Advanced statistical methods for analysis of NDE data
|
|
|
- Flora Linette Haynes
- 6 years ago
- Views:
Transcription
1 Retrospective Theses and Dissertations 2006 Advanced statistical methods for analysis of NDE data Yurong Wang Iowa State University Follow this and additional works at: Part of the Statistics and Probability Commons Recommended Citation Wang, Yurong, "Advanced statistical methods for analysis of NDE data " (2006). Retrospective Theses and Dissertations This Dissertation is brought to you for free and open access by Iowa State University Digital Repository. It has been accepted for inclusion in Retrospective Theses and Dissertations by an authorized administrator of Iowa State University Digital Repository. For more information, please contact
2 Advanced statistical methods for analysis of NDE data by Yurong Wang A dissertation submitted to the graduate faculty in partial fulfillment of the requirements for the degree of DOCTOR OF PHILOSOPHY Major: Statistics Program of Study Committee: William Q. Meeker, Jr., Major Professor Bruce R. Thompson Huaiqing Wu Ranjan Maitra Petrutza C. Caragea Iowa State University Ames, Iowa 2006 Copyright Yurong Wang, All rights reserved.
3 UMI Number: INFORMATION TO USERS The quality of this reproduction is dependent upon the quality of the copy submitted. Broken or indistinct print, colored or poor quality illustrations and photographs, print bleed-through, substandard margins, and improper alignment can adversely affect reproduction. In the unlikely event that the author did not send a complete manuscript and there are missing pages, these will be noted. Also, if unauthorized copyright material had to be removed, a note will indicate the deletion. UMI UMI Microform Copyright 2006 by ProQuest Information and Learning Company. All rights reserved. This microform edition is protected against unauthorized copying under Title 17, United States Code. ProQuest Information and Learning Company 300 North Zeeb Road P.O. Box 1346 Ann Arbor, Ml
4 ii Graduate College Iowa State University This is to certify that the doctoral dissertation of Yurong Wang has met the dissertation requirements of Iowa State University Signature was redacted for privacy. Committee Member Signature was redacted for privacy. Committee Member Signature was redacted for privacy. Committee Member Signature was redacted for privacy. Committee Member Signature was redacted for privacy. Major Professor Signature was redacted for privacy.
5 iii TABLE OF CONTENTS LIST OF TABLES LIST OF FIGURES ACKNOWLEDGEMENT ABSTRACT vii viii x xi CHAPTER 1. GENERAL INTRODUCTION Background Motivation Bivariate à versus a Method Allowing Censoring and Truncation à versus a Method Capable of Adjusting Flaw Sizing Errors Variance Components Analysis of NDE Inspections Dissertation Organization 6 Reference 7 CHAPTER 2. ASSESSMENT OF NONDESTRUCTIVE PROBABILITY OF DETECTION FOR INSPECTION WITH A BIVARIATE RESPONSE Introduction Background Related Work Motivation Overview Experimental Data Contaminated Billet Study Ultrasonic Inspection Methods 13
6 iv CBS Inspection Data The à versus a Method Model POD The Extended â versus a Method Extending the Classical â versus a Method Maximum Likelihood Analysis with Censoring and Truncation POD for the Bivariate â versus a Model Fitting the Bivariate â versus a Model to the CBS Multizone Data The CBS Multizone Inspection Data ML Estimates for the Bivariate Model Parameters Multizone POD The Bivariate â versus a Model for Atypical Misses with Accommodation Typical and Atypical Misses Likelihood for the Bivariate Response Model with Accommodation Terms Accommodation Models POD for the Bivariate â versus a Model with Atypical Miss Model Accommodation Terms Analyzing the Conventional CBS Data Using the Extended â versus a Model with Atypical Miss Model Accommodation Terms Results from Fitting the Models Comparison of the Models The POD Estimation for the CBS Conventional Study Concluding Remarks and Areas for Future Work Acknowledgements 40 Reference 40 CHAPTER 3. A STATISTICAL MODEL TO ADJUST FOR FLAW-SIZING ERRORS IN THE ESTIMATION OF PROBABILITY OF DETECTION Introduction 44
7 V Background Related Work and Motivation Overview The Classical Measurement Error Model General Errors-in-Variables (GEV) Model General Maximum Likelihood Approach for Estimation The Flaw Area Measurement Process The Burkel Measurement Error Model The Burkel Measurement Error Model Maximum Likelihood Estimation for the Burkel Model Simulation of the Burkel Model GEV Method Application to Simulated Inspection Data The Geometrical Measurement Error Model The Geometrical Measurement Error Model Maximum Likelihood Estimation for the Geometrical Model Simulation of the Geometrical Model GEV Method Application to the Simulated Inspection Data Concluding Remarks and Future Research Work Acknowledgements 70 Reference 70 CHAPTER 4. APPLICATION OF STATISTICAL METHODS FOR AS SESSMENT OF COMPONENTS OF VARIANCE IN PROBABILITY OF DETECTION MODELS Introduction Background and Motivation Related Work Overview Classical Mixed Effects Model Experimental Study 77
8 vi Experimental Design Inspection Data Mixed Effects Model Bayesian Model Bayesian Hierarchical Model Prior Distributions Posterior Distributions Evaluation of Posterior Distributions via Simulation Simulation MCMC and WinBUGS Full Conditional Distribution and Gibbs Sampling in WinBUGS Bayesian Application for the Simulation Study Model WinBUGS Inputs Simulation Data Analysis Bayesian Approach for the Experimental Study Concluding Remarks and Areas for Future Research Acknowledgements 94 Reference 94 CHAPTER 5. CONCLUSIONS 96 APPENDIX A. SUMMARY OF CBS DATA 98 APPENDIX B. WINBUGS PROGRAM FOR NDE VARIANCE COMPO NENT ANALYSIS AND PART OF INSPECTION DATA 101
9 vii LIST OF TABLES Table Multi Data ML Estimation Results under Bivariate â versus a Model 25 Table Conventional Data ML Estimation Results under the Bivariate â versus a Model with Accommodation Model 1 35 Table Conventional Data ML Estimation Results under the Bivariate â versus a Model with Accommodation Model 2 36 Table Conventional Data ML Estimation Results under the Bivariate â versus a Model with Accommodation Model 3 36 Table 3.1 Example Parameter Estimates for the Geometrical Model 68 Table 4.1 Parameter Estimation for the Simulated MultiZone Inspection 92 Table 4.2 Parameter Estimation for the Multizone Inspection Experiment 92 Table A.l 1995 CBS Multizone Inspection Data 99 Table A CBS Conventional Inspection Data 100 Table B.l Part of Variability Study Inspection Data 106
10 viii LIST OF FIGURES Figure 2.1 Simulated data used to illustrate bivariate left censoring 17 Figure 2.2 Contribution of censored data to likelihood in bivariate model (Continued). 20 Figure 2.3 Contribution of censored data to likelihood in bivariate model 21 Figure 2.4 Plot illustrating the bivariate à vs. a model for CBS multizone 1995 data. 26 Figure 2.5 POD plot of bivariate â vs. a model for CBS multizone 1995 data Figure 2.6 POD plot of hit/miss method for CBS conventional normal and angle 1994 data and POD estimated from a logistic regression model 28 Figure 2.7 Censored data due to typical and atypical misses 30 Figure 2.8 Contribution of atypical miss data to likelihood in bivariate model Figure 2.9 POD and probability of atypical misses for bivariate model for CBS 1994 conventional inspection data and POD when atypical misses are not eliminated 38 Figure 2.10 Probability of atypical miss for bivariate model for CBS 1994 conventional inspection data and POD when atypical misses are eliminated Figure 3.1 Simulated data with/without measurement error 50 Figure 3.2 Effect of measurement error on the regression 51 Figure 3.3 Effect of the standard deviation on measurement error using (3q = 6.3, (3\ = 0.5, <7 e = 0.44, MinFlawRatio = Figure 3.4 Comparison of the naive and GEV methods for different values of the standard deviation of measurement error 55 Figure 3.5 The density plot of the flaw Area ratio for different standard deviation of measurement error 56
11 ix Figure 3.6 Effect of the minimum flaw area ratio on measurement error 58 Figure 3.7 The density plot of the flaw area ratio at different minimum flaw area ratio 59 Figure 3.8 Comparison of the naive and the GEV methods for different values of minimum flaw ratio exp(5i) 60 Figure 3.9 Plot showing simulated UT inspection data with measurement error and both naive and GEV regression lines 62 Figure 3.10 POD plots for the conventional inspection using simulated data 62 Figure 3.11 Simulated data with/without measurement error for geometrical model. 67 Figure 3.12 Simulated data with/without measurement error for geometrical model. 67 Figure 3.13 Plot showing simulated UT inspection data with measurement error under geometrical measurement error model and both naive and GEV regression lines 69 Figure 3.14 POD plots for the conventional inspection using simulated data under geometrical measurement error model 69 Figure 4.1 Measured ultrasonic responses from synthetic hard alpha flaws 75 Figure 4.2 Plot of the multizone amplitude inspection data. Note the saturated observations at 100% FSE 79 Figure 4.3 Plot of the three thinned MCMC samples for four of the unknown parameters 90 Figure 4.4 The proportion of variation accounted for by sources 93
12 X ACKNOWLEDGEMENT I would like to express my deep gratitude for my advisor, Professor William Q. Meeker, Jr., who has guided, encouraged and supported me in many different ways during my Ph.D. study. With his excellent guidance and helpful suggestions, my research has come so far. I am very grateful that I had the opportunity to study under his supervision. I would also like to thank Dr. Bruce R. Thompson, Dr. Huaiqing Wu, Dr. Ranjan Maitra, Dr. Petrutza C. Caragea for serving on my thesis committee and for many helpful comments and guidance on my research. I am also grateful to many other people at the center for NDE, especially Ms. Lisa J. H. Brasche, Dr. Thomas Chiou, and Mr. Rick Lopez for their help during my research. I want to take this opportunity to thank many other people I have worked with. They have extended my knowledge and kindly offered me various help. Only a few are named here: Ms. Angela Zuo, Mr. Chunwang Gao, Mr. Zhigang Zhou, Ms. Xia Xu and Mr. Gabriel Camano. I wish them all the best. Last but not least, I would like to thank my husband, Linxiao Yu, and my daughter, Julia, for their continuous love and support. Without their support I would not have been able to complete this work. Very special thank you must go to my parents, my older sister for their utmost supports and encouragements that have made me go this far. Also I would like to thank my parents-in-law for their taking care of Julia during my thesis work.
