Closed Form Bounds for Clock Synchronization Under Simple Uncertainty Assumptions
|
|
|
- Darrell Dennis
- 5 years ago
- Views:
Transcription
1 Closed Form Bounds for Clock Synchronization Under Simple Uncertainty Assumptions Saâd Biaz Λ Jennifer L. Welch y Key words: Distributed Computing Clock Synchronization Optimal Precision Generalized Hypercube Lower Bound. 1 Introduction Many applications in a distributed system rely on processors having synchronized local clocks. Many studies have been dedicated to algorithms and lower bounds for clock synchronization under various network assumptions. We consider the problem of synchronizing the clocks of processors in a failure-free distributed system when the hardware clocks do not drift but there is uncertainty in the message delays. Our goal is to develop closed form expressions for how closely the clocks can be synchronized. Lundelius and Lynch [5] showed that the local clocks of n processors in a fully connected network with the same uncertainty u on each link cannot be synchronized any more closely than u (1 1 ). They provide n a simple algorithm that achieves this bound. Halpern et al. [3] subsequently extended this work to consider arbitrary topologies in which each directed edge may have a different uncertainty. They established a closed form expression for the optimal synchronization in a tree and a triangle. For the tree, the bound is equal to 1diam, wherediam is the diameter of the tree with respect to the uncertainties on the links. For the general case, they show that the optimal synchronization is the solution of an optimization problem using linear programming techniques, but they do not give a closed form expression. In this paper we address open question 7 in [3]:...it would be interesting to obtain precise formulas for the imprecision for a number of graphs that arise in practice. For an arbitrary undirected topology with arbitrary symmetric uncertainties, we prove a lower bound of 1 diam on the closeness of synchronization achievable, where diam is the diameter of the graph when the edges are weighted with the uncertainties. Taken together with the upper bound of radius (the radius of the graph with respect to the uncertainties) previously shown in [3], our result indicates that the tight bound for any (symmetric) topology is known to within a factor of two, since the radius is at most the diameter. Λ School of Science and Engineering, Al Akhawayn University, Ifrane, MOROCCO. saadb@cs.tamu.edu. Phone: (1) Supported by the Fulbright program. On leave from the Ecole Supérieure de Technologie Fès (MOROCCO). y Department of Computer Science, Texas A&M University, College Station, T welch@cs.tamu.edu. Phone: (979) Fax: (979) Supported in part by NSF CCR
2 We then consider the class of topologies described as k-ary m-cubes, both with and without wraparound. The number of nodes, n, equals k m. We assume that every edge has the same uncertainty, u. For the k-ary m-cube without wrap-around, we show that our lower bound 1diam = 1 um(k 1) is tight, by analyzing the synchronization achieved by a simple algorithm. Since chains, (square) meshes, and hypercubes are special cases of this topology, we have the following tight bounds: for an n-processor chain (k = n; m =1), 1 u(n 1); forap n p n mesh (k = p n; m =), u( p n 1); foralog n-dimensional hypercube (k =;m = log n), 1 u log n. For the k-ary m-cube with wrap-around, we show using the same algorithm that our lower bound 1diam = 1 umb k c is tight when k is even and is almost tight when k is odd. We restrict attention to the case k 3; otherwise wrap-around does not add any additional communication possibilities. When k is even, the tight bound is 1 umk. When k is odd, the lower bound is 1 um(k 4 4 1) and the upper bound is 1 um(k 4 1 k ). This result implies tight or almost tight bounds for rings and tori. In particular, we have the following tight bounds: for n-processor ring with n even (k = n; m = 1), 1 un; 4 forp n p n torus with p n even (k = p n; m = ), 1 up n. The analogous bounds when n is odd are not quite tight. In particular, for the ring the lower bound is 1 u(n 4 1) and the upper bound is 1 u(n 4 1 ); for the torus the lower bound is n 1 u(p n 1) and the upper bound is 1 u(p n p 1 n ). Attiya et al. [1] take a different approach to the problem. They consider arbitrary topologies under different delay assumptions. Instead of trying to establish the optimal closeness of synchronization achievable in a given network, they consider the problem of establishing the tightest clock synchronization for any given execution. In other words, given the information collected by any algorithm strategy, they give the optimal synchronization possible. They show how an external observer who has access to all the views of the processors can compute the optimal adjustment to each clock. Patt-Shamir and Rajsbaum [6] extended this work to provide an on-line algorithm optimal for every execution. In Section, we present our model and review relevant prior results. In Section 3, we establish a lower bound for an arbitrary topology. Section 4 is dedicated to establish closed forms for the upper bounds for k-ary m-cube networks, first for networks without wrap-around and then for networks with wrap-around. We conclude in Section 5 with some open problems. Definitions and Prior Results We first describe our formal model and problem definition (following [], which is based on those in [5] and [3]). Then we summarize previous results upon which our results rely, namely the conversion of any communication network to an equivalent clique and the technique of shifting executions..1 Model We consider a set of n processors p 0 through p, connected via point-to-point links. Each link, say the one between p i and p j, reliably delivers messages from p i to p j and vice versa subject to some arbitrary delay
3 within a known range. (We assume the range is the same in both directions.) The topology and message delay ranges are represented with an undirected graph G =(V;E), whose nodes represent processors and whose edges represent links, together with two mappings L and H from E to nonnegative reals. L(i; j) is the minimum delay on the edge between p i and p j and H(i; j) is the maximum delay on the edge between p i and p j. (Thus H(i; j) must be at least as large as L(i; j).) The difference, H(i; j) L(i; j), isthe uncertainty on the edge. G =(V;E;L;H) is said to be a communication network. The events that can occur at a processor include the arrival of messages from processors that are neighbors in the given topology, as well as internal happenings. Processor p i has a hardware clock value HC i, which is a function from reals (real time) to reals (clock time) of the form HC i (t) =t+c i for some constant c i. This is a hardware clock with no drift; it runs at the same rate as real time. A processor p i is a state machine with a set of initial states and a transition function. The transition function takes as input the current state, the current value of the hardware clock, and the current event and produces a new state and a set of messages to send to p i s neighbors. The hardware clock is not part of the processor s state and cannot be modified by the processor. A history of processor p i is a sequence of alternating states and (event,hardware clock value) pairs for p i, beginning with p i s initial state. We require that each subsequent state follows correctly, according to p i s transition function, from p i s previous state, event and hardware clock value. A timed history of p i is a history of p i together with an assignment of real times to each (event,hardware clock value) pair. The real times must be consistent with the hardware clock values, i.e., the time t assigned to (e; T ) must satisfy HC i (t) =T.Anexecution (of the entire system) is a set of n timed histories, one per processor. For every pair of processors p i and p j, there must be a bijection from messages sent by p i to messages received by p j (i.e., every message sent is received, and only messages sent are received). The delay of a message is the difference between the real time when it was sent and the real time when it was received. Two executions ff 1 and ff are indistinguishable if, for each processor p i, p i has the same (untimed) history in ff 1 as in ff. An execution ff is admissible for communication network G =(V;E;L;H) if every message between any two processors p i and p j has delay within the interval [L(i; j);h(i; j)].. The Clock Synchronization Problem We now precisely define the problem of synchronizing clocks. We assume that each processor p i has a state component adj i which is used to adjust the clock value. We define the processor s adjusted clock AC i (t) to be equal to HC i (t) +adj i (t) (the second term is the value of adj i at real time t). The algorithm has terminated in an execution at a point if no processor ever changes its adj variable thereafter. Achieving "-Synchronized Clocks (in communication network G): In every execution that is admissible for G, there exists a real time t f such that the algorithm has terminated by real time t f, and, for all processors p i and p j, and all t t f, jac i (t) AC j (t)j»". 3
