Sorting and Selection with Imprecise Comparisons
|
|
|
- Shawn Gregory
- 5 years ago
- Views:
Transcription
1 Sorting and Selection with Imprecise Comparisons Miklós Ajtai 1, Vitaly Feldman 1, Avinatan Hassidim 2, and Jelani Nelson 2 1 IBM Almaden Research Center, San Jose CA 95120, USA 2 MIT, Cambridge MA 02139, USA Abstract. In experimental psychology, the method of paired comparisons was proposed as a means for ranking preferences amongst n elements of a human subject. The method requires performing all `n 2 comparisons then sorting elements according to the number of wins. The large number of comparisons is performed to counter the potentially faulty decision-making of the human subject, who acts as an imprecise comparator. We consider a simple model of the imprecise comparisons: there exists some δ > 0 such that when a subject is given two elements to compare, if the values of those elements (as perceived by the subject) differ by at least δ, then the comparison will be made correctly; when the two elements have values that are within δ, the outcome of the comparison is unpredictable. This δ corresponds to the just noticeable difference unit (JND) or difference threshold in the psychophysics literature, but does not require the statistical assumptions used to define this value. In this model, the standard method of paired comparisons minimizes the errors introduced by the imprecise comparisons at the cost of `n 2 comparisons. We show that the same optimal guarantees can be achieved using 4n 3/2 comparisons, and we prove the optimality of our method. We then explore the general tradeoff between the guarantees on the error that can be made and number of comparisons for the problems of sorting, max-finding, and selection. Our results provide close-to-optimal solutions for each of these problems. 1 Introduction Let x 1,..., x n be n elements where each x i has an unknown value val(x i ). We want to find the element with the maximum value using only pairwise comparisons. However, the outcomes of comparisons are imprecise in the following sense. For some fixed δ > 0, if val(x i ) val(x j ) δ, then the result of the comparison can be either or. Otherwise, the result of the comparison is correct. It is easy to see that in such a setting it might be impossible to find the true maximum (for example when the values of all the elements are within δ). It might however be possible to identify an approximate maximum, that is an element x i such that for all x i, val(x i ) val(x i ) kδ for some, preferably small, value k. In addition, our goal is to minimize the number of comparisons
2 2 performed to find x i. We refer to the minimum value k such that an algorithm s output is always guaranteed to be kδ-close to the maximum as the error of the algorithm in this setting. Similarly, to sort the above elements with error k we need to find a permutation π such that if π(i) < π(j) then val(x i ) val(x j ) kδ. A key issue that our work addresses is that in any sorting (or max-finding) algorithm, errors resulting from imprecise comparisons might accumulate, causing the final output to have high error. Consider, for example, applying the classical bubble sort algorithm to a list of elements that are originally sorted in the reverse order and the difference between two adjacent elements is exactly δ. All the comparisons will be between elements within δ and therefore, in the worst case, the order will not be modified by the sorting, yielding error (n 1)δ. Numerous other known algorithms that primarily optimize the number of comparisons can be easily shown to incur a relatively high error. As can be easily demonstrated (Theorem 1), performing all ( n 2) comparisons then sorting elements according to the number of wins, a round-robin tournament, achieves error k = 2, which is lowest possible (Theorem 2). A natural question we ask here is whether ( n 2) comparisons are necessary to achieve the same error. We explore the same question for all values of k in the problems of sorting, max-finding, and general selection. One motivation for studying this problem comes from social sciences. A common problem both in experimental psychology and sociology is to have a human subject rank preferences amongst many candidate options. It also occurs frequently in marketing research [20, Chapter 10], and in training information retrieval algorithms using human evaluators [1, Section 2.2]. The basic method to elicit preferences is to present the subject two alternatives at a time and ask which is the preferred one. The common approach to this problem today was presented by Thurstone as early as 1927, and is called the method of paired comparisons (see [8] for a thorough treatment). In this method, one asks the subject to give preferences for all pairwise comparisons amongst n elements. A ranked preference list is then determined by the number of wins each candidate element receives. A central concept in these studies introduced as far back as the 1800s by Weber and Fechner is that of just noticeable difference (JND) unit or difference threshold δ. If two physical stimuli with intensities x < y have x y δ, a human will not be able to reliably distinguish which intensity is greater 3. The idea was later generalized by Thurstone to having humans not only compare physical stimuli, but also abstract concepts [21]. Most previous work on the method of paired comparisons has been through the lens of statistics. In such work the JND is modeled as a random variable and the statistical properties of Thurstone s method are studied [8]. Our problem corresponds to a simplified model of this problem which does not require any statistical assumptions, and is primarily from a combinatorial perspective. Another context that captures the intuition of our model is that of designing a sporting tournament based on win/lose games. There, biases of a judge and 3 The JND is typically defined relative to x rather than as an absolute value. This is identical to absolute difference in the logarithmic scale and hence our discussion extends to this setting.
3 3 unpredictable events can change the outcome of a game when the strengths of the players are close. Hence one cannot necessarily assume that the outcome is truly random in such a close call. It is clear that both restricting the influence of the faulty outcomes and reducing the total number of games required are important in this scenario, and hence exploring the tradeoff between the two is of interest. For convenience, in the rest of the paper we often use the terminology borrowed from this scenario. 1.1 Our Results We first examine the simpler problem of finding only the maximum element. For this problem, we give a deterministic max-finding algorithm with error 2 using 2n 3/2 comparisons. This contrasts with the method of paired comparisons, which makes (n 2 n)/2 comparisons to achieve the same error. Using our algorithm recursively, we build deterministic algorithms with error k that require O(n 1+1/((3/4) 2k 1) ) comparisons. We also give a lower bound of Ω(n 1+1/(2k 1) ). The bounds are almost tight the upper bound for our error-k algorithm is less than our lower bound for error-(k 1) algorithms. We also give a linear-time randomized algorithm that achieves error 3 with probability at least 1 1/n 2, showing that randomization greatly changes the complexity of the problem. We then study the problem of sorting. For k = 2, we give an algorithm using 4 n 3/2 comparisons. For general k, we show O((n 1+1/(3 2 k/2 1 1) + nk) log n) comparisons is achievable, and we show a lower bound of Ω(n 1+1/2k 1 ) comparisons. When k = O(1), or if only a single element of specific order needs to be selected, the log n factor disappears from our upper bound. Our lower bounds for selection depend on the order of the element that needs to be selected and interpolate between the lower bounds for max-finding and the lower bounds for sorting. For k 3, our lower bound for finding the median (and also for sorting) is strictly larger than our upper bound for max-finding. For example, for k = 3 the lower bound for sorting is Ω(n 5/4 ), whereas max-finding requires only O(n 6/5 ) comparisons. Note that we achieve log log n error for max-finding in O(n) comparisons, and 2 log log n error for sorting in O(n log n) comparisons. Standard methods using the same number of comparisons (e.g. a binary tournament tree, or Mergesort) can be shown to incur at least log n error. Also, all the algorithms we give are efficient in that their running times are of the same order as the number of comparisons they make. The main idea in our deterministic upper bounds for both max-finding and selection is to develop efficient algorithms for a small value of k (k = 2), then for larger k show how to partition elements, recursively use algorithms for smaller k, then combine results. Achieving nearly tight results for max-finding requires in part relaxing the problem to that of finding a small k-max-set, or a set which is guaranteed to contain at least one element of value at least x kδ, where x is the maximum value of an element (we interchangeably use x to refer to an element of maximum value as well). It turns out we can find a k-max-set
4 4 in a fewer number of comparisons than the lower bound for error-k max-finding algorithms. Exploiting this allows us to develop an efficient recursive max-finding algorithm. We note a similar approach of finding a small set of good elements was used by Borgstrom and Kosaraju [6] in the context of noisy binary search. For our randomized max-finding algorithm, we use a type of tournament with random seeds at each level, in combination with random subsampling at each level of the tournament tree. By performing a round-robin tournament on the top few tournament players together with the subsampled elements, we obtain an element of value at least x 3δ with high probability. To obtain lower bounds we translate our problems into problems on directed graphs in which the goal is to ensure existence of short paths from a certain node to most other nodes. Using a comparison oracle that always prefers elements that had fewer wins in previous rounds, we obtain bounds on the minimum of edges that are required to create the paths of desired length. Such bounds are then translated back into bounds on the number of comparisons required to achieve specific error guarantees for the problems we consider. We are unaware of directly comparable techniques having been used before. Some of the proofs are omitted from this extended abstract and appear in the full version of the paper. 1.2 Related Work Handling noise in binary search procedures was first considered by Rényi [18] and by Ulam [22]. An algorithm for solving Ulam s game was proposed by Rivest et. al. in [19], where an adversarial comparator can err a bounded number of times. They gave an algorithm with query complexity O(log n) which succeeds if the number of adversarial errors is constant. Yao and Yao [24] introduced the problem of sorting and of finding the maximal element in a sorting network when each comparison gate either returns the right answer or does not work at all. For finding the maximal element, they showed that it is necessary and sufficient to use (e + 1)(n 1) comparators when e comparators can be faulty. Ravikumar, Ganesan and Lakshmanan extended the model to arbitrary errors, showing that O(en) comparisons are necessary and sufficient [17]. For sorting, Yao and Yao showed that O(n log n + en) gates are sufficient. In a different fault model, and with a different definition of a successful sort, Finocchi and Italiano [11] showed an O(n log n) time algorithm resilient to (n log n) 1/3 faults. An improved algorithm handling (n log n) 1/2 faults was later given by Finocchi, Grandoni and Italiano [10]. In the model where each comparison is incorrect with some probability p, Feige et al. [9] and Assaf and Upfal [2] give algorithms for several comparison problems, and [3, 15] give algorithms for binary search. We refer the reader interested in the history of faulty comparison problems to a survey of Pelc [16]. We point out that some of the bounds we obtain appear similar to those known for max-finding, selection, and sorting in parallel in Valiant s model [23]. In particular, our bounds for max-finding are close to those obtained by Valiant for the parallel analogue of the problem (with the error used in place of parallel
5 5 time) [23], and our lower bound of Ω(n 1+1/(2k 1) ) for max-finding with error k is identical to a lower (and upper) bound given by Häggkvist and Hell [14] for merging two sorted arrays each of length n using a k-round parallel algorithm. Despite these similarities in bounds, our techniques are different, and we are not aware of any deep connections. For example, sorting in k parallel rounds Ω(n 1+1/k ) comparisons are required [5, 13], whereas in our model, for constant k, we can sort with error k in n 1+1/2Θ(k) comparisons. For a survey on parallel sorting algorithms, the reader is referred to [12]. 2 Notation Throughout this document we let x denote some x i of the maximum value (if there are several such elements, we choose one arbitrarily). Furthermore, we use x i interchangeably to refer to the both the ith element and its value, e.g. x i > x j should be interpreted as val(x i ) > val(x j ). We assume δ = 1 without loss of generality, since the problem with arbitrary δ > 0 is equivalent to the problem with δ = 1 and input values x i /δ. We say x defeats y when the comparator claims that x is larger than y (and we similarly use the phrase y loses to x). We say x is k-greater than y (x k y) if x y k. The term k-smaller is defined analogously. We say an element is a k-max of a set if it is k-greater than all other elements in the set, and a permutation x π(1),..., x π(n) is k-sorted if x π(i) k x π(j) for every i > j. All logarithms throughout this document are base-2. For simplicity of presentation, we frequently omit floors and ceilings and ignore rounding errors when they have an insignificant effect on the bounds. 3 Max-Finding In this section we give deterministic and randomized algorithms for max-finding. 3.1 Deterministic Algorithms We start by showing that the method of paired comparisons provides an optimal error guarantee, not just for max-finding, but also for sorting. Theorem 1. Sorting according to the number of wins in a round-robin tournament yields error 2. Proof. Let x, y be arbitrary elements with y strictly less than x 2. For any z that y defeats, x also defeats z. Furthermore, x defeats y, and thus x has strictly more wins than y, implying y is placed lower in the sorted order. Theorem 2. No deterministic max-finding algorithm has error less than 2. Proof. Given three elements a, b, c, the comparator can claim a > b > c > a, making the elements indistinguishable. Without loss of generality, suppose A outputs a. Then the values could be a = 0, b = 1, c = 2, implying A has error 2.
