Arithmetic in Integer Rings and Prime Fields
|
|
|
- Brenda Stephens
- 5 years ago
- Views:
Transcription
1 Arithmetic in Integer Rings and Prime Fields A 3 B 3 A 2 B 2 A 1 B 1 A 0 B 0 FA C 3 FA C 2 FA C 1 FA C 0 C 4 S 3 S 2 S 1 S 0 Çetin Kaya Koç Spring / 71
2 Contents Arithmetic in Integer Rings and Prime Fields Integer Rings and Finite Fields Addition and Multiplication Modular Addition and Multiplication Montgomery Multiplication and Exponentiation The CIOS Algorithm Arithmetic with Special Primes Çetin Kaya Koç Spring / 71
3 Integer Rings and Finite Fields in Cryptography Several cryptographic algorithms are based on similar mathematical structures built upon finite sets of integers: Rings Z n or groups Z n for a composite n Fields GF(p) or their multiplicative groups for a prime p The arithmetic of such structures are often called modular arithmetic The arithmetic operations of interest in cryptography are addition, multiplication and inversion mod n or mod p The modulus n or p is either composite or prime The fact that modulus is prime or composite makes little difference in addition and multiplication algorithms Çetin Kaya Koç Spring / 71
4 Integer Addition The computation of two k-bit numbers a and b The bits are represented using A i and B i A k 1 A k 2 A 1 A 0 + B k 1 B k 2 B 1 B 0 C k S k 1 S k 2 S 1 S 0 Carry propagate adder Carry completion sensing adder Carry look-ahead adder Carry save adder Çetin Kaya Koç Spring / 71
5 Carry Propagate Adder: CPA The full adder box: FA A i B i S i = A i B i C i C i+1 Topology: FA S i C i C i+1 = A i B i + A i C i + B i C i XOR AND + OR A 3 B 3 A 2 B 2 A 1 B 1 A 0 B 0 FA C 3 FA C 2 FA C 1 FA C 0 C 4 S 3 S 2 S 1 S 0 Çetin Kaya Koç Spring / 71
6 Properties of CPA Total (worst case) delay = k FA delay The circuit needs consider the worst case scenarios Total area = k FA area Scales up easily for k Subtraction is easy: Use 2 s complement arithmetic Sign detection is easy: MSB gives the sign Çetin Kaya Koç Spring / 71
7 Carry Completion Sensing Adder While the worst case carry propagation length is k, there will be many cases in which carry propagation length will be a lot less The carry completion sensing adder waits only as long as the longest carry, which is less than k The carry completion sensing adder is an asynchronous adder which detects the completion of the carry propagation process An example of carry propagation processes Analysis shows that average carry length is bounded by log 2 (k) Çetin Kaya Koç Spring / 71
8 Carry Completion Sensing Adder Carry completion signal is a bit pair (C, N) which is produced from the current input bit pair (A, B) The carry completion signals are then applied to a wide AND gate which computes the product of all carry completion signals C + N (A, B) = (0, 0) (C, N) (0, 1) (A, B) = (1, 1) (C, N) (1, 0) (A, B) = (0, 1) (C, N) previous (C, N) (A, B) = (1, 0) (C, N) previous (C, N) When C + N is determined, it will be 1 and it remains at 1 Undetermined C + N values are kept at logic 0 Çetin Kaya Koç Spring / 71
9 Carry Completion Sensing Adder A B C N C + N C N C + N C N C + N C N C + N C N C + N Çetin Kaya Koç Spring / 71
10 Carry Look-Ahead Adder Compute C i s in advance using more logic Then, use C i s to compute S i s in parallel Let G i = A i B i and P i = A i + B i C i+1 is a function of C 0 and G 0, G 1,..., G i and P 0, P 1,..., P i C 1 = A 0 B 0 + C 0 (A 0 + B 0 ) = G 0 + C 0 P 0 C 2 = G 1 + C 1 P 1 = G 1 + G 0 P 1 + C 0 P 0 P 1 C 3 = G 2 + C 2 P 2 = G 2 + G 1 P 2 + G 0 P 1 P 2 + C 0 P 0 P 1 P 2 C 4 = G 3 + C 3 P 3 = G 3 + G 2 P 3 + G 1 P 2 P 3 + G 0 P 1 P 2 P 3 + C 0 P 0 P 1 P 2 P 3 Çetin Kaya Koç Spring / 71
11 Properties of CLA The total delay is O(log k) The total area is essentially O(k) using parallel prefix circuits (See: Ladner & Fischer, Brent & Kung) A complete CLA is not cost-effective for large k (> 256) By grouping G and P functions, larger CLAs can be designed Even with grouping, design of a 1024-bit adder may not be feasible or cost-effective Çetin Kaya Koç Spring / 71
12 Carry Save Adder Input: 3 k-bit numbers a, b, and c a = (A k 1 A k 2 A 1 A 0 ) b = (B k 1 B k 2 B 1 B 0 ) c = (C k 1 C k 2 C 1 C 0 ) Output: 2 k-bit numbers c and s such that c + s = a + b + c s = (S k S k 1 S 1 S 0 ) c = (C k C k 1 C 2C 1) The individual bits of s and c are computed as S i = A i B i C i C i+1 = A i B i + A i C i + B i C i Çetin Kaya Koç Spring / 71
13 Carry Save Adder Topology: A 3 B 3 C 3 A 2 B 2 C 2 A 1 B 1 C 1 A 0 B 0 C 0 FA FA FA FA S 3 C 4 S 2 C 3 S 1 C 2 S 0 C 1 An example: A = B = C = S = C = Çetin Kaya Koç Spring / 71
14 Properties of Carry Save Adder The total delay is O(1) (a single FA delay) The total area is k FA area Scales up easily for large k Subtraction is easy: Use 2 s complement arithmetic Sign detection is complicated Çetin Kaya Koç Spring / 71
15 Sign Detection Problem for Carry Save Adders Numbers are represented in Carry and Sum pairs x = (c, s) The actual value of the number is x = c + s Unless the addition is performed in full length, the correct sign may never be determined Example: a = 18, b = 19, and c = 6 are given We compute their sum using the CSA a = b = c = s = c = (1 MSB) 11 (2 MSB) 000 (3 MSB) 0001 (4 MSB) (5 MSB) Çetin Kaya Koç Spring / 71
16 A Sign Estimation Algorithm for CSA We add the most significant t bits of c and s to estimate the sign of x = c + s, represented as esign t (c, s) c = s = esign 1 (c, s) = 0 esign 2 (c, s) = 01 esign 3 (c, s) = 100 esign 4 (c, s) = 1001 esign 5 (c, s) = It is shown: if esign t (c, s) is used for mod n reduction, then: C + S < n + 2 k t where n is the modulus and k is its length in bits Çetin Kaya Koç Spring / 71
17 Addition and Subtraction mod n The computation of s = a + b mod n Add and Reduce: Given a, b < n Compute s = a + b Compute s = s n If s 0 then s = s else s = s Requires fast sign detection: Is s 0? Çetin Kaya Koç Spring / 71
18 Incomplete (Lazy) Reduction Given a, b < 2 k (a, b can be n) Compute s = a + b If there is a carry out of the k-bit register then s = s + m else s = s Correction factor: m = 2 k n (precomputed) Çetin Kaya Koç Spring / 71
19 Incomplete Reduction Carry out of the k-bit register implies (s ) = a + b 2 k Thus, if the carry is discarded, we essentially compute s = a + b 2 k The result is then corrected by adding m to s s = s + m = a + b 2 k + m = a + b n A temporary value may be larger than n, but it is always less than 2 k Whenever it exceeds 2 k, we discard the carry, and perform a correction Çetin Kaya Koç Spring / 71
20 Incomplete Reduction Example n = 39, thus m = = 25 = (011001) a = 23 = (010111) b = 26 = (011010) s = a + b = 0(110001) no carry out s = s = (110001) a = 40 = (101000) b = 30 = (011110) s = s + b = 1(000110) carry out m = (011001) s = s + m = (011111) correction Çetin Kaya Koç Spring / 71
21 Final Correction Phase After all additions are completed, a final result that is out of range can be corrected by adding m: s = (110001) m = (011001) s = s + m = 1(001010) s = (001010) Çetin Kaya Koç Spring / 71
22 Modular Multiplication Given a, b < n, compute p = a b mod n Methods: Multiply and reduce: Multiply: p = a b (2k-bit number) Reduce: p = p mod n (k-bit number) Interleave multiply and reduce steps The Montgomery multiplication Çetin Kaya Koç Spring / 71
23 Interleaving Multiply and Reduce The product p = a b can be written as k 1 p = a B i 2 i = a (B 0 + B B B k 1 2 k 1 ) i=0 We can apply Horner s rule to this formulation of p The initial value p = 0 and the loop starts with B k 1 and moves down with B k 2, B k 3,... p 2 p + a B k 1 = a B k 1 p 2 p + a B k 2 = 2 a B k 1 + a B k 2. p 2 p + a B i Çetin Kaya Koç Spring / 71
24 Interleaving Multiply and Reduce This formulation yields the shift-add multiplication algorithm 1: p 0 2: for i = k 1 downto 0 2a: p 2 p + a B i 3: return p We can also reduce the partial product mod n at each step: 1: p 0 2: for i = k 1 downto 0 2a: p 2 p + a B i 2b: p p mod n 3: return p Çetin Kaya Koç Spring / 71
25 Interleaving Multiply and Reduce Assuming that a, b, p < n, we have p 2 p + a B j 2(n 1) + (n 1) = 3n 3 Thus, at most two subtractions are needed to reduce p to the range 0 p < n We can use p p n ; if p 0 then p p p p n ; if p 0 then p p Addition and subtraction steps need to be performed faster Çetin Kaya Koç Spring / 71
