing 20093, China
A New Approach to Estimating the Expected First Hitting Time of Evolutionary Algorithms Yang Yu and Zhi-Hua Zhou National Laboratory for Novel Software Technology Nanjing University, Nanjing 20093, China
Renormalization: An Attack on Critical Exponents
 Renormalization: An Attack on Critical Exponents Zebediah Engberg March 15, 2010 1 Introduction Suppose L R d is a lattice with critical probability p c. Percolation on L is significantly differs depending
Renormalization: An Attack on Critical Exponents Zebediah Engberg March 15, 2010 1 Introduction Suppose L R d is a lattice with critical probability p c. Percolation on L is significantly differs depending
THREE DIMENSIONAL SYSTEMS. Lecture 6: The Lorenz Equations
 THREE DIMENSIONAL SYSTEMS Lecture 6: The Lorenz Equations 6. The Lorenz (1963) Equations The Lorenz equations were originally derived by Saltzman (1962) as a minimalist model of thermal convection in a
THREE DIMENSIONAL SYSTEMS Lecture 6: The Lorenz Equations 6. The Lorenz (1963) Equations The Lorenz equations were originally derived by Saltzman (1962) as a minimalist model of thermal convection in a
Combinatorial Criteria for Uniqueness of Gibbs Measures
 Combinatorial Criteria for Uniqueness of Gibbs Measures Dror Weitz School of Mathematics, Institute for Advanced Study, Princeton, NJ 08540, U.S.A. dror@ias.edu April 12, 2005 Abstract We generalize previously
Combinatorial Criteria for Uniqueness of Gibbs Measures Dror Weitz School of Mathematics, Institute for Advanced Study, Princeton, NJ 08540, U.S.A. dror@ias.edu April 12, 2005 Abstract We generalize previously
NGSS Example Bundles. Page 1 of 23
 High School Conceptual Progressions Model III Bundle 2 Evolution of Life This is the second bundle of the High School Conceptual Progressions Model Course III. Each bundle has connections to the other
High School Conceptual Progressions Model III Bundle 2 Evolution of Life This is the second bundle of the High School Conceptual Progressions Model Course III. Each bundle has connections to the other
CPSC 467b: Cryptography and Computer Security
 CPSC 467b: Cryptography and Computer Security Michael J. Fischer Lecture 10 February 19, 2013 CPSC 467b, Lecture 10 1/45 Primality Tests Strong primality tests Weak tests of compositeness Reformulation
CPSC 467b: Cryptography and Computer Security Michael J. Fischer Lecture 10 February 19, 2013 CPSC 467b, Lecture 10 1/45 Primality Tests Strong primality tests Weak tests of compositeness Reformulation
The halting problem is decidable on a set of asymptotic probability one
 The halting problem is decidable on a set of asymptotic probability one Joel David Hamkins The City University of New York http://jdh.hamkins.org Alexei Miasnikov The City University of New York http://www.cs.gc.cuny.edu/
The halting problem is decidable on a set of asymptotic probability one Joel David Hamkins The City University of New York http://jdh.hamkins.org Alexei Miasnikov The City University of New York http://www.cs.gc.cuny.edu/
Stochastic optimization Markov Chain Monte Carlo
 Stochastic optimization Markov Chain Monte Carlo Ethan Fetaya Weizmann Institute of Science 1 Motivation Markov chains Stationary distribution Mixing time 2 Algorithms Metropolis-Hastings Simulated Annealing
Stochastic optimization Markov Chain Monte Carlo Ethan Fetaya Weizmann Institute of Science 1 Motivation Markov chains Stationary distribution Mixing time 2 Algorithms Metropolis-Hastings Simulated Annealing
Computational Integer Programming. Lecture 2: Modeling and Formulation. Dr. Ted Ralphs
 Computational Integer Programming Lecture 2: Modeling and Formulation Dr. Ted Ralphs Computational MILP Lecture 2 1 Reading for This Lecture N&W Sections I.1.1-I.1.6 Wolsey Chapter 1 CCZ Chapter 2 Computational
Computational Integer Programming Lecture 2: Modeling and Formulation Dr. Ted Ralphs Computational MILP Lecture 2 1 Reading for This Lecture N&W Sections I.1.1-I.1.6 Wolsey Chapter 1 CCZ Chapter 2 Computational
Lecture Notes 7 Random Processes. Markov Processes Markov Chains. Random Processes
 Lecture Notes 7 Random Processes Definition IID Processes Bernoulli Process Binomial Counting Process Interarrival Time Process Markov Processes Markov Chains Classification of States Steady State Probabilities
Lecture Notes 7 Random Processes Definition IID Processes Bernoulli Process Binomial Counting Process Interarrival Time Process Markov Processes Markov Chains Classification of States Steady State Probabilities
