Stochastic Network Calculus
|
|
|
- Lynn Fisher
- 5 years ago
- Views:
Transcription
1 Stochastic Network Calculus Assessing the Performance of the Future Internet Markus Fidler joint work with Amr Rizk Institute of Communications Technology Leibniz Universität Hannover April 22, 2010 c Markus Fidler IKT LUH 1/27
2 Outline Motivation Traffic characteristics Related results Research goal FBm sample path envelope Definition of envelopes FBm envelopes Backlog bound End-to-end analysis Leftover service curves Network service curves Scaling properties c Markus Fidler IKT LUH 2/27
3 Internet applications by volume News 11% Telnet 14% HTTP 5% 8% FTP 20% 2008/09 HTTP 74% Video 31% P2P 44% Mix of heterogeneous traffic characteristics and service requirements c Markus Fidler IKT LUH 3/27
4 Network performance evaluation traffic matrix links, routers, topology, routing traffic statistics network calculus evaluate, plan, optimize, design HTTP 5% 8% traffic mix FTP 20% News 11% Telnet 14% application requirements quality of service delay packet loss throughput fairness c Markus Fidler IKT LUH 4/27
5 Queuing networks Queuing theory has been used since the 60 s to understand the performance of computer networks, most prominently to prove the efficiency of packet switching over circuit switching. A th 1 2 n... A cr,1 A cr,2 A cr,n c Markus Fidler IKT LUH 5/27
6 Queuing networks Queuing theory has been used since the 60 s to understand the performance of computer networks, most prominently to prove the efficiency of packet switching over circuit switching. A th 1 2 n... A cr,1 A cr,2 A cr,n c Markus Fidler IKT LUH 5/27
7 Queuing networks Queuing theory has been used since the 60 s to understand the performance of computer networks, most prominently to prove the efficiency of packet switching over circuit switching. A th 1 2 n... A cr,1 A cr,2 A cr,n Basic assumption: Memoryless arrivals and service requirements closed form results for single queues product forms for tandem queues simple results for multiplexing and de-multiplexing of traffic c Markus Fidler IKT LUH 5/27
8 Self-similarity Zooming in/out does repeatedly reveal the same basic structures. c Markus Fidler IKT LUH 6/27
9 Memoryless versus Internet traffic s aggregation s aggregation data [kbyte] 10 5 data [kbyte] time [s] time [s] statistical self-similarity of a random process X(t): z H X(t) d = X(zt) long-range dependence: Hurst parameter H (0.5, 1) auto-covariance v(t) at lag t: t=0 v(t) = c Markus Fidler IKT LUH 7/27
10 Memoryless versus Internet traffic s aggregation s aggregation data [kbyte] 40 data [kbyte] time [s] time [s] statistical self-similarity of a random process X(t): z H X(t) d = X(zt) long-range dependence: Hurst parameter H (0.5, 1) auto-covariance v(t) at lag t: t=0 v(t) = c Markus Fidler IKT LUH 7/27
11 Memoryless versus Internet traffic s aggregation s aggregation data [kbyte] data [kbyte] time [s] time [s] statistical self-similarity of a random process X(t): z H X(t) d = X(zt) long-range dependence: Hurst parameter H (0.5, 1) auto-covariance v(t) at lag t: t=0 v(t) = c Markus Fidler IKT LUH 7/27
12 Memoryless versus Internet traffic s aggregation s aggregation data [kbyte] data [kbyte] time [s] time [s] statistical self-similarity of a random process X(t): z H X(t) d = X(zt) long-range dependence: Hurst parameter H (0.5, 1) auto-covariance v(t) at lag t: t=0 v(t) = c Markus Fidler IKT LUH 7/27
13 Fractional Brownian motion Fractional Brownian motion (fbm) is a model for self-similar traffic with long memory. FBm arrivals A(t) are composed of a mean rate λ and a correlated Gaussian increment process Z(t) with zero mean A(t) = λt + Z(t). The increment process is fully characterized by two parameters variance σ 2 Hurst parameter H c Markus Fidler IKT LUH 8/27
14 Fractional Brownian motion Fractional Brownian motion (fbm) is a model for self-similar traffic with long memory. FBm arrivals A(t) are composed of a mean rate λ and a correlated Gaussian increment process Z(t) with zero mean A(t) = λt + Z(t). The increment process is fully characterized by two parameters variance σ 2 Hurst parameter H FBm traffic has effective bandwidth α(θ, t) = 1 θt log E[eθA(t) ] = λ + θσ2 2 t2h 1 α lies between the mean rate and peak rate and characterizes the resource requirements of a flow. Note the continuous growth with t. c Markus Fidler IKT LUH 8/27
15 Lindley s recursion Model of a buffered work-conserving link with capacity C A(t), D(t) cumulative arrivals, resp., departures in [0, t) B(t) = A(t) D(t) backlog, i.e. unfinished work, at time t A(t) C D(t) Lindley equation B(t) B(t + 1) = max{0, B(t) + A(t, t + 1) C} By induction with B(0) = 0 B(t) = max {A(τ, t) C(t τ)} τ [0,t] c Markus Fidler IKT LUH 9/27
16 Largest term approximation Lindley s recursion for the backlog B(t) at a system with capacity C B(t) = sup {A(τ, t) C(t τ)}. τ [0,t] permits a stochastic formulation of a backlog bound b [ ] P[B > b] = P sup {A(τ, t) C(t τ)} > b τ [0,t]. c Markus Fidler IKT LUH 10/27
17 Largest term approximation Lindley s recursion for the backlog B(t) at a system with capacity C B(t) = sup {A(τ, t) C(t τ)}. τ [0,t] permits a stochastic formulation of a backlog bound b [ ] P[B > b] = P sup {A(τ, t) C(t τ)} > b τ [0,t]. For fbm arrivals known backlog bounds are derived from an approximation by the largest term { } P[B > b] sup P [A(τ, t) C(t τ) > b] τ [0,t] that strictly provides, however, only a lower bound. c Markus Fidler IKT LUH 10/27
18 Performance bounds for fbm traffic The fundamental finding is the asymptotic resp. approximate result ( lim P[B > b] = exp 1 ( ) C λ 2H ( ) ) b 2 2H b 2σ 2 = ε a H 1 H that has been derived from the Gaussian increments [Norros, 94] large deviations theory [Duffield, O Connell, 95] statistical envelopes [Fonseca, Mayor, Neto, 00]. c Markus Fidler IKT LUH 11/27
19 Performance bounds for fbm traffic The fundamental finding is the asymptotic resp. approximate result ( lim P[B > b] = exp 1 ( ) C λ 2H ( ) ) b 2 2H b 2σ 2 = ε a H 1 H that has been derived from the Gaussian increments [Norros, 94] large deviations theory [Duffield, O Connell, 95] statistical envelopes [Fonseca, Mayor, Neto, 00]. It provides clear rules for dimensioning, e.g. regarding packet loss is it better to double the buffer size b or is it better to double the unused capacity C λ? The result is, however, limited to through traffic at a single system. c Markus Fidler IKT LUH 11/27
20 Networks under fbm cross-traffic The goal of this work is to provide end-to-end performance bounds for a through flow in a network under fbm cross-traffic. A th 1 2 n... A cr,1 A cr,2 A cr,n We seek to answer: Given the delay of a through flow at single system is w. What is the end-to-end delay for n tandem systems? c Markus Fidler IKT LUH 12/27
21 Networks under fbm cross-traffic The goal of this work is to provide end-to-end performance bounds for a through flow in a network under fbm cross-traffic. A th 1 2 n... A cr,1 A cr,2 A cr,n We seek to answer: Given the delay of a through flow at single system is w. What is the end-to-end delay for n tandem systems? To this end, we use the framework of stochastic network calculus. Essential intermediate steps are an envelope for fbm sample paths a leftover service curve for systems under fbm cross-traffic a convolution form for service curves of tandem systems c Markus Fidler IKT LUH 12/27
22 Table of contents Motivation Traffic characteristics Related results Research goal FBm sample path envelope Definition of envelopes FBm envelopes Backlog bound End-to-end analysis Leftover service curves Network service curves Scaling properties c Markus Fidler IKT LUH 13/27
23 Point-wise versus sample path envelopes data envelopes sample paths time [from Liebeherr, statcalc talk, 05] the point-wise envelope is violated at most with probability 1/4 at any point in time c Markus Fidler IKT LUH 14/27
24 Point-wise versus sample path envelopes data envelopes sample paths time [from Liebeherr, statcalc talk, 05] the point-wise envelope is violated at most with probability 1/4 at any point in time the sample path envelope is violated at most by a share of 1/4 of the sample paths c Markus Fidler IKT LUH 14/27
25 Construction of sample path envelopes A point-wise definition of stochastic envelope E(t) is P[A(τ, t) E(t τ) > 0] ε p for any τ [0, t] as opposed to the sample path definition P[ τ [0, t] : A(τ, t) E(t τ) > 0] ε s c Markus Fidler IKT LUH 15/27
26 Construction of sample path envelopes A point-wise definition of stochastic envelope E(t) is P[A(τ, t) E(t τ) > 0] ε p for any τ [0, t] as opposed to the sample path definition P[ τ [0, t] : A(τ, t) E(t τ) > 0] ε s that is equivalent to the backlog-like form (E(t) = b + Ct) [ ] P sup {A(τ, t) E(t τ)} > 0 τ [0,t] ε s c Markus Fidler IKT LUH 15/27
