Timing Attacks on Cognitive Authentication Schemes
|
|
|
- Doreen Flynn
- 5 years ago
- Views:
Transcription
1 Timing Attacks on Cognitive Authentication Schemes Mario Čagaj, Toni Perković, Member, IEEE, Marin Bugarić Department of Eectrica Engineering, FESB, University of Spit, Croatia {mcagaj, toperkov, Abstract Cassica password/pin-based authentication methods have proven to be vunerabe to a broad range of observation attacks such as key-ogging, video-recording or shouder surfing attacks. In order to mitigate these attacks, a number of soutions have been proposed, most of them being cognitive authentication schemes chaenge-response protocos that require users to perform some kind of cognitive operations. In this paper we show successfu passive side-channe timing attacks on two cognitive authentication schemes, a we-known Hopper-Bum HB protoco and a US patent Mod method, previousy beieved to be secure against observation attacks. As we show, the main security weakness of these methods comes from detectabe variations in the user s cognitive oad that resuts from cognitive operations during the authentication procedure. We carried out theoretica anaysis of both Mod and HB methods, as we as an experimenta user study of Mod method with 58 participants to vaidate the resuts of our timing attacks. We aso propose security enhancements of these schemes aimed to mitigate the timing side-channe attacks. The proposed enhancements show the existence of a strong tradeoff between security and usabiity, indicating that the security of cognitive authentication schemes comes at a non-negigibe usabiity cost e.g., increased overa ogin time. For this reason, the designers of new cognitive authentication schemes shoud not ignore possibe threats induced by side-channe timing attacks. Keywords Authentication, cognitive authentication schemes, human factors, observation attack, side-channe timing attack I. INTRODUCTION Internet services such as socia networks, e-banking, emai, coud services, bogs, a require some form of user authentication. Despite the avaiabiity of advanced authentication technoogies such as smart cards, biometrics or USB tokens [], passwords and PINs are sti the most prevaent form of user authentication. This is primariy due to simpicity and ow cost of their creation, maintenance and revocation. At the same time, traditiona password/pin-based authentication systems are vunerabe to different forms of observation attacks, ranging from a simpe shouder-surfing [2] to a more advanced keyogging and camera recording attacks [3]. A number of soutions have been proposed to strengthen password/pin-based soutions against such observation attacks. Most soutions use chaenge-response protocos where users are required to perform some form of a cognitive task e.g., sma additions, recognition, visua reca [4], [5], [6], [7], prior to being granted an access. More specificay, in each authentication session, the user gives back the response r i to a number of chaenges c i based on the knowedge of the shared key s i ; the user performs a cognitive operation fc i, s i to cacuate the response r i. Whie mitigating certain observations attacks, these cognitive authentication schemes inevitaby incur a higher cognitive oad on a user due to cognitive operations compared to traditiona password-based authentication. For this reason, besides the protoco security, the designers of such protocos put a ot of attention on the usabiity e.g., try to minimize the overa user s oad. However, subte variations in the difficuty of cognitive operations whie cacuating the response r i = fc i, s i coud ead to the asymmetry in the user s cognitive oad. Athough the designers often negect these subte variations, they coud be used for cognitive-asymmetry side-channe attacks. As we show in this paper, cognitive asymmetry can be expoited in a passive side-channe timing attack to partiay or competey recover secret PINs/passwords. Pease note that this is different from the timing attacks that expoit asymmetry of physica user interfaces such as keyboards [8] or asymmetry of virtua interfaces i.e., asymmetric graphica ayouts, as found in Undercover [5], [9]. To demonstrate cognitive-asymmetry side-channes, in this paper we anayze the security of two cognitive authentication schemes that were designed to mitigate shouder-surfing attacks. More precisey, we present successfu side-channe timing attacks on two authentication schemes: a Mod [] scheme and a we-known Hopper-Bum HB protoco [2]. Our attacks expoit detectabe variations in the user s cognitive oad during the course of the authentication protoco variations in user s reaction times when responding to different chaenges. For the Mod authentication scheme, that is based on a secret PIN and moduo arithmetic, we show that it is possibe to reduce the entropy of each PIN digit by approximatey 6%. We vaidated the resuts of timing attack through a user study invoving 58 participants. In the case of the Hopper-Bum protoco, the main security resut in [2] states that the protoco is secure against computationay bounded eavesdropping adversaries. As we wi show, this proof hods in the setting where the adversary does not obtain the timing information. Based on the assumptions of our theoretica mode, a passive attacker can competey recover the user s secret after observing a reasonaby sma number of authentication rounds. The Mod scheme, originay proposed in a US patent [], has been suggested for use severa times in the iterature due to its simpicity and fast ogin times around seconds [], [6].
2 2 Re. freq. Re. freq Digit Response digit Digit Response digit Fig.. Reative frequency with which a given response digit appears within = 4 fastest response digits, for PIN digits: 2, 4, 6 and 8. HB and Mod schemes are representatives of authentication paradigms that require users to perform some form of a cognitive task, such as addition, visua reca and counting, mutipication, moduo operations etc. However, there is a pethora of protocos that have simiarities with HB and Mod schemes, such as Foxtai [3], Asghar, Pieprzyk and Wang APW [4] protocos and virtua password scheme [5], where users are aso required to perform a cognitive operation fc i, s i to compute the response r i. We beieve that these schemes are aso vunerabe to cognitive-asymmetry side channes. Moreover, we stress here the HB protoco has been extended for use in RFID systems [6] and that it shoud be expored whether our attack is appicabe in this context too under the assumptions of our authentication mode. We further show that eiminating the timing side channes in Mod and HB schemes necessariy comes at a non-negigibe usabiity cost i.e., onger authentication times and/or onger PINs/passwords. This is an important resut since a usabiity score of a given authentication scheme is correated with its authentication times and the PIN/password size. Therefore, when designing and evauating a new scheme, designers cannot negect cognitive-asymmetry side-channe timing attacks. II. THE ATTACKER MODEL In this paper we consider a passive attacker who eavesdrops on a pubic communication between the user and the end system pubic chaenges and/or responses. The attacker aso has the capabiity of recording the user s reaction time during the course of the ogin procedure by, for exampe, using keyogging maware, a simpe camera or an acceerator within a smartphone as a high bandwidth side channe [7]. III. TIMING ATTACK ON MOD METHOD Mod scheme impements a one-time pad paradigm. To enter the ith digit d i of their PIN, the users receive a chaenge c i one digit ong seected uniformy at random from the set,..., 9 via a protected channe e.g., earphones, add two digits moduo r i = c i + d i mod and enter back the outcome r i via the pubic channe e.g., a numerica pad. The main intuition that ead us to investigate cognitiveasymmetry side channes in Mod scheme is simpe: during the authentication process, a user wi take ess time to respond to a chaenge if the chaenge digit c i is, or 2. The Mod scheme was originay proposed in a US patent []. The security of Mod scheme against the timing attack recenty anayzed in ASIACCS 3 paper [8] named NumPad scheme does not revea weakness to the cognitiveasymmetry side channes. However, our preiminary study of the Mod scheme in [6] ed to the discovery of variations in the user s cognitive oad response times whie responding to different chaenges, which aows the attacker to reduce the PIN space. The main intuition why NumPad scheme proposed in [8] does not find any weaknesses to side-channe timing attack is because NumPad timing attack anaysis is based on observation of imited number of features, i.e. the average response times per PIN digit that have arge variances induce high noise. To eiminate the effect of noise in our study we focus on observing ony the fastest ogin times. This aows us to use mutipe features and create a set of unique patterns for every PIN digit. In this paper we present an extensive anaysis of Mod scheme against side-channe timing attacks verified via user studies in our own impementation of Mod. Pease note that chaenges in Mod are broadcast over a secret channe, therefore, in our attacker mode we assume that the user sees the next chaenge immediatey after he responds to the current one. In this way, the adversary is abe to infer when the user started working on each new chaenge and thus obtain the timing information. We impemented the Mod scheme as a web appication and coected test statistics from 58 users, where each user was asked to ogin at east 3 times. An overa ogin success rate out of 249 ogin attempts was about 85%, whie the average ogin time was.39 seconds. It is known that arithmetic operations with sma-vaued numbers additions with chaenges from the set {,, 2} score faster response times [9], [2], [2], [22]. These observations can be seen in Fig., where we pot the reative frequencies for PIN digits 2, 4, 6 and 8 that is generated in such a way that for the fixed PIN digit d i we count how many users with PIN digits d i have a given response digit within their fastest response digits in our case = 4. This cognitive asymmetry variations in the user cognitive oad in Mod scheme inspired us to run a side-channe timing attack. On the high eve, the timing attack is based on the observation of two attributes: a vector r = r, r 2,..., r representing the fastest response digits, and a scaar t r representing the fastest response time, both for the unknown/sought cass PIN digit. Our decision to use fastest response digits and response times as a fiter for our timing attack was based on the intuition that users cannot provide answers faster than their cognitive capabiities aow them as opposite to sow answers. The timing attack presents a cassification probem in which the observed data is assigned to one of the predefined casses PIN digits. These decisions are based on two cassifiers and the approach based on the naive Bayesian cassifier. A. Cassification-based Timing Attack on Mod In our cassification we used a continuous output from each cassifier that was normaized to the interva [ ] posterior probabiity. These vaues for each PIN digit were combined using an agebraic combination rue [23]. We used a sum
3 3 Re.cum.freq Re.cum.freq Re.cum.freq Re.cum.freq Re.cum.freq Digit 4 Resp. digit Resp. digit Resp. digit 3 Resp. digit Resp. digit 5 Resp. digit Resp. digit 7 Resp. digit Resp. digit 9 Resp. digit Fig. 2. Reative cumuative frequency with which a given response digit appears within fastest response digits {,..., }, for PIN digit 4. decision rue that combines posterior probabiity from each cassifier, because it achieves the best cassification resuts. We first describe the impementation of each cassifier. Agorithm Estimating the cass conditiona probabiity P r m d i from the training set Initiaize: C i j =, r i j, d i, 2 Repeat d i : if r i j in fastest, then C i j,m = Ci j,m +, m {,..., }, 3 Cacuate: P r m d i C i j, /Ci j, Cassifier Trained on Fastest Response Digits: The first cassifier expoits the cognitive asymmetry of easy additions with sma-vaued chaenges e.g.,, and 2 that achieve fast response times. To earn these distributions of response digits rj i ri j {,..., 9} for every cass vaue PIN digit d i, the cassifier is first trained on the ogin resuts from 57 out of 58 users eave-one-out crossvaidation technique. For every PIN digit d i d i {,..., 9} we repeat the foowing steps, as described by Agorithm : for every response digit rj i rj i {,..., 9} create a vector Ci j of counters C i j =. After that, for a users from the training set whose PIN comprises digit d i, and for a such digits d i for the given user repeat the foowing steps: first, rank the response digits rj i for the given PIN digit d i according to the fastest response times. If the response digit rj i fas within fastest response digits, increment the counters Cj, i to Ci j, by one. As a resut we obtain, for every PIN digit d i, the cumuative frequency Cj, i that indicates the number of times a given response digit rj i fas within fastest response digits. Dividing Ci j, by Cj, i we get the corresponding reative cumuative frequency. Fig. 2 shows the reative cumuative frequency of a response digits for PIN digit 4. Note that the response digits 4, 5 and 6 are characterized by higher reative cumuative frequencies at sma vaues of. This indicates that those response digits generay have faster response times for the corresponding PIN digit [24] easy additions with, and 2. PIN digit Response time s Fig. 3. The cacuation resuts indicate that additions with sma singe integers achieve fastest response times PIN digits, and 2. Our first cassifier uses the resuting frequency distributions to perform the cassification task of the feature vector r = r, r 2,..., r of fastest response digits for the given PIN digit position. Given the feature vector r, our cassifier first estimates the posterior probabiity P d i r for a PIN digits d i and then seects into the fina candidate set n digits d i that have the highest posterior probabiities. We use the cassica naive Bayes technique/assumption where we assume that conditioned on a cass d i, the feature vector eements r, r 2,..., r are mutuay independent. Then we can express P d i r as foows: m= P d i r = P r m d i P d i = m= P r m d P d, with P d i = / for a the digits d i. As described in Agorithm, the cass conditiona probabiities P r m d i are estimated from the reative cumuative frequency distributions obtained in the training phase. 2 Cassification Based on Fastest Response Times: In our second Bayesian cassifier we use ony the fastest response time t r among a the response digits. The second cassifier expoits the cognitive asymmetry in Mod method by using the phenomenon caed probem-size effect in simpe arithmetic operations [22]. Basicay, direct menta mapping technique that is characteristic for sma-vaued additions e.g., is faster than the procedura techniques of addition that use arge-vaued additions e.g., [9]. The resuts of fastest response times for a PIN digits in Fig. 3 show that additions with sma one-digit integers achieve faster response times. Note that users with PIN digit on average achieve faster response times the response equas to the chaenge. In Fig. 3 we can see that mutipe casses PIN digits have overapping distributions of response times, and accordingy, the observed fastest response time t r can be attributed to mutipe basic casses PIN digits. Simiary to [25], instead of assigning an observed feature t r to a specific cass d i, it may be assigned to the meta-cass C j that comprises of mutipe basic casses. Our cassifier uses two meta-casses C f and C s, where C f is comprised of fast response digits {,, 2, 7, 9}, whie C s is comprised of sow response digits {3, 4, 5, 6, 8}. We first cacuate the posterior probabiities P C j t r for
