Network Scheduling for Secure Cyber-Physical Systems
|
|
|
- Asher Fletcher
- 5 years ago
- Views:
Transcription
1 Nework Schedulng for Secure Cyber-Physcal Sysems Vuk Les, Ilja Jovanov and Mroslav Pajc Deparmen of Elecrcal & Compuer Engneerng Duke Unversy {vuk.les, lja.jovanov, Easy o Reuse * Conssen * Well Documened * Absrac Exsng desgn echnques for provdng secury guaranees agans nework-based aacks n cyber-physcal sysems (CPS) are based on connuous use of sandard crypographc ools o ensure daa negry. Ths creaes an apparen conflc wh common resource lmaons n hese sysems, gven ha, for nsance, lenghy message auhencaon codes (MAC) nroduce sgnfcan overheads. We presen a framework o ensure boh mng guaranees for real-me nework messages and Qualy-of-Conrol (QoC) n he presence of nework-based aacks. We explo physcal properes of conrolled sysems o relax consan negry enforcemen requremens, and show how he problem of feasbly esng of nermenly auhencaed real-me messages can be cas as a mxed neger lnear programmng problem. Besdes schedulng a se of real-me messages wh predefned auhencaon raes obaned from QoC requremens, we show how o opmally ncrease he overall sysem QoC whle ensurng ha all real-me messages are schedulable. Fnally, we nroduce an effcen runme bandwdh allocaon mehod, based on opporunsc schedulng, n order o mprove QoC. We evaluae our framework on a sandard benchmark desgned for CAN bus, and show how an nfeasble message se wh srong secury guaranees can be scheduled f dynamcs of conrolled sysems are aken no accoun along wh real-me requremens. I. INTRODUCTION Recen years have wnessed sgnfcan ncrease n he number of secury relaed ncdens n cyber-physcal sysems (CPS). For nsance, auomove aacks (e.g., [1], [2]) as well as he capurng of he RQ-170 Sennel US drone [3] have llusraed ha even safey-crcal auomove and mlary CPS can be ampered wh or compleely hjacked. One of he man reasons for such dre suaons s he expanson n nework connecvy and complee relance on permeer secury n hese sysems. Thus, by compromsng an nernal sysem componen and ulzng nerconnecons beween he componens, an aacker could easly launch aacks over lowlevel neworks used for real-me communcaon of safeycrcal and conrol-relaed packes. Ths, n urn, could allow hm o force he conrolled physcal process no any desred sae as llusraed n [1], [2] for auomove sysems. Some of hese nework-based aacks, such as he Man-nhe-Mddle (MM) aacks, can be avoded wh he use of sandard crypographc ools. For example, n CAN neworks, a common approach s o add a message auhencaon code Ths work was suppored n par by he NSF CNS and CNS grans, and he Inel-NSF Parnershp for Cyber-Physcal Sysems Secury and Prvacy. Ths maeral s also based on research sponsored by he ONR under agreemens number N and N (MAC) o all ransmed measuremens, n order o auhencae daa and ensure negry of receved packages. On he oher hand, CPS are ofen resource consraned, and mgh no be able o handle he connuous overhead caused by compuaon and communcaon of such codes for a suffcen number of sensors. For example, as presened n [4], [5], addng more han 30 MAC bs o CPS sysems based on CAN neworks may no be feasble due o he message lengh lmaon (e.g., only 64 payload bs n he basc CAN proocol); ye, splng hem no several communcaon packes can sgnfcanly ncrease he message ransmsson me and reduce sysem/conrol performance. Ths conflcng se of requremens, beween he overhead nroduced wh he use of secury mechansms and he obaned secury guaranees, s common for securyrelaed research. However, o he bes of our knowledge, no work provdes drec relaonshp beween he use of sysem resources and he overall sysem performance, n erms of s man funconaly, n he presence of aacks. For example, [6] explores opporunsc execuon of securyrelaed asks on op of exsng legacy sysems n order o negrae secury mechansms. The auhors formulae opmzaon problems around adapon of parameers of securyrelaed asks, whle mananng schedulably of exsng nonsecury-relaed asks. In [7] a novel schedulng algorhm s proposed o jonly ake no accoun secury and real-me requremens for embedded sysems. The approach s evaluaed only absracly, by he measure of an absrac secury level wh no drec relaonshp wh sysem performance n he presence of aacks. In [8], a smlarly defned secury level s maxmzed by opmally choosng acve secury servces wh respec o schedulably condons. In hs work, we focus on provdng secury guaranees, n erms of Qualy-of-Conrol (QoC), for conrol componens n CPS n he presence of nework-based aacks. We assume ha he aacker may have access o he low-level nework and could njec false sensor measuremens and acuaor commands. Whle such aacks on acuaor commands canno say undeeced (.e., sealhy), by changng messages from a subse of sensors a sealhy aacker can force he conrolled plan far from he desred operang pon hrough he acons of he conroller [9], [10]. On he oher hand, we have recenly shown ha s no necessary o connuously ensure daa negry for sasfable conrol performance n he presence of aacks [11], [12]. Snce we explo lmaons mposed on he aacker by he physcal laws governng behavor of
2 dynamcal sysems, our dea s somewha complemenary o he self/even-rggered conrol paradgm ha s used o reduce nework ulzaon n neworked conrol sysems [13]. We nroduce a mehod o relae he QoC guaranees n he presence of aack and he bandwdh overhead due o he use of nermen daa auhencaon n communcaon over a shared nework. Ths lays he foundaon for our nework schedulably analyss for non-preempve realme sensor messages wh nermen negry enforcemens, whch ensure predefned QoC requremens. Furhermore, we presen a Mxed-Ineger Lnear Programmng (MILP)-based echnque o perform radeoff analyss beween he nework ulzaon and he overall QoC guaranees for a se of conrol loops communcang over a shared nework. Ths faclaes opmal bandwdh allocaon ha maxmzes he overall QoC guaranees n he presence of aacks wh respec o he avalable resources (.e., nework bandwdh). Fnally, on a realworld auomove case sudy, we llusrae how he proposed desgn-me framework can be used o provde secure-conrol guaranees for CAN-based CPS. Specfcally, we show how we can negrae sensor measuremens wh nermen daa auhencaon such ha we maxmze QoC under aack whle ensurng ha mng guaranees for exsng real-me messages are no volaed. Ths paper s organzed as follows. Secon II nroduces he problem consdered n hs work, before we presen he concep of nermen daa negry enforcemens and a framework o relae QoC guaranees n he presence of aacks wh he negry enforcemen rae (Secon III). In Secon IV, we presen a real-me message model wh nermen auhencaon, and n Secon V we nroduce an MILP-based mehod for synhess of schedulable messages wh QoC guaranees based on nermen daa auhencaon. Secon VI presens a mehod o derve a message se wh he opmal balance beween he overall QoC and avalable resources. Fnally, n VII we evaluae our approach on a real-world auomove case sudy, before provdng concludng remarks n Secon VIII. II. MOTIVATION AND PROBLEM STATEMENT In hs work, we focus on neworked conrol of N dscreeme plans Σ, = 1,..., N, of he form x [k + 1] = A x [k] + B u [k] + w [k], y [k] = C x [k] + v [k], where x [k] R n, u [k] R m, and y [k] R p denoe sae, npu and oupus of he h plan a me k, respecvely, and w R n and v R p are he process and measuremen nose. The above models are obaned by dscrezng he correspondng connuous plan model. Alhough we assume ha w and v are ndependen dencally dsrbued Gaussan random varables our work can be exended o bounded-sze nose. For each sysem Σ, we specfy desgned conrollers as ˆx [k + 1] = f (ˆx [k], ŷ [k]), u [k] = g (ˆx [k], ŷ [k]), where f ( ) and g ( ) are any lnear mappngs, ˆx [k] s he conroller s sae, such as he esmaed plan sae, and ŷ [k] are receved sensor measuremens n sep k. The above formulaon s general, capurng observer-based sae feedback Acuaors [ ] Plan Σ [ ] [ ] Conroller, Sensors Acuaors [ ] [ ] Nework Plan Σ [ ] [ ] Conroller, Sensors Fg. 1. Neworked sysem archecure for wh N conrol-loops; noe ha n general some conrollers may be mapped on shared CPUs. as well as sandard feedback conrollers, whch can be desgned usng varous echnques focused on sably, opmal performance or robusness o modelng errors. Sensor measuremens are ransmed as real-me messages over a nework llusraed n Fg. 1, whch s shared wh non real-me communcaon packes. We absrac a sandard realme message by a 3-uple M(c, p, d) where c s he nonpreempve message ransmsson me, s he ransmsson perod.e., he me beween message arrvals (equal o he plan s samplng me), and d s he message deadlne relave o s arrval me. To smplfy our noaon, non real-me messages are absraced wh a sngle parameer c NRT max ha capures he ransmsson me of he longes such message. To model he aacker, we use he sandard aack model from [9] [11], [14]. When no MM aacks on he nework occur, we have ha ŷ [k] = y [k]. On he oher hand, wh MM aacks, sensor measuremens receved by he conroller ŷ [k] could poenally dffer from he acual sensor measuremens y [k]. We dfferenae sysem evoluons wh and whou aacks by addng superscrp a o all varables affeced by he aacker s nfluence. For example, he plan s sae and oupus when he sysem s under aack are denoed as x a [k] and y a [k], respecvely. Thus, aacks on sensor measuremens delvered o he conroller can be modeled as ŷ a [k] = y a [k] + a [k] = C x a [k] + v a [k] + a [k], where a [k] s a sparse vecor capurng values njeced by he aacker. Noe ha sparsy of vecor a [k] depends on he se of compromsed sensor flows f communcaon from a sensor o he conroller s no corruped hen he correspondng value n a [k] has o be zero. Hence, we can capure any assumpons abou he se of compromsed sensor flows (e.g., he number of he flows) by nroducng consrans on he sparsy of he vecor. Ye, unless saed oherwse, we smplfy our presenaon by focusng on he wors-case scenaro, where he aacker can compromse all sensor flows once he decdes o launch an aack. Commonly, MM aacks are deal wh by employng sandard crypographc mechansms such as MACs; we assume ha he aacker does no have access o he shared secre keys used o generae he MACs. Thus, when auhencaon s enforced wh he use of MACs, we assume ha he aacker avods nserng false daa measuremens n order o say undeeced, meanng ha a hese mes a [k] = 0. 1 We assume ha he aacker has full knowledge of he sysem, enablng hm o smarly craf false measuremens n order o deceve he conroller no pushng he plan away from he desred 1 Alhough he aacker could poenally preven auhencaed messages from beng delvered, we do no consder such aacks, snce Denal-of-Servce aacks are easer o deec n CPS wh relable communcaon neworks. [ ]
3 M 1 M 2 M 1 M 1 M 2 M 1 daa MAC daa MAC daa daa daa MAC daa Fg. 2. Schedulng messages from wo sensors; feasble message se M 1(15, 50, 50) and M 2(15, 100, 100) becomes nfeasble when MACs of lengh 20 are added o every message. However, hey can be scheduled f e.g., every fourh ransmsson of M 1 s auhencaed, whle M 2 s auhencaed on every perod. operang pon. The aacker also knows he mes when auhencaon wll be used, allowng hm o plan ahead and avod beng deeced. Fnally, he aacker s goal s o maxmally reduce conrol performance (.e., QoC), usng he nsered false measuremens, whle remanng sealhy.e., undeeced by he sysem; hus, n addon o no nserng false daa packes n me-frames when auhencaon s enforced, he falsfed sensor measuremens should no rgger he Inruson Deecon Sysem (IDS) employed a he conroller. However, ensurng auhencaon for every ransmed sensor measuremen could mpose unfeasble consrans on he underlyng nework. For example, consder wo perodc real-me sensor messages modeled as M 1 (15, 50, 50) and M 2 (15, 100, 100) when MACs are no added. These wo messages can be scheduled over he nework. However, f addng MACs ncreases ransmsson me for M 1 and M 2 by 20 me uns, he resulng message se M 1(35, 50, 50) and M 2(35, 100, 100) becomes unfeasble. On he oher hand, f every fourh message for M 1 s auhencaed, he messages can mee her deadlnes as llusraed n Fg. 2. From he perspecve of QoC guaranees even wh he adversaral presence, hs level of negry guaranees may be suffcen; we recenly showed ha even nermen daa negry guaranees sgnfcanly lm he aacker s mpac [11], [12]. Therefore, hs work focuses on radeoffs beween he QoC n he presence of aacks and negry enforcemen overhead for sensor messages. We address he followng problems: How o map requremens for QoC n he presence of aacks no auhencaon consrans for real-me sensor messages? How can such real-me messages be scheduled over a shared nework, whle ensurng he desred QoC level for each of he conrol loops even n he presence of aacks? How o perform opmal bandwdh allocaon for each conrol loop such ha he overall (.e., for all loops) secury guaranees, n erms of QoC under aacks, are maxmzed? We sar wh our recenly nroduced framework for secury aware conrol wh nermen daa-negry enforcemens. III. SECURITY-AWARE CONTROL WITH INTERMITTENT DATA INTEGRITY ENFORCEMENTS CPS conrollers usually ncorporae a sae esmaor feedng a feedback conroller as shown n Fg. 3. Furhermore, an IDS s used o deec dscrepances beween physcal properes of he sysem (.e., s model) and he receved sensor measuremens. The acual IDS employed n hese applcaon drecly depends on he plan (specfcally nose) model. For example, for bounded-sze nose, secury-aware esmaors and sebased IDSs have been recenly proposed (e.g., [14]). Smlarly, for Gaussan nose model, Kalman fler-based esmaors can [ ] Feedback Conroller Conroller Fg. 3. [ ] [ ] Esmaor Inruson Deecor ALARM General conroller archecure. be used wh sascal IDSs, such as χ 2 [9] [11] or Sequenal Probably Rao Tes (SPRT) deecors [12]. I was recenly shown (e.g., [10], [14]) ha a sealhy aack can sgnfcanly reduce QoC when he aacker s able o compromse a ceran number of sensor flows. For any ype of he consdered conrollers (.e., esmaors and IDSs), hs can be acheved by njecng false sensor measuremens ha resul n a skewed sae esmaon; hs n-urn deceves he conroller no seerng he sysem away from he desred rajecory/operang pon by applyng ll-sued conrol commands. However, he sae esmaon error has o be slowly ncreased n order for he aacker o say undeeced. Ths, coupled wh he fac ha each plan has s own domnan me-consan (capured by he plan model Σ ) mples ha QoC can be sgnfcanly degraded only some me afer a sealhy aack s launched. To analyze hs formally, we nroduce he reachable regon R[k] of he sae esmaon error under aack (.e., e a [k]), k seps afer he aack s launched. For plans wh Gaussan nose, as n hs work, he regons can be defned as [11], [12] 2 { R[k] = e R n ee T E[e a [k]]e[e a [k]] T + γcov(e a k ), } e a [k] = e a k (a. 1..k), a 1..k A k Here, a 1..k = [ a[1] T...a[k] ] T T capures all njeced false sensor measuremens, A k denoes he se of all sealhy aacks, and e a k (a 1..k) s he esmaon error evoluon caused by he aacks a 1..k. In [12], we also showed ha Cov(e a k ) s equal o he esmaon error covarance marx when no aacks are nroduced, and hus s known n advance. Furhermore, he global reachable regon R (.e., for all k > 0) of he sae esmaon error e a [k] s he se R = k=0 R[k]. In [11], [12], we recenly nroduced echnques o ghly evaluae regons R[k], sarng from he sysem model (.e., plan dynamcs Σ and employed IDS) as well as he aack model from Secon II, whch can be exended wh addonal poenally avalable nformaon, ncludng he maxmal number of compromsed sensor flows; when such nformaon s no avalable, we assume ha measuremens from all sensors can be compromsed. In addon, hese echnques faclae capurng he effecs of daa negry enforcemens a specfc me-pons defned by negry enforcemen polcy µ. Defnon 1 ([11], [12]): Inermen daa negry enforcemen polcy (µ, l), where µ = { k } k=0, wh k 1 < k for all k > 0 and l = sup k>0 k k 1, ensures ha a k = 0, for all k 0. Defnon 1 mposes a maxmum me beween negry enforcemens, capured by he parameer l. I also capures perodc enforcemens when l = k k 1 for all k > 0, as well 2 A smlar defnon can be used for sysems wh bounded-sze nose [14].