4 Given a communication network G,letopt(G) be the smallest " such that "-synchronized clocks can be achieved in G. This quantity is the optimal clock synchronization that can be achieved in the network. We are interested in obtaining tight bounds on opt(g) for various G s..3 The Equivalent Clique If two communication networks G and G 0 satisfy opt(g) = opt(g 0 ), then we say that they are equivalent. Consider any communication network G = (V; E;L;H). Let G 0 be the communication network (V;E 0 ;L 0 ;H 0 ),wheree 0 = V V (i.e., G 0 is a clique), and for all i and j, L 0 (i; j) =0and H 0 (i; j) is the length of the shortest path between p i and p j in G with respect to the uncertainties. Section 6 of [3] shows: Theorem 1 The communication networks G and G 0 are equivalent. We prove our lower bound and analyze our algorithm for cliques, instead of more complicated topologies. Theorem 1 shows that the results obtained on the cliques apply to the original topologies. Note that the uncertainties in G 0 satisfy the triangle inequality, since H 0 is defined using shortest path lengths..4 Shifting Like those in [5] and [3], our lower bound result is obtained by shifting executions, that is, by shifting the real times at which events occur. More formally, let ff =( 0 ; 1 ;:::; )be an execution and let x i be a real number, 0» i» n 1. Defineshift(ff; hx 0 ;:::;x i)to be ( 0 0 ; 0 1 ;:::; 0 ), where each 0 i is the timed history resulting from i by adding x i to the real time associated with each event in i. Shifting an execution changes the hardware clocks and the delays experienced by messages. Lundelius and Lynch [5] quantified the changes as follows: Lemma Let ff be an execution with hardware clocks HC i and let x i be a real number, 0» i» n 1. Then shift(ff; hx 0 ;:::;x i)is an execution that is indistinguishable from ff, and in which (a) the hardware clock of p i,hc 0 i (t), is equal to HC i(t) x i for all t, and (b) every message from p i to p j has delay ffi x i + x j,whereffi is the delay of the message in ff. Note that shifting an execution might not result in an admissible execution. 3 Lower Bound for Arbitrary Topology Let diam(g) denote the diameter of communication network G with respect to the uncertainties. Theorem 3 For any communication network G, opt(g) 1 diam(g). 4
5 Proof Let G 0 be the clique from Section.3 that is equivalent to G. Letu ij denote H 0 (i; j), the uncertainty on edge (p i ;p j ) in G 0. We will show that opt(g 0 ) is at least 1 diam(g0 ). Since Theorem 1 implies that opt(g 0 )=opt(g) and since the diameter of G is the same as that of G 0, the result follows. Let p a and p b be two processors in G 0 such that u ab equals the diameter of G 0. Choose any algorithm for G 0 that achieves "-synchronized clocks. Consider the admissible execution ff in which the delays are as follows. For any two processors p i and p j,whereu ai < u aj (i.e., p i is at least as close to p a, w.r.t. uncertainties, as p j is), the delay of every message from p i to p j is 0, and the delay of every message from p j to p i is u ij.whenu ai = u aj, we choose the delay of every message from p i to p j to be 0, and the delay of every message from p j to p i to be u ij. Since the algorithm must work correctly in ff, AC a AC b ": (1) Let ff 0 = shift(ff; ~x), wherex i = u ai u ab, 0» i» n 1. Note that p a is shifted by u ab and p b is shifted by 0. By Lemma, the delay of every message in ff 0 from p i to p j is 0 (u ai u ab )+(u aj u ab )=u aj u ai. This expression is at most u ij, by the triangle inequality, so the new delay is not too big. This expression is at least 0, since u ai» u aj, so the new delay is not too small. By Lemma, the delay of every message in ff 0 from p j to p i is u ij (u aj u ab )+(u ai u ab ) = u ij + u ai u aj. This expression is at most u ij,sinceu ai» u aj, so the new delay is not too big. This expression is at least 0, by the triangle inequality, so the new delay is not too small. Therefore ff 0 is admissible. Since the algorithm must work correctly in ff 0,wehave: ACb 0 AC0 a ": () Since AC 0 b = AC b +0and AC 0 a = AC a + u ab, inequalities (1) and () imply that " 1 u ab. Thus for the arbitrary algorithm, " is at least half the diameter. 4 Upper Bounds 4.1 The Algorithm We consider the averaging algorithm of [5] for a clique, slightly modified to handle the fact that different edges have different uncertainties. (The description of the algorithm and Lemma 4 are modeled after [].) Each processor p i begins by sending its current hardware clock value to all the other processors. It has an array diff whose j-th entry is set equal to p i s estimated difference between p i s hardware clock and p j s hardware clock. For j 6= i, this difference is estimated using the value T contained in the message that p i receives from p j and assuming that this message took u ij time to arrive. Once p i has an estimate for 5
6 initially diff i [i] =0 at first computation step: 1: send HC i (current hardware clock value) to all other processors upon receiving message T from some p j : : diff i [j] :=T+ u ij HC i 3: if a message has been received from every other processor then 4: adj i P := 1 n diff k=0 i[k] Figure 1: Averaging algorithm; code for processor p i, 0» i» n 1. every processor, it sets its adjustment to the average of all the estimated differences. (See Figure 1.) We will analyze the clock synchronization achieved by the averaging algorithm for a clique G 0 with arbitrary symmetric uncertainties (denoted u ij ). Then we will show how the general result can be specialized into closed forms for specific cliques that are equivalent to certain topologies. Theorem 1 shows that the upper bounds obtained for these cliques also hold for the other topologies. The applicability of the averaging algorithm to general topologies requires all-pairs shortest-paths computation. Lemma 4 Consider any execution of the averaging algorithm that is admissible for G 0. For any two processors p i and p j and any time t after the algorithm terminates (executes Line 4), jac i (t) AC j (t)j» 1 n l=0;l6=i u li + l=0;l6=j u lj 1 A : Proof For every time t after p i sets diff i [j], diff i [j](t) =HC j (t) HC i (t)+ err ji,whereerr ji is a constant. The definition of the algorithm shows that jac i (t) AC j (t)j» 1 n jerrij j + jerr ji j + The bounds on err ji and the rules of absolute value give the result. l=0;l6=i;j 1 jerr li err lj ja : 4. Generalized Hypercubes Without Wrap-around The k-ary m-cube network is a generalization of the hypercube architecture where k =. Inthek-ary m-cube, there are m dimensions and k nodes on each dimension (see [4], p. 86). More formally, each node is represented as a vector ha 0 ;a 1 ;:::;a m 1 i, where each a r is an element of f0; 1;:::;k 1g. Thus there 6
7 are n = k m nodes. There is an edge between two nodes ~a and ~ b if they differ in exactly one component, say the r-th, and a r = b r +1. We need the following fact about distances in (unweighted) k-ary m-cubes without wrap-around. Given such a graph G, letdist G (~a; ~ b) be the minimum number of edges in any path from ~a to ~ b in G. Lemma 5 For any k-ary m-cube G =(V; E) without wrap-around, for any node ~a in V, dist G (~a; ~ 1 b)» m(km+1 k m ): ~ b Proof Consider a particular node ~ b. The distance between ~a and ~ b is the sum, over all dimensions P r, ofthe distance from a r to b r. With no wrap-around, this distance is jb r a r j. It is obvious that ~ b dist G (~a; ~ b)» P~ b dist G (~ 0; ~ b) where ~ 0 is the vector of all zeroes. Let us then compute P ~ b dist G (~ 0; ~ b). This sum can be written: m 1 ~ b r=0 b r : (3) Now let us concentrate on dimension r. For how many vectors ~ b is b r equal to 0? There are k independent choices for each of the m 1 other entries, so the answer is k m 1. The same is true for every value of b r between 0 and k 1. Thus the contribution to the sum in expression (3) from dimension r is k m 1 k 1 h=0 This sum can be written as 1 (km+1 k m ). We multiply this expression by m, to account for all the dimensions. Theorem 6 For any k-ary m-cube (without wrap-around) communication network G with uncertainty u on each edge, opt(g) is at most 1 um(k 1). Proof Let G 0 be the equivalent clique communication network from Section.3. By Theorem 1, it suffices to show that the averaging function on G 0 achieves "-synchronized clocks, where " = 1 um(k 1). Consider any execution of the algorithm that is admissible for G 0. By Lemma 4, for any two processors p i and p j and any time t after the algorithm terminates jac i (t) AC j (t)j» 1 n h: l=0;l6=i u li + l=0;l6=j u lj 1 A : By the definition of G 0, u lh = u dist G (l; h), forh = i; j. By Lemma 5, for h = i; j, Since n = k m, the result follows. l=0;l6=h u lh» um 1 (km+1 k m ): 7
8 4.3 Generalized Hypercubes With Wrap-around The definition of the k-ary m-cube with wrap-around is the same as for the k-ary m-cube without wraparound, except that we add mod k to the condition under which there is an edge between two nodes. That is, there is an edge between two nodes ~a and ~ b if they differ in exactly one component, say the r-th, and if a r = b r + 1 mod k. Given a graph G, letdist G (~a; ~ b) be the minimum number of edges in any path from ~a to ~ b in G. We need the following fact about distances in (unweighted) k-ary m-cubes with wrap-around. Lemma 7 For any k-ary m-cube G =(V; E) with wrap-around, for any node ~a in V, ( 1 dist G (~a; ~ 4 b)= mkm+1 when k is even 1 ~ b 4 m(km+1 k m 1 ) when k is odd: Proof Consider a particular node ~ b. The distance between ~a and ~ b is the sum, over all dimensions r, ofthe distance from a r to b r. However, we must take into account the wrap-around edges. In this case the distance is jb r a r j if this quantity is at most b k c, otherwise it is k jb r a r j. Thus the desired sum can be written: m 1 ~ b r=0 min(jb r a r j;k jb r a r j): (4) Now let us concentrate on dimension r. For how many vectors ~ b is b r equal to 0? There are k independent choices for each of the m 1 other entries, so the answer is k m 1. The same is true for every value of b r between 0 and k 1. Thus the contribution to the sum in expression (4) from dimension r is k m 1 k 1 h=0 min(jh a r j;k jh a r j): (5) This sum contains two terms equal to 1 (there are two nodes at distance 1 from ~a along dimension r), two terms equal to, etc., up to two terms equal to b k 1 c, and, if k is even, one term equal to k (there is one node at distance k from ~a along dimension r). First consider the case when k is odd. Then expression (5) becomes k m 1 b k 1 c j=1 Algebraic manipulations reduce this to 1 4 (km+1 k m 1 ). We multiply this expression by m, to account for all the dimensions. Now consider the case when k is even. Expression (5) now becomes k m 1 k 1 j=1 j: j + k m 1 k : Algebraic manipulations reduce this to 1 4 km+1. We multiply by m to account for all dimensions. 8
