Scalar Optimisation Part 1
|
|
|
- Cecil White
- 5 years ago
- Views:
Transcription
1 calar Optimisation Part 1 Michael O Boyle January, 2014
2 1 Course tructure L1 Introduction and Recap 4/5 lectures on classical optimisation 2 lectures on scalar optimisation Today example optimisations Next lecture dataflow framework and A 5 lectures on high level approaches 4-5 lectures on adaptive compilation
3 2 Overview Machine dependent vs independent optimisations Redundant elimination example Local value numbering uper value numbering ominator value numbering Alternative general approach Global Redundancy Elimination Based on iterative dataflow analysis Other dataflow analysis: Live variable analysis
4 3 Optimisation Classification Machine independent vs dependent - not always a clear distinction. Main trends in architecture increased memory latency and exploitation of ILP are machine dependent Machine independent applicable to all. Eliminate redundant work, accesses. Use less expensive operations where possible Optimisation can be performed at source, IR, assembler, machine code level. Concentrate on machine independent scalar optimisation - IR level. Optimisation = analysis + transformation. Form depends on IR - impact on complexity.
5 4 Redundant expression elimination An expression x + y is redundant if already evaluated and not redefined Value numbering: Associate numbers with operators/operands and hash lookup in table Hash (+,x,y) return value number If value number already there replace with reference to variable a 3 = x 1 + y 2 b 4 = x 1 + y 2 a 3 = 17 c 5 = x 1 + y 2 a 3 = x 1 + y 2 b 4 = a 3 a 3 = 17 c 5 = a 3!! a 3 0 = x y 2 0 b 4 0 = x y 2 0 a 3 1 = 17 c 5 0 = x y 2 0 a 3 0 = x y 2 0 b 4 0 = a 3 0 a 3 1 = 17 4 c 5 0 = a 3 0 Can be extended to handle larger scope based on dominators. Fails in presence of general control-flow
6 Example: CFG rep of program. Basic blocks + control-flow. 5 A m = a+b n = a+b L B p = c + d r = c + d L C q = a+b r = c+d e = b + 18 s = a + b u = e + f E e = a + 17 t = c + d u = e + f F v = a + b w = c + d x = e + f G y = a + b z = c + d LVN removes some but not all of redundant expressions: L vs
7 6 uper Local Value numbering VN Basic blocks(bb) have just one entry and exit. Extended BB: (EBB) A tree of BBs {B 1,..., B n } where B 1 may have multiple predecessors. All others have a single unique predecessor but possibly multiple exits. This tree is only entered at the root. In our example 3 EBBs (A,B,C,,E), (F), (G) VN considers each path within an EBB as single block o (A,B), (A,C,), (A,C,E) are considered paths for LVN
8 7 Example: Extended Basic Blocks. A m = a+b n = a+b L B p = c + d r = c + d L C q = a+b r = c+d e = b + 18 s = a + b u = e + f E e = a + 17 t = c + d u = e + f F v = a + b w = c + d x = e + f G y = a + b z = c + d
9 8 ominator Value numbering VN VN based on EBBs fail when there are join paths in the graph. Use concept of dominators. Basic idea if reaching paths to a node share common ancestor nodes, then these can be used for redundancy elimination A node X strictly dominates Y (X >> Y ) if X Y and if X appears on every path from the graph entry to Y Node A B C E F G OM - A A A,C A,C A,C A IOM - A A C C C A IOM- immediate dominator - forms a dominator tree. o if expression appears in F but defined in A,C then redundant
10 9 Example: ominator value numbering. A m = a+b n = a+b L B p = c + d r = c + d L C q = a+b r = c+d e = b + 18 s = a + b u = e + f E e = a + 17 t = c + d u = e + f F v = a + b w = c + d x = e + f G y = a + b z = c + d What about the remaining two s in G and F
11 10 ataflow analysis A formal program analysis that has a wide range of application. escribed property of a program at a particular point in set based recurrence equations Assumes a control-flow graph(cfg) consisting of nodes (basic blocks) and edges: control-flow etermines property at a point in the program as a function of local information and approximation of global information Approx solutions will converge to exact solution in finite number of iterations for finite lattices - more detail next lecture
12 ataflow analysis for redundant expressions: calculate available EExpr(b) - subexpressions not overwritten in this block b (local) NOTKILLE(b) - subexpressions that are not killed (local) AV AIL(b) = p pred(b) (EExpr(p) (AV AIL(p) NOTKILLE(p))) EExpr(b) and NOTKILLE(b) can be calculated locally for each basic block b Initialise AV AIL(b) = For each block in turn calculate AV AIL(b) based on predecessors Keep repeating the procedure till results stabilise. 11
13 Find available expressions part 1 Node A B C E F G pred - A A C C,E B,F EExpr a+b c+d a+b b+18 a+17 a+b a+b c+d a+b c+d c+d c+d e+f e+f e+f Kill e+f e+f Calculate Avail(b) for each Basic Block b starting at block A AV AIL(B) = (EExpr(A) (AV AIL(A) NOTKILLE(A))) = {a + b} ( U) = {a + b} AV AIL(C) = (EExpr(A) (AV AIL(A) NOTKILLE(A))) = {a + b} ( U) = {a + b} 12
14 and E are the same Find available expressions part 2 AV AIL() = (EExpr(C) (AV AIL(C) NOTKILLE(C))) = {a + b, c + d} ({a + b} U) = {a + b, c + d} AV AIL(E) = (EExpr(C) (AV AIL(C) NOTKILLE(C))) = {a + b, c + d} ({a + b} U) = {a + b, c + d} F is a join point: 2 predecessors AV AIL(F) = (EExpr() (AV AIL() NOTKILLE())) (EExpr(E) (AV AIL(E) NOTKILLE(E)) = {b + 18, a + b, e + f} ({a + b,c + d} U {e + f}) {a + 17, c + d, e + f} ({a + b,c + d} U {e + f}) = {a + b, c + d, e + f} 13
15 G another join point Find available expressions part 3 AV AIL(G) = (EExpr(B) (AV AIL(B) NOTKILLE(B))) (EExpr(F) (AV AIL(F) NOTKILLE(F))) Calculate this one yourselves 14
16 Example: Global redundancy elim using AVAIL() 15 A m = a+b n = a+b L B p = c + d r = c + d L C q = a+b r = c+d e = b + 18 s = a + b u = e + f E e = a + 17 t = c + d u = e + f F v = a + b w = c + d x = e + f G G y = a + b z = c + d G
17 16 ummary Levels of optimisations Redundant expression elimination LVN, VN, VN Introduced dataflow as a generic optimisation framework Iterative solution to equations Next time: More detailed examination of dataflow and A
Scalar Optimisation Part 2
 Scalar Optimisation Part 2 Michael O Boyle January 2014 1 Course Structure L1 Introduction and Recap 4-5 lectures on classical optimisation 2 lectures on scalar optimisation Last lecture on redundant expressions
Scalar Optimisation Part 2 Michael O Boyle January 2014 1 Course Structure L1 Introduction and Recap 4-5 lectures on classical optimisation 2 lectures on scalar optimisation Last lecture on redundant expressions
Lecture 10: Data Flow Analysis II
 CS 515 Programming Language and Compilers I Lecture 10: Data Flow Analysis II (The lectures are based on the slides copyrighted by Keith Cooper and Linda Torczon from Rice University.) Zheng (Eddy) Zhang