13 xi ABSTRACT Nondestructive Evaluation (NDE) uses noninvasive techniques to determine the integrity of a material, component or structure. In modern industry, NDE methods are often used in quality control and quality assurance. For example, ultrasonic inspection is a routine NDE method to detect flaws/defects in rotating components of jet engines. However, in any NDE system, there are random factors that can affect the performance and reliability of the system. Probability of detection (POD) is an important metric for quantifying NDE capability and reliability. The most commonly used POD assessment method is known as the â versus a method. However, the standard â versus a method can not be directly applied to some situations encountered in modern NDE operations. The objective of this research is to 1) extend the â versus a method to handle bivariate response allowing for data censoring and truncation. 2) extend the standard method to adjust for bias in POD estimates due to flaw sizing errors. 3) develop a more complete understanding of inspection variability by using statistical models to identify and quantify the variance components in NDE operations. In Chapter 1, the standard â versus a method is extended to handle bivariate responses. The method of maximum likelihood (ML) estimation is used to deal with data censoring and truncation. To estimate the POD of a bivariate-response NDE system, a dual detection criterion is defined. The extended model is used to analyze two sets of available inspection data. In one set of inspection data, there were more flaw misses that could not be directly accounted for by the bivariate â versus a model. Extra modelling efforts were made to accommodate these flaw misses. The standard ô versus a method assumes that the flaw sizes are known without error. However, the true flaw size is usually not known exactly due to cost constraints. The measurement errors in flaw sizing will bias the POD estimates. In Chapter 2 of this thesis, we develop two
14 xii statistical models for adjusting for bias in POD estimates that is caused by flaw sizing errors. The models are fitted by using the ML estimation method. We present the results of simulation studies that show how the use of our models will reduce flaw-sizing bias and we demonstrate the use of the methods with simulated inspection data based on the collected real inspection data. The model behind the standard à versus a method contains only one component of variance for the response. There are, however, many random factors introducing variability to NDE inspection. Excessive variability from various sources can degrade NDE inspection quality. There are strong needs to identify and quantify variability sources in NDE applications, as such information is needed to properly decide on strategies to reduce variability. In the Chapter 3 of this thesis, we develop the Bayesian hierarchial model to identify and quantify the variance components of inspection in the presence of data censoring. The Bayesian approach is demonstrated with simulated data and experimental data. The computations use MCMC simulation implemented in the in WinBUGS software.
15 1 CHAPTER 1. GENERAL INTRODUCTION 1.1 Background Nondestructive Evaluation (NDE) uses noninvasive techniques to determine the integrity of a material, component or structure or quantitatively measure some characteristic of an object. In modern industries, NDE is an important technique for quality control and assurance. It can be used to determine properties of materials, detect flaws in parts, or even classify flaws by size, shape and location (Olin and Meeker, 1996). Compared with the traditional destructive testing methods, it has the advantages of much lower cost and good repeatability. For example, to evaluate an anomaly within a critical component in a jet engine, the traditional metallographic examination method has to destroy the sample unit. Also, because of the destructive nature of this method, the destructive evaluation has no repeatability. NDE methods, on the other hand, do not destroy the unit, are relatively inexpensive, and are repeatable. With these advantages, NDE is widely used in the industries and plays an important role in: Process quality control Sample inspection of newly manufactured products to ensure quality Assuring that in-service parts are working safely and to increase system reliability Life extension of expensive components in systems such as aircraft and power generation equipment. In any nondestructive inspection process, however, there are many factors that can affect the performance of inspection system. Examples of sources of variability include system alignment, material properties, flaw geometry, flaw orientation, operator differences, and so on. These
16 2 factors can be partitioned into three groups: factors relating to the inspection system Xg Ys> factors relating to the material x PART, and factors relating to the flaw itself (xplaw ) 1. The factors x SYg relating to the NDE inspection system include the transducer parameters, scan resolution (mechanical increment of the scanning system in X and Y dimensions), system alignment/angulations, as well as operators in the experiment. 2. The factors z PART relating to the part to be inspected include part geometry (particularly the degree of curvature at the inspection location), material microstructure and anisotropy, surface roughness, etc. 3. The factors Eflaw characterizing a flaw include flaw size, shape, orientation, depth and density (e.g., percent nitrogen and degree of cracking and voiding for a hard alpha inclusions), etc. All these factors contribute to inspection variability. This variability leads to the need to use a probabilistic characterization of NDE inspection capability. Probability of detection (POD) is an important metric for quantifying NDE capability caused by such uncertainty and it is an essential part of NDE applications. POD related research is a relatively new topic in the NDE field. Berens (1989) described how methods for analyzing NDE inspection capability data have undergone a considerable evolution since the 1970's. Initially, a constant probability of detection of all flaws of a given size was postulated, and binomial distribution methods using hit-miss data were used to estimate the probability. "Hit" means that an NDE system response was interpreted as having detected a flaw while "Miss" means that an NDE system response was interpreted as not having detected a flaw. A more appropriate hit-miss analysis based on a binary regression versus flaw size was developed subsequently and was illustrated in various places including MIL-HDBK-1823 (1999). For a general treatment of binary regression, see Agresti (1990). In the early 1980's, other methods of estimating POD were developed for surface defects with more general characteristics, using more advanced statistical methods. One widely-used method is known as the "ô versus a" method. In NDE work, a is used to denote flaw size. The flaw-response signal is often translated into an estimate of flaw size and this leads to the
17 3 use of "â" to denote the flaw-signal response, even for applications where such a translation is not used. Data with this nature are called "â versus a" data. Berens (1989) found that a natural logarithmic transformation on the response, ô and the flaw size, a, data often obeys the commonly used normal distribution simple linear regression model. Depending on the character of the NDE system, some data may be right censored due to saturation (e.g., a signal exceeding 100% full screen height on an oscilloscope). If the signal is below the noise level, it is a miss. If it is known that there was a particular miss (e.g., a seeded flaw that was not detected), the observation is left censored. Annis and others at Pratt and Whitney (private communication) extended the â versus a method to allow for censoring and this approach is also described in MIL-HDBK-1823 (1999). When there is a possibility that there are misses that are not recorded and remain unknown (as in field-find data), the finds can be viewed as having come from a left-truncated distribution and are said to be "left truncated data." Burkel, Sturges, Turker and Gilmore (1996) extended the â versus a method to allow for censoring and truncation. For truncated or censored data, ordinary least square are not appropriate. Maximum likelihood (ML) methods have capability of dealing with such data issues. Meeker and Escobar (1998) describe statistical methods to analyze censored or truncated data. Burkel, Sturges, Tucker and Gilmore (1996) described the "effective reflectivity" or "Re" method. This method can be shown to be equivalent to â versus a method except that regression slope is constrained to be 1 (which has a physical basis for certain applications). 1.2 Motivation The objective of this research is to provide statistical methods that can be used to help improve the NDE reliability by Extending the standard â versus a method for some advanced NDE applications; Identifying and quantifying the variance components of NDE inspection. Specifically, this thesis covers the following three research topics: extending the standard "ô versus o" method for bivariate responses encountered in modern NDE inspection systems;
