Learning Theory: Basic Guarantees
|
|
|
- Edwin Jessie Harvey
- 5 years ago
- Views:
Transcription
1 Learning Theory: Basic Guarantees Daniel Khashabi Fall 2014 Last Update: April 28, Introduction The Learning Theory 1, is somewhat least practical part of Machine Learning, which is most about the theoretical guarantees in learning concepts, in different conditions and scenarios. These guarantees are usually expressed in the form of probabilistic concentration of some measure, around some optimal value which is unknown and need to discovered. These bounds are functions of problem specifications, for example, The number of samples: the more samples we have, there is a better chance of learning. The easiness of the underlying distribution need to be learned. The generalization power (or flexibility) of the family of the functions which is being used to approximate the target distribution. To begin with let s start with a simple example. Suppose we have a sequence of binary observations: y 1,..., y n, y i {0, 1} Consider the following tasks: Estimation: One task is to model this binary sequence. We want to take the easy way and model it with Binomial distribution, with parameter p. We call a good parameter for our model ˆp that models the original sequence is called the Estimation problem. Suppose someone tells us that the original sequence is sampled i.i.d. from a Bernoulli distribution with parameter p. In this case we can create an averaging estimation ˆp = 1 n n i=1 y i and have the following bound on our estimation: p p < ɛ(n, δ) with probability at least 1 δ (1) where ɛ(n, δ) is proportional to 1 n. In general, we are looking for finding tighter estimations ( i.e. ɛ(n, δ) getting smaller with faster rate). In finding the above bound, we assumed that the original samples are from a Bernoulli distribution. One challenge in real world is that, we don t know from which distribution 1 Some people that are on the statistics side usually call it, Statistical Learning Theory, and others at the computational side, call it Computational Learning Theory. I was fortunate to work with people from the both sides, and these notes will include both computational and statistical tastes of the problems. 1
2 the data is coming from, and therefore finding bounds on estimations is not very trivial. Estimation in real problems means, learning the best model which describes the model, which is our first problem in the learning theory. Batch prediction: Suppose, given a model for the sequence we want to predict the next coming number y n+1 {0, 1}. What is the best prediction and how do we define it? A good measure is to compare the number of the mistakes our prediction might make, relative to the total number of the mistakes that the best algorithm could make in retrospect. R n = 1 1{ŷ i y i } min E yi P1{y n y i y i } (2) i i The above value is usually called Regret. The second term min y i E yi P1{y i y i } is the minimum achievable expected loss, on observations sampled from the distribution P. Without making any assumptions about P, evaluating min y i E yi P1{y i y i } is almost impossible. Let s say the data is coming from a Bernoulli distributions with parameter p (i.e. P = Ber(p )) and we are using our previous estimate ˆp n = 1 n n i=1 y i. In this case, the expected error by the best estimation is (why?): min E y yi Ber(p )1{y i y i } min{p, 1 p } i The best estimator for y n+1 (minimizer of the regret) is the majority vote (why?): y n+1 = 1{ˆp n > 0.5} If p = ˆp, our prediction is exact. But with limited data we have the bound 1 on estimation of ˆp, which means that we can find a similar bound on our prediction. Again, like the estimation, one challenge is that, we don t know if the data is coming from a Binomial distribution or not, which adds further complication. Online prediction: This scenario is very similar to the previous case, but instead of having all the data together, we ate getting one by one up to the i-th instance, and we are suppose to make the best prediction for the (i + 1)-th label and then see the real value. This is called online learning since we learn the model by seeing the data sequentially, and at each observation we make prediction based on previous observations and past predictions. What is the best best prediction? Again we resort to the Regret in Equation 2. At each step j n we use choose the y j+1 which minimizes R j. Like the previous type, the best prediction is via majority vote up to step j: y j+1 = 1{ˆp j > 0.5}, where ˆp j = 1 j Although the answer to online and batch prediction in this example were very similar, in more complicated problems their answers can be very different. Remark 1. Consider the strong Law of Large numbers, which says there exists a predictor, without any assumptions on the generative process of data, such that lim sup R n 0, n a.s. although it does not say anything about this magical method! 2 j i=1 y i
3 Proposition 1. Our method for the Bernoulli example, by minimizing regret (either batch or online case) with y n+1 = 1{ˆp n > 0.5} can be arbitrary bad, depending on the sequence. Suppose there is a sequence of {1, 0} with alternating signs. The predictor will also alternate between 0 and 1, but in opposite of the observation sequence. In other words, this predictor will make mistake on all of the instances. In fact, many problems are like this; without many assumption on the underlying generative process for the data, it is almost impossible to come up with prediction guarantees, for a fixed predictor. One other method is to find guarantees in expectation (rather than finding deterministic guarantees). We will talk more about randomization in later sections. Problem 1 (Randomized bound). Consider the following two problems: 1. Define a function φ(a) to be stable, iff φ(a) φ(a ) 1 n, for any a, a with a a 1 = 1 Suppose we find a stable function such that it upperbounds expected average of mistakes: [ ] 1 E 1{ŷ i y i } φ n (y 1,..., y n ), y 1,..., y n n i Prove that this upper bound holds, if and only if, for a uniform distribution of {0, 1} n, Eφ n (y 1,..., y n ) 1 2, y 1,..., y n 2. Show that, using the previous characterization of φ n (.) show existence of an algorithm that achieves the following guarantee: [ ] 1 E 1{ŷ i y i } min{ˆp n, 1 ˆp n } + Cn 1/2 n What is the smallest value of C? Hint: The term min{ˆp n, 1 ˆp n } is at least Initial steps to model learning 2.1 Some combinatorial problems and consistency i To make the progress we will start with some combinatorial problems, and define our goal. In these problems we aim to reach at consistency, which is defined as following: Definition 1 (Consistency). A set of labeled examples are given as S. Suppose we want to to learn to predict S, by choosing a concept c, that belongs to a concept class C. If c is consistent with all of the elements in S, we output it; otherwise we output that there is no consistent concept. Now let s read about some problems. 3
4 x 4 = 1 N x 8 = 0 N x 8 = 0 N Y Y Y True False True Figure 1: An example of a decision list. Problem 2 (Monotone CNFs). Suppose we have binary feature vectors of size d. Our concept class is the set of all CNFs of the feature values (without negation). For example, one feature vector, and its associated label could be the following: , + Obviously d = 10. A concept consistent with the above instance is x 1 x 2 x 7 x 10. Now a class of instances S is given to us, and we want to find a consistent function with S. Here is an algorithm that would do this for us: Remove all of the features (from all of the instances), that are zero in at least one positive instance (Since these features cannot be included in the target function). Take AND of the every feature remained. If nothing is remained, output that such consistent function is impossible to be made. There is a Monotone DNF problem, similar to the Monotone-CNF, but replaced with. A consistent function for this concept class could be found using the De Morgan law and solution for the Monotone CNF. There are similar and relevant problems: non-monotone CNF or simply CNF problem, in which we can use negations for each feature vector (Similarly non-monotone DNF or simply DNF problem). If we limit the size of each laterals to k features, we call it k CNF problem (similarly k DNF problem). Another hypothesis class which we will talk about is Decision List. A Decision List is a chain of if-else rules. An example is shown in the Figure 1. This example corresponds to the following rules: x 4 T rue x 8 F alse x 10 T rue... Although in the figure, our conditions are on single features, in general the conditional could be laterals (conjunctions or disjunctions of single features). The case when each literal is a conjunction of k variables is commonly called k-decision List; in the rest of these notes, we will limit ourselves to only one variables. Note that, for each variable there are four possible cases. For example for 4
5 x 1, x 1 T rue x 1 T rue x 1 F alse x 1 F alse As a result, the size of the hypothesis space is H = n!4 n (n! for different orderings). Example 1 (Algorithm to find consistent DL). Given a training data, we want to create decision list consistent with S. Here is a bottom-up algorithm for doing that: Start with an empty list. Find laterals that are consistent with a subset of the data, add it to the end of the DL, and cross-out all of the instances covered. If we fail to find a consistent lateral, output no consistent DL with the data. The above construction of a consistent DL is not unique. One can do a top-down approach, by creating a list of all rules, and removing the inconsistent ones by observing instances (left as an exercise to the reader). Exercise 1. It is easy to show the conjunctions or disjunctions are special cases of decision lists. Show that, decision lists are special cases of Linear Thresholding Functions (LTF). In other words, given any decision list, it can be written as a weighted linear combination of some binary variables. f(x) = { 0 + w i x i < 0 i Proof. For a given decision list, one possible LTF is the following: f(x) = i h(x i )g(x i ) 1 2 i where, { x i if in the decison list, the condition is x i g(x i ) = 1 x i if in the decison list, the condition is x i { +1 if in the decison list outputs T h(x i ) = 1 if in the decison list outputs F Proving this can be done with induction. 5