6 6 Algorithm A 2: // Returns an element of value at least x 2. The value s > 1 is a parameter which is by default n when not specified. 1. Label all x i as candidates. 2. while there are more than s candidate elements: (a) Pick an arbitrary set of s candidate elements and play them in a round-robin tournament. Let x have the most number of wins. (b) Compare x against all candidate elements and eliminate all elements that lose to x. 3. Play the final at most s candidate elements in a round-robin tournament and return the element with the most wins. Fig. 1. The algorithm A 2 for finding a 2-max. In Figure 1 we give an error-2 algorithm for max-finding. Lemma 1. The max-finding algorithm A 2 has error 2 and makes at most ns + n 2 /s comparisons. In particular, the number of comparisons is at most 2n 3/2 for s = n. Proof. We analyze the error in two cases. If x is never eliminated then x participates in Step 3. Theorem 1 then ensures that the final output is of value at least x 2. Otherwise, consider the iteration when x is eliminated. In this iteration, it must be the case that the x chosen in Step 2(b) has x x 1, and thus any element with value less than x 2 was also eliminated in this iteration. In this case all future iterations only contain elements of value at least x 2, and so again the final output has value at least x 2. In each step at least (s 1)/2 elements are eliminated implying the given bound on the total number of comparisons. The key recursion step of our general error max-finding is the algorithm 1-Cover of Lemma 3 which is based on A 2 and the following lemma. Lemma 2. There is a deterministic algorithm which makes ( n 2) comparisons and outputs a 1-max-set of size at most log n. The algorithm performs a round-robin tournament and then iteratively greedily picks an element which defeats as many thus-far undefeated elements as possible. We now obtain 1-Cover by setting s = n /8 in Figure 1, then returning the union of the x that were chosen in any iteration of Step 2(a), in addition to the output of Lemma 2 on the elements in the final tournament in Step 3. Lemma 3. There is an algorithm 1-Cover making O(n 3/2 ) comparisons which finds a 1-max-set of size at most n/4 (for sufficiently large n). We are now ready to present our main algorithm for finding a k-max.
7 7 Algorithm A k : // Returns a k-max for k 3 1. return A 2(A k 1(x 1, x 2,..., x n)) Algorithm A k: // Returns a (k 1)-max set of size O(n 2k /(3 2 k 4) ) for k 2 1. if k = 2, return 1-Cover(x 1, x 2,..., x n). 2. else (a) Equipartition the n elements into t = b k n 2k 1 /(2 k 4/3) sets S 1,..., S t. (b) Recursively call A k 1 on each set S i to recover a (k 2)-max set T i. (c) Return the output of 1-Cover with t i=1t i as input. Fig. 2. The algorithm A k for finding a k-max based on a recursive algorithm A k for finding a (k 1)-max-set. The value b k is (1/2) (3/4) k 3 for k 10 and 2 (3/4)k+5 (3 2 k 1 4)/4 otherwise. Theorem 3. For every 3 k log log n, there exists an algorithm A k finds a k-max element using O(n 1+1/((3/4)2k 1) ) comparisons. Corollary 1. There is a max-finding algorithm using O(n) comparisons with error log log n. 3.2 Randomized Max-Finding We now show that randomization can significantly reduce the number of comparisons required to find an approximate maximum. We emphasize that although an adversary is not allowed to adaptively change the input values during the course of an algorithm s execution, the adversary can adaptively choose how to err when two elements are close. In particular, the classic randomized selection algorithm can take quadratic time since for an input with all equal values, the adversary can claim that the randomly chosen pivot is smaller than all other elements. Nevertheless, we show the following. Theorem 4. There exists a linear-time randomized algorithm which finds a 3- max with probability at least 1 n c for any constant c and n large enough. Taking c > 1, and using the fact that the error of our algorithm can never be more than n 1, this gives an algorithm which finds an element with expected value at least x 4. The high-level idea of the algorithm is as follows. We randomly equipartition the elements into constant-sized sets. In each set we play a round-robin tournament and advance everyone who was not the absolute loser in their set. We also randomly subsample a set of players at each level of the tournament tree. We show that either (1) at some round of the tournament there is an abundance of elements with value at least x 1, in which case at least one such element is subsampled with high probability, or (2) x makes it as one of the top few tournament players with high probability. We describe the
8 8 properties of the tournament in Lemma 4. In Figure 3 we present the subroutine SampledTournament for the tournament. Algorithm SampledTournament: // For constant c and n sufficiently large, returns a 1-max-set with probability at least 1 n c. 1. Initialize N 0 {x 1,..., x n}, W, and i if N i n 0.3, insert N i into W and return W. 3. else randomly sample n 0.3 elements from N i and insert them into W. 4. Randomly partition the elements in N i into sets of size 80(c + 2). In each set, perform a round-robin tournament to find the minimal element (the element with the fewest wins, with ties broken arbitrarily). 5. Let N i+1 contain all of N i except for the minimal elements found in Step 4. That is, from each set of 80(c + 2) elements of N i, only one does not belong to N i+1. Increment i and goto Step 2. Fig. 3. The algorithm SampledTournament. Lemma 4. SampledTournament outputs a W of size O(n 0.3 log n) after O(n) comparisons such that W is a 1-max-set with probability at least 1 n c. Theorem 4 follows immediately from Lemma 4: run the algorithm Sampled- Tournament, then return the winner of W in a round-robin tournament. 4 Sorting and Selection Definition 1. Element x j in the set x 1,..., x n is of k-order i if there exists a partition S 1, S 2 of [n] with j S 1, S 1 = i, x l k x j for all l S 1, and x l k x l for all l S 1, l S 2. A k-median is an element of k-order n/2. Our sorting and selection algorithms are based on the following lemma. Lemma 5. In a round-robin tournament on n elements, the element with the median number of wins has at least (n 2)/4 wins and at least (n 2)/4 losses. We can now obtain an error-2 sorting algorithm B 2 which needs only 4 n 3/2 comparisons. The idea is to modify A 2 so that the x found in Step 2(a) of Figure 1 is a pivot in the sense of Lemma 5. We then compare this x against all elements and pivot into two sets, recursively sort each, then concatenate. Lemma 6. There is a deterministic sorting algorithm B 2 with error 2 that requires at most 4 n 3/2 comparisons. At a high level our algorithm for k-order selection is similar to the classical selection algorithm of Blum et al. [4], in that in each step we try to find a pivot that allows us to recurse on a problem of geometrically decreasing size. In our
9 9 Algorithm C k : // Returns an element of k-order i. 1. if k 3, sort the elements using B 2 then return the element with index i. 2. else (a) Set k = k/ (b) Equipartition the n elements into t = b k n 2k 1 /(2 k 4/3) sets S 1,..., S t. (c) Recursively call C k 2 on each set S i to obtain a (k 2)-median y i. (d) Play the y 1,..., y t in a round-robin tournament and let y be the element with the median number of wins. (e) Compare y with each of the other n 1 elements. If y defeats at least (n 1)/2 elements then let X 2 be a set of d = (t 2)/4 ((n/t) 1)/2 elements (k 1)- greater than y, and let X 1 be the set of at least (n 1)/2 d elements that y defeats which are not in X 2 (thus every (x, x ) (X 1 {y}) X 2 satisfies x k x). If y defeats less than (n 1)/2 elements, X 1 and X 2 are defined symmetrically. i. if X 1 = i 1, return i. ii. else if i X 1, recursively find an element of k-order i in X 1. iii. else recursively find an element of k-order (i X 1 1) in X 2. Fig. 4. The algorithm C k. The value b k is chosen as in the algorithm A k (see Figure 2). scenario though, a good pivot must not only partition the input into nearly equal-sized chunks, but must itself be of (k 2)-order c n for some constant 0 < c < 1. The base case k = 2 can be solved by Lemma 6 since the element placed in position i of the sorted permutation is of 2-order i. Our algorithm is given in Figure 4. Lemma 7. For any i [n] and 2 k 2 log log n, the deterministic algorithm C k finds an element of k-order i in O(n 1+1/(3 2 k/2 1 1) ) comparisons. Theorem 5. For any 2 k 2 log log n, there is a deterministic sorting algorithm B k with error k using O((n 1+1/(3 2 k/2 1 1) + nk) log n) comparisons. If k = O(1), the number of comparisons reduces to O(n 1+1/(3 2 k/2 1 1) ). Proof. We find a k-median using C k, equipartition the elements into sets S 1, S 2 such that every element of S 2 is k-greater than every element of S 1 {x}, recursively sort each partition, then concatenate the sorted results. The upper bound on the number of comparisons follows from the Master theorem (see [7, Theorem 4.1]), and correctness is immediate from the definition of a k-median. 5 Lower Bounds Here we prove lower bounds against deterministic max-finding, sorting, and selection algorithms. In particular, we show that Theorem 3 and Theorem 5 achieve almost optimal trade-off between error and number of comparisons.