18 4 developing statistical models to adjust the bias in POD estimates caused by flaw sizing errors; developing and illustrating statistical methods to identify and quantify the variance components of NDE process. The detailed discussion for each research topic is given below Bivariate â versus a Method Allowing Censoring and Truncation Today, for the case of Hit/Miss data, POD is usually estimated by using binary regression. The â versus a method is used when data provide signal strength information. The standard â versus a method assumes a univariate response. In modern NDE operations, however, a bivariate response results from some inspection methods. To estimate the POD of these new NDE inspection methods, an extended model is needed to handle the bivariate responses. This part of our research is to extend the standard â versus a method to handle such bivariate responses. The â versus a method can be extended to handle a bivariate response by using bivariate regression. The bivariate regression model assumes an underlying joint distribution in which the means of the marginal logarithm of bivariate signal values depend on flaw size, but the standard deviations and correlation of bivariate response do not depend on flaw size. Data censoring and truncation also arise in NDE inspection systems having bivariate responses. Left-censored observations occur when a known flaw is missed in inspection. That is, if the existence of a flaw is known and the value of the measurement is below the threshold, the flaw is said to have been missed. Right censoring occurs in NDE applications due to saturation (i.e., observations that are so large that they exceed the upper bound of the measuring device). Truncation is similar to but different from censoring. In NDE applications, truncation usually is left truncation due to field flaw misses. The extended â versus a method allows for data censoring and truncation. The method of maximum likelihood (ML) estimation is used to handle data censoring and truncation. ML estimation is preferred over other methods because it has good statistical prosperities (e.g., the invariance property) and some asymptotic optimality properties (e.g. minimum variance). As in the standard univariate method, detection criteria need to be specified to estimate the POD of a bivariate-response NDE system. We defined a dual detection criterion in the
19 5 extended model. Specifically, a detection can occur if either one of bivariate response exceeds its corresponding threshold. As examples of application, the extended model was used to analyze two sets of available inspection data in our research. One data set came from a conventional inspection and the other came from a relatively new multi-zone method of inspection. In the conventional inspection data, there were more misses than could be directly accounted for by the extended â versus a method. Extra modelling efforts were made to accommodate those data misses â versus a Method Capable of Adjusting Flaw Sizing Errors The â versus a method of analysis is widely used in the NDE field to estimate POD for various NDE inspection systems. The symbol "a" is used to denote flaw size. The flaw-response signal is often translated into an estimate of flaw size and this led to the use of the notation "ô" to denote the flaw-signal response. The basic idea behind the â versus a method is a simple linear regression with assumptions that the logarithm of â has a normal distribution with mean depending on flaw size and a constant standard deviation. If the â signal for a flaw is greater than the detection threshold, the flaw is detected, otherwise, it is missed. The standard â versus a method for POD computation assumes that the flaws in the available data have sizes that are known without error. Usually the true flaw size is not known exactly and must be inferred from some inexact method such as metallographic analysis based on only one or two slices through a flaw. Results in the classical statistical literature indicate that such errors-in-variables (EV) will bias the estimated regression coefficients. The presence of measurement errors will also affect the linear regression in POD computations. Fuller (1987) introduced classical measurement error model, investigated the effects of measurement error on the ordinary least squares estimators, and provided methods to do correction. Carroll, Ruppert and Stefanski (1995) extended these ideas to cover the nonlinear measurement error model and provided general approaches to solve measurement error problem. The effect of EV issues has not been studied in NDE applications before. The objective of this part of our research is to adapt the classical measurement error model to NDE applications and extend the standard â versus a method to
20 6 adjust for measurement error in flaw sizing. Based on the knowledge of the flaw sizing process (metallographic study), we developed two measurement error models: the Burkel model and a geometrical model. The two models allow for data truncation and censoring using ML estimation Variance Components Analysis of NDE Inspections As discussed before, there are several factors that can introduce variability into NDE inspection and thus affect the inspection performance. Improvement of inspection performance requires the identification and quantification of variability sources. This paper develops and illustrates the use of statistical methods that can be used to identify and quantify the variance components of NDE inspection in the presence of censoring and truncation. The experimental data used in this research were taken from a manufactured "block" of material containing seeded defects of known size and character. This block was inspected according to an experimental design that will capture all different sources of variability. We build the variability model for the experimental data. A Bayesian approach was used to analyze and quantify variability sources. The Bayesian approach can handle complicated problems of variance component analysis, even allowing for data censoring. Computations were done with the Winbugs software tools. Congdon (2003) illustrates the Bayesian approach to data analysis and modelling in various applications using WinBugs software. 1.3 Dissertation Organization This dissertation consists of 3 main chapters, preceded by the present general introduction and followed by a general conclusion. Each chapter corresponds to a to-be-submitted journal article. Chapter 1 describes an extension of the standard â versus a method for bivariate response encountered in modern NDE inspection system. Chapter 2 describes the development of advanced statistical methods to adjust for bias caused by flaw sizing errors. Chapter 3 develops and illustrates statistical methods to identify and quantify the variance components in NDE processes.
21 7 References Olin, B. D. and Meeker, W. Q. (1996), "Applications of Statistics in Nondestructive Evaluation," Technometrics 38, Berens, A. P. (1989), "NDE Reliability Data Analysis," Metals Handbook (9th ed., Vol. 17, Nondestructive Evaluation and Quality Control), Metals Park, OH: American Society for Metals pp MIL-HDBK-1823 (1999), Non-Destructive Evaluation System Reliability Assessment, Standardization Order Desk, Building 4D, 700 Roberts Avenue, Philadephia, PA Agresti, A. (1990), Categorical Data Analysis, New York: John Wiley. Burkel, R. H., Sturges, D. J., Tucker, W. T., and Gilmore, R. S. (1996), "Probability of Detection for Applied Ultrasonic Inspection," Review of Progress in Quantitative NDE, Vol. 15, edited by D. O. Thompson and D. E. Chimenti, Plenum Press, New York, NY, Meeker, W. Q., and Escobar, L. A. (1998), Statistical Methods for Reliability Data, New York: John Wiley & Sons. Fuller, W. A. (1987), Measurement Error Models, New York: Wiley. Carroll, R. J., Ruppert D., and Stefanski, L. A. (1995), Measurement Error in Nonlinear Models, London; New York, Chapman Hall. Congdon, P. (2003), Applied Bayesian Modelling, New York: John Wiley & Sons.
22 8 CHAPTER 2. ASSESSMENT OF NONDESTRUCTIVE PROBABILITY OF DETECTION FOR INSPECTION WITH A BIVARIATE RESPONSE A paper to be submitted to Technometrics Yurong Wang and William Meeker Department of Statistics Iowa State University Ames, IA Abstract Nondestructive evaluation (NDE) methods are used widely in modern industry to assure the integrity of critical system components. Examples include rotating components of jet engines and heat-transfer tubes in nuclear power plants. There is an important need to quantify the probability of detection (POD) for NDE applications in both production quality control and in-service inspection for expensive components that degrade over time. The standard method of estimating POD, known as â versus a, uses a linear regression relating NDE signal response to flaw or defect size. This paper extends this standard one-dimensional POD estimation method for bivariate responses. The extended methods allow for truncation and censoring encountered in many NDE applications. Atypical flaw misses in one of our NDE application examples could not be directly accounted for by the the extended ô versus a method. Extra modeling efforts were made to accommodate those flaw misses.
