Managing a Large Database of Camera Fingerprints
|
|
|
- Ashlyn Foster
- 6 years ago
- Views:
Transcription
1 Managing a Large Database of Camera Fingerprints Miroslav Goljan, Jessica Fridrich, Tomáš Filler Department of Electrical and Computer Engineering State University of New Yor, Binghamton, New Yor, {mgoljan,fridrich,tfiller}@binghamton.edu ABSTRACT Sensor fingerprint is a unique noise-lie pattern caused by slightly varying pixel dimensions and inhomogeneity of the silicon wafer from which the sensor is made. The fingerprint can be used to prove that an image came from a specific digital camera. The presence of a camera fingerprint in an image is usually established using a detector that evaluates cross-correlation between the fingerprint and image noise. The complexity of the detector is thus proportional to the number of pixels in the image. Although computing the detector statistic for a few megapixel image taes several seconds on a single-processor PC, the processing time becomes impractically large if a sizeable database of camera fingerprints needs to be searched through. In this paper, we present a fast searching algorithm that utilizes special fingerprint digests and sparse data structures to address several tass that forensic analysts will find useful when deploying camera identification from fingerprints in practice. In particular, we develop fast algorithms for finding if a given fingerprint already resides in the database and for determining whether a given image was taen by a camera whose fingerprint is in the database. Keywords: Camera identification, image forensics, sensor fingerprint, fast search, image database.. INTRODUCTION Systematic artifacts of imaging sensors can be used as their unique identifiers (fingerprints) for various forensic tass, such as verifying digital media origin or their integrity. The basis of the recently proposed camera fingerprint is the Photo-Response Non-Uniformity (PRNU). The PRNU signal is caused by slightly varying pixel dimensions and inhomogeneity of the silicon wafer from which the sensor is made. Each image/video produced by the same sensor is overlaid with the same noise-lie pattern, which is modulated by the scene light intensity. To provide evidence that a given image was taen by a certain camera, the image is shown to contain the camera fingerprint. References [ 5] describe the camera identification process in more detail. Anticipating future use of camera identification from sensor fingerprint by law enforcement and government, we visualize a situation when a large database of N fingerprints is queried whether it already contains a given fingerprint or whether it contains a fingerprint of the camera that too a given query image. The search is a multiple-hypothesis testing problem with a correlation detector applied to each fingerprint from the database. The complexity of this direct brute-force search is O(nN), where n is the number of pixels in each image/fingerprint. Considering the fact that most cameras today have n > 0 6 pixels and that there could be tens of thousands of fingerprints in the database (N > 0 4 ), the cost of the direct search could become prohibitively large. To provide forensic investigators with operability, flexibility, and ease of use, we develop fast algorithms for finding a given fingerprint in a database of fingerprints and for determining whether a given image was taen a by a camera whose fingerprint resides in the database. In the first case, we match a given fingerprint to other fingerprints, while the second tas consists of matching a noise residual to fingerprints. Note that there is not really a fundamental difference between these two tass as the noise residual from a single image can be considered as a poor-quality fingerprint. Because the correlation detector has been established as an approximate version of the generalized lielihood ratio test for the problem of detecting the presence of the fingerprint, reducing the computation time by further simplifying the detector will liely increase the probability of an erroneous decision. Thus, this direction is not pursued in this paper. Instead, we focus on finding a reasonable trade-off between the probability of identification (when the camera fingerprint is contained in the database) and the speed/memory requirements of the search. Interestingly, it is not
2 necessary to have a low false-alarm rate because the correlation detector can be run as a double chec on all fingerprints identified as candidates by the search. Too many candidate fingerprints, however, would slow down the search. In the next section, we introduce the notation, terminology, and some bacground material pertaining to camera identification using sensor noise. Section 3 contains a discussion of several possible strategies that one might use to decrease the computational complexity of the fingerprint search. By analyzing their wea points, we arrive at the fingerprint digest, a ey concept based on which the fast search algorithm is constructed. The algorithm itself is detailed in Section 4. Experimental tests of the proposed search algorithm are included in Section 5, where we evaluate the time needed to find a fingerprint in the database and the time to determine that a fingerprint is not present in the database. This section also analyzes the effect of the search on identification errors when compared to the direct brute-force search. The paper is concluded in Section 6.. PRELIMINARIES In this section, we introduce the basic notation, terminology, and some bacground material. Vectors and matrices will be always in bold upright font. Sometimes, we will index a matrix with a one-dimensional index, in which case it is assumed that the matrix has been converted to a vector, for example, by rows. Unless stated otherwise, all operations between vectors/matrices are understood as element-wise. Denoting the dot product of X and Y as n X Y= [] i [] i, i = X Y X = X X is the norm of X, and X the sample mean. The normalized correlation is ( X X) ( Y Y) corr( XY, ) =. X X Y Y In digital forensics using sensor noise, we usually wor with image noise residuals obtained using a denoising filter F: W = I F(I) = aik + Θ. Here, W is the noise residual of image I, a is an attenuation factor, K is the multiplicative PRNU factor, which plays the role of the sensor fingerprint, and Θ is the modeling noise. The fingerprint K can be estimated from noise residuals of several images taen by the same sensor (camera). The presence of the signal IK in the noise residual of I can be interpreted as evidence that I was taen by a sensor with fingerprint K. The presence is 5 usually established using a correlation-based detector. Throughout this paper, we will assume that we are given a database D, D = { F i}, i =,, N, containing N camera fingerprints F i of the same length n, which is also the length of the query fingerprint X. Further, for simplicity, we assume perfect pixel synchronization between the query fingerprint and database fingerprints, i.e., no geometrical transformation of images and a search for its parameters is involved. We denote the fingerprints residing in the database with letter F instead of K because they are only estimates of the corresponding true PRNU factors. Without loss of generality, we also assume that the fingerprints are normalized: n ( F [ i]) =, F D. n i = We further assume the following model for any two fingerprint estimates: F = ak+ Θ, F = bk' + Θ, where K and K are the PRNU factors and Θ, Θ are i.i.d. Gaussians N(0,σ ), N(0,σ ), respectively. Having observed F and F, matching two fingerprints leads to the following two-channel hypothesis testing problem: H 0 : K K (the two fingerprints are from different cameras) () H : K = K (the two fingerprints are from the same camera). A simplified version of the generalized lielihood ratio test for this problem decides between H 0 and H by comparing the normalized correlation ρ, ρ = corr F, F, () ( ) to a threshold t. The detector decides H when ρ > t. When the decision is H while H 0 is true, we spea of a false alarm. The other type of error is called missed detection. The probability of the false alarm and missed detection will be denoted P FA and P MD, respectively. From the central limit theorem, ρ is approximately Gaussian N(0, /n) under H 0. Note that the variance of the correlation decreases linearly with increasing length of the vectors. This implies that for a chosen probability of false alarm P FA,
3 = ( ), (3) n t Q PFA where Q(x) is the probability that one realization of a standard normal variable exceeds x. 3. COMPLEXITY REDUCTION To reduce the computational complexity of the fingerprint search, one needs to either decrease the number of correlations that need to be carried out or somehow decrease the length of the fingerprint. Note that both options will increase the error probabilities of the search. In this section, we explore both ideas, analyze their weanesses, and then naturally arrive at the concept of the so-called fingerprint digest, a ey ingredient in our fast search algorithm detailed in Section Composite fingerprints The first and a quite natural idea is to combine multiple fingerprints into one composite fingerprint. By correlating a query fingerprint with the composite fingerprint, we will essentially perform a simultaneous correlation test against many fingerprints with the cost of computing a single correlation. Without loss of generality, let the number of fingerprints in the database be N = m. Form m subsets S m {,,, N} of size (N+)/ such that i S m if and only if b m (i) =, where (b (i), b (i),, b m (i)) is the binary representation of i. For the database of N camera fingerprints, pre-compute m composite fingerprints M r, r =,, m: Mr = F i. (4) S r i Sr Let X be the query fingerprint and let F q be the fingerprint of the same camera from the database. In other words, we assume that the camera is in the database. The search algorithm computes m normalized correlations, ( ) ( r) c = corr, r, r =,, m XM, (5) and then compares them to a pre-determined threshold t. The matching index from the database is given by its binary representation (b, b,, b m ), b r = (c (r) > t), r =,, m. A positive identification of the fingerprint will occur when the search algorithm finds q as the matching index. When b r = 0, r, the algorithm decides that X is not in D. The complexity of this algorithm is O(nlog N), as the composite fingerprints can be pre-computed. The logarithmic complexity, however, comes with a significant performance drop. Due to lac of space, we only provide a brief qualitative argument, leaving out the details to the report [0], where the ROC for this detector is computed. Assuming q S, a necessary condition for positive identification is: X F + X ( M Fq) cq < = = = + =. (6) ( N + )/ () q t c corr( XM, ) corr X, Fi corr XF, q Fi i S i S, i q X M This means that only sufficiently strong fingerprints satisfying c q > t = t ( N + )/ have a chance to be positively identified. The drop in correlation (6) indicates that for sufficiently large N this algorithm will fail with probability approaching. For example, for n =,90,000 (the number of pixels in iphone cameras used in experiments in Section 5) and c q = 0.3, the probability of detection P D = 0.99 for N = 55, but it decreases to P D = 0.70 for N = 5 and P D = for N = Sequential trimming An alternative and quite simple way to speed up the search is to trim all fingerprints to a fixed length n, which would speed up the search by the factor of n/. The expected correlation c q does not change after this trimming, while the threshold t needs to be increased due to the shorter length of the correlated signals and the fact that N comparisons are carried out. A successful detection occurs when ρ > t only for the matching qth fingerprint and ρ t for the