27 Construction of sample path envelopes A point-wise definition of stochastic envelope E(t) is P[A(τ, t) E(t τ) > 0] ε p for any τ [0, t] as opposed to the sample path definition P[ τ [0, t] : A(τ, t) E(t τ) > 0] ε s that is equivalent to the backlog-like form (E(t) = b + Ct) [ ] P sup {A(τ, t) E(t τ)} > 0 τ [0,t] ε s For a set of supporting points the union bound yields [ t ] t P {A(τ, t) E(t τ) > 0} ε p. τ=0 For t the difficulty is to select ε p such that its sum is bounded. τ=0 c Markus Fidler IKT LUH 15/27
28 Construction of fbm envelopes With Chernoff s bound an envelope with point-wise violation probability ε p (t) follows from the effective bandwidth of fbm traffic. The optimal solution is E(t) = λt + 2 log ε p (t)σt H. c Markus Fidler IKT LUH 16/27
29 Construction of fbm envelopes With Chernoff s bound an envelope with point-wise violation probability ε p (t) follows from the effective bandwidth of fbm traffic. The optimal solution is E(t) = λt + 2 log ε p (t)σt H. To derive a sample path envelope we have to select ε p (t) such that it has a finite sum. We choose resulting in ε p (t) = η t2β E(t) = λt + 2 log ησt H+β. Selecting β (0, 1 H) ensures a linear growth of E(t) in t. c Markus Fidler IKT LUH 16/27
30 Example fbm envelopes β = 0.12 the parameter β relaxes the envelope E(t) [Mb] β = t [ms] ε p (t) β = 0 β = 0.04 β = 0.08 β = t [ms] the point-wise violation probability decays with t the decay is, however, slower than exponential c Markus Fidler IKT LUH 17/27
31 Sample path violation probability Summing the point-wise violation probability ε p (t) = η t2β for all t [0, ) the envelope is violated by sample paths at most with ε s = Γ( 1 2β ) 2β( log η) 1 2β. c Markus Fidler IKT LUH 18/27
32 Sample path violation probability Summing the point-wise violation probability ε p (t) = η t2β for all t [0, ) the envelope is violated by sample paths at most with ε s = Γ( 1 2β ) 2β( log η) 1 2β We optimize the parameters η and β to find a closed form backlog bound from the envelope: the optimal η follows by fitting E(t) below b + Ct when deriving the backlog bound b at a server with capacity C a near optimal β is derived using Stirling s approximation of the Gamma function Γ(x) 2π/x (x/e) x for x 1 After some algebra we express the sample path violation probability ε s as a multiple of the known approximation ε a. This supports earlier conclusions from ε a by a rigorous sample path argument.. c Markus Fidler IKT LUH 18/27
33 Tail decay of backlog bounds ε fbm H=0.8 H= T=0.2 EBB T=0.4 T=0.6 H= b [kb] the EBB model includes all traffic types that have exponentially bounded burstiness, e.g. Markov on-off traffic the decay of tail probabilities for fbm traffic log ε b 2 2H is much slower Weibull-type making buffering less effective ms c Markus Fidler IKT LUH 19/27
34 Table of contents Motivation Traffic characteristics Related results Research goal FBm sample path envelope Definition of envelopes FBm envelopes Backlog bound End-to-end analysis Leftover service curves Network service curves Scaling properties c Markus Fidler IKT LUH 20/27
35 Leftover stochastic service curve Stochastic service curves make service guarantees subject to a violation probability ε [Cruz, 96] [ P D(t) < inf {A(τ) + S(t τ)} τ [0,t] ] ε. inf τ {A(τ) + S(t τ)} =: A S(t) is known as min-plus convolution. c Markus Fidler IKT LUH 21/27
36 Leftover stochastic service curve Stochastic service curves make service guarantees subject to a violation probability ε [Cruz, 96] [ P D(t) < inf {A(τ) + S(t τ)} τ [0,t] ] ε. inf τ {A(τ) + S(t τ)} =: A S(t) is known as min-plus convolution. A th C D th A cr D cr Given cross-traffic with sample path envelope E cr (t) at a server with capacity C. A leftover service curve for the through traffic is S th (t) = max{0, Ct E cr (t)}. c Markus Fidler IKT LUH 21/27
37 End-to-end convolution of service curves A th 1 2 n... A cr,1 A cr,2 A cr,n A network service curve can be derived by recursive insertion of the definition of service curve. In case of deterministic service curves D n = A n S n = D n 1 S n = A n 1 S n 1 S n = = A 1 n i=1s i c Markus Fidler IKT LUH 22/27
38 End-to-end convolution of service curves A th 1 2 n... A cr,1 A cr,2 A cr,n A network service curve can be derived by recursive insertion of the definition of service curve. In case of deterministic service curves D n = A n S n = D n 1 S n = A n 1 S n 1 S n = = A 1 n i=1s i A simple recursive insertion of stochastic service curves [ ] P D(t) < inf {A(τ) + S(t τ) b} ε(b). τ [0,t] is, however, not possible since the definition requires sample path arguments for the arrivals A(t) makes only point-wise statements for the departures D(t) c Markus Fidler IKT LUH 22/27
39 Construction of sample path service curves The construction of stochastic service curves that provide sample path guarantees for the departures has been open for a while. The method [Ciucu, Burchard, Liebeherr, 05] resorts to the union bound introduces a slack rate and thus achieves integrable violation probabilities We provide a solution for end-to-end leftover service curves under fbm cross-traffic and optimize its parameters as before. c Markus Fidler IKT LUH 23/27
40 Scaling of end-to-end delays w/n [ms] EBB T cr =0.6 ms T cr =0.4 ms T cr =0.2 ms fbm H cr =0.8 H cr =0.75 H cr = n Performance bounds for networks under fbm cross-traffic grow as O ( 1 ) n(log n) 2 2H for n tandem systems. For H = 0.5 the EBB result O(n log n) [Ciucu, Burchard, Liebeherr, 05] is recovered. c Markus Fidler IKT LUH 24/27
41 Impact of spare capacity on end-to-end delays w [ms] H cr = 0.8 H cr = 0.75 H cr = 0.7 H cr = mean spare capacity [Mb/s] Under LRD spare capacity is essential for network performance, e.g. for H cr = 0.75 (0.5) halving the spare capacity increases the delay bound tenfold (twofold). c Markus Fidler IKT LUH 25/27
42 Conclusions We contributed a sample path envelope for fbm traffic that complements and agrees with previous approximate results a sample path leftover service curve for systems under fbm cross-traffic to derive performance bounds for networks under fbm cross-traffic. We showed that end-to-end bounds under fbm cross-traffic grow as O ( 1 ) n(log n) 2 2H. Our result complements O(n) for deterministic traffic [LeBoudec, Thiran, 01] Θ(n log n) for EBB traffic [Ciucu, Burchard, Liebeherr, 05] O(n) for statistically independent EBB traffic [Fidler, 06] c Markus Fidler IKT LUH 26/27
43 References Amr Rizk, Markus Fidler: End-to-end Performance Bounds for Networks under Long-memory fbm Cross-traffic, September Amr Rizk, Markus Fidler: Sample Path Bounds for Long-memory fbm Traffic, Proc. of IEEE INFOCOM MC, March Amr Rizk, Markus Fidler: End-to-end Performance Bounds for Networks under Long-memory fbm Cross-traffic, Proc. of IEEE IWQoS, June c Markus Fidler IKT LUH 27/27
Delay Bounds in Communication Networks with Heavy-Tailed and Self-Similar Traffic
 Delay Bounds in Communication Networks with Heavy-Tailed and Self-Similar Traffic Jörg Liebeherr, Almut Burchard, Florin Ciucu 1 Abstract Traffic with self-similar and heavy-tailed characteristics has
Delay Bounds in Communication Networks with Heavy-Tailed and Self-Similar Traffic Jörg Liebeherr, Almut Burchard, Florin Ciucu 1 Abstract Traffic with self-similar and heavy-tailed characteristics has
Delay Bounds for Networks with Heavy-Tailed and Self-Similar Traffic
 Delay Bounds for Networks with Heavy-Tailed and Self-Similar Traffic Jörg Liebeherr, Almut Burchard, Florin Ciucu Abstract 1 arxiv:0911.3856v1 [cs.ni] 19 Nov 2009 We provide upper bounds on the end-to-end
Delay Bounds for Networks with Heavy-Tailed and Self-Similar Traffic Jörg Liebeherr, Almut Burchard, Florin Ciucu Abstract 1 arxiv:0911.3856v1 [cs.ni] 19 Nov 2009 We provide upper bounds on the end-to-end
A Network Calculus with Effective Bandwidth
 A Network Calculus with Effective Bandwidth Technical Report: University of Virginia, CS-2003-20, November 2003 Chengzhi Li Almut Burchard Jörg Liebeherr Department of Computer Science Department of Mathematics
A Network Calculus with Effective Bandwidth Technical Report: University of Virginia, CS-2003-20, November 2003 Chengzhi Li Almut Burchard Jörg Liebeherr Department of Computer Science Department of Mathematics
Window Flow Control Systems with Random Service
 Window Flow Control Systems with Random Service Alireza Shekaramiz Joint work with Prof. Jörg Liebeherr and Prof. Almut Burchard April 6, 2016 1 / 20 Content 1 Introduction 2 Related work 3 State-of-the-art
Window Flow Control Systems with Random Service Alireza Shekaramiz Joint work with Prof. Jörg Liebeherr and Prof. Almut Burchard April 6, 2016 1 / 20 Content 1 Introduction 2 Related work 3 State-of-the-art
Amr Rizk TU Darmstadt
 Saving Resources on Wireless Uplinks: Models of Queue-aware Scheduling 1 Amr Rizk TU Darmstadt - joint work with Markus Fidler 6. April 2016 KOM TUD Amr Rizk 1 Cellular Uplink Scheduling freq. time 6.