23 9 Key Words: Atypical flaw misses, Censoring, Nondestructive Evaluation (NDE), Probability of Detection (POD), Truncation
24 Introduction Background Nondestructive Evaluation (NDE) is an important technique for ensuring quality in certain industrial applications. It can be used to determine properties of material, detect flaws in components, or even classify flaws by size, shape and location (Olin and Meeker, 1996). Compared with the traditional destructive testing methods, it has the advantages of lower cost and good repeatability. For example, to evaluate an anomaly in a critical component in a jet engine, the traditional metallographic examination method has to destroy the component. NDE methods, on the other hand, do not destroy the unit, are relatively inexpensive, and are repeatable. Because of these advantages, NDE is widely used in certain industries and plays an important role in: Process quality control Sample inspection of newly manufactured products to ensure quality Assuring that in-service components are working safely and increase system reliability Life extension of expensive components in systems such as aircraft and power generation equipment. In nondestructive inspection processes, however, there are many factors that can affect the performance of inspection system, such as material properties, flaw geometry, flaw orientation, operators and so on. All these factors contribute to inspection variability that requires a probabilistic characterization of NDE inspection capability. Probability of detection (POD) is an important metric for quantifying NDE inspection capability and is an essential part of NDE applications Related Work Berens (1989) describes how methods for analyzing NDE reliability data underwent a considerable evolution between then and the 1970's. Initially, a constant probability of detection
25 11 of all flaws of a given size was postulated, and binomial distribution methods using hit-miss data were used to estimate the probability. A "hit" implies that an NDE system response was interpreted as having detected a flaw while a "miss" implies that an NDE system response was interpreted as not having detected a flaw. A more appropriate hit-miss analysis is based on a binary regression in which POD is modelled as a function of flaw size and is illustrated in various places including MIL-HDBK-1823 (1999). For a general treatment of binary regression, see Agresti (1990). In the early 1980's, other methods of estimating POD were developed for surface defects with more general characteristics, using more advanced statistical methods. One widely-used method is known as the "â versus a" method. In NDE applications, a is used to denote flaw size. The flaw-response signal is often translated into an estimate of flaw size and this led to the use of "â" to denote the flaw-signal response, even for applications where such a translation is not used. Berens (1989) found that with a natural logarithmic transformation on the response â and the flaw size a, data can often be described by the commonly used normal distribution simple linear regression model. Burkel, Sturges, Tucker, and Gilmore (1996) describe the "effective reflectivity" or "Re" method. This method can be shown to be equivalent to â versus a method when the regression slope is constrained to be 1. Depending on the character of the NDE system, some data may be right censored due to saturation (e.g., greater than 100% full screen height (FSB) on an oscilloscope). If the signal is below the noise level, it is a miss. If it is known that there was a particular miss (e.g., a seeded flaw that was not detected), the observation is left censored. Annis and others at Pratt and Whitney (private communication) extended the â versus a method to allow for censoring and this approach is also described in MIL-HDBK-1823 (1999). When there is a possibility that there are misses that are not recorded (as in field-find data), the finds can be viewed as having come from a left-truncated distribution and are said to be "left truncated data." Burkel, Sturges, Tucker, and Gilmore (1996) extended â versus a method to allow for truncation. For truncated or censored data, the ordinary least square method is not appropriate. Maximum likelihood (ML) methods have the capability of dealing with such data issues. Meeker and
26 12 Escobar (1998), for example, provided statistical methods to analyze data that are censored and truncated Motivation The standard â versus a method assumes a univariate response. In modern NDE operations, however, some inspection methods provide a bivariate response. This paper develops and illustrates bivariate regression models and estimation methods that also allow for truncation and censoring. In one of our applications of the bivariate response NDE model, we encountered misses that could not be directly accounted for by the extended method. We show how to include model terms to accommodate those misses Overview The remaining parts of this paper are organized as follows. Section 2 describes the FA A "Contaminated Billet Study (CBS)" that provided the data for our example and the motivation for this research. This section also describes the conventional and multizone inspection data that arose from these NDE ultrasonic studies. Section 3 reviews the univariate â versus a method. Section 4 presents the bivariate extension to the univariate â versus a method for estimating POD. Section 5 applies the bivariate â versus a model to the CBS multizone data. In the CBS conventional inspections, there were more misses than those could be accounted for directly by the â versus a method. In Section 6, we describe the use of accommodation model terms to handle the large number of misses. Section 7 applies the bivariate â versus a model with accommodation terms to conventional data. Section 8 gives conclusions and discussion about future research. 2.2 Experimental Data Contaminated Billet Study The safety of aircraft jet engines depends on the use of NDE inspection techniques for the detection of flaws in titanium alloys used in production of engine components. A major flaw
27 13 type of concern for titanium alloys used in production of jet engine fan discs is hard alpha defects. Hard alpha defects are more brittle than nominal material (CBS report, 2004) and can cause dangerous crack growth rates that have led to in-service disk failures. Because natural hard alpha flaws are very rare in rotor grade titanium, their availability for study and evaluation is limited. A melter, while producing titanium for a non-aerospace customer, found numerous natural hard alpha defects (a total 64 were detected) in 12 contaminated billets, from a single heat. The FAA purchased the 12 billets in 1994 in order to support NDE research efforts. FAAfunded inspection studies were conducted on the 12 contaminated billets in 1994 and In these studies, both conventional and multizone inspections were conducted Ultrasonic Inspection Methods In the conventional study, inspections were made with a 5-MHz longitudinal, cylindrically focused transducer at normal incidence (i.e., incident angle of 0 ) and a 5-MHz refracted longitudinal, spherically focused transducer at angle incidence (i.e., incident angle of 9.6 ) to produce 45 longitudinal wave. Bivariate responses were amplitude from the normal incidence transducer and the angle incidence transducer for each flaw. In the multizone study, separate 5-MHz bi-cylindrical focused transducers were used to cover five different depth zones. For each flaw, the multizone data has a bivariate responses: ultrasonic signal amplitude (in % full screen height or FSH)and signal to noise ratio (SNR) for each flaw CBS Inspection Data In the CBS study, to obtain the flaw morphology and area information, 10 of the 64 flaws were cut out and sectioned at 5-mil increments and studied metallographically. The flaw areas for the other flaws were estimated from multizone ultrasonic C-Scan images. In NDE applications involving actual field inspection, data can be censored (left or right) and/or left truncated. The multizone data in the CBS study are left truncated because there might have been missed flaws, but there is no information about the existence of such flaws is available. Based on the information from the multizone data, in the CBS conventional inspection, there was a large
28 14 number of flaw misses. The number of misses was so large that not all could be explained by the â versus a model. Such flaw misses might have different unknown causes. One possible cause is human factor mistakes. Because of this "referee" information provided in the multizone study, we assume that the conventional study data are not truncated. This is justified because the conventional truncation level, implied by the multizone truncation level, is small enough to ignore. The conventional data do have left censoring due to the misses and right censoring due to saturation. 2.3 The â versus a Method Model The ô versus a model, introduced in Section 4.1.2, can be expressed as: log(â) = Po + j3i log (a) + e, (2.1) where e has a normal distribution with mean 0 and variance a 2. According to Equation (2.1) and the linear property of normal distribution, log(â) has a normal distribution. Let y = log(â), then 2/~;V(/%+Alog(o),c^). (2.2) The ML estimates of /%, /?i, and a are typically used today in practice when there are data censoring and/or truncation (Burkel, Sturges, Tucker, and Gilmore, 1996) POD POD is the probability that the signal response â exceeds the threshold a TH. That is, POD(o) = Pr(â>2 ;o) 1 f /log(o ) -p Q-p 1 log(q) ^ where $ is the cumulative probability function of standard normal distribution (2.3) From Equa- tion (2.3), it is easy to see that
29 15 1. POD decreases as a TH increases, for a given flaw size a. 2. POD increases as flaw size a increases, for a given fixed threshold o TH. Based on the ML estimators of /3q, Pi, and a, the estimated POD is: PODia) = 1-$ (2.4) where /3q, (3\, and â are the ML estimates of (3q, /3i, and cr, respectively. 2.4 The Extended â versus a Method Extending the Classical â versus a Method The â versus a method can be extended to handle a bivariate response using bivariate regression. The bivariate regression model assumes an underlying joint distribution in which the means of the marginal logarithm of bivariate responses depend on flaw size, but the standard deviations and correlation of the bivariate responses do not depend on flaw size. In this application, flaw size is flaw area. In the rest of this paper, flaw area will be used. This bivariate â versus a model can be written as: n / Po Pi 2/2 av2 (2.5) ei \ / 0 N 2 ) V 0 a yi a y2p a yi a y2p.2 a: 2/2 where /3q 1,, /?q 2, j3f 2, a yi, a y2, and p are unknown parameters that need to be estimated. The random error term (ei, 62)' is assumed to have a bivariate normal distribution with mean 0, standard deviation a yi, a y2, and correlation p. According to these assumptions, (Yi, Y2) has bivariate normal distribution with density function: f{yi! U2] Pyi ) Py2 ; a yi ' tj V2 ' P) ~ 1 f 1. exp I -- Q 27rcr^o-^\/l-^ \ 2
30 16 where Q l l p 2 a, y 1, (2/2-^2)^ ip 1 5 V2 The regression relationships %i Py2 log(a) express the dependency of the distribution means on flaw area. The joint cumulative distribution function (CDF) of Y\ and Y2 can be written as: / y 1 ry2 / / ( m, 2 / 2 : ^ 1, ( 2. 6 ) -oo J oo Maximum Likelihood Analysis with Censoring and Truncation Censoring and truncation A left-censored observation occurs when the exact value of the response has not been observed and we have, instead, an upper bound on the response (e.g., pages of Meeker and Escobar, 1998). In NDE applications, a left-censored observation occurs when a known flaw is missed. That is, the existence of a flaw is known and only an upper bound on the signal value is available. Right censoring arises when the exact value of the response can not be observed and there is only a lower bound on the response. Right censoring occurs in NDE applications due to saturation (i.e., observations that are so large that they exceed the upper bound of the measuring device). Figure 2.1 uses simulated data to illustrate bivariate left censored data. The top graph shows data without censoring. The bottom graph shows the corresponding left censored data. Due to left censoring, the exact values of the data with the responses below the thresholds in the top graph become unknown except that the responses are below the thresholds. Truncation is similar to but different from censoring. Truncation occurs when a response can be observed only when it falls in particular range, outside of which the existence of the flaw
31 S ! 5 1 ' Data without censoring 1 1.Mi': ', ' ' ' '. 1 ' Amplitude (Normal) ' 'A' ' i* '» $ J? 500 o TO i'w,. ##»*###**##*$»*yww «<! * I* i *» Amplitude (Normal) Figure 2.1 Simulated data used to illustrate bivariate left censoring.