6 2.2 PAC model Assume we are given labeled data S, sampled i.i.d. from an unknown distribution D over the instance space X, and labeled by some unknown target concept c. Suppose we learn concept ĉ C. If we find a good concept class that is guaranteed to have a desired error rate, with a desired probability, we have a PAC (Probably Approximately Correct) solution for the problem. We will explain this more formally. First let s start explaining the concept on the Decision List problem, which we talked about in the Section 2.1. Example 2 (Decision List Algorithm). Given a training data, we want to create decision list consistent with S. Here is a bottom-up algorithm for doing that: Start with an empty list. Find laterals that are consistent with a subset of the data, add it to the end of the DL, and cross-out all of the instances covered. If we fail to find a consistent lateral, output no consistent DL with the data. The above construction of a consistent DL is not unique. One can do a top-down approach, by creating a list of all rules, and removing the inconsistent ones by observing instances. Now given this algorithm, we show that, if S is of reasonable size, then the hypothesis is approximately correct, or, P [ h H DL with err(h) ɛ] δ Proof. Consider a bad hypothesis h whose error probability is at least ɛ: err(h) ɛ. The probability that this this bad hypothesis is consistent with the training data S (given the independence assumption): (1 ɛ) m Since size of the hypothesis space is at most n!4 n, then the union bound for all of the hypothesis would give us, P [ h H DL with err(h) ɛ is consistent ] H (1 ɛ) m H e ɛ S Equivalently, for any ɛ > 0, δ > 0, and enough training data, S 1 [ ln H + ln 1 ] = 1 [ n ln n + ln 1 ] ɛ δ ɛ δ we will have a Probably Approximately Correct prediction. Remark 2 (Sample complexity). Given a PAC-learnable hypothesis space, and ɛ > 0, δ > 0, the number of the data needed is called sample complexity. 6
7 Exercise 2. Suppose our hypothesis class is conjunction of features. Here is an example, x 1 x 2 x 3... x n x n Given a training set S, give an algorithm that finds a consistent member of this class, and prove that this hypothesis class is PAC-learnable. Hint: For a given, ɛ > 0, δ > 0, you should end up with sample complexity better than 1 ɛ [n ln(3) + ln (1/δ)]. Hint 2: Show that, the size of the hypothesis space is 3 n. After giving example, we give the formal definition. Definition 2 (PAC Learning). If for any concept class C, and any target concept c C, and for any distribution D over the instance space X, and for any given arbitrary δ > 0, ɛ > 0, 1. the algorithm A using the labeled instances sampled with distribution D, produces a hypothesis h H (where H is a hypothesis class), which with probability at least 1 δ produces at most ɛ error. 2. A runs in time poly(n, S ), where S is sample size, and n is size of an example. 3. The sample size needed to achieve this goal is poly(1/ɛ, 1/δ, n, size(c )) Then the algorithm A, PAC-learns the concept class C. Remark 3 (Proper PAC-learning). If H = C, then we call it Proper Learning scenario. In the practical scenarios it is usually the case that, H C. We call the learning agnostic if we simply want to find the best h H we can, without having any prior assumption on the target concept. In this case, instead of trying to reach a constant error probability ɛ, we try to read reach the error by the best predictor, OP T (H) + ɛ. This is related to another notion called regret, which we will talk later. Remark 4 (Weak Learning). If instead of fixing ɛ, we require to learn a hypothesis of error at most 1 2 1/poly(n), it is usually called Weak Learning scenario. Remark 5 (Decision Trees). Decision Trees are not known to be PAC-learnable! Although it might be easy to find a consistent hypothesis of the data (how?). Exercise 3. Find out the reason that, Decision Trees are not PAC-learnable. argument break? Where does the Remark 6. If the computation time is not an issue, any hypothesis class is PAC-learnable! Remark 7. Some drawbacks of the PAC-learning model: 1. It doesn t not consider the prior knowledge or prior belief in the models. 2. It doesn t address the unlabeled or similar scenarios. 7
8 2.3 Mistake Bound model Suppose we are in the online learning scenario. Definition 3. An algorithm A is said to learn the concept class C with mistake-bound C, if for any ordering of the examples consistent with c, the total number of the mistakes made by A is bounded by poly(n, size(c)), where n is size of an example. Remark 8. The definition of the mistake-bound has nothing to do with the running time of the algorithm. Remark 9. Based on the definition of the mistake-bound, it doesn t make sense to talk about how much data is needed for learning. Since the algorithm might see many instances and doesn t make any mistakes (hence, doesn t learn anything!). Definition 4 (MB-learnable). The concept class is called MB-learnable, if there exists an algorthm with a constant mistake bound, and running time poly(n, s). Example 3 (Conjunction of features). Suppose our hypothesis class is conjunction of features. Given a training set S, how can we learn with this hypothesis class? 1. Initialize h to be x 1 x 1 x 2 x 2... x n x n 2. For each instance in the training set x i, do prediction with h(x). 3. If the prediction is false and y i is true, remove all the features, which given x i are false, so that after this h(x i ) will be true. 4. If the prediction is true and y i is false, then return no consistent hypothesis. 5. Return to the step 2. The above algorithm will make at most n mistakes. Since the first mistake will shrink down the size of h to n, and the forthcoming mistakes will reduce the size of the h, by at most one. It can also be shown that, there is no deterministic algorithm to learn this hypothesis class with mistake bound less than n. Consider a training set, in which all of the bits, except the i-th are zero. If there is a deterministic algorithm which correctly predicts the label for the i-th instance. One can create another data, and the label of i-th instance flipped, and the algorithm will make mistake on that. Since this argument can be repeated for any i = 1,..., n, this proves that the mistake bound for any deterministic algorithm is at least n. Exercise 4 (MB for disjunctions). Suppose our hypothesis class is conjunction of features. Given a training set S, how can we learn with this hypothesis class? Present an mistake-bounded algorithm, and find its mistake bound. Hint: Use a similar argument to the previous example, and show the the mistake bound in n. Remark 10. An algorithm A is called conservative, when it updates its current state, when it makes mistake. Proposition 2. MB-learnabality implies PAC-learnability! 8
9 Remark 11. Fancier transformation could give bound O ( 1 ɛ [M + ln(1/δ)])! Exercise 5 (Lazy decision list). Suppose a set of learning data is given. Find a consistent decision list with decision bound O(nL) in a lazy fashion, where L is the size of the target decision list. Generalize this to learning k-decision lists with mistake bound O(n k L). Proof. There are multiple answers to this question. Here we present two answers. Answer 1: Create a list of all possible rules: x 1 T x 1 T x 1 F x 1 F. Also, call the two dummy rules P = {T T, T F }. O(4n + 2). Now run the following algorithm: In overall the number of the rules is 1. Create a decision list with the rules created, with arbitrary order, call it Q. Create a copy of Q and call it Q. 2. Loop over the following steps, until there is no inconsistency (a) Loop over the instances, and find the first rule that fires. (b) If the rule is consistent with the label remove it. (c) If at some point there is no rule fired, add Q to the end of the list, and continue removing the inconsistent rules. (d) If after adding Q no rule gets fired, add the two rules in C to the end of the list, and keep the consistent one. Now we need to prove that this would result in a valid decision list (exercise). To show that this would have mistake bound of O(nL), you just need to show adding new Q to the end of the decision list, wouldn t repeat more than L times(exercise). Answer 2: Consider the same rules we have before in Q and the dummy rules in Q. Consider the union of the rules in U = Q Q. The necessity of having these rules will become clear in the correctness analysis. In overall the number of the rules is O(4n + 2). In this algorithm we will have a notion called level, which is defined in the following form. Suppose we start with the the decision list Q, and remove rule r, and create a new level: Q converted to Q \ {r} else {r} This can be repeated many times to get multiple levels. The representation of levels is just to ease the analysis. The algorithm is the following: 9
10 1. Create a decision list with the rules created, with arbitrary order. 2. Loop over the following steps, until there is no inconsistency (a) Loop over the instances, and find the first rule that fires. (b) If the rule is consistent with the label, move it to the next level. First prove that, choosing the subset of the rules, until the end of the first trivial rule (of the rules in Q ) would give a valid consistent decision list (exercise). Then prove that the mistake bound is O(nL). To prove that, show that the resulting answer will not have more than L levels (exercise). Extending the above answers to the k-decision list, is a trivial extension. Remark 12. In PAC model, we can just pick any consistent model. Can we do the same thing for MC models? 2.4 The halving algorithm Consider this form of the problem. Define an expert to be a function which scores the input. Note that an expert is not necessary a good predictor! Suppose we have n experts, and we want to choose the best one. Here we present a relatively naive algorithm for that, which is based on sequential halving of the search space. At the beginning suppose there is at least one perfect expert (an expert which does not make any mistake on any of the instances). Consider the following algorithm: For each instance, run all the experts, and choose the output label predicted by the majority of the experts, and remove the experts which don t make the majority prediction. This algorithm would make log n mistakes until it finds the best expert. It can easily proved by observing that, at each step we remove almost half of the experts. To be more exact, we remove at least 25% of the remaining experts (why?). Now consider the case when there is not a perfect expert. We can do the same strategy as we had before, but once we cross off all of the experts start over. If the number of mistakes the best expert makes in the hindside is OP T, this algorithm would make O((OP T + 1) log n). 2.5 Weighted Majority algorithm Here instead of crossing off experts, we use a weighted strategy; instead of removing an expert, we halve its weight by half. For decision, choose the prediction, which has the biggest weight. Theorem 1. The weighted majority algorithm has mistake bound 2.4(m + log n), where n is the number of the mistakes, and m is the number of the mistake the best expert has made so far. 10