10 10 Lemma 8. Suppose a deterministic algorithm A upon given n elements guarantees that after m comparisons it can list r elements, each of which is guaranteed to be k-greater than at least q elements. Then m = Ω(max{q 1+1/(2k 1), q r 1/(2k 1) }). Proof. We define a comparator that decides how to answer queries online in such a way that we can later choose values for the elements which are consistent with the given answers, while maximizing the error of the algorithm. Let G t be the comparison graph at time t. That is, G t is a digraph whose vertices are the x i and which contains the directed edge (x i, x j ) if and only if before time t a comparison between x i and x j has been made, and the comparator has responded with x i x j. We denote the out-degree of x i in G t by d t (x i ). Assume that at time t the algorithm wants to compare some x i and x j. If d t (x i ) d t (x j ) then the comparator responds with x j x i, and it responds with x i x j otherwise. (The response is arbitrary when d t (x i ) = d t (x j ).) Let x be an element that is declared by A to be k-greater than at least q elements. Let y i = dist(x, x i ), where dist gives the length of the shortest (directed) path in the final graph G m. If no such path exists, we set y i = n. After the algorithm is done, we define val(x i ) = y i, We first claim that the values are consistent with the responses of the comparator. If for some pair of objects x i, x j the comparator has responded with x i x j, then G m contains edge (x i, x j ). This implies that for any x, dist(x, x j ) dist(x, x i ) + 1, or y i y j 1. Therefore the answer x i x j is consistent with the given values. Consider the nodes x i that x can reach via a path of length at most k. These are exactly the elements k-smaller than x, and thus there must be at least q of them. For i k let S i = {x j y j = i} and s i = S i. We claim that for every i [k], m s 2 i /(2s i 1) s i /2. For a node u S i, let pred(u) be a node in S i 1 such that the edge (pred(u), u) is in the graph. For a node v S i 1, let S i,v = {u S i v = pred(u)}. Further, let d o (pred(u), u) be the out-degree of pred(u) when the comparison between pred(u) and u was made (as a result of which the edge was added to G m ). Note that for any distinct nodes u, u S i,v, d o (v, u) d o (v, u ) since the out-degree of v grows each time an edge to a node in S i,v is added. This implies that d o (v, u) d = S i,v ( S i,v 1)/2. u S i,v d S i,v 1 By the definition of our comparator, for every u S i, d m (u) d o (pred(u), u). This implies that m S i,v ( S i,v 1) v S d m (u) = i 1 S i,v 2 S i. 2 2 u S i,v v S i 1 v S i 1 Using the inequality between the quadratic and arithmetic means, S i,v 2 2 S i,v / S i 1 = s 2 i /s i 1. v S i 1 v S i 1
11 11 This implies that m s2 i 2s i 1 si 2. We can therefore conclude that s i (2m + s i )s i 1 3ms i 1 since s i n m. By applying this inequality and using the fact that s 0 = 1 we obtain that s 2 1/3 m and s i 3m (3m/s 1 ) 2 (i 1) for i > 1. Since i k s i q + 1, we thus find that q 12 m (3m/s 1 ) 2 (k 1). This holds since either 1. (3m/s 1 ) 2 (k 1) > 1/2 and then 12 m (3m/s 1 ) 2 (k 1) 6m > n, or 2. (3m/s 1 ) 2 (k 1) 1/2 and then (3m/s 1 ) 2 i+1 /(3m/s 1 ) 2 i = (3m/s 1 ) 2 i (3m/s 1 ) 2 (k 1) 1/2 for i k 1, where the penultimate inequality holds since s 1 < 3m. In this case q s 1 k k s i 1 ) i=2(3m)(3m/s 2 (i 1) 2 i k (3m)(3m/s 1 ) 2 (k 1) i k i=2 < 2(3m) 1 2 (k 1) s 2 (k 1) 1 If s 1 q/2, then m = Ω(q 2 ) since m s 2 1/3. Otherwise we have that m (q/4) 1/(1 2 (k 1)) /(3s 1/(2(k 1) 1) 1 ), implying m = Ω(max{s 2 1, q 1/(1 2 (k 1)) /s 1/(2(k 1) 1) 1 }) = Ω(q 1+1/(2k 1) ) where the final equality can be seen by making the two terms in the max equal. Also, note that the choice of x amongst the r elements of the theorem statement was arbitrary, and that s 1 is just the out-degree of x. Let s min be the minimum out-degree amongst the r elements. Then we trivially have m r s min. Thus, if s min q/2 then m qr/2, and otherwise m = Ω(max{r s min, q 1/(1 2 (k 1)) /s 1/(2(k 1) 1) min }) = Ω(q r 1/(2k 1) ) where the final equality is again seen by making the two terms in the max equal. From Lemma 8 we immediately obtain a lower bound for max-finding by setting r = 1, q = n 1, and for median-finding and sorting by setting r = q = n/2. In general, the sorting lower bound holds for k-order selection of the ith element for any i = c n for constant 0 < c < 1. Theorem 6. Every deterministic max-finding algorithm A with error k requires Ω(n 1+1/(2k 1) ) comparisons. Theorem 7. Every deterministic algorithm A which k-sorts n elements, or finds an element of k-order i for i = c n with 0 < c < 1 a constant, requires Ω(n 1+1/2k 1 ) comparisons. Theorem 6 implies the following, showing that Corollary 1 is tight. Corollary 2. Let A be a deterministic max-finding algorithm that makes O(n) comparisons. Then A has error at least log log n O(1).
12 12 References 1. G. Aggarwal, N. Ailon, F. Constantin, E. Even-Dar, J. Feldman, G. Frahling, M. R. Henzinger, S. Muthukrishnan, N. Nisan, M. Pál, M. Sandler, and A. Sidiropoulos. Theory research at Google. SIGACT News, 39(2):10 28, S. Assaf and E. Upfal. Fault tolerant sorting networks. SIAM J. Discrete Math, 4(4): , M. Ben-Or and A. Hassidim. The bayesian learner is optimal for noisy binary search (and pretty good for quantum as well). In FOCS, pages , M. Blum, R. W. Floyd, V. R. Pratt, R. L. Rivest, and R. E. Tarjan. Time bounds for selection. J. Comput. Syst. Sci., 7(4): , B. Bollobás and A. Thomason. Parallel sorting. Discrete Appl. Math., 6:1 11, R. S. Borgstrom and S. R. Kosaraju. Comparison-based search in the presence of errors. In STOC, pages , T. H. Cormen, C. E. Leiserson, R. L. Rivest, and C. Stein. Introduction to Algorithms. The MIT Press, second edition, H. A. David. The Method of Paired Comparisons. Charles Griffin & Company Limited, 2nd edition, U. Feige, P. Raghavan, D. Peleg, and E. Upfal. Computing with noisy information. SIAM J. Comput., 23(5), I. Finocchi, F. Grandoni, and G. F. Italiano. Optimal resilient sorting and searching in the presence of memory faults. In ICALP, pages , I. Finocchi and G. F. Italiano. Sorting and searching in the presence of memory faults (without redundancy). In STOC, pages , W. I. Gasarch, E. Golub, and C. P. Kruskal. Constant time parallel sorting: an empirical view. J. Comput. Syst. Sci., 67(1):63 91, R. Häggkvist and P. Hell. Parallel sorting with constant time for comparisons. SIAM J. Comput., 10(3): , R. Häggkvist and P. Hell. Sorting and merging in rounds. SIAM Journal on Algebraic and Discrete Methods, 3(4): , R. M. Karp and R. Kleinberg. Noisy binary search and its applications. In SODA, pages , A. Pelc. Searching games with errors fifty years of coping with liars. Theor. Comput. Sci., 270(1-2):71 109, B. Ravikumar, K. Ganesan, and K. B. Lakshmanan. On selecting the largest element in spite of erroneous information. In STACS, pages 88 99, A. Rényi. On a problem in information theory. Magyar Tud. Akad. Mat. Kutató Int. Közl, 6: , R. L. Rivest, A. R. Meyer, D. J. Kleitman, K. Winklmann, and J. Spencer. Coping with errors in binary search procedures. J. Comput. Sys. Sci., 20(3): , S. M. Smith and G. S. Albaum. Fundamentals of Marketing Research. Sage Publications, Inc., first edition, L. L. Thurstone. A law of comparative judgment. Psychological Review, 34: , S. M. Ulam. Adventures of a Mathematician. Scribner s, New York, L. G. Valiant. Parallelism in comparison problems. SIAM J. Comput., 4(3): , A. C. Yao and F. F. Yao. On fault-tolerant networks for sorting. SIAM J. Comput., 14(1): , 1985.