Saving Resources on Wireless Uplinks: Models of Queue-aware Scheduling 1 Amr Rizk TU Darmstadt - joint work with Markus Fidler 6. April 2016 KOM TUD Amr Rizk 1 Cellular Uplink Scheduling freq. time 6.
Scaling Properties in the Stochastic Network Calculus
 Scaling Properties in the Stochastic Network Calculus A Dissertation Presented to the faculty of the School of Engineering and Applied Science University of Virginia In Partial Fulfillment of the requirements
Scaling Properties in the Stochastic Network Calculus A Dissertation Presented to the faculty of the School of Engineering and Applied Science University of Virginia In Partial Fulfillment of the requirements
Recent Progress on a Statistical Network Calculus
 Recent Progress on a Statistical Network Calculus Jorg Liebeherr Deartment of Comuter Science University of Virginia Collaborators Almut Burchard Robert Boorstyn Chaiwat Oottamakorn Stehen Patek Chengzhi
Recent Progress on a Statistical Network Calculus Jorg Liebeherr Deartment of Comuter Science University of Virginia Collaborators Almut Burchard Robert Boorstyn Chaiwat Oottamakorn Stehen Patek Chengzhi
On the Impact of Link Scheduling on End-to-End Delays in Large Networks
 1 On the Impact of Link Scheduling on End-to-End Delays in Large Networks Jörg Liebeherr, Yashar Ghiassi-Farrokhfal, Almut Burchard Abstract We seek to provide an analytical answer whether the impact of
1 On the Impact of Link Scheduling on End-to-End Delays in Large Networks Jörg Liebeherr, Yashar Ghiassi-Farrokhfal, Almut Burchard Abstract We seek to provide an analytical answer whether the impact of
Design of IP networks with Quality of Service
 Course of Multimedia Internet (Sub-course Reti Internet Multimediali ), AA 2010-2011 Prof. Pag. 1 Design of IP networks with Quality of Service 1 Course of Multimedia Internet (Sub-course Reti Internet
Course of Multimedia Internet (Sub-course Reti Internet Multimediali ), AA 2010-2011 Prof. Pag. 1 Design of IP networks with Quality of Service 1 Course of Multimedia Internet (Sub-course Reti Internet
A Network Calculus with Effective Bandwidth
 A Network Calculus with Effective Bandwidth Chengzhi Li, Almut Burchard, Jörg Liebeherr Abstract This paper establishes a link between two principal tools for the analysis of network traffic, namely, effective
A Network Calculus with Effective Bandwidth Chengzhi Li, Almut Burchard, Jörg Liebeherr Abstract This paper establishes a link between two principal tools for the analysis of network traffic, namely, effective
Effect of the Traffic Bursts in the Network Queue
 RICE UNIVERSITY Effect of the Traffic Bursts in the Network Queue by Alireza KeshavarzHaddad A Thesis Submitted in Partial Fulfillment of the Requirements for the Degree Master of Science Approved, Thesis
RICE UNIVERSITY Effect of the Traffic Bursts in the Network Queue by Alireza KeshavarzHaddad A Thesis Submitted in Partial Fulfillment of the Requirements for the Degree Master of Science Approved, Thesis
Network Calculus Analysis of Feedback Systems with Random Service. Alireza Shekaramiz
 Network Calculus Analysis of Feedback Systems with Random Service by Alireza Shekaramiz A thesis submitted in conformity with the requirements for the degree of Master of Applied Science Graduate Department
Network Calculus Analysis of Feedback Systems with Random Service by Alireza Shekaramiz A thesis submitted in conformity with the requirements for the degree of Master of Applied Science Graduate Department
CONVERGENCE TO FRACTIONAL BROWNIAN MOTION AND LOSS PROBABILITY. Jin-Chun Kim and Hee-Choon Lee
 Kangweon-Kyungki Math. Jour. (2003), No., pp. 35 43 CONVERGENCE TO FRACTIONAL BROWNIAN MOTION AND LOSS PROBABILITY Jin-Chun Kim and Hee-Choon Lee Abstract. We study the weak convergence to Fractional Brownian
Kangweon-Kyungki Math. Jour. (2003), No., pp. 35 43 CONVERGENCE TO FRACTIONAL BROWNIAN MOTION AND LOSS PROBABILITY Jin-Chun Kim and Hee-Choon Lee Abstract. We study the weak convergence to Fractional Brownian
A Measurement-Analytic Approach for QoS Estimation in a Network Based on the Dominant Time Scale
 222 IEEE/ACM TRANSACTIONS ON NETWORKING, VOL. 11, NO. 2, APRIL 2003 A Measurement-Analytic Approach for QoS Estimation in a Network Based on the Dominant Time Scale Do Young Eun and Ness B. Shroff, Senior
222 IEEE/ACM TRANSACTIONS ON NETWORKING, VOL. 11, NO. 2, APRIL 2003 A Measurement-Analytic Approach for QoS Estimation in a Network Based on the Dominant Time Scale Do Young Eun and Ness B. Shroff, Senior
A Calculus for End-to-end Statistical Service Guarantees
 A Calculus for End-to-end Statistical Service Guarantees Almut Burchard y Jörg Liebeherr Stephen Patek y Department of Mathematics Department of Computer Science Department of Systems and Information Engineering
A Calculus for End-to-end Statistical Service Guarantees Almut Burchard y Jörg Liebeherr Stephen Patek y Department of Mathematics Department of Computer Science Department of Systems and Information Engineering
Resource Allocation for Video Streaming in Wireless Environment
 Resource Allocation for Video Streaming in Wireless Environment Shahrokh Valaee and Jean-Charles Gregoire Abstract This paper focuses on the development of a new resource allocation scheme for video streaming
Resource Allocation for Video Streaming in Wireless Environment Shahrokh Valaee and Jean-Charles Gregoire Abstract This paper focuses on the development of a new resource allocation scheme for video streaming
A Network Calculus Approach for the Analysis of Multi-Hop Fading Channels
 A Network Calculus Approach for the Analysis of Multi-Hop Fading Channels Hussein Al-Zubaidy*, Jörg Liebeherr*, Almut Burchard** * Department of ECE, University of Toronto, Canada. ** Department of Mathematics,
A Network Calculus Approach for the Analysis of Multi-Hop Fading Channels Hussein Al-Zubaidy*, Jörg Liebeherr*, Almut Burchard** * Department of ECE, University of Toronto, Canada. ** Department of Mathematics,
Network-Layer Performance Analysis of Multi-Hop Fading Channels
 Network-Layer Performance Analysis of Multi-Hop Fading Channels Hussein Al-Zubaidy, Jörg Liebeherr, Almut Burchard Abstract A fundamental problem for the delay and backlog analysis across multi-hop paths
Network-Layer Performance Analysis of Multi-Hop Fading Channels Hussein Al-Zubaidy, Jörg Liebeherr, Almut Burchard Abstract A fundamental problem for the delay and backlog analysis across multi-hop paths
Statistical Per-Flow Service Bounds in a Network with Aggregate Provisioning
 Statistical Per-Flow Service Bounds in a Network with Aggregate Provisioning Technical Report: University of Virginia, S-2002-27 Jörg Liebeherr Stephen Patek Almut Burchard y y Department of Mathematics
Statistical Per-Flow Service Bounds in a Network with Aggregate Provisioning Technical Report: University of Virginia, S-2002-27 Jörg Liebeherr Stephen Patek Almut Burchard y y Department of Mathematics
The Burstiness Behavior of Regulated Flows in Networks
 The Burstiness Behavior of Regulated Flows in Networks Yu Ying 1, Ravi Mazumdar 2, Catherine Rosenberg 2 and Fabrice Guillemin 3 1 Dept. of ECE, Purdue University, West Lafayette, IN, 47906, U.S.A. yingy@ecn.purdue.edu