CS 515 Programming Language and Compilers I Lecture 10: Data Flow Analysis II (The lectures are based on the slides copyrighted by Keith Cooper and Linda Torczon from Rice University.) Zheng (Eddy) Zhang
Lecture 11: Data Flow Analysis III
 CS 515 Programming Language and Compilers I Lecture 11: Data Flow Analysis III (The lectures are based on the slides copyrighted by Keith Cooper and Linda Torczon from Rice University.) Zheng (Eddy) Zhang
CS 515 Programming Language and Compilers I Lecture 11: Data Flow Analysis III (The lectures are based on the slides copyrighted by Keith Cooper and Linda Torczon from Rice University.) Zheng (Eddy) Zhang
CSE P 501 Compilers. Value Numbering & Op;miza;ons Hal Perkins Winter UW CSE P 501 Winter 2016 S-1
 CSE P 501 Compilers Value Numbering & Op;miza;ons Hal Perkins Winter 2016 UW CSE P 501 Winter 2016 S-1 Agenda Op;miza;on (Review) Goals Scope: local, superlocal, regional, global (intraprocedural), interprocedural
CSE P 501 Compilers Value Numbering & Op;miza;ons Hal Perkins Winter 2016 UW CSE P 501 Winter 2016 S-1 Agenda Op;miza;on (Review) Goals Scope: local, superlocal, regional, global (intraprocedural), interprocedural
Lecture 5 Introduction to Data Flow Analysis
 Lecture 5 Introduction to Data Flow Analysis I. Structure of data flow analysis II. III. IV. Example 1: Reaching definition analysis Example 2: Liveness analysis Framework Phillip B. Gibbons 15-745: Intro
Lecture 5 Introduction to Data Flow Analysis I. Structure of data flow analysis II. III. IV. Example 1: Reaching definition analysis Example 2: Liveness analysis Framework Phillip B. Gibbons 15-745: Intro
Dataflow Analysis Lecture 2. Simple Constant Propagation. A sample program int fib10(void) {
 -4 Lecture Dataflow Analysis Basic Blocks Related Optimizations Copyright Seth Copen Goldstein 00 Dataflow Analysis Last time we looked at code transformations Constant propagation Copy propagation Common
-4 Lecture Dataflow Analysis Basic Blocks Related Optimizations Copyright Seth Copen Goldstein 00 Dataflow Analysis Last time we looked at code transformations Constant propagation Copy propagation Common
Adventures in Dataflow Analysis
 Adventures in Dataflow Analysis CSE 401 Section 9-ish Jack Eggleston, Aaron Johnston, & Nate Yazdani Announcements - Code Generation due Announcements - Code Generation due - Compiler Additions due next
Adventures in Dataflow Analysis CSE 401 Section 9-ish Jack Eggleston, Aaron Johnston, & Nate Yazdani Announcements - Code Generation due Announcements - Code Generation due - Compiler Additions due next
Dataflow Analysis. A sample program int fib10(void) { int n = 10; int older = 0; int old = 1; Simple Constant Propagation
 -74 Lecture 2 Dataflow Analysis Basic Blocks Related Optimizations SSA Copyright Seth Copen Goldstein 200-8 Dataflow Analysis Last time we looked at code transformations Constant propagation Copy propagation
-74 Lecture 2 Dataflow Analysis Basic Blocks Related Optimizations SSA Copyright Seth Copen Goldstein 200-8 Dataflow Analysis Last time we looked at code transformations Constant propagation Copy propagation
Topic-I-C Dataflow Analysis
 Topic-I-C Dataflow Analysis 2012/3/2 \course\cpeg421-08s\topic4-a.ppt 1 Global Dataflow Analysis Motivation We need to know variable def and use information between basic blocks for: constant folding dead-code
Topic-I-C Dataflow Analysis 2012/3/2 \course\cpeg421-08s\topic4-a.ppt 1 Global Dataflow Analysis Motivation We need to know variable def and use information between basic blocks for: constant folding dead-code
Compiler Design. Data Flow Analysis. Hwansoo Han
 Compiler Design Data Flow Analysis Hwansoo Han Control Flow Graph What is CFG? Represents program structure for internal use of compilers Used in various program analyses Generated from AST or a sequential
Compiler Design Data Flow Analysis Hwansoo Han Control Flow Graph What is CFG? Represents program structure for internal use of compilers Used in various program analyses Generated from AST or a sequential
CMSC 631 Program Analysis and Understanding. Spring Data Flow Analysis
 CMSC 631 Program Analysis and Understanding Spring 2013 Data Flow Analysis Data Flow Analysis A framework for proving facts about programs Reasons about lots of little facts Little or no interaction between
CMSC 631 Program Analysis and Understanding Spring 2013 Data Flow Analysis Data Flow Analysis A framework for proving facts about programs Reasons about lots of little facts Little or no interaction between
Introduction to data-flow analysis. Data-flow analysis. Control-flow graphs. Data-flow analysis. Example: liveness. Requirements
 Data-flow analysis Michel Schinz based on material by Erik Stenman and Michael Schwartzbach Introduction to data-flow analysis Data-flow analysis Example: liveness Data-flow analysis is a global analysis
Data-flow analysis Michel Schinz based on material by Erik Stenman and Michael Schwartzbach Introduction to data-flow analysis Data-flow analysis Example: liveness Data-flow analysis is a global analysis
Data flow analysis. DataFlow analysis
 Data flow analysis DataFlow analysis compile time reasoning about the runtime flow of values in the program represent facts about runtime behavior represent effect of executing each basic block propagate
Data flow analysis DataFlow analysis compile time reasoning about the runtime flow of values in the program represent facts about runtime behavior represent effect of executing each basic block propagate
Data Flow Analysis. Lecture 6 ECS 240. ECS 240 Data Flow Analysis 1
 Data Flow Analysis Lecture 6 ECS 240 ECS 240 Data Flow Analysis 1 The Plan Introduce a few example analyses Generalize to see the underlying theory Discuss some more advanced issues ECS 240 Data Flow Analysis
Data Flow Analysis Lecture 6 ECS 240 ECS 240 Data Flow Analysis 1 The Plan Introduce a few example analyses Generalize to see the underlying theory Discuss some more advanced issues ECS 240 Data Flow Analysis
Generalizing Data-flow Analysis
 Generalizing Data-flow Analysis Announcements PA1 grades have been posted Today Other types of data-flow analysis Reaching definitions, available expressions, reaching constants Abstracting data-flow analysis
Generalizing Data-flow Analysis Announcements PA1 grades have been posted Today Other types of data-flow analysis Reaching definitions, available expressions, reaching constants Abstracting data-flow analysis
Beyond Superlocal: Dominators, Data-Flow Analysis, and DVNT. COMP 506 Rice University Spring target code. source code OpJmizer
 COMP 506 Rice University Spring 2017 Beyond Superlocal: Dominators, Data-Flow Analysis, and DVNT source code Front End IR OpJmizer IR Back End target code Copyright 2017, Keith D. Cooper & Linda Torczon,