4 Sysem Model Σ, (, ) Aack Model In. Enf. Polcy ( ) Reachably Analyss R [ ] QoC Guaranees ( ) Fg. 4. Desgn-me framework o evaluae effecs of nermen negry enforcemen polces on QoC guaranees n he presence of aack based on he reachably analyss from [11], [12]. as polces wh connuous negry enforcemens (for l = 1). Snce our goal s o reduce communcaon overhead assocaed wh negry enforcemen, we wll nally focus on polces where enforcemens are maxmally spread apar,.e., for whch l = k k 1 for all k > 0. In general, QoC depends on sae esmaon errors. For nsance, as llusraed n [15] when lnear-quadrac conrol cos s consder as QoC, a gh bound on QoC degradaon can be obaned as L 2 -gan (whch s known n advance) scaled bound on he sze of esmaon error. Consequenly, gh guaranees on he sze of sae-esmaon error due o aacks can be ulzed o capure QoC n he presence of aacks. Ths effecvely allows us o oban a desgn-me reachably-based framework from Fg. 4 o evaluae mpac of sealhy aacks on sysems wh (and whou) negry enforcemen polces. Furhermore, he sysem and aack models are fxed for any CPS under consderaon, and herefore he framework can be used o analyze mpac of he negry enforcemen parameer l on he aack-nduced sae esmaon error (and hus QoC). Formally, hs can be capured usng J (l) funcons defned as J (l) = supp{ e 2 e R l }, where R l = R l [k], k=0 and R l [k] denoes R[k] compued for all negry polces wh parameer l. For example, funcons J (l) for hree auomove closed-loop sysems are presened n Fg. 8. The aforemenoned J (l) funcons are he foundaon for our analyss of radeoffs beween QoC guaranees n he presence of aacks and he requred nework resources employed for daa auhencaon. In addon, snce J (l) are nondecreasng funcons of l, for each plan Σ, QoC requremens (e.g., a bound on J (l)) can be mapped no consrans on l.e., he number of non-auhencaed communcaon packes beween consecuve auhencaed ones. We show effecs of negry enforcemens on auomove cruse conrol by focusng on he reachable regons for sae esmaon errors (Fg. 5); he vehcle can be modeled as a dynamcal sysem [16] wh hree saes capurng he dfference beween he desred and curren dsance from he precedng vehcle (x 1 ), he dfference beween he desred and developed speed (x 2 ), and acceleraon (x 3 ). A sealhy aack ha compromses only dsance measuremens can sll resul n unbounded esmaon errors when no daa negry s enforced. On he oher hand, when dsance sensor s negry s enforced a me k = 4, here exss a noable reducon n he sze of 4-reachable regon for esmaon error. Fg. 5. Evoluon of he sae esmaon error regons R[k] for auomove cruse conrol n he presence of aacks on he dsance sensor, wh and whou daa negry enforcemen a k = 4. Esmaon errors for saes ha correspond o he dsance, speed, and acceleraon are e 1, e 2, and e 3, respecvely; snce R[k] R 3, correspondng 2D projecons are also presened. IV. MODELING OF REAL-TIME MESSAGES WITH INTERMITTENT AUTHENTICATION Le s revs he example from Secon II wh wo perodc real-me messages M 1 (15, 50, 50) and M 2 (15, 100, 100), as well as he correspondng messages M 1(35, 50, 50) and M 2(35, 100, 100) when auhencaon s added. Snce nework ulzaon for each message M and he overall ulzaon are defned as U = c and U M = N U, respecvely, follows ha he se of messages wh connuous daa auhencaon has U M = 1.05, and s hus nfeasble. On he oher hand, assume for example, ha negry enforcemen for daa ransmed va M 1 s requred only every fourh ransmsson (.e., every 200 me uns). Then he nework demand for hese wo messages can be depced as shown n Fg. 6(a), (b). Now, le s assume ha boh auhencaed ransmssons of M 1 and M 2 are ready a = 0 when he nework has jus sared ransmng a non realme message of lengh 25 me uns. In hs case, M 1 wll mss s deadlne a = 50, as shown n Fg. 6(c). However, f he nal auhencaon of message M 1 s delayed by, for example, 100 me uns, he messages are schedulable wh EDF scheduler, as shown n Fg. 6(d). Furhermore, noe ha he negry requremens are no volaed snce every sequence of four consecuve ransmssons of message M 1 conans exacly one auhencaed ransmsson. As llusraed n he example, s benefcal o expand he sandard real-me message model by allowng for perodc message exensons ha nclude a MAC. Addonally, o gve a degree of freedom durng schedulng and avod he scenaro from Fg. 6(c), he model should faclae capurng offses o he nal auhencaon. Thus, we model he se M of real-me messages wh nermen auhencaon by defnng each message as M (C,, l, s ), 1 N where C = [c norm, c ex ] conans he ransmsson mes, normal and exended, of he h message n non-auhencaed and auhencaed ransmsson mode, respecvely, s he normal message perod.e., he me beween consecuve message ransmsson requess, l s he perod of exended messages specfed as an neger mulple of normal message perods.e., every l consecuve messages conan exacly one auhen-
5 (a) (b) (c) (d) M 1 M Deadlne mss s 2 =0 s 1 = Fg. 6. Two messages M 1 ([15, 35], 50, 4, s 1 ) and M 2 ([15, 35], 100, 1, s 2 ) sharng a nework wh a non real-me message wh ransmsson me 25 me uns. As shown n (c) hs message se s nfeasble f boh messages are auhencaed a = 0 (deadlne mss a = 50). However, f he nal auhencaed ransmsson of M 1 s offse by, for example, 100 me uns (s 1 = 2), hs message se becomes feasble, as shown n (d), whle negry enforcemen requremens reman sasfed. caed message, s s he offse of he nal auhencaed message ha sasfes 0 s l 1,.e., he ransmsson reques me of he frs auhencaed message s s. To smplfy our noaon we assume ha he relave deadlne of each message M s, alhough hs work can be drecly exended o cover any deadlne d, whch would n urn faclae capurng of local packe processng and conrol updang asks a each CPU. Fnally, for he message model, he message and overall ulzaons are U = cnorm + cex c norm N, U M = U. (1) l Gven he presened message model, we pose wo essenal problems. Frs, noe ha n our example from Fg. 6, offses of he nal auhencaed ransmssons were no a pror gven. In fac, our goal s o deermne a se of offses of nal auhencaed messages s 1,..., s N, f such se exss, ha yelds a feasble se of messages over a shared nework, whle sll sasfyng negry enforcemen requremens capured as predefned l 1,..., l N. Furhermore, a closer nspecon of our example n Fg. 6, yelds o a concluson ha negry can be enforced n every hrd ransmed message for M 1 (.e., l 1 = 3), nsead of every fourh one, whle sll ensurng nework schedulably. Ths would effecvely mprove QoC guaranees n he presence of aacks, as descrbed n Secon II. Therefore, he second problem can be cas as an opmzaon problem ha srves o fnd an assgnmen of nal auhencaed ransmsson offses (s 1,..., s N ) and negry enforcemen raes (l 1,..., l N ) ha mnmze he overall QoC degradaon whle ensurng nework schedulably, and even allocang some level of ulzaon for non real-me messages. Here, he overall QoC degradaon can be capured as N ω J (l ), where weghs ω > 0 encode he mporance of he specfc conrol loop. Noe ha hs mus be done wh respec o he mnmum requred negry enforcemen rae (capured by l1 max,..., ln max ), ha guaranees he mnmum QoC specfed a desgn me. The aforemenoned problems can be formally specfed as follows. Problem 1: For a se of real-me messages M wh l 1,..., l N capurng prespecfed QoC requremens, fnd offses s 1,..., s N for nal auhencaed messages such ha he obaned complee se M s feasble under non-preempve EDF. Problem 2: For a se of real-me messages M and a se of assocaed cos funcons J (l ), = 1,..., N, fnd offses s 1,..., s N for nal auhencaed messages and opmal auhencaon perods l 1,..., l N such ha he obaned complee message se M s feasble under non-preempve EDF, and he objecve N ω J (l ) s mnmzed. Fnally, s mporan o hghlgh ha we focus on schedulably wh EDF scheduler, whch s opmal for non-dle schedules and ouperforms rae-monoonc schedulers for realsc loads on neworks such as CAN [13], [17]. V. SCHEDULING QOC-AWARE NETWORK MESSAGES WITH INTERMITTENT AUTHENTICATION In hs secon, we nroduce a mehod o solve Problem 1. Specfcally, we sar wh schedulably condons for nonpremepve messages under EDF, before presenng a MILP formulaon o oban feasble auhencaon offses s 1,..., s N. A. Schedulably wh Non-Preempve EDF Schedulably condons for a se of sandard real-me messages under non-preempve EDF were nroduced n [18]. Theorem 1 ([18]): Consder a se of real-me messages M (c,, d ), 1 N. The message se s schedulable under non-preempve EDF over a nework shared wh non real-me messages wh maxmum ransmsson me c NRT max f N c 1 and N { } d max 0, + 1 c + c m k, k T S, (2) where T S = N { d + j j = 0,..., max d }, max = { ( max d 1,..., d N, c m + ( ) ) } N 1 d c /(1 U M ), and c m = max{c NRT max, max N c }. Remark 1: The bound on he me esng se n Theorem 1 depends on max, whch sgnfcanly ncreases as ulzaon approaches one. In [18], he auhors sugges ha hghly ulzed lnks/neworks should be avoded. Anoher opon s o es he above condon (2) over he whole hyperperod P H, beyond whch he schedule repeas, where P H = lcm{p 1,..., p N },.e., he leas common mulple of message perods p 1,..., p N. Remark 2: The condon n (2) does no suppor offses, as was derved for sporadc messages. Consequenly, necessarly defends agans he wors-case message algnmen. Thus, can suffcenly be used for perodc messages wh offses as long as offses are neger mulples of perods, snce hs shfng of messages does no nroduce any new arrval paerns. However, he condon n (2) mus hen be evaluaed a absolue deadlnes and max mus be exended accordngly. Observe ha he nework load condon from (2), akes he form of a weghed sum, where wegh facors are message ransmsson mes and weghed addends are negers counng he number of ransmssons of every message, from he zeroh nsan and up o me k. We capure hese message couns
6 conrbung o he nework demand durng he me [0, k ] as { } η n&e k ( k ) = max 0, + 1 (3) for he number of normal and exended messages, and { } η ex k s ( k ) = max 0, + 1 (4) l for he number of exended messages (wh MAC). Ths allows us o formulae he oal lnk demand of real-me messages M (C,, l, s ), 1 N up o he me k as N ( η c&e ( k )c norm + η ex ) ( k ) c. The me esng se n our case has o nclude deadlnes of all (normal and exended) messages, whch are mulples of normal message perods. The upper bound on he me esng nsans becomes max gven ha d = and normal frame offses are always zero. Smlarly, max akes he maxmum value of all offse deadlnes (due o exended messages), and s upper bound ha depends on he ulzaon (.e., (c m + N d (1 )c )/(1 U M ) n Theorem 1), ransforms no (c m + N l 1 l c ex )/(1 U M ). Ths s caused by he fac ha only exended messages yeld a nonzero numeraor n he sum.e., he perod of hese messages s l whle deadlnes are sll and ransmsson mes of hese messages are c ex. Fnally, c m remans he ransmsson me of he longes of all messages. Thus, we can formulae he followng resul. Theorem 2: A se of real-me messages M (C,, l, s ), N s schedulable by non-preempve EDF f U M 1 and N ( η c&e ( k )c norm + η ex ) ( k ) c + cm k, k T S, where T S = N max {max N (s + 1), cm+ N { j j = 1,..., max l } 1 l c ex 1 U M } (5), max =, c = c ex c norm, and c m = max{c NRT max, max N cex }. Proof: The proof follows drecly from he proof of he correspondng heorem from [18] and s hus omed. B. Message Se Compleon wh Predefned QoC For synhess of feasble message ses (.e., o solve Problem 1) our goal s o fnd a se of parameers s 1,..., s N resulng n a complee message se ha s feasble under nonpreempve EDF. In oher words, we consder our message ses as ncomplee,.e., offses of nal auhencaed ransmssons are aken o be varables. On he oher hand, QoC requremens are predefned as specfc negry enforcemen raes l 1,..., l N. Le us defne bnary varables a k,j as ndcaors ha by he k h nsan he j h auhencaed ransmsson of message M should have compleed ransmsson. Here, 1 N, 1 j max l, 1 k T S. The relaon beween varables and real-me message parameers can be expressed as a k,j a k,j = 1 k (s + 1) + (j 1)l. (6) For example, for he schedule from Fg. 6(d), varable assgnmen for message