26 Interleaving Multiply and Reduce Carry propagate adder gives O(k) delay Incomplete reduction can be used to avoid unnecessary subtractions: 2a. p 2p 2b. if carry-out then p p + m 2c. p p + a B j 2d. if carry-out then p p + m Carry save adder gives O(1) delay; fast sign detection is needed to decide if the partial product needs to be reduced modulo n 2a. (c, s) 2c + 2s + a B i 2b. (c, s ) c + s n 2c. if esign t (c, s ) 0 then (c, s) (c, s ) Function esign t (c, s ) estimates the sign of c + s Çetin Kaya Koç Spring / 71
27 Montgomery Multiplication The Montgomery multiplication algorithm replaces division by n operation with division by r = 2 k If n is a k-bit odd integer, i.e., 2 k 1 < n < 2 k, we assign r = 2 k We map the integers a [0, n 1] to the integers ā [0, n 1] using ā = a r (mod n) For example, for n = 11 and r = 16 the mapping is a : ā : Çetin Kaya Koç Spring / 71
28 Definition of Montgomery Product The Montgomery product of a, b [0, n 1] is defined as MonPro(a, b) = a b r 1 (mod n) Here r 1 is the multiplicative inverse of r modulo n The inverse of r = 2 k exists if the modulus n is odd Interestingly the Montgomery product of two integers actually involves two multiplications, instead of one Furthermore, we need r 1 (mod n), but it can be precomputed Çetin Kaya Koç Spring / 71
29 Properties of the Montgomery Product Property 1: If c = a b (mod n), then c = MonPro(ā, b) MonPro(ā, b) = ā b r 1 (mod n) = (a r) (b r) r 1 (mod n) = a b r (mod n) = c r (mod n) = c Çetin Kaya Koç Spring / 71
30 Properties of the Montgomery Product Property 2: ā = MonPro(a, r 2 ) MonPro(a, r 2 ) = a r 2 r 1 (mod n) = a r (mod n) = ā Property 3: c = MonPro( c, 1) MonPro( c, 1) = c 1 r 1 (mod n) = (c r) 1 r 1 (mod n) = c Çetin Kaya Koç Spring / 71
31 Classical Montgomery Algorithm Peter Montgomery introduced his original algorithm in 1985 The function MonPro(a, b) computes a b r 1 (mod n) Interestingly the algorithm does not need r 1 (mod n) However, it requires another quantity n which is related to it function MonPro(a, b) Input: a, b, n, n Output: u = a b r 1 mod n 1: t a b 2: m t n (mod r) 3: u (t + m n)/r 4: if u n then u u n 5: return u Çetin Kaya Koç Spring / 71
32 Computation of n The quantity n appears in the computation of r 1 (mod n) using the extended Euclidean algorithm The EEA computes r 1 and n using (s, t) EEA(r, n) s r + t n = 1 Here we have r 1 = s (mod n) and n is defined to be n = t While r 1 (mod n) is not needed, the Montgomery function requires n which is also computed using the EEA Furthermore, they are related as r 1 r + ( n ) n = 1 n = 1 + r r 1 n Çetin Kaya Koç Spring / 71
33 Properties of the Montgomery Algorithm Steps 2 and 3 of the Montgomery algorithm seem complicated, as they are modular multiplication and division operations However, the modular reduction and division operations involve the modulus and divisor as r which is a power of 2 Step 2: The Montgomery function performs modular multiplication m t n (mod r), however, the modulus is r = 2 k, which means the reduction by r is accomplished by taking the least significant k bits of the product Example: Given 273 = ( ), we reduce it mod 16 = 2 4 by taking its least significant 4 bits: (0111) = 7 Indeed 273 = 7 (mod 16) Çetin Kaya Koç Spring / 71
34 Properties of the Montgomery Algorithm Step 3: The Montgomery function first performs u (t + m n), and then divides u by r = 2 k, which implies a k-bit right shift u (t + m n)/2 k, i.e., discarding the least significant k bits Example: Given 208 = ( ), we divide it by 16 = 2 4 by discarding its least significant 4 bits and obtain (1101) = 13 Indeed 208/16 = 13 Thus, we conclude that the modular reduction by r in Step 2 and the division by r in Step 3 are simple operations on a digital computer They are easily accomplished: Reduction by r = 2 k : taking least significant k bits Division by r = 2 k : discarding least significant k bits Çetin Kaya Koç Spring / 71
35 Properties of the Montgomery Algorithm To compute a b r 1 (mod n) for a k-bit odd n < r and r = 2 k, the MonPro function performs only multiplications in Steps 1, 2, and 3 Multiplication operations require O(k 2 ) bit operations if the standard algorithms are being utilized The modular reduction by r operation in Step 2 and the division by r operation in Step 3 require only O(k) bit operations Similarly, the subtraction in Step 4 is also O(k) The power of the Montgomery algorithm is that it requires no division or reduction by n which is an arbitrary k-bit integer However, it requires computation of n using the EEA It also requires 3 integer multiplications (Steps 1, 2, and 3) Çetin Kaya Koç Spring / 71
36 Correctness of the Montgomery Algorithm For proof, we use two facts n = ( 1 + r r 1 )/n implies 1 + n n = r r 1 m = t n (mod r) implies m = t n + N r for some N MonPro computes u = (t + m n)/r = (t + [t n + N r] n)/r = (t [1 + n n] + N r n)/r = (t r r 1 + N r n)/r = t r 1 + N n = a b r 1 + N n = a b r 1 (mod n) Çetin Kaya Koç Spring / 71
37 Montgomery Exponentiation MonPro function is not suitable for a single modular multiplication c = a b (mod n) since it has significant overhead Compute n using the EEA Convert a and b to bar notation (s, t) EEA(r, n) n = t ā MonPro(a, r 2 ) b MonPro(b, r 2 ) Perform the Montgomery product: c MonPro(ā, b) Convert c to unbar notation: c MonPro( c, 1) Çetin Kaya Koç Spring / 71
38 Montgomery Exponentiation However, MonPro function is very suitable for several modular multiplications with the same modulus: Montgomery Exponentiation function MonExp(m, d, n) Input: m, d, n Output: s = m d mod n 1: m MonPro(m, r 2 ) 2: s MonPro(1, r 2 ) 3: for i = k 1 downto 0 4a: s MonPro( s, s) 4b: if d i = 1 then s MonPro( s, m) 5: s MonPro( s, 1) 3: return s Çetin Kaya Koç Spring / 71
39 Montgomery Exponentiation Example Computation of MonExp(3, 50, 55) = 3 50 (mod 55) Since n = 55, we can take r is the next power of 2 as r = 64 Using the EEA we compute EEA(r, n) = EEA(64, 55) (r 1, n ) = (49, 57) Thus, we obtain r 1 = 49 and n = 57 We start with m = 3 and s = 1 m MonPro(m, r 2 ) = MonPro(3, 64 2 ) which gives m = 27 s MonPro(s, r 2 ) = MonPro(1, 64 2 ) which gives s = 9 Çetin Kaya Koç Spring / 71
40 Montgomery Exponentiation Example e = 50 = (110010) 2 e i Step 5 Step 6 1 MonPro(9, 9) = 9 MonPro(9, 27) = 27 1 MonPro(27, 27) = 26 MonPro(26, 27) = 23 0 MonPro(23, 23) = 16 0 MonPro(16, 16) = 4 1 MonPro(4, 4) = 14 MonPro(14, 27) = 42 0 MonPro(42, 42) = 31 s = MonPro(31, 1) = 34 Çetin Kaya Koç Spring / 71
41 The Montgomery Exponentiation Example Computation of MonPro(27, 27): t = 729 m (mod 64) (mod 64) ( ) = 17 u ( )/ /64 ( ) = 26 Çetin Kaya Koç Spring / 71
42 The Montgomery Exponentiation Example Computation of MonPro(31, 1): t 31 1 = 31 m (mod 64) 1767 (mod 64) ( ) = 39 u ( )/ /64 ( ) = 34 Çetin Kaya Koç Spring / 71
43 Derivation of the CIOS Algorithm CIOS stands for Coarsely Integrated Operand Scanning CIOS performs the MonPro function It is more efficient than the classical Montgomery algorithm CIOS requires 1.5 integer multiplications instead of 3 Furthermore, the binary CIOS algorithm does not require the computation of n 0 because it is always equal to 1 The word-level CIOS requires the computation of only the least significant word (the least significant w bits) of n 0 Çetin Kaya Koç Spring / 71
44 Derivation of the binary CIOS Consider the Montgomery function which computes MonPro(a, b) = a b r 1 (mod n) Since r = 2 k, we can write it as u = a b 2 k (mod n) ( k 1 ) = A i 2 i b 2 k (mod n) = Thus, we obtain i=0 ( k 1 ) A i 2 i k b (mod n) i=0 u = (A 0 2 k + A 1 2 k A k ) b (mod n) Çetin Kaya Koç Spring / 71
45 Derivation of the binary CIOS We can apply Horner s rule to this formulation of u u = (A 0 2 k + A 1 2 k A k ) b (mod n) The initial value of the sum u = 0 and the innermost loop starts with A 0 and moves up with A 1, A 2,... u (u + A 0 b) 2 1 (mod n) = A 0 b 2 1 (mod n) u (u + A 1 b) 2 1 (mod n) = A 0 b A 1 b 2 1 (mod n) u (u + A 2 b) 2 1 (mod n) = A 0 b A 1 b A 2 b 2 1 (mod n). u (u + A i b) 2 1 (mod n) Çetin Kaya Koç Spring / 71
46 Derivation of the binary CIOS This formulation gives the following code for the binary CIOS: 1: u 0 2: for i = 0 to k 1 3: u (u + A i b) 2 1 (mod n) 4: return u We can separate Step 3 into two steps 1: u 0 2: for i = 0 to k 1 3a: u u + A i b 3b: u u 2 1 (mod n) 4: return u Çetin Kaya Koç Spring / 71
47 Derivation of the binary CIOS The computation of u 2 1 (mod n) for a given u can be performed without explicitly computing 2 1 (mod n) If u in Step 3a is even, such that u = 2v, then Step 3b gives u = 2v { Step 3a } u (2v) 2 1 (mod n) = v If u in Step 3a is odd, then we know u + n will be even since n is always odd, therefore, Step 3 gives u = odd { Step 3a } u + n = 2v u (2v) 2 1 (mod n) = v Çetin Kaya Koç Spring / 71