32 18 is not known. Truncation usually is left truncation due to field flaw misses in NDE applications. The model for truncated data in the ML method is based on conditional probability Likelihood The method of maximum likelihood (ML) estimation is one of the most versatile and popular statistical estimation techniques. Especially when there are complicating factors like censoring and truncation, ML estimation is preferred over other methods because it has good statistical properties (e.g., the invariance property) and some asymptotic optimality properties (e.g., minimum variance). The likelihood function is central to estimation and inference. The natural log function is strictly increasing and thus the estimates maximizing log likelihood will also maximize the likelihood. Therefore, log likelihood is usually used because, numerically, it is much easier to maximize the log likelihood than likelihood. The log likelihood for the bivariate regression model defined in Equation (2.5) is n i=1 (2.7) where Ci represents the contribution from the observation i. When censoring and truncation mechanisms are active, the log likelihood function becomes more complicated, especially for the bivariate response. This is because the log likelihood needs to describe the probability behavior of parameters of statistical model for given complicated observed data. The contribution from each observation is defined in the next subsections. The ML estimates are the values of (jsq 1, 0^, /3q 2,(3\ 2, <J yi, u y2, p) that maximize the log likelihood in Equation (2.10). There are different ways to maximize the likelihood in Equation (2.10). For most practical problems involving complications like censoring or truncation, the likelihood must be maximized directly by using numerical methods, such as Newton's method Probability of the data contributions for different kinds of censoring Because the combination of censoring and truncation can make the log likelihood function complicated, we first study the log likelihood contribution without truncation. For a univariate
33 19 response, there are three possibilities: left censoring, right censoring, and no censoring. For a bivariate response, we need to consider, potentially, 9 combinations of these observation types. Figures 2.2 and 2.3 provide a visualization of the likelihood contributions from observations with different types of censoring, assuming no truncation. For example, with a doubly left censored observation, the bivariate response is below the given values in both dimensions. Thus the contribution to the likelihood is proportional to the probability of data falling into the rectangle of Area# 1.1 in Figure 2.2. The contribution is computed as the cumulative probability, FY lly 2(y\,y2) defined in Equation (2.6). An uncensored response for Yi and a left censored response for Y\ has a contribution equal to the probability of data falling into Slice# 1.1 in Figure 2.2. The likelihood contributions for doubly left censoring, left censoring only in Y\, and other censoring types are defined as follows. Let Si and S2 denote the data status (i.e., left censoring (L), no censoring (E), and right censoring (R)) with respect to yi and 3/2, respectively. The probability of observation i with response (2/1,2/2) can be expressed as = Pr(i/1 < 2/1 < 2/Ï and 2/2 < 2/2 < 2/2 ) = Prob(2/, 2/2,!/i, 3/2,^1,%) If Si = L, then y\ = -00, yf = yf L, where yf L is the left censoring level. If Si = E, then y\ = y t - 5, yf = y^ + 5. If Si = R, then y\ = yf R, y" = 00, where yf R is the right censoring level Density approximations for observation reported as exact values Typically there is enough precision in measured response values (amplitude and SNR in the current context) that they are recorded as exact values. Referring to the definitions of Prob(yJ, y l 2,2S1, S2) in the subsection , when S approaches 0, the limit of Prob(y^, y l 2, yf, 2/2, Si, can be approximated by using a density function that is probability of the data. For example, when the width of the Slice#l.l, ô, approaches 0, the contribution can be written in probabil-
34 Doubly left censored Left censored in the Y1 dimension, Exact in the Y2 dimension CM > 00 //Area#!.1 CM > Slice#1.1 Y1 Y1 Left censored in the Y1 dimension, Right censored in the Y2 dimension Exact in the Y1 dimension, Left censored in the Y2 dimension CM CM Area#1.3 Slice#1.2 Y1 Y1 Figure 2.2 Contribution of censored data to likelihood in bivariate model (Continued).
35 Exact in the Y1 dimension, Right censored in the Y2 dimension Right censored in the Y1 dimension, Eaxct in the Y2 dimension CXI > CM > Slice#1.3 Slice#1.4 Y1 Y1 Right censored in the Y1 dimension, Left censored in the Y2 dimension Doubly right censored Area#1.4 2 CM > Area#1.2 Y1 Y1 Figure 2.3 Contribution of censored data to likelihood in bivariate model.
36 ! 22 ity density form as F Yi\y 2(vi) x f 2(1/2)- Using the density approximations provide definitions of the likelihood contributions that are easier to specify and compute. In particular, the log likelihood contribution is Ci = log (Contrat/;, yi)), where Contr^)(3/1,1/2) can be expressed as: FY 1,Y 2{y\,y2) Si = L, S 2 = L -Fyi yz(3/i) x AtW Si = L, Si = E FYiiyi) - F YltY 2{yi,yi) Si = L, S 2 = R Fy 2\Yi (2/2) x fy 1(yi) Si = E, S 2 = L Contrai,#) /n,^2 (2/1,2/2) Si = B,% = E (2.8) $ X G Si = E, Si = R -^5-2(2/2) - F YliY 2(yi,yi) Si = R, S 2 = L (1 - F Yl\Y 2(yi)) x /y 2(2/2) Si = R,% = E 1 - F Yl(2/1) - Fy 2(yi) + F Yi,y 2(3/1,2/2) Si = R, Si = R. Note that, Some of the Contr^)(3/1,3/2) contributions (e.g., 1,2/2)) are in density form. Fy x (yi) and Fy 2(yi) denote the CDF of the marginal distribution of Yi and Yg, respectively. fy l (2/1) and fy 2 (3/2) denote the PDF of the marginal distribution of Yi and Yi, respectively. Fy 2\Yi (2/2) denotes the CDF of the conditional distribution of Yi given a particular value of Yi. F Yl\Y 2{yi) denotes the CDF of the conditional distribution of Yi given a particular value of Yi Contributions with censoring and truncation When considering data truncation, we assume that (Yi, Yg)' has a doubly truncated distribution with truncation levels yj L and yj h - This truncated distribution is adapted from the untruncated distribution whose CDF is denoted by F( YliY2)(yi,yi)- The CDF of the doubly
37 23 truncated bivariate distribution can be written as (2/1,2/2) f (Yi,y 2)(m,y2)-F( Y,,y 2)(y[ b,y 2) ^,tl ^ ^,tl 2/1 > or 1/2 > ^ (2.9) 0 Otherwise, where yf = yj L A yi and y l 2 = 2/J L A 1/2 ("A" denotes minimum function). The term in the denominator of Equation (2.9) accounts for truncation and makes total probability under truncated density function equal to 1. In some applications, there is truncation in only one dimension or there is no truncation. Left one-dimensional truncation is just a special case of left doubly truncation where either yj L = 00 or y 2 h = -00. The no truncation case (i.e., yj h = 00 and yj L = 00) was described in subsection For the case with both censoring and truncation, we can write the contribution for observation i with response (2/1,1/2) as Contr^i/i, y 2) \ U = log (2.10).i-f(yi,y,)(!/7\^)y ' where Contr^yi,2/2) is the same as described in Equation (2.8), except when either or both of Y\ and Y 2 is left censored. When one or both of the responses are left censored, Contr^yi, y 2) is defined as: Fy^ivum) - F Yl, Y2(y[,y l 2) Si = L, S 2 = L {F Yl\Y 2{yi) - F Yl\Y 2{y l i)) X fy 2(y2) SI = L, S 2 = E Contrai, 1/2)= < (F Yl(y 1) - F Yly 2{yi,y 2)) - {FY 1(y[) - F Yl,Y 2{y[,y l 2)) Si =L,S 2 = R (Fy 2\ Yi (2/2) - FY 2 \ YL (Y 2)) X f Yl (yi) SI = E,S 2 = L (F Y2(y 2) - F Yly 2{yi,y 2)) - (F Y2(y l 2) - F YltY2(y[,y l 2)) Si = R, S 2 = L (2.11) where the definitions of y[ and y l 2 depend on the type of censoring and on which of Y\ and Y 2 is truncated.
POD Tutorial Part I I Review of ahat versus a Strategies
 POD Tutorial Part I I Review of ahat versus a Strategies William Q. Meeker wqmeeker@iastate.edu Center for Nondestructive Evaluation Department of Statistics Iowa State University 1 Overview versus a data
POD Tutorial Part I I Review of ahat versus a Strategies William Q. Meeker wqmeeker@iastate.edu Center for Nondestructive Evaluation Department of Statistics Iowa State University 1 Overview versus a data
POD(a) = Pr (Y(a) > '1').
