Two binomial methods for evaluating the aggregate claims distribution in De Pril s individual risk model
|
|
|
- Jason Barber
- 6 years ago
- Views:
Transcription
1 Two binomial methods for evaluating the aggregate claims distribution in De Pril s individual risk model Sundt, Bjørn Vital Forsikring ASA P.O.Box 250, N-1326 Lysaker, Norway Phone: (+47) Fax: (+47) bjoern.sundt@vital.no Vernic, Raluca Department of Mathematics and Informatics Ovidius University of Constanta 124, Bd. Mamaia, 8700 Constanta, Romania Fax: (+40) rvernic@univ-ovidius.ro April 16, 2005 Abstract In this paper, we deduce two new methods for evaluating the aggregate claims distribution in De Pril s individual risk model and compare them with some other methods by counting the number of dot operations (multiplications and divisions). Finally we consider one of the new methods in the individual life model. Keywords: De Pril s individual risk model, aggregate claims distribution, recursions. 1
2 1 Introduction 1A. In the present paper, we shall represent probability distributions on the non-negative integers by their probability function, and we shall therefore normally mean the probability function when we refer to a distribution. De Pril (1989) introduced a two-way individual risk model. We consider a portfolio of independent insurance policies during a specified period. It is assumed that a policy can have at most one claim during the period. The claim amounts are positive and integer-valued. In cell (i, j) for i =1, 2,..., I and j =1, 2,...,J, the probability that a claim occurs, is π j and the claim amount distribution given that a claim has occurred, is h i.inthiscell,there are n ij policies. We are interested in the aggregate claims distribution f of the whole portfolio. De Pril (1989) presented two exact methods for recursive evaluation of f and discussed three approximations. Dhaene & Vandebroek (1995) presented another exact method that could be more efficient than De Pril s exact methods. In the present paper, we shall introduce two other exact methods and compare them with the methods of De Pril (1989) and Dhaene & Vandebroek (1995). The first one is based on developing a recursive method for evaluating the probability function f i of the subportfolio of the policies with probability function h i. Finally, we evaluate the convolution f = I i=1f i. For the evaluation of f i, we utilise that the number of claims in cell (i, j) is binomially distributed. Thus, f i is a compound distribution where the counting distribution is a convolution of binomial distributions and the severity distribution is h i, and we apply methodology from Sundt (1992) to deduce a recursion for f i. In the second method, we introduce some features from the first method into Dhaene-Vandebroek s method. Because of the relation between the new methods and the binomial distribution, we shall refer to them as binomial methods. 1B. After having introduced some notation in Section 2, we deduce the first binomial method in Section 3. In this connection, we also recapitulate some results from Sundt (1992). In Section 4, we describe some of the earlier methods for evaluation of f under the present conditions. Section 5 introduces the second binomial method. In Section 6, the methods will be compared by counting the number of dot operations (multiplication and division). Although this criterion is not perfect, it can give an idea of the efficiency of the methods. However, to not put too much into it and not drowning in details, we restrict to the case when the support of all the h i s 2
3 is the set of positive integers, and compare the number of dot operations for the methods in an asymptotic setting. In this situation, we show that the winner is normally the first binomial method when there is a high number of non-empty cells for each i, and Dhaene-Vandebroek s method when there is a low number of non-empty cells for each i. It is also shown that sometimes it can be efficient to combine Dhaeme-Vandebroek s method with one of the binomial methods by using the binomial method for is with many non-empty cells and Dhaene-Vandebroek s method for is with few non-empty cells. Finally, in Section 7, we discuss application of the first binomial method in the individual life model where each severity distribution is concentrated in one point. 2 Notation Let P 0 denote the class of distributions on the non-negative integers with a positive probability at zero and P + the class of distributions on the positive integers. We denote by p h a compound distribution with counting distribution p P 0 and severity distribution h P +,thatis,p h = P n=0 p (n) hn.as h n (x) =0when n>x,wehave (p h)(x) = x p (n) h n (x). (x =0, 1, 2,...) n=0 In subsection 1A, we have already introduced some notation for our De Pril model. Let us now introduce some more. To see how the methods are affected by a finite range of the h i s, we assume that h i has range {1, 2,...,m i }, where m i could either be some positive integer or infinity. We let g ij denote the aggregate claims distribution for a policy in cell (i, j),thatis,g ij = p j h i, where p j is the claim number distribution of the policy, that is, the Bernoulli distribution given by p j (1) = 1 p j (0) = π j.thenwehave g ij (x) = ½ 1 πj (x =0) π j h i (x). (x =1, 2,...,m i ) (2.1) The aggregate claims distribution of all the policies in cell (i, j) is f ij = g n ij Thus, we have f i = J j=1f ij = J j=1g n ij ij. Continuing on this, we obtain f = I i=1f i = I i=1 J j=1 f ij = I i=1 J j=1 g n ij ij = I i=1 J j=1 (p j h i ) nij = I i=1 J j=1 p n ij j hi = I i=1 J j=1 q ij hi = I i=1 (q i h i ), 3 ij.
4 where we have introduced the distribution of the number of claims in cell (i, j), q ij = p n ij j, and the distribution of the number of claims from the union of these cells for fixed i, q i = J j=1q ij. For i =1, 2,...,I,weletJ i be the number of non-empty cells among the cells (i, 1), (i, 2),...,(i, J) and n i = P J j=1 n ij the total number of policies in these cells, and we let J = P I i=1 J i be the total number of non-empty cells. We let [z] denote the greatest integer less than or equal to z and by {z} the smallest integer greater than or equal to z; whenx is a positive integer and m i =, welet{x/m i } =1. We let P b k=a =0when b<a. 3 The first binomial method 3A. Sundt (1992) studied the classes R k of distributions p P 0 that satisfy a recursion in the form p (n) = min(k,n) u=1 µ a (u)+ b (u) n p (n u) ; (n =1, 2,...) (3.1) we denote this distribution by R k [a, b], andwhenk =1,wedroptheargument of a and b. In particular, he proved the following results: Lemma 3.1. A distribution in P 0 can be represented as R k [a, b] if and only if its probability generating function ψ satisfies d ln ψ (s) = ds P k u=1 (ua (u)+b(u)) su 1 1 P k u=1 a (u). su Lemma 3.2. The convolution between a distribution in R k and a distribution in R l is a distribution in R k+l. Lemma 3.3. If p is R k [a, b] and h P +,thenp h is R [c, d] with c (y) = min(k,y) u=1 min(k,y) a (u) h u (y) ; d (y) =y u=1 b (u) u hu (y). (y =1, 2,...) (3.2) Lemma 3.2 easily follows from Lemma 3.1. Panjer (1981) studied the class R 1. In particular, he proved the following lemma. 4
5 Lemma 3.4. The binomial distribution µ m p (n) = π n (1 π) m n (n =0, 1, 2,...,m; 0 <π<1; m =1, 2,...) n (3.3) is R 1 [ π/ (1 π), (m +1)π/ (1 π)]. We denote this distribution by bin (m, π). We now have the main tools for evaluation of f i as defined in subsection 1A: We express the binomial claim number distribution of the policies in cell (i, j) as an R 1 distribution. Then we express the distribution of the aggregate number of claims from these cells as an R Ji distribution, and finally we evaluate f i recursively by Lemma 3.3 and (3.1). 3B. Theorem 8 in Sundt (1992) gives explicit expressions for the functions a and b when expressing the convolution of k R 1 distributions in the form R k [a, b]. In practice, it seems more convenient to do this recursively. We shall deduce such a recursion and start with the following lemma. Lemma 3.5. The convolution of R k 1 [a, b] and R 1 [c, d] is R k [α, β] with α (u) =a (u) ca (u 1) (3.4) β (u) =b (u) cb (u 1) da (u 1). (3.5) for u =1, 2,...,k with a (0) = 1 and a (k) =b (k) =b (0) = 0. Proof. Let ψ k 1, ψ, andψ k denote the probability generating functions of R k 1 [a, b], R 1 [c, d], andr k [α, β]. By using Lemma 3.1, we obtain d ds ln ψ k (s) = d ds ln ψ k 1 (s) ψ (s) = d ds ln ψ k 1 (s)+ d ln ψ (s) = ds P k 1 u=1 (ua (u)+b(u)) su 1 1 P k 1 u=1 a (u) + c + d su 1 cs = ³ su 1 Pk 1 ³ u=1 (ua (u)+b(u)) (1 cs)+(c + d) 1 P k 1 u=1 a (u) su ³ 1 P su = k 1 u=1 a (u) (1 cs) c + d + P k 1 u=1 ((ua (u)+b(u)) su 1 (c (ua (u)+b(u)) + (c + d) a (u)) s u ) ³ 1 cs + P = k 1 u=1 (a (u) su ca (u) s u+1 ) P k u=1 (uα (u)+β (u)) su 1 1 P k u=1 α (u) su 5
6 with α given by (3.4) and uα (u)+β(u) =ua (u)+b(u) c ((u 1) a (u 1) + b (u 1)) (c + d) a (u 1). (u =1, 2,...,k) Solving for β (u) and insertion of (3.4) gives (3.5). This completes the proof of Lemma 3.5. Q.E.D. Theorem 3.1. For k =1, 2,..., the convolution of bin (m 1,π 1 ), bin (m 2,π 2 ),...,bin (m k,π k ) is R k [α k,β k ] where α k and β k can be evaluated recursively by π k α k (u) =α k 1 (u)+ α k 1 (u 1) 1 π k (3.6) β k (u) =β k 1 (u)+ π k (β k 1 (u 1) (m k +1)α k 1 (u 1)) 1 π k (3.7) for k =2, 3,... and u =1, 2,...,k with α k 1 (0) = 1; α k 1 (k) =β k 1 (k) =β k 1 (0) = 0 α 1 (1) = π 1 π 1 ; β 1 (1) = (m 1 +1). (3.8) 1 π 1 1 π 1 Proof. Formula (3.8) follows from Lemma 3.4, and by letting a = α k 1 ; b = β k 1 ; α = α k ; β = β k π k π k c = ; d =(m k +1) 1 π k 1 π k in Lemma 3.5, we obtain (3.6) and (3.7). This completes the proof of Theorem 3.1. Q.E.D. 3C. As pointed out at the end of subsection 3A, f i is a compound distribution with severity distribution h i, and the counting distribution is a convolution of J i binomial distributions. Thus, the counting distribution can be expressed as R Ji [a i,b i ], and the functions a i and b i can be evaluated by Theorem 3.1. From Lemma 3.3 and (3.1), we obtain that f i can be evaluated recursively by f i (x) = min(j i m i,x) µ c i (y)+ d i (y) x f i (x y) (x =1, 2,...) (3.9) 6