48 Derivation of the binary CIOS Furthermore, v is easily computed for an even u as v u/2 Therefore, we revise Step 3b into two steps, the first step is the if-then statement checking if the number is odd, while the second step performs division by 2 1: u 0 2: for i = 0 to k 1 3a: u u + A i b 3b: if u is odd then u u + n 3c: u u/2 4: return u The resulting algorithm has several nice properties Çetin Kaya Koç Spring / 71
49 The Binary CIOS Algorithm However, we should also add the subtraction step Furthermore, checking if u is odd can be made more efficient Given u, the LSB U 0 = 1 implies that u is odd 1: u 0 2: for i = 0 to k 1 3a: u u + A i b 3b: u u + U 0 n 3c: u u/2 4: if u > n then u u n 5: return u Çetin Kaya Koç Spring / 71
50 An Example of the Binary CIOS Algorithm Consider the computation of MonPro(27, 27) using the binary CIOS algorithm for n = 55 and k = 6 We have a = 27 = (011011) and b = 27 i a i Step 3a (u) u 0 Step 3b (u) Step 3c (u) = = 82 82/2 = = /2 = = /2 = = /2 = = = /2 = = /2 = 26 The subtraction (Step 4) is not needed since u < n The result is found as MonPro(27, 27) = 26 Çetin Kaya Koç Spring / 71
51 Properties of the Binary CIOS Algorithm The binary CIOS algorithm performs 2 multiplications with k-bit numbers in Steps 3a and 3b, requiring O(k 2 ) operations Step 3c is a simple bit-level shift operation, requiring at most O(k) However, Step 3b does not perform a multiplication when u 0 = 0 Assuming U 0 will be 1 or 0 with uniform probability, we can deduce that, in the average, half of the time Step 3b will be skipped Thus, the binary CIOS algorithm requires 1.5 multiplications with k-bit numbers in the average Çetin Kaya Koç Spring / 71
52 The Word-Level CIOS Algorithm The word-level algorithm scans the words of a, n, and u a = (A s 1 A s 2 A 1 A 0 ) n = (N s 1 N s 2 N 1 N 0 ) u = (U s 1 U s 2 U 1 U 0 ) for sw = k where w is the word size in bits The least significant w bits, in other words, the least significant words (LSW) of a, n, u are A 0, N 0, U 0 Now we consider the steps of the binary CIOS algorithm, and extend them to word level Step 3a is easily extended as u u + A i b Çetin Kaya Koç Spring / 71
53 The Word-Level CIOS Algorithm Since Step 3c performs a w-bit right shift, Step 3b should update u so that its LSW is zero Let M be a 1-word integer such that the LSW of u + M n is zero u + M n = 0 (mod 2 w ) M = u n 1 (mod 2 w ) Since the modulus is 2 w, we only need the LSW of u and n M = U 0 ( N 1 0 ) (mod 2w ) Interestingly, the identity r r 1 + ( n ) n = 1 implies ( n ) n = 1 (mod 2 w ) N 1 0 = N 0 (mod 2 w ) Therefore, N0 1 is actually equal to N 0, the LSW of N Çetin Kaya Koç Spring / 71
54 The Word-Level CIOS Algorithm 1: u 0 2: for i = 0 to s 1 3a: u u + A i b 3b: M U 0 ( N0 1 ) 3c: u u + M n 3d: u u/2 w 4: if u > n then u u n 5: return u Çetin Kaya Koç Spring / 71
55 An Example of the Word-Level CIOS Algorithm Consider the computation of MonPro(27, 27) using the word-level CIOS algorithm for n = 55, k = 6, and w = 3 We have a = 27 = (011011) 2 = (33) 8 and b = 27 We also have n = 55 = (110111) 2 = (67) 8 Furthermore, N 0 = 7 an N 0 = N 1 0 = 7 1 = 1 (mod 8) i A i Step 3a (u) U 0 Step 3b (M) Step 3c (u) Step 3d (u) 0 (3) = 81 (1) = = /8 = 17 1 (3) = 98 (2) = = /8 = 26 The subtraction (Step 4) is not needed since u < n The result is found as MonPro(27, 27) = 26 Çetin Kaya Koç Spring / 71
56 Properties of the Word-Level CIOS Algorithm The word-level CIOS performs 2 multiplications with s word numbers in Steps 3a and 3c, requiring O(s 2 ) operations Step 3b requires a 1-word operation: O(1) Step 3d is a simple word-level shift operation, requiring at most O(s) The word-level CIOS algorithm is more efficient than the classical Montgomery algorithm because: It does not require the k-bit (s-word) number n, instead, it only requires computation of the w-bit (1-word) number N 0 The classical Montgomery algorithm requires the k-bit number n It requires 2 multiplications with k-bit (s-word) numbers The classical Montgomery algorithm requires 3 multiplications with k-bit numbers Çetin Kaya Koç Spring / 71
57 Fast Computation of N 0 There is an efficient algorithm for computing the one-word integer N 0 = N 1 0 (mod 2 w ) It is based on a specialized version of the extended Euclidean algorithm for computing the inverse The following algorithm computes x 1 (mod 2 w ) for an odd x function ModInverse(x, 2 w ) 1: y 1 2: for i = 2 to w 3: if 2 i 1 < x y (mod 2 i ) then y y + 2 i 1 4: return y Çetin Kaya Koç Spring / 71
58 An Example Computation of n 0 As an example, we compute 23 1 (mod 2 6 ) Here we have x = 23 and w = 6. We start with y = 1 i 2 i 1 2 i y x y (mod 2 i ) y = 3 (mod 4) 3 > = = 5 (mod 8) 5 > = = 1 (mod 16) = 1 (mod 32) = 33 (mod 64) 33 > = 39 Thus, we find y = 39, implying 23 1 = 39 (mod 64) This is true, since = 897 = 1 (mod 64) Çetin Kaya Koç Spring / 71
59 Arithmetic with Special Primes Until now we considered modular arithmetic with arbitrary composite or prime numbers However, elliptic cryptographic algorithms often use special primes For example, the NIST elliptic curves over GF(p) use these primes Curve Field prime p P P P P P Çetin Kaya Koç Spring / 71
60 Arithmetic with Special Primes Similarly, SECG elliptic curves over GF(p) use these primes Curve Field prime p secp192k secp192r secp224k secp224r secp256k secp256r secp384r secp521r Furthermore, Curve25519 also uses a special prime p = Çetin Kaya Koç Spring / 71
61 Arithmetic with Special Primes We can use the existing modular addition and multiplication algorithms, including the classical Montgomery algorithm and the binary and word-level versions of the CIOS algorithm for arithmetic with these special primes However, these algorithms are designed for arbitrary primes They will not be as efficient as the algorithms that are designed and optimized for particular primes Several algorithms proposed for such special primes These algorithms however work only for the type of primes or for the primes for which they are designed Çetin Kaya Koç Spring / 71
62 Arithmetic with NIST Prime P-192 Consider the NIST prime P-192 which is p = Assume w = 64 and represent a word using A i Assume we are performing reduction modulo this prime For example, we can take a number that is the twice the length of p and reduce it mod p Such number may appear in computations after a multiplication, and thus, it will need to be reduced mod p Çetin Kaya Koç Spring / 71
63 Arithmetic with NIST Prime P-192 Since p is k bits, we can take a 2k-bit integer a and reduce it mod p Every 2k-bit integer a can be represented using 6 words a = A A A A A A 0 We can also use the compact notation a = (A 5 A 4 A 3 A 2 A 1 A 0 ) After the reduction mod p = , the result will be 3 words b = a (mod p) implies b = (B 2 B 1 B 0 ) Çetin Kaya Koç Spring / 71
64 Reduction with NIST Prime P-192 In order to obtain the reduced number b, we first compute T = (A 2 A 1 A 0 ) S 1 = (0 A 3 A 3 ) S 2 = (A 4 A 4 0) S 3 = (A 5 A 5 A 5 ) Then, we compute b = a (mod p) using modular addition b = (B 2 B 1 B 0 ) = T + S 1 + S 2 + S 3 (mod p) This is a special reduction algorithm that works only for this p Çetin Kaya Koç Spring / 71
65 Reduction with NIST Prime P-192 How can we prove that this reduction is correct? For r = 2 64, we can express the prime as p = r 3 r 1 Given a = A 5 r 5 + A 4 r 4 + A 3 r 3 + A 2 r 2 + A 1 r + A 0, the reduction operation can be expressed as a polynomial reduction b = A 5 r 5 + A 4 r 4 + A 3 r 3 + A 2 r 2 + A 1 r + A 0 (mod r 3 r 1) Using a computer algebra tool, we obtain b as b = (A 5 + A 4 + A 2 )r 2 + (A 5 + A 4 + A 3 + A 1 )r + (A 5 + A 3 + A 0 ) Çetin Kaya Koç Spring / 71
66 Reduction with NIST Prime P-192 By rearranging the terms, we can write Therefore, we obtain r 2 A 2 0 A 4 A 5 r A 1 A 3 A 4 A 5 1 A 0 A 3 0 A 5 T S 1 S 2 S 3 T = (A 2 A 1 A 0 ) S 1 = (0 A 3 A 3 ) S 2 = (A 4 A 4 0) S 3 = (A 5 A 5 A 5 ) Finally: b = T + S 1 + S 2 + S 3 (mod p) Çetin Kaya Koç Spring / 71
67 Reduction with NIST Prime P-521 These specialized algorithms require fewer terms to be computed and added if the binary expansion of the prime contains fewer 1s, i.e., the power of 2 terms in its expression Therefore, primes with few 1s or few power of 2 terms are preferred The NIST P-521 is one such prime: p = Primes of this form are called the Mersenne primes Reduction with such primes is significantly simpler Çetin Kaya Koç Spring / 71