4 remaining fingerprints. In contrast to the approach based on composite fingerprints, the complexity of this algorithm is still linear in N, but no longer dependent on n. Another advantage is a reduced demand for memory space. Most importantly, however, sequential trimming does not exhibit a performance floor with respect to increasing N. The detailed analysis, including a parametric expression for the ROC curve, appears again in [0]. Here, we limit the exposition to the same example as in the previous section. For n =,90,000 and the three values of N, the fingerprints were trimmed to such a length to obtain the same speed up factor as in the approach using composite fingerprints. The probability of detection P D with very low P FA for correlations as low as c q = 0. for N = 4095 and c q = 0.03 for N Fingerprint digest We now further improve on the sequential trimming and propose an approach that utilizes a selective dimensionality reduction. For each fingerprint F in the database, we eep its short digest consisting of an ordered list V F of largest (in magnitude) values from the fingerprint F and their locations L F within the fingerprint captured using a one-dimensional index l[d], d =,,, l[d] n: L {[ ]} F = ld d =, VF = F[ L F ]. For better readability, we will abbreviate V as Vi and LF i as Li. The liely elements of the digest are defective pixels, such as hot pixels represented with large positive values and dead pixels with large negative values. For a given query fingerprint X, we compute the normalized correlation between each digest V i = F i [L i ] and X[L i ]: ( ) ρ ( α ) = corr V, X[ L i ], (7) i where we denoted α = /n, the relative length of the digest. The hypothesis test () is resolved by comparing ρ i (α) to a threshold t that returns the same probability of false alarm P FA as the threshold for ρ in the original hypothesis test with detection statistic ρ i = corr(f i, X). When X and F q D are correlated, e.g., when they are two fingerprints for the same camera corrupted by an additive white Gaussian noise, the expected normalized correlation (7) is positive. In contrast to the sequential trimming of Section 3., when ρ q (α) was constant and equal to ρ for all α, ρ q now becomes an increasing function of α (see the appendix for derivation): / ρq = ρq( α, ρ) +, (8) ρ F( α) where F( α) = + Q ( α /)exp{ ( Q ( α /)) /}. (9) α π Although (8) is only approximate, it is fairly accurate as shown in Figure (middle and right) on simulated data. Note that although F(α) and ρ q (α, ρ), as α 0 (see Figure middle), the detector cannot improve with decreasing α. This is because the decreased length of the vectors increases the variance of the correlation, which, in turn, increases t = t α = Q P, using formula (3). The p-value of ρ q the decision threshold corresponding to a fixed P FA : ( ) depends monotonically on the outlier measure d = ρ q /Var[ρ H 0 ] = ρ q αn, which decreases with α 0 slower than the same quantity in the sequential trimming (see Figure right). The digests allow us to eep rather small (such as = 0,000 or less, Figure left) and thus speed up the search with a reasonable drop in reliability of testing even if we have to calculate ρ i for all fingerprints F i D. For example, for ρ = 0.05, when switching from the full-length fingerprints with n = 3,000,000 pixels to digests with = 0,000 pixels, the outlier measure d decreases only 9-times while it decreases n/ = 300 times for the non-selective trimming of Section 3.. (See the curved line near zero in Figure right.) The normalized correlations can thus be computed more than 0-times faster (for α = ) with the same probability of miss compared to the sequential trimming and more than 3000-times faster when compared to the computation of full-length correlations. i FA F i
5 Sequential Trimming Simulation Experiment Model ρ(α) α d Sequential Trimming 500 Simulation Experiment Model α Figure. Scatter plot of a 0,000-pixel digest from a Nion CoolPix Mpixel digital camera fingerprint estimated from 50 images (left), the normalized correlation (7) between digests simulated as i.i.d. Gaussian signals with ρ = 0.05 compared to the correlation computed from a cropped central part of the same length as the digest (middle), the outlier measure d vs. relative digest length for the same simulated data (right). 4. FAST SEARCH ALGORITHM In the previous section, we introduced the concept of a fingerprint digest and described a search algorithm that goes through all digests in the database and computes the correlation between each database digest F[L] and the query fingerprint only at the digest locations L. This already decreases the computational complexity by the factor of α, the relative digest length. We now describe a modification of this algorithm called the Approximate Ran Matching Search algorithm (ARMS) that can identify the correct fingerprint even faster provided the correlation ρ = corr( XF, ) is large, e.g., ρ > 0.. This would be the case, for example, when both X and F are good quality fingerprints. For better clarity, from now on we strictly use i to index fingerprints/digests, j to index ordered pixels, d to index pixels in the digest, and u to index fingerprint candidates. ARMS was inspired by the Spearman ran correlation. 6 The Spearman rans R X and R F are the inverse permutations (on pixel indices) to the pixel location vectors L X and L F. With D= {[]} δ j n j= = RX RF, the Spearman ran correlation is n 6 δ[ j] j= ρs = corr ( RX, R F) =. (0) nn ( )( n+ ) The most influential indices j in (0) are those for which δ[j] is relatively small. Such indices are more liely located in the beginning of the digests when j is small. We will mae use of the following sparse n matrix S whose elements are lists of fingerprint indices, i {,, N}: i S[a,b] iff F = F i D and l F [b] = a. () The matrix S has as many rows as there are pixels in the fingerprints and as many columns as the digest length. The index i is in position [a,b] when pixel a is the bth outlier in the ith digest. Because there are the total of N fingerprint indices, at most N lists S[a,b] are non-empty, and thus the density of S is N/n = N/n. Consequently, providing the number of image pixels is much larger than the number of fingerprints in the database, n N, the matrix S is sparse. This data structure will allow us to identify fingerprints that are more liely candidates for being correlated with the query fingerprint X without having to evaluate the correlation. For example, let the pixel lx[], which has the largest (positive or negative) value V X [] in X (it might be a hot or dead pixel), be raned high in the camera fingerprint F i. This means that the camera index i is not far from the st column of S in row l X []. The algorithm retrieves all camera indices u (if there are any) from row l X [] between column and +w and considers them as candidates whenever V X [] has the same sign as V u [c], where u is the retrieved index and c {,, +w} is the column. The distance (window) w of how far we loo is a parameter of ARMS. In the second iteration, the pixel (or row) l X [] is processed the same way and all camera indices from columns to +w are retrieved. In the lth iteration, the columns l w to l+w are processed in row l X [l]. Each candidate u is subjected to the hypothesis test in which the correlation ρ u (α) given in (7) is compared with the threshold t. The iterations stop when ρ u (α) > t (the matching fingerprint with index u is found) or when a time
6 limit is exceeded. The time limit is discussed further below. The larger the correlation between X and the matching fingerprint F is, the more liely will F appear early among the candidates. Notice that fingerprints F that appear early as candidates have δ[j] w in (0) for some small j, meaning that both the Spearman and the Pearson correlation receive large increments in their summations. We improved this algorithm by further sifting through the candidates, which we now call potential candidates. A potential candidate becomes a valid candidate if its accumulated evidence Z exceeds a threshold t cand. Clearly, we need to be able to compute Z very fast. In particular, its complexity must be much lower than O(). We propose to sum the squares of digest values as shown in the pseudo-code below. This is related to the estimation of an increment in the Pearson correlation (up to a scaling factor). The sparser the matrix S is, the fewer potential candidates ARMS will have to process and the faster the search will run. The average computation time for finding the matching camera fingerprint when it is present in the database and identifiable by the correlation (7) depends (for fixed N,, t) on ρ, w, t cand, and on the particular implementation. Even though the correlation (7) is the costliest operation, the implementation of the data structure S is crucial for fast searching times as well. The number of considered candidates, w, may be minimized by choosing the threshold t cand large enough, but not too large to miss the correct candidate. So far, we focused on the case when the camera whose fingerprint is queried is in the database. When the database does not contain a matching fingerprint or when it is missed by the correlation test on digests of length, the search time of this proposed algorithm can be much longer than if we used a simple brute-force search on digests described in Section 3.3. In order to limit the processing time, we introduce a continue_criterion (command line 4 in the pseudo-code below). As soon as this criterion becomes false, ARMS switches to a brute-force search on all fingerprints that were not considered yet. Optimization of this criterion with respect to the expected search time would require nowledge of the prior probability of finding a fingerprint in the database, which will not be available in practice. To eep the worst case time below twice the time for the brute force digest search, we simply set the criterion to false once the current processing time exceeds that of the brute force search. Psedo-code for ARMS % ARMS finds a correlated (matching) item to X in database D.. = 0,000; w =,000; t cand = 0. w; t = 60 ; % set up parameters (default values). Compute digest L X of length from X. 3. d = 0; ρ = 0; Z = 0; 4. While {ρ t and d w and continue_criterion} do 5. d = d + ; c = L X [d]; % move to the next element of L. 6. Retrieve fingerprint indices from all lists S[c, b], such that b d < w, U = S[, c b]; b d < w 7. While {U is not empty and ρ t } do 8. choose u U; % potential candidate is F u 9. If {sign(v X [d]) = sign(v u [b])} 0. Z[u] = Z[u] + (V u [b]) ;. end. If {Z[u] > t cand and u has not been considered yet} % considered candidate 3. ρ = corr(v u, X[L u ]); 4. end 5. U = U {u}; 6. end 7. end 8. While {ρ t and u has not been considered yet} do % brute force search on digests 9. ρ = corr(v u, X[L u ]); 0. end. If {ρ > t } q = u; end % q is the matching fingerprint index in D
7 4. Analysis of ARMS We now investigate the conditions under which ARMS correctly finds the matching fingerprint without computing too many correlations (lines 3 and 9). Figure depicts the distribution of Z[u] for randomly generated correlated Gaussian fingerprints with correlations () ρ = 0, 0.05, 0., 0.5, 0., 0.5, 0.3. The plotted values correspond to w =,000 and = 0,000. For better clarity, in Figure the sample distributions are displayed through their Gaussian fits. These distributions would be obtained in experiments if we always let ARMS go through all iterations. It is the positive correlation ρ that determines how much the distributions overlap with the one for ρ = 0 and thus ρ determines the probability of considering a non-matching fingerprint as a candidate (line 3 of the pseudo-code). The separation between hypotheses H 0 and H (the distribution for ρ = 0 and for a fixed ρ > 0) improves with increasing w. This means that w should be larger than,000 if we expect ρ to be below 0. (see Figure ). On the other hand, w should not be too large as it increases the search time. Because the separation improves with ρ, which is typically unnown to us, one possible remedy can be introducing a varying w. One simple choice is to set w = l + w in the lth iteration, i.e., the fingerprint indices u are taen from the first l + w columns of S. Repeating the simulation experiment for such a varying window w with w = 000, gives the plot in Figure ρ = 0 ρ = 0.05 ρ = ρ = ρ = 0. ρ = 0.5 ρ = Z[u] Figure. Gaussian fits of histograms of Z[u] (after iterations of ARMS) for randomly generated fingerprints F u that have correlation ρ with X as denoted in the plot (all simulated data, w =,000, = 0,000, n = ). The threshold t cand also influences the number of iterations of ARMS (before it switches to the brute-force loop) and should be chosen rather small to reduce overhead computations. If ARMS stops after l (l < ) iterations, Z[u] will be /l times smaller than what plotted in Figure andfigure 3. If we want ARMS to find a matching fingerprint F u with correlation ρ > ρ 0 (formula ()) within l iterations with probability at least p without resolving to the brute-force search (lines 8 0), we need to choose t cand as zl/, where z is such that Z[u] > z with probability p, where Z is distributed according to the pdf from Figure labeled with ρ 0. We note that the sparse matrix S needs to be updated with every new fingerprint included in D. With every next query, all data structures are reused. Alternatively, for one query X, we can build only the needed portion of S on the fly. This is because, in each iteration of ARMS, we need to access only rows corresponding to the pixels represented by L X (for a single query X) and w+ columns. We will spea of a truncated matrix S when it has size (w+).
