|
|
|
- Leon Ball
- 5 years ago
- Views:
Transcription
1 This article was published in an Elsevier journal. The attached copy is furnished to the author for non-commercial research and education use, including for instruction at the author s institution, sharing with colleagues and providing to institution administration. Other uses, including reproduction and distribution, or selling or licensing copies, or posting to personal, institutional or third party websites are prohibited. In most cases authors are permitted to post their version of the article (e.g. in Word or Tex form) to their personal website or institutional repository. Authors requiring further information regarding Elsevier s archiving and manuscript policies are encouraged to visit:
2 Theoretical Computer Science 382 (2007) Applications of regularized least squares to pattern classification Nicolò Cesa-Bianchi DSI, Università degli Studi di Milano, via Comelico 39, Milano, Italy Abstract We survey a number of recent results concerning the behaviour of algorithms for learning classifiers based on the solution of a regularized least-squares problem. c 2007 Elsevier B.V. All rights reserved. Keywords: On-line learning; Selective sampling; Ridge regression; Perceptron 1. Introduction In pattern classification some unknown source is supposed to generate a sequence x 1, x 2,... of instances (data elements) x t X. Each instance x t is associated with a class label y t Y (where Y is a finite set) indicating a certain semantic property of the instance. For example, in a handwritten digit recognition task, x t is the digitalized image of a digit and its label y t {0, 1,..., 9} is the corresponding numeral. A learning algorithm for pattern classification operates by observing a sequence of training examples, that is pairs (x t, y t ) where x t is emitted by the source and y t is the associated label (usually obtained via human supervision). The goal of the learner is to build a classifier f : X Y that predicts as accurately as possible the label of any further instance generated by the source. The performance of a learning algorithm is measured in terms of its ability to trade-off the accuracy of the generated classifier with the amount of training data used. In the case X = R d, which we study here, an important parametric family of classification functions are the linear classifiers f (x) = SGN(w x), where w R d is the parameter vector and SGN( ) { 1, +1} is the signum function. Although these classifiers can be only applied to binary classification problems, where the label set is Y = { 1, +1}, there are several effective techniques to reduce a nonbinary classification task to a set of binary classification problems (see, e.g., [1]). 1 Hence in this survey we will restrict our attention to the simple binary classification task. Another issue that we discuss is the fact that linear classifiers are usually too simple to perform accurate predictions on real-world data. To fix this problem we may use kernel functions. Kernels define embeddings of the instance space R d in complex high-dimensional feature spaces in such a way that functions that are nonlinear in terms of the A preliminary version appeared in the Proceedings of the 15th International Conference on Algorithmic Learning Theory. LNAI 3244, Springer, address: cesa-bianchi@dsi.unimi.it. 1 Other more sophisticated approaches use specific loss measures for multiclass problems [2 4]. The application of these specific losses to the algorithms considered here is still an open problem /$ - see front matter c 2007 Elsevier B.V. All rights reserved. doi: /j.tcs
3 222 N. Cesa-Bianchi / Theoretical Computer Science 382 (2007) instances x R d become linear when expressed as functions of the embedded instances. If the predictions of a linear learning algorithm do not change when training instances are rotated in R d (a property that holds for all the algorithms studied here), then linear classifiers can be learned in feature space with a reasonable computational overhead. See the monographs [5,6] for a thorough analysis of kernel-based learning. In this survey we focus on a specific family of algorithms for learning linear classifiers based on the solution of a regularized least squares (RLS) problem. We advocate the use of these algorithms in learning for several reasons. Incremental learning. Like the Perceptron, RLS algorithms can be run on large amounts of data since they are trained incrementally. Empirical performance. RLS algorithms are generally as accurate as the best incremental linear learners, and often comparable to the best batch classifiers. Learning with kernels. The computations performed by RLS algorithms can be expressed using just inner products, thus allowing efficient implementation of kernel-based learning. Versatility. Applications of RLS have been derived for tasks such as data filtering [7], active learning [8], and hierarchical classification [9]. Performance guarantees. RLS algorithms are analytically very tractable. For the basic binary classification task we can prove theoretical performance bounds in both the adversarial and statistical data models; more specialized bounds have been proven for filtering, active learning, and hierarchical classification. The paper is organized as follows. In Section 2 we introduce the framework of regularized least squares and describe some of the basic algorithms. In Section 3 we state and discuss performance bounds for three types of data sources. In Section 4 we study the properties of RLS algorithms in an active learning scenario, where the goal is to attain a certain learning performance using as few training labels as possible. Section 5 is devoted to the conclusions. 2. Regularized least squares for classification Regularized least squares methods have been introduced to solve linear regression problems where the labels y t are real numbers. The most basic algorithm of this family is the ridge regression (RR) procedure of Hoerl and Kennard [13]. Given a training set (x 1, y 1 ),..., (x n, y n ), where (x t, y t ) R d R, the RR algorithm outputs a linear function f (x) = w x where w is the solution of min v R d ( ) (v x t y t ) 2 + a v 2 and a > 0 is the regularization parameter. A closed form expression for w is (ai + S S ) 1 S y, where I is the n n identity matrix, S is the matrix whose columns are the instances x 1,..., x n and y = (y 1,..., y n ) is the vector of instance labels. The presence of the regularization term a v 2 guarantees unicity of the solution in the case x 1,..., x n do not span R d. We may apply RR directly to a binary classification problem. In this case, since labels y t belong to { 1, +1}, problem (1) can be equivalently rewritten as min v R d ( ) (1 y t v x t ) 2 + a v 2. The minimization problem (2) is quite similar to the 2-norm support vector machine (see, e.g, [14]), whose classifier is based on the solution of ( ) ( [1 yt v ) 2 x t ] + + a v 2. (3) min v R d Here we use [x] + to denote max{0, x}. An important difference between the two expressions is that the solution of (2) always depends on all training examples (x 1,..., x n ), whereas the solution of (3) is sparse, as it only depends on a (often small) subset of the training instances (the support vectors). (1) (2)
4 N. Cesa-Bianchi / Theoretical Computer Science 382 (2007) Sparsity is important in controlling the time required to compute predictions when using kernel functions (see the discussion at the end of this section). Moreover, sparsity can be an indicator of good predictive power. For instance, it can be directly used to control the generalization error in statistical learning [15]. In the binary classification case, sparsity can be obtained in the RR solution through a simple technique which we now describe. The RR algorithm generating sparse solutions is called second-order Perceptron algorithm [16]. This algorithm works incrementally, starting with the constant linear classifier w 0 = (0,..., 0). At each time step t = 1, 2,... a new instance x t is obtained from the source and the algorithm outputs the prediction ŷ t = SGN(w t 1 x t) for the label of x t, where w t 1 is the parameter of the current linear classifier. Then, the label y t is obtained. If ŷ t y t, the example (x t, y t ) is stored by updating w t 1 to w t = (ai + S t St ) 1 S t y t. Here S t is defined as the matrix whose columns are the stored instances and y t is the vector of labels of the stored instances. If ŷ t = y t then w t = w t 1 and no update occurs. Expressing w t in a form similar to (2) we obtain ( ) w t = argmin v R d s M t (1 y s v x s ) 2 + a v 2 where M t = { 1 s t : SGN(w s 1 x s) y s } is the set of indices of the examples (xs, y s ) stored in the first t steps. Note that by keeping the representation of w t 1 split in the inverse matrix (ai + S t 1 S t 1 ) 1 and the vector S t 1 y t 1, we can compute the weight w t in constant time Θ(d 2 ) using using standard linear algebra techniques. If kernel functions are used, we can compute w t from w t 1 in time order of (dm) 2, where m is the number of examples stored so far. The same time is also needed to compute each prediction ŷ t = SGN(w t 1 x t). By contrast, the kernel (first-order) Perceptron takes constant time to update the weight vector and time of the order of dm to compute a prediction. See [16] for details on these computations. 3. Analysis We now state bounds on the predictive error of regularized least squares for classification under different assumptions on the source generating the data. In particular, we consider three families of sources. Arbitrary sources: no assumption is made on the mechanism generating the instances x t and their associated labels y t. Performance bounds proven for this source therefore hold on any individual sequence of examples. Independent and identically distributed sources: here the examples (x t, y t ) are drawn independently from a fixed and unknown distribution on R d { 1, +1}. Probabilistic linear sources: instances are generated arbitrarily (as in the first source) while the following linear noise model is assumed for the labels. There exists a fixed and unknown vector v R d with v = 1 such that P(y t = 1 x t ) = (1 + v x t )/2 for all x t. To guarantee that v x t [ 1, 1] we also assume x t = 1 for all t (in other words, each instance is normalized before being fed into the learning algorithm). The analysis of learning algorithms on arbitrary data sequences has been introduced in learning theory by Angluin [17] and Littlestone [18]. However, the Perceptron convergence theorem [19,20] can be viewed as an early example of this approach. The i.i.d. sources are the standard data model used in statistical learning theory [21,22]. Here we illustrate a simple technique showing how results for arbitrary sources can be specialized to obtain good bounds in the case of i.i.d. sources. Probabilistic linear sources have been considered in [9] to analyze the properties of regularized least squares as a statistical estimator in binary classifications tasks. To measure the performance of our learning algorithms we count prediction mistakes. We say that an example (x t, y t ) R d { 1, +1} is mistaken by a linear classifier w t 1 when ŷ t y t, where ŷ t = SGN(w t 1 x t). The mistake indicator function I {ŷt y t } is also called zero one loss. Our results are all derived from analysis of on-line learning processes. They cannot be directly used to relate the training error of a classifier to its generalization error, as in the traditional statistical learning approach. On the other hand, our results for i.i.d. sources provide bounds on the generalization error of the linear classifiers generated by the run of the on-line algorithm. Rather than being expressed in terms of the training error, these results are expressed in terms of the number of mistakes made by the on-line algorithm on the training set.