68 Reduction with NIST Prime P-521 Assume A 1 and A 0 are 521-bit integers Every integer less than p 2 can be represented a = A A 0 The compact representation a = (A 1 A 0 ) Consider the reduction operation b = a (mod p) The expression for b is simply given as b = A 1 + A 0 (mod p) A single modular addition suffices to obtain b = a (mod p) Çetin Kaya Koç Spring / 71
69 Reduction with NIST Prime P-521 The expression for b is also easily proven by assigning r = Therefore, p = r 1 and a = A 1 r + A 0 Now we can compute b using polynomial reduction b = A 1 r + A 0 (mod r 1) = A 1 (r 1) + A 1 + A 0 (mod r 1) = A 1 + A 0 (mod r 1) Therefore, b = A 1 + A 0 (mod p) In other words, the reduction requires a single modular addition Çetin Kaya Koç Spring / 71
70 Reduction with Primes of the Form 2 k c The prime for Curve25519 is given as p = Primes of the form p = 2 k c are commonly used in cryptography, where c is a 1-word integer, If we assign r = 2 k, we get p = r c Consider the 2k-bit number a = A 1 r + A 0 To compute b = a (mod p), we perform polynomial reduction b = A 1 r + A 0 (mod r c) = A 1 (r c) + c A 1 + A 0 (mod r c) = c A 1 + A 0 (mod r c) The final reduced value is computed as b = c A 1 + A 0 (mod p) Çetin Kaya Koç Spring / 71
71 Generalized Mersenne Numbers The reduction algorithm for prime p = is invented by Jerome Solinas, who developed several specialized reduction algorithms for the NIST primes For example, consider p = Given the 32-bit numbers A i, the mod p reduction of the 2k-bit number a = (A 13 A 12 A 1 A 0 ) is accomplished as T = (A 6 A 5 A 4 A 3 A 2 A 1 A 0 ) S 1 = (A 10 A 9 A 8 A ) S 2 = (0 A 13 A 12 A ) D 1 = (A 13 A 12 A 11 A 10 A 9 A 8 A 7 ) D 2 = ( A 13 A 12 A 11 ) b = T + S 1 + A 2 D 1 D 2 (mod p) Çetin Kaya Koç Spring / 71
Exponentiation and Point Multiplication. Çetin Kaya Koç Spring / 70
 Exponentiation and Point Multiplication 1 2 3 4 5 6 8 7 10 9 12 16 14 11 13 15 20 http://koclab.org Çetin Kaya Koç Spring 2018 1 / 70 Contents Exponentiation and Point Multiplication Exponentiation and
Exponentiation and Point Multiplication 1 2 3 4 5 6 8 7 10 9 12 16 14 11 13 15 20 http://koclab.org Çetin Kaya Koç Spring 2018 1 / 70 Contents Exponentiation and Point Multiplication Exponentiation and
Numbers. Çetin Kaya Koç Winter / 18
 Çetin Kaya Koç http://koclab.cs.ucsb.edu Winter 2016 1 / 18 Number Systems and Sets We represent the set of integers as Z = {..., 3, 2, 1,0,1,2,3,...} We denote the set of positive integers modulo n as
Çetin Kaya Koç http://koclab.cs.ucsb.edu Winter 2016 1 / 18 Number Systems and Sets We represent the set of integers as Z = {..., 3, 2, 1,0,1,2,3,...} We denote the set of positive integers modulo n as
RSA Implementation. Oregon State University
 RSA Implementation Çetin Kaya Koç Oregon State University 1 Contents: Exponentiation heuristics Multiplication algorithms Computation of GCD and Inverse Chinese remainder algorithm Primality testing 2
RSA Implementation Çetin Kaya Koç Oregon State University 1 Contents: Exponentiation heuristics Multiplication algorithms Computation of GCD and Inverse Chinese remainder algorithm Primality testing 2
SUFFIX PROPERTY OF INVERSE MOD
 IEEE TRANSACTIONS ON COMPUTERS, 2018 1 Algorithms for Inversion mod p k Çetin Kaya Koç, Fellow, IEEE, Abstract This paper describes and analyzes all existing algorithms for computing x = a 1 (mod p k )
IEEE TRANSACTIONS ON COMPUTERS, 2018 1 Algorithms for Inversion mod p k Çetin Kaya Koç, Fellow, IEEE, Abstract This paper describes and analyzes all existing algorithms for computing x = a 1 (mod p k )
Lecture 8: Sequential Multipliers
 Lecture 8: Sequential Multipliers ECE 645 Computer Arithmetic 3/25/08 ECE 645 Computer Arithmetic Lecture Roadmap Sequential Multipliers Unsigned Signed Radix-2 Booth Recoding High-Radix Multiplication
Lecture 8: Sequential Multipliers ECE 645 Computer Arithmetic 3/25/08 ECE 645 Computer Arithmetic Lecture Roadmap Sequential Multipliers Unsigned Signed Radix-2 Booth Recoding High-Radix Multiplication
Fields in Cryptography. Çetin Kaya Koç Winter / 30
 Fields in Cryptography http://koclab.org Çetin Kaya Koç Winter 2017 1 / 30 Field Axioms Fields in Cryptography A field F consists of a set S and two operations which we will call addition and multiplication,
Fields in Cryptography http://koclab.org Çetin Kaya Koç Winter 2017 1 / 30 Field Axioms Fields in Cryptography A field F consists of a set S and two operations which we will call addition and multiplication,
Logic and Computer Design Fundamentals. Chapter 5 Arithmetic Functions and Circuits
 Logic and Computer Design Fundamentals Chapter 5 Arithmetic Functions and Circuits Arithmetic functions Operate on binary vectors Use the same subfunction in each bit position Can design functional block
Logic and Computer Design Fundamentals Chapter 5 Arithmetic Functions and Circuits Arithmetic functions Operate on binary vectors Use the same subfunction in each bit position Can design functional block
Carry Look Ahead Adders
 Carry Look Ahead Adders Lesson Objectives: The objectives of this lesson are to learn about: 1. Carry Look Ahead Adder circuit. 2. Binary Parallel Adder/Subtractor circuit. 3. BCD adder circuit. 4. Binary
Carry Look Ahead Adders Lesson Objectives: The objectives of this lesson are to learn about: 1. Carry Look Ahead Adder circuit. 2. Binary Parallel Adder/Subtractor circuit. 3. BCD adder circuit. 4. Binary
Hardware Design I Chap. 4 Representative combinational logic
 Hardware Design I Chap. 4 Representative combinational logic E-mail: shimada@is.naist.jp Already optimized circuits There are many optimized circuits which are well used You can reduce your design workload
Hardware Design I Chap. 4 Representative combinational logic E-mail: shimada@is.naist.jp Already optimized circuits There are many optimized circuits which are well used You can reduce your design workload
Chapter 5 Arithmetic Circuits
 Chapter 5 Arithmetic Circuits SKEE2263 Digital Systems Mun im/ismahani/izam {munim@utm.my,e-izam@utm.my,ismahani@fke.utm.my} February 11, 2016 Table of Contents 1 Iterative Designs 2 Adders 3 High-Speed
Chapter 5 Arithmetic Circuits SKEE2263 Digital Systems Mun im/ismahani/izam {munim@utm.my,e-izam@utm.my,ismahani@fke.utm.my} February 11, 2016 Table of Contents 1 Iterative Designs 2 Adders 3 High-Speed
The goal differs from prime factorization. Prime factorization would initialize all divisors to be prime numbers instead of integers*
 Quantum Algorithm Processor For Finding Exact Divisors Professor J R Burger Summary Wiring diagrams are given for a quantum algorithm processor in CMOS to compute, in parallel, all divisors of an n-bit
Quantum Algorithm Processor For Finding Exact Divisors Professor J R Burger Summary Wiring diagrams are given for a quantum algorithm processor in CMOS to compute, in parallel, all divisors of an n-bit
EECS150 - Digital Design Lecture 24 - Arithmetic Blocks, Part 2 + Shifters
 EECS150 - Digital Design Lecture 24 - Arithmetic Blocks, Part 2 + Shifters April 15, 2010 John Wawrzynek 1 Multiplication a 3 a 2 a 1 a 0 Multiplicand b 3 b 2 b 1 b 0 Multiplier X a 3 b 0 a 2 b 0 a 1 b
EECS150 - Digital Design Lecture 24 - Arithmetic Blocks, Part 2 + Shifters April 15, 2010 John Wawrzynek 1 Multiplication a 3 a 2 a 1 a 0 Multiplicand b 3 b 2 b 1 b 0 Multiplier X a 3 b 0 a 2 b 0 a 1 b
ARITHMETIC COMBINATIONAL MODULES AND NETWORKS
 ARITHMETIC COMBINATIONAL MODULES AND NETWORKS 1 SPECIFICATION OF ADDER MODULES FOR POSITIVE INTEGERS HALF-ADDER AND FULL-ADDER MODULES CARRY-RIPPLE AND CARRY-LOOKAHEAD ADDER MODULES NETWORKS OF ADDER MODULES
ARITHMETIC COMBINATIONAL MODULES AND NETWORKS 1 SPECIFICATION OF ADDER MODULES FOR POSITIVE INTEGERS HALF-ADDER AND FULL-ADDER MODULES CARRY-RIPPLE AND CARRY-LOOKAHEAD ADDER MODULES NETWORKS OF ADDER MODULES
Chinese Remainder Algorithms. Çetin Kaya Koç Spring / 22
 Chinese Remainder Algorithms http://koclab.org Çetin Kaya Koç Spring 2018 1 / 22 The Chinese Remainder Theorem Some cryptographic algorithms work with two (such as RSA) or more moduli (such as secret-sharing)
Chinese Remainder Algorithms http://koclab.org Çetin Kaya Koç Spring 2018 1 / 22 The Chinese Remainder Theorem Some cryptographic algorithms work with two (such as RSA) or more moduli (such as secret-sharing)
Looking at a two binary digit sum shows what we need to extend addition to multiple binary digits.