8 7 x ρ = 0 ρ = 0.05 ρ = 0. 5 ρ = ρ = 0. ρ = 0.5 ρ = Z[u] Figure 3. Gaussian fits of histograms of Z[u] (after iterations of ARMS) for a varying window parameter w. The randomly generated fingerprints F u have correlation ρ with X as denoted in the plot (all simulated data, w =,000, = 0,000, n = ). 5. EXPERIMENTS The ARMS functionality and performance was verified on images downloaded from the Flicr image-sharing website. While this source provides a convenient access to a large number of diverse cameras for our tests, we have no control over the image content and their source. For example, some users post completely blac images, which only taint our tests and need to be eliminated from experiments. Moreover, some users share their cameras or exchange images. We believe that shared images constitute only a small fraction of all images and that we will actually be able to pinpoint the users that use the same camera. We test ARMS on a large number of cameras of exactly the same model, the Apple iphone, with a built-in Mpixel camera. Its resolution is pixels, which is rather small compared to typical cameras in use today. We chose this homogenous database of one camera model for two reasons. First, in practice the search algorithm will liely be deployed only on cameras of the same model, as one can extract this information from the EXIF header. Second, fingerprints of sensors from cameras of the same model contain residuals of wea non-unique artifacts (NUAs) that may slightly increase the false alarm rate. In short, we intentionally chose the source of database fingerprints and their resolution far from the most favorable case for camera identification. For experiments, we collected more than 00,000 color images in full resolution from 45 Flicr users. Images in landscape orientation were arranged in groups of 60 and the camera PRNU was estimated from each group using the maximum lielihood estimator. For some users, more than 0 images were downloaded to allow us to obtain two different fingerprint estimates for their camera. Thus, the total number of fingerprints was 309. The fingerprints were estimated for each color channel separately and then processed by zero-meaning as described in Ref. [9]. This process separates the three color channels and also the green, blue, and red pixels (assuming the sensor has the Bayer color filter array), subtracts the averages from each column and row and in each color and then re-arranges the colors bac to form a colored noise fingerprint. After converting it to a grayscale real-valued matrix, the fingerprint is filtered with a Wiener filter in the DFT domain (magnitude only). The resulting -D signal is converted to a vector the final fingerprint by column-wise scanning. 5. Model validation Our first test involves two fingerprints of the same iphone camera computed from two different sets of 60 images. The goal here is to compare our theoretical model for which relation (8) was derived. Figure 4 shows a noticeable mismatch between the model and the measured data. For digests of length = 0,000, n = , α 0 = /n = 0.005, we computed ρ (α 0 ) = 0.678, while formula (8) gives ρ (α 0 ) = A closer inspection revealed that iphone fingerprints
9 exhibit some residual periodic NUAs that might be responsible for this discrepancy. The difference between the shapes of the plots in Figure 4 and Figure (right) is due to a large initial correlation ρ () = between the two fingerprints of the same camera. ρ(α) Sequential Trimming Simulation Experiment Model Digest: =0000, N=00x α Figure 4. Function ρ(α) (left), outlier measure d (the curved line on the right). d x Sequential Trimming 0. Simulation Experiment Model α 5. Finding a matching fingerprint in the database This is the main experiment that demonstrates the performance of ARMS on the above database of 309 fingerprints from (at most) 45 iphone cameras. The experiment consisted of 667 searches for which the camera of the query fingerprint was present in the database. We repeat that the query and the database fingerprints were estimated from a different set of images. The fingerprint chosen as the query was removed from the database, leaving N = 309 others to search among. The digest length was fixed to = 0,000. We recorded the following quantities: ρ u (α 0 ), the number of ρ evaluations for the considered candidates, and the search time after the data was loaded in the memory. To determine the appropriate thresholds, we considered the results of the large scale experiments with the correlation detector reported in Ref. [7], even though the tests there were run on cameras other than iphones. In particular, this wor showed that in order to obtain the probability of false alarm P FA 0 6, one needs to use a larger threshold than Q (P FA )/ given by (3). Based on the results of Ref. [7], we set t = 60 = The expected correlation ρ between two full-length i.i.d. Gaussian fingerprints with ρ(α, ρ) = is ρ = This value of ρ is the digest s sensitivity limit that will determine, along with the fingerprints quality, the probability of a missed detection. When ρ < 0.05 for the matching fingerprint, a missed identification will liely occur. Because the typical value of the correlation ρ between two matching fingerprints (from the same camera) in our test was around ρ = 0.5 (ten times our digests sensitivity limit), we expect no missed detections. The average correlation ρ u (α 0 ) for pairs of digests from the same camera was Our Matlab implementation of ARMS was run without any attempt to optimize the speed of the implementation (the sparse matrix S was created with the spalloc command), with two different thresholds t cand. The first one (the first column in Table ) leads to a small average number of considered candidates and promises a faster search time after code optimization and using a pre-computed matrix S. The second test with a smaller value of t cand leads to a short average search time of 0.7 seconds (including the time for updating the truncated matrix S). This processing time should be compared to 4.8 sec needed for the brute-force search on fingerprint digests (the last column in Table ) and to 35 minutes needed when searching on full-length fingerprints that requires reading the large fingerprints from external memory. All tests were run on a Dual Core AMD Opteron Processor,. GHz. When the query fingerprint belongs to a camera that is not contained in D, i.e., when H 0 () is true, the running time of ARMS is upper bounded by twice the processing time for the brute force search on digests as stated in Section 4. The
10 time for the brute-force search will be about twice the average time for the matching fingerprints because the algorithm has to go through all fingerprints rather than its half. Table. The search for a matching fingerprint in the database of 309 fingerprints of 45 different iphone cameras. ARMS ARMS Brute-force search on fingerprint digests N K 0,000 0,000 0,000 t cand w = w = t mean(ρ u (α 0 )) (min, max) (0.377, ) (0.377, ) (0.377, ) mean(ρ u ()) (min, max) 0.5 (0.089, 0.837) 0.5 (0.089, 0.837) 0.5 (0.089, 0.837) Missed/false identification 0/0 0/0 0/0 Average number of evaluations of correlation ρ.030 (.06) 8.95 (.65) 545 (77) (best 95% cases) Time for testing candidate sec sec sec Average search time 3. sec 0.7 sec 4.80 sec Surprisingly, the test found two matching fingerprints with high correlations ρ u (α 0 ) 0.63 belonging to different users. Further inspection of the images confirmed that the camera users were closely related if not the same, suggesting that the images were, indeed, all taen with identical cameras. Consequently, in the caption of Table we decreased the total number of different cameras in this test to Find the source camera in the database for a given image The last experiment deals with the tas of finding the source camera for a single query image, which corresponds to the case when the query fingerprint is estimated from a single image and is thus of a very low quality. We used the database of N = 43 fingerprints of 43 different iphone cameras and tested randomly chosen 69 images from 69 different cameras. We stress that none of the 69 images was used to estimate the database fingerprints. Because the correlation between the matching fingerprint and the query fingerprint is liely to be quite low, we did not apply ARMS in this case and instead used the brute-force search on digests described in Section 3.3. The average search time was 3.4 sec (= N/ sec.), the empirical missed detection rate was P MD = 0.9 and P FA = 0 (while for = 30,000, P MD = and P FA = 0). The typical value of the correlation ρ between the image noise residual (PRNU estimate from one image) and the matching camera fingerprint was only around 0.04, which is quite close to the digest sensitivity limit (0.05) for = 0,000. A brief inspection of Figure andfigure 3 tells us that we would have to increase substantially to provide ARMS an advantage over the brute-force search on digests. The proper value of could be obtained by extending the error analysis of sequential trimming [0] to digests. Due to time and space constraints, we postpone this analysis to our future wor. 5.4 Memory requirements A straightforward implementation requires eeping in the memory the digests V i and the indices L i, i =,, N, of the fingerprints in the database, the sparse matrix S, the query fingerprint X, and its digest. All digests tae (4+4)(N+) bytes when a single precision is opted for, or (8+4)(N+) bytes for double precision. The sparse matrix taes at most double the space required for the digests. The required space is thus proportional to N and, as long as N is not too large, the requested memory space is confined. When N is large (or comparable to the number of pixels n) and the above requirements exceed the available memory, the matrix S can be prepared in advance and its (partial) rows read whenever necessary. This approach pays off when the number of queries n q to the same database is such that n q ~ n/. Otherwise, the matrix S does not have to be even fully available. Instead, during the lth iteration only the w+ elements in columns l w,, l+w and row l X [l] of S need to be obtained one at a time until the search stops. This is the implementation (in Matlab) we used in the experiments.