Lecture 2: Convergence of Random Variables
 Lecture 2: Convergence of Random Variables Hyang-Won Lee Dept. of Internet & Multimedia Eng. Konkuk University Lecture 2 Introduction to Stochastic Processes, Fall 2013 1 / 9 Convergence of Random Variables
Lecture 2: Convergence of Random Variables Hyang-Won Lee Dept. of Internet & Multimedia Eng. Konkuk University Lecture 2 Introduction to Stochastic Processes, Fall 2013 1 / 9 Convergence of Random Variables
14 Branching processes
 4 BRANCHING PROCESSES 6 4 Branching processes In this chapter we will consider a rom model for population growth in the absence of spatial or any other resource constraints. So, consider a population of
4 BRANCHING PROCESSES 6 4 Branching processes In this chapter we will consider a rom model for population growth in the absence of spatial or any other resource constraints. So, consider a population of
THE ROLE OF DISPERSAL IN INTERACTING PATCHES SUBJECT TO AN ALLEE EFFECT
 Adv. Appl. Prob. 45, 1182 1197 (2013) Printed in Northern Ireland Applied Probability Trust 2013 THE ROLE OF DISPERSAL IN INTERACTING PATCHES SUBJECT TO AN ALLEE EFFECT N. LANCHIER, Arizona State University
Adv. Appl. Prob. 45, 1182 1197 (2013) Printed in Northern Ireland Applied Probability Trust 2013 THE ROLE OF DISPERSAL IN INTERACTING PATCHES SUBJECT TO AN ALLEE EFFECT N. LANCHIER, Arizona State University
Is the Field of Numbers a Real Physical Field? On the Frequent Distribution and Masses of the Elementary Particles
 Is the Field of Numbers a Real Physical Field? On the Frequent Distribution and Masses of the Elementary Particles Anatoly V. Belyakov E-mail: belyakov.lih@gmail.com Frequent distributions of the databases
Is the Field of Numbers a Real Physical Field? On the Frequent Distribution and Masses of the Elementary Particles Anatoly V. Belyakov E-mail: belyakov.lih@gmail.com Frequent distributions of the databases
6.842 Randomness and Computation March 3, Lecture 8
 6.84 Randomness and Computation March 3, 04 Lecture 8 Lecturer: Ronitt Rubinfeld Scribe: Daniel Grier Useful Linear Algebra Let v = (v, v,..., v n ) be a non-zero n-dimensional row vector and P an n n
6.84 Randomness and Computation March 3, 04 Lecture 8 Lecturer: Ronitt Rubinfeld Scribe: Daniel Grier Useful Linear Algebra Let v = (v, v,..., v n ) be a non-zero n-dimensional row vector and P an n n
Planning With Information States: A Survey Term Project for cs397sml Spring 2002
 Planning With Information States: A Survey Term Project for cs397sml Spring 2002 Jason O Kane jokane@uiuc.edu April 18, 2003 1 Introduction Classical planning generally depends on the assumption that the
Planning With Information States: A Survey Term Project for cs397sml Spring 2002 Jason O Kane jokane@uiuc.edu April 18, 2003 1 Introduction Classical planning generally depends on the assumption that the
Oblivious Equilibrium: A Mean Field Approximation for Large-Scale Dynamic Games
 Oblivious Equilibrium: A Mean Field Approximation for Large-Scale Dynamic Games Gabriel Y. Weintraub, Lanier Benkard, and Benjamin Van Roy Stanford University {gweintra,lanierb,bvr}@stanford.edu Abstract
Oblivious Equilibrium: A Mean Field Approximation for Large-Scale Dynamic Games Gabriel Y. Weintraub, Lanier Benkard, and Benjamin Van Roy Stanford University {gweintra,lanierb,bvr}@stanford.edu Abstract
Convex relaxations of chance constrained optimization problems
 Convex relaxations of chance constrained optimization problems Shabbir Ahmed School of Industrial & Systems Engineering, Georgia Institute of Technology, 765 Ferst Drive, Atlanta, GA 30332. May 12, 2011
Convex relaxations of chance constrained optimization problems Shabbir Ahmed School of Industrial & Systems Engineering, Georgia Institute of Technology, 765 Ferst Drive, Atlanta, GA 30332. May 12, 2011
Milford Public Schools Curriculum. Department: Mathematics Course Name: Algebra 1 Level 2
 Milford Public Schools Curriculum Department: Mathematics Course Name: Algebra 1 Level 2 UNIT 1 Unit Title: Intro to Functions and Exponential Expressions Unit Description: Students explore the main functions
Milford Public Schools Curriculum Department: Mathematics Course Name: Algebra 1 Level 2 UNIT 1 Unit Title: Intro to Functions and Exponential Expressions Unit Description: Students explore the main functions