4 4.95 First cassifier Combining cassifier.9 Sum combination rue.9 Sum combination rue meta users.8.8 Success rate.9.85 Success rate Success rate Rand. guess =4.2. Rand. guess = fastest response digits Candidate set size n Candidate set size n a b c Fig. 4. a Combining cassifier achieves better resuts than the first cassifier. b Effectiveness of the sum combination rue that combines the resuts of two cassifiers. Dotted ine presents guessing attack. c Effectiveness of the sum combination rue that aggregates the resuts of m=3 users into a singe meta-user. TABLE I. EFFECTIVENESS OF THE SECOND CLASSIFIER TRAINED ON THE FASTEST RESPONSE TIMES. PIN digit Meta-cass C f C f C f C s C s C s C s C f C s C f Probabiity of correct assignment j {f, s} using Bayes theorem, i.e.: P C j t r = P t r C j P C j, 2 P t r where P C f = P C s = /2 for the prior probabiities. Concerning the cass-conditiona probabiities P t r C j we use Fexibe Bayes earning agorithm for estimating continuous distributions in Bayesian cassifier [26] where conditiona probabiities are estimated using the kerne estimation with Gaussian kerne. By assuming that every digit d i within the meta-cass C j is uniformy distributed [27], the posterior probabiities P d i t r for every cass within the subset are obtained using the foowing rue: if d i C j then P d i t r = P C j t r. 3 C j 3 Cassifier Combination Using a Sum Decision Rue: We use the sum decision rue to combine the output posterior probabiities from each cassifier, because it achieves the best cassification resuts compared to min/max/product rue [23]. The posterior probabiities can be combined as foows [23]: P d i r, t r const. + P d i r + P d i t r. 4 As before, using the resuting posterior probabiities P d i r, t r we can rank the casses d i and seect the ones with the highest rank into the fina candidate set. 4 Effectiveness of the Cassifiers: We can measure the effectiveness of a given cassifier by estimating the probabiity that the unknown PIN digit wi fa into the output candidate set and by comparing it against a random guessing strategy. Pease note that a random guessing strategy wi be successfu with probabiity at most n/ for a candidate set of size n. For = 4 and n = 4 the first cassifier achieves 65% better resuts than pure random guessing. Moreover, for n = 7 the cassifier hods a sought PIN digit with probabiity.88 Fig. 4a. The effectiveness of the second cassifier is summarized in Tabe I. It shows the probabiity that the PIN digit d i wi be assigned to the correct meta-cass. As expected, digits with the fastest response times within the meta-cass C f e.g.,, in Fig. 3 and digits with the sowest response times within C s e.g., 5, 6 and 8 in Fig. 3 have higher probabiity to be cassified to the correct meta-cass. After combining the resuts from each cassifier using the sum combination rue, we can see a sighty better performance in the cassification correctness as shown in Fig. 4b. It shows the probabiity that a tested unknown digit d i wi fa in a candidate set of size n. For exampe, for the same parameters as before = 4 and n = 4 our combining cassifier performs 72% better than random guessing. Generay, the combining cassifier performs better than the first cassifier for amost a candidate set sizes n; in Fig. 4a we compare the combining against the first cassifier for a candidate set size of n = 7. We next estimate the amount of information about an unknown PIN that the attacker can extract using our combining cassifier. Let us denote with n a candidate set size that hods unknown PIN digit with the probabiity above 9%. Then, og 2 /n is the approximate number of extracted bits per PIN digit. As shown in Fig. 4a the combining cassifier for a candidate set of the size n = 7 and = 4 fastest response digits wi comprise the sought unknown PIN digit with probabiity sighty over 9%. Therefore, the attacker can extract approximatey og 2 /7.5 bits per PIN digit. Accordingy, the attacker can extract approximatey 2 bits of information about an unknown 4 digit PIN, i.e., the PIN entropy is reduced from 4 og bits to.3 bits. By observing more ogin sessions but sti a poynomia number we expect even more significant reduction in the PIN entropy. To prove our assumption we aggregated the resuts from m = 3 randomy seected users who had the same PIN digit and created a metauser with 9 successfu ogins on average. Using the same cassification technique, we were abe to reduce a candidate set size to n = 6 digits, as shown in
5 5 Fig. 4c. Therefore, the attacker can extract approximatey.73 bits per PIN digit by observing more ogin sessions. We assumed that the maximum amount of information the attacker can earn about the PIN digit was based on the resuts obtained by appying our combining cassifier. We wi next estimate the conditiona entropy for the given response digit r i and response time t r : HD R = r i, T r = t r = j= P d j r i, t r og 2 P d j r i, t r. 5 The probabiity P d j r i, t r can be cacuated as foows: P d j r i, t r = pt r d j,r i = pt r d,r i. 6 We estimate the probabiity pt r d j, r i using the data coected in our tests, by assuming that they have Gaussian distribution. To estimate the expected conditiona entropy HD R, t r over a possibe response digits R we do the foowing: HD R, T r = i= 3.5 j= t r=.8 pt r r i, d j HD r i, t r dt r. 7 By evauating the Eq. 7, we finay obtain HD R, T r 2 bits; i.e. the attacker can extract approximatey 2 bits of information about the unknown PIN digit. IV. TIMING ATTACK ON THE HOPPER-BLUM HB AUTHENTICATION PROTOCOL Hopper-Bum HB protoco became popuar as one of the first human authentication protocos that was provaby secure against passive observation attacks [2]. The HB protoco impements k-out-of-n paradigm, where the user U and the end system S share a secret binary vector s {, } n. The Hamming weight of the vector s is k, that is, the secret vector s has k non-zero vaued components. The HB authentication proceeds as foows: Agorithm 2 The Hopper-Bum protoco [2] S sets t := 2 Repeat m times: a S generates a random chaenge c t U {, } n. b With prob. η, U responds with r t := c t s, otherwise U responds with r t := c t s. c if r t = c t s, S increments t. 3 if t > ηm, S accepts U. During a singe chaenge-response round t, the user has to compute the binary inner product c t s. To accompish this, the user recas the positions of k non-zero vaued components of s and counts the number of ones appearing in the binary chaenge c t at those k positions; i.e., he/she cacuates a Hamming weight s c t. The user then responds with the parity bit r t of s c t, under the restriction that once in a whie i.e., with the fixed probabiity η the user intentionay responds with an incorrect parity bit. The main intuition that ead us to investigate cognitive-asymmetry side channes in the HB protoco is the foowing: a user wi take more time to respond to a chaenge when he needs to add more nonzero bits together to compute the response. Let us denote the Hamming weight of s c t as the counting oad k. The counting oad thus represents the number of non-zero vaued components appearing at same indexes in both the secret vector s and the chaenge c t. This design choice in the HB protoco inevitaby eads to variations in user response times at each chaenge-response round t. More specificay, the user response atency wi be highy correated with the counting oad, thus potentiay eaking information about the secret vector s through the timing channe. In order to understand the extent of this vunerabiity, we designed a probabiistic agorithm through which the attacker can graduay earn the user s secret s, after observing a poynomia number of rounds. Before giving detais of our attacking agorithm we first present a generative probabiistic mode for a human running the HB protoco. A. Modeing a Human Running the HB Protoco In this section we describe a genera and reaistic mode of a user running the HB protoco on which we buid our attack. Cognitive-asymmetry side channe in our mode is based on the fact that users enter their responses immediatey after cacuating them and the fact that they can not execute menta operations faster then their abiities aow them. This, for different chaenges c t, resuts in different user s response times RT that can be observed by a passive attacker. We first present a probabiistic mode for the user s response time RT associated with the fixed counting oad. For this purpose, we extend the mode first described in the paper by Yan et a. []: RT = δ: a fixed deay {}}{ φ γ k k + α +D. 8 In this mode, the expression φ γ k is a formua for the reaction time of cued reca obtained from the experimenta resuts [28], [29], where φ is the ratio of cued reca compared to a singe item recognition φ =.969 in [28], whie γ is the additiona penaty if subjects are required to simutaneousy reca the position of an item γ =.37 in [29], k is the size of the user s password, whie α =.738 is the average reaction time for moduo 2 reduction operations reported in experiments [3]. Pease note that in Eq. 8 δ represents a fixed deay, whie D > denotes a random deay associated with the counting oad. Let f D t be the probabiity density function pdf of D, i.e., D f D t; f D t can take any form appropriate for modeing human reaction times e.g., ex-gaussian [3], ex- Wad, Weibu, etc.. We parametrize f D t as foows: f D t = ft d, p, with support t > 9 where d is the mean of f D t, and p represents a other reevant density parameters i.e. variance, shape. We assume d to be an arbitrary increasing positive function of that is stricty increasing for at east one counting oad. This
6 6 RT RT s RT f f RT t d = β + β Agorithm 3 Weight-updating agorithm Initiaize: {w, w 2,..., w T } = {,..., } c i,t, if S t 2 Repeat: t: w i,t = c i,t, if F t, i, otherwise 3 Output: W i = T t= w i,t, i Fig. 5. An exampe of a human mode where for a f RT t we have the same density parameters p and where the mean is defined by d = β +β k with β i >. The expected vaue E[RT ] = δ + β + β as by []. 2 constraint on d refects a reasonabe assumption that a higher vaue of the counting oad wi ikey resut in a higher atency in the observabe user s response time RT. Using f D t, we can easiy derive the distribution of RT : f RT t = ft δ + d, p, with support t > Reca, in the HB protoco, the user s counting oad depends on a random n-bit chaenge c t. Therefore, the observabe user s response time RT can be characterized by the foowing mixture distribution: k k k f RT t = π f RT t, where π = 2 k and π =. = The expected vaue of RT is E[RT ] = k = π E[RT ]. Fig. 5 iustrates an exampe of one possibe mode of a human running the HB protoco; here we assume d := β + β with β i >. B. Probabiistic Attacking Agorithm In this section we describe a weight-updating agorithm Agorithm 3 used in our cognitive-asymmetry based timing attack. For a given secret vector s {, } n and a chaenge vector c t U {, } n et us define a set {w, w 2,..., w T } of vectors w t {, } n, t {, 2,..., T }, t being a protoco round. A vector w t consists of n binary weights w i,t associated with the individua components of s, in round t. Let us define two threshods RT f and RT s, where RT f RT s. Finay, for the observed user s response time RT in round t, et F t := {RT < RT f } be a fast event, and S t := {RT RT s } a sow event. Cognitive asymmetry in HB protoco is manifested as different atencies in user response times. Weight-updating agorithm Agorithm 3 can be interpreted as foows. If, in a given chaenge-response round t, the user enters his/her response r t with a ow atency the fast event F t takes pace, the agorithm wi set to those weights w i,t of s that correspond to the positions of zero vaued components in c t. Likewise, if a high atency is detected the sow event S t occurs, the = agorithm wi set to those weights w i,t of s that correspond to the positions of non-zero vaued components in c t. By repeating the above process over mutipe rounds, we cacuate the cumuative weight W i = T t= w i,t, for each component i of the secret vector s. As we show in the seque, the weights w i,t associated with the non-zero vaued components of the secret vector s take vaue more often on average compared to the weights of the zero vaued components, resuting in the higher cumuative weights W i. This aows us to recognize the positions of the k non-zero vaued components of the secret vector s, after observing a poynomia number of protoco rounds - see Section IV-C for a detaied anaysis. C. Anaysis of the Weight-updating Agorithm Before proceeding with the anaysis of the Agorithm 3, we make some remarks concerning notation. From now on, a variabes associated with non-zero vaued components of the secret vector s wi be marked with the sign. Accordingy, w i,t represents the binary weight associated with the component s i of s, where s i =, whie w j,t represents the binary weight of the jth component of s, where s j =. Simiary, W i and W j are associated with the non-zero and zero vaued components of the secret vector s, respectivey. Theorem. Weights w i,t and w j,t are Bernoui random variabes with success probabiities p := P w i,t = and p := P w j,t =, respectivey. Under some mid assumptions given in the proof beow, the foowing hods: p > p. Proof: The first part is trivia: by Agorithm 3, the weights w i,t and w j,t are - random variabes. Next we prove that p > p, under two mid and reaistic assumptions. In this direction, we use F RT to denote the probabiity that the user response time satisfies RT RT f, given the counting oad ight-shaded areas in Fig. 5; i.e., F RT := RT f f D t dt. In a simiar manner, we define S RT := + RT s f D t dt dark-shaded areas in Fig. 5. By Agorithm 3 we have: p = P w j,t = = P c j,t =, F t + P c j,t =, S t = 2 P F t c j,t = + P S t c j,t =, 2 p = 2 P F t c i,t = + P S t c i,t =. 3 From the definitions of F t and S t, and the distribution of RT