COMP 506 Rice University Spring 2017 Beyond Superlocal: Dominators, Data-Flow Analysis, and DVNT source code Front End IR OpJmizer IR Back End target code Copyright 2017, Keith D. Cooper & Linda Torczon,
Lecture 4 Introduc-on to Data Flow Analysis
 Lecture 4 Introduc-on to Data Flow Analysis I. Structure of data flow analysis II. Example 1: Reaching defini?on analysis III. Example 2: Liveness analysis IV. Generaliza?on 15-745: Intro to Data Flow
Lecture 4 Introduc-on to Data Flow Analysis I. Structure of data flow analysis II. Example 1: Reaching defini?on analysis III. Example 2: Liveness analysis IV. Generaliza?on 15-745: Intro to Data Flow
What is SSA? each assignment to a variable is given a unique name all of the uses reached by that assignment are renamed
 Another Form of Data-Flow Analysis Propagation of values for a variable reference, where is the value produced? for a variable definition, where is the value consumed? Possible answers reaching definitions,
Another Form of Data-Flow Analysis Propagation of values for a variable reference, where is the value produced? for a variable definition, where is the value consumed? Possible answers reaching definitions,
Dataflow analysis. Theory and Applications. cs6463 1
 Dataflow analysis Theory and Applications cs6463 1 Control-flow graph Graphical representation of runtime control-flow paths Nodes of graph: basic blocks (straight-line computations) Edges of graph: flows
Dataflow analysis Theory and Applications cs6463 1 Control-flow graph Graphical representation of runtime control-flow paths Nodes of graph: basic blocks (straight-line computations) Edges of graph: flows
CSC D70: Compiler Optimization Dataflow-2 and Loops
 CSC D70: Compiler Optimization Dataflow-2 and Loops Prof. Gennady Pekhimenko University of Toronto Winter 2018 The content of this lecture is adapted from the lectures of Todd Mowry and Phillip Gibbons
CSC D70: Compiler Optimization Dataflow-2 and Loops Prof. Gennady Pekhimenko University of Toronto Winter 2018 The content of this lecture is adapted from the lectures of Todd Mowry and Phillip Gibbons
3/11/18. Final Code Generation and Code Optimization
 Final Code Generation and Code Optimization 1 2 3 for ( i=0; i < N; i++) { base = &a[0]; crt = *(base + i); } original code base = &a[0]; for ( i=0; i < N; i++) { crt = *(base + i); } optimized code e1
Final Code Generation and Code Optimization 1 2 3 for ( i=0; i < N; i++) { base = &a[0]; crt = *(base + i); } original code base = &a[0]; for ( i=0; i < N; i++) { crt = *(base + i); } optimized code e1
We define a dataflow framework. A dataflow framework consists of:
 So far been talking about various dataflow problems (e.g. reaching definitions, live variable analysis) in very informal terms. Now we will discuss a more fundamental approach to handle many of the dataflow
So far been talking about various dataflow problems (e.g. reaching definitions, live variable analysis) in very informal terms. Now we will discuss a more fundamental approach to handle many of the dataflow
Program Analysis. Lecture 5. Rayna Dimitrova WS 2016/2017
 Program Analysis Lecture 5 Rayna Dimitrova WS 2016/2017 2/21 Recap: Constant propagation analysis Goal: For each program point, determine whether a variale has a constant value whenever an execution reaches
Program Analysis Lecture 5 Rayna Dimitrova WS 2016/2017 2/21 Recap: Constant propagation analysis Goal: For each program point, determine whether a variale has a constant value whenever an execution reaches
Compiling Techniques
 Lecture 11: Introduction to 13 November 2015 Table of contents 1 Introduction Overview The Backend The Big Picture 2 Code Shape Overview Introduction Overview The Backend The Big Picture Source code FrontEnd
Lecture 11: Introduction to 13 November 2015 Table of contents 1 Introduction Overview The Backend The Big Picture 2 Code Shape Overview Introduction Overview The Backend The Big Picture Source code FrontEnd
Data Flow Analysis (I)
 Compiler Design Data Flow Analysis (I) Hwansoo Han Control Flow Graph What is CFG? Represents program structure for internal use of compilers Used in various program analyses Generated from AST or a sequential
Compiler Design Data Flow Analysis (I) Hwansoo Han Control Flow Graph What is CFG? Represents program structure for internal use of compilers Used in various program analyses Generated from AST or a sequential
MEE224: Engineering Mechanics Lecture 4
 Lecture 4: Structural Analysis Part 1: Trusses So far we have only analysed forces and moments on a single rigid body, i.e. bars. Remember that a structure is a formed by and this lecture will investigate
Lecture 4: Structural Analysis Part 1: Trusses So far we have only analysed forces and moments on a single rigid body, i.e. bars. Remember that a structure is a formed by and this lecture will investigate
MIT Loop Optimizations. Martin Rinard
 MIT 6.035 Loop Optimizations Martin Rinard Loop Optimizations Important because lots of computation occurs in loops We will study two optimizations Loop-invariant code motion Induction variable elimination
MIT 6.035 Loop Optimizations Martin Rinard Loop Optimizations Important because lots of computation occurs in loops We will study two optimizations Loop-invariant code motion Induction variable elimination
(b). Identify all basic blocks in your three address code. B1: 1; B2: 2; B3: 3,4,5,6; B4: 7,8,9; B5: 10; B6: 11; B7: 12,13,14; B8: 15;
 (a). Translate the program into three address code as defined in Section 6.2, dragon book. (1) i := 2 (2) if i > n goto (7) (3) a[i] := TRUE (4) t2 := i+1 (5) i := t2 (6) goto (2) (7) count := 0 (8) s
(a). Translate the program into three address code as defined in Section 6.2, dragon book. (1) i := 2 (2) if i > n goto (7) (3) a[i] := TRUE (4) t2 := i+1 (5) i := t2 (6) goto (2) (7) count := 0 (8) s
Compiler Design Spring 2017
 Compiler Design Spring 2017 8.5 Reaching definitions Dr. Zoltán Majó Compiler Group Java HotSpot Virtual Machine Oracle Corporation Admin issues Brief reminder: Code review takes place today @ 15:15 You
Compiler Design Spring 2017 8.5 Reaching definitions Dr. Zoltán Majó Compiler Group Java HotSpot Virtual Machine Oracle Corporation Admin issues Brief reminder: Code review takes place today @ 15:15 You
Register Allocation. Maryam Siahbani CMPT 379 4/5/2016 1
 Register Allocation Maryam Siahbani CMPT 379 4/5/2016 1 Register Allocation Intermediate code uses unlimited temporaries Simplifying code generation and optimization Complicates final translation to assembly
Register Allocation Maryam Siahbani CMPT 379 4/5/2016 1 Register Allocation Intermediate code uses unlimited temporaries Simplifying code generation and optimization Complicates final translation to assembly