5 224 N. Cesa-Bianchi / Theoretical Computer Science 382 (2007) Arbitrary sources We start by studying the behaviour of the second-order Perceptron run over an arbitrary sequence of examples. In particular, we bound the number of time steps t in which the next example (x t, y t ) is mistaken by the current classifier w t 1. The bound is expressed in terms of the structure of the data sequence and in terms of the performance of an arbitrary fixed linear classifier u R d (which we call the reference classifier) on the same sequence. We measure the performance of a reference classifier u using the hinge loss [1 y u x] +, which is the loss function occurring in the expression (3) related to the support vector machine algorithm. Note that [1 yp] + I {ŷ y} for ŷ = SGN(p). Hence the hinge loss upper bounds the zero one loss. The definition and analysis of the second-order Perceptron are based on three different losses (the squared loss, the zero one loss and the hinge loss). The square loss, which is the loss defining the predictions of RLS algorithms, allows us to express each linear classifier w t in a simple closed form. On the other hand the zero one loss, which counts the prediction mistakes, is a more natural performance measure in binary classification tasks. However, devising a simple and efficient on-line linear classifier that does well against the best fixed linear classifier is a hard problem when the zero one loss is used to score both algorithms. Indeed, it is well known that the problem of approximating the mistakes of the best linear classifier, even when the sequence of examples is known in advance, cannot be solved in polynomial time unless P = NP (see [10,11]). This justifies the use of the hinge loss in the competitive analysis of linear learning algorithms. We also remark that other approaches succeeded in comparing Perceptron-like algorithms and reference classifiers using the squared hinge loss as the common performance measure [12]. However, these alternative analyses typically cause the appearance in the bound of a factor larger than 1 multiplying the loss of the reference classifier. For any fixed u and for any fixed sequence (x 1, y 1 ), (x 2, y 2 )... R d { 1, +1} define the cumulative hinge loss L n (u) = ] [1 y t u x t +. We are now ready to state the main result for the second-order Perceptron. For a proof of this bound we refer to [16]. Theorem 1. If the second-order Perceptron is run with regularization parameter a > 0 on a sequence (x 1, y 1 ), (x 2, y 2 )... R d { 1, +1}, then, for all n 1 and for all u R d, I {ŷt y t } L n (u) + ( a u 2 + u A n u ) d ln(1 + λ i /a) where λ 1,..., λ d are the eigenvalues of the matrix A n = x t x t I {ŷt y t }. For a, the bound of Theorem 1 reduces to the bound for the classical Perceptron algorithm (see, e.g., [23]). To see this, note that lim a ( a u 2 + u A n u ) d ( ln(1 + λ i /a) = lim a u 2 + u A n u ) d λ i /a a = u 2 tr ( A n A ) n where tr( ) is the trace (sum of the eigenvalues) of a matrix. Let m = n I {ŷt y t } be the total number of mistakes made by the second-order Perceptron. We now use a basic algebraic fact stating that A n has the same nonzero eigenvalues as the m m matrix G with entries G i, j = xi x j (G is called the Gram matrix of the instances x 1,..., x m ). This implies that tr ( A n A ) ( ) n = tr A n A n = x 1 x x m x m m max x t 2 (4) t
6 N. Cesa-Bianchi / Theoretical Computer Science 382 (2007) where max t ranges over the mistaken examples (x t, y t ). Hence, for a, the bound of Theorem 1 can be written as m L n (u) + u ( max x t ) m. t Solving for m gives the Perceptron mistake bound. The bound of Theorem 1 is not in closed form as the matrix A n is defined in terms of the mistakes I {ŷt y t }. In order to help the reader compare this result with other mistake bounds, we now derive a (somewhat weaker) closed form version of the second-order mistake bound. To keep things simple, we assume that the sequence (x 1, y 1 ), (x 2, y 2 )... R d { 1, +1} is linearly separable with margin γ > 0. That is, there exist u R d such that u = 1 and y t u x t γ for all t 1. Moreover, we assume that instances x t are normalized, x t = 1 for all t 1. Under these assumptions, and setting the parameter a of the algorithm to 1, the bound of Theorem 1 becomes m 1 ( 1 + λ(u) ) d ln(1 + λ i ) γ where m is the number of mistakes and we write λ(u) = u A n u = ( u ) 2I{ŷt x t y t }. t Since u is a unit-norm linear separator with margin γ, and since x t = 1, we know that γ 2 m λ(u) m. Thus we may write λ(u) = λ 0 m for some γ 2 λ 0 1. Moreover, from (4) we know that λ λ d = m. The quantity (1 + λ 1 ) (1 + λ d ), under the constraint λ λ d = m, is maximized when λ i = m/d for all i. Thus the bound of Theorem 1 can be weakened to m 1 γ (1 + λ0 m ) d ln(1 + m/d). (5) To get a reasonable bound, we now need to assume that λ 0 cγ for some c > 0. This amounts to saying that the second-order Perceptron tends to make mistakes on instances x t such that u x t γ. Although this condition is not particularly nice, as it is defined in terms of the behaviour of the algorithm on the sequence, it is certainly plausible that many mistakes are made on instances on which the separating hyperplane u achieves a small margin. If λ 0 cγ holds, then one can easily show that ( d m = Θ γ ln 1 ) γ satisfies (5). This bound is related to the essentially optimal mistake bound d ln(1/γ ) achieved by the Bayes Point Machine [24]. However, whereas for the second-order Perceptron updating the weight vector takes only time Θ(d 2 ) (see Section 2), the Bayes Point Machine must solve a computationally intractable (#P-hard) problem at each step. In [16] we show that whenever the reference classifier u is correlated with some eigenvector of the matrix A n associated with an eigenvalue significantly smaller than the largest eigenvalue (see Fig. 1), then the bound of Theorem 1 reaches its minimum at a <. This means that, in such situations, the bound for the second-order Perceptron with parameter a properly tuned is better than the corresponding bound for the classical Perceptron algorithm. The cases where the second-order bound loses its advantage are those when the matrix A n has a nearly uniform spectrum (the eigenvalues are close to each other) and d m (which typically happens when the algorithm is run with kernels). In practice, however, if the instances x t are normalized so that x t = 1, then the second-order Perceptron, run with a = 1 and without using kernels, performs typically better than the classical Perceptron even on high-dimensional real-world datasets such as Reuters Corpus Volume Independent and identically distributed sources We now move on to analyzing the performance of the second-order Perceptron in the classical statistical learning model, where data sequences (x t, y t ) R d { 1, +1} for t = 1, 2,... are generated via independent draws from a fixed and unknown distribution. To stress that instances and labels are now random variables we write X t and Y t.
7 226 N. Cesa-Bianchi / Theoretical Computer Science 382 (2007) Fig. 1. A linearly separable set of instances x t on which the second-order Perceptron has an advantage over the classical Perceptron algorithm. The data correlation matrix has two eigenvectors aligned with the axis shown in the picture. The vector perpendicular to the separating hyperplane turns out to be well aligned with the eigenvector associated with the smallest eigenvalue. In this framework, the standard measure of performance for a classifier f : R d { 1, +1} is the risk R( f ) = P ( f (X) Y ). This is the probability that f misclassifies the next example (X t, Y t ) generated by the source. Introduce the notation R(w) = P ( SGN(w X) Y ) to indicate the risk of the linear classifier using weight w. Consider the second-order Perceptron run on a data sequence of length n and let w 0, w 1,..., w n 1 be the weights that have been used by the algorithm to compute the sequence ŷ 1,..., ŷ n of predictions. Define M n = I {ŷt Y t } where ŷ t = SGN(w t 1 X t). We now show that the average risk 1 n R(w t 1 ) is close to M n /n with high probability over the random draw of (X 1, Y 1 ),..., (X n, Y n ). In other words, the average risk of the linear classifiers generated by the second-order Perceptron during its run on a data sequence is close to the fraction of mistakes made. To see this note that, since each example (X t, Y t ) is drawn i.i.d., E [ I {ŷt Y t } (X 1, Y 1 ),..., (X t 1, Y t 1 ) ] = R(w t 1 ). Hence the stochastic process R(w t 1 ) I {ŷt Y t } is a bounded martingale difference sequence. We may now use standard large deviation results (such as the Hoeffding Azuma inequality [25,26]) to show that, for any fixed δ (0, 1) 1 R(w t 1 ) M n 2 n n + n ln 1 δ holds with probability at least 1 δ. We are now left with the problem of exhibiting a specific linear classifier whose risk is close to the average. In [27] a technique is described to select a weight w among the ensemble w 0, w 1,..., w n 1 such that the linear classifier using w achieves a risk just slightly higher than the average risk of the ensemble. In particular, it is shown that R(w ) M n n n ln 2(n + 1) δ holds with probability at least 1 δ. (6)
8 N. Cesa-Bianchi / Theoretical Computer Science 382 (2007) We have thus probabilistically bounded the risk of a linear classifier generated by the second-order Perceptron algorithm in terms of the number M n of mistakes made by the algorithm run on a random training sequence. Note that (6) has been derived without exploiting any specific property of the learning algorithm. Hence the bound actually holds for any incremental learning algorithm making M n mistakes on the data sequence. When considering a specific incremental learning algorithm, we can specialize (6) by replacing M n with a bound proven in the arbitrary source model. In particular, for the second-order Perceptron we may bound M n using Theorem 1 and thus obtain a data-dependent bound on the risk which depends on the spectrum of the observed data sequence. Note that, in the case of i.i.d. sources, the hinge loss term L n (u) in Theorem 1 appears as an expected value E L n (u)/n. Since the source is i.i.d., we have that 1 n E L n(u) = E [ 1 Y u X ] +. Hence, this analysis enables us to compare the risk of w with the expected hinge loss of an arbitrary linear classifier Probabilistic linear sources In this section we temporarily abandon the analysis of the second-order Perceptron and go back to the RR procedure (1). Recall that, unlike the second-order Perceptron, the classifiers generated by RR depend on all previously observed examples. In regression tasks, if the real labels are expressed by a linear function of the instances plus a Gaussian noise term, then RR provides a (biased) estimator of this hidden linear function (see, e.g., [28]). We now show that, in an appropriate classification noise model, RR is a biased estimator of a hidden linear classifier. Given an arbitrary sequence x 1, x 2,... of instances x t R d with x t = 1, we assume that the labels Y 1, Y 2,... are random variables with conditional distribution P(Y t = 1 x t ) = (1 + v x t )/2 for some fixed and hidden v R d with v = 1. Note that the linear classifier SGN(v x t ) is Bayes optimal for this data model. We consider a slight variant of the RR algorithm (2). In this variant, which has been introduced in [29] for solving regression problems, the weight used to predict the label of the next instance x t is defined as (ai + S t S t ) 1 S t 1 y t 1 (7) where, for each t = 1, 2,..., S t is the matrix [x 1,..., x t ]. Note that the only difference with the weight (ai + S t 1 S t 1 ) 1 S t 1 y t 1 of the RR algorithm is that we have added the current instance x t in the inverse matrix. This amounts to a slightly stronger regularization, and has the side effect of making the final classifier nonlinear. For this reason, we denote with ŵ t (with index t rather than t 1) the weight (7) used at time t to compute the prediction ŷ t = SGN(ŵ t x t ) for the random label Y t. In the case of probabilistic linear sources we evaluate the performance of the modified RR algorithm by directly comparing the number of mistakes made by the algorithm with the number of mistakes made by the Bayes optimal classifier based on the hidden vector v. That is, we look at the expected value of the difference I {ŷt Y t } I {SGN(v x t ) Y t }. In [9] the following result is proved. Theorem 2. Suppose that the modified RR algorithm (7) is run with regularization parameter a = 1 on a sequence (x 1, Y 1 ), (x 2, Y 2 )... R d { 1, +1} such that x t = 1 and P(Y t = 1 x t ) = (1 + v x t )/2 for all t and for some v R d with v = 1. Then, for all n 1, P(ŷ t Y t ) P ( SGN(v x t ) Y t ) 16(1 + 1/e) γ 2 d log(1 + λ i ) where γ = min,...,n v x t and λ 1,..., λ d are the eigenvalues of the matrix Λ n = x 1 x x n x n.