7 7, we can easiy obtain: k k k k p = 2 k F RT + = = k k k k p = 2 k F RT + = = S RT, 4 S + RT. 5 To prove that p > p, using 4 and 5, it suffice to show that: k = F RT F + RT k >, 6 S + RT S RT >. 7 k = k It is a matter of a straightforward cacuation to show that both conditions 6 and 7 hod under the foowing mid and reaistic assumptions about the human behavior Fig. 5: i F + RT F RT and for at east one we have F + RT < F RT, ii S + RT S RT and for at east one we have S + RT > S RT. These assumptions hod if i d Eq. 9 is an increasing positive function that is stricty increasing for at east one, and ii f D t Eq. 9 takes any form appropriate for modeing human reaction times e.g., ex-gaussian, etc.. Coroary. The weights Wi = T t= w i,t and W j = T t= w j,t, output by Agorithm 3, have binomia distributions, i.e. W i BT, p and W j BT, p. Indeed, because chaenges c t are randomy generated in each round t, w i,t, t {, 2,..., T }, are mutuay independent Bernoui random variabes. Simiar observation hods for w j,t. Combining this resut and the fact that p > p by Theorem we have the foowing resut on the correctness of Agorithm 3: Coroary 2. For a sufficienty arge T, E[ W i ] > E[W j ]. Coroary 2 shows that after observing a sufficient number of chaenge-response rounds T, we wi be abe to distinguish zero from non-zero vaued components of the secret vector s. Let us examine some other properties of the random variabes w i,t and w j,t. In a singe chaenge-response round t, w i,t and w j,t are not mutuay independent in genera. However, those variabes are defined on the same probabiity space, so it makes sense to anayze them jointy as bivariate Bernoui random variabes. Lemma. The correation coefficients ρ wi,t,w j,t and ρ wj,t,w k,t of the bivariate Bernoui random variabes w i,t, w j,t and w j,t, w k,t, respectivey, are given by: ρ wi,t,w j,t = p/2 p p pp p, ρ wj,t,w k,t = /2 p p 8 We provide the proof in the Appendix. In genera, we have ρ wi,t,w j,t and ρ wj,t,w k,t, except for p = /2. Theorem 2. The condition RT f = RT s impies p = /2 and the independence of Bernoui random variabes w i,t and w j,t, as we as the independence of the Bernoui random variabes w j,t and w k,t. Moreover, to maximize the difference p p it is sufficient to consider the threshods satisfying RT f = RT s. We provide the proof of Theorem 2 in the Appendix. As shown in [32], a sequence of independent bivariate Bernoui random variabes w i,, w j,, w i,2, w j,2,..., w i,t, w j,t gives rise to the bivariate binomia random variabe W i, W j with the correation coefficient ρ wi,t,w j,t. Likewise, the bivariate binomia random variabe W j, W k has the correation coefficient ρ wj,t,w k,t. Theorem 3. [32] When T, the distribution of the bivariate binomia random variabe W i, W j converges to the bivariate norma distribution with the correation coefficient ρ Wi,W j = ρ wi,t,w j,t ; i.e., Wi and W j are jointy norma. The same hods for the bivariate binomia random variabe W j, W k, with ρ Wj,W k = ρ wj,t,w k,t. Coroary 3. For RT f = RT s and assuming T, the jointy norma random variabes W i and W j, as we as the jointy norma random variabes W j and W k, are independent. Proof: Setting RT f = RT s impies p = /2 by Theorem 2. Therefore, ρ Wi,W j = and ρ Wj,W k = by Theorem 3 and Lemma. We concude the proof by observing that two jointy norma random variabes that are uncorreated, are aso independent [32]. Estimating the Required Number of Rounds T : So far, we know that by setting RT f = RT s and when T is arge, the random variabes W i and W j, as we as W j and W k, are normay distributed and mutuay independent by Theorem 3 and Coroary 3, and we know that their expected difference is maximized by Theorem 2. By using these resuts that arise from the cognitive asymmetry in the HB protoco, we can now estimate the number of rounds T required to discover a non-zero vaued components of the secret vector s with high probabiity. In other words, we want to determine the number of rounds T so the foowing hods: P min W i > max W j. 9 i k j n k Using the norma approximation for W i and W j, we have: W i N µ Wi, σ 2 Wi, µ Wi = T p, σ 2 Wi = T p p 2 W j N µ Wj, σ 2 W j, µ Wj = T p, σ 2 W j = T p p 2 Let us define W crit such that P W j < W crit. From this and the fact that the random variabes W i and W j are independent for RT f = RT s the foowing hods: P min W i > max W j i k j n k P W > W crit,..., W 22 k > W crit kp Wi W crit. By combining 9 and 22 we obtain: P Wi W crit = ε/k, 23
8 8 where ε is a negigibe probabiity. By standardizing W i = zσ Wi + µ W i and W crit = z crit σ Wj + µ Wj we get: P Wi W crit = P z zcritσw j +µw j µ Wi σ = ε/k. 24 Wi The standard score z crit is obtained from the condition P W j < W crit = P z < z crit. Ceary, z crit must be sufficienty arger than. Knowing that RT f = RT s impies p =.5 Theorem 2, and using 2 and 2, Eq. 24 can be re-written as: P Wi W crit = P z.5z crit T p.5 = ε/k. 25 p p }{{} z ε/k Observe from Eq. 25 how the standard score z ε/k and impicity the number of chaenge-response rounds T reates to the targeted probabiity for P Wi W crit, i.e., ε/k. We can see that in order to have ε/k as by 23, z ε/k must be sufficienty smaer than. Moreover, using Eq. 25, we can obtain the foowing expicit expression for the number of chaenge-response rounds T required to earn a the nonzero vaued components of the secret vector s, with high probabiity 2 : 2.5zcrit z ε/k p p T =. 26 p.5 For practica vaues of n and k, z crit can be bounded above by a sma postive constant and z ε/k can be bounded beow by a sma negative constant. Combined with Eq. 26, this eads to the foowing approximation for T : T = O p In what foows, we evauate and verify our theoretica resuts through numerica anaysis. Exampe: In the foowing exampe, our goa is to estimate the number of rounds T required to discover a the k nonzero vaued components of s {, } n, where n = 2 and k = 5 [2]. We use the probabiistic generative mode introduced in Section IV-A to mode a user running the HB protoco, i.e., his/her response times. We make the foowing assumptions about the user mode: the pdf of the user response time RT is given by and is parametrized by a inear positive function d = β + β Fig. 5, where β and β account for counting cacuation β = β =.738 s []. The density parameters in p e.g., the shape of the distribution, variance are estimated from the study of the Mod method with 58 rea users pease check Section III for more detais 3. As a first step in our anaysis, we need to estimate the probabiity p reca, p = /2. For this purpose, we used the above probabiistic mode and generated traces, each trace comprising 5 chaenge-response rounds. Fig. 6 shows 2 Pease note that this impies z crit and z ε/k to be sufficienty arger and smaer than, respectivey. 3 Ony operations invoving or as an operand or answer from Mod study are used in this exampe []. Response time s Chaenge response round t RTf=RTs Fig. 6. A trace of response times RT generated by the proposed generative mode of the human behavior. The average of the coected response times was seected as a threshod RT f = RT s. one such trace. As a threshod for RT f = RT s Theorem 2 we used the average of the generated response times of 34.5 seconds which is cose to the expected user reaction time of 33.4 seconds from the mode in []. Athough the average of the response times might not aways be the optima strategy for the threshod RT f = RT s, it wi sti provide good resuts as we show ater on in this section. Due to ack of space, we do not provide the proof for this statement. From each trace we randomy extracted the normay distributed variabe W i Eq. 2. Since variabes W i were independenty drawn from each trace, we were abe to estimate the mean, and µ Wi finay p = By pugging in the vaue of p =.5929 into Eq. 26 we can estimate the number of chaenge-response rounds T required to discover a non-zero vaued components of s. By setting the vaue of z crit reativey high 3. and z ε/k reativey ow 3. the agorithm wi discover a non-zero vaued components with probabiity P min W i > max W j after observing approximatey T rounds. Furthermore, rounds represents approximatey 58 ogins each ogin consists of 7 rounds, meaning that the HB protoco can be broken in a poynomia time. In Tabe II we aso estimate the number of rounds required to discover a non-zero vaued components of s as we change the sope β of the inear positive function d where d = β o + β. Pease note, even for a sma sope β =.5 we sti satisfy the condition p > p Theorem. However, since p =.58 is very cose to p =.5 Theorem 2, the attacker wi now have to observe a arger, but sti a poynomia number of chaenge-response rounds required to discover a non-zero vaued components of s. Indeed, for a smaer sope β we wi have a arger overap between probabiity density functions f D f D D that wi ead to a decreased discriminatory potentia. Our choice to use β = β =.738 in our mode to estimate the number of rounds T required to discover a non-zero vaued components of secret s was inspired by experimenta data in [3] that states that user on average achieves.738 seconds to sove zero-andone probems, such as counting specific for HB method. Fig. 7 shows the probabiity P min W i > max W j given
9 9.9 2^5 2^45 Pmin Wi > Wcrit Pmin Wi > Wcrit.9 ~ Pmin Wi > max Wj Simuations Lower bound Attack compexity 2^4 2^35 2^3 2^25 2^2 2^5 2^ 2^ Chaenge-response round t 2^ Chaenge-response round t Fig. 7. The probabiity where attacker earns a non-zero vaued components of the secret vector s. TABLE II. THE NUMBER OF CHALLENGE-RESPONSE ROUNDS THE ATTACKER HAS TO OBSERVE TO RECOVER SECRET S AS A FUNCTION OF THE SLOPE β BEING THE PART OF d. Basic attack Optimized attack β p p Login sessions Login sessions P min W i > W c Login sessions P min W i > W c by Eq. 22 at which the agorithm distinguishes a nonzero components of s in reation to the number of coected chaenge-response rounds based on the cognitive asymmetry in the HB protoco. To confirm the vaidity of our mode we aso pot the this probabiity P min W i > max W j obtained as a success rate from N = traces simuations with 2 chaenge-response rounds.we can see an inaccuracy of simuations with Eq. 22 for sma vaues of observed chaenge-response rounds. This inaccuracy foows from a sum-bound Eq. 22 that actuay presents a ower-bound. Pease note in Fig. 7 that ower bound becomes accurate for arge chaenge-response rounds T T > 8 where ε is negigibe Eq Speeding up the Attack reducing the number of rounds T : As we can see from Eq. 26, for practica vaues of n and k, we sti require a somewhat arge number of observed rounds T necessary to earn a non-zero vaued components of the secret vector s with high probabiity. Pease note that the computationa compexity of the origina weight updating agorithm is essentiay zero. As we show, by sighty modifying the weight updating agorithm we can significanty reduce the observed number of chaenge-response rounds T at the cost of the increased computationa compexity. After a sufficient number of rounds T, our modified agorithm outputs M = k + K components that hods k actua non-zero vaued components with high probabiity aong with K extra zero-vaued components. To distinguish a k non-zero components from M = k + K candidates, every candidate for the secret vector s is tested on the coected T chaengeresponse pairs. Pease note, the computationa compexity of Fig. 8. Attack compexity of the brute-force attack in which the attacker discovers a non-zero vaued components of s with high probabiity. K n k such attack is M k. The candidate whose responses match the coected ones with highest success rate presents the targeted secret vector s. Since users intentionay respond with an incorrect parity bit with probabiity η the HB protoco description in Agorithm 2 the best candidate has matches with rate around η. Essentiay, our goa is to find a sufficient number of rounds T that hods a k non-zero vaued components of secret vector s within M non-zero vaued component candidates. From Eq. 26 it is obvious that the number of required rounds T can be reduced by either infuencing the vaues of z crit or z ε/k. Reca from Eq. 24, to estimate the number of rounds T required to discover a non-zero vaued components of secret vector s with high probabiity, the variabe z ε/k must be sufficienty sma. Therefore, we can decrease the number of rounds T by decreasing z crit. Since z crit is obtained by standardizing W crit, smaer z crit impies smaer W crit. Furthermore, n k variabes W j are mutuay independent Coroary 3 and identicay distributed from the same norma distribution Eq. 2. According to the aw of arge numbers, for arge n k and a fixed K, approximatey corresponds to the fraction of the tota number of independent variabes W j arger or equa than some chosen vaue W crit : P W j W crit K n k 28 Therefore, a arger number of extra components K reduces the vaue of W crit and z crit, eading to a smaer number of rounds T Eq. 26. In the foowing exampes we wi estimate the computationa compexity of the modified weight updating agorithm as we as the number of rounds T. Exampe: Fig. 8 iustrates the reation between the computationa attack compexity of modified weight updating agorithm and the number of observed chaenge-response rounds T for different probabiities P min W i > W crit. For P min W i > W crit, K = 56 z crit =.566, p =.5929 and p =.5 Theorem 2 the computationa compexity of the agorithm wi wi be k+k k 2 5 sovabe in poynomia time [33]. However, the agorithm