Sorting and Selection with Imprecise Comparisons
 Sorting and Selection with Imprecise Comparisons Miklós Ajtai IBM Research - Almaden ajtai@us.ibm.com Vitaly Feldman IBM Research - Almaden vitaly@post.harvad.edu Jelani Nelson Harvard University minilek@seas.harvard.edu
Sorting and Selection with Imprecise Comparisons Miklós Ajtai IBM Research - Almaden ajtai@us.ibm.com Vitaly Feldman IBM Research - Almaden vitaly@post.harvad.edu Jelani Nelson Harvard University minilek@seas.harvard.edu
Divide and Conquer Algorithms. CSE 101: Design and Analysis of Algorithms Lecture 14
 Divide and Conquer Algorithms CSE 101: Design and Analysis of Algorithms Lecture 14 CSE 101: Design and analysis of algorithms Divide and conquer algorithms Reading: Sections 2.3 and 2.4 Homework 6 will
Divide and Conquer Algorithms CSE 101: Design and Analysis of Algorithms Lecture 14 CSE 101: Design and analysis of algorithms Divide and conquer algorithms Reading: Sections 2.3 and 2.4 Homework 6 will
1 Terminology and setup
 15-451/651: Design & Analysis of Algorithms August 31, 2017 Lecture #2 last changed: August 29, 2017 In this lecture, we will examine some simple, concrete models of computation, each with a precise definition
15-451/651: Design & Analysis of Algorithms August 31, 2017 Lecture #2 last changed: August 29, 2017 In this lecture, we will examine some simple, concrete models of computation, each with a precise definition
b + O(n d ) where a 1, b > 1, then O(n d log n) if a = b d d ) if a < b d O(n log b a ) if a > b d
 CS161, Lecture 4 Median, Selection, and the Substitution Method Scribe: Albert Chen and Juliana Cook (2015), Sam Kim (2016), Gregory Valiant (2017) Date: January 23, 2017 1 Introduction Last lecture, we
CS161, Lecture 4 Median, Selection, and the Substitution Method Scribe: Albert Chen and Juliana Cook (2015), Sam Kim (2016), Gregory Valiant (2017) Date: January 23, 2017 1 Introduction Last lecture, we
CSC 8301 Design & Analysis of Algorithms: Lower Bounds
 CSC 8301 Design & Analysis of Algorithms: Lower Bounds Professor Henry Carter Fall 2016 Recap Iterative improvement algorithms take a feasible solution and iteratively improve it until optimized Simplex
CSC 8301 Design & Analysis of Algorithms: Lower Bounds Professor Henry Carter Fall 2016 Recap Iterative improvement algorithms take a feasible solution and iteratively improve it until optimized Simplex
1 Approximate Quantiles and Summaries
 CS 598CSC: Algorithms for Big Data Lecture date: Sept 25, 2014 Instructor: Chandra Chekuri Scribe: Chandra Chekuri Suppose we have a stream a 1, a 2,..., a n of objects from an ordered universe. For simplicity
CS 598CSC: Algorithms for Big Data Lecture date: Sept 25, 2014 Instructor: Chandra Chekuri Scribe: Chandra Chekuri Suppose we have a stream a 1, a 2,..., a n of objects from an ordered universe. For simplicity
arxiv: v2 [cs.ds] 28 Jan 2009
![arxiv: v2 [cs.ds] 28 Jan 2009 arxiv: v2 [cs.ds] 28 Jan 2009](/thumbs/87/95711442.jpg) Minimax Trees in Linear Time Pawe l Gawrychowski 1 and Travis Gagie 2, arxiv:0812.2868v2 [cs.ds] 28 Jan 2009 1 Institute of Computer Science University of Wroclaw, Poland gawry1@gmail.com 2 Research Group
Minimax Trees in Linear Time Pawe l Gawrychowski 1 and Travis Gagie 2, arxiv:0812.2868v2 [cs.ds] 28 Jan 2009 1 Institute of Computer Science University of Wroclaw, Poland gawry1@gmail.com 2 Research Group
Computing with voting trees
 Computing with voting trees Jennifer Iglesias Nathaniel Ince Po-Shen Loh Abstract The classical paradox of social choice theory asserts that there is no fair way to deterministically select a winner in
Computing with voting trees Jennifer Iglesias Nathaniel Ince Po-Shen Loh Abstract The classical paradox of social choice theory asserts that there is no fair way to deterministically select a winner in
Binary Searching in the Presence of Comparison Errors
 Binary Searching in the Presence of Comparison Errors Bruno Carpentieri Dipartimento di Informatica ed Applicazioni Università di Salerno 84081 Baronissi (SA), Italy Abstract We consider the problem of
Binary Searching in the Presence of Comparison Errors Bruno Carpentieri Dipartimento di Informatica ed Applicazioni Università di Salerno 84081 Baronissi (SA), Italy Abstract We consider the problem of
Concrete models and tight upper/lower bounds
 Lecture 3 Concrete models and tight upper/lower bounds 3.1 Overview In this lecture, we will examine some simple, concrete models of computation, each with a precise definition of what counts as a step,
Lecture 3 Concrete models and tight upper/lower bounds 3.1 Overview In this lecture, we will examine some simple, concrete models of computation, each with a precise definition of what counts as a step,
Convergence Rate of Best Response Dynamics in Scheduling Games with Conflicting Congestion Effects
 Convergence Rate of est Response Dynamics in Scheduling Games with Conflicting Congestion Effects Michal Feldman Tami Tamir Abstract We study resource allocation games with conflicting congestion effects.
Convergence Rate of est Response Dynamics in Scheduling Games with Conflicting Congestion Effects Michal Feldman Tami Tamir Abstract We study resource allocation games with conflicting congestion effects.
Online Learning, Mistake Bounds, Perceptron Algorithm
 Online Learning, Mistake Bounds, Perceptron Algorithm 1 Online Learning So far the focus of the course has been on batch learning, where algorithms are presented with a sample of training data, from which
Online Learning, Mistake Bounds, Perceptron Algorithm 1 Online Learning So far the focus of the course has been on batch learning, where algorithms are presented with a sample of training data, from which
Divide and Conquer. Maximum/minimum. Median finding. CS125 Lecture 4 Fall 2016
 CS125 Lecture 4 Fall 2016 Divide and Conquer We have seen one general paradigm for finding algorithms: the greedy approach. We now consider another general paradigm, known as divide and conquer. We have
CS125 Lecture 4 Fall 2016 Divide and Conquer We have seen one general paradigm for finding algorithms: the greedy approach. We now consider another general paradigm, known as divide and conquer. We have
Sorting n Objects with a k-sorter. Richard Beigel. Dept. of Computer Science. P.O. Box 2158, Yale Station. Yale University. New Haven, CT
 Sorting n Objects with a -Sorter Richard Beigel Dept. of Computer Science P.O. Box 258, Yale Station Yale University New Haven, CT 06520-258 John Gill Department of Electrical Engineering Stanford University
Sorting n Objects with a -Sorter Richard Beigel Dept. of Computer Science P.O. Box 258, Yale Station Yale University New Haven, CT 06520-258 John Gill Department of Electrical Engineering Stanford University
Kartsuba s Algorithm and Linear Time Selection
 CS 374: Algorithms & Models of Computation, Fall 2015 Kartsuba s Algorithm and Linear Time Selection Lecture 09 September 22, 2015 Chandra & Manoj (UIUC) CS374 1 Fall 2015 1 / 32 Part I Fast Multiplication
CS 374: Algorithms & Models of Computation, Fall 2015 Kartsuba s Algorithm and Linear Time Selection Lecture 09 September 22, 2015 Chandra & Manoj (UIUC) CS374 1 Fall 2015 1 / 32 Part I Fast Multiplication
Error-Correcting Tournaments
 Error-Correcting Tournaments Alina Beygelzimer 1, John Langford 2, and Pradeep Raviumar 3 1 IBM Thomas J. Watson Research Center, Hawthorne, NY 10532, USA beygel@us.ibm.com 2 Yahoo! Research, New Yor,
Error-Correcting Tournaments Alina Beygelzimer 1, John Langford 2, and Pradeep Raviumar 3 1 IBM Thomas J. Watson Research Center, Hawthorne, NY 10532, USA beygel@us.ibm.com 2 Yahoo! Research, New Yor,
CSE 4502/5717: Big Data Analytics
 CSE 4502/5717: Big Data Analytics otes by Anthony Hershberger Lecture 4 - January, 31st, 2018 1 Problem of Sorting A known lower bound for sorting is Ω is the input size; M is the core memory size; and
CSE 4502/5717: Big Data Analytics otes by Anthony Hershberger Lecture 4 - January, 31st, 2018 1 Problem of Sorting A known lower bound for sorting is Ω is the input size; M is the core memory size; and
Algorithms and Data Structures in the noisy comparison model and applications
 Algorithms and Data Structures in the noisy comparison model and applications Nishanth Dikkala, Anil Shanbhag, Emmanouil Zampetakis Massachusetts Institute of Technology Abstract In contrast to classical
Algorithms and Data Structures in the noisy comparison model and applications Nishanth Dikkala, Anil Shanbhag, Emmanouil Zampetakis Massachusetts Institute of Technology Abstract In contrast to classical
CS 161 Summer 2009 Homework #2 Sample Solutions
 CS 161 Summer 2009 Homework #2 Sample Solutions Regrade Policy: If you believe an error has been made in the grading of your homework, you may resubmit it for a regrade. If the error consists of more than
CS 161 Summer 2009 Homework #2 Sample Solutions Regrade Policy: If you believe an error has been made in the grading of your homework, you may resubmit it for a regrade. If the error consists of more than
Manipulating Stochastically Generated Single-Elimination Tournaments for Nearly All Players
 Manipulating Stochastically Generated Single-Elimination Tournaments for Nearly All Players Isabelle Stanton and Virginia Vassilevska Williams {isabelle,virgi}@eecs.berkeley.edu Computer Science Department
Manipulating Stochastically Generated Single-Elimination Tournaments for Nearly All Players Isabelle Stanton and Virginia Vassilevska Williams {isabelle,virgi}@eecs.berkeley.edu Computer Science Department
Learning convex bodies is hard
 Learning convex bodies is hard Navin Goyal Microsoft Research India navingo@microsoft.com Luis Rademacher Georgia Tech lrademac@cc.gatech.edu Abstract We show that learning a convex body in R d, given
Learning convex bodies is hard Navin Goyal Microsoft Research India navingo@microsoft.com Luis Rademacher Georgia Tech lrademac@cc.gatech.edu Abstract We show that learning a convex body in R d, given
Lecture 8: Decision-making under total uncertainty: the multiplicative weight algorithm. Lecturer: Sanjeev Arora
 princeton univ. F 13 cos 521: Advanced Algorithm Design Lecture 8: Decision-making under total uncertainty: the multiplicative weight algorithm Lecturer: Sanjeev Arora Scribe: (Today s notes below are
princeton univ. F 13 cos 521: Advanced Algorithm Design Lecture 8: Decision-making under total uncertainty: the multiplicative weight algorithm Lecturer: Sanjeev Arora Scribe: (Today s notes below are
Upper and Lower Bounds on the Number of Faults. a System Can Withstand Without Repairs. Cambridge, MA 02139