9 Theorem 8 For any k-ary m-cube (with wrap-around) communication network G with uncertainty u on each edge, opt(g) is at most 1 umk when k is even and 1 um(k k ) when k is odd. Proof The proof is essentially the same as that for Theorem 6. The differences are that " = 1 umk when k 4 is even and 1 um(k 4 1 k ) otherwise, and that Lemma 7 is invoked instead of Lemma 5. 5 Open Questions The obvious open question in our work is to tighten the bounds for k-ary m-cubes with wrap-around when k is odd. We believe that the algorithm is optimal and that a more involved shifting argument is needed to strengthen the lower bound. The evidence for this is that a 3-ary 1-cube is a ring with three processors, which is also a clique. Lundelius and Lynch [5] showed in this case that the tight bound is u, which is what 3 the algorithm gives, and not 1 u as given by the lower bound of this paper. It would be interesting to characterize the class of networks and uncertainty assumptions for which the simple algorithm is optimal, and similarly those for which the 1 diam lower bound is tight. Further work is needed to obtain closed form expressions for other networks and delay assumptions. References [1] H. Attiya, A. Herzberg, and S. Rajsbaum, Optimal Clock Synchronization Under Different Delay Assumptions, Proc. of the 1th Annual ACM Symp. on Principles of Distributed Computing, pp , [] H. Attiya and J. L. Welch, Distributed Computing: Fundamentals, Simulations and Advanced Topics, (Section 6.3), McGraw-Hill Publishing Company, [3] J. Y. Halpern, N. Megiddo, and A. A. Munshi, Optimal Precision in The Presence of Uncertainty, Journal of Complexity, vol. 1, pp , [4] K. Hwang, Advanced Computer Architecture, McGraw-Hill Inc., New York, [5] J. Lundelius and N. A. Lynch, An Upper and Lower Bound for Clock Synchronization, Information and Control, vol. 6, pp , [6] B. Patt-Shamir and S. Rajsbaum, A Theory of Clock Synchronization, Proceedings of the 6th Annual ACM Symposium on Theory of Computing, pp ,
Causality and Time. The Happens-Before Relation
 Causality and Time The Happens-Before Relation Because executions are sequences of events, they induce a total order on all the events It is possible that two events by different processors do not influence
Causality and Time The Happens-Before Relation Because executions are sequences of events, they induce a total order on all the events It is possible that two events by different processors do not influence
Gradient Clock Synchronization
 Noname manuscript No. (will be inserted by the editor) Rui Fan Nancy Lynch Gradient Clock Synchronization the date of receipt and acceptance should be inserted later Abstract We introduce the distributed
Noname manuscript No. (will be inserted by the editor) Rui Fan Nancy Lynch Gradient Clock Synchronization the date of receipt and acceptance should be inserted later Abstract We introduce the distributed
Time Synchronization
 Massachusetts Institute of Technology Lecture 7 6.895: Advanced Distributed Algorithms March 6, 2006 Professor Nancy Lynch Time Synchronization Readings: Fan, Lynch. Gradient clock synchronization Attiya,
Massachusetts Institute of Technology Lecture 7 6.895: Advanced Distributed Algorithms March 6, 2006 Professor Nancy Lynch Time Synchronization Readings: Fan, Lynch. Gradient clock synchronization Attiya,
Verification of clock synchronization algorithm (Original Welch-Lynch algorithm and adaptation to TTA)
 Verification of clock synchronization algorithm (Original Welch-Lynch algorithm and adaptation to TTA) Christian Mueller November 25, 2005 1 Contents 1 Clock synchronization in general 3 1.1 Introduction............................
Verification of clock synchronization algorithm (Original Welch-Lynch algorithm and adaptation to TTA) Christian Mueller November 25, 2005 1 Contents 1 Clock synchronization in general 3 1.1 Introduction............................
Gradient Clock Synchronization
 Gradient Clock Synchronization Rui Fan Nancy Lynch Computer Science and Articial Intelligence Laboratory Massachusetts Institute of Technology {rfan, lynch}@theory.csail.mit.edu ABSTRACT We introduce the
Gradient Clock Synchronization Rui Fan Nancy Lynch Computer Science and Articial Intelligence Laboratory Massachusetts Institute of Technology {rfan, lynch}@theory.csail.mit.edu ABSTRACT We introduce the
Fault-Tolerant Consensus
 Fault-Tolerant Consensus CS556 - Panagiota Fatourou 1 Assumptions Consensus Denote by f the maximum number of processes that may fail. We call the system f-resilient Description of the Problem Each process
Fault-Tolerant Consensus CS556 - Panagiota Fatourou 1 Assumptions Consensus Denote by f the maximum number of processes that may fail. We call the system f-resilient Description of the Problem Each process
Lecture 4: An FPTAS for Knapsack, and K-Center
 Comp 260: Advanced Algorithms Tufts University, Spring 2016 Prof. Lenore Cowen Scribe: Eric Bailey Lecture 4: An FPTAS for Knapsack, and K-Center 1 Introduction Definition 1.0.1. The Knapsack problem (restated)
Comp 260: Advanced Algorithms Tufts University, Spring 2016 Prof. Lenore Cowen Scribe: Eric Bailey Lecture 4: An FPTAS for Knapsack, and K-Center 1 Introduction Definition 1.0.1. The Knapsack problem (restated)
Lecture 13: Spectral Graph Theory
 CSE 521: Design and Analysis of Algorithms I Winter 2017 Lecture 13: Spectral Graph Theory Lecturer: Shayan Oveis Gharan 11/14/18 Disclaimer: These notes have not been subjected to the usual scrutiny reserved
CSE 521: Design and Analysis of Algorithms I Winter 2017 Lecture 13: Spectral Graph Theory Lecturer: Shayan Oveis Gharan 11/14/18 Disclaimer: These notes have not been subjected to the usual scrutiny reserved
Online Packet Routing on Linear Arrays and Rings
 Proc. 28th ICALP, LNCS 2076, pp. 773-784, 2001 Online Packet Routing on Linear Arrays and Rings Jessen T. Havill Department of Mathematics and Computer Science Denison University Granville, OH 43023 USA
Proc. 28th ICALP, LNCS 2076, pp. 773-784, 2001 Online Packet Routing on Linear Arrays and Rings Jessen T. Havill Department of Mathematics and Computer Science Denison University Granville, OH 43023 USA
Lower Bounds for Achieving Synchronous Early Stopping Consensus with Orderly Crash Failures
 Lower Bounds for Achieving Synchronous Early Stopping Consensus with Orderly Crash Failures Xianbing Wang 1, Yong-Meng Teo 1,2, and Jiannong Cao 3 1 Singapore-MIT Alliance, 2 Department of Computer Science,
Lower Bounds for Achieving Synchronous Early Stopping Consensus with Orderly Crash Failures Xianbing Wang 1, Yong-Meng Teo 1,2, and Jiannong Cao 3 1 Singapore-MIT Alliance, 2 Department of Computer Science,
6.852: Distributed Algorithms Fall, Class 24
 6.852: Distributed Algorithms Fall, 2009 Class 24 Today s plan Self-stabilization Self-stabilizing algorithms: Breadth-first spanning tree Mutual exclusion Composing self-stabilizing algorithms Making
6.852: Distributed Algorithms Fall, 2009 Class 24 Today s plan Self-stabilization Self-stabilizing algorithms: Breadth-first spanning tree Mutual exclusion Composing self-stabilizing algorithms Making
Simple Bivalency Proofs of the Lower Bounds in Synchronous Consensus Problems
 Simple Bivalency Proofs of the Lower Bounds in Synchronous Consensus Problems Xianbing Wang, Yong-Meng Teo, and Jiannong Cao Singapore-MIT Alliance E4-04-10, 4 Engineering Drive 3, Singapore 117576 Abstract
Simple Bivalency Proofs of the Lower Bounds in Synchronous Consensus Problems Xianbing Wang, Yong-Meng Teo, and Jiannong Cao Singapore-MIT Alliance E4-04-10, 4 Engineering Drive 3, Singapore 117576 Abstract
6.852: Distributed Algorithms Fall, Class 10
 6.852: Distributed Algorithms Fall, 2009 Class 10 Today s plan Simulating synchronous algorithms in asynchronous networks Synchronizers Lower bound for global synchronization Reading: Chapter 16 Next:
6.852: Distributed Algorithms Fall, 2009 Class 10 Today s plan Simulating synchronous algorithms in asynchronous networks Synchronizers Lower bound for global synchronization Reading: Chapter 16 Next:
arxiv: v1 [cs.gr] 25 Nov 2015
![arxiv: v1 [cs.gr] 25 Nov 2015 arxiv: v1 [cs.gr] 25 Nov 2015](/thumbs/82/86765976.jpg) EMBEDDING OF HYPERCUBE INTO CYLINDER WEIXING JI, QINGHUI LIU, GUIZHEN WANG, AND ZHUOJIA SHEN arxiv:1511.07932v1 [cs.gr] 25 Nov 2015 Abstract. Task mapping in modern high performance parallel computers
EMBEDDING OF HYPERCUBE INTO CYLINDER WEIXING JI, QINGHUI LIU, GUIZHEN WANG, AND ZHUOJIA SHEN arxiv:1511.07932v1 [cs.gr] 25 Nov 2015 Abstract. Task mapping in modern high performance parallel computers
2 Notation and Preliminaries
 On Asymmetric TSP: Transformation to Symmetric TSP and Performance Bound Ratnesh Kumar Haomin Li epartment of Electrical Engineering University of Kentucky Lexington, KY 40506-0046 Abstract We show that
On Asymmetric TSP: Transformation to Symmetric TSP and Performance Bound Ratnesh Kumar Haomin Li epartment of Electrical Engineering University of Kentucky Lexington, KY 40506-0046 Abstract We show that
Asynchronous Models For Consensus
 Distributed Systems 600.437 Asynchronous Models for Consensus Department of Computer Science The Johns Hopkins University 1 Asynchronous Models For Consensus Lecture 5 Further reading: Distributed Algorithms
Distributed Systems 600.437 Asynchronous Models for Consensus Department of Computer Science The Johns Hopkins University 1 Asynchronous Models For Consensus Lecture 5 Further reading: Distributed Algorithms
Determinants - Uniqueness and Properties
 Determinants - Uniqueness and Properties 2-2-2008 In order to show that there s only one determinant function on M(n, R), I m going to derive another formula for the determinant It involves permutations
Determinants - Uniqueness and Properties 2-2-2008 In order to show that there s only one determinant function on M(n, R), I m going to derive another formula for the determinant It involves permutations
2 Introduction to Network Theory
 Introduction to Network Theory In this section we will introduce some popular families of networks and will investigate how well they allow to support routing.. Basic network topologies The most basic
Introduction to Network Theory In this section we will introduce some popular families of networks and will investigate how well they allow to support routing.. Basic network topologies The most basic
Distributed Systems Byzantine Agreement
 Distributed Systems Byzantine Agreement He Sun School of Informatics University of Edinburgh Outline Finish EIG algorithm for Byzantine agreement. Number-of-processors lower bound for Byzantine agreement.
