Utility Analysis of Simple FEC Schemes for VoIP
|
|
|
- Marcia Walton
- 5 years ago
- Views:
Transcription
1 Utility Analysis of Simple FEC Schemes for VoIP Parijat Dube and Eitan Altman,2 INRIA, BP93, 692 Sophia-Antipolis, 2 CESIMO, Facultad de Ingeneria, Universidad de Los Andes, Mérida, Venezuela Abstract Forward Error Correction (FEC) is an attractive solution for recovering from packet losses in real-time applications However, in many such applications, due to delay constraints, complex FEC schemes that may enable to approach the Shannon channel capacity cannot be used In those cases, much simpler FEC schemes are implemented, in which a compressed copy of a packet is concatenated to some subsequent packet In this paper we analyze the utility gained by such schemes in the case where losses are due to queueing congestion in the network Loss probabilities in presence of FEC are obtained using sophisticated tools based on Ballot theorems Our explicit expressions allows us to study numerically several approaches for adding FEC Introduction Forward Error Correction (FEC) is considered to be an attractive solution for recovering from packet losses in real-time applications (over high speed networks [8,2]) without increasing latency Though there are different proposals for FEC schemes,in this paper we shall focus on a simple FEC scheme that has been proposed [4] in the IETF (Internet Engineering Task Force) and implemented in audio tools like Freephone [] and Rat [5] The scheme consists in adding a redundant copy of the original packet to the tail of the subsequent packet If a packet is lost in the network then it can be reconstructed from its redundant copy (if it is correctly received) It was suggested to use PCM coding for data in the original packet and a low bit rate coding (like LPC, GSM, or 2-bit ADPCM) for the redundant information Proposals to enhance the performance of this simple FEC scheme include: (i) increasing the offset φ between the original packet and its redundant copy [,9] at the codec, (ii) adding multiple redundant copies of a packet in multiple subsequent ones [], (iii) adding to a packet a redundant copy computed from a block of some preceding packets [5] etc Let the offset between the original packet and its redundant copy at the bottleneck be φ In a recent work [6], treating φ as a parameter it has been shown via a queueing analysis that the simple FEC scheme may not lead to an improvement in audio quality The assumptions made in [6] include: (i) a single bottleneck link with dedicated buffer for audio flows implementing FEC and (ii) a linear utility function (A utility function is an indication of the variation E Gregori et al (Eds): NETWORKING 22, LNCS 2345, pp , 22 c Springer-Verlag Berlin Heidelberg 22
2 Utility Analysis of Simple FEC Schemes for VoIP 227 of the audio quality at the receiver as a function of the transmission rate) The authors showed that for a buffer size K, the ratio of the volume of the redundant information to the volume of the original information α, a Poisson arrival of packets, exponential distribution of service times and for φ less than the scaled K (+α) buffer size (in terms of number of packets) K α =, adding FEC according to the simple FEC scheme always leads to a deterioration in quality caused by increased load in the network due to redundant data They further showed that the same is also true for the limiting case φ, which forms an upper bound on the audio quality In their subsequent work [7], the authors showed that improvement in quality is possible with the simple FEC scheme when: (i) the (total) rate of flow(s) adding FEC is small compared to the total rate of the other flow(s), called exogenous flows not adding FEC and sharing the same bottleneck and (ii) with particular non-linear utility functions It was also concluded that the audio quality is always an increasing function of the offset φ between the original packet and its copy They also provided lower and upper bounds on the audio quality for case (i) with Poisson arrivals of packets but with exponential distribution of packet sizes for exogenous flows and deterministic packet sizes for audio flows implementing FEC It was argued in [6] that φ>k α may not be interesting as it could lead to unacceptable delays at the receiver But it should be noticed that the actual offset between the original packet and its redundant copy at the bottleneck could become larger than the offset generated at the transmission codec due to multiplexing of different flows (either implementing FEC or not) at the bottleneck Moreover, in the case of large bandwidth, when many connections can be supported, a large offset does not generate necessarily a large delay, as the transmission time of a packet at the bottleneck is still very short In this paper we first complement the work in [6] and compute the performance for a fixed φ>k α It turns out that this case requires much more sophisticated computations than those in [6] Using these results, we then compute the performances for the case of random offset obtained in situations where several flows are multiplexed In particular, we obtain expressions for the expected audio quality for general utility functions We use these results for an extensive numerical investigation using six different utility functions In this paper we deal with a Markovian framework: Poisson arrivals of packets and exponential distribution of all packet lengths and with the simple FEC scheme with φ = We derive expressions for the quality function of an audio flow implementing FEC, multiplexed with: (i) other audio flows implementing FEC and/or (ii) exogenous flows not implementing FEC and different utility functions and Φ varying from to These calculations will finally help us in the evaluation of the expected value of the quality function and the (possible) gain achievable with FEC in a more realistic framework of multiplexing of different flows In presence of other multiplexed traffic, the offset φ is not deterministic anymore: it becomes a random variable Φ, taking values from φ (the offset generated at the codec) to
3 228 P Dube and E Altman 2 Model In this section we shall use a simple (same as in [6]) M/M//K queue to model the network and thus the loss process of audio packets In other words, we assume that packets arrive at the bottleneck 2 according to a Poisson process with intensity and the lengths of the packets are exponentially distributed with parameter µ Let ρ = /µ, be the intensity of the audio traffic and with ρ<, the loss probability of a packet in steady state is given by (see []), π ρ,k = ρ ρ K, and for ρ = it is equal to, π ρ K+ ρ,k = K+ Let U(α) be the utility function associated with receiving only a compressed version of a packet with a redundancy factor α, α We assume that U(α) is non-decreasing in α and lim α U(α) =LetY 3 n be a random variable defined as, { if packet n is lost Y n = if packet n is correctly received 2 Case I: All Flows Implementing FEC We consider the case when an audio flow implementing FEC (we shall refer to this flow as the tagged flow) shares the bottleneck with other audio flows also implementing same type of FEC and arriving as independent Poisson processes Let a be the total arrival rate of all other audio flows at the bottleneck For each flow, the redundant information of a packet is located in the next Thus j + packet of an audio flow will contain in addition to its own useful information some redundant information of the jth packet of the same flow Let ρ =( + a )/µ We shall consider two scenarios concerning the influence of redundancy on the packet size Constant packet size model: We assume that the size of a packet is not affected by adding redundancy and thus redundancy is a overhead The more the redundancy the less is the useful information carried by the packet Constant amount of useful information: We assume that the packet size increases when adding redundancy (and thus increases with α) so that the amount of useful information contained in a packet is unchanged Increasing packet size has an impact both on the service times, and on the number of packets that can be stored at buffers To account for this we assume [6]: the service time is exponentially distributed with parameter µ α = µ +α Thus ρ α = ρ( + α) The amount of buffering is diminished by + α Thus the scaled buffer size is K α = K +α 2 Most of the losses from a flow occur in the router having the smallest available bandwidth in the chain of routers, so that one may model the whole chain of routers by one single router called the bottleneck This assumption has both theoretical and experimental [4,2] justification 3 subscript n is for the nth packet of the total flow at the queue
4 Utility Analysis of Simple FEC Schemes for VoIP 229 The loss probability in the presence of redundancy for this case is π ρα,k α = ρ α ( ρ α) Kα+ ( ρ α ) Kα In the following analysis we shall denote by P α (), the probabilities evaluated at µ α and K α Observe that by taking α =inp α () and π ρα,k α we get the corresponding expressions for the case of constant packet size as K = K and ρ = ρ Let P α (Y n+φ =,Φ = φ Y n = ) be the probability that due to multiplexing there are φ packets between two consecutive packets of the tagged audio flow at the bottleneck and that the n+φth packet is received correctly given that the nth packet is lost Without loss of generality we assume that packet n belongs to the tagged audio flow We define below the expected quality function Q(α) for the two cases Constant packet size Q(α) = () P (Y n =)U( α)+u(α)p (Y n =) P (Y n+φ =,Φ= φ Y n =) = U( α) π ρ,k (U( α) U(α) φ= P (Y n+φ =,Φ= φ Y n = )) Constant amount of useful information: as the amount of useful information carried by a packet remains unchanged we define φ= Q(α) = (2) P α (Y n =)U() + U(α)P α (Y n =) P α (Y n+φ =,Φ= φ Y n =) = U() π ρα,k α (U() U(α) φ= P α (Y n+φ =,Φ= φ Y n = )) φ= We will next find the complementary probability P α (Y n+φ =,Φ = φ Y n = ) In steady state we need to evaluate the probability P α (Y Φ =,Φ = φ Y =) which in terms of the buffer level is P α (X Φ = K α,φ = φ X = K α ), where X k is the queue size as seen by an arriving kth packet We will now evaluate P α (X Φ = K α,φ = φ X = K α ) for φ = {, 2,} using results from ballot theorem Let A be the event of the loss of the th packet and A φ the event of the loss of the φth packet We consider the following cases: Case : no packet is lost in the interval between the happening of A and A φ the first lost packet after the th packet is the φth packet Case 2: i( i φ ) packets are lost between A and A φ We consider the two cases separately The main difficulty in the case when the redundancy-offset is larger than the (scaled) buffer, ie, φ>k α is that paths