11 6. CONCLUSION Camera identification based on detecting sensor noise is nowadays an established technology that has already been used in court 8 to provide evidence in prosecution whenever a crime has been committed by taing a digital picture or video. It is anticipated by the authors of this article that this technology will be used increasingly more often not only in criminal cases but in digital forensic analysis in general. In particular, analysts may need to decide whether a given sensor fingerprint already resides in a large database of camera fingerprints or whether a given image was taen by a camera whose fingerprint is in the database. The straightforward approach in which the query fingerprint is correlated with each fingerprint from the database has complexity proportional to the product of the database size and the number of pixels in the fingerprint. With increasing resolution of digital sensors, the search time may become prohibitively large even for moderately sized fingerprint database, when the search may require hours to finish. The complexity becomes an even more serious issue when an analyst needs to cluster images according to their common source. Here, the processing time is quadratic in the number of clusters. In this paper, we describe a fast search algorithm whose worst-case complexity is still proportional to the database size but does not depend on the sensor resolution. As the constant of proportionality is very small, the search is very fast in practice. For example, when the fingerprint resides in a database of 3000 two-megapixel fingerprints, the average search time is about 0. seconds. The algorithm wors by extracting a digest of the query fingerprint formed by the most extreme 0,000 fingerprint values and then approximately matches their positions with the positions of pixels in the digests of all database fingerprints. The algorithm requires a sparse data structure that needs to be updated with every new fingerprint included in the database. The algorithm is designed to mae sure that the probability of a match and false alarm for the fast search is identical to the corresponding error probabilities of the direct brute-force search. Experiments on a database of 000 iphones prove the feasibility of the proposed approach. The fast search algorithm introduced here does not rely on any structure or special properties of the fingerprints in the database. It can be utilized in any application where a database contains n-dimensional elements, and n is a fixed large number. The only requirement is that the elements consist of real numbers or integers from a large range. Integers from a small range would lead to ill-defined rans. An extreme case when the ran correlation and, consequently, the fast search algorithm cannot be used, are binary vectors (one bit for each vector element). 7. ACKNOWLEDGEMENTS This research was supported by an NSF award no. CNF REFERENCES [] Fridrich, J.: Digital Image Forensic Using Sensor Noise, IEEE Signal Processing Magazine, vol. 6(), pp. 6 37, 009. [] Luáš J., Fridrich J., and Goljan M.: Digital Camera Identification from Sensor Pattern Noise, IEEE Transactions on Information Forensics and Security, vol. (), pp. 05 4, June 006. [3] Chen, M., Fridrich, J., Goljan, M., and Luáš, J.: Determining Image Origin and Integrity Using Sensor Noise, IEEE Transactions on Information Security and Forensics, vol. (), pp , March 008. [4] Chen, M., Fridrich, J., and Goljan, M.: Source Digital Camcorder Identification Using Sensor Photo-Response Non-Uniformity, Proc. SPIE Electronic Imaging, Security, Steganography, and Watermaring of Multimedia Contents IX, vol. 6505, San Jose, CA, January 8 February, pp. G H, 007. [5] Goljan, M. and Fridrich, J.: Camera Identification from Cropped and Scaled Images, Proc. SPIE Electronic Imaging, Forensics, Security, Steganography, and Watermaring of Multimedia Contents X, vol. 689, San Jose, CA, January 8 30, pp. 0E 0F, 008. [6] Spearman's ran correlation coefficient. [7] Goljan, M., Fridrich, J., and Filler, T.: Large Scale Test of Sensor Fingerprint Camera Identification, Proc. SPIE Electronic Imaging, Media Forensics and Security XI, vol. 754, San Jose, CA, January 7, pp. 0I 0J, 009. [8] Spy Blog, May 9,
12 [9] Goljan, M.: Digital Camera Identification from Images Estimating False Acceptance Probability, Digital Watermaring, 7th International Worshop, IWDW 008, Busan, Korea, LNCS, vol. 5450, Springer Berlin / Heidelberg, pp , 009. [0] Fridrich, J. and Goljan, M.: Derivation of ROCs for Composite Fingerprints and Sequential Trimming, Technical Report, Binghamton University, January APPENDIX In this appendix we compute the expected value of the normalized correlation between the database fingerprint digest and its (query) noisy version (formulas (8) and (9)). The fingerprint x,, x n is modeled as n i.i.d. samples of a Gaussian random variable ξ ~ N(0,σ ). Without loss of generality, let us further assume that the pixels are already ordered so that x j x j+ for each j {,, n }. We remind that the fingerprint digest is formed by the = αn most extreme values in the estimated fingerprint: x,, x. To avoid woring with rather complicated order statistics, we adopt the following simplification. We will assume that the outlier values x,, x, all come from a random variable φ T distributed on U = (, T] [T, ), where T > 0 is such that the probability Pr(ξ U) = α. The pdf f T (x) of φ T is just x /( σ ) a scaled Gaussian density: f ( x) = /( πσα) e, for x U, and f T (x) = 0 otherwise. Using the Q-function, Q(T/σ) = α or T = σ Q (α /). T We now compute the expected value of the correlation between the database fingerprint digest x = (x,, x ) and the query digest, which is a noisy version of x, x + η, where η is a zero-mean white Gaussian noise uncorrelated with x: where xj( xj + η j) j = ρα ( ) = corr( xx, + η) =, (A.) + SNR xj ( xj + η j) j= j= x j j= Var[ φt ] SNR =. (A.) Var[ η] η j j= Thus, all we need to establish is the variance of φ T. By integrating by parts and substituting for T = σ Q (α /): x /( σ ) t / xe σ te t / Var[ φt ] = dx = { x / σ = t} = dt { u t, v' te } T α = = = πσα T / σ π σ T ( ( /)) /( ) Q α T σ σ = e Q( T / σ ) Q ( α /) e σ α + = + σ π α π ( ( /)) Q α = σ + Q ( α / ) e σ F( α). α π Using (A.3), we write the SNR (A.) as SNR = σ F(α)/Var[η]. Because the correlation between the full-length / fingerprints is ρ = ( + σ / Var[ η]), we have σ / Var[ η] = ρ and thus (A.) can be finally written as (A.3) / ρα ( ) = + = +. SNR ρ F( α) (A.4) /
A Source Cell-phone Identification Scheme Based on Canonical Correlation Analysis of Photo Response Non-uniformity
 Journal of Computational Information Systems 8: 4 (212) 1433 144 Available at http://www.jofcis.com A Source Cell-phone Identification Scheme Based on Canonical Analysis of Photo Response Non-uniformity
Journal of Computational Information Systems 8: 4 (212) 1433 144 Available at http://www.jofcis.com A Source Cell-phone Identification Scheme Based on Canonical Analysis of Photo Response Non-uniformity
DETECTION theory deals primarily with techniques for
 ADVANCED SIGNAL PROCESSING SE Optimum Detection of Deterministic and Random Signals Stefan Tertinek Graz University of Technology turtle@sbox.tugraz.at Abstract This paper introduces various methods for
ADVANCED SIGNAL PROCESSING SE Optimum Detection of Deterministic and Random Signals Stefan Tertinek Graz University of Technology turtle@sbox.tugraz.at Abstract This paper introduces various methods for
Lecture 5: Likelihood ratio tests, Neyman-Pearson detectors, ROC curves, and sufficient statistics. 1 Executive summary
 ECE 830 Spring 207 Instructor: R. Willett Lecture 5: Likelihood ratio tests, Neyman-Pearson detectors, ROC curves, and sufficient statistics Executive summary In the last lecture we saw that the likelihood
ECE 830 Spring 207 Instructor: R. Willett Lecture 5: Likelihood ratio tests, Neyman-Pearson detectors, ROC curves, and sufficient statistics Executive summary In the last lecture we saw that the likelihood
14.30 Introduction to Statistical Methods in Economics Spring 2009
 MIT OpenCourseWare http://ocw.mit.edu.30 Introduction to Statistical Methods in Economics Spring 009 For information about citing these materials or our Terms of Use, visit: http://ocw.mit.edu/terms. .30
MIT OpenCourseWare http://ocw.mit.edu.30 Introduction to Statistical Methods in Economics Spring 009 For information about citing these materials or our Terms of Use, visit: http://ocw.mit.edu/terms. .30
2. What are the tradeoffs among different measures of error (e.g. probability of false alarm, probability of miss, etc.)?
 ECE 830 / CS 76 Spring 06 Instructors: R. Willett & R. Nowak Lecture 3: Likelihood ratio tests, Neyman-Pearson detectors, ROC curves, and sufficient statistics Executive summary In the last lecture we
ECE 830 / CS 76 Spring 06 Instructors: R. Willett & R. Nowak Lecture 3: Likelihood ratio tests, Neyman-Pearson detectors, ROC curves, and sufficient statistics Executive summary In the last lecture we
A Reservoir Sampling Algorithm with Adaptive Estimation of Conditional Expectation
 A Reservoir Sampling Algorithm with Adaptive Estimation of Conditional Expectation Vu Malbasa and Slobodan Vucetic Abstract Resource-constrained data mining introduces many constraints when learning from
A Reservoir Sampling Algorithm with Adaptive Estimation of Conditional Expectation Vu Malbasa and Slobodan Vucetic Abstract Resource-constrained data mining introduces many constraints when learning from
ECE531 Lecture 6: Detection of Discrete-Time Signals with Random Parameters
 ECE531 Lecture 6: Detection of Discrete-Time Signals with Random Parameters D. Richard Brown III Worcester Polytechnic Institute 26-February-2009 Worcester Polytechnic Institute D. Richard Brown III 26-February-2009
ECE531 Lecture 6: Detection of Discrete-Time Signals with Random Parameters D. Richard Brown III Worcester Polytechnic Institute 26-February-2009 Worcester Polytechnic Institute D. Richard Brown III 26-February-2009
Putting the PRNU Model in Reverse Gear: Findings with Synthetic Signals
 Putting the PRNU Model in Reverse Gear: Findings with Synthetic Signals Miguel Masciopinto, Fernando Pérez-González Signal Theory and Communications Department, University of Vigo E. E. Telecomunicación,
Putting the PRNU Model in Reverse Gear: Findings with Synthetic Signals Miguel Masciopinto, Fernando Pérez-González Signal Theory and Communications Department, University of Vigo E. E. Telecomunicación,
Recursive Least Squares for an Entropy Regularized MSE Cost Function
 Recursive Least Squares for an Entropy Regularized MSE Cost Function Deniz Erdogmus, Yadunandana N. Rao, Jose C. Principe Oscar Fontenla-Romero, Amparo Alonso-Betanzos Electrical Eng. Dept., University
Recursive Least Squares for an Entropy Regularized MSE Cost Function Deniz Erdogmus, Yadunandana N. Rao, Jose C. Principe Oscar Fontenla-Romero, Amparo Alonso-Betanzos Electrical Eng. Dept., University
Detection theory 101 ELEC-E5410 Signal Processing for Communications
 Detection theory 101 ELEC-E5410 Signal Processing for Communications Binary hypothesis testing Null hypothesis H 0 : e.g. noise only Alternative hypothesis H 1 : signal + noise p(x;h 0 ) γ p(x;h 1 ) Trade-off
Detection theory 101 ELEC-E5410 Signal Processing for Communications Binary hypothesis testing Null hypothesis H 0 : e.g. noise only Alternative hypothesis H 1 : signal + noise p(x;h 0 ) γ p(x;h 1 ) Trade-off
4. Quantization and Data Compression. ECE 302 Spring 2012 Purdue University, School of ECE Prof. Ilya Pollak
 4. Quantization and Data Compression ECE 32 Spring 22 Purdue University, School of ECE Prof. What is data compression? Reducing the file size without compromising the quality of the data stored in the
4. Quantization and Data Compression ECE 32 Spring 22 Purdue University, School of ECE Prof. What is data compression? Reducing the file size without compromising the quality of the data stored in the
Model-based Correlation Measure for Gain and Offset Nonuniformity in Infrared Focal-Plane-Array Sensors
 Model-based Correlation Measure for Gain and Offset Nonuniformity in Infrared Focal-Plane-Array Sensors César San Martin Sergio Torres Abstract In this paper, a model-based correlation measure between
Model-based Correlation Measure for Gain and Offset Nonuniformity in Infrared Focal-Plane-Array Sensors César San Martin Sergio Torres Abstract In this paper, a model-based correlation measure between
Communication Engineering Prof. Surendra Prasad Department of Electrical Engineering Indian Institute of Technology, Delhi
 Communication Engineering Prof. Surendra Prasad Department of Electrical Engineering Indian Institute of Technology, Delhi Lecture - 41 Pulse Code Modulation (PCM) So, if you remember we have been talking
Communication Engineering Prof. Surendra Prasad Department of Electrical Engineering Indian Institute of Technology, Delhi Lecture - 41 Pulse Code Modulation (PCM) So, if you remember we have been talking
What is Image Deblurring?
 What is Image Deblurring? When we use a camera, we want the recorded image to be a faithful representation of the scene that we see but every image is more or less blurry, depending on the circumstances.
What is Image Deblurring? When we use a camera, we want the recorded image to be a faithful representation of the scene that we see but every image is more or less blurry, depending on the circumstances.