The Burstiness Behavior of Regulated Flows in Networks Yu Ying 1, Ravi Mazumdar 2, Catherine Rosenberg 2 and Fabrice Guillemin 3 1 Dept. of ECE, Purdue University, West Lafayette, IN, 47906, U.S.A. yingy@ecn.purdue.edu
M/G/FQ: STOCHASTIC ANALYSIS OF FAIR QUEUEING SYSTEMS
 M/G/FQ: STOCHASTIC ANALYSIS OF FAIR QUEUEING SYSTEMS MOHAMMED HAWA AND DAVID W. PETR Information and Telecommunications Technology Center University of Kansas, Lawrence, Kansas, 66045 email: {hawa, dwp}@ittc.ku.edu
M/G/FQ: STOCHASTIC ANALYSIS OF FAIR QUEUEING SYSTEMS MOHAMMED HAWA AND DAVID W. PETR Information and Telecommunications Technology Center University of Kansas, Lawrence, Kansas, 66045 email: {hawa, dwp}@ittc.ku.edu
Network management and QoS provisioning - Network Calculus
 Network Calculus Network calculus is a metodology to study in a deterministic approach theory of queues. First a linear modelization is needed: it means that, for example, a system like: ρ can be modelized
Network Calculus Network calculus is a metodology to study in a deterministic approach theory of queues. First a linear modelization is needed: it means that, for example, a system like: ρ can be modelized
A Network Service Curve Approach for the Stochastic Analysis of Networks
 A Network Service Curve Approach for the Stochastic Analysis of Networks Florin Ciucu Dept of Computer Science University of Virginia Charlottesville, VA 94 florin@csvirginiaedu Almut Burchard Department
A Network Service Curve Approach for the Stochastic Analysis of Networks Florin Ciucu Dept of Computer Science University of Virginia Charlottesville, VA 94 florin@csvirginiaedu Almut Burchard Department
Queue Analysis for Wireless Packet Data Traffic
 Queue Analysis for Wireless Packet Data Traffic Shahram Teymori and Weihua Zhuang Centre for Wireless Communications (CWC), Department of Electrical and Computer Engineering, University of Waterloo, Waterloo,
Queue Analysis for Wireless Packet Data Traffic Shahram Teymori and Weihua Zhuang Centre for Wireless Communications (CWC), Department of Electrical and Computer Engineering, University of Waterloo, Waterloo,
Statistical Per-Flow Service Bounds in a Network with Aggregate Provisioning
 1 Statistical Per-Flow Service Bounds in a Network with Aggregate Provisioning Jörg Liebeherr, Department of omputer Science, University of Virginia Stephen D. Patek, Department of Systems and Information
1 Statistical Per-Flow Service Bounds in a Network with Aggregate Provisioning Jörg Liebeherr, Department of omputer Science, University of Virginia Stephen D. Patek, Department of Systems and Information
Network Traffic Characteristic
 Network Traffic Characteristic Hojun Lee hlee02@purros.poly.edu 5/24/2002 EL938-Project 1 Outline Motivation What is self-similarity? Behavior of Ethernet traffic Behavior of WAN traffic Behavior of WWW
Network Traffic Characteristic Hojun Lee hlee02@purros.poly.edu 5/24/2002 EL938-Project 1 Outline Motivation What is self-similarity? Behavior of Ethernet traffic Behavior of WAN traffic Behavior of WWW
ORIGINATING from the seminal works by Shannon in
 1280 IEEE TRANSACTIONS ON WIRELESS COMMUNICATIONS, VOL. 14, NO. 3, MARCH 2015 Capacity Delay Error Boundaries: A Composable Model of Sources and Systems Markus Fidler, Senior Member, IEEE, Ralf Lübben,
1280 IEEE TRANSACTIONS ON WIRELESS COMMUNICATIONS, VOL. 14, NO. 3, MARCH 2015 Capacity Delay Error Boundaries: A Composable Model of Sources and Systems Markus Fidler, Senior Member, IEEE, Ralf Lübben,
Capturing Network Traffic Dynamics Small Scales. Rolf Riedi
 Capturing Network Traffic Dynamics Small Scales Rolf Riedi Dept of Statistics Stochastic Systems and Modelling in Networking and Finance Part II Dependable Adaptive Systems and Mathematical Modeling Kaiserslautern,
Capturing Network Traffic Dynamics Small Scales Rolf Riedi Dept of Statistics Stochastic Systems and Modelling in Networking and Finance Part II Dependable Adaptive Systems and Mathematical Modeling Kaiserslautern,
Different Scenarios of Concatenation at Aggregate Scheduling of Multiple Nodes
 ICNS 03 : The Ninth International Conference on Networking and Services Different Scenarios of Concatenation at Aggregate Scheduling of Multiple Nodes Ulrich Klehmet Kai-Steffen Hielscher Computer Networks
ICNS 03 : The Ninth International Conference on Networking and Services Different Scenarios of Concatenation at Aggregate Scheduling of Multiple Nodes Ulrich Klehmet Kai-Steffen Hielscher Computer Networks
NICTA Short Course. Network Analysis. Vijay Sivaraman. Day 1 Queueing Systems and Markov Chains. Network Analysis, 2008s2 1-1
 NICTA Short Course Network Analysis Vijay Sivaraman Day 1 Queueing Systems and Markov Chains Network Analysis, 2008s2 1-1 Outline Why a short course on mathematical analysis? Limited current course offering
NICTA Short Course Network Analysis Vijay Sivaraman Day 1 Queueing Systems and Markov Chains Network Analysis, 2008s2 1-1 Outline Why a short course on mathematical analysis? Limited current course offering
Sample path large deviations of a Gaussian process with stationary increments and regularily varying variance
 Sample path large deviations of a Gaussian process with stationary increments and regularily varying variance Tommi Sottinen Department of Mathematics P. O. Box 4 FIN-0004 University of Helsinki Finland
Sample path large deviations of a Gaussian process with stationary increments and regularily varying variance Tommi Sottinen Department of Mathematics P. O. Box 4 FIN-0004 University of Helsinki Finland
MASSACHUSETTS INSTITUTE OF TECHNOLOGY 6.265/15.070J Fall 2013 Lecture 22 12/09/2013. Skorokhod Mapping Theorem. Reflected Brownian Motion
 MASSACHUSETTS INSTITUTE OF TECHNOLOGY 6.265/15.7J Fall 213 Lecture 22 12/9/213 Skorokhod Mapping Theorem. Reflected Brownian Motion Content. 1. G/G/1 queueing system 2. One dimensional reflection mapping
MASSACHUSETTS INSTITUTE OF TECHNOLOGY 6.265/15.7J Fall 213 Lecture 22 12/9/213 Skorokhod Mapping Theorem. Reflected Brownian Motion Content. 1. G/G/1 queueing system 2. One dimensional reflection mapping
On the Delay Performance of Interference Channels
 On the Delay Performance of Interference Channels Sebastian Schiessl, Farshad Naghibi, Hussein Al-Zubaidy, Markus Fidler, James Gross School of Electrical Engineering, KTH Royal Institute of Technology,
On the Delay Performance of Interference Channels Sebastian Schiessl, Farshad Naghibi, Hussein Al-Zubaidy, Markus Fidler, James Gross School of Electrical Engineering, KTH Royal Institute of Technology,
Window Flow Control Systems with Random Service
 Window Flow Control Systems with Random Service Alireza Shekaramiz*, Jörg Liebeherr*, Almut Burchard** arxiv:1507.04631v1 [cs.pf] 16 Jul 2015 * Department of ECE, University of Toronto, Canada. ** Department
Window Flow Control Systems with Random Service Alireza Shekaramiz*, Jörg Liebeherr*, Almut Burchard** arxiv:1507.04631v1 [cs.pf] 16 Jul 2015 * Department of ECE, University of Toronto, Canada. ** Department
Efficient Network-wide Available Bandwidth Estimation through Active Learning and Belief Propagation
 Efficient Network-wide Available Bandwidth Estimation through Active Learning and Belief Propagation mark.coates@mcgill.ca McGill University Department of Electrical and Computer Engineering Montreal,