Distributed Systems Byzantine Agreement He Sun School of Informatics University of Edinburgh Outline Finish EIG algorithm for Byzantine agreement. Number-of-processors lower bound for Byzantine agreement.
Message Passing Algorithms and Junction Tree Algorithms
 Message Passing lgorithms and Junction Tree lgorithms Le Song Machine Learning II: dvanced Topics S 8803ML, Spring 2012 Inference in raphical Models eneral form of the inference problem P X 1,, X n Ψ(
Message Passing lgorithms and Junction Tree lgorithms Le Song Machine Learning II: dvanced Topics S 8803ML, Spring 2012 Inference in raphical Models eneral form of the inference problem P X 1,, X n Ψ(
ONLINE SCHEDULING OF MALLEABLE PARALLEL JOBS
 ONLINE SCHEDULING OF MALLEABLE PARALLEL JOBS Richard A. Dutton and Weizhen Mao Department of Computer Science The College of William and Mary P.O. Box 795 Williamsburg, VA 2317-795, USA email: {radutt,wm}@cs.wm.edu
ONLINE SCHEDULING OF MALLEABLE PARALLEL JOBS Richard A. Dutton and Weizhen Mao Department of Computer Science The College of William and Mary P.O. Box 795 Williamsburg, VA 2317-795, USA email: {radutt,wm}@cs.wm.edu
Conquering Edge Faults in a Butterfly with Automorphisms
 International Conference on Theoretical and Mathematical Foundations of Computer Science (TMFCS-0) Conquering Edge Faults in a Butterfly with Automorphisms Meghanad D. Wagh and Khadidja Bendjilali Department
International Conference on Theoretical and Mathematical Foundations of Computer Science (TMFCS-0) Conquering Edge Faults in a Butterfly with Automorphisms Meghanad D. Wagh and Khadidja Bendjilali Department
Gray Codes for Torus and Edge Disjoint Hamiltonian Cycles Λ
 Gray Codes for Torus and Edge Disjoint Hamiltonian Cycles Λ Myung M. Bae Scalable POWERparallel Systems, MS/P963, IBM Corp. Poughkeepsie, NY 6 myungbae@us.ibm.com Bella Bose Dept. of Computer Science Oregon
Gray Codes for Torus and Edge Disjoint Hamiltonian Cycles Λ Myung M. Bae Scalable POWERparallel Systems, MS/P963, IBM Corp. Poughkeepsie, NY 6 myungbae@us.ibm.com Bella Bose Dept. of Computer Science Oregon
Perfect Dominating Sets in Gaussian Graphs
 Perfect Dominating Sets in Gaussian Graphs Carmen Martínez 1, Miquel Moretó 2 and Ramón Beivide 3. Abstract Gaussian Graphs are introduced and analyzed in this paper. The set of vertices of these Cayley
Perfect Dominating Sets in Gaussian Graphs Carmen Martínez 1, Miquel Moretó 2 and Ramón Beivide 3. Abstract Gaussian Graphs are introduced and analyzed in this paper. The set of vertices of these Cayley
TIME BOUNDS FOR SHARED OBJECTS IN PARTIALLY SYNCHRONOUS SYSTEMS. A Thesis JIAQI WANG
 TIME BOUNDS FOR SHARED OBJECTS IN PARTIALLY SYNCHRONOUS SYSTEMS A Thesis by JIAQI WANG Submitted to the Office of Graduate Studies of Texas A&M University in partial fulfillment of the requirements for
TIME BOUNDS FOR SHARED OBJECTS IN PARTIALLY SYNCHRONOUS SYSTEMS A Thesis by JIAQI WANG Submitted to the Office of Graduate Studies of Texas A&M University in partial fulfillment of the requirements for
Convergence of Time Decay for Event Weights
 Convergence of Time Decay for Event Weights Sharon Simmons and Dennis Edwards Department of Computer Science, University of West Florida 11000 University Parkway, Pensacola, FL, USA Abstract Events of
Convergence of Time Decay for Event Weights Sharon Simmons and Dennis Edwards Department of Computer Science, University of West Florida 11000 University Parkway, Pensacola, FL, USA Abstract Events of
Unreliable Failure Detectors for Reliable Distributed Systems
 Unreliable Failure Detectors for Reliable Distributed Systems A different approach Augment the asynchronous model with an unreliable failure detector for crash failures Define failure detectors in terms
Unreliable Failure Detectors for Reliable Distributed Systems A different approach Augment the asynchronous model with an unreliable failure detector for crash failures Define failure detectors in terms
INVERSE SPANNING TREE PROBLEMS: FORMULATIONS AND ALGORITHMS
 INVERSE SPANNING TREE PROBLEMS: FORMULATIONS AND ALGORITHMS P. T. Sokkalingam Department of Mathematics Indian Institute of Technology, Kanpur-208 016, INDIA Ravindra K. Ahuja Dept. of Industrial & Management
INVERSE SPANNING TREE PROBLEMS: FORMULATIONS AND ALGORITHMS P. T. Sokkalingam Department of Mathematics Indian Institute of Technology, Kanpur-208 016, INDIA Ravindra K. Ahuja Dept. of Industrial & Management
arxiv: v1 [math.co] 29 Jul 2010
![arxiv: v1 [math.co] 29 Jul 2010 arxiv: v1 [math.co] 29 Jul 2010](/thumbs/71/66087520.jpg) RADIO NUMBERS FOR GENERALIZED PRISM GRAPHS PAUL MARTINEZ, JUAN ORTIZ, MAGGY TOMOVA, AND CINDY WYELS arxiv:1007.5346v1 [math.co] 29 Jul 2010 Abstract. A radio labeling is an assignment c : V (G) N such
RADIO NUMBERS FOR GENERALIZED PRISM GRAPHS PAUL MARTINEZ, JUAN ORTIZ, MAGGY TOMOVA, AND CINDY WYELS arxiv:1007.5346v1 [math.co] 29 Jul 2010 Abstract. A radio labeling is an assignment c : V (G) N such
CS 347 Parallel and Distributed Data Processing
 CS 347 Parallel and Distributed Data Processing Spring 2016 & Clocks, Clocks, and the Ordering of Events in a Distributed System. L. Lamport, Communications of the ACM, 1978 Notes 15: & Clocks CS 347 Notes
CS 347 Parallel and Distributed Data Processing Spring 2016 & Clocks, Clocks, and the Ordering of Events in a Distributed System. L. Lamport, Communications of the ACM, 1978 Notes 15: & Clocks CS 347 Notes
Online Interval Coloring and Variants
 Online Interval Coloring and Variants Leah Epstein 1, and Meital Levy 1 Department of Mathematics, University of Haifa, 31905 Haifa, Israel. Email: lea@math.haifa.ac.il School of Computer Science, Tel-Aviv
Online Interval Coloring and Variants Leah Epstein 1, and Meital Levy 1 Department of Mathematics, University of Haifa, 31905 Haifa, Israel. Email: lea@math.haifa.ac.il School of Computer Science, Tel-Aviv
NP-Completeness. Andreas Klappenecker. [based on slides by Prof. Welch]
![NP-Completeness. Andreas Klappenecker. [based on slides by Prof. Welch] NP-Completeness. Andreas Klappenecker. [based on slides by Prof. Welch]](/thumbs/79/79291182.jpg) NP-Completeness Andreas Klappenecker [based on slides by Prof. Welch] 1 Prelude: Informal Discussion (Incidentally, we will never get very formal in this course) 2 Polynomial Time Algorithms Most of the
NP-Completeness Andreas Klappenecker [based on slides by Prof. Welch] 1 Prelude: Informal Discussion (Incidentally, we will never get very formal in this course) 2 Polynomial Time Algorithms Most of the
Degradable Agreement in the Presence of. Byzantine Faults. Nitin H. Vaidya. Technical Report #
 Degradable Agreement in the Presence of Byzantine Faults Nitin H. Vaidya Technical Report # 92-020 Abstract Consider a system consisting of a sender that wants to send a value to certain receivers. Byzantine
Degradable Agreement in the Presence of Byzantine Faults Nitin H. Vaidya Technical Report # 92-020 Abstract Consider a system consisting of a sender that wants to send a value to certain receivers. Byzantine