University of Siena. Multimedia Security. Watermark extraction. Mauro Barni University of Siena. M. Barni, University of Siena
 Multimedia Security Mauro Barni University of Siena : summary Optimum decoding/detection Additive SS watermarks Decoding/detection of QIM watermarks The dilemma of de-synchronization attacks Geometric
Multimedia Security Mauro Barni University of Siena : summary Optimum decoding/detection Additive SS watermarks Decoding/detection of QIM watermarks The dilemma of de-synchronization attacks Geometric
Estimating Gaussian Mixture Densities with EM A Tutorial
 Estimating Gaussian Mixture Densities with EM A Tutorial Carlo Tomasi Due University Expectation Maximization (EM) [4, 3, 6] is a numerical algorithm for the maximization of functions of several variables
Estimating Gaussian Mixture Densities with EM A Tutorial Carlo Tomasi Due University Expectation Maximization (EM) [4, 3, 6] is a numerical algorithm for the maximization of functions of several variables
Chapter 2 Signal Processing at Receivers: Detection Theory
 Chapter Signal Processing at Receivers: Detection Theory As an application of the statistical hypothesis testing, signal detection plays a key role in signal processing at receivers of wireless communication
Chapter Signal Processing at Receivers: Detection Theory As an application of the statistical hypothesis testing, signal detection plays a key role in signal processing at receivers of wireless communication
Clustering by Mixture Models. General background on clustering Example method: k-means Mixture model based clustering Model estimation
 Clustering by Mixture Models General bacground on clustering Example method: -means Mixture model based clustering Model estimation 1 Clustering A basic tool in data mining/pattern recognition: Divide
Clustering by Mixture Models General bacground on clustering Example method: -means Mixture model based clustering Model estimation 1 Clustering A basic tool in data mining/pattern recognition: Divide
Lecture 14 October 22
 EE 2: Coding for Digital Communication & Beyond Fall 203 Lecture 4 October 22 Lecturer: Prof. Anant Sahai Scribe: Jingyan Wang This lecture covers: LT Code Ideal Soliton Distribution 4. Introduction So
EE 2: Coding for Digital Communication & Beyond Fall 203 Lecture 4 October 22 Lecturer: Prof. Anant Sahai Scribe: Jingyan Wang This lecture covers: LT Code Ideal Soliton Distribution 4. Introduction So
New Traceability Codes against a Generalized Collusion Attack for Digital Fingerprinting
 New Traceability Codes against a Generalized Collusion Attack for Digital Fingerprinting Hideki Yagi 1, Toshiyasu Matsushima 2, and Shigeichi Hirasawa 2 1 Media Network Center, Waseda University 1-6-1,
New Traceability Codes against a Generalized Collusion Attack for Digital Fingerprinting Hideki Yagi 1, Toshiyasu Matsushima 2, and Shigeichi Hirasawa 2 1 Media Network Center, Waseda University 1-6-1,
CSCI5654 (Linear Programming, Fall 2013) Lectures Lectures 10,11 Slide# 1
 CSCI5654 (Linear Programming, Fall 2013) Lectures 10-12 Lectures 10,11 Slide# 1 Today s Lecture 1. Introduction to norms: L 1,L 2,L. 2. Casting absolute value and max operators. 3. Norm minimization problems.
CSCI5654 (Linear Programming, Fall 2013) Lectures 10-12 Lectures 10,11 Slide# 1 Today s Lecture 1. Introduction to norms: L 1,L 2,L. 2. Casting absolute value and max operators. 3. Norm minimization problems.
The Perceptron algorithm
 The Perceptron algorithm Tirgul 3 November 2016 Agnostic PAC Learnability A hypothesis class H is agnostic PAC learnable if there exists a function m H : 0,1 2 N and a learning algorithm with the following
The Perceptron algorithm Tirgul 3 November 2016 Agnostic PAC Learnability A hypothesis class H is agnostic PAC learnable if there exists a function m H : 0,1 2 N and a learning algorithm with the following
A Piggybacking Design Framework for Read-and Download-efficient Distributed Storage Codes
 A Piggybacing Design Framewor for Read-and Download-efficient Distributed Storage Codes K V Rashmi, Nihar B Shah, Kannan Ramchandran, Fellow, IEEE Department of Electrical Engineering and Computer Sciences
A Piggybacing Design Framewor for Read-and Download-efficient Distributed Storage Codes K V Rashmi, Nihar B Shah, Kannan Ramchandran, Fellow, IEEE Department of Electrical Engineering and Computer Sciences
Designing Information Devices and Systems I Spring 2017 Babak Ayazifar, Vladimir Stojanovic Homework 2
 EECS 16A Designing Information Devices and Systems I Spring 2017 Babak Ayazifar, Vladimir Stojanovic Homework 2 This homework is due February 6, 2017, at 23:59. Self-grades are due February 9, 2017, at
EECS 16A Designing Information Devices and Systems I Spring 2017 Babak Ayazifar, Vladimir Stojanovic Homework 2 This homework is due February 6, 2017, at 23:59. Self-grades are due February 9, 2017, at
The peculiarities of the model: - it is allowed to use by attacker only noisy version of SG C w (n), - CO can be known exactly for attacker.
 Lecture 6. SG based on noisy channels [4]. CO Detection of SG The peculiarities of the model: - it is alloed to use by attacker only noisy version of SG C (n), - CO can be knon exactly for attacker. Practical
Lecture 6. SG based on noisy channels [4]. CO Detection of SG The peculiarities of the model: - it is alloed to use by attacker only noisy version of SG C (n), - CO can be knon exactly for attacker. Practical
Sequential Procedure for Testing Hypothesis about Mean of Latent Gaussian Process
 Applied Mathematical Sciences, Vol. 4, 2010, no. 62, 3083-3093 Sequential Procedure for Testing Hypothesis about Mean of Latent Gaussian Process Julia Bondarenko Helmut-Schmidt University Hamburg University
Applied Mathematical Sciences, Vol. 4, 2010, no. 62, 3083-3093 Sequential Procedure for Testing Hypothesis about Mean of Latent Gaussian Process Julia Bondarenko Helmut-Schmidt University Hamburg University
RADIO SYSTEMS ETIN15. Lecture no: Equalization. Ove Edfors, Department of Electrical and Information Technology
 RADIO SYSTEMS ETIN15 Lecture no: 8 Equalization Ove Edfors, Department of Electrical and Information Technology Ove.Edfors@eit.lth.se Contents Inter-symbol interference Linear equalizers Decision-feedback
RADIO SYSTEMS ETIN15 Lecture no: 8 Equalization Ove Edfors, Department of Electrical and Information Technology Ove.Edfors@eit.lth.se Contents Inter-symbol interference Linear equalizers Decision-feedback
Detection theory. H 0 : x[n] = w[n]
![Detection theory. H 0 : x[n] = w[n] Detection theory. H 0 : x[n] = w[n]](/thumbs/89/98950636.jpg) Detection Theory Detection theory A the last topic of the course, we will briefly consider detection theory. The methods are based on estimation theory and attempt to answer questions such as Is a signal
Detection Theory Detection theory A the last topic of the course, we will briefly consider detection theory. The methods are based on estimation theory and attempt to answer questions such as Is a signal
PARAMETER ESTIMATION AND ORDER SELECTION FOR LINEAR REGRESSION PROBLEMS. Yngve Selén and Erik G. Larsson
 PARAMETER ESTIMATION AND ORDER SELECTION FOR LINEAR REGRESSION PROBLEMS Yngve Selén and Eri G Larsson Dept of Information Technology Uppsala University, PO Box 337 SE-71 Uppsala, Sweden email: yngveselen@ituuse
PARAMETER ESTIMATION AND ORDER SELECTION FOR LINEAR REGRESSION PROBLEMS Yngve Selén and Eri G Larsson Dept of Information Technology Uppsala University, PO Box 337 SE-71 Uppsala, Sweden email: yngveselen@ituuse
MA 575 Linear Models: Cedric E. Ginestet, Boston University Revision: Probability and Linear Algebra Week 1, Lecture 2
 MA 575 Linear Models: Cedric E Ginestet, Boston University Revision: Probability and Linear Algebra Week 1, Lecture 2 1 Revision: Probability Theory 11 Random Variables A real-valued random variable is
MA 575 Linear Models: Cedric E Ginestet, Boston University Revision: Probability and Linear Algebra Week 1, Lecture 2 1 Revision: Probability Theory 11 Random Variables A real-valued random variable is
Grassmann Averages for Scalable Robust PCA Supplementary Material
 Grassmann Averages for Scalable Robust PCA Supplementary Material Søren Hauberg DTU Compute Lyngby, Denmark sohau@dtu.dk Aasa Feragen DIKU and MPIs Tübingen Denmark and Germany aasa@diku.dk Michael J.
Grassmann Averages for Scalable Robust PCA Supplementary Material Søren Hauberg DTU Compute Lyngby, Denmark sohau@dtu.dk Aasa Feragen DIKU and MPIs Tübingen Denmark and Germany aasa@diku.dk Michael J.