M 1 s a 1 1,1 = 0, a 1 2,1 = 0, a 1 3,1 = 1, a 1 4,1 = 1. From (4) follows ha η ex ( k ) = max l j=1 a k,j, whle η c&e ( k ) from (3) evaluaes o a consan for any me nsan. Thus, we can express he condon (5) as max l N p c norm η c&e ( k ) + c + c m k, (7) j=1 a k,j wh c m = max{c NRT max, max N cex }. The nework demand condon s now expressed as a se of lnear consrans snce only depends on bnary varables a k,j. The logcal condons from (6) can be cas as lnear consrans by applyng he Bg M mehod [19]. Thus, equvalen lnear consrans are (s + 1) + (j 1)l k + M(1 a k,j), (8) (s + 1) + (j 1)l > k Ma k,j, (9) where M s a large consan. Also, for negry requremens o be sasfed (.e., ha n every l ransmsson perods, exacly one ransmsson s auhencaed), neger varables s sasfy 0 s l 1. (10) Fnally, he complee MILP formulaon ha fnds a feasble soluon o Problem 1 consss of consrans (7)-(10), where ndces are n her respecve ranges.e., max 1 N, 1 j, 1 k T S. (11) l Noe ha snce only feasbly s of neres here, we dd no specfy any objecves for he opmzaon problem above. In addon, he obaned assgnmen s 1,..., s n, f exsen, produces a feasble message se due o Theorem 2. Fnally, snce MILP solvers requre he use of non-src nequales, (9) can be expressed as (s + 1) + (j 1)l k Ma k,j + ε, for a small ε > 0. In hs case, he values for M and ε have o be assgned n a way ha assures no poenal errors are nroduced due o fne precson mplemenaons of MILP solvers. More deals can be found n [20, Remark 1]. VI. QOC-OPTIMAL BANDWIDTH ALLOCATION To solve Problem 2, opmal lnk allocaon s of neres,.e., we wsh o ncrease he negry enforcemen raes as much as possble whle mananng schedulably. Ths explos he fac ha QoC degradaon funcons J (l ) map he negry enforcemen rae no QoC. In addon, wh respec o he lowes allowable QoC for a gven conrol loop, mnmum negry enforcemen raes are defned hrough a se of consans l1 max,..., ln max. We denfy a couple of challenges n solvng Problem 2. Frs, suable cos funcons need o be formed capurng he relaonshp beween he negry enforcemen rae and QoC, n a way ha suppors solvng he opmzaon problem. Based on a weghed sum of hese funcons, we can opmze he overall QoC subjec o schedulably consrans. Second, s necessary o avod specfyng he exac ulzaon n he bound of he me esng se max n (5), as he overall ulzaon
7 U M s no known whle opmzng auhencaon raes. We address hese challenges n he remander of hs secon. Message parameers l 1,..., l N are now varables bounded from above wh he mnmum QoC requremen 1 l l max, 1 N. Ths does no affec he lneary of he problem and consrans expressed n (7)-(10) reman unchanged. The frs challenge o address s specfyng QoC degradaon funcons J (l ). As we dscussed n Secon III, our reachably analyss framework provdes numercal descrpons for hese funcons. We observe ha for praccal sysems, pecewse-lnear approxmaons can be fed o QoC degradaon funcons J (l ) whou sgnfcan effecs on accuracy, as shown on example cos funcons n Fg. 8. Therefore, we can adop he pece-wse lnear descrpon of approxmaed QoC degradaon funcons as ˆ J (l ) = F r=1 ( (α r l + βr)b ) r. Here, F denoes he number of approxmang lnear segmens of he cos funcon for he h closed-loop, αrl + βr s he equaon of he r h segmen over he range l [ l r, l r ], and Jˆ (l ) s connuous so ha [1, l max ] = F r=1 [ lr, l r ]. Selecor varables b r {0, 1} ensure ha he correc lnear segmen s enabled based on he curren value of l.e., b r = 1 lr l l r, 1 r F. (12) For example, he QoC-degradaon curve n Fg. 8(lef) has 4 segmens: {[1, 2], [2, 3], [3, 18], [18, 30]}. Noe ha he mulplcaon of varables b rl s nonlnear. Ths can be solved by nroducng addonal varables c r = b rl. By applyng he Bg M mehod, as before, a se of lnear consrans specfyng hese relaons can be formulaed as lr M(1 b r) l l r + Mb r, lr Mb r l l r + M(1 b r), F r=1 (13) b r = 1, 1 N, (14) c r b rm, c r l (1 b r)m, 0 c r l. (15) Here, consrans (13) mplemen selecor varable condons n (12). Consrans n (14) guaranee ha exacly one lnear segmen of he pecewse lnear approxmaon s acve. The frs consran n (15) provdes c r = 0 when he correspondng segmen s nacve,.e., l / [ l r, l r ] and b r = 0, whle he second one guaranees c r = 1 when l [ l r, l r ] and b r = 1. Noe ha he number of auhencaed ransmssons, capured as he range of j n (11), mus accoun for he case when every message auhencaes every ransmsson, snce he range of ndces n MILP may no depend on varables. Thus, we consder he upper bound for he number of auhencaed ransmssons j as max l l mn =1 = max. Addonal ssue arses from he need o specfy exac lnk ulzaon whle calculang he bound on he me esng se n (5), because U M affecs max. One soluon s o se an upper bound on he overall ulzaon. Ths can be of praccal use snce he nework s usually shared beween real-me and non real-me messages. In hs scenaro, he sysem desgner can desgnae Iner-enforcemen dsance for second sysem U M > 0.98 U M Iner-enforcemen dsance for frs sysem Fg. 7. Example of an allowable regon of ner-enforcemen dsances gven a prese upper ulzaon bound of ŪM = 0.98, for he cruse conrol and seerng conrol for lane rackng case sudes from Secon VII. a lower-bound on ulzaon assgned o non real-me raffc. We can ransform he expresson for ulzaon n (1) no an nequaly specfyng upper lnk ulzaon bound as N U M (l 1,..., l N ) = c l + N c norm ŪM, (16) where ŪM s he desred upper bound for nework ulzaon. Noce ha negry enforcemen raes for all messages are encoded n varables l, and hose are he only varables n (16). The relaon n (16) s, however, no lnear. Moreover, a seemngly convenen change of varables f = 1 l as n [21] resuls n consrans ha are no easly cas as lnear. We hus ake a dfferen approach by drecly capurng he se of neger values l 1,..., l N for whch U M (l 1,..., l N ) sasfes (16). For example, Fg. 7 llusraes an example of such a regon when negry enforcemen s opmzed for wo sysems and a predefned upper ulzaon bound, based on a realsc case sudy from Secon VII. Here, s mporan o noe ha hs regon can be expressed usng lnear consrans on varables l 1 and l 2 as: l 1 l1 mn = 3, l 2 l2 mn = 3, l 1 + l 2 9, M(l 2 3) 8 l 1. The frs wo consrans bound varables l 1 and l 2 from below, and he hrd ensures he varables do no ake any values below he lne l 1 + l 2 = 9. Snce hs s no suffcen (e.g., pons (l 1, l 2 ) {(6, 3), (7, 3)} sasfy he hree consrans bu volae he ulzaon bound), he las consran ensures ha l 2 = 3 l 1 8 holds. Even hough he added number of consrans s no sgnfcan, hs specfcaon of an upper ulzaon bound becomes less appealng when he number of messages wh opmzable negry enforcemen rae rses, and as he allowable regon ges more complex. Neverheless, hs echnque offers an effcen way of compleng a QoC-opmal message se. Consequenly, we can now specfy our MILP-formulaon for he QoC-opmal lnk allocaon as he followng problem [ ] N F mn ω r=1 (α rc r + β rb r) subjec o: (7)-(10), (13)-(15), (17) l mn l l max, U M (l 1,..., l N ) ŪM max 1 N, 1 j, 1 k T S. In he case of our runnng example, hs formulaon produces a oal of 92 varables, sx of whch are negers (s -s,
8 l -s, c r-s), and a oal of 193 consrans f a wo-segmen cos funcon s used for M 1. Resulng negry enforcemen raes are, as prevously expeced, l1 = 3, l2 = 1, f maxmum raes are se a nal values of he example (l1 max = 4, l2 max = 1). The followng secon proposes an approach o deal wh an a-pror unknown ulzaon for opmal lnk allocaon. A. Opporunsc Bandwdh Allocaon Consder a se M of complee real-me messages M, = 1,...N; we assume ha offses of nal auhencaed ransmssons s 1,..., s N are obaned usng he MILP formulaon descrbed n Secons V-B or VI, and ha QoC parameers (.e., negry enforcemen raes l 1,..., l N ) are eher predefned, f MILP formulaon from Secon V-B s used (Scenaro 1), or obaned usng he MILP formulaon from Secon VI wh respec o an upper ulzaon bound ŪM (referred o as Scenaro 2). Thus, M s schedulable wh non-preempve EDF scheduler n he presence of non realme raffc. However, unless he overall ulzaon U M s 1, spare bandwdh wll always be avalable a runme. Then, he queson s wheher he remanng avalable bandwdh can be opporunscally used o furher mprove QoC by addng MACs o acve sensor messages, and f so, how should he bandwdh be allocaed o he messages? Noe ha Scenaro 2 capures suaons where he sysem desgner may use a lower value for overall ulzaon bound Ū M o reduce he sze of MILP problem from (17), followed by opporunsc allocaon of spare bandwdh among all sensors n he nework; he bandwdh should be allocaed based on he mprovemen o he overall QoC ha any specfc auhencaed ransmsson would provde. For example, a QoC-opmal message se could be desgned o ulze he nework up o 95%, for whch he MILP sze, deermned by he sze of he me esng se, s no ye drascally affeced by he ulzaon. One of he man requremens for such opporunsc bandwdh allocaon s ha opporunscally addng auhencaon o ransmed sensor measuremens should no affec schedulably of he nal real-me message se M. Thus, for a message o receve an opporuny o exend s ransmsson durng a nework dle me, he dle me has o appear durng a perod when s normal (.e., non-auhencaed) ransmsson occurs and he duraon of he dle me mus be such ha he message (once exended) can be compleely ransmed pror o s deadlne. Noe ha n order for a sensor o perform such analyss locally, s only needed o know parameers of each message M snce message requess occur a he begnnng of each perod. Hence, such opporunsc bandwdh allocaon wll only add addonal auhencaons o normal messages and hus he overall QoC guaranees wll only be mproved. The man remanng challenge s he assgnmen of prores o messages wh addonal MACs such ha he mprovemen n he overall QoC guaranees s maxmzed. Noe ha n some proocols such as CAN, whch s consdered n he case sudy n Secon VII, he message wh hghes prory wll be ransmed and he proocol nrnscally resolves any conflcs. Our approach s o use a polcy ha maxmzes he ncrease n he overall QoC by assgnng he prory o hese addonal messages such ha corresponds o he mprovemen of he specfc J ˆ. Specfcally, consder opporunscally addng auhencaon o message M released a me nsan, where k 1 < k, and k 1 and k are he closes precedng and followng me nsans when auhencaed messages are o be released accordng o he nal complee real-me message se. We defne l () and he reward funcon r () as ( mn k 1 l () =, k ), r () = ω J ˆ ( l ()), and assgn prory o exend he message wh MAC a me o be equal o reward funcon r (). Inuvely, mprovemen n QoC from negry enforcemen closer o he mddle beween wo scheduled perodc negry enforcemens s larger, han from mmedae successve negry enforcemens followed by longer perods wh no auhencaons before he nex scheduled perodc enforcemen. As we wll show n Secon VII, based on he above prores, he nework dle mes can be farly dsrbued over messages, so ha he resulng negry enforcemens are nermen, raher han perodc, whch effecvely furher lms effecs of aacks. VII. EVALUATION To evaluae our approach for nework schedulng and bandwdh allocaon wh QoC guaranees n he presence of aacks, we use a sandard benchmark proposed by he Socey of Auomove Engneers (SAE) [22]. Ths benchmark specfes communcaon requremens for auomove subsysems on an elecrc vehcle plaform. Communcaon requremens conss of 53 messages beween seven subsysems ncludng he drver, brakng sysem, ransmsson and vehcle conrol, baery and nverer/moor conrollers, and he nsrumenaon cluser. Full message specfcaons are provded n Appendx A. Sporadc messages are no assgned mnmum ner-arrval mes n he benchmark specfcaon. For our analyss, we assume ha all sporadc messages are ransmed wh 20 ms perod, and respecve deadlnes equal o her perods. All oher messages are also assumed o have deadlnes equal o her perods. Addonally, we wll assume ha he longes possble message s a full-lengh CAN message (64 b payload wh 533 µs ransmsson me a 240 kbps). We exend he benchmark by addng seven more messages (54 60 specfed n Appendx A) ha are necessary for realzaon of hree addonal conrol loops cruse conrol, dfferenal brakng, and seerng conrol for lane rackng, presened n deal n [16], [23], [24], respecvely. We use avalable models of hese hree sysems as an npu o our reachably analyss framework presened n Secon III o oban QoC degradaon curves. These curves and her pecewse lnear approxmaons are shown n Fg. 8. Vehcle model used for cruse conrol conans hree saes devaon from desred dsance o he precedng vehcle, devaon from desred speed, and acceleraon. In seady sae, all of hese values are equal o zero, snce he vehcle s movng a consan desred speed wh correc dsance from precedng vehcle. To deermne maxmal ner-enforcemen dsance l1 max, we need o decde on he maxmal error e max 1 ha provdes sasfacory sysem performance. In hs work,