Dataflow Analysis. Chapter 9, Section 9.2, 9.3, 9.4
 Dataflow Analysis Chapter 9, Section 9.2, 9.3, 9.4 2 Dataflow Analysis Dataflow analysis is a sub area of static program analysis Used in the compiler back end for optimizations of three address code and
Dataflow Analysis Chapter 9, Section 9.2, 9.3, 9.4 2 Dataflow Analysis Dataflow analysis is a sub area of static program analysis Used in the compiler back end for optimizations of three address code and
Construction of Static Single-Assignment Form
 COMP 506 Rice University Spring 2018 Construction of Static Single-Assignment Form Part II source IR IR target code Front End Optimizer Back End code Copyright 2018, Keith D. Cooper & Linda Torczon, all
COMP 506 Rice University Spring 2018 Construction of Static Single-Assignment Form Part II source IR IR target code Front End Optimizer Back End code Copyright 2018, Keith D. Cooper & Linda Torczon, all
Worst-Case Execution Time Analysis. LS 12, TU Dortmund
 Worst-Case Execution Time Analysis Prof. Dr. Jian-Jia Chen LS 12, TU Dortmund 02, 03 May 2016 Prof. Dr. Jian-Jia Chen (LS 12, TU Dortmund) 1 / 53 Most Essential Assumptions for Real-Time Systems Upper
Worst-Case Execution Time Analysis Prof. Dr. Jian-Jia Chen LS 12, TU Dortmund 02, 03 May 2016 Prof. Dr. Jian-Jia Chen (LS 12, TU Dortmund) 1 / 53 Most Essential Assumptions for Real-Time Systems Upper
COSE312: Compilers. Lecture 17 Intermediate Representation (2)
 COSE312: Compilers Lecture 17 Intermediate Representation (2) Hakjoo Oh 2017 Spring Hakjoo Oh COSE312 2017 Spring, Lecture 17 May 31, 2017 1 / 19 Common Intermediate Representations Three-address code
COSE312: Compilers Lecture 17 Intermediate Representation (2) Hakjoo Oh 2017 Spring Hakjoo Oh COSE312 2017 Spring, Lecture 17 May 31, 2017 1 / 19 Common Intermediate Representations Three-address code
Verifying the LLVM. Steve Zdancewic DeepSpec Summer School 2017
 Verifying the LLVM Steve Zdancewic DeepSpec Summer School 2017 Vminus OperaAonal SemanAcs Only 5 kinds of instrucaons: Binary arithmeac Memory Load Memory Store Terminators Phi nodes What is the state
Verifying the LLVM Steve Zdancewic DeepSpec Summer School 2017 Vminus OperaAonal SemanAcs Only 5 kinds of instrucaons: Binary arithmeac Memory Load Memory Store Terminators Phi nodes What is the state
Before We Start. The Pumping Lemma. Languages. Context Free Languages. Plan for today. Now our picture looks like. Any questions?
 Before We Start The Pumping Lemma Any questions? The Lemma & Decision/ Languages Future Exam Question What is a language? What is a class of languages? Context Free Languages Context Free Languages(CFL)
Before We Start The Pumping Lemma Any questions? The Lemma & Decision/ Languages Future Exam Question What is a language? What is a class of languages? Context Free Languages Context Free Languages(CFL)
Compiler Optimisation
 Compiler Optimisation 8 Dependence Analysis Hugh Leather IF 1.18a hleather@inf.ed.ac.uk Institute for Computing Systems Architecture School of Informatics University of Edinburgh 2018 Introduction This
Compiler Optimisation 8 Dependence Analysis Hugh Leather IF 1.18a hleather@inf.ed.ac.uk Institute for Computing Systems Architecture School of Informatics University of Edinburgh 2018 Introduction This
Department of Computer Science and Engineering, IIT Kanpur, INDIA. Code Optimization. Sanjeev K Aggarwal Code Optimization 1 of I
 Code Optimization Sanjeev K Aggarwal Code Optimization 1 of 23 2007-08-I Code Optimization int a,b,c,d ldw a,r1 add r1,r2,r3 c = a+b ldw b,r2 add r3,1,r4 d = c+1 add r1,r2,r3 stw r3,c ldw c,r3 add r3,1,r4
Code Optimization Sanjeev K Aggarwal Code Optimization 1 of 23 2007-08-I Code Optimization int a,b,c,d ldw a,r1 add r1,r2,r3 c = a+b ldw b,r2 add r3,1,r4 d = c+1 add r1,r2,r3 stw r3,c ldw c,r3 add r3,1,r4
CSC D70: Compiler Optimization Static Single Assignment (SSA)
 CSC D70: Compiler Optimization Static Single Assignment (SSA) Prof. Gennady Pekhimenko University of Toronto Winter 08 The content of this lecture is adapted from the lectures of Todd Mowry and Phillip
CSC D70: Compiler Optimization Static Single Assignment (SSA) Prof. Gennady Pekhimenko University of Toronto Winter 08 The content of this lecture is adapted from the lectures of Todd Mowry and Phillip
Static Program Analysis
 Static Program Analysis Xiangyu Zhang The slides are compiled from Alex Aiken s Michael D. Ernst s Sorin Lerner s A Scary Outline Type-based analysis Data-flow analysis Abstract interpretation Theorem
Static Program Analysis Xiangyu Zhang The slides are compiled from Alex Aiken s Michael D. Ernst s Sorin Lerner s A Scary Outline Type-based analysis Data-flow analysis Abstract interpretation Theorem
ECE 5775 (Fall 17) High-Level Digital Design Automation. Scheduling: Exact Methods
 ECE 5775 (Fall 17) High-Level Digital Design Automation Scheduling: Exact Methods Announcements Sign up for the first student-led discussions today One slot remaining Presenters for the 1st session will
ECE 5775 (Fall 17) High-Level Digital Design Automation Scheduling: Exact Methods Announcements Sign up for the first student-led discussions today One slot remaining Presenters for the 1st session will
Data-Flow Analysis. Compiler Design CSE 504. Preliminaries
 Data-Flow Analysis Compiler Design CSE 504 1 Preliminaries 2 Live Variables 3 Data Flow Equations 4 Other Analyses Last modifled: Thu May 02 2013 at 09:01:11 EDT Version: 1.3 15:28:44 2015/01/25 Compiled
Data-Flow Analysis Compiler Design CSE 504 1 Preliminaries 2 Live Variables 3 Data Flow Equations 4 Other Analyses Last modifled: Thu May 02 2013 at 09:01:11 EDT Version: 1.3 15:28:44 2015/01/25 Compiled
Communication Complexity
 Communication Complexity Jaikumar Radhakrishnan School of Technology and Computer Science Tata Institute of Fundamental Research Mumbai 31 May 2012 J 31 May 2012 1 / 13 Plan 1 Examples, the model, the
Communication Complexity Jaikumar Radhakrishnan School of Technology and Computer Science Tata Institute of Fundamental Research Mumbai 31 May 2012 J 31 May 2012 1 / 13 Plan 1 Examples, the model, the
ECE 5775 (Fall 17) High-Level Digital Design Automation. Control Flow Graph
 ECE 5775 (Fall 17) High-Level Digital Design Automation Control Flow Graph Announcements ECE colloquium on Monday 9/11 from 4:30pm, PHL 233 Smart Healthcare by Prof. Niraj Jha of Princeton Lab 1 is due
ECE 5775 (Fall 17) High-Level Digital Design Automation Control Flow Graph Announcements ECE colloquium on Monday 9/11 from 4:30pm, PHL 233 Smart Healthcare by Prof. Niraj Jha of Princeton Lab 1 is due
Graph Transformations T1 and T2