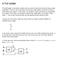 A Full Adder The half-adder is extremely useful until you want to add more that one binary digit quantities. The slow way to develop a two binary digit adders would be to make a truth table and reduce
A Full Adder The half-adder is extremely useful until you want to add more that one binary digit quantities. The slow way to develop a two binary digit adders would be to make a truth table and reduce
Binary addition by hand. Adding two bits
 Chapter 3 Arithmetic is the most basic thing you can do with a computer We focus on addition, subtraction, multiplication and arithmetic-logic units, or ALUs, which are the heart of CPUs. ALU design Bit
Chapter 3 Arithmetic is the most basic thing you can do with a computer We focus on addition, subtraction, multiplication and arithmetic-logic units, or ALUs, which are the heart of CPUs. ALU design Bit
A Bit-Serial Unified Multiplier Architecture for Finite Fields GF(p) and GF(2 m )
 A Bit-Serial Unified Multiplier Architecture for Finite Fields GF(p) and GF(2 m ) Johann Großschädl Graz University of Technology Institute for Applied Information Processing and Communications Inffeldgasse
A Bit-Serial Unified Multiplier Architecture for Finite Fields GF(p) and GF(2 m ) Johann Großschädl Graz University of Technology Institute for Applied Information Processing and Communications Inffeldgasse
Continuing discussion of CRC s, especially looking at two-bit errors
 Continuing discussion of CRC s, especially looking at two-bit errors The definition of primitive binary polynomials Brute force checking for primitivity A theorem giving a better test for primitivity Fast
Continuing discussion of CRC s, especially looking at two-bit errors The definition of primitive binary polynomials Brute force checking for primitivity A theorem giving a better test for primitivity Fast
ECE 545 Digital System Design with VHDL Lecture 1. Digital Logic Refresher Part A Combinational Logic Building Blocks
 ECE 545 Digital System Design with VHDL Lecture Digital Logic Refresher Part A Combinational Logic Building Blocks Lecture Roadmap Combinational Logic Basic Logic Review Basic Gates De Morgan s Law Combinational
ECE 545 Digital System Design with VHDL Lecture Digital Logic Refresher Part A Combinational Logic Building Blocks Lecture Roadmap Combinational Logic Basic Logic Review Basic Gates De Morgan s Law Combinational
Efficient Hardware Implementation of Finite Fields with Applications to Cryptography
 Acta Appl Math (2006) 93: 75 118 DOI 10.1007/s10440-006-9072-z Efficient Hardware Implementation of Finite Fields with Applications to Cryptography Jorge Guajardo Tim Güneysu Sandeep S. Kumar Christof
Acta Appl Math (2006) 93: 75 118 DOI 10.1007/s10440-006-9072-z Efficient Hardware Implementation of Finite Fields with Applications to Cryptography Jorge Guajardo Tim Güneysu Sandeep S. Kumar Christof
A High-Speed Realization of Chinese Remainder Theorem
 Proceedings of the 2007 WSEAS Int. Conference on Circuits, Systems, Signal and Telecommunications, Gold Coast, Australia, January 17-19, 2007 97 A High-Speed Realization of Chinese Remainder Theorem Shuangching
Proceedings of the 2007 WSEAS Int. Conference on Circuits, Systems, Signal and Telecommunications, Gold Coast, Australia, January 17-19, 2007 97 A High-Speed Realization of Chinese Remainder Theorem Shuangching
Frequency Domain Finite Field Arithmetic for Elliptic Curve Cryptography
 Frequency Domain Finite Field Arithmetic for Elliptic Curve Cryptography Selçuk Baktır, Berk Sunar {selcuk,sunar}@wpi.edu Department of Electrical & Computer Engineering Worcester Polytechnic Institute
Frequency Domain Finite Field Arithmetic for Elliptic Curve Cryptography Selçuk Baktır, Berk Sunar {selcuk,sunar}@wpi.edu Department of Electrical & Computer Engineering Worcester Polytechnic Institute
Number representation
 Number representation A number can be represented in binary in many ways. The most common number types to be represented are: Integers, positive integers one-complement, two-complement, sign-magnitude
Number representation A number can be represented in binary in many ways. The most common number types to be represented are: Integers, positive integers one-complement, two-complement, sign-magnitude
Computer Architecture 10. Fast Adders
 Computer Architecture 10 Fast s Ma d e wi t h Op e n Of f i c e. o r g 1 Carry Problem Addition is primary mechanism in implementing arithmetic operations Slow addition directly affects the total performance
Computer Architecture 10 Fast s Ma d e wi t h Op e n Of f i c e. o r g 1 Carry Problem Addition is primary mechanism in implementing arithmetic operations Slow addition directly affects the total performance
CPSC 467: Cryptography and Computer Security
 CPSC 467: Cryptography and Computer Security Michael J. Fischer Lecture 9 September 30, 2015 CPSC 467, Lecture 9 1/47 Fast Exponentiation Algorithms Number Theory Needed for RSA Elementary Number Theory
CPSC 467: Cryptography and Computer Security Michael J. Fischer Lecture 9 September 30, 2015 CPSC 467, Lecture 9 1/47 Fast Exponentiation Algorithms Number Theory Needed for RSA Elementary Number Theory
Residue Number Systems Ivor Page 1
 Residue Number Systems 1 Residue Number Systems Ivor Page 1 7.1 Arithmetic in a modulus system The great speed of arithmetic in Residue Number Systems (RNS) comes from a simple theorem from number theory:
Residue Number Systems 1 Residue Number Systems Ivor Page 1 7.1 Arithmetic in a modulus system The great speed of arithmetic in Residue Number Systems (RNS) comes from a simple theorem from number theory:
Stream Ciphers. Çetin Kaya Koç Winter / 20
 Çetin Kaya Koç http://koclab.cs.ucsb.edu Winter 2016 1 / 20 Linear Congruential Generators A linear congruential generator produces a sequence of integers x i for i = 1,2,... starting with the given initial
Çetin Kaya Koç http://koclab.cs.ucsb.edu Winter 2016 1 / 20 Linear Congruential Generators A linear congruential generator produces a sequence of integers x i for i = 1,2,... starting with the given initial
Chapter 5. Digital Design and Computer Architecture, 2 nd Edition. David Money Harris and Sarah L. Harris. Chapter 5 <1>
 Chapter 5 Digital Design and Computer Architecture, 2 nd Edition David Money Harris and Sarah L. Harris Chapter 5 Chapter 5 :: Topics Introduction Arithmetic Circuits umber Systems Sequential Building
Chapter 5 Digital Design and Computer Architecture, 2 nd Edition David Money Harris and Sarah L. Harris Chapter 5 Chapter 5 :: Topics Introduction Arithmetic Circuits umber Systems Sequential Building
1 Short adders. t total_ripple8 = t first + 6*t middle + t last = 4t p + 6*2t p + 2t p = 18t p
 UNIVERSITY OF CALIFORNIA College of Engineering Department of Electrical Engineering and Computer Sciences Study Homework: Arithmetic NTU IC54CA (Fall 2004) SOLUTIONS Short adders A The delay of the ripple
UNIVERSITY OF CALIFORNIA College of Engineering Department of Electrical Engineering and Computer Sciences Study Homework: Arithmetic NTU IC54CA (Fall 2004) SOLUTIONS Short adders A The delay of the ripple
Groups in Cryptography. Çetin Kaya Koç Winter / 13
 http://koclab.org Çetin Kaya Koç Winter 2017 1 / 13 A set S and a binary operation A group G = (S, ) if S and satisfy: Closure: If a, b S then a b S Associativity: For a, b, c S, (a b) c = a (b c) A neutral
http://koclab.org Çetin Kaya Koç Winter 2017 1 / 13 A set S and a binary operation A group G = (S, ) if S and satisfy: Closure: If a, b S then a b S Associativity: For a, b, c S, (a b) c = a (b c) A neutral
Adders, subtractors comparators, multipliers and other ALU elements
 CSE4: Components and Design Techniques for Digital Systems Adders, subtractors comparators, multipliers and other ALU elements Instructor: Mohsen Imani UC San Diego Slides from: Prof.Tajana Simunic Rosing
CSE4: Components and Design Techniques for Digital Systems Adders, subtractors comparators, multipliers and other ALU elements Instructor: Mohsen Imani UC San Diego Slides from: Prof.Tajana Simunic Rosing
Efficient Software-Implementation of Finite Fields with Applications to Cryptography
 DOI 10.1007/s10440-006-9046-1 Efficient Software-Implementation of Finite Fields with Applications to Cryptography Jorge Guajardo Sandeep S. Kumar Christof Paar Jan Pelzl Springer Science + Business Media
DOI 10.1007/s10440-006-9046-1 Efficient Software-Implementation of Finite Fields with Applications to Cryptography Jorge Guajardo Sandeep S. Kumar Christof Paar Jan Pelzl Springer Science + Business Media
A VLSI Algorithm for Modular Multiplication/Division
 A VLSI Algorithm for Modular Multiplication/Division Marcelo E. Kaihara and Naofumi Takagi Department of Information Engineering Nagoya University Nagoya, 464-8603, Japan mkaihara@takagi.nuie.nagoya-u.ac.jp
A VLSI Algorithm for Modular Multiplication/Division Marcelo E. Kaihara and Naofumi Takagi Department of Information Engineering Nagoya University Nagoya, 464-8603, Japan mkaihara@takagi.nuie.nagoya-u.ac.jp
Basic elements of number theory
 Cryptography Basic elements of number theory Marius Zimand By default all the variables, such as a, b, k, etc., denote integer numbers. Divisibility a 0 divides b if b = a k for some integer k. Notation
Cryptography Basic elements of number theory Marius Zimand By default all the variables, such as a, b, k, etc., denote integer numbers. Divisibility a 0 divides b if b = a k for some integer k. Notation
Basic elements of number theory
 Cryptography Basic elements of number theory Marius Zimand 1 Divisibility, prime numbers By default all the variables, such as a, b, k, etc., denote integer numbers. Divisibility a 0 divides b if b = a
Cryptography Basic elements of number theory Marius Zimand 1 Divisibility, prime numbers By default all the variables, such as a, b, k, etc., denote integer numbers. Divisibility a 0 divides b if b = a
Combinational Logic Design Arithmetic Functions and Circuits
 Combinational Logic Design Arithmetic Functions and Circuits Overview Binary Addition Half Adder Full Adder Ripple Carry Adder Carry Look-ahead Adder Binary Subtraction Binary Subtractor Binary Adder-Subtractor
Combinational Logic Design Arithmetic Functions and Circuits Overview Binary Addition Half Adder Full Adder Ripple Carry Adder Carry Look-ahead Adder Binary Subtraction Binary Subtractor Binary Adder-Subtractor
Lecture 8. Sequential Multipliers
 Lecture 8 Sequential Multipliers Required Reading Behrooz Parhami, Computer Arithmetic: Algorithms and Hardware Design Chapter 9, Basic Multiplication Scheme Chapter 10, High-Radix Multipliers Chapter
Lecture 8 Sequential Multipliers Required Reading Behrooz Parhami, Computer Arithmetic: Algorithms and Hardware Design Chapter 9, Basic Multiplication Scheme Chapter 10, High-Radix Multipliers Chapter
Discrete Logarithm Problem
 Discrete Logarithm Problem Çetin Kaya Koç koc@cs.ucsb.edu (http://cs.ucsb.edu/~koc/ecc) Elliptic Curve Cryptography lect08 discrete log 1 / 46 Exponentiation and Logarithms in a General Group In a multiplicative
Discrete Logarithm Problem Çetin Kaya Koç koc@cs.ucsb.edu (http://cs.ucsb.edu/~koc/ecc) Elliptic Curve Cryptography lect08 discrete log 1 / 46 Exponentiation and Logarithms in a General Group In a multiplicative
Galois Field Algebra and RAID6. By David Jacob