 PROBABILITY OF DETECTION MODELING FOR ULTRASONIC TESTING Pradipta Sarkar, William Q. Meeker, R. Bruce Thompson, Timothy A. Gray Center for Nondestructive Evaluation Iowa State University Ames, IA 511 Warren
PROBABILITY OF DETECTION MODELING FOR ULTRASONIC TESTING Pradipta Sarkar, William Q. Meeker, R. Bruce Thompson, Timothy A. Gray Center for Nondestructive Evaluation Iowa State University Ames, IA 511 Warren
IMPROVED METHODOLOGY FOR INSPECTION RELIABILITY ASSESSMENT FOR DETECTING SYNTHETIC HARD ALPHA INCLUSIONS IN TITANIUM
 IMPROVED METHODOLOGY FOR INSPECTION RELIABILITY ASSESSMENT FOR DETECTING SYNTHETIC HARD ALPHA INCLUSIONS IN TITANIUM William Q. Meeker, Shuen-Lin Jeng, Chien-Ping Chiou, R. Bruce Thompson Center for Nondestructive
IMPROVED METHODOLOGY FOR INSPECTION RELIABILITY ASSESSMENT FOR DETECTING SYNTHETIC HARD ALPHA INCLUSIONS IN TITANIUM William Q. Meeker, Shuen-Lin Jeng, Chien-Ping Chiou, R. Bruce Thompson Center for Nondestructive
Quantile POD for Hit-Miss Data
 Quantile POD for Hit-Miss Data Yew-Meng Koh a and William Q. Meeker a a Center for Nondestructive Evaluation, Department of Statistics, Iowa State niversity, Ames, Iowa 50010 Abstract. Probability of detection
Quantile POD for Hit-Miss Data Yew-Meng Koh a and William Q. Meeker a a Center for Nondestructive Evaluation, Department of Statistics, Iowa State niversity, Ames, Iowa 50010 Abstract. Probability of detection
Model-Assisted Probability of Detection for Ultrasonic Structural Health Monitoring
 4th European-American Workshop on Reliability of NDE - Th.2.A.2 Model-Assisted Probability of Detection for Ultrasonic Structural Health Monitoring Adam C. COBB and Jay FISHER, Southwest Research Institute,
4th European-American Workshop on Reliability of NDE - Th.2.A.2 Model-Assisted Probability of Detection for Ultrasonic Structural Health Monitoring Adam C. COBB and Jay FISHER, Southwest Research Institute,
Bayesian Defect Signal Analysis
 Electrical and Computer Engineering Publications Electrical and Computer Engineering 26 Bayesian Defect Signal Analysis Aleksandar Dogandžić Iowa State University, ald@iastate.edu Benhong Zhang Iowa State
Electrical and Computer Engineering Publications Electrical and Computer Engineering 26 Bayesian Defect Signal Analysis Aleksandar Dogandžić Iowa State University, ald@iastate.edu Benhong Zhang Iowa State
Experimental designs for multiple responses with different models
 Graduate Theses and Dissertations Graduate College 2015 Experimental designs for multiple responses with different models Wilmina Mary Marget Iowa State University Follow this and additional works at:
Graduate Theses and Dissertations Graduate College 2015 Experimental designs for multiple responses with different models Wilmina Mary Marget Iowa State University Follow this and additional works at:
Statisical method and simulation on detecting cracks in vibrothermography inspection
 Graduate Theses and Dissertations Iowa State University Capstones, Theses and Dissertations 2010 Statisical method and simulation on detecting cracks in vibrothermography inspection Chunwang Gao Iowa State
Graduate Theses and Dissertations Iowa State University Capstones, Theses and Dissertations 2010 Statisical method and simulation on detecting cracks in vibrothermography inspection Chunwang Gao Iowa State
Simultaneous Prediction Intervals for the (Log)- Location-Scale Family of Distributions
 Statistics Preprints Statistics 10-2014 Simultaneous Prediction Intervals for the (Log)- Location-Scale Family of Distributions Yimeng Xie Virginia Tech Yili Hong Virginia Tech Luis A. Escobar Louisiana
Statistics Preprints Statistics 10-2014 Simultaneous Prediction Intervals for the (Log)- Location-Scale Family of Distributions Yimeng Xie Virginia Tech Yili Hong Virginia Tech Luis A. Escobar Louisiana
Ronald Christensen. University of New Mexico. Albuquerque, New Mexico. Wesley Johnson. University of California, Irvine. Irvine, California
 Texts in Statistical Science Bayesian Ideas and Data Analysis An Introduction for Scientists and Statisticians Ronald Christensen University of New Mexico Albuquerque, New Mexico Wesley Johnson University
Texts in Statistical Science Bayesian Ideas and Data Analysis An Introduction for Scientists and Statisticians Ronald Christensen University of New Mexico Albuquerque, New Mexico Wesley Johnson University
The Relationship Between Confidence Intervals for Failure Probabilities and Life Time Quantiles
 Statistics Preprints Statistics 2008 The Relationship Between Confidence Intervals for Failure Probabilities and Life Time Quantiles Yili Hong Iowa State University, yili_hong@hotmail.com William Q. Meeker
Statistics Preprints Statistics 2008 The Relationship Between Confidence Intervals for Failure Probabilities and Life Time Quantiles Yili Hong Iowa State University, yili_hong@hotmail.com William Q. Meeker
Lifetime prediction and confidence bounds in accelerated degradation testing for lognormal response distributions with an Arrhenius rate relationship
 Scholars' Mine Doctoral Dissertations Student Research & Creative Works Spring 01 Lifetime prediction and confidence bounds in accelerated degradation testing for lognormal response distributions with
Scholars' Mine Doctoral Dissertations Student Research & Creative Works Spring 01 Lifetime prediction and confidence bounds in accelerated degradation testing for lognormal response distributions with
Logistic Regression and Item Response Theory: Estimation Item and Ability Parameters by Using Logistic Regression in IRT.
 Louisiana State University LSU Digital Commons LSU Historical Dissertations and Theses Graduate School 1998 Logistic Regression and Item Response Theory: Estimation Item and Ability Parameters by Using
Louisiana State University LSU Digital Commons LSU Historical Dissertations and Theses Graduate School 1998 Logistic Regression and Item Response Theory: Estimation Item and Ability Parameters by Using
Estimating Probability of Detection Curves Related to Eddy Current Sender Receiver Probes
 5 th European-American Workshop on Reliability of NDE Lecture 9 Estimating Probability of Detection Curves Related to Eddy Current Sender Receiver Probes Anders ROSELL 1, 2, Gert PERSSON 2, Håkan WIRDELIUS
5 th European-American Workshop on Reliability of NDE Lecture 9 Estimating Probability of Detection Curves Related to Eddy Current Sender Receiver Probes Anders ROSELL 1, 2, Gert PERSSON 2, Håkan WIRDELIUS
Bivariate Degradation Modeling Based on Gamma Process
 Bivariate Degradation Modeling Based on Gamma Process Jinglun Zhou Zhengqiang Pan Member IAENG and Quan Sun Abstract Many highly reliable products have two or more performance characteristics (PCs). The
Bivariate Degradation Modeling Based on Gamma Process Jinglun Zhou Zhengqiang Pan Member IAENG and Quan Sun Abstract Many highly reliable products have two or more performance characteristics (PCs). The
Effects of pioglitazone on cardiovascular function in type I and type II diabetes mellitus
 University of Montana ScholarWorks at University of Montana Graduate Student Theses, Dissertations, & Professional Papers Graduate School 1993 Effects of pioglitazone on cardiovascular function in type
University of Montana ScholarWorks at University of Montana Graduate Student Theses, Dissertations, & Professional Papers Graduate School 1993 Effects of pioglitazone on cardiovascular function in type
LOGISTIC REGRESSION Joseph M. Hilbe
 LOGISTIC REGRESSION Joseph M. Hilbe Arizona State University Logistic regression is the most common method used to model binary response data. When the response is binary, it typically takes the form of
LOGISTIC REGRESSION Joseph M. Hilbe Arizona State University Logistic regression is the most common method used to model binary response data. When the response is binary, it typically takes the form of
Bayesian Life Test Planning for the Weibull Distribution with Given Shape Parameter
 Statistics Preprints Statistics 10-8-2002 Bayesian Life Test Planning for the Weibull Distribution with Given Shape Parameter Yao Zhang Iowa State University William Q. Meeker Iowa State University, wqmeeker@iastate.edu
Statistics Preprints Statistics 10-8-2002 Bayesian Life Test Planning for the Weibull Distribution with Given Shape Parameter Yao Zhang Iowa State University William Q. Meeker Iowa State University, wqmeeker@iastate.edu
ACCELERATED DESTRUCTIVE DEGRADATION TEST PLANNING. Presented by Luis A. Escobar Experimental Statistics LSU, Baton Rouge LA 70803
 ACCELERATED DESTRUCTIVE DEGRADATION TEST PLANNING Presented by Luis A. Escobar Experimental Statistics LSU, Baton Rouge LA 70803 This is jointly work with Ying Shi and William Q. Meeker both from Iowa
ACCELERATED DESTRUCTIVE DEGRADATION TEST PLANNING Presented by Luis A. Escobar Experimental Statistics LSU, Baton Rouge LA 70803 This is jointly work with Ying Shi and William Q. Meeker both from Iowa
Accelerated Destructive Degradation Tests: Data, Models, and Analysis
 Statistics Preprints Statistics 03 Accelerated Destructive Degradation Tests: Data, Models, and Analysis Luis A. Escobar Louisiana State University William Q. Meeker Iowa State University, wqmeeker@iastate.edu
Statistics Preprints Statistics 03 Accelerated Destructive Degradation Tests: Data, Models, and Analysis Luis A. Escobar Louisiana State University William Q. Meeker Iowa State University, wqmeeker@iastate.edu
Logistic Regression: Regression with a Binary Dependent Variable
 Logistic Regression: Regression with a Binary Dependent Variable LEARNING OBJECTIVES Upon completing this chapter, you should be able to do the following: State the circumstances under which logistic regression
Logistic Regression: Regression with a Binary Dependent Variable LEARNING OBJECTIVES Upon completing this chapter, you should be able to do the following: State the circumstances under which logistic regression
Generalized Linear Models for Non-Normal Data
 Generalized Linear Models for Non-Normal Data Today s Class: 3 parts of a generalized model Models for binary outcomes Complications for generalized multivariate or multilevel models SPLH 861: Lecture
Generalized Linear Models for Non-Normal Data Today s Class: 3 parts of a generalized model Models for binary outcomes Complications for generalized multivariate or multilevel models SPLH 861: Lecture
Department of Statistical Science FIRST YEAR EXAM - SPRING 2017
 Department of Statistical Science Duke University FIRST YEAR EXAM - SPRING 017 Monday May 8th 017, 9:00 AM 1:00 PM NOTES: PLEASE READ CAREFULLY BEFORE BEGINNING EXAM! 1. Do not write solutions on the exam;
Department of Statistical Science Duke University FIRST YEAR EXAM - SPRING 017 Monday May 8th 017, 9:00 AM 1:00 PM NOTES: PLEASE READ CAREFULLY BEFORE BEGINNING EXAM! 1. Do not write solutions on the exam;
Basics of Uncertainty Analysis
 Basics of Uncertainty Analysis Chapter Six Basics of Uncertainty Analysis 6.1 Introduction As shown in Fig. 6.1, analysis models are used to predict the performances or behaviors of a product under design.