Gradient Clock Synchronization in Dynamic Networks Fabian Kuhn, Thomas Locher, and Rotem Oshman
 Computer Science and Artificial Intelligence Laboratory Technical Report MIT-CSAIL-TR-2009-022 May 29, 2009 Gradient Clock Synchronization in Dynamic Networks Fabian Kuhn, Thomas Locher, and Rotem Oshman
Computer Science and Artificial Intelligence Laboratory Technical Report MIT-CSAIL-TR-2009-022 May 29, 2009 Gradient Clock Synchronization in Dynamic Networks Fabian Kuhn, Thomas Locher, and Rotem Oshman
Atomic m-register operations
 Atomic m-register operations Michael Merritt Gadi Taubenfeld December 15, 1993 Abstract We investigate systems where it is possible to access several shared registers in one atomic step. We characterize
Atomic m-register operations Michael Merritt Gadi Taubenfeld December 15, 1993 Abstract We investigate systems where it is possible to access several shared registers in one atomic step. We characterize
Concurrent Counting is Harder than Queuing
 Concurrent Counting is Harder than Queuing Srikanta Tirthapura 1, Costas Busch 2 1 Iowa State University 2 Rensselaer Polytechnic Inst. Dept. of Elec. and Computer Engg. Computer Science Department Ames,
Concurrent Counting is Harder than Queuing Srikanta Tirthapura 1, Costas Busch 2 1 Iowa State University 2 Rensselaer Polytechnic Inst. Dept. of Elec. and Computer Engg. Computer Science Department Ames,
Gossip Latin Square and The Meet-All Gossipers Problem
 Gossip Latin Square and The Meet-All Gossipers Problem Nethanel Gelernter and Amir Herzberg Department of Computer Science Bar Ilan University Ramat Gan, Israel 52900 Email: firstname.lastname@gmail.com
Gossip Latin Square and The Meet-All Gossipers Problem Nethanel Gelernter and Amir Herzberg Department of Computer Science Bar Ilan University Ramat Gan, Israel 52900 Email: firstname.lastname@gmail.com
Clocks in Asynchronous Systems
 Clocks in Asynchronous Systems The Internet Network Time Protocol (NTP) 8 Goals provide the ability to externally synchronize clients across internet to UTC provide reliable service tolerating lengthy
Clocks in Asynchronous Systems The Internet Network Time Protocol (NTP) 8 Goals provide the ability to externally synchronize clients across internet to UTC provide reliable service tolerating lengthy
Appendix A. Formal Proofs
 Distributed Reasoning for Multiagent Simple Temporal Problems Appendix A Formal Proofs Throughout this paper, we provided proof sketches to convey the gist of the proof when presenting the full proof would
Distributed Reasoning for Multiagent Simple Temporal Problems Appendix A Formal Proofs Throughout this paper, we provided proof sketches to convey the gist of the proof when presenting the full proof would
Finding a Heaviest Triangle is not Harder than Matrix Multiplication
 Finding a Heaviest Triangle is not Harder than Matrix Multiplication Artur Czumaj Department of Computer Science New Jersey Institute of Technology aczumaj@acm.org Andrzej Lingas Department of Computer
Finding a Heaviest Triangle is not Harder than Matrix Multiplication Artur Czumaj Department of Computer Science New Jersey Institute of Technology aczumaj@acm.org Andrzej Lingas Department of Computer
Logical Time. 1. Introduction 2. Clock and Events 3. Logical (Lamport) Clocks 4. Vector Clocks 5. Efficient Implementation
 Logical Time Nicola Dragoni Embedded Systems Engineering DTU Compute 1. Introduction 2. Clock and Events 3. Logical (Lamport) Clocks 4. Vector Clocks 5. Efficient Implementation 2013 ACM Turing Award:
Logical Time Nicola Dragoni Embedded Systems Engineering DTU Compute 1. Introduction 2. Clock and Events 3. Logical (Lamport) Clocks 4. Vector Clocks 5. Efficient Implementation 2013 ACM Turing Award:
Index coding with side information
 Index coding with side information Ehsan Ebrahimi Targhi University of Tartu Abstract. The Index Coding problem has attracted a considerable amount of attention in the recent years. The problem is motivated
Index coding with side information Ehsan Ebrahimi Targhi University of Tartu Abstract. The Index Coding problem has attracted a considerable amount of attention in the recent years. The problem is motivated
On the Exponent of the All Pairs Shortest Path Problem
 On the Exponent of the All Pairs Shortest Path Problem Noga Alon Department of Mathematics Sackler Faculty of Exact Sciences Tel Aviv University Zvi Galil Department of Computer Science Sackler Faculty
On the Exponent of the All Pairs Shortest Path Problem Noga Alon Department of Mathematics Sackler Faculty of Exact Sciences Tel Aviv University Zvi Galil Department of Computer Science Sackler Faculty
Concurrent Counting is harder than Queuing
 Concurrent Counting is harder than Queuing Costas Busch Rensselaer Polytechnic Intitute Srikanta Tirthapura Iowa State University 1 rbitrary graph 2 Distributed Counting count count count count Some processors
Concurrent Counting is harder than Queuing Costas Busch Rensselaer Polytechnic Intitute Srikanta Tirthapura Iowa State University 1 rbitrary graph 2 Distributed Counting count count count count Some processors
AGREEMENT PROBLEMS (1) Agreement problems arise in many practical applications:
 AGREEMENT PROBLEMS (1) AGREEMENT PROBLEMS Agreement problems arise in many practical applications: agreement on whether to commit or abort the results of a distributed atomic action (e.g. database transaction)
AGREEMENT PROBLEMS (1) AGREEMENT PROBLEMS Agreement problems arise in many practical applications: agreement on whether to commit or abort the results of a distributed atomic action (e.g. database transaction)
Timing Results of a Parallel FFTsynth
 Purdue University Purdue e-pubs Department of Computer Science Technical Reports Department of Computer Science 1994 Timing Results of a Parallel FFTsynth Robert E. Lynch Purdue University, rel@cs.purdue.edu
Purdue University Purdue e-pubs Department of Computer Science Technical Reports Department of Computer Science 1994 Timing Results of a Parallel FFTsynth Robert E. Lynch Purdue University, rel@cs.purdue.edu
The Weighted Byzantine Agreement Problem
 The Weighted Byzantine Agreement Problem Vijay K. Garg and John Bridgman Department of Electrical and Computer Engineering The University of Texas at Austin Austin, TX 78712-1084, USA garg@ece.utexas.edu,
The Weighted Byzantine Agreement Problem Vijay K. Garg and John Bridgman Department of Electrical and Computer Engineering The University of Texas at Austin Austin, TX 78712-1084, USA garg@ece.utexas.edu,
Radio Network Clustering from Scratch
 Radio Network Clustering from Scratch Fabian Kuhn, Thomas Moscibroda, Roger Wattenhofer {kuhn,moscitho,wattenhofer}@inf.ethz.ch Department of Computer Science, ETH Zurich, 8092 Zurich, Switzerland Abstract.
Radio Network Clustering from Scratch Fabian Kuhn, Thomas Moscibroda, Roger Wattenhofer {kuhn,moscitho,wattenhofer}@inf.ethz.ch Department of Computer Science, ETH Zurich, 8092 Zurich, Switzerland Abstract.