 Graph Transformations T1 and T2 We now introduce two graph transformations T1 and T2. Reducibility by successive application of these two transformations is equivalent to reducibility by intervals. The
Graph Transformations T1 and T2 We now introduce two graph transformations T1 and T2. Reducibility by successive application of these two transformations is equivalent to reducibility by intervals. The
Top-Down Parsing, Part II
 op-down Parsing, Part II Announcements Programming Project 1 due Friday, 11:59PM Office hours every day until then. ubmission instructions will be emailed out tonight. Where We Are ource Code Lexical Analysis
op-down Parsing, Part II Announcements Programming Project 1 due Friday, 11:59PM Office hours every day until then. ubmission instructions will be emailed out tonight. Where We Are ource Code Lexical Analysis
Variable Elimination (VE) Barak Sternberg
 Variable Elimination (VE) Barak Sternberg Basic Ideas in VE Example 1: Let G be a Chain Bayesian Graph: X 1 X 2 X n 1 X n How would one compute P X n = k? Using the CPDs: P X 2 = x = x Val X1 P X 1 = x
Variable Elimination (VE) Barak Sternberg Basic Ideas in VE Example 1: Let G be a Chain Bayesian Graph: X 1 X 2 X n 1 X n How would one compute P X n = k? Using the CPDs: P X 2 = x = x Val X1 P X 1 = x
Intelligent Systems (AI-2)
 Intelligent Systems (AI-2) Computer Science cpsc422, Lecture 11 Oct, 3, 2016 CPSC 422, Lecture 11 Slide 1 422 big picture: Where are we? Query Planning Deterministic Logics First Order Logics Ontologies
Intelligent Systems (AI-2) Computer Science cpsc422, Lecture 11 Oct, 3, 2016 CPSC 422, Lecture 11 Slide 1 422 big picture: Where are we? Query Planning Deterministic Logics First Order Logics Ontologies
Maximal Antichain Lattice Algorithms for Distributed Computatio
 Maximal Antichain Lattice Algorithms for Distributed Computations Vijay K. Garg Parallel and Distributed Systems Lab, Department of Electrical and Computer Engineering, The University of Texas at Austin,
Maximal Antichain Lattice Algorithms for Distributed Computations Vijay K. Garg Parallel and Distributed Systems Lab, Department of Electrical and Computer Engineering, The University of Texas at Austin,
Principles of Program Analysis: A Sampler of Approaches
 Principles of Program Analysis: A Sampler of Approaches Transparencies based on Chapter 1 of the book: Flemming Nielson, Hanne Riis Nielson and Chris Hankin: Principles of Program Analysis Springer Verlag
Principles of Program Analysis: A Sampler of Approaches Transparencies based on Chapter 1 of the book: Flemming Nielson, Hanne Riis Nielson and Chris Hankin: Principles of Program Analysis Springer Verlag
Dataflow Analysis. Dragon book, Chapter 9, Section 9.2, 9.3, 9.4
 Dataflow Analysis Dragon book, Chapter 9, Section 9.2, 9.3, 9.4 2 Dataflow Analysis Dataflow analysis is a sub-area of static program analysis Used in the compiler back end for optimizations of three-address
Dataflow Analysis Dragon book, Chapter 9, Section 9.2, 9.3, 9.4 2 Dataflow Analysis Dataflow analysis is a sub-area of static program analysis Used in the compiler back end for optimizations of three-address
Monotone Data Flow Analysis Framework
 Monotone Data Flow Analysis Framework Definition. A relation R on a set S is (a) reflexive iff ( x S)[xRx], (b) antisymmetric iff [xry yrx x=y] (c) transitive iff ( x,y,z S) [xry yrz xrz] Definition. A
Monotone Data Flow Analysis Framework Definition. A relation R on a set S is (a) reflexive iff ( x S)[xRx], (b) antisymmetric iff [xry yrx x=y] (c) transitive iff ( x,y,z S) [xry yrz xrz] Definition. A
Static Analysis of Programs: A Heap-Centric View
 Static Analysis of Programs: A Heap-Centric View (www.cse.iitb.ac.in/ uday) Department of Computer Science and Engineering, Indian Institute of Technology, Bombay 5 April 2008 Part 1 Introduction ETAPS
Static Analysis of Programs: A Heap-Centric View (www.cse.iitb.ac.in/ uday) Department of Computer Science and Engineering, Indian Institute of Technology, Bombay 5 April 2008 Part 1 Introduction ETAPS
Alternative Parameterizations of Markov Networks. Sargur Srihari
 Alternative Parameterizations of Markov Networks Sargur srihari@cedar.buffalo.edu 1 Topics Three types of parameterization 1. Gibbs Parameterization 2. Factor Graphs 3. Log-linear Models with Energy functions
Alternative Parameterizations of Markov Networks Sargur srihari@cedar.buffalo.edu 1 Topics Three types of parameterization 1. Gibbs Parameterization 2. Factor Graphs 3. Log-linear Models with Energy functions
February 17, Simplex Method Continued
 15.053 February 17, 2005 Simplex Method Continued 1 Today s Lecture Review of the simplex algorithm. Formalizing the approach Alternative Optimal Solutions Obtaining an initial bfs Is the simplex algorithm
15.053 February 17, 2005 Simplex Method Continued 1 Today s Lecture Review of the simplex algorithm. Formalizing the approach Alternative Optimal Solutions Obtaining an initial bfs Is the simplex algorithm
Analysis of Uninformed Search Methods
 nalysis of Uninformed earch Methods rian. Williams 16.410-13 ep 21 st, 2004 lides adapted from: 6.034 Tomas Lozano Perez, Russell and Norvig IM rian Williams, Fall 04 1 ssignments Remember: Problem et
nalysis of Uninformed earch Methods rian. Williams 16.410-13 ep 21 st, 2004 lides adapted from: 6.034 Tomas Lozano Perez, Russell and Norvig IM rian Williams, Fall 04 1 ssignments Remember: Problem et
Alternative Parameterizations of Markov Networks. Sargur Srihari
 Alternative Parameterizations of Markov Networks Sargur srihari@cedar.buffalo.edu 1 Topics Three types of parameterization 1. Gibbs Parameterization 2. Factor Graphs 3. Log-linear Models Features (Ising,
Alternative Parameterizations of Markov Networks Sargur srihari@cedar.buffalo.edu 1 Topics Three types of parameterization 1. Gibbs Parameterization 2. Factor Graphs 3. Log-linear Models Features (Ising,
Iterative Dataflow Analysis
 Iterative Dataflow Analysis CS 352 9/24/07 Slides adapted from Nielson, Nielson, Hankin Principles of Program Analysis Key Ideas Need a mechanism to evaluate (statically) statements in a program Problem:
Iterative Dataflow Analysis CS 352 9/24/07 Slides adapted from Nielson, Nielson, Hankin Principles of Program Analysis Key Ideas Need a mechanism to evaluate (statically) statements in a program Problem:
Theory of Computation
 Theory of Computation Lecture #2 Sarmad Abbasi Virtual University Sarmad Abbasi (Virtual University) Theory of Computation 1 / 1 Lecture 2: Overview Recall some basic definitions from Automata Theory.
Theory of Computation Lecture #2 Sarmad Abbasi Virtual University Sarmad Abbasi (Virtual University) Theory of Computation 1 / 1 Lecture 2: Overview Recall some basic definitions from Automata Theory.