9 228 N. Cesa-Bianchi / Theoretical Computer Science 382 (2007) Note that the bound of Theorem 2 implies that the expected number of mistakes made by the modified RR algorithm in excess with respect to those made by the Bayes optimal classifier is bounded by a logarithmic function of n. To prove this logarithmic bound, we use (4) to show that λ λ d = x 1 x x n x n n. Similarly to the reasoning used to derive (5), we observe that (1 + λ 1 ) (1 + λ d ) is maximized when λ i = n/d for all i = 1,..., d. Thus we conclude d ( ln(1 + λ i ) d ln 1 + n ). d Hence, in this probabilistic linear model, regularized least squares ensures fast convergence to the mistake rate of the Bayes optimal classifier. 4. Selective sampling Theorem 2 states that modified ridge regression has a good performance bound when data are generated by probabilistic linear sources. However, to achieve this bound all examples have to be stored. This becomes a problem if we use kernels, as the space required to represent a classifier built on t observed instances is Θ(t 2 ). To control the space requirements without a significant reduction in predictive performance, we now introduce a selective sampling version of this algorithm. At each time step t, selective sampling uses weights having the same form as the weights (7)) used by the modified RR algorithm. However, selective sampling stores the current example (x t, y t ) only if ŵ t x t c (ln t)/n t, where N t is the number of examples stored up to time t and c is some constant (the choice c = 5 works well in practice when instances are normalized). Note the following important fact: to decide whether to store an example (x t, Y t ) selective sampling does not need to observe the label Y t. Thus, without loss of generality, we may assume that the labels of non-stored examples remain forever unknown (for this reason, selective sampling algorithms are also called label efficient). We performed some experiments using the 50 most frequent categories in the first 40,000 news stories (in chronological order) of the Reuters Corpus Volume 1 [30] dataset. During the preprocessing phase we first encoded the documents using a standard TF-IDF bag-of-words representation, and then we normalized all the encoded vectors with respect to the Euclidean norm. We compared the average F-measure of Perceptron, second-order Perceptron and selective sampling on 50 binary classification tasks (one task for each one of the 50 categories). In all experiments the parameter a, used by the RLS algorithms, was set to 1 and we did not use kernels. These experiments (see Fig. 2) show that selective sampling works very effectively, achieving the same performance as the second-order Perceptron while storing a rapidly decreasing fraction of the observed instances (we did not compare the performance of selective sampling with that of the modified RR algorithm as the latter cannot be run in a reasonable amount of time on the moderately large datasets used in our experiments). The use of a threshold τ t = (ln t)/n t in the selective sampling procedure is motivated by the following observation: when enough examples have been stored then, with high probability, ŵ t and the Bayes optimal v classify in the same way any new instance that has a large enough margin. That is, any instance x t such that ŵ t x t > τ t. The form of the dependence of τ t on t and N t is derived from simple large deviation analysis. Although the theoretical investigation of the selective sampling procedure is still in progress, some preliminary results have been published in [8]. We close this section by describing a selective sampling technique guaranteeing good predictive performance even when data are generated by arbitrary sources. More precisely, we consider the second-order Perceptron using the following randomized selective sampling rule: with probability C/(C + ŵ t x t ), where C > 0 is a parameter, get the true label y t. Then store (x t, y t ) if ŷ t y t. Thus, an example whose label is correctly predicted is never stored, and an example (x t, y t ) on which a mistake is made is stored with a probability inversely proportional to the margin ŵ t x t. In [31] the following is proven. Theorem 3. If the selective sampling second-order Perceptron is run on a sequence (x 1, y 1 ), (x 2, y 2 )... R d { 1, +1}, then, for all n 1 and for all u R d,
10 N. Cesa-Bianchi / Theoretical Computer Science 382 (2007) Fig. 2. Behaviour of the selective sampling variant of the modified RR algorithm on the first 40,000 documents in the Reuters Corpus Volume 1 dataset. The increasing curves are the F-measures for the second-order Perceptron and the Perceptron (both observing all labels), and for selective sampling. The decreasing curve is the rate of labels used by the selective sampling procedure. All quantities are averaged over 50 binary classification tasks. Note that the label rate of selective sampling decreases very fast and the performance eventually reaches the performance of the second-order Perceptron, which is allowed to observe all labels. E [ I {ŷt y t } ] L n (u) + C 2 ( a u 2 + ( u x t ) 2E Kt ) + 1 2C d ( E ln 1 + Λ ) i a where K t is the indicator of the event (x t, y t ) is stored, and Λ 1,..., Λ d are the eigenvalues of the random matrix (x 1 x 1 )K (x n x n )K n. It is important to remark that Theorem 3 provides a bound on the expected number of mistakes made on the whole sequence of examples, irrespective of which of these examples have been stored. Note also that, similarly to Theorem 1, the bound proven in Theorem 3 is not in closed form as the random variables K t depend on the algorithm s mistakes. This result also reveals an interesting phenomenon. A proper choice of the parameter C of the randomized rule yields, in expectation, the same bound as that stated in Theorem 1 for the second-order Perceptron without the selective sampling mechanism. Hence, in some sense, this technique uses the margin information to select those labels that can be ignored without increasing (in expectation) the overall number of mistakes. One may suspect that this gain is not real, as the tuning of C preserving the original mistake bound might force the algorithm to sample all but an insignificant number of labels. Fig. 3 brings experimental evidence that goes against this claim. By running the algorithms on real-world textual data, we show that no significant decrease in the predictive performance is suffered even when the parameter C is set to values that cause a significant fraction of the labels to be not observed. We refer the interested reader to [31] for more extensive experiments. 5. Conclusions In this survey we have reported on an ongoing research project aimed at studying the theoretical properties of regularized least squares algorithms for classification tasks. Due to their analytic tractability, versatility and good empirical behaviour, RLS methods provide a nice case in support to the systematic use of principled methods for solving learning problems. The results mentioned here leave many problems open. We lack a tight closed form expression for the second-order Perceptron bound. Our risk bound (6) for arbitrary incremental algorithms is not tight when M n is very small. Finally, our analysis of selective sampling for probabilistic linear sources is only done for a simpler and less effective variant of the algorithm described here.