11 Proof. Define the following two variables: { M = #number of the mistakes made so far. W = #total weight. First, we know that the initial value of the W is n. At each mistake, the total weight W drops by at least %25. So after M mistakes, the total weight is at most n(3/4) M. Also the weight of the best expert is (1/2) m. Then: (1/2) m n(3/4) M M 2.4(m + lg n) Exercise 6. Define an alternative strategy for the weighted majority algorithm and prove that its mistake bound is O(m + log n), where n is the number of the experts, and m is the number of the mistakes the best expert makes in the hind sight. Just like before we choose the expert with the maximum weight, but instead of halving the weights of all the wrong experts, we apply the halving, only if the weight of the expert is at least 1/4 of the average weight of all the experts. Proof. Just like the example we showed, define the following variables: M = #number of the mistakes made so far. W begin = #total weight at the begining of the interval. W end = #total weight at the end of the interval.w (t) = #total weight at time t. First observation is that, the weight of each expert is at least the W (t)/(8n). The reason is that, the weight of each expert gets halved only if its weight is more than W (t)/(8n). Therefore no weight goes bellow W (t)/(8n). Since this holds for all of the weights, essentially this also holds for the weight of the best expert. Since the weight of the best expert gets halved for m times, the weight of the best expert is lower bounded by ( 1 2) m Wstart /(8n). Another observation is that, at each mistake at most W/4 of the total weight is fixed, and at least W/2 W/4 = W/4 gets cut in half. In other words, Which would give us the desired bound. W end = ( ) 1 m W start/(8n) 2 ( ) 7 M W start 8 ( ) 7 M W start 8 Can we make better? yes! If make the strategy randomized, it will give us an improved bound. 11
12 2.6 Randomized Weighted Majority algorithm In the randomized strategy, instead of choosing the decision with maximum weight, we use the weights as probability distribution and choose the label randomly with respect to the weight distribution. Also, let s make the strategy a little more complicated, by multiplying (or dividing) by 1 ɛ (instead of 1/2). Theorem 2. The (expected) mistake bound of the randomized weighted majority algorithm is: M m ln 1 1 ɛ + ln n ɛ The followings are special cases for different values of ɛ: ɛ = 1/2 M 1.39m + 2 log n ɛ = 1/2 M 1.15m + 4 log n ɛ = 1/2 M 1.07m + 8 log n Proof. Suppose at time t, α t is the fraction of the weights (of the experts) that have made mistake. So, we remove ɛα t of the total weight at step t: Note that: ln W (T ) = ln n + W (T ) = n T (1 ɛα t ) t=1 T ln(1 ɛα t ) ln n + ɛ t=1 M = E [# of mistakes ] = ln W (T ) ln n ɛm If the best expert makes m mistake up to time T, we know that: T t=1 α t T t=1 (1 ɛ) m W (T ) m log(1 ɛ) ln W (T ) m ln(1 ɛ) ln n ɛm M 1 ɛ [ m ln(1 ɛ) + ln n] (1 + ɛ/2)m + 1 ln n (3) ɛ α t Remark 13. The bound in the Equation 3 could be written in the following form: E [# of mistakes ] (1 + ɛ)op T + ɛ 1 log n To make tighter bound (and assuming that we know OP T, and OP T logn), we set ɛ = (logn/op T ) 1/2. With simplification it can be shown that ( ) E [# of mistakes ] OP T log n + O T T T As it can be seen, as T +, the regret goes to zero. Algorithms with this property are usually called no-regret algorithms. 12
13 3 Winnow algorithm Developed in more than 20 years ago, in [1]. It is very relevant and similar to the perceptron algorithm, but with different properties. The only difference is that, in the Winnow algorithm, the updates are multiplicative. During this note, we will represent multiple versions of Winnow, but all of them have similar properties and analysis. The key property of the Winnow update rule [1] is that the number of examples required to learn a linear function grows linearly with the number of relevant features and only logarithmically with the total number of features. This is a desirable property if there are many irrelevant features in the instances, while the relevant features might be small. The versions we introduce here all have positive weights, although the Winnow algorithm is not limited to positive weights LTFs. 3.1 Winnow for LTF (Linear Thresholding Function) Consider the following definition for hypothesis class of LTF: Predict positive if i w[i]x[i] n The Winnow algorithm is as following: Initialize all weights w i = 1. Loop over instances (x j, y j ) Given input instance x j, make prediction h(x j ). If h(x j ) y j and y j, then w[i] 2 w[i], for all i. If h(x j ) y j and y j, then w[i] 0, for all i. Note that, disjunction functions are special case of LTF (see??). In other words, any disjunction could represented with an LTF. Therefore, our presented Winnow could solve disjunctions. Theorem 3. Suppose the target function is a (r out of n) disjunction function. The mistake bound of the algorithm presented above is the following: 1 + r(1 + lg n) = O(r lg n) Proof. To prove this, we first prove that, the number of the mistakes on positive instances is bounded. At first, each of weights are 1. Also, on positive instances, only the weights that are less than n can be updated (doubled). In other words, each weight can be updated at most log 2 n + 1 times. Thus the number of the mistakes on positive instances is bounded by: M + r(1 + log 2 n) 13
14 Then we bound the number of the mistakes on negative instances by a constant factor of the number of the mistakes on positive instances, which would result in the final bound. First, note that, when making mistake on negative instances, the value of the total weight decreases at least by n(why?). Also, when making mistake on a positive instance, the total weight increases by at most n. Also, initially the total weight is n. Then, This would give the over bound on mistakes: n + M + n M n > 0 M < M M = M + M + 2r(1 + log 2 n) + 1 O(r(1 + log 2 n)) 3.2 A general form for Winnow Here is a more general algorithm: Initialize all weights w i = 1, and ɛ = 1/(2k). Loop over instances (x j, y j ) Given input instance x j, make prediction h(x j ). If h(x j ) y j and y j = 1, then w[i] w[i](1 + ɛ), for all i. If h(x j ) y j and y j = 1, then w[i] w[i]/(1 + ɛ), for all i that x[i] = 1. Theorem 4. The Winnow algorithm with the above representation makes at most O(rk log n) mistakes. Proof. Suppose the number of the mistakes on positive examples is M +, and the number of the mistakes on negative examples is M. This the mistake bound is M = M + + M. Define the total sum to be S = i w[i] Also define the following short hands: { positive-instance-mistake = p.i.m negative-instance-mistake = n.i.m We know at first: and w[i] = 1, i, S = w[i] = n. i On any p.i.m. the increase of S is at most ɛn. Thus for all the p.i.m. the increase of S is ɛnm +. On ɛ any n.i.m. the decrease of S is at least 1+ɛ n. Thus for all the n.i.m. the decrease of S is ɛ 1+ɛ nm. At the end of the algorithm, the sum is: S = n + ɛnm + 14 ɛ 1 + ɛ nm
15 Since the sum never goes negative then we have the constraint that, S = n + ɛnm + ɛ 1 + ɛ nm 0. (4) We can make another inequality by focusing on the number of the relevant features (attribute) which has size k. For any positive instance, the number of the active features is at least k (in particular the k relevant one), and in the negative instances, the number of the active relevant features is at most k 1. For any feature, suppose we increase its weight c + times, and decrease its weight c times. We know that its weight shouldn t be more than n (unless all predictions become positive). Thus, (1 + ɛ) c + (1 + ɛ) c n (1 + ɛ)c + c n which means the absolute number of increases c + c 2 is upper bounded by log 1+ɛ n. Since this holds for any k feature, the sum of absolute number of increases (sum of coins; see the footnote) for all the relevant features must be less than k log 1+ɛ n. For any p.i.m, the number of the coins added is k (since at least k active relevant feature), and in the n.i.m at most k 1 active instances. And we need to have: km + + (k 1)M k log 1+ɛ n. (5) Combining Equations 4 and 5 we get the following: M O(rk log n) Problem 3. Suppose there exists a w such that, { w.x i c for all i such that y i = +1 w.x i c γ for all i such that y i = 1 Then for the choice of ɛ = γ/2, the mistake bound for the Winnow algorithm is O((l 1 (w )/γ) 2 log n). Hint: think about the variations of i w [i] log 1+ɛ w[i] Proof. Define the potential function at time t to be the following: Φ t = i w [i] log 1+ɛ w t [i] We know the updates could be written in the following short form: w t+1 [i] w t [i](1 + ɛ) yx[i] 2 Increases minus decreases; some people like to think about c + as adding coin on each relevant feature, and c removing relevant feature from the feature. 15
16 where y {±1}, and x[i] {0, 1}. Also given this update we know that: Φ t+1 = i = i w [i] log 1+ɛ w t+1 [i] = ( w [i] log 1+ɛ w t [i](1 + ɛ) yx[i]) i ( w [i] log 1+ɛ w t [i](1 + ɛ) yx[i]) = i w [i] log 1+ɛ w t [i] + i yx[i] = Φ t + i y.w [i].x[i] Φ t+1 = Φ t + i y.w [i].x[i] (6) Based on the assumption in the question, we can make the following conclusions. 1. On positive instances (y = +1), the potential function Φ t increases by at least c. 2. On negative instances (y = 1), the potential function Φ t decreases by at most c γ. At each step we know that (otherwise we never make mistake on positive instances) w[i] n(1 + ɛ). Then, log 1+ɛ w[i] log 1+ɛ n(1 + ɛ) = log 1+ɛ n + 1. i w [i] log 1+ɛ w[i] i w [i] { log 1+ɛ n + 1 } = l 1 (w ) ( 1 + log 1+ɛ n ). Then using the results we got from the Equation 6: M + c M (c γ) l 1 (w ) ( 1 + log 1+ɛ n ) (7) Also from the original analysis, remember the inequality: ɛ n + M + ɛn M 1 + ɛ n 0 (8) Combining these two inequalities proper choice of ɛ as a function of γ, would give us the following bound: ( (l1 (w ) ) 2 M = M + + M O log n) γ If we set l 1 (w ) = 1, it would give the desired bound. Remark 14. One interesting open question is that, can we learn a computationally efficient decition list with mistake bound poly(l, logn)? Note that, although the halving algorithm attains this mistake bound, it is not computationally efficient. 16