Efficient Network-wide Available Bandwidth Estimation through Active Learning and Belief Propagation mark.coates@mcgill.ca McGill University Department of Electrical and Computer Engineering Montreal,
Performance Evaluation of Queuing Systems
 Performance Evaluation of Queuing Systems Introduction to Queuing Systems System Performance Measures & Little s Law Equilibrium Solution of Birth-Death Processes Analysis of Single-Station Queuing Systems
Performance Evaluation of Queuing Systems Introduction to Queuing Systems System Performance Measures & Little s Law Equilibrium Solution of Birth-Death Processes Analysis of Single-Station Queuing Systems
Stochastic Optimization for Undergraduate Computer Science Students
 Stochastic Optimization for Undergraduate Computer Science Students Professor Joongheon Kim School of Computer Science and Engineering, Chung-Ang University, Seoul, Republic of Korea 1 Reference 2 Outline
Stochastic Optimization for Undergraduate Computer Science Students Professor Joongheon Kim School of Computer Science and Engineering, Chung-Ang University, Seoul, Republic of Korea 1 Reference 2 Outline
Sharp Per-Flow Delay Bounds for Bursty Arrivals: The Case of FIFO, SP, and EDF Scheduling
 Sharp Per-Flow Delay Bounds for Bursty Arrivals: The Case of FIFO, SP, and EDF Scheduling Florin Ciucu University of Warwick Felix Poloczek University of Warwick / TU Berlin Jens Schmitt University of
Sharp Per-Flow Delay Bounds for Bursty Arrivals: The Case of FIFO, SP, and EDF Scheduling Florin Ciucu University of Warwick Felix Poloczek University of Warwick / TU Berlin Jens Schmitt University of
Dynamic Power Allocation and Routing for Time Varying Wireless Networks
 Dynamic Power Allocation and Routing for Time Varying Wireless Networks X 14 (t) X 12 (t) 1 3 4 k a P ak () t P a tot X 21 (t) 2 N X 2N (t) X N4 (t) µ ab () rate µ ab µ ab (p, S 3 ) µ ab µ ac () µ ab (p,
Dynamic Power Allocation and Routing for Time Varying Wireless Networks X 14 (t) X 12 (t) 1 3 4 k a P ak () t P a tot X 21 (t) 2 N X 2N (t) X N4 (t) µ ab () rate µ ab µ ab (p, S 3 ) µ ab µ ac () µ ab (p,
Effective Bandwidth for Traffic Engineering
 Brigham Young University BYU ScholarsArchive All Faculty Publications 2-5- Effective Bandwidth for Traffic Engineering Mark J. Clement clement@cs.byu.edu Rob Kunz See next page for additional authors Follow
Brigham Young University BYU ScholarsArchive All Faculty Publications 2-5- Effective Bandwidth for Traffic Engineering Mark J. Clement clement@cs.byu.edu Rob Kunz See next page for additional authors Follow
Towards a Statistical Network Calculus Dealing with Uncertainty in Arrivals
 Towards a Statistical Network Calculus Dealing with Uncertainty in Arrivals Michael A. Beck, Sebastian A. Henningsen, Simon B. Birnbach, Jens B. Schmitt Distributed Computer Systems DISCO Lab, University
Towards a Statistical Network Calculus Dealing with Uncertainty in Arrivals Michael A. Beck, Sebastian A. Henningsen, Simon B. Birnbach, Jens B. Schmitt Distributed Computer Systems DISCO Lab, University
Window Flow Control in Stochastic Network Calculus The General Service Case
 Window Flow Control in Stochastic Network Calculus The General Service Case Michael Beck University of Kaiserslautern Distributed Computer Systems Lab (DISCO Germany beck@cs.uni-kl.de ABSTRACT The problem
Window Flow Control in Stochastic Network Calculus The General Service Case Michael Beck University of Kaiserslautern Distributed Computer Systems Lab (DISCO Germany beck@cs.uni-kl.de ABSTRACT The problem
Homework 1 - SOLUTION
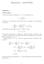 Homework - SOLUTION Problem M/M/ Queue ) Use the fact above to express π k, k > 0, as a function of π 0. π k = ( ) k λ π 0 µ 2) Using λ < µ and the fact that all π k s sum to, compute π 0 (as a function
Homework - SOLUTION Problem M/M/ Queue ) Use the fact above to express π k, k > 0, as a function of π 0. π k = ( ) k λ π 0 µ 2) Using λ < µ and the fact that all π k s sum to, compute π 0 (as a function
Min Congestion Control for High- Speed Heterogeneous Networks. JetMax: Scalable Max-Min
 JetMax: Scalable Max-Min Min Congestion Control for High- Speed Heterogeneous Networks Yueping Zhang Joint work with Derek Leonard and Dmitri Loguinov Internet Research Lab Department of Computer Science
JetMax: Scalable Max-Min Min Congestion Control for High- Speed Heterogeneous Networks Yueping Zhang Joint work with Derek Leonard and Dmitri Loguinov Internet Research Lab Department of Computer Science
Stochastic Service Guarantee Analysis Based on Time-Domain Models
 Stochastic Service Guarantee Analysis Based on Time-Domain Models Jing Xie Department of Telematics Norwegian University of Science and Technology Email: jingxie@item.ntnu.no Yuming Jiang Department of
Stochastic Service Guarantee Analysis Based on Time-Domain Models Jing Xie Department of Telematics Norwegian University of Science and Technology Email: jingxie@item.ntnu.no Yuming Jiang Department of
Sharp Bounds in Stochastic Network Calculus
 1 Sharp Bounds in Stochastic Network Calculus Florin Ciucu, Felix Poloczek, and Jens Schmitt Abstract arxiv:1303.4114v2 [cs.pf] 22 Jul 2013 The practicality of the stochastic network calculus SNC is often
1 Sharp Bounds in Stochastic Network Calculus Florin Ciucu, Felix Poloczek, and Jens Schmitt Abstract arxiv:1303.4114v2 [cs.pf] 22 Jul 2013 The practicality of the stochastic network calculus SNC is often
Glossary availability cellular manufacturing closed queueing network coefficient of variation (CV) conditional probability CONWIP
 Glossary availability The long-run average fraction of time that the processor is available for processing jobs, denoted by a (p. 113). cellular manufacturing The concept of organizing the factory into
Glossary availability The long-run average fraction of time that the processor is available for processing jobs, denoted by a (p. 113). cellular manufacturing The concept of organizing the factory into
Stochastic Network Calculus for Rician Fading in Underwater Wireless Networks
 Appl. Math. Inf. Sci. 10, No. 4, 1465-1474 (2016) 1465 Applied Mathematics & Information Sciences An International Journal http://dx.doi.org/10.18576/amis/100425 Stochastic Network Calculus for Rician
Appl. Math. Inf. Sci. 10, No. 4, 1465-1474 (2016) 1465 Applied Mathematics & Information Sciences An International Journal http://dx.doi.org/10.18576/amis/100425 Stochastic Network Calculus for Rician
Convexity Properties of Loss and Overflow Functions
 Convexity Properties of Loss and Overflow Functions Krishnan Kumaran?, Michel Mandjes y, and Alexander Stolyar? email: kumaran@lucent.com, michel@cwi.nl, stolyar@lucent.com? Bell Labs/Lucent Technologies,
Convexity Properties of Loss and Overflow Functions Krishnan Kumaran?, Michel Mandjes y, and Alexander Stolyar? email: kumaran@lucent.com, michel@cwi.nl, stolyar@lucent.com? Bell Labs/Lucent Technologies,
Introduction to queuing theory
 Introduction to queuing theory Claude Rigault ENST claude.rigault@enst.fr Introduction to Queuing theory 1 Outline The problem The number of clients in a system The client process Delay processes Loss
Introduction to queuing theory Claude Rigault ENST claude.rigault@enst.fr Introduction to Queuing theory 1 Outline The problem The number of clients in a system The client process Delay processes Loss
Performance Evaluation and Service Rate Provisioning for a Queue with Fractional Brownian Input
 Performance Evaluation and Service Rate Provisioning for a Queue with Fractional Brownian Input Jiongze Chen 1, Ronald G. Addie 2, Moshe Zukerman 1 Abstract The Fractional Brownian motion (fbm) traffic
Performance Evaluation and Service Rate Provisioning for a Queue with Fractional Brownian Input Jiongze Chen 1, Ronald G. Addie 2, Moshe Zukerman 1 Abstract The Fractional Brownian motion (fbm) traffic
TOWARDS BETTER MULTI-CLASS PARAMETRIC-DECOMPOSITION APPROXIMATIONS FOR OPEN QUEUEING NETWORKS
 TOWARDS BETTER MULTI-CLASS PARAMETRIC-DECOMPOSITION APPROXIMATIONS FOR OPEN QUEUEING NETWORKS by Ward Whitt AT&T Bell Laboratories Murray Hill, NJ 07974-0636 March 31, 199 Revision: November 9, 199 ABSTRACT
TOWARDS BETTER MULTI-CLASS PARAMETRIC-DECOMPOSITION APPROXIMATIONS FOR OPEN QUEUEING NETWORKS by Ward Whitt AT&T Bell Laboratories Murray Hill, NJ 07974-0636 March 31, 199 Revision: November 9, 199 ABSTRACT
Quality of Real-Time Streaming in Wireless Cellular Networks : Stochastic Modeling and Analysis
 Quality of Real-Time Streaming in Wireless Cellular Networs : Stochastic Modeling and Analysis B. Blaszczyszyn, M. Jovanovic and M. K. Karray Based on paper [1] WiOpt/WiVid Mai 16th, 2014 Outline Introduction
Quality of Real-Time Streaming in Wireless Cellular Networs : Stochastic Modeling and Analysis B. Blaszczyszyn, M. Jovanovic and M. K. Karray Based on paper [1] WiOpt/WiVid Mai 16th, 2014 Outline Introduction
Intro to Queueing Theory
 1 Intro to Queueing Theory Little s Law M/G/1 queue Conservation Law 1/31/017 M/G/1 queue (Simon S. Lam) 1 Little s Law No assumptions applicable to any system whose arrivals and departures are observable
1 Intro to Queueing Theory Little s Law M/G/1 queue Conservation Law 1/31/017 M/G/1 queue (Simon S. Lam) 1 Little s Law No assumptions applicable to any system whose arrivals and departures are observable
Asymptotic Delay Distribution and Burst Size Impact on a Network Node Driven by Self-similar Traffic
 Èíôîðìàöèîííûå ïðîöåññû, Òîì 5, 1, 2005, ñòð. 4046. c 2004 D'Apice, Manzo. INFORMATION THEORY AND INFORMATION PROCESSING Asymptotic Delay Distribution and Burst Size Impact on a Network Node Driven by
Èíôîðìàöèîííûå ïðîöåññû, Òîì 5, 1, 2005, ñòð. 4046. c 2004 D'Apice, Manzo. INFORMATION THEORY AND INFORMATION PROCESSING Asymptotic Delay Distribution and Burst Size Impact on a Network Node Driven by
ON THE CONVERGENCE OF FARIMA SEQUENCE TO FRACTIONAL GAUSSIAN NOISE. Joo-Mok Kim* 1. Introduction
 JOURNAL OF THE CHUNGCHEONG MATHEMATICAL SOCIETY Volume 26, No. 2, May 2013 ON THE CONVERGENCE OF FARIMA SEQUENCE TO FRACTIONAL GAUSSIAN NOISE Joo-Mok Kim* Abstract. We consider fractional Gussian noise
JOURNAL OF THE CHUNGCHEONG MATHEMATICAL SOCIETY Volume 26, No. 2, May 2013 ON THE CONVERGENCE OF FARIMA SEQUENCE TO FRACTIONAL GAUSSIAN NOISE Joo-Mok Kim* Abstract. We consider fractional Gussian noise
A Virtual Queue Approach to Loss Estimation
 A Virtual Queue Approach to Loss Estimation Guoqiang Hu, Yuming Jiang, Anne Nevin Centre for Quantifiable Quality of Service in Communication Systems Norwegian University of Science and Technology, Norway
A Virtual Queue Approach to Loss Estimation Guoqiang Hu, Yuming Jiang, Anne Nevin Centre for Quantifiable Quality of Service in Communication Systems Norwegian University of Science and Technology, Norway
A Simple Memoryless Proof of the Capacity of the Exponential Server Timing Channel
 A Simple Memoryless Proof of the Capacity of the Exponential Server iming Channel odd P. Coleman ECE Department Coordinated Science Laboratory University of Illinois colemant@illinois.edu Abstract his
A Simple Memoryless Proof of the Capacity of the Exponential Server iming Channel odd P. Coleman ECE Department Coordinated Science Laboratory University of Illinois colemant@illinois.edu Abstract his
Mixed Stochastic and Event Flows
 Simulation Mixed and Event Flows Modeling for Simulation Dynamics Robert G. Cole 1, George Riley 2, Derya Cansever 3 and William Yurcick 4 1 Johns Hopkins University 2 Georgia Institue of Technology 3
Simulation Mixed and Event Flows Modeling for Simulation Dynamics Robert G. Cole 1, George Riley 2, Derya Cansever 3 and William Yurcick 4 1 Johns Hopkins University 2 Georgia Institue of Technology 3
Stochastic Hybrid Systems: Applications to Communication Networks
 research supported by NSF Stochastic Hybrid Systems: Applications to Communication Networks João P. Hespanha Center for Control Engineering and Computation University of California at Santa Barbara Talk
research supported by NSF Stochastic Hybrid Systems: Applications to Communication Networks João P. Hespanha Center for Control Engineering and Computation University of California at Santa Barbara Talk
1 Introduction Future high speed digital networks aim to serve integrated trac, such as voice, video, fax, and so forth. To control interaction among
 On Deterministic Trac Regulation and Service Guarantees: A Systematic Approach by Filtering Cheng-Shang Chang Dept. of Electrical Engineering National Tsing Hua University Hsinchu 30043 Taiwan, R.O.C.
On Deterministic Trac Regulation and Service Guarantees: A Systematic Approach by Filtering Cheng-Shang Chang Dept. of Electrical Engineering National Tsing Hua University Hsinchu 30043 Taiwan, R.O.C.
Stochastic-Process Limits
 Ward Whitt Stochastic-Process Limits An Introduction to Stochastic-Process Limits and Their Application to Queues With 68 Illustrations Springer Contents Preface vii 1 Experiencing Statistical Regularity
Ward Whitt Stochastic-Process Limits An Introduction to Stochastic-Process Limits and Their Application to Queues With 68 Illustrations Springer Contents Preface vii 1 Experiencing Statistical Regularity
Strong Performance Guarantees for Asynchronous Buffered Crossbar Schedulers
 Strong Performance Guarantees for Asynchronous Buffered Crossbar Schedulers Jonathan Turner Washington University jon.turner@wustl.edu January 30, 2008 Abstract Crossbar-based switches are commonly used
Strong Performance Guarantees for Asynchronous Buffered Crossbar Schedulers Jonathan Turner Washington University jon.turner@wustl.edu January 30, 2008 Abstract Crossbar-based switches are commonly used
ELEMENTS OF PROBABILITY THEORY
 ELEMENTS OF PROBABILITY THEORY Elements of Probability Theory A collection of subsets of a set Ω is called a σ algebra if it contains Ω and is closed under the operations of taking complements and countable
ELEMENTS OF PROBABILITY THEORY Elements of Probability Theory A collection of subsets of a set Ω is called a σ algebra if it contains Ω and is closed under the operations of taking complements and countable
SAMPLING AND INVERSION
 SAMPLING AND INVERSION Darryl Veitch dveitch@unimelb.edu.au CUBIN, Department of Electrical & Electronic Engineering University of Melbourne Workshop on Sampling the Internet, Paris 2005 A TALK WITH TWO
SAMPLING AND INVERSION Darryl Veitch dveitch@unimelb.edu.au CUBIN, Department of Electrical & Electronic Engineering University of Melbourne Workshop on Sampling the Internet, Paris 2005 A TALK WITH TWO
Postprint.
 http://www.diva-portal.org Postprint This is the accepted version of a paper presented at IEEE Global Telecommunications Conference 2016 GLOBECOM 2016). Citation for the original published paper: Yang,
http://www.diva-portal.org Postprint This is the accepted version of a paper presented at IEEE Global Telecommunications Conference 2016 GLOBECOM 2016). Citation for the original published paper: Yang,
Stability, Queue Length and Delay of Deterministic and Stochastic Queueing Networks Cheng-Shang Chang IBM Research Division T.J. Watson Research Cente
 Stability, Queue Length and Delay of Deterministic and Stochastic Queueing Networks Cheng-Shang Chang IBM Research Division T.J. Watson Research Center P.O. Box 704 Yorktown Heights, NY 10598 cschang@watson.ibm.com
Stability, Queue Length and Delay of Deterministic and Stochastic Queueing Networks Cheng-Shang Chang IBM Research Division T.J. Watson Research Center P.O. Box 704 Yorktown Heights, NY 10598 cschang@watson.ibm.com
On Stochastic Adaptive Control & its Applications. Bozenna Pasik-Duncan University of Kansas, USA
 On Stochastic Adaptive Control & its Applications Bozenna Pasik-Duncan University of Kansas, USA ASEAS Workshop, AFOSR, 23-24 March, 2009 1. Motivation: Work in the 1970's 2. Adaptive Control of Continuous
On Stochastic Adaptive Control & its Applications Bozenna Pasik-Duncan University of Kansas, USA ASEAS Workshop, AFOSR, 23-24 March, 2009 1. Motivation: Work in the 1970's 2. Adaptive Control of Continuous
A Queueing System with Queue Length Dependent Service Times, with Applications to Cell Discarding in ATM Networks
 A Queueing System with Queue Length Dependent Service Times, with Applications to Cell Discarding in ATM Networks by Doo Il Choi, Charles Knessl and Charles Tier University of Illinois at Chicago 85 South
A Queueing System with Queue Length Dependent Service Times, with Applications to Cell Discarding in ATM Networks by Doo Il Choi, Charles Knessl and Charles Tier University of Illinois at Chicago 85 South
CPSC 531: System Modeling and Simulation. Carey Williamson Department of Computer Science University of Calgary Fall 2017
 CPSC 531: System Modeling and Simulation Carey Williamson Department of Computer Science University of Calgary Fall 2017 Motivating Quote for Queueing Models Good things come to those who wait - poet/writer
CPSC 531: System Modeling and Simulation Carey Williamson Department of Computer Science University of Calgary Fall 2017 Motivating Quote for Queueing Models Good things come to those who wait - poet/writer
Estimation of the long Memory parameter using an Infinite Source Poisson model applied to transmission rate measurements
 of the long Memory parameter using an Infinite Source Poisson model applied to transmission rate measurements François Roueff Ecole Nat. Sup. des Télécommunications 46 rue Barrault, 75634 Paris cedex 13,
of the long Memory parameter using an Infinite Source Poisson model applied to transmission rate measurements François Roueff Ecole Nat. Sup. des Télécommunications 46 rue Barrault, 75634 Paris cedex 13,
Efficient Nonlinear Optimizations of Queuing Systems
 Efficient Nonlinear Optimizations of Queuing Systems Mung Chiang, Arak Sutivong, and Stephen Boyd Electrical Engineering Department, Stanford University, CA 9435 Abstract We present a systematic treatment
Efficient Nonlinear Optimizations of Queuing Systems Mung Chiang, Arak Sutivong, and Stephen Boyd Electrical Engineering Department, Stanford University, CA 9435 Abstract We present a systematic treatment
Queueing Theory II. Summary. ! M/M/1 Output process. ! Networks of Queue! Method of Stages. ! General Distributions
 Queueing Theory II Summary! M/M/1 Output process! Networks of Queue! Method of Stages " Erlang Distribution " Hyperexponential Distribution! General Distributions " Embedded Markov Chains M/M/1 Output
Queueing Theory II Summary! M/M/1 Output process! Networks of Queue! Method of Stages " Erlang Distribution " Hyperexponential Distribution! General Distributions " Embedded Markov Chains M/M/1 Output
Figure 10.1: Recording when the event E occurs
 10 Poisson Processes Let T R be an interval. A family of random variables {X(t) ; t T} is called a continuous time stochastic process. We often consider T = [0, 1] and T = [0, ). As X(t) is a random variable
10 Poisson Processes Let T R be an interval. A family of random variables {X(t) ; t T} is called a continuous time stochastic process. We often consider T = [0, 1] and T = [0, ). As X(t) is a random variable
On queueing in coded networks queue size follows degrees of freedom
 On queueing in coded networks queue size follows degrees of freedom Jay Kumar Sundararajan, Devavrat Shah, Muriel Médard Laboratory for Information and Decision Systems, Massachusetts Institute of Technology,
On queueing in coded networks queue size follows degrees of freedom Jay Kumar Sundararajan, Devavrat Shah, Muriel Médard Laboratory for Information and Decision Systems, Massachusetts Institute of Technology,
Part I Stochastic variables and Markov chains
 Part I Stochastic variables and Markov chains Random variables describe the behaviour of a phenomenon independent of any specific sample space Distribution function (cdf, cumulative distribution function)
Part I Stochastic variables and Markov chains Random variables describe the behaviour of a phenomenon independent of any specific sample space Distribution function (cdf, cumulative distribution function)
FRACTIONAL BROWNIAN MOTION WITH H < 1/2 AS A LIMIT OF SCHEDULED TRAFFIC
 Applied Probability Trust ( April 20) FRACTIONAL BROWNIAN MOTION WITH H < /2 AS A LIMIT OF SCHEDULED TRAFFIC VICTOR F. ARAMAN, American University of Beirut PETER W. GLYNN, Stanford University Keywords:
Applied Probability Trust ( April 20) FRACTIONAL BROWNIAN MOTION WITH H < /2 AS A LIMIT OF SCHEDULED TRAFFIC VICTOR F. ARAMAN, American University of Beirut PETER W. GLYNN, Stanford University Keywords:
Internet Traffic Modeling and Its Implications to Network Performance and Control
 Internet Traffic Modeling and Its Implications to Network Performance and Control Kihong Park Department of Computer Sciences Purdue University park@cs.purdue.edu Outline! Motivation! Traffic modeling!
Internet Traffic Modeling and Its Implications to Network Performance and Control Kihong Park Department of Computer Sciences Purdue University park@cs.purdue.edu Outline! Motivation! Traffic modeling!
Lecture 7: Simulation of Markov Processes. Pasi Lassila Department of Communications and Networking
 Lecture 7: Simulation of Markov Processes Pasi Lassila Department of Communications and Networking Contents Markov processes theory recap Elementary queuing models for data networks Simulation of Markov
Lecture 7: Simulation of Markov Processes Pasi Lassila Department of Communications and Networking Contents Markov processes theory recap Elementary queuing models for data networks Simulation of Markov
THROUGHPUT ANALYSIS OF STOCHASTIC NETWORKS USING FLUID LIMITS. By John Musacchio University of California, Santa Cruz and
 Submitted to the Annals of Applied Probability THROUGHPUT ANALYSIS OF STOCHASTIC NETWORKS USING FLUID LIMITS. By John Musacchio University of California, Santa Cruz and By Jean Walrand University of California,
Submitted to the Annals of Applied Probability THROUGHPUT ANALYSIS OF STOCHASTIC NETWORKS USING FLUID LIMITS. By John Musacchio University of California, Santa Cruz and By Jean Walrand University of California,
Multi-Hop Probing Asymptotics in Available Bandwidth Estimation: Stochastic Analysis
 Multi-Hop Probing Asymptotics in Available Bandwidth Estimation: Stochastic Analysis Xiliang Liu City University of New York xliu@gc.cuny.edu Kaliappa Ravindran City College of New York ravi@cs.ccny.cuny.edu
Multi-Hop Probing Asymptotics in Available Bandwidth Estimation: Stochastic Analysis Xiliang Liu City University of New York xliu@gc.cuny.edu Kaliappa Ravindran City College of New York ravi@cs.ccny.cuny.edu
Introduction to Markov Chains, Queuing Theory, and Network Performance
 Introduction to Markov Chains, Queuing Theory, and Network Performance Marceau Coupechoux Telecom ParisTech, departement Informatique et Réseaux marceau.coupechoux@telecom-paristech.fr IT.2403 Modélisation
Introduction to Markov Chains, Queuing Theory, and Network Performance Marceau Coupechoux Telecom ParisTech, departement Informatique et Réseaux marceau.coupechoux@telecom-paristech.fr IT.2403 Modélisation
The Effective Bandwidth of Markov Modulated Fluid Process Sources with a Generalized Processor Sharing Server
 The Effective Bandwidth of Markov Modulated Fluid Process Sources with a Generalized Processor Sharing Server Shiwen Mao Shivendra S. Panwar Dept. of ECE, Polytechnic University, 6 MetroTech Center, Brooklyn,
The Effective Bandwidth of Markov Modulated Fluid Process Sources with a Generalized Processor Sharing Server Shiwen Mao Shivendra S. Panwar Dept. of ECE, Polytechnic University, 6 MetroTech Center, Brooklyn,
Queueing Theory I Summary! Little s Law! Queueing System Notation! Stationary Analysis of Elementary Queueing Systems " M/M/1 " M/M/m " M/M/1/K "
 Queueing Theory I Summary Little s Law Queueing System Notation Stationary Analysis of Elementary Queueing Systems " M/M/1 " M/M/m " M/M/1/K " Little s Law a(t): the process that counts the number of arrivals
Queueing Theory I Summary Little s Law Queueing System Notation Stationary Analysis of Elementary Queueing Systems " M/M/1 " M/M/m " M/M/1/K " Little s Law a(t): the process that counts the number of arrivals
Singular perturbation analysis of an additive increase multiplicative decrease control algorithm under time-varying buffering delays.
 Singular perturbation analysis of an additive increase multiplicative decrease control algorithm under time-varying buffering delays. V. Guffens 1 and G. Bastin 2 Intelligent Systems and Networks Research
Singular perturbation analysis of an additive increase multiplicative decrease control algorithm under time-varying buffering delays. V. Guffens 1 and G. Bastin 2 Intelligent Systems and Networks Research
A Data Center Interconnects Calculus
 A Data Center Interconnects Calculus Hao Wang, Haoyun Shen, Philipp Wieder, Ramin Yahyapour GWDG / University of Göttingen, Germany Abstract For many application scenarios, interconnected data centers
A Data Center Interconnects Calculus Hao Wang, Haoyun Shen, Philipp Wieder, Ramin Yahyapour GWDG / University of Göttingen, Germany Abstract For many application scenarios, interconnected data centers
Optimal scaling of average queue sizes in an input-queued switch: an open problem
 DOI 10.1007/s11134-011-9234-1 Optimal scaling of average queue sizes in an input-queued switch: an open problem Devavrat Shah John N. Tsitsiklis Yuan Zhong Received: 9 May 2011 / Revised: 9 May 2011 Springer
DOI 10.1007/s11134-011-9234-1 Optimal scaling of average queue sizes in an input-queued switch: an open problem Devavrat Shah John N. Tsitsiklis Yuan Zhong Received: 9 May 2011 / Revised: 9 May 2011 Springer
queue KTH, Royal Institute of Technology, Department of Microelectronics and Information Technology
 Analysis of the Packet oss Process in an MMPP+M/M/1/K queue György Dán, Viktória Fodor KTH, Royal Institute of Technology, Department of Microelectronics and Information Technology {gyuri,viktoria}@imit.kth.se
Analysis of the Packet oss Process in an MMPP+M/M/1/K queue György Dán, Viktória Fodor KTH, Royal Institute of Technology, Department of Microelectronics and Information Technology {gyuri,viktoria}@imit.kth.se
Modeling and Analysis of Traffic in High Speed Networks
 The University of Kansas Technical Report Modeling and Analysis of Traffic in High Speed Networks Soma S. Muppidi Victor S. Frost ITTC-FY98-TR-10980-22 August 1997 Project Sponsor: Sprint Corporation Under
The University of Kansas Technical Report Modeling and Analysis of Traffic in High Speed Networks Soma S. Muppidi Victor S. Frost ITTC-FY98-TR-10980-22 August 1997 Project Sponsor: Sprint Corporation Under
MARKOV PROCESSES. Valerio Di Valerio
 MARKOV PROCESSES Valerio Di Valerio Stochastic Process Definition: a stochastic process is a collection of random variables {X(t)} indexed by time t T Each X(t) X is a random variable that satisfy some
MARKOV PROCESSES Valerio Di Valerio Stochastic Process Definition: a stochastic process is a collection of random variables {X(t)} indexed by time t T Each X(t) X is a random variable that satisfy some
Other properties of M M 1
 Other properties of M M 1 Přemysl Bejda premyslbejda@gmail.com 2012 Contents 1 Reflected Lévy Process 2 Time dependent properties of M M 1 3 Waiting times and queue disciplines in M M 1 Contents 1 Reflected
Other properties of M M 1 Přemysl Bejda premyslbejda@gmail.com 2012 Contents 1 Reflected Lévy Process 2 Time dependent properties of M M 1 3 Waiting times and queue disciplines in M M 1 Contents 1 Reflected
Background Concrete Greedy Shapers Min-Plus Algebra Abstract Greedy Shapers Acknowledgment. Greedy Shaper
 Greedy Shaper Modular Performance Analysis and Interface-Based Design for Embedded Real-Time Systems: Section 3.1 od Reading Group on Real-Time Calculus Outline 1 Background The Curves Drawback 2 Concrete
Greedy Shaper Modular Performance Analysis and Interface-Based Design for Embedded Real-Time Systems: Section 3.1 od Reading Group on Real-Time Calculus Outline 1 Background The Curves Drawback 2 Concrete
Class 11 Non-Parametric Models of a Service System; GI/GI/1, GI/GI/n: Exact & Approximate Analysis.
 Service Engineering Class 11 Non-Parametric Models of a Service System; GI/GI/1, GI/GI/n: Exact & Approximate Analysis. G/G/1 Queue: Virtual Waiting Time (Unfinished Work). GI/GI/1: Lindley s Equations
Service Engineering Class 11 Non-Parametric Models of a Service System; GI/GI/1, GI/GI/n: Exact & Approximate Analysis. G/G/1 Queue: Virtual Waiting Time (Unfinished Work). GI/GI/1: Lindley s Equations
Transient Analysis for Wireless Networks
 Transient Analysis for Wireless Networks Jaya Prakash Champati, Hussein Al-Zubaidy, James Gross School of Electrical Engineering, KTH Royal Institute of Technology, Stockholm, Sweden E-mail:jpra@kth.se,james.gross@ee.kth.se
Transient Analysis for Wireless Networks Jaya Prakash Champati, Hussein Al-Zubaidy, James Gross School of Electrical Engineering, KTH Royal Institute of Technology, Stockholm, Sweden E-mail:jpra@kth.se,james.gross@ee.kth.se
IEEE Journal of Selected Areas in Communication, special issue on Advances in the Fundamentals of Networking ( vol. 13, no. 6 ), Aug
 IEEE Journal of Selected Areas in Communication, special issue on Advances in the Fundamentals of Networking ( vol. 13, no. 6 ), Aug. 1995. Quality of Service Guarantees in Virtual Circuit Switched Networks
IEEE Journal of Selected Areas in Communication, special issue on Advances in the Fundamentals of Networking ( vol. 13, no. 6 ), Aug. 1995. Quality of Service Guarantees in Virtual Circuit Switched Networks
Markov processes and queueing networks
 Inria September 22, 2015 Outline Poisson processes Markov jump processes Some queueing networks The Poisson distribution (Siméon-Denis Poisson, 1781-1840) { } e λ λ n n! As prevalent as Gaussian distribution
Inria September 22, 2015 Outline Poisson processes Markov jump processes Some queueing networks The Poisson distribution (Siméon-Denis Poisson, 1781-1840) { } e λ λ n n! As prevalent as Gaussian distribution
Integral representations in models with long memory
 Integral representations in models with long memory Georgiy Shevchenko, Yuliya Mishura, Esko Valkeila, Lauri Viitasaari, Taras Shalaiko Taras Shevchenko National University of Kyiv 29 September 215, Ulm
Integral representations in models with long memory Georgiy Shevchenko, Yuliya Mishura, Esko Valkeila, Lauri Viitasaari, Taras Shalaiko Taras Shevchenko National University of Kyiv 29 September 215, Ulm
I 2 (t) R (t) R 1 (t) = R 0 (t) B 1 (t) R 2 (t) B b (t) = N f. C? I 1 (t) R b (t) N b. Acknowledgements
 Proc. 34th Allerton Conf. on Comm., Cont., & Comp., Monticello, IL, Oct., 1996 1 Service Guarantees for Window Flow Control 1 R. L. Cruz C. M. Okino Department of Electrical & Computer Engineering University
Proc. 34th Allerton Conf. on Comm., Cont., & Comp., Monticello, IL, Oct., 1996 1 Service Guarantees for Window Flow Control 1 R. L. Cruz C. M. Okino Department of Electrical & Computer Engineering University
Congestion In Large Balanced Fair Links
 Congestion In Large Balanced Fair Links Thomas Bonald (Telecom Paris-Tech), Jean-Paul Haddad (Ernst and Young) and Ravi R. Mazumdar (Waterloo) ITC 2011, San Francisco Introduction File transfers compose
Congestion In Large Balanced Fair Links Thomas Bonald (Telecom Paris-Tech), Jean-Paul Haddad (Ernst and Young) and Ravi R. Mazumdar (Waterloo) ITC 2011, San Francisco Introduction File transfers compose
TWO PROBLEMS IN NETWORK PROBING
 TWO PROBLEMS IN NETWORK PROBING DARRYL VEITCH The University of Melbourne 1 Temporal Loss and Delay Tomography 2 Optimal Probing in Convex Networks Paris Networking 27 Juin 2007 TEMPORAL LOSS AND DELAY
TWO PROBLEMS IN NETWORK PROBING DARRYL VEITCH The University of Melbourne 1 Temporal Loss and Delay Tomography 2 Optimal Probing in Convex Networks Paris Networking 27 Juin 2007 TEMPORAL LOSS AND DELAY