5 23 P Dube and E Altman with this property may cause the buffer to become empty (even several times) This makes the analysis substantially more complex than in [6] To proceed we first consider a general path that starts when there are K α packets in the buffer, ends with K α packets in the buffer, contains η events (arrivals of Poisson process with parameter + a and departures) and no packets are lost Let ζ η be the probability of such a path We will now express P α (X Φ = K α,φ= φ X = K α ) for the two cases in terms of this probability Case : for the φ packet to be the first lost packet there must be an epoch after the arrival of the φ packet that the buffer is full and the next event is an arrival Upto that epoch the number of departures must be equal to the number of arrivals The number of arrivals upto that epoch is φ and so the number of departures is φ to yield a total number of η =2(φ ) events Thus the probability for this case is: ζ 2(φ ) + a+µ α However we also require that all the φ arrivals should be from other audio flows (coming as a Poisson process with intensity a ) Hence the joint probability that there are φ packets from other flows (due to multiplexing) at the ( φ a + a+µ α a+) bottleneck and the φth packet is lost is ζ 2(φ ) Case 2: First we look at i = Let the lost packet be the jth arrival ( j φ ) Thus there should be no loss from the instant of the loss of th packet till the epoch before the arrival of the jth packet Since the queue size is K α at A and since the jth packet is the first to be lost, there must be an epoch after the arrival of the j packet that the buffer is again full and the next event is an arrival Again, upto this epoch, the number of departures must be equal to the number of departures The number of arrivals upto that epoch is j, so the number of departures is j yielding a total number of η =2(j ) Thus the probability of the path is: ζ a 2(j ) + a+µ α ζ 2(φ j ) a++µ α Also, since we require that all the φ arrivals should be from other audio flows we have ( ) φ 2 the probability of the path as ζ a 2(j ) + a+µ α ζ a 2(φ j ) a++µ α + a Since j can take values from to φ, the total probability for this case is ( ) φ 2 a φ + a j= ζ a 2(j ) + a+µ α ζ 2(φ j ) + a+µ α Now consider the case when i = 2 We will first calculate the probability of a single path with two losses before the loss of the φ packet Let the first loss be of j and second of j 2 packet (j <j 2, j φ 2, 2 j 2 φ ) By previous arguments the probability of such a path is: ( ) ζ 2(j )ζ a 2(j2 j ) + a+µ α 2ζ2(φ j2 ) + a+µ α The total probability for this case is (taking into consideration the requirement that all the φ packets should be from other audio flows): ( a + a ) φ 3 φ 2 φ ζ 2(j )ζ 2(j2 j )ζ 2(φ j2 ) j = j 2=j + a ( + a + µ α ) 3
6 Utility Analysis of Simple FEC Schemes for VoIP 23 In general for i = k( k φ ), we can write the probability as: ( a + a ) φ (k+) φ k φ k+ j = j 2=j + ζ 2(jk j k )ζ 2(φ jk ) ( φ j k =j k + a + a + µ α ζ 2(j )ζ 2(j2 j ) ) k + a + µ α Thus to complete the analysis we need to evaluate the quantity ζ η where η =2, 4, 6, To evaluate this we use the result of [3] which is based on ballot theorems In this paper the authors have obtained the following general expression for ζ η (ι, v), ie, the probability of a path that starts with ι( ι K α ) packets in the buffer ends with v( v K α ) packets in the buffer and contains η( η 2φ + ι v) events (arrivals and departures) and no packets are lost: ζ η (ι, v) =ξ η (ι, v)+ R W ι Y r [Z(ι, v)], r= where ξ η (ι, v) is the probability of a path that starts with ι packets in the buffer ends with v packets in the buffer and contains η events ( ι v η 2n + ι v, ι K α, v K α ) and the buffer never empties along this path, R =+ η ι v 2, W ι and Z are R-length row and Y is an RXR matrix defined as W ι = ( ξ ι (ι, ),ξ ι+2 (ι, ),,ξ ι+2(r ) (ι, ) ), Z(ι, v) = ( ξ η ι (,v),ξ η ι 2 (,v),,ξ η ι 2(R ) (,v) ), ξ 2 (, ) ξ 4 (, ) ξ 2(R ) (, ) ξ 2 (, ) ξ 2(R 2) (, ) Y = ξ 2 (, ) For our analysis we need ζ η (= ζ η (K α,k α )) Thus we get, ζ η (K α,k α )=ζ η = ξ η (K α,k α )+ R W Kα Y r Z(K α,k α ), where R =+ η 2Kα 2 =+ η 2 K α The steps for evaluation of ξ η (ι, v) are available in [3] Thus we can write P α (X Φ = K α,φ= φ X = K α )as r= P α (X Φ = K α,φ= φ X = K α ) = (3) ( ) φ a ζ 2(φ ) + a + + µ α + a a + + µ α
7 232 P Dube and E Altman k=φ k= φ k φ k+ j = j 2=j + φ j k =j k + ζ 2(j )ζ 2(j2 j ) ( ) k ( ) ] φ (k+) a a ζ 2(jk j k )ζ 2(φ jk ) a + + µ α + a Thus knowing P α (X Φ = K α,φ = φ X = K α )wehavep α (Y Φ =,Φ = φ Y = ) and thus we have P α (Y Φ =,Φ= φ Y =)=P α (Φ = φ Y n =) P α (Y Φ =,Φ = φ Y =)=P α (Φ = φ) P α (Y Φ =,Φ = φ Y =, φ< We next find the distribution of Φ Observe that Φ is the number of packets of other flows (other audio flows arriving as an independent Poisson process with parameter a ) Thus Φ is geometrically distributed: P α (Φ = n) =γ n ( γ) for n, with γ = γ = a + a Knowing this we can evaluate the expected quality function Q(α) using (),(2) 22 Case II: Multiplexing between Audio Flows Implementing FEC and Exogenous Flows for the Constant Packet Size Case The case when an audio flow implementing FEC shares the bottleneck with other audio flows also implementing the same FEC scheme and with some other exogenous flows not implementing FEC can be analysed similarly for the case of constant packet size We model the packets of exogenous arriving as an independent (from audio flows) Poisson process with intensity e and hence the total arrival process is again a Poisson process with parameter + a + e Further we assume that the distribution of the size of all packets of all flows is exponential with parameter µ With ρ = +a+e µ, the loss probability of a packet is steady state (with ρ <) is π ρ = ρ ρ K, and for ρ = it is equal to ρ K+ π ρ = (+K) The expressions for expected quality can be obtained from the expressions for the case without exogenous but with a replaced by a + e everywhere For the case of constant amount of useful information it is not clear how we should scale the service rate and the buffer size for this scenario 3 Numerical Examples with Different Utility Functions We will next evaluate the expected quality achieved using different utility functions The utility functions that we consider are used in [6,7] and are of the form proposed in [,6] We define: U (α) =α, U 2 (α) = α, U 3 (α) =α /, U 4 (α) =esc(α α ) ( cos(πα) 2 ) /, U5 (α) = ( cos(πα) 2 ) /3 and U6 (α) =if α> otherwise U 6 (α) = All utilities are concave starting at some minimum and reach U(α) =forα = The least concave is the linear utility function U, which is thus proportional to the amount of information which is well received The most concave function is U 6 Although it does not represent a utility of any real application, it can be used to obtain an upper bound on the gain achieved with employing FEC Indeed, we see that U 6 is larger than any other
8 Utility Analysis of Simple FEC Schemes for VoIP 233 utility, so it follows that in both models described by () and (2), it should give the best quality The utility U 4 is zero for α α This is typical for real time applications with a minimum hard constraint For example, the constraint may represent the fact that the throughput of existing codecs for voice applications cannot go beneath some bound We shall plot the quality (expected) function with these six utility functions under different scenarios For the plots we denote by M the actual buffer size and by ρ that total load Also note that in all the plots that follow the utility functions are represented as: U, + U 2, U 3, o U 4, U 5 and finally U 6 A single audio flow implementing FEC traversing the bottleneck (no multiplexing): When a single audio flow traverses the bottleneck (ie, a = e = ), then the spacing between a packet and its redundancy at the bottleneck is the same as that generated at the transmission codec We take = and ρ = /µ We next plot the quality function with the six utility functions for this scenario and for the cases when: (i) the packet sizes (and hence the buffer sizes) remains unchanged after adding redundancy and the quality function is given by () in Figs, 2 (ii) when the packet sizes changes after adding redundancy and the quality function is given by (2) in Figs 3, 4 M=5,ρ= M=5, ρ=5 2 2 M=5, ρ=9 M=5, ρ=5 2 2 Fig A single audio flow implementing simple FEC traversing the bottleneck with quality function given by () We observe that as expected, U 6 gives an upper bound for the quality More generally, for two utility functions, U j and U i,ifu i U j for all α, then the corre-
9 234 P Dube and E Altman M=5, ρ= M=5, ρ=5 2 2 M=5, ρ=9 M=5, ρ=5 2 2 Fig 2 A single audio flow implementing simple FEC traversing the bottleneck with quality function given by () M=5,ρ= M=5, ρ= M=5, ρ=9 7 M=5, ρ= Fig 3 A single audio flow implementing simple FEC traversing the bottleneck with quality function given by (2)