10 wi extract a k non-zero vaued components after observing T 38 rounds. Pease note that the required number of chaengeresponse rounds can be further reduced by sighty increasing the vaue of z ε/k whie sti maintaining the arge probabiity of success. For exampe, with probabiity P min W i > W crit.9 and K = 56 the compexity of the attack is 2 5, the agorithm wi be abe to determine the targeted secret vector s after T = 95 rounds. If a singe ogin session contains m = 7 rounds, the attacker wi have to observe 3 ogin sessions! In Tabe II we aso estimate the number of ogin sessions required to discover a non-zero vaued components of s as we change the sope β of the inear positive function d. As expected, a smaer p wi require a arger number of ogin sessions for the attacker. V. USABILITY IMPLICATIONS OF STRENGTHENING MOD AND HB SCHEMES We have shown that both Mod and HB, as cognitive authentication schemes, are vunerabe to cognitive-asymmetry side channes, or more precisey to passive side-channe timing attacks. In the foowing, we argue that the ony way to strengthen these schemes is to perturb the usabiity e.g. increase the overa ogin time and/or increase PIN/password size. A. Entering a Response After a Predefined Deay One way to strengthen the security of Mod and HB schemes against the passive side-channe timing attack is to prevent users to enter the response immediatey after cacuating it. In this way, the attacker wi not be abe to extract sufficient information about the user s secret from the recorded response times. For exampe, for Mod scheme, if we assume a Gaussian probabiity distribution, the majority of response times are not greater than 3.5 seconds. By preventing the users to enter the response in ess than 3.5 seconds, we eiminate the sidechanne attack based on the variations in the users cognitive oad response times. However, the overa authentication time wi increase from the initia.4 to approximatey 5 seconds waiting cost [sec]. Simiary, for HB scheme we can see in Fig. 6 that the majority of response times are not greater than 4 seconds. By preventing the users to enter the response in ess than 4 seconds, this means that the overa authentication time increases from the initia 24.5 to approximatey 28 seconds 4 7 [sec]. Atogether, it is possibe to strengthen the security of both cognitive authentication schemes by preventing users to enter the response faster than the predefined deay. Nevertheess, we have shown that this soution necessariy increases overa authentication time; thus a higher security comes at some form of the decreased usabiity. B. Increasing the PIN Size and Reated Usabiity Cost In this section we investigate how a sighty onger secret k affects the security and usabiity of Mod and HB schemes. In the case of Mod protoco users woud have to remember a arger PIN aso denoted with k, whie in HB protoco users woud have to remember a arger number k of non-zero vaued components of secret vector s. By increasing the number of non-zero vaued components k, the HB protoco sti remains insecure against the timing attack. This can be ceary seen from Eq. 27, where the time compexity of the attack is independent of the practica vaues of k. A arger k can sighty increase the number of ogin rounds the attacker has to observe, but cannot prevent the attacker from earning a k components expressed through the standardized variabe z ε/k in Eq. 26. For Mod scheme, pease note that the minimum PIN size, denoted with k, has to satisfy the foowing expression: k = 4 og2 HD r, t r, 29 where HD r, t r is the conditiona entropy of the random PIN digit D given the vectors of observed response digits r and response times t r. The reduction in entropy due to the time-based side-channe has to be compensated by extending the 4-digit PIN size. Reca, by evauating Eq. 7 numericay, we were abe to reduce the entropy by approximatey 2 bits per PIN digit. So, according to Eq. 29, the new PIN size shoud be at east k = 7 digits ong. In order to estimate the associated usabiity cost for the Mod scheme, we use the computationa mode proposed in []. The expected vaue of response time for a singe PIN digit is given by the foowing equation: E[RT ] = ϕ k + α + α 3 where ϕ k is the reaction time by the user to reca k PIN digits, α =.738 and α =.773 are the average reaction times for moduo reduction operations and sma additions, respectivey, whie ϕ =.969 is the ratio of cued reca compared to singe item recognition []. From Eq. 3 we obtain E[RT ] = 2.82 seconds what is consistent with the average user reaction time of 2.98 seconds for a singe digit from our test. Using this mode, we can see that by increasing the PIN size k from the initia 4 to 7 digits, the expected vaue of the overa authentication time increases from initia to [sec] seconds. We have shown that onger PIN strengthens the security of Mod scheme against timing attacks. However, a higher security comes at non-negigibe usabiity cost; i.e., an increase in both the PIN size and the overa authentication time. C. Discussion In the previous section we have shown that the ony way to strengthen the security of HB and Mod schemes against the timing attack is to increase the overa authentication time. In the case of the HB scheme we have shown that the security can ony be strengthened by preventing the users to enter the response before the predefined deay expires, what inevitaby increases the overa authentication time the usabiity cost. The increase of the overa authentication time is aso inevitabe when strengthening the Mod scheme, either
11 by increasing the PIN size or by introducing a predefined deay. Since usabiity score of an authentication scheme is correated with short authentication times, the designers of new cognitive authentication schemes shoud not negect the timing side channe attack. VI. RELATED WORK There is a body of research focused on designing secure PIN-entry schemes in face of the threat posed by observation attacks [34], [35], [36]. Some research design their soutions secure against a short-term memory attackers, using the fact that the human short-term memory has a imited capacity. In these soutions, the user is requested to give answers to a set of chaenges during a ogin procedure. However, the authentication scheme is designed in a way that the user can easiy respond to the questions, whie the cognitive capacity exceeds the attacker human memory. Bianchi et a. proposed a nonvisua unimoda schemes, which uses hidden audio and vibration chaenges for user authentication [37]. In another work by Bianch et a. Spinock, Coorock and Timeock schemes that achieve faster times than Spinock [38], [39]. However, a three schemes have partia eakage of information in the observation attack. Other soutions assume the existence of stronger attacker that can record the compete ogin session and try to recover the user s secret PIN/password [4], [2], [7], [3], [4], [4]. However, a these scheme are not usabe in practice since they a take arge authentication time. Designing a scheme secure against even a simpe passive attack in a mode where the attacker can observe both chaenges and responses appears to be chaenging [7], [42], []. In Cognitive authentication scheme CAS [7], a user mentay computes a path formed by his portfoio images, and gives an answer based on that mentay computed path. CAS scheme is vunerabe to SAT sover attacks [42] and an attack based on probabiistic decision tree []. However, the speed of such attacks can be improved in combination with a timing attack. This comes from the fact that not a decision paths are of the same ength, what eads to faster or sower user response times. By measuring this time, the attacker can eiminate some of the possibe decision paths what can speed up the whoe process of finding the user s password. To speed up the ogin process whie keeping the soution safe against observation attacks, some soutions rey on the presence of secondary-based unobservabe channes. Kuber and Yu [43] and Sasamoto et. a. [5] use a tactie channe as a secure hidden chaenge channe. In VibraPass authentication system user receives hidden chaenges via his mobie phone [44] a vibration teing the user to enter true/fase response. Hidden chaenges are used to avoid possibe manipuations by the attacker. The authors mentioned confused waiting as a potentia timing attack. In the Undercover soution the user simutaneousy receives a visua chaenge and a hidden tactie chaenge via a protected channe and authenticates by answering correcty to severa chaenges. One of authors of Undercover, Hasegawa et. a. proposed two aternative designs to Undercover [4], one of which uses an audio channe as the carrier of the hidden chaenges. However, the proposed soution is prone to intersection attacks [9]. Unfortunatey, Undercover is aso prone to intersection attacks as independenty demonstrated in [9] and []. This probem can be easiy mitigated if chaenges are fixed instead of being randomized [9]. Unfortunatey, Undercover is not secure in a very strong attacker mode where attacker records user s response time [9]. The attack is based on design faws and expoits human users nonuniform behavior on how users respond to different chaenges. VII. CONCLUSIONS In this paper we have shown how it is possibe to expoit detectabe variations in the user s cognitive oad when authenticating using cognitive authentication schemes. We demonstrated this by expoiting vunerabiity of two weknown cognitive authentication schemes Hopper-Bum HB and Mod methods to cognitive-asymmetry side-channe timing attacks. The novety of these attacks is that they are not based on the asymmetry of neither physica nor virtua user interfaces of a certain method. With this, we have shown the existence of a strong tradeoff between security and usabiity in cognitive authentication methods, where security can ony be achieved at a cost of a perturbed usabiity e.g. onger authentication time and/or onger PINs/passwords. An important concusion from the resuts presented in this paper is that researchers designing and evauating cognitive authentication schemes shoud exercise caution when caiming superiority of their proposas in terms of usabiity with respect to existing proposas. High usabiity scores are often correated with short authentication times. However, potentia vunerabiities of those authentication methods to timing attacks coud easiy render the caimed short authentication times not so short in the end. A genera concusion that resuts from the study of HB and Mod methods as representatives of a whoe range of cognitive authentication schemes can be summarized in the foowing guideine: When designing new cognitive authentication methods designers shoud pay particuar attention to potentia asymmetry in both the cognitive oad cognitive-asymmetry side-channes and the physica interface of different eements of their methods. For future work we pan to investigate the infuence of other factors such as memory factor on the effectiveness of the side-channe timing attacks on cognitive authentication schemes by conducting a ong term study with users. Aso, as HB protoco found its appication in secure RFID systems [6], we pan to investigate the security of such RFID systems against the timing attack in detai. REFERENCES [] E. Grosse and M. Upadhyay, Authentication at Scae, IEEE Security and Privacy, vo., pp. 5 22, 23. [2] F. Tari, A. A. Ozok, and S. H. Hoden, A comparison of perceived and rea shouder-surfing risks between aphanumeric and graphica passwords, in Proc. Symposium on Usabe Privacy and Security, ser. SOUPS. ACM, 26, pp
A Brief Introduction to Markov Chains and Hidden Markov Models
 A Brief Introduction to Markov Chains and Hidden Markov Modes Aen B MacKenzie Notes for December 1, 3, &8, 2015 Discrete-Time Markov Chains You may reca that when we first introduced random processes,
A Brief Introduction to Markov Chains and Hidden Markov Modes Aen B MacKenzie Notes for December 1, 3, &8, 2015 Discrete-Time Markov Chains You may reca that when we first introduced random processes,
CS229 Lecture notes. Andrew Ng
 CS229 Lecture notes Andrew Ng Part IX The EM agorithm In the previous set of notes, we taked about the EM agorithm as appied to fitting a mixture of Gaussians. In this set of notes, we give a broader view
CS229 Lecture notes Andrew Ng Part IX The EM agorithm In the previous set of notes, we taked about the EM agorithm as appied to fitting a mixture of Gaussians. In this set of notes, we give a broader view
Cryptanalysis of PKP: A New Approach
 Cryptanaysis of PKP: A New Approach Éiane Jaumes and Antoine Joux DCSSI 18, rue du Dr. Zamenhoff F-92131 Issy-es-Mx Cedex France eiane.jaumes@wanadoo.fr Antoine.Joux@ens.fr Abstract. Quite recenty, in
Cryptanaysis of PKP: A New Approach Éiane Jaumes and Antoine Joux DCSSI 18, rue du Dr. Zamenhoff F-92131 Issy-es-Mx Cedex France eiane.jaumes@wanadoo.fr Antoine.Joux@ens.fr Abstract. Quite recenty, in
Bayesian Learning. You hear a which which could equally be Thanks or Tanks, which would you go with?