17 w γ γ Figure 2: A representation of Perceptron Algorithm updates, and its margin. 4 Perceptron Algorithm The perceptron algorithm is one of the oldest algorithms for learning linear separators which is invented around 1960s. Although being very simple, it is still being widely used. Even many fancier and newer algorithms, are modifications of the this algorithm. Suppose we have linear combination of features x and their weights w, as w.x. If w.x 0, we consider the prediction positive, otherwise we consider it negative. Here is the algorithm in its simplest form: Initialize the weights w = 0 If mistake on positive example, If mistake on negative example, w w + x w w x Theorem 5. Suppose the data (scaled to to the unit ball) is consistent with some LTF with w, such that w.x > 0 Then the number of mistakes is less than 1/γ 2. w = 1 w γ = min.x x x Proof. The key to prove this, is in analyzing the behavior of w and w.w. First, we show that each mistake increases w.w by at least γ. (w + x).w = w.w + x.w w.w + γ And after M mistakes: w.w γm 17
18 Each mistake increases w 2 = w.w by at most one. And after M mistake (updates), w + x 2 = (w + x).(w + x) = w.w + 2w.x + x.x w.w + 1 w M Combining the two inequalities, by knowing that w.w w (since w is a unit vector) we get: And we get M 1 γ 2. γm w.w w M Remark 15. One way of looking at the perceptron updates is optimizing an objective function via gradient descent updates. Specifically if you define the following objective function based on the hinge loss on a given daataset: F (w) = 1 T T max (0, y t (w.x t )) t=1 The gradient descent updates for minimizing this objective would result in the following updates: { w t + ηy t x t y 1 (w.x t ) < 0 w t+1 o.w. w t One can prove that the mistake /update bound for the perceptron is optimal in terms γ. The next theorem is proving this. Theorem 6. The Perceptron algorithm is optimal in terms of γ. No deterministic algorithm can have mistake bound less than 1/γ 2, which maintaining a separation margin of γ. Proof. For proof, we design a set of 1/γ 2 data points, such that they always satisfy the margin separation of γ, and show that, for any algorithm, we can label then in a way that it makes mistake on all the data points. Suppose our data points are the unit vectors e i in dimension i. x 1 = e 1,..., x 1/γ 2 = e 1/γ 2. Consider the following family of target functions: w = γ(±x 1 ± x 2... ± x 1/γ 2) For any of these target functions (with any arbitrary signs) w = 1, and it separates points with margin γ (with respect to any of e i ). So, for any deterministic algorithm, as adversary could choose the signs of the target separator in a way that, it makes mistake on all of the data points. By now, we have seen that, if the data is linearly separable by some (relatively big) γ (largemargin condition) the Perceptron algorithm is a very good algorithm. In the previous case, the analysis were dependent on having a separator and the separation width, γ. But what if we don t have such grantees on our data? Can we get other bounds on our algorithm? (In other words, w is not perfect) 18
19 Problem 4. Remember the Problem 3. We can make a similar statement in the perceptron algorithm. Specifically, suppose there exists a w such that, { w.x i c for all i such that y i = +1 w.x i c γ for all i such that y i = 1 Then the mistake bound for the Perceptron algorithm is O((l 2 (w )l 2 (X)/γ) 2 ). Initialize α of lenght T for each t 1 to T Receive x t ( T ) ŷ t sign s=1 α sy s (x s.x t ) Receive y t Update α t : Return α α t { α t + 1 α t ŷ t y t o.w. Remark 16. One cam make the above dual percentron kernelized (aka Kernel-Perceptron) by simply replacing the dot product x s.x t with a kernel evaluation K(x s, x t ). References [1] Nick Littlestone. Learning quickly when irrelevant attributes abound: A new linear-threshold algorithm. Machine learning, 2(4): , [2] Maxim Raginsky. Lecture notes: Ece 299: Statistical learning theory. Tutorial, [3] Alexander Rakhlin and A Tewari. Lecture notes on online learning. Draft, April, [4] Shai Shalev-Shwartz. Online learning and online convex optimization. Foundations and Trends in Machine Learning, 4(2): ,
Online Learning, Mistake Bounds, Perceptron Algorithm
 Online Learning, Mistake Bounds, Perceptron Algorithm 1 Online Learning So far the focus of the course has been on batch learning, where algorithms are presented with a sample of training data, from which
Online Learning, Mistake Bounds, Perceptron Algorithm 1 Online Learning So far the focus of the course has been on batch learning, where algorithms are presented with a sample of training data, from which
Introduction to Algorithms / Algorithms I Lecturer: Michael Dinitz Topic: Intro to Learning Theory Date: 12/8/16
 600.463 Introduction to Algorithms / Algorithms I Lecturer: Michael Dinitz Topic: Intro to Learning Theory Date: 12/8/16 25.1 Introduction Today we re going to talk about machine learning, but from an
600.463 Introduction to Algorithms / Algorithms I Lecturer: Michael Dinitz Topic: Intro to Learning Theory Date: 12/8/16 25.1 Introduction Today we re going to talk about machine learning, but from an
PAC Learning. prof. dr Arno Siebes. Algorithmic Data Analysis Group Department of Information and Computing Sciences Universiteit Utrecht
 PAC Learning prof. dr Arno Siebes Algorithmic Data Analysis Group Department of Information and Computing Sciences Universiteit Utrecht Recall: PAC Learning (Version 1) A hypothesis class H is PAC learnable
PAC Learning prof. dr Arno Siebes Algorithmic Data Analysis Group Department of Information and Computing Sciences Universiteit Utrecht Recall: PAC Learning (Version 1) A hypothesis class H is PAC learnable
1 Learning Linear Separators
 10-601 Machine Learning Maria-Florina Balcan Spring 2015 Plan: Perceptron algorithm for learning linear separators. 1 Learning Linear Separators Here we can think of examples as being from {0, 1} n or
10-601 Machine Learning Maria-Florina Balcan Spring 2015 Plan: Perceptron algorithm for learning linear separators. 1 Learning Linear Separators Here we can think of examples as being from {0, 1} n or
Web-Mining Agents Computational Learning Theory
 Web-Mining Agents Computational Learning Theory Prof. Dr. Ralf Möller Dr. Özgür Özcep Universität zu Lübeck Institut für Informationssysteme Tanya Braun (Exercise Lab) Computational Learning Theory (Adapted)
Web-Mining Agents Computational Learning Theory Prof. Dr. Ralf Möller Dr. Özgür Özcep Universität zu Lübeck Institut für Informationssysteme Tanya Braun (Exercise Lab) Computational Learning Theory (Adapted)
1 Learning Linear Separators
 8803 Machine Learning Theory Maria-Florina Balcan Lecture 3: August 30, 2011 Plan: Perceptron algorithm for learning linear separators. 1 Learning Linear Separators Here we can think of examples as being
8803 Machine Learning Theory Maria-Florina Balcan Lecture 3: August 30, 2011 Plan: Perceptron algorithm for learning linear separators. 1 Learning Linear Separators Here we can think of examples as being
Midterm: CS 6375 Spring 2015 Solutions
 Midterm: CS 6375 Spring 2015 Solutions The exam is closed book. You are allowed a one-page cheat sheet. Answer the questions in the spaces provided on the question sheets. If you run out of room for an
Midterm: CS 6375 Spring 2015 Solutions The exam is closed book. You are allowed a one-page cheat sheet. Answer the questions in the spaces provided on the question sheets. If you run out of room for an
Computational Learning Theory
 CS 446 Machine Learning Fall 2016 OCT 11, 2016 Computational Learning Theory Professor: Dan Roth Scribe: Ben Zhou, C. Cervantes 1 PAC Learning We want to develop a theory to relate the probability of successful
CS 446 Machine Learning Fall 2016 OCT 11, 2016 Computational Learning Theory Professor: Dan Roth Scribe: Ben Zhou, C. Cervantes 1 PAC Learning We want to develop a theory to relate the probability of successful
CS 446: Machine Learning Lecture 4, Part 2: On-Line Learning
 CS 446: Machine Learning Lecture 4, Part 2: On-Line Learning 0.1 Linear Functions So far, we have been looking at Linear Functions { as a class of functions which can 1 if W1 X separate some data and not
CS 446: Machine Learning Lecture 4, Part 2: On-Line Learning 0.1 Linear Functions So far, we have been looking at Linear Functions { as a class of functions which can 1 if W1 X separate some data and not
1 The Probably Approximately Correct (PAC) Model
 COS 511: Theoretical Machine Learning Lecturer: Rob Schapire Lecture #3 Scribe: Yuhui Luo February 11, 2008 1 The Probably Approximately Correct (PAC) Model A target concept class C is PAC-learnable by
COS 511: Theoretical Machine Learning Lecturer: Rob Schapire Lecture #3 Scribe: Yuhui Luo February 11, 2008 1 The Probably Approximately Correct (PAC) Model A target concept class C is PAC-learnable by
Introduction to Machine Learning
 Introduction to Machine Learning PAC Learning and VC Dimension Varun Chandola Computer Science & Engineering State University of New York at Buffalo Buffalo, NY, USA chandola@buffalo.edu Chandola@UB CSE
Introduction to Machine Learning PAC Learning and VC Dimension Varun Chandola Computer Science & Engineering State University of New York at Buffalo Buffalo, NY, USA chandola@buffalo.edu Chandola@UB CSE
Littlestone s Dimension and Online Learnability
 Littlestone s Dimension and Online Learnability Shai Shalev-Shwartz Toyota Technological Institute at Chicago The Hebrew University Talk at UCSD workshop, February, 2009 Joint work with Shai Ben-David
Littlestone s Dimension and Online Learnability Shai Shalev-Shwartz Toyota Technological Institute at Chicago The Hebrew University Talk at UCSD workshop, February, 2009 Joint work with Shai Ben-David
Computational learning theory. PAC learning. VC dimension.
 Computational learning theory. PAC learning. VC dimension. Petr Pošík Czech Technical University in Prague Faculty of Electrical Engineering Dept. of Cybernetics COLT 2 Concept...........................................................................................................
Computational learning theory. PAC learning. VC dimension. Petr Pošík Czech Technical University in Prague Faculty of Electrical Engineering Dept. of Cybernetics COLT 2 Concept...........................................................................................................
