A statistical analysis of the Evolutionary Trace method. Heidi Spratt
|
|
|
- Clementine Clarke
- 5 years ago
- Views:
Transcription
1 1 A tatitical analyi of the Evolutionary Trace method Heidi Spratt
2 2 Content Lit of Illutration iii 1 Introduction 1 Evolution of Protein 1.1 Protein Multiple Sequence Alignment Model of Protein Evolution Phylogenetic Tree 7 2 Tree Building Method Ditance Matrix Method Unweighted Pair Group Method Uing Arithmetic Average The Neighbor-Joining Method Maximum Parimony Maximum Likelihood Method Method of Felentein Method of Subtitution Probabilitie The Pulley Principle Finding the Maximum Likelihood Tree Searching Among Tree Topologie Method of Kihino, Miyata, and Haegawa 21 3 Evolutionary Trace Evolutionary Trace Method Trace Integral 28
3 3 4 Preliminary Work Boottrap Non-parametric Boottrap Parametric Boottrap Confidence Interval on Phylogenie Analyi of YRS Protein Analyi of SRP Protein 39 5 Future Work Maximum Likelihood Tree for Protein Sequence Noie-level Detection 42 Bibliography 44
4 4 Illutration 2.1 An unrooted tree A rooted tree A rooted tree Likelihood computation tree The Evolutionary Trace method A profile graph Hitogram of integral value for YRS Hitogram of integral value for YRS with fewer gap Hitogram of integral value for YRS with fewer gap uing the parametric boottrap Hitogram of integral value for SRP Hitogram of integral value for SRP with fewer gap...39
5 5 Chapter 1 Introduction Computational tool for claifying equence, detecting imilaritie between DNA and protein equence, predicting molecular tructure and function, and recontructing the evolutionary hitory of DNA and protein equence are an important part of the recent development in the field of bioinformatic. All of thee reearch area are important to the undertanding of life and evolution, a well a to the dicovery of new drug and therapie Baldi and Brunak 1998). The expanion of the field of bioinformatic i being fueled by the demand for ophiticated analye of biological equence Durbin, et. al 1998). Part of the challenge aociated with the field i to organize, pare, and claify the immene amount of equence data. Little i known about the complex relationhip between a protein equence, it tructure, and the function of the protein. Thu, Lichtarge 1998) devied a method to examine the relationhip between the protein equence and the important function of the protein while utilizing the tructure of the protein. Protein active ite control nearly all protein function and determine the interaction upon which biological pathway and cellular network are built. Characterization of the active ite in a protein would therefore lead to new method of controlling protein and ultimately controlling cell. Thi thei work hope to better facilitate the work of Lichtarge and add ome tatitical analyi to the procedure a well. Chapter 2 explain protein, the proce of obtaining a multiple equence alignment, and phylogenetic tree. Chapter 3 decribe the variou method ued for
6 6 inferring evolutionary tree and how to build them. Chapter 4 explain the method of the evolutionary trace and why it i ueful. Chapter 5 decribe the method of the boottrap and ome preliminary analye of two protein familie. Chapter 6 decribe the work that i intended to be done for thi thei.
7 7 Chapter 2 Evolution of Protein 2.1 Protein Protein are unbranched chain made by linking together everal hundred amino acid by peptide bond which are trong covalent link Wood et. al. 1997). Amino acid, the building block of protein, are formed by combining three nucleic acid together. In a living ytem, a protein i aembled in a long polypeptide chain, one amino acid at a time. Protein are formed when one or more chain coil up in certain way to form threedimenional tructure with certain propertie. The equence of amino acid in a polypeptide chain determine the biological character of the protein molecule; even one mall variation in the equence may alter or detroy the way in which the protein function Curti & Barne 1989). Protein play many different role in living organim and take on many different form. The different amino acid in a protein determine the chemical and tructural propertie of the protein. Some of the function that protein perform are binding and carrying pecific molecule or ion from one organ to another known a tranport protein), acting a chemical meenger between cell in different part of the body in order to modify the activity of the recipient cell called hormone), providing protection againt invading bacteria and foreign virue antibodie), and regulating the expreion of gene regulatory protein) Blacktock 1998). The evolution of protein i caued by mutation that alter the bae equence of a DNA egment. Thee mutation caue the alteration of one or more amino acid in a
8 8 protein depending on how evere the mutation i. Harmful mutation are uually eliminated quickly becaue they are lethal to the carrier. A mutation at an unimportant ite imply change the amino acid at a ite or two but leave the tructure of the protein unchanged. Reearcher believe that mutation occur more frequently at unimportant ite that at functionally important one. 2.2 Multiple Sequence Alignment Sequence are compared to look for evidence of mutation and election when it i aumed the equence diverged from ome common ancetor Durbin et. al. 1998). Subtitution, which change reidue in a equence, a well a inertion and deletion, which add or remove reidue in a equence, are the baic mutational procee. Inertion and deletion are commonly referred to a gap. The method of Needlman and Wunch 1970) i a baic dynamic programming algorithm ued for the alignment of two biological equence. The method i baed on the mallet unit of comparion between two protein equence: amino acid. One amino acid from each protein equence i compared to the other. The maximum match between the two equence i the larget number of amino acid that, when aligned, match with thoe of the other equence. The bet match can be determined by creating a matrix of all poible pair combination that can be contructed from the two equence. The aim of pairwie alignment i to align two entire homologou protein region by uing a balance between matche and gap Hilli et. al. 1996). Becaue any two equence could be perfectly aligned given enough gap, gap mut be penalized omehow. Gap penaltie can thu be a combination of the length of the gap a well a the
9 9 quantity of gap. The quantity of gap hould be penalized more than the length of the gap. Thi i becaue there i no reaon one hould believe a priori that inertion/deletion event are more likely to only involve equence of hort length. If two equence do not have the ame length, penaltie may alo be aigned for leading and trailing gap thoe at the beginning and end of the equence repectively). However, thee penaltie are uually lower than thoe for internal gap ince leading and trailing gap uually have more to do with equalizing equence length than evolutionary change. All ubtitution can be aigned the ame penalty, or they can be aigned a matrix of penaltie giving different penaltie for tranition and tranverion or for any change between two amino acid. For mot phylogenetic tudie, multiple equence, intead of jut two equence, mut be aligned. The method of Needleman and Wunch could be extended to deal with multiple equence, but uch an approach would be computationally burdenome. One approach would be to create pairwie alignment from the equence then add equence together to form the multiple equence alignment MSA) by inerting additional gap acro the alignment a needed Hilli et. al. 1996). The main problem with thi method i that the MSA created i highly dependent on the order of the pecie conidered. Feng and Doolittle 1987) uggeted obtaining the order of the equence baed on an initial tree produced from a matrix of ditance collected from all pairwie alignment. The method of Feng and Doolittle 1987) i a progreive alignment method which utilize the method of Needleman and Wunch iteratively in order to obtain a MSA and to contruct an evolutionary tree to depict the relationhip between protein equence. The method put more value in the comparion of recently diverged
10 10 equence than in thoe that are very ditantly related Feng and Doolittle 1987). Similarity core are calculated via the Needleman-Wunch algorithm and then converted to difference core by the relationhip Sreal Srand D = ln Seff 100 = ln ) S S where S real i the alignment core, S rand i the core obtained with random equence of the ame length and compoition, and S ident i the average core of the two equence being compared when each i aligned with itelf. The value for S rand wa obtained from many previou obervation of the author. A tree ued to etablih preliminary branching order i then contructed. The mallet difference core i determined and a new matrix i contructed containing the average ditance between member of the firt pair and the remaining equence. The procedure i repeated until all core have been incorporated. ident rand 2.3 Protein Model of Evolution Eential to producing reliable reult further along in the analyi i the etimation of amino acid replacement frequencie during molecular evolution. Independence of evolution at different reidue i aumed o that ite can be examined one by one. Model of evolution in ue today rely on Markov procee. Tranition probabilitie rely only on the current tate of the amino acid and not on pat hitory. Start with an intantaneou rate matrix Q, the rate at which one amino acid i replaced by another. It i important to note that the diagonal element of Q are defined by a mathematical requirement that all the row add to zero. From thi, one can write the
11 11 tranition probabilitie from one amino acid to another a a matrix Pt). Thi matrix can be defined by the equation P t + dt) = P t) I + Qdt) 2.2) where dt i a mall amount of time and I i the identity matrix. Equation 2.2) can be olved to give Lio and Goldman 1998) Qt P t) = e. 2.3) Thi Markov proce i homogeneou, tationary, and reverible. Thi mean the rate matrix i independent of time, or that the rate of amino acid ubtitution remain the ame throughout the different level of the phylogenetic tree. Stationarity give the matrix the quality that the amino acid tranition frequencie have remained virtually unchanged throughout the coure of evolution. Reveribility mean that the proce i viewed the ame from the preent time to the pat a it i from the pat to the preent time. There are two widely accepted model in ue today: the PAM matrice of Dayhoff et.al 1978) and the BLOSUM matrice of Henikoff and Henikoff 1992). In the PAM matrice amino acid replacement rate are obtained from alignment of protein equence that are at leat 85% identical. The BLOSUM matrice ued local, ungapped alignment of ditantly related equence intead. The BLOSUM matrice are alo etimated without the reference to a rate matrix Q. 2.4 Phylogenetic Tree The imilarity of molecular mechanim or organim tudied by biologit ugget that all organim on Earth had a common ancetor Durbin et. al. 1998). Becaue of thi all
12 12 pecie are believed to be related and their relationhip i called a phylogeny. The relationhip i uually repreented by a phylogenetic tree: a figure depicting which organim are more cloely related to which other organim. It i a graph compoed of branche and node where two pecie become one). Any given branch connect to exactly two adjacent node in a bifurcating tree. The branche repreent the relationhip among the internal node in term of ancetry and decent. The terminal external) node repreent the taxonomic unit, or pecie, preent today Adachi and Haegawa 1996). The phylogenetic tree i inferred from obervation of the organim exiting today Durbin et. al. 1998). A true biological phylogeny ha an ultimate ancetor of all pecie. Tree can be either unrooted a tree decribing the relationhip between the pecie but not defining a pecific ancetor or a time direction), a depicted in Figure 2.1, or rooted having a pecific common ancetor) a depicted in Figure Figure 2.1 An unrooted tree Figure 2.2 A rooted tree The leave of the tree repreent the pecie preent today. The node of the tree repreent the time in hitory when thoe two pecie had a common ancetor. Sometime the leave of a tree can be wapped without altering the tree a in witching number 4
13 13 and 5 in Figure 2.3), but more often than not doing o change the tructure of the tree a in witching number 1 and 2 in Figure 2.3) Durbin et. al. 1998) Figure 2.3: A rooted tree
14 14 Chapter 3 Tree Building Methodologie There are everal different method in ue today for contructing phylogenetic tree. Some of the method deal with creating a ditance matrix ued to contruct a phylogenetic tree by joining equence having the mallet ditance between them. Some of the method are baed on maximum parimony which work by finding the tree that can explain the oberved equence with the minimum number of ubtitution Durbin et. al. 1998). The lat of the method deal with finding the tree topology that maximize the likelihood of all poible tree. 3.1 Ditance Matrix Procedure For every pair of equence in the MSA, ditance matrix method calculate an etimate of the branch length eparating the equence. Branch length here i defined a the product of time and rate of evolution Felentein 1996). The evolutionary tree choen i then the one that make the bet prediction of thee pairwie ditance baed on ome criterion. For protein equence, a probabilitic model of evolution need to be choen to bae the ditance on. Juke and Cantor 1969) created a imple model where all pair of amino acid have an equal probability of change. Thi model i overimplified ince it i known that ome amino acid prefer to change to certain other amino acid more frequently than other. Thu Dayhoff, Schwartz, and Orcutt 1978) created a table of probabilitie known a the PAM matrice) baed on empirical probabilitie of change between amino
15 15 acid over hort period of evolutionary time. Another et of ubtitution matrice, known a the BLOSUM matrice, wa created by Henikoff and Henikoff 1992). The BLOSUM matrice were created from multiple alignment of more ditantly related protein than thoe of the PAM matrice Unweighted Pair Group Method Uing Arithmetic Average Some of the method of tree building begin with a et of ditance d ij between each pair i,j of equence in the data et. There are everal different way of defining ditance. One method to do o i employed in the UPGMA Unweighted Pair Group Method uing Arithmetic Average) Sokal and Michener 1958) method which work by clutering the equence of the MSA. The method take the initial cluter and join a new equence at each level, thu creating a new node in the tree. The tree in thi cae can be enviioned a being built upward from the node to the ancetor. The UPGMA method produce a rooted tree with edge length that can be viewed a meaured by a molecular clock with a contant rate. Thi mean the divergence of equence i aumed to occur at ome contant rate throughout the tree. The ditance d ij between two cluter C i and C j i defined a the average ditance between pair of equence from each cluter: d ij = C i 1 C j d pq p in Ci, q in C j 3.1) where C i and C j are the number of equence in cluter i and j Durbin et al 1998). The method begin with the aignment of each equence i to it own cluter C i. Then one leaf of the tree i defined for each equence and placed at height equal to zero. Two