7 with c i (y) = min(j i,y) u={y/m i } min(j i,y) a i (u) h u i (y) ; d i (y) =y u={y/m i } (y =1, 2,...,J i m i ) b i (u) u hu i (y) (3.10) f i (0) = q i (0) = JY q ij (0) = j=1 JY p j (0) n ij = j=1 JY (1 π j ) n ij. (3.11) 3D. We can now summarise the algorithm for evaluation of f as follows: 1. For each non-empty cell (i, j), express the claim number distribution q ij as a binomial distribution. 2. For each i: (a) Express the claim number distribution q i in the form R Ji [a i,b i ] by using Theorem 3.1. (b) Express the aggregate claims distribution f i in the form R [c i,d i ] with c i and d i given by (3.10). (c) Evaluate f i recursively by (3.9) and (3.11). j=1 3. Evaluate f = I i=1f i (3.12) by brute force convolution. 4 Earlier methods 4.1 Brute force convolution The most obvious way to evaluate f is by brute force convolution, that is, if g i P 0 for k =1, 2,...,thenweevaluate k i=1g i recursively by k i=1 g i (x) = k 1 i=1 g i gk (x) = x We apply this procedure to evaluate y=0 g k (y) k 1 i=1 g i (x y). (4.1) (x =0, 1, 2,...; k =2, 3,...) f = I i=1 J j=1 f ij. (4.2) 7
8 In particular, this method can be applied by first evaluating f i = J j=1f ij for each i and then f = I i=1f i. For each non-empty cell (i, j), weevaluateg ij by (2.1) and then f ij = g n ij ij by brute force convolution or De Pril s (1985) recursion f ij (x) = 1 g ij (0) min(m i,x) ³(n ij +1) y x 1 g ij (y) f ij (x y), (4.3) (x =1, 2,...,n ij m i ) which can also be expressed as a recursion for a compound binomial distribution f ij (x) = π j 1 π j min(m i,x) ³(n ij +1) y x 1 h i (y) f ij (x y) (x =1, 2,...,n ij m i ) (cf. Lemma 3.4). Using the number of algebraic operations as measure of efficiency, Sundt & Dickson (2000) compare these methods and discuss the most efficient way of applying brute force convolution. 4.2 De Pril s methods Inspired by De Pril (1989), Sundt (1995) pointed out that for any g P 0 there exists a unique function ϕ g such that g is R [0,ϕ g ], and called ϕ g the De Pril transform of g. From (3.1), we immediately get g (x) = 1 x x ϕ g (y) g (x y) (x =1, 2,...) (4.4) and solving for ϕ g (x) gives Ã! ϕ g (x) = 1 x 1 xg (x) ϕ g (y) g (x y). (x =1, 2,...) (4.5) g (0) Furthermore, Lemma 3.3 gives that ϕ p h (x) =x x ϕ p (y) h y (x). (x =1, 2,...) (4.6) y 8
9 Sundt (1995) also showed that ϕ k i=1 g i = k ϕ gi (g 1,g 2,...,g k P 0 ) (4.7) i=1 In De Pril s first exact method, for each non-empty cell (i, j), weevaluate g ij by (2.1) and its De Pril transform ϕ gij by (4.5). From (4.7), we obtain I J ϕ f = n ij ϕ gij, (4.8) i=1 j=1 from which we evaluate f by (4.4), starting with f (0) = IY i=1 j=1 JY (1 π j ) n ij. (4.9) For De Pril s second exact method, we utilise that µ x πj ϕ pj (x) =. (x =1, 2,...) (4.10) π j 1 By insertion of (4.6) in (4.8) and some reorganisation, we obtain ϕ f (x) =x I x i=1 y={x/m i } and insertion of (4.10) gives ϕ f (x) = x I x i=1 y={x/m i } h y i (x) y h y i (x) y J n ij ϕ pj (y), (x =1, 2,...) (4.11) j=1 J µ n ij j=1 πj π j 1 y, (x =1, 2,...) (4.12) by which we evaluate ϕ f. Finally, we evaluate f recursively by (4.4), starting with (4.9). The approximations studied by De Pril (1989) are based on approximating each ϕ pj in (4.11) in De Pril s second exact method by a function that is equal to zero for all y greater than some finite r, and he gave error bounds for the approximations of f. Such approximations have later been discussed by Dhaene & De Pril (1994) and Dhaene & Sundt (1998). As an example of these approximations, we shall consider the rth order De Pril approximation f (r), which is obtained by simply summing up to y = r in the second summation in (4.12), that is, ϕ f (r) (x) = x I min(r,x) i=1 y={x/m i } h y i (x) y J µ n ij j=1 9 πj π j 1 y, (x =1, 2,...)
10 which is equal to zero when x>rmax m i. Finally, we evaluate f (r) recursively by (4.4) with f (r) (0) = f (0). 4.3 Dhaene-Vandebroek s method By inserting (4.8) in (4.4), we obtain f (x) = 1 I J n ij ψ ij (x) x (x =1, 2,...) (4.13) with ψ ij (x) = i=1 j=1 x ϕ gij (y) f (x y). (x =1, 2,...) Dhaene & Vandebroek (1995) showed that for each cell (i, j) we have the recursion ψ ij (x) = 1 min(m i,x) (yf (x y) ψ ij (x y)) g ij (y). (x =1, 2,...) g ij (0) (4.14) with ψ ij (0) = 0. 5 The second binomial method For i =1, 2,...,I and x =1, 2,...,let x ψ i (x) = ϕ fi (y) f (x y) = x j=1 J n ij ϕ gij (y) f (x y) = x ϕ J j=1 g n ij ij J n ij ψ ij (x). j=1 (y) f (x y) = Then f (x) = 1 I ψ i (x). (x =1, 2,...) (5.1) x i=1 From Theorem 11 in Sundt (1995), we obtain that ψ i (x) = min(j i m i,x) ((yc i (y)+d i (y)) f (x y)+c i (y) ψ i (x y)). (5.2) Using this, we can evaluate f in the following way: 10 (x =1, 2,...; i =1, 2,...,I)
11 1. For each non-empty cell (i, j), express the claim number distribution q ij as a binomial distribution. 2. For each i: (a) Express the claim number distribution q i in the form R Ji [a i,b i ] by using Theorem 3.1. (b) Express the aggregate claims distribution f i in the form R [c i,d i ] with c i and d i given by (3.10) 3. For each x: (a) For each i, evaluateψ i (x) recursively by (5.2). (b) Evaluate f (x) by (5.1). 6 Comparison 6A. A characteristic feature of De Pril s model is the two-way classification. We know more than just that we have IJ cells and that the aggregate claims distribution of each policy in cell (i, j) is f ij ;weknowthatf ij = p j h i. Thus, all cells with the same i have the same severity distribution, and all cells with the same j have the same claim frequency, that is, cells with the same i or j have something in common, as opposed to just knowing that all the f ij saredifferent. One would expect this additional information to be reflected in the method of evaluating f and simplify it. This is the case with the two binomial methods and De Pril s second exact method (as well as the approximations based on it), but not with De Pril s first exact method and Dhaene-Vandebroek s method. From these considerations, one should expect that one should just concentrate on De Pril s second exact method and the two binomial methods. Unfortunately, it is not that simple in general. In particular, the outcome would depend on whether the severity distributions have finite or infinite support. One way of comparing the efficiency of methods, is counting elementary algebraic operations; summation, subtraction, multiplication, and division. Such operations are sometimes classified as bar operations (summation and subtraction) and dot operations (multiplication and division) as bar operations are normally less time-consuming on computers than dot operations. Some authors (e.g. Kuon, Reich, & Reimers (1987), Sundt & Dickson (2000), and Dickson & Sundt (2001)) count bar operationsanddotoperationsseparately whereas others (e.g. Bühlmann (1984), Dhaene & Vandebroek (1995), 11
12 and Dhaene, Ribas, & Vernic (2005)) count only dot operations. Sundt & Dickson (2000) discuss reasons for not putting too much emphasis on the counting of algebraic operations. When restricting to dot operations, we also have the additional issue that dot operations can sometimes be converted to bar operations, but that should not be overdone; for a large integer n, itdoes x,butweshalldoitforn =2. It may seem that the effort of pedantically counting all the algebraic operations is not proportional to the value of this measure of efficiency. To only get an idea of the efficiency of the methods, we shall restrict to dot operations and not go too much into detail. Furthermore, we count as if the support of all the severity distributions is the set of all positive integers. This does not mean that the methods break down when a distribution has probability zero for some positive integer. However, in that case, we may count multiplications even when one of the factors is equal to zero. As optimality criterion, we use the number of dot operations needed for evaluating f (x) for x =0, 1, 2,...,s. A more extensive comparison between some of the earlier methods by counting dot operations is done by Dhaene, Ribas, & Vernic (2005). Dickson & Sundt (2001) compare some methods for evaluation of two compound R 1 distributions. not seem reasonable to calculate nx as P n i=1 6B. For a method A, we denote by τ A (s) the number of dot operations needed for evaluation of f (x) for x =0, 1, 2,...,s. The indicator A can have the following values: Indicator B1 B2 BFC DP1 DP2 DV DP(r) Method first binomial method second binomial method brute force convolution De Pril s first exact method De Pril s second exact method Dhaene-Vandebroek s method rth order De Pril approximation The last method is not fully comparable with the others as it is not an exact method, only an approximation. As a measure of efficiency between two methods A and B, we use ε A,B = lim s τ B (s) /τ A (s). Under our present assumptions, the dot operations can typically be classified in three groups when s is sufficiently large: 1. Initial operations that we need to do only once. This is a bit imprecise; there could be recursions there too, like for the evaluation of c i and 12