11 230 N. Cesa-Bianchi / Theoretical Computer Science 382 (2007) Fig. 3. Behaviour of the label efficient second-order Perceptron on the same news story categorization task of Fig. 2 (in this experiment we only used the first 20,000 documents). For each value of the parameter C two curves are plotted as a function of the number of instances observed. As in Fig. 2, the increasing curve is the average F-measure and the decreasing curve is the rate of sampled labels. Note that, for the range of parameter values displayed, the performance does not get significantly worse as the parameter value decreases causing the label rate to drop faster. In all cases, the performance remains close to that of the algorithm that queries all labels (corresponding to the choice C ). Acknowledgement This work was supported in part by the PASCAL Network of Excellence under EC grant no This publication only reflects the authors views. References [1] R. Rifkin, A. Klautau, In defense of one-vs-all classification, Journal of Machine Learning Research 5 (2004) [2] J. Weston, C. Watkins, Support vector machines for multi-class pattern recognition, in: Proceedings of the Seventh European Symposium on Artificial Neural Networks, April [3] A. Elisseeff, J. Weston, A kernel method for multi-labeled classification, in: Advances in Neural Information Processing Systems 14, [4] K. Crammer, Y. Singer, Ultraconservative online algorithms for multiclass problems, Journal of Machine Learning Research 3 (2003) [5] N. Cristianini, J. Shawe-Taylor, Kernel Methods for Pattern Analysis, Cambridge University Press, [6] B. Schölkopf, A. Smola, Learning with Kernels, MIT Press, [7] N. Cesa-Bianchi, A. Conconi, C. Gentile, Margin-based algorithms for information filtering, in: Advances in Neural Information Processing Systems, vol. 15, MIT Press, 2003, pp [8] N. Cesa-Bianchi, A. Conconi, C. Gentile, Learning probabilistic linear-threshold classifiers via selective sampling, in: Proceedings of the 16th Annual Conference on Learning Theory, in: LNAI, vol. 2777, Springer, 2003, pp [9] N. Cesa-Bianchi, C. Gentile, L. Zaniboni, Incremental algorithms for hierarchical classification, Journal of Machine Learning Research 7 (2006) [10] E. Amaldi, V. Kann, The complexity and approximability of finding maximum feasible subsystems of linear relations, Theoretical Computer Science 147 (1995) [11] S. Ben-David, N. Eiron, P.M. Long, On the difficulty of approximately maximizing agreements, Journal of Computer and System Sciences 66 (3) (2003) [12] K. Crammer, O. Dekel, J. Keshet, S. Shalev-Shwartz, Y. Singer, Online passive-aggressive algorithms, Journal of Machine Learning Research 7 (2006) [13] A. Hoerl, R. Kennard, Ridge regression: Biased estimation for nonorthogonal problems, Technometrics 12 (1970) [14] N. Cristianini, J. Shawe-Taylor, An Introduction to Support Vector Machines, Cambridge University Press, [15] T. Graepel, R. Herbrich, J. Shawe-Taylor, Generalisation error bounds for sparse linear classifiers, in: Proceedings of the 13th Annual Conference on Computational Learning Theory, ACM Press, 2000, pp [16] N. Cesa-Bianchi, A. Conconi, C. Gentile, A second-order Perceptron algorithm, SIAM Journal on Computing 43 (3) (2005) [17] D. Angluin, Queries and concept learning, Machine Learning 2 (4) (1988) [18] N. Littlestone, Learning quickly when irrelevant attributes abound: a new linear-threshold algorithm, Machine Learning 2 (4) (1988)
12 N. Cesa-Bianchi / Theoretical Computer Science 382 (2007) [19] H. Block, The Perceptron: A model for brain functioning, Review of Modern Physics 34 (1962) [20] A. Novikoff, On convergence proofs of Perceptrons, in: Proceedings of the Symposium on the Mathematical Theory of Automata, vol. XII, 1962, pp [21] L. Devroye, L. Győrfi, G. Lugosi, A Probabilistic Theory of Pattern Recognition, Springer Verlag, [22] V. Vapnik, Statistical Learning Theory, Wiley, [23] C. Gentile, The robustness of the p-norm algorithms, Machine Learning 53 (3) (2003) [24] R. Gilad-Bachrach, A. Navot, N. Tishby, Bayes and Tukey meet at the center point, in: Proceedings of the 17th Annual Conference on Learning Theory, in: LNAI, vol. 3120, Springer, 2004, pp [25] W. Hoeffding, Probability inequalities for sums of bounded random variables, Journal of the American Statistical Association 58 (1963) [26] K. Azuma, Weighted sums of certain dependent random variables, Tohoku Mathematical Journal 68 (1967) [27] N. Cesa-Bianchi, A. Conconi, C. Gentile, On the generalization ability of on-line learning algorithms, IEEE Transactions on Information Theory 50 (9) (2004) [28] T. Hastie, R. Tishbirani, J. Friedman, The Elements of Statistical Learning, Springer, [29] V. Vovk, Competitive on-line statistics, International Statistical Review 69 (2001) [30] about.reuters.com/researchandstandards/corpus/. [31] N. Cesa-Bianchi, C. Gentile, L. Zaniboni, Worst-case analysis of selective sampling for linear classification, Journal of Machine Learning Research 7 (2006)
Better Algorithms for Selective Sampling
 Francesco Orabona Nicolò Cesa-Bianchi DSI, Università degli Studi di Milano, Italy francesco@orabonacom nicolocesa-bianchi@unimiit Abstract We study online algorithms for selective sampling that use regularized
Francesco Orabona Nicolò Cesa-Bianchi DSI, Università degli Studi di Milano, Italy francesco@orabonacom nicolocesa-bianchi@unimiit Abstract We study online algorithms for selective sampling that use regularized
Adaptive Sampling Under Low Noise Conditions 1
 Manuscrit auteur, publié dans "41èmes Journées de Statistique, SFdS, Bordeaux (2009)" Adaptive Sampling Under Low Noise Conditions 1 Nicolò Cesa-Bianchi Dipartimento di Scienze dell Informazione Università
Manuscrit auteur, publié dans "41èmes Journées de Statistique, SFdS, Bordeaux (2009)" Adaptive Sampling Under Low Noise Conditions 1 Nicolò Cesa-Bianchi Dipartimento di Scienze dell Informazione Università
Foundations of Machine Learning On-Line Learning. Mehryar Mohri Courant Institute and Google Research
 Foundations of Machine Learning On-Line Learning Mehryar Mohri Courant Institute and Google Research mohri@cims.nyu.edu Motivation PAC learning: distribution fixed over time (training and test). IID assumption.
Foundations of Machine Learning On-Line Learning Mehryar Mohri Courant Institute and Google Research mohri@cims.nyu.edu Motivation PAC learning: distribution fixed over time (training and test). IID assumption.
Online Passive-Aggressive Algorithms
 Online Passive-Aggressive Algorithms Koby Crammer Ofer Dekel Shai Shalev-Shwartz Yoram Singer School of Computer Science & Engineering The Hebrew University, Jerusalem 91904, Israel {kobics,oferd,shais,singer}@cs.huji.ac.il
Online Passive-Aggressive Algorithms Koby Crammer Ofer Dekel Shai Shalev-Shwartz Yoram Singer School of Computer Science & Engineering The Hebrew University, Jerusalem 91904, Israel {kobics,oferd,shais,singer}@cs.huji.ac.il
Online Passive-Aggressive Algorithms
 Online Passive-Aggressive Algorithms Koby Crammer Ofer Dekel Shai Shalev-Shwartz Yoram Singer School of Computer Science & Engineering The Hebrew University, Jerusalem 91904, Israel {kobics,oferd,shais,singer}@cs.huji.ac.il
Online Passive-Aggressive Algorithms Koby Crammer Ofer Dekel Shai Shalev-Shwartz Yoram Singer School of Computer Science & Engineering The Hebrew University, Jerusalem 91904, Israel {kobics,oferd,shais,singer}@cs.huji.ac.il
On the Generalization Ability of Online Strongly Convex Programming Algorithms
 On the Generalization Ability of Online Strongly Convex Programming Algorithms Sham M. Kakade I Chicago Chicago, IL 60637 sham@tti-c.org Ambuj ewari I Chicago Chicago, IL 60637 tewari@tti-c.org Abstract
On the Generalization Ability of Online Strongly Convex Programming Algorithms Sham M. Kakade I Chicago Chicago, IL 60637 sham@tti-c.org Ambuj ewari I Chicago Chicago, IL 60637 tewari@tti-c.org Abstract
Linear Classification and Selective Sampling Under Low Noise Conditions
 Linear Classification and Selective Sampling Under Low Noise Conditions Giovanni Cavallanti DSI, Università degli Studi di Milano, Italy cavallanti@dsi.unimi.it Nicolò Cesa-Bianchi DSI, Università degli
Linear Classification and Selective Sampling Under Low Noise Conditions Giovanni Cavallanti DSI, Università degli Studi di Milano, Italy cavallanti@dsi.unimi.it Nicolò Cesa-Bianchi DSI, Università degli
A New Perspective on an Old Perceptron Algorithm
 A New Perspective on an Old Perceptron Algorithm Shai Shalev-Shwartz 1,2 and Yoram Singer 1,2 1 School of Computer Sci & Eng, The Hebrew University, Jerusalem 91904, Israel 2 Google Inc, 1600 Amphitheater
A New Perspective on an Old Perceptron Algorithm Shai Shalev-Shwartz 1,2 and Yoram Singer 1,2 1 School of Computer Sci & Eng, The Hebrew University, Jerusalem 91904, Israel 2 Google Inc, 1600 Amphitheater
Margin-Based Algorithms for Information Filtering
 MarginBased Algorithms for Information Filtering Nicolò CesaBianchi DTI University of Milan via Bramante 65 26013 Crema Italy cesabianchi@dti.unimi.it Alex Conconi DTI University of Milan via Bramante
MarginBased Algorithms for Information Filtering Nicolò CesaBianchi DTI University of Milan via Bramante 65 26013 Crema Italy cesabianchi@dti.unimi.it Alex Conconi DTI University of Milan via Bramante
New bounds on the price of bandit feedback for mistake-bounded online multiclass learning
 Journal of Machine Learning Research 1 8, 2017 Algorithmic Learning Theory 2017 New bounds on the price of bandit feedback for mistake-bounded online multiclass learning Philip M. Long Google, 1600 Amphitheatre
Journal of Machine Learning Research 1 8, 2017 Algorithmic Learning Theory 2017 New bounds on the price of bandit feedback for mistake-bounded online multiclass learning Philip M. Long Google, 1600 Amphitheatre
The Power of Selective Memory: Self-Bounded Learning of Prediction Suffix Trees
 The Power of Selective Memory: Self-Bounded Learning of Prediction Suffix Trees Ofer Dekel Shai Shalev-Shwartz Yoram Singer School of Computer Science & Engineering The Hebrew University, Jerusalem 91904,
The Power of Selective Memory: Self-Bounded Learning of Prediction Suffix Trees Ofer Dekel Shai Shalev-Shwartz Yoram Singer School of Computer Science & Engineering The Hebrew University, Jerusalem 91904,
Perceptron Mistake Bounds
 Perceptron Mistake Bounds Mehryar Mohri, and Afshin Rostamizadeh Google Research Courant Institute of Mathematical Sciences Abstract. We present a brief survey of existing mistake bounds and introduce
Perceptron Mistake Bounds Mehryar Mohri, and Afshin Rostamizadeh Google Research Courant Institute of Mathematical Sciences Abstract. We present a brief survey of existing mistake bounds and introduce
Logistic regression and linear classifiers COMS 4771
 Logistic regression and linear classifiers COMS 4771 1. Prediction functions (again) Learning prediction functions IID model for supervised learning: (X 1, Y 1),..., (X n, Y n), (X, Y ) are iid random
Logistic regression and linear classifiers COMS 4771 1. Prediction functions (again) Learning prediction functions IID model for supervised learning: (X 1, Y 1),..., (X n, Y n), (X, Y ) are iid random
Online Passive- Aggressive Algorithms