 Bayesian Learning A powerfu and growing approach in machine earning We use it in our own decision making a the time You hear a which which coud equay be Thanks or Tanks, which woud you go with? Combine
Bayesian Learning A powerfu and growing approach in machine earning We use it in our own decision making a the time You hear a which which coud equay be Thanks or Tanks, which woud you go with? Combine
A. Distribution of the test statistic
 A. Distribution of the test statistic In the sequentia test, we first compute the test statistic from a mini-batch of size m. If a decision cannot be made with this statistic, we keep increasing the mini-batch
A. Distribution of the test statistic In the sequentia test, we first compute the test statistic from a mini-batch of size m. If a decision cannot be made with this statistic, we keep increasing the mini-batch
Explicit overall risk minimization transductive bound
 1 Expicit overa risk minimization transductive bound Sergio Decherchi, Paoo Gastado, Sandro Ridea, Rodofo Zunino Dept. of Biophysica and Eectronic Engineering (DIBE), Genoa University Via Opera Pia 11a,
1 Expicit overa risk minimization transductive bound Sergio Decherchi, Paoo Gastado, Sandro Ridea, Rodofo Zunino Dept. of Biophysica and Eectronic Engineering (DIBE), Genoa University Via Opera Pia 11a,
6.434J/16.391J Statistics for Engineers and Scientists May 4 MIT, Spring 2006 Handout #17. Solution 7
 6.434J/16.391J Statistics for Engineers and Scientists May 4 MIT, Spring 2006 Handout #17 Soution 7 Probem 1: Generating Random Variabes Each part of this probem requires impementation in MATLAB. For the
6.434J/16.391J Statistics for Engineers and Scientists May 4 MIT, Spring 2006 Handout #17 Soution 7 Probem 1: Generating Random Variabes Each part of this probem requires impementation in MATLAB. For the
Algorithms to solve massively under-defined systems of multivariate quadratic equations
 Agorithms to sove massivey under-defined systems of mutivariate quadratic equations Yasufumi Hashimoto Abstract It is we known that the probem to sove a set of randomy chosen mutivariate quadratic equations
Agorithms to sove massivey under-defined systems of mutivariate quadratic equations Yasufumi Hashimoto Abstract It is we known that the probem to sove a set of randomy chosen mutivariate quadratic equations
Asynchronous Control for Coupled Markov Decision Systems
 INFORMATION THEORY WORKSHOP (ITW) 22 Asynchronous Contro for Couped Marov Decision Systems Michae J. Neey University of Southern Caifornia Abstract This paper considers optima contro for a coection of
INFORMATION THEORY WORKSHOP (ITW) 22 Asynchronous Contro for Couped Marov Decision Systems Michae J. Neey University of Southern Caifornia Abstract This paper considers optima contro for a coection of
Separation of Variables and a Spherical Shell with Surface Charge
 Separation of Variabes and a Spherica She with Surface Charge In cass we worked out the eectrostatic potentia due to a spherica she of radius R with a surface charge density σθ = σ cos θ. This cacuation
Separation of Variabes and a Spherica She with Surface Charge In cass we worked out the eectrostatic potentia due to a spherica she of radius R with a surface charge density σθ = σ cos θ. This cacuation
Unconditional security of differential phase shift quantum key distribution
 Unconditiona security of differentia phase shift quantum key distribution Kai Wen, Yoshihisa Yamamoto Ginzton Lab and Dept of Eectrica Engineering Stanford University Basic idea of DPS-QKD Protoco. Aice
Unconditiona security of differentia phase shift quantum key distribution Kai Wen, Yoshihisa Yamamoto Ginzton Lab and Dept of Eectrica Engineering Stanford University Basic idea of DPS-QKD Protoco. Aice
Some Measures for Asymmetry of Distributions
 Some Measures for Asymmetry of Distributions Georgi N. Boshnakov First version: 31 January 2006 Research Report No. 5, 2006, Probabiity and Statistics Group Schoo of Mathematics, The University of Manchester
Some Measures for Asymmetry of Distributions Georgi N. Boshnakov First version: 31 January 2006 Research Report No. 5, 2006, Probabiity and Statistics Group Schoo of Mathematics, The University of Manchester
XSAT of linear CNF formulas
 XSAT of inear CN formuas Bernd R. Schuh Dr. Bernd Schuh, D-50968 Kön, Germany; bernd.schuh@netcoogne.de eywords: compexity, XSAT, exact inear formua, -reguarity, -uniformity, NPcompeteness Abstract. Open
XSAT of inear CN formuas Bernd R. Schuh Dr. Bernd Schuh, D-50968 Kön, Germany; bernd.schuh@netcoogne.de eywords: compexity, XSAT, exact inear formua, -reguarity, -uniformity, NPcompeteness Abstract. Open
Chemical Kinetics Part 2
 Integrated Rate Laws Chemica Kinetics Part 2 The rate aw we have discussed thus far is the differentia rate aw. Let us consider the very simpe reaction: a A à products The differentia rate reates the rate
Integrated Rate Laws Chemica Kinetics Part 2 The rate aw we have discussed thus far is the differentia rate aw. Let us consider the very simpe reaction: a A à products The differentia rate reates the rate
MARKOV CHAINS AND MARKOV DECISION THEORY. Contents
 MARKOV CHAINS AND MARKOV DECISION THEORY ARINDRIMA DATTA Abstract. In this paper, we begin with a forma introduction to probabiity and expain the concept of random variabes and stochastic processes. After
MARKOV CHAINS AND MARKOV DECISION THEORY ARINDRIMA DATTA Abstract. In this paper, we begin with a forma introduction to probabiity and expain the concept of random variabes and stochastic processes. After
Chemical Kinetics Part 2. Chapter 16
 Chemica Kinetics Part 2 Chapter 16 Integrated Rate Laws The rate aw we have discussed thus far is the differentia rate aw. Let us consider the very simpe reaction: a A à products The differentia rate reates
Chemica Kinetics Part 2 Chapter 16 Integrated Rate Laws The rate aw we have discussed thus far is the differentia rate aw. Let us consider the very simpe reaction: a A à products The differentia rate reates
T.C. Banwell, S. Galli. {bct, Telcordia Technologies, Inc., 445 South Street, Morristown, NJ 07960, USA
 ON THE SYMMETRY OF THE POWER INE CHANNE T.C. Banwe, S. Gai {bct, sgai}@research.tecordia.com Tecordia Technoogies, Inc., 445 South Street, Morristown, NJ 07960, USA Abstract The indoor power ine network
ON THE SYMMETRY OF THE POWER INE CHANNE T.C. Banwe, S. Gai {bct, sgai}@research.tecordia.com Tecordia Technoogies, Inc., 445 South Street, Morristown, NJ 07960, USA Abstract The indoor power ine network
An Algorithm for Pruning Redundant Modules in Min-Max Modular Network
 An Agorithm for Pruning Redundant Modues in Min-Max Moduar Network Hui-Cheng Lian and Bao-Liang Lu Department of Computer Science and Engineering, Shanghai Jiao Tong University 1954 Hua Shan Rd., Shanghai
An Agorithm for Pruning Redundant Modues in Min-Max Moduar Network Hui-Cheng Lian and Bao-Liang Lu Department of Computer Science and Engineering, Shanghai Jiao Tong University 1954 Hua Shan Rd., Shanghai
Centralized Coded Caching of Correlated Contents
 Centraized Coded Caching of Correated Contents Qianqian Yang and Deniz Gündüz Information Processing and Communications Lab Department of Eectrica and Eectronic Engineering Imperia Coege London arxiv:1711.03798v1
Centraized Coded Caching of Correated Contents Qianqian Yang and Deniz Gündüz Information Processing and Communications Lab Department of Eectrica and Eectronic Engineering Imperia Coege London arxiv:1711.03798v1
First-Order Corrections to Gutzwiller s Trace Formula for Systems with Discrete Symmetries
 c 26 Noninear Phenomena in Compex Systems First-Order Corrections to Gutzwier s Trace Formua for Systems with Discrete Symmetries Hoger Cartarius, Jörg Main, and Günter Wunner Institut für Theoretische
c 26 Noninear Phenomena in Compex Systems First-Order Corrections to Gutzwier s Trace Formua for Systems with Discrete Symmetries Hoger Cartarius, Jörg Main, and Günter Wunner Institut für Theoretische
Improving the Accuracy of Boolean Tomography by Exploiting Path Congestion Degrees
 Improving the Accuracy of Booean Tomography by Expoiting Path Congestion Degrees Zhiyong Zhang, Gaoei Fei, Fucai Yu, Guangmin Hu Schoo of Communication and Information Engineering, University of Eectronic
Improving the Accuracy of Booean Tomography by Expoiting Path Congestion Degrees Zhiyong Zhang, Gaoei Fei, Fucai Yu, Guangmin Hu Schoo of Communication and Information Engineering, University of Eectronic
FRST Multivariate Statistics. Multivariate Discriminant Analysis (MDA)
 1 FRST 531 -- Mutivariate Statistics Mutivariate Discriminant Anaysis (MDA) Purpose: 1. To predict which group (Y) an observation beongs to based on the characteristics of p predictor (X) variabes, using
1 FRST 531 -- Mutivariate Statistics Mutivariate Discriminant Anaysis (MDA) Purpose: 1. To predict which group (Y) an observation beongs to based on the characteristics of p predictor (X) variabes, using
Uniprocessor Feasibility of Sporadic Tasks with Constrained Deadlines is Strongly conp-complete
 Uniprocessor Feasibiity of Sporadic Tasks with Constrained Deadines is Strongy conp-compete Pontus Ekberg and Wang Yi Uppsaa University, Sweden Emai: {pontus.ekberg yi}@it.uu.se Abstract Deciding the feasibiity
Uniprocessor Feasibiity of Sporadic Tasks with Constrained Deadines is Strongy conp-compete Pontus Ekberg and Wang Yi Uppsaa University, Sweden Emai: {pontus.ekberg yi}@it.uu.se Abstract Deciding the feasibiity
Efficient Generation of Random Bits from Finite State Markov Chains
 Efficient Generation of Random Bits from Finite State Markov Chains Hongchao Zhou and Jehoshua Bruck, Feow, IEEE Abstract The probem of random number generation from an uncorreated random source (of unknown
Efficient Generation of Random Bits from Finite State Markov Chains Hongchao Zhou and Jehoshua Bruck, Feow, IEEE Abstract The probem of random number generation from an uncorreated random source (of unknown
C. Fourier Sine Series Overview
 12 PHILIP D. LOEWEN C. Fourier Sine Series Overview Let some constant > be given. The symboic form of the FSS Eigenvaue probem combines an ordinary differentia equation (ODE) on the interva (, ) with a
12 PHILIP D. LOEWEN C. Fourier Sine Series Overview Let some constant > be given. The symboic form of the FSS Eigenvaue probem combines an ordinary differentia equation (ODE) on the interva (, ) with a
II. PROBLEM. A. Description. For the space of audio signals
 CS229 - Fina Report Speech Recording based Language Recognition (Natura Language) Leopod Cambier - cambier; Matan Leibovich - matane; Cindy Orozco Bohorquez - orozcocc ABSTRACT We construct a rea time
CS229 - Fina Report Speech Recording based Language Recognition (Natura Language) Leopod Cambier - cambier; Matan Leibovich - matane; Cindy Orozco Bohorquez - orozcocc ABSTRACT We construct a rea time
Componentwise Determination of the Interval Hull Solution for Linear Interval Parameter Systems
 Componentwise Determination of the Interva Hu Soution for Linear Interva Parameter Systems L. V. Koev Dept. of Theoretica Eectrotechnics, Facuty of Automatics, Technica University of Sofia, 1000 Sofia,
Componentwise Determination of the Interva Hu Soution for Linear Interva Parameter Systems L. V. Koev Dept. of Theoretica Eectrotechnics, Facuty of Automatics, Technica University of Sofia, 1000 Sofia,
More Scattering: the Partial Wave Expansion
 More Scattering: the Partia Wave Expansion Michae Fower /7/8 Pane Waves and Partia Waves We are considering the soution to Schrödinger s equation for scattering of an incoming pane wave in the z-direction
More Scattering: the Partia Wave Expansion Michae Fower /7/8 Pane Waves and Partia Waves We are considering the soution to Schrödinger s equation for scattering of an incoming pane wave in the z-direction
Tracking Control of Multiple Mobile Robots
 Proceedings of the 2001 IEEE Internationa Conference on Robotics & Automation Seou, Korea May 21-26, 2001 Tracking Contro of Mutipe Mobie Robots A Case Study of Inter-Robot Coision-Free Probem Jurachart