 Galois Field Algebra and RAID6 By David Jacob 1 Overview Galois Field Definitions Addition/Subtraction Multiplication Division Hardware Implementation RAID6 Definitions Encoding Error Detection Error Correction
Galois Field Algebra and RAID6 By David Jacob 1 Overview Galois Field Definitions Addition/Subtraction Multiplication Division Hardware Implementation RAID6 Definitions Encoding Error Detection Error Correction
Linear Feedback Shift Registers (LFSRs) 4-bit LFSR
 Linear Feedback Shift Registers (LFSRs) These are n-bit counters exhibiting pseudo-random behavior. Built from simple shift-registers with a small number of xor gates. Used for: random number generation
Linear Feedback Shift Registers (LFSRs) These are n-bit counters exhibiting pseudo-random behavior. Built from simple shift-registers with a small number of xor gates. Used for: random number generation
Part II Addition / Subtraction
 Part II Addition / Subtraction Parts Chapters I. Number Representation 1. 2. 3. 4. Numbers and Arithmetic Representing Signed Numbers Redundant Number Systems Residue Number Systems Elementary Operations
Part II Addition / Subtraction Parts Chapters I. Number Representation 1. 2. 3. 4. Numbers and Arithmetic Representing Signed Numbers Redundant Number Systems Residue Number Systems Elementary Operations
Reducing the Complexity of Normal Basis Multiplication
 Reducing the Complexity of Normal Basis Multiplication Ömer Eǧecioǧlu and Çetin Kaya Koç Department of Computer Science University of California Santa Barbara {omer,koc}@cs.ucsb.edu Abstract In this paper
Reducing the Complexity of Normal Basis Multiplication Ömer Eǧecioǧlu and Çetin Kaya Koç Department of Computer Science University of California Santa Barbara {omer,koc}@cs.ucsb.edu Abstract In this paper
Chapter 4 Finite Fields
 Chapter 4 Finite Fields Introduction will now introduce finite fields of increasing importance in cryptography AES, Elliptic Curve, IDEA, Public Key concern operations on numbers what constitutes a number
Chapter 4 Finite Fields Introduction will now introduce finite fields of increasing importance in cryptography AES, Elliptic Curve, IDEA, Public Key concern operations on numbers what constitutes a number
New Algorithm for Classical Modular Inverse
 New Algorithm for Classical Modular Inverse Róbert órencz C in Prague CR 9/8/00 CHE 00 1 Introduction - Modular Inverse Inseparable part of cryptographic algorithms. Always needed classical modular inverse
New Algorithm for Classical Modular Inverse Róbert órencz C in Prague CR 9/8/00 CHE 00 1 Introduction - Modular Inverse Inseparable part of cryptographic algorithms. Always needed classical modular inverse
Algorithms (II) Yu Yu. Shanghai Jiaotong University
 Algorithms (II) Yu Yu Shanghai Jiaotong University Chapter 1. Algorithms with Numbers Two seemingly similar problems Factoring: Given a number N, express it as a product of its prime factors. Primality:
Algorithms (II) Yu Yu Shanghai Jiaotong University Chapter 1. Algorithms with Numbers Two seemingly similar problems Factoring: Given a number N, express it as a product of its prime factors. Primality:
ECE380 Digital Logic. Positional representation
 ECE380 Digital Logic Number Representation and Arithmetic Circuits: Number Representation and Unsigned Addition Dr. D. J. Jackson Lecture 16-1 Positional representation First consider integers Begin with
ECE380 Digital Logic Number Representation and Arithmetic Circuits: Number Representation and Unsigned Addition Dr. D. J. Jackson Lecture 16-1 Positional representation First consider integers Begin with
Cryptographic Hash Functions
 Cryptographic Hash Functions Çetin Kaya Koç koc@ece.orst.edu Electrical & Computer Engineering Oregon State University Corvallis, Oregon 97331 Technical Report December 9, 2002 Version 1.5 1 1 Introduction
Cryptographic Hash Functions Çetin Kaya Koç koc@ece.orst.edu Electrical & Computer Engineering Oregon State University Corvallis, Oregon 97331 Technical Report December 9, 2002 Version 1.5 1 1 Introduction
Binary Multipliers. Reading: Study Chapter 3. The key trick of multiplication is memorizing a digit-to-digit table Everything else was just adding
 Binary Multipliers The key trick of multiplication is memorizing a digit-to-digit table Everything else was just adding 2 3 4 5 6 7 8 9 2 3 4 5 6 7 8 9 2 2 4 6 8 2 4 6 8 3 3 6 9 2 5 8 2 24 27 4 4 8 2 6
Binary Multipliers The key trick of multiplication is memorizing a digit-to-digit table Everything else was just adding 2 3 4 5 6 7 8 9 2 3 4 5 6 7 8 9 2 2 4 6 8 2 4 6 8 3 3 6 9 2 5 8 2 24 27 4 4 8 2 6
CS 140 Lecture 14 Standard Combinational Modules
 CS 14 Lecture 14 Standard Combinational Modules Professor CK Cheng CSE Dept. UC San Diego Some slides from Harris and Harris 1 Part III. Standard Modules A. Interconnect B. Operators. Adders Multiplier
CS 14 Lecture 14 Standard Combinational Modules Professor CK Cheng CSE Dept. UC San Diego Some slides from Harris and Harris 1 Part III. Standard Modules A. Interconnect B. Operators. Adders Multiplier
EECS150 - Digital Design Lecture 21 - Design Blocks
 EECS150 - Digital Design Lecture 21 - Design Blocks April 3, 2012 John Wawrzynek Spring 2012 EECS150 - Lec21-db3 Page 1 Fixed Shifters / Rotators fixed shifters hardwire the shift amount into the circuit.
EECS150 - Digital Design Lecture 21 - Design Blocks April 3, 2012 John Wawrzynek Spring 2012 EECS150 - Lec21-db3 Page 1 Fixed Shifters / Rotators fixed shifters hardwire the shift amount into the circuit.
Midterm Exam Two is scheduled on April 8 in class. On March 27 I will help you prepare Midterm Exam Two.
 Announcements Midterm Exam Two is scheduled on April 8 in class. On March 27 I will help you prepare Midterm Exam Two. Chapter 5 1 Chapter 3: Part 3 Arithmetic Functions Iterative combinational circuits
Announcements Midterm Exam Two is scheduled on April 8 in class. On March 27 I will help you prepare Midterm Exam Two. Chapter 5 1 Chapter 3: Part 3 Arithmetic Functions Iterative combinational circuits
Part II Addition / Subtraction
 Part II Addition / Subtraction Parts Chapters I. Number Representation 1. 2. 3. 4. Numbers and Arithmetic Representing Signed Numbers Redundant Number Systems Residue Number Systems Elementary Operations
Part II Addition / Subtraction Parts Chapters I. Number Representation 1. 2. 3. 4. Numbers and Arithmetic Representing Signed Numbers Redundant Number Systems Residue Number Systems Elementary Operations
A Simple Left-to-Right Algorithm for Minimal Weight Signed Radix-r Representations
 A Simple Left-to-Right Algorithm for Minimal Weight Signed Radix-r Representations James A. Muir School of Computer Science Carleton University, Ottawa, Canada http://www.scs.carleton.ca/ jamuir 23 October
A Simple Left-to-Right Algorithm for Minimal Weight Signed Radix-r Representations James A. Muir School of Computer Science Carleton University, Ottawa, Canada http://www.scs.carleton.ca/ jamuir 23 October
Adders, subtractors comparators, multipliers and other ALU elements
 CSE4: Components and Design Techniques for Digital Systems Adders, subtractors comparators, multipliers and other ALU elements Adders 2 Circuit Delay Transistors have instrinsic resistance and capacitance
CSE4: Components and Design Techniques for Digital Systems Adders, subtractors comparators, multipliers and other ALU elements Adders 2 Circuit Delay Transistors have instrinsic resistance and capacitance
Number Theory. CSS322: Security and Cryptography. Sirindhorn International Institute of Technology Thammasat University CSS322. Number Theory.
 CSS322: Security and Cryptography Sirindhorn International Institute of Technology Thammasat University Prepared by Steven Gordon on 29 December 2011 CSS322Y11S2L06, Steve/Courses/2011/S2/CSS322/Lectures/number.tex,
CSS322: Security and Cryptography Sirindhorn International Institute of Technology Thammasat University Prepared by Steven Gordon on 29 December 2011 CSS322Y11S2L06, Steve/Courses/2011/S2/CSS322/Lectures/number.tex,
Reduce-by-Feedback: Timing resistant and DPA-aware Modular Multiplication plus: How to Break RSA by DPA
 Reduce-by-Feedback: Timing resistant and DPA-aware Modular Multiplication plus: How to Break RSA by DPA M. Vielhaber vielhaber@gmail.com Hochschule Bremerhaven und/y Universidad Austral de Chile CHES 2012
Reduce-by-Feedback: Timing resistant and DPA-aware Modular Multiplication plus: How to Break RSA by DPA M. Vielhaber vielhaber@gmail.com Hochschule Bremerhaven und/y Universidad Austral de Chile CHES 2012
Number theory (Chapter 4)
 EECS 203 Spring 2016 Lecture 10 Page 1 of 8 Number theory (Chapter 4) Review Questions: 1. Does 5 1? Does 1 5? 2. Does (129+63) mod 10 = (129 mod 10)+(63 mod 10)? 3. Does (129+63) mod 10 = ((129 mod 10)+(63
EECS 203 Spring 2016 Lecture 10 Page 1 of 8 Number theory (Chapter 4) Review Questions: 1. Does 5 1? Does 1 5? 2. Does (129+63) mod 10 = (129 mod 10)+(63 mod 10)? 3. Does (129+63) mod 10 = ((129 mod 10)+(63
Chapter 4 Mathematics of Cryptography
 Chapter 4 Mathematics of Cryptography Part II: Algebraic Structures Copyright The McGraw-Hill Companies, Inc. Permission required for reproduction or display. 4.1 Chapter 4 Objectives To review the concept
Chapter 4 Mathematics of Cryptography Part II: Algebraic Structures Copyright The McGraw-Hill Companies, Inc. Permission required for reproduction or display. 4.1 Chapter 4 Objectives To review the concept
ELEN Electronique numérique
 ELEN0040 - Electronique numérique Patricia ROUSSEAUX Année académique 2014-2015 CHAPITRE 3 Combinational Logic Circuits ELEN0040 3-4 1 Combinational Functional Blocks 1.1 Rudimentary Functions 1.2 Functions
ELEN0040 - Electronique numérique Patricia ROUSSEAUX Année académique 2014-2015 CHAPITRE 3 Combinational Logic Circuits ELEN0040 3-4 1 Combinational Functional Blocks 1.1 Rudimentary Functions 1.2 Functions
Dual-Field Arithmetic Unit for GF(p) and GF(2 m ) *
 Institute for Applied Information Processing and Communications Graz University of Technology Dual-Field Arithmetic Unit for GF(p) and GF(2 m ) * CHES 2002 Workshop on Cryptographic Hardware and Embedded
Institute for Applied Information Processing and Communications Graz University of Technology Dual-Field Arithmetic Unit for GF(p) and GF(2 m ) * CHES 2002 Workshop on Cryptographic Hardware and Embedded
GF(2 m ) arithmetic: summary
 GF(2 m ) arithmetic: summary EE 387, Notes 18, Handout #32 Addition/subtraction: bitwise XOR (m gates/ops) Multiplication: bit serial (shift and add) bit parallel (combinational) subfield representation
GF(2 m ) arithmetic: summary EE 387, Notes 18, Handout #32 Addition/subtraction: bitwise XOR (m gates/ops) Multiplication: bit serial (shift and add) bit parallel (combinational) subfield representation
Hybrid Binary-Ternary Joint Sparse Form and its Application in Elliptic Curve Cryptography
 Hybrid Binary-Ternary Joint Sparse Form and its Application in Elliptic Curve Cryptography Jithra Adikari, Student Member, IEEE, Vassil Dimitrov, and Laurent Imbert Abstract Multi-exponentiation is a common
Hybrid Binary-Ternary Joint Sparse Form and its Application in Elliptic Curve Cryptography Jithra Adikari, Student Member, IEEE, Vassil Dimitrov, and Laurent Imbert Abstract Multi-exponentiation is a common
Are standards compliant Elliptic Curve Cryptosystems feasible on RFID?