 Online Passive- Aggressive Algorithms Jean-Baptiste Behuet 28/11/2007 Tutor: Eneldo Loza Mencía Seminar aus Maschinellem Lernen WS07/08 Overview Online algorithms Online Binary Classification Problem Perceptron
Online Passive- Aggressive Algorithms Jean-Baptiste Behuet 28/11/2007 Tutor: Eneldo Loza Mencía Seminar aus Maschinellem Lernen WS07/08 Overview Online algorithms Online Binary Classification Problem Perceptron
The Perceptron Algorithm with Uneven Margins
 The Perceptron Algorithm with Uneven Margins Yaoyong Li Royal Holloway, University of London, Egham, Surrey, TW20 0EX, UK Hugo Zaragoza Microsoft Research, 7 J J Thomson Avenue, CB3 0FB Cambridge, UK Ralf
The Perceptron Algorithm with Uneven Margins Yaoyong Li Royal Holloway, University of London, Egham, Surrey, TW20 0EX, UK Hugo Zaragoza Microsoft Research, 7 J J Thomson Avenue, CB3 0FB Cambridge, UK Ralf
Linear Discrimination Functions
 Laurea Magistrale in Informatica Nicola Fanizzi Dipartimento di Informatica Università degli Studi di Bari November 4, 2009 Outline Linear models Gradient descent Perceptron Minimum square error approach
Laurea Magistrale in Informatica Nicola Fanizzi Dipartimento di Informatica Università degli Studi di Bari November 4, 2009 Outline Linear models Gradient descent Perceptron Minimum square error approach
Worst-Case Analysis of the Perceptron and Exponentiated Update Algorithms
 Worst-Case Analysis of the Perceptron and Exponentiated Update Algorithms Tom Bylander Division of Computer Science The University of Texas at San Antonio San Antonio, Texas 7849 bylander@cs.utsa.edu April
Worst-Case Analysis of the Perceptron and Exponentiated Update Algorithms Tom Bylander Division of Computer Science The University of Texas at San Antonio San Antonio, Texas 7849 bylander@cs.utsa.edu April
Linear & nonlinear classifiers
 Linear & nonlinear classifiers Machine Learning Hamid Beigy Sharif University of Technology Fall 1394 Hamid Beigy (Sharif University of Technology) Linear & nonlinear classifiers Fall 1394 1 / 34 Table
Linear & nonlinear classifiers Machine Learning Hamid Beigy Sharif University of Technology Fall 1394 Hamid Beigy (Sharif University of Technology) Linear & nonlinear classifiers Fall 1394 1 / 34 Table
A simpler unified analysis of Budget Perceptrons
 Ilya Sutskever University of Toronto, 6 King s College Rd., Toronto, Ontario, M5S 3G4, Canada ILYA@CS.UTORONTO.CA Abstract The kernel Perceptron is an appealing online learning algorithm that has a drawback:
Ilya Sutskever University of Toronto, 6 King s College Rd., Toronto, Ontario, M5S 3G4, Canada ILYA@CS.UTORONTO.CA Abstract The kernel Perceptron is an appealing online learning algorithm that has a drawback:
Online Learning, Mistake Bounds, Perceptron Algorithm
 Online Learning, Mistake Bounds, Perceptron Algorithm 1 Online Learning So far the focus of the course has been on batch learning, where algorithms are presented with a sample of training data, from which
Online Learning, Mistake Bounds, Perceptron Algorithm 1 Online Learning So far the focus of the course has been on batch learning, where algorithms are presented with a sample of training data, from which
1 Machine Learning Concepts (16 points)
 CSCI 567 Fall 2018 Midterm Exam DO NOT OPEN EXAM UNTIL INSTRUCTED TO DO SO PLEASE TURN OFF ALL CELL PHONES Problem 1 2 3 4 5 6 Total Max 16 10 16 42 24 12 120 Points Please read the following instructions
CSCI 567 Fall 2018 Midterm Exam DO NOT OPEN EXAM UNTIL INSTRUCTED TO DO SO PLEASE TURN OFF ALL CELL PHONES Problem 1 2 3 4 5 6 Total Max 16 10 16 42 24 12 120 Points Please read the following instructions
CS6375: Machine Learning Gautam Kunapuli. Support Vector Machines
 Gautam Kunapuli Example: Text Categorization Example: Develop a model to classify news stories into various categories based on their content. sports politics Use the bag-of-words representation for this
Gautam Kunapuli Example: Text Categorization Example: Develop a model to classify news stories into various categories based on their content. sports politics Use the bag-of-words representation for this
Sample width for multi-category classifiers
 R u t c o r Research R e p o r t Sample width for multi-category classifiers Martin Anthony a Joel Ratsaby b RRR 29-2012, November 2012 RUTCOR Rutgers Center for Operations Research Rutgers University
R u t c o r Research R e p o r t Sample width for multi-category classifiers Martin Anthony a Joel Ratsaby b RRR 29-2012, November 2012 RUTCOR Rutgers Center for Operations Research Rutgers University
The No-Regret Framework for Online Learning
 The No-Regret Framework for Online Learning A Tutorial Introduction Nahum Shimkin Technion Israel Institute of Technology Haifa, Israel Stochastic Processes in Engineering IIT Mumbai, March 2013 N. Shimkin,
The No-Regret Framework for Online Learning A Tutorial Introduction Nahum Shimkin Technion Israel Institute of Technology Haifa, Israel Stochastic Processes in Engineering IIT Mumbai, March 2013 N. Shimkin,
9 Classification. 9.1 Linear Classifiers
 9 Classification This topic returns to prediction. Unlike linear regression where we were predicting a numeric value, in this case we are predicting a class: winner or loser, yes or no, rich or poor, positive
9 Classification This topic returns to prediction. Unlike linear regression where we were predicting a numeric value, in this case we are predicting a class: winner or loser, yes or no, rich or poor, positive
Support Vector Machines for Classification: A Statistical Portrait
 Support Vector Machines for Classification: A Statistical Portrait Yoonkyung Lee Department of Statistics The Ohio State University May 27, 2011 The Spring Conference of Korean Statistical Society KAIST,
Support Vector Machines for Classification: A Statistical Portrait Yoonkyung Lee Department of Statistics The Ohio State University May 27, 2011 The Spring Conference of Korean Statistical Society KAIST,
CSE 417T: Introduction to Machine Learning. Final Review. Henry Chai 12/4/18
 CSE 417T: Introduction to Machine Learning Final Review Henry Chai 12/4/18 Overfitting Overfitting is fitting the training data more than is warranted Fitting noise rather than signal 2 Estimating! "#$
CSE 417T: Introduction to Machine Learning Final Review Henry Chai 12/4/18 Overfitting Overfitting is fitting the training data more than is warranted Fitting noise rather than signal 2 Estimating! "#$
ECE521 week 3: 23/26 January 2017
 ECE521 week 3: 23/26 January 2017 Outline Probabilistic interpretation of linear regression - Maximum likelihood estimation (MLE) - Maximum a posteriori (MAP) estimation Bias-variance trade-off Linear
ECE521 week 3: 23/26 January 2017 Outline Probabilistic interpretation of linear regression - Maximum likelihood estimation (MLE) - Maximum a posteriori (MAP) estimation Bias-variance trade-off Linear
This article appeared in a journal published by Elsevier. The attached copy is furnished to the author for internal non-commercial research and
 This article appeared in a journal published by Elsevier. The attached copy is furnished to the author for internal non-commercial research education use, including for instruction at the authors institution
This article appeared in a journal published by Elsevier. The attached copy is furnished to the author for internal non-commercial research education use, including for instruction at the authors institution
Learning noisy linear classifiers via adaptive and selective sampling
 Mach Learn (2011) 83: 71 102 DOI 10.1007/s10994-010-5191-x Learning noisy linear classifiers via adaptive and selective sampling Giovanni Cavallanti Nicolò Cesa-Bianchi Claudio Gentile Received: 13 January
Mach Learn (2011) 83: 71 102 DOI 10.1007/s10994-010-5191-x Learning noisy linear classifiers via adaptive and selective sampling Giovanni Cavallanti Nicolò Cesa-Bianchi Claudio Gentile Received: 13 January
Online Learning and Sequential Decision Making
 Online Learning and Sequential Decision Making Emilie Kaufmann CNRS & CRIStAL, Inria SequeL, emilie.kaufmann@univ-lille.fr Research School, ENS Lyon, Novembre 12-13th 2018 Emilie Kaufmann Online Learning
Online Learning and Sequential Decision Making Emilie Kaufmann CNRS & CRIStAL, Inria SequeL, emilie.kaufmann@univ-lille.fr Research School, ENS Lyon, Novembre 12-13th 2018 Emilie Kaufmann Online Learning
Support vector machines Lecture 4
 Support vector machines Lecture 4 David Sontag New York University Slides adapted from Luke Zettlemoyer, Vibhav Gogate, and Carlos Guestrin Q: What does the Perceptron mistake bound tell us? Theorem: The
Support vector machines Lecture 4 David Sontag New York University Slides adapted from Luke Zettlemoyer, Vibhav Gogate, and Carlos Guestrin Q: What does the Perceptron mistake bound tell us? Theorem: The
CS 446: Machine Learning Lecture 4, Part 2: On-Line Learning
 CS 446: Machine Learning Lecture 4, Part 2: On-Line Learning 0.1 Linear Functions So far, we have been looking at Linear Functions { as a class of functions which can 1 if W1 X separate some data and not
CS 446: Machine Learning Lecture 4, Part 2: On-Line Learning 0.1 Linear Functions So far, we have been looking at Linear Functions { as a class of functions which can 1 if W1 X separate some data and not
Using Additive Expert Ensembles to Cope with Concept Drift
 Jeremy Z. Kolter and Marcus A. Maloof {jzk, maloof}@cs.georgetown.edu Department of Computer Science, Georgetown University, Washington, DC 20057-1232, USA Abstract We consider online learning where the
Jeremy Z. Kolter and Marcus A. Maloof {jzk, maloof}@cs.georgetown.edu Department of Computer Science, Georgetown University, Washington, DC 20057-1232, USA Abstract We consider online learning where the
The sample complexity of agnostic learning with deterministic labels
 The sample complexity of agnostic learning with deterministic labels Shai Ben-David Cheriton School of Computer Science University of Waterloo Waterloo, ON, N2L 3G CANADA shai@uwaterloo.ca Ruth Urner College
The sample complexity of agnostic learning with deterministic labels Shai Ben-David Cheriton School of Computer Science University of Waterloo Waterloo, ON, N2L 3G CANADA shai@uwaterloo.ca Ruth Urner College
A note on the generalization performance of kernel classifiers with margin. Theodoros Evgeniou and Massimiliano Pontil
 MASSACHUSETTS INSTITUTE OF TECHNOLOGY ARTIFICIAL INTELLIGENCE LABORATORY and CENTER FOR BIOLOGICAL AND COMPUTATIONAL LEARNING DEPARTMENT OF BRAIN AND COGNITIVE SCIENCES A.I. Memo No. 68 November 999 C.B.C.L
MASSACHUSETTS INSTITUTE OF TECHNOLOGY ARTIFICIAL INTELLIGENCE LABORATORY and CENTER FOR BIOLOGICAL AND COMPUTATIONAL LEARNING DEPARTMENT OF BRAIN AND COGNITIVE SCIENCES A.I. Memo No. 68 November 999 C.B.C.L
Efficient and Principled Online Classification Algorithms for Lifelon
 Efficient and Principled Online Classification Algorithms for Lifelong Learning Toyota Technological Institute at Chicago Chicago, IL USA Talk @ Lifelong Learning for Mobile Robotics Applications Workshop,
Efficient and Principled Online Classification Algorithms for Lifelong Learning Toyota Technological Institute at Chicago Chicago, IL USA Talk @ Lifelong Learning for Mobile Robotics Applications Workshop,
Brief Introduction to Machine Learning