9 Max. nroduced error e max e max Orgnal curve Lnear approxmaon Iner-enforcemen dsance l 1 Iner-enforcemen dsance l 2 e max Iner-enforcemen dsance l 3 Fg. 8. QoC degradaon (capured as he wors-case mean nduced sae esmaon error) n he presence of aacks, wh respec o negry enforcemen perods for: (lef) Cruse conrol, (mddle) Dfferenal brakng, and (rgh) Seerng conrol for lane rackng. we se allowed errors o be 0.1 m s on acceleraon, 0.5 m 2 s on speed and 1 m on dsance. Ths resuls n he norm of he mean esmaon error of e max 1 = , whch mapped hrough he QoC degradaon curve shown n Fg. 8(lef) gves he maxmum ner-enforcemen dsance of l1 max = 13 samplng perods. Dfferenal brakng model akes fve saes no consderaon brake pressure, laeral velocy, yaw rae of he vehcle, and neral laeral poson and velocy. Usng parameers of he model from [23], we oban he QoC degradaon curve shown n Fg. 8(mddle). Ths shows ha he aacker has freedom o nroduce an error ha s several orders of magnude larger han he nose, for any l 2 > 1. Hence, we consder l2 max = 1. Fnally, seerng conrol for lane rackng consders four saes laeral poson error, laeral speed, yaw angle dfference beween vehcle and he road, and he speed a whch hs angle s changed. In seady sae, when he vehcle s movng along a sragh road, values of each of he saes are zero, snce he vehcle s holdng cener poson. We assume ha he vehcle s movng a speed of 30 m s and oban addonal model parameers as n [24]. Gven hese parameers, we oban he QoC degradaon curve shown n Fg. 8(rgh). Followng he same mehodology as for he cruse conrol sysem, we se allowed errors for laeral poson error, laeral speed, seerng angle, and angular velocy of axle as 0.2m, 0.02 m s, 0.18rad, and rad s respecvely, whch yelds e max 3 = Ths, n urn, maps o maxmum ner-enforcemen dsance of l3 max = 6 samplng perods. We sar by evaluang effcency and scalably of our approach. To solve our MILP formulaons we use Gurob MILP solver [25]. We measure solver execuon mes on a plaform wh a 5 h gen. 3.0 GHz Inel 7 CPU and 16 GB of memory. If negry s enforced on every daa pon for relevan subsysems n our message se, he lnk s overulsed wh U M = (n case of CAN bus speed of 240 kbps). However, f we se he negry enforcemen raes o he predeermned maxmum values (l1 max = 13, l2 max = 1, l3 max = 6), ulzaon reduces o U M = Average solver execuon me for he formulaon wh predefned QoC s s. Fg. 9 shows average MILP solver execuon mes for he same formulaon and ulzaons n ncremens of 0.1, as well as for and Opmzer execuon me rends n case of opmal bandwdh allocaon (presened n Secon VI), are smlar and are hus omed. The ncrease n he problem sze due o hgh ulzaon s vsble, whch Solver execuon me [s] Lnk ulzaon Fg. 9. Average MILP solver execuon mes and respecve 95% confdence nervals for he modfed SAE benchmark wh ulzaons , as well as for 0.998, and The execuon me ncreases sgnfcanly due o ncrease n he problem sze as U M approaches 1. suppors our effors on opporunsc bandwdh allocaon. For a specfc upper ulzaon bound of ŪM = 0.98, we oban l1 = 5, l2 = 1, l3 = 4, whle he solver akes an average of s. Obaned ulzaon s UM = < Fnally, we analyzed conrol performance for he hese sysems n he presence of aacks; he resuls are shown n Fg. 10 and Fg. 11. Fg. 10 (lef) and Fg. 11 (lef) confrm ha sysem performance conforms o requred mnmum performance when l 1 = l1 max = 13, l 2 = l2 max = 1, and l 3 = l3 max = 6, snce he mean sae errors do no exceed requred lms. Fg. 10 (mddle) and Fg. 11 (mddle) llusrae he mprovemen n QoC when enforcemen raes are opmzed wh respec o he upper ulzaon bound Ū M = 0.98, resulng n l1 = 5, l2 = 1, l3 = 4. Fnally, Fg. 10, Fg. 11 (rgh), show sgnfcan QoC mprovemen when respecve conrol loops can opporunscally use avalable nework dle mes o auhencae sensor measuremens, as proposed n Secon VI-A, sarng from he message se obaned from he opmzaon procedure for ŪM = In hs case, average resulng auhencaon raes l oppor 1 = 1.64, l oppor 2 = 1, and l oppor 3 = 1.61 are sgnfcanly hgher han for he opmal allocaon wh ŪM = Noe ha he aacker s assumed o have full knowledge on nsans when boh perodc and opporunsc auhencaon occur, and plans aacks accordngly. If opporunsc auhencaon pons were unknown a aack desgn me, or mpossble o predc, he aacker would evenually volae sealhness condons [12]. The fnal lnk ulzaon wh dle mes exhaused by opporunsc ransmssons s VIII. CONCLUSION In hs paper, we have presened a schedulng framework ha jonly consders mng and secury requremens for communcaon beween sensors and conrollers. We have shown how physcs-aware QoC requremens can be ranslaed
10 Reference Allowed mean poson error [m] Allowed mean speed error [m/s] Error n poson [m] Error n speed [m/s] Amplude Tme [s] Tme [s] Tme [s] Fg. 10. Cruse conrol wh hree dfferen negry enforcemen polces: l1 max = 13 (lef), l1 = 5 (mddle), and varable loppor 1 ha ranges from 1 o 5, wh mean value of 1.64 (rgh). The aack begns a 20 s, and we presen wo saes devaon from desred dsance and devaon from desred speed. Amplude Reference Allowed mean dsance error [m] Allowed mean angle error [rad] Dsance from road cener [m] Angle of wheels o he road [rad] Tme [s] Tme [s] Tme [s] Fg. 11. Seerng conrol for lane rackng wh 3 negry enforcemen polces: l3 max = 6 (lef), l3 = 4 (mddle), and varable loppor 3 rangng from 1 o 4, wh mean value 1.61 (rgh). The aack begns a 20 s, and we presen wo saes dsance from he road cener and wheels angle relave o he road. no real-me consrans, based on whch an MILP problem can be formulaed for QoC-aware bandwdh allocaon. Addonally, we have shown how an MILP opmzaon could be used o maxmze he overall QoC guaranees and ensure schedulably of non-preempve sensor messages. Moreover, n cases where opmal bandwdh allocaon may become neffcen (as nework ulzaon approaches 1), we have provded an effcen runme mehod for opporunsc bandwdh ulzaon n order o addonally mprove QoC guaranees. Fnally, we have demonsraed applcably of our framework on a sandard auomove benchmark for CAN bus, and shown how an oherwse nfeasble message se can be scheduled whle ensurng ha exsng real-me guaranees are no volaed, as well as sasfyng QoC requremens. As an avenue for fuure work we wll exend hs work o ncorporae recen resuls on local (sensor-wse) auhencaon, as well as negrae he presened approach for schedulng of real-me messages wh nermen auhencaon wh our work on schedulng secury-aware real-me asks [20]. REFERENCES [1] S. Checkoway e al., Comprehensve expermenal analyses of auomove aack surfaces, n Proc. of USENIX Secury, [2] A. Greenberg, Hackers Remoely Kll a Jeep on he Hghway, Wred Magazne, [3] D. Shepard, J. Bha, and T. Humphreys, Drone hack, GPS World, vol. 23, no. 8, pp , [4] C.-W. Ln, Q. Zhu, C. Phung, and A. Sangovann-Vncenell, Securyaware mappng for CAN-based real-me dsrbued auomove sysems, n In. Conf. on Compuer-Aded Desgn (ICCAD), 2013, pp [5] C.-W. Ln, B. Zheng, Q. Zhu, and A. Sangovann-Vncenell, Securyaware desgn mehodology and opmzaon for auomove sysems, ACM Trans. on Des. Auom. of Elec. Sys., vol. 21, no. 1, p. 18, [6] M. Hasan, S. Mohan, R. B. Bobba, and R. Pellzzon, Explorng opporunsc execuon for negrang secury no legacy hard realme sysems, n IEEE RTSS, 2016, pp [7] T. Xe and X. Qn, Improvng secury for perodc asks n embedded sysems hrough schedulng, ACM Trans. Embed. Compu. Sys., vol. 6, no. 3, Jul [8] M. Ln, L. Xu, L. T. Yang, X. Qn, N. Zheng, Z. Wu, and M. Qu, Sac secury opmzaon for real-me sysems, IEEE Transacons on Indusral Informacs, vol. 5, no. 1, pp , Feb [9] Y. Mo, E. Garone, A. Casavola, and B. Snopol, False daa njecon aacks agans sae esmaon n wreless sensor neworks, n 49h IEEE Conf. on Decson and Conrol (CDC), 2010, pp [10] C. Kwon, W. Lu, and I. Hwang, Analyss and desgn of sealhy cyber aacks on unmanned aeral sysems, Journal of Aerospace Informaon Sysems, vol. 1, no. 8, [11] I. Jovanov and M. Pajc, Relaxng negry requremens for reslen conrol sysems, n 56h IEEE Conference on Decson and Conrol (CDC), [12], Relaxng negry requremens for reslen conrol sysems, CoRR, vol. abs/ , [13] A. Ana and P. Tabuada, On he benefs of relaxng he perodcy assumpon for neworked conrol sysems over CAN, n 30h IEEE Real-Tme Sysems Symposum (RTSS), 2009, pp [14] M. Pajc, I. Lee, and G. J. Pappas, Aack-reslen sae esmaon for nosy dynamcal sysems, IEEE Transacons on Conrol of Nework Sysems, vol. 4, no. 1, pp , March [15] R. Majumdar, I. Saha, and M. Zaman, Synhess of mnmal-error conrol sofware, n ACM EMSOFT, 2012, pp [16] S. L, K. L, R. Rajaman, and J. Wang, Model predcve mulobjecve vehcular adapve cruse conrol, IEEE Transacons on Conrol Sysems Technology, vol. 19, no. 3, pp , [17] K. M. Zuber and K. G. Shn, Schedulng messages on conroller area nework for real-me CIM applcaons, IEEE Transacons on Robocs and Auomaon, vol. 13, no. 2, pp , [18] Q. Zheng and K. G. Shn, On he ably of esablshng real-me channels n pon-o-pon packe-swched neworks, IEEE Transacons on Communcaons, vol. 42, no. 234, pp , Feb [19] P. Belo e.al, On handlng ndcaor consrans n mxed neger programmng, Compuaonal Opmzaon and Applcaons, vol. 65, no. 3, pp , [20] V. Les, I. Jovanov, and M. Pajc, Secury-aware schedulng of embedded conrol asks, ACM Trans. Embed. Compu Sys., [21] A. Cervn, J. Eker, B. Bernhardsson, and K. Årzén, Feedback feedforward schedulng of conrol asks, Real-Tme Sysems, vol. 23, no. 1-2, pp , [22] Class C Applcaon Requremen Consderaons, SAE J2056/1, 1994 SAE Handbook, Vol, 2, pp [23] T. Plu, G. Ulsoy, and D. Hrova, Vehcle seerng nervenon hrough dfferenal brakng, n ACC, vol. 3, 1995, pp [24] R. Rajaman, Vehcle dynamcs and conrol. Sprnger Scence & Busness Meda, [25] Gurob Opmzaon Inc., Gurob opmzer reference manual, [Onlne]. Avalable: hp://
V.Abramov - FURTHER ANALYSIS OF CONFIDENCE INTERVALS FOR LARGE CLIENT/SERVER COMPUTER NETWORKS
 R&RATA # Vol.) 8, March FURTHER AALYSIS OF COFIDECE ITERVALS FOR LARGE CLIET/SERVER COMPUTER ETWORKS Vyacheslav Abramov School of Mahemacal Scences, Monash Unversy, Buldng 8, Level 4, Clayon Campus, Wellngon
R&RATA # Vol.) 8, March FURTHER AALYSIS OF COFIDECE ITERVALS FOR LARGE CLIET/SERVER COMPUTER ETWORKS Vyacheslav Abramov School of Mahemacal Scences, Monash Unversy, Buldng 8, Level 4, Clayon Campus, Wellngon
Dynamic Team Decision Theory. EECS 558 Project Shrutivandana Sharma and David Shuman December 10, 2005
 Dynamc Team Decson Theory EECS 558 Proec Shruvandana Sharma and Davd Shuman December 0, 005 Oulne Inroducon o Team Decson Theory Decomposon of he Dynamc Team Decson Problem Equvalence of Sac and Dynamc
Dynamc Team Decson Theory EECS 558 Proec Shruvandana Sharma and Davd Shuman December 0, 005 Oulne Inroducon o Team Decson Theory Decomposon of he Dynamc Team Decson Problem Equvalence of Sac and Dynamc
CS 268: Packet Scheduling
 Pace Schedulng Decde when and wha pace o send on oupu ln - Usually mplemened a oupu nerface CS 68: Pace Schedulng flow Ion Soca March 9, 004 Classfer flow flow n Buffer managemen Scheduler soca@cs.bereley.edu
Pace Schedulng Decde when and wha pace o send on oupu ln - Usually mplemened a oupu nerface CS 68: Pace Schedulng flow Ion Soca March 9, 004 Classfer flow flow n Buffer managemen Scheduler soca@cs.bereley.edu
In the complete model, these slopes are ANALYSIS OF VARIANCE FOR THE COMPLETE TWO-WAY MODEL. (! i+1 -! i ) + [(!") i+1,q - [(!