 Upper and Lower Bounds on the Number of Faults a System Can Withstand Without Repairs Michel Goemans y Nancy Lynch z Isaac Saias x Laboratory for Computer Science Massachusetts Institute of Technology
Upper and Lower Bounds on the Number of Faults a System Can Withstand Without Repairs Michel Goemans y Nancy Lynch z Isaac Saias x Laboratory for Computer Science Massachusetts Institute of Technology
Monotone Submodular Maximization over a Matroid
 Monotone Submodular Maximization over a Matroid Yuval Filmus January 31, 2013 Abstract In this talk, we survey some recent results on monotone submodular maximization over a matroid. The survey does not
Monotone Submodular Maximization over a Matroid Yuval Filmus January 31, 2013 Abstract In this talk, we survey some recent results on monotone submodular maximization over a matroid. The survey does not
Randomized Algorithms
 Randomized Algorithms Prof. Tapio Elomaa tapio.elomaa@tut.fi Course Basics A new 4 credit unit course Part of Theoretical Computer Science courses at the Department of Mathematics There will be 4 hours
Randomized Algorithms Prof. Tapio Elomaa tapio.elomaa@tut.fi Course Basics A new 4 credit unit course Part of Theoretical Computer Science courses at the Department of Mathematics There will be 4 hours
Testing Problems with Sub-Learning Sample Complexity
 Testing Problems with Sub-Learning Sample Complexity Michael Kearns AT&T Labs Research 180 Park Avenue Florham Park, NJ, 07932 mkearns@researchattcom Dana Ron Laboratory for Computer Science, MIT 545 Technology
Testing Problems with Sub-Learning Sample Complexity Michael Kearns AT&T Labs Research 180 Park Avenue Florham Park, NJ, 07932 mkearns@researchattcom Dana Ron Laboratory for Computer Science, MIT 545 Technology
Coin-flipping games immune against linear-sized coalitions (Extended abstract)
 Coin-flipping games immune against linear-sized coalitions (Extended abstract) Abstract Noga Alon IBM Almaden Research Center, San Jose, CA 9510 and Sackler Faculty of Exact Sciences, Tel Aviv University,
Coin-flipping games immune against linear-sized coalitions (Extended abstract) Abstract Noga Alon IBM Almaden Research Center, San Jose, CA 9510 and Sackler Faculty of Exact Sciences, Tel Aviv University,
DIMACS Technical Report March Game Seki 1
 DIMACS Technical Report 2007-05 March 2007 Game Seki 1 by Diogo V. Andrade RUTCOR, Rutgers University 640 Bartholomew Road Piscataway, NJ 08854-8003 dandrade@rutcor.rutgers.edu Vladimir A. Gurvich RUTCOR,
DIMACS Technical Report 2007-05 March 2007 Game Seki 1 by Diogo V. Andrade RUTCOR, Rutgers University 640 Bartholomew Road Piscataway, NJ 08854-8003 dandrade@rutcor.rutgers.edu Vladimir A. Gurvich RUTCOR,
CS 577 Introduction to Algorithms: Strassen s Algorithm and the Master Theorem
 CS 577 Introduction to Algorithms: Jin-Yi Cai University of Wisconsin Madison In the last class, we described InsertionSort and showed that its worst-case running time is Θ(n 2 ). Check Figure 2.2 for
CS 577 Introduction to Algorithms: Jin-Yi Cai University of Wisconsin Madison In the last class, we described InsertionSort and showed that its worst-case running time is Θ(n 2 ). Check Figure 2.2 for
0.1 Motivating example: weighted majority algorithm
 princeton univ. F 16 cos 521: Advanced Algorithm Design Lecture 8: Decision-making under total uncertainty: the multiplicative weight algorithm Lecturer: Sanjeev Arora Scribe: Sanjeev Arora (Today s notes
princeton univ. F 16 cos 521: Advanced Algorithm Design Lecture 8: Decision-making under total uncertainty: the multiplicative weight algorithm Lecturer: Sanjeev Arora Scribe: Sanjeev Arora (Today s notes
Data Structures and Algorithms
 Data Structures and Algorithms Spring 2017-2018 Outline 1 Sorting Algorithms (contd.) Outline Sorting Algorithms (contd.) 1 Sorting Algorithms (contd.) Analysis of Quicksort Time to sort array of length
Data Structures and Algorithms Spring 2017-2018 Outline 1 Sorting Algorithms (contd.) Outline Sorting Algorithms (contd.) 1 Sorting Algorithms (contd.) Analysis of Quicksort Time to sort array of length
A General Lower Bound on the I/O-Complexity of Comparison-based Algorithms
 A General Lower ound on the I/O-Complexity of Comparison-based Algorithms Lars Arge Mikael Knudsen Kirsten Larsent Aarhus University, Computer Science Department Ny Munkegade, DK-8000 Aarhus C. August
A General Lower ound on the I/O-Complexity of Comparison-based Algorithms Lars Arge Mikael Knudsen Kirsten Larsent Aarhus University, Computer Science Department Ny Munkegade, DK-8000 Aarhus C. August
Sliding Windows with Limited Storage
 Electronic Colloquium on Computational Complexity, Report No. 178 (2012) Sliding Windows with Limited Storage Paul Beame Computer Science and Engineering University of Washington Seattle, WA 98195-2350
Electronic Colloquium on Computational Complexity, Report No. 178 (2012) Sliding Windows with Limited Storage Paul Beame Computer Science and Engineering University of Washington Seattle, WA 98195-2350
Maximum union-free subfamilies
 Maximum union-free subfamilies Jacob Fox Choongbum Lee Benny Sudakov Abstract An old problem of Moser asks: how large of a union-free subfamily does every family of m sets have? A family of sets is called
Maximum union-free subfamilies Jacob Fox Choongbum Lee Benny Sudakov Abstract An old problem of Moser asks: how large of a union-free subfamily does every family of m sets have? A family of sets is called
Lecture 3: Error Correcting Codes
 CS 880: Pseudorandomness and Derandomization 1/30/2013 Lecture 3: Error Correcting Codes Instructors: Holger Dell and Dieter van Melkebeek Scribe: Xi Wu In this lecture we review some background on error
CS 880: Pseudorandomness and Derandomization 1/30/2013 Lecture 3: Error Correcting Codes Instructors: Holger Dell and Dieter van Melkebeek Scribe: Xi Wu In this lecture we review some background on error
Oblivious and Adaptive Strategies for the Majority and Plurality Problems
 Oblivious and Adaptive Strategies for the Majority and Plurality Problems Fan Chung 1, Ron Graham 1, Jia Mao 1, and Andrew Yao 2 1 Department of Computer Science and Engineering, University of California,
Oblivious and Adaptive Strategies for the Majority and Plurality Problems Fan Chung 1, Ron Graham 1, Jia Mao 1, and Andrew Yao 2 1 Department of Computer Science and Engineering, University of California,
25 Minimum bandwidth: Approximation via volume respecting embeddings
 25 Minimum bandwidth: Approximation via volume respecting embeddings We continue the study of Volume respecting embeddings. In the last lecture, we motivated the use of volume respecting embeddings by
25 Minimum bandwidth: Approximation via volume respecting embeddings We continue the study of Volume respecting embeddings. In the last lecture, we motivated the use of volume respecting embeddings by
Lecture 3: Randomness in Computation
 Great Ideas in Theoretical Computer Science Summer 2013 Lecture 3: Randomness in Computation Lecturer: Kurt Mehlhorn & He Sun Randomness is one of basic resources and appears everywhere. In computer science,
Great Ideas in Theoretical Computer Science Summer 2013 Lecture 3: Randomness in Computation Lecturer: Kurt Mehlhorn & He Sun Randomness is one of basic resources and appears everywhere. In computer science,
Lecture 5: February 21, 2017
 COMS 6998: Advanced Complexity Spring 2017 Lecture 5: February 21, 2017 Lecturer: Rocco Servedio Scribe: Diana Yin 1 Introduction 1.1 Last Time 1. Established the exact correspondence between communication
COMS 6998: Advanced Complexity Spring 2017 Lecture 5: February 21, 2017 Lecturer: Rocco Servedio Scribe: Diana Yin 1 Introduction 1.1 Last Time 1. Established the exact correspondence between communication
Lecture 1 : Probabilistic Method
 IITM-CS6845: Theory Jan 04, 01 Lecturer: N.S.Narayanaswamy Lecture 1 : Probabilistic Method Scribe: R.Krithika The probabilistic method is a technique to deal with combinatorial problems by introducing
IITM-CS6845: Theory Jan 04, 01 Lecturer: N.S.Narayanaswamy Lecture 1 : Probabilistic Method Scribe: R.Krithika The probabilistic method is a technique to deal with combinatorial problems by introducing
Avoider-Enforcer games played on edge disjoint hypergraphs
 Avoider-Enforcer games played on edge disjoint hypergraphs Asaf Ferber Michael Krivelevich Alon Naor July 8, 2013 Abstract We analyze Avoider-Enforcer games played on edge disjoint hypergraphs, providing
Avoider-Enforcer games played on edge disjoint hypergraphs Asaf Ferber Michael Krivelevich Alon Naor July 8, 2013 Abstract We analyze Avoider-Enforcer games played on edge disjoint hypergraphs, providing
Problem Set 2 Solutions
 Introduction to Algorithms October 1, 2004 Massachusetts Institute of Technology 6.046J/18.410J Professors Piotr Indyk and Charles E. Leiserson Handout 9 Problem Set 2 Solutions Reading: Chapters 5-9,
Introduction to Algorithms October 1, 2004 Massachusetts Institute of Technology 6.046J/18.410J Professors Piotr Indyk and Charles E. Leiserson Handout 9 Problem Set 2 Solutions Reading: Chapters 5-9,
Network Algorithms and Complexity (NTUA-MPLA) Reliable Broadcast. Aris Pagourtzis, Giorgos Panagiotakos, Dimitris Sakavalas
 Network Algorithms and Complexity (NTUA-MPLA) Reliable Broadcast Aris Pagourtzis, Giorgos Panagiotakos, Dimitris Sakavalas Slides are partially based on the joint work of Christos Litsas, Aris Pagourtzis,
Network Algorithms and Complexity (NTUA-MPLA) Reliable Broadcast Aris Pagourtzis, Giorgos Panagiotakos, Dimitris Sakavalas Slides are partially based on the joint work of Christos Litsas, Aris Pagourtzis,
5. DIVIDE AND CONQUER I
 5. DIVIDE AND CONQUER I mergesort counting inversions closest pair of points median and selection Lecture slides by Kevin Wayne Copyright 2005 Pearson-Addison Wesley http://www.cs.princeton.edu/~wayne/kleinberg-tardos
5. DIVIDE AND CONQUER I mergesort counting inversions closest pair of points median and selection Lecture slides by Kevin Wayne Copyright 2005 Pearson-Addison Wesley http://www.cs.princeton.edu/~wayne/kleinberg-tardos
Lecture: Aggregation of General Biased Signals
 Social Networks and Social Choice Lecture Date: September 7, 2010 Lecture: Aggregation of General Biased Signals Lecturer: Elchanan Mossel Scribe: Miklos Racz So far we have talked about Condorcet s Jury
Social Networks and Social Choice Lecture Date: September 7, 2010 Lecture: Aggregation of General Biased Signals Lecturer: Elchanan Mossel Scribe: Miklos Racz So far we have talked about Condorcet s Jury
Online Learning versus Offline Learning*
 Machine Learning, 29, 45 63 (1997) c 1997 Kluwer Academic Publishers. Manufactured in The Netherlands. Online Learning versus Offline Learning* SHAI BEN-DAVID Computer Science Dept., Technion, Israel.