16 16 cluter i,j for which d ij i minimal are determined. However, if there are everal minimal pair with the ame value one pair hould be randomly choen. Next a new cluter k i defined by C k = C i U C j and the ditance d kl i defined by d kl d il Ci + d jl C j = 3.2) C + C i j for all l. A new node k i defined next with the two daughter node being i and j. The new node i placed at a height of d ij /2. K i added to the current cluter and i and j are removed. The lat five tep are repeated until only two cluter i,j remain and the root i placed at the height d ij / The Neighbor-Joining Method In the cae of the tree contructed via the UPGMA method, the tree i aumed to follow a molecular clock having a contant rate of divergence of equence) a well a have the additive property. The additive property mean that the um of the length of the branche connecting any two node on a tree i the ditance between any pair of node. The neighbor-joining method Saitou and Nei 1987) wa created to deal with tree which follow a molecular clock but are not additive. The neighbor-joining algorithm work by tarting out with a tar tree an unrooted tree where all node radiate from the center) and joining neighboring leave according to ome ditance criteria. The tree i then contructed by linking the leat-ditant pair of node a defined by a ditance matrix where the eparation between each pair of node i adjuted on the bai of their average divergence from all other node Swofford et. al 1996). When two node are linked, their common ancetral node i added to the tree and
17 17 the terminal node are removed from the tree. Thi proce convert the tree from a tarlike tree to a true phylogeny. At each tage in the neighbor-joining method, two terminal node are thu replaced by one internal node. The proce i complete when two node remain which are eparated by a ingle branch. 3.2 Maximum Parimony Maximum parimony method are the mot widely ued method in which to infer phylogenetic tree directly from character data. Maximum parimony doe not ue a model of equence evolution. Thi method imply elect tree that minimize the total tree length, the number of tranformation from one character tate to another required to explain a given et of equence Swofford et. al. 1996). Unlike ditance method, maximum parimony aign a cot to a given tree and earche through all poible tree topologie to find the tree with the mallet cot. Parimony treat each ite independently and then add the number of ubtitution neceary for all ite. However, Felentein 1978) ha hown the method of parimony to be inconitent when the evolutionary rate differ among lineage. 3.3 Maximum Likelihood Method If one aume that a phylogenetic tree for a et of equence i an unknown entity to be etimated then the method of maximum likelihood etimation i well-uited for the data at hand. In thi ene, maximum likelihood etimation involve finding the evolutionary tree which ha the highet probability of evolving the given data Felentein 1981). More pecifically, one eek the evolutionary tree and it branch length that have the
18 18 highet probability of giving rie to the given amino acid equence. The probability of uch a tree i computed via a tochatic model on reidue ubtitution in an evolutionary proce. Such a model aume that a reidue ubtitution at a particular reidue occur independently of any ubtitution at another reidue location Method of Felentein According the Felentein, the problem of computing the maximum likelihood etimate can be reduced to computing the probability of a given et of equence on an evolutionary tree and maximizing the probability over all tree. Given a model tating the probability equence S 1 change to equence S 2 during ome time interval t one can compute the probability of obtaining a given et of equence at the tip of an evolutionary tree. Independence of ite change need to be aumed for the method to be computationally feaible. However, independence i not entirely a valid aumption to make becaue gap inertion and/or deletion event) can not be properly modeled if one aume ite evolve independently of each other. But, by auming independence, the probability of a given et of equence ariing on a tree can be computed ite by ite. The product can then be taken acro ite to compute the likelihood. For a ingle ite we calculate P ij t), the probability that a lineage initially in tate i will be in tate j after t time unit. i and j take the value 1, 2,, 20 correponding to the twenty amino acid. Auming two lineage evolve independently after peciation and the ame bae ubtitution proce occur in all lineage, calculation of the likelihood are made poible.
19 19 If the tate at particular ite on node of the tree not currently preent are known then the likelihood of the given tree would be the product of the probabilitie of change in each leaf of the tree time the prior probability of the ancetor of the tree. The general expreion for the likelihood can be written, but it will be more inightful to go through a mall example to undertand the proce better. Figure 3.1 how the phylogeny tree that will be ued in the calculation of the likelihood. Figure 3.1: Tree ued in computation of the likelihood The length of the branche of the tree are denoted by t i. If the particular amino acid are known at point 0,6,7, and 8 on the tree then the likelihood would imply be the product of the probabilitie of change in each egment of the tree time the prior probability of the original bae at the origin. The likelihood would then be Felentein 1981) L = π P 0 06 t ) P t1 ) P t2 ) P t8 ) P t3) P t7 ) P t4 ) P t5 ) ) where i i the amino acid tate) at poition i on the tree and π 0 i the prior probability of being in tate 0. However, the amino acid at interior node of the tree are not generally known, o the likelihood ha to be generalized. The firt generalization i to um over all
20 20 the poible aignment of amino acid to the plit of the tree. The reulting likelihood i ). ) ) ) ) ) ) ) t P t P t P t P t P t P t P t P L = π 3.4) In general thi expreion will have 2 2n-2 term for n pecie. Thu, the likelihood can be rewritten in a impler manner. Namely, ))]}. )) ) [ )] )[ )]}{ )][ )[ { = t P t P t P t P t P t P t P t P L π 3.5) Since the full likelihood ha been written out, it i now poible to retate everything in term of conditional likelihood, thu making computation feaible. Define L k) a the likelihood baed on the data at or above point k on the tree, given that point k i known to have tate for the pecific ite under conideration. Then the above equation 3.5) i equivalent to working down the tree from the tip to the root. For a given point k, whoe immediate decendant are i and j, the conditional likelihood can be computed for all twenty value of k via ). ) ) ) ) ) ) = i j j j k i i k k j j i i k L t P L t P L 3.6) If point k i a tip of the tree then L k) will be zero for all value of except that tate actually oberved, for which the conditional likelihood will be one. All the term in eq. 3.5) will have been computed once the bottom fork on the tree i reached. Thu, the overall likelihood of the tree for a pecific ite can be written a 0) L L = π. 3.7)
21 21 Thi i the theoretical approach to calculating the likelihood. However, thi approach i computationally infeaible cauing Felentein to create the Pulley Principle to deal with the computational iue Calculation of Subtitution Probabilitie The quantitie P ij t) are the probabilitie of tranition from one amino acid to another over a egment of length t. Thee probabilitie are aumed to follow a Markov proce, one in which the probability of an amino acid changing may depend on the current amino acid but not on pat hitory. Aume that in a mall interval of time of length t there i ome probability, u dt, that the current amino acid at a particular ite i changed. u i the rate of amino acid ubtitution per unit of time. Since thi model aume that tranition and tranverion are the ame, for infiniteimal dt the ubtitution probabilitie are P ij ij j dt) = 1 u dt) δ + u dt π, 3.8) where π j i the probability of amino acid i being replaced by amino acid j, and δ ij i the Kronecker delta function. From eq. 3.8) it can be hown that for an arbitrary t, P ij ij j ut ut t) = e δ + 1 e ) π. 3.9) Here e -ut i the probability that a ite remain contant over a length of time t. If that ite doe change over time then the probability that it end up in tate j i imply π j. One nice property of thi Markov proce i that it i reverible. Thi mean that the proce of amino acid ubtitution will look exactly the ame whether we tart at the root of the tree and work toward the node or whether we tart at the node of the tree and work our way toward the root. Reveribility alo require that π P t) = P t) π. 3.10) i ij ji j
22 The Pulley Principle Since the Markov proce i reverible and there are no contraint placed on the length of the branche in the tree a ueful property to the etimation of the phylogenetic tree can be etablihed. Thi property i called the Pulley Principle by Felentein 1981). It can be eaily hown that the likelihood of the entire tree i unaffected if the placement of the root i altered. For intance, conider the lat two tep in the calculation of the likelihood for the above example of Figure 3.1. The likelihood of the tree at one ite involve fork 0, 6, and 8 of the tree and i 6) 8) L = π P t ) L ) P t ) L ). 3.11) The reveribility property eq. 3.10)) can be invoked to how that 8 8 π P t ) = π P t ), 3.12) which mean that the likelihood can be written a 6) 6 8) 8 L = π L L P t ) P t ). 3.13) The Chapman-Kolmogorov equation tate that the ummation on the right of eq. 3.13) can be replaced by P t + t ). Thi mean that the likelihood of the tree depend only on the um of the branch length t 6 + t 8 o that the root of the tree may be placed anywhere on the egment joining node 6 to node 8. In other word, the root of the tree act a a ort of pulley; all the part of the tree to one ide of the root can be hifted up while thoe on the other ide of the root can be hifted down by the ame amount. Thi proce can be repeated to how that the likelihood i independent of the placement of the root on the tree.
23 Finding the Maximum Likelihood Tree The Pulley Principle allow one to alter the length of any given branch of the tree in an optimal fahion. A pecific cae of the general EM algorithm of Dempter et al. 1977) i ued to arrive at an iterative method for finding the optimal tree branch length. I will ue an example to how how the iterative method can be obtained. Conider the right half of the tree in Figure 3.1. The root of thi partial tree can be thought to lie between node 7 and 8. Suppoe that the root lie immediately to the right of node 8. The likelihood for one particular ite in the protein equence i then given by Thi then become = ) ) 7 L π P 0) L ) P t ) L ). 3.14) t7 8) 7) t7 8) 7) L = e π L L + 1 e )[ π L ][ π L ] 3.15) upon ubtitution of eq. 3.14) into eq. 3.9) with u = 1. Eq. 3.15) i imply the likelihood correponding to one ite of the protein equence; the full likelihood i then of the form t7 t7 where q e, p = 1 e L = A q + B p) 3.16) i =, 8) 7) = = 8) A, and ) i L L Bi π L 8 8 i i π π L ) for the i th protein ite. The logarithm of eq. 3.16) can be taken to obtain an iterative equation for finding the optimal branch length; thi equation i 7 7) 7 k ) k + 1) 1 Bi p p =, k ) k ) K A q + B p i i i 3.17)
24 24 where K i the total number of ite in the protein equence of interet, and q k) = 1-p k). Iteration i performed for each ite until eq. 3.17) converge before moving on to the next ite. The iteration i finihed when a complete pa through the tree can be made without any of the p i changing ubtantially Searching Among Tree Topologie In an ideal ituation, one would be able to find the maximum likelihood tree by finding the tree that maximize the likelihood for all poible tree topologie. However, the number of poible unrooted tree topologie grow very rapidly via the expreion 2n 5)! n 3)!2 n 3 for n pecie Edward and Cavalli-Sforza 1964). Thu, a method mut be devied to arrive at the maximum likelihood tree that doe not take into account every ingle tree topology. One poible method i to build the tree by ucceively adding pecie to a tree tarting with jut two pecie. Each time a new pecie i added to the tree, there will be 2k-5 egment from which the k th pecie could arie. Each poition i tried; the final poition i determined by the iteration method decribed in ection The poition of the pecie on the tree topology i determined by that topology which yield the highet likelihood. If more than four pecie are preent in the tree, a local rearrangement of the branche i performed in order to ee if the rearrangement improve the likelihood. If any of the rearrangement doe improve the likelihood, then the new order i accepted and the next pecie i added in the manner jut decribed. Thi proce i iterated until all the pecie have been added and local rearrangement doe not provide a higher likelihood. An important thing to note about thi method i that it depend on the order of the original equence in the alignment. The order of the equence i the
25 25 ame order that the new pecie are added to find the maximum likelihood tree. Becaue of thi, Felentein 1981) recommend trying everal run with different ordering of the input equence. Although thi i not an exhautive method i.e. not all tree topologie are utilized), Felentein 1981) ha found the method to be ucceful in practice Method of Kihino, Miyata, and Haegawa In addition to the likelihood method of Felentein 1981), Kihino, Miyata, and Haegawa 1990) developed a method to maximize the likelihood of a given tree topology. Thi i a method baed on a Markov model that doe not aume a contant evolutionary rate among amino acid and take into account unequal tranition probabilitie among pair of amino acid Kihino et. al. 1990). The model alo trie to incorporate inertion/deletion event during evolution. Since unequal tranition probabilitie are aumed, the empirical tranition matrix of Dayhoff Dayhoff et. al. 1978) i ued. Dayhoff howed that an amino acid in a protein i replaced more often than expected under equal tranition probabilitie by a phyicochemically imilar amino acid. If independence of evolution at different ite i aumed, the probability of a given et of data can be computed ite by ite. The product of probabilitie can then be taken acro all ite at the final tage of computation Felentein 1981). The likelihood for a given tree topology T and equence data X i written a L=ProbX T, θ) where θ i a vector of parameter. A general expreion for the likelihood of a tree i poible to arrive at, but it i more illutrative to preent the cae of only four taxonomic unit. The formulation of the general reult will be clear from the impler example.