Basics of Uncertainty Analysis Chapter Six Basics of Uncertainty Analysis 6.1 Introduction As shown in Fig. 6.1, analysis models are used to predict the performances or behaviors of a product under design.
HANDBOOK OF APPLICABLE MATHEMATICS
 HANDBOOK OF APPLICABLE MATHEMATICS Chief Editor: Walter Ledermann Volume VI: Statistics PART A Edited by Emlyn Lloyd University of Lancaster A Wiley-Interscience Publication JOHN WILEY & SONS Chichester
HANDBOOK OF APPLICABLE MATHEMATICS Chief Editor: Walter Ledermann Volume VI: Statistics PART A Edited by Emlyn Lloyd University of Lancaster A Wiley-Interscience Publication JOHN WILEY & SONS Chichester
Sample Size and Number of Failure Requirements for Demonstration Tests with Log-Location-Scale Distributions and Type II Censoring
 Statistics Preprints Statistics 3-2-2002 Sample Size and Number of Failure Requirements for Demonstration Tests with Log-Location-Scale Distributions and Type II Censoring Scott W. McKane 3M Pharmaceuticals
Statistics Preprints Statistics 3-2-2002 Sample Size and Number of Failure Requirements for Demonstration Tests with Log-Location-Scale Distributions and Type II Censoring Scott W. McKane 3M Pharmaceuticals
Defect Detection Using Hidden Markov Random Fields
 Electrical and Computer Engineering Publications Electrical and Computer Engineering 5 Defect Detection Using Hidden Markov Random Fields Aleksandar Dogandžić Iowa State University, ald@iastate.edu Nawanat
Electrical and Computer Engineering Publications Electrical and Computer Engineering 5 Defect Detection Using Hidden Markov Random Fields Aleksandar Dogandžić Iowa State University, ald@iastate.edu Nawanat
STA 4273H: Statistical Machine Learning
 STA 4273H: Statistical Machine Learning Russ Salakhutdinov Department of Computer Science! Department of Statistical Sciences! rsalakhu@cs.toronto.edu! h0p://www.cs.utoronto.ca/~rsalakhu/ Lecture 7 Approximate
STA 4273H: Statistical Machine Learning Russ Salakhutdinov Department of Computer Science! Department of Statistical Sciences! rsalakhu@cs.toronto.edu! h0p://www.cs.utoronto.ca/~rsalakhu/ Lecture 7 Approximate
Introduction to Bayesian Statistics and Markov Chain Monte Carlo Estimation. EPSY 905: Multivariate Analysis Spring 2016 Lecture #10: April 6, 2016
 Introduction to Bayesian Statistics and Markov Chain Monte Carlo Estimation EPSY 905: Multivariate Analysis Spring 2016 Lecture #10: April 6, 2016 EPSY 905: Intro to Bayesian and MCMC Today s Class An
Introduction to Bayesian Statistics and Markov Chain Monte Carlo Estimation EPSY 905: Multivariate Analysis Spring 2016 Lecture #10: April 6, 2016 EPSY 905: Intro to Bayesian and MCMC Today s Class An
EPSY 905: Fundamentals of Multivariate Modeling Online Lecture #7
 Introduction to Generalized Univariate Models: Models for Binary Outcomes EPSY 905: Fundamentals of Multivariate Modeling Online Lecture #7 EPSY 905: Intro to Generalized In This Lecture A short review
Introduction to Generalized Univariate Models: Models for Binary Outcomes EPSY 905: Fundamentals of Multivariate Modeling Online Lecture #7 EPSY 905: Intro to Generalized In This Lecture A short review
Measurement Error and Linear Regression of Astronomical Data. Brandon Kelly Penn State Summer School in Astrostatistics, June 2007
 Measurement Error and Linear Regression of Astronomical Data Brandon Kelly Penn State Summer School in Astrostatistics, June 2007 Classical Regression Model Collect n data points, denote i th pair as (η
Measurement Error and Linear Regression of Astronomical Data Brandon Kelly Penn State Summer School in Astrostatistics, June 2007 Classical Regression Model Collect n data points, denote i th pair as (η
Bayesian Methods for Accelerated Destructive Degradation Test Planning
 Statistics Preprints Statistics 11-2010 Bayesian Methods for Accelerated Destructive Degradation Test Planning Ying Shi Iowa State University William Q. Meeker Iowa State University, wqmeeker@iastate.edu
Statistics Preprints Statistics 11-2010 Bayesian Methods for Accelerated Destructive Degradation Test Planning Ying Shi Iowa State University William Q. Meeker Iowa State University, wqmeeker@iastate.edu
Advanced Software for Integrated Probabilistic Damage Tolerance Analysis Including Residual Stress Effects
 Advanced Software for Integrated Probabilistic Damage Tolerance Analysis Including Residual Stress Effects Residual Stress Summit 2010 Tahoe City, California September 26-29, 2010 Michael P. Enright R.
Advanced Software for Integrated Probabilistic Damage Tolerance Analysis Including Residual Stress Effects Residual Stress Summit 2010 Tahoe City, California September 26-29, 2010 Michael P. Enright R.
From Practical Data Analysis with JMP, Second Edition. Full book available for purchase here. About This Book... xiii About The Author...
 From Practical Data Analysis with JMP, Second Edition. Full book available for purchase here. Contents About This Book... xiii About The Author... xxiii Chapter 1 Getting Started: Data Analysis with JMP...
From Practical Data Analysis with JMP, Second Edition. Full book available for purchase here. Contents About This Book... xiii About The Author... xxiii Chapter 1 Getting Started: Data Analysis with JMP...