9 Classification. 9.1 Linear Classifiers
 9 Classification This topic returns to prediction. Unlike linear regression where we were predicting a numeric value, in this case we are predicting a class: winner or loser, yes or no, rich or poor, positive
9 Classification This topic returns to prediction. Unlike linear regression where we were predicting a numeric value, in this case we are predicting a class: winner or loser, yes or no, rich or poor, positive
AUTOMATED TEMPLATE MATCHING METHOD FOR NMIS AT THE Y-12 NATIONAL SECURITY COMPLEX
 AUTOMATED TEMPLATE MATCHING METHOD FOR NMIS AT THE Y-1 NATIONAL SECURITY COMPLEX J. A. Mullens, J. K. Mattingly, L. G. Chiang, R. B. Oberer, J. T. Mihalczo ABSTRACT This paper describes a template matching
AUTOMATED TEMPLATE MATCHING METHOD FOR NMIS AT THE Y-1 NATIONAL SECURITY COMPLEX J. A. Mullens, J. K. Mattingly, L. G. Chiang, R. B. Oberer, J. T. Mihalczo ABSTRACT This paper describes a template matching
TARGET DETECTION WITH FUNCTION OF COVARIANCE MATRICES UNDER CLUTTER ENVIRONMENT
 TARGET DETECTION WITH FUNCTION OF COVARIANCE MATRICES UNDER CLUTTER ENVIRONMENT Feng Lin, Robert C. Qiu, James P. Browning, Michael C. Wicks Cognitive Radio Institute, Department of Electrical and Computer
TARGET DETECTION WITH FUNCTION OF COVARIANCE MATRICES UNDER CLUTTER ENVIRONMENT Feng Lin, Robert C. Qiu, James P. Browning, Michael C. Wicks Cognitive Radio Institute, Department of Electrical and Computer
Learning features by contrasting natural images with noise
 Learning features by contrasting natural images with noise Michael Gutmann 1 and Aapo Hyvärinen 12 1 Dept. of Computer Science and HIIT, University of Helsinki, P.O. Box 68, FIN-00014 University of Helsinki,
Learning features by contrasting natural images with noise Michael Gutmann 1 and Aapo Hyvärinen 12 1 Dept. of Computer Science and HIIT, University of Helsinki, P.O. Box 68, FIN-00014 University of Helsinki,
Super-Resolution. Shai Avidan Tel-Aviv University
 Super-Resolution Shai Avidan Tel-Aviv University Slide Credits (partial list) Ric Szelisi Steve Seitz Alyosha Efros Yacov Hel-Or Yossi Rubner Mii Elad Marc Levoy Bill Freeman Fredo Durand Sylvain Paris
Super-Resolution Shai Avidan Tel-Aviv University Slide Credits (partial list) Ric Szelisi Steve Seitz Alyosha Efros Yacov Hel-Or Yossi Rubner Mii Elad Marc Levoy Bill Freeman Fredo Durand Sylvain Paris
Over-enhancement Reduction in Local Histogram Equalization using its Degrees of Freedom. Alireza Avanaki
 Over-enhancement Reduction in Local Histogram Equalization using its Degrees of Freedom Alireza Avanaki ABSTRACT A well-known issue of local (adaptive) histogram equalization (LHE) is over-enhancement
Over-enhancement Reduction in Local Histogram Equalization using its Degrees of Freedom Alireza Avanaki ABSTRACT A well-known issue of local (adaptive) histogram equalization (LHE) is over-enhancement
Residual Versus Suppressed-Carrier Coherent Communications
 TDA Progress Report -7 November 5, 996 Residual Versus Suppressed-Carrier Coherent Communications M. K. Simon and S. Million Communications and Systems Research Section This article addresses the issue
TDA Progress Report -7 November 5, 996 Residual Versus Suppressed-Carrier Coherent Communications M. K. Simon and S. Million Communications and Systems Research Section This article addresses the issue
Advanced Statistical Methods: Beyond Linear Regression
 Advanced Statistical Methods: Beyond Linear Regression John R. Stevens Utah State University Notes 3. Statistical Methods II Mathematics Educators Worshop 28 March 2009 1 http://www.stat.usu.edu/~jrstevens/pcmi
Advanced Statistical Methods: Beyond Linear Regression John R. Stevens Utah State University Notes 3. Statistical Methods II Mathematics Educators Worshop 28 March 2009 1 http://www.stat.usu.edu/~jrstevens/pcmi
SMO vs PDCO for SVM: Sequential Minimal Optimization vs Primal-Dual interior method for Convex Objectives for Support Vector Machines
 vs for SVM: Sequential Minimal Optimization vs Primal-Dual interior method for Convex Objectives for Support Vector Machines Ding Ma Michael Saunders Working paper, January 5 Introduction In machine learning,
vs for SVM: Sequential Minimal Optimization vs Primal-Dual interior method for Convex Objectives for Support Vector Machines Ding Ma Michael Saunders Working paper, January 5 Introduction In machine learning,
Cross entropy-based importance sampling using Gaussian densities revisited
 Cross entropy-based importance sampling using Gaussian densities revisited Sebastian Geyer a,, Iason Papaioannou a, Daniel Straub a a Engineering Ris Analysis Group, Technische Universität München, Arcisstraße
Cross entropy-based importance sampling using Gaussian densities revisited Sebastian Geyer a,, Iason Papaioannou a, Daniel Straub a a Engineering Ris Analysis Group, Technische Universität München, Arcisstraße
Data Mining and Matrices
 Data Mining and Matrices 05 Semi-Discrete Decomposition Rainer Gemulla, Pauli Miettinen May 16, 2013 Outline 1 Hunting the Bump 2 Semi-Discrete Decomposition 3 The Algorithm 4 Applications SDD alone SVD
Data Mining and Matrices 05 Semi-Discrete Decomposition Rainer Gemulla, Pauli Miettinen May 16, 2013 Outline 1 Hunting the Bump 2 Semi-Discrete Decomposition 3 The Algorithm 4 Applications SDD alone SVD
Hadamard speckle contrast reduction
 Published in OPTICS LETTERS 29, -3 (2004) Hadamard speckle contrast reduction Jahja I. Trisnadi Silicon Light Machines, 385 Moffett Park Drive, Sunnyvale, California 94089 The conditon for a diffuser to
Published in OPTICS LETTERS 29, -3 (2004) Hadamard speckle contrast reduction Jahja I. Trisnadi Silicon Light Machines, 385 Moffett Park Drive, Sunnyvale, California 94089 The conditon for a diffuser to
Topic 17: Simple Hypotheses
 Topic 17: November, 2011 1 Overview and Terminology Statistical hypothesis testing is designed to address the question: Do the data provide sufficient evidence to conclude that we must depart from our
Topic 17: November, 2011 1 Overview and Terminology Statistical hypothesis testing is designed to address the question: Do the data provide sufficient evidence to conclude that we must depart from our
LINEAR SYSTEMS (11) Intensive Computation
 LINEAR SYSTEMS () Intensive Computation 27-8 prof. Annalisa Massini Viviana Arrigoni EXACT METHODS:. GAUSSIAN ELIMINATION. 2. CHOLESKY DECOMPOSITION. ITERATIVE METHODS:. JACOBI. 2. GAUSS-SEIDEL 2 CHOLESKY
LINEAR SYSTEMS () Intensive Computation 27-8 prof. Annalisa Massini Viviana Arrigoni EXACT METHODS:. GAUSSIAN ELIMINATION. 2. CHOLESKY DECOMPOSITION. ITERATIVE METHODS:. JACOBI. 2. GAUSS-SEIDEL 2 CHOLESKY
CHAPTER 4 PRINCIPAL COMPONENT ANALYSIS-BASED FUSION
 59 CHAPTER 4 PRINCIPAL COMPONENT ANALYSIS-BASED FUSION 4. INTRODUCTION Weighted average-based fusion algorithms are one of the widely used fusion methods for multi-sensor data integration. These methods
59 CHAPTER 4 PRINCIPAL COMPONENT ANALYSIS-BASED FUSION 4. INTRODUCTION Weighted average-based fusion algorithms are one of the widely used fusion methods for multi-sensor data integration. These methods
Linear & nonlinear classifiers
 Linear & nonlinear classifiers Machine Learning Hamid Beigy Sharif University of Technology Fall 1396 Hamid Beigy (Sharif University of Technology) Linear & nonlinear classifiers Fall 1396 1 / 44 Table
Linear & nonlinear classifiers Machine Learning Hamid Beigy Sharif University of Technology Fall 1396 Hamid Beigy (Sharif University of Technology) Linear & nonlinear classifiers Fall 1396 1 / 44 Table
Compressive Sensing Forensics Xiaoyu Chu, Student Member, IEEE, Matthew Christopher Stamm, Member, IEEE, and K. J. Ray Liu, Fellow, IEEE
 1416 IEEE TRANSACTIONS ON INFORMATION FORENSICS AND SECURITY, VOL. 10, NO. 7, JULY 2015 Compressive Sensing Forensics Xiaoyu Chu, Student Member, IEEE, Matthew Christopher Stamm, Member, IEEE, and K. J.
1416 IEEE TRANSACTIONS ON INFORMATION FORENSICS AND SECURITY, VOL. 10, NO. 7, JULY 2015 Compressive Sensing Forensics Xiaoyu Chu, Student Member, IEEE, Matthew Christopher Stamm, Member, IEEE, and K. J.
Supplemental Material : A Unified Framework for Multi-Target Tracking and Collective Activity Recognition
 Supplemental Material : A Unified Framewor for Multi-Target Tracing and Collective Activity Recognition Wongun Choi and Silvio Savarese Electrical and Computer Engineering University of Michigan Ann Arbor
Supplemental Material : A Unified Framewor for Multi-Target Tracing and Collective Activity Recognition Wongun Choi and Silvio Savarese Electrical and Computer Engineering University of Michigan Ann Arbor
Maximum Likelihood Diffusive Source Localization Based on Binary Observations
 Maximum Lielihood Diffusive Source Localization Based on Binary Observations Yoav Levinboo and an F. Wong Wireless Information Networing Group, University of Florida Gainesville, Florida 32611-6130, USA
Maximum Lielihood Diffusive Source Localization Based on Binary Observations Yoav Levinboo and an F. Wong Wireless Information Networing Group, University of Florida Gainesville, Florida 32611-6130, USA
ECE 661: Homework 10 Fall 2014
 ECE 661: Homework 10 Fall 2014 This homework consists of the following two parts: (1) Face recognition with PCA and LDA for dimensionality reduction and the nearest-neighborhood rule for classification;
ECE 661: Homework 10 Fall 2014 This homework consists of the following two parts: (1) Face recognition with PCA and LDA for dimensionality reduction and the nearest-neighborhood rule for classification;
Dependence and independence
 Roberto s Notes on Linear Algebra Chapter 7: Subspaces Section 1 Dependence and independence What you need to now already: Basic facts and operations involving Euclidean vectors. Matrices determinants
Roberto s Notes on Linear Algebra Chapter 7: Subspaces Section 1 Dependence and independence What you need to now already: Basic facts and operations involving Euclidean vectors. Matrices determinants
Linear Prediction Theory
 Linear Prediction Theory Joseph A. O Sullivan ESE 524 Spring 29 March 3, 29 Overview The problem of estimating a value of a random process given other values of the random process is pervasive. Many problems
Linear Prediction Theory Joseph A. O Sullivan ESE 524 Spring 29 March 3, 29 Overview The problem of estimating a value of a random process given other values of the random process is pervasive. Many problems
EVALUATING THE REPEATABILITY OF TWO STUDIES OF A LARGE NUMBER OF OBJECTS: MODIFIED KENDALL RANK-ORDER ASSOCIATION TEST
 EVALUATING THE REPEATABILITY OF TWO STUDIES OF A LARGE NUMBER OF OBJECTS: MODIFIED KENDALL RANK-ORDER ASSOCIATION TEST TIAN ZHENG, SHAW-HWA LO DEPARTMENT OF STATISTICS, COLUMBIA UNIVERSITY Abstract. In
EVALUATING THE REPEATABILITY OF TWO STUDIES OF A LARGE NUMBER OF OBJECTS: MODIFIED KENDALL RANK-ORDER ASSOCIATION TEST TIAN ZHENG, SHAW-HWA LO DEPARTMENT OF STATISTICS, COLUMBIA UNIVERSITY Abstract. In