 ANALYSIS OF VARIANCE FOR THE COMPLETE TWO-WAY MODEL The frs hng o es n wo-way ANOVA: Is here neracon? "No neracon" means: The man effecs model would f. Ths n urn means: In he neracon plo (wh A on he horzonal
ANALYSIS OF VARIANCE FOR THE COMPLETE TWO-WAY MODEL The frs hng o es n wo-way ANOVA: Is here neracon? "No neracon" means: The man effecs model would f. Ths n urn means: In he neracon plo (wh A on he horzonal
Time-interval analysis of β decay. V. Horvat and J. C. Hardy
 Tme-nerval analyss of β decay V. Horva and J. C. Hardy Work on he even analyss of β decay [1] connued and resuled n he developmen of a novel mehod of bea-decay me-nerval analyss ha produces hghly accurae
Tme-nerval analyss of β decay V. Horva and J. C. Hardy Work on he even analyss of β decay [1] connued and resuled n he developmen of a novel mehod of bea-decay me-nerval analyss ha produces hghly accurae
Solution in semi infinite diffusion couples (error function analysis)
 Soluon n sem nfne dffuson couples (error funcon analyss) Le us consder now he sem nfne dffuson couple of wo blocks wh concenraon of and I means ha, n a A- bnary sysem, s bondng beween wo blocks made of
Soluon n sem nfne dffuson couples (error funcon analyss) Le us consder now he sem nfne dffuson couple of wo blocks wh concenraon of and I means ha, n a A- bnary sysem, s bondng beween wo blocks made of
Robustness Experiments with Two Variance Components
 Naonal Insue of Sandards and Technology (NIST) Informaon Technology Laboraory (ITL) Sascal Engneerng Dvson (SED) Robusness Expermens wh Two Varance Componens by Ana Ivelsse Avlés avles@ns.gov Conference
Naonal Insue of Sandards and Technology (NIST) Informaon Technology Laboraory (ITL) Sascal Engneerng Dvson (SED) Robusness Expermens wh Two Varance Componens by Ana Ivelsse Avlés avles@ns.gov Conference
Linear Response Theory: The connection between QFT and experiments
 Phys540.nb 39 3 Lnear Response Theory: The connecon beween QFT and expermens 3.1. Basc conceps and deas Q: ow do we measure he conducvy of a meal? A: we frs nroduce a weak elecrc feld E, and hen measure
Phys540.nb 39 3 Lnear Response Theory: The connecon beween QFT and expermens 3.1. Basc conceps and deas Q: ow do we measure he conducvy of a meal? A: we frs nroduce a weak elecrc feld E, and hen measure
Graduate Macroeconomics 2 Problem set 5. - Solutions
 Graduae Macroeconomcs 2 Problem se. - Soluons Queson 1 To answer hs queson we need he frms frs order condons and he equaon ha deermnes he number of frms n equlbrum. The frms frs order condons are: F K
Graduae Macroeconomcs 2 Problem se. - Soluons Queson 1 To answer hs queson we need he frms frs order condons and he equaon ha deermnes he number of frms n equlbrum. The frms frs order condons are: F K
Variants of Pegasos. December 11, 2009
 Inroducon Varans of Pegasos SooWoong Ryu bshboy@sanford.edu December, 009 Youngsoo Cho yc344@sanford.edu Developng a new SVM algorhm s ongong research opc. Among many exng SVM algorhms, we wll focus on
Inroducon Varans of Pegasos SooWoong Ryu bshboy@sanford.edu December, 009 Youngsoo Cho yc344@sanford.edu Developng a new SVM algorhm s ongong research opc. Among many exng SVM algorhms, we wll focus on
GENERATING CERTAIN QUINTIC IRREDUCIBLE POLYNOMIALS OVER FINITE FIELDS. Youngwoo Ahn and Kitae Kim
 Korean J. Mah. 19 (2011), No. 3, pp. 263 272 GENERATING CERTAIN QUINTIC IRREDUCIBLE POLYNOMIALS OVER FINITE FIELDS Youngwoo Ahn and Kae Km Absrac. In he paper [1], an explc correspondence beween ceran
Korean J. Mah. 19 (2011), No. 3, pp. 263 272 GENERATING CERTAIN QUINTIC IRREDUCIBLE POLYNOMIALS OVER FINITE FIELDS Youngwoo Ahn and Kae Km Absrac. In he paper [1], an explc correspondence beween ceran
Reactive Methods to Solve the Berth AllocationProblem with Stochastic Arrival and Handling Times
 Reacve Mehods o Solve he Berh AllocaonProblem wh Sochasc Arrval and Handlng Tmes Nsh Umang* Mchel Berlare* * TRANSP-OR, Ecole Polyechnque Fédérale de Lausanne Frs Workshop on Large Scale Opmzaon November
Reacve Mehods o Solve he Berh AllocaonProblem wh Sochasc Arrval and Handlng Tmes Nsh Umang* Mchel Berlare* * TRANSP-OR, Ecole Polyechnque Fédérale de Lausanne Frs Workshop on Large Scale Opmzaon November
Increasing the Probablility of Timely and Correct Message Delivery in Road Side Unit Based Vehicular Communcation
 Halmsad Unversy For he Developmen of Organsaons Producs and Qualy of Lfe. Increasng he Probablly of Tmely and Correc Message Delvery n Road Sde Un Based Vehcular Communcaon Magnus Jonsson Krsna Kuner and
Halmsad Unversy For he Developmen of Organsaons Producs and Qualy of Lfe. Increasng he Probablly of Tmely and Correc Message Delvery n Road Sde Un Based Vehcular Communcaon Magnus Jonsson Krsna Kuner and
Tight results for Next Fit and Worst Fit with resource augmentation
 Tgh resuls for Nex F and Wors F wh resource augmenaon Joan Boyar Leah Epsen Asaf Levn Asrac I s well known ha he wo smple algorhms for he classc n packng prolem, NF and WF oh have an approxmaon rao of
Tgh resuls for Nex F and Wors F wh resource augmenaon Joan Boyar Leah Epsen Asaf Levn Asrac I s well known ha he wo smple algorhms for he classc n packng prolem, NF and WF oh have an approxmaon rao of
FTCS Solution to the Heat Equation
 FTCS Soluon o he Hea Equaon ME 448/548 Noes Gerald Reckenwald Porland Sae Unversy Deparmen of Mechancal Engneerng gerry@pdxedu ME 448/548: FTCS Soluon o he Hea Equaon Overvew Use he forward fne d erence
FTCS Soluon o he Hea Equaon ME 448/548 Noes Gerald Reckenwald Porland Sae Unversy Deparmen of Mechancal Engneerng gerry@pdxedu ME 448/548: FTCS Soluon o he Hea Equaon Overvew Use he forward fne d erence
Lecture 18: The Laplace Transform (See Sections and 14.7 in Boas)
 Lecure 8: The Lalace Transform (See Secons 88- and 47 n Boas) Recall ha our bg-cure goal s he analyss of he dfferenal equaon, ax bx cx F, where we emloy varous exansons for he drvng funcon F deendng on
Lecure 8: The Lalace Transform (See Secons 88- and 47 n Boas) Recall ha our bg-cure goal s he analyss of he dfferenal equaon, ax bx cx F, where we emloy varous exansons for he drvng funcon F deendng on
Performance Analysis for a Network having Standby Redundant Unit with Waiting in Repair
 TECHNI Inernaonal Journal of Compung Scence Communcaon Technologes VOL.5 NO. July 22 (ISSN 974-3375 erformance nalyss for a Nework havng Sby edundan Un wh ang n epar Jendra Sngh 2 abns orwal 2 Deparmen
TECHNI Inernaonal Journal of Compung Scence Communcaon Technologes VOL.5 NO. July 22 (ISSN 974-3375 erformance nalyss for a Nework havng Sby edundan Un wh ang n epar Jendra Sngh 2 abns orwal 2 Deparmen
( ) () we define the interaction representation by the unitary transformation () = ()
 Hgher Order Perurbaon Theory Mchael Fowler 3/7/6 The neracon Represenaon Recall ha n he frs par of hs course sequence, we dscussed he chrödnger and Hesenberg represenaons of quanum mechancs here n he chrödnger
Hgher Order Perurbaon Theory Mchael Fowler 3/7/6 The neracon Represenaon Recall ha n he frs par of hs course sequence, we dscussed he chrödnger and Hesenberg represenaons of quanum mechancs here n he chrödnger
Department of Economics University of Toronto
 Deparmen of Economcs Unversy of Torono ECO408F M.A. Economercs Lecure Noes on Heeroskedascy Heeroskedascy o Ths lecure nvolves lookng a modfcaons we need o make o deal wh he regresson model when some of
Deparmen of Economcs Unversy of Torono ECO408F M.A. Economercs Lecure Noes on Heeroskedascy Heeroskedascy o Ths lecure nvolves lookng a modfcaons we need o make o deal wh he regresson model when some of
[ ] 2. [ ]3 + (Δx i + Δx i 1 ) / 2. Δx i-1 Δx i Δx i+1. TPG4160 Reservoir Simulation 2018 Lecture note 3. page 1 of 5
![[ ] 2. [ ]3 + (Δx i + Δx i 1 ) / 2. Δx i-1 Δx i Δx i+1. TPG4160 Reservoir Simulation 2018 Lecture note 3. page 1 of 5 [ ] 2. [ ]3 + (Δx i + Δx i 1 ) / 2. Δx i-1 Δx i Δx i+1. TPG4160 Reservoir Simulation 2018 Lecture note 3. page 1 of 5](/thumbs/85/92299540.jpg) TPG460 Reservor Smulaon 08 page of 5 DISCRETIZATIO OF THE FOW EQUATIOS As we already have seen, fne dfference appromaons of he paral dervaves appearng n he flow equaons may be obaned from Taylor seres
TPG460 Reservor Smulaon 08 page of 5 DISCRETIZATIO OF THE FOW EQUATIOS As we already have seen, fne dfference appromaons of he paral dervaves appearng n he flow equaons may be obaned from Taylor seres
Existence and Uniqueness Results for Random Impulsive Integro-Differential Equation
 Global Journal of Pure and Appled Mahemacs. ISSN 973-768 Volume 4, Number 6 (8), pp. 89-87 Research Inda Publcaons hp://www.rpublcaon.com Exsence and Unqueness Resuls for Random Impulsve Inegro-Dfferenal
Global Journal of Pure and Appled Mahemacs. ISSN 973-768 Volume 4, Number 6 (8), pp. 89-87 Research Inda Publcaons hp://www.rpublcaon.com Exsence and Unqueness Resuls for Random Impulsve Inegro-Dfferenal
( t) Outline of program: BGC1: Survival and event history analysis Oslo, March-May Recapitulation. The additive regression model
 BGC1: Survval and even hsory analyss Oslo, March-May 212 Monday May 7h and Tuesday May 8h The addve regresson model Ørnulf Borgan Deparmen of Mahemacs Unversy of Oslo Oulne of program: Recapulaon Counng
BGC1: Survval and even hsory analyss Oslo, March-May 212 Monday May 7h and Tuesday May 8h The addve regresson model Ørnulf Borgan Deparmen of Mahemacs Unversy of Oslo Oulne of program: Recapulaon Counng
TSS = SST + SSE An orthogonal partition of the total SS
 ANOVA: Topc 4. Orhogonal conrass [ST&D p. 183] H 0 : µ 1 = µ =... = µ H 1 : The mean of a leas one reamen group s dfferen To es hs hypohess, a basc ANOVA allocaes he varaon among reamen means (SST) equally
ANOVA: Topc 4. Orhogonal conrass [ST&D p. 183] H 0 : µ 1 = µ =... = µ H 1 : The mean of a leas one reamen group s dfferen To es hs hypohess, a basc ANOVA allocaes he varaon among reamen means (SST) equally
WiH Wei He
 Sysem Idenfcaon of onlnear Sae-Space Space Baery odels WH We He wehe@calce.umd.edu Advsor: Dr. Chaochao Chen Deparmen of echancal Engneerng Unversy of aryland, College Par 1 Unversy of aryland Bacground
Sysem Idenfcaon of onlnear Sae-Space Space Baery odels WH We He wehe@calce.umd.edu Advsor: Dr. Chaochao Chen Deparmen of echancal Engneerng Unversy of aryland, College Par 1 Unversy of aryland Bacground
CS286.2 Lecture 14: Quantum de Finetti Theorems II
 CS286.2 Lecure 14: Quanum de Fne Theorems II Scrbe: Mara Okounkova 1 Saemen of he heorem Recall he las saemen of he quanum de Fne heorem from he prevous lecure. Theorem 1 Quanum de Fne). Le ρ Dens C 2
CS286.2 Lecure 14: Quanum de Fne Theorems II Scrbe: Mara Okounkova 1 Saemen of he heorem Recall he las saemen of he quanum de Fne heorem from he prevous lecure. Theorem 1 Quanum de Fne). Le ρ Dens C 2
Comb Filters. Comb Filters
 The smple flers dscussed so far are characered eher by a sngle passband and/or a sngle sopband There are applcaons where flers wh mulple passbands and sopbands are requred Thecomb fler s an example of
The smple flers dscussed so far are characered eher by a sngle passband and/or a sngle sopband There are applcaons where flers wh mulple passbands and sopbands are requred Thecomb fler s an example of
Volatility Interpolation
 Volaly Inerpolaon Prelmnary Verson March 00 Jesper Andreasen and Bran Huge Danse Mares, Copenhagen wan.daddy@danseban.com brno@danseban.com Elecronc copy avalable a: hp://ssrn.com/absrac=69497 Inro Local
Volaly Inerpolaon Prelmnary Verson March 00 Jesper Andreasen and Bran Huge Danse Mares, Copenhagen wan.daddy@danseban.com brno@danseban.com Elecronc copy avalable a: hp://ssrn.com/absrac=69497 Inro Local
Relative controllability of nonlinear systems with delays in control
 Relave conrollably o nonlnear sysems wh delays n conrol Jerzy Klamka Insue o Conrol Engneerng, Slesan Techncal Unversy, 44- Glwce, Poland. phone/ax : 48 32 37227, {jklamka}@a.polsl.glwce.pl Keywor: Conrollably.
Relave conrollably o nonlnear sysems wh delays n conrol Jerzy Klamka Insue o Conrol Engneerng, Slesan Techncal Unversy, 44- Glwce, Poland. phone/ax : 48 32 37227, {jklamka}@a.polsl.glwce.pl Keywor: Conrollably.