10 Utility Analysis of Simple FEC Schemes for VoIP M=5, ρ= M=5, ρ= M=5, ρ=9 M=5, ρ= Fig 4 A single audio flow implementing simple FEC traversing the bottleneck with quality function given by (2) sponding quality is larger for both cases () and (2) This is confirmed in the figures, taking into account that U 6 U 3 U 2 U For large buffer size (M = 5) the quality is almost the same for all ρ 9; the reason is that the loss probabilities are very small and almost all contribution for the quality is from the utility of unlost packets For ρ> we see that we gain by adding FEC (for any buffer size, and for both cases described by () and (2)), for utilities U 3,U 4,U 6 For small buffer size M = 5 we gain also for ρ =9 when using utility U 3,U 4,U 6 for both the cases but for very low α, or less The linear utility function always decreases with FEC for any ρ and any M The quality is higher with constant information model than with constant packet size model 2 An audio flow implementing simple FEC sharing the bottleneck with other audio flows implementing the same FEC: This is the case I (Sec 2) of our analysis We take = and a =9 and ρ =( + a )/µ We plot the expected quality function with the six utility functions for this scenario and for the cases when: (i) the packet sizes (and hence the buffer sizes) remains unchanged after adding redundancy and the quality function is given by () in Figs 5, 6 (ii) when the packet sizes changes after adding redundancy and the quality function is given by 7, 8 Due to multiplexing Φ takes values in {, 2,} For our numerical calculations we restricted to φ = {, 2,,8} as for φ 9, the contribution to Q(α) was negligible Thus for buffer size of 5 we will have the spacing exceeding the buffer size Observe that the
11 236 P Dube and E Altman M=5,ρ= M=5, ρ=5 2 2 M=5, ρ=9 M=5, ρ=5 2 2 Fig 5 An audio flow implementing simple FEC sharing the bottleneck with other audio flows implementing the same FEC scheme with quality function given by () M=5, ρ= M=5, ρ=5 2 2 M=5, ρ=9 M=5, ρ=5 2 2 Fig 6 An audio flow implementing simple FEC sharing the bottleneck with other audio flows implementing the same FEC scheme with quality function given by ()
12 Utility Analysis of Simple FEC Schemes for VoIP 237 M=5,ρ= M=5, ρ= M=5, ρ=9 7 M=5, ρ= Fig 7 An audio flow implementing simple FEC sharing the bottleneck with other audio flows implementing the same FEC scheme with quality function given by (2) 2 M=5, ρ= M=5, ρ= M=5, ρ=9 M=5, ρ= Fig 8 An audio flow implementing simple FEC sharing the bottleneck with other audio flows implementing the same FEC scheme with quality function given by (2)
13 238 P Dube and E Altman plots (5) and (6) are almost similar to plots () and (2) respectively From (7) and (8) We observe that for large ρ(> ), the buffer size does not affect the expected quality Also from all the plots it is observed that U 5 always gives a lower bound on expected quality for large α( 2) 4 Conclusion In this paper we studied the (possible) gain obtained with a simple FEC scheme when the losses are due to buffer overflow at the bottleneck We obtained the loss probabilities in the presence of FEC using ballot theorem To this end we generalize the analysis in [6] (which was for φ<k α ) and computed the loss probability for a fixed φ taking values from to Using these results we obtained the expressions for the expected audio quality for general utility functions and then utilised the tools developed for a detailed numerical studies with six utility functions under various scenarios of multiplexing at the bottleneck Our future work is to analyse delay aware utility functions [3] and to do utility analysis of other more intelligent and efficient FEC schemes to quantize the (possible) gain References A V Garcia, S Fosse-Parisis (FreePhone Audio Tool) High-Speed Networking Group INRIA, Sophia Antipolis, France 2 J C Bolot End-to-End Delay and Loss Behavior in the Internet Proc Sigcomm 93, pages , C Boutremans, J L Boudec Adative Delay Aware Error Control for Internet Telephony Proc IPTEL 2, 2 4 C Perkins, L Kouvelas, O Hodson, V Hardman RTP payload for redundant audio data RFC 298 (997) 5 D R Figueiredo, E de Souza e Silva Efficient Mechanisms for Recovering Voice Packets in the Internet Proc IEEE Globecom 99, E Altman, C Barakat and V M Ramos R Queueing Analysis of Simple FEC Schemes for IP Telephony Proc IEEE Infocom 2, April 2 7 E Altman, C Barakat, V M Ramos R On the Utility of FEC Mechanisms for Audio Applications Proc Second International Workshop on Quality of Future Internet Services, Qofis 2, Sept, 2, Coimbra, Portugal See also INRIA Research Report No RR-3998 at 8 E W Biersack Performance Evaluation of FEC in ATM Networks Proc ACM Sigcomm 92, pages , Aug I Kouvelas, O Hodson, V Hardman, J Crowcroft Redundancy Control in Real- Time Internet Audio Conferencing Proc of AVSPN 97, Aberdeen, Scotland, Sept 997 J C Bolot, S Fosse-Parisis, D Towsley Adaptive FEC-Based Error Control for Interactive Audio in the Internet Proc IEEE Infocom 999 L Kleinrock Queueing Systems, Vol I John Wiley, New York, 976
14 Utility Analysis of Simple FEC Schemes for VoIP N Shacham, P McKenney Packet Recovery in High-Speed Networks Using Coding and Buffer MAnagement Proc IEEE Infocom 9, pages 24 3, May 99 3 O Gurewitz, M Sidi, I Cidon The Ballot Theorem Strikes Again: Packet Loss Process Distribution IEEE Trans on Information Theory, 46(7): , 2 4 O J Boxma Sojourn Times in Cyclic Queues: the influence of the slowest server, Computer Performnace and Reliability Elsevier Science Pubs B V (North- Holland), Mice Project (RAT: Robust Audio Tool) Multimedia Integrated Conferencing for European Researchers University College London, UK 6 S Shenker Fundamental Design Issues for the Future Internet IEEE Journal on Selected Areas in Communication, 3(7), September 995
REAL -time audio transmission is now widely used over the
 Queueing analysis of simple FEC schemes for IP Telephony Eitan Altman, Chadi Barakat, Victor M Ramos R Abstract In interactive voice applications, FEC schemes are necessary for the recovery from packet
Queueing analysis of simple FEC schemes for IP Telephony Eitan Altman, Chadi Barakat, Victor M Ramos R Abstract In interactive voice applications, FEC schemes are necessary for the recovery from packet
Hybrid FEC/ARQ Performance and Audio. Quality over Wireless Links
 Applied Mathematical Sciences, Vol. 4, 200, no. 30, 467-488 Hybrid FEC/ARQ Performance and Audio Quality over Wireless Links Samia Jalil*, Rachid El Azouzi**, Thierry Peyre** & Mohammed Abbad* *Dép. Math-Info,
Applied Mathematical Sciences, Vol. 4, 200, no. 30, 467-488 Hybrid FEC/ARQ Performance and Audio Quality over Wireless Links Samia Jalil*, Rachid El Azouzi**, Thierry Peyre** & Mohammed Abbad* *Dép. Math-Info,
queue KTH, Royal Institute of Technology, Department of Microelectronics and Information Technology
 Analysis of the Packet oss Process in an MMPP+M/M/1/K queue György Dán, Viktória Fodor KTH, Royal Institute of Technology, Department of Microelectronics and Information Technology {gyuri,viktoria}@imit.kth.se
Analysis of the Packet oss Process in an MMPP+M/M/1/K queue György Dán, Viktória Fodor KTH, Royal Institute of Technology, Department of Microelectronics and Information Technology {gyuri,viktoria}@imit.kth.se
Analysis of the Packet Loss Process for Multimedia Traffic
 Analysis of the Packet Loss Process for Multimedia Traffic György Dán, Viktória Fodor and Gunnar Karlsson KTH, Royal Institute of Technology, Department of Microelectronics and Information Technology {gyuri,viktoria,gk}@imit.kth.se
Analysis of the Packet Loss Process for Multimedia Traffic György Dán, Viktória Fodor and Gunnar Karlsson KTH, Royal Institute of Technology, Department of Microelectronics and Information Technology {gyuri,viktoria,gk}@imit.kth.se
Performance Evaluation of Queuing Systems
 Performance Evaluation of Queuing Systems Introduction to Queuing Systems System Performance Measures & Little s Law Equilibrium Solution of Birth-Death Processes Analysis of Single-Station Queuing Systems
Performance Evaluation of Queuing Systems Introduction to Queuing Systems System Performance Measures & Little s Law Equilibrium Solution of Birth-Death Processes Analysis of Single-Station Queuing Systems
Analysis of the Packet Loss Process for Multimedia Traffic
 Analysis of the Packet Loss Process for Multimedia Traffic György Dán, Viktória Fodor and Gunnar Karlsson KTH, Royal Institute of Technology, Department of Microelectronics and Information Technology Electrum
Analysis of the Packet Loss Process for Multimedia Traffic György Dán, Viktória Fodor and Gunnar Karlsson KTH, Royal Institute of Technology, Department of Microelectronics and Information Technology Electrum
Analysis of two competing TCP/IP connections
 Performance Evaluation 49 (2002 43 55 Analysis of two competing TCP/IP connections E. Altman a,b,, T. Jiménez b, R. Núñez-Queija c,d a INRIA, 2004 Route des Lucioles, 06902 Sophia Antipolis, France b CESIMO,
Performance Evaluation 49 (2002 43 55 Analysis of two competing TCP/IP connections E. Altman a,b,, T. Jiménez b, R. Núñez-Queija c,d a INRIA, 2004 Route des Lucioles, 06902 Sophia Antipolis, France b CESIMO,
An Admission Control Mechanism for Providing Service Differentiation in Optical Burst-Switching Networks
 An Admission Control Mechanism for Providing Service Differentiation in Optical Burst-Switching Networks Igor M. Moraes, Daniel de O. Cunha, Marco D. D. Bicudo, Rafael P. Laufer, and Otto Carlos M. B.
An Admission Control Mechanism for Providing Service Differentiation in Optical Burst-Switching Networks Igor M. Moraes, Daniel de O. Cunha, Marco D. D. Bicudo, Rafael P. Laufer, and Otto Carlos M. B.
A Stochastic Model for TCP with Stationary Random Losses
 A Stochastic Model for TCP with Stationary Random Losses Eitan Altman, Kostya Avrachenkov Chadi Barakat INRIA Sophia Antipolis - France ACM SIGCOMM August 31, 2000 Stockholm, Sweden Introduction Outline
A Stochastic Model for TCP with Stationary Random Losses Eitan Altman, Kostya Avrachenkov Chadi Barakat INRIA Sophia Antipolis - France ACM SIGCOMM August 31, 2000 Stockholm, Sweden Introduction Outline
Queueing Theory I Summary! Little s Law! Queueing System Notation! Stationary Analysis of Elementary Queueing Systems " M/M/1 " M/M/m " M/M/1/K "
 Queueing Theory I Summary Little s Law Queueing System Notation Stationary Analysis of Elementary Queueing Systems " M/M/1 " M/M/m " M/M/1/K " Little s Law a(t): the process that counts the number of arrivals
Queueing Theory I Summary Little s Law Queueing System Notation Stationary Analysis of Elementary Queueing Systems " M/M/1 " M/M/m " M/M/1/K " Little s Law a(t): the process that counts the number of arrivals
A Queueing System with Queue Length Dependent Service Times, with Applications to Cell Discarding in ATM Networks
 A Queueing System with Queue Length Dependent Service Times, with Applications to Cell Discarding in ATM Networks by Doo Il Choi, Charles Knessl and Charles Tier University of Illinois at Chicago 85 South
A Queueing System with Queue Length Dependent Service Times, with Applications to Cell Discarding in ATM Networks by Doo Il Choi, Charles Knessl and Charles Tier University of Illinois at Chicago 85 South
TCP modeling in the presence of nonlinear window growth
 TCP modeling in the presence of nonlinear window growth Eitan Altman, Kostia Avrachenkov, Chadi Barakat Rudesindo Núñez-Queija Abstract We develop a model for TCP that accounts for both sublinearity and
TCP modeling in the presence of nonlinear window growth Eitan Altman, Kostia Avrachenkov, Chadi Barakat Rudesindo Núñez-Queija Abstract We develop a model for TCP that accounts for both sublinearity and
ON MAIN CHARACTERISTICS OF THE M/M/1/N QUEUE WITH SINGLE AND BATCH ARRIVALS AND THE QUEUE SIZE CONTROLLED BY AQM ALGORITHMS
 K Y B E R N E T I K A V O L U M E 4 7 ( 2 0 1 1 ), N U M B E R 6, P A G E S 9 3 0 9 4 3 ON MAIN CHARACTERISTICS OF THE M/M/1/N QUEUE WITH SINGLE AND BATCH ARRIVALS AND THE QUEUE SIZE CONTROLLED BY AQM
K Y B E R N E T I K A V O L U M E 4 7 ( 2 0 1 1 ), N U M B E R 6, P A G E S 9 3 0 9 4 3 ON MAIN CHARACTERISTICS OF THE M/M/1/N QUEUE WITH SINGLE AND BATCH ARRIVALS AND THE QUEUE SIZE CONTROLLED BY AQM
Packet Loss Analysis of Load-Balancing Switch with ON/OFF Input Processes
 Packet Loss Analysis of Load-Balancing Switch with ON/OFF Input Processes Yury Audzevich, Levente Bodrog 2, Yoram Ofek, and Miklós Telek 2 Department of Information Engineering and Computer Science, University
Packet Loss Analysis of Load-Balancing Switch with ON/OFF Input Processes Yury Audzevich, Levente Bodrog 2, Yoram Ofek, and Miklós Telek 2 Department of Information Engineering and Computer Science, University
A discrete-time priority queue with train arrivals
 A discrete-time priority queue with train arrivals Joris Walraevens, Sabine Wittevrongel and Herwig Bruneel SMACS Research Group Department of Telecommunications and Information Processing (IR07) Ghent
A discrete-time priority queue with train arrivals Joris Walraevens, Sabine Wittevrongel and Herwig Bruneel SMACS Research Group Department of Telecommunications and Information Processing (IR07) Ghent
Performance Analysis and Evaluation of Digital Connection Oriented Internet Service Systems
 Performance Analysis and Evaluation of Digital Connection Oriented Internet Service Systems Shunfu Jin 1 and Wuyi Yue 2 1 College of Information Science and Engineering Yanshan University, Qinhuangdao
Performance Analysis and Evaluation of Digital Connection Oriented Internet Service Systems Shunfu Jin 1 and Wuyi Yue 2 1 College of Information Science and Engineering Yanshan University, Qinhuangdao
Performance Analysis of Priority Queueing Schemes in Internet Routers
 Conference on Information Sciences and Systems, The Johns Hopkins University, March 8, Performance Analysis of Priority Queueing Schemes in Internet Routers Ashvin Lakshmikantha Coordinated Science Lab
Conference on Information Sciences and Systems, The Johns Hopkins University, March 8, Performance Analysis of Priority Queueing Schemes in Internet Routers Ashvin Lakshmikantha Coordinated Science Lab
M/G/FQ: STOCHASTIC ANALYSIS OF FAIR QUEUEING SYSTEMS
 M/G/FQ: STOCHASTIC ANALYSIS OF FAIR QUEUEING SYSTEMS MOHAMMED HAWA AND DAVID W. PETR Information and Telecommunications Technology Center University of Kansas, Lawrence, Kansas, 66045 email: {hawa, dwp}@ittc.ku.edu
M/G/FQ: STOCHASTIC ANALYSIS OF FAIR QUEUEING SYSTEMS MOHAMMED HAWA AND DAVID W. PETR Information and Telecommunications Technology Center University of Kansas, Lawrence, Kansas, 66045 email: {hawa, dwp}@ittc.ku.edu
Efficient Nonlinear Optimizations of Queuing Systems
 Efficient Nonlinear Optimizations of Queuing Systems Mung Chiang, Arak Sutivong, and Stephen Boyd Electrical Engineering Department, Stanford University, CA 9435 Abstract We present a systematic treatment
Efficient Nonlinear Optimizations of Queuing Systems Mung Chiang, Arak Sutivong, and Stephen Boyd Electrical Engineering Department, Stanford University, CA 9435 Abstract We present a systematic treatment
Asymptotics for Polling Models with Limited Service Policies
 Asymptotics for Polling Models with Limited Service Policies Woojin Chang School of Industrial and Systems Engineering Georgia Institute of Technology Atlanta, GA 30332-0205 USA Douglas G. Down Department
Asymptotics for Polling Models with Limited Service Policies Woojin Chang School of Industrial and Systems Engineering Georgia Institute of Technology Atlanta, GA 30332-0205 USA Douglas G. Down Department
Optimal Association of Stations and APs in an IEEE WLAN
 Optimal Association of Stations and APs in an IEEE 802. WLAN Anurag Kumar and Vinod Kumar Abstract We propose a maximum utility based formulation for the problem of optimal association of wireless stations
Optimal Association of Stations and APs in an IEEE 802. WLAN Anurag Kumar and Vinod Kumar Abstract We propose a maximum utility based formulation for the problem of optimal association of wireless stations
An engineering approximation for the mean waiting time in the M/H 2 b /s queue
 An engineering approximation for the mean waiting time in the M/H b /s queue Francisco Barceló Universidad Politécnica de Catalunya c/ Jordi Girona, -3, Barcelona 08034 Email : barcelo@entel.upc.es Abstract
An engineering approximation for the mean waiting time in the M/H b /s queue Francisco Barceló Universidad Politécnica de Catalunya c/ Jordi Girona, -3, Barcelona 08034 Email : barcelo@entel.upc.es Abstract
6 Solving Queueing Models
 6 Solving Queueing Models 6.1 Introduction In this note we look at the solution of systems of queues, starting with simple isolated queues. The benefits of using predefined, easily classified queues will
6 Solving Queueing Models 6.1 Introduction In this note we look at the solution of systems of queues, starting with simple isolated queues. The benefits of using predefined, easily classified queues will
A Mathematical Model of the Skype VoIP Congestion Control Algorithm
 A Mathematical Model of the Skype VoIP Congestion Control Algorithm Luca De Cicco, S. Mascolo, V. Palmisano Dipartimento di Elettrotecnica ed Elettronica, Politecnico di Bari 47th IEEE Conference on Decision
A Mathematical Model of the Skype VoIP Congestion Control Algorithm Luca De Cicco, S. Mascolo, V. Palmisano Dipartimento di Elettrotecnica ed Elettronica, Politecnico di Bari 47th IEEE Conference on Decision
class class ff ff (t) packet loss packet loss (t) - - RED controlled queue Figure : Illustration of a Differentiad Services framework. RED has been an
 Modeling RED with Two Traffic Classes P. Kuusela and J. T. Virtamo Laboratory of Telecommunications Technology Helsinki University of Technology P. O. Box 3000, FIN-005 HUT, Finland Email: fpirkko.kuusela,
Modeling RED with Two Traffic Classes P. Kuusela and J. T. Virtamo Laboratory of Telecommunications Technology Helsinki University of Technology P. O. Box 3000, FIN-005 HUT, Finland Email: fpirkko.kuusela,
Modelling an Isolated Compound TCP Connection