Multiclass Classification-1
 CS 446 Machine Learning Fall 2016 Oct 27, 2016 Multiclass Classification Professor: Dan Roth Scribe: C. Cheng Overview Binary to multiclass Multiclass SVM Constraint classification 1 Introduction Multiclass
CS 446 Machine Learning Fall 2016 Oct 27, 2016 Multiclass Classification Professor: Dan Roth Scribe: C. Cheng Overview Binary to multiclass Multiclass SVM Constraint classification 1 Introduction Multiclass
Recap from end of last time
 Topics in Machine Learning Theory Avrim Blum 09/03/4 Lecture 3: Shifting/Sleeping Experts, the Winnow Algorithm, and L Margin Bounds Recap from end of last time RWM (multiplicative weights alg) p i = w
Topics in Machine Learning Theory Avrim Blum 09/03/4 Lecture 3: Shifting/Sleeping Experts, the Winnow Algorithm, and L Margin Bounds Recap from end of last time RWM (multiplicative weights alg) p i = w
Lecture 25 of 42. PAC Learning, VC Dimension, and Mistake Bounds
 Lecture 25 of 42 PAC Learning, VC Dimension, and Mistake Bounds Thursday, 15 March 2007 William H. Hsu, KSU http://www.kddresearch.org/courses/spring2007/cis732 Readings: Sections 7.4.17.4.3, 7.5.17.5.3,
Lecture 25 of 42 PAC Learning, VC Dimension, and Mistake Bounds Thursday, 15 March 2007 William H. Hsu, KSU http://www.kddresearch.org/courses/spring2007/cis732 Readings: Sections 7.4.17.4.3, 7.5.17.5.3,
Support vector machines Lecture 4
 Support vector machines Lecture 4 David Sontag New York University Slides adapted from Luke Zettlemoyer, Vibhav Gogate, and Carlos Guestrin Q: What does the Perceptron mistake bound tell us? Theorem: The
Support vector machines Lecture 4 David Sontag New York University Slides adapted from Luke Zettlemoyer, Vibhav Gogate, and Carlos Guestrin Q: What does the Perceptron mistake bound tell us? Theorem: The
Computational Learning Theory. Definitions
 Computational Learning Theory Computational learning theory is interested in theoretical analyses of the following issues. What is needed to learn effectively? Sample complexity. How many examples? Computational
Computational Learning Theory Computational learning theory is interested in theoretical analyses of the following issues. What is needed to learn effectively? Sample complexity. How many examples? Computational
From Batch to Transductive Online Learning
 From Batch to Transductive Online Learning Sham Kakade Toyota Technological Institute Chicago, IL 60637 sham@tti-c.org Adam Tauman Kalai Toyota Technological Institute Chicago, IL 60637 kalai@tti-c.org
From Batch to Transductive Online Learning Sham Kakade Toyota Technological Institute Chicago, IL 60637 sham@tti-c.org Adam Tauman Kalai Toyota Technological Institute Chicago, IL 60637 kalai@tti-c.org
An Algorithms-based Intro to Machine Learning
 CMU 15451 lecture 12/08/11 An Algorithmsbased Intro to Machine Learning Plan for today Machine Learning intro: models and basic issues An interesting algorithm for combining expert advice Avrim Blum [Based
CMU 15451 lecture 12/08/11 An Algorithmsbased Intro to Machine Learning Plan for today Machine Learning intro: models and basic issues An interesting algorithm for combining expert advice Avrim Blum [Based
Computational Learning Theory
 09s1: COMP9417 Machine Learning and Data Mining Computational Learning Theory May 20, 2009 Acknowledgement: Material derived from slides for the book Machine Learning, Tom M. Mitchell, McGraw-Hill, 1997
09s1: COMP9417 Machine Learning and Data Mining Computational Learning Theory May 20, 2009 Acknowledgement: Material derived from slides for the book Machine Learning, Tom M. Mitchell, McGraw-Hill, 1997
Lecture 5: Efficient PAC Learning. 1 Consistent Learning: a Bound on Sample Complexity
 Universität zu Lübeck Institut für Theoretische Informatik Lecture notes on Knowledge-Based and Learning Systems by Maciej Liśkiewicz Lecture 5: Efficient PAC Learning 1 Consistent Learning: a Bound on
Universität zu Lübeck Institut für Theoretische Informatik Lecture notes on Knowledge-Based and Learning Systems by Maciej Liśkiewicz Lecture 5: Efficient PAC Learning 1 Consistent Learning: a Bound on
Agnostic Online learnability
 Technical Report TTIC-TR-2008-2 October 2008 Agnostic Online learnability Shai Shalev-Shwartz Toyota Technological Institute Chicago shai@tti-c.org ABSTRACT We study a fundamental question. What classes
Technical Report TTIC-TR-2008-2 October 2008 Agnostic Online learnability Shai Shalev-Shwartz Toyota Technological Institute Chicago shai@tti-c.org ABSTRACT We study a fundamental question. What classes
Computational Learning Theory. CS534 - Machine Learning
 Computational Learning Theory CS534 Machine Learning Introduction Computational learning theory Provides a theoretical analysis of learning Shows when a learning algorithm can be expected to succeed Shows
Computational Learning Theory CS534 Machine Learning Introduction Computational learning theory Provides a theoretical analysis of learning Shows when a learning algorithm can be expected to succeed Shows
Computational Learning Theory
 Computational Learning Theory Slides by and Nathalie Japkowicz (Reading: R&N AIMA 3 rd ed., Chapter 18.5) Computational Learning Theory Inductive learning: given the training set, a learning algorithm
Computational Learning Theory Slides by and Nathalie Japkowicz (Reading: R&N AIMA 3 rd ed., Chapter 18.5) Computational Learning Theory Inductive learning: given the training set, a learning algorithm
A Tutorial on Computational Learning Theory Presented at Genetic Programming 1997 Stanford University, July 1997
 A Tutorial on Computational Learning Theory Presented at Genetic Programming 1997 Stanford University, July 1997 Vasant Honavar Artificial Intelligence Research Laboratory Department of Computer Science
A Tutorial on Computational Learning Theory Presented at Genetic Programming 1997 Stanford University, July 1997 Vasant Honavar Artificial Intelligence Research Laboratory Department of Computer Science
The Perceptron Algorithm
 The Perceptron Algorithm Machine Learning Spring 2018 The slides are mainly from Vivek Srikumar 1 Outline The Perceptron Algorithm Perceptron Mistake Bound Variants of Perceptron 2 Where are we? The Perceptron
The Perceptron Algorithm Machine Learning Spring 2018 The slides are mainly from Vivek Srikumar 1 Outline The Perceptron Algorithm Perceptron Mistake Bound Variants of Perceptron 2 Where are we? The Perceptron
The Perceptron algorithm
 The Perceptron algorithm Tirgul 3 November 2016 Agnostic PAC Learnability A hypothesis class H is agnostic PAC learnable if there exists a function m H : 0,1 2 N and a learning algorithm with the following
The Perceptron algorithm Tirgul 3 November 2016 Agnostic PAC Learnability A hypothesis class H is agnostic PAC learnable if there exists a function m H : 0,1 2 N and a learning algorithm with the following
Lecture 16: Perceptron and Exponential Weights Algorithm
 EECS 598-005: Theoretical Foundations of Machine Learning Fall 2015 Lecture 16: Perceptron and Exponential Weights Algorithm Lecturer: Jacob Abernethy Scribes: Yue Wang, Editors: Weiqing Yu and Andrew
EECS 598-005: Theoretical Foundations of Machine Learning Fall 2015 Lecture 16: Perceptron and Exponential Weights Algorithm Lecturer: Jacob Abernethy Scribes: Yue Wang, Editors: Weiqing Yu and Andrew
Foundations of Machine Learning On-Line Learning. Mehryar Mohri Courant Institute and Google Research
 Foundations of Machine Learning On-Line Learning Mehryar Mohri Courant Institute and Google Research mohri@cims.nyu.edu Motivation PAC learning: distribution fixed over time (training and test). IID assumption.
Foundations of Machine Learning On-Line Learning Mehryar Mohri Courant Institute and Google Research mohri@cims.nyu.edu Motivation PAC learning: distribution fixed over time (training and test). IID assumption.
CS446: Machine Learning Spring Problem Set 4
 CS446: Machine Learning Spring 2017 Problem Set 4 Handed Out: February 27 th, 2017 Due: March 11 th, 2017 Feel free to talk to other members of the class in doing the homework. I am more concerned that
CS446: Machine Learning Spring 2017 Problem Set 4 Handed Out: February 27 th, 2017 Due: March 11 th, 2017 Feel free to talk to other members of the class in doing the homework. I am more concerned that
Active Learning: Disagreement Coefficient
 Advanced Course in Machine Learning Spring 2010 Active Learning: Disagreement Coefficient Handouts are jointly prepared by Shie Mannor and Shai Shalev-Shwartz In previous lectures we saw examples in which
Advanced Course in Machine Learning Spring 2010 Active Learning: Disagreement Coefficient Handouts are jointly prepared by Shie Mannor and Shai Shalev-Shwartz In previous lectures we saw examples in which
Classes of Boolean Functions
 Classes of Boolean Functions Nader H. Bshouty Eyal Kushilevitz Abstract Here we give classes of Boolean functions that considered in COLT. Classes of Functions Here we introduce the basic classes of functions
Classes of Boolean Functions Nader H. Bshouty Eyal Kushilevitz Abstract Here we give classes of Boolean functions that considered in COLT. Classes of Functions Here we introduce the basic classes of functions
Part of the slides are adapted from Ziko Kolter
 Part of the slides are adapted from Ziko Kolter OUTLINE 1 Supervised learning: classification........................................................ 2 2 Non-linear regression/classification, overfitting,
Part of the slides are adapted from Ziko Kolter OUTLINE 1 Supervised learning: classification........................................................ 2 2 Non-linear regression/classification, overfitting,
Online Convex Optimization
 Advanced Course in Machine Learning Spring 2010 Online Convex Optimization Handouts are jointly prepared by Shie Mannor and Shai Shalev-Shwartz A convex repeated game is a two players game that is performed
Advanced Course in Machine Learning Spring 2010 Online Convex Optimization Handouts are jointly prepared by Shie Mannor and Shai Shalev-Shwartz A convex repeated game is a two players game that is performed
Foundations of Machine Learning and Data Science. Lecturer: Avrim Blum Lecture 9: October 7, 2015
 10-806 Foundations of Machine Learning and Data Science Lecturer: Avrim Blum Lecture 9: October 7, 2015 1 Computational Hardness of Learning Today we will talk about some computational hardness results
10-806 Foundations of Machine Learning and Data Science Lecturer: Avrim Blum Lecture 9: October 7, 2015 1 Computational Hardness of Learning Today we will talk about some computational hardness results
Supervised Machine Learning (Spring 2014) Homework 2, sample solutions
 58669 Supervised Machine Learning (Spring 014) Homework, sample solutions Credit for the solutions goes to mainly to Panu Luosto and Joonas Paalasmaa, with some additional contributions by Jyrki Kivinen
58669 Supervised Machine Learning (Spring 014) Homework, sample solutions Credit for the solutions goes to mainly to Panu Luosto and Joonas Paalasmaa, with some additional contributions by Jyrki Kivinen
A Course in Machine Learning
 A Course in Machine Learning Hal Daumé III 10 LEARNING THEORY For nothing ought to be posited without a reason given, unless it is self-evident or known by experience or proved by the authority of Sacred
A Course in Machine Learning Hal Daumé III 10 LEARNING THEORY For nothing ought to be posited without a reason given, unless it is self-evident or known by experience or proved by the authority of Sacred
Name (NetID): (1 Point)
 CS446: Machine Learning Fall 2016 October 25 th, 2016 This is a closed book exam. Everything you need in order to solve the problems is supplied in the body of this exam. This exam booklet contains four
CS446: Machine Learning Fall 2016 October 25 th, 2016 This is a closed book exam. Everything you need in order to solve the problems is supplied in the body of this exam. This exam booklet contains four
Weighted Majority and the Online Learning Approach
 Statistical Techniques in Robotics (16-81, F12) Lecture#9 (Wednesday September 26) Weighted Majority and the Online Learning Approach Lecturer: Drew Bagnell Scribe:Narek Melik-Barkhudarov 1 Figure 1: Drew
Statistical Techniques in Robotics (16-81, F12) Lecture#9 (Wednesday September 26) Weighted Majority and the Online Learning Approach Lecturer: Drew Bagnell Scribe:Narek Melik-Barkhudarov 1 Figure 1: Drew
Name (NetID): (1 Point)
 CS446: Machine Learning (D) Spring 2017 March 16 th, 2017 This is a closed book exam. Everything you need in order to solve the problems is supplied in the body of this exam. This exam booklet contains
CS446: Machine Learning (D) Spring 2017 March 16 th, 2017 This is a closed book exam. Everything you need in order to solve the problems is supplied in the body of this exam. This exam booklet contains
Lecture 4: Linear predictors and the Perceptron
 Lecture 4: Linear predictors and the Perceptron Introduction to Learning and Analysis of Big Data Kontorovich and Sabato (BGU) Lecture 4 1 / 34 Inductive Bias Inductive bias is critical to prevent overfitting.