Proceedings of the 2001 IEEE Internationa Conference on Robotics & Automation Seou, Korea May 21-26, 2001 Tracking Contro of Mutipe Mobie Robots A Case Study of Inter-Robot Coision-Free Probem Jurachart
Statistical Learning Theory: A Primer
 Internationa Journa of Computer Vision 38(), 9 3, 2000 c 2000 uwer Academic Pubishers. Manufactured in The Netherands. Statistica Learning Theory: A Primer THEODOROS EVGENIOU, MASSIMILIANO PONTIL AND TOMASO
Internationa Journa of Computer Vision 38(), 9 3, 2000 c 2000 uwer Academic Pubishers. Manufactured in The Netherands. Statistica Learning Theory: A Primer THEODOROS EVGENIOU, MASSIMILIANO PONTIL AND TOMASO
Efficiently Generating Random Bits from Finite State Markov Chains
 1 Efficienty Generating Random Bits from Finite State Markov Chains Hongchao Zhou and Jehoshua Bruck, Feow, IEEE Abstract The probem of random number generation from an uncorreated random source (of unknown
1 Efficienty Generating Random Bits from Finite State Markov Chains Hongchao Zhou and Jehoshua Bruck, Feow, IEEE Abstract The probem of random number generation from an uncorreated random source (of unknown
Inductive Bias: How to generalize on novel data. CS Inductive Bias 1
 Inductive Bias: How to generaize on nove data CS 478 - Inductive Bias 1 Overfitting Noise vs. Exceptions CS 478 - Inductive Bias 2 Non-Linear Tasks Linear Regression wi not generaize we to the task beow
Inductive Bias: How to generaize on nove data CS 478 - Inductive Bias 1 Overfitting Noise vs. Exceptions CS 478 - Inductive Bias 2 Non-Linear Tasks Linear Regression wi not generaize we to the task beow
A Novel Learning Method for Elman Neural Network Using Local Search
 Neura Information Processing Letters and Reviews Vo. 11, No. 8, August 2007 LETTER A Nove Learning Method for Eman Neura Networ Using Loca Search Facuty of Engineering, Toyama University, Gofuu 3190 Toyama
Neura Information Processing Letters and Reviews Vo. 11, No. 8, August 2007 LETTER A Nove Learning Method for Eman Neura Networ Using Loca Search Facuty of Engineering, Toyama University, Gofuu 3190 Toyama
Statistical Inference, Econometric Analysis and Matrix Algebra
 Statistica Inference, Econometric Anaysis and Matrix Agebra Bernhard Schipp Water Krämer Editors Statistica Inference, Econometric Anaysis and Matrix Agebra Festschrift in Honour of Götz Trenker Physica-Verag
Statistica Inference, Econometric Anaysis and Matrix Agebra Bernhard Schipp Water Krämer Editors Statistica Inference, Econometric Anaysis and Matrix Agebra Festschrift in Honour of Götz Trenker Physica-Verag
AST 418/518 Instrumentation and Statistics
 AST 418/518 Instrumentation and Statistics Cass Website: http://ircamera.as.arizona.edu/astr_518 Cass Texts: Practica Statistics for Astronomers, J.V. Wa, and C.R. Jenkins, Second Edition. Measuring the
AST 418/518 Instrumentation and Statistics Cass Website: http://ircamera.as.arizona.edu/astr_518 Cass Texts: Practica Statistics for Astronomers, J.V. Wa, and C.R. Jenkins, Second Edition. Measuring the
Do Schools Matter for High Math Achievement? Evidence from the American Mathematics Competitions Glenn Ellison and Ashley Swanson Online Appendix
 VOL. NO. DO SCHOOLS MATTER FOR HIGH MATH ACHIEVEMENT? 43 Do Schoos Matter for High Math Achievement? Evidence from the American Mathematics Competitions Genn Eison and Ashey Swanson Onine Appendix Appendix
VOL. NO. DO SCHOOLS MATTER FOR HIGH MATH ACHIEVEMENT? 43 Do Schoos Matter for High Math Achievement? Evidence from the American Mathematics Competitions Genn Eison and Ashey Swanson Onine Appendix Appendix
Stochastic Complement Analysis of Multi-Server Threshold Queues. with Hysteresis. Abstract
 Stochastic Compement Anaysis of Muti-Server Threshod Queues with Hysteresis John C.S. Lui The Dept. of Computer Science & Engineering The Chinese University of Hong Kong Leana Goubchik Dept. of Computer
Stochastic Compement Anaysis of Muti-Server Threshod Queues with Hysteresis John C.S. Lui The Dept. of Computer Science & Engineering The Chinese University of Hong Kong Leana Goubchik Dept. of Computer
ASummaryofGaussianProcesses Coryn A.L. Bailer-Jones
 ASummaryofGaussianProcesses Coryn A.L. Baier-Jones Cavendish Laboratory University of Cambridge caj@mrao.cam.ac.uk Introduction A genera prediction probem can be posed as foows. We consider that the variabe
ASummaryofGaussianProcesses Coryn A.L. Baier-Jones Cavendish Laboratory University of Cambridge caj@mrao.cam.ac.uk Introduction A genera prediction probem can be posed as foows. We consider that the variabe
STA 216 Project: Spline Approach to Discrete Survival Analysis
 : Spine Approach to Discrete Surviva Anaysis November 4, 005 1 Introduction Athough continuous surviva anaysis differs much from the discrete surviva anaysis, there is certain ink between the two modeing
: Spine Approach to Discrete Surviva Anaysis November 4, 005 1 Introduction Athough continuous surviva anaysis differs much from the discrete surviva anaysis, there is certain ink between the two modeing
Emmanuel Abbe Colin Sandon
 Detection in the stochastic bock mode with mutipe custers: proof of the achievabiity conjectures, acycic BP, and the information-computation gap Emmanue Abbe Coin Sandon Abstract In a paper that initiated
Detection in the stochastic bock mode with mutipe custers: proof of the achievabiity conjectures, acycic BP, and the information-computation gap Emmanue Abbe Coin Sandon Abstract In a paper that initiated
Efficient Similarity Search across Top-k Lists under the Kendall s Tau Distance
 Efficient Simiarity Search across Top-k Lists under the Kenda s Tau Distance Koninika Pa TU Kaisersautern Kaisersautern, Germany pa@cs.uni-k.de Sebastian Miche TU Kaisersautern Kaisersautern, Germany smiche@cs.uni-k.de
Efficient Simiarity Search across Top-k Lists under the Kenda s Tau Distance Koninika Pa TU Kaisersautern Kaisersautern, Germany pa@cs.uni-k.de Sebastian Miche TU Kaisersautern Kaisersautern, Germany smiche@cs.uni-k.de
Turbo Codes. Coding and Communication Laboratory. Dept. of Electrical Engineering, National Chung Hsing University
 Turbo Codes Coding and Communication Laboratory Dept. of Eectrica Engineering, Nationa Chung Hsing University Turbo codes 1 Chapter 12: Turbo Codes 1. Introduction 2. Turbo code encoder 3. Design of intereaver
Turbo Codes Coding and Communication Laboratory Dept. of Eectrica Engineering, Nationa Chung Hsing University Turbo codes 1 Chapter 12: Turbo Codes 1. Introduction 2. Turbo code encoder 3. Design of intereaver
Data Mining Technology for Failure Prognostic of Avionics
 IEEE Transactions on Aerospace and Eectronic Systems. Voume 38, #, pp.388-403, 00. Data Mining Technoogy for Faiure Prognostic of Avionics V.A. Skormin, Binghamton University, Binghamton, NY, 1390, USA
IEEE Transactions on Aerospace and Eectronic Systems. Voume 38, #, pp.388-403, 00. Data Mining Technoogy for Faiure Prognostic of Avionics V.A. Skormin, Binghamton University, Binghamton, NY, 1390, USA
Stochastic Variational Inference with Gradient Linearization
 Stochastic Variationa Inference with Gradient Linearization Suppementa Materia Tobias Pötz * Anne S Wannenwetsch Stefan Roth Department of Computer Science, TU Darmstadt Preface In this suppementa materia,
Stochastic Variationa Inference with Gradient Linearization Suppementa Materia Tobias Pötz * Anne S Wannenwetsch Stefan Roth Department of Computer Science, TU Darmstadt Preface In this suppementa materia,
Melodic contour estimation with B-spline models using a MDL criterion
 Meodic contour estimation with B-spine modes using a MDL criterion Damien Loive, Ney Barbot, Oivier Boeffard IRISA / University of Rennes 1 - ENSSAT 6 rue de Kerampont, B.P. 80518, F-305 Lannion Cedex
Meodic contour estimation with B-spine modes using a MDL criterion Damien Loive, Ney Barbot, Oivier Boeffard IRISA / University of Rennes 1 - ENSSAT 6 rue de Kerampont, B.P. 80518, F-305 Lannion Cedex
Throughput Optimal Scheduling for Wireless Downlinks with Reconfiguration Delay
 Throughput Optima Scheduing for Wireess Downinks with Reconfiguration Deay Vineeth Baa Sukumaran vineethbs@gmai.com Department of Avionics Indian Institute of Space Science and Technoogy. Abstract We consider
Throughput Optima Scheduing for Wireess Downinks with Reconfiguration Deay Vineeth Baa Sukumaran vineethbs@gmai.com Department of Avionics Indian Institute of Space Science and Technoogy. Abstract We consider
Lecture 6: Moderately Large Deflection Theory of Beams
 Structura Mechanics 2.8 Lecture 6 Semester Yr Lecture 6: Moderatey Large Defection Theory of Beams 6.1 Genera Formuation Compare to the cassica theory of beams with infinitesima deformation, the moderatey
Structura Mechanics 2.8 Lecture 6 Semester Yr Lecture 6: Moderatey Large Defection Theory of Beams 6.1 Genera Formuation Compare to the cassica theory of beams with infinitesima deformation, the moderatey
The EM Algorithm applied to determining new limit points of Mahler measures
 Contro and Cybernetics vo. 39 (2010) No. 4 The EM Agorithm appied to determining new imit points of Maher measures by Souad E Otmani, Georges Rhin and Jean-Marc Sac-Épée Université Pau Veraine-Metz, LMAM,
Contro and Cybernetics vo. 39 (2010) No. 4 The EM Agorithm appied to determining new imit points of Maher measures by Souad E Otmani, Georges Rhin and Jean-Marc Sac-Épée Université Pau Veraine-Metz, LMAM,
6 Wave Equation on an Interval: Separation of Variables
 6 Wave Equation on an Interva: Separation of Variabes 6.1 Dirichet Boundary Conditions Ref: Strauss, Chapter 4 We now use the separation of variabes technique to study the wave equation on a finite interva.
6 Wave Equation on an Interva: Separation of Variabes 6.1 Dirichet Boundary Conditions Ref: Strauss, Chapter 4 We now use the separation of variabes technique to study the wave equation on a finite interva.
Formulas for Angular-Momentum Barrier Factors Version II
 BNL PREPRINT BNL-QGS-06-101 brfactor1.tex Formuas for Anguar-Momentum Barrier Factors Version II S. U. Chung Physics Department, Brookhaven Nationa Laboratory, Upton, NY 11973 March 19, 2015 abstract A
BNL PREPRINT BNL-QGS-06-101 brfactor1.tex Formuas for Anguar-Momentum Barrier Factors Version II S. U. Chung Physics Department, Brookhaven Nationa Laboratory, Upton, NY 11973 March 19, 2015 abstract A
From Margins to Probabilities in Multiclass Learning Problems
 From Margins to Probabiities in Muticass Learning Probems Andrea Passerini and Massimiiano Ponti 2 and Paoo Frasconi 3 Abstract. We study the probem of muticass cassification within the framework of error
From Margins to Probabiities in Muticass Learning Probems Andrea Passerini and Massimiiano Ponti 2 and Paoo Frasconi 3 Abstract. We study the probem of muticass cassification within the framework of error
SydU STAT3014 (2015) Second semester Dr. J. Chan 18
 STAT3014/3914 Appied Stat.-Samping C-Stratified rand. sampe Stratified Random Samping.1 Introduction Description The popuation of size N is divided into mutuay excusive and exhaustive subpopuations caed
STAT3014/3914 Appied Stat.-Samping C-Stratified rand. sampe Stratified Random Samping.1 Introduction Description The popuation of size N is divided into mutuay excusive and exhaustive subpopuations caed
Iterative Decoding Performance Bounds for LDPC Codes on Noisy Channels
 Iterative Decoding Performance Bounds for LDPC Codes on Noisy Channes arxiv:cs/060700v1 [cs.it] 6 Ju 006 Chun-Hao Hsu and Achieas Anastasopouos Eectrica Engineering and Computer Science Department University
Iterative Decoding Performance Bounds for LDPC Codes on Noisy Channes arxiv:cs/060700v1 [cs.it] 6 Ju 006 Chun-Hao Hsu and Achieas Anastasopouos Eectrica Engineering and Computer Science Department University
12.2. Maxima and Minima. Introduction. Prerequisites. Learning Outcomes
 Maima and Minima 1. Introduction In this Section we anayse curves in the oca neighbourhood of a stationary point and, from this anaysis, deduce necessary conditions satisfied by oca maima and oca minima.
Maima and Minima 1. Introduction In this Section we anayse curves in the oca neighbourhood of a stationary point and, from this anaysis, deduce necessary conditions satisfied by oca maima and oca minima.