Class 5. Review; questions. Data-flow Analysis Review. Slicing overview Problem Set 2: due 9/3/09 Problem Set 3: due 9/8/09
 Class 5 Review; questions Assign (see Schedule for links) Slicing overview Problem Set 2: due 9/3/09 Problem Set 3: due 9/8/09 1 Data-flow Analysis Review Start at slide 21 of Basic Analysis 3 1 Static
Class 5 Review; questions Assign (see Schedule for links) Slicing overview Problem Set 2: due 9/3/09 Problem Set 3: due 9/8/09 1 Data-flow Analysis Review Start at slide 21 of Basic Analysis 3 1 Static
Multi-Level Logic Optimization. Technology Independent. Thanks to R. Rudell, S. Malik, R. Rutenbar. University of California, Berkeley, CA
 Technology Independent Multi-Level Logic Optimization Prof. Kurt Keutzer Prof. Sanjit Seshia EECS University of California, Berkeley, CA Thanks to R. Rudell, S. Malik, R. Rutenbar 1 Logic Optimization
Technology Independent Multi-Level Logic Optimization Prof. Kurt Keutzer Prof. Sanjit Seshia EECS University of California, Berkeley, CA Thanks to R. Rudell, S. Malik, R. Rutenbar 1 Logic Optimization
Static Program Analysis
 Static Program Analysis Thomas Noll Software Modeling and Verification Group RWTH Aachen University https://moves.rwth-aachen.de/teaching/ss-18/spa/ Recap: Interprocedural Dataflow Analysis Outline of
Static Program Analysis Thomas Noll Software Modeling and Verification Group RWTH Aachen University https://moves.rwth-aachen.de/teaching/ss-18/spa/ Recap: Interprocedural Dataflow Analysis Outline of
Lecture 23 Branch-and-Bound Algorithm. November 3, 2009
 Branch-and-Bound Algorithm November 3, 2009 Outline Lecture 23 Modeling aspect: Either-Or requirement Special ILPs: Totally unimodular matrices Branch-and-Bound Algorithm Underlying idea Terminology Formal
Branch-and-Bound Algorithm November 3, 2009 Outline Lecture 23 Modeling aspect: Either-Or requirement Special ILPs: Totally unimodular matrices Branch-and-Bound Algorithm Underlying idea Terminology Formal
Finite Automata Theory and Formal Languages TMV027/DIT321 LP4 2018
 Finite Automata Theory and Formal Languages TMV027/DIT321 LP4 2018 Lecture 9 Ana Bove April 19th 2018 Recap: Regular Expressions Algebraic representation of (regular) languages; R, S ::= a R + S RS R......
Finite Automata Theory and Formal Languages TMV027/DIT321 LP4 2018 Lecture 9 Ana Bove April 19th 2018 Recap: Regular Expressions Algebraic representation of (regular) languages; R, S ::= a R + S RS R......
Overview. Discrete Event Systems Verification of Finite Automata. What can finite automata be used for? What can finite automata be used for?
 Computer Engineering and Networks Overview Discrete Event Systems Verification of Finite Automata Lothar Thiele Introduction Binary Decision Diagrams Representation of Boolean Functions Comparing two circuits
Computer Engineering and Networks Overview Discrete Event Systems Verification of Finite Automata Lothar Thiele Introduction Binary Decision Diagrams Representation of Boolean Functions Comparing two circuits
/633 Introduction to Algorithms Lecturer: Michael Dinitz Topic: Dynamic Programming II Date: 10/12/17
 601.433/633 Introduction to Algorithms Lecturer: Michael Dinitz Topic: Dynamic Programming II Date: 10/12/17 12.1 Introduction Today we re going to do a couple more examples of dynamic programming. While
601.433/633 Introduction to Algorithms Lecturer: Michael Dinitz Topic: Dynamic Programming II Date: 10/12/17 12.1 Introduction Today we re going to do a couple more examples of dynamic programming. While
Geometry Chapter 3 3-6: PROVE THEOREMS ABOUT PERPENDICULAR LINES
 Geometry Chapter 3 3-6: PROVE THEOREMS ABOUT PERPENDICULAR LINES Warm-Up 1.) What is the distance between the points (2, 3) and (5, 7). 2.) If < 1 and < 2 are complements, and m < 1 = 49, then what is
Geometry Chapter 3 3-6: PROVE THEOREMS ABOUT PERPENDICULAR LINES Warm-Up 1.) What is the distance between the points (2, 3) and (5, 7). 2.) If < 1 and < 2 are complements, and m < 1 = 49, then what is
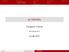 = (, ) V λ (1) λ λ ( + + ) P = [ ( ), (1)] ( ) ( ) = ( ) ( ) ( 0 ) ( 0 ) = ( 0 ) ( 0 ) 0 ( 0 ) ( ( 0 )) ( ( 0 )) = ( ( 0 )) ( ( 0 )) ( + ( 0 )) ( + ( 0 )) = ( + ( 0 )) ( ( 0 )) P V V V V V P V P V V V
= (, ) V λ (1) λ λ ( + + ) P = [ ( ), (1)] ( ) ( ) = ( ) ( ) ( 0 ) ( 0 ) = ( 0 ) ( 0 ) 0 ( 0 ) ( ( 0 )) ( ( 0 )) = ( ( 0 )) ( ( 0 )) ( + ( 0 )) ( + ( 0 )) = ( + ( 0 )) ( ( 0 )) P V V V V V P V P V V V
Space-aware data flow analysis
 Space-aware data flow analysis C. Bernardeschi, G. Lettieri, L. Martini, P. Masci Dip. di Ingegneria dell Informazione, Università di Pisa, Via Diotisalvi 2, 56126 Pisa, Italy {cinzia,g.lettieri,luca.martini,paolo.masci}@iet.unipi.it
Space-aware data flow analysis C. Bernardeschi, G. Lettieri, L. Martini, P. Masci Dip. di Ingegneria dell Informazione, Università di Pisa, Via Diotisalvi 2, 56126 Pisa, Italy {cinzia,g.lettieri,luca.martini,paolo.masci}@iet.unipi.it
Register Alloca.on. CMPT 379: Compilers Instructor: Anoop Sarkar. anoopsarkar.github.io/compilers-class
 Register Alloca.on CMPT 379: Compilers Instructor: Anoop Sarkar anoopsarkar.github.io/compilers-class 1 Register Alloca.on Intermediate code uses unlimited temporaries Simplifying code genera.on and op.miza.on
Register Alloca.on CMPT 379: Compilers Instructor: Anoop Sarkar anoopsarkar.github.io/compilers-class 1 Register Alloca.on Intermediate code uses unlimited temporaries Simplifying code genera.on and op.miza.on
Week 4. (1) 0 f ij u ij.
 Week 4 1 Network Flow Chapter 7 of the book is about optimisation problems on networks. Section 7.1 gives a quick introduction to the definitions of graph theory. In fact I hope these are already known
Week 4 1 Network Flow Chapter 7 of the book is about optimisation problems on networks. Section 7.1 gives a quick introduction to the definitions of graph theory. In fact I hope these are already known
Handout 2 Gaussian elimination: Special cases
 06-21254 Mathematical Techniques for Computer Science The University of Birmingham Autumn Semester 2017 School of Computer Science c Achim Jung September 28, 2017 Handout 2 Gaussian elimination: Special
06-21254 Mathematical Techniques for Computer Science The University of Birmingham Autumn Semester 2017 School of Computer Science c Achim Jung September 28, 2017 Handout 2 Gaussian elimination: Special
DSP Design Lecture 7. Unfolding cont. & Folding. Dr. Fredrik Edman.