Lecture 4: Linear predictors and the Perceptron Introduction to Learning and Analysis of Big Data Kontorovich and Sabato (BGU) Lecture 4 1 / 34 Inductive Bias Inductive bias is critical to prevent overfitting.
Online Learning. Jordan Boyd-Graber. University of Colorado Boulder LECTURE 21. Slides adapted from Mohri
 Online Learning Jordan Boyd-Graber University of Colorado Boulder LECTURE 21 Slides adapted from Mohri Jordan Boyd-Graber Boulder Online Learning 1 of 31 Motivation PAC learning: distribution fixed over
Online Learning Jordan Boyd-Graber University of Colorado Boulder LECTURE 21 Slides adapted from Mohri Jordan Boyd-Graber Boulder Online Learning 1 of 31 Motivation PAC learning: distribution fixed over
Lecture 29: Computational Learning Theory
 CS 710: Complexity Theory 5/4/2010 Lecture 29: Computational Learning Theory Instructor: Dieter van Melkebeek Scribe: Dmitri Svetlov and Jake Rosin Today we will provide a brief introduction to computational
CS 710: Complexity Theory 5/4/2010 Lecture 29: Computational Learning Theory Instructor: Dieter van Melkebeek Scribe: Dmitri Svetlov and Jake Rosin Today we will provide a brief introduction to computational
On the tradeoff between computational complexity and sample complexity in learning
 On the tradeoff between computational complexity and sample complexity in learning Shai Shalev-Shwartz School of Computer Science and Engineering The Hebrew University of Jerusalem Joint work with Sham
On the tradeoff between computational complexity and sample complexity in learning Shai Shalev-Shwartz School of Computer Science and Engineering The Hebrew University of Jerusalem Joint work with Sham
Machine Learning (CS 567) Lecture 3
 Machine Learning (CS 567) Lecture 3 Time: T-Th 5:00pm - 6:20pm Location: GFS 118 Instructor: Sofus A. Macskassy (macskass@usc.edu) Office: SAL 216 Office hours: by appointment Teaching assistant: Cheol
Machine Learning (CS 567) Lecture 3 Time: T-Th 5:00pm - 6:20pm Location: GFS 118 Instructor: Sofus A. Macskassy (macskass@usc.edu) Office: SAL 216 Office hours: by appointment Teaching assistant: Cheol
1 Review of the Perceptron Algorithm
 COS 511: Theoretical Machine Learning Lecturer: Rob Schapire Lecture #15 Scribe: (James) Zhen XIANG April, 008 1 Review of the Perceptron Algorithm In the last few lectures, we talked about various kinds
COS 511: Theoretical Machine Learning Lecturer: Rob Schapire Lecture #15 Scribe: (James) Zhen XIANG April, 008 1 Review of the Perceptron Algorithm In the last few lectures, we talked about various kinds
The Perceptron Algorithm, Margins
 The Perceptron Algorithm, Margins MariaFlorina Balcan 08/29/2018 The Perceptron Algorithm Simple learning algorithm for supervised classification analyzed via geometric margins in the 50 s [Rosenblatt
The Perceptron Algorithm, Margins MariaFlorina Balcan 08/29/2018 The Perceptron Algorithm Simple learning algorithm for supervised classification analyzed via geometric margins in the 50 s [Rosenblatt
CS 395T Computational Learning Theory. Scribe: Mike Halcrow. x 4. x 2. x 6
 CS 395T Computational Learning Theory Lecture 3: September 0, 2007 Lecturer: Adam Klivans Scribe: Mike Halcrow 3. Decision List Recap In the last class, we determined that, when learning a t-decision list,
CS 395T Computational Learning Theory Lecture 3: September 0, 2007 Lecturer: Adam Klivans Scribe: Mike Halcrow 3. Decision List Recap In the last class, we determined that, when learning a t-decision list,
Support Vector Machines. Machine Learning Fall 2017
 Support Vector Machines Machine Learning Fall 2017 1 Where are we? Learning algorithms Decision Trees Perceptron AdaBoost 2 Where are we? Learning algorithms Decision Trees Perceptron AdaBoost Produce
Support Vector Machines Machine Learning Fall 2017 1 Where are we? Learning algorithms Decision Trees Perceptron AdaBoost 2 Where are we? Learning algorithms Decision Trees Perceptron AdaBoost Produce
Linear smoother. ŷ = S y. where s ij = s ij (x) e.g. s ij = diag(l i (x))
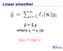 Linear smoother ŷ = S y where s ij = s ij (x) e.g. s ij = diag(l i (x)) 2 Online Learning: LMS and Perceptrons Partially adapted from slides by Ryan Gabbard and Mitch Marcus (and lots original slides by
Linear smoother ŷ = S y where s ij = s ij (x) e.g. s ij = diag(l i (x)) 2 Online Learning: LMS and Perceptrons Partially adapted from slides by Ryan Gabbard and Mitch Marcus (and lots original slides by
CS 446 Machine Learning Fall 2016 Nov 01, Bayesian Learning
 CS 446 Machine Learning Fall 206 Nov 0, 206 Bayesian Learning Professor: Dan Roth Scribe: Ben Zhou, C. Cervantes Overview Bayesian Learning Naive Bayes Logistic Regression Bayesian Learning So far, we
CS 446 Machine Learning Fall 206 Nov 0, 206 Bayesian Learning Professor: Dan Roth Scribe: Ben Zhou, C. Cervantes Overview Bayesian Learning Naive Bayes Logistic Regression Bayesian Learning So far, we
The PAC Learning Framework -II
 The PAC Learning Framework -II Prof. Dan A. Simovici UMB 1 / 1 Outline 1 Finite Hypothesis Space - The Inconsistent Case 2 Deterministic versus stochastic scenario 3 Bayes Error and Noise 2 / 1 Outline
The PAC Learning Framework -II Prof. Dan A. Simovici UMB 1 / 1 Outline 1 Finite Hypothesis Space - The Inconsistent Case 2 Deterministic versus stochastic scenario 3 Bayes Error and Noise 2 / 1 Outline
Comp487/587 - Boolean Formulas
 Comp487/587 - Boolean Formulas 1 Logic and SAT 1.1 What is a Boolean Formula Logic is a way through which we can analyze and reason about simple or complicated events. In particular, we are interested
Comp487/587 - Boolean Formulas 1 Logic and SAT 1.1 What is a Boolean Formula Logic is a way through which we can analyze and reason about simple or complicated events. In particular, we are interested
CS261: A Second Course in Algorithms Lecture #12: Applications of Multiplicative Weights to Games and Linear Programs
 CS26: A Second Course in Algorithms Lecture #2: Applications of Multiplicative Weights to Games and Linear Programs Tim Roughgarden February, 206 Extensions of the Multiplicative Weights Guarantee Last
CS26: A Second Course in Algorithms Lecture #2: Applications of Multiplicative Weights to Games and Linear Programs Tim Roughgarden February, 206 Extensions of the Multiplicative Weights Guarantee Last
Introduction to Machine Learning (67577) Lecture 3
 Introduction to Machine Learning (67577) Lecture 3 Shai Shalev-Shwartz School of CS and Engineering, The Hebrew University of Jerusalem General Learning Model and Bias-Complexity tradeoff Shai Shalev-Shwartz
Introduction to Machine Learning (67577) Lecture 3 Shai Shalev-Shwartz School of CS and Engineering, The Hebrew University of Jerusalem General Learning Model and Bias-Complexity tradeoff Shai Shalev-Shwartz
Minimax risk bounds for linear threshold functions
 CS281B/Stat241B (Spring 2008) Statistical Learning Theory Lecture: 3 Minimax risk bounds for linear threshold functions Lecturer: Peter Bartlett Scribe: Hao Zhang 1 Review We assume that there is a probability
CS281B/Stat241B (Spring 2008) Statistical Learning Theory Lecture: 3 Minimax risk bounds for linear threshold functions Lecturer: Peter Bartlett Scribe: Hao Zhang 1 Review We assume that there is a probability
Computational and Statistical Learning theory
 Computational and Statistical Learning theory Problem set 2 Due: January 31st Email solutions to : karthik at ttic dot edu Notation : Input space : X Label space : Y = {±1} Sample : (x 1, y 1,..., (x n,
Computational and Statistical Learning theory Problem set 2 Due: January 31st Email solutions to : karthik at ttic dot edu Notation : Input space : X Label space : Y = {±1} Sample : (x 1, y 1,..., (x n,
Linear Discrimination Functions
 Laurea Magistrale in Informatica Nicola Fanizzi Dipartimento di Informatica Università degli Studi di Bari November 4, 2009 Outline Linear models Gradient descent Perceptron Minimum square error approach
Laurea Magistrale in Informatica Nicola Fanizzi Dipartimento di Informatica Università degli Studi di Bari November 4, 2009 Outline Linear models Gradient descent Perceptron Minimum square error approach
Generalization bounds
 Advanced Course in Machine Learning pring 200 Generalization bounds Handouts are jointly prepared by hie Mannor and hai halev-hwartz he problem of characterizing learnability is the most basic question
Advanced Course in Machine Learning pring 200 Generalization bounds Handouts are jointly prepared by hie Mannor and hai halev-hwartz he problem of characterizing learnability is the most basic question
Computational Learning Theory
 0. Computational Learning Theory Based on Machine Learning, T. Mitchell, McGRAW Hill, 1997, ch. 7 Acknowledgement: The present slides are an adaptation of slides drawn by T. Mitchell 1. Main Questions
0. Computational Learning Theory Based on Machine Learning, T. Mitchell, McGRAW Hill, 1997, ch. 7 Acknowledgement: The present slides are an adaptation of slides drawn by T. Mitchell 1. Main Questions
Introduction to Computational Learning Theory