Introduction to Statistical Inference
 Structural Health Monitoring Using Statistical Pattern Recognition Introduction to Statistical Inference Presented by Charles R. Farrar, Ph.D., P.E. Outline Introduce statistical decision making for Structural
Structural Health Monitoring Using Statistical Pattern Recognition Introduction to Statistical Inference Presented by Charles R. Farrar, Ph.D., P.E. Outline Introduce statistical decision making for Structural
Solution of Kirchhoff's Time-Domain Integral Equation in Acoustics
 Solution of Kirchhoff's Time-Domain Integral Equation in Acoustics Dr. George Benthien and Dr. Stephen Hobbs March 29, 2005 E-mail: george@gbenthien.net In this paper we will loo at the time-domain equivalent
Solution of Kirchhoff's Time-Domain Integral Equation in Acoustics Dr. George Benthien and Dr. Stephen Hobbs March 29, 2005 E-mail: george@gbenthien.net In this paper we will loo at the time-domain equivalent
Fast Angular Synchronization for Phase Retrieval via Incomplete Information
 Fast Angular Synchronization for Phase Retrieval via Incomplete Information Aditya Viswanathan a and Mark Iwen b a Department of Mathematics, Michigan State University; b Department of Mathematics & Department
Fast Angular Synchronization for Phase Retrieval via Incomplete Information Aditya Viswanathan a and Mark Iwen b a Department of Mathematics, Michigan State University; b Department of Mathematics & Department
Gaussian Mixture Distance for Information Retrieval
 Gaussian Mixture Distance for Information Retrieval X.Q. Li and I. King fxqli, ingg@cse.cuh.edu.h Department of omputer Science & Engineering The hinese University of Hong Kong Shatin, New Territories,
Gaussian Mixture Distance for Information Retrieval X.Q. Li and I. King fxqli, ingg@cse.cuh.edu.h Department of omputer Science & Engineering The hinese University of Hong Kong Shatin, New Territories,
Machine Learning Lecture Notes
 Machine Learning Lecture Notes Predrag Radivojac January 25, 205 Basic Principles of Parameter Estimation In probabilistic modeling, we are typically presented with a set of observations and the objective
Machine Learning Lecture Notes Predrag Radivojac January 25, 205 Basic Principles of Parameter Estimation In probabilistic modeling, we are typically presented with a set of observations and the objective
JPEG-Compatibility Steganalysis Using Block-Histogram of Recompression Artifacts
 JPEG-Compatibility Steganalysis Using Block-Histogram of Recompression Artifacts Jan Kodovský and Jessica Fridrich Department of ECE, Binghamton University, NY, USA {fridrich,jan.kodovsky}@binghamton.edu
JPEG-Compatibility Steganalysis Using Block-Histogram of Recompression Artifacts Jan Kodovský and Jessica Fridrich Department of ECE, Binghamton University, NY, USA {fridrich,jan.kodovsky}@binghamton.edu
Linear Classifiers as Pattern Detectors
 Intelligent Systems: Reasoning and Recognition James L. Crowley ENSIMAG 2 / MoSIG M1 Second Semester 2014/2015 Lesson 16 8 April 2015 Contents Linear Classifiers as Pattern Detectors Notation...2 Linear
Intelligent Systems: Reasoning and Recognition James L. Crowley ENSIMAG 2 / MoSIG M1 Second Semester 2014/2015 Lesson 16 8 April 2015 Contents Linear Classifiers as Pattern Detectors Notation...2 Linear
Synthetic Aperture Radar Ship Detection Using Modified Gamma Fisher Metric
 Progress In Electromagnetics Research Letters, Vol. 68, 85 91, 2017 Synthetic Aperture Radar Ship Detection Using Modified Gamma Fisher Metric Meng Yang * Abstract This article proposes a novel ship detection
Progress In Electromagnetics Research Letters, Vol. 68, 85 91, 2017 Synthetic Aperture Radar Ship Detection Using Modified Gamma Fisher Metric Meng Yang * Abstract This article proposes a novel ship detection
Bayesian Classifiers and Probability Estimation. Vassilis Athitsos CSE 4308/5360: Artificial Intelligence I University of Texas at Arlington
 Bayesian Classifiers and Probability Estimation Vassilis Athitsos CSE 4308/5360: Artificial Intelligence I University of Texas at Arlington 1 Data Space Suppose that we have a classification problem The
Bayesian Classifiers and Probability Estimation Vassilis Athitsos CSE 4308/5360: Artificial Intelligence I University of Texas at Arlington 1 Data Space Suppose that we have a classification problem The
MAT 585: Johnson-Lindenstrauss, Group testing, and Compressed Sensing
 MAT 585: Johnson-Lindenstrauss, Group testing, and Compressed Sensing Afonso S. Bandeira April 9, 2015 1 The Johnson-Lindenstrauss Lemma Suppose one has n points, X = {x 1,..., x n }, in R d with d very
MAT 585: Johnson-Lindenstrauss, Group testing, and Compressed Sensing Afonso S. Bandeira April 9, 2015 1 The Johnson-Lindenstrauss Lemma Suppose one has n points, X = {x 1,..., x n }, in R d with d very
Performance of DS-CDMA Systems With Optimal Hard-Decision Parallel Interference Cancellation
 2918 IEEE TRANSACTIONS ON INFORMATION THEORY, VOL. 49, NO. 11, NOVEMBER 2003 Performance of DS-CDMA Systems With Optimal Hard-Decision Parallel Interference Cancellation Remco van der Hofstad Marten J.
2918 IEEE TRANSACTIONS ON INFORMATION THEORY, VOL. 49, NO. 11, NOVEMBER 2003 Performance of DS-CDMA Systems With Optimal Hard-Decision Parallel Interference Cancellation Remco van der Hofstad Marten J.
Approximate Minimum Bit-Error Rate Multiuser Detection
 Approximate Minimum Bit-Error Rate Multiuser Detection Chen-Chu Yeh, Renato R. opes, and John R. Barry School of Electrical and Computer Engineering Georgia Institute of Technology, Atlanta, Georgia 30332-0250
Approximate Minimum Bit-Error Rate Multiuser Detection Chen-Chu Yeh, Renato R. opes, and John R. Barry School of Electrical and Computer Engineering Georgia Institute of Technology, Atlanta, Georgia 30332-0250
More on Unsupervised Learning
 More on Unsupervised Learning Two types of problems are to find association rules for occurrences in common in observations (market basket analysis), and finding the groups of values of observational data
More on Unsupervised Learning Two types of problems are to find association rules for occurrences in common in observations (market basket analysis), and finding the groups of values of observational data
Introduction: The Perceptron
 Introduction: The Perceptron Haim Sompolinsy, MIT October 4, 203 Perceptron Architecture The simplest type of perceptron has a single layer of weights connecting the inputs and output. Formally, the perceptron
Introduction: The Perceptron Haim Sompolinsy, MIT October 4, 203 Perceptron Architecture The simplest type of perceptron has a single layer of weights connecting the inputs and output. Formally, the perceptron
APPENDIX 1 NEYMAN PEARSON CRITERIA
 54 APPENDIX NEYMAN PEARSON CRITERIA The design approaches for detectors directly follow the theory of hypothesis testing. The primary approaches to hypothesis testing problem are the classical approach
54 APPENDIX NEYMAN PEARSON CRITERIA The design approaches for detectors directly follow the theory of hypothesis testing. The primary approaches to hypothesis testing problem are the classical approach
Data Detection for Controlled ISI. h(nt) = 1 for n=0,1 and zero otherwise.
 Data Detection for Controlled ISI *Symbol by symbol suboptimum detection For the duobinary signal pulse h(nt) = 1 for n=0,1 and zero otherwise. The samples at the output of the receiving filter(demodulator)
Data Detection for Controlled ISI *Symbol by symbol suboptimum detection For the duobinary signal pulse h(nt) = 1 for n=0,1 and zero otherwise. The samples at the output of the receiving filter(demodulator)
Recovery Based on Kolmogorov Complexity in Underdetermined Systems of Linear Equations
 Recovery Based on Kolmogorov Complexity in Underdetermined Systems of Linear Equations David Donoho Department of Statistics Stanford University Email: donoho@stanfordedu Hossein Kakavand, James Mammen
Recovery Based on Kolmogorov Complexity in Underdetermined Systems of Linear Equations David Donoho Department of Statistics Stanford University Email: donoho@stanfordedu Hossein Kakavand, James Mammen
Asymptotically Optimal and Bandwith-efficient Decentralized Detection
 Asymptotically Optimal and Bandwith-efficient Decentralized Detection Yasin Yılmaz and Xiaodong Wang Electrical Engineering Department, Columbia University New Yor, NY 10027 Email: yasin,wangx@ee.columbia.edu
Asymptotically Optimal and Bandwith-efficient Decentralized Detection Yasin Yılmaz and Xiaodong Wang Electrical Engineering Department, Columbia University New Yor, NY 10027 Email: yasin,wangx@ee.columbia.edu
Lecture Notes 1: Vector spaces
 Optimization-based data analysis Fall 2017 Lecture Notes 1: Vector spaces In this chapter we review certain basic concepts of linear algebra, highlighting their application to signal processing. 1 Vector
Optimization-based data analysis Fall 2017 Lecture Notes 1: Vector spaces In this chapter we review certain basic concepts of linear algebra, highlighting their application to signal processing. 1 Vector
NATIONAL RADIO ASTRONOMY OBSERVATORY MEMORANDUM
 NATIONAL RADIO ASTRONOMY OBSERVATORY MEMORANDUM DATE: September 16, 1996 TO: M. Clark, B. Garwood, D. Hogg, H. Liszt FROM: Ron Maddalena SUBJECT: GBT and Aips++ requirements for traditional, all-sky pointing
NATIONAL RADIO ASTRONOMY OBSERVATORY MEMORANDUM DATE: September 16, 1996 TO: M. Clark, B. Garwood, D. Hogg, H. Liszt FROM: Ron Maddalena SUBJECT: GBT and Aips++ requirements for traditional, all-sky pointing
Abstract. 1 Introduction. Cointerpretation of Flow Rate-Pressure-Temperature Data from Permanent Downhole Gauges. Deconvolution. Breakpoint detection
 Cointerpretation of Flow Rate-Pressure-Temperature Data from Permanent Downhole Gauges CS 229 Course Final Report Chuan Tian chuant@stanford.edu Yue Li yuel@stanford.edu Abstract This report documents
Cointerpretation of Flow Rate-Pressure-Temperature Data from Permanent Downhole Gauges CS 229 Course Final Report Chuan Tian chuant@stanford.edu Yue Li yuel@stanford.edu Abstract This report documents
Entity Resolution with Crowd Errors
 Entity Resolution with Crowd Errors Vasilis Verroios Stanford University verroios@stanford.edu Hector Garcia-Molina Stanford University hector@cs.stanford.edu ABSTRACT Given a set of records, an ER algorithm
Entity Resolution with Crowd Errors Vasilis Verroios Stanford University verroios@stanford.edu Hector Garcia-Molina Stanford University hector@cs.stanford.edu ABSTRACT Given a set of records, an ER algorithm
PATTERN RECOGNITION AND MACHINE LEARNING
 PATTERN RECOGNITION AND MACHINE LEARNING Slide Set 3: Detection Theory January 2018 Heikki Huttunen heikki.huttunen@tut.fi Department of Signal Processing Tampere University of Technology Detection theory
PATTERN RECOGNITION AND MACHINE LEARNING Slide Set 3: Detection Theory January 2018 Heikki Huttunen heikki.huttunen@tut.fi Department of Signal Processing Tampere University of Technology Detection theory