A Deterministic Almost-Tight Distributed Algorithm for Approximating Single-Source Shortest Paths
 A Deterministic Almost-Tight Distributed Algorithm for Approximating Single-Source Shortest Paths Monika Henzinger 1 Sebastian Krinninger 2 Danupon Nanongkai 3 1 University of Vienna 2 Max Planck Institute
A Deterministic Almost-Tight Distributed Algorithm for Approximating Single-Source Shortest Paths Monika Henzinger 1 Sebastian Krinninger 2 Danupon Nanongkai 3 1 University of Vienna 2 Max Planck Institute
The Multiple Traveling Salesman Problem with Time Windows: Bounds for the Minimum Number of Vehicles
 The Multiple Traveling Salesman Problem with Time Windows: Bounds for the Minimum Number of Vehicles Snežana Mitrović-Minić Ramesh Krishnamurti School of Computing Science, Simon Fraser University, Burnaby,
The Multiple Traveling Salesman Problem with Time Windows: Bounds for the Minimum Number of Vehicles Snežana Mitrović-Minić Ramesh Krishnamurti School of Computing Science, Simon Fraser University, Burnaby,
A Self-Stabilizing Algorithm for Finding a Minimal Distance-2 Dominating Set in Distributed Systems
 JOURNAL OF INFORMATION SCIENCE AND ENGINEERING 24, 1709-1718 (2008) A Self-Stabilizing Algorithm for Finding a Minimal Distance-2 Dominating Set in Distributed Systems JI-CHERNG LIN, TETZ C. HUANG, CHENG-PIN
JOURNAL OF INFORMATION SCIENCE AND ENGINEERING 24, 1709-1718 (2008) A Self-Stabilizing Algorithm for Finding a Minimal Distance-2 Dominating Set in Distributed Systems JI-CHERNG LIN, TETZ C. HUANG, CHENG-PIN
Distributed MST for constant diameter graphs
 Distrib. Comput. (2006) 18(6): 453 460 DOI 10.1007/s00446-005-0127-6 ORIGINAL ARTICLE Zvi Lotker Boaz Patt-Shamir David Peleg Distributed MST for constant diameter graphs Received: 1 December 2003 / Accepted:
Distrib. Comput. (2006) 18(6): 453 460 DOI 10.1007/s00446-005-0127-6 ORIGINAL ARTICLE Zvi Lotker Boaz Patt-Shamir David Peleg Distributed MST for constant diameter graphs Received: 1 December 2003 / Accepted:
The Hamming Codes and Delsarte s Linear Programming Bound
 The Hamming Codes and Delsarte s Linear Programming Bound by Sky McKinley Under the Astute Tutelage of Professor John S. Caughman, IV A thesis submitted in partial fulfillment of the requirements for the
The Hamming Codes and Delsarte s Linear Programming Bound by Sky McKinley Under the Astute Tutelage of Professor John S. Caughman, IV A thesis submitted in partial fulfillment of the requirements for the
Distributed Algorithms of Finding the Unique Minimum Distance Dominating Set in Directed Split-Stars
 Distributed Algorithms of Finding the Unique Minimum Distance Dominating Set in Directed Split-Stars Fu Hsing Wang 1 Jou Ming Chang 2 Yue Li Wang 1, 1 Department of Information Management, National Taiwan
Distributed Algorithms of Finding the Unique Minimum Distance Dominating Set in Directed Split-Stars Fu Hsing Wang 1 Jou Ming Chang 2 Yue Li Wang 1, 1 Department of Information Management, National Taiwan
Minimum Moment Steiner Trees
 Minimum Moment Steiner Trees Wangqi Qiu Weiping Shi Abstract For a rectilinear Steiner tree T with a root, define its k-th moment M k (T ) = (d T (u)) k du, T where the integration is over all edges of
Minimum Moment Steiner Trees Wangqi Qiu Weiping Shi Abstract For a rectilinear Steiner tree T with a root, define its k-th moment M k (T ) = (d T (u)) k du, T where the integration is over all edges of
Preliminaries and Complexity Theory
 Preliminaries and Complexity Theory Oleksandr Romanko CAS 746 - Advanced Topics in Combinatorial Optimization McMaster University, January 16, 2006 Introduction Book structure: 2 Part I Linear Algebra
Preliminaries and Complexity Theory Oleksandr Romanko CAS 746 - Advanced Topics in Combinatorial Optimization McMaster University, January 16, 2006 Introduction Book structure: 2 Part I Linear Algebra
The 2-valued case of makespan minimization with assignment constraints
 The 2-valued case of maespan minimization with assignment constraints Stavros G. Kolliopoulos Yannis Moysoglou Abstract We consider the following special case of minimizing maespan. A set of jobs J and
The 2-valued case of maespan minimization with assignment constraints Stavros G. Kolliopoulos Yannis Moysoglou Abstract We consider the following special case of minimizing maespan. A set of jobs J and
New Constructions for De Bruijn Tori
 New Constructions for De Bruijn Tori Glenn Hurlbert Garth Isaak Dedicated to the memory of Tony Brewster Abstract A De Bruijn torus is a periodic d dimensional k ary array such that each n 1 n d k ary
New Constructions for De Bruijn Tori Glenn Hurlbert Garth Isaak Dedicated to the memory of Tony Brewster Abstract A De Bruijn torus is a periodic d dimensional k ary array such that each n 1 n d k ary
Analogies and discrepancies between the vertex cover number and the weakly connected domination number of a graph
 Analogies and discrepancies between the vertex cover number and the weakly connected domination number of a graph M. Lemańska a, J. A. Rodríguez-Velázquez b, Rolando Trujillo-Rasua c, a Department of Technical
Analogies and discrepancies between the vertex cover number and the weakly connected domination number of a graph M. Lemańska a, J. A. Rodríguez-Velázquez b, Rolando Trujillo-Rasua c, a Department of Technical
QR FACTORIZATIONS USING A RESTRICTED SET OF ROTATIONS
 QR FACTORIZATIONS USING A RESTRICTED SET OF ROTATIONS DIANNE P. O LEARY AND STEPHEN S. BULLOCK Dedicated to Alan George on the occasion of his 60th birthday Abstract. Any matrix A of dimension m n (m n)
QR FACTORIZATIONS USING A RESTRICTED SET OF ROTATIONS DIANNE P. O LEARY AND STEPHEN S. BULLOCK Dedicated to Alan George on the occasion of his 60th birthday Abstract. Any matrix A of dimension m n (m n)
Impossibility Results for Weak Threshold Networks? a Department of Computer Science, Brown University, Providence, RI 02912
 Impossibility Results for Weak Threshold Networks? Costas Busch a 1 and Marios Mavronicolas b 2 a Department of Computer Science, Brown University, Providence, RI 02912 b Department of Computer Science,
Impossibility Results for Weak Threshold Networks? Costas Busch a 1 and Marios Mavronicolas b 2 a Department of Computer Science, Brown University, Providence, RI 02912 b Department of Computer Science,
Combining Shared Coin Algorithms
 Combining Shared Coin Algorithms James Aspnes Hagit Attiya Keren Censor Abstract This paper shows that shared coin algorithms can be combined to optimize several complexity measures, even in the presence
Combining Shared Coin Algorithms James Aspnes Hagit Attiya Keren Censor Abstract This paper shows that shared coin algorithms can be combined to optimize several complexity measures, even in the presence
Information-Theoretic Lower Bounds on the Storage Cost of Shared Memory Emulation
 Information-Theoretic Lower Bounds on the Storage Cost of Shared Memory Emulation Viveck R. Cadambe EE Department, Pennsylvania State University, University Park, PA, USA viveck@engr.psu.edu Nancy Lynch
Information-Theoretic Lower Bounds on the Storage Cost of Shared Memory Emulation Viveck R. Cadambe EE Department, Pennsylvania State University, University Park, PA, USA viveck@engr.psu.edu Nancy Lynch
Complexity Theory VU , SS The Polynomial Hierarchy. Reinhard Pichler
 Complexity Theory Complexity Theory VU 181.142, SS 2018 6. The Polynomial Hierarchy Reinhard Pichler Institut für Informationssysteme Arbeitsbereich DBAI Technische Universität Wien 15 May, 2018 Reinhard
Complexity Theory Complexity Theory VU 181.142, SS 2018 6. The Polynomial Hierarchy Reinhard Pichler Institut für Informationssysteme Arbeitsbereich DBAI Technische Universität Wien 15 May, 2018 Reinhard
Outline. Complexity Theory EXACT TSP. The Class DP. Definition. Problem EXACT TSP. Complexity of EXACT TSP. Proposition VU 181.