In-plane shear stiffness of bare steel deck through shell finite element models. G. Bian, B.W. Schafer. June 2017
 In-pane shear stiffness of bare stee deck through she finite eement modes G. Bian, B.W. Schafer June 7 COLD-FORMED STEEL RESEARCH CONSORTIUM REPORT SERIES CFSRC R-7- SDII Stee Diaphragm Innovation Initiative
In-pane shear stiffness of bare stee deck through she finite eement modes G. Bian, B.W. Schafer June 7 COLD-FORMED STEEL RESEARCH CONSORTIUM REPORT SERIES CFSRC R-7- SDII Stee Diaphragm Innovation Initiative
Expectation-Maximization for Estimating Parameters for a Mixture of Poissons
 Expectation-Maximization for Estimating Parameters for a Mixture of Poissons Brandon Maone Department of Computer Science University of Hesini February 18, 2014 Abstract This document derives, in excrutiating
Expectation-Maximization for Estimating Parameters for a Mixture of Poissons Brandon Maone Department of Computer Science University of Hesini February 18, 2014 Abstract This document derives, in excrutiating
Count-Min Sketches for Estimating Password Frequency within Hamming Distance Two
 Count-Min Sketches for Estimating Password Frequency within Hamming Distance Two Leah South and Dougas Stebia Schoo of Mathematica Sciences, Queensand University of Technoogy, Brisbane, Queensand, Austraia
Count-Min Sketches for Estimating Password Frequency within Hamming Distance Two Leah South and Dougas Stebia Schoo of Mathematica Sciences, Queensand University of Technoogy, Brisbane, Queensand, Austraia
17 Lecture 17: Recombination and Dark Matter Production
 PYS 652: Astrophysics 88 17 Lecture 17: Recombination and Dark Matter Production New ideas pass through three periods: It can t be done. It probaby can be done, but it s not worth doing. I knew it was
PYS 652: Astrophysics 88 17 Lecture 17: Recombination and Dark Matter Production New ideas pass through three periods: It can t be done. It probaby can be done, but it s not worth doing. I knew it was
Scalable Spectrum Allocation for Large Networks Based on Sparse Optimization
 Scaabe Spectrum ocation for Large Networks ased on Sparse Optimization innan Zhuang Modem R&D Lab Samsung Semiconductor, Inc. San Diego, C Dongning Guo, Ermin Wei, and Michae L. Honig Department of Eectrica
Scaabe Spectrum ocation for Large Networks ased on Sparse Optimization innan Zhuang Modem R&D Lab Samsung Semiconductor, Inc. San Diego, C Dongning Guo, Ermin Wei, and Michae L. Honig Department of Eectrica
Lecture Note 3: Stationary Iterative Methods
 MATH 5330: Computationa Methods of Linear Agebra Lecture Note 3: Stationary Iterative Methods Xianyi Zeng Department of Mathematica Sciences, UTEP Stationary Iterative Methods The Gaussian eimination (or
MATH 5330: Computationa Methods of Linear Agebra Lecture Note 3: Stationary Iterative Methods Xianyi Zeng Department of Mathematica Sciences, UTEP Stationary Iterative Methods The Gaussian eimination (or
High Spectral Resolution Infrared Radiance Modeling Using Optimal Spectral Sampling (OSS) Method
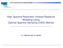 High Spectra Resoution Infrared Radiance Modeing Using Optima Spectra Samping (OSS) Method J.-L. Moncet and G. Uymin Background Optima Spectra Samping (OSS) method is a fast and accurate monochromatic
High Spectra Resoution Infrared Radiance Modeing Using Optima Spectra Samping (OSS) Method J.-L. Moncet and G. Uymin Background Optima Spectra Samping (OSS) method is a fast and accurate monochromatic
Absolute Value Preconditioning for Symmetric Indefinite Linear Systems
 MITSUBISHI ELECTRIC RESEARCH LABORATORIES http://www.mer.com Absoute Vaue Preconditioning for Symmetric Indefinite Linear Systems Vecharynski, E.; Knyazev, A.V. TR2013-016 March 2013 Abstract We introduce
MITSUBISHI ELECTRIC RESEARCH LABORATORIES http://www.mer.com Absoute Vaue Preconditioning for Symmetric Indefinite Linear Systems Vecharynski, E.; Knyazev, A.V. TR2013-016 March 2013 Abstract We introduce
Problem set 6 The Perron Frobenius theorem.
 Probem set 6 The Perron Frobenius theorem. Math 22a4 Oct 2 204, Due Oct.28 In a future probem set I want to discuss some criteria which aow us to concude that that the ground state of a sef-adjoint operator
Probem set 6 The Perron Frobenius theorem. Math 22a4 Oct 2 204, Due Oct.28 In a future probem set I want to discuss some criteria which aow us to concude that that the ground state of a sef-adjoint operator
Gauss Law. 2. Gauss s Law: connects charge and field 3. Applications of Gauss s Law
 Gauss Law 1. Review on 1) Couomb s Law (charge and force) 2) Eectric Fied (fied and force) 2. Gauss s Law: connects charge and fied 3. Appications of Gauss s Law Couomb s Law and Eectric Fied Couomb s
Gauss Law 1. Review on 1) Couomb s Law (charge and force) 2) Eectric Fied (fied and force) 2. Gauss s Law: connects charge and fied 3. Appications of Gauss s Law Couomb s Law and Eectric Fied Couomb s
VALIDATED CONTINUATION FOR EQUILIBRIA OF PDES
 SIAM J. NUMER. ANAL. Vo. 0, No. 0, pp. 000 000 c 200X Society for Industria and Appied Mathematics VALIDATED CONTINUATION FOR EQUILIBRIA OF PDES SARAH DAY, JEAN-PHILIPPE LESSARD, AND KONSTANTIN MISCHAIKOW
SIAM J. NUMER. ANAL. Vo. 0, No. 0, pp. 000 000 c 200X Society for Industria and Appied Mathematics VALIDATED CONTINUATION FOR EQUILIBRIA OF PDES SARAH DAY, JEAN-PHILIPPE LESSARD, AND KONSTANTIN MISCHAIKOW
A Bayesian Framework for Learning Rule Sets for Interpretable Classification
 Journa of Machine Learning Research 18 (2017) 1-37 Submitted 1/16; Revised 2/17; Pubished 8/17 A Bayesian Framework for Learning Rue Sets for Interpretabe Cassification Tong Wang Cynthia Rudin Finae Doshi-Veez
Journa of Machine Learning Research 18 (2017) 1-37 Submitted 1/16; Revised 2/17; Pubished 8/17 A Bayesian Framework for Learning Rue Sets for Interpretabe Cassification Tong Wang Cynthia Rudin Finae Doshi-Veez
Asymptotic Properties of a Generalized Cross Entropy Optimization Algorithm
 1 Asymptotic Properties of a Generaized Cross Entropy Optimization Agorithm Zijun Wu, Michae Koonko, Institute for Appied Stochastics and Operations Research, Caustha Technica University Abstract The discrete
1 Asymptotic Properties of a Generaized Cross Entropy Optimization Agorithm Zijun Wu, Michae Koonko, Institute for Appied Stochastics and Operations Research, Caustha Technica University Abstract The discrete
A proposed nonparametric mixture density estimation using B-spline functions
 A proposed nonparametric mixture density estimation using B-spine functions Atizez Hadrich a,b, Mourad Zribi a, Afif Masmoudi b a Laboratoire d Informatique Signa et Image de a Côte d Opae (LISIC-EA 4491),
A proposed nonparametric mixture density estimation using B-spine functions Atizez Hadrich a,b, Mourad Zribi a, Afif Masmoudi b a Laboratoire d Informatique Signa et Image de a Côte d Opae (LISIC-EA 4491),
Sequential Decoding of Polar Codes with Arbitrary Binary Kernel
 Sequentia Decoding of Poar Codes with Arbitrary Binary Kerne Vera Miosavskaya, Peter Trifonov Saint-Petersburg State Poytechnic University Emai: veram,petert}@dcn.icc.spbstu.ru Abstract The probem of efficient
Sequentia Decoding of Poar Codes with Arbitrary Binary Kerne Vera Miosavskaya, Peter Trifonov Saint-Petersburg State Poytechnic University Emai: veram,petert}@dcn.icc.spbstu.ru Abstract The probem of efficient
PHYS 110B - HW #1 Fall 2005, Solutions by David Pace Equations referenced as Eq. # are from Griffiths Problem statements are paraphrased
 PHYS 110B - HW #1 Fa 2005, Soutions by David Pace Equations referenced as Eq. # are from Griffiths Probem statements are paraphrased [1.] Probem 6.8 from Griffiths A ong cyinder has radius R and a magnetization
PHYS 110B - HW #1 Fa 2005, Soutions by David Pace Equations referenced as Eq. # are from Griffiths Probem statements are paraphrased [1.] Probem 6.8 from Griffiths A ong cyinder has radius R and a magnetization
A Statistical Framework for Real-time Event Detection in Power Systems
 1 A Statistica Framework for Rea-time Event Detection in Power Systems Noan Uhrich, Tim Christman, Phiip Swisher, and Xichen Jiang Abstract A quickest change detection (QCD) agorithm is appied to the probem
1 A Statistica Framework for Rea-time Event Detection in Power Systems Noan Uhrich, Tim Christman, Phiip Swisher, and Xichen Jiang Abstract A quickest change detection (QCD) agorithm is appied to the probem
Automobile Prices in Market Equilibrium. Berry, Pakes and Levinsohn
 Automobie Prices in Market Equiibrium Berry, Pakes and Levinsohn Empirica Anaysis of demand and suppy in a differentiated products market: equiibrium in the U.S. automobie market. Oigopoistic Differentiated
Automobie Prices in Market Equiibrium Berry, Pakes and Levinsohn Empirica Anaysis of demand and suppy in a differentiated products market: equiibrium in the U.S. automobie market. Oigopoistic Differentiated
Testing for the Existence of Clusters
 Testing for the Existence of Custers Caudio Fuentes and George Casea University of Forida November 13, 2008 Abstract The detection and determination of custers has been of specia interest, among researchers
Testing for the Existence of Custers Caudio Fuentes and George Casea University of Forida November 13, 2008 Abstract The detection and determination of custers has been of specia interest, among researchers
<C 2 2. λ 2 l. λ 1 l 1 < C 1
 Teecommunication Network Contro and Management (EE E694) Prof. A. A. Lazar Notes for the ecture of 7/Feb/95 by Huayan Wang (this document was ast LaT E X-ed on May 9,995) Queueing Primer for Muticass Optima
Teecommunication Network Contro and Management (EE E694) Prof. A. A. Lazar Notes for the ecture of 7/Feb/95 by Huayan Wang (this document was ast LaT E X-ed on May 9,995) Queueing Primer for Muticass Optima
Coded Caching for Files with Distinct File Sizes
 Coded Caching for Fies with Distinct Fie Sizes Jinbei Zhang iaojun Lin Chih-Chun Wang inbing Wang Department of Eectronic Engineering Shanghai Jiao ong University China Schoo of Eectrica and Computer Engineering
Coded Caching for Fies with Distinct Fie Sizes Jinbei Zhang iaojun Lin Chih-Chun Wang inbing Wang Department of Eectronic Engineering Shanghai Jiao ong University China Schoo of Eectrica and Computer Engineering
On Non-Optimally Expanding Sets in Grassmann Graphs
 ectronic Cooquium on Computationa Compexity, Report No. 94 (07) On Non-Optimay xpanding Sets in Grassmann Graphs Irit Dinur Subhash Khot Guy Kinder Dor Minzer Mui Safra Abstract The paper investigates
ectronic Cooquium on Computationa Compexity, Report No. 94 (07) On Non-Optimay xpanding Sets in Grassmann Graphs Irit Dinur Subhash Khot Guy Kinder Dor Minzer Mui Safra Abstract The paper investigates
Nearly Optimal Constructions of PIR and Batch Codes
 arxiv:700706v [csit] 5 Jun 07 Neary Optima Constructions of PIR and Batch Codes Hia Asi Technion - Israe Institute of Technoogy Haifa 3000, Israe shea@cstechnionaci Abstract In this work we study two famiies
arxiv:700706v [csit] 5 Jun 07 Neary Optima Constructions of PIR and Batch Codes Hia Asi Technion - Israe Institute of Technoogy Haifa 3000, Israe shea@cstechnionaci Abstract In this work we study two famiies