 Introduction to Computational Learning Theory The classification problem Consistent Hypothesis Model Probably Approximately Correct (PAC) Learning c Hung Q. Ngo (SUNY at Buffalo) CSE 694 A Fun Course 1
Introduction to Computational Learning Theory The classification problem Consistent Hypothesis Model Probably Approximately Correct (PAC) Learning c Hung Q. Ngo (SUNY at Buffalo) CSE 694 A Fun Course 1
Computational Learning Theory (COLT)
 Computational Learning Theory (COLT) Goals: Theoretical characterization of 1 Difficulty of machine learning problems Under what conditions is learning possible and impossible? 2 Capabilities of machine
Computational Learning Theory (COLT) Goals: Theoretical characterization of 1 Difficulty of machine learning problems Under what conditions is learning possible and impossible? 2 Capabilities of machine
Lecture 11. Linear Soft Margin Support Vector Machines
 CS142: Machine Learning Spring 2017 Lecture 11 Instructor: Pedro Felzenszwalb Scribes: Dan Xiang, Tyler Dae Devlin Linear Soft Margin Support Vector Machines We continue our discussion of linear soft margin
CS142: Machine Learning Spring 2017 Lecture 11 Instructor: Pedro Felzenszwalb Scribes: Dan Xiang, Tyler Dae Devlin Linear Soft Margin Support Vector Machines We continue our discussion of linear soft margin
FORMULATION OF THE LEARNING PROBLEM
 FORMULTION OF THE LERNING PROBLEM MIM RGINSKY Now that we have seen an informal statement of the learning problem, as well as acquired some technical tools in the form of concentration inequalities, we
FORMULTION OF THE LERNING PROBLEM MIM RGINSKY Now that we have seen an informal statement of the learning problem, as well as acquired some technical tools in the form of concentration inequalities, we
10.1 The Formal Model
 67577 Intro. to Machine Learning Fall semester, 2008/9 Lecture 10: The Formal (PAC) Learning Model Lecturer: Amnon Shashua Scribe: Amnon Shashua 1 We have see so far algorithms that explicitly estimate
67577 Intro. to Machine Learning Fall semester, 2008/9 Lecture 10: The Formal (PAC) Learning Model Lecturer: Amnon Shashua Scribe: Amnon Shashua 1 We have see so far algorithms that explicitly estimate
Final Exam, Fall 2002
 15-781 Final Exam, Fall 22 1. Write your name and your andrew email address below. Name: Andrew ID: 2. There should be 17 pages in this exam (excluding this cover sheet). 3. If you need more room to work
15-781 Final Exam, Fall 22 1. Write your name and your andrew email address below. Name: Andrew ID: 2. There should be 17 pages in this exam (excluding this cover sheet). 3. If you need more room to work
The Decision List Machine
 The Decision List Machine Marina Sokolova SITE, University of Ottawa Ottawa, Ont. Canada,K1N-6N5 sokolova@site.uottawa.ca Nathalie Japkowicz SITE, University of Ottawa Ottawa, Ont. Canada,K1N-6N5 nat@site.uottawa.ca
The Decision List Machine Marina Sokolova SITE, University of Ottawa Ottawa, Ont. Canada,K1N-6N5 sokolova@site.uottawa.ca Nathalie Japkowicz SITE, University of Ottawa Ottawa, Ont. Canada,K1N-6N5 nat@site.uottawa.ca
Midterm, Fall 2003
 5-78 Midterm, Fall 2003 YOUR ANDREW USERID IN CAPITAL LETTERS: YOUR NAME: There are 9 questions. The ninth may be more time-consuming and is worth only three points, so do not attempt 9 unless you are
5-78 Midterm, Fall 2003 YOUR ANDREW USERID IN CAPITAL LETTERS: YOUR NAME: There are 9 questions. The ninth may be more time-consuming and is worth only three points, so do not attempt 9 unless you are
1 Overview. 2 Learning from Experts. 2.1 Defining a meaningful benchmark. AM 221: Advanced Optimization Spring 2016
 AM 1: Advanced Optimization Spring 016 Prof. Yaron Singer Lecture 11 March 3rd 1 Overview In this lecture we will introduce the notion of online convex optimization. This is an extremely useful framework
AM 1: Advanced Optimization Spring 016 Prof. Yaron Singer Lecture 11 March 3rd 1 Overview In this lecture we will introduce the notion of online convex optimization. This is an extremely useful framework
Machine Learning. Computational Learning Theory. Eric Xing , Fall Lecture 9, October 5, 2016
 Machine Learning 10-701, Fall 2016 Computational Learning Theory Eric Xing Lecture 9, October 5, 2016 Reading: Chap. 7 T.M book Eric Xing @ CMU, 2006-2016 1 Generalizability of Learning In machine learning
Machine Learning 10-701, Fall 2016 Computational Learning Theory Eric Xing Lecture 9, October 5, 2016 Reading: Chap. 7 T.M book Eric Xing @ CMU, 2006-2016 1 Generalizability of Learning In machine learning
Introduction to Bayesian Learning. Machine Learning Fall 2018
 Introduction to Bayesian Learning Machine Learning Fall 2018 1 What we have seen so far What does it mean to learn? Mistake-driven learning Learning by counting (and bounding) number of mistakes PAC learnability
Introduction to Bayesian Learning Machine Learning Fall 2018 1 What we have seen so far What does it mean to learn? Mistake-driven learning Learning by counting (and bounding) number of mistakes PAC learnability
PAC-learning, VC Dimension and Margin-based Bounds
 More details: General: http://www.learning-with-kernels.org/ Example of more complex bounds: http://www.research.ibm.com/people/t/tzhang/papers/jmlr02_cover.ps.gz PAC-learning, VC Dimension and Margin-based
More details: General: http://www.learning-with-kernels.org/ Example of more complex bounds: http://www.research.ibm.com/people/t/tzhang/papers/jmlr02_cover.ps.gz PAC-learning, VC Dimension and Margin-based
COMPUTATIONAL LEARNING THEORY
 COMPUTATIONAL LEARNING THEORY XIAOXU LI Abstract. This paper starts with basic concepts of computational learning theory and moves on with examples in monomials and learning rays to the final discussion
COMPUTATIONAL LEARNING THEORY XIAOXU LI Abstract. This paper starts with basic concepts of computational learning theory and moves on with examples in monomials and learning rays to the final discussion
18.9 SUPPORT VECTOR MACHINES
 744 Chapter 8. Learning from Examples is the fact that each regression problem will be easier to solve, because it involves only the examples with nonzero weight the examples whose kernels overlap the
744 Chapter 8. Learning from Examples is the fact that each regression problem will be easier to solve, because it involves only the examples with nonzero weight the examples whose kernels overlap the
Computational Learning Theory - Hilary Term : Introduction to the PAC Learning Framework
 Computational Learning Theory - Hilary Term 2018 1 : Introduction to the PAC Learning Framework Lecturer: Varun Kanade 1 What is computational learning theory? Machine learning techniques lie at the heart
Computational Learning Theory - Hilary Term 2018 1 : Introduction to the PAC Learning Framework Lecturer: Varun Kanade 1 What is computational learning theory? Machine learning techniques lie at the heart
Learning from Examples
 Learning from Examples Data fitting Decision trees Cross validation Computational learning theory Linear classifiers Neural networks Nonparametric methods: nearest neighbor Support vector machines Ensemble
Learning from Examples Data fitting Decision trees Cross validation Computational learning theory Linear classifiers Neural networks Nonparametric methods: nearest neighbor Support vector machines Ensemble
Kernels. Machine Learning CSE446 Carlos Guestrin University of Washington. October 28, Carlos Guestrin
 Kernels Machine Learning CSE446 Carlos Guestrin University of Washington October 28, 2013 Carlos Guestrin 2005-2013 1 Linear Separability: More formally, Using Margin Data linearly separable, if there
Kernels Machine Learning CSE446 Carlos Guestrin University of Washington October 28, 2013 Carlos Guestrin 2005-2013 1 Linear Separability: More formally, Using Margin Data linearly separable, if there
Online Learning Class 12, 20 March 2006 Andrea Caponnetto, Sanmay Das
 Online Learning 9.520 Class 12, 20 March 2006 Andrea Caponnetto, Sanmay Das About this class Goal To introduce the general setting of online learning. To describe an online version of the RLS algorithm
Online Learning 9.520 Class 12, 20 March 2006 Andrea Caponnetto, Sanmay Das About this class Goal To introduce the general setting of online learning. To describe an online version of the RLS algorithm
Understanding Generalization Error: Bounds and Decompositions
 CIS 520: Machine Learning Spring 2018: Lecture 11 Understanding Generalization Error: Bounds and Decompositions Lecturer: Shivani Agarwal Disclaimer: These notes are designed to be a supplement to the
CIS 520: Machine Learning Spring 2018: Lecture 11 Understanding Generalization Error: Bounds and Decompositions Lecturer: Shivani Agarwal Disclaimer: These notes are designed to be a supplement to the
Logistic Regression Logistic
 Case Study 1: Estimating Click Probabilities L2 Regularization for Logistic Regression Machine Learning/Statistics for Big Data CSE599C1/STAT592, University of Washington Carlos Guestrin January 10 th,