13 d i in(3.9),butwemeanthatthenumberofdotoperationsdoesnot depend on s. Let us call them α A. 2. Operations that we have to do for each value of x and where the number ofdotoperationsisthesameforallvaluesofx. Let us call them β A. 3. Operations that we have to do for each value of x and where the number of dot operations is proportional with x. Let the proportionality factor be γ A,sothatweneedγ A x operations at the step for x. If Method A satisfies this condition, then τ A (s) =α A + β A s + γ A s x=1 s (s +1) x = α A + β A s + γ A. 2 Thus, if it is satisfied by both Methods A and B with γ A and γ B positive, then s(s+1) τ B (s) ε A,B = lim s τ A (s) = lim α B + β B s + γ B 2 = γ B, s s(s+1) α A + β A s + γ A γ A 2 that is, we need to consider only γ A and γ B. With this procedure, we avoid counting the dot operations for initiating the methods. Hence, for methods with heavy initiation, like the binomials method, the performance would be worse for low values of s. 6C. We shall now count the γ operations for each of various methods. We start with De Pril s first exact method. Here, the γ operations arise for each value of y in the summations in (4.4) and (4.5). At each place, we have one dot operation, and we use (4.4) on one distribution and (4.5) on J distributions. Hence, γ DP1 = J +1. For Dhaene-Vandebroek s method, we rewrite (4.14) as with ψ ij (x) = 1 x 1 v ij (x, y) g ij (x y) (x =1, 2,...) g ij (0) y=0 which can be evaluated recursively by v ij (x, y) =(x y) f (y) ψ ij (y), v ij (x, y) =v ij (x 1,y)+f (y) v ij (y, y) = ψ ij (y). (x = y +1,y+2,...) 13
14 Hence, whereas at first glance it seemed that we needed two dot operations for each y in(4.14),wehavenowreducedittoone. Aswehavetoapply (4.14) on J distributions, we obtain γ DV = J, so that Dhaene-Vandebroek s method is always better than De Pril s first exact method when all the severity distributions have infinite support. We now turn to the first binomial method. Here, the γ operations arise in (3.9), for hi u (x) for u =1, 2,...,J i in (3.10), and when taking the convolution of the f i sin(3.12). Let us first consider the h u i = h (u 1) s. The natural way to do this, is to apply (4.1) on h u i i h i. However, Sundt & Dickson (2000) point out that when u is even, it is usually more efficient to use h u i = h u 2 i h u 2 i. As they considered distributions in P 0 whereas we have distributions in P +,we cannot immediately transfer the results. For the direct method, we utilise that h i (0) = 0 and, thus, h u i (y) =0 when y<u,sothat h u i (x) = x 1 y=u 1 h (u 1) i (y) h i (x y), (x = u, u +1,...) (6.1) which needs x u +1dot operations. When u is even, for x = u, u +1,...,wehave h u i (x) = 2 P x+1 2 y= u 2 2 P x 2 1 y= u 2 x u 2 y= u 2 h u 2 i (y) h u 2 i (x y) = h u 2 i (y) h u 2 h u 2 i (y) h u 2 i i (x y) (x odd) (x y)+h u 2 u x i 2 h 2 (6.2) x i 2, (x even) which gives (x u +3)/2 dot operations when x is odd and (x u +2)/2 when x is even. When counting the γ operations, it is the operations of order x that we have to take into account, that is, one when u is odd, and 1/2 when u is even. Counting as if u is odd half the times, we count as if on the average each of these convolutions contributes to γ B1 with 3/4. Foreachi,wehaveto perform J i 1 such convolutions, so for all is together, we get a contribution to γ B1 of 3 (J 4 I). At first glance, it seems that in (3.9), we need two dot operations for each y. However, by rewriting it as f i (x) = 1 x w i (x, y) f i (x y) (x =1, 2,...) x 14
15 with w i (x, y) =xc i (y)+d i (y), which can be evaluated recursively by w i (x, y) =w i (x 1,y)+c i (y) (y =1, 2,...,x 1) w i (x, x) =xc i (x)+d i (x), we have converted one of the dot operations to bar operation, so that we have only one dot operation left. We have I recursions like (3.9), so totally they contribute with I to γ B1. Finally, each of the I 1 convolutions of f i s in (3.12) contributes to γ B1 with one. Thus, γ B1 = 3 4 (J I)+I + I 1= 3J +5I 1. 4 Comparing with Dhaene-Vandebroek s method, we see that γ B1 <γ DV when J > 5I 4. In particular, this implies that the first binomial method is always better than Dhaene-Vandebroek s method when there are at least five non-empty cells for each value of i. For the second binomial method, the work in the h u i sisthesameas for the first binomial method, that is, the contribution to γ B2 is 3 (J 4 I). Then, for each value of y in (5.2), there are two dot operations (assuming that yc i (y)+d i (y) is evaluated only once for each (y, i), and there are I such recursions. Hence, γ B2 = 3 4 (J I)+2I = 3J +5I. 4 As γ B1 γ B2 =1this method is slightly beaten by the first binomial method, so that we have to discard it. For De Pril s second exact method, we also have to evaluate h u i (x)s. However, whereas for the binomial methods we needed these convolutions up to order J i in (3.10), for De Pril s second exact method, we need them up to order x in (4.12) so that τ DPT2 (s) becomes a polynomial of third order. Hence, for large s, it will perform worse than the other methods. However, in this connection it should be emphasised that the strength of De Pril s second method is as a basis for approximations that will perform better with respect to dot operations. On the other hand, for the rth order De Pril approximation, we need the convolutions only up to order r. WehavetodothisforI distributions, and their total contribution to γ DP(r) is 3 (r 1) I. In addition, we have to apply 4 (4.4) once, so that γ DP(r) = 3 (r 1) I +1. (6.3) 4 15
16 With brute force convolutions, the J 1 convolutions in (4.2) contribute with J 1 to γ BFC. In addition, we have to evaluate f ij = g n ij ij when n ij > 1. At first glance, using (4.3) for one f ij seems to give a contribution of two to γ BFC, but by proceeding like we did with (4.14) and (3.9) above, we can reduce it to one. However, when n ij =2, we can reduce it to 1/2 by proceeding similar to (6.2). Nevertheless, when comparing with Dhaene-Vandebroek s method and the first binomial method, we see that there cannot be more than two cells with more than one policy if brute force convolution should be the best method. These considerations lead to the following conclusions about the exact methods under the present conditions: 1. De Pril s exact methods and the second binomial method can be discarded. 2. Brute force convolution can be discarded unless there are only one or two cells with more than one policy. 3. The first binomial method is better than Dhaene-Vandebroek s method when J > 5I 4. It is logical that it is when there are many non-empty cells with the same severity distribution that the binomial methods perform best, as that is when the extra information through the two-way classification is most significant. 6D. The race between the first binomial method and Dhaene-Vandebroek s method as well as De Pril s first method and the second binomial method is remarkably close. It is amazing that it is the application of (6.2) that rescues the first binomial method. If we had used the direct method (6.1) for all u, then we would have got γ B1 = J I + I + I 1=J + I 1, that is, then the first binomial method is not better than Dhaene-Vandebroek s method for any value of I, and it is better than De Pril s first exact method only when I =1. Furthermore, the first binomial method is more complex to program, even when using (6.1) for all u. It seems surprising if utilisation of the extra information from the twoway classification does not give a larger gain for exact methods. On the other hand, from (6.3) we see that the gain is very pronounced for De Pril approximations of low order. 16
17 6E. We have γ B1 = γ DV = I i=1 I i=1 3J i +5 4 J i 1 (6.4) and analogous if we consider only a subset of the possible is. We could also use a combination of these two methods where we use Dhaene-Vandebroek s method when J i < (3J i +5)/4, thatis,j i < 5, and the first binomial method when J i 5. Thenwegetoneextraconvolution between the aggregate claims distribution of all the policies treated with the first binomial method and the aggregate claims distribution of all the other policies. Let A = {i : J i 5}. Then the γ value of this combined method is γ comb = i A 3J i i ea J i = γ DV i A J i 5 4 = γ bin i ea 5 J i 4 1. Hence, the combined method is at least as good as Dhaene-Vandebroek s method, and it is better than the first binomial method when P i ea (5 J i) > 4. Now let us instead replace the first binomial method with the second binomial method. Then we have to drop the subtraction of one in (6.4). However, that disadvantage is canceled by the advantage that we do not need the extra convolution that we have to do when combining Dhaene-Vandebroek s method with the first binomial method. Hence, in combination with Dhaene- Vandebroek s method, the two binomial methods are equally good with respect to γ operations. However, the second binomial method is more similar to Dhaene-Vandebroek s methods and seems to easier to program for such combinations as we do not need to perform the brute force convolutions of the f i s, so we recommend that method. 7 The firstbinomialmethodintheindividual life model Let us finally consider the first binomial method in the individual life model where each severity distribution is concentrated in one point, that is, for each i, h i is concentrated in one positive integer m i.wenowhave ½ qi (x/m f i (x) = i ) (x =0,m i, 2m i,...,m i n i ) 0 (otherwise) 17