 Are standards compliant Elliptic Curve Cryptosystems feasible on RFID? Sandeep S. Kumar and Christof Paar Horst Görtz Institute for IT Security, Ruhr-Universität Bochum, Germany Abstract. With elliptic
Are standards compliant Elliptic Curve Cryptosystems feasible on RFID? Sandeep S. Kumar and Christof Paar Horst Görtz Institute for IT Security, Ruhr-Universität Bochum, Germany Abstract. With elliptic
Finite Fields. Mike Reiter
 1 Finite Fields Mike Reiter reiter@cs.unc.edu Based on Chapter 4 of: W. Stallings. Cryptography and Network Security, Principles and Practices. 3 rd Edition, 2003. Groups 2 A group G, is a set G of elements
1 Finite Fields Mike Reiter reiter@cs.unc.edu Based on Chapter 4 of: W. Stallings. Cryptography and Network Security, Principles and Practices. 3 rd Edition, 2003. Groups 2 A group G, is a set G of elements
COMPUTERS ORGANIZATION 2ND YEAR COMPUTE SCIENCE MANAGEMENT ENGINEERING UNIT 3 - ARITMETHIC-LOGIC UNIT JOSÉ GARCÍA RODRÍGUEZ JOSÉ ANTONIO SERRA PÉREZ
 OMUTERS ORGANIZATION 2ND YEAR OMUTE SIENE MANAGEMENT ENGINEERING UNIT 3 - ARITMETHI-LOGI UNIT JOSÉ GARÍA RODRÍGUEZ JOSÉ ANTONIO SERRA ÉREZ Tema 3. La Unidad entral de roceso. A.L.U. Arithmetic Logic Unit
OMUTERS ORGANIZATION 2ND YEAR OMUTE SIENE MANAGEMENT ENGINEERING UNIT 3 - ARITMETHI-LOGI UNIT JOSÉ GARÍA RODRÍGUEZ JOSÉ ANTONIO SERRA ÉREZ Tema 3. La Unidad entral de roceso. A.L.U. Arithmetic Logic Unit
Chinese Remainder Theorem
 Chinese Remainder Theorem Çetin Kaya Koç koc@cs.ucsb.edu Çetin Kaya Koç http://koclab.org Winter 2017 1 / 16 The Chinese Remainder Theorem Some cryptographic algorithms work with two (such as RSA) or more
Chinese Remainder Theorem Çetin Kaya Koç koc@cs.ucsb.edu Çetin Kaya Koç http://koclab.org Winter 2017 1 / 16 The Chinese Remainder Theorem Some cryptographic algorithms work with two (such as RSA) or more
Chapter 03: Computer Arithmetic. Lesson 03: Arithmetic Operations Adder and Subtractor circuits Design
 Chapter 03: Computer Arithmetic Lesson 03: Arithmetic Operations Adder and Subtractor circuits Design Objective To understand adder circuit Subtractor circuit Fast adder circuit 2 Adder Circuit 3 Full
Chapter 03: Computer Arithmetic Lesson 03: Arithmetic Operations Adder and Subtractor circuits Design Objective To understand adder circuit Subtractor circuit Fast adder circuit 2 Adder Circuit 3 Full
COMS W4995 Introduction to Cryptography September 29, Lecture 8: Number Theory
 COMS W4995 Introduction to Cryptography September 29, 2005 Lecture 8: Number Theory Lecturer: Tal Malkin Scribes: Elli Androulaki, Mohit Vazirani Summary This lecture focuses on some basic Number Theory.
COMS W4995 Introduction to Cryptography September 29, 2005 Lecture 8: Number Theory Lecturer: Tal Malkin Scribes: Elli Androulaki, Mohit Vazirani Summary This lecture focuses on some basic Number Theory.
An Optimized Hardware Architecture of Montgomery Multiplication Algorithm
 An Optimized Hardware Architecture of Montgomery Multiplication Algorithm Miaoqing Huang 1, Kris Gaj 2, Soonhak Kwon 3, and Tarek El-Ghazawi 1 1 The George Washington University, Washington, DC 20052,
An Optimized Hardware Architecture of Montgomery Multiplication Algorithm Miaoqing Huang 1, Kris Gaj 2, Soonhak Kwon 3, and Tarek El-Ghazawi 1 1 The George Washington University, Washington, DC 20052,
Modular Multiplication in GF (p k ) using Lagrange Representation
 Modular Multiplication in GF (p k ) using Lagrange Representation Jean-Claude Bajard, Laurent Imbert, and Christophe Nègre Laboratoire d Informatique, de Robotique et de Microélectronique de Montpellier
Modular Multiplication in GF (p k ) using Lagrange Representation Jean-Claude Bajard, Laurent Imbert, and Christophe Nègre Laboratoire d Informatique, de Robotique et de Microélectronique de Montpellier
2WF15 - Discrete Mathematics 2 - Part 1. Algorithmic Number Theory
 1 2WF15 - Discrete Mathematics 2 - Part 1 Algorithmic Number Theory Benne de Weger version 0.54, March 6, 2012 version 0.54, March 6, 2012 2WF15 - Discrete Mathematics 2 - Part 1 2 2WF15 - Discrete Mathematics
1 2WF15 - Discrete Mathematics 2 - Part 1 Algorithmic Number Theory Benne de Weger version 0.54, March 6, 2012 version 0.54, March 6, 2012 2WF15 - Discrete Mathematics 2 - Part 1 2 2WF15 - Discrete Mathematics
ax b mod m. has a solution if and only if d b. In this case, there is one solution, call it x 0, to the equation and there are d solutions x m d
 10. Linear congruences In general we are going to be interested in the problem of solving polynomial equations modulo an integer m. Following Gauss, we can work in the ring Z m and find all solutions to
10. Linear congruences In general we are going to be interested in the problem of solving polynomial equations modulo an integer m. Following Gauss, we can work in the ring Z m and find all solutions to
Counting Prime Numbers with Short Binary Signed Representation
 Counting Prime Numbers with Short Binary Signed Representation José de Jesús Angel Angel and Guillermo Morales-Luna Computer Science Section, CINVESTAV-IPN, Mexico jjangel@computacion.cs.cinvestav.mx,
Counting Prime Numbers with Short Binary Signed Representation José de Jesús Angel Angel and Guillermo Morales-Luna Computer Science Section, CINVESTAV-IPN, Mexico jjangel@computacion.cs.cinvestav.mx,
Combinational Logic. By : Ali Mustafa
 Combinational Logic By : Ali Mustafa Contents Adder Subtractor Multiplier Comparator Decoder Encoder Multiplexer How to Analyze any combinational circuit like this? Analysis Procedure To obtain the output
Combinational Logic By : Ali Mustafa Contents Adder Subtractor Multiplier Comparator Decoder Encoder Multiplexer How to Analyze any combinational circuit like this? Analysis Procedure To obtain the output
Total Time = 90 Minutes, Total Marks = 100. Total /10 /25 /20 /10 /15 /20
 University of Waterloo Department of Electrical & Computer Engineering E&CE 223 Digital Circuits and Systems Midterm Examination Instructor: M. Sachdev October 30th, 2006 Total Time = 90 Minutes, Total
University of Waterloo Department of Electrical & Computer Engineering E&CE 223 Digital Circuits and Systems Midterm Examination Instructor: M. Sachdev October 30th, 2006 Total Time = 90 Minutes, Total
Quantum Arithmetic on Galois Fields
 Quantum rithmetic on Galois Fields arxiv:quant-ph/31163v1 9 Jan 3 Stéphane Beauregard, Gilles Brassard, José Manuel Fernande 11 pril bstract In this paper we discuss the problem of performing elementary
Quantum rithmetic on Galois Fields arxiv:quant-ph/31163v1 9 Jan 3 Stéphane Beauregard, Gilles Brassard, José Manuel Fernande 11 pril bstract In this paper we discuss the problem of performing elementary
EFFICIENT MULTIOUTPUT CARRY LOOK-AHEAD ADDERS
 INTERNATIONAL JOURNAL OF RESEARCH IN COMPUTER APPLICATIONS AND ROBOTICS ISSN 2320-7345 EFFICIENT MULTIOUTPUT CARRY LOOK-AHEAD ADDERS B. Venkata Sreecharan 1, C. Venkata Sudhakar 2 1 M.TECH (VLSI DESIGN)
INTERNATIONAL JOURNAL OF RESEARCH IN COMPUTER APPLICATIONS AND ROBOTICS ISSN 2320-7345 EFFICIENT MULTIOUTPUT CARRY LOOK-AHEAD ADDERS B. Venkata Sreecharan 1, C. Venkata Sudhakar 2 1 M.TECH (VLSI DESIGN)
What s the Deal? MULTIPLICATION. Time to multiply
 What s the Deal? MULTIPLICATION Time to multiply Multiplying two numbers requires a multiply Luckily, in binary that s just an AND gate! 0*0=0, 0*1=0, 1*0=0, 1*1=1 Generate a bunch of partial products
What s the Deal? MULTIPLICATION Time to multiply Multiplying two numbers requires a multiply Luckily, in binary that s just an AND gate! 0*0=0, 0*1=0, 1*0=0, 1*1=1 Generate a bunch of partial products
A. Algebra and Number Theory
 A. Algebra and Number Theory Public-key cryptosystems are based on modular arithmetic. In this section, we summarize the concepts and results from algebra and number theory which are necessary for an understanding
A. Algebra and Number Theory Public-key cryptosystems are based on modular arithmetic. In this section, we summarize the concepts and results from algebra and number theory which are necessary for an understanding
Hardware implementations of ECC
 Hardware implementations of ECC The University of Electro- Communications Introduction Public- key Cryptography (PKC) The most famous PKC is RSA and ECC Used for key agreement (Diffie- Hellman), digital
Hardware implementations of ECC The University of Electro- Communications Introduction Public- key Cryptography (PKC) The most famous PKC is RSA and ECC Used for key agreement (Diffie- Hellman), digital
2x 1 7. A linear congruence in modular arithmetic is an equation of the form. Why is the solution a set of integers rather than a unique integer?