 Complexity Theory Complexity Theory Outline Complexity Theory VU 181.142, SS 2018 6. The Polynomial Hierarchy Reinhard Pichler Institut für Informationssysteme Arbeitsbereich DBAI Technische Universität
Complexity Theory Complexity Theory Outline Complexity Theory VU 181.142, SS 2018 6. The Polynomial Hierarchy Reinhard Pichler Institut für Informationssysteme Arbeitsbereich DBAI Technische Universität
An Improved Approximation Algorithm for Virtual Private Network Design
 An Improved Approximation Algorithm for Virtual Private Network Design Friedrich Eisenbrand Fabrizio Grandoni Abstract Virtual private network design deals with the reservation of capacities in a network,
An Improved Approximation Algorithm for Virtual Private Network Design Friedrich Eisenbrand Fabrizio Grandoni Abstract Virtual private network design deals with the reservation of capacities in a network,
Computer Science 385 Analysis of Algorithms Siena College Spring Topic Notes: Limitations of Algorithms
 Computer Science 385 Analysis of Algorithms Siena College Spring 2011 Topic Notes: Limitations of Algorithms We conclude with a discussion of the limitations of the power of algorithms. That is, what kinds
Computer Science 385 Analysis of Algorithms Siena College Spring 2011 Topic Notes: Limitations of Algorithms We conclude with a discussion of the limitations of the power of algorithms. That is, what kinds
Expressiveness of predicate logic: Some motivation
 Expressiveness of predicate logic: Some motivation In computer science the analysis of the expressiveness of predicate logic (a.k.a. first-order logic) is of particular importance, for instance In database
Expressiveness of predicate logic: Some motivation In computer science the analysis of the expressiveness of predicate logic (a.k.a. first-order logic) is of particular importance, for instance In database
5 + 9(10) + 3(100) + 0(1000) + 2(10000) =
 Chapter 5 Analyzing Algorithms So far we have been proving statements about databases, mathematics and arithmetic, or sequences of numbers. Though these types of statements are common in computer science,
Chapter 5 Analyzing Algorithms So far we have been proving statements about databases, mathematics and arithmetic, or sequences of numbers. Though these types of statements are common in computer science,
1 Algebraic Methods. 1.1 Gröbner Bases Applied to SAT
 1 Algebraic Methods In an algebraic system Boolean constraints are expressed as a system of algebraic equations or inequalities which has a solution if and only if the constraints are satisfiable. Equations
1 Algebraic Methods In an algebraic system Boolean constraints are expressed as a system of algebraic equations or inequalities which has a solution if and only if the constraints are satisfiable. Equations
Networks Cannot Compute Their Diameter in Sublinear Time
 Networks Cannot Compute Their Diameter in Sublinear Time Preliminary version, please check for updates Silvio Frischknecht Stephan Holzer Roger Wattenhofer {fsilvio, stholzer, wattenhofer}@ethzch Computer
Networks Cannot Compute Their Diameter in Sublinear Time Preliminary version, please check for updates Silvio Frischknecht Stephan Holzer Roger Wattenhofer {fsilvio, stholzer, wattenhofer}@ethzch Computer
HYPERCUBE ALGORITHMS FOR IMAGE PROCESSING AND PATTERN RECOGNITION SANJAY RANKA SARTAJ SAHNI Sanjay Ranka and Sartaj Sahni
 HYPERCUBE ALGORITHMS FOR IMAGE PROCESSING AND PATTERN RECOGNITION SANJAY RANKA SARTAJ SAHNI 1989 Sanjay Ranka and Sartaj Sahni 1 2 Chapter 1 Introduction 1.1 Parallel Architectures Parallel computers may
HYPERCUBE ALGORITHMS FOR IMAGE PROCESSING AND PATTERN RECOGNITION SANJAY RANKA SARTAJ SAHNI 1989 Sanjay Ranka and Sartaj Sahni 1 2 Chapter 1 Introduction 1.1 Parallel Architectures Parallel computers may
Remark 3.2. The cross product only makes sense in R 3.
 3. Cross product Definition 3.1. Let v and w be two vectors in R 3. The cross product of v and w, denoted v w, is the vector defined as follows: the length of v w is the area of the parallelogram with
3. Cross product Definition 3.1. Let v and w be two vectors in R 3. The cross product of v and w, denoted v w, is the vector defined as follows: the length of v w is the area of the parallelogram with
CS 70 Discrete Mathematics and Probability Theory Fall 2016 Seshia and Walrand Midterm 1 Solutions
 CS 70 Discrete Mathematics and Probability Theory Fall 2016 Seshia and Walrand Midterm 1 Solutions PRINT Your Name: Answer: Oski Bear SIGN Your Name: PRINT Your Student ID: CIRCLE your exam room: Dwinelle
CS 70 Discrete Mathematics and Probability Theory Fall 2016 Seshia and Walrand Midterm 1 Solutions PRINT Your Name: Answer: Oski Bear SIGN Your Name: PRINT Your Student ID: CIRCLE your exam room: Dwinelle
Locality Lower Bounds
 Chapter 8 Locality Lower Bounds In Chapter 1, we looked at distributed algorithms for coloring. In particular, we saw that rings and rooted trees can be colored with 3 colors in log n + O(1) rounds. 8.1
Chapter 8 Locality Lower Bounds In Chapter 1, we looked at distributed algorithms for coloring. In particular, we saw that rings and rooted trees can be colored with 3 colors in log n + O(1) rounds. 8.1
Failure detectors Introduction CHAPTER
 CHAPTER 15 Failure detectors 15.1 Introduction This chapter deals with the design of fault-tolerant distributed systems. It is widely known that the design and verification of fault-tolerent distributed
CHAPTER 15 Failure detectors 15.1 Introduction This chapter deals with the design of fault-tolerant distributed systems. It is widely known that the design and verification of fault-tolerent distributed
Parity Dominating Sets in Grid Graphs
 Parity Dominating Sets in Grid Graphs John L. Goldwasser and William F. Klostermeyer Dept. of Mathematics West Virginia University Morgantown, WV 26506 Dept. of Computer and Information Sciences University
Parity Dominating Sets in Grid Graphs John L. Goldwasser and William F. Klostermeyer Dept. of Mathematics West Virginia University Morgantown, WV 26506 Dept. of Computer and Information Sciences University
15.1 Matching, Components, and Edge cover (Collaborate with Xin Yu)
 15.1 Matching, Components, and Edge cover (Collaborate with Xin Yu) First show l = c by proving l c and c l. For a maximum matching M in G, let V be the set of vertices covered by M. Since any vertex in
15.1 Matching, Components, and Edge cover (Collaborate with Xin Yu) First show l = c by proving l c and c l. For a maximum matching M in G, let V be the set of vertices covered by M. Since any vertex in
Robust Network Codes for Unicast Connections: A Case Study
 Robust Network Codes for Unicast Connections: A Case Study Salim Y. El Rouayheb, Alex Sprintson, and Costas Georghiades Department of Electrical and Computer Engineering Texas A&M University College Station,
Robust Network Codes for Unicast Connections: A Case Study Salim Y. El Rouayheb, Alex Sprintson, and Costas Georghiades Department of Electrical and Computer Engineering Texas A&M University College Station,
MODEL ANSWERS TO THE SEVENTH HOMEWORK. (b) We proved in homework six, question 2 (c) that. But we also proved homework six, question 2 (a) that
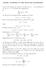 MODEL ANSWERS TO THE SEVENTH HOMEWORK 1. Let X be a finite set, and let A, B and A 1, A 2,..., A n be subsets of X. Let A c = X \ A denote the complement. (a) χ A (x) = A. x X (b) We proved in homework
MODEL ANSWERS TO THE SEVENTH HOMEWORK 1. Let X be a finite set, and let A, B and A 1, A 2,..., A n be subsets of X. Let A c = X \ A denote the complement. (a) χ A (x) = A. x X (b) We proved in homework
Computer Engineering Department, Ege University 35100, Bornova Izmir, Turkey
 Selçuk J. Appl. Math. Vol. 10. No. 1. pp. 107-10, 009 Selçuk Journal of Applied Mathematics Computing the Tenacity of Some Graphs Vecdi Aytaç Computer Engineering Department, Ege University 35100, Bornova
Selçuk J. Appl. Math. Vol. 10. No. 1. pp. 107-10, 009 Selçuk Journal of Applied Mathematics Computing the Tenacity of Some Graphs Vecdi Aytaç Computer Engineering Department, Ege University 35100, Bornova
How to deal with uncertainties and dynamicity?
 How to deal with uncertainties and dynamicity? http://graal.ens-lyon.fr/ lmarchal/scheduling/ 19 novembre 2012 1/ 37 Outline 1 Sensitivity and Robustness 2 Analyzing the sensitivity : the case of Backfilling
How to deal with uncertainties and dynamicity? http://graal.ens-lyon.fr/ lmarchal/scheduling/ 19 novembre 2012 1/ 37 Outline 1 Sensitivity and Robustness 2 Analyzing the sensitivity : the case of Backfilling
IP = PSPACE using Error Correcting Codes
 Electronic Colloquium on Computational Complexity, Report No. 137 (2010 IP = PSPACE using Error Correcting Codes Or Meir Abstract The IP theorem, which asserts that IP = PSPACE (Lund et. al., and Shamir,
Electronic Colloquium on Computational Complexity, Report No. 137 (2010 IP = PSPACE using Error Correcting Codes Or Meir Abstract The IP theorem, which asserts that IP = PSPACE (Lund et. al., and Shamir,
Lecture 3: graph theory
 CONTENTS 1 BASIC NOTIONS Lecture 3: graph theory Sonia Martínez October 15, 2014 Abstract The notion of graph is at the core of cooperative control. Essentially, it allows us to model the interaction topology
CONTENTS 1 BASIC NOTIONS Lecture 3: graph theory Sonia Martínez October 15, 2014 Abstract The notion of graph is at the core of cooperative control. Essentially, it allows us to model the interaction topology
Section 6 Fault-Tolerant Consensus
 Section 6 Fault-Tolerant Consensus CS586 - Panagiota Fatourou 1 Description of the Problem Consensus Each process starts with an individual input from a particular value set V. Processes may fail by crashing.