18 and evaluate q i by J i µ q i (x) = Then a i (y)+ b i (y) x [x/m k ] k i=1 f i (x) = Ã ( y=max 0, x P )! k 1 i=1 m i n i m k q i (x y). (x =1, 2,...,n i ) q k (y) k 1 i=1 f i (x mk y), (7.1) ³ x =0, 1, 2,..., P k i=1 m in i ; k =2, 3,...,I and finally we get f = I i=1f i. We would normally have k i=1f i (x) =0for many values of x, and, hence, we ought to try to avoid evaluating the product sum in (7.1) for such values of x. One way to avoid some of these values, is to choose the monetary unit solargethatthem i s do not have any common factor. Furthermore, even in that case, k i=1f i (x) > 0 if and only if x can be written in the form x = k v i m i. (v i =0, 1, 2,...,n i ; i =0, 1, 2,...,k) (7.2) i=1 Hence, we ought to evaluate the product sum only when this condition is satisfied. This can be tested quite simply. We know that k i=1 f i (0) = qk (0) k 1 i=1 f i (0) > 0, whereas, for x =1, 2,..., P k i=1 m in i, k i=1f i (x) > 0 if and only if at least one of the conditions k i=1f i (x mk ) > 0 and i=1 k 1 f i (x mk ) > 0 is satisfied. We could also reduce the summation in (7.1) to the set {y =0, 1, 2,...,[x/m k ]:x m k y satisfies (7.2) with k replaced with k 1}. However, then it seems simpler to just test whether k 1 i=1 f i (x mk y) > 0, so this seems to be stretching too far the criterion of minimising the number of dot operations. The multiplication in x m k y in (7.1) could be avoided by evaluating t k (x, y) =x m k y recursively by t k (x, y) =t k (x, y 1) m k (y =1, 2,...,[x/m k ]) t k (x, 0) = x. 18
19 For a discussion of application of the earlier methods in the individual life model, we refer to Dhaene, Ribas, & Vernic (2005). The procedure we have suggested for the convolution of f 1,f 2,...,f I, can of course also be applied in connection with the brute force convolution method of subsection 4.1. References Bühlmann, H. (1984). Numerical evaluation of the compound Poisson distribution: Recursion or Fast Fourier Transform? Scandinavian Actuarial Journal, De Pril, N. (1985). Recursions for convolutions of arithmetic distributions. ASTIN Bulletin 15, De Pril, N. (1989). The aggregate claims distribution in the individual model with arbitrary positive claims. ASTIN Bulletin 19, Dhaene, J. & De Pril, N. (1994). On a class of approximative computation methods in the individual model. Insurance: Mathematics and Economics 14, Dhaene, J., Ribas, C., & Vernic, R. (2005). Recursions for the individual life model. In preparation. Dhaene, J. & Sundt, B. (1998). On approximating distributions by approximating their De Pril transforms. Scandinavian Actuarial Journal, Dhaene, J. & Vandebroek, M. (1995). Recursions for the individual model. Insurance: Mathenatics and Economics 16, Dickson, D.C.M. & Sundt, B. (2001). Comparison of methods for evaluation of convolutions of two compound R 1 distributions. Scandinavian Actuarial Journal, Kuon, S., Reich, A. & Reimers, S. (1987). Panjer vs Kornya vs De Pril: A comparison. ASTIN Bulletin 17, Letter to the editors. ASTIN Bulletin 18, Panjer, H.H. (1981). Recursive evaluation of a family of compound distributions. ASTIN Bulletin 12, Sundt, B. (1992). On some extensions of Panjer s class of counting distributions. ASTIN Bulletin 22, Sundt, B. (1995). On some properties of De Pril transforms of counting distributions. ASTIN Bulletin 25,
20 Sundt, B. & Dickson, D.C.M. (2000). Comparison of methods for evaluation of the n-fold convolution of an arithmetic distribution. Bulletin of the Swiss Association of Actuaries,
EVALUATING THE BIVARIATE COMPOUND GENERALIZED POISSON DISTRIBUTION
 An. Şt. Univ. Ovidius Constanţa Vol. 92), 2001, 181 192 EVALUATING THE BIVARIATE COMPOUND GENERALIZED POISSON DISTRIBUTION Raluca Vernic Dedicated to Professor Mirela Ştefănescu on the occasion of her
An. Şt. Univ. Ovidius Constanţa Vol. 92), 2001, 181 192 EVALUATING THE BIVARIATE COMPOUND GENERALIZED POISSON DISTRIBUTION Raluca Vernic Dedicated to Professor Mirela Ştefănescu on the occasion of her
ON BOUNDS FOR THE DIFFERENCE BETWEEN THE STOP-LOSS TRANSFORMS OF TWO COMPOUND DISTRIBUTIONS
 ON BOUNDS FOR THE DIFFERENCE BETWEEN THE STOP-LOSS TRANSFORMS OF TWO COMPOUND DISTRIBUTIONS BJORN SUNDT I AND JAN DHAENE 2 ABSTRACT In the present note we deduce a class of bounds for the difference between
ON BOUNDS FOR THE DIFFERENCE BETWEEN THE STOP-LOSS TRANSFORMS OF TWO COMPOUND DISTRIBUTIONS BJORN SUNDT I AND JAN DHAENE 2 ABSTRACT In the present note we deduce a class of bounds for the difference between
DEP ARTEMENT TOEGEP ASTE ECONOMISCHE WETENSCHAPPEN
 DEP ARTEMENT TOEGEP ASTE ECONOMISCHE WETENSCHAPPEN ONDERZOEKSRAPPORT NR 9513 Some Moment Relations for the Hipp Approximation by JanDHAENE Bj0mSUNDT Nelson DE PRIL Katholieke Universiteit Leuven Naamsestraat
DEP ARTEMENT TOEGEP ASTE ECONOMISCHE WETENSCHAPPEN ONDERZOEKSRAPPORT NR 9513 Some Moment Relations for the Hipp Approximation by JanDHAENE Bj0mSUNDT Nelson DE PRIL Katholieke Universiteit Leuven Naamsestraat
. As the binomial coefficients are integers we have that. 2 n(n 1).
 Math 580 Homework. 1. Divisibility. Definition 1. Let a, b be integers with a 0. Then b divides b iff there is an integer k such that b = ka. In the case we write a b. In this case we also say a is a factor
Math 580 Homework. 1. Divisibility. Definition 1. Let a, b be integers with a 0. Then b divides b iff there is an integer k such that b = ka. In the case we write a b. In this case we also say a is a factor
Ruin Probabilities of a Discrete-time Multi-risk Model
 Ruin Probabilities of a Discrete-time Multi-risk Model Andrius Grigutis, Agneška Korvel, Jonas Šiaulys Faculty of Mathematics and Informatics, Vilnius University, Naugarduko 4, Vilnius LT-035, Lithuania
Ruin Probabilities of a Discrete-time Multi-risk Model Andrius Grigutis, Agneška Korvel, Jonas Šiaulys Faculty of Mathematics and Informatics, Vilnius University, Naugarduko 4, Vilnius LT-035, Lithuania
The Sommerfeld Polynomial Method: Harmonic Oscillator Example
 Chemistry 460 Fall 2017 Dr. Jean M. Standard October 2, 2017 The Sommerfeld Polynomial Method: Harmonic Oscillator Example Scaling the Harmonic Oscillator Equation Recall the basic definitions of the harmonic
Chemistry 460 Fall 2017 Dr. Jean M. Standard October 2, 2017 The Sommerfeld Polynomial Method: Harmonic Oscillator Example Scaling the Harmonic Oscillator Equation Recall the basic definitions of the harmonic
The compound Poisson random variable s approximation to the individual risk model
 Insurance: Mathematics and Economics 36 (25) 57 77 The compound Poisson random variable s approximation to the individual risk model Jingping Yang, Shulin Zhou, Zhenyong Zhang LMAM, School of Mathematical
Insurance: Mathematics and Economics 36 (25) 57 77 The compound Poisson random variable s approximation to the individual risk model Jingping Yang, Shulin Zhou, Zhenyong Zhang LMAM, School of Mathematical
Notes on generating functions in automata theory
 Notes on generating functions in automata theory Benjamin Steinberg December 5, 2009 Contents Introduction: Calculus can count 2 Formal power series 5 3 Rational power series 9 3. Rational power series
Notes on generating functions in automata theory Benjamin Steinberg December 5, 2009 Contents Introduction: Calculus can count 2 Formal power series 5 3 Rational power series 9 3. Rational power series
Estimating VaR in credit risk: Aggregate vs single loss distribution
 Estimating VaR in credit risk: Aggregate vs single loss distribution M. Assadsolimani and D. Chetalova arxiv:172.4388v1 [q-fin.cp] 14 Feb 217 Abstract Using Monte Carlo simulation to calculate the Value
Estimating VaR in credit risk: Aggregate vs single loss distribution M. Assadsolimani and D. Chetalova arxiv:172.4388v1 [q-fin.cp] 14 Feb 217 Abstract Using Monte Carlo simulation to calculate the Value
Chebyshev coordinates and Salem numbers
 Chebyshev coordinates and Salem numbers S.Capparelli and A. Del Fra arxiv:181.11869v1 [math.co] 31 Dec 018 January 1, 019 Abstract By expressing polynomials in the basis of Chebyshev polynomials, certain
Chebyshev coordinates and Salem numbers S.Capparelli and A. Del Fra arxiv:181.11869v1 [math.co] 31 Dec 018 January 1, 019 Abstract By expressing polynomials in the basis of Chebyshev polynomials, certain
WUCT121. Discrete Mathematics. Numbers
 WUCT121 Discrete Mathematics Numbers 1. Natural Numbers 2. Integers and Real Numbers 3. The Principle of Mathematical Induction 4. Elementary Number Theory 5. Congruence Arithmetic WUCT121 Numbers 1 Section
WUCT121 Discrete Mathematics Numbers 1. Natural Numbers 2. Integers and Real Numbers 3. The Principle of Mathematical Induction 4. Elementary Number Theory 5. Congruence Arithmetic WUCT121 Numbers 1 Section
CHAPTER 4: EXPLORING Z
 CHAPTER 4: EXPLORING Z MATH 378, CSUSM. SPRING 2009. AITKEN 1. Introduction In this chapter we continue the study of the ring Z. We begin with absolute values. The absolute value function Z N is the identity
CHAPTER 4: EXPLORING Z MATH 378, CSUSM. SPRING 2009. AITKEN 1. Introduction In this chapter we continue the study of the ring Z. We begin with absolute values. The absolute value function Z N is the identity
1 Basic Combinatorics
 1 Basic Combinatorics 1.1 Sets and sequences Sets. A set is an unordered collection of distinct objects. The objects are called elements of the set. We use braces to denote a set, for example, the set
1 Basic Combinatorics 1.1 Sets and sequences Sets. A set is an unordered collection of distinct objects. The objects are called elements of the set. We use braces to denote a set, for example, the set
The theory of numbers
 1 AXIOMS FOR THE INTEGERS 1 The theory of numbers UCU Foundations of Mathematics course 2017 Author: F. Beukers 1 Axioms for the integers Roughly speaking, number theory is the mathematics of the integers.
1 AXIOMS FOR THE INTEGERS 1 The theory of numbers UCU Foundations of Mathematics course 2017 Author: F. Beukers 1 Axioms for the integers Roughly speaking, number theory is the mathematics of the integers.