 Brief Introduction to Machine Learning Yuh-Jye Lee Lab of Data Science and Machine Intelligence Dept. of Applied Math. at NCTU August 29, 2016 1 / 49 1 Introduction 2 Binary Classification 3 Support Vector
Brief Introduction to Machine Learning Yuh-Jye Lee Lab of Data Science and Machine Intelligence Dept. of Applied Math. at NCTU August 29, 2016 1 / 49 1 Introduction 2 Binary Classification 3 Support Vector
Lecture Support Vector Machine (SVM) Classifiers
 Introduction to Machine Learning Lecturer: Amir Globerson Lecture 6 Fall Semester Scribe: Yishay Mansour 6.1 Support Vector Machine (SVM) Classifiers Classification is one of the most important tasks in
Introduction to Machine Learning Lecturer: Amir Globerson Lecture 6 Fall Semester Scribe: Yishay Mansour 6.1 Support Vector Machine (SVM) Classifiers Classification is one of the most important tasks in
Introduction to Machine Learning Lecture 13. Mehryar Mohri Courant Institute and Google Research
 Introduction to Machine Learning Lecture 13 Mehryar Mohri Courant Institute and Google Research mohri@cims.nyu.edu Multi-Class Classification Mehryar Mohri - Introduction to Machine Learning page 2 Motivation
Introduction to Machine Learning Lecture 13 Mehryar Mohri Courant Institute and Google Research mohri@cims.nyu.edu Multi-Class Classification Mehryar Mohri - Introduction to Machine Learning page 2 Motivation
The Perceptron algorithm
 The Perceptron algorithm Tirgul 3 November 2016 Agnostic PAC Learnability A hypothesis class H is agnostic PAC learnable if there exists a function m H : 0,1 2 N and a learning algorithm with the following
The Perceptron algorithm Tirgul 3 November 2016 Agnostic PAC Learnability A hypothesis class H is agnostic PAC learnable if there exists a function m H : 0,1 2 N and a learning algorithm with the following
Machine Learning and Computational Statistics, Spring 2017 Homework 2: Lasso Regression
 Machine Learning and Computational Statistics, Spring 2017 Homework 2: Lasso Regression Due: Monday, February 13, 2017, at 10pm (Submit via Gradescope) Instructions: Your answers to the questions below,
Machine Learning and Computational Statistics, Spring 2017 Homework 2: Lasso Regression Due: Monday, February 13, 2017, at 10pm (Submit via Gradescope) Instructions: Your answers to the questions below,
Analysis of perceptron-based active learning
 Analysis of perceptron-based active learning Sanjoy Dasgupta 1, Adam Tauman Kalai 2, and Claire Monteleoni 3 1 UCSD CSE 9500 Gilman Drive #0114, La Jolla, CA 92093 dasgupta@csucsdedu 2 TTI-Chicago 1427
Analysis of perceptron-based active learning Sanjoy Dasgupta 1, Adam Tauman Kalai 2, and Claire Monteleoni 3 1 UCSD CSE 9500 Gilman Drive #0114, La Jolla, CA 92093 dasgupta@csucsdedu 2 TTI-Chicago 1427
3.4 Linear Least-Squares Filter
 X(n) = [x(1), x(2),..., x(n)] T 1 3.4 Linear Least-Squares Filter Two characteristics of linear least-squares filter: 1. The filter is built around a single linear neuron. 2. The cost function is the sum
X(n) = [x(1), x(2),..., x(n)] T 1 3.4 Linear Least-Squares Filter Two characteristics of linear least-squares filter: 1. The filter is built around a single linear neuron. 2. The cost function is the sum
The Forgetron: A Kernel-Based Perceptron on a Fixed Budget
 The Forgetron: A Kernel-Based Perceptron on a Fixed Budget Ofer Dekel Shai Shalev-Shwartz Yoram Singer School of Computer Science & Engineering The Hebrew University, Jerusalem 91904, Israel {oferd,shais,singer}@cs.huji.ac.il
The Forgetron: A Kernel-Based Perceptron on a Fixed Budget Ofer Dekel Shai Shalev-Shwartz Yoram Singer School of Computer Science & Engineering The Hebrew University, Jerusalem 91904, Israel {oferd,shais,singer}@cs.huji.ac.il
Statistical Data Mining and Machine Learning Hilary Term 2016
 Statistical Data Mining and Machine Learning Hilary Term 2016 Dino Sejdinovic Department of Statistics Oxford Slides and other materials available at: http://www.stats.ox.ac.uk/~sejdinov/sdmml Naïve Bayes
Statistical Data Mining and Machine Learning Hilary Term 2016 Dino Sejdinovic Department of Statistics Oxford Slides and other materials available at: http://www.stats.ox.ac.uk/~sejdinov/sdmml Naïve Bayes
Comparison of Modern Stochastic Optimization Algorithms
 Comparison of Modern Stochastic Optimization Algorithms George Papamakarios December 214 Abstract Gradient-based optimization methods are popular in machine learning applications. In large-scale problems,
Comparison of Modern Stochastic Optimization Algorithms George Papamakarios December 214 Abstract Gradient-based optimization methods are popular in machine learning applications. In large-scale problems,
CS 231A Section 1: Linear Algebra & Probability Review
 CS 231A Section 1: Linear Algebra & Probability Review 1 Topics Support Vector Machines Boosting Viola-Jones face detector Linear Algebra Review Notation Operations & Properties Matrix Calculus Probability
CS 231A Section 1: Linear Algebra & Probability Review 1 Topics Support Vector Machines Boosting Viola-Jones face detector Linear Algebra Review Notation Operations & Properties Matrix Calculus Probability
Machine Learning 2017
 Machine Learning 2017 Volker Roth Department of Mathematics & Computer Science University of Basel 21st March 2017 Volker Roth (University of Basel) Machine Learning 2017 21st March 2017 1 / 41 Section
Machine Learning 2017 Volker Roth Department of Mathematics & Computer Science University of Basel 21st March 2017 Volker Roth (University of Basel) Machine Learning 2017 21st March 2017 1 / 41 Section
CS 231A Section 1: Linear Algebra & Probability Review. Kevin Tang
 CS 231A Section 1: Linear Algebra & Probability Review Kevin Tang Kevin Tang Section 1-1 9/30/2011 Topics Support Vector Machines Boosting Viola Jones face detector Linear Algebra Review Notation Operations
CS 231A Section 1: Linear Algebra & Probability Review Kevin Tang Kevin Tang Section 1-1 9/30/2011 Topics Support Vector Machines Boosting Viola Jones face detector Linear Algebra Review Notation Operations
Learning the Semantic Correlation: An Alternative Way to Gain from Unlabeled Text
 Learning the Semantic Correlation: An Alternative Way to Gain from Unlabeled Text Yi Zhang Machine Learning Department Carnegie Mellon University yizhang1@cs.cmu.edu Jeff Schneider The Robotics Institute
Learning the Semantic Correlation: An Alternative Way to Gain from Unlabeled Text Yi Zhang Machine Learning Department Carnegie Mellon University yizhang1@cs.cmu.edu Jeff Schneider The Robotics Institute
Regularization. CSCE 970 Lecture 3: Regularization. Stephen Scott and Vinod Variyam. Introduction. Outline
 Other Measures 1 / 52 sscott@cse.unl.edu learning can generally be distilled to an optimization problem Choose a classifier (function, hypothesis) from a set of functions that minimizes an objective function
Other Measures 1 / 52 sscott@cse.unl.edu learning can generally be distilled to an optimization problem Choose a classifier (function, hypothesis) from a set of functions that minimizes an objective function
Empirical Risk Minimization
 Empirical Risk Minimization Fabrice Rossi SAMM Université Paris 1 Panthéon Sorbonne 2018 Outline Introduction PAC learning ERM in practice 2 General setting Data X the input space and Y the output space
Empirical Risk Minimization Fabrice Rossi SAMM Université Paris 1 Panthéon Sorbonne 2018 Outline Introduction PAC learning ERM in practice 2 General setting Data X the input space and Y the output space
Online Bounds for Bayesian Algorithms
 Online Bounds for Bayesian Algorithms Sham M. Kakade Computer and Information Science Department University of Pennsylvania Andrew Y. Ng Computer Science Department Stanford University Abstract We present
Online Bounds for Bayesian Algorithms Sham M. Kakade Computer and Information Science Department University of Pennsylvania Andrew Y. Ng Computer Science Department Stanford University Abstract We present
Online Passive-Aggressive Algorithms
 Online Passive-Aggressive Algorithms Koby Crammer Ofer Dekel Joseph Keshet Shai Shalev-Shwartz Yoram Singer School of Computer Science and Engineering The Hebrew University Jerusalem, 91904, Israel CRAMMER@CIS.UPENN.EDU
Online Passive-Aggressive Algorithms Koby Crammer Ofer Dekel Joseph Keshet Shai Shalev-Shwartz Yoram Singer School of Computer Science and Engineering The Hebrew University Jerusalem, 91904, Israel CRAMMER@CIS.UPENN.EDU
Mining Classification Knowledge
 Mining Classification Knowledge Remarks on NonSymbolic Methods JERZY STEFANOWSKI Institute of Computing Sciences, Poznań University of Technology COST Doctoral School, Troina 2008 Outline 1. Bayesian classification
Mining Classification Knowledge Remarks on NonSymbolic Methods JERZY STEFANOWSKI Institute of Computing Sciences, Poznań University of Technology COST Doctoral School, Troina 2008 Outline 1. Bayesian classification
Online multiclass learning with bandit feedback under a Passive-Aggressive approach
 ESANN 205 proceedings, European Symposium on Artificial Neural Networks, Computational Intelligence and Machine Learning. Bruges (Belgium), 22-24 April 205, i6doc.com publ., ISBN 978-28758704-8. Online
ESANN 205 proceedings, European Symposium on Artificial Neural Networks, Computational Intelligence and Machine Learning. Bruges (Belgium), 22-24 April 205, i6doc.com publ., ISBN 978-28758704-8. Online
Linear smoother. ŷ = S y. where s ij = s ij (x) e.g. s ij = diag(l i (x))
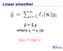 Linear smoother ŷ = S y where s ij = s ij (x) e.g. s ij = diag(l i (x)) 2 Online Learning: LMS and Perceptrons Partially adapted from slides by Ryan Gabbard and Mitch Marcus (and lots original slides by
Linear smoother ŷ = S y where s ij = s ij (x) e.g. s ij = diag(l i (x)) 2 Online Learning: LMS and Perceptrons Partially adapted from slides by Ryan Gabbard and Mitch Marcus (and lots original slides by
Machine Learning. VC Dimension and Model Complexity. Eric Xing , Fall 2015
 Machine Learning 10-701, Fall 2015 VC Dimension and Model Complexity Eric Xing Lecture 16, November 3, 2015 Reading: Chap. 7 T.M book, and outline material Eric Xing @ CMU, 2006-2015 1 Last time: PAC and
Machine Learning 10-701, Fall 2015 VC Dimension and Model Complexity Eric Xing Lecture 16, November 3, 2015 Reading: Chap. 7 T.M book, and outline material Eric Xing @ CMU, 2006-2015 1 Last time: PAC and
Linear & nonlinear classifiers
 Linear & nonlinear classifiers Machine Learning Hamid Beigy Sharif University of Technology Fall 1396 Hamid Beigy (Sharif University of Technology) Linear & nonlinear classifiers Fall 1396 1 / 44 Table
Linear & nonlinear classifiers Machine Learning Hamid Beigy Sharif University of Technology Fall 1396 Hamid Beigy (Sharif University of Technology) Linear & nonlinear classifiers Fall 1396 1 / 44 Table
A Large Deviation Bound for the Area Under the ROC Curve
 A Large Deviation Bound for the Area Under the ROC Curve Shivani Agarwal, Thore Graepel, Ralf Herbrich and Dan Roth Dept. of Computer Science University of Illinois Urbana, IL 680, USA {sagarwal,danr}@cs.uiuc.edu
A Large Deviation Bound for the Area Under the ROC Curve Shivani Agarwal, Thore Graepel, Ralf Herbrich and Dan Roth Dept. of Computer Science University of Illinois Urbana, IL 680, USA {sagarwal,danr}@cs.uiuc.edu
Machine Learning. Lecture 9: Learning Theory. Feng Li.