On One Analytic Method of. Constructing Program Controls
 Appled Mahemacal Scences, Vol. 9, 05, no. 8, 409-407 HIKARI Ld, www.m-hkar.com hp://dx.do.org/0.988/ams.05.54349 On One Analyc Mehod of Consrucng Program Conrols A. N. Kvko, S. V. Chsyakov and Yu. E. Balyna
Appled Mahemacal Scences, Vol. 9, 05, no. 8, 409-407 HIKARI Ld, www.m-hkar.com hp://dx.do.org/0.988/ams.05.54349 On One Analyc Mehod of Consrucng Program Conrols A. N. Kvko, S. V. Chsyakov and Yu. E. Balyna
CS434a/541a: Pattern Recognition Prof. Olga Veksler. Lecture 4
 CS434a/54a: Paern Recognon Prof. Olga Veksler Lecure 4 Oulne Normal Random Varable Properes Dscrmnan funcons Why Normal Random Varables? Analycally racable Works well when observaon comes form a corruped
CS434a/54a: Paern Recognon Prof. Olga Veksler Lecure 4 Oulne Normal Random Varable Properes Dscrmnan funcons Why Normal Random Varables? Analycally racable Works well when observaon comes form a corruped
Motion in Two Dimensions
 Phys 1 Chaper 4 Moon n Two Dmensons adzyubenko@csub.edu hp://www.csub.edu/~adzyubenko 005, 014 A. Dzyubenko 004 Brooks/Cole 1 Dsplacemen as a Vecor The poson of an objec s descrbed by s poson ecor, r The
Phys 1 Chaper 4 Moon n Two Dmensons adzyubenko@csub.edu hp://www.csub.edu/~adzyubenko 005, 014 A. Dzyubenko 004 Brooks/Cole 1 Dsplacemen as a Vecor The poson of an objec s descrbed by s poson ecor, r The
Single-loop System Reliability-Based Design & Topology Optimization (SRBDO/SRBTO): A Matrix-based System Reliability (MSR) Method
 10 h US Naonal Congress on Compuaonal Mechancs Columbus, Oho 16-19, 2009 Sngle-loop Sysem Relably-Based Desgn & Topology Opmzaon (SRBDO/SRBTO): A Marx-based Sysem Relably (MSR) Mehod Tam Nguyen, Junho
10 h US Naonal Congress on Compuaonal Mechancs Columbus, Oho 16-19, 2009 Sngle-loop Sysem Relably-Based Desgn & Topology Opmzaon (SRBDO/SRBTO): A Marx-based Sysem Relably (MSR) Mehod Tam Nguyen, Junho
UNIVERSITAT AUTÒNOMA DE BARCELONA MARCH 2017 EXAMINATION
 INTERNATIONAL TRADE T. J. KEHOE UNIVERSITAT AUTÒNOMA DE BARCELONA MARCH 27 EXAMINATION Please answer wo of he hree quesons. You can consul class noes, workng papers, and arcles whle you are workng on he
INTERNATIONAL TRADE T. J. KEHOE UNIVERSITAT AUTÒNOMA DE BARCELONA MARCH 27 EXAMINATION Please answer wo of he hree quesons. You can consul class noes, workng papers, and arcles whle you are workng on he
Li An-Ping. Beijing , P.R.China
 A New Type of Cpher: DICING_csb L An-Png Bejng 100085, P.R.Chna apl0001@sna.com Absrac: In hs paper, we wll propose a new ype of cpher named DICING_csb, whch s derved from our prevous sream cpher DICING.
A New Type of Cpher: DICING_csb L An-Png Bejng 100085, P.R.Chna apl0001@sna.com Absrac: In hs paper, we wll propose a new ype of cpher named DICING_csb, whch s derved from our prevous sream cpher DICING.
Modeling and Solving of Multi-Product Inventory Lot-Sizing with Supplier Selection under Quantity Discounts
 nernaonal ournal of Appled Engneerng Research SSN 0973-4562 Volume 13, Number 10 (2018) pp. 8708-8713 Modelng and Solvng of Mul-Produc nvenory Lo-Szng wh Suppler Selecon under Quany Dscouns Naapa anchanaruangrong
nernaonal ournal of Appled Engneerng Research SSN 0973-4562 Volume 13, Number 10 (2018) pp. 8708-8713 Modelng and Solvng of Mul-Produc nvenory Lo-Szng wh Suppler Selecon under Quany Dscouns Naapa anchanaruangrong
Efficient Asynchronous Channel Hopping Design for Cognitive Radio Networks
 Effcen Asynchronous Channel Hoppng Desgn for Cognve Rado Neworks Chh-Mn Chao, Chen-Yu Hsu, and Yun-ng Lng Absrac In a cognve rado nework (CRN), a necessary condon for nodes o communcae wh each oher s ha
Effcen Asynchronous Channel Hoppng Desgn for Cognve Rado Neworks Chh-Mn Chao, Chen-Yu Hsu, and Yun-ng Lng Absrac In a cognve rado nework (CRN), a necessary condon for nodes o communcae wh each oher s ha
Online Supplement for Dynamic Multi-Technology. Production-Inventory Problem with Emissions Trading
 Onlne Supplemen for Dynamc Mul-Technology Producon-Invenory Problem wh Emssons Tradng by We Zhang Zhongsheng Hua Yu Xa and Baofeng Huo Proof of Lemma For any ( qr ) Θ s easy o verfy ha he lnear programmng
Onlne Supplemen for Dynamc Mul-Technology Producon-Invenory Problem wh Emssons Tradng by We Zhang Zhongsheng Hua Yu Xa and Baofeng Huo Proof of Lemma For any ( qr ) Θ s easy o verfy ha he lnear programmng
EEL 6266 Power System Operation and Control. Chapter 5 Unit Commitment
 EEL 6266 Power Sysem Operaon and Conrol Chaper 5 Un Commmen Dynamc programmng chef advanage over enumeraon schemes s he reducon n he dmensonaly of he problem n a src prory order scheme, here are only N
EEL 6266 Power Sysem Operaon and Conrol Chaper 5 Un Commmen Dynamc programmng chef advanage over enumeraon schemes s he reducon n he dmensonaly of he problem n a src prory order scheme, here are only N
Lecture 6: Learning for Control (Generalised Linear Regression)
 Lecure 6: Learnng for Conrol (Generalsed Lnear Regresson) Conens: Lnear Mehods for Regresson Leas Squares, Gauss Markov heorem Recursve Leas Squares Lecure 6: RLSC - Prof. Sehu Vjayakumar Lnear Regresson
Lecure 6: Learnng for Conrol (Generalsed Lnear Regresson) Conens: Lnear Mehods for Regresson Leas Squares, Gauss Markov heorem Recursve Leas Squares Lecure 6: RLSC - Prof. Sehu Vjayakumar Lnear Regresson
Econ107 Applied Econometrics Topic 5: Specification: Choosing Independent Variables (Studenmund, Chapter 6)
 Econ7 Appled Economercs Topc 5: Specfcaon: Choosng Independen Varables (Sudenmund, Chaper 6 Specfcaon errors ha we wll deal wh: wrong ndependen varable; wrong funconal form. Ths lecure deals wh wrong ndependen
Econ7 Appled Economercs Topc 5: Specfcaon: Choosng Independen Varables (Sudenmund, Chaper 6 Specfcaon errors ha we wll deal wh: wrong ndependen varable; wrong funconal form. Ths lecure deals wh wrong ndependen
5th International Conference on Advanced Design and Manufacturing Engineering (ICADME 2015)
 5h Inernaonal onference on Advanced Desgn and Manufacurng Engneerng (IADME 5 The Falure Rae Expermenal Sudy of Specal N Machne Tool hunshan He, a, *, La Pan,b and Bng Hu 3,c,,3 ollege of Mechancal and
5h Inernaonal onference on Advanced Desgn and Manufacurng Engneerng (IADME 5 The Falure Rae Expermenal Sudy of Specal N Machne Tool hunshan He, a, *, La Pan,b and Bng Hu 3,c,,3 ollege of Mechancal and
Lecture 11 SVM cont
 Lecure SVM con. 0 008 Wha we have done so far We have esalshed ha we wan o fnd a lnear decson oundary whose margn s he larges We know how o measure he margn of a lnear decson oundary Tha s: he mnmum geomerc
Lecure SVM con. 0 008 Wha we have done so far We have esalshed ha we wan o fnd a lnear decson oundary whose margn s he larges We know how o measure he margn of a lnear decson oundary Tha s: he mnmum geomerc
Cubic Bezier Homotopy Function for Solving Exponential Equations
 Penerb Journal of Advanced Research n Compung and Applcaons ISSN (onlne: 46-97 Vol. 4, No.. Pages -8, 6 omoopy Funcon for Solvng Eponenal Equaons S. S. Raml *,,. Mohamad Nor,a, N. S. Saharzan,b and M.
Penerb Journal of Advanced Research n Compung and Applcaons ISSN (onlne: 46-97 Vol. 4, No.. Pages -8, 6 omoopy Funcon for Solvng Eponenal Equaons S. S. Raml *,,. Mohamad Nor,a, N. S. Saharzan,b and M.
e-journal Reliability: Theory& Applications No 2 (Vol.2) Vyacheslav Abramov
 June 7 e-ournal Relably: Theory& Applcaons No (Vol. CONFIDENCE INTERVALS ASSOCIATED WITH PERFORMANCE ANALYSIS OF SYMMETRIC LARGE CLOSED CLIENT/SERVER COMPUTER NETWORKS Absrac Vyacheslav Abramov School
June 7 e-ournal Relably: Theory& Applcaons No (Vol. CONFIDENCE INTERVALS ASSOCIATED WITH PERFORMANCE ANALYSIS OF SYMMETRIC LARGE CLOSED CLIENT/SERVER COMPUTER NETWORKS Absrac Vyacheslav Abramov School
Chapter 6: AC Circuits
 Chaper 6: AC Crcus Chaper 6: Oulne Phasors and he AC Seady Sae AC Crcus A sable, lnear crcu operang n he seady sae wh snusodal excaon (.e., snusodal seady sae. Complee response forced response naural response.
Chaper 6: AC Crcus Chaper 6: Oulne Phasors and he AC Seady Sae AC Crcus A sable, lnear crcu operang n he seady sae wh snusodal excaon (.e., snusodal seady sae. Complee response forced response naural response.
Higher Initial Value for Time Demand Analysis
 Inernaonal Journal of Appled Engneerng Research ISSN 097-62 Volume, Number 8 (208) pp. 809-8 Research Inda Publcaons. hp://www.rpublcaon.com Hgher Inal Value for Tme Demand Analyss Saleh Alrashed Imam
Inernaonal Journal of Appled Engneerng Research ISSN 097-62 Volume, Number 8 (208) pp. 809-8 Research Inda Publcaons. hp://www.rpublcaon.com Hgher Inal Value for Tme Demand Analyss Saleh Alrashed Imam
On computing differential transform of nonlinear non-autonomous functions and its applications
 On compung dfferenal ransform of nonlnear non-auonomous funcons and s applcaons Essam. R. El-Zahar, and Abdelhalm Ebad Deparmen of Mahemacs, Faculy of Scences and Humanes, Prnce Saam Bn Abdulazz Unversy,
On compung dfferenal ransform of nonlnear non-auonomous funcons and s applcaons Essam. R. El-Zahar, and Abdelhalm Ebad Deparmen of Mahemacs, Faculy of Scences and Humanes, Prnce Saam Bn Abdulazz Unversy,
HEAT CONDUCTION PROBLEM IN A TWO-LAYERED HOLLOW CYLINDER BY USING THE GREEN S FUNCTION METHOD
 Journal of Appled Mahemacs and Compuaonal Mechancs 3, (), 45-5 HEAT CONDUCTION PROBLEM IN A TWO-LAYERED HOLLOW CYLINDER BY USING THE GREEN S FUNCTION METHOD Sansław Kukla, Urszula Sedlecka Insue of Mahemacs,
Journal of Appled Mahemacs and Compuaonal Mechancs 3, (), 45-5 HEAT CONDUCTION PROBLEM IN A TWO-LAYERED HOLLOW CYLINDER BY USING THE GREEN S FUNCTION METHOD Sansław Kukla, Urszula Sedlecka Insue of Mahemacs,
Mechanics Physics 151
 Mechancs Physcs 5 Lecure 9 Hamlonan Equaons of Moon (Chaper 8) Wha We Dd Las Tme Consruced Hamlonan formalsm H ( q, p, ) = q p L( q, q, ) H p = q H q = p H = L Equvalen o Lagrangan formalsm Smpler, bu
Mechancs Physcs 5 Lecure 9 Hamlonan Equaons of Moon (Chaper 8) Wha We Dd Las Tme Consruced Hamlonan formalsm H ( q, p, ) = q p L( q, q, ) H p = q H q = p H = L Equvalen o Lagrangan formalsm Smpler, bu
Including the ordinary differential of distance with time as velocity makes a system of ordinary differential equations.
 Soluons o Ordnary Derenal Equaons An ordnary derenal equaon has only one ndependen varable. A sysem o ordnary derenal equaons consss o several derenal equaons each wh he same ndependen varable. An eample
Soluons o Ordnary Derenal Equaons An ordnary derenal equaon has only one ndependen varable. A sysem o ordnary derenal equaons consss o several derenal equaons each wh he same ndependen varable. An eample
APOC #232 Capacity Planning for Fault-Tolerant All-Optical Network
 APOC #232 Capacy Plannng for Faul-Toleran All-Opcal Nework Mchael Kwok-Shng Ho and Kwok-wa Cheung Deparmen of Informaon ngneerng The Chnese Unversy of Hong Kong Shan, N.T., Hong Kong SAR, Chna -mal: kwcheung@e.cuhk.edu.hk
APOC #232 Capacy Plannng for Faul-Toleran All-Opcal Nework Mchael Kwok-Shng Ho and Kwok-wa Cheung Deparmen of Informaon ngneerng The Chnese Unversy of Hong Kong Shan, N.T., Hong Kong SAR, Chna -mal: kwcheung@e.cuhk.edu.hk
Outline. Probabilistic Model Learning. Probabilistic Model Learning. Probabilistic Model for Time-series Data: Hidden Markov Model
 Probablsc Model for Tme-seres Daa: Hdden Markov Model Hrosh Mamsuka Bonformacs Cener Kyoo Unversy Oulne Three Problems for probablsc models n machne learnng. Compung lkelhood 2. Learnng 3. Parsng (predcon
Probablsc Model for Tme-seres Daa: Hdden Markov Model Hrosh Mamsuka Bonformacs Cener Kyoo Unversy Oulne Three Problems for probablsc models n machne learnng. Compung lkelhood 2. Learnng 3. Parsng (predcon
An introduction to Support Vector Machine
 An nroducon o Suppor Vecor Machne 報告者 : 黃立德 References: Smon Haykn, "Neural Neworks: a comprehensve foundaon, second edon, 999, Chaper 2,6 Nello Chrsann, John Shawe-Tayer, An Inroducon o Suppor Vecor Machnes,
An nroducon o Suppor Vecor Machne 報告者 : 黃立德 References: Smon Haykn, "Neural Neworks: a comprehensve foundaon, second edon, 999, Chaper 2,6 Nello Chrsann, John Shawe-Tayer, An Inroducon o Suppor Vecor Machnes,
Mechanics Physics 151
 Mechancs Physcs 5 Lecure 9 Hamlonan Equaons of Moon (Chaper 8) Wha We Dd Las Tme Consruced Hamlonan formalsm Hqp (,,) = qp Lqq (,,) H p = q H q = p H L = Equvalen o Lagrangan formalsm Smpler, bu wce as
Mechancs Physcs 5 Lecure 9 Hamlonan Equaons of Moon (Chaper 8) Wha We Dd Las Tme Consruced Hamlonan formalsm Hqp (,,) = qp Lqq (,,) H p = q H q = p H L = Equvalen o Lagrangan formalsm Smpler, bu wce as
The preemptive resource-constrained project scheduling problem subject to due dates and preemption penalties: An integer programming approach
 Journal of Indusral Engneerng 1 (008) 35-39 The preempve resource-consraned projec schedulng problem subjec o due daes and preempon penales An neger programmng approach B. Afshar Nadjaf Deparmen of Indusral
Journal of Indusral Engneerng 1 (008) 35-39 The preempve resource-consraned projec schedulng problem subjec o due daes and preempon penales An neger programmng approach B. Afshar Nadjaf Deparmen of Indusral
II. Light is a Ray (Geometrical Optics)
 II Lgh s a Ray (Geomercal Opcs) IIB Reflecon and Refracon Hero s Prncple of Leas Dsance Law of Reflecon Hero of Aleandra, who lved n he 2 nd cenury BC, posulaed he followng prncple: Prncple of Leas Dsance:
II Lgh s a Ray (Geomercal Opcs) IIB Reflecon and Refracon Hero s Prncple of Leas Dsance Law of Reflecon Hero of Aleandra, who lved n he 2 nd cenury BC, posulaed he followng prncple: Prncple of Leas Dsance:
Dual Approximate Dynamic Programming for Large Scale Hydro Valleys
 Dual Approxmae Dynamc Programmng for Large Scale Hydro Valleys Perre Carpener and Jean-Phlppe Chanceler 1 ENSTA ParsTech and ENPC ParsTech CMM Workshop, January 2016 1 Jon work wh J.-C. Alas, suppored
Dual Approxmae Dynamc Programmng for Large Scale Hydro Valleys Perre Carpener and Jean-Phlppe Chanceler 1 ENSTA ParsTech and ENPC ParsTech CMM Workshop, January 2016 1 Jon work wh J.-C. Alas, suppored
THE PREDICTION OF COMPETITIVE ENVIRONMENT IN BUSINESS
 THE PREICTION OF COMPETITIVE ENVIRONMENT IN BUSINESS INTROUCTION The wo dmensonal paral dfferenal equaons of second order can be used for he smulaon of compeve envronmen n busness The arcle presens he
THE PREICTION OF COMPETITIVE ENVIRONMENT IN BUSINESS INTROUCTION The wo dmensonal paral dfferenal equaons of second order can be used for he smulaon of compeve envronmen n busness The arcle presens he
Inter-Class Resource Sharing using Statistical Service Envelopes
 In Proceedngs of IEEE INFOCOM 99 Iner-Class Resource Sharng usng Sascal Servce Envelopes Jng-yu Qu and Edward W. Knghly Deparmen of Elecrcal and Compuer Engneerng Rce Unversy Absrac Neworks ha suppor mulple
In Proceedngs of IEEE INFOCOM 99 Iner-Class Resource Sharng usng Sascal Servce Envelopes Jng-yu Qu and Edward W. Knghly Deparmen of Elecrcal and Compuer Engneerng Rce Unversy Absrac Neworks ha suppor mulple
Clustering (Bishop ch 9)
 Cluserng (Bshop ch 9) Reference: Daa Mnng by Margare Dunham (a slde source) 1 Cluserng Cluserng s unsupervsed learnng, here are no class labels Wan o fnd groups of smlar nsances Ofen use a dsance measure
Cluserng (Bshop ch 9) Reference: Daa Mnng by Margare Dunham (a slde source) 1 Cluserng Cluserng s unsupervsed learnng, here are no class labels Wan o fnd groups of smlar nsances Ofen use a dsance measure
John Geweke a and Gianni Amisano b a Departments of Economics and Statistics, University of Iowa, USA b European Central Bank, Frankfurt, Germany
 Herarchcal Markov Normal Mxure models wh Applcaons o Fnancal Asse Reurns Appendx: Proofs of Theorems and Condonal Poseror Dsrbuons John Geweke a and Gann Amsano b a Deparmens of Economcs and Sascs, Unversy
Herarchcal Markov Normal Mxure models wh Applcaons o Fnancal Asse Reurns Appendx: Proofs of Theorems and Condonal Poseror Dsrbuons John Geweke a and Gann Amsano b a Deparmens of Economcs and Sascs, Unversy
Genetic Algorithm in Parameter Estimation of Nonlinear Dynamic Systems
 Genec Algorhm n Parameer Esmaon of Nonlnear Dynamc Sysems E. Paeraks manos@egnaa.ee.auh.gr V. Perds perds@vergna.eng.auh.gr Ah. ehagas kehagas@egnaa.ee.auh.gr hp://skron.conrol.ee.auh.gr/kehagas/ndex.hm
Genec Algorhm n Parameer Esmaon of Nonlnear Dynamc Sysems E. Paeraks manos@egnaa.ee.auh.gr V. Perds perds@vergna.eng.auh.gr Ah. ehagas kehagas@egnaa.ee.auh.gr hp://skron.conrol.ee.auh.gr/kehagas/ndex.hm
Fall 2010 Graduate Course on Dynamic Learning
 Fall 200 Graduae Course on Dynamc Learnng Chaper 4: Parcle Flers Sepember 27, 200 Byoung-Tak Zhang School of Compuer Scence and Engneerng & Cognve Scence and Bran Scence Programs Seoul aonal Unversy hp://b.snu.ac.kr/~bzhang/
Fall 200 Graduae Course on Dynamc Learnng Chaper 4: Parcle Flers Sepember 27, 200 Byoung-Tak Zhang School of Compuer Scence and Engneerng & Cognve Scence and Bran Scence Programs Seoul aonal Unversy hp://b.snu.ac.kr/~bzhang/
Bernoulli process with 282 ky periodicity is detected in the R-N reversals of the earth s magnetic field
 Submed o: Suden Essay Awards n Magnecs Bernoull process wh 8 ky perodcy s deeced n he R-N reversals of he earh s magnec feld Jozsef Gara Deparmen of Earh Scences Florda Inernaonal Unversy Unversy Park,
Submed o: Suden Essay Awards n Magnecs Bernoull process wh 8 ky perodcy s deeced n he R-N reversals of he earh s magnec feld Jozsef Gara Deparmen of Earh Scences Florda Inernaonal Unversy Unversy Park,
Approximate Analytic Solution of (2+1) - Dimensional Zakharov-Kuznetsov(Zk) Equations Using Homotopy
 Arcle Inernaonal Journal of Modern Mahemacal Scences, 4, (): - Inernaonal Journal of Modern Mahemacal Scences Journal homepage: www.modernscenfcpress.com/journals/jmms.aspx ISSN: 66-86X Florda, USA Approxmae
Arcle Inernaonal Journal of Modern Mahemacal Scences, 4, (): - Inernaonal Journal of Modern Mahemacal Scences Journal homepage: www.modernscenfcpress.com/journals/jmms.aspx ISSN: 66-86X Florda, USA Approxmae
First-order piecewise-linear dynamic circuits
 Frs-order pecewse-lnear dynamc crcus. Fndng he soluon We wll sudy rs-order dynamc crcus composed o a nonlnear resse one-por, ermnaed eher by a lnear capacor or a lnear nducor (see Fg.. Nonlnear resse one-por
Frs-order pecewse-lnear dynamc crcus. Fndng he soluon We wll sudy rs-order dynamc crcus composed o a nonlnear resse one-por, ermnaed eher by a lnear capacor or a lnear nducor (see Fg.. Nonlnear resse one-por
Dynamic Team Decision Theory
 Dynamc Team Decson Theory EECS 558 Proec Repor Shruvandana Sharma and Davd Shuman December, 005 I. Inroducon Whle he sochasc conrol problem feaures one decson maker acng over me, many complex conrolled
Dynamc Team Decson Theory EECS 558 Proec Repor Shruvandana Sharma and Davd Shuman December, 005 I. Inroducon Whle he sochasc conrol problem feaures one decson maker acng over me, many complex conrolled
Robust and Accurate Cancer Classification with Gene Expression Profiling
 Robus and Accurae Cancer Classfcaon wh Gene Expresson Proflng (Compuaonal ysems Bology, 2005) Auhor: Hafeng L, Keshu Zhang, ao Jang Oulne Background LDA (lnear dscrmnan analyss) and small sample sze problem
Robus and Accurae Cancer Classfcaon wh Gene Expresson Proflng (Compuaonal ysems Bology, 2005) Auhor: Hafeng L, Keshu Zhang, ao Jang Oulne Background LDA (lnear dscrmnan analyss) and small sample sze problem
CH.3. COMPATIBILITY EQUATIONS. Continuum Mechanics Course (MMC) - ETSECCPB - UPC
 CH.3. COMPATIBILITY EQUATIONS Connuum Mechancs Course (MMC) - ETSECCPB - UPC Overvew Compably Condons Compably Equaons of a Poenal Vecor Feld Compably Condons for Infnesmal Srans Inegraon of he Infnesmal
CH.3. COMPATIBILITY EQUATIONS Connuum Mechancs Course (MMC) - ETSECCPB - UPC Overvew Compably Condons Compably Equaons of a Poenal Vecor Feld Compably Condons for Infnesmal Srans Inegraon of he Infnesmal
Lecture VI Regression
 Lecure VI Regresson (Lnear Mehods for Regresson) Conens: Lnear Mehods for Regresson Leas Squares, Gauss Markov heorem Recursve Leas Squares Lecure VI: MLSC - Dr. Sehu Vjayakumar Lnear Regresson Model M
Lecure VI Regresson (Lnear Mehods for Regresson) Conens: Lnear Mehods for Regresson Leas Squares, Gauss Markov heorem Recursve Leas Squares Lecure VI: MLSC - Dr. Sehu Vjayakumar Lnear Regresson Model M
. The geometric multiplicity is dim[ker( λi. number of linearly independent eigenvectors associated with this eigenvalue.
 Lnear Algebra Lecure # Noes We connue wh he dscusson of egenvalues, egenvecors, and dagonalzably of marces We wan o know, n parcular wha condons wll assure ha a marx can be dagonalzed and wha he obsrucons
Lnear Algebra Lecure # Noes We connue wh he dscusson of egenvalues, egenvecors, and dagonalzably of marces We wan o know, n parcular wha condons wll assure ha a marx can be dagonalzed and wha he obsrucons
Networked Estimation with an Area-Triggered Transmission Method
 Sensors 2008, 8, 897-909 sensors ISSN 1424-8220 2008 by MDPI www.mdp.org/sensors Full Paper Neworked Esmaon wh an Area-Trggered Transmsson Mehod Vnh Hao Nguyen and Young Soo Suh * Deparmen of Elecrcal
Sensors 2008, 8, 897-909 sensors ISSN 1424-8220 2008 by MDPI www.mdp.org/sensors Full Paper Neworked Esmaon wh an Area-Trggered Transmsson Mehod Vnh Hao Nguyen and Young Soo Suh * Deparmen of Elecrcal
P R = P 0. The system is shown on the next figure:
 TPG460 Reservor Smulaon 08 page of INTRODUCTION TO RESERVOIR SIMULATION Analycal and numercal soluons of smple one-dmensonal, one-phase flow equaons As an nroducon o reservor smulaon, we wll revew he smples
TPG460 Reservor Smulaon 08 page of INTRODUCTION TO RESERVOIR SIMULATION Analycal and numercal soluons of smple one-dmensonal, one-phase flow equaons As an nroducon o reservor smulaon, we wll revew he smples
Math 128b Project. Jude Yuen
 Mah 8b Proec Jude Yuen . Inroducon Le { Z } be a sequence of observed ndependen vecor varables. If he elemens of Z have a on normal dsrbuon hen { Z } has a mean vecor Z and a varancecovarance marx z. Geomercally
Mah 8b Proec Jude Yuen . Inroducon Le { Z } be a sequence of observed ndependen vecor varables. If he elemens of Z have a on normal dsrbuon hen { Z } has a mean vecor Z and a varancecovarance marx z. Geomercally
Chapter Lagrangian Interpolation
 Chaper 5.4 agrangan Inerpolaon Afer readng hs chaper you should be able o:. dere agrangan mehod of nerpolaon. sole problems usng agrangan mehod of nerpolaon and. use agrangan nerpolans o fnd deraes and
Chaper 5.4 agrangan Inerpolaon Afer readng hs chaper you should be able o:. dere agrangan mehod of nerpolaon. sole problems usng agrangan mehod of nerpolaon and. use agrangan nerpolans o fnd deraes and
12d Model. Civil and Surveying Software. Drainage Analysis Module Detention/Retention Basins. Owen Thornton BE (Mech), 12d Model Programmer
 d Model Cvl and Surveyng Soware Dranage Analyss Module Deenon/Reenon Basns Owen Thornon BE (Mech), d Model Programmer owen.hornon@d.com 4 January 007 Revsed: 04 Aprl 007 9 February 008 (8Cp) Ths documen
d Model Cvl and Surveyng Soware Dranage Analyss Module Deenon/Reenon Basns Owen Thornon BE (Mech), d Model Programmer owen.hornon@d.com 4 January 007 Revsed: 04 Aprl 007 9 February 008 (8Cp) Ths documen
Attribute Reduction Algorithm Based on Discernibility Matrix with Algebraic Method GAO Jing1,a, Ma Hui1, Han Zhidong2,b
 Inernaonal Indusral Informacs and Compuer Engneerng Conference (IIICEC 05) Arbue educon Algorhm Based on Dscernbly Marx wh Algebrac Mehod GAO Jng,a, Ma Hu, Han Zhdong,b Informaon School, Capal Unversy
Inernaonal Indusral Informacs and Compuer Engneerng Conference (IIICEC 05) Arbue educon Algorhm Based on Dscernbly Marx wh Algebrac Mehod GAO Jng,a, Ma Hu, Han Zhdong,b Informaon School, Capal Unversy
Ordinary Differential Equations in Neuroscience with Matlab examples. Aim 1- Gain understanding of how to set up and solve ODE s
 Ordnary Dfferenal Equaons n Neuroscence wh Malab eamples. Am - Gan undersandng of how o se up and solve ODE s Am Undersand how o se up an solve a smple eample of he Hebb rule n D Our goal a end of class
Ordnary Dfferenal Equaons n Neuroscence wh Malab eamples. Am - Gan undersandng of how o se up and solve ODE s Am Undersand how o se up an solve a smple eample of he Hebb rule n D Our goal a end of class
A Tour of Modeling Techniques
 A Tour of Modelng Technques John Hooker Carnege Mellon Unversy EWO Semnar February 8 Slde Oulne Med neger lnear (MILP) modelng Dsuncve modelng Knapsack modelng Consran programmng models Inegraed Models
A Tour of Modelng Technques John Hooker Carnege Mellon Unversy EWO Semnar February 8 Slde Oulne Med neger lnear (MILP) modelng Dsuncve modelng Knapsack modelng Consran programmng models Inegraed Models
Appendix H: Rarefaction and extrapolation of Hill numbers for incidence data
 Anne Chao Ncholas J Goell C seh lzabeh L ander K Ma Rober K Colwell and Aaron M llson 03 Rarefacon and erapolaon wh ll numbers: a framewor for samplng and esmaon n speces dversy sudes cology Monographs
Anne Chao Ncholas J Goell C seh lzabeh L ander K Ma Rober K Colwell and Aaron M llson 03 Rarefacon and erapolaon wh ll numbers: a framewor for samplng and esmaon n speces dversy sudes cology Monographs
2.1 Constitutive Theory
 Secon.. Consuve Theory.. Consuve Equaons Governng Equaons The equaons governng he behavour of maerals are (n he spaal form) dρ v & ρ + ρdv v = + ρ = Conservaon of Mass (..a) d x σ j dv dvσ + b = ρ v& +
Secon.. Consuve Theory.. Consuve Equaons Governng Equaons The equaons governng he behavour of maerals are (n he spaal form) dρ v & ρ + ρdv v = + ρ = Conservaon of Mass (..a) d x σ j dv dvσ + b = ρ v& +
Advanced Macroeconomics II: Exchange economy
 Advanced Macroeconomcs II: Exchange economy Krzyszof Makarsk 1 Smple deermnsc dynamc model. 1.1 Inroducon Inroducon Smple deermnsc dynamc model. Defnons of equlbrum: Arrow-Debreu Sequenal Recursve Equvalence
Advanced Macroeconomcs II: Exchange economy Krzyszof Makarsk 1 Smple deermnsc dynamc model. 1.1 Inroducon Inroducon Smple deermnsc dynamc model. Defnons of equlbrum: Arrow-Debreu Sequenal Recursve Equvalence
Multi-priority Online Scheduling with Cancellations
 Submed o Operaons Research manuscrp (Please, provde he manuscrp number!) Auhors are encouraged o subm new papers o INFORMS journals by means of a syle fle emplae, whch ncludes he journal le. However, use
Submed o Operaons Research manuscrp (Please, provde he manuscrp number!) Auhors are encouraged o subm new papers o INFORMS journals by means of a syle fle emplae, whch ncludes he journal le. However, use
Should Exact Index Numbers have Standard Errors? Theory and Application to Asian Growth
 Should Exac Index umbers have Sandard Errors? Theory and Applcaon o Asan Growh Rober C. Feensra Marshall B. Rensdorf ovember 003 Proof of Proposon APPEDIX () Frs, we wll derve he convenonal Sao-Vara prce
Should Exac Index umbers have Sandard Errors? Theory and Applcaon o Asan Growh Rober C. Feensra Marshall B. Rensdorf ovember 003 Proof of Proposon APPEDIX () Frs, we wll derve he convenonal Sao-Vara prce
Tools for Analysis of Accelerated Life and Degradation Test Data
 Acceleraed Sress Tesng and Relably Tools for Analyss of Acceleraed Lfe and Degradaon Tes Daa Presened by: Reuel Smh Unversy of Maryland College Park smhrc@umd.edu Sepember-5-6 Sepember 28-30 206, Pensacola
Acceleraed Sress Tesng and Relably Tools for Analyss of Acceleraed Lfe and Degradaon Tes Daa Presened by: Reuel Smh Unversy of Maryland College Park smhrc@umd.edu Sepember-5-6 Sepember 28-30 206, Pensacola
Polymerization Technology Laboratory Course
 Prakkum Polymer Scence/Polymersaonsechnk Versuch Resdence Tme Dsrbuon Polymerzaon Technology Laboraory Course Resdence Tme Dsrbuon of Chemcal Reacors If molecules or elemens of a flud are akng dfferen
Prakkum Polymer Scence/Polymersaonsechnk Versuch Resdence Tme Dsrbuon Polymerzaon Technology Laboraory Course Resdence Tme Dsrbuon of Chemcal Reacors If molecules or elemens of a flud are akng dfferen
Appendix to Online Clustering with Experts
 A Appendx o Onlne Cluserng wh Expers Furher dscusson of expermens. Here we furher dscuss expermenal resuls repored n he paper. Ineresngly, we observe ha OCE (and n parcular Learn- ) racks he bes exper
A Appendx o Onlne Cluserng wh Expers Furher dscusson of expermens. Here we furher dscuss expermenal resuls repored n he paper. Ineresngly, we observe ha OCE (and n parcular Learn- ) racks he bes exper
10. A.C CIRCUITS. Theoretically current grows to maximum value after infinite time. But practically it grows to maximum after 5τ. Decay of current :
 . A. IUITS Synopss : GOWTH OF UNT IN IUIT : d. When swch S s closed a =; = d. A me, curren = e 3. The consan / has dmensons of me and s called he nducve me consan ( τ ) of he crcu. 4. = τ; =.63, n one
. A. IUITS Synopss : GOWTH OF UNT IN IUIT : d. When swch S s closed a =; = d. A me, curren = e 3. The consan / has dmensons of me and s called he nducve me consan ( τ ) of he crcu. 4. = τ; =.63, n one
Sampling Procedure of the Sum of two Binary Markov Process Realizations
 Samplng Procedure of he Sum of wo Bnary Markov Process Realzaons YURY GORITSKIY Dep. of Mahemacal Modelng of Moscow Power Insue (Techncal Unversy), Moscow, RUSSIA, E-mal: gorsky@yandex.ru VLADIMIR KAZAKOV
Samplng Procedure of he Sum of wo Bnary Markov Process Realzaons YURY GORITSKIY Dep. of Mahemacal Modelng of Moscow Power Insue (Techncal Unversy), Moscow, RUSSIA, E-mal: gorsky@yandex.ru VLADIMIR KAZAKOV
CHAPTER 10: LINEAR DISCRIMINATION
 CHAPER : LINEAR DISCRIMINAION Dscrmnan-based Classfcaon 3 In classfcaon h K classes (C,C,, C k ) We defned dscrmnan funcon g j (), j=,,,k hen gven an es eample, e chose (predced) s class label as C f g
CHAPER : LINEAR DISCRIMINAION Dscrmnan-based Classfcaon 3 In classfcaon h K classes (C,C,, C k ) We defned dscrmnan funcon g j (), j=,,,k hen gven an es eample, e chose (predced) s class label as C f g
Mechanics Physics 151
 Mechancs Physcs 5 Lecure 0 Canoncal Transformaons (Chaper 9) Wha We Dd Las Tme Hamlon s Prncple n he Hamlonan formalsm Dervaon was smple δi δ Addonal end-pon consrans pq H( q, p, ) d 0 δ q ( ) δq ( ) δ
Mechancs Physcs 5 Lecure 0 Canoncal Transformaons (Chaper 9) Wha We Dd Las Tme Hamlon s Prncple n he Hamlonan formalsm Dervaon was smple δi δ Addonal end-pon consrans pq H( q, p, ) d 0 δ q ( ) δq ( ) δ
Epistemic Game Theory: Online Appendix
 Epsemc Game Theory: Onlne Appendx Edde Dekel Lucano Pomao Marcano Snscalch July 18, 2014 Prelmnares Fx a fne ype srucure T I, S, T, β I and a probably µ S T. Le T µ I, S, T µ, βµ I be a ype srucure ha
Epsemc Game Theory: Onlne Appendx Edde Dekel Lucano Pomao Marcano Snscalch July 18, 2014 Prelmnares Fx a fne ype srucure T I, S, T, β I and a probably µ S T. Le T µ I, S, T µ, βµ I be a ype srucure ha
Comparison of Differences between Power Means 1
 In. Journal of Mah. Analyss, Vol. 7, 203, no., 5-55 Comparson of Dfferences beween Power Means Chang-An Tan, Guanghua Sh and Fe Zuo College of Mahemacs and Informaon Scence Henan Normal Unversy, 453007,
In. Journal of Mah. Analyss, Vol. 7, 203, no., 5-55 Comparson of Dfferences beween Power Means Chang-An Tan, Guanghua Sh and Fe Zuo College of Mahemacs and Informaon Scence Henan Normal Unversy, 453007,
A Deterministic Algorithm for Summarizing Asynchronous Streams over a Sliding Window
 A Deermnsc Algorhm for Summarzng Asynchronous Sreams over a Sldng ndow Cosas Busch Rensselaer Polyechnc Insue Srkana Trhapura Iowa Sae Unversy Oulne of Talk Inroducon Algorhm Analyss Tme C Daa sream: 3
A Deermnsc Algorhm for Summarzng Asynchronous Sreams over a Sldng ndow Cosas Busch Rensselaer Polyechnc Insue Srkana Trhapura Iowa Sae Unversy Oulne of Talk Inroducon Algorhm Analyss Tme C Daa sream: 3
Filtrage particulaire et suivi multi-pistes Carine Hue Jean-Pierre Le Cadre and Patrick Pérez
 Chaînes de Markov cachées e flrage parculare 2-22 anver 2002 Flrage parculare e suv mul-pses Carne Hue Jean-Perre Le Cadre and Parck Pérez Conex Applcaons: Sgnal processng: arge rackng bearngs-onl rackng
Chaînes de Markov cachées e flrage parculare 2-22 anver 2002 Flrage parculare e suv mul-pses Carne Hue Jean-Perre Le Cadre and Parck Pérez Conex Applcaons: Sgnal processng: arge rackng bearngs-onl rackng
SOME NOISELESS CODING THEOREMS OF INACCURACY MEASURE OF ORDER α AND TYPE β
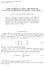 SARAJEVO JOURNAL OF MATHEMATICS Vol.3 (15) (2007), 137 143 SOME NOISELESS CODING THEOREMS OF INACCURACY MEASURE OF ORDER α AND TYPE β M. A. K. BAIG AND RAYEES AHMAD DAR Absrac. In hs paper, we propose
SARAJEVO JOURNAL OF MATHEMATICS Vol.3 (15) (2007), 137 143 SOME NOISELESS CODING THEOREMS OF INACCURACY MEASURE OF ORDER α AND TYPE β M. A. K. BAIG AND RAYEES AHMAD DAR Absrac. In hs paper, we propose
. The geometric multiplicity is dim[ker( λi. A )], i.e. the number of linearly independent eigenvectors associated with this eigenvalue.
![. The geometric multiplicity is dim[ker( λi. A )], i.e. the number of linearly independent eigenvectors associated with this eigenvalue. . The geometric multiplicity is dim[ker( λi. A )], i.e. the number of linearly independent eigenvectors associated with this eigenvalue.](/thumbs/78/77822798.jpg) Mah E-b Lecure #0 Noes We connue wh he dscusson of egenvalues, egenvecors, and dagonalzably of marces We wan o know, n parcular wha condons wll assure ha a marx can be dagonalzed and wha he obsrucons are
Mah E-b Lecure #0 Noes We connue wh he dscusson of egenvalues, egenvecors, and dagonalzably of marces We wan o know, n parcular wha condons wll assure ha a marx can be dagonalzed and wha he obsrucons are
FI 3103 Quantum Physics
 /9/4 FI 33 Quanum Physcs Aleander A. Iskandar Physcs of Magnesm and Phooncs Research Grou Insu Teknolog Bandung Basc Conces n Quanum Physcs Probably and Eecaon Value Hesenberg Uncerany Prncle Wave Funcon
/9/4 FI 33 Quanum Physcs Aleander A. Iskandar Physcs of Magnesm and Phooncs Research Grou Insu Teknolog Bandung Basc Conces n Quanum Physcs Probably and Eecaon Value Hesenberg Uncerany Prncle Wave Funcon
The Dynamic Programming Models for Inventory Control System with Time-varying Demand
 The Dynamc Programmng Models for Invenory Conrol Sysem wh Tme-varyng Demand Truong Hong Trnh (Correspondng auhor) The Unversy of Danang, Unversy of Economcs, Venam Tel: 84-236-352-5459 E-mal: rnh.h@due.edu.vn
The Dynamc Programmng Models for Invenory Conrol Sysem wh Tme-varyng Demand Truong Hong Trnh (Correspondng auhor) The Unversy of Danang, Unversy of Economcs, Venam Tel: 84-236-352-5459 E-mal: rnh.h@due.edu.vn
Testing a new idea to solve the P = NP problem with mathematical induction
 Tesng a new dea o solve he P = NP problem wh mahemacal nducon Bacground P and NP are wo classes (ses) of languages n Compuer Scence An open problem s wheher P = NP Ths paper ess a new dea o compare he
Tesng a new dea o solve he P = NP problem wh mahemacal nducon Bacground P and NP are wo classes (ses) of languages n Compuer Scence An open problem s wheher P = NP Ths paper ess a new dea o compare he