Recursive Calculation of Finite Time Ruin Probabilities Under Interest Force
 Recursive Calculation of Finite Time Ruin Probabilities Under Interest Force Rui M R Cardoso and Howard R Waters Abstract In this paper we consider a classical insurance surplus process affected by a constant
Recursive Calculation of Finite Time Ruin Probabilities Under Interest Force Rui M R Cardoso and Howard R Waters Abstract In this paper we consider a classical insurance surplus process affected by a constant
On the Infinitude of Twin-Primes Bao Qi Feng
 On the Infinitude of Twin-Primes Bao Qi Feng Department of Mathematical Sciences, Kent State University at Tuscarawas 330 University Dr. NE, New Philadelphia, OH 44663, USA. Abstract In this article, we
On the Infinitude of Twin-Primes Bao Qi Feng Department of Mathematical Sciences, Kent State University at Tuscarawas 330 University Dr. NE, New Philadelphia, OH 44663, USA. Abstract In this article, we
Math 324 Summer 2012 Elementary Number Theory Notes on Mathematical Induction
 Math 4 Summer 01 Elementary Number Theory Notes on Mathematical Induction Principle of Mathematical Induction Recall the following axiom for the set of integers. Well-Ordering Axiom for the Integers If
Math 4 Summer 01 Elementary Number Theory Notes on Mathematical Induction Principle of Mathematical Induction Recall the following axiom for the set of integers. Well-Ordering Axiom for the Integers If
On the discounted penalty function in a discrete time renewal risk model with general interclaim times
 On the discounted penalty function in a discrete time renewal risk model with general interclaim times Xueyuan Wu, Shuanming Li Centre for Actuarial Studies, Department of Economics The University of Melbourne,
On the discounted penalty function in a discrete time renewal risk model with general interclaim times Xueyuan Wu, Shuanming Li Centre for Actuarial Studies, Department of Economics The University of Melbourne,
MATH 117 LECTURE NOTES
 MATH 117 LECTURE NOTES XIN ZHOU Abstract. This is the set of lecture notes for Math 117 during Fall quarter of 2017 at UC Santa Barbara. The lectures follow closely the textbook [1]. Contents 1. The set
MATH 117 LECTURE NOTES XIN ZHOU Abstract. This is the set of lecture notes for Math 117 during Fall quarter of 2017 at UC Santa Barbara. The lectures follow closely the textbook [1]. Contents 1. The set
Contribution of Problems
 Exam topics 1. Basic structures: sets, lists, functions (a) Sets { }: write all elements, or define by condition (b) Set operations: A B, A B, A\B, A c (c) Lists ( ): Cartesian product A B (d) Functions
Exam topics 1. Basic structures: sets, lists, functions (a) Sets { }: write all elements, or define by condition (b) Set operations: A B, A B, A\B, A c (c) Lists ( ): Cartesian product A B (d) Functions
Algorithms: Lecture 2
 1 Algorithms: Lecture 2 Basic Structures: Sets, Functions, Sequences, and Sums Jinwoo Kim jwkim@jjay.cuny.edu 2.1 Sets 2 1 2.1 Sets 3 2.1 Sets 4 2 2.1 Sets 5 2.1 Sets 6 3 2.1 Sets 7 2.2 Set Operations
1 Algorithms: Lecture 2 Basic Structures: Sets, Functions, Sequences, and Sums Jinwoo Kim jwkim@jjay.cuny.edu 2.1 Sets 2 1 2.1 Sets 3 2.1 Sets 4 2 2.1 Sets 5 2.1 Sets 6 3 2.1 Sets 7 2.2 Set Operations
Mathematics 324 Riemann Zeta Function August 5, 2005
 Mathematics 324 Riemann Zeta Function August 5, 25 In this note we give an introduction to the Riemann zeta function, which connects the ideas of real analysis with the arithmetic of the integers. Define
Mathematics 324 Riemann Zeta Function August 5, 25 In this note we give an introduction to the Riemann zeta function, which connects the ideas of real analysis with the arithmetic of the integers. Define
ON THE TRUNCATED COMPOSITE WEIBULL-PARETO MODEL
 ON THE TRUNCATED COMPOSITE WEIBULL-PARETO MODEL SANDRA TEODORESCU and EUGENIA PANAITESCU The composite Weibull-Pareto model 2] was introduced as an alternative to the composite Lognormal-Pareto ] used
ON THE TRUNCATED COMPOSITE WEIBULL-PARETO MODEL SANDRA TEODORESCU and EUGENIA PANAITESCU The composite Weibull-Pareto model 2] was introduced as an alternative to the composite Lognormal-Pareto ] used
On a discrete time risk model with delayed claims and a constant dividend barrier
 On a discrete time risk model with delayed claims and a constant dividend barrier Xueyuan Wu, Shuanming Li Centre for Actuarial Studies, Department of Economics The University of Melbourne, Parkville,
On a discrete time risk model with delayed claims and a constant dividend barrier Xueyuan Wu, Shuanming Li Centre for Actuarial Studies, Department of Economics The University of Melbourne, Parkville,
Algebra II Vocabulary Word Wall Cards
 Algebra II Vocabulary Word Wall Cards Mathematics vocabulary word wall cards provide a display of mathematics content words and associated visual cues to assist in vocabulary development. The cards should
Algebra II Vocabulary Word Wall Cards Mathematics vocabulary word wall cards provide a display of mathematics content words and associated visual cues to assist in vocabulary development. The cards should
Math Lecture 18 Notes
 Math 1010 - Lecture 18 Notes Dylan Zwick Fall 2009 In our last lecture we talked about how we can add, subtract, and multiply polynomials, and we figured out that, basically, if you can add, subtract,
Math 1010 - Lecture 18 Notes Dylan Zwick Fall 2009 In our last lecture we talked about how we can add, subtract, and multiply polynomials, and we figured out that, basically, if you can add, subtract,
Fermat's Little Theorem
 Fermat's Little Theorem CS 2800: Discrete Structures, Spring 2015 Sid Chaudhuri Not to be confused with... Fermat's Last Theorem: x n + y n = z n has no integer solution for n > 2 Recap: Modular Arithmetic
Fermat's Little Theorem CS 2800: Discrete Structures, Spring 2015 Sid Chaudhuri Not to be confused with... Fermat's Last Theorem: x n + y n = z n has no integer solution for n > 2 Recap: Modular Arithmetic
Introduction and Preliminaries
 Chapter 1 Introduction and Preliminaries This chapter serves two purposes. The first purpose is to prepare the readers for the more systematic development in later chapters of methods of real analysis
Chapter 1 Introduction and Preliminaries This chapter serves two purposes. The first purpose is to prepare the readers for the more systematic development in later chapters of methods of real analysis
Applying the proportional hazard premium calculation principle
 Applying the proportional hazard premium calculation principle Maria de Lourdes Centeno and João Andrade e Silva CEMAPRE, ISEG, Technical University of Lisbon, Rua do Quelhas, 2, 12 781 Lisbon, Portugal
Applying the proportional hazard premium calculation principle Maria de Lourdes Centeno and João Andrade e Silva CEMAPRE, ISEG, Technical University of Lisbon, Rua do Quelhas, 2, 12 781 Lisbon, Portugal
ON THE BIVARIATE GENERALIZED POISSON DISTRIBUTION. University "Ovidius" Constanta, Romania
 ON THE BIVARIATE GENERALIZED POISSON DISTRIBUTION RALUCA VERNIC University "Ovidius" Constanta, Romania ABSTRACT This paper deals with the bivariate generalized Poisson distribution. The distribution is
ON THE BIVARIATE GENERALIZED POISSON DISTRIBUTION RALUCA VERNIC University "Ovidius" Constanta, Romania ABSTRACT This paper deals with the bivariate generalized Poisson distribution. The distribution is
ELEMENTARY LINEAR ALGEBRA
 ELEMENTARY LINEAR ALGEBRA K R MATTHEWS DEPARTMENT OF MATHEMATICS UNIVERSITY OF QUEENSLAND First Printing, 99 Chapter LINEAR EQUATIONS Introduction to linear equations A linear equation in n unknowns x,
ELEMENTARY LINEAR ALGEBRA K R MATTHEWS DEPARTMENT OF MATHEMATICS UNIVERSITY OF QUEENSLAND First Printing, 99 Chapter LINEAR EQUATIONS Introduction to linear equations A linear equation in n unknowns x,
The Distributions of Stopping Times For Ordinary And Compound Poisson Processes With Non-Linear Boundaries: Applications to Sequential Estimation.
 The Distributions of Stopping Times For Ordinary And Compound Poisson Processes With Non-Linear Boundaries: Applications to Sequential Estimation. Binghamton University Department of Mathematical Sciences
The Distributions of Stopping Times For Ordinary And Compound Poisson Processes With Non-Linear Boundaries: Applications to Sequential Estimation. Binghamton University Department of Mathematical Sciences
What is an inequality? What is an equation? What do the algebraic and graphical solutions to an equation or inequality represent?
 WDHS Curriculum Map: created by Christina Berth, Jaclyn Falcone, Julia Holloway Course: RC Algebra I July 2013 Time Interval/ Content Standards/ Strands Essential Questions Skills Assessment Unit 1: Solving
WDHS Curriculum Map: created by Christina Berth, Jaclyn Falcone, Julia Holloway Course: RC Algebra I July 2013 Time Interval/ Content Standards/ Strands Essential Questions Skills Assessment Unit 1: Solving
Solving a linear equation in a set of integers II
 ACTA ARITHMETICA LXXII.4 (1995) Solving a linear equation in a set of integers II by Imre Z. Ruzsa (Budapest) 1. Introduction. We continue the study of linear equations started in Part I of this paper.
ACTA ARITHMETICA LXXII.4 (1995) Solving a linear equation in a set of integers II by Imre Z. Ruzsa (Budapest) 1. Introduction. We continue the study of linear equations started in Part I of this paper.
Assignment 10. Arfken Show that Stirling s formula is an asymptotic expansion. The remainder term is. B 2n 2n(2n 1) x1 2n.
 Assignment Arfken 5.. Show that Stirling s formula is an asymptotic expansion. The remainder term is R N (x nn+ for some N. The condition for an asymptotic series, lim x xn R N lim x nn+ B n n(n x n B
Assignment Arfken 5.. Show that Stirling s formula is an asymptotic expansion. The remainder term is R N (x nn+ for some N. The condition for an asymptotic series, lim x xn R N lim x nn+ B n n(n x n B
Discrete Mathematics and Probability Theory Fall 2013 Vazirani Note 1
 CS 70 Discrete Mathematics and Probability Theory Fall 013 Vazirani Note 1 Induction Induction is a basic, powerful and widely used proof technique. It is one of the most common techniques for analyzing
CS 70 Discrete Mathematics and Probability Theory Fall 013 Vazirani Note 1 Induction Induction is a basic, powerful and widely used proof technique. It is one of the most common techniques for analyzing
1 Homework. Recommended Reading:
 Analysis MT43C Notes/Problems/Homework Recommended Reading: R. G. Bartle, D. R. Sherbert Introduction to real analysis, principal reference M. Spivak Calculus W. Rudin Principles of mathematical analysis
Analysis MT43C Notes/Problems/Homework Recommended Reading: R. G. Bartle, D. R. Sherbert Introduction to real analysis, principal reference M. Spivak Calculus W. Rudin Principles of mathematical analysis
DR.RUPNATHJI( DR.RUPAK NATH )
 Contents 1 Sets 1 2 The Real Numbers 9 3 Sequences 29 4 Series 59 5 Functions 81 6 Power Series 105 7 The elementary functions 111 Chapter 1 Sets It is very convenient to introduce some notation and terminology
Contents 1 Sets 1 2 The Real Numbers 9 3 Sequences 29 4 Series 59 5 Functions 81 6 Power Series 105 7 The elementary functions 111 Chapter 1 Sets It is very convenient to introduce some notation and terminology
COMPLETELY INVARIANT JULIA SETS OF POLYNOMIAL SEMIGROUPS
 Series Logo Volume 00, Number 00, Xxxx 19xx COMPLETELY INVARIANT JULIA SETS OF POLYNOMIAL SEMIGROUPS RICH STANKEWITZ Abstract. Let G be a semigroup of rational functions of degree at least two, under composition
Series Logo Volume 00, Number 00, Xxxx 19xx COMPLETELY INVARIANT JULIA SETS OF POLYNOMIAL SEMIGROUPS RICH STANKEWITZ Abstract. Let G be a semigroup of rational functions of degree at least two, under composition
PANJER CLASS UNITED One formula for the probabilities of the Poisson, Binomial, and Negative Binomial distribution.