 Machine Learning Lecture 9: Learning Theory Feng Li fli@sdu.edu.cn https://funglee.github.io School of Computer Science and Technology Shandong University Fall 2018 Why Learning Theory How can we tell
Machine Learning Lecture 9: Learning Theory Feng Li fli@sdu.edu.cn https://funglee.github.io School of Computer Science and Technology Shandong University Fall 2018 Why Learning Theory How can we tell
The Perceptron Algorithm 1
 CS 64: Machine Learning Spring 5 College of Computer and Information Science Northeastern University Lecture 5 March, 6 Instructor: Bilal Ahmed Scribe: Bilal Ahmed & Virgil Pavlu Introduction The Perceptron
CS 64: Machine Learning Spring 5 College of Computer and Information Science Northeastern University Lecture 5 March, 6 Instructor: Bilal Ahmed Scribe: Bilal Ahmed & Virgil Pavlu Introduction The Perceptron
The Perceptron Algorithm
 The Perceptron Algorithm Greg Grudic Greg Grudic Machine Learning Questions? Greg Grudic Machine Learning 2 Binary Classification A binary classifier is a mapping from a set of d inputs to a single output
The Perceptron Algorithm Greg Grudic Greg Grudic Machine Learning Questions? Greg Grudic Machine Learning 2 Binary Classification A binary classifier is a mapping from a set of d inputs to a single output
COMS F18 Homework 3 (due October 29, 2018)
 COMS 477-2 F8 Homework 3 (due October 29, 208) Instructions Submit your write-up on Gradescope as a neatly typeset (not scanned nor handwritten) PDF document by :59 PM of the due date. On Gradescope, be
COMS 477-2 F8 Homework 3 (due October 29, 208) Instructions Submit your write-up on Gradescope as a neatly typeset (not scanned nor handwritten) PDF document by :59 PM of the due date. On Gradescope, be
Maximum Likelihood, Logistic Regression, and Stochastic Gradient Training
 Maximum Likelihood, Logistic Regression, and Stochastic Gradient Training Charles Elkan elkan@cs.ucsd.edu January 17, 2013 1 Principle of maximum likelihood Consider a family of probability distributions
Maximum Likelihood, Logistic Regression, and Stochastic Gradient Training Charles Elkan elkan@cs.ucsd.edu January 17, 2013 1 Principle of maximum likelihood Consider a family of probability distributions
FORMULATION OF THE LEARNING PROBLEM
 FORMULTION OF THE LERNING PROBLEM MIM RGINSKY Now that we have seen an informal statement of the learning problem, as well as acquired some technical tools in the form of concentration inequalities, we
FORMULTION OF THE LERNING PROBLEM MIM RGINSKY Now that we have seen an informal statement of the learning problem, as well as acquired some technical tools in the form of concentration inequalities, we
6.036 midterm review. Wednesday, March 18, 15
 6.036 midterm review 1 Topics covered supervised learning labels available unsupervised learning no labels available semi-supervised learning some labels available - what algorithms have you learned that
6.036 midterm review 1 Topics covered supervised learning labels available unsupervised learning no labels available semi-supervised learning some labels available - what algorithms have you learned that
IFT Lecture 7 Elements of statistical learning theory
 IFT 6085 - Lecture 7 Elements of statistical learning theory This version of the notes has not yet been thoroughly checked. Please report any bugs to the scribes or instructor. Scribe(s): Brady Neal and
IFT 6085 - Lecture 7 Elements of statistical learning theory This version of the notes has not yet been thoroughly checked. Please report any bugs to the scribes or instructor. Scribe(s): Brady Neal and
The Perceptron Algorithm
 The Perceptron Algorithm Machine Learning Spring 2018 The slides are mainly from Vivek Srikumar 1 Outline The Perceptron Algorithm Perceptron Mistake Bound Variants of Perceptron 2 Where are we? The Perceptron
The Perceptron Algorithm Machine Learning Spring 2018 The slides are mainly from Vivek Srikumar 1 Outline The Perceptron Algorithm Perceptron Mistake Bound Variants of Perceptron 2 Where are we? The Perceptron
MinOver Revisited for Incremental Support-Vector-Classification
 MinOver Revisited for Incremental Support-Vector-Classification Thomas Martinetz Institute for Neuro- and Bioinformatics University of Lübeck D-23538 Lübeck, Germany martinetz@informatik.uni-luebeck.de
MinOver Revisited for Incremental Support-Vector-Classification Thomas Martinetz Institute for Neuro- and Bioinformatics University of Lübeck D-23538 Lübeck, Germany martinetz@informatik.uni-luebeck.de
Natural Language Processing (CSEP 517): Text Classification
 Natural Language Processing (CSEP 517): Text Classification Noah Smith c 2017 University of Washington nasmith@cs.washington.edu April 10, 2017 1 / 71 To-Do List Online quiz: due Sunday Read: Jurafsky
Natural Language Processing (CSEP 517): Text Classification Noah Smith c 2017 University of Washington nasmith@cs.washington.edu April 10, 2017 1 / 71 To-Do List Online quiz: due Sunday Read: Jurafsky
THE ADVICEPTRON: GIVING ADVICE TO THE PERCEPTRON
 THE ADVICEPTRON: GIVING ADVICE TO THE PERCEPTRON Gautam Kunapuli Kristin P. Bennett University of Wisconsin Madison Rensselaer Polytechnic Institute Madison, WI 5375 Troy, NY 1218 kunapg@wisc.edu bennek@rpi.edu
THE ADVICEPTRON: GIVING ADVICE TO THE PERCEPTRON Gautam Kunapuli Kristin P. Bennett University of Wisconsin Madison Rensselaer Polytechnic Institute Madison, WI 5375 Troy, NY 1218 kunapg@wisc.edu bennek@rpi.edu
Computational Learning Theory
 Computational Learning Theory Pardis Noorzad Department of Computer Engineering and IT Amirkabir University of Technology Ordibehesht 1390 Introduction For the analysis of data structures and algorithms
Computational Learning Theory Pardis Noorzad Department of Computer Engineering and IT Amirkabir University of Technology Ordibehesht 1390 Introduction For the analysis of data structures and algorithms
MIRA, SVM, k-nn. Lirong Xia
 MIRA, SVM, k-nn Lirong Xia Linear Classifiers (perceptrons) Inputs are feature values Each feature has a weight Sum is the activation activation w If the activation is: Positive: output +1 Negative, output
MIRA, SVM, k-nn Lirong Xia Linear Classifiers (perceptrons) Inputs are feature values Each feature has a weight Sum is the activation activation w If the activation is: Positive: output +1 Negative, output
This article appeared in a journal published by Elsevier. The attached copy is furnished to the author for internal non-commercial research and
 This article appeared in a journal published by Elsevier. The attached copy is furnished to the author for internal non-commercial research and education use, including for instruction at the authors institution
This article appeared in a journal published by Elsevier. The attached copy is furnished to the author for internal non-commercial research and education use, including for instruction at the authors institution
Learning Methods for Linear Detectors
 Intelligent Systems: Reasoning and Recognition James L. Crowley ENSIMAG 2 / MoSIG M1 Second Semester 2011/2012 Lesson 20 27 April 2012 Contents Learning Methods for Linear Detectors Learning Linear Detectors...2
Intelligent Systems: Reasoning and Recognition James L. Crowley ENSIMAG 2 / MoSIG M1 Second Semester 2011/2012 Lesson 20 27 April 2012 Contents Learning Methods for Linear Detectors Learning Linear Detectors...2
Optimization Methods for Machine Learning (OMML)
 Optimization Methods for Machine Learning (OMML) 2nd lecture (2 slots) Prof. L. Palagi 16/10/2014 1 What is (not) Data Mining? By Namwar Rizvi - Ad Hoc Query: ad Hoc queries just examines the current data
Optimization Methods for Machine Learning (OMML) 2nd lecture (2 slots) Prof. L. Palagi 16/10/2014 1 What is (not) Data Mining? By Namwar Rizvi - Ad Hoc Query: ad Hoc queries just examines the current data
Click Prediction and Preference Ranking of RSS Feeds
 Click Prediction and Preference Ranking of RSS Feeds 1 Introduction December 11, 2009 Steven Wu RSS (Really Simple Syndication) is a family of data formats used to publish frequently updated works. RSS
Click Prediction and Preference Ranking of RSS Feeds 1 Introduction December 11, 2009 Steven Wu RSS (Really Simple Syndication) is a family of data formats used to publish frequently updated works. RSS
Introduction to Machine Learning
 10-701 Introduction to Machine Learning Homework 2, version 1.0 Due Oct 16, 11:59 am Rules: 1. Homework submission is done via CMU Autolab system. Please package your writeup and code into a zip or tar
10-701 Introduction to Machine Learning Homework 2, version 1.0 Due Oct 16, 11:59 am Rules: 1. Homework submission is done via CMU Autolab system. Please package your writeup and code into a zip or tar
Support Vector Machines
 Support Vector Machines Reading: Ben-Hur & Weston, A User s Guide to Support Vector Machines (linked from class web page) Notation Assume a binary classification problem. Instances are represented by vector