 Chapter 3: Theory of Modular Arithmetic 25 SECTION C Solving Linear Congruences By the end of this section you will be able to solve congruence equations determine the number of solutions find the multiplicative
Chapter 3: Theory of Modular Arithmetic 25 SECTION C Solving Linear Congruences By the end of this section you will be able to solve congruence equations determine the number of solutions find the multiplicative
A COMBINED 16-BIT BINARY AND DUAL GALOIS FIELD MULTIPLIER. Jesus Garcia and Michael J. Schulte
 A COMBINED 16-BIT BINARY AND DUAL GALOIS FIELD MULTIPLIER Jesus Garcia and Michael J. Schulte Lehigh University Department of Computer Science and Engineering Bethlehem, PA 15 ABSTRACT Galois field arithmetic
A COMBINED 16-BIT BINARY AND DUAL GALOIS FIELD MULTIPLIER Jesus Garcia and Michael J. Schulte Lehigh University Department of Computer Science and Engineering Bethlehem, PA 15 ABSTRACT Galois field arithmetic
Modular Reduction without Pre-Computation for Special Moduli
 Modular Reduction without Pre-Computation for Special Moduli Tolga Acar and Dan Shumow Extreme Computing Group, Microsoft Research, Microsoft One Microsoft Way, Redmond, WA 98052, USA {tolga,danshu}@microsoft.com
Modular Reduction without Pre-Computation for Special Moduli Tolga Acar and Dan Shumow Extreme Computing Group, Microsoft Research, Microsoft One Microsoft Way, Redmond, WA 98052, USA {tolga,danshu}@microsoft.com
Outline. EECS Components and Design Techniques for Digital Systems. Lec 18 Error Coding. In the real world. Our beautiful digital world.
 Outline EECS 150 - Components and esign Techniques for igital Systems Lec 18 Error Coding Errors and error models Parity and Hamming Codes (SECE) Errors in Communications LFSRs Cyclic Redundancy Check
Outline EECS 150 - Components and esign Techniques for igital Systems Lec 18 Error Coding Errors and error models Parity and Hamming Codes (SECE) Errors in Communications LFSRs Cyclic Redundancy Check
A Suggestion for a Fast Residue Multiplier for a Family of Moduli of the Form (2 n (2 p ± 1))
 The Computer Journal, 47(1), The British Computer Society; all rights reserved A Suggestion for a Fast Residue Multiplier for a Family of Moduli of the Form ( n ( p ± 1)) Ahmad A. Hiasat Electronics Engineering
The Computer Journal, 47(1), The British Computer Society; all rights reserved A Suggestion for a Fast Residue Multiplier for a Family of Moduli of the Form ( n ( p ± 1)) Ahmad A. Hiasat Electronics Engineering
a = a i 2 i a = All such series are automatically convergent with respect to the standard norm, but note that this representation is not unique: i<0
 p-adic Numbers K. Sutner v0.4 1 Modular Arithmetic rings integral domains integers gcd, extended Euclidean algorithm factorization modular numbers add Lemma 1.1 (Chinese Remainder Theorem) Let a b. Then
p-adic Numbers K. Sutner v0.4 1 Modular Arithmetic rings integral domains integers gcd, extended Euclidean algorithm factorization modular numbers add Lemma 1.1 (Chinese Remainder Theorem) Let a b. Then
4 Number Theory and Cryptography
 4 Number Theory and Cryptography 4.1 Divisibility and Modular Arithmetic This section introduces the basics of number theory number theory is the part of mathematics involving integers and their properties.
4 Number Theory and Cryptography 4.1 Divisibility and Modular Arithmetic This section introduces the basics of number theory number theory is the part of mathematics involving integers and their properties.
Mathematical Foundations of Cryptography
 Mathematical Foundations of Cryptography Cryptography is based on mathematics In this chapter we study finite fields, the basis of the Advanced Encryption Standard (AES) and elliptical curve cryptography
Mathematical Foundations of Cryptography Cryptography is based on mathematics In this chapter we study finite fields, the basis of the Advanced Encryption Standard (AES) and elliptical curve cryptography
A Simple Left-to-Right Algorithm for Minimal Weight Signed Radix-r Representations
 IEEE TRANSACTIONS ON INFORMATION THEORY, VOL. XX, NO. X, MONTH 2007 1 A Simple Left-to-Right Algorithm for Minimal Weight Signed Radix-r Representations James A. Muir Abstract We present a simple algorithm
IEEE TRANSACTIONS ON INFORMATION THEORY, VOL. XX, NO. X, MONTH 2007 1 A Simple Left-to-Right Algorithm for Minimal Weight Signed Radix-r Representations James A. Muir Abstract We present a simple algorithm
3 The fundamentals: Algorithms, the integers, and matrices
 3 The fundamentals: Algorithms, the integers, and matrices 3.4 The integers and division This section introduces the basics of number theory number theory is the part of mathematics involving integers
3 The fundamentals: Algorithms, the integers, and matrices 3.4 The integers and division This section introduces the basics of number theory number theory is the part of mathematics involving integers
Digital Design for Multiplication
 Digital Design for Multiplication Norman Matloff October 15, 2003 c 2003, N.S. Matloff 1 Overview A cottage industry exists in developing fast digital logic to perform arithmetic computations. Fast addition,
Digital Design for Multiplication Norman Matloff October 15, 2003 c 2003, N.S. Matloff 1 Overview A cottage industry exists in developing fast digital logic to perform arithmetic computations. Fast addition,
14:332:231 DIGITAL LOGIC DESIGN. Why Binary Number System?
 :33:3 DIGITAL LOGIC DESIGN Ivan Marsic, Rutgers University Electrical & Computer Engineering Fall 3 Lecture #: Binary Number System Complement Number Representation X Y Why Binary Number System? Because
:33:3 DIGITAL LOGIC DESIGN Ivan Marsic, Rutgers University Electrical & Computer Engineering Fall 3 Lecture #: Binary Number System Complement Number Representation X Y Why Binary Number System? Because
2x 1 7. A linear congruence in modular arithmetic is an equation of the form. Why is the solution a set of integers rather than a unique integer?
 Chapter 3: Theory of Modular Arithmetic 25 SECTION C Solving Linear Congruences By the end of this section you will be able to solve congruence equations determine the number of solutions find the multiplicative
Chapter 3: Theory of Modular Arithmetic 25 SECTION C Solving Linear Congruences By the end of this section you will be able to solve congruence equations determine the number of solutions find the multiplicative
Area-Time Optimal Adder with Relative Placement Generator
 Area-Time Optimal Adder with Relative Placement Generator Abstract: This paper presents the design of a generator, for the production of area-time-optimal adders. A unique feature of this generator is
Area-Time Optimal Adder with Relative Placement Generator Abstract: This paper presents the design of a generator, for the production of area-time-optimal adders. A unique feature of this generator is
Subquadratic space complexity multiplier for a class of binary fields using Toeplitz matrix approach
 Subquadratic space complexity multiplier for a class of binary fields using Toeplitz matrix approach M A Hasan 1 and C Negre 2 1 ECE Department and CACR, University of Waterloo, Ontario, Canada 2 Team
Subquadratic space complexity multiplier for a class of binary fields using Toeplitz matrix approach M A Hasan 1 and C Negre 2 1 ECE Department and CACR, University of Waterloo, Ontario, Canada 2 Team
Logic. Combinational. inputs. outputs. the result. system can
 Digital Electronics Combinational Logic Functions Digital logic circuits can be classified as either combinational or sequential circuits. A combinational circuit is one where the output at any time depends
Digital Electronics Combinational Logic Functions Digital logic circuits can be classified as either combinational or sequential circuits. A combinational circuit is one where the output at any time depends
Chapter 9 Mathematics of Cryptography Part III: Primes and Related Congruence Equations
 Chapter 9 Mathematics of Cryptography Part III: Primes and Related Congruence Equations Copyright The McGraw-Hill Companies, Inc. Permission required for reproduction or display. 9.1 Chapter 9 Objectives
Chapter 9 Mathematics of Cryptography Part III: Primes and Related Congruence Equations Copyright The McGraw-Hill Companies, Inc. Permission required for reproduction or display. 9.1 Chapter 9 Objectives
9. Datapath Design. Jacob Abraham. Department of Electrical and Computer Engineering The University of Texas at Austin VLSI Design Fall 2017
 9. Datapath Design Jacob Abraham Department of Electrical and Computer Engineering The University of Texas at Austin VLSI Design Fall 2017 October 2, 2017 ECE Department, University of Texas at Austin
9. Datapath Design Jacob Abraham Department of Electrical and Computer Engineering The University of Texas at Austin VLSI Design Fall 2017 October 2, 2017 ECE Department, University of Texas at Austin
This is a recursive algorithm. The procedure is guaranteed to terminate, since the second argument decreases each time.
 8 Modular Arithmetic We introduce an operator mod. Let d be a positive integer. For c a nonnegative integer, the value c mod d is the remainder when c is divided by d. For example, c mod d = 0 if and only
8 Modular Arithmetic We introduce an operator mod. Let d be a positive integer. For c a nonnegative integer, the value c mod d is the remainder when c is divided by d. For example, c mod d = 0 if and only
 Implementation Options for Finite Field Arithmetic for Elliptic Curve Cryptosystems Christof Paar Electrical & Computer Engineering Dept. and Computer Science Dept. Worcester Polytechnic Institute Worcester,
Implementation Options for Finite Field Arithmetic for Elliptic Curve Cryptosystems Christof Paar Electrical & Computer Engineering Dept. and Computer Science Dept. Worcester Polytechnic Institute Worcester,