Section 6 Fault-Tolerant Consensus CS586 - Panagiota Fatourou 1 Description of the Problem Consensus Each process starts with an individual input from a particular value set V. Processes may fail by crashing.
c 1999 Society for Industrial and Applied Mathematics
 SIAM J. DISCRETE MATH. Vol. 1, No. 1, pp. 64 77 c 1999 Society for Industrial and Applied Mathematics OPTIMAL BOUNDS FOR MATCHING ROUTING ON TREES LOUXIN ZHANG Abstract. The permutation routing problem
SIAM J. DISCRETE MATH. Vol. 1, No. 1, pp. 64 77 c 1999 Society for Industrial and Applied Mathematics OPTIMAL BOUNDS FOR MATCHING ROUTING ON TREES LOUXIN ZHANG Abstract. The permutation routing problem
CHAPTER 8: EXPLORING R
 CHAPTER 8: EXPLORING R LECTURE NOTES FOR MATH 378 (CSUSM, SPRING 2009). WAYNE AITKEN In the previous chapter we discussed the need for a complete ordered field. The field Q is not complete, so we constructed
CHAPTER 8: EXPLORING R LECTURE NOTES FOR MATH 378 (CSUSM, SPRING 2009). WAYNE AITKEN In the previous chapter we discussed the need for a complete ordered field. The field Q is not complete, so we constructed
R ij = 2. Using all of these facts together, you can solve problem number 9.
 Help for Homework Problem #9 Let G(V,E) be any undirected graph We want to calculate the travel time across the graph. Think of each edge as one resistor of 1 Ohm. Say we have two nodes: i and j Let the
Help for Homework Problem #9 Let G(V,E) be any undirected graph We want to calculate the travel time across the graph. Think of each edge as one resistor of 1 Ohm. Say we have two nodes: i and j Let the
The structure of bull-free graphs II elementary trigraphs
 The structure of bull-free graphs II elementary trigraphs Maria Chudnovsky Columbia University, New York, NY 10027 USA May 6, 2006; revised April 25, 2011 Abstract The bull is a graph consisting of a triangle
The structure of bull-free graphs II elementary trigraphs Maria Chudnovsky Columbia University, New York, NY 10027 USA May 6, 2006; revised April 25, 2011 Abstract The bull is a graph consisting of a triangle
Orthogonal Arrays & Codes
 Orthogonal Arrays & Codes Orthogonal Arrays - Redux An orthogonal array of strength t, a t-(v,k,λ)-oa, is a λv t x k array of v symbols, such that in any t columns of the array every one of the possible
Orthogonal Arrays & Codes Orthogonal Arrays - Redux An orthogonal array of strength t, a t-(v,k,λ)-oa, is a λv t x k array of v symbols, such that in any t columns of the array every one of the possible
Data Gathering and Personalized Broadcasting in Radio Grids with Interferences
 Data Gathering and Personalized Broadcasting in Radio Grids with Interferences Jean-Claude Bermond a,, Bi Li a,b, Nicolas Nisse a, Hervé Rivano c, Min-Li Yu d a Coati Project, INRIA I3S(CNRS/UNSA), Sophia
Data Gathering and Personalized Broadcasting in Radio Grids with Interferences Jean-Claude Bermond a,, Bi Li a,b, Nicolas Nisse a, Hervé Rivano c, Min-Li Yu d a Coati Project, INRIA I3S(CNRS/UNSA), Sophia
On Embeddings of Hamiltonian Paths and Cycles in Extended Fibonacci Cubes
 American Journal of Applied Sciences 5(11): 1605-1610, 2008 ISSN 1546-9239 2008 Science Publications On Embeddings of Hamiltonian Paths and Cycles in Extended Fibonacci Cubes 1 Ioana Zelina, 2 Grigor Moldovan
American Journal of Applied Sciences 5(11): 1605-1610, 2008 ISSN 1546-9239 2008 Science Publications On Embeddings of Hamiltonian Paths and Cycles in Extended Fibonacci Cubes 1 Ioana Zelina, 2 Grigor Moldovan
Aditya Bhaskara CS 5968/6968, Lecture 1: Introduction and Review 12 January 2016
 Lecture 1: Introduction and Review We begin with a short introduction to the course, and logistics. We then survey some basics about approximation algorithms and probability. We also introduce some of
Lecture 1: Introduction and Review We begin with a short introduction to the course, and logistics. We then survey some basics about approximation algorithms and probability. We also introduce some of
Tight Bounds on the Diameter of Gaussian Cubes
 Tight Bounds on the Diameter of Gaussian Cubes DING-MING KWAI AND BEHROOZ PARHAMI Department of Electrical and Computer Engineering, University of California, Santa Barbara, CA 93106 9560, USA Email: parhami@ece.ucsb.edu
Tight Bounds on the Diameter of Gaussian Cubes DING-MING KWAI AND BEHROOZ PARHAMI Department of Electrical and Computer Engineering, University of California, Santa Barbara, CA 93106 9560, USA Email: parhami@ece.ucsb.edu
Consistent Global States of Distributed Systems: Fundamental Concepts and Mechanisms. CS 249 Project Fall 2005 Wing Wong
 Consistent Global States of Distributed Systems: Fundamental Concepts and Mechanisms CS 249 Project Fall 2005 Wing Wong Outline Introduction Asynchronous distributed systems, distributed computations,
Consistent Global States of Distributed Systems: Fundamental Concepts and Mechanisms CS 249 Project Fall 2005 Wing Wong Outline Introduction Asynchronous distributed systems, distributed computations,
Diagnosis of Repeated/Intermittent Failures in Discrete Event Systems
 Diagnosis of Repeated/Intermittent Failures in Discrete Event Systems Shengbing Jiang, Ratnesh Kumar, and Humberto E. Garcia Abstract We introduce the notion of repeated failure diagnosability for diagnosing
Diagnosis of Repeated/Intermittent Failures in Discrete Event Systems Shengbing Jiang, Ratnesh Kumar, and Humberto E. Garcia Abstract We introduce the notion of repeated failure diagnosability for diagnosing
Structuring Unreliable Radio Networks
 Structuring Unreliable Radio Networks Keren Censor-Hillel Seth Gilbert Fabian Kuhn Nancy Lynch Calvin Newport August 25, 2013 Abstract In this paper we study the problem of building a constant-degree connected
Structuring Unreliable Radio Networks Keren Censor-Hillel Seth Gilbert Fabian Kuhn Nancy Lynch Calvin Newport August 25, 2013 Abstract In this paper we study the problem of building a constant-degree connected
56 CHAPTER 3. POLYNOMIAL FUNCTIONS
 56 CHAPTER 3. POLYNOMIAL FUNCTIONS Chapter 4 Rational functions and inequalities 4.1 Rational functions Textbook section 4.7 4.1.1 Basic rational functions and asymptotes As a first step towards understanding
56 CHAPTER 3. POLYNOMIAL FUNCTIONS Chapter 4 Rational functions and inequalities 4.1 Rational functions Textbook section 4.7 4.1.1 Basic rational functions and asymptotes As a first step towards understanding
Embeddings of finite metric spaces in Euclidean space: a probabilistic view
 Embeddings of finite metric spaces in Euclidean space: a probabilistic view Yuval Peres May 11, 2006 Talk based on work joint with: Assaf Naor, Oded Schramm and Scott Sheffield Definition: An invertible
Embeddings of finite metric spaces in Euclidean space: a probabilistic view Yuval Peres May 11, 2006 Talk based on work joint with: Assaf Naor, Oded Schramm and Scott Sheffield Definition: An invertible
Partition is reducible to P2 C max. c. P2 Pj = 1, prec Cmax is solvable in polynomial time. P Pj = 1, prec Cmax is NP-hard
 I. Minimizing Cmax (Nonpreemptive) a. P2 C max is NP-hard. Partition is reducible to P2 C max b. P Pj = 1, intree Cmax P Pj = 1, outtree Cmax are both solvable in polynomial time. c. P2 Pj = 1, prec Cmax
I. Minimizing Cmax (Nonpreemptive) a. P2 C max is NP-hard. Partition is reducible to P2 C max b. P Pj = 1, intree Cmax P Pj = 1, outtree Cmax are both solvable in polynomial time. c. P2 Pj = 1, prec Cmax