Support Vector Machines Reading: Ben-Hur & Weston, A User s Guide to Support Vector Machines (linked from class web page) Notation Assume a binary classification problem. Instances are represented by vector
Introduction to Machine Learning
 1, DATA11002 Introduction to Machine Learning Lecturer: Teemu Roos TAs: Ville Hyvönen and Janne Leppä-aho Department of Computer Science University of Helsinki (based in part on material by Patrik Hoyer
1, DATA11002 Introduction to Machine Learning Lecturer: Teemu Roos TAs: Ville Hyvönen and Janne Leppä-aho Department of Computer Science University of Helsinki (based in part on material by Patrik Hoyer
Efficient Bandit Algorithms for Online Multiclass Prediction
 Efficient Bandit Algorithms for Online Multiclass Prediction Sham Kakade, Shai Shalev-Shwartz and Ambuj Tewari Presented By: Nakul Verma Motivation In many learning applications, true class labels are
Efficient Bandit Algorithms for Online Multiclass Prediction Sham Kakade, Shai Shalev-Shwartz and Ambuj Tewari Presented By: Nakul Verma Motivation In many learning applications, true class labels are
Randomized Algorithms
 Randomized Algorithms Saniv Kumar, Google Research, NY EECS-6898, Columbia University - Fall, 010 Saniv Kumar 9/13/010 EECS6898 Large Scale Machine Learning 1 Curse of Dimensionality Gaussian Mixture Models
Randomized Algorithms Saniv Kumar, Google Research, NY EECS-6898, Columbia University - Fall, 010 Saniv Kumar 9/13/010 EECS6898 Large Scale Machine Learning 1 Curse of Dimensionality Gaussian Mixture Models
Support Vector and Kernel Methods
 SIGIR 2003 Tutorial Support Vector and Kernel Methods Thorsten Joachims Cornell University Computer Science Department tj@cs.cornell.edu http://www.joachims.org 0 Linear Classifiers Rules of the Form:
SIGIR 2003 Tutorial Support Vector and Kernel Methods Thorsten Joachims Cornell University Computer Science Department tj@cs.cornell.edu http://www.joachims.org 0 Linear Classifiers Rules of the Form:
Solving Classification Problems By Knowledge Sets
 Solving Classification Problems By Knowledge Sets Marcin Orchel a, a Department of Computer Science, AGH University of Science and Technology, Al. A. Mickiewicza 30, 30-059 Kraków, Poland Abstract We propose
Solving Classification Problems By Knowledge Sets Marcin Orchel a, a Department of Computer Science, AGH University of Science and Technology, Al. A. Mickiewicza 30, 30-059 Kraków, Poland Abstract We propose
Support Vector Machine. Industrial AI Lab.
 Support Vector Machine Industrial AI Lab. Classification (Linear) Autonomously figure out which category (or class) an unknown item should be categorized into Number of categories / classes Binary: 2 different
Support Vector Machine Industrial AI Lab. Classification (Linear) Autonomously figure out which category (or class) an unknown item should be categorized into Number of categories / classes Binary: 2 different
Learning Theory. Ingo Steinwart University of Stuttgart. September 4, 2013
 Learning Theory Ingo Steinwart University of Stuttgart September 4, 2013 Ingo Steinwart University of Stuttgart () Learning Theory September 4, 2013 1 / 62 Basics Informal Introduction Informal Description
Learning Theory Ingo Steinwart University of Stuttgart September 4, 2013 Ingo Steinwart University of Stuttgart () Learning Theory September 4, 2013 1 / 62 Basics Informal Introduction Informal Description
Evaluation requires to define performance measures to be optimized
 Evaluation Basic concepts Evaluation requires to define performance measures to be optimized Performance of learning algorithms cannot be evaluated on entire domain (generalization error) approximation
Evaluation Basic concepts Evaluation requires to define performance measures to be optimized Performance of learning algorithms cannot be evaluated on entire domain (generalization error) approximation
SVAN 2016 Mini Course: Stochastic Convex Optimization Methods in Machine Learning
 SVAN 2016 Mini Course: Stochastic Convex Optimization Methods in Machine Learning Mark Schmidt University of British Columbia, May 2016 www.cs.ubc.ca/~schmidtm/svan16 Some images from this lecture are
SVAN 2016 Mini Course: Stochastic Convex Optimization Methods in Machine Learning Mark Schmidt University of British Columbia, May 2016 www.cs.ubc.ca/~schmidtm/svan16 Some images from this lecture are
Support Vector Machines Explained
 December 23, 2008 Support Vector Machines Explained Tristan Fletcher www.cs.ucl.ac.uk/staff/t.fletcher/ Introduction This document has been written in an attempt to make the Support Vector Machines (SVM),
December 23, 2008 Support Vector Machines Explained Tristan Fletcher www.cs.ucl.ac.uk/staff/t.fletcher/ Introduction This document has been written in an attempt to make the Support Vector Machines (SVM),
MIDTERM: CS 6375 INSTRUCTOR: VIBHAV GOGATE October,
 MIDTERM: CS 6375 INSTRUCTOR: VIBHAV GOGATE October, 23 2013 The exam is closed book. You are allowed a one-page cheat sheet. Answer the questions in the spaces provided on the question sheets. If you run
MIDTERM: CS 6375 INSTRUCTOR: VIBHAV GOGATE October, 23 2013 The exam is closed book. You are allowed a one-page cheat sheet. Answer the questions in the spaces provided on the question sheets. If you run
Linking non-binned spike train kernels to several existing spike train metrics
 Linking non-binned spike train kernels to several existing spike train metrics Benjamin Schrauwen Jan Van Campenhout ELIS, Ghent University, Belgium Benjamin.Schrauwen@UGent.be Abstract. This work presents
Linking non-binned spike train kernels to several existing spike train metrics Benjamin Schrauwen Jan Van Campenhout ELIS, Ghent University, Belgium Benjamin.Schrauwen@UGent.be Abstract. This work presents
CSCI-567: Machine Learning (Spring 2019)
 CSCI-567: Machine Learning (Spring 2019) Prof. Victor Adamchik U of Southern California Mar. 19, 2019 March 19, 2019 1 / 43 Administration March 19, 2019 2 / 43 Administration TA3 is due this week March
CSCI-567: Machine Learning (Spring 2019) Prof. Victor Adamchik U of Southern California Mar. 19, 2019 March 19, 2019 1 / 43 Administration March 19, 2019 2 / 43 Administration TA3 is due this week March
Evaluation. Andrea Passerini Machine Learning. Evaluation
 Andrea Passerini passerini@disi.unitn.it Machine Learning Basic concepts requires to define performance measures to be optimized Performance of learning algorithms cannot be evaluated on entire domain
Andrea Passerini passerini@disi.unitn.it Machine Learning Basic concepts requires to define performance measures to be optimized Performance of learning algorithms cannot be evaluated on entire domain
On a Theory of Learning with Similarity Functions
 Maria-Florina Balcan NINAMF@CS.CMU.EDU Avrim Blum AVRIM@CS.CMU.EDU School of Computer Science, Carnegie Mellon University, 5000 Forbes Avenue, Pittsburgh, PA 15213-3891 Abstract Kernel functions have become
Maria-Florina Balcan NINAMF@CS.CMU.EDU Avrim Blum AVRIM@CS.CMU.EDU School of Computer Science, Carnegie Mellon University, 5000 Forbes Avenue, Pittsburgh, PA 15213-3891 Abstract Kernel functions have become
Classification of handwritten digits using supervised locally linear embedding algorithm and support vector machine
 Classification of handwritten digits using supervised locally linear embedding algorithm and support vector machine Olga Kouropteva, Oleg Okun, Matti Pietikäinen Machine Vision Group, Infotech Oulu and
Classification of handwritten digits using supervised locally linear embedding algorithm and support vector machine Olga Kouropteva, Oleg Okun, Matti Pietikäinen Machine Vision Group, Infotech Oulu and
Linear Classifiers and the Perceptron
 Linear Classifiers and the Perceptron William Cohen February 4, 2008 1 Linear classifiers Let s assume that every instance is an n-dimensional vector of real numbers x R n, and there are only two possible
Linear Classifiers and the Perceptron William Cohen February 4, 2008 1 Linear classifiers Let s assume that every instance is an n-dimensional vector of real numbers x R n, and there are only two possible
Support'Vector'Machines. Machine(Learning(Spring(2018 March(5(2018 Kasthuri Kannan
 Support'Vector'Machines Machine(Learning(Spring(2018 March(5(2018 Kasthuri Kannan kasthuri.kannan@nyumc.org Overview Support Vector Machines for Classification Linear Discrimination Nonlinear Discrimination
Support'Vector'Machines Machine(Learning(Spring(2018 March(5(2018 Kasthuri Kannan kasthuri.kannan@nyumc.org Overview Support Vector Machines for Classification Linear Discrimination Nonlinear Discrimination
Links between Perceptrons, MLPs and SVMs
 Links between Perceptrons, MLPs and SVMs Ronan Collobert Samy Bengio IDIAP, Rue du Simplon, 19 Martigny, Switzerland Abstract We propose to study links between three important classification algorithms:
Links between Perceptrons, MLPs and SVMs Ronan Collobert Samy Bengio IDIAP, Rue du Simplon, 19 Martigny, Switzerland Abstract We propose to study links between three important classification algorithms:
