OVER the past two decades, extensive studies have been
|
|
|
- Edward Newton
- 5 years ago
- Views:
Transcription
1 PREPRNT - DO :.9/TRO Stability Analysis for Bilateral Teleoperation: An QC Formulation İlhan Polat and Carsten W. Scherer, Senior Member, EEE Abstract We present the stability analysis of uncertain bilateral teleoperation systems and numerical test cases via a formulation in terms of ntegral Quadratic Constraints QCs. Frequently used robust stability conditions originating from network theory in the face of passive human and environment operators are shown to be particular cases in this framework. This allows to subsume seemingly different frequency domain methods to one formulation. Using this unified approach, different uncertainty classes can be incorporated into the stability test simultaneously. A few commonly encountered uncertainty types and the corresponding stability analysis tests are derived and numerically illustrated for a simple teleoperation system. These numerical examples highlight the need for a refined modeling of the human and the environment in teleoperation systems. ndex Terms Bilateral teleoperation, Stability analysis, Robust control, ntegral Quadratic Constraints.. NTRODUCTON OVER the past two decades, extensive studies have been published concerning the stability analysis of bilateral teleoperation systems, mainly relying on the conditions which originate from two-port network theory see, e.g., [] [6] and also [7] for a survey. One of the main stability results of network theory is the so-called unconditional stability theorem see [8] and [9], which states the conditions on the network to remain stable whenever they are connected to any passive immittances on the load and the source side. Thus, the designer can skip the explicit modeling of the load and the source of a network by just verifying that the terminations are passive. Since interconnection stability of a bilateral teleoperation system driven by a human and exploring a remote environment is analogous to that of a two-port network, this manner of modeling bilateral teleoperation systems has dominated the literature. n this setting, the human and the environment are assumed to be passive or, more properly, to be represented by passive operators. This allows testing of interconnection stability by Manuscript received January 2, 22; revised June 3, 22; accepted July 2, 22. This paper was recommended for publication by Associate Editor D. Lee and Editor W. K. Chung upon evaluation of the reviewers comments. This work is financially supported by the MicroNED program a part of the BSK program of the Dutch government, The Netherlands. İ. Polat is with Delft Center for Systems and Control DCSC, Delft University of Technology, Mekelweg 2, 2628CD, Delft, The Netherlands, i.polat@tudelft.nl. C.W. Scherer is with Department of Mathematics, University of Stuttgart, Pfaffenwaldring 57, 7569, Stuttgart, Germany, carsten.scherer@mathematik.uni-stuttgart.de. Color versions of one or more of the figures in this paper are available online at Digital Object dentifier.9/tro /$3. c 22 EEE just applying the unconditional stability theorem. Moreover, if the human and the environment are assumed passive and linear time invariant LT, the unconditional stability theorem becomes an exact stability characterization via Llewellyn s theorem. Therefore, passivity based analysis makes it relatively easy to verify interconnection stability under different environment and human configurations during the interaction. Over the past two decades, the passivity assumption became a de facto requirement to perform analysis of teleoperation systems. Even in cases where certain blocks might be active, methods for passification of the nonpassive interactions have been derived see, e.g., [] in which the passivity of the blocks is monitored and regulated. Obviously, this convenience comes with a price. The cost of simplifying the problem is the resulting conservatism of the analysis results. n other words, the proposed tests guarantee stability in the face of an uncertainty set that is often much larger than the set of potential uncertainties that can occur in the physical system. Because of this oversimplified uncertainty structure, worst cases that would not occur in the physical setup are still accounted for. Therefore, an important class of stable interconnections is ruled out due to the conservatism brought in by this assumption. To reduce the involved conservatism, it has been suggested to confine the range of environment dynamics to suitable subsets of all passive LT operators see, e.g., [] [5]. Another approach was to utilize structured singular value SSV tools see [6] and [6] [22] to analyze the bilateral teleoperation systems. The main usage was to transform the passive operators to norm-bounded uncertainties via loop transformations that, in turn, offered a direct handle for the delay problem. Alternatively, a mass spring damper system with uncertain coefficients was used to model human/environment for the stability analysis. These studies revealed that it is quite difficult to capture all possible human and environment configurations with a particular LT uncertainty structure that is compatible with SSV tools. This conclusion has been strongly influenced by two important points: the limitations of the analysis methods that severely restricted the class of allowed uncertainties and the tendency to use an uncertain mechanical system often of second order in order to model the human and the environment. These findings led to a diminishing interest in this line of research and to a more intensive focus on the passivity-based modeling avoidance paradigm in order to circumvent refined modeling issues. On the other hand, contemporary analysis and synthesis tools in robust control allow us to consider a much larger variety of
2 2 PREPRNT - DO :.9/TRO classes of uncertainties/nonlinearities. Hence, it has become, once again, relevant to strive for a more accurate human model to relax the conservative passivity assumption. Note that when we discuss a possible refined human model, we do not refer to a precise physical model, e.g., of the human arm/hand, which is very difficult, if not impossible, to obtain. nstead, we have in mind a model that is represented by a possibly uncertain mathematical operator that captures the essential features that remain preserved among individuals, such as constraints on the bandwidth or other bounds on specific properties directionality, cognitive delay, positioning precision, etc.. We would like to emphasize that this can lead to a more complicated family of models than that of a secondorder mechanical system. The last 5 years have witnessed the development of robustness analysis tools based on integral quadratic constraints QCs see [23], which unify many classical results allow us to capture time-varying and/or nonlinear uncertainty operators. Despite these improvements, it is worth noting that the teleoperation and haptics literature still refers to classical SSV results if addressing the issues of robustness. n some places, the terminology of nominal performance, robust stability, and robust performance is used interchangeably e.g. H vs. µ. This reveals that there is only a limited tendency to utilize these more advanced QC tools in the teleoperation community. Still, after a hiatus of explicit use of robust control techniques, the number of studies devoted to teleoperation along this direction has been increasing see, e.g., [24] [27] and references therein to name a few among many others. n this paper, which has been partially presented in [28] [3], stability conditions from network theory are reformulated in terms of quadratic constraints. Their equivalence is shown to emphasize that the analysis and synthesis problems can be carried over to the robust control framework without giving away the exactness of the conditions and without relying on the particular terminology of network theory. Our main purpose is to unify the existing frequency-domain analysis tools in a systematic way and, furthermore, to point out the underlying connections explicitly. Based on this formulation, we show how one can extend the stability analysis to cases that are excluded by the hypotheses of the classical tools and we provide illustrations by numerical examples. As another important advantage of this approach, it allows for a fair comparison of various control design algorithms that have been proposed in the teleoperation literature as discussed in [3] and [32].. PRELMNARES n this section, we will give a brief technical overview of the multiplier methods and their relation to passivity results. The notation is standard. L n 2 is the space of R n -valued square summable functions on,, the extended real line is R e := R { }, and ˆf denotes the Fourier transform of f. For Hermitian matrices M, M M, M means positive and negative semi definiteness respectively. The symbol is used as a placeholder to save space, such as in QN which means N QN. RH RH denotes the set of real rational, Fig.. + s G l a Two representations of a 2-port network. + q y s l G G 2 G 2 G 22 proper and stable transfer functions matrices and G is the H -norm, the largest singular value of G RH over frequency. An upper lower linear fractional transformation is denoted by G = G 22 + G 2 G G 2 G = G +G 2 G 22 G 2 with an appropriate partitioning of G. State-space realizations ] Gs = Cs A B + D are denoted as G = [ A B C D A. System Representations n network theory, as well as in its application to bilateral teleoperation, the system refers to the network model that is hypothetically disconnected thus admitting virtual terminals from its surroundings such as the load and the source of a circuit. This system is allowed to interact with its surroundings via ports or, more generally, circuit terminal pairings that satisfy some technical assumptions. n the teleoperation context, if one uses the load-source analogy for the manipulated environment and the human, then the system models all the bilateral interaction between the load and the source ports [as in Fig. a]. Furthermore, by imposing an artificial causality scheme, two of these signals can be selected as free variables and the remaining ones become dependent variables see [33]. Depending on the choice of the free variables, the system can be expressed in terms of impedance, admittance and hybrid parameters for two-port networks and their combinations for general n-port network interconnections. With a slight abuse of notation, we will use the term immittance matrix to refer to any of these representations. Suppose that a two-port immittance matrix is partitioned as q G G = 2 p y G 4 u G 3 where q, y, p and u represent the flow and the effort signals. Then, obtaining one representation from another is possible by a combination of the following elementary permutation and partial inversion operations such that the mapping is converted into u p y q and u q y p respectively assuming that the inverses exist in the latter. For our purposes, we consider only the immittance matrices that describe G as an input-output mapping as opposed to transmission or ABCD parameters as follows: q G G = 2 p p s q, =. y G 4 u u l y G 3 Therefore, the overall interconnection can be depicted by the block diagram given in Fig. b. n relation to teleoperation, b p u
3 PREPRNT - DO :.9/TRO v G a u v G p Fig. 2. The general interconnection a and the assumed interconnection for passive systems b. n general, the power variables require a sign change relative to the from and to ports in order to indicate the travel direction which translates to a negative sign in the block diagrams. the blocks s and l refer to the human and the unknown environment. Throughout the paper, we will not distinguish the system G from its transfer matrix Gs unless specifically stated otherwise. B. Passivity, Well posedness and Stability Let us start by recalling the key concept of passivity. Definition : Let G : L n 2 L n 2 be an operator. G is said to be passive if the following condition holds for all u L n 2 : Guτ T uτdτ = b u Ĝuiω ûiωdω. For an LT operator G, passivity is equivalent to the corresponding transfer function Gs being positive real i.e., Re {Giω} for all ω R e. Furthermore, if the condition Guτ T uτdτ δ u ɛ Gu 2 2 is satisfied with δ >, ɛ = or δ =, ɛ > then the operator is said to be strictly input output passive with level δ or level ɛ respectively. Definition 2: Consider the interconnection depicted in of compatible dimensions. This G interconnection is said to be well-posed if G s has a proper inverse. Moreover, the interconnection is said to be stable if it is well-posed and if the inverse of G s is stable. These definitions do apply to the negative feedback interconnection of G p and in Fig. 2b as well by just replacing G with G p. Theorem : [Passivity] The G p interconnection in Fig. 2a with G, RH Fig. 2b for LT systems G p, RH passive if and only if G p is strictly input passive. is stable for all Theorem 2: [Small-Gain] The G interconnection in Fig. 2a for LT systems G, RH is stable for all with if and only if G <. C. Quadratic Forms for Stability Analysis n the sequel, instead of 2-port networks, we rather consider system interconnections as depicted in Fig. 2a. n this setting, G is the model of the nominal bilateral teleoperation system and is a block diagonal collection of uncertainties, such as the human, the environment, delays, etc. Stability tests are based on structural hypotheses on the diagonal blocks of the operator such as gain bounds or passivity. These properties should allow us to develop numerically verifiable conditions for the system G that guarantee interconnection stability. This is intuitive because we have no access to the actual and we can only describe its components by means of indirect properties. Over the past three decades many classical stability results have been unified and generalized in this direction by utilizing quadratic forms see [23] and [34] [36]. t is beyond the scope of this paper to include a comprehensive treatment of the subject, but for the sake of completeness, we present the general methodology by sampling a few important special cases. To begin with, consider the following reformulation of the conditions of the small-gain theorem: iω iω G < < Giω Giω for all ω R e. The middle 2 2 matrix on the right-hand side is called the multiplier typically denoted by Π. t has been observed that the appearance of the same multiplier on both inequalities is far from a mere coincidence. n fact, it led to the following stability test: Assume that G, RH. Then, the G interconnection in Fig. 2a is well posed and stable if there exists a Hermitian matrix Π such that iω iω Π, Π Giω 2 Giω hold for all ω R e ; one only requires the mild technical hypothesis that the left-upper/right-lower block of Π is negative/positive semi-definite. Thus, the intuition that we touched upon above is mathematically formalized by 2. ndeed, one can see that the former condition constrains the family of uncertainties, while the latter provides the related condition imposed on the plant for interconnection stability, both expressed in terms of the multiplier Π. n particular, we recover the passivity theorem in a similar fashion, if using the constant symmetric matrix Π = as the multiplier under negative feedback. See [34] for a lucid topological seperation argument. Various other classical stability tests fall under this particular scenario based on the so-called static frequency-independent multipliers which, therefore, presents a significantly unified methodology. f admits a diagonal structure [as in Fig. b], it is well known that the small-gain theorem and passivity theorem are conservative. A natural generalization toward a tighter analysis test is using a frequency-dependent Π matrix, which can be interpreted as adding dynamics to the multiplier. Two prominent examples of interest are the celebrated upper bound computations for µ or κ m in robust control theory and, as we will show later, Llewellyn s stability conditions. As a shortcoming, these results are only valid for LT operators but the real power and flexibility of these multiplier methods come from their generalizations to classes of nonlinear/time-varying operators via the QC framework that appeared in [23]. An QC for the input and output signals of is expressed as viω ˆviω Πiω viω dω. 3 ˆviω
4 4 PREPRNT - DO :.9/TRO A bounded operator : L m 2 L n 2 is said to satisfy the constraint defined by Πiω if 3 holds for all v L m 2. The following sufficient stability condition for the interconnection in Fig. 2a forms the basis for the QC framework. Theorem 3 see [23]: Let G RH n m be given and let : L m 2 L n 2 be a bounded causal operator. Suppose that for every τ [, ], the interconnection of G and τ is well posed; 2 for every τ [, ], τ satisfies the QC defined by Πiω which is bounded as a function of ω R; 3 there exists some ɛ > such that Πiω ɛ for all ω R. 4 Giω Giω Then the G interconnection in Fig. 2a is stable. Remark : Note that both properties and 2 in Theorem 3 have to hold for τ if τ moves from τ = for which stability is obvious to the target value τ = for which stability is desired. n our examples the left-upper m m block the right-lower n n block of Πiω is negativepositive semi-definite for all ω R e respectively. t is then easy to see that 3 implies property 2 in Theorem 3; hence one only needs to verify 3 for the original uncertainty. 2 Often Πiω is a continuous function of ω R e. Then property 3 is equivalent to Giω Πiω Giω for all ω R e. 5 f is LT then 3 holds for all v L m 2 if and only if iω iω Πiω for all ω R. 6 The QC reduces to a frequency-domain inequality FD. This provides the link to our introductory discussion. Suppose that is LT and Πiω is a continuous function of ω R e. t is possible to show that 5 and 6 imply det Giω iω for all ω R e, 7 which is the precise condition that forms the basis of SSV theory [37]. This gives some intuition for the validity of the QC theorem and relates to µ in SSV theory. 3 n combination with the previous remarks, properties 2 and 3 imply det τg for τ [, ] which is nothing but property. Two conclusions can be drawn: On one hand, under these circumstances property is redundant in Theorem 3. On the other hand, if and 2 have been verified, it suffices to check 5 only for finite ω R in order to infer stability with the QC theorem. f we have an QC constraint that is satisfied for all with some particular uncertainty set, checking robust stability boils down to the verification of the corresponding FD 4 or 5. nstead of validating these in a frequency-by-frequency fashion, one can make use of the Kalman-Yakubovich-Popov KYP Lemma see [38] and below in order to convert the FD into a genuine linear matrix inequality LM by using state space representations. For the finite frequency intervals, one can further use the Generalized KYP Lemma [39] to limit the analysis to some physically relevant frequency band.. EQUVALENT NTEGRAL QUADRATC CONSTRANTS STABLTY TESTS FOR COMMON STABLTY ANALYSS APPROACHES n this section, we present the equivalent QC tests for some widely used results from network theory. Our main motivation is to show the underlying basic connection to the QC framework. t is revealed that the frequency-domain stability tests in the context of bilateral teleoperation can be seen as particular cases of robustness tests with suitable multipliers. This reformulation forms the basis for substantial extensions as discussed later in the paper. Subsequently, we will present proofs of sufficiency and only include some brief remarks about necessity exactness of these tests in Section -E. A. Llewellyn s Stability Criteria The well known conditions for stability of a two-port network, formulated in [8], [9], and [4], are recalled in the following theorem. An explicit indication of the frequency dependence is often omitted for notational convenience. Theorem 4 Unconditional Stability: A two-port network N, described by its transfer matrix N iω N Niω = 2 iω N 2 iω N 22 iω and interconnected to passive termination immittances, as in Fig. a, is stable if and only if and or R > or R 22 >, 8 4 R R 22 + X 2 X 2 R R 22 R 2 R 2 R 2 X 2 R 2 X 2 2 > 9 2R R 22 N 2 N 2 Re {N 2 N 2 } > 9 for all ω R e, where R ij and X ij denote the real and imaginary parts of N ij, respectively. Remark 2: n contrast to some references, this result is formulated with strict inequalities in order to guarantee L 2 -gain stability See also [, Sec. V] and [4, Thm. 6.]. As shown in [4], the conditions stated in Theorem 4 are invariant under immittance substitution. Hence, we assume that the network and the terminations are represented with an input/output mapping, as depicted in Fig. 2b. The stability conditions of Theorem 4 can be reproduced via the QC theorem as follows. f l and s are passive and stable LT systems, they satisfy l + l and s + s
5 PREPRNT - DO :.9/TRO for all ω R e. f we choose arbitrary λ ω > and λ 2 ω >, it is clear that the inequalities λ 2 l + l and λ s + s persist to hold, which can, in turn, be combined into s l λ λ 2 λ λ 2 s l. After division by λ 2 ω and with λω = λω λ 2ω, we obtain s l λ λ s l. n this fashion we have constructed a whole family of multipliers, parameterized by λω >, such that the quadratic constraint holds for all passive l, s RH. Stability of the N interconnection is then guaranteed if one can find a positive λω for which the FD λ λ N N 2 N 2 N 22 is also satisfied at each frequency ω R e negation of N results from the application of the QC theorem to the negative feedback interconnection [see Fig. 2b]. The resulting condition is equivalent to checking whether, at each frequency, there exists a λ > such that [ ] 2λR H = λn 2 N2 λn2 N 2 2R 22 holds. This leads us to the relation with the classical results. ndeed, the 2 2 matrix H is negative definite if and only if and R > or R 22 > det H = R 2 2 X 2 2 λ 2 R 2 2 X R R 22 2R 2 R 2 + 2X 2 X 2 λ >. Since the leading and constant coefficient of the involved polynomial are negative, the apex of the corresponding parabola should stay above the λ-axis. Using the apex coordinates of a concave parabola, one can show that this is equivalent to 9. Symmetry of the resulting conditions with respect to the indices is shown by simply switching the roles of λ and λ 2 in our derivation. Remark 3: n the previous FD condition and if assuming λ = over all frequencies, we also recover the Raisbeck s conditions [42]. A comparison of Raisbeck s and Llewellyn s criteria indicates that the use of frequency dependent multipliers demonstrates the possibility of a substantial decrease of conservatism in stability analysis. n fact, the difference between Llewellyn s conditions and of Raisbeck s is the use of dynamic multipliers instead of static ones. Remark 4: One should also note that Llewellyn s original conditions are both sufficient and necessary and, hence, involve no conservatism. Exactness is due to the vast generality of the uncertainties, since one just assumes that the human and the environment are represented by passive LT operators. The Nyquist curves of the corresponding positive real functions are only constrained to be lying in the closed right half-plane. n reality, however, one is rather interested in operators whose Nyquist curves are confined to a sub-region of the closed right-half plane or even to other bounded sets elsewhere in the complex plane. Covering the relevant region of interest in the complex plane with the full closed right-half plane for describing the involved uncertainty provides a clear account of the conservatism of the stability tests in teleoperation systems. Thus, if one wishes to reduce conservatism, additional structural information about the operators should be included in order to further constrain the uncertainty set see, e.g., [2], [4], [5], and [3]. t will be illustrated in Section V how this can be achieved by using conic combinations of different multipliers which express refined properties of the involved operators. B. Unconditional Stability Analysis of Three-Port Networks For the analysis of three-port networks, there exists no obvious unconditional stability result other than terminating one of the ports with a known environment model and then performing an analysis on the resulting two-port network see, e.g., [43] and references therein. Still, we can obtain the exact conditions for a three-port case in a straightforward fashion along the previously described lines without port termination. However, as expected, the test derived in this section is more conservative than those of port-termination based methods, since the additional information about the model with which the port is terminated renders the uncertainty set significantly smaller. f compared to the previous section, the only modification is to take a system representation N RH 3 3 and three passive uncertainty blocks living in RH which are collected as iω = diag iω, 2 iω, 3 iω 2 in order to model the three port terminations. With Λiω = diag λ ω, λ 2 ω, λ 3 ω 3 we obtain the following quadratic constraint: Λ Λ which reflects passivity of the three sub-blocks. The corresponding FD for guaranteeing stability reads as Λ. 4 N Λ N Theorem 5 Llewellyn s Three-Port Criteria: A network, which is represented by its 3 3 transfer function N RH 3 3 and interconnected to the stable, passive and block diagonal as given in 2 is stable if and only if there exists a structured Λ with 3 such that 4 holds for all ω R e. Exact conditions for unconditional stability could be obtained from 4 by symbolic computations. However, getting
6 6 PREPRNT - DO :.9/TRO formulas similar to those in 8, 9 would lead to quite cumbersome expressions see, e.g., [44],[45], and [43]. Moreover, variants of expressing negative definiteness would result in different formulations of the stability conditions in terms of scalar inequalities. n the QC formulation this is completely avoided while it is still possible to easily verify the resulting conditions numerically. e sτ s Z ms+b s C. Rollett s Stability Condition Similarly, as is for Llewellyn s stability conditions, it is straightforward to derive unconditional stability tests if the network is represented by scattering parameters. n what follows, we denote transformed passive LT uncertainties with s, l which are unity gain bounded. The corresponding interconnection is supposed to be given by the loop equations q = Sp, p = q i.e., q = q 2 q S S 2 S 2 S 22 S p, p 2 p p s = p 2 l q q 2. 5 Rollett s conditions [46],[4], and [47] for stability are then formulated as follows: The inequality K = + 2 S 2 S S 2 S 2 > 6 holds for all frequencies together with an auxiliary condition in terms of = S S 22 S 2 S 2. This extra condition can be stated in at least five different ways, such as S 2 > S 2 S 2 or S 22 2 > S 2 S 2. See [48] for further details. With almost identical arguments as for Llewellyn s test, one derives the following quadratic constraints for positive λ and for stable LT systems l and s whose gains are bounded by one: s l λ λ s l. nterconnection stability is then assured if one can find a positive frequency dependent λ for which the FD λ S S 2 S 2 S 22 λ S S 2 S 2 S 22 7 or, equivalently, [ S2 2 + λ S H = 2 ] S 22 S2 + λs 2 S S22S 2 + λs2s S λ S 2 2 holds for all ω R e. Then, it is elementary to express H by det H > and by negativity of the diagonal entries of H for all ω R e. Positivity of the determinant of H means S 22 2 S λ S 2 2 λ 2 S 2 2 >. Hz Fig. 3. The teleoperation setup from [6] Unilateral Constraint f this is expressed as fλ = aλ 2 + bλ c > with b a, c >, we require the apex coordinates 2a, b2 4ac 4a both to be positive. Since a >, we have + 2 S 22 2 S 2 2 > 4 S 2 S due to b 2 > 4ac. Moreover, negativity of the diagonal terms is expressed as λ S 2 > S 2 2 or S 22 2 > λ S To make the connection to the classical auxiliary conditions, observe that evaluating fλ at λ = c a = S 2 would lead S 2 to the condition b > since fλ = b c a 2c >. Hence, 9 becomes S 2 > S 2 S 2 or S 22 2 > S 2 S 2. 2 n the literature, the quantity λ is called the maximum stable power gain. Finally, after explicitly including the condition b >, one can take the square root of 8 and obtain + 2 S 22 2 S 2 > 2 S 2 S 2, which is precisely Rollett s first condition. There has been quite some discussion in various studies see, e.g., [48] [5] whether testing both conditions in 2 is really required, while it rolls out from our FD arguments that one of these auxiliary inequalities is sufficient. n fact, 7 renders this discussion obsolete since we deal with a single matrix inequality to be tested at each frequency. This test is equivalent to the one based on the Edwards-Sinsky stability parameter µ see [48] in the sense that only one condition needs to be verified. Alternatively, one can perform a symbolic computation of the largest eigenvalue of H and search for a positive λ that renders that quantity strictly negative. Recently, the µ parameter has been used in the context of teleoperation in [4] and their results can also be recovered by using multipliers similar to the ones given in the next section. D. Colgate s Minimum Damping Condition n this section, the analysis problem from [7] and [8] is investigated by QCs. n this example, the master device is modeled as /ms + b and is combined with a passive T
7 PREPRNT - DO :.9/TRO operator impedance Z s as shown in Fig. 3. We limit the analysis to the situation without the unilateral constraint. The overall operator and master device transfer function reads as s = /ms + b + Z s. Since Z s is passive and b is positive, the Nyquist curve of s is confined to the halfplane {z C : Re {z} b} and s is strictly input passive with parameter b. n [7], the problem is converted to the small gain theorem with a geometric reasoning. n our setting, passivity is expressed as 2b iω iω which is clearly equivalent to iω 2b iω for all ω R e. The FD guaranteeing stability then reads as 2b < G d iω G d iω for all ω R e. Using the closed-form formula in [7], G d iω = T 2 e iωt cos ωt HeiωT, this directly leads to Colgate s original condition: 2b G diω G d iω < b > T 2 cos ωt Re { e iωt He iωt }. The employed multiplier can be transformed into the one for the small-gain theorem along the following lines: iω 2b iω 2b [ 2b T ] = 2b iω = 2b iω 2b iω. This links our arguments to those appearing in [7] and [8] and reveals that the direct application of tools from robust control allows to circumvent any transformation to scattering parameters or, in other words, the application of a loop transformation for obtaining the stability conditions. n fact, the congruence transformation 2b b b T 2b b b = with the scattering transformation matrix turns the small-gain multiplier into the one for passivity. This observation allows to easily show the equivalence of the small gain and passivity theorems through scattering transformations [4] and wave variable methods see [5] and [52]. E. Exactness of Robustness Tests As mentioned before, QC-based stability criteria are typically only sufficient. Still the classical conditions as discussed above turn out to be also necessary. Necessity of these criteria can as well be seen to be a specialization of celebrated exactness results in structured singular-value theory. n fact, QC tests for structured LT uncertainties with two or three full diagonal blocks as derived above are known to be always exact. This implies, in particular, that the three-port counterpart of Llewellyn s conditions is indeed a necessary and sufficient test for stability. t is far beyond the scope of this paper to provide all possible cases in which QC-based robustness tests are known to be exact. For a detailed discussion related to LT uncertainties, see [37],[53], amd [54]. We would like to emphasize that these beautiful exactness properties come at the price of some limitations of the classical framework. For instance, Llewellyn s conditions are not sufficient for stability any more if we only assume that the uncertainties are passive but not necessarily LT. On the other hand, if allowing for arbitrary causal and passive uncertainties, stability is still guaranteed if we can find a frequency-independent λ > which renders the FD satisfied, and this property can be easily verified numerically. V. BASC QC MULTPLER CLASSES n the previous section, we have shown how classical frequency-domain techniques can be embedded into the QC formulation. n this section, we focus on the types of existing multipliers for different uncertainty classes. Although they frequently appear in the robust control literature, we include them for completeness. A. Parametrized Passivity Another well-known version of the passivity theorem, which we will denote as theorem of parameterized passivity see, e.g., [55, Thm. V.5.], allows to consider cases in which the nonpassivity of some block is compensated by an excess of passivity in other blocks without endangering stability. This can even be utilized to determine the lowest tolerable level of passivity of the uncertainties for which a given interconnection remains stable. For output strictly passive uncertainties, stability can be characterized as in the next result, which is a direct consequence of the general QC theorem. Corollary : The interconnection of G p, RH as in Fig. 2b is stable if there exist a p such that iω p iω 2 G p iω p G p iω hold for all ω R e. Remark 5: Note that 2 and 22 are nothing but 22 iω + iω p iω iω, 23 G p iω + G piω p. 24
8 8 PREPRNT - DO :.9/TRO m p Re Fig. 4. As p increases, the admissible region for the Nyquist curves of shrinks to smaller disks in the right half plane. The case p = recovers the classical passivity theorem. Moreover, the larger the value of p >, the smaller is the set of uncertainties described by 23, as illustrated in Fig. 4 for different values of p. n fact, this result is used in Colgate s condition thanks to the damping term b and closely related to the impedance bounds of Bounded mpedance Absolute Stability [4] using impedance circles. B. Real Parametric Uncertainties n many applications, the uncertainties originate from the lack of the precision on the actual values of the parameters in the system model. This applies in particular to the models used in bilateral teleoperation. Parameters such as the stiffness and the damping of the environment or the human arm are the simplest examples of this kind. After rescaling and shifting, the real parametric uncertainties are assumed to take values in the interval [ r, r] centered around the nominal value zero. Linear Time-nvariant Uncertain Parameters: The wellknown DG multiplier family see [56] and [53] is used to assess robustness against unknown but constant parameters. n fact, for all bounded functions D : R, and G : R ir one has δ Dω Gω δ G ω r 2 Dω for all δ [ r, r], just because it reads as Dω δ 2 + r 2 Dω + Gω + Gωδ ; this holds since δ 2 r 2, Dω > and Gω + Gω =. 2 Time-Varying Parameters With Arbitrary Rate-of- Variation: n this case we employ constant multipliers; the time-varying parameter δ : [, [ r, r] satisfies the quadratic constraint δt D ig δt ig r 2 D for all D >, G R and for all t. This implies the validity of 3 for the multiplication operator which maps v L n 2 into w L n 2 with wt = δtvt. 3 Time-Varying Parameters With Bounded Rate-of- Variation: f there is a known bound on the rate-of-variation ROV of the time-varying parameter, it is conservative to use constant DG scalings. To characterize slowly-varying real parametric uncertainties, we use the so-called swapping lemma see [57] [59], cf. [6], which allows us to take the ROV bound explicitly into account. For the sake of completeness, we include a scalar version of this well known result from adaptive control. Lemma Swapping Lemma: Consider the bounded and differentiable function δ : [, R whose derivative is bounded as δt d for all t. Moreover, let T s = Cs A B + D be a transfer function with a stable statespace realization and define T c s := Cs A, T b s := s A B. f viewing T, T c, T b and δ by point-wise multiplication as operators L 2 L 2, one has δt = T δ + T c δtb and thus T Tc δ δ T = δt b δ Tb }{{}}{{}}{{}}{{} T left s x T right where x, s stand for extended and Stacked respectively. We now claim that Πiω = Tleft iω Ms T right iω with D a ig a M s = D b ig b ig a r 2 D a ig b d 2 D b for T D a T >, D b >, and G a, G b R is a valid QC multiplier for the uncertainty s. n fact, one easily verifies T x t x t M s for all t in the time domain. f we choose any v L 2 and define w = x Tright v, we hence infer wt T M s wt dt. On the other hand, due to Lemma, we also have δ Tleft w = s Tleft v = δt T right T b right which proves the claim. Thus, after augmenting the corresponding channel with zero columns to make the plant compatible with s, the robustness test can be performed. C. Delay Uncertainty The delay robustness problem has been studied extensively and the dominating approach is the use of scattering transformations/wave variable techniques, among other methods see [4], [5], [7], [9], [52], and [6] [67]. We refer to the survey article [7] for a detailed exposition of these methods. A great deal of research has been devoted to delay robustness tests in robust control that are applicable to a wide class of teleoperation systems. We also refer to [68] for a general treatment of the subject e.g., based on Lyapunov-Krasovskii functionals and to QC based results as, e.g., in [69] [72]. Here, we consider constant but uncertain delays and the maximum delay duration is bounded from above by τ > s.
9 PREPRNT - DO :.9/TRO G e sτ G a Magnitude [abs] Frequency [Hz] b e.2s Fig. 5. a Rewriting the interconnection such that τ = implies =. b Frequency domain covering of the shifted delay operator. We emphasize that it requires only a simple modification of the multiplier in order to arrive at robustness tests for different types of delays, as reported in the literature. f using the uncertainty s = e sτ in the configuration of Fig. 2a, the nominal value τ = leads to s = and not to zero, as desired. This is resolved by utilizing the shifted uncertainty s = e sτ and correspondingly modifying the system to G by unity feedback around G as in Fig. 5a and without modifying the interconnection cf., [9]. The uncertainty is then characterized by using two properties of : For all ω, τ, the complex number z = e iωτ is located on the unit circle centered at, in the complex plane. Since condition z + = translates into z z + z + z =, we infer for all bounded Ω : R R that iω Ωω Ωω Ωω iω Wd = ω R 25 for any delay time τ R. Furthermore, we need to take the low frequency property of the magnitude of the frequency response into account. This is typically captured by a frequencydependent weight. f we define s + 4 π τ s + β τ W d s = 2 s π 2 τ eiθ s π 2 τ e iθ with θ = π 2 2 and some small β >, then Wd covers the delay uncertainty in the sense that iω W iω for all ω R and for all τ [, τ]. An example of magnitude covering is shown in Fig. 5b. This property, in turn, translates into Wd W d for all ω R. Then, we can utilize the classical D-scalings to obtain the following constraint with a dynamic multiplier: Dω iω W d iω DωW d iω 26 for all bounded D : R,. Then the overall multiplier family results from a conic combination of 25 and 26: D + Ω Ω Ω Wd DW ω R d e V. NUMERCAL CASE STUDES n this section, we show how frequently encountered analysis problems can be solved under the QC formulation. We utilize the multipliers as given above for robustness tests applied to a simple teleoperation system taken from [5] and [73]. Our main emphasis is on showing how one can reproduce the numerical results of such frequency-domain techniques and, as the key contribution of this paper, how it is possible to substantially widen the range of allowed uncertainties in the QC framework for which no classical analytical stability tests exist. This serves as an illustration for the possibility to improve analysis and, more importantly in future work, optimization-based controller synthesis results if better human/environment models become available. A. Algorithmic Verification We have discussed some classical stability tests that reduce to explicit scalar inequalities, which can be verified in a frequency-by-frequency fashion. n contrast, the equivalent reformulations in terms of QCs open the way to verifying these conditions numerically, by applying algorithms from the by now well-established area of semi-definite programming [74]. For example, checking at each frequency the existence of some diagonal Λ which satisfies 4 boils down to an efficiently tractable LM problem in the three diagonal entries of Λ, which can be readily implemented in software environments such as [75]. We also show how it is even possible to avoid any frequency gridding and to reduce the tests to finite-dimensional semidefinite programming problems that can be solved in one shot. This section serves to illustrate this procedure for Rollett s stability condition, which requires the determination of a frequency-dependent, bounded, and strictly positive λ satisfying the FD 7. Without loss of generality, it suffices to search for proper and rational functions λ that have no poles and are positive on the extended imaginary axis. Thanks to the wellestablished spectral factorization theorem see, e.g., [76], we can express any such function as ψ ψ with some stable transfer function ψ without zeros in the closed right half-plane. For some fixed pole a <, let us choose the basis vectors Φ n s = s a T s a 2 s a n for n =,, 2,.... By a well-known fact from approximation theory see [77], the function ψ can be approximated to an arbitrary degree by L T Φ n for some suitable L R n uniformly on the imaginary axis, if only n is taken sufficiently large. More precisely, inf L R n ψ L T Φ n converges to zero for n. n summary, any proper rational λ with λiω > for ω R e can be approximated arbitrarily closely by Φ nll T Φ n or, in turn, by Φ ndφ n with D = D T R n n. This discussion justifies why one can parameterize the multiplier middle term in 7 as Ψ n D Φ n D Φ n }{{}}{{} M Ψ n in terms of a frequency-dependent outer factor Ψ n and a diagonally structured real symmetric matrix M in the middle. Let us denote the set of all these matrices M by M dropping
10 PREPRNT - DO :.9/TRO the dependence on n. For checking Rollet s condition we then need to verify the existence of M M such that the FDs Φ ndφ n > and Ψ S nmψ n S are satisfied. We include the classical result see [38] that allows us to convert these frequency domain inequalities into LMs. ] Theorem 6 KYP Lemma: Let G = and suppose that [ A B C D A has no eigenvalues on the imaginary axis. For a real matrix P = P T, the following two statements are equivalent. The following FD holds: Giω P Giω ω R e There exists a symmetric matrix X with T X A B X A B. 28 C D P C D Now choose the minimal state space realizations [ ] [ AΦ B Φ n = Φ A B and Ψ n = S C D C Φ D Φ This allows us to apply the KYP Lemma in order to equivalently convert λ > and 7 into the feasibility of the LMs T Z A Φ B Φ Z A Φ B Φ 29 D and C Φ D Φ A B C D T C Φ D Φ ]. X X A B. 3 M C D More precisely, if one can computationally verify the existence of X, Z, M M and D = D T which satisfy 29 and 3, we have verified Rollet s condition. Conversely, if Rollet s condition holds, then these LMs are guaranteed to have solutions if n is chosen sufficiently large. Let us emphasize again that the very same procedure applies to considerably more complex interconnections and structured uncertainties. n fact, for many interesting classes of uncertainties, one can systematically construct multiplier families see, e.g., [23] which are known to admit a description of the form Π = Ψ MΨ, M M with a stable outer factor transfer matrix Ψ and with some set of structured symmetric matrices M that can itself be described as the feasible set of an LM. Checking stability of the G interconnection in Fig. 2a then requires to verify the validity of the FD Ψ MΨ. G G Literally along the same lines as described previously, this is translated into a semi-definite program with Theorem 6. Remark 6: n our numerical examples the basis length n is chosen large enough that the performance level does not significantly change by further increasing n. As shown below, the required length n for adequate accuracy in the multipler Fig. 6. h e Y Y 2 Y 2 Y 22 a Unconditional Stability h δ e Y Y 2 Y 2 Y 22 b Uncertain stiff environment System interconnections for Section V-C and Section V-D. approximation is regardless of the conservatism of the test often quite small in practice. n what follows, we will continue to utilize the shorthand notation of state-space realizations in a similar manner, i.e., A, B, C, D for the combined outer factors by replacing S with the respective plant, and A Φ, B Φ, C Φ, D Φ for the basis vector. B. System Model n [73], a simple teleoperation system described with the following equations is considered: F h + τ m = M m ẍ m + B m ẋ m τ s F e = M s ẍ s + B s ẋ s. Here M m, M s are the masses, B m, B s are the damping coefficients, τ m, τ s are the device motor torques, and x m, x s are the position coordinates of the local and the remote devices, respectively. F h, F e denote the human and the environment forces. The human and the environment are assumed to be LT passive operators and are denoted by h, e, which substitute s, l as employed in the more general network-related context in the earlier sections. Additionally, a particular PD type of a position-force controller scheme, denoted by P-F, is used: τ s = K p µx m x s K v ẋ s, τ m = K f F e. The overall teleoperation system is then described, with µk Y m s = /M m s + B m and Y s s = p M ss 2 +B s+k vs+k p, in terms of the following admittance matrix: Ym K f Y m Y =. 3 Y m Y s M ms 2 +B ms+µk f K p M ss 2 +B s+k vs+k p Y m As shown in [73], the system s performance is related to the transparency of the teleoperator, which is characterized by the maximal attainable product µk f while maintaining stability see also [78]. We will evaluate our results with respect to this performance measure. For all computations, we have used [75], [79], [8] with MATLAB 7.2. on a computer with a 2.4 GHz processor and with 4 GB RAM memory running Win 7-64 Bit OS. The system parameters are M m =.64, M s =.6, B m =.64, B s =, K v = 87.8, K p = 4. C. Case : Unconditional Stability Analysis via ntegral Quadratic Constraints We start with applying Llewellyn s test based on to the system given above. n a first computation, we choose a frequency grid of 2 logarithmically spaced points in
11 PREPRNT - DO :.9/TRO [, ]rad/s and solve, at each grid point, a feasibility problem in λ >. This is incorporated into a bisection algorithm that searches for the maximum value of µk f for which feasibility at each grid-point can be guaranteed. Due to gridding, this method typically gives an upper bound rather than the exact value on the guaranteed performance level, just because there is a chance to miss critical frequencies. Nevertheless, we obtained the exact value.37 as in [73]. The inner search for λ requires 8.52 s, while the overall computation takes about 7 s; note that the latter heavily depends on the initial bisection interval and on the desired accuracy. n a second computation, we follow the path as described in Section V-A. The resulting FD is where Ψ Y M Ψ 32 Y Φ M Ψ = Φ, M = M 33 with some unstructured real symmetric matrix M. Corollary 2: The Y interconnection depicted in Fig. 6a is stable for all passive blocks h and e if there exist symmetric matrices X, Z, M such that T X A B X A B C D M C D A Φ C Φ B Φ D Φ T Z Z M. A Φ C Φ B Φ D Φ We applied Corollary 2 with a basis of length n = 8 and with the pole a = 7. n this way, we computed again the maximal value µk f.37 for which stability can be guaranteed in about 36 s. Remark 7: Since Y is strictly proper, 32 cannot be satisfied at ω = because its left-hand side vanishes. However, the interconnection is certainly well posed such that the FD only needs to be verified for all finite frequencies Remark. Therefore, the gridding approach can be applied directly. n the alternative path without gridding, we can circumvent this trouble by replacing Y with Y + ɛ, with ɛ = 5 in our case. Let us stress that this perturbation also in the cases presented below is only required in those channels that are related to passive uncertainties. D. Case 2: Stability With Uncertain Stiff Environments We characterize the admissible environments as pure springs modeled by Z e = k/s with an uncertain constant stiffness coefficient k [, k] N/m. After merging k/s with the system and slightly perturbing the pole of the integrator to render the nominal system stable, we are left with the uncertainty structure = diag h, δ e where the human uncertainty is assumed to be passive LT and δ e is an uncertain real scalar parameter in the interval [, ]. Using a modified DG-scaling for the shifted parameter range, we can easily adapt the multiplier and obtain, next to λ > and d >, the following FD for interconnection stability: λ d d 2 + ig λ d 2 ig Y Y 2 Y 2 Y With the frequency grid as in the previous case we obtained too optimistic results after comparing the values with those computed below, which suggests the need to refine the grid. With additional 5 points in the interval [ 6, ] rad s, we obtained the exact value of µk f max.25 for k = N/m in 27.7 s. We infer that the grid resolution, whether logarithmic or linear, plays a crucial role for the computations. This reveals that, especially for systems that have high bandwidth and complex dynamics, it is instrumental to choose a sufficiently fine frequency grid in stability analysis. This is the very reason for the alternative path of computations via multiplier parametrization and LMs in state-space, as proposed above. n this particular example, the resulting condition boils down to two simple LMs to be verified numerically. After normalizing the environment uncertainty by scaling, we just need to verify feasibility of the LMs in the next result. Corollary 3: The Y interconnection in Fig. 6b is stable for all passive LT h and LT real parametric uncertainty δ e [, ] if there exist symmetric matrices X, Z 2, D 2 and a skew symmetric matrix G 2 such that A B C D A Φ C Φ B Φ D Φ X X A B, M C D T Z 2 Z 2 A Φ B Φ D 2 C Φ D Φ T hold, where M = D 2 2 D 2 + G 2, Ψ = Φ 2. 2 D 2 G 2 Φ 2 For this example we have used the basis Φ 2 with length 2 and selected the pole a = 6. Bisection over µk f took 29.3 s and the resulting maximum admissible value is found to be.25 for a sample value of k =. Values higher than.25 would render the nominal system unstable, which means that we obtain the best possible result. The performance curve for different values of k is given in Fig. 7. E. Case 3: Robustness Against Delays We reconsider the plant given in 3 and modify it in order to relate the results to the undelayed cases given above. We assume that there exist communication delays present in the forward and backward path and, without loss of generality, we
12 2 PREPRNT - DO :.9/TRO µkf k [N/m] Fig. 7. Performance loss for increasing environment stiffness uncertainty. The dashed line shows the value for unconditional stability from Section V-C. This test has been applied for various maximum delay durations τ [.,.] s with.5 s increments and the results are shown in Fig. 8. At each τ point, the bisection algorithm took on average s varying in [435,4] s. The basis lengths and the pole locations are selected as n i = 3, 3, 3, 3, 5, 5 and a i = 6, 7, 9, 8, 3, 4, respectively. The pole locations are selected away from the system s poles but arbitrary otherwise. choose both maximally allowed delay durations to be equal for simplicity. We thus consider Y m K f Y m e sτ Y = Y m Y s µk p e sτ M ms 2 +B ms+µk f K pe 2sτ M ss 2 +B s+k vs+k pm ms+b m where τ [, τ]. By pulling out the delay uncertainties from Y, the nominal plant Y d is given by Y m Y m Y d = sy s K p Y s K f µy m µy m and is interconnected to the structured uncertainty block = diag h, e, e sτ, e sτ. n accordance with Section V-C, a unity feedback is applied and two delay weights are included in the plant. Corollary 4: The Y d interconnection is stable for all passive LT h, e, and LT delay uncertainties if there exist symmetric matrices X, M, M 2, D 3, D 4, R 3, R 4 and Z i for i =,..., 4 such that T X A B X A B C D P C D and A i Φ CΦ i Bi Φ Di Φ T Z i Z i A i Φ Bi Φ Υ i C i Φ Di Φ hold where Υ = M, Υ 2 = M 2, Υ 3 = D 3, Υ 4 = D 4, P = diag,, D 3, R 3, D 4, R 4, P P P = 2 P2 T, P P 2 = diag M, M 2,, R 3,, R 4, 22 P 22 = diag,, D 3,, D 4, and Ψ = Φ Φ 2 Φ 3 Φ 5 Φ 4 Φ 6 Φ Φ 2 Φ 3 W d Φ 5 Φ 4 W d Φ 6. F. Additional Remarks n concluding this section, we would like to address the issue of conservatism in our numerical examples. The first two cases involve none at all for sufficiently long basis functions as confirmed numerically. f considering only passive LT uncertainties in standard problems, there is no room for further algorithmic improvements, since the resulting tests are guaranteed to be exact. On the other hand, there is a huge potential in searching for refined uncertainty characterizations in order to reduce conservatism. We have illustrated that there is no need to confine the analysis to passive uncertainties as long as they can be associated with some QC, possibly through some physical experiments see, e.g., [8] for a parametric uncertainty case which can be improved directly using the multipliers given above. Thus, once QCs are known for individual uncertainty blocks, it has been also demonstrated how to computationally verify robust stability against their combined influence on the interconnection with ease. On the other hand, this might not be the case for the test in Corollary 4. To quantify the potential conservatism, we use extreme values for the stiff environment and the delay uncertainty and determine the maximum achievable values of µk f for which the transfer function seen by the human is still strictly passive. Environments that are modeled as pure stiffnesses are considered to be worst cases since their Nyquist curves are located at the boundary of the closed right half plane and since their low frequency contribution, unlike pure mass models, is significant. As shown in Fig. 9, the performance decreases for increasing levels of τ and k, but the tradeoff curve does not change significantly beyond the value k = N/m. We have also overlayed the results of Fig. 8. f it is indeed true that a pure stiffness environment is the worst case, then the difference between the two lowest curves in Fig. 9 can be attributed to the conservatism of the test in Corollary 4. Thus, we can conclude that the conservatism is not very large; this is of particular significance for delay-independent robust stability tests which would result in values in the range of µk f 5. Let us briefly compare with results obtained for time-varying environments. This makes a particularly interesting case, since, in practice, a remote device might explore environments with varying characteristics. We have analyzed the nondelayed system where the environment is a pure spring with a stiffness coefficient kt [, ] N/m and different bounds on the ROV, as shown in Fig.. Classical absolute stability tests can only handle arbitrary fast variations which leads to small values of performance of 2 5. The inclusion of information about the ROV as possible through the class of multipliers
13 PREPRNT - DO :.9/TRO Fig. 8. Lower bound on µkf τ [s] Performance loss for increasing maximal delay duration. µkf τ [s] Fig. 8 Fig. 9. Robust performance for different stiff environment cases in the face of increasing delay uncertainty duration. discussed previously substantially reduces the conservatism as is visible in the plot. We include a final remark about the performance criterion. n the literature, one often encounters PD-based controller architectures which makes it possible to analyze the effect of variations in the controller gains onto the performance of the teleoperation system. n our set-up, we can attribute the increase of performance to the increase of µk f due to the simplicity of the system structure. f moving towards more complicated controller architectures, such clear relations are not expected to be valid any more. This precludes obtaining graphical or analytical stability and performance tests with robustness guarantees. Although not made explicit for reasons of space, the QC framework allows the incorporation of a performance channel and to develop robust performance analysis tests, very much along the same lines as discussed for stability in this paper. Such formulations of the performance problems make it convenient to compare different PD controllers. n conjunction with robust performance analysis, we can further utilize robust controller synthesis methods with dynamic QCs, as recently developed in [82] and [83]. n [82], a general class of robust synthesis problems has been identified, which can be handled by convex optimization techniques. The wellknown µ-synthesis algorithm, based on the so-called D/Kiteration, has been extended to general dynamic QCs in [83] for problems that do not admit a convex formulation. n addition to robustness analysis for existing PD controllers, this opens the way for model based controller synthesis in future work. V. CONCLUSONS n this paper, we advocate the application of the QC framework to achieve refined analysis results and to highlight the µkf max kt [N/ms] t Fig.. The performance loss with respect to the increase in ROV bound of the time-varying uncertaint parameter kt [, ]N/m. need for models tailored towards bilateral teleoperation. For this purpose, we have provided a number of theoretical and numerical analysis examples, all of which are special cases of the QC theorem. We emphasize the link between contemporary and celebrated classical analysis results in the literature and reveal how to obtain substantial generalizations. Our examples show that the quality of the characterization of uncertainties is the key for improved analysis results. We strongly believe that the proposed framework together with task dependent human and environment models would lead to substantial improvements for both stability analysis and model-based controller synthesis. REFERENCES [] D. Lawrence, Stability and transparency in bilateral teleoperation, EEE Transactions on Robotics and Automation, vol. 9, no. 5, pp , 992. [2] B. Hannaford, A design framework for teleoperators with kinesthetic feedback, EEE Transactions on Robotics and Automation, vol. 5, no. 4, pp , 989. [3] R. Adams and B. Hannaford, Stable haptic interaction with virtual environments, EEE Transactions on Robotics and Automation, vol. 5, no. 3, pp , 999. [4] R. Anderson and M. Spong, Bilateral control of teleoperators with time delay, EEE Transactions on Automatic Control, vol. 34, no. 5, pp , 989. [5] G. Niemeyer and J. J. Slotine, Stable adaptive teleoperation, EEE Journal of Oceanic Engineering, vol. 6, no., pp , 99. [6] Y. Yokokohji and T. Yoshikawa, Bilateral control of master-slave manipulators for ideal kinesthetic coupling-formulation and experiment, EEE Transactions on Robotics and Automation, vol., no. 5, pp , 994. [7] P. F. Hokayem and M. W. Spong, Bilateral teleoperation: An historical survey, Automatica, vol. 42, no. 2, pp , 26. [8] F. B. Llewellyn, Some fundamental properties of transmission systems, Proceedings of the RE, vol. 4, no. 3, pp , 952. [9] E. F. Bolinder, Survey of some properties of linear networks, RE Transactions on Circuit Theory, vol. 4, no. 3, pp. 7 78, 957. [] J.-H. Ryu, D.-S. Kwon, and B. Hannaford, Stability guaranteed control: time domain passivity approach, EEE Transactions on Control Systems Technology, vol. 2, no. 6, pp , 24. [] R. Adams and B. Hannaford, Control law design for haptic interfaces to virtual reality, EEE Transactions on Control Systems Technology, vol., no., pp. 3 3, 22. [2] H. C. Cho and J. H. Park, mpedance control with variable damping for bilateral teleoperation under time delay, JSME nternational Journal Series C Mechanical Systems, Machine Elements and Manufacturing, vol. 48, no. 4, pp , 25. [3] A. Peer and M. Buss, Robust stability analysis of a bilateral teleoperation system using the parameter space approach, in Proc. EEE/RSJ nt. Conf. ntelligent Robots and Systems ROS 28, 28, pp [4] A. Haddadi and K. Hashtrudi-Zaad, Bounded-impedance absolute stability of bilateral teleoperation control systems, EEE Transactions on Haptics, vol. 3, pp. 5 27, 29. [5] B. Willaert, B. Corteville, D. Reynaerts, H. Van Brussel, and E. B. Vander Poorten, A mechatronic analysis of the classical position-force controller based on bounded environment passivity, The nternational Journal of Robotics Research, vol. 3, no. 4, pp , 2.
14 4 PREPRNT - DO :.9/TRO [6] J. Colgate, Robust impedance shaping telemanipulation, EEE Transactions on Robotics and Automation, vol. 9, no. 4, pp , 993. [7] J. Colgate and G. Schenkel, Passivity of a class of sampled-data systems: Application to haptic interfaces, Journal of Robotic Systems, vol. 4, no., pp , 997. [8] J. E. Colgate, Coordinate transformations and logical operations for minimizing conservativeness in coupled stability criteria, Journal of Dynamic Systems, Measurement, and Control, vol. 6, no. 4, pp , 994. [9] G. Leung, B. Francis, and J. Apkarian, Bilateral controller for teleoperators with time delay via µ-synthesis, EEE Transactions on Robotics and Automation, vol., no., pp. 5 6, 995. [2] H. Kazerooni, T.-. Tsay, and K. Hollerbach, A controller design framework for telerobotic systems, EEE Transactions on Control Systems Technology, vol., no., pp. 5 62, 993. [2] Z. Hu, S. Salcudean, and P. Loewen, Robust controller design for teleoperation systems, in EEE nternational Conference on Systems, Man and Cybernetics, vol. 3, 995, pp [22] C. Andriot and R. Fournier, Bilateral control of teleoperators with flexible joints by the h approach, in Telemanipulator Technology, H. Das, Ed., vol. 833, no.. SPE, 993, pp [23] A. Megretski and A. Rantzer, System analysis via integral quadratic constraints, EEE Transactions on Automatic Control, vol. 42, no. 6, pp , 997. [24] E. Van der Poorten, T. Kanno, and Y. Yokokohji, Robust variablescale bilateral control for micro teleoperation, in EEE nternational Conference on Robotics and Automation, CRA, 28, pp [25] M. Boukhnifer, A. Ferreira, and J. Fontaine, Loop shaping robust control for scaled teleoperation system, in 44th EEE Conference on Decision and Control and European Control Conference. CDC-ECC, 25, pp [26] P. Naghshtabrizi and J. Hespanha, Designing transparent stabilizing haptic controllers, in American Control Conference, 26, 26, pp [27] K. Kim, M. C. Çavuşoğlu, and W. K. Chung, Quantitative comparison of bilateral teleoperation systems using µ-synthesis, EEE Transactions on Robotics, vol. 23, no. 4, pp , 27. [28] İ. Polat, Stability analysis of bilateral teleoperation systems with timevarying environments, in American Control Conference ACC, 2, 2, pp [29], A note on passivity based stability conditions for bilateral teleoperation, in Proceedings of 8th FAC World Congress, Milano, 2. [3], An QC formulation of stability analysis for bilateral teleoperation systems with time delays, in Proceedings of EEE World Haptics Conference, WHC, 2, pp [3] K. Hashtrudi-Zaad and S. E. Salcudean, Analysis of Control Architectures for Teleoperation Systems with mpedance/admittance Master and Slave Manipulators, The nternational Journal of Robotics Research, vol. 2, no. 6, pp , 2. [32] E. J. Rodríguez-Seda, D. Lee, and M. W. Spong, Experimental comparison study of control architectures for bilateral teleoperators, EEE Transactions on Robotics, vol. 25, no. 6, pp , 29. [33] J. W. Polderman and J. C. Willems, ntroduction to Mathematical Systems Theory: A behavioral approach, ser. Texts n Applied Mathematics. Springer New York, 998, vol. 26. [34] M. G. Safonov, Stability and Robustness of Multivariable Feedback Systems. MT Press, Cambridge, MA, 98. [35] C. W. Scherer, LPV control and full block multipliers, Automatica, vol. 37, no. 3, pp , 2. [36] T. wasaki and S. Hara, Well-posedness of feedback systems: insights into exact robustness analysis and approximate computations, EEE Transactions on Automatic Control, vol. 43, no. 5, pp , 998. [37] A. Packard and J. Doyle, The complex structured singular value, Automatica, vol. 29, no., pp. 7 9, 993. [38] A. Rantzer, On the Kalman Yakubovich Popov lemma, Systems & Control Letters, vol. 28, no., pp. 7, 996. [39] T. wasaki and S. Hara, Generalized kyp lemma: unified frequency domain inequalities with design applications, EEE Transactions on Automatic Control, vol. 5, no., pp. 4 59, 25. [4] J. Rollett, Stability and power-gain invariants of linear twoports, RE Transactions on Circuit Theory, vol. 9, no., pp , 962. [4] H. K. Khalil, Nonlinear Systems, 3rd ed. Prentice Hall, 22. [42] G. Raisbeck, A definition of passive linear networks in terms of time and energy, Journal of Applied Physics, vol. 25, no. 2, pp. 5 54, 954. [43] B. Khademian and K. Hashtrudi-Zaad, Unconditional stability analysis of dual-user teleoperation systems, in Proceedings of EEE Haptics Symposium, 2, pp [44] R.-F. Kuo and T.-H. Chu, Unconditional stability boundaries of a threeport network, EEE Transactions on Microwave Theory and Techniques, vol. 58, no. 2, pp , 2. [45] E. L. Tan, Simplified graphical analysis of linear three-port stability, EE Proceedings Microwaves, Antennas and Propagation, vol. 52, no. 4, pp , 25. [46] A. P. Stern, Stability and power gain of tuned transistor amplifiers, Proceedings of the RE, vol. 45, no. 3, pp , 957. [47] K. Kurokawa, Power waves and scattering matrix, EEE Transactions on Microwave Theory and Techniques, vol. 3, no. 3, pp , 965. [48] M. Edwards and J. Sinsky, A new criterion for linear 2-port stability using a single geometrically derived parameter, EEE Transactions on Microwave Theory and Techniques, vol. 4, no. 2, pp , 992. [49] G. Lombardi and B. Neri, Criteria for the evaluation of unconditional stability of microwave linear two-ports: a critical review and new proof, EEE Transactions on Microwave Theory and Techniques, vol. 47, no. 6, pp , 999. [5] D. Woods, Reappraisal of the unconditional stability criteria for active 2-port networks in terms of s parameters, EEE Transactions on Circuits and Systems, vol. 23, no. 2, pp. 73 8, 976. [5] M. Pirola and G. Ghione, mmittance and S-parameter-based criteria for the unconditional stability of linear two-ports: Relations and invariance properties, EEE Transactions on Microwave Theory and Techniques, vol. 57, no. 3, pp , 29. [52] G. Niemeyer and J. J. Slotine, Telemanipulation with time delays, The nternational Journal of Robotics Research, vol. 23, no. 9, pp , 24. [53] M. Fan, A. Tits, and J. Doyle, Robustness in the presence of mixed parametric uncertainty and unmodeled dynamics, Automatic Control, EEE Transactions on, vol. 36, no., pp , 99. [54] C. W. Scherer, Relaxations for robust linear matrix inequality problems with verifications for exactness, SAM Journal on Matrix Analysis and Applications, vol. 27, no. 2, pp , 25. [55] C. A. Desoer and M. Vidyasagar, Feedback Systems: nput-output Properties, ser. Electrical Science Series. Academic Press, New York, 975. [56] G. Meinsma, Y. Shrivastava, and M. Fu, A dual formulation of mixed µ and on the losslessness of d, g scaling, EEE Transactions on Automatic Control, vol. 42, no. 7, pp , 997. [57] A. Helmersson, An QC-based stability criterion for systems with slowly varying parameters, in 4th World Congress of FAC, vol. F. Beijing, China: FAC, 999, pp [58] U. Jönsson and A. Rantzer, Systems with uncertain parameters timevariations with bounded derivatives, nternational Journal of Robust and Nonlinear Control, vol. 6, no. 9/, pp , 996. [59] H. Köroğlu and C. W. Scherer, Robust performance analysis for structured linear time-varying perturbations with bounded rates-of-variation, EEE Transactions on Automatic Control, vol. 52, no. 2, pp. 97 2, 27. [6] A. Packard and J. Teng, Robust stability with time varying perturbations, in Proceedings of 28th Allerton Conference, 99. [6] L. Eusebi and C. Melchiorri, Force reflecting telemanipulators with time-delay: stability analysis and control design, EEE Transactions on Robotics and Automation, vol. 4, no. 4, pp , 998. [62] Y. Yokokohji, T. maida, and T. Yoshikawa, Bilateral teleoperation under time-varying communication delay, in EEE/RSJ nternational Conference on ntelligent Robots and Systems,ROS, vol. 3, 999, pp [63] R. Lozano, N. Chopra, and M. Spong, Passivation of force reflecting bilateral teleoperators with time varying delay, in Proceedings of the 8. Mechatronics Forum, 22, pp [64] P. Arcara and C. Melchiorri, Control schemes for teleoperation with time delay: A comparative study, Robotics and Autonomous Systems, vol. 38, no., pp , 22. [65] J. H. Park and H. C. Cho, Sliding-mode controller for bilateral teleoperation with varying time delay, in EEE/ASME nternational Conference on Advanced ntelligent Mechatronics,, 999, pp [66] A. Aziminejad, M. Tavakoli, R. V. Patel, and M. Moallem, Transparent time-delayed bilateral teleoperation using wave variables, EEE Transactions on Control Systems Technology, vol. 6, no. 3, pp , 28. [67] D. Lee and M. W. Spong, Passive bilateral teleoperation with constant time delay, EEE Transactions on Robotics, vol. 22, no. 2, pp , 26.
15 PREPRNT - DO :.9/TRO [68] J.-P. Richard, Time-delay systems: An overview of some recent advances and open problems, Automatica, vol. 39, no., pp , 23. [69] G. Scorletti, Robustness analysis with time-delays, in Proceedings of the 36th EEE Conference on Decision and Control, vol. 4, 997, pp [7] M. Jun and M. Safonov, Rational multiplier QCs for uncertain timedelays and LM stability conditions, EEE Transactions on Automatic Control, vol. 47, no., pp , 22. [7] C.-Y. Kao and A. Rantzer, Stability analysis of systems with uncertain time-varying delays, Automatica, vol. 43, no. 6, pp , 27. [72] M. Fu, H. Li, and S. Niculescu, Robust stability and stabilization of timedelay systems via integral quadratic constraint approach, in Stability and Control of Time-delay Systems, ser. Lecture Notes in Control and nformation Sciences, L. Dugard and E. Verriest, Eds. Springer Berlin / Heidelberg, 998, vol. 228, pp. 6. [73] B. Willaert, B. Corteville, D. Reynaerts, H. Van Brussel, and E. Vander Poorten, Bounded environment passivity of the classical positionforce teleoperation controller, in EEE/RSJ nternational Conference on ntelligent Robots and Systems ROS, 29, pp [74] S. Boyd, L. E. Ghaoui, E. Feron, and V. Balakrishnan, Linear Matrix nequalities in System and Control Theory, ser. Studies in Applied Mathematics. Society for ndustrial and Applied Mathematics SAM, 994, vol. 5. [75] J. Löfberg, YALMP : A toolbox for modeling and optimization in MATLAB, in Proceedings of the CACSD Conference, Taipei, Taiwan, 24. [Online]. Available: [76] B. A. Francis, A Course on H Control Theory, ser. Lecture Notes in Control and nformation Sciences. Springer Berlin / Heidelberg, 987, vol. 88. [77] A. Pinkus, N-widths in Approximation Theory,, 98. Springer Verlag, New York, 98. [78] R. Daniel and P. McAree, Fundamental limits of performance for force reflecting teleoperation, The nternational Journal of Robotics Research, vol. 7, no. 8, pp. 8 83, 998. [79] R. H. Tütüncü, K. C. Toh, and M. J. Todd, Solving semidefinitequadratic-linear programs using SDPT3, Mathematical Programming, vol. 95, no. 2, pp , 23. [8] J. F. Sturm, Using SeDuMi.2, a Matlab Toolbox for Optimization Over Symmetric Cones,, Optimization Methods and Software, vol., no. 2, pp , 999. [8] S. Buerger and N. Hogan, Complementary stability and loop shaping for improved human robot interaction, EEE Transactions on Robotics, vol. 23, no. 2, pp , 27. [82] C. W. Scherer, Robust controller synthesis is convex for systems without control channel uncertainties, in Model-Based Control : Bridging Rigorous Theory and Advanced Technology. Springer US, 29, pp [83] J. Veenman and C. W. Scherer, QC-synthesis with general dynamic multipliers, in Proceedings of 8th FAC World Congress, Milano, 2, pp İlhan Polat received the B.Sc. and M.Sc. degrees in mechanical engineering from İstanbul Technical University and Boğaziçi University in 22 and 26 respectively. He is currently pursuing his Ph.D. degree in the Delft Center for Systems and Control at Delft University of Technology, The Netherlands. Carsten W. Scherer M 94 SM 7 received the Ph.D. degree in mathematics from the University of Würzburg Germany in 99. After six months of research at the University of Groningen The Netherlands, the University of Michigan Ann Arbor and Washington University St. Louis respectively, Dr. Scherer joined Delft University of Technology The Netherlands in 993 where he held positions as an assistant and associate professor. n fall 999 he spent a three months sabbatical as a visiting professor at the Automatic Control Laboratory of ETH Zurich. From December 2 until February 2 he was a full professor within the Delft Center for Systems and Control at Delft University of Technology. Since March 2 he holds the SRC SimTech Chair Mathematical Systems Theory in the Department of Mathematics at the University of Stuttgart in Germany. His main research interests cover various topics in applying optimization techniques for developing new advanced controller design algorithms and their application to mechatronics and aerospace systems. Dr. Scherer acted as the chair of the FAC technical committee on Robust Control 22 28, and he has served as an associated editor for EEE TRANSACTONS ON AUTOMATC CONTROL , Automatica 2 26 and Systems and Control Letters; he is currently active on the editorial board of the European Journal of Control.
Robust Stability. Robust stability against time-invariant and time-varying uncertainties. Parameter dependent Lyapunov functions
 Robust Stability Robust stability against time-invariant and time-varying uncertainties Parameter dependent Lyapunov functions Semi-infinite LMI problems From nominal to robust performance 1/24 Time-Invariant
Robust Stability Robust stability against time-invariant and time-varying uncertainties Parameter dependent Lyapunov functions Semi-infinite LMI problems From nominal to robust performance 1/24 Time-Invariant
Linear Matrix Inequalities in Control
 Linear Matrix Inequalities in Control Delft Center for Systems and Control (DCSC) Delft University of Technology The Netherlands Department of Electrical Engineering Eindhoven University of Technology
Linear Matrix Inequalities in Control Delft Center for Systems and Control (DCSC) Delft University of Technology The Netherlands Department of Electrical Engineering Eindhoven University of Technology
EXAMPLES OF CLASSICAL ITERATIVE METHODS
 EXAMPLES OF CLASSICAL ITERATIVE METHODS In these lecture notes we revisit a few classical fixpoint iterations for the solution of the linear systems of equations. We focus on the algebraic and algorithmic
EXAMPLES OF CLASSICAL ITERATIVE METHODS In these lecture notes we revisit a few classical fixpoint iterations for the solution of the linear systems of equations. We focus on the algebraic and algorithmic
Selected Examples of CONIC DUALITY AT WORK Robust Linear Optimization Synthesis of Linear Controllers Matrix Cube Theorem A.
 . Selected Examples of CONIC DUALITY AT WORK Robust Linear Optimization Synthesis of Linear Controllers Matrix Cube Theorem A. Nemirovski Arkadi.Nemirovski@isye.gatech.edu Linear Optimization Problem,
. Selected Examples of CONIC DUALITY AT WORK Robust Linear Optimization Synthesis of Linear Controllers Matrix Cube Theorem A. Nemirovski Arkadi.Nemirovski@isye.gatech.edu Linear Optimization Problem,
Some of the different forms of a signal, obtained by transformations, are shown in the figure. jwt e z. jwt z e
 Transform methods Some of the different forms of a signal, obtained by transformations, are shown in the figure. X(s) X(t) L - L F - F jw s s jw X(jw) X*(t) F - F X*(jw) jwt e z jwt z e X(nT) Z - Z X(z)
Transform methods Some of the different forms of a signal, obtained by transformations, are shown in the figure. X(s) X(t) L - L F - F jw s s jw X(jw) X*(t) F - F X*(jw) jwt e z jwt z e X(nT) Z - Z X(z)
RECENTLY, there has been renewed research interest
 IEEE TRANSACTIONS ON AUTOMATIC CONTROL, VOL 49, NO 12, DECEMBER 2004 2113 Distributed Control of Heterogeneous Systems Geir E Dullerud Raffaello D Andrea Abstract This paper considers control design for
IEEE TRANSACTIONS ON AUTOMATIC CONTROL, VOL 49, NO 12, DECEMBER 2004 2113 Distributed Control of Heterogeneous Systems Geir E Dullerud Raffaello D Andrea Abstract This paper considers control design for
Control of Electromechanical Systems
 Control of Electromechanical Systems November 3, 27 Exercise Consider the feedback control scheme of the motor speed ω in Fig., where the torque actuation includes a time constant τ A =. s and a disturbance
Control of Electromechanical Systems November 3, 27 Exercise Consider the feedback control scheme of the motor speed ω in Fig., where the torque actuation includes a time constant τ A =. s and a disturbance
Chapter 7 Interconnected Systems and Feedback: Well-Posedness, Stability, and Performance 7. Introduction Feedback control is a powerful approach to o
 Lectures on Dynamic Systems and Control Mohammed Dahleh Munther A. Dahleh George Verghese Department of Electrical Engineering and Computer Science Massachuasetts Institute of Technology c Chapter 7 Interconnected
Lectures on Dynamic Systems and Control Mohammed Dahleh Munther A. Dahleh George Verghese Department of Electrical Engineering and Computer Science Massachuasetts Institute of Technology c Chapter 7 Interconnected
Fast Algorithms for SDPs derived from the Kalman-Yakubovich-Popov Lemma
 Fast Algorithms for SDPs derived from the Kalman-Yakubovich-Popov Lemma Venkataramanan (Ragu) Balakrishnan School of ECE, Purdue University 8 September 2003 European Union RTN Summer School on Multi-Agent
Fast Algorithms for SDPs derived from the Kalman-Yakubovich-Popov Lemma Venkataramanan (Ragu) Balakrishnan School of ECE, Purdue University 8 September 2003 European Union RTN Summer School on Multi-Agent
An IQC Approach to Robust Estimation against Perturbations of Smoothly Time-Varying Parameters
 Proceedings of the 47th EEE Conference on Decision and Control Cancun, Mexico, Dec 9-11, 8 An QC Approach to Robust Estimation against Perturbations of Smoothly Time-Varying Parameters Joost Veenman and
Proceedings of the 47th EEE Conference on Decision and Control Cancun, Mexico, Dec 9-11, 8 An QC Approach to Robust Estimation against Perturbations of Smoothly Time-Varying Parameters Joost Veenman and
Robust fixed-order H Controller Design for Spectral Models by Convex Optimization
 Robust fixed-order H Controller Design for Spectral Models by Convex Optimization Alireza Karimi, Gorka Galdos and Roland Longchamp Abstract A new approach for robust fixed-order H controller design by
Robust fixed-order H Controller Design for Spectral Models by Convex Optimization Alireza Karimi, Gorka Galdos and Roland Longchamp Abstract A new approach for robust fixed-order H controller design by
Decentralized Stabilization of Heterogeneous Linear Multi-Agent Systems
 1 Decentralized Stabilization of Heterogeneous Linear Multi-Agent Systems Mauro Franceschelli, Andrea Gasparri, Alessandro Giua, and Giovanni Ulivi Abstract In this paper the formation stabilization problem
1 Decentralized Stabilization of Heterogeneous Linear Multi-Agent Systems Mauro Franceschelli, Andrea Gasparri, Alessandro Giua, and Giovanni Ulivi Abstract In this paper the formation stabilization problem
only nite eigenvalues. This is an extension of earlier results from [2]. Then we concentrate on the Riccati equation appearing in H 2 and linear quadr
![only nite eigenvalues. This is an extension of earlier results from [2]. Then we concentrate on the Riccati equation appearing in H 2 and linear quadr only nite eigenvalues. This is an extension of earlier results from [2]. Then we concentrate on the Riccati equation appearing in H 2 and linear quadr](/thumbs/90/102827704.jpg) The discrete algebraic Riccati equation and linear matrix inequality nton. Stoorvogel y Department of Mathematics and Computing Science Eindhoven Univ. of Technology P.O. ox 53, 56 M Eindhoven The Netherlands
The discrete algebraic Riccati equation and linear matrix inequality nton. Stoorvogel y Department of Mathematics and Computing Science Eindhoven Univ. of Technology P.O. ox 53, 56 M Eindhoven The Netherlands
Chapter Stability Robustness Introduction Last chapter showed how the Nyquist stability criterion provides conditions for the stability robustness of
 Lectures on Dynamic Systems and Control Mohammed Dahleh Munther A Dahleh George Verghese Department of Electrical Engineering and Computer Science Massachuasetts Institute of Technology c Chapter Stability
Lectures on Dynamic Systems and Control Mohammed Dahleh Munther A Dahleh George Verghese Department of Electrical Engineering and Computer Science Massachuasetts Institute of Technology c Chapter Stability
Dissipative Systems Analysis and Control
 Bernard Brogliato, Rogelio Lozano, Bernhard Maschke and Olav Egeland Dissipative Systems Analysis and Control Theory and Applications 2nd Edition With 94 Figures 4y Sprin er 1 Introduction 1 1.1 Example
Bernard Brogliato, Rogelio Lozano, Bernhard Maschke and Olav Egeland Dissipative Systems Analysis and Control Theory and Applications 2nd Edition With 94 Figures 4y Sprin er 1 Introduction 1 1.1 Example
Copyrighted Material. 1.1 Large-Scale Interconnected Dynamical Systems
 Chapter One Introduction 1.1 Large-Scale Interconnected Dynamical Systems Modern complex dynamical systems 1 are highly interconnected and mutually interdependent, both physically and through a multitude
Chapter One Introduction 1.1 Large-Scale Interconnected Dynamical Systems Modern complex dynamical systems 1 are highly interconnected and mutually interdependent, both physically and through a multitude
Near-Potential Games: Geometry and Dynamics
 Near-Potential Games: Geometry and Dynamics Ozan Candogan, Asuman Ozdaglar and Pablo A. Parrilo January 29, 2012 Abstract Potential games are a special class of games for which many adaptive user dynamics
Near-Potential Games: Geometry and Dynamics Ozan Candogan, Asuman Ozdaglar and Pablo A. Parrilo January 29, 2012 Abstract Potential games are a special class of games for which many adaptive user dynamics
Output Input Stability and Minimum-Phase Nonlinear Systems
 422 IEEE TRANSACTIONS ON AUTOMATIC CONTROL, VOL. 47, NO. 3, MARCH 2002 Output Input Stability and Minimum-Phase Nonlinear Systems Daniel Liberzon, Member, IEEE, A. Stephen Morse, Fellow, IEEE, and Eduardo
422 IEEE TRANSACTIONS ON AUTOMATIC CONTROL, VOL. 47, NO. 3, MARCH 2002 Output Input Stability and Minimum-Phase Nonlinear Systems Daniel Liberzon, Member, IEEE, A. Stephen Morse, Fellow, IEEE, and Eduardo
FINITE HORIZON ROBUST MODEL PREDICTIVE CONTROL USING LINEAR MATRIX INEQUALITIES. Danlei Chu, Tongwen Chen, Horacio J. Marquez
 FINITE HORIZON ROBUST MODEL PREDICTIVE CONTROL USING LINEAR MATRIX INEQUALITIES Danlei Chu Tongwen Chen Horacio J Marquez Department of Electrical and Computer Engineering University of Alberta Edmonton
FINITE HORIZON ROBUST MODEL PREDICTIVE CONTROL USING LINEAR MATRIX INEQUALITIES Danlei Chu Tongwen Chen Horacio J Marquez Department of Electrical and Computer Engineering University of Alberta Edmonton
Navigation and Obstacle Avoidance via Backstepping for Mechanical Systems with Drift in the Closed Loop
 Navigation and Obstacle Avoidance via Backstepping for Mechanical Systems with Drift in the Closed Loop Jan Maximilian Montenbruck, Mathias Bürger, Frank Allgöwer Abstract We study backstepping controllers
Navigation and Obstacle Avoidance via Backstepping for Mechanical Systems with Drift in the Closed Loop Jan Maximilian Montenbruck, Mathias Bürger, Frank Allgöwer Abstract We study backstepping controllers
(Continued on next page)
 (Continued on next page) 18.2 Roots of Stability Nyquist Criterion 87 e(s) 1 S(s) = =, r(s) 1 + P (s)c(s) where P (s) represents the plant transfer function, and C(s) the compensator. The closedloop characteristic
(Continued on next page) 18.2 Roots of Stability Nyquist Criterion 87 e(s) 1 S(s) = =, r(s) 1 + P (s)c(s) where P (s) represents the plant transfer function, and C(s) the compensator. The closedloop characteristic
Characterization of Convex and Concave Resource Allocation Problems in Interference Coupled Wireless Systems
 2382 IEEE TRANSACTIONS ON SIGNAL PROCESSING, VOL 59, NO 5, MAY 2011 Characterization of Convex and Concave Resource Allocation Problems in Interference Coupled Wireless Systems Holger Boche, Fellow, IEEE,
2382 IEEE TRANSACTIONS ON SIGNAL PROCESSING, VOL 59, NO 5, MAY 2011 Characterization of Convex and Concave Resource Allocation Problems in Interference Coupled Wireless Systems Holger Boche, Fellow, IEEE,
Lecture 6. Chapter 8: Robust Stability and Performance Analysis for MIMO Systems. Eugenio Schuster.
 Lecture 6 Chapter 8: Robust Stability and Performance Analysis for MIMO Systems Eugenio Schuster schuster@lehigh.edu Mechanical Engineering and Mechanics Lehigh University Lecture 6 p. 1/73 6.1 General
Lecture 6 Chapter 8: Robust Stability and Performance Analysis for MIMO Systems Eugenio Schuster schuster@lehigh.edu Mechanical Engineering and Mechanics Lehigh University Lecture 6 p. 1/73 6.1 General
1 Lyapunov theory of stability
 M.Kawski, APM 581 Diff Equns Intro to Lyapunov theory. November 15, 29 1 1 Lyapunov theory of stability Introduction. Lyapunov s second (or direct) method provides tools for studying (asymptotic) stability
M.Kawski, APM 581 Diff Equns Intro to Lyapunov theory. November 15, 29 1 1 Lyapunov theory of stability Introduction. Lyapunov s second (or direct) method provides tools for studying (asymptotic) stability
EML5311 Lyapunov Stability & Robust Control Design
 EML5311 Lyapunov Stability & Robust Control Design 1 Lyapunov Stability criterion In Robust control design of nonlinear uncertain systems, stability theory plays an important role in engineering systems.
EML5311 Lyapunov Stability & Robust Control Design 1 Lyapunov Stability criterion In Robust control design of nonlinear uncertain systems, stability theory plays an important role in engineering systems.
Theory of Robust Control
 Theory of Robust Control Carsten Scherer Mathematical Systems Theory Department of Mathematics University of Stuttgart Germany Contents 1 Introduction to Basic Concepts 6 1.1 Systems and Signals..............................
Theory of Robust Control Carsten Scherer Mathematical Systems Theory Department of Mathematics University of Stuttgart Germany Contents 1 Introduction to Basic Concepts 6 1.1 Systems and Signals..............................
Near-Potential Games: Geometry and Dynamics
 Near-Potential Games: Geometry and Dynamics Ozan Candogan, Asuman Ozdaglar and Pablo A. Parrilo September 6, 2011 Abstract Potential games are a special class of games for which many adaptive user dynamics
Near-Potential Games: Geometry and Dynamics Ozan Candogan, Asuman Ozdaglar and Pablo A. Parrilo September 6, 2011 Abstract Potential games are a special class of games for which many adaptive user dynamics
Subject: Optimal Control Assignment-1 (Related to Lecture notes 1-10)
 Subject: Optimal Control Assignment- (Related to Lecture notes -). Design a oil mug, shown in fig., to hold as much oil possible. The height and radius of the mug should not be more than 6cm. The mug must
Subject: Optimal Control Assignment- (Related to Lecture notes -). Design a oil mug, shown in fig., to hold as much oil possible. The height and radius of the mug should not be more than 6cm. The mug must
Outline. Linear Matrix Inequalities in Control. Outline. System Interconnection. j _jst. ]Bt Bjj. Generalized plant framework
![Outline. Linear Matrix Inequalities in Control. Outline. System Interconnection. j _jst. ]Bt Bjj. Generalized plant framework Outline. Linear Matrix Inequalities in Control. Outline. System Interconnection. j _jst. ]Bt Bjj. Generalized plant framework](/thumbs/80/80431829.jpg) Outline Linear Matrix Inequalities in Control Carsten Scherer and Siep Weiland 7th Elgersburg School on Mathematical Systems heory Class 3 1 Single-Objective Synthesis Setup State-Feedback Output-Feedback
Outline Linear Matrix Inequalities in Control Carsten Scherer and Siep Weiland 7th Elgersburg School on Mathematical Systems heory Class 3 1 Single-Objective Synthesis Setup State-Feedback Output-Feedback
More on Bracket Algebra
 7 More on Bracket Algebra Algebra is generous; she often gives more than is asked of her. D Alembert The last chapter demonstrated, that determinants (and in particular multihomogeneous bracket polynomials)
7 More on Bracket Algebra Algebra is generous; she often gives more than is asked of her. D Alembert The last chapter demonstrated, that determinants (and in particular multihomogeneous bracket polynomials)
arzelier
 COURSE ON LMI OPTIMIZATION WITH APPLICATIONS IN CONTROL PART II.1 LMIs IN SYSTEMS CONTROL STATE-SPACE METHODS STABILITY ANALYSIS Didier HENRION www.laas.fr/ henrion henrion@laas.fr Denis ARZELIER www.laas.fr/
COURSE ON LMI OPTIMIZATION WITH APPLICATIONS IN CONTROL PART II.1 LMIs IN SYSTEMS CONTROL STATE-SPACE METHODS STABILITY ANALYSIS Didier HENRION www.laas.fr/ henrion henrion@laas.fr Denis ARZELIER www.laas.fr/
chapter 12 MORE MATRIX ALGEBRA 12.1 Systems of Linear Equations GOALS
 chapter MORE MATRIX ALGEBRA GOALS In Chapter we studied matrix operations and the algebra of sets and logic. We also made note of the strong resemblance of matrix algebra to elementary algebra. The reader
chapter MORE MATRIX ALGEBRA GOALS In Chapter we studied matrix operations and the algebra of sets and logic. We also made note of the strong resemblance of matrix algebra to elementary algebra. The reader
Extremum Seeking with Drift
 Extremum Seeking with Drift Jan aximilian ontenbruck, Hans-Bernd Dürr, Christian Ebenbauer, Frank Allgöwer Institute for Systems Theory and Automatic Control, University of Stuttgart Pfaffenwaldring 9,
Extremum Seeking with Drift Jan aximilian ontenbruck, Hans-Bernd Dürr, Christian Ebenbauer, Frank Allgöwer Institute for Systems Theory and Automatic Control, University of Stuttgart Pfaffenwaldring 9,
UNCERTAINTY MODELING VIA FREQUENCY DOMAIN MODEL VALIDATION
 AIAA 99-3959 UNCERTAINTY MODELING VIA FREQUENCY DOMAIN MODEL VALIDATION Martin R. Waszak, * NASA Langley Research Center, Hampton, Virginia Dominick Andrisani II, Purdue University, West Lafayette, Indiana
AIAA 99-3959 UNCERTAINTY MODELING VIA FREQUENCY DOMAIN MODEL VALIDATION Martin R. Waszak, * NASA Langley Research Center, Hampton, Virginia Dominick Andrisani II, Purdue University, West Lafayette, Indiana
Designing Stable Inverters and State Observers for Switched Linear Systems with Unknown Inputs
 Designing Stable Inverters and State Observers for Switched Linear Systems with Unknown Inputs Shreyas Sundaram and Christoforos N. Hadjicostis Abstract We present a method for estimating the inputs and
Designing Stable Inverters and State Observers for Switched Linear Systems with Unknown Inputs Shreyas Sundaram and Christoforos N. Hadjicostis Abstract We present a method for estimating the inputs and
Chapter 9 Robust Stability in SISO Systems 9. Introduction There are many reasons to use feedback control. As we have seen earlier, with the help of a
 Lectures on Dynamic Systems and Control Mohammed Dahleh Munther A. Dahleh George Verghese Department of Electrical Engineering and Computer Science Massachuasetts Institute of Technology c Chapter 9 Robust
Lectures on Dynamic Systems and Control Mohammed Dahleh Munther A. Dahleh George Verghese Department of Electrical Engineering and Computer Science Massachuasetts Institute of Technology c Chapter 9 Robust
On the Power of Robust Solutions in Two-Stage Stochastic and Adaptive Optimization Problems
 MATHEMATICS OF OPERATIONS RESEARCH Vol. xx, No. x, Xxxxxxx 00x, pp. xxx xxx ISSN 0364-765X EISSN 156-5471 0x xx0x 0xxx informs DOI 10.187/moor.xxxx.xxxx c 00x INFORMS On the Power of Robust Solutions in
MATHEMATICS OF OPERATIONS RESEARCH Vol. xx, No. x, Xxxxxxx 00x, pp. xxx xxx ISSN 0364-765X EISSN 156-5471 0x xx0x 0xxx informs DOI 10.187/moor.xxxx.xxxx c 00x INFORMS On the Power of Robust Solutions in
Didier HENRION henrion
 POLYNOMIAL METHODS FOR ROBUST CONTROL PART I.1 ROBUST STABILITY ANALYSIS: SINGLE PARAMETER UNCERTAINTY Didier HENRION www.laas.fr/ henrion henrion@laas.fr Pont Neuf over river Garonne in Toulouse June
POLYNOMIAL METHODS FOR ROBUST CONTROL PART I.1 ROBUST STABILITY ANALYSIS: SINGLE PARAMETER UNCERTAINTY Didier HENRION www.laas.fr/ henrion henrion@laas.fr Pont Neuf over river Garonne in Toulouse June
Zeros and zero dynamics
 CHAPTER 4 Zeros and zero dynamics 41 Zero dynamics for SISO systems Consider a linear system defined by a strictly proper scalar transfer function that does not have any common zero and pole: g(s) =α p(s)
CHAPTER 4 Zeros and zero dynamics 41 Zero dynamics for SISO systems Consider a linear system defined by a strictly proper scalar transfer function that does not have any common zero and pole: g(s) =α p(s)
1 The Observability Canonical Form
 NONLINEAR OBSERVERS AND SEPARATION PRINCIPLE 1 The Observability Canonical Form In this Chapter we discuss the design of observers for nonlinear systems modelled by equations of the form ẋ = f(x, u) (1)
NONLINEAR OBSERVERS AND SEPARATION PRINCIPLE 1 The Observability Canonical Form In this Chapter we discuss the design of observers for nonlinear systems modelled by equations of the form ẋ = f(x, u) (1)
Variable-gain output feedback control
 7. Variable-gain output feedback control 7.1. Introduction PUC-Rio - Certificação Digital Nº 611865/CA In designing control laws, the usual first step is to describe the plant at a given operating point
7. Variable-gain output feedback control 7.1. Introduction PUC-Rio - Certificação Digital Nº 611865/CA In designing control laws, the usual first step is to describe the plant at a given operating point
On the Power of Robust Solutions in Two-Stage Stochastic and Adaptive Optimization Problems
 MATHEMATICS OF OPERATIONS RESEARCH Vol. 35, No., May 010, pp. 84 305 issn 0364-765X eissn 156-5471 10 350 084 informs doi 10.187/moor.1090.0440 010 INFORMS On the Power of Robust Solutions in Two-Stage
MATHEMATICS OF OPERATIONS RESEARCH Vol. 35, No., May 010, pp. 84 305 issn 0364-765X eissn 156-5471 10 350 084 informs doi 10.187/moor.1090.0440 010 INFORMS On the Power of Robust Solutions in Two-Stage
CHAPTER 5 ROBUSTNESS ANALYSIS OF THE CONTROLLER
 114 CHAPTER 5 ROBUSTNESS ANALYSIS OF THE CONTROLLER 5.1 INTRODUCTION Robust control is a branch of control theory that explicitly deals with uncertainty in its approach to controller design. It also refers
114 CHAPTER 5 ROBUSTNESS ANALYSIS OF THE CONTROLLER 5.1 INTRODUCTION Robust control is a branch of control theory that explicitly deals with uncertainty in its approach to controller design. It also refers
Stability theory is a fundamental topic in mathematics and engineering, that include every
 Stability Theory Stability theory is a fundamental topic in mathematics and engineering, that include every branches of control theory. For a control system, the least requirement is that the system is
Stability Theory Stability theory is a fundamental topic in mathematics and engineering, that include every branches of control theory. For a control system, the least requirement is that the system is
Math 350 Fall 2011 Notes about inner product spaces. In this notes we state and prove some important properties of inner product spaces.
 Math 350 Fall 2011 Notes about inner product spaces In this notes we state and prove some important properties of inner product spaces. First, recall the dot product on R n : if x, y R n, say x = (x 1,...,
Math 350 Fall 2011 Notes about inner product spaces In this notes we state and prove some important properties of inner product spaces. First, recall the dot product on R n : if x, y R n, say x = (x 1,...,
Static Output Feedback Stabilisation with H Performance for a Class of Plants
 Static Output Feedback Stabilisation with H Performance for a Class of Plants E. Prempain and I. Postlethwaite Control and Instrumentation Research, Department of Engineering, University of Leicester,
Static Output Feedback Stabilisation with H Performance for a Class of Plants E. Prempain and I. Postlethwaite Control and Instrumentation Research, Department of Engineering, University of Leicester,
Lecture 1: Entropy, convexity, and matrix scaling CSE 599S: Entropy optimality, Winter 2016 Instructor: James R. Lee Last updated: January 24, 2016
 Lecture 1: Entropy, convexity, and matrix scaling CSE 599S: Entropy optimality, Winter 2016 Instructor: James R. Lee Last updated: January 24, 2016 1 Entropy Since this course is about entropy maximization,
Lecture 1: Entropy, convexity, and matrix scaling CSE 599S: Entropy optimality, Winter 2016 Instructor: James R. Lee Last updated: January 24, 2016 1 Entropy Since this course is about entropy maximization,
We are IntechOpen, the world s leading publisher of Open Access books Built by scientists, for scientists. International authors and editors
 We are IntechOpen, the world s leading publisher of Open Access books Built by scientists, for scientists 3,500 08,000.7 M Open access books available International authors and editors Downloads Our authors
We are IntechOpen, the world s leading publisher of Open Access books Built by scientists, for scientists 3,500 08,000.7 M Open access books available International authors and editors Downloads Our authors
The Q-parametrization (Youla) Lecture 13: Synthesis by Convex Optimization. Lecture 13: Synthesis by Convex Optimization. Example: Spring-mass System
 The Q-parametrization (Youla) Lecture 3: Synthesis by Convex Optimization controlled variables z Plant distubances w Example: Spring-mass system measurements y Controller control inputs u Idea for lecture
The Q-parametrization (Youla) Lecture 3: Synthesis by Convex Optimization controlled variables z Plant distubances w Example: Spring-mass system measurements y Controller control inputs u Idea for lecture
THIS paper deals with robust control in the setup associated
 IEEE TRANSACTIONS ON AUTOMATIC CONTROL, VOL 50, NO 10, OCTOBER 2005 1501 Control-Oriented Model Validation and Errors Quantification in the `1 Setup V F Sokolov Abstract A priori information required for
IEEE TRANSACTIONS ON AUTOMATIC CONTROL, VOL 50, NO 10, OCTOBER 2005 1501 Control-Oriented Model Validation and Errors Quantification in the `1 Setup V F Sokolov Abstract A priori information required for
The Integers. Peter J. Kahn
 Math 3040: Spring 2009 The Integers Peter J. Kahn Contents 1. The Basic Construction 1 2. Adding integers 6 3. Ordering integers 16 4. Multiplying integers 18 Before we begin the mathematics of this section,
Math 3040: Spring 2009 The Integers Peter J. Kahn Contents 1. The Basic Construction 1 2. Adding integers 6 3. Ordering integers 16 4. Multiplying integers 18 Before we begin the mathematics of this section,
CHAPTER 4 THE COMMON FACTOR MODEL IN THE SAMPLE. From Exploratory Factor Analysis Ledyard R Tucker and Robert C. MacCallum
 CHAPTER 4 THE COMMON FACTOR MODEL IN THE SAMPLE From Exploratory Factor Analysis Ledyard R Tucker and Robert C. MacCallum 1997 65 CHAPTER 4 THE COMMON FACTOR MODEL IN THE SAMPLE 4.0. Introduction In Chapter
CHAPTER 4 THE COMMON FACTOR MODEL IN THE SAMPLE From Exploratory Factor Analysis Ledyard R Tucker and Robert C. MacCallum 1997 65 CHAPTER 4 THE COMMON FACTOR MODEL IN THE SAMPLE 4.0. Introduction In Chapter
Computational Tasks and Models
 1 Computational Tasks and Models Overview: We assume that the reader is familiar with computing devices but may associate the notion of computation with specific incarnations of it. Our first goal is to
1 Computational Tasks and Models Overview: We assume that the reader is familiar with computing devices but may associate the notion of computation with specific incarnations of it. Our first goal is to
The output voltage is given by,
 71 The output voltage is given by, = (3.1) The inductor and capacitor values of the Boost converter are derived by having the same assumption as that of the Buck converter. Now the critical value of the
71 The output voltage is given by, = (3.1) The inductor and capacitor values of the Boost converter are derived by having the same assumption as that of the Buck converter. Now the critical value of the
10 Transfer Matrix Models
 MIT EECS 6.241 (FALL 26) LECTURE NOTES BY A. MEGRETSKI 1 Transfer Matrix Models So far, transfer matrices were introduced for finite order state space LTI models, in which case they serve as an important
MIT EECS 6.241 (FALL 26) LECTURE NOTES BY A. MEGRETSKI 1 Transfer Matrix Models So far, transfer matrices were introduced for finite order state space LTI models, in which case they serve as an important
THIS paper studies the input design problem in system identification.
 1534 IEEE TRANSACTIONS ON AUTOMATIC CONTROL, VOL. 50, NO. 10, OCTOBER 2005 Input Design Via LMIs Admitting Frequency-Wise Model Specifications in Confidence Regions Henrik Jansson Håkan Hjalmarsson, Member,
1534 IEEE TRANSACTIONS ON AUTOMATIC CONTROL, VOL. 50, NO. 10, OCTOBER 2005 Input Design Via LMIs Admitting Frequency-Wise Model Specifications in Confidence Regions Henrik Jansson Håkan Hjalmarsson, Member,
Contents. 0.1 Notation... 3
 Contents 0.1 Notation........................................ 3 1 A Short Course on Frame Theory 4 1.1 Examples of Signal Expansions............................ 4 1.2 Signal Expansions in Finite-Dimensional
Contents 0.1 Notation........................................ 3 1 A Short Course on Frame Theory 4 1.1 Examples of Signal Expansions............................ 4 1.2 Signal Expansions in Finite-Dimensional
Problem Set 5 Solutions 1
 Massachusetts Institute of Technology Department of Electrical Engineering and Computer Science 6.245: MULTIVARIABLE CONTROL SYSTEMS by A. Megretski Problem Set 5 Solutions The problem set deals with Hankel
Massachusetts Institute of Technology Department of Electrical Engineering and Computer Science 6.245: MULTIVARIABLE CONTROL SYSTEMS by A. Megretski Problem Set 5 Solutions The problem set deals with Hankel
QUANTITATIVE L P STABILITY ANALYSIS OF A CLASS OF LINEAR TIME-VARYING FEEDBACK SYSTEMS
 Int. J. Appl. Math. Comput. Sci., 2003, Vol. 13, No. 2, 179 184 QUANTITATIVE L P STABILITY ANALYSIS OF A CLASS OF LINEAR TIME-VARYING FEEDBACK SYSTEMS PINI GURFIL Department of Mechanical and Aerospace
Int. J. Appl. Math. Comput. Sci., 2003, Vol. 13, No. 2, 179 184 QUANTITATIVE L P STABILITY ANALYSIS OF A CLASS OF LINEAR TIME-VARYING FEEDBACK SYSTEMS PINI GURFIL Department of Mechanical and Aerospace
DELFT UNIVERSITY OF TECHNOLOGY
 DELFT UNIVERSITY OF TECHNOLOGY REPORT -09 Computational and Sensitivity Aspects of Eigenvalue-Based Methods for the Large-Scale Trust-Region Subproblem Marielba Rojas, Bjørn H. Fotland, and Trond Steihaug
DELFT UNIVERSITY OF TECHNOLOGY REPORT -09 Computational and Sensitivity Aspects of Eigenvalue-Based Methods for the Large-Scale Trust-Region Subproblem Marielba Rojas, Bjørn H. Fotland, and Trond Steihaug
Spectral Graph Theory Lecture 2. The Laplacian. Daniel A. Spielman September 4, x T M x. ψ i = arg min
 Spectral Graph Theory Lecture 2 The Laplacian Daniel A. Spielman September 4, 2015 Disclaimer These notes are not necessarily an accurate representation of what happened in class. The notes written before
Spectral Graph Theory Lecture 2 The Laplacian Daniel A. Spielman September 4, 2015 Disclaimer These notes are not necessarily an accurate representation of what happened in class. The notes written before
Figure 3.1: Unity feedback interconnection
 Chapter 3 Small Gain Theorem and Integral Quadratic Constraints This chapter presents a version of the small gain theorem for L2 gains, and then proceeds to introduce the general technique of working with
Chapter 3 Small Gain Theorem and Integral Quadratic Constraints This chapter presents a version of the small gain theorem for L2 gains, and then proceeds to introduce the general technique of working with
Two-Layer Network Equivalent for Electromagnetic Transients
 1328 IEEE TRANSACTIONS ON POWER DELIVERY, VOL. 18, NO. 4, OCTOBER 2003 Two-Layer Network Equivalent for Electromagnetic Transients Mohamed Abdel-Rahman, Member, IEEE, Adam Semlyen, Life Fellow, IEEE, and
1328 IEEE TRANSACTIONS ON POWER DELIVERY, VOL. 18, NO. 4, OCTOBER 2003 Two-Layer Network Equivalent for Electromagnetic Transients Mohamed Abdel-Rahman, Member, IEEE, Adam Semlyen, Life Fellow, IEEE, and
Chapter Robust Performance and Introduction to the Structured Singular Value Function Introduction As discussed in Lecture 0, a process is better desc
 Lectures on Dynamic Systems and Control Mohammed Dahleh Munther A Dahleh George Verghese Department of Electrical Engineering and Computer Science Massachuasetts Institute of Technology c Chapter Robust
Lectures on Dynamic Systems and Control Mohammed Dahleh Munther A Dahleh George Verghese Department of Electrical Engineering and Computer Science Massachuasetts Institute of Technology c Chapter Robust
ROBUST STABLE NONLINEAR CONTROL AND DESIGN OF A CSTR IN A LARGE OPERATING RANGE. Johannes Gerhard, Martin Mönnigmann, Wolfgang Marquardt
 ROBUST STABLE NONLINEAR CONTROL AND DESIGN OF A CSTR IN A LARGE OPERATING RANGE Johannes Gerhard, Martin Mönnigmann, Wolfgang Marquardt Lehrstuhl für Prozesstechnik, RWTH Aachen Turmstr. 46, D-5264 Aachen,
ROBUST STABLE NONLINEAR CONTROL AND DESIGN OF A CSTR IN A LARGE OPERATING RANGE Johannes Gerhard, Martin Mönnigmann, Wolfgang Marquardt Lehrstuhl für Prozesstechnik, RWTH Aachen Turmstr. 46, D-5264 Aachen,
Revisiting Llewellyn s Absolute Stability Criterion for Bilateral Teleoperation Systems under Non-passive Operator or Environment
 2012 IEEE/RSJ International Conference on Intelligent Robots and Systems October 712, 2012. Vilamoura, Algarve, Portugal visiting Llewellyn s Absolute Stability Criterion for Bilateral Teleoperation Systems
2012 IEEE/RSJ International Conference on Intelligent Robots and Systems October 712, 2012. Vilamoura, Algarve, Portugal visiting Llewellyn s Absolute Stability Criterion for Bilateral Teleoperation Systems
Structured eigenvalue/eigenvector backward errors of matrix pencils arising in optimal control
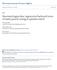 Electronic Journal of Linear Algebra Volume 34 Volume 34 08) Article 39 08 Structured eigenvalue/eigenvector backward errors of matrix pencils arising in optimal control Christian Mehl Technische Universitaet
Electronic Journal of Linear Algebra Volume 34 Volume 34 08) Article 39 08 Structured eigenvalue/eigenvector backward errors of matrix pencils arising in optimal control Christian Mehl Technische Universitaet
AC&ST AUTOMATIC CONTROL AND SYSTEM THEORY SYSTEMS AND MODELS. Claudio Melchiorri
 C. Melchiorri (DEI) Automatic Control & System Theory 1 AUTOMATIC CONTROL AND SYSTEM THEORY SYSTEMS AND MODELS Claudio Melchiorri Dipartimento di Ingegneria dell Energia Elettrica e dell Informazione (DEI)
C. Melchiorri (DEI) Automatic Control & System Theory 1 AUTOMATIC CONTROL AND SYSTEM THEORY SYSTEMS AND MODELS Claudio Melchiorri Dipartimento di Ingegneria dell Energia Elettrica e dell Informazione (DEI)
Proximal-like contraction methods for monotone variational inequalities in a unified framework
 Proximal-like contraction methods for monotone variational inequalities in a unified framework Bingsheng He 1 Li-Zhi Liao 2 Xiang Wang Department of Mathematics, Nanjing University, Nanjing, 210093, China
Proximal-like contraction methods for monotone variational inequalities in a unified framework Bingsheng He 1 Li-Zhi Liao 2 Xiang Wang Department of Mathematics, Nanjing University, Nanjing, 210093, China
Linear Programming Redux
 Linear Programming Redux Jim Bremer May 12, 2008 The purpose of these notes is to review the basics of linear programming and the simplex method in a clear, concise, and comprehensive way. The book contains
Linear Programming Redux Jim Bremer May 12, 2008 The purpose of these notes is to review the basics of linear programming and the simplex method in a clear, concise, and comprehensive way. The book contains
Introduction. Performance and Robustness (Chapter 1) Advanced Control Systems Spring / 31
 Introduction Classical Control Robust Control u(t) y(t) G u(t) G + y(t) G : nominal model G = G + : plant uncertainty Uncertainty sources : Structured : parametric uncertainty, multimodel uncertainty Unstructured
Introduction Classical Control Robust Control u(t) y(t) G u(t) G + y(t) G : nominal model G = G + : plant uncertainty Uncertainty sources : Structured : parametric uncertainty, multimodel uncertainty Unstructured
FRTN10 Multivariable Control, Lecture 13. Course outline. The Q-parametrization (Youla) Example: Spring-mass System
 FRTN Multivariable Control, Lecture 3 Anders Robertsson Automatic Control LTH, Lund University Course outline The Q-parametrization (Youla) L-L5 Purpose, models and loop-shaping by hand L6-L8 Limitations
FRTN Multivariable Control, Lecture 3 Anders Robertsson Automatic Control LTH, Lund University Course outline The Q-parametrization (Youla) L-L5 Purpose, models and loop-shaping by hand L6-L8 Limitations
An Observation on the Positive Real Lemma
 Journal of Mathematical Analysis and Applications 255, 48 49 (21) doi:1.16/jmaa.2.7241, available online at http://www.idealibrary.com on An Observation on the Positive Real Lemma Luciano Pandolfi Dipartimento
Journal of Mathematical Analysis and Applications 255, 48 49 (21) doi:1.16/jmaa.2.7241, available online at http://www.idealibrary.com on An Observation on the Positive Real Lemma Luciano Pandolfi Dipartimento
IEEE TRANSACTIONS ON INFORMATION THEORY, VOL. 52, NO. 2, FEBRUARY Uplink Downlink Duality Via Minimax Duality. Wei Yu, Member, IEEE (1) (2)
 IEEE TRANSACTIONS ON INFORMATION THEORY, VOL. 52, NO. 2, FEBRUARY 2006 361 Uplink Downlink Duality Via Minimax Duality Wei Yu, Member, IEEE Abstract The sum capacity of a Gaussian vector broadcast channel
IEEE TRANSACTIONS ON INFORMATION THEORY, VOL. 52, NO. 2, FEBRUARY 2006 361 Uplink Downlink Duality Via Minimax Duality Wei Yu, Member, IEEE Abstract The sum capacity of a Gaussian vector broadcast channel
Research Article Stabilization Analysis and Synthesis of Discrete-Time Descriptor Markov Jump Systems with Partially Unknown Transition Probabilities
 Research Journal of Applied Sciences, Engineering and Technology 7(4): 728-734, 214 DOI:1.1926/rjaset.7.39 ISSN: 24-7459; e-issn: 24-7467 214 Maxwell Scientific Publication Corp. Submitted: February 25,
Research Journal of Applied Sciences, Engineering and Technology 7(4): 728-734, 214 DOI:1.1926/rjaset.7.39 ISSN: 24-7459; e-issn: 24-7467 214 Maxwell Scientific Publication Corp. Submitted: February 25,
Denis ARZELIER arzelier
 COURSE ON LMI OPTIMIZATION WITH APPLICATIONS IN CONTROL PART II.2 LMIs IN SYSTEMS CONTROL STATE-SPACE METHODS PERFORMANCE ANALYSIS and SYNTHESIS Denis ARZELIER www.laas.fr/ arzelier arzelier@laas.fr 15
COURSE ON LMI OPTIMIZATION WITH APPLICATIONS IN CONTROL PART II.2 LMIs IN SYSTEMS CONTROL STATE-SPACE METHODS PERFORMANCE ANALYSIS and SYNTHESIS Denis ARZELIER www.laas.fr/ arzelier arzelier@laas.fr 15
Math 471 (Numerical methods) Chapter 3 (second half). System of equations
 Math 47 (Numerical methods) Chapter 3 (second half). System of equations Overlap 3.5 3.8 of Bradie 3.5 LU factorization w/o pivoting. Motivation: ( ) A I Gaussian Elimination (U L ) where U is upper triangular
Math 47 (Numerical methods) Chapter 3 (second half). System of equations Overlap 3.5 3.8 of Bradie 3.5 LU factorization w/o pivoting. Motivation: ( ) A I Gaussian Elimination (U L ) where U is upper triangular
Computational Methods for Feedback Control in Damped Gyroscopic Second-order Systems 1
 Computational Methods for Feedback Control in Damped Gyroscopic Second-order Systems 1 B. N. Datta, IEEE Fellow 2 D. R. Sarkissian 3 Abstract Two new computationally viable algorithms are proposed for
Computational Methods for Feedback Control in Damped Gyroscopic Second-order Systems 1 B. N. Datta, IEEE Fellow 2 D. R. Sarkissian 3 Abstract Two new computationally viable algorithms are proposed for
Iterative Encoder-Controller Design for Feedback Control Over Noisy Channels
 IEEE TRANSACTIONS ON AUTOMATIC CONTROL 1 Iterative Encoder-Controller Design for Feedback Control Over Noisy Channels Lei Bao, Member, IEEE, Mikael Skoglund, Senior Member, IEEE, and Karl Henrik Johansson,
IEEE TRANSACTIONS ON AUTOMATIC CONTROL 1 Iterative Encoder-Controller Design for Feedback Control Over Noisy Channels Lei Bao, Member, IEEE, Mikael Skoglund, Senior Member, IEEE, and Karl Henrik Johansson,
A Short Course on Frame Theory
 A Short Course on Frame Theory Veniamin I. Morgenshtern and Helmut Bölcskei ETH Zurich, 8092 Zurich, Switzerland E-mail: {vmorgens, boelcskei}@nari.ee.ethz.ch April 2, 20 Hilbert spaces [, Def. 3.-] and
A Short Course on Frame Theory Veniamin I. Morgenshtern and Helmut Bölcskei ETH Zurich, 8092 Zurich, Switzerland E-mail: {vmorgens, boelcskei}@nari.ee.ethz.ch April 2, 20 Hilbert spaces [, Def. 3.-] and
Stability of linear time-varying systems through quadratically parameter-dependent Lyapunov functions
 Stability of linear time-varying systems through quadratically parameter-dependent Lyapunov functions Vinícius F. Montagner Department of Telematics Pedro L. D. Peres School of Electrical and Computer
Stability of linear time-varying systems through quadratically parameter-dependent Lyapunov functions Vinícius F. Montagner Department of Telematics Pedro L. D. Peres School of Electrical and Computer
Delay-dependent Stability Analysis for Markovian Jump Systems with Interval Time-varying-delays
 International Journal of Automation and Computing 7(2), May 2010, 224-229 DOI: 10.1007/s11633-010-0224-2 Delay-dependent Stability Analysis for Markovian Jump Systems with Interval Time-varying-delays
International Journal of Automation and Computing 7(2), May 2010, 224-229 DOI: 10.1007/s11633-010-0224-2 Delay-dependent Stability Analysis for Markovian Jump Systems with Interval Time-varying-delays
Global stabilization of feedforward systems with exponentially unstable Jacobian linearization
 Global stabilization of feedforward systems with exponentially unstable Jacobian linearization F Grognard, R Sepulchre, G Bastin Center for Systems Engineering and Applied Mechanics Université catholique
Global stabilization of feedforward systems with exponentially unstable Jacobian linearization F Grognard, R Sepulchre, G Bastin Center for Systems Engineering and Applied Mechanics Université catholique
Übersetzungshilfe / Translation aid (English) To be returned at the end of the exam!
 Prüfung Regelungstechnik I (Control Systems I) Prof. Dr. Lino Guzzella 3.. 24 Übersetzungshilfe / Translation aid (English) To be returned at the end of the exam! Do not mark up this translation aid -
Prüfung Regelungstechnik I (Control Systems I) Prof. Dr. Lino Guzzella 3.. 24 Übersetzungshilfe / Translation aid (English) To be returned at the end of the exam! Do not mark up this translation aid -
Andrea Zanchettin Automatic Control AUTOMATIC CONTROL. Andrea M. Zanchettin, PhD Spring Semester, Linear systems (frequency domain)
 1 AUTOMATIC CONTROL Andrea M. Zanchettin, PhD Spring Semester, 2018 Linear systems (frequency domain) 2 Motivations Consider an LTI system Thanks to the Lagrange s formula we can compute the motion of
1 AUTOMATIC CONTROL Andrea M. Zanchettin, PhD Spring Semester, 2018 Linear systems (frequency domain) 2 Motivations Consider an LTI system Thanks to the Lagrange s formula we can compute the motion of
Iterative Learning Control Analysis and Design I
 Iterative Learning Control Analysis and Design I Electronics and Computer Science University of Southampton Southampton, SO17 1BJ, UK etar@ecs.soton.ac.uk http://www.ecs.soton.ac.uk/ Contents Basics Representations
Iterative Learning Control Analysis and Design I Electronics and Computer Science University of Southampton Southampton, SO17 1BJ, UK etar@ecs.soton.ac.uk http://www.ecs.soton.ac.uk/ Contents Basics Representations
Introduction to Control (034040) lecture no. 2
 Introduction to Control (034040) lecture no. 2 Leonid Mirkin Faculty of Mechanical Engineering Technion IIT Setup: Abstract control problem to begin with y P(s) u where P is a plant u is a control signal
Introduction to Control (034040) lecture no. 2 Leonid Mirkin Faculty of Mechanical Engineering Technion IIT Setup: Abstract control problem to begin with y P(s) u where P is a plant u is a control signal
Return Difference Function and Closed-Loop Roots Single-Input/Single-Output Control Systems
 Spectral Properties of Linear- Quadratic Regulators Robert Stengel Optimal Control and Estimation MAE 546 Princeton University, 2018! Stability margins of single-input/singleoutput (SISO) systems! Characterizations
Spectral Properties of Linear- Quadratic Regulators Robert Stengel Optimal Control and Estimation MAE 546 Princeton University, 2018! Stability margins of single-input/singleoutput (SISO) systems! Characterizations
Passivity Indices for Symmetrically Interconnected Distributed Systems
 9th Mediterranean Conference on Control and Automation Aquis Corfu Holiday Palace, Corfu, Greece June 0-3, 0 TuAT Passivity Indices for Symmetrically Interconnected Distributed Systems Po Wu and Panos
9th Mediterranean Conference on Control and Automation Aquis Corfu Holiday Palace, Corfu, Greece June 0-3, 0 TuAT Passivity Indices for Symmetrically Interconnected Distributed Systems Po Wu and Panos
Control of Mobile Robots
 Control of Mobile Robots Regulation and trajectory tracking Prof. Luca Bascetta (luca.bascetta@polimi.it) Politecnico di Milano Dipartimento di Elettronica, Informazione e Bioingegneria Organization and
Control of Mobile Robots Regulation and trajectory tracking Prof. Luca Bascetta (luca.bascetta@polimi.it) Politecnico di Milano Dipartimento di Elettronica, Informazione e Bioingegneria Organization and
Complex Numbers. The set of complex numbers can be defined as the set of pairs of real numbers, {(x, y)}, with two operations: (i) addition,
 Complex Numbers Complex Algebra The set of complex numbers can be defined as the set of pairs of real numbers, {(x, y)}, with two operations: (i) addition, and (ii) complex multiplication, (x 1, y 1 )
Complex Numbers Complex Algebra The set of complex numbers can be defined as the set of pairs of real numbers, {(x, y)}, with two operations: (i) addition, and (ii) complex multiplication, (x 1, y 1 )
On Spectral Factorization and Riccati Equations for Time-Varying Systems in Discrete Time
 On Spectral Factorization and Riccati Equations for Time-Varying Systems in Discrete Time Alle-Jan van der Veen and Michel Verhaegen Delft University of Technology Department of Electrical Engineering
On Spectral Factorization and Riccati Equations for Time-Varying Systems in Discrete Time Alle-Jan van der Veen and Michel Verhaegen Delft University of Technology Department of Electrical Engineering
NOWADAYS, many control applications have some control
 1650 IEEE TRANSACTIONS ON AUTOMATIC CONTROL, VOL 49, NO 10, OCTOBER 2004 Input Output Stability Properties of Networked Control Systems D Nešić, Senior Member, IEEE, A R Teel, Fellow, IEEE Abstract Results
1650 IEEE TRANSACTIONS ON AUTOMATIC CONTROL, VOL 49, NO 10, OCTOBER 2004 Input Output Stability Properties of Networked Control Systems D Nešić, Senior Member, IEEE, A R Teel, Fellow, IEEE Abstract Results
Fundamental Design Limitations of the General Control Configuration
 IEEE TRANSACTIONS ON AUTOMATIC CONTROL, VOL 48, NO 8, AUGUST 2003 1355 Fundamental Design Limitations of the General Control Configuration Jim S Freudenberg, Fellow, IEEE, C V Hollot, Senior Member, IEEE,
IEEE TRANSACTIONS ON AUTOMATIC CONTROL, VOL 48, NO 8, AUGUST 2003 1355 Fundamental Design Limitations of the General Control Configuration Jim S Freudenberg, Fellow, IEEE, C V Hollot, Senior Member, IEEE,
The Rationale for Second Level Adaptation
 The Rationale for Second Level Adaptation Kumpati S. Narendra, Yu Wang and Wei Chen Center for Systems Science, Yale University arxiv:1510.04989v1 [cs.sy] 16 Oct 2015 Abstract Recently, a new approach
The Rationale for Second Level Adaptation Kumpati S. Narendra, Yu Wang and Wei Chen Center for Systems Science, Yale University arxiv:1510.04989v1 [cs.sy] 16 Oct 2015 Abstract Recently, a new approach
1030 IEEE TRANSACTIONS ON AUTOMATIC CONTROL, VOL. 56, NO. 5, MAY 2011
 1030 IEEE TRANSACTIONS ON AUTOMATIC CONTROL, VOL 56, NO 5, MAY 2011 L L 2 Low-Gain Feedback: Their Properties, Characterizations Applications in Constrained Control Bin Zhou, Member, IEEE, Zongli Lin,
1030 IEEE TRANSACTIONS ON AUTOMATIC CONTROL, VOL 56, NO 5, MAY 2011 L L 2 Low-Gain Feedback: Their Properties, Characterizations Applications in Constrained Control Bin Zhou, Member, IEEE, Zongli Lin,
and Mixed / Control of Dual-Actuator Hard Disk Drive via LMIs
 and Mixed / Control of Dual-Actuator Hard Disk Drive via LMIs Nasser Mohamad Zadeh Electrical Engineering Department Tarbiat Modares University Tehran, Iran mohamadzadeh@ieee.org Ramin Amirifar Electrical
and Mixed / Control of Dual-Actuator Hard Disk Drive via LMIs Nasser Mohamad Zadeh Electrical Engineering Department Tarbiat Modares University Tehran, Iran mohamadzadeh@ieee.org Ramin Amirifar Electrical
Didier HENRION henrion
 GRADUATE COURSE ON POLYNOMIAL METHODS FOR ROBUST CONTROL PART II.1 ROBUST STABILITY ANALYSIS: POLYTOPIC UNCERTAINTY Didier HENRION www.laas.fr/ henrion henrion@laas.fr Cité de l espace with Ariane launcher
GRADUATE COURSE ON POLYNOMIAL METHODS FOR ROBUST CONTROL PART II.1 ROBUST STABILITY ANALYSIS: POLYTOPIC UNCERTAINTY Didier HENRION www.laas.fr/ henrion henrion@laas.fr Cité de l espace with Ariane launcher
Math 676. A compactness theorem for the idele group. and by the product formula it lies in the kernel (A K )1 of the continuous idelic norm
 Math 676. A compactness theorem for the idele group 1. Introduction Let K be a global field, so K is naturally a discrete subgroup of the idele group A K and by the product formula it lies in the kernel
Math 676. A compactness theorem for the idele group 1. Introduction Let K be a global field, so K is naturally a discrete subgroup of the idele group A K and by the product formula it lies in the kernel
Lecture Note 5: Semidefinite Programming for Stability Analysis
 ECE7850: Hybrid Systems:Theory and Applications Lecture Note 5: Semidefinite Programming for Stability Analysis Wei Zhang Assistant Professor Department of Electrical and Computer Engineering Ohio State
ECE7850: Hybrid Systems:Theory and Applications Lecture Note 5: Semidefinite Programming for Stability Analysis Wei Zhang Assistant Professor Department of Electrical and Computer Engineering Ohio State