Machine Learning, 29, 45 63 (1997) c 1997 Kluwer Academic Publishers. Manufactured in The Netherlands. Online Learning versus Offline Learning* SHAI BEN-DAVID Computer Science Dept., Technion, Israel.
EFRON S COINS AND THE LINIAL ARRANGEMENT
 EFRON S COINS AND THE LINIAL ARRANGEMENT To (Richard P. S. ) 2 Abstract. We characterize the tournaments that are dominance graphs of sets of (unfair) coins in which each coin displays its larger side
EFRON S COINS AND THE LINIAL ARRANGEMENT To (Richard P. S. ) 2 Abstract. We characterize the tournaments that are dominance graphs of sets of (unfair) coins in which each coin displays its larger side
Approximating maximum satisfiable subsystems of linear equations of bounded width
 Approximating maximum satisfiable subsystems of linear equations of bounded width Zeev Nutov The Open University of Israel Daniel Reichman The Open University of Israel Abstract We consider the problem
Approximating maximum satisfiable subsystems of linear equations of bounded width Zeev Nutov The Open University of Israel Daniel Reichman The Open University of Israel Abstract We consider the problem
Quantum Algorithms for Graph Traversals and Related Problems
 Quantum Algorithms for Graph Traversals and Related Problems Sebastian Dörn Institut für Theoretische Informatik, Universität Ulm, 89069 Ulm, Germany sebastian.doern@uni-ulm.de Abstract. We study the complexity
Quantum Algorithms for Graph Traversals and Related Problems Sebastian Dörn Institut für Theoretische Informatik, Universität Ulm, 89069 Ulm, Germany sebastian.doern@uni-ulm.de Abstract. We study the complexity
Analysis of Algorithms I: Asymptotic Notation, Induction, and MergeSort
 Analysis of Algorithms I: Asymptotic Notation, Induction, and MergeSort Xi Chen Columbia University We continue with two more asymptotic notation: o( ) and ω( ). Let f (n) and g(n) are functions that map
Analysis of Algorithms I: Asymptotic Notation, Induction, and MergeSort Xi Chen Columbia University We continue with two more asymptotic notation: o( ) and ω( ). Let f (n) and g(n) are functions that map
1 Divide and Conquer (September 3)
 The control of a large force is the same principle as the control of a few men: it is merely a question of dividing up their numbers. Sun Zi, The Art of War (c. 400 C.E.), translated by Lionel Giles (1910)
The control of a large force is the same principle as the control of a few men: it is merely a question of dividing up their numbers. Sun Zi, The Art of War (c. 400 C.E.), translated by Lionel Giles (1910)
Approximation algorithms for cycle packing problems
 Approximation algorithms for cycle packing problems Michael Krivelevich Zeev Nutov Raphael Yuster Abstract The cycle packing number ν c (G) of a graph G is the maximum number of pairwise edgedisjoint cycles
Approximation algorithms for cycle packing problems Michael Krivelevich Zeev Nutov Raphael Yuster Abstract The cycle packing number ν c (G) of a graph G is the maximum number of pairwise edgedisjoint cycles
Lower Bounds for Dynamic Connectivity (2004; Pǎtraşcu, Demaine)
 Lower Bounds for Dynamic Connectivity (2004; Pǎtraşcu, Demaine) Mihai Pǎtraşcu, MIT, web.mit.edu/ mip/www/ Index terms: partial-sums problem, prefix sums, dynamic lower bounds Synonyms: dynamic trees 1
Lower Bounds for Dynamic Connectivity (2004; Pǎtraşcu, Demaine) Mihai Pǎtraşcu, MIT, web.mit.edu/ mip/www/ Index terms: partial-sums problem, prefix sums, dynamic lower bounds Synonyms: dynamic trees 1
Quick Sort Notes , Spring 2010
 Quick Sort Notes 18.310, Spring 2010 0.1 Randomized Median Finding In a previous lecture, we discussed the problem of finding the median of a list of m elements, or more generally the element of rank m.
Quick Sort Notes 18.310, Spring 2010 0.1 Randomized Median Finding In a previous lecture, we discussed the problem of finding the median of a list of m elements, or more generally the element of rank m.
arxiv: v2 [cs.ds] 3 Oct 2017
![arxiv: v2 [cs.ds] 3 Oct 2017 arxiv: v2 [cs.ds] 3 Oct 2017](/thumbs/84/90870651.jpg) Orthogonal Vectors Indexing Isaac Goldstein 1, Moshe Lewenstein 1, and Ely Porat 1 1 Bar-Ilan University, Ramat Gan, Israel {goldshi,moshe,porately}@cs.biu.ac.il arxiv:1710.00586v2 [cs.ds] 3 Oct 2017 Abstract
Orthogonal Vectors Indexing Isaac Goldstein 1, Moshe Lewenstein 1, and Ely Porat 1 1 Bar-Ilan University, Ramat Gan, Israel {goldshi,moshe,porately}@cs.biu.ac.il arxiv:1710.00586v2 [cs.ds] 3 Oct 2017 Abstract
CS 350 Algorithms and Complexity
 CS 350 Algorithms and Complexity Winter 2019 Lecture 15: Limitations of Algorithmic Power Introduction to complexity theory Andrew P. Black Department of Computer Science Portland State University Lower
CS 350 Algorithms and Complexity Winter 2019 Lecture 15: Limitations of Algorithmic Power Introduction to complexity theory Andrew P. Black Department of Computer Science Portland State University Lower
Contents 30. Score Sets and Kings 1501 Bibliography 1540 Subject Index 1542 Name Index 1544
 Contents 30. Score Sets and Kings........................... 1501 30.1. Score sets in 1-tournaments....................... 1502 30.1.1. Determining the score set of 1-tournaments.......... 1503 30.1.2.
Contents 30. Score Sets and Kings........................... 1501 30.1. Score sets in 1-tournaments....................... 1502 30.1.1. Determining the score set of 1-tournaments.......... 1503 30.1.2.
A Separator Theorem for Graphs with an Excluded Minor and its Applications
 A Separator Theorem for Graphs with an Excluded Minor and its Applications Noga Alon IBM Almaden Research Center, San Jose, CA 95120,USA and Sackler Faculty of Exact Sciences, Tel Aviv University, Tel
A Separator Theorem for Graphs with an Excluded Minor and its Applications Noga Alon IBM Almaden Research Center, San Jose, CA 95120,USA and Sackler Faculty of Exact Sciences, Tel Aviv University, Tel
The Complexity of a Reliable Distributed System
 The Complexity of a Reliable Distributed System Rachid Guerraoui EPFL Alexandre Maurer EPFL Abstract Studying the complexity of distributed algorithms typically boils down to evaluating how the number
The Complexity of a Reliable Distributed System Rachid Guerraoui EPFL Alexandre Maurer EPFL Abstract Studying the complexity of distributed algorithms typically boils down to evaluating how the number
Discrete Applied Mathematics
 Discrete Applied Mathematics 159 (011) 1398 1417 Contents lists available at ScienceDirect Discrete Applied Mathematics journal homepage: www.elsevier.com/locate/dam Recursive merge sort with erroneous
Discrete Applied Mathematics 159 (011) 1398 1417 Contents lists available at ScienceDirect Discrete Applied Mathematics journal homepage: www.elsevier.com/locate/dam Recursive merge sort with erroneous
CS 350 Algorithms and Complexity
 1 CS 350 Algorithms and Complexity Fall 2015 Lecture 15: Limitations of Algorithmic Power Introduction to complexity theory Andrew P. Black Department of Computer Science Portland State University Lower
1 CS 350 Algorithms and Complexity Fall 2015 Lecture 15: Limitations of Algorithmic Power Introduction to complexity theory Andrew P. Black Department of Computer Science Portland State University Lower
15.1 Introduction to Lower Bounds Proofs
 15 Lower Bounds How do I know if I have a good algorithm to solve a problem? If my algorithm runs in Θ(n log n) time, is that good? It would be if I were sorting the records stored in an array. But it
15 Lower Bounds How do I know if I have a good algorithm to solve a problem? If my algorithm runs in Θ(n log n) time, is that good? It would be if I were sorting the records stored in an array. But it
CSE 591 Homework 3 Sample Solutions. Problem 1
 CSE 591 Homework 3 Sample Solutions Problem 1 (a) Let p = max{1, k d}, q = min{n, k + d}, it suffices to find the pth and qth largest element of L and output all elements in the range between these two
CSE 591 Homework 3 Sample Solutions Problem 1 (a) Let p = max{1, k d}, q = min{n, k + d}, it suffices to find the pth and qth largest element of L and output all elements in the range between these two
IS 709/809: Computational Methods in IS Research Fall Exam Review
 IS 709/809: Computational Methods in IS Research Fall 2017 Exam Review Nirmalya Roy Department of Information Systems University of Maryland Baltimore County www.umbc.edu Exam When: Tuesday (11/28) 7:10pm
IS 709/809: Computational Methods in IS Research Fall 2017 Exam Review Nirmalya Roy Department of Information Systems University of Maryland Baltimore County www.umbc.edu Exam When: Tuesday (11/28) 7:10pm
Find an Element x in an Unsorted Array
 Find an Element x in an Unsorted Array What if we try to find a lower bound for the case where the array is not necessarily sorted? J.-L. De Carufel (U. of O.) Design & Analysis of Algorithms Fall 2017
Find an Element x in an Unsorted Array What if we try to find a lower bound for the case where the array is not necessarily sorted? J.-L. De Carufel (U. of O.) Design & Analysis of Algorithms Fall 2017
Mechanism Design for Bounded Agents
 Chapter 8 Mechanism Design for Bounded Agents Any fool can tell the truth, but it requires a man of some sense to know how to lie well. Samuel Butler Mechanism design has traditionally taken the conservative
Chapter 8 Mechanism Design for Bounded Agents Any fool can tell the truth, but it requires a man of some sense to know how to lie well. Samuel Butler Mechanism design has traditionally taken the conservative
On the Complexity of Computing an Equilibrium in Combinatorial Auctions
 On the Complexity of Computing an Equilibrium in Combinatorial Auctions Shahar Dobzinski Hu Fu Robert Kleinberg April 8, 2014 Abstract We study combinatorial auctions where each item is sold separately
On the Complexity of Computing an Equilibrium in Combinatorial Auctions Shahar Dobzinski Hu Fu Robert Kleinberg April 8, 2014 Abstract We study combinatorial auctions where each item is sold separately
5. DIVIDE AND CONQUER I
 5. DIVIDE AND CONQUER I mergesort counting inversions closest pair of points randomized quicksort median and selection Lecture slides by Kevin Wayne Copyright 2005 Pearson-Addison Wesley http://www.cs.princeton.edu/~wayne/kleinberg-tardos
5. DIVIDE AND CONQUER I mergesort counting inversions closest pair of points randomized quicksort median and selection Lecture slides by Kevin Wayne Copyright 2005 Pearson-Addison Wesley http://www.cs.princeton.edu/~wayne/kleinberg-tardos
Limitations of Algorithm Power
 Limitations of Algorithm Power Objectives We now move into the third and final major theme for this course. 1. Tools for analyzing algorithms. 2. Design strategies for designing algorithms. 3. Identifying
Limitations of Algorithm Power Objectives We now move into the third and final major theme for this course. 1. Tools for analyzing algorithms. 2. Design strategies for designing algorithms. 3. Identifying
Lecture 5: Efficient PAC Learning. 1 Consistent Learning: a Bound on Sample Complexity
 Universität zu Lübeck Institut für Theoretische Informatik Lecture notes on Knowledge-Based and Learning Systems by Maciej Liśkiewicz Lecture 5: Efficient PAC Learning 1 Consistent Learning: a Bound on
Universität zu Lübeck Institut für Theoretische Informatik Lecture notes on Knowledge-Based and Learning Systems by Maciej Liśkiewicz Lecture 5: Efficient PAC Learning 1 Consistent Learning: a Bound on
Approximating Graph Spanners
 Approximating Graph Spanners Michael Dinitz Johns Hopkins University Joint work with combinations of Robert Krauthgamer (Weizmann), Eden Chlamtáč (Ben Gurion), Ran Raz (Weizmann), Guy Kortsarz (Rutgers-Camden)
Approximating Graph Spanners Michael Dinitz Johns Hopkins University Joint work with combinations of Robert Krauthgamer (Weizmann), Eden Chlamtáč (Ben Gurion), Ran Raz (Weizmann), Guy Kortsarz (Rutgers-Camden)
Worst case analysis for a general class of on-line lot-sizing heuristics
 Worst case analysis for a general class of on-line lot-sizing heuristics Wilco van den Heuvel a, Albert P.M. Wagelmans a a Econometric Institute and Erasmus Research Institute of Management, Erasmus University
Worst case analysis for a general class of on-line lot-sizing heuristics Wilco van den Heuvel a, Albert P.M. Wagelmans a a Econometric Institute and Erasmus Research Institute of Management, Erasmus University
arxiv: v1 [math.pr] 14 Dec 2016
![arxiv: v1 [math.pr] 14 Dec 2016 arxiv: v1 [math.pr] 14 Dec 2016](/thumbs/83/87703379.jpg) Random Knockout Tournaments arxiv:1612.04448v1 [math.pr] 14 Dec 2016 Ilan Adler Department of Industrial Engineering and Operations Research University of California, Berkeley Yang Cao Department of Industrial
Random Knockout Tournaments arxiv:1612.04448v1 [math.pr] 14 Dec 2016 Ilan Adler Department of Industrial Engineering and Operations Research University of California, Berkeley Yang Cao Department of Industrial
Chapter 1. Comparison-Sorting and Selecting in. Totally Monotone Matrices. totally monotone matrices can be found in [4], [5], [9],
![Chapter 1. Comparison-Sorting and Selecting in. Totally Monotone Matrices. totally monotone matrices can be found in [4], [5], [9], Chapter 1. Comparison-Sorting and Selecting in. Totally Monotone Matrices. totally monotone matrices can be found in [4], [5], [9],](/thumbs/90/103870969.jpg) Chapter 1 Comparison-Sorting and Selecting in Totally Monotone Matrices Noga Alon Yossi Azar y Abstract An mn matrix A is called totally monotone if for all i 1 < i 2 and j 1 < j 2, A[i 1; j 1] > A[i 1;
Chapter 1 Comparison-Sorting and Selecting in Totally Monotone Matrices Noga Alon Yossi Azar y Abstract An mn matrix A is called totally monotone if for all i 1 < i 2 and j 1 < j 2, A[i 1; j 1] > A[i 1;
Zero-Sum Games Public Strategies Minimax Theorem and Nash Equilibria Appendix. Zero-Sum Games. Algorithmic Game Theory.
 Public Strategies Minimax Theorem and Nash Equilibria Appendix 2013 Public Strategies Minimax Theorem and Nash Equilibria Appendix Definition Definition A zero-sum game is a strategic game, in which for
Public Strategies Minimax Theorem and Nash Equilibria Appendix 2013 Public Strategies Minimax Theorem and Nash Equilibria Appendix Definition Definition A zero-sum game is a strategic game, in which for
Communication is bounded by root of rank
 Electronic Colloquium on Computational Complexity, Report No. 84 (2013) Communication is bounded by root of rank Shachar Lovett June 7, 2013 Abstract We prove that any total boolean function of rank r
Electronic Colloquium on Computational Complexity, Report No. 84 (2013) Communication is bounded by root of rank Shachar Lovett June 7, 2013 Abstract We prove that any total boolean function of rank r
The Size and Depth of Layered Boolean Circuits
 The Size and Depth of Layered Boolean Circuits Anna Gál a,1, Jing-Tang Jang a,2 a Dept. of Computer Science, University of Texas at Austin, Austin, TX 78712-1188, USA Abstract We consider the relationship
The Size and Depth of Layered Boolean Circuits Anna Gál a,1, Jing-Tang Jang a,2 a Dept. of Computer Science, University of Texas at Austin, Austin, TX 78712-1188, USA Abstract We consider the relationship
Some Formal Analysis of Rocchio s Similarity-Based Relevance Feedback Algorithm
 Some Formal Analysis of Rocchio s Similarity-Based Relevance Feedback Algorithm Zhixiang Chen (chen@cs.panam.edu) Department of Computer Science, University of Texas-Pan American, 1201 West University
Some Formal Analysis of Rocchio s Similarity-Based Relevance Feedback Algorithm Zhixiang Chen (chen@cs.panam.edu) Department of Computer Science, University of Texas-Pan American, 1201 West University
Lecture 4. Quicksort
 Lecture 4. Quicksort T. H. Cormen, C. E. Leiserson and R. L. Rivest Introduction to Algorithms, 3rd Edition, MIT Press, 2009 Sungkyunkwan University Hyunseung Choo choo@skku.edu Copyright 2000-2018 Networking
Lecture 4. Quicksort T. H. Cormen, C. E. Leiserson and R. L. Rivest Introduction to Algorithms, 3rd Edition, MIT Press, 2009 Sungkyunkwan University Hyunseung Choo choo@skku.edu Copyright 2000-2018 Networking
Disjoint-Set Forests
 Disjoint-Set Forests Thanks for Showing Up! Outline for Today Incremental Connectivity Maintaining connectivity as edges are added to a graph. Disjoint-Set Forests A simple data structure for incremental
Disjoint-Set Forests Thanks for Showing Up! Outline for Today Incremental Connectivity Maintaining connectivity as edges are added to a graph. Disjoint-Set Forests A simple data structure for incremental
2.6 Complexity Theory for Map-Reduce. Star Joins 2.6. COMPLEXITY THEORY FOR MAP-REDUCE 51
 2.6. COMPLEXITY THEORY FOR MAP-REDUCE 51 Star Joins A common structure for data mining of commercial data is the star join. For example, a chain store like Walmart keeps a fact table whose tuples each
2.6. COMPLEXITY THEORY FOR MAP-REDUCE 51 Star Joins A common structure for data mining of commercial data is the star join. For example, a chain store like Walmart keeps a fact table whose tuples each
On the errors introduced by the naive Bayes independence assumption
 On the errors introduced by the naive Bayes independence assumption Author Matthijs de Wachter 3671100 Utrecht University Master Thesis Artificial Intelligence Supervisor Dr. Silja Renooij Department of
On the errors introduced by the naive Bayes independence assumption Author Matthijs de Wachter 3671100 Utrecht University Master Thesis Artificial Intelligence Supervisor Dr. Silja Renooij Department of
Exercise Sheet #1 Solutions, Computer Science, A M. Hallett, K. Smith a k n b k = n b + k. a k n b k c 1 n b k. a k n b.