 PANJER CLASS UNITED One formula for the probabilities of the Poisson, Binomial, and Negative Binomial distribution Michael Facler 1 Abstract. This paper gives a formula representing all discrete loss distributions
PANJER CLASS UNITED One formula for the probabilities of the Poisson, Binomial, and Negative Binomial distribution Michael Facler 1 Abstract. This paper gives a formula representing all discrete loss distributions
On the Converse Law of Large Numbers
 On the Converse Law of Large Numbers H. Jerome Keisler Yeneng Sun This version: March 15, 2018 Abstract Given a triangular array of random variables and a growth rate without a full upper asymptotic density,
On the Converse Law of Large Numbers H. Jerome Keisler Yeneng Sun This version: March 15, 2018 Abstract Given a triangular array of random variables and a growth rate without a full upper asymptotic density,
a 11 x 1 + a 12 x a 1n x n = b 1 a 21 x 1 + a 22 x a 2n x n = b 2.
 Chapter 1 LINEAR EQUATIONS 11 Introduction to linear equations A linear equation in n unknowns x 1, x,, x n is an equation of the form a 1 x 1 + a x + + a n x n = b, where a 1, a,, a n, b are given real
Chapter 1 LINEAR EQUATIONS 11 Introduction to linear equations A linear equation in n unknowns x 1, x,, x n is an equation of the form a 1 x 1 + a x + + a n x n = b, where a 1, a,, a n, b are given real
On binary reflected Gray codes and functions
 Discrete Mathematics 308 (008) 1690 1700 www.elsevier.com/locate/disc On binary reflected Gray codes and functions Martin W. Bunder, Keith P. Tognetti, Glen E. Wheeler School of Mathematics and Applied
Discrete Mathematics 308 (008) 1690 1700 www.elsevier.com/locate/disc On binary reflected Gray codes and functions Martin W. Bunder, Keith P. Tognetti, Glen E. Wheeler School of Mathematics and Applied
Subquadratic Space Complexity Multiplication over Binary Fields with Dickson Polynomial Representation
 Subquadratic Space Complexity Multiplication over Binary Fields with Dickson Polynomial Representation M A Hasan and C Negre Abstract We study Dickson bases for binary field representation Such representation
Subquadratic Space Complexity Multiplication over Binary Fields with Dickson Polynomial Representation M A Hasan and C Negre Abstract We study Dickson bases for binary field representation Such representation
Part IA Numbers and Sets
 Part IA Numbers and Sets Definitions Based on lectures by A. G. Thomason Notes taken by Dexter Chua Michaelmas 2014 These notes are not endorsed by the lecturers, and I have modified them (often significantly)
Part IA Numbers and Sets Definitions Based on lectures by A. G. Thomason Notes taken by Dexter Chua Michaelmas 2014 These notes are not endorsed by the lecturers, and I have modified them (often significantly)
MATH10040 Chapter 1: Integers and divisibility
 MATH10040 Chapter 1: Integers and divisibility Recall the basic definition: 1. Divisibilty Definition 1.1. If a, b Z, we say that b divides a, or that a is a multiple of b and we write b a if there is
MATH10040 Chapter 1: Integers and divisibility Recall the basic definition: 1. Divisibilty Definition 1.1. If a, b Z, we say that b divides a, or that a is a multiple of b and we write b a if there is
NOTES ON FINITE FIELDS
 NOTES ON FINITE FIELDS AARON LANDESMAN CONTENTS 1. Introduction to finite fields 2 2. Definition and constructions of fields 3 2.1. The definition of a field 3 2.2. Constructing field extensions by adjoining
NOTES ON FINITE FIELDS AARON LANDESMAN CONTENTS 1. Introduction to finite fields 2 2. Definition and constructions of fields 3 2.1. The definition of a field 3 2.2. Constructing field extensions by adjoining
Fourier Analysis Fourier Series C H A P T E R 1 1
 C H A P T E R Fourier Analysis 474 This chapter on Fourier analysis covers three broad areas: Fourier series in Secs...4, more general orthonormal series called Sturm iouville epansions in Secs..5 and.6
C H A P T E R Fourier Analysis 474 This chapter on Fourier analysis covers three broad areas: Fourier series in Secs...4, more general orthonormal series called Sturm iouville epansions in Secs..5 and.6
A Study of the Impact of a Bonus-Malus System in Finite and Continuous Time Ruin Probabilities in Motor Insurance
 A Study of the Impact of a Bonus-Malus System in Finite and Continuous Time Ruin Probabilities in Motor Insurance L.B. Afonso, R.M.R. Cardoso, A.D. Egídio dos Reis, G.R Guerreiro This work was partially
A Study of the Impact of a Bonus-Malus System in Finite and Continuous Time Ruin Probabilities in Motor Insurance L.B. Afonso, R.M.R. Cardoso, A.D. Egídio dos Reis, G.R Guerreiro This work was partially
PUTNAM TRAINING NUMBER THEORY. Exercises 1. Show that the sum of two consecutive primes is never twice a prime.
 PUTNAM TRAINING NUMBER THEORY (Last updated: December 11, 2017) Remark. This is a list of exercises on Number Theory. Miguel A. Lerma Exercises 1. Show that the sum of two consecutive primes is never twice
PUTNAM TRAINING NUMBER THEORY (Last updated: December 11, 2017) Remark. This is a list of exercises on Number Theory. Miguel A. Lerma Exercises 1. Show that the sum of two consecutive primes is never twice
Undergraduate Notes in Mathematics. Arkansas Tech University Department of Mathematics. College Algebra for STEM
 Undergraduate Notes in Mathematics Arkansas Tech University Department of Mathematics College Algebra for STEM Marcel B. Finan c All Rights Reserved 2015 Edition To my children Amin & Nadia Preface From
Undergraduate Notes in Mathematics Arkansas Tech University Department of Mathematics College Algebra for STEM Marcel B. Finan c All Rights Reserved 2015 Edition To my children Amin & Nadia Preface From
Upper Bounds for the Ruin Probability in a Risk Model With Interest WhosePremiumsDependonthe Backward Recurrence Time Process
 Λ4flΛ4» ν ff ff χ Vol.4, No.4 211 8fl ADVANCES IN MATHEMATICS Aug., 211 Upper Bounds for the Ruin Probability in a Risk Model With Interest WhosePremiumsDependonthe Backward Recurrence Time Process HE
Λ4flΛ4» ν ff ff χ Vol.4, No.4 211 8fl ADVANCES IN MATHEMATICS Aug., 211 Upper Bounds for the Ruin Probability in a Risk Model With Interest WhosePremiumsDependonthe Backward Recurrence Time Process HE
West Windsor-Plainsboro Regional School District Algebra Grade 8
 West Windsor-Plainsboro Regional School District Algebra Grade 8 Content Area: Mathematics Unit 1: Foundations of Algebra This unit involves the study of real numbers and the language of algebra. Using
West Windsor-Plainsboro Regional School District Algebra Grade 8 Content Area: Mathematics Unit 1: Foundations of Algebra This unit involves the study of real numbers and the language of algebra. Using
Generating Functions of Partitions
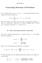 CHAPTER B Generating Functions of Partitions For a complex sequence {α n n 0,, 2, }, its generating function with a complex variable q is defined by A(q) : α n q n α n [q n ] A(q). When the sequence has
CHAPTER B Generating Functions of Partitions For a complex sequence {α n n 0,, 2, }, its generating function with a complex variable q is defined by A(q) : α n q n α n [q n ] A(q). When the sequence has
Some approximation theorems in Math 522. I. Approximations of continuous functions by smooth functions
 Some approximation theorems in Math 522 I. Approximations of continuous functions by smooth functions The goal is to approximate continuous functions vanishing at ± by smooth functions. In a previous homewor
Some approximation theorems in Math 522 I. Approximations of continuous functions by smooth functions The goal is to approximate continuous functions vanishing at ± by smooth functions. In a previous homewor
SECTION 9.2: ARITHMETIC SEQUENCES and PARTIAL SUMS
 (Chapter 9: Discrete Math) 9.11 SECTION 9.2: ARITHMETIC SEQUENCES and PARTIAL SUMS PART A: WHAT IS AN ARITHMETIC SEQUENCE? The following appears to be an example of an arithmetic (stress on the me ) sequence:
(Chapter 9: Discrete Math) 9.11 SECTION 9.2: ARITHMETIC SEQUENCES and PARTIAL SUMS PART A: WHAT IS AN ARITHMETIC SEQUENCE? The following appears to be an example of an arithmetic (stress on the me ) sequence:
A matrix over a field F is a rectangular array of elements from F. The symbol
 Chapter MATRICES Matrix arithmetic A matrix over a field F is a rectangular array of elements from F The symbol M m n (F ) denotes the collection of all m n matrices over F Matrices will usually be denoted
Chapter MATRICES Matrix arithmetic A matrix over a field F is a rectangular array of elements from F The symbol M m n (F ) denotes the collection of all m n matrices over F Matrices will usually be denoted
Epsilon Delta proofs
 Epsilon Delta proofs Before reading this guide, please go over inequalities (if needed). Eample Prove lim(4 3) = 5 2 First we have to know what the definition of a limit is: i.e rigorous way of saying
Epsilon Delta proofs Before reading this guide, please go over inequalities (if needed). Eample Prove lim(4 3) = 5 2 First we have to know what the definition of a limit is: i.e rigorous way of saying
Section 2: Classes of Sets
 Section 2: Classes of Sets Notation: If A, B are subsets of X, then A \ B denotes the set difference, A \ B = {x A : x B}. A B denotes the symmetric difference. A B = (A \ B) (B \ A) = (A B) \ (A B). Remarks
Section 2: Classes of Sets Notation: If A, B are subsets of X, then A \ B denotes the set difference, A \ B = {x A : x B}. A B denotes the symmetric difference. A B = (A \ B) (B \ A) = (A B) \ (A B). Remarks
CS 360, Winter Morphology of Proof: An introduction to rigorous proof techniques
 CS 30, Winter 2011 Morphology of Proof: An introduction to rigorous proof techniques 1 Methodology of Proof An example Deep down, all theorems are of the form If A then B, though they may be expressed
CS 30, Winter 2011 Morphology of Proof: An introduction to rigorous proof techniques 1 Methodology of Proof An example Deep down, all theorems are of the form If A then B, though they may be expressed
STEP Support Programme. Pure STEP 1 Questions
 STEP Support Programme Pure STEP 1 Questions 2012 S1 Q4 1 Preparation Find the equation of the tangent to the curve y = x at the point where x = 4. Recall that x means the positive square root. Solve the
STEP Support Programme Pure STEP 1 Questions 2012 S1 Q4 1 Preparation Find the equation of the tangent to the curve y = x at the point where x = 4. Recall that x means the positive square root. Solve the
On Finite-Time Ruin Probabilities in a Risk Model Under Quota Share Reinsurance
 Applied Mathematical Sciences, Vol. 11, 217, no. 53, 269-2629 HIKARI Ltd, www.m-hikari.com https://doi.org/1.12988/ams.217.7824 On Finite-Time Ruin Probabilities in a Risk Model Under Quota Share Reinsurance
Applied Mathematical Sciences, Vol. 11, 217, no. 53, 269-2629 HIKARI Ltd, www.m-hikari.com https://doi.org/1.12988/ams.217.7824 On Finite-Time Ruin Probabilities in a Risk Model Under Quota Share Reinsurance
Sequences of Real Numbers
 Chapter 8 Sequences of Real Numbers In this chapter, we assume the existence of the ordered field of real numbers, though we do not yet discuss or use the completeness of the real numbers. In the next
Chapter 8 Sequences of Real Numbers In this chapter, we assume the existence of the ordered field of real numbers, though we do not yet discuss or use the completeness of the real numbers. In the next
On the power-free parts of consecutive integers
 ACTA ARITHMETICA XC4 (1999) On the power-free parts of consecutive integers by B M M de Weger (Krimpen aan den IJssel) and C E van de Woestijne (Leiden) 1 Introduction and main results Considering the
ACTA ARITHMETICA XC4 (1999) On the power-free parts of consecutive integers by B M M de Weger (Krimpen aan den IJssel) and C E van de Woestijne (Leiden) 1 Introduction and main results Considering the
Vector Spaces. Chapter 1
 Chapter 1 Vector Spaces Linear algebra is the study of linear maps on finite-dimensional vector spaces. Eventually we will learn what all these terms mean. In this chapter we will define vector spaces
Chapter 1 Vector Spaces Linear algebra is the study of linear maps on finite-dimensional vector spaces. Eventually we will learn what all these terms mean. In this chapter we will define vector spaces
College Algebra To learn more about all our offerings Visit Knewton.com
 College Algebra 978-1-63545-097-2 To learn more about all our offerings Visit Knewton.com Source Author(s) (Text or Video) Title(s) Link (where applicable) OpenStax Text Jay Abramson, Arizona State University
College Algebra 978-1-63545-097-2 To learn more about all our offerings Visit Knewton.com Source Author(s) (Text or Video) Title(s) Link (where applicable) OpenStax Text Jay Abramson, Arizona State University
1300 Linear Algebra and Vector Geometry
 1300 Linear Algebra and Vector Geometry R. Craigen Office: MH 523 Email: craigenr@umanitoba.ca May-June 2017 Matrix Inversion Algorithm One payoff from this theorem: It gives us a way to invert matrices.
1300 Linear Algebra and Vector Geometry R. Craigen Office: MH 523 Email: craigenr@umanitoba.ca May-June 2017 Matrix Inversion Algorithm One payoff from this theorem: It gives us a way to invert matrices.
Number Theory: Niven Numbers, Factorial Triangle, and Erdos' Conjecture
 Sacred Heart University DigitalCommons@SHU Mathematics Undergraduate Publications Mathematics -2018 Number Theory: Niven Numbers, Factorial Triangle, and Erdos' Conjecture Sarah Riccio Sacred Heart University,
Sacred Heart University DigitalCommons@SHU Mathematics Undergraduate Publications Mathematics -2018 Number Theory: Niven Numbers, Factorial Triangle, and Erdos' Conjecture Sarah Riccio Sacred Heart University,
Finding Divisors, Number of Divisors and Summation of Divisors. Jane Alam Jan
 Finding Divisors, Number of Divisors and Summation of Divisors by Jane Alam Jan Finding Divisors If we observe the property of the numbers, we will find some interesting facts. Suppose we have a number
Finding Divisors, Number of Divisors and Summation of Divisors by Jane Alam Jan Finding Divisors If we observe the property of the numbers, we will find some interesting facts. Suppose we have a number
Mathematics Course 111: Algebra I Part I: Algebraic Structures, Sets and Permutations
 Mathematics Course 111: Algebra I Part I: Algebraic Structures, Sets and Permutations D. R. Wilkins Academic Year 1996-7 1 Number Systems and Matrix Algebra Integers The whole numbers 0, ±1, ±2, ±3, ±4,...
Mathematics Course 111: Algebra I Part I: Algebraic Structures, Sets and Permutations D. R. Wilkins Academic Year 1996-7 1 Number Systems and Matrix Algebra Integers The whole numbers 0, ±1, ±2, ±3, ±4,...
Math 4606, Summer 2004: Inductive sets, N, the Peano Axioms, Recursive Sequences Page 1 of 10
 Math 4606, Summer 2004: Inductive sets, N, the Peano Axioms, Recursive Sequences Page 1 of 10 Inductive sets (used to define the natural numbers as a subset of R) (1) Definition: A set S R is an inductive
Math 4606, Summer 2004: Inductive sets, N, the Peano Axioms, Recursive Sequences Page 1 of 10 Inductive sets (used to define the natural numbers as a subset of R) (1) Definition: A set S R is an inductive
P -adic root separation for quadratic and cubic polynomials
 P -adic root separation for quadratic and cubic polynomials Tomislav Pejković Abstract We study p-adic root separation for quadratic and cubic polynomials with integer coefficients. The quadratic and reducible
P -adic root separation for quadratic and cubic polynomials Tomislav Pejković Abstract We study p-adic root separation for quadratic and cubic polynomials with integer coefficients. The quadratic and reducible
Logic, Sets, and Proofs
 Logic, Sets, and Proofs David A. Cox and Catherine C. McGeoch Amherst College 1 Logic Logical Operators. A logical statement is a mathematical statement that can be assigned a value either true or false.
Logic, Sets, and Proofs David A. Cox and Catherine C. McGeoch Amherst College 1 Logic Logical Operators. A logical statement is a mathematical statement that can be assigned a value either true or false.
Approximation and Aggregation of Risks by Variants of Panjer s Recursion
 Approximation and Aggregation of Risks by Variants of Panjer s Recursion Uwe Schmock Vienna University of Technology, Austria Version of Slides: Feb. 8, 2013 Presentation based on joint work with Stefan
Approximation and Aggregation of Risks by Variants of Panjer s Recursion Uwe Schmock Vienna University of Technology, Austria Version of Slides: Feb. 8, 2013 Presentation based on joint work with Stefan
Solution. 1 Solutions of Homework 1. 2 Homework 2. Sangchul Lee. February 19, Problem 1.2
 Solution Sangchul Lee February 19, 2018 1 Solutions of Homework 1 Problem 1.2 Let A and B be nonempty subsets of R + :: {x R : x > 0} which are bounded above. Let us define C = {xy : x A and y B} Show
Solution Sangchul Lee February 19, 2018 1 Solutions of Homework 1 Problem 1.2 Let A and B be nonempty subsets of R + :: {x R : x > 0} which are bounded above. Let us define C = {xy : x A and y B} Show
Linear Algebra March 16, 2019
 Linear Algebra March 16, 2019 2 Contents 0.1 Notation................................ 4 1 Systems of linear equations, and matrices 5 1.1 Systems of linear equations..................... 5 1.2 Augmented
Linear Algebra March 16, 2019 2 Contents 0.1 Notation................................ 4 1 Systems of linear equations, and matrices 5 1.1 Systems of linear equations..................... 5 1.2 Augmented
ELEMENTARY LINEAR ALGEBRA
 ELEMENTARY LINEAR ALGEBRA K. R. MATTHEWS DEPARTMENT OF MATHEMATICS UNIVERSITY OF QUEENSLAND Second Online Version, December 1998 Comments to the author at krm@maths.uq.edu.au Contents 1 LINEAR EQUATIONS
ELEMENTARY LINEAR ALGEBRA K. R. MATTHEWS DEPARTMENT OF MATHEMATICS UNIVERSITY OF QUEENSLAND Second Online Version, December 1998 Comments to the author at krm@maths.uq.edu.au Contents 1 LINEAR EQUATIONS
Comonotonicity and Maximal Stop-Loss Premiums
 Comonotonicity and Maximal Stop-Loss Premiums Jan Dhaene Shaun Wang Virginia Young Marc J. Goovaerts November 8, 1999 Abstract In this paper, we investigate the relationship between comonotonicity and
Comonotonicity and Maximal Stop-Loss Premiums Jan Dhaene Shaun Wang Virginia Young Marc J. Goovaerts November 8, 1999 Abstract In this paper, we investigate the relationship between comonotonicity and
55 Separable Extensions
 55 Separable Extensions In 54, we established the foundations of Galois theory, but we have no handy criterion for determining whether a given field extension is Galois or not. Even in the quite simple
55 Separable Extensions In 54, we established the foundations of Galois theory, but we have no handy criterion for determining whether a given field extension is Galois or not. Even in the quite simple
Practical Algebra. A Step-by-step Approach. Brought to you by Softmath, producers of Algebrator Software
 Practical Algebra A Step-by-step Approach Brought to you by Softmath, producers of Algebrator Software 2 Algebra e-book Table of Contents Chapter 1 Algebraic expressions 5 1 Collecting... like terms 5
Practical Algebra A Step-by-step Approach Brought to you by Softmath, producers of Algebrator Software 2 Algebra e-book Table of Contents Chapter 1 Algebraic expressions 5 1 Collecting... like terms 5
Minimal basis for connected Markov chain over 3 3 K contingency tables with fixed two-dimensional marginals. Satoshi AOKI and Akimichi TAKEMURA
 Minimal basis for connected Markov chain over 3 3 K contingency tables with fixed two-dimensional marginals Satoshi AOKI and Akimichi TAKEMURA Graduate School of Information Science and Technology University
Minimal basis for connected Markov chain over 3 3 K contingency tables with fixed two-dimensional marginals Satoshi AOKI and Akimichi TAKEMURA Graduate School of Information Science and Technology University
Fall 2017 Test II review problems
 Fall 2017 Test II review problems Dr. Holmes October 18, 2017 This is a quite miscellaneous grab bag of relevant problems from old tests. Some are certainly repeated. 1. Give the complete addition and
Fall 2017 Test II review problems Dr. Holmes October 18, 2017 This is a quite miscellaneous grab bag of relevant problems from old tests. Some are certainly repeated. 1. Give the complete addition and
CDM. Recurrences and Fibonacci
 CDM Recurrences and Fibonacci Klaus Sutner Carnegie Mellon University 20-fibonacci 2017/12/15 23:16 1 Recurrence Equations Second Order The Fibonacci Monoid Recurrence Equations 3 We can define a sequence
CDM Recurrences and Fibonacci Klaus Sutner Carnegie Mellon University 20-fibonacci 2017/12/15 23:16 1 Recurrence Equations Second Order The Fibonacci Monoid Recurrence Equations 3 We can define a sequence
THE DENSITY OF THE PRODUCT OF ARITHMETIC PROGRESSION
 THE DENSITY OF THE PRODUCT OF ARITHMETIC PROGRESSION S. K. STEIN University of California, Davis, California This paper is devoted to the proof of the following theorem. Theorem. Let a, b, c, and d be
THE DENSITY OF THE PRODUCT OF ARITHMETIC PROGRESSION S. K. STEIN University of California, Davis, California This paper is devoted to the proof of the following theorem. Theorem. Let a, b, c, and d be
PRACTICE PROBLEMS: SET 1
 PRACTICE PROBLEMS: SET MATH 437/537: PROF. DRAGOS GHIOCA. Problems Problem. Let a, b N. Show that if gcd(a, b) = lcm[a, b], then a = b. Problem. Let n, k N with n. Prove that (n ) (n k ) if and only if
PRACTICE PROBLEMS: SET MATH 437/537: PROF. DRAGOS GHIOCA. Problems Problem. Let a, b N. Show that if gcd(a, b) = lcm[a, b], then a = b. Problem. Let n, k N with n. Prove that (n ) (n k ) if and only if
Finite Fields: An introduction through exercises Jonathan Buss Spring 2014
 Finite Fields: An introduction through exercises Jonathan Buss Spring 2014 A typical course in abstract algebra starts with groups, and then moves on to rings, vector spaces, fields, etc. This sequence
Finite Fields: An introduction through exercises Jonathan Buss Spring 2014 A typical course in abstract algebra starts with groups, and then moves on to rings, vector spaces, fields, etc. This sequence
Asymptotic behavior for sums of non-identically distributed random variables
 Appl. Math. J. Chinese Univ. 2019, 34(1: 45-54 Asymptotic behavior for sums of non-identically distributed random variables YU Chang-jun 1 CHENG Dong-ya 2,3 Abstract. For any given positive integer m,
Appl. Math. J. Chinese Univ. 2019, 34(1: 45-54 Asymptotic behavior for sums of non-identically distributed random variables YU Chang-jun 1 CHENG Dong-ya 2,3 Abstract. For any given positive integer m,
FINITE ABELIAN GROUPS Amin Witno
 WON Series in Discrete Mathematics and Modern Algebra Volume 7 FINITE ABELIAN GROUPS Amin Witno Abstract We detail the proof of the fundamental theorem of finite abelian groups, which states that every
WON Series in Discrete Mathematics and Modern Algebra Volume 7 FINITE ABELIAN GROUPS Amin Witno Abstract We detail the proof of the fundamental theorem of finite abelian groups, which states that every
Chapter 5: Integer Compositions and Partitions and Set Partitions
 Chapter 5: Integer Compositions and Partitions and Set Partitions Prof. Tesler Math 184A Winter 2017 Prof. Tesler Ch. 5: Compositions and Partitions Math 184A / Winter 2017 1 / 32 5.1. Compositions A strict
Chapter 5: Integer Compositions and Partitions and Set Partitions Prof. Tesler Math 184A Winter 2017 Prof. Tesler Ch. 5: Compositions and Partitions Math 184A / Winter 2017 1 / 32 5.1. Compositions A strict
Solutions to Tutorial for Week 4
 The University of Sydney School of Mathematics and Statistics Solutions to Tutorial for Week 4 MATH191/1931: Calculus of One Variable (Advanced) Semester 1, 018 Web Page: sydneyeduau/science/maths/u/ug/jm/math191/
The University of Sydney School of Mathematics and Statistics Solutions to Tutorial for Week 4 MATH191/1931: Calculus of One Variable (Advanced) Semester 1, 018 Web Page: sydneyeduau/science/maths/u/ug/jm/math191/
 Twitter: @Owen134866 www.mathsfreeresourcelibrary.com Prior Knowledge Check 1) Factorise each polynomial: a) x 2 6x + 5 b) x 2 16 c) 9x 2 25 2) Simplify the following algebraic fractions fully: a) x 2
Twitter: @Owen134866 www.mathsfreeresourcelibrary.com Prior Knowledge Check 1) Factorise each polynomial: a) x 2 6x + 5 b) x 2 16 c) 9x 2 25 2) Simplify the following algebraic fractions fully: a) x 2
g(x) = 1 1 x = 1 + x + x2 + x 3 + is not a polynomial, since it doesn t have finite degree. g(x) is an example of a power series.
 6 Polynomial Rings We introduce a class of rings called the polynomial rings, describing computation, factorization and divisibility in such rings For the case where the coefficients come from an integral
6 Polynomial Rings We introduce a class of rings called the polynomial rings, describing computation, factorization and divisibility in such rings For the case where the coefficients come from an integral
Discrete Mathematics and Probability Theory Fall 2013 Vazirani Note 12. Random Variables: Distribution and Expectation
 CS 70 Discrete Mathematics and Probability Theory Fall 203 Vazirani Note 2 Random Variables: Distribution and Expectation We will now return once again to the question of how many heads in a typical sequence
CS 70 Discrete Mathematics and Probability Theory Fall 203 Vazirani Note 2 Random Variables: Distribution and Expectation We will now return once again to the question of how many heads in a typical sequence
A Combinatorial Interpretation of the Numbers 6 (2n)! /n! (n + 2)!
 1 2 3 47 6 23 11 Journal of Integer Sequences, Vol. 8 (2005), Article 05.2.3 A Combinatorial Interpretation of the Numbers 6 (2n)! /n! (n + 2)! Ira M. Gessel 1 and Guoce Xin Department of Mathematics Brandeis
1 2 3 47 6 23 11 Journal of Integer Sequences, Vol. 8 (2005), Article 05.2.3 A Combinatorial Interpretation of the Numbers 6 (2n)! /n! (n + 2)! Ira M. Gessel 1 and Guoce Xin Department of Mathematics Brandeis
CDM. Recurrences and Fibonacci. 20-fibonacci 2017/12/15 23:16. Terminology 4. Recurrence Equations 3. Solution and Asymptotics 6.
 CDM Recurrences and Fibonacci 1 Recurrence Equations Klaus Sutner Carnegie Mellon University Second Order 20-fibonacci 2017/12/15 23:16 The Fibonacci Monoid Recurrence Equations 3 Terminology 4 We can
CDM Recurrences and Fibonacci 1 Recurrence Equations Klaus Sutner Carnegie Mellon University Second Order 20-fibonacci 2017/12/15 23:16 The Fibonacci Monoid Recurrence Equations 3 Terminology 4 We can
MA1131 Lecture 15 (2 & 3/12/2010) 77. dx dx v + udv dx. (uv) = v du dx dx + dx dx dx
 MA3 Lecture 5 ( & 3//00) 77 0.3. Integration by parts If we integrate both sides of the proct rule we get d (uv) dx = dx or uv = d (uv) = dx dx v + udv dx v dx dx + v dx dx + u dv dx dx u dv dx dx This
MA3 Lecture 5 ( & 3//00) 77 0.3. Integration by parts If we integrate both sides of the proct rule we get d (uv) dx = dx or uv = d (uv) = dx dx v + udv dx v dx dx + v dx dx + u dv dx dx u dv dx dx This
Part IA Numbers and Sets
 Part IA Numbers and Sets Theorems Based on lectures by A. G. Thomason Notes taken by Dexter Chua Michaelmas 2014 These notes are not endorsed by the lecturers, and I have modified them (often significantly)
Part IA Numbers and Sets Theorems Based on lectures by A. G. Thomason Notes taken by Dexter Chua Michaelmas 2014 These notes are not endorsed by the lecturers, and I have modified them (often significantly)
TABLE OF CONTENTS. Our aim is to give people math skillss in a very simple way Raymond J. Page 2 of 29
 TABLE OF CONTENTS Topic.Page# 1. Numbers..04 2. Ratio, Profit & Loss 06 3. Angles......06 4. Interest..06 5. Algebra..07 6. Quadratic Equations.08 7. Logarithms...09 8. Series..10 9. Sphere.11 10. Coordinate
TABLE OF CONTENTS Topic.Page# 1. Numbers..04 2. Ratio, Profit & Loss 06 3. Angles......06 4. Interest..06 5. Algebra..07 6. Quadratic Equations.08 7. Logarithms...09 8. Series..10 9. Sphere.11 10. Coordinate
Preparing for the CS 173 (A) Fall 2018 Midterm 1
 Preparing for the CS 173 (A) Fall 2018 Midterm 1 1 Basic information Midterm 1 is scheduled from 7:15-8:30 PM. We recommend you arrive early so that you can start exactly at 7:15. Exams will be collected
Preparing for the CS 173 (A) Fall 2018 Midterm 1 1 Basic information Midterm 1 is scheduled from 7:15-8:30 PM. We recommend you arrive early so that you can start exactly at 7:15. Exams will be collected