 Modelling an Isolated Compound TCP Connection Alberto Blanc and Denis Collange Orange Labs 905 rue Albert Einstein Sophia Antipolis, France {Email: alberto.blanc,denis.collange}@orange-ftgroup.com Konstantin
Modelling an Isolated Compound TCP Connection Alberto Blanc and Denis Collange Orange Labs 905 rue Albert Einstein Sophia Antipolis, France {Email: alberto.blanc,denis.collange}@orange-ftgroup.com Konstantin
Burst Scheduling Based on Time-slotting and Fragmentation in WDM Optical Burst Switched Networks
 Burst Scheduling Based on Time-slotting and Fragmentation in WDM Optical Burst Switched Networks G. Mohan, M. Ashish, and K. Akash Department of Electrical and Computer Engineering National University
Burst Scheduling Based on Time-slotting and Fragmentation in WDM Optical Burst Switched Networks G. Mohan, M. Ashish, and K. Akash Department of Electrical and Computer Engineering National University
Analysis of Scalable TCP in the presence of Markovian Losses
 Analysis of Scalable TCP in the presence of Markovian Losses E Altman K E Avrachenkov A A Kherani BJ Prabhu INRIA Sophia Antipolis 06902 Sophia Antipolis, France Email:altman,kavratchenkov,alam,bprabhu}@sophiainriafr
Analysis of Scalable TCP in the presence of Markovian Losses E Altman K E Avrachenkov A A Kherani BJ Prabhu INRIA Sophia Antipolis 06902 Sophia Antipolis, France Email:altman,kavratchenkov,alam,bprabhu}@sophiainriafr
NICTA Short Course. Network Analysis. Vijay Sivaraman. Day 1 Queueing Systems and Markov Chains. Network Analysis, 2008s2 1-1
 NICTA Short Course Network Analysis Vijay Sivaraman Day 1 Queueing Systems and Markov Chains Network Analysis, 2008s2 1-1 Outline Why a short course on mathematical analysis? Limited current course offering
NICTA Short Course Network Analysis Vijay Sivaraman Day 1 Queueing Systems and Markov Chains Network Analysis, 2008s2 1-1 Outline Why a short course on mathematical analysis? Limited current course offering
Link Models for Circuit Switching
 Link Models for Circuit Switching The basis of traffic engineering for telecommunication networks is the Erlang loss function. It basically allows us to determine the amount of telephone traffic that can
Link Models for Circuit Switching The basis of traffic engineering for telecommunication networks is the Erlang loss function. It basically allows us to determine the amount of telephone traffic that can
A Quantitative View: Delay, Throughput, Loss
 A Quantitative View: Delay, Throughput, Loss Antonio Carzaniga Faculty of Informatics University of Lugano September 27, 2017 Outline Quantitative analysis of data transfer concepts for network applications
A Quantitative View: Delay, Throughput, Loss Antonio Carzaniga Faculty of Informatics University of Lugano September 27, 2017 Outline Quantitative analysis of data transfer concepts for network applications
Compound TCP with Random Losses
 Compound TCP with Random Losses Alberto Blanc 1, Konstantin Avrachenkov 2, Denis Collange 1, and Giovanni Neglia 2 1 Orange Labs, 905 rue Albert Einstein, 06921 Sophia Antipolis, France {alberto.blanc,denis.collange}@orange-ftgroup.com
Compound TCP with Random Losses Alberto Blanc 1, Konstantin Avrachenkov 2, Denis Collange 1, and Giovanni Neglia 2 1 Orange Labs, 905 rue Albert Einstein, 06921 Sophia Antipolis, France {alberto.blanc,denis.collange}@orange-ftgroup.com
Resource Allocation for Video Streaming in Wireless Environment
 Resource Allocation for Video Streaming in Wireless Environment Shahrokh Valaee and Jean-Charles Gregoire Abstract This paper focuses on the development of a new resource allocation scheme for video streaming
Resource Allocation for Video Streaming in Wireless Environment Shahrokh Valaee and Jean-Charles Gregoire Abstract This paper focuses on the development of a new resource allocation scheme for video streaming
Min Congestion Control for High- Speed Heterogeneous Networks. JetMax: Scalable Max-Min
 JetMax: Scalable Max-Min Min Congestion Control for High- Speed Heterogeneous Networks Yueping Zhang Joint work with Derek Leonard and Dmitri Loguinov Internet Research Lab Department of Computer Science
JetMax: Scalable Max-Min Min Congestion Control for High- Speed Heterogeneous Networks Yueping Zhang Joint work with Derek Leonard and Dmitri Loguinov Internet Research Lab Department of Computer Science
GI/M/1 and GI/M/m queuing systems
 GI/M/1 and GI/M/m queuing systems Dmitri A. Moltchanov moltchan@cs.tut.fi http://www.cs.tut.fi/kurssit/tlt-2716/ OUTLINE: GI/M/1 queuing system; Methods of analysis; Imbedded Markov chain approach; Waiting
GI/M/1 and GI/M/m queuing systems Dmitri A. Moltchanov moltchan@cs.tut.fi http://www.cs.tut.fi/kurssit/tlt-2716/ OUTLINE: GI/M/1 queuing system; Methods of analysis; Imbedded Markov chain approach; Waiting
Analysis of TCP Westwood+ in high speed networks
 Analysis of TCP Westwood+ in high speed networks 1 E. Altman, C. Barakat, S. Mascolo, N. Möller and J. Sun Abstract TCP Westwood+ is modelled and analyzed using stochastic recursive equations. It is shown
Analysis of TCP Westwood+ in high speed networks 1 E. Altman, C. Barakat, S. Mascolo, N. Möller and J. Sun Abstract TCP Westwood+ is modelled and analyzed using stochastic recursive equations. It is shown
On a Theory of Interacting Queues
 On a Theory of Interacting Queues Alexander Stepanenko, Costas C Constantinou, Theodoros N Arvanitis, and Kevin Baughan School of Electrical, Electronic and Computer Engineering, University of Birmingham,
On a Theory of Interacting Queues Alexander Stepanenko, Costas C Constantinou, Theodoros N Arvanitis, and Kevin Baughan School of Electrical, Electronic and Computer Engineering, University of Birmingham,
BIRTH DEATH PROCESSES AND QUEUEING SYSTEMS
 BIRTH DEATH PROCESSES AND QUEUEING SYSTEMS Andrea Bobbio Anno Accademico 999-2000 Queueing Systems 2 Notation for Queueing Systems /λ mean time between arrivals S = /µ ρ = λ/µ N mean service time traffic
BIRTH DEATH PROCESSES AND QUEUEING SYSTEMS Andrea Bobbio Anno Accademico 999-2000 Queueing Systems 2 Notation for Queueing Systems /λ mean time between arrivals S = /µ ρ = λ/µ N mean service time traffic
Stochastic Network Calculus
 Stochastic Network Calculus Assessing the Performance of the Future Internet Markus Fidler joint work with Amr Rizk Institute of Communications Technology Leibniz Universität Hannover April 22, 2010 c
Stochastic Network Calculus Assessing the Performance of the Future Internet Markus Fidler joint work with Amr Rizk Institute of Communications Technology Leibniz Universität Hannover April 22, 2010 c
CPSC 531: System Modeling and Simulation. Carey Williamson Department of Computer Science University of Calgary Fall 2017
 CPSC 531: System Modeling and Simulation Carey Williamson Department of Computer Science University of Calgary Fall 2017 Motivating Quote for Queueing Models Good things come to those who wait - poet/writer
CPSC 531: System Modeling and Simulation Carey Williamson Department of Computer Science University of Calgary Fall 2017 Motivating Quote for Queueing Models Good things come to those who wait - poet/writer
M/G/1/MLPS compared to M/G/1/PS
 Operations Research Letters 33 (25) 519 524 Operations Research Letters www.elsevier.com/locate/orl M/G/1/MLPS compared to M/G/1/PS Samuli Aalto a,, Urtzi Ayesta b, Eeva Nyberg-Oksanen a,1 a Networking
Operations Research Letters 33 (25) 519 524 Operations Research Letters www.elsevier.com/locate/orl M/G/1/MLPS compared to M/G/1/PS Samuli Aalto a,, Urtzi Ayesta b, Eeva Nyberg-Oksanen a,1 a Networking
THE prediction of network behavior is an important task for
 TCP Networ Calculus: The case of large delay-bandwidth product Eitan Altman, Konstantin Avrachenov, Chadi Baraat Abstract We present in this paper an analytical model for the calculation of networ load
TCP Networ Calculus: The case of large delay-bandwidth product Eitan Altman, Konstantin Avrachenov, Chadi Baraat Abstract We present in this paper an analytical model for the calculation of networ load
Queueing Networks G. Rubino INRIA / IRISA, Rennes, France
 Queueing Networks G. Rubino INRIA / IRISA, Rennes, France February 2006 Index 1. Open nets: Basic Jackson result 2 2. Open nets: Internet performance evaluation 18 3. Closed nets: Basic Gordon-Newell result
Queueing Networks G. Rubino INRIA / IRISA, Rennes, France February 2006 Index 1. Open nets: Basic Jackson result 2 2. Open nets: Internet performance evaluation 18 3. Closed nets: Basic Gordon-Newell result
Link Models for Packet Switching
 Link Models for Packet Switching To begin our study of the performance of communications networks, we will study a model of a single link in a message switched network. The important feature of this model
Link Models for Packet Switching To begin our study of the performance of communications networks, we will study a model of a single link in a message switched network. The important feature of this model
On Tandem Blocking Queues with a Common Retrial Queue
 On Tandem Blocking Queues with a Common Retrial Queue K. Avrachenkov U. Yechiali Abstract We consider systems of tandem blocking queues having a common retrial queue. The model represents dynamics of short
On Tandem Blocking Queues with a Common Retrial Queue K. Avrachenkov U. Yechiali Abstract We consider systems of tandem blocking queues having a common retrial queue. The model represents dynamics of short
Sensitivity Analysis for Discrete-Time Randomized Service Priority Queues
 Sensitivity Analysis for Discrete-Time Randomized Service Priority Queues George Kesidis 1, Takis Konstantopoulos 2, Michael Zazanis 3 1. Elec. & Comp. Eng. Dept, University of Waterloo, Waterloo, ON,
Sensitivity Analysis for Discrete-Time Randomized Service Priority Queues George Kesidis 1, Takis Konstantopoulos 2, Michael Zazanis 3 1. Elec. & Comp. Eng. Dept, University of Waterloo, Waterloo, ON,
CDA5530: Performance Models of Computers and Networks. Chapter 4: Elementary Queuing Theory
 CDA5530: Performance Models of Computers and Networks Chapter 4: Elementary Queuing Theory Definition Queuing system: a buffer (waiting room), service facility (one or more servers) a scheduling policy
CDA5530: Performance Models of Computers and Networks Chapter 4: Elementary Queuing Theory Definition Queuing system: a buffer (waiting room), service facility (one or more servers) a scheduling policy
Solutions to COMP9334 Week 8 Sample Problems
 Solutions to COMP9334 Week 8 Sample Problems Problem 1: Customers arrive at a grocery store s checkout counter according to a Poisson process with rate 1 per minute. Each customer carries a number of items
Solutions to COMP9334 Week 8 Sample Problems Problem 1: Customers arrive at a grocery store s checkout counter according to a Poisson process with rate 1 per minute. Each customer carries a number of items
Compound TCP with Random Losses
 Compound TCP with Random Losses Alberto Blanc 1, Konstantin Avrachenkov 2, Denis Collange 1, and Giovanni Neglia 2 1 Orange Labs, 905 rue Albert Einstein, 06921 Sophia Antipolis, France {alberto.blanc,denis.collange}@orange-ftgroup.com
Compound TCP with Random Losses Alberto Blanc 1, Konstantin Avrachenkov 2, Denis Collange 1, and Giovanni Neglia 2 1 Orange Labs, 905 rue Albert Einstein, 06921 Sophia Antipolis, France {alberto.blanc,denis.collange}@orange-ftgroup.com
A Retrial Queueing model with FDL at OBS core node
 A Retrial Queueing model with FDL at OBS core node Chuong Dang Thanh a, Duc Pham Trung a, Thang Doan Van b a Faculty of Information Technology, College of Sciences, Hue University, Hue, Viet Nam. E-mail:
A Retrial Queueing model with FDL at OBS core node Chuong Dang Thanh a, Duc Pham Trung a, Thang Doan Van b a Faculty of Information Technology, College of Sciences, Hue University, Hue, Viet Nam. E-mail:
Optimal Measurement-based Pricing for an M/M/1 Queue
 Optimal Measurement-based Pricing for an M/M/1 Queue Yezekael Hayel 1 and Bruno Tuffin 1 IRISA-INRIA Rennes, Campus universitaire de Beaulieu 3542 Rennes Cedex - FRANCE {yhayel,btuffin}@irisa.fr tel: (+33)299847134
Optimal Measurement-based Pricing for an M/M/1 Queue Yezekael Hayel 1 and Bruno Tuffin 1 IRISA-INRIA Rennes, Campus universitaire de Beaulieu 3542 Rennes Cedex - FRANCE {yhayel,btuffin}@irisa.fr tel: (+33)299847134
Introduction to queuing theory
 Introduction to queuing theory Claude Rigault ENST claude.rigault@enst.fr Introduction to Queuing theory 1 Outline The problem The number of clients in a system The client process Delay processes Loss
Introduction to queuing theory Claude Rigault ENST claude.rigault@enst.fr Introduction to Queuing theory 1 Outline The problem The number of clients in a system The client process Delay processes Loss
Queuing Networks: Burke s Theorem, Kleinrock s Approximation, and Jackson s Theorem. Wade Trappe
 Queuing Networks: Burke s Theorem, Kleinrock s Approximation, and Jackson s Theorem Wade Trappe Lecture Overview Network of Queues Introduction Queues in Tandem roduct Form Solutions Burke s Theorem What
Queuing Networks: Burke s Theorem, Kleinrock s Approximation, and Jackson s Theorem Wade Trappe Lecture Overview Network of Queues Introduction Queues in Tandem roduct Form Solutions Burke s Theorem What
Delay characteristics in discrete-time GI-G-1 queues with non-preemptive priority queueing discipline
 Delay characteristics in discrete-time GI-G-1 queues with non-preemptive priority queueing discipline Joris Walraevens, Bart Steyaert, Herwig Bruneel SMACS Research Group, University of Ghent, Vakgroep
Delay characteristics in discrete-time GI-G-1 queues with non-preemptive priority queueing discipline Joris Walraevens, Bart Steyaert, Herwig Bruneel SMACS Research Group, University of Ghent, Vakgroep
The Burstiness Behavior of Regulated Flows in Networks
 The Burstiness Behavior of Regulated Flows in Networks Yu Ying 1, Ravi Mazumdar 2, Catherine Rosenberg 2 and Fabrice Guillemin 3 1 Dept. of ECE, Purdue University, West Lafayette, IN, 47906, U.S.A. yingy@ecn.purdue.edu
The Burstiness Behavior of Regulated Flows in Networks Yu Ying 1, Ravi Mazumdar 2, Catherine Rosenberg 2 and Fabrice Guillemin 3 1 Dept. of ECE, Purdue University, West Lafayette, IN, 47906, U.S.A. yingy@ecn.purdue.edu
CHAPTER 4. Networks of queues. 1. Open networks Suppose that we have a network of queues as given in Figure 4.1. Arrivals
 CHAPTER 4 Networks of queues. Open networks Suppose that we have a network of queues as given in Figure 4.. Arrivals Figure 4.. An open network can occur from outside of the network to any subset of nodes.
CHAPTER 4 Networks of queues. Open networks Suppose that we have a network of queues as given in Figure 4.. Arrivals Figure 4.. An open network can occur from outside of the network to any subset of nodes.
Modelling the Arrival Process for Packet Audio
 Modelling the Arrival Process for Packet Audio Ingemar Kaj and Ian Marsh 2 Dept. of Mathematics, Uppsala University, Sweden ikaj@math.uu.se 2 SICS AB, Stockholm, Sweden ianm@sics.se Abstract. Packets in
Modelling the Arrival Process for Packet Audio Ingemar Kaj and Ian Marsh 2 Dept. of Mathematics, Uppsala University, Sweden ikaj@math.uu.se 2 SICS AB, Stockholm, Sweden ianm@sics.se Abstract. Packets in
P e = 0.1. P e = 0.01
 23 10 0 10-2 P e = 0.1 Deadline Failure Probability 10-4 10-6 10-8 P e = 0.01 10-10 P e = 0.001 10-12 10 11 12 13 14 15 16 Number of Slots in a Frame Fig. 10. The deadline failure probability as a function
23 10 0 10-2 P e = 0.1 Deadline Failure Probability 10-4 10-6 10-8 P e = 0.01 10-10 P e = 0.001 10-12 10 11 12 13 14 15 16 Number of Slots in a Frame Fig. 10. The deadline failure probability as a function
Capacity management for packet-switched networks with heterogeneous sources. Linda de Jonge. Master Thesis July 29, 2009.
 Capacity management for packet-switched networks with heterogeneous sources Linda de Jonge Master Thesis July 29, 2009 Supervisors Dr. Frank Roijers Prof. dr. ir. Sem Borst Dr. Andreas Löpker Industrial
Capacity management for packet-switched networks with heterogeneous sources Linda de Jonge Master Thesis July 29, 2009 Supervisors Dr. Frank Roijers Prof. dr. ir. Sem Borst Dr. Andreas Löpker Industrial
2905 Queueing Theory and Simulation PART III: HIGHER DIMENSIONAL AND NON-MARKOVIAN QUEUES
 295 Queueing Theory and Simulation PART III: HIGHER DIMENSIONAL AND NON-MARKOVIAN QUEUES 16 Queueing Systems with Two Types of Customers In this section, we discuss queueing systems with two types of customers.
295 Queueing Theory and Simulation PART III: HIGHER DIMENSIONAL AND NON-MARKOVIAN QUEUES 16 Queueing Systems with Two Types of Customers In this section, we discuss queueing systems with two types of customers.