 SP esign Lecture 7 Unfolding cont. & Folding r. Fredrik Edman fredrik.edman@eit.lth.se Unfolding Unfolding creates a program with more than one iteration, J=unfolding factor Unfolding is a structured way
SP esign Lecture 7 Unfolding cont. & Folding r. Fredrik Edman fredrik.edman@eit.lth.se Unfolding Unfolding creates a program with more than one iteration, J=unfolding factor Unfolding is a structured way
Multilevel Logic Synthesis Algebraic Methods
 Multilevel Logic Synthesis Algebraic Methods Logic Circuits Design Seminars WS2010/2011, Lecture 6 Ing. Petr Fišer, Ph.D. Department of Digital Design Faculty of Information Technology Czech Technical
Multilevel Logic Synthesis Algebraic Methods Logic Circuits Design Seminars WS2010/2011, Lecture 6 Ing. Petr Fišer, Ph.D. Department of Digital Design Faculty of Information Technology Czech Technical
Data Mining Concepts & Techniques
 Data Mining Concepts & Techniques Lecture No. 04 Association Analysis Naeem Ahmed Email: naeemmahoto@gmail.com Department of Software Engineering Mehran Univeristy of Engineering and Technology Jamshoro
Data Mining Concepts & Techniques Lecture No. 04 Association Analysis Naeem Ahmed Email: naeemmahoto@gmail.com Department of Software Engineering Mehran Univeristy of Engineering and Technology Jamshoro
Finite Automata Theory and Formal Languages TMV027/DIT321 LP4 2018
 Finite Automata Theory and Formal Languages TMV027/DIT321 LP4 2018 Lecture 14 Ana Bove May 14th 2018 Recap: Context-free Grammars Simplification of grammars: Elimination of ǫ-productions; Elimination of
Finite Automata Theory and Formal Languages TMV027/DIT321 LP4 2018 Lecture 14 Ana Bove May 14th 2018 Recap: Context-free Grammars Simplification of grammars: Elimination of ǫ-productions; Elimination of
Static Program Analysis
 Reinhard Wilhelm Universität des Saarlandes Static Program Analysis Slides based on: Beihang University June 2012 H. Seidl, R. Wilhelm, S. Hack: Compiler Design, Volume 3, Analysis and Transformation,
Reinhard Wilhelm Universität des Saarlandes Static Program Analysis Slides based on: Beihang University June 2012 H. Seidl, R. Wilhelm, S. Hack: Compiler Design, Volume 3, Analysis and Transformation,
Learning in State-Space Reinforcement Learning CIS 32
 Learning in State-Space Reinforcement Learning CIS 32 Functionalia Syllabus Updated: MIDTERM and REVIEW moved up one day. MIDTERM: Everything through Evolutionary Agents. HW 2 Out - DUE Sunday before the
Learning in State-Space Reinforcement Learning CIS 32 Functionalia Syllabus Updated: MIDTERM and REVIEW moved up one day. MIDTERM: Everything through Evolutionary Agents. HW 2 Out - DUE Sunday before the
A Functional Perspective
 A Functional Perspective on SSA Optimization Algorithms Patryk Zadarnowski jotly with Manuel M. T. Chakravarty Gabriele Keller 19 April 2004 University of New South Wales Sydney THE PLAN ➀ Motivation an
A Functional Perspective on SSA Optimization Algorithms Patryk Zadarnowski jotly with Manuel M. T. Chakravarty Gabriele Keller 19 April 2004 University of New South Wales Sydney THE PLAN ➀ Motivation an
Algebra 1. Predicting Patterns & Examining Experiments. Unit 5: Changing on a Plane Section 4: Try Without Angles
 Section 4 Examines triangles in the coordinate plane, we will mention slope, but not angles (we will visit angles in Unit 6). Students will need to know the definition of collinear, isosceles, and congruent...
Section 4 Examines triangles in the coordinate plane, we will mention slope, but not angles (we will visit angles in Unit 6). Students will need to know the definition of collinear, isosceles, and congruent...
Worst-Case Execution Time Analysis. LS 12, TU Dortmund
 Worst-Case Execution Time Analysis Prof. Dr. Jian-Jia Chen LS 12, TU Dortmund 09/10, Jan., 2018 Prof. Dr. Jian-Jia Chen (LS 12, TU Dortmund) 1 / 43 Most Essential Assumptions for Real-Time Systems Upper
Worst-Case Execution Time Analysis Prof. Dr. Jian-Jia Chen LS 12, TU Dortmund 09/10, Jan., 2018 Prof. Dr. Jian-Jia Chen (LS 12, TU Dortmund) 1 / 43 Most Essential Assumptions for Real-Time Systems Upper
Linear algebra and differential equations (Math 54): Lecture 13
 Linear algebra and differential equations (Math 54): Lecture 13 Vivek Shende March 3, 016 Hello and welcome to class! Last time We discussed change of basis. This time We will introduce the notions of
Linear algebra and differential equations (Math 54): Lecture 13 Vivek Shende March 3, 016 Hello and welcome to class! Last time We discussed change of basis. This time We will introduce the notions of
Linear Programming Duality
 Summer 2011 Optimization I Lecture 8 1 Duality recap Linear Programming Duality We motivated the dual of a linear program by thinking about the best possible lower bound on the optimal value we can achieve
Summer 2011 Optimization I Lecture 8 1 Duality recap Linear Programming Duality We motivated the dual of a linear program by thinking about the best possible lower bound on the optimal value we can achieve
Exploring the Potential of Instruction-Level Parallelism of Exposed Datapath Architectures with Buffered Processing Units
 Exploring the Potential of Instruction-Level Parallelism of Exposed Datapath Architectures with Buffered Processing Units Anoop Bhagyanath and Klaus Schneider Embedded Systems Chair University of Kaiserslautern
Exploring the Potential of Instruction-Level Parallelism of Exposed Datapath Architectures with Buffered Processing Units Anoop Bhagyanath and Klaus Schneider Embedded Systems Chair University of Kaiserslautern
Inference in Bayesian Networks
 Andrea Passerini passerini@disi.unitn.it Machine Learning Inference in graphical models Description Assume we have evidence e on the state of a subset of variables E in the model (i.e. Bayesian Network)
Andrea Passerini passerini@disi.unitn.it Machine Learning Inference in graphical models Description Assume we have evidence e on the state of a subset of variables E in the model (i.e. Bayesian Network)
MATH c UNIVERSITY OF LEEDS Examination for the Module MATH2210 (May/June 2004) INTRODUCTION TO DISCRETE MATHEMATICS. Time allowed : 2 hours
 This question paper consists of 5 printed pages, each of which is identified by the reference MATH221001 MATH221001 No calculators allowed c UNIVERSITY OF LEEDS Examination for the Module MATH2210 (May/June
This question paper consists of 5 printed pages, each of which is identified by the reference MATH221001 MATH221001 No calculators allowed c UNIVERSITY OF LEEDS Examination for the Module MATH2210 (May/June
CSC 412 (Lecture 4): Undirected Graphical Models