Compositions, Bijections, and Enumerations
 Georgia Southern University Digital Commons@Georgia Southern Electronic Theses & Dissertations COGS- Jack N. Averitt College of Graduate Studies Fall 2012 Compositions, Bijections, and Enumerations Charles
Georgia Southern University Digital Commons@Georgia Southern Electronic Theses & Dissertations COGS- Jack N. Averitt College of Graduate Studies Fall 2012 Compositions, Bijections, and Enumerations Charles
Multivariate Assays With Values Below the Lower Limit of Quantitation: Parametric Estimation By Imputation and Maximum Likelihood
 Multivariate Assays With Values Below the Lower Limit of Quantitation: Parametric Estimation By Imputation and Maximum Likelihood Robert E. Johnson and Heather J. Hoffman 2* Department of Biostatistics,
Multivariate Assays With Values Below the Lower Limit of Quantitation: Parametric Estimation By Imputation and Maximum Likelihood Robert E. Johnson and Heather J. Hoffman 2* Department of Biostatistics,
ULTRASONIC A TTENUA TION RESULTS OF THERMOPLASTIC RESIN COMPOSITES UNDERGOING THERMAL AND FATIGUE LOADING
 ULTRASONIC A TTENUA TION RESULTS OF THERMOPLASTIC RESIN COMPOSITES UNDERGOING THERMAL AND FATIGUE LOADING Eric I. Madaras NASA Langley Research Center MS 231 Hampton,. VA 23681-0001 INTRODUCTION Before
ULTRASONIC A TTENUA TION RESULTS OF THERMOPLASTIC RESIN COMPOSITES UNDERGOING THERMAL AND FATIGUE LOADING Eric I. Madaras NASA Langley Research Center MS 231 Hampton,. VA 23681-0001 INTRODUCTION Before
STATISTICAL ANALYSIS WITH MISSING DATA
 STATISTICAL ANALYSIS WITH MISSING DATA SECOND EDITION Roderick J.A. Little & Donald B. Rubin WILEY SERIES IN PROBABILITY AND STATISTICS Statistical Analysis with Missing Data Second Edition WILEY SERIES
STATISTICAL ANALYSIS WITH MISSING DATA SECOND EDITION Roderick J.A. Little & Donald B. Rubin WILEY SERIES IN PROBABILITY AND STATISTICS Statistical Analysis with Missing Data Second Edition WILEY SERIES
STATISTICAL INFERENCE IN ACCELERATED LIFE TESTING WITH GEOMETRIC PROCESS MODEL. A Thesis. Presented to the. Faculty of. San Diego State University
 STATISTICAL INFERENCE IN ACCELERATED LIFE TESTING WITH GEOMETRIC PROCESS MODEL A Thesis Presented to the Faculty of San Diego State University In Partial Fulfillment of the Requirements for the Degree
STATISTICAL INFERENCE IN ACCELERATED LIFE TESTING WITH GEOMETRIC PROCESS MODEL A Thesis Presented to the Faculty of San Diego State University In Partial Fulfillment of the Requirements for the Degree
ULTRASONIC INSPECTION, MATERIAL NOISE AND. Mehmet Bilgen and James H. Center for NDE Iowa State University Ames, IA 50011
 ULTRASONIC INSPECTION, MATERIAL NOISE AND SURFACE ROUGHNESS Mehmet Bilgen and James H. Center for NDE Iowa State University Ames, IA 511 Rose Peter B. Nagy Department of Welding Engineering Ohio State
ULTRASONIC INSPECTION, MATERIAL NOISE AND SURFACE ROUGHNESS Mehmet Bilgen and James H. Center for NDE Iowa State University Ames, IA 511 Rose Peter B. Nagy Department of Welding Engineering Ohio State
An Approach to Constructing Good Two-level Orthogonal Factorial Designs with Large Run Sizes
 An Approach to Constructing Good Two-level Orthogonal Factorial Designs with Large Run Sizes by Chenlu Shi B.Sc. (Hons.), St. Francis Xavier University, 013 Project Submitted in Partial Fulfillment of
An Approach to Constructing Good Two-level Orthogonal Factorial Designs with Large Run Sizes by Chenlu Shi B.Sc. (Hons.), St. Francis Xavier University, 013 Project Submitted in Partial Fulfillment of
Stat 5101 Lecture Notes
 Stat 5101 Lecture Notes Charles J. Geyer Copyright 1998, 1999, 2000, 2001 by Charles J. Geyer May 7, 2001 ii Stat 5101 (Geyer) Course Notes Contents 1 Random Variables and Change of Variables 1 1.1 Random
Stat 5101 Lecture Notes Charles J. Geyer Copyright 1998, 1999, 2000, 2001 by Charles J. Geyer May 7, 2001 ii Stat 5101 (Geyer) Course Notes Contents 1 Random Variables and Change of Variables 1 1.1 Random
DROP WEIGHT TEST WORK
 CHAPTER 4 4.1 Introduction The purpose of the drop-weight-test work was to establish a consistent quantification of fracture response of the material to the energy spectra predicted by the DEM software.
CHAPTER 4 4.1 Introduction The purpose of the drop-weight-test work was to establish a consistent quantification of fracture response of the material to the energy spectra predicted by the DEM software.
TOWARD A VIABLE STRATEGY FOR ESTIMATING VIBROTHERMOGRAPHIC PROBABILITY OF DETECTION
 TOWARD A VIABLE STRATEGY FOR ESTIMATING VIBROTHERMOGRAPHIC PROBABILITY OF DETECTION Stephen D. Holland, Christopher Uhl, Jeremy Renshaw^ ^Center for NDE and Aerospace Eng Dept, Iowa State Univ, Ames, Iowa
TOWARD A VIABLE STRATEGY FOR ESTIMATING VIBROTHERMOGRAPHIC PROBABILITY OF DETECTION Stephen D. Holland, Christopher Uhl, Jeremy Renshaw^ ^Center for NDE and Aerospace Eng Dept, Iowa State Univ, Ames, Iowa
Bayesian Inference: Probit and Linear Probability Models
 Utah State University DigitalCommons@USU All Graduate Plan B and other Reports Graduate Studies 5-1-2014 Bayesian Inference: Probit and Linear Probability Models Nate Rex Reasch Utah State University Follow
Utah State University DigitalCommons@USU All Graduate Plan B and other Reports Graduate Studies 5-1-2014 Bayesian Inference: Probit and Linear Probability Models Nate Rex Reasch Utah State University Follow
PART I INTRODUCTION The meaning of probability Basic definitions for frequentist statistics and Bayesian inference Bayesian inference Combinatorics
 Table of Preface page xi PART I INTRODUCTION 1 1 The meaning of probability 3 1.1 Classical definition of probability 3 1.2 Statistical definition of probability 9 1.3 Bayesian understanding of probability
Table of Preface page xi PART I INTRODUCTION 1 1 The meaning of probability 3 1.1 Classical definition of probability 3 1.2 Statistical definition of probability 9 1.3 Bayesian understanding of probability
Chapter 9 Regression with a Binary Dependent Variable. Multiple Choice. 1) The binary dependent variable model is an example of a
 Chapter 9 Regression with a Binary Dependent Variable Multiple Choice ) The binary dependent variable model is an example of a a. regression model, which has as a regressor, among others, a binary variable.
Chapter 9 Regression with a Binary Dependent Variable Multiple Choice ) The binary dependent variable model is an example of a a. regression model, which has as a regressor, among others, a binary variable.
Utah Math Standards for College Prep Mathematics
 A Correlation of 8 th Edition 2016 To the A Correlation of, 8 th Edition to the Resource Title:, 8 th Edition Publisher: Pearson Education publishing as Prentice Hall ISBN: SE: 9780133941753/ 9780133969078/
A Correlation of 8 th Edition 2016 To the A Correlation of, 8 th Edition to the Resource Title:, 8 th Edition Publisher: Pearson Education publishing as Prentice Hall ISBN: SE: 9780133941753/ 9780133969078/
Robust Parameter Estimation in the Weibull and the Birnbaum-Saunders Distribution
 Clemson University TigerPrints All Theses Theses 8-2012 Robust Parameter Estimation in the Weibull and the Birnbaum-Saunders Distribution Jing Zhao Clemson University, jzhao2@clemson.edu Follow this and
Clemson University TigerPrints All Theses Theses 8-2012 Robust Parameter Estimation in the Weibull and the Birnbaum-Saunders Distribution Jing Zhao Clemson University, jzhao2@clemson.edu Follow this and
Reliability Monitoring Using Log Gaussian Process Regression
 COPYRIGHT 013, M. Modarres Reliability Monitoring Using Log Gaussian Process Regression Martin Wayne Mohammad Modarres PSA 013 Center for Risk and Reliability University of Maryland Department of Mechanical
COPYRIGHT 013, M. Modarres Reliability Monitoring Using Log Gaussian Process Regression Martin Wayne Mohammad Modarres PSA 013 Center for Risk and Reliability University of Maryland Department of Mechanical
Examining the accuracy of the normal approximation to the poisson random variable
 Eastern Michigan University DigitalCommons@EMU Master's Theses and Doctoral Dissertations Master's Theses, and Doctoral Dissertations, and Graduate Capstone Projects 2009 Examining the accuracy of the
Eastern Michigan University DigitalCommons@EMU Master's Theses and Doctoral Dissertations Master's Theses, and Doctoral Dissertations, and Graduate Capstone Projects 2009 Examining the accuracy of the
Robust Mechanism synthesis with random and interval variables
 Scholars' Mine Masters Theses Student Research & Creative Works Fall 2007 Robust Mechanism synthesis with random and interval variables Pavan Kumar Venigella Follow this and additional works at: http://scholarsmine.mst.edu/masters_theses
Scholars' Mine Masters Theses Student Research & Creative Works Fall 2007 Robust Mechanism synthesis with random and interval