CHAPTER 14. Quantifying the Quality of Audio and Video Transmissions over the Internet: The PSQA Approach. Gerardo Rubino
 CHAPTER 14 Quantifying the Quality of Audio and Video Transmissions over the Internet: The PSQA Approach Gerardo Rubino INRIA / IRISA, Campus de Beaulieu 35042 Rennes Cedex, France E-mail: rubino@irisa.fr
CHAPTER 14 Quantifying the Quality of Audio and Video Transmissions over the Internet: The PSQA Approach Gerardo Rubino INRIA / IRISA, Campus de Beaulieu 35042 Rennes Cedex, France E-mail: rubino@irisa.fr
Inequality Comparisons and Traffic Smoothing in Multi-Stage ATM Multiplexers
 IEEE Proceedings of the International Conference on Communications, 2000 Inequality Comparisons and raffic Smoothing in Multi-Stage AM Multiplexers Michael J. Neely MI -- LIDS mjneely@mit.edu Abstract
IEEE Proceedings of the International Conference on Communications, 2000 Inequality Comparisons and raffic Smoothing in Multi-Stage AM Multiplexers Michael J. Neely MI -- LIDS mjneely@mit.edu Abstract
A Direct Approach to Transient Queue-Size Distribution in a Finite-Buffer Queue with AQM
 Appl. Math. Inf. Sci. 7, No. 3, 99-915 (213) 99 Applied Mathematics & Information Sciences An International Journal A Direct Approach to Transient Queue-Size Distribution in a Finite-Buffer Queue with
Appl. Math. Inf. Sci. 7, No. 3, 99-915 (213) 99 Applied Mathematics & Information Sciences An International Journal A Direct Approach to Transient Queue-Size Distribution in a Finite-Buffer Queue with
Lecture 7: Simulation of Markov Processes. Pasi Lassila Department of Communications and Networking
 Lecture 7: Simulation of Markov Processes Pasi Lassila Department of Communications and Networking Contents Markov processes theory recap Elementary queuing models for data networks Simulation of Markov
Lecture 7: Simulation of Markov Processes Pasi Lassila Department of Communications and Networking Contents Markov processes theory recap Elementary queuing models for data networks Simulation of Markov
Asymptotic Delay Distribution and Burst Size Impact on a Network Node Driven by Self-similar Traffic
 Èíôîðìàöèîííûå ïðîöåññû, Òîì 5, 1, 2005, ñòð. 4046. c 2004 D'Apice, Manzo. INFORMATION THEORY AND INFORMATION PROCESSING Asymptotic Delay Distribution and Burst Size Impact on a Network Node Driven by
Èíôîðìàöèîííûå ïðîöåññû, Òîì 5, 1, 2005, ñòð. 4046. c 2004 D'Apice, Manzo. INFORMATION THEORY AND INFORMATION PROCESSING Asymptotic Delay Distribution and Burst Size Impact on a Network Node Driven by
LIMITS FOR QUEUES AS THE WAITING ROOM GROWS. Bell Communications Research AT&T Bell Laboratories Red Bank, NJ Murray Hill, NJ 07974
 LIMITS FOR QUEUES AS THE WAITING ROOM GROWS by Daniel P. Heyman Ward Whitt Bell Communications Research AT&T Bell Laboratories Red Bank, NJ 07701 Murray Hill, NJ 07974 May 11, 1988 ABSTRACT We study the
LIMITS FOR QUEUES AS THE WAITING ROOM GROWS by Daniel P. Heyman Ward Whitt Bell Communications Research AT&T Bell Laboratories Red Bank, NJ 07701 Murray Hill, NJ 07974 May 11, 1988 ABSTRACT We study the
Nash Equilibria for Combined Flow Control and Routing in Networks: Asymptotic Behavior for a Large Number of Users
 IEEE TRANSACTIONS ON AUTOMATIC CONTROL, VOL. 47, NO. 6, JUNE 2002 917 Nash Equilibria for Combined Flow Control and Routing in Networks: Asymptotic Behavior for a Large Number of Users Eitan Altman, Senior
IEEE TRANSACTIONS ON AUTOMATIC CONTROL, VOL. 47, NO. 6, JUNE 2002 917 Nash Equilibria for Combined Flow Control and Routing in Networks: Asymptotic Behavior for a Large Number of Users Eitan Altman, Senior
Performance analysis of IEEE WLANs with saturated and unsaturated sources
 Performance analysis of IEEE 82.11 WLANs with saturated and unsaturated sources Suong H. Nguyen, Hai L. Vu, Lachlan L. H. Andrew Centre for Advanced Internet Architectures, Technical Report 11811A Swinburne
Performance analysis of IEEE 82.11 WLANs with saturated and unsaturated sources Suong H. Nguyen, Hai L. Vu, Lachlan L. H. Andrew Centre for Advanced Internet Architectures, Technical Report 11811A Swinburne
On Tandem Blocking Queues with a Common Retrial Queue
 On Tandem Blocking Queues with a Common Retrial Queue K. Avrachenkov U. Yechiali Abstract We consider systems of tandem blocking queues having a common retrial queue, for which explicit analytic results
On Tandem Blocking Queues with a Common Retrial Queue K. Avrachenkov U. Yechiali Abstract We consider systems of tandem blocking queues having a common retrial queue, for which explicit analytic results
Chapter 5. Elementary Performance Analysis
 Chapter 5 Elementary Performance Analysis 1 5.0 2 5.1 Ref: Mischa Schwartz Telecommunication Networks Addison-Wesley publishing company 1988 3 4 p t T m T P(k)= 5 6 5.2 : arrived rate : service rate 7
Chapter 5 Elementary Performance Analysis 1 5.0 2 5.1 Ref: Mischa Schwartz Telecommunication Networks Addison-Wesley publishing company 1988 3 4 p t T m T P(k)= 5 6 5.2 : arrived rate : service rate 7
Introduction to Markov Chains, Queuing Theory, and Network Performance
 Introduction to Markov Chains, Queuing Theory, and Network Performance Marceau Coupechoux Telecom ParisTech, departement Informatique et Réseaux marceau.coupechoux@telecom-paristech.fr IT.2403 Modélisation
Introduction to Markov Chains, Queuing Theory, and Network Performance Marceau Coupechoux Telecom ParisTech, departement Informatique et Réseaux marceau.coupechoux@telecom-paristech.fr IT.2403 Modélisation
AN increasing number of multimedia applications require. Streaming Codes with Partial Recovery over Channels with Burst and Isolated Erasures
 1 Streaming Codes with Partial Recovery over Channels with Burst and Isolated Erasures Ahmed Badr, Student Member, IEEE, Ashish Khisti, Member, IEEE, Wai-Tian Tan, Member IEEE and John Apostolopoulos,
1 Streaming Codes with Partial Recovery over Channels with Burst and Isolated Erasures Ahmed Badr, Student Member, IEEE, Ashish Khisti, Member, IEEE, Wai-Tian Tan, Member IEEE and John Apostolopoulos,
Multiaccess Problem. How to let distributed users (efficiently) share a single broadcast channel? How to form a queue for distributed users?
 Multiaccess Problem How to let distributed users (efficiently) share a single broadcast channel? How to form a queue for distributed users? z The protocols we used to solve this multiaccess problem are
Multiaccess Problem How to let distributed users (efficiently) share a single broadcast channel? How to form a queue for distributed users? z The protocols we used to solve this multiaccess problem are
A Virtual Queue Approach to Loss Estimation
 A Virtual Queue Approach to Loss Estimation Guoqiang Hu, Yuming Jiang, Anne Nevin Centre for Quantifiable Quality of Service in Communication Systems Norwegian University of Science and Technology, Norway
A Virtual Queue Approach to Loss Estimation Guoqiang Hu, Yuming Jiang, Anne Nevin Centre for Quantifiable Quality of Service in Communication Systems Norwegian University of Science and Technology, Norway
Chapter 1. Introduction. 1.1 Stochastic process
 Chapter 1 Introduction Process is a phenomenon that takes place in time. In many practical situations, the result of a process at any time may not be certain. Such a process is called a stochastic process.
Chapter 1 Introduction Process is a phenomenon that takes place in time. In many practical situations, the result of a process at any time may not be certain. Such a process is called a stochastic process.
Intro Refresher Reversibility Open networks Closed networks Multiclass networks Other networks. Queuing Networks. Florence Perronnin
 Queuing Networks Florence Perronnin Polytech Grenoble - UGA March 23, 27 F. Perronnin (UGA) Queuing Networks March 23, 27 / 46 Outline Introduction to Queuing Networks 2 Refresher: M/M/ queue 3 Reversibility
Queuing Networks Florence Perronnin Polytech Grenoble - UGA March 23, 27 F. Perronnin (UGA) Queuing Networks March 23, 27 / 46 Outline Introduction to Queuing Networks 2 Refresher: M/M/ queue 3 Reversibility
CS 798: Homework Assignment 3 (Queueing Theory)
 1.0 Little s law Assigned: October 6, 009 Patients arriving to the emergency room at the Grand River Hospital have a mean waiting time of three hours. It has been found that, averaged over the period of
1.0 Little s law Assigned: October 6, 009 Patients arriving to the emergency room at the Grand River Hospital have a mean waiting time of three hours. It has been found that, averaged over the period of
Decodability Analysis of Finite Memory Random Linear Coding in Line Networks
 Decodability Analysis of Finite Memory Random Linear Coding in Line Networks Nima Torabkhani, Faramarz Fekri School of Electrical and Computer Engineering Georgia Institute of Technology, Atlanta GA 30332,
Decodability Analysis of Finite Memory Random Linear Coding in Line Networks Nima Torabkhani, Faramarz Fekri School of Electrical and Computer Engineering Georgia Institute of Technology, Atlanta GA 30332,
A Stochastic Model of TCP/IP with Stationary Random Losses
 1 A Stochastic Model of TCP/IP with Stationary Random Losses Eitan Altman, Konstantin Avrachenkov, Chadi Barakat INRIA, 24 route des Lucioles, 692 Sophia Antipolis, France Email:{altman,kavratch,cbarakat}@sophiainriafr
1 A Stochastic Model of TCP/IP with Stationary Random Losses Eitan Altman, Konstantin Avrachenkov, Chadi Barakat INRIA, 24 route des Lucioles, 692 Sophia Antipolis, France Email:{altman,kavratch,cbarakat}@sophiainriafr
Lecture 20: Reversible Processes and Queues
 Lecture 20: Reversible Processes and Queues 1 Examples of reversible processes 11 Birth-death processes We define two non-negative sequences birth and death rates denoted by {λ n : n N 0 } and {µ n : n
Lecture 20: Reversible Processes and Queues 1 Examples of reversible processes 11 Birth-death processes We define two non-negative sequences birth and death rates denoted by {λ n : n N 0 } and {µ n : n
Computer Networks More general queuing systems
 Computer Networks More general queuing systems Saad Mneimneh Computer Science Hunter College of CUNY New York M/G/ Introduction We now consider a queuing system where the customer service times have a
Computer Networks More general queuing systems Saad Mneimneh Computer Science Hunter College of CUNY New York M/G/ Introduction We now consider a queuing system where the customer service times have a
Real-Time Status Updating: Multiple Sources
 Real-Time Status Updating: Multiple Sources Roy D. Yates WINLAB, ECE Dept. Rutgers University email: ryates@winlab.rutgers.edu Sanjit Kaul IIIT-Delhi email: skkaul@iiitd.ac.in Abstract We examine multiple
Real-Time Status Updating: Multiple Sources Roy D. Yates WINLAB, ECE Dept. Rutgers University email: ryates@winlab.rutgers.edu Sanjit Kaul IIIT-Delhi email: skkaul@iiitd.ac.in Abstract We examine multiple
Analysis of TCP-AQM Interaction via Periodic Optimization and Linear Programming: The Case of Sigmoidal Utility Function
 Analysis of TCP-AQM Interaction via Periodic Optimization and Linear Programming: The Case of Sigmoidal Utility Function K. Avrachenkov 1, L. Finlay 2, and V. Gaitsgory 2 1 INRIA Sophia Antipolis, France
Analysis of TCP-AQM Interaction via Periodic Optimization and Linear Programming: The Case of Sigmoidal Utility Function K. Avrachenkov 1, L. Finlay 2, and V. Gaitsgory 2 1 INRIA Sophia Antipolis, France
CSE 4201, Ch. 6. Storage Systems. Hennessy and Patterson
 CSE 4201, Ch. 6 Storage Systems Hennessy and Patterson Challenge to the Disk The graveyard is full of suitors Ever heard of Bubble Memory? There are some technologies that refuse to die (silicon, copper...).