26 26 Rarely i an individual intereted in the evolutionary hitory of only four pecie. Hence, a implified method for dealing with more than five pecie i preented ince the method of maximum likelihood preented here will explode computationally for any more than five pecie. Start by breaking the total number of pecie into five group. The determination of thee five group i important. Hopefully, the group will be apparent at the beginning and the member will be known to cluter together in advance. Label the five group 1, 2, 3, 4, 5, where = i the total number of pecie one wihe to know the evolutionary hitory of. In other word, the equence data can be repreented a follow: Group 1 Specie 1.1) X 1.1)1 X 1.1)2 X 1.1)n M Specie 1. 1 ) X 1.1)1 X 1.1)2 X 1.1)n M M Group 5 Specie 5.1) X 5.1)1 X 5.1)2 X 5.1)n M Specie 5. 5 ) X 5.5)1 X 5.5)2 X 5.5)n By picking one pecie from each group, the maximum likelihood procedure of Felentein 1981) can be applied to the data for m alternative tree topologie of the five group. The probability of occupying amino acid x 1, x 2, x 3, x 4, and x 5 at a ite in the election from pecie 1, 2, 3, 4, and 5 i given by
27 27 f x, x π P, x 3, x t ) P, x t θ ) = ) 20 i ix1 1 ix2 2 i= 1 j= P t ij 6 ) P jx 3 t 3 ) P jx 4 t 4 ) P jx5 t 5 ). 3.18) The log-likelihood i n l θ X ) = log f θ ). 3.19) h= 1 where n i the total number of ite in the equence of interet. A maximum likelihood etimate of θ can be obtained via Newton method and following the procedure decribed. An alternate trategy to that mentioned above in ection for finding the maximum likelihood tree i called tar decompoition. Thi method i employed in the MOLPHY program developed by Adachi and Haegawa 1996). Star decompoition i very imilar to the neighbor-joining algorithm for a ditance matrix decribed in ection 3.1.2). Jut a the neighbor-joining algorithm, thi procedure tart with a tar-like tree Adachi and Haegawa 1996). From the tar-like tree, a pair of pecie i eparated from the other. Among all poible pairwie combination of pecie, a pairing giving the highet likelihood i choen. Thi proce i continued until all the multifurcation can be reolved into bifurcation. If not, the Akaike Information Criterion AIC) Akaike 1974) i ued to determine if the multifurcation hould be reolved. The final tree obtained by the method of tar decompoition i uniquely defined. Once an approximate tree topology i obtained by the tar decompoition method, local rearragement of the equence are performed to ee if a better topology can be found. Thi i done by moving all the poible internal node around to ee if a tree topology with a higher likelihood X h
28 28 can be found. If uch a tree doe exit, then the rearragement of the equence i carried out Adachi and Haegawa 1996). The local rearragement procedure i carried out through the entire tree until no further improvement of the likelihood i obtained. It i not guaranteed that thi procedure will obtain the maximum likelihood tree. Therefore, the ue of everal alternative input tree topologie i recommended. The choen tree hould then be the tree with the highet likelihood from all the initial poibilitie.
29 29 Chapter 4 Evolutionary Trace 4.1 Evolutionary Trace Method Reearcher believe that important reidue mutate le than unimportant reidue; part of the bai for the theory behind the evolutionary trace method i baed on the previou obervation. The evolutionary trace ET) Lichtarge 1996) i a method to identify active ite in a protein equence by looking for conerved reidue in the branche of an evolutionary tree. The purpoe of the method i to be able to rank the functional importance of amino acid in the protein tructure a well a to imply ome information about the protein equence-tructure-function relationhip. Thi will hopefully lead to better drug deign for pharmacologically important protein. Sequence fragment ued for analyi are gathered from the Baic Local Alignment Search Tool BLAST) Altchul et al. 1990) which match the query domain of interet. BLAST i a oftware package which find high coring local alignment between a query equence of interet and ome target databae. Thee homologou protein equence are aligned via a GCG program PILEUP) to create a multiple equence alignment. PILEUP Higgin and Sharp 1989) follow the progreive alignment method of Feng and Doolittle 1987) decribed earlier. Thu, a tree contructed by imilarity method from the initial equence data i ued for contructing the proper MSA. Changing the input order of the original equence into PILEUP can change the final MSA obtained. Currently, there i no method for varying the equence
30 30 order to obtain a conitent MSA. The tructure of the protein i known for one of the equence in the MSA. From the alignment, pairwie imilarity core are computed alo via PILEUP) between each pair of equence. From thee imilarity core an evolutionary tree i created via the method of UPGMA. Partition of the tree cluter of branche) are examined to ae functional importance of equence reidue. Thi i indicated in the tree column of Figure 4.1. In order to analyze the data, the tree i vertically cut into a certain number of branche. For example, the tree in Figure 4.1 i cut into four branche. For each cut made in the tree, an evolutionary trace can be calculated. In other word, the evolutionary trace can be calculated for a tree when there are five branche preent, when there are ix branche preent, or for however many branche the reearcher wihe to examine. The ideal number of branche to cut the tree into depend on the protein of interet. The exact cut-off value i determined by viualization at preent and better method are being dicued. For each branch of the tree at a particular cut point) a conenu equence i compiled ee the group column of Figure 4.1). To do thi imply look at all the equence in a given branch of the tree. If all the reidue at a given ite are the ame conerved), the conenu equence i given the conerved reidue type. When equence are conerved within each branch, but different acro branche at a given ite, that ite i called cla pecific. If all the equence do not have the ame reidue at each ite, then the conenu equence i neutral and left blank at that ite. Thi i made clear in the upper portion of the Conenu Sequence column of Figure 4.1.
31 31 Once a conenu equence ha been obtained for each branch of the cut tree, the conenu equence are aligned to get an evolutionary trace. If all conenu equence have the ame reidue at any given ite, that ite ha a conerved reidue in the trace. If the reidue varie between conenu equence, but i never a gap, then that ite ha a cla-pecific reidue in the trace, a depicted in the lat line of the Conenu Sequence column of Figure 4.1. If a reidue in any of the conenu equence i neutral then the trace i alo neutral at that ite. In other word, the trace completely ignore reidue containing a gap omewhere in the alignment. The protein reidue are then mapped onto the protein tructure via RASMOL Sayle and Milner-White 1995)) and color-coded to reflect conervation, cla pecificity, and neutrality, a depicted in the trace column of Figure 4.1.
32 32 GROUP GROUP GROUP TREE OUP GROUP 2 GROUP KERTFTGHKKLM KERTFTGHKRLM KERTFTVHKRLM KEKTFTGHKKLM VERTFTGHKSQM VERTDTGHKRQM VERTFTGMKRQM ASR.YTGVKKNV ASR.YTGVKKNV CONSENSUS SEQUENCE KE-TFT-HK-LM VERT-TG-K-QM ASR.YTGVKKNV ASR.YTGHKKNM XX T K_XX TRACE Active ite ASR.YTGHKKNM ASR.YTGHKKNM Cla pecific reidue of rank 4 or below... 3 Figure 4.1: The Evolutionary Trace Method. The Tree column decribe the tree at it branche, the Group column decribe the equence at each branch of the tree, the Conenu Sequence column how how the trace i formed from the individual equence, and the Trace column depict which tie on the protein tructure are deemed important by the trace. An X in the lat line of the Conenu Sequence column mean that ite i not conerved, a _ mean there i a gap omewhere in the conenu equence, and a pecific letter mean that ite i conerved at the given cut-off value. 4.2 Trace Integral The rank of each ite i the output of the evolutionary trace procedure. The rank i imply the number of branche the tree i vertically cut into in order for a particular ite to become cla pecific. If a ite ha a rank of 1 then that ite i completely conerved. A ite that ha a rank of 0 mean that ite ha a gap omewhere in the alignment referred to in the above ection a being neutral). A ite which ha a rank of anything ele i one
33 33 in which there i ome variation but at ome point along the tree the ite become cla pecific. One meaure of how good the evolutionary trace perform i the trace integral, which can be obtained from the rank data. However, the data need to be lightly tranformed before an integral can be taken. The way to do thi i by looking at the profile core intead of the rank. The profile can be thought of a the revere of the rank; it i how many branche need to be ubtracted from the terminal node of the tree to obtain cla pecificity at a given ite. An example of a profile graph for the analyi done in Section 5.2 i Figure 4.2. To calculate the profile core ubtract the rank from one more than the total number of equence preent in the alignment. However, if the rank i zero, the profile core i alo zero. The integral i then the area under the profile graph. Thu, the higher the trace integral the better the evolutionary trace method performed on that particular protein. The integral value for Figure 4.2 i Profile Graph of YRS with Fewer Gap profile ite Figure 4.2 The profile graph of the YRS protein with fewer gap
34 34 The profile graph i jut one meaure of how the trace perform. It i alo ued to help determine where the tree hould be cut off to determine which ite are important in the protein and which do not perform any given function. The peak in the profile graph indicate important ite, thoe that become cla pecific early in the phylogeny. For thi particular protein, the cut-off value wa determined to be 19 branche.
35 35 Chapter 5 Preliminary Work 5.1 Boottrap Reampling technology, like boottrapping, can be ued to determine if the cluter of an evolutionary tree are likely to be due to random coincidence. The boottrap i a computer-baed method frequently ued to ae the accuracy of many tatitical etimate developed by Efron 1979). The baic idea of the boottrap involve making aumption about the variability of an unknown ditribution from which the data were drawn by reampling from the data. The jutification of the reampling i that, if the original ample ize n i large, each poible value of x will be repreented in the ame proportion a in the underlying ditribution, and reampling from the data point with replacement will be the ame a ampling from the underlying ditribution Felentein 1985). There exit both parametric and non-parametric boottrap method Non-parametric Boottrap Felentein 1985) decribe the method of the boottrap a follow. Start with data point x 1,x 2,, x n which are aumed to be drawn independently from the ame ditribution. From thee value, one can apply ome method of tatitical etimation to obtain an etimate of the parameter of interet. If the exact ditribution of the data wa known and if our function were tractable, an etimate of the tandard error could be obtained a well a confidence interval for the etimate. However, when the ditribution of the data i unknown a i frequently the cae), the boottrap i a ueful alternative. The boottrap procedure ugget that the data be reampled to contruct everal fake
36 36 data et. Each of the fake boottrapped) data et i contructed by reampling n point from the original data with replacement. For each fake data et, compute the etimate of interet. The reampling procedure i performed many time, uually on the order of The idea of the boottrap i that the 1000 etimate approximate the ditribution of the actual etimate of interet. The variance of the etimate of interet can be etimated from the boottrapped etimate, a well a confidence interval for the parameter. For phylogenetic tree, the boottrap can be ued to reample the MSA creating new alignment. Confidence in each branch of the original evolutionary tree can be aeed from thee boottrapped alignment. The confidence etimate i baed on the proportion of boottrapped tree exhibiting the ame clutering a the original tree or partial clutering at a particular partition). A non-parametric boottrap ample i created from the original alignment by ampling the column of the alignment with replacement. Thu, the new alignment may have everal repeated column and everal miing column from the original alignment. It i important to note that the equence length of the boottrapped alignment and the MSA are exactly the ame Parametric Boottrap Unlike the non-parametric boottrap, the parametric boottrap create new ample replicate) by imulation involving maximum likelihood etimate. Firt, a model of evolution i aumed. Then the parameter of the model are etimated from the data. The parameter of phylogenetic data are the tree topology, the branch length of the tree, and tranition/tranverion rate. The ubtitution matrice incorporate the
37 37 tranition/tranverion rate. New character matrice multiple equence alignment) are then imulated auming the parameterized model from above. Finally, the new replicate are analyzed Huelenbeck and Hilli 1996). The main advantage of the parametric boottrap i that it generate independent tochatic replicate while the non-parametric boottrap preerve bia preent in the MSA. The main advantage of the non-parametric boottrap i that it doe not bae it replicate on any aumption about the ditribution of the data. The parametric boottrap depend on a detailed model of protein evolution mainly ubtitution matrice) and more computational reource aociated with obtaining the detail Confidence Interval on Phylogenie Each boottrap ample involve a tree topology a well a branch length. Confidence limit on a tatitic are uually baed on the percentile method: for a 95% confidence interval take the upper and lower 2.5% point of the ditribution of the boottrapped tatitic Felentein 1985). In the cae of phylogenie, reearcher are often intereted in the topology of portion of the tree rather than the whole tree. Thi i preciely what we wih to ae in the cae of the ET, not the total phylogeny but the imilarity of the cluter preent at a pre-determined cut point of the tree. For intance, if the cut-off value for a particular tree i 19, we wih to examine the different cluter of pecie preent when there are 19 tree in all the boottrapped ample. Boottrapping provide u with a confidence interval containing not the true phylogeny, but the phylogeny that would be etimated from repeated ampling of everal amino acid from the original data et Felentein 1985).
38 Analyi of YRS Protein The original et of equence for the tyroyl trna ynthetae YRS) protein, an eential enzyme for protein ynthei, wa 699 reidue long and conited of 35 pecie. The firt tep in the analyi i to boottrap the MSA. Thi i accomplihed by uing the computer package PHYLIP Felentein 1993) created by Joe Felentein and widely ditributed on the web. Thi package contain a program to boottrap MSA called SEQBOOT. Seqboot require an original multiple equence alignment a well a the length of the equence and number of pecie. The reult i a boottrapped MSA. Several boottrapped ample can be created at once o it i an eay tak to create 1000 boottrapped alignment. The evolutionary trace method i then run on the 1000 boottrapped ample. The ET method require the input of a mf file a well a a pileout file. The mf file i a format of the MSA. The pileout file i imply the pairwie imilarity core of the equence in the alignment. In order to perform the analyi the original mf file i ent to the ET program along with the pileout file created from the boottrapped ample. The original mf i included becaue we are jut trying to create new tree at thi point which are created via the pileout file) and we do not want to detroy the equence information preent in the original alignment. The trace integral core are calculated for each boottrapped ample and are compared to the original integral. The hitogram of thee value i een in Figure 5.1.
39 39 Figure 5.1: Hitogram of integral value for the boottrapped ample of the YRS protein. The vertical line i the integral value 4701) of the original MSA. A i clearly een, the value of the original integral i a great deal higher than for any of the boottrapped ample. It wa conjectured that ince the ET method ignore thoe ite with a gap, the original integral would be much higher than the boottrapped. Thi i becaue the boottrapped alignment might favor a ite with a gap and reample it more frequently than another. Thi could alter the pairwie imilarity core ignificantly and thuly create a ditorted tree. Thu, the deciion wa made to look at a new MSA of the YRS protein: one with fewer gap. All non-important gap were removed from the original alignment. An unimportant gap i one that i not fundamental in the tructure of the protein. New boottrapped ample were created uing thi horter alignment which contained only 318 reidue. The ET program wa then re-run uing thee horter
40 40 boottrapped alignment, and new integral were calculated. The reulting hitogram of integral value i Figure 5.2. Thi time the value for the original integral actually fall on the hitogram, not far off to the right of it. In thi cae, there are only twelve boottrapped ample that have an integral equal to or better than the original trace. Figure 5.2: Hitogram of integral value for the boottrapped ample of the YRS protein with fewer gap. The vertical line i the integral value 4768) of the original MSA with fewer gap. The next tep i to look at each of the boottrapped ample with a better integral value to ee if the important reidue are altered very much. It wa deemed that for the YRS protein a cut-off value of 19 wa ufficient. Thi mean that when the tree ha 19 branche one can determine the functionally important reidue by finding thoe reidue which are conerved. By looking at a linear correlation of each of the better boottrap ample to the original it can be een that all tree are very highly correlated ee the firt
41 41 column of Table 5.1). Thi hold true for the boottrapped ample with the wort tree lowet integral core), boottrapped tree in the middle of the integral ditribution, and randomly elected boottrapped tree. All correlation value were above 0.90 which indicate that all MSA are very highly correlated with each other a well a with the original MSA. The ame hold true for Spearman rank baed correlation coefficient a well. When looking at jut thoe ite which are deemed to be important in the original MSA at a cut-off of 19, the correlation drop off lightly ee the econd column of Table 5.1). However, there i no ignificant difference between the better group and the wore group. In both intance the correlation i never wore than 0.84 for all boottrapped ample. Linear Linear Correlation Correlation with rank of 19 or lower Table 5.1: Linear correlation of boottrapped ample to the original. The row repreent the correlation of different boottrapped ample to the original. The parametric boottrap wa alo utilized to examine the trace integral in the cae of the YRS protein. A program called Peq-Gen developed by Graly, Adachi, and Rambaut 1997) implement the parametric boottrap procedure. Thi program take a
42 42 input a phylogenetic tree with branch length and output a multiple equence alignment created from the input tree. Ideally, the input tree would be created via the maximum likelihood method. For the initial analyi, the input tree wa created via the method of UPGMA uing the NEIGHBOR program from PHYLIP. Since the ET ignore thoe poition in the MSA where a gap i preent, I ued the YRS MSA with fewer gap for the parametric boottrap analyi. Peq-Gen created 1000 equence of length 318 uing the UPGMA tree created from PHYLIP and the PAM001 ubtitution matrix. The ET analyi wa run on the parametric boottrapped ample uing the pairwie imilarity core calculated from the parametric boottrapped MSA and the original MSA. Integral value were then calculated for all 1000 boottrapped ample. Figure 5.3 depict the hitogram of integral value. A can clearly be een from Figure 5.3, the value of the original integral i much larger than that of the parametric boottrapped ample.
43 43 Figure 5.3: Hitogram of integral value for the parametric boottrapped ample of the YRS protein with fewer gap. The vertical line i the integral value 4768) of the original MSA with fewer gap. 5.3 Analyi of SRP Protein The original et of equence for the ignal recognition particle receptor SRP) protein wa 707 reidue long and conited of 36 pecie. A above, the firt tep in the analyi i to ue PHYLIP to boottrap the MSA. The evolutionary trace method i then run on the 1000 boottrapped ample. The trace integral core are then calculated for each boottrapped ample and are compared to the original integral. The hitogram of thee value i Figure 5.4.
44 44 Figure 5.4: Hitogram of integral value for the boottrapped ample of the SRP protein. The vertical line indicate the value, 3095, of the integral for the original MSA. A in the cae of the YRS protein, the value of the original integral i a great deal higher than for any of the boottrapped ample. Thu, the deciion wa made to look at a new MSA of the SRP protein: one with fewer gap. All non-important gap were removed from the original alignment. New boottrapped ample were created uing thi horter alignment which contained only 294 reidue. The trace wa then re-run uing thee horter boottrapped alignment, and new integral were calculated. The reulting hitogram of integral value i Figure 5.5. Thi time the value for the original integral actually fall on the hitogram, not way off to the right of it. In thi cae, there are only 21 boottrapped ample that have an integral equal to or better than the original trace.
45 45 Figure 5.5: Hitogram of the integral value for the boottrapped ample of the SRP protein with fewer gap. The vertical line indicate the integral value, 3146, of the original MSA with fewer gap. The next tep i to look at each of the boottrapped ample with a better integral and ee if the important reidue are altered very much. It wa deemed that for the SRP protein a cut-off value of 19 wa ufficient. Thi mean that when the tree ha 19 branche all the functionally important reidue will be preent. It i pure coincidence that the YRS protein and the SRP protein have the ame cut-off value. Again, the correlation analyi how that all the boottrapped ample are highly correlated with the original ample. Thu, the important reidue do not appear to change much from one boottrapped ample to another or vary much from the original.
Comparing Means: t-tests for Two Independent Samples
 Comparing ean: t-tet for Two Independent Sample Independent-eaure Deign t-tet for Two Independent Sample Allow reearcher to evaluate the mean difference between two population uing data from two eparate
Comparing ean: t-tet for Two Independent Sample Independent-eaure Deign t-tet for Two Independent Sample Allow reearcher to evaluate the mean difference between two population uing data from two eparate
Social Studies 201 Notes for March 18, 2005
 1 Social Studie 201 Note for March 18, 2005 Etimation of a mean, mall ample ize Section 8.4, p. 501. When a reearcher ha only a mall ample ize available, the central limit theorem doe not apply to the
1 Social Studie 201 Note for March 18, 2005 Etimation of a mean, mall ample ize Section 8.4, p. 501. When a reearcher ha only a mall ample ize available, the central limit theorem doe not apply to the
Clustering Methods without Given Number of Clusters
 Clutering Method without Given Number of Cluter Peng Xu, Fei Liu Introduction A we now, mean method i a very effective algorithm of clutering. It mot powerful feature i the calability and implicity. However,
Clutering Method without Given Number of Cluter Peng Xu, Fei Liu Introduction A we now, mean method i a very effective algorithm of clutering. It mot powerful feature i the calability and implicity. However,
Social Studies 201 Notes for November 14, 2003
 1 Social Studie 201 Note for November 14, 2003 Etimation of a mean, mall ample ize Section 8.4, p. 501. When a reearcher ha only a mall ample ize available, the central limit theorem doe not apply to the
1 Social Studie 201 Note for November 14, 2003 Etimation of a mean, mall ample ize Section 8.4, p. 501. When a reearcher ha only a mall ample ize available, the central limit theorem doe not apply to the
Source slideplayer.com/fundamentals of Analytical Chemistry, F.J. Holler, S.R.Crouch. Chapter 6: Random Errors in Chemical Analysis
 Source lideplayer.com/fundamental of Analytical Chemitry, F.J. Holler, S.R.Crouch Chapter 6: Random Error in Chemical Analyi Random error are preent in every meaurement no matter how careful the experimenter.
Source lideplayer.com/fundamental of Analytical Chemitry, F.J. Holler, S.R.Crouch Chapter 6: Random Error in Chemical Analyi Random error are preent in every meaurement no matter how careful the experimenter.
Bogoliubov Transformation in Classical Mechanics
 Bogoliubov Tranformation in Claical Mechanic Canonical Tranformation Suppoe we have a et of complex canonical variable, {a j }, and would like to conider another et of variable, {b }, b b ({a j }). How
Bogoliubov Tranformation in Claical Mechanic Canonical Tranformation Suppoe we have a et of complex canonical variable, {a j }, and would like to conider another et of variable, {b }, b b ({a j }). How
Codes Correcting Two Deletions
 1 Code Correcting Two Deletion Ryan Gabry and Frederic Sala Spawar Sytem Center Univerity of California, Lo Angele ryan.gabry@navy.mil fredala@ucla.edu Abtract In thi work, we invetigate the problem of
1 Code Correcting Two Deletion Ryan Gabry and Frederic Sala Spawar Sytem Center Univerity of California, Lo Angele ryan.gabry@navy.mil fredala@ucla.edu Abtract In thi work, we invetigate the problem of
Lecture 4 Topic 3: General linear models (GLMs), the fundamentals of the analysis of variance (ANOVA), and completely randomized designs (CRDs)
 Lecture 4 Topic 3: General linear model (GLM), the fundamental of the analyi of variance (ANOVA), and completely randomized deign (CRD) The general linear model One population: An obervation i explained
Lecture 4 Topic 3: General linear model (GLM), the fundamental of the analyi of variance (ANOVA), and completely randomized deign (CRD) The general linear model One population: An obervation i explained
Multiple Sequence Alignment. Progressive Alignment Iterative Pairwise Guide Tree ClustalW Co-linearity Multiple Sequence Alignment Editors
 Yverdon Le Bain Introduction to Bioinformatic Introduction to Bioinformatic ami Khuri Department of Computer cience an Joé tate Univerity an Joé, California, UA khuri@c.ju.edu www.c.ju.edu/faculty/khuri
Yverdon Le Bain Introduction to Bioinformatic Introduction to Bioinformatic ami Khuri Department of Computer cience an Joé tate Univerity an Joé, California, UA khuri@c.ju.edu www.c.ju.edu/faculty/khuri
CHAPTER 8 OBSERVER BASED REDUCED ORDER CONTROLLER DESIGN FOR LARGE SCALE LINEAR DISCRETE-TIME CONTROL SYSTEMS
 CHAPTER 8 OBSERVER BASED REDUCED ORDER CONTROLLER DESIGN FOR LARGE SCALE LINEAR DISCRETE-TIME CONTROL SYSTEMS 8.1 INTRODUCTION 8.2 REDUCED ORDER MODEL DESIGN FOR LINEAR DISCRETE-TIME CONTROL SYSTEMS 8.3
CHAPTER 8 OBSERVER BASED REDUCED ORDER CONTROLLER DESIGN FOR LARGE SCALE LINEAR DISCRETE-TIME CONTROL SYSTEMS 8.1 INTRODUCTION 8.2 REDUCED ORDER MODEL DESIGN FOR LINEAR DISCRETE-TIME CONTROL SYSTEMS 8.3
Problem Set 8 Solutions
 Deign and Analyi of Algorithm April 29, 2015 Maachuett Intitute of Technology 6.046J/18.410J Prof. Erik Demaine, Srini Devada, and Nancy Lynch Problem Set 8 Solution Problem Set 8 Solution Thi problem
Deign and Analyi of Algorithm April 29, 2015 Maachuett Intitute of Technology 6.046J/18.410J Prof. Erik Demaine, Srini Devada, and Nancy Lynch Problem Set 8 Solution Problem Set 8 Solution Thi problem
Lecture 7: Testing Distributions
 CSE 5: Sublinear (and Streaming) Algorithm Spring 014 Lecture 7: Teting Ditribution April 1, 014 Lecturer: Paul Beame Scribe: Paul Beame 1 Teting Uniformity of Ditribution We return today to property teting
CSE 5: Sublinear (and Streaming) Algorithm Spring 014 Lecture 7: Teting Ditribution April 1, 014 Lecturer: Paul Beame Scribe: Paul Beame 1 Teting Uniformity of Ditribution We return today to property teting
Dimensional Analysis A Tool for Guiding Mathematical Calculations
 Dimenional Analyi A Tool for Guiding Mathematical Calculation Dougla A. Kerr Iue 1 February 6, 2010 ABSTRACT AND INTRODUCTION In converting quantitie from one unit to another, we may know the applicable
Dimenional Analyi A Tool for Guiding Mathematical Calculation Dougla A. Kerr Iue 1 February 6, 2010 ABSTRACT AND INTRODUCTION In converting quantitie from one unit to another, we may know the applicable
Suggested Answers To Exercises. estimates variability in a sampling distribution of random means. About 68% of means fall
 Beyond Significance Teting ( nd Edition), Rex B. Kline Suggeted Anwer To Exercie Chapter. The tatitic meaure variability among core at the cae level. In a normal ditribution, about 68% of the core fall
Beyond Significance Teting ( nd Edition), Rex B. Kline Suggeted Anwer To Exercie Chapter. The tatitic meaure variability among core at the cae level. In a normal ditribution, about 68% of the core fall
Nonlinear Single-Particle Dynamics in High Energy Accelerators
 Nonlinear Single-Particle Dynamic in High Energy Accelerator Part 6: Canonical Perturbation Theory Nonlinear Single-Particle Dynamic in High Energy Accelerator Thi coure conit of eight lecture: 1. Introduction
Nonlinear Single-Particle Dynamic in High Energy Accelerator Part 6: Canonical Perturbation Theory Nonlinear Single-Particle Dynamic in High Energy Accelerator Thi coure conit of eight lecture: 1. Introduction
Chapter 2 Sampling and Quantization. In order to investigate sampling and quantization, the difference between analog
 Chapter Sampling and Quantization.1 Analog and Digital Signal In order to invetigate ampling and quantization, the difference between analog and digital ignal mut be undertood. Analog ignal conit of continuou
Chapter Sampling and Quantization.1 Analog and Digital Signal In order to invetigate ampling and quantization, the difference between analog and digital ignal mut be undertood. Analog ignal conit of continuou
Avoiding Forbidden Submatrices by Row Deletions
 Avoiding Forbidden Submatrice by Row Deletion Sebatian Wernicke, Jochen Alber, Jen Gramm, Jiong Guo, and Rolf Niedermeier Wilhelm-Schickard-Intitut für Informatik, niverität Tübingen, Sand 13, D-72076
Avoiding Forbidden Submatrice by Row Deletion Sebatian Wernicke, Jochen Alber, Jen Gramm, Jiong Guo, and Rolf Niedermeier Wilhelm-Schickard-Intitut für Informatik, niverität Tübingen, Sand 13, D-72076
Lecture 9: Shor s Algorithm
 Quantum Computation (CMU 8-859BB, Fall 05) Lecture 9: Shor Algorithm October 7, 05 Lecturer: Ryan O Donnell Scribe: Sidhanth Mohanty Overview Let u recall the period finding problem that wa et up a a function
Quantum Computation (CMU 8-859BB, Fall 05) Lecture 9: Shor Algorithm October 7, 05 Lecturer: Ryan O Donnell Scribe: Sidhanth Mohanty Overview Let u recall the period finding problem that wa et up a a function
7.2 INVERSE TRANSFORMS AND TRANSFORMS OF DERIVATIVES 281
 72 INVERSE TRANSFORMS AND TRANSFORMS OF DERIVATIVES 28 and i 2 Show how Euler formula (page 33) can then be ued to deduce the reult a ( a) 2 b 2 {e at co bt} {e at in bt} b ( a) 2 b 2 5 Under what condition
72 INVERSE TRANSFORMS AND TRANSFORMS OF DERIVATIVES 28 and i 2 Show how Euler formula (page 33) can then be ued to deduce the reult a ( a) 2 b 2 {e at co bt} {e at in bt} b ( a) 2 b 2 5 Under what condition
DYNAMIC MODELS FOR CONTROLLER DESIGN
 DYNAMIC MODELS FOR CONTROLLER DESIGN M.T. Tham (996,999) Dept. of Chemical and Proce Engineering Newcatle upon Tyne, NE 7RU, UK.. INTRODUCTION The problem of deigning a good control ytem i baically that
DYNAMIC MODELS FOR CONTROLLER DESIGN M.T. Tham (996,999) Dept. of Chemical and Proce Engineering Newcatle upon Tyne, NE 7RU, UK.. INTRODUCTION The problem of deigning a good control ytem i baically that
CHAPTER 6. Estimation
 CHAPTER 6 Etimation Definition. Statitical inference i the procedure by which we reach a concluion about a population on the bai of information contained in a ample drawn from that population. Definition.
CHAPTER 6 Etimation Definition. Statitical inference i the procedure by which we reach a concluion about a population on the bai of information contained in a ample drawn from that population. Definition.
DIFFERENTIAL EQUATIONS
 DIFFERENTIAL EQUATIONS Laplace Tranform Paul Dawkin Table of Content Preface... Laplace Tranform... Introduction... The Definition... 5 Laplace Tranform... 9 Invere Laplace Tranform... Step Function...4
DIFFERENTIAL EQUATIONS Laplace Tranform Paul Dawkin Table of Content Preface... Laplace Tranform... Introduction... The Definition... 5 Laplace Tranform... 9 Invere Laplace Tranform... Step Function...4
Control Systems Analysis and Design by the Root-Locus Method
 6 Control Sytem Analyi and Deign by the Root-Locu Method 6 1 INTRODUCTION The baic characteritic of the tranient repone of a cloed-loop ytem i cloely related to the location of the cloed-loop pole. If
6 Control Sytem Analyi and Deign by the Root-Locu Method 6 1 INTRODUCTION The baic characteritic of the tranient repone of a cloed-loop ytem i cloely related to the location of the cloed-loop pole. If
Alternate Dispersion Measures in Replicated Factorial Experiments
 Alternate Diperion Meaure in Replicated Factorial Experiment Neal A. Mackertich The Raytheon Company, Sudbury MA 02421 Jame C. Benneyan Northeatern Univerity, Boton MA 02115 Peter D. Krau The Raytheon
Alternate Diperion Meaure in Replicated Factorial Experiment Neal A. Mackertich The Raytheon Company, Sudbury MA 02421 Jame C. Benneyan Northeatern Univerity, Boton MA 02115 Peter D. Krau The Raytheon
Singular perturbation theory
 Singular perturbation theory Marc R. Rouel June 21, 2004 1 Introduction When we apply the teady-tate approximation (SSA) in chemical kinetic, we typically argue that ome of the intermediate are highly
Singular perturbation theory Marc R. Rouel June 21, 2004 1 Introduction When we apply the teady-tate approximation (SSA) in chemical kinetic, we typically argue that ome of the intermediate are highly
Optimal Coordination of Samples in Business Surveys
 Paper preented at the ICES-III, June 8-, 007, Montreal, Quebec, Canada Optimal Coordination of Sample in Buine Survey enka Mach, Ioana Şchiopu-Kratina, Philip T Rei, Jean-Marc Fillion Statitic Canada New
Paper preented at the ICES-III, June 8-, 007, Montreal, Quebec, Canada Optimal Coordination of Sample in Buine Survey enka Mach, Ioana Şchiopu-Kratina, Philip T Rei, Jean-Marc Fillion Statitic Canada New
Theoretical Population Biology
 Theoretical Population Biology 8 () 3 Content lit available at ScienceDirect Theoretical Population Biology journal homepage: www.elevier.com/locate/tpb On the ize ditribution of private microatellite
Theoretical Population Biology 8 () 3 Content lit available at ScienceDirect Theoretical Population Biology journal homepage: www.elevier.com/locate/tpb On the ize ditribution of private microatellite
ON THE APPROXIMATION ERROR IN HIGH DIMENSIONAL MODEL REPRESENTATION. Xiaoqun Wang
 Proceeding of the 2008 Winter Simulation Conference S. J. Maon, R. R. Hill, L. Mönch, O. Roe, T. Jefferon, J. W. Fowler ed. ON THE APPROXIMATION ERROR IN HIGH DIMENSIONAL MODEL REPRESENTATION Xiaoqun Wang
Proceeding of the 2008 Winter Simulation Conference S. J. Maon, R. R. Hill, L. Mönch, O. Roe, T. Jefferon, J. W. Fowler ed. ON THE APPROXIMATION ERROR IN HIGH DIMENSIONAL MODEL REPRESENTATION Xiaoqun Wang
Chapter 4. The Laplace Transform Method
 Chapter 4. The Laplace Tranform Method The Laplace Tranform i a tranformation, meaning that it change a function into a new function. Actually, it i a linear tranformation, becaue it convert a linear combination
Chapter 4. The Laplace Tranform Method The Laplace Tranform i a tranformation, meaning that it change a function into a new function. Actually, it i a linear tranformation, becaue it convert a linear combination
SMALL-SIGNAL STABILITY ASSESSMENT OF THE EUROPEAN POWER SYSTEM BASED ON ADVANCED NEURAL NETWORK METHOD
 SMALL-SIGNAL STABILITY ASSESSMENT OF THE EUROPEAN POWER SYSTEM BASED ON ADVANCED NEURAL NETWORK METHOD S.P. Teeuwen, I. Erlich U. Bachmann Univerity of Duiburg, Germany Department of Electrical Power Sytem
SMALL-SIGNAL STABILITY ASSESSMENT OF THE EUROPEAN POWER SYSTEM BASED ON ADVANCED NEURAL NETWORK METHOD S.P. Teeuwen, I. Erlich U. Bachmann Univerity of Duiburg, Germany Department of Electrical Power Sytem
If Y is normally Distributed, then and 2 Y Y 10. σ σ
 ull Hypothei Significance Teting V. APS 50 Lecture ote. B. Dudek. ot for General Ditribution. Cla Member Uage Only. Chi-Square and F-Ditribution, and Diperion Tet Recall from Chapter 4 material on: ( )
ull Hypothei Significance Teting V. APS 50 Lecture ote. B. Dudek. ot for General Ditribution. Cla Member Uage Only. Chi-Square and F-Ditribution, and Diperion Tet Recall from Chapter 4 material on: ( )
University of Washington Department of Chemistry Chemistry 453 Winter Quarter 2015
 Lecture 8. 1/3/15 Univerity of Wahington Department of Chemitry Chemitry 453 Winter Quarter 015 A. Statitic of Conformational Equilibria in Protein It i known from experiment that ome protein, DA, and
Lecture 8. 1/3/15 Univerity of Wahington Department of Chemitry Chemitry 453 Winter Quarter 015 A. Statitic of Conformational Equilibria in Protein It i known from experiment that ome protein, DA, and
A FUNCTIONAL BAYESIAN METHOD FOR THE SOLUTION OF INVERSE PROBLEMS WITH SPATIO-TEMPORAL PARAMETERS AUTHORS: CORRESPONDENCE: ABSTRACT
 A FUNCTIONAL BAYESIAN METHOD FOR THE SOLUTION OF INVERSE PROBLEMS WITH SPATIO-TEMPORAL PARAMETERS AUTHORS: Zenon Medina-Cetina International Centre for Geohazard / Norwegian Geotechnical Intitute Roger
A FUNCTIONAL BAYESIAN METHOD FOR THE SOLUTION OF INVERSE PROBLEMS WITH SPATIO-TEMPORAL PARAMETERS AUTHORS: Zenon Medina-Cetina International Centre for Geohazard / Norwegian Geotechnical Intitute Roger
Design By Emulation (Indirect Method)
 Deign By Emulation (Indirect Method he baic trategy here i, that Given a continuou tranfer function, it i required to find the bet dicrete equivalent uch that the ignal produced by paing an input ignal
Deign By Emulation (Indirect Method he baic trategy here i, that Given a continuou tranfer function, it i required to find the bet dicrete equivalent uch that the ignal produced by paing an input ignal
Lecture 10 Filtering: Applied Concepts
 Lecture Filtering: Applied Concept In the previou two lecture, you have learned about finite-impule-repone (FIR) and infinite-impule-repone (IIR) filter. In thee lecture, we introduced the concept of filtering
Lecture Filtering: Applied Concept In the previou two lecture, you have learned about finite-impule-repone (FIR) and infinite-impule-repone (IIR) filter. In thee lecture, we introduced the concept of filtering
into a discrete time function. Recall that the table of Laplace/z-transforms is constructed by (i) selecting to get
 Lecture 25 Introduction to Some Matlab c2d Code in Relation to Sampled Sytem here are many way to convert a continuou time function, { h( t) ; t [0, )} into a dicrete time function { h ( k) ; k {0,,, }}
Lecture 25 Introduction to Some Matlab c2d Code in Relation to Sampled Sytem here are many way to convert a continuou time function, { h( t) ; t [0, )} into a dicrete time function { h ( k) ; k {0,,, }}
Solving Differential Equations by the Laplace Transform and by Numerical Methods
 36CH_PHCalter_TechMath_95099 3//007 :8 PM Page Solving Differential Equation by the Laplace Tranform and by Numerical Method OBJECTIVES When you have completed thi chapter, you hould be able to: Find the
36CH_PHCalter_TechMath_95099 3//007 :8 PM Page Solving Differential Equation by the Laplace Tranform and by Numerical Method OBJECTIVES When you have completed thi chapter, you hould be able to: Find the
NCAAPMT Calculus Challenge Challenge #3 Due: October 26, 2011
 NCAAPMT Calculu Challenge 011 01 Challenge #3 Due: October 6, 011 A Model of Traffic Flow Everyone ha at ome time been on a multi-lane highway and encountered road contruction that required the traffic
NCAAPMT Calculu Challenge 011 01 Challenge #3 Due: October 6, 011 A Model of Traffic Flow Everyone ha at ome time been on a multi-lane highway and encountered road contruction that required the traffic
Introduction to Laplace Transform Techniques in Circuit Analysis
 Unit 6 Introduction to Laplace Tranform Technique in Circuit Analyi In thi unit we conider the application of Laplace Tranform to circuit analyi. A relevant dicuion of the one-ided Laplace tranform i found
Unit 6 Introduction to Laplace Tranform Technique in Circuit Analyi In thi unit we conider the application of Laplace Tranform to circuit analyi. A relevant dicuion of the one-ided Laplace tranform i found
Predicting the Performance of Teams of Bounded Rational Decision-makers Using a Markov Chain Model
 The InTITuTe for ytem reearch Ir TechnIcal report 2013-14 Predicting the Performance of Team of Bounded Rational Deciion-maer Uing a Marov Chain Model Jeffrey Herrmann Ir develop, applie and teache advanced
The InTITuTe for ytem reearch Ir TechnIcal report 2013-14 Predicting the Performance of Team of Bounded Rational Deciion-maer Uing a Marov Chain Model Jeffrey Herrmann Ir develop, applie and teache advanced
Advanced Algorithms and Models for Computational Biology -- a machine learning approach. Some important dates in history (billions of years ago)
 Advanced Algorithm and Model for Computational Biology -- a machine learning approach Molecular Evolution: nucleotide ubtitution model Eric Xing Lecture 20, April 3, 2006 Reading: DTW book, Chap 12 DEKM
Advanced Algorithm and Model for Computational Biology -- a machine learning approach Molecular Evolution: nucleotide ubtitution model Eric Xing Lecture 20, April 3, 2006 Reading: DTW book, Chap 12 DEKM
A Constraint Propagation Algorithm for Determining the Stability Margin. The paper addresses the stability margin assessment for linear systems
 A Contraint Propagation Algorithm for Determining the Stability Margin of Linear Parameter Circuit and Sytem Lubomir Kolev and Simona Filipova-Petrakieva Abtract The paper addree the tability margin aement
A Contraint Propagation Algorithm for Determining the Stability Margin of Linear Parameter Circuit and Sytem Lubomir Kolev and Simona Filipova-Petrakieva Abtract The paper addree the tability margin aement
μ + = σ = D 4 σ = D 3 σ = σ = All units in parts (a) and (b) are in V. (1) x chart: Center = μ = 0.75 UCL =
 Our online Tutor are available 4*7 to provide Help with Proce control ytem Homework/Aignment or a long term Graduate/Undergraduate Proce control ytem Project. Our Tutor being experienced and proficient
Our online Tutor are available 4*7 to provide Help with Proce control ytem Homework/Aignment or a long term Graduate/Undergraduate Proce control ytem Project. Our Tutor being experienced and proficient
Lecture 21. The Lovasz splitting-off lemma Topics in Combinatorial Optimization April 29th, 2004
 18.997 Topic in Combinatorial Optimization April 29th, 2004 Lecture 21 Lecturer: Michel X. Goeman Scribe: Mohammad Mahdian 1 The Lovaz plitting-off lemma Lovaz plitting-off lemma tate the following. Theorem
18.997 Topic in Combinatorial Optimization April 29th, 2004 Lecture 21 Lecturer: Michel X. Goeman Scribe: Mohammad Mahdian 1 The Lovaz plitting-off lemma Lovaz plitting-off lemma tate the following. Theorem
Vector-Space Methods and Kirchhoff Graphs for Reaction Networks
 Vector-Space Method and Kirchhoff Graph for Reaction Network Joeph D. Fehribach Fuel Cell Center WPI Mathematical Science and Chemical Engineering 00 Intitute Rd. Worceter, MA 0609-2247 Thi article preent
Vector-Space Method and Kirchhoff Graph for Reaction Network Joeph D. Fehribach Fuel Cell Center WPI Mathematical Science and Chemical Engineering 00 Intitute Rd. Worceter, MA 0609-2247 Thi article preent
Laplace Transformation
 Univerity of Technology Electromechanical Department Energy Branch Advance Mathematic Laplace Tranformation nd Cla Lecture 6 Page of 7 Laplace Tranformation Definition Suppoe that f(t) i a piecewie continuou
Univerity of Technology Electromechanical Department Energy Branch Advance Mathematic Laplace Tranformation nd Cla Lecture 6 Page of 7 Laplace Tranformation Definition Suppoe that f(t) i a piecewie continuou
At the end of this lesson, the students should be able to understand:
 Intructional Objective: At the end of thi leon, the tudent hould be able to undertand: Baic failure mechanim of riveted joint. Concept of deign of a riveted joint. 1. Strength of riveted joint: Strength
Intructional Objective: At the end of thi leon, the tudent hould be able to undertand: Baic failure mechanim of riveted joint. Concept of deign of a riveted joint. 1. Strength of riveted joint: Strength
Confusion matrices. True / False positives / negatives. INF 4300 Classification III Anne Solberg The agenda today: E.g., testing for cancer
 INF 4300 Claification III Anne Solberg 29.10.14 The agenda today: More on etimating claifier accuracy Cure of dimenionality knn-claification K-mean clutering x i feature vector for pixel i i- The cla label
INF 4300 Claification III Anne Solberg 29.10.14 The agenda today: More on etimating claifier accuracy Cure of dimenionality knn-claification K-mean clutering x i feature vector for pixel i i- The cla label
DIFFERENTIAL EQUATIONS Laplace Transforms. Paul Dawkins
 DIFFERENTIAL EQUATIONS Laplace Tranform Paul Dawkin Table of Content Preface... Laplace Tranform... Introduction... The Definition... 5 Laplace Tranform... 9 Invere Laplace Tranform... Step Function...
DIFFERENTIAL EQUATIONS Laplace Tranform Paul Dawkin Table of Content Preface... Laplace Tranform... Introduction... The Definition... 5 Laplace Tranform... 9 Invere Laplace Tranform... Step Function...
RELIABILITY OF REPAIRABLE k out of n: F SYSTEM HAVING DISCRETE REPAIR AND FAILURE TIMES DISTRIBUTIONS
 www.arpapre.com/volume/vol29iue1/ijrras_29_1_01.pdf RELIABILITY OF REPAIRABLE k out of n: F SYSTEM HAVING DISCRETE REPAIR AND FAILURE TIMES DISTRIBUTIONS Sevcan Demir Atalay 1,* & Özge Elmataş Gültekin
www.arpapre.com/volume/vol29iue1/ijrras_29_1_01.pdf RELIABILITY OF REPAIRABLE k out of n: F SYSTEM HAVING DISCRETE REPAIR AND FAILURE TIMES DISTRIBUTIONS Sevcan Demir Atalay 1,* & Özge Elmataş Gültekin
Jul 4, 2005 turbo_code_primer Revision 0.0. Turbo Code Primer
 Jul 4, 5 turbo_code_primer Reviion. Turbo Code Primer. Introduction Thi document give a quick tutorial on MAP baed turbo coder. Section develop the background theory. Section work through a imple numerical
Jul 4, 5 turbo_code_primer Reviion. Turbo Code Primer. Introduction Thi document give a quick tutorial on MAP baed turbo coder. Section develop the background theory. Section work through a imple numerical
CHAPTER 4 DESIGN OF STATE FEEDBACK CONTROLLERS AND STATE OBSERVERS USING REDUCED ORDER MODEL
 98 CHAPTER DESIGN OF STATE FEEDBACK CONTROLLERS AND STATE OBSERVERS USING REDUCED ORDER MODEL INTRODUCTION The deign of ytem uing tate pace model for the deign i called a modern control deign and it i
98 CHAPTER DESIGN OF STATE FEEDBACK CONTROLLERS AND STATE OBSERVERS USING REDUCED ORDER MODEL INTRODUCTION The deign of ytem uing tate pace model for the deign i called a modern control deign and it i
Preemptive scheduling on a small number of hierarchical machines
 Available online at www.ciencedirect.com Information and Computation 06 (008) 60 619 www.elevier.com/locate/ic Preemptive cheduling on a mall number of hierarchical machine György Dóa a, Leah Eptein b,
Available online at www.ciencedirect.com Information and Computation 06 (008) 60 619 www.elevier.com/locate/ic Preemptive cheduling on a mall number of hierarchical machine György Dóa a, Leah Eptein b,
The Influence of the Load Condition upon the Radial Distribution of Electromagnetic Vibration and Noise in a Three-Phase Squirrel-Cage Induction Motor
 The Influence of the Load Condition upon the Radial Ditribution of Electromagnetic Vibration and Noie in a Three-Phae Squirrel-Cage Induction Motor Yuta Sato 1, Iao Hirotuka 1, Kazuo Tuboi 1, Maanori Nakamura
The Influence of the Load Condition upon the Radial Ditribution of Electromagnetic Vibration and Noie in a Three-Phae Squirrel-Cage Induction Motor Yuta Sato 1, Iao Hirotuka 1, Kazuo Tuboi 1, Maanori Nakamura
Lecture 17: Analytic Functions and Integrals (See Chapter 14 in Boas)
 Lecture 7: Analytic Function and Integral (See Chapter 4 in Boa) Thi i a good point to take a brief detour and expand on our previou dicuion of complex variable and complex function of complex variable.
Lecture 7: Analytic Function and Integral (See Chapter 4 in Boa) Thi i a good point to take a brief detour and expand on our previou dicuion of complex variable and complex function of complex variable.
On the Isomorphism of Fractional Factorial Designs 1
 journal of complexity 17, 8697 (2001) doi:10.1006jcom.2000.0569, available online at http:www.idealibrary.com on On the Iomorphim of Fractional Factorial Deign 1 Chang-Xing Ma Department of Statitic, Nankai
journal of complexity 17, 8697 (2001) doi:10.1006jcom.2000.0569, available online at http:www.idealibrary.com on On the Iomorphim of Fractional Factorial Deign 1 Chang-Xing Ma Department of Statitic, Nankai
The Hassenpflug Matrix Tensor Notation
 The Haenpflug Matrix Tenor Notation D.N.J. El Dept of Mech Mechatron Eng Univ of Stellenboch, South Africa e-mail: dnjel@un.ac.za 2009/09/01 Abtract Thi i a ample document to illutrate the typeetting of
The Haenpflug Matrix Tenor Notation D.N.J. El Dept of Mech Mechatron Eng Univ of Stellenboch, South Africa e-mail: dnjel@un.ac.za 2009/09/01 Abtract Thi i a ample document to illutrate the typeetting of
Learning Multiplicative Interactions
 CSC2535 2011 Lecture 6a Learning Multiplicative Interaction Geoffrey Hinton Two different meaning of multiplicative If we take two denity model and multiply together their probability ditribution at each
CSC2535 2011 Lecture 6a Learning Multiplicative Interaction Geoffrey Hinton Two different meaning of multiplicative If we take two denity model and multiply together their probability ditribution at each
Advanced Digital Signal Processing. Stationary/nonstationary signals. Time-Frequency Analysis... Some nonstationary signals. Time-Frequency Analysis
 Advanced Digital ignal Proceing Prof. Nizamettin AYDIN naydin@yildiz.edu.tr Time-Frequency Analyi http://www.yildiz.edu.tr/~naydin 2 tationary/nontationary ignal Time-Frequency Analyi Fourier Tranform
Advanced Digital ignal Proceing Prof. Nizamettin AYDIN naydin@yildiz.edu.tr Time-Frequency Analyi http://www.yildiz.edu.tr/~naydin 2 tationary/nontationary ignal Time-Frequency Analyi Fourier Tranform
Root Locus Diagram. Root loci: The portion of root locus when k assume positive values: that is 0
 Objective Root Locu Diagram Upon completion of thi chapter you will be able to: Plot the Root Locu for a given Tranfer Function by varying gain of the ytem, Analye the tability of the ytem from the root
Objective Root Locu Diagram Upon completion of thi chapter you will be able to: Plot the Root Locu for a given Tranfer Function by varying gain of the ytem, Analye the tability of the ytem from the root
Correction for Simple System Example and Notes on Laplace Transforms / Deviation Variables ECHE 550 Fall 2002
 Correction for Simple Sytem Example and Note on Laplace Tranform / Deviation Variable ECHE 55 Fall 22 Conider a tank draining from an initial height of h o at time t =. With no flow into the tank (F in
Correction for Simple Sytem Example and Note on Laplace Tranform / Deviation Variable ECHE 55 Fall 22 Conider a tank draining from an initial height of h o at time t =. With no flow into the tank (F in
A Bluffer s Guide to... Sphericity
 A Bluffer Guide to Sphericity Andy Field Univerity of Suex The ue of repeated meaure, where the ame ubject are teted under a number of condition, ha numerou practical and tatitical benefit. For one thing
A Bluffer Guide to Sphericity Andy Field Univerity of Suex The ue of repeated meaure, where the ame ubject are teted under a number of condition, ha numerou practical and tatitical benefit. For one thing
online learning Unit Workbook 4 RLC Transients
 online learning Pearon BTC Higher National in lectrical and lectronic ngineering (QCF) Unit 5: lectrical & lectronic Principle Unit Workbook 4 in a erie of 4 for thi unit Learning Outcome: RLC Tranient
online learning Pearon BTC Higher National in lectrical and lectronic ngineering (QCF) Unit 5: lectrical & lectronic Principle Unit Workbook 4 in a erie of 4 for thi unit Learning Outcome: RLC Tranient
Factor Analysis with Poisson Output
 Factor Analyi with Poion Output Gopal Santhanam Byron Yu Krihna V. Shenoy, Department of Electrical Engineering, Neurocience Program Stanford Univerity Stanford, CA 94305, USA {gopal,byronyu,henoy}@tanford.edu
Factor Analyi with Poion Output Gopal Santhanam Byron Yu Krihna V. Shenoy, Department of Electrical Engineering, Neurocience Program Stanford Univerity Stanford, CA 94305, USA {gopal,byronyu,henoy}@tanford.edu
Gain and Phase Margins Based Delay Dependent Stability Analysis of Two- Area LFC System with Communication Delays
 Gain and Phae Margin Baed Delay Dependent Stability Analyi of Two- Area LFC Sytem with Communication Delay Şahin Sönmez and Saffet Ayaun Department of Electrical Engineering, Niğde Ömer Halidemir Univerity,
Gain and Phae Margin Baed Delay Dependent Stability Analyi of Two- Area LFC Sytem with Communication Delay Şahin Sönmez and Saffet Ayaun Department of Electrical Engineering, Niğde Ömer Halidemir Univerity,
Question 1 Equivalent Circuits
 MAE 40 inear ircuit Fall 2007 Final Intruction ) Thi exam i open book You may ue whatever written material you chooe, including your cla note and textbook You may ue a hand calculator with no communication
MAE 40 inear ircuit Fall 2007 Final Intruction ) Thi exam i open book You may ue whatever written material you chooe, including your cla note and textbook You may ue a hand calculator with no communication
Stochastic Perishable Inventory Control in a Service Facility System Maintaining Inventory for Service: Semi Markov Decision Problem
 Stochatic Perihable Inventory Control in a Service Facility Sytem Maintaining Inventory for Service: Semi Markov Deciion Problem R.Mugeh 1,S.Krihnakumar 2, and C.Elango 3 1 mugehrengawamy@gmail.com 2 krihmathew@gmail.com
Stochatic Perihable Inventory Control in a Service Facility Sytem Maintaining Inventory for Service: Semi Markov Deciion Problem R.Mugeh 1,S.Krihnakumar 2, and C.Elango 3 1 mugehrengawamy@gmail.com 2 krihmathew@gmail.com
Math 273 Solutions to Review Problems for Exam 1
 Math 7 Solution to Review Problem for Exam True or Fale? Circle ONE anwer for each Hint: For effective tudy, explain why if true and give a counterexample if fale (a) T or F : If a b and b c, then a c
Math 7 Solution to Review Problem for Exam True or Fale? Circle ONE anwer for each Hint: For effective tudy, explain why if true and give a counterexample if fale (a) T or F : If a b and b c, then a c
Improving the Efficiency of a Digital Filtering Scheme for Diabatic Initialization
 1976 MONTHLY WEATHER REVIEW VOLUME 15 Improving the Efficiency of a Digital Filtering Scheme for Diabatic Initialization PETER LYNCH Met Éireann, Dublin, Ireland DOMINIQUE GIARD CNRM/GMAP, Météo-France,
1976 MONTHLY WEATHER REVIEW VOLUME 15 Improving the Efficiency of a Digital Filtering Scheme for Diabatic Initialization PETER LYNCH Met Éireann, Dublin, Ireland DOMINIQUE GIARD CNRM/GMAP, Météo-France,
Math Skills. Scientific Notation. Uncertainty in Measurements. Appendix A5 SKILLS HANDBOOK
 ppendix 5 Scientific Notation It i difficult to work with very large or very mall number when they are written in common decimal notation. Uually it i poible to accommodate uch number by changing the SI
ppendix 5 Scientific Notation It i difficult to work with very large or very mall number when they are written in common decimal notation. Uually it i poible to accommodate uch number by changing the SI
Unavoidable Cycles in Polynomial-Based Time-Invariant LDPC Convolutional Codes
 European Wirele, April 7-9,, Vienna, Autria ISBN 978--87-4-9 VE VERLAG GMBH Unavoidable Cycle in Polynomial-Baed Time-Invariant LPC Convolutional Code Hua Zhou and Norbert Goertz Intitute of Telecommunication
European Wirele, April 7-9,, Vienna, Autria ISBN 978--87-4-9 VE VERLAG GMBH Unavoidable Cycle in Polynomial-Baed Time-Invariant LPC Convolutional Code Hua Zhou and Norbert Goertz Intitute of Telecommunication
66 Lecture 3 Random Search Tree i unique. Lemma 3. Let X and Y be totally ordered et, and let be a function aigning a ditinct riority in Y to each ele
 Lecture 3 Random Search Tree In thi lecture we will decribe a very imle robabilitic data tructure that allow inert, delete, and memberhi tet (among other oeration) in exected logarithmic time. Thee reult
Lecture 3 Random Search Tree In thi lecture we will decribe a very imle robabilitic data tructure that allow inert, delete, and memberhi tet (among other oeration) in exected logarithmic time. Thee reult
New bounds for Morse clusters
 New bound for More cluter Tamá Vinkó Advanced Concept Team, European Space Agency, ESTEC Keplerlaan 1, 2201 AZ Noordwijk, The Netherland Tama.Vinko@ea.int and Arnold Neumaier Fakultät für Mathematik, Univerität
New bound for More cluter Tamá Vinkó Advanced Concept Team, European Space Agency, ESTEC Keplerlaan 1, 2201 AZ Noordwijk, The Netherland Tama.Vinko@ea.int and Arnold Neumaier Fakultät für Mathematik, Univerität
Stochastic Neoclassical Growth Model
 Stochatic Neoclaical Growth Model Michael Bar May 22, 28 Content Introduction 2 2 Stochatic NGM 2 3 Productivity Proce 4 3. Mean........................................ 5 3.2 Variance......................................
Stochatic Neoclaical Growth Model Michael Bar May 22, 28 Content Introduction 2 2 Stochatic NGM 2 3 Productivity Proce 4 3. Mean........................................ 5 3.2 Variance......................................
Reliability Analysis of Embedded System with Different Modes of Failure Emphasizing Reboot Delay
 International Journal of Applied Science and Engineering 3., 4: 449-47 Reliability Analyi of Embedded Sytem with Different Mode of Failure Emphaizing Reboot Delay Deepak Kumar* and S. B. Singh Department
International Journal of Applied Science and Engineering 3., 4: 449-47 Reliability Analyi of Embedded Sytem with Different Mode of Failure Emphaizing Reboot Delay Deepak Kumar* and S. B. Singh Department
Sampling and the Discrete Fourier Transform
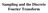 Sampling and the Dicrete Fourier Tranform Sampling Method Sampling i mot commonly done with two device, the ample-and-hold (S/H) and the analog-to-digital-converter (ADC) The S/H acquire a CT ignal at
Sampling and the Dicrete Fourier Tranform Sampling Method Sampling i mot commonly done with two device, the ample-and-hold (S/H) and the analog-to-digital-converter (ADC) The S/H acquire a CT ignal at
Design spacecraft external surfaces to ensure 95 percent probability of no mission-critical failures from particle impact.
 PREFERRED RELIABILITY PAGE 1 OF 6 PRACTICES METEOROIDS & SPACE DEBRIS Practice: Deign pacecraft external urface to enure 95 percent probability of no miion-critical failure from particle impact. Benefit:
PREFERRED RELIABILITY PAGE 1 OF 6 PRACTICES METEOROIDS & SPACE DEBRIS Practice: Deign pacecraft external urface to enure 95 percent probability of no miion-critical failure from particle impact. Benefit:
Unified Design Method for Flexure and Debonding in FRP Retrofitted RC Beams
 Unified Deign Method for Flexure and Debonding in FRP Retrofitted RC Beam G.X. Guan, Ph.D. 1 ; and C.J. Burgoyne 2 Abtract Flexural retrofitting of reinforced concrete (RC) beam uing fibre reinforced polymer
Unified Deign Method for Flexure and Debonding in FRP Retrofitted RC Beam G.X. Guan, Ph.D. 1 ; and C.J. Burgoyne 2 Abtract Flexural retrofitting of reinforced concrete (RC) beam uing fibre reinforced polymer
Optimization model in Input output analysis and computable general. equilibrium by using multiple criteria non-linear programming.
 Optimization model in Input output analyi and computable general equilibrium by uing multiple criteria non-linear programming Jing He * Intitute of ytem cience, cademy of Mathematic and ytem cience Chinee
Optimization model in Input output analyi and computable general equilibrium by uing multiple criteria non-linear programming Jing He * Intitute of ytem cience, cademy of Mathematic and ytem cience Chinee
STOCHASTIC GENERALIZED TRANSPORTATION PROBLEM WITH DISCRETE DISTRIBUTION OF DEMAND
 OPERATIONS RESEARCH AND DECISIONS No. 4 203 DOI: 0.5277/ord30402 Marcin ANHOLCER STOCHASTIC GENERALIZED TRANSPORTATION PROBLEM WITH DISCRETE DISTRIBUTION OF DEMAND The generalized tranportation problem
OPERATIONS RESEARCH AND DECISIONS No. 4 203 DOI: 0.5277/ord30402 Marcin ANHOLCER STOCHASTIC GENERALIZED TRANSPORTATION PROBLEM WITH DISCRETE DISTRIBUTION OF DEMAND The generalized tranportation problem
SERIES COMPENSATION: VOLTAGE COMPENSATION USING DVR (Lectures 41-48)
 Chapter 5 SERIES COMPENSATION: VOLTAGE COMPENSATION USING DVR (Lecture 41-48) 5.1 Introduction Power ytem hould enure good quality of electric power upply, which mean voltage and current waveform hould
Chapter 5 SERIES COMPENSATION: VOLTAGE COMPENSATION USING DVR (Lecture 41-48) 5.1 Introduction Power ytem hould enure good quality of electric power upply, which mean voltage and current waveform hould
Approximating discrete probability distributions with Bayesian networks
 Approximating dicrete probability ditribution with Bayeian network Jon Williamon Department of Philoophy King College, Str and, London, WC2R 2LS, UK Abtract I generalie the argument of [Chow & Liu 1968]
Approximating dicrete probability ditribution with Bayeian network Jon Williamon Department of Philoophy King College, Str and, London, WC2R 2LS, UK Abtract I generalie the argument of [Chow & Liu 1968]
V = 4 3 πr3. d dt V = d ( 4 dv dt. = 4 3 π d dt r3 dv π 3r2 dv. dt = 4πr 2 dr
 0.1 Related Rate In many phyical ituation we have a relationhip between multiple quantitie, and we know the rate at which one of the quantitie i changing. Oftentime we can ue thi relationhip a a convenient
0.1 Related Rate In many phyical ituation we have a relationhip between multiple quantitie, and we know the rate at which one of the quantitie i changing. Oftentime we can ue thi relationhip a a convenient
1. The F-test for Equality of Two Variances
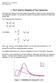 . The F-tet for Equality of Two Variance Previouly we've learned how to tet whether two population mean are equal, uing data from two independent ample. We can alo tet whether two population variance are
. The F-tet for Equality of Two Variance Previouly we've learned how to tet whether two population mean are equal, uing data from two independent ample. We can alo tet whether two population variance are
III.9. THE HYSTERESIS CYCLE OF FERROELECTRIC SUBSTANCES
 III.9. THE HYSTERESIS CYCLE OF FERROELECTRIC SBSTANCES. Work purpoe The analyi of the behaviour of a ferroelectric ubtance placed in an eternal electric field; the dependence of the electrical polariation
III.9. THE HYSTERESIS CYCLE OF FERROELECTRIC SBSTANCES. Work purpoe The analyi of the behaviour of a ferroelectric ubtance placed in an eternal electric field; the dependence of the electrical polariation
CHEAP CONTROL PERFORMANCE LIMITATIONS OF INPUT CONSTRAINED LINEAR SYSTEMS
 Copyright 22 IFAC 5th Triennial World Congre, Barcelona, Spain CHEAP CONTROL PERFORMANCE LIMITATIONS OF INPUT CONSTRAINED LINEAR SYSTEMS Tritan Pérez Graham C. Goodwin Maria M. Serón Department of Electrical
Copyright 22 IFAC 5th Triennial World Congre, Barcelona, Spain CHEAP CONTROL PERFORMANCE LIMITATIONS OF INPUT CONSTRAINED LINEAR SYSTEMS Tritan Pérez Graham C. Goodwin Maria M. Serón Department of Electrical
A BATCH-ARRIVAL QUEUE WITH MULTIPLE SERVERS AND FUZZY PARAMETERS: PARAMETRIC PROGRAMMING APPROACH
 Mathematical and Computational Application Vol. 11 No. pp. 181-191 006. Aociation for Scientific Reearch A BATCH-ARRIVA QEE WITH MTIPE SERVERS AND FZZY PARAMETERS: PARAMETRIC PROGRAMMING APPROACH Jau-Chuan
Mathematical and Computational Application Vol. 11 No. pp. 181-191 006. Aociation for Scientific Reearch A BATCH-ARRIVA QEE WITH MTIPE SERVERS AND FZZY PARAMETERS: PARAMETRIC PROGRAMMING APPROACH Jau-Chuan
The Secret Life of the ax + b Group
 The Secret Life of the ax + b Group Linear function x ax + b are prominent if not ubiquitou in high chool mathematic, beginning in, or now before, Algebra I. In particular, they are prime exhibit in any
The Secret Life of the ax + b Group Linear function x ax + b are prominent if not ubiquitou in high chool mathematic, beginning in, or now before, Algebra I. In particular, they are prime exhibit in any
Lecture 8: Period Finding: Simon s Problem over Z N
 Quantum Computation (CMU 8-859BB, Fall 205) Lecture 8: Period Finding: Simon Problem over Z October 5, 205 Lecturer: John Wright Scribe: icola Rech Problem A mentioned previouly, period finding i a rephraing
Quantum Computation (CMU 8-859BB, Fall 205) Lecture 8: Period Finding: Simon Problem over Z October 5, 205 Lecturer: John Wright Scribe: icola Rech Problem A mentioned previouly, period finding i a rephraing
3.1 The Revised Simplex Algorithm. 3 Computational considerations. Thus, we work with the following tableau. Basic observations = CARRY. ... m.
 3 Computational conideration In what follow, we analyze the complexity of the Simplex algorithm more in detail For thi purpoe, we focu on the update proce in each iteration of thi procedure Clearly, ince,
3 Computational conideration In what follow, we analyze the complexity of the Simplex algorithm more in detail For thi purpoe, we focu on the update proce in each iteration of thi procedure Clearly, ince,
ALLOCATING BANDWIDTH FOR BURSTY CONNECTIONS
 SIAM J. COMPUT. Vol. 30, No. 1, pp. 191 217 c 2000 Society for Indutrial and Applied Mathematic ALLOCATING BANDWIDTH FOR BURSTY CONNECTIONS JON KLEINBERG, YUVAL RABANI, AND ÉVA TARDOS Abtract. In thi paper,
SIAM J. COMPUT. Vol. 30, No. 1, pp. 191 217 c 2000 Society for Indutrial and Applied Mathematic ALLOCATING BANDWIDTH FOR BURSTY CONNECTIONS JON KLEINBERG, YUVAL RABANI, AND ÉVA TARDOS Abtract. In thi paper,
Evolutionary Algorithms Based Fixed Order Robust Controller Design and Robustness Performance Analysis
 Proceeding of 01 4th International Conference on Machine Learning and Computing IPCSIT vol. 5 (01) (01) IACSIT Pre, Singapore Evolutionary Algorithm Baed Fixed Order Robut Controller Deign and Robutne
Proceeding of 01 4th International Conference on Machine Learning and Computing IPCSIT vol. 5 (01) (01) IACSIT Pre, Singapore Evolutionary Algorithm Baed Fixed Order Robut Controller Deign and Robutne
Performance Evaluation
 Performance Evaluation 95 (206) 40 Content lit available at ScienceDirect Performance Evaluation journal homepage: www.elevier.com/locate/peva Optimal cheduling in call center with a callback option Benjamin
Performance Evaluation 95 (206) 40 Content lit available at ScienceDirect Performance Evaluation journal homepage: www.elevier.com/locate/peva Optimal cheduling in call center with a callback option Benjamin
What lies between Δx E, which represents the steam valve, and ΔP M, which is the mechanical power into the synchronous machine?
 A 2.0 Introduction In the lat et of note, we developed a model of the peed governing mechanim, which i given below: xˆ K ( Pˆ ˆ) E () In thee note, we want to extend thi model o that it relate the actual
A 2.0 Introduction In the lat et of note, we developed a model of the peed governing mechanim, which i given below: xˆ K ( Pˆ ˆ) E () In thee note, we want to extend thi model o that it relate the actual
Finite Element Analysis of a Fiber Bragg Grating Accelerometer for Performance Optimization
 Finite Element Analyi of a Fiber Bragg Grating Accelerometer for Performance Optimization N. Baumallick*, P. Biwa, K. Dagupta and S. Bandyopadhyay Fiber Optic Laboratory, Central Gla and Ceramic Reearch
Finite Element Analyi of a Fiber Bragg Grating Accelerometer for Performance Optimization N. Baumallick*, P. Biwa, K. Dagupta and S. Bandyopadhyay Fiber Optic Laboratory, Central Gla and Ceramic Reearch
Lecture 15 - Current. A Puzzle... Advanced Section: Image Charge for Spheres. Image Charge for a Grounded Spherical Shell
 Lecture 15 - Current Puzzle... Suppoe an infinite grounded conducting plane lie at z = 0. charge q i located at a height h above the conducting plane. Show in three different way that the potential below
Lecture 15 - Current Puzzle... Suppoe an infinite grounded conducting plane lie at z = 0. charge q i located at a height h above the conducting plane. Show in three different way that the potential below
UNIT 15 RELIABILITY EVALUATION OF k-out-of-n AND STANDBY SYSTEMS
 UNIT 1 RELIABILITY EVALUATION OF k-out-of-n AND STANDBY SYSTEMS Structure 1.1 Introduction Objective 1.2 Redundancy 1.3 Reliability of k-out-of-n Sytem 1.4 Reliability of Standby Sytem 1. Summary 1.6 Solution/Anwer
UNIT 1 RELIABILITY EVALUATION OF k-out-of-n AND STANDBY SYSTEMS Structure 1.1 Introduction Objective 1.2 Redundancy 1.3 Reliability of k-out-of-n Sytem 1.4 Reliability of Standby Sytem 1. Summary 1.6 Solution/Anwer
Beta Burr XII OR Five Parameter Beta Lomax Distribution: Remarks and Characterizations
 Marquette Univerity e-publication@marquette Mathematic, Statitic and Computer Science Faculty Reearch and Publication Mathematic, Statitic and Computer Science, Department of 6-1-2014 Beta Burr XII OR
Marquette Univerity e-publication@marquette Mathematic, Statitic and Computer Science Faculty Reearch and Publication Mathematic, Statitic and Computer Science, Department of 6-1-2014 Beta Burr XII OR
Coupling of Three-Phase Sequence Circuits Due to Line and Load Asymmetries
 Coupling of Three-Phae Sequence Circuit Due to Line and Load Aymmetrie DEGO BELLAN Department of Electronic nformation and Bioengineering Politecnico di Milano Piazza Leonardo da inci 01 Milano TALY diego.ellan@polimi.it
Coupling of Three-Phae Sequence Circuit Due to Line and Load Aymmetrie DEGO BELLAN Department of Electronic nformation and Bioengineering Politecnico di Milano Piazza Leonardo da inci 01 Milano TALY diego.ellan@polimi.it
Inference for Two Stage Cluster Sampling: Equal SSU per PSU. Projections of SSU Random Variables on Each SSU selection.
 Inference for Two Stage Cluter Sampling: Equal SSU per PSU Projection of SSU andom Variable on Eac SSU election By Ed Stanek Introduction We review etimating equation for PSU mean in a two tage cluter
Inference for Two Stage Cluter Sampling: Equal SSU per PSU Projection of SSU andom Variable on Eac SSU election By Ed Stanek Introduction We review etimating equation for PSU mean in a two tage cluter