 CSC 412 (Lecture 4): Undirected Graphical Models Raquel Urtasun University of Toronto Feb 2, 2016 R Urtasun (UofT) CSC 412 Feb 2, 2016 1 / 37 Today Undirected Graphical Models: Semantics of the graph:
CSC 412 (Lecture 4): Undirected Graphical Models Raquel Urtasun University of Toronto Feb 2, 2016 R Urtasun (UofT) CSC 412 Feb 2, 2016 1 / 37 Today Undirected Graphical Models: Semantics of the graph:
7.6 The Inverse of a Square Matrix
 7.6 The Inverse of a Square Matrix Copyright Cengage Learning. All rights reserved. What You Should Learn Verify that two matrices are inverses of each other. Use Gauss-Jordan elimination to find inverses
7.6 The Inverse of a Square Matrix Copyright Cengage Learning. All rights reserved. What You Should Learn Verify that two matrices are inverses of each other. Use Gauss-Jordan elimination to find inverses
Math Models of OR: Extreme Points and Basic Feasible Solutions
 Math Models of OR: Extreme Points and Basic Feasible Solutions John E. Mitchell Department of Mathematical Sciences RPI, Troy, NY 1180 USA September 018 Mitchell Extreme Points and Basic Feasible Solutions
Math Models of OR: Extreme Points and Basic Feasible Solutions John E. Mitchell Department of Mathematical Sciences RPI, Troy, NY 1180 USA September 018 Mitchell Extreme Points and Basic Feasible Solutions
Goal. Partially-ordered set. Game plan 2/2/2013. Solving fixpoint equations
 Goal Solving fixpoint equations Many problems in programming languages can be formulated as the solution of a set of mutually recursive equations: D: set, f,g:dxd D x = f(x,y) y = g(x,y) Examples Parsing:
Goal Solving fixpoint equations Many problems in programming languages can be formulated as the solution of a set of mutually recursive equations: D: set, f,g:dxd D x = f(x,y) y = g(x,y) Examples Parsing:
Push Down Automaton. Announcement. Puzzle of the day. Last lecture. Running Example. 10/2 things Chomsky hates about CFGs
 Announcement Push Down Automaton Mid term If you have not collected yours yet, see me after/before class. Atri Rudra May 10 A. Rudra, CSE322 2 Puzzle of the day Last lecture Design a context free grammar
Announcement Push Down Automaton Mid term If you have not collected yours yet, see me after/before class. Atri Rudra May 10 A. Rudra, CSE322 2 Puzzle of the day Last lecture Design a context free grammar
Model Checking for Propositions CS477 Formal Software Dev Methods
 S477 Formal Software Dev Methods Elsa L Gunter 2112 S, UIU egunter@illinois.edu http://courses.engr.illinois.edu/cs477 Slides based in part on previous lectures by Mahesh Vishwanathan, and by Gul gha January
S477 Formal Software Dev Methods Elsa L Gunter 2112 S, UIU egunter@illinois.edu http://courses.engr.illinois.edu/cs477 Slides based in part on previous lectures by Mahesh Vishwanathan, and by Gul gha January
Lecture 13 Spectral Graph Algorithms
 COMS 995-3: Advanced Algorithms March 6, 7 Lecture 3 Spectral Graph Algorithms Instructor: Alex Andoni Scribe: Srikar Varadaraj Introduction Today s topics: Finish proof from last lecture Example of random
COMS 995-3: Advanced Algorithms March 6, 7 Lecture 3 Spectral Graph Algorithms Instructor: Alex Andoni Scribe: Srikar Varadaraj Introduction Today s topics: Finish proof from last lecture Example of random
11 The Max-Product Algorithm
 Massachusetts Institute of Technology Department of Electrical Engineering and Computer Science 6.438 Algorithms for Inference Fall 2014 11 The Max-Product Algorithm In the previous lecture, we introduced
Massachusetts Institute of Technology Department of Electrical Engineering and Computer Science 6.438 Algorithms for Inference Fall 2014 11 The Max-Product Algorithm In the previous lecture, we introduced
Control Dependence. Stanford University CS243 Winter 2006 Wei Li 1
 Control Dependence Wei Li 1 Control Dependence Introduction Formal Definition Optimal Control Dependence Computation 2 xample START a b c d CFG ND b is control dependent on a c is control dependent on
Control Dependence Wei Li 1 Control Dependence Introduction Formal Definition Optimal Control Dependence Computation 2 xample START a b c d CFG ND b is control dependent on a c is control dependent on
MTH MTH Lecture 6. Yevgeniy Kovchegov Oregon State University
 MTH 306 0 MTH 306 - Lecture 6 Yevgeniy Kovchegov Oregon State University MTH 306 1 Topics Lines and planes. Systems of linear equations. Systematic elimination of unknowns. Coe cient matrix. Augmented
MTH 306 0 MTH 306 - Lecture 6 Yevgeniy Kovchegov Oregon State University MTH 306 1 Topics Lines and planes. Systems of linear equations. Systematic elimination of unknowns. Coe cient matrix. Augmented
CS473 - Algorithms I
 CS473 - Algorithms I Lecture 10 Dynamic Programming View in slide-show mode CS 473 Lecture 10 Cevdet Aykanat and Mustafa Ozdal, Bilkent University 1 Introduction An algorithm design paradigm like divide-and-conquer
CS473 - Algorithms I Lecture 10 Dynamic Programming View in slide-show mode CS 473 Lecture 10 Cevdet Aykanat and Mustafa Ozdal, Bilkent University 1 Introduction An algorithm design paradigm like divide-and-conquer
As it is not necessarily possible to satisfy this equation, we just ask for a solution to the more general equation
 Graphs and Networks Page 1 Lecture 2, Ranking 1 Tuesday, September 12, 2006 1:14 PM I. II. I. How search engines work: a. Crawl the web, creating a database b. Answer query somehow, e.g. grep. (ex. Funk
Graphs and Networks Page 1 Lecture 2, Ranking 1 Tuesday, September 12, 2006 1:14 PM I. II. I. How search engines work: a. Crawl the web, creating a database b. Answer query somehow, e.g. grep. (ex. Funk
Notes taken by Graham Taylor. January 22, 2005
 CSC4 - Linear Programming and Combinatorial Optimization Lecture : Different forms of LP. The algebraic objects behind LP. Basic Feasible Solutions Notes taken by Graham Taylor January, 5 Summary: We first
CSC4 - Linear Programming and Combinatorial Optimization Lecture : Different forms of LP. The algebraic objects behind LP. Basic Feasible Solutions Notes taken by Graham Taylor January, 5 Summary: We first
Dataflow Analysis - 2. Monotone Dataflow Frameworks
 Dataflow Analysis - 2 Monotone dataflow frameworks Definition Convergence Safety Relation of MOP to MFP Constant propagation Categorization of dataflow problems DataflowAnalysis 2, Sp06 BGRyder 1 Monotone
Dataflow Analysis - 2 Monotone dataflow frameworks Definition Convergence Safety Relation of MOP to MFP Constant propagation Categorization of dataflow problems DataflowAnalysis 2, Sp06 BGRyder 1 Monotone