CSE 4201, Ch. 6 Storage Systems Hennessy and Patterson Challenge to the Disk The graveyard is full of suitors Ever heard of Bubble Memory? There are some technologies that refuse to die (silicon, copper...).
On Burst Assembly in Optical Burst Switching Networks A Performance Evaluation of Just-Enough-Time
 in: Proceedings of the 7th International Teletraffic Congress, Salvador, Brazil, September 24-28, 2 On Burst Assembly in Optical Burst Switching Networks A Performance Evaluation of Just-Enough-Time K.
in: Proceedings of the 7th International Teletraffic Congress, Salvador, Brazil, September 24-28, 2 On Burst Assembly in Optical Burst Switching Networks A Performance Evaluation of Just-Enough-Time K.
An M/M/1 Queue in Random Environment with Disasters
 An M/M/1 Queue in Random Environment with Disasters Noam Paz 1 and Uri Yechiali 1,2 1 Department of Statistics and Operations Research School of Mathematical Sciences Tel Aviv University, Tel Aviv 69978,
An M/M/1 Queue in Random Environment with Disasters Noam Paz 1 and Uri Yechiali 1,2 1 Department of Statistics and Operations Research School of Mathematical Sciences Tel Aviv University, Tel Aviv 69978,
The Effective Bandwidth of Markov Modulated Fluid Process Sources with a Generalized Processor Sharing Server
 The Effective Bandwidth of Markov Modulated Fluid Process Sources with a Generalized Processor Sharing Server Shiwen Mao Shivendra S. Panwar Dept. of ECE, Polytechnic University, 6 MetroTech Center, Brooklyn,
The Effective Bandwidth of Markov Modulated Fluid Process Sources with a Generalized Processor Sharing Server Shiwen Mao Shivendra S. Panwar Dept. of ECE, Polytechnic University, 6 MetroTech Center, Brooklyn,
Homework 1 - SOLUTION
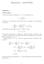 Homework - SOLUTION Problem M/M/ Queue ) Use the fact above to express π k, k > 0, as a function of π 0. π k = ( ) k λ π 0 µ 2) Using λ < µ and the fact that all π k s sum to, compute π 0 (as a function
Homework - SOLUTION Problem M/M/ Queue ) Use the fact above to express π k, k > 0, as a function of π 0. π k = ( ) k λ π 0 µ 2) Using λ < µ and the fact that all π k s sum to, compute π 0 (as a function
CS418 Operating Systems
 CS418 Operating Systems Lecture 14 Queuing Analysis Textbook: Operating Systems by William Stallings 1 1. Why Queuing Analysis? If the system environment changes (like the number of users is doubled),
CS418 Operating Systems Lecture 14 Queuing Analysis Textbook: Operating Systems by William Stallings 1 1. Why Queuing Analysis? If the system environment changes (like the number of users is doubled),
Chapter 3 Balance equations, birth-death processes, continuous Markov Chains
 Chapter 3 Balance equations, birth-death processes, continuous Markov Chains Ioannis Glaropoulos November 4, 2012 1 Exercise 3.2 Consider a birth-death process with 3 states, where the transition rate
Chapter 3 Balance equations, birth-death processes, continuous Markov Chains Ioannis Glaropoulos November 4, 2012 1 Exercise 3.2 Consider a birth-death process with 3 states, where the transition rate
On the Pathwise Optimal Bernoulli Routing Policy for Homogeneous Parallel Servers
 On the Pathwise Optimal Bernoulli Routing Policy for Homogeneous Parallel Servers Ger Koole INRIA Sophia Antipolis B.P. 93, 06902 Sophia Antipolis Cedex France Mathematics of Operations Research 21:469
On the Pathwise Optimal Bernoulli Routing Policy for Homogeneous Parallel Servers Ger Koole INRIA Sophia Antipolis B.P. 93, 06902 Sophia Antipolis Cedex France Mathematics of Operations Research 21:469
Equivalent Models and Analysis for Multi-Stage Tree Networks of Deterministic Service Time Queues
 Proceedings of the 38th Annual Allerton Conference on Communication, Control, and Computing, Oct. 2000. Equivalent Models and Analysis for Multi-Stage ree Networks of Deterministic Service ime Queues Michael
Proceedings of the 38th Annual Allerton Conference on Communication, Control, and Computing, Oct. 2000. Equivalent Models and Analysis for Multi-Stage ree Networks of Deterministic Service ime Queues Michael
Design of IP networks with Quality of Service
 Course of Multimedia Internet (Sub-course Reti Internet Multimediali ), AA 2010-2011 Prof. Pag. 1 Design of IP networks with Quality of Service 1 Course of Multimedia Internet (Sub-course Reti Internet
Course of Multimedia Internet (Sub-course Reti Internet Multimediali ), AA 2010-2011 Prof. Pag. 1 Design of IP networks with Quality of Service 1 Course of Multimedia Internet (Sub-course Reti Internet
A Measurement-Analytic Approach for QoS Estimation in a Network Based on the Dominant Time Scale
 222 IEEE/ACM TRANSACTIONS ON NETWORKING, VOL. 11, NO. 2, APRIL 2003 A Measurement-Analytic Approach for QoS Estimation in a Network Based on the Dominant Time Scale Do Young Eun and Ness B. Shroff, Senior
222 IEEE/ACM TRANSACTIONS ON NETWORKING, VOL. 11, NO. 2, APRIL 2003 A Measurement-Analytic Approach for QoS Estimation in a Network Based on the Dominant Time Scale Do Young Eun and Ness B. Shroff, Senior
Transient Behaviors of TCP-friendly Congestion Control Protocols
 Abbreviated version in Proceedings of IEEE INFOCOM 21, April 21. Transient Behaviors of -friendly Congestion Control Protocols Y. Richard Yang, Min Sik Kim, Simon S. Lam Department of Computer Sciences
Abbreviated version in Proceedings of IEEE INFOCOM 21, April 21. Transient Behaviors of -friendly Congestion Control Protocols Y. Richard Yang, Min Sik Kim, Simon S. Lam Department of Computer Sciences
Discrete-event simulations
 Discrete-event simulations Lecturer: Dmitri A. Moltchanov E-mail: moltchan@cs.tut.fi http://www.cs.tut.fi/kurssit/elt-53606/ OUTLINE: Why do we need simulations? Step-by-step simulations; Classifications;
Discrete-event simulations Lecturer: Dmitri A. Moltchanov E-mail: moltchan@cs.tut.fi http://www.cs.tut.fi/kurssit/elt-53606/ OUTLINE: Why do we need simulations? Step-by-step simulations; Classifications;
Internet Traffic Modeling and Its Implications to Network Performance and Control
 Internet Traffic Modeling and Its Implications to Network Performance and Control Kihong Park Department of Computer Sciences Purdue University park@cs.purdue.edu Outline! Motivation! Traffic modeling!
Internet Traffic Modeling and Its Implications to Network Performance and Control Kihong Park Department of Computer Sciences Purdue University park@cs.purdue.edu Outline! Motivation! Traffic modeling!
ABSTRACT. We investigate the routing and performance of sparse crossbar packet concentrators
 ABSTRACT Title of Thesis: ON ROUTING AND PERFORMANCE EVALUATION OF BUFFERED SPARSE CROSSBAR CONCENTRA- TORS Degree candidate: Rahul Ratan Degree and year: Master of Science, 2002 Thesis directed by: Professor
ABSTRACT Title of Thesis: ON ROUTING AND PERFORMANCE EVALUATION OF BUFFERED SPARSE CROSSBAR CONCENTRA- TORS Degree candidate: Rahul Ratan Degree and year: Master of Science, 2002 Thesis directed by: Professor
Queueing Theory II. Summary. ! M/M/1 Output process. ! Networks of Queue! Method of Stages. ! General Distributions
 Queueing Theory II Summary! M/M/1 Output process! Networks of Queue! Method of Stages " Erlang Distribution " Hyperexponential Distribution! General Distributions " Embedded Markov Chains M/M/1 Output
Queueing Theory II Summary! M/M/1 Output process! Networks of Queue! Method of Stages " Erlang Distribution " Hyperexponential Distribution! General Distributions " Embedded Markov Chains M/M/1 Output
OPTIMALITY OF RANDOMIZED TRUNK RESERVATION FOR A PROBLEM WITH MULTIPLE CONSTRAINTS
 OPTIMALITY OF RANDOMIZED TRUNK RESERVATION FOR A PROBLEM WITH MULTIPLE CONSTRAINTS Xiaofei Fan-Orzechowski Department of Applied Mathematics and Statistics State University of New York at Stony Brook Stony
OPTIMALITY OF RANDOMIZED TRUNK RESERVATION FOR A PROBLEM WITH MULTIPLE CONSTRAINTS Xiaofei Fan-Orzechowski Department of Applied Mathematics and Statistics State University of New York at Stony Brook Stony