A MODEL FOR ESTIMATING THE LATERAL OVERLAP PROBABILITY OF AIRCRAFT WITH RNP ALERTING CAPABILITY IN PARALLEL RNAV ROUTES
 6 TH INTERNATIONAL CONGRESS OF THE AERONAUTICAL SCIENCES A MODEL FOR ESTIMATING THE LATERAL OVERLAP PROBABILITY OF AIRCRAFT WITH RNP ALERTING CAPABILITY IN PARALLEL RNAV ROUTES Sakae NAGAOKA* *Eectronic
6 TH INTERNATIONAL CONGRESS OF THE AERONAUTICAL SCIENCES A MODEL FOR ESTIMATING THE LATERAL OVERLAP PROBABILITY OF AIRCRAFT WITH RNP ALERTING CAPABILITY IN PARALLEL RNAV ROUTES Sakae NAGAOKA* *Eectronic
VALIDATED CONTINUATION FOR EQUILIBRIA OF PDES
 VALIDATED CONTINUATION FOR EQUILIBRIA OF PDES SARAH DAY, JEAN-PHILIPPE LESSARD, AND KONSTANTIN MISCHAIKOW Abstract. One of the most efficient methods for determining the equiibria of a continuous parameterized
VALIDATED CONTINUATION FOR EQUILIBRIA OF PDES SARAH DAY, JEAN-PHILIPPE LESSARD, AND KONSTANTIN MISCHAIKOW Abstract. One of the most efficient methods for determining the equiibria of a continuous parameterized
4 1-D Boundary Value Problems Heat Equation
 4 -D Boundary Vaue Probems Heat Equation The main purpose of this chapter is to study boundary vaue probems for the heat equation on a finite rod a x b. u t (x, t = ku xx (x, t, a < x < b, t > u(x, = ϕ(x
4 -D Boundary Vaue Probems Heat Equation The main purpose of this chapter is to study boundary vaue probems for the heat equation on a finite rod a x b. u t (x, t = ku xx (x, t, a < x < b, t > u(x, = ϕ(x
NEW DEVELOPMENT OF OPTIMAL COMPUTING BUDGET ALLOCATION FOR DISCRETE EVENT SIMULATION
 NEW DEVELOPMENT OF OPTIMAL COMPUTING BUDGET ALLOCATION FOR DISCRETE EVENT SIMULATION Hsiao-Chang Chen Dept. of Systems Engineering University of Pennsyvania Phiadephia, PA 904-635, U.S.A. Chun-Hung Chen
NEW DEVELOPMENT OF OPTIMAL COMPUTING BUDGET ALLOCATION FOR DISCRETE EVENT SIMULATION Hsiao-Chang Chen Dept. of Systems Engineering University of Pennsyvania Phiadephia, PA 904-635, U.S.A. Chun-Hung Chen
DIGITAL FILTER DESIGN OF IIR FILTERS USING REAL VALUED GENETIC ALGORITHM
 DIGITAL FILTER DESIGN OF IIR FILTERS USING REAL VALUED GENETIC ALGORITHM MIKAEL NILSSON, MATTIAS DAHL AND INGVAR CLAESSON Bekinge Institute of Technoogy Department of Teecommunications and Signa Processing
DIGITAL FILTER DESIGN OF IIR FILTERS USING REAL VALUED GENETIC ALGORITHM MIKAEL NILSSON, MATTIAS DAHL AND INGVAR CLAESSON Bekinge Institute of Technoogy Department of Teecommunications and Signa Processing
Ant Colony Algorithms for Constructing Bayesian Multi-net Classifiers
 Ant Coony Agorithms for Constructing Bayesian Muti-net Cassifiers Khaid M. Saama and Aex A. Freitas Schoo of Computing, University of Kent, Canterbury, UK. {kms39,a.a.freitas}@kent.ac.uk December 5, 2013
Ant Coony Agorithms for Constructing Bayesian Muti-net Cassifiers Khaid M. Saama and Aex A. Freitas Schoo of Computing, University of Kent, Canterbury, UK. {kms39,a.a.freitas}@kent.ac.uk December 5, 2013
Approximate Bandwidth Allocation for Fixed-Priority-Scheduled Periodic Resources (WSU-CS Technical Report Version)
 Approximate Bandwidth Aocation for Fixed-Priority-Schedued Periodic Resources WSU-CS Technica Report Version) Farhana Dewan Nathan Fisher Abstract Recent research in compositiona rea-time systems has focused
Approximate Bandwidth Aocation for Fixed-Priority-Schedued Periodic Resources WSU-CS Technica Report Version) Farhana Dewan Nathan Fisher Abstract Recent research in compositiona rea-time systems has focused
Coupling of LWR and phase transition models at boundary
 Couping of LW and phase transition modes at boundary Mauro Garaveo Dipartimento di Matematica e Appicazioni, Università di Miano Bicocca, via. Cozzi 53, 20125 Miano Itay. Benedetto Piccoi Department of
Couping of LW and phase transition modes at boundary Mauro Garaveo Dipartimento di Matematica e Appicazioni, Università di Miano Bicocca, via. Cozzi 53, 20125 Miano Itay. Benedetto Piccoi Department of
Partial permutation decoding for MacDonald codes
 Partia permutation decoding for MacDonad codes J.D. Key Department of Mathematics and Appied Mathematics University of the Western Cape 7535 Bevie, South Africa P. Seneviratne Department of Mathematics
Partia permutation decoding for MacDonad codes J.D. Key Department of Mathematics and Appied Mathematics University of the Western Cape 7535 Bevie, South Africa P. Seneviratne Department of Mathematics
8 Digifl'.11 Cth:uits and devices
 8 Digif'. Cth:uits and devices 8. Introduction In anaog eectronics, votage is a continuous variabe. This is usefu because most physica quantities we encounter are continuous: sound eves, ight intensity,
8 Digif'. Cth:uits and devices 8. Introduction In anaog eectronics, votage is a continuous variabe. This is usefu because most physica quantities we encounter are continuous: sound eves, ight intensity,
SEMINAR 2. PENDULUMS. V = mgl cos θ. (2) L = T V = 1 2 ml2 θ2 + mgl cos θ, (3) d dt ml2 θ2 + mgl sin θ = 0, (4) θ + g l
 Probem 7. Simpe Penduum SEMINAR. PENDULUMS A simpe penduum means a mass m suspended by a string weightess rigid rod of ength so that it can swing in a pane. The y-axis is directed down, x-axis is directed
Probem 7. Simpe Penduum SEMINAR. PENDULUMS A simpe penduum means a mass m suspended by a string weightess rigid rod of ength so that it can swing in a pane. The y-axis is directed down, x-axis is directed
SUPPLEMENTARY MATERIAL TO INNOVATED SCALABLE EFFICIENT ESTIMATION IN ULTRA-LARGE GAUSSIAN GRAPHICAL MODELS
 ISEE 1 SUPPLEMENTARY MATERIAL TO INNOVATED SCALABLE EFFICIENT ESTIMATION IN ULTRA-LARGE GAUSSIAN GRAPHICAL MODELS By Yingying Fan and Jinchi Lv University of Southern Caifornia This Suppementary Materia
ISEE 1 SUPPLEMENTARY MATERIAL TO INNOVATED SCALABLE EFFICIENT ESTIMATION IN ULTRA-LARGE GAUSSIAN GRAPHICAL MODELS By Yingying Fan and Jinchi Lv University of Southern Caifornia This Suppementary Materia
General Certificate of Education Advanced Level Examination June 2010
 Genera Certificate of Education Advanced Leve Examination June 2010 Human Bioogy HBI6T/P10/task Unit 6T A2 Investigative Skis Assignment Task Sheet The effect of temperature on the rate of photosynthesis
Genera Certificate of Education Advanced Leve Examination June 2010 Human Bioogy HBI6T/P10/task Unit 6T A2 Investigative Skis Assignment Task Sheet The effect of temperature on the rate of photosynthesis
Paragraph Topic Classification
 Paragraph Topic Cassification Eugene Nho Graduate Schoo of Business Stanford University Stanford, CA 94305 enho@stanford.edu Edward Ng Department of Eectrica Engineering Stanford University Stanford, CA
Paragraph Topic Cassification Eugene Nho Graduate Schoo of Business Stanford University Stanford, CA 94305 enho@stanford.edu Edward Ng Department of Eectrica Engineering Stanford University Stanford, CA
Rate-Distortion Theory of Finite Point Processes
 Rate-Distortion Theory of Finite Point Processes Günther Koiander, Dominic Schuhmacher, and Franz Hawatsch, Feow, IEEE Abstract We study the compression of data in the case where the usefu information
Rate-Distortion Theory of Finite Point Processes Günther Koiander, Dominic Schuhmacher, and Franz Hawatsch, Feow, IEEE Abstract We study the compression of data in the case where the usefu information
The influence of temperature of photovoltaic modules on performance of solar power plant
 IOSR Journa of Engineering (IOSRJEN) ISSN (e): 2250-3021, ISSN (p): 2278-8719 Vo. 05, Issue 04 (Apri. 2015), V1 PP 09-15 www.iosrjen.org The infuence of temperature of photovotaic modues on performance
IOSR Journa of Engineering (IOSRJEN) ISSN (e): 2250-3021, ISSN (p): 2278-8719 Vo. 05, Issue 04 (Apri. 2015), V1 PP 09-15 www.iosrjen.org The infuence of temperature of photovotaic modues on performance
Two view learning: SVM-2K, Theory and Practice
 Two view earning: SVM-2K, Theory and Practice Jason D.R. Farquhar jdrf99r@ecs.soton.ac.uk Hongying Meng hongying@cs.york.ac.uk David R. Hardoon drh@ecs.soton.ac.uk John Shawe-Tayor jst@ecs.soton.ac.uk
Two view earning: SVM-2K, Theory and Practice Jason D.R. Farquhar jdrf99r@ecs.soton.ac.uk Hongying Meng hongying@cs.york.ac.uk David R. Hardoon drh@ecs.soton.ac.uk John Shawe-Tayor jst@ecs.soton.ac.uk
Committed MPC. Maliciously Secure Multiparty Computation from Homomorphic Commitments. 1 Introduction
 Committed MPC Maiciousy Secure Mutiparty Computation from Homomorphic Commitments Tore K. Frederiksen 1, Benny Pinkas 2, and Avishay Yanai 2 1 Security Lab, Aexandra Institute, Denmark 2 Department of
Committed MPC Maiciousy Secure Mutiparty Computation from Homomorphic Commitments Tore K. Frederiksen 1, Benny Pinkas 2, and Avishay Yanai 2 1 Security Lab, Aexandra Institute, Denmark 2 Department of
THE REACHABILITY CONES OF ESSENTIALLY NONNEGATIVE MATRICES
 THE REACHABILITY CONES OF ESSENTIALLY NONNEGATIVE MATRICES by Michae Neumann Department of Mathematics, University of Connecticut, Storrs, CT 06269 3009 and Ronad J. Stern Department of Mathematics, Concordia
THE REACHABILITY CONES OF ESSENTIALLY NONNEGATIVE MATRICES by Michae Neumann Department of Mathematics, University of Connecticut, Storrs, CT 06269 3009 and Ronad J. Stern Department of Mathematics, Concordia
General Certificate of Education Advanced Level Examination June 2010
 Genera Certificate of Education Advanced Leve Examination June 2010 Human Bioogy HBI6T/Q10/task Unit 6T A2 Investigative Skis Assignment Task Sheet The effect of using one or two eyes on the perception
Genera Certificate of Education Advanced Leve Examination June 2010 Human Bioogy HBI6T/Q10/task Unit 6T A2 Investigative Skis Assignment Task Sheet The effect of using one or two eyes on the perception
Fast Blind Recognition of Channel Codes
 Fast Bind Recognition of Channe Codes Reza Moosavi and Erik G. Larsson Linköping University Post Print N.B.: When citing this work, cite the origina artice. 213 IEEE. Persona use of this materia is permitted.
Fast Bind Recognition of Channe Codes Reza Moosavi and Erik G. Larsson Linköping University Post Print N.B.: When citing this work, cite the origina artice. 213 IEEE. Persona use of this materia is permitted.
c 2007 Society for Industrial and Applied Mathematics
 SIAM REVIEW Vo. 49,No. 1,pp. 111 1 c 7 Society for Industria and Appied Mathematics Domino Waves C. J. Efthimiou M. D. Johnson Abstract. Motivated by a proposa of Daykin [Probem 71-19*, SIAM Rev., 13 (1971),
SIAM REVIEW Vo. 49,No. 1,pp. 111 1 c 7 Society for Industria and Appied Mathematics Domino Waves C. J. Efthimiou M. D. Johnson Abstract. Motivated by a proposa of Daykin [Probem 71-19*, SIAM Rev., 13 (1971),
BP neural network-based sports performance prediction model applied research
 Avaiabe onine www.jocpr.com Journa of Chemica and Pharmaceutica Research, 204, 6(7:93-936 Research Artice ISSN : 0975-7384 CODEN(USA : JCPRC5 BP neura networ-based sports performance prediction mode appied
Avaiabe onine www.jocpr.com Journa of Chemica and Pharmaceutica Research, 204, 6(7:93-936 Research Artice ISSN : 0975-7384 CODEN(USA : JCPRC5 BP neura networ-based sports performance prediction mode appied