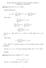 Exercise Sheet #1 Solutions, Computer Science, 308-251A M. Hallett, K. Smith 2002 Question 1.1: Prove (n + a) b = Θ(n b ). Binomial Expansion: Show O(n b ): (n + a) b = For any c 1 > b = O(n b ). Show
Exercise Sheet #1 Solutions, Computer Science, 308-251A M. Hallett, K. Smith 2002 Question 1.1: Prove (n + a) b = Θ(n b ). Binomial Expansion: Show O(n b ): (n + a) b = For any c 1 > b = O(n b ). Show
Asymptotic redundancy and prolixity
 Asymptotic redundancy and prolixity Yuval Dagan, Yuval Filmus, and Shay Moran April 6, 2017 Abstract Gallager (1978) considered the worst-case redundancy of Huffman codes as the maximum probability tends
Asymptotic redundancy and prolixity Yuval Dagan, Yuval Filmus, and Shay Moran April 6, 2017 Abstract Gallager (1978) considered the worst-case redundancy of Huffman codes as the maximum probability tends
Computational Game Theory Spring Semester, 2005/6. Lecturer: Yishay Mansour Scribe: Ilan Cohen, Natan Rubin, Ophir Bleiberg*
 Computational Game Theory Spring Semester, 2005/6 Lecture 5: 2-Player Zero Sum Games Lecturer: Yishay Mansour Scribe: Ilan Cohen, Natan Rubin, Ophir Bleiberg* 1 5.1 2-Player Zero Sum Games In this lecture
Computational Game Theory Spring Semester, 2005/6 Lecture 5: 2-Player Zero Sum Games Lecturer: Yishay Mansour Scribe: Ilan Cohen, Natan Rubin, Ophir Bleiberg* 1 5.1 2-Player Zero Sum Games In this lecture
A lower bound for scheduling of unit jobs with immediate decision on parallel machines
 A lower bound for scheduling of unit jobs with immediate decision on parallel machines Tomáš Ebenlendr Jiří Sgall Abstract Consider scheduling of unit jobs with release times and deadlines on m identical
A lower bound for scheduling of unit jobs with immediate decision on parallel machines Tomáš Ebenlendr Jiří Sgall Abstract Consider scheduling of unit jobs with release times and deadlines on m identical
Efficient Probabilistically Checkable Debates
 Efficient Probabilistically Checkable Debates Andrew Drucker MIT Andrew Drucker MIT, Efficient Probabilistically Checkable Debates 1/53 Polynomial-time Debates Given: language L, string x; Player 1 argues
Efficient Probabilistically Checkable Debates Andrew Drucker MIT Andrew Drucker MIT, Efficient Probabilistically Checkable Debates 1/53 Polynomial-time Debates Given: language L, string x; Player 1 argues
Algorithms and Data Structures
 Algorithms and Data Structures, Divide and Conquer Albert-Ludwigs-Universität Freiburg Prof. Dr. Rolf Backofen Bioinformatics Group / Department of Computer Science Algorithms and Data Structures, December
Algorithms and Data Structures, Divide and Conquer Albert-Ludwigs-Universität Freiburg Prof. Dr. Rolf Backofen Bioinformatics Group / Department of Computer Science Algorithms and Data Structures, December
Valency Arguments CHAPTER7
 CHAPTER7 Valency Arguments In a valency argument, configurations are classified as either univalent or multivalent. Starting from a univalent configuration, all terminating executions (from some class)
CHAPTER7 Valency Arguments In a valency argument, configurations are classified as either univalent or multivalent. Starting from a univalent configuration, all terminating executions (from some class)
Combining Shared Coin Algorithms
 Combining Shared Coin Algorithms James Aspnes Hagit Attiya Keren Censor Abstract This paper shows that shared coin algorithms can be combined to optimize several complexity measures, even in the presence
Combining Shared Coin Algorithms James Aspnes Hagit Attiya Keren Censor Abstract This paper shows that shared coin algorithms can be combined to optimize several complexity measures, even in the presence
Partitions and Covers
 University of California, Los Angeles CS 289A Communication Complexity Instructor: Alexander Sherstov Scribe: Dong Wang Date: January 2, 2012 LECTURE 4 Partitions and Covers In previous lectures, we saw
University of California, Los Angeles CS 289A Communication Complexity Instructor: Alexander Sherstov Scribe: Dong Wang Date: January 2, 2012 LECTURE 4 Partitions and Covers In previous lectures, we saw
A Note on Approximate Nash Equilibria
 A Note on Approximate Nash Equilibria Constantinos Daskalakis, Aranyak Mehta, and Christos Papadimitriou University of California, Berkeley, USA. Supported by NSF grant CCF-05559 IBM Almaden Research Center,
A Note on Approximate Nash Equilibria Constantinos Daskalakis, Aranyak Mehta, and Christos Papadimitriou University of California, Berkeley, USA. Supported by NSF grant CCF-05559 IBM Almaden Research Center,
Hamiltonian paths in tournaments A generalization of sorting DM19 notes fall 2006
 Hamiltonian paths in tournaments A generalization of sorting DM9 notes fall 2006 Jørgen Bang-Jensen Imada, SDU 30. august 2006 Introduction and motivation Tournaments which we will define mathematically
Hamiltonian paths in tournaments A generalization of sorting DM9 notes fall 2006 Jørgen Bang-Jensen Imada, SDU 30. august 2006 Introduction and motivation Tournaments which we will define mathematically
Linear Time Selection
 Linear Time Selection Given (x,y coordinates of N houses, where should you build road These lecture slides are adapted from CLRS.. Princeton University COS Theory of Algorithms Spring 0 Kevin Wayne Given
Linear Time Selection Given (x,y coordinates of N houses, where should you build road These lecture slides are adapted from CLRS.. Princeton University COS Theory of Algorithms Spring 0 Kevin Wayne Given
On the Resilience and Uniqueness of CPA for Secure Broadcast
 On the Resilience and Uniqueness of CPA for Secure Broadcast Chris Litsas, Aris Pagourtzis, Giorgos Panagiotakos and Dimitris Sakavalas School of Electrical and Computer Engineering National Technical
On the Resilience and Uniqueness of CPA for Secure Broadcast Chris Litsas, Aris Pagourtzis, Giorgos Panagiotakos and Dimitris Sakavalas School of Electrical and Computer Engineering National Technical
CPSC 320 Sample Final Examination December 2013
 CPSC 320 Sample Final Examination December 2013 [10] 1. Answer each of the following questions with true or false. Give a short justification for each of your answers. [5] a. 6 n O(5 n ) lim n + This is
CPSC 320 Sample Final Examination December 2013 [10] 1. Answer each of the following questions with true or false. Give a short justification for each of your answers. [5] a. 6 n O(5 n ) lim n + This is
A Linear Time Algorithm for Ordered Partition
 A Linear Time Algorithm for Ordered Partition Yijie Han School of Computing and Engineering University of Missouri at Kansas City Kansas City, Missouri 64 hanyij@umkc.edu Abstract. We present a deterministic
A Linear Time Algorithm for Ordered Partition Yijie Han School of Computing and Engineering University of Missouri at Kansas City Kansas City, Missouri 64 hanyij@umkc.edu Abstract. We present a deterministic
Jeffrey D. Ullman Stanford University
 Jeffrey D. Ullman Stanford University 3 We are given a set of training examples, consisting of input-output pairs (x,y), where: 1. x is an item of the type we want to evaluate. 2. y is the value of some
Jeffrey D. Ullman Stanford University 3 We are given a set of training examples, consisting of input-output pairs (x,y), where: 1. x is an item of the type we want to evaluate. 2. y is the value of some
Block Sensitivity of Minterm-Transitive Functions
 Block Sensitivity of Minterm-Transitive Functions Andrew Drucker Abstract Boolean functions with a high degree of symmetry are interesting from a complexity theory perspective: extensive research has shown
Block Sensitivity of Minterm-Transitive Functions Andrew Drucker Abstract Boolean functions with a high degree of symmetry are interesting from a complexity theory perspective: extensive research has shown
Notes on Logarithmic Lower Bounds in the Cell Probe Model
 Notes on Logarithmic Lower Bounds in the Cell Probe Model Kevin Zatloukal November 10, 2010 1 Overview Paper is by Mihai Pâtraşcu and Erik Demaine. Both were at MIT at the time. (Mihai is now at AT&T Labs.)
Notes on Logarithmic Lower Bounds in the Cell Probe Model Kevin Zatloukal November 10, 2010 1 Overview Paper is by Mihai Pâtraşcu and Erik Demaine. Both were at MIT at the time. (Mihai is now at AT&T Labs.)