Solving Zero-Sum Security Games in Discretized Spatio-Temporal Domains
 Solving Zero-Sum Security Games in Discretized Spatio-Temporal Domains APPENDIX LP Formulation for Constant Number of Resources (Fang et al. 3) For the sae of completeness, we describe the LP formulation
Solving Zero-Sum Security Games in Discretized Spatio-Temporal Domains APPENDIX LP Formulation for Constant Number of Resources (Fang et al. 3) For the sae of completeness, we describe the LP formulation
Defect Detection Using Hidden Markov Random Fields
 Electrical and Computer Engineering Publications Electrical and Computer Engineering 5 Defect Detection Using Hidden Markov Random Fields Aleksandar Dogandžić Iowa State University, ald@iastate.edu Nawanat
Electrical and Computer Engineering Publications Electrical and Computer Engineering 5 Defect Detection Using Hidden Markov Random Fields Aleksandar Dogandžić Iowa State University, ald@iastate.edu Nawanat
Computational statistics
 Computational statistics Markov Chain Monte Carlo methods Thierry Denœux March 2017 Thierry Denœux Computational statistics March 2017 1 / 71 Contents of this chapter When a target density f can be evaluated
Computational statistics Markov Chain Monte Carlo methods Thierry Denœux March 2017 Thierry Denœux Computational statistics March 2017 1 / 71 Contents of this chapter When a target density f can be evaluated
Descriptive Data Summarization
 Descriptive Data Summarization Descriptive data summarization gives the general characteristics of the data and identify the presence of noise or outliers, which is useful for successful data cleaning
Descriptive Data Summarization Descriptive data summarization gives the general characteristics of the data and identify the presence of noise or outliers, which is useful for successful data cleaning
Iterative Solvers. Lab 6. Iterative Methods
 Lab 6 Iterative Solvers Lab Objective: Many real-world problems of the form Ax = b have tens of thousands of parameters Solving such systems with Gaussian elimination or matrix factorizations could require
Lab 6 Iterative Solvers Lab Objective: Many real-world problems of the form Ax = b have tens of thousands of parameters Solving such systems with Gaussian elimination or matrix factorizations could require
Stochastic Monitoring and Testing of Digital LTI Filters
 Stochastic Monitoring and Testing of Digital LTI Filters CHRISTOFOROS N. HADJICOSTIS Department of Electrical and Computer Engineering University of Illinois at Urbana-Champaign 148 C&SRL, 1308 West Main
Stochastic Monitoring and Testing of Digital LTI Filters CHRISTOFOROS N. HADJICOSTIS Department of Electrical and Computer Engineering University of Illinois at Urbana-Champaign 148 C&SRL, 1308 West Main
Performance Analysis and Code Optimization of Low Density Parity-Check Codes on Rayleigh Fading Channels
 Performance Analysis and Code Optimization of Low Density Parity-Check Codes on Rayleigh Fading Channels Jilei Hou, Paul H. Siegel and Laurence B. Milstein Department of Electrical and Computer Engineering
Performance Analysis and Code Optimization of Low Density Parity-Check Codes on Rayleigh Fading Channels Jilei Hou, Paul H. Siegel and Laurence B. Milstein Department of Electrical and Computer Engineering
Half-Pel Accurate Motion-Compensated Orthogonal Video Transforms
 Flierl and Girod: Half-Pel Accurate Motion-Compensated Orthogonal Video Transforms, IEEE DCC, Mar. 007. Half-Pel Accurate Motion-Compensated Orthogonal Video Transforms Markus Flierl and Bernd Girod Max
Flierl and Girod: Half-Pel Accurate Motion-Compensated Orthogonal Video Transforms, IEEE DCC, Mar. 007. Half-Pel Accurate Motion-Compensated Orthogonal Video Transforms Markus Flierl and Bernd Girod Max
A Framework for Optimizing Nonlinear Collusion Attacks on Fingerprinting Systems
 A Framework for Optimizing onlinear Collusion Attacks on Fingerprinting Systems egar iyavash Department of Electrical and Computer Engineering University of Illinois at Urbana-Champaign Coordinated Science
A Framework for Optimizing onlinear Collusion Attacks on Fingerprinting Systems egar iyavash Department of Electrical and Computer Engineering University of Illinois at Urbana-Champaign Coordinated Science
Static-Priority Scheduling. CSCE 990: Real-Time Systems. Steve Goddard. Static-priority Scheduling
 CSCE 990: Real-Time Systems Static-Priority Scheduling Steve Goddard goddard@cse.unl.edu http://www.cse.unl.edu/~goddard/courses/realtimesystems Static-priority Scheduling Real-Time Systems Static-Priority
CSCE 990: Real-Time Systems Static-Priority Scheduling Steve Goddard goddard@cse.unl.edu http://www.cse.unl.edu/~goddard/courses/realtimesystems Static-priority Scheduling Real-Time Systems Static-Priority
Linear Discrimination Functions
 Laurea Magistrale in Informatica Nicola Fanizzi Dipartimento di Informatica Università degli Studi di Bari November 4, 2009 Outline Linear models Gradient descent Perceptron Minimum square error approach
Laurea Magistrale in Informatica Nicola Fanizzi Dipartimento di Informatica Università degli Studi di Bari November 4, 2009 Outline Linear models Gradient descent Perceptron Minimum square error approach
Previously on TT, Target Tracking: Lecture 2 Single Target Tracking Issues. Lecture-2 Outline. Basic ideas on track life
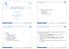 REGLERTEKNIK Previously on TT, AUTOMATIC CONTROL Target Tracing: Lecture 2 Single Target Tracing Issues Emre Özan emre@isy.liu.se Division of Automatic Control Department of Electrical Engineering Linöping
REGLERTEKNIK Previously on TT, AUTOMATIC CONTROL Target Tracing: Lecture 2 Single Target Tracing Issues Emre Özan emre@isy.liu.se Division of Automatic Control Department of Electrical Engineering Linöping
A STATE-SPACE APPROACH FOR THE ANALYSIS OF WAVE AND DIFFUSION FIELDS
 ICASSP 2015 A STATE-SPACE APPROACH FOR THE ANALYSIS OF WAVE AND DIFFUSION FIELDS Stefano Maranò Donat Fäh Hans-Andrea Loeliger ETH Zurich, Swiss Seismological Service, 8092 Zürich ETH Zurich, Dept. Information
ICASSP 2015 A STATE-SPACE APPROACH FOR THE ANALYSIS OF WAVE AND DIFFUSION FIELDS Stefano Maranò Donat Fäh Hans-Andrea Loeliger ETH Zurich, Swiss Seismological Service, 8092 Zürich ETH Zurich, Dept. Information
STONY BROOK UNIVERSITY. CEAS Technical Report 829
 1 STONY BROOK UNIVERSITY CEAS Technical Report 829 Variable and Multiple Target Tracking by Particle Filtering and Maximum Likelihood Monte Carlo Method Jaechan Lim January 4, 2006 2 Abstract In most applications
1 STONY BROOK UNIVERSITY CEAS Technical Report 829 Variable and Multiple Target Tracking by Particle Filtering and Maximum Likelihood Monte Carlo Method Jaechan Lim January 4, 2006 2 Abstract In most applications
Sensor Tasking and Control
 Sensor Tasking and Control Sensing Networking Leonidas Guibas Stanford University Computation CS428 Sensor systems are about sensing, after all... System State Continuous and Discrete Variables The quantities
Sensor Tasking and Control Sensing Networking Leonidas Guibas Stanford University Computation CS428 Sensor systems are about sensing, after all... System State Continuous and Discrete Variables The quantities
Detection of Artificial Satellites in Images Acquired in Track Rate Mode.
 Detection of Artificial Satellites in Images Acquired in Track Rate Mode. Martin P. Lévesque Defence R&D Canada- Valcartier, 2459 Boul. Pie-XI North, Québec, QC, G3J 1X5 Canada, martin.levesque@drdc-rddc.gc.ca
Detection of Artificial Satellites in Images Acquired in Track Rate Mode. Martin P. Lévesque Defence R&D Canada- Valcartier, 2459 Boul. Pie-XI North, Québec, QC, G3J 1X5 Canada, martin.levesque@drdc-rddc.gc.ca
Statistical Models and Algorithms for Real-Time Anomaly Detection Using Multi-Modal Data
 Statistical Models and Algorithms for Real-Time Anomaly Detection Using Multi-Modal Data Taposh Banerjee University of Texas at San Antonio Joint work with Gene Whipps (US Army Research Laboratory) Prudhvi
Statistical Models and Algorithms for Real-Time Anomaly Detection Using Multi-Modal Data Taposh Banerjee University of Texas at San Antonio Joint work with Gene Whipps (US Army Research Laboratory) Prudhvi
THE EGG GAME DR. WILLIAM GASARCH AND STUART FLETCHER
 THE EGG GAME DR. WILLIAM GASARCH AND STUART FLETCHER Abstract. We present a game and proofs for an optimal solution. 1. The Game You are presented with a multistory building and some number of superstrong
THE EGG GAME DR. WILLIAM GASARCH AND STUART FLETCHER Abstract. We present a game and proofs for an optimal solution. 1. The Game You are presented with a multistory building and some number of superstrong
17 Solution of Nonlinear Systems
 17 Solution of Nonlinear Systems We now discuss the solution of systems of nonlinear equations. An important ingredient will be the multivariate Taylor theorem. Theorem 17.1 Let D = {x 1, x 2,..., x m
17 Solution of Nonlinear Systems We now discuss the solution of systems of nonlinear equations. An important ingredient will be the multivariate Taylor theorem. Theorem 17.1 Let D = {x 1, x 2,..., x m
Stochastic Analogues to Deterministic Optimizers
 Stochastic Analogues to Deterministic Optimizers ISMP 2018 Bordeaux, France Vivak Patel Presented by: Mihai Anitescu July 6, 2018 1 Apology I apologize for not being here to give this talk myself. I injured
Stochastic Analogues to Deterministic Optimizers ISMP 2018 Bordeaux, France Vivak Patel Presented by: Mihai Anitescu July 6, 2018 1 Apology I apologize for not being here to give this talk myself. I injured
EXTENDED GLRT DETECTORS OF CORRELATION AND SPHERICITY: THE UNDERSAMPLED REGIME. Xavier Mestre 1, Pascal Vallet 2
 EXTENDED GLRT DETECTORS OF CORRELATION AND SPHERICITY: THE UNDERSAMPLED REGIME Xavier Mestre, Pascal Vallet 2 Centre Tecnològic de Telecomunicacions de Catalunya, Castelldefels, Barcelona (Spain) 2 Institut
EXTENDED GLRT DETECTORS OF CORRELATION AND SPHERICITY: THE UNDERSAMPLED REGIME Xavier Mestre, Pascal Vallet 2 Centre Tecnològic de Telecomunicacions de Catalunya, Castelldefels, Barcelona (Spain) 2 Institut
Lecture 6 Random walks - advanced methods
 Lecture 6: Random wals - advanced methods 1 of 11 Course: M362K Intro to Stochastic Processes Term: Fall 2014 Instructor: Gordan Zitovic Lecture 6 Random wals - advanced methods STOPPING TIMES Our last
Lecture 6: Random wals - advanced methods 1 of 11 Course: M362K Intro to Stochastic Processes Term: Fall 2014 Instructor: Gordan Zitovic Lecture 6 Random wals - advanced methods STOPPING TIMES Our last
EUSIPCO
 EUSIPCO 3 569736677 FULLY ISTRIBUTE SIGNAL ETECTION: APPLICATION TO COGNITIVE RAIO Franc Iutzeler Philippe Ciblat Telecom ParisTech, 46 rue Barrault 753 Paris, France email: firstnamelastname@telecom-paristechfr
EUSIPCO 3 569736677 FULLY ISTRIBUTE SIGNAL ETECTION: APPLICATION TO COGNITIVE RAIO Franc Iutzeler Philippe Ciblat Telecom ParisTech, 46 rue Barrault 753 Paris, France email: firstnamelastname@telecom-paristechfr