Case Study 1: Estimating Click Probabilities L2 Regularization for Logistic Regression Machine Learning/Statistics for Big Data CSE599C1/STAT592, University of Washington Carlos Guestrin January 10 th,
1 Active Learning Foundations of Machine Learning and Data Science. Lecturer: Maria-Florina Balcan Lecture 20 & 21: November 16 & 18, 2015
 10-806 Foundations of Machine Learning and Data Science Lecturer: Maria-Florina Balcan Lecture 20 & 21: November 16 & 18, 2015 1 Active Learning Most classic machine learning methods and the formal learning
10-806 Foundations of Machine Learning and Data Science Lecturer: Maria-Florina Balcan Lecture 20 & 21: November 16 & 18, 2015 1 Active Learning Most classic machine learning methods and the formal learning
Linear Classifiers and the Perceptron
 Linear Classifiers and the Perceptron William Cohen February 4, 2008 1 Linear classifiers Let s assume that every instance is an n-dimensional vector of real numbers x R n, and there are only two possible
Linear Classifiers and the Perceptron William Cohen February 4, 2008 1 Linear classifiers Let s assume that every instance is an n-dimensional vector of real numbers x R n, and there are only two possible
Computational Learning Theory
 Computational Learning Theory Sinh Hoa Nguyen, Hung Son Nguyen Polish-Japanese Institute of Information Technology Institute of Mathematics, Warsaw University February 14, 2006 inh Hoa Nguyen, Hung Son
Computational Learning Theory Sinh Hoa Nguyen, Hung Son Nguyen Polish-Japanese Institute of Information Technology Institute of Mathematics, Warsaw University February 14, 2006 inh Hoa Nguyen, Hung Son
Seminaar Abstrakte Wiskunde Seminar in Abstract Mathematics Lecture notes in progress (27 March 2010)
 http://math.sun.ac.za/amsc/sam Seminaar Abstrakte Wiskunde Seminar in Abstract Mathematics 2009-2010 Lecture notes in progress (27 March 2010) Contents 2009 Semester I: Elements 5 1. Cartesian product
http://math.sun.ac.za/amsc/sam Seminaar Abstrakte Wiskunde Seminar in Abstract Mathematics 2009-2010 Lecture notes in progress (27 March 2010) Contents 2009 Semester I: Elements 5 1. Cartesian product
CSC 5170: Theory of Computational Complexity Lecture 5 The Chinese University of Hong Kong 8 February 2010
 CSC 5170: Theory of Computational Complexity Lecture 5 The Chinese University of Hong Kong 8 February 2010 So far our notion of realistic computation has been completely deterministic: The Turing Machine
CSC 5170: Theory of Computational Complexity Lecture 5 The Chinese University of Hong Kong 8 February 2010 So far our notion of realistic computation has been completely deterministic: The Turing Machine
MIDTERM SOLUTIONS: FALL 2012 CS 6375 INSTRUCTOR: VIBHAV GOGATE
 MIDTERM SOLUTIONS: FALL 2012 CS 6375 INSTRUCTOR: VIBHAV GOGATE March 28, 2012 The exam is closed book. You are allowed a double sided one page cheat sheet. Answer the questions in the spaces provided on
MIDTERM SOLUTIONS: FALL 2012 CS 6375 INSTRUCTOR: VIBHAV GOGATE March 28, 2012 The exam is closed book. You are allowed a double sided one page cheat sheet. Answer the questions in the spaces provided on
The sample complexity of agnostic learning with deterministic labels
 The sample complexity of agnostic learning with deterministic labels Shai Ben-David Cheriton School of Computer Science University of Waterloo Waterloo, ON, N2L 3G CANADA shai@uwaterloo.ca Ruth Urner College
The sample complexity of agnostic learning with deterministic labels Shai Ben-David Cheriton School of Computer Science University of Waterloo Waterloo, ON, N2L 3G CANADA shai@uwaterloo.ca Ruth Urner College
Online Learning With Kernel
 CS 446 Machine Learning Fall 2016 SEP 27, 2016 Online Learning With Kernel Professor: Dan Roth Scribe: Ben Zhou, C. Cervantes Overview Stochastic Gradient Descent Algorithms Regularization Algorithm Issues
CS 446 Machine Learning Fall 2016 SEP 27, 2016 Online Learning With Kernel Professor: Dan Roth Scribe: Ben Zhou, C. Cervantes Overview Stochastic Gradient Descent Algorithms Regularization Algorithm Issues
CS 6375: Machine Learning Computational Learning Theory
 CS 6375: Machine Learning Computational Learning Theory Vibhav Gogate The University of Texas at Dallas Many slides borrowed from Ray Mooney 1 Learning Theory Theoretical characterizations of Difficulty
CS 6375: Machine Learning Computational Learning Theory Vibhav Gogate The University of Texas at Dallas Many slides borrowed from Ray Mooney 1 Learning Theory Theoretical characterizations of Difficulty
Support Vector Machines
 Support Vector Machines Hypothesis Space variable size deterministic continuous parameters Learning Algorithm linear and quadratic programming eager batch SVMs combine three important ideas Apply optimization
Support Vector Machines Hypothesis Space variable size deterministic continuous parameters Learning Algorithm linear and quadratic programming eager batch SVMs combine three important ideas Apply optimization
Lecture 9: Large Margin Classifiers. Linear Support Vector Machines
 Lecture 9: Large Margin Classifiers. Linear Support Vector Machines Perceptrons Definition Perceptron learning rule Convergence Margin & max margin classifiers (Linear) support vector machines Formulation
Lecture 9: Large Margin Classifiers. Linear Support Vector Machines Perceptrons Definition Perceptron learning rule Convergence Margin & max margin classifiers (Linear) support vector machines Formulation
Introduction to Machine Learning
 Outline Contents Introduction to Machine Learning Concept Learning Varun Chandola February 2, 2018 1 Concept Learning 1 1.1 Example Finding Malignant Tumors............. 2 1.2 Notation..............................
Outline Contents Introduction to Machine Learning Concept Learning Varun Chandola February 2, 2018 1 Concept Learning 1 1.1 Example Finding Malignant Tumors............. 2 1.2 Notation..............................
CS 395T Computational Learning Theory. Scribe: Rahul Suri
 CS 395T Computational Learning Theory Lecture 6: September 19, 007 Lecturer: Adam Klivans Scribe: Rahul Suri 6.1 Overview In Lecture 5, we showed that for any DNF formula f with n variables and s terms
CS 395T Computational Learning Theory Lecture 6: September 19, 007 Lecturer: Adam Klivans Scribe: Rahul Suri 6.1 Overview In Lecture 5, we showed that for any DNF formula f with n variables and s terms
Lecture 8. Instructor: Haipeng Luo
 Lecture 8 Instructor: Haipeng Luo Boosting and AdaBoost In this lecture we discuss the connection between boosting and online learning. Boosting is not only one of the most fundamental theories in machine
Lecture 8 Instructor: Haipeng Luo Boosting and AdaBoost In this lecture we discuss the connection between boosting and online learning. Boosting is not only one of the most fundamental theories in machine
Lecture 4: Training a Classifier
 Lecture 4: Training a Classifier Roger Grosse 1 Introduction Now that we ve defined what binary classification is, let s actually train a classifier. We ll approach this problem in much the same way as
Lecture 4: Training a Classifier Roger Grosse 1 Introduction Now that we ve defined what binary classification is, let s actually train a classifier. We ll approach this problem in much the same way as
Online Passive-Aggressive Algorithms
 Online Passive-Aggressive Algorithms Koby Crammer Ofer Dekel Shai Shalev-Shwartz Yoram Singer School of Computer Science & Engineering The Hebrew University, Jerusalem 91904, Israel {kobics,oferd,shais,singer}@cs.huji.ac.il
Online Passive-Aggressive Algorithms Koby Crammer Ofer Dekel Shai Shalev-Shwartz Yoram Singer School of Computer Science & Engineering The Hebrew University, Jerusalem 91904, Israel {kobics,oferd,shais,singer}@cs.huji.ac.il
Qualifier: CS 6375 Machine Learning Spring 2015
 Qualifier: CS 6375 Machine Learning Spring 2015 The exam is closed book. You are allowed to use two double-sided cheat sheets and a calculator. If you run out of room for an answer, use an additional sheet
Qualifier: CS 6375 Machine Learning Spring 2015 The exam is closed book. You are allowed to use two double-sided cheat sheets and a calculator. If you run out of room for an answer, use an additional sheet
Deep Learning for Computer Vision
 Deep Learning for Computer Vision Lecture 4: Curse of Dimensionality, High Dimensional Feature Spaces, Linear Classifiers, Linear Regression, Python, and Jupyter Notebooks Peter Belhumeur Computer Science
Deep Learning for Computer Vision Lecture 4: Curse of Dimensionality, High Dimensional Feature Spaces, Linear Classifiers, Linear Regression, Python, and Jupyter Notebooks Peter Belhumeur Computer Science
The No-Regret Framework for Online Learning
 The No-Regret Framework for Online Learning A Tutorial Introduction Nahum Shimkin Technion Israel Institute of Technology Haifa, Israel Stochastic Processes in Engineering IIT Mumbai, March 2013 N. Shimkin,
The No-Regret Framework for Online Learning A Tutorial Introduction Nahum Shimkin Technion Israel Institute of Technology Haifa, Israel Stochastic Processes in Engineering IIT Mumbai, March 2013 N. Shimkin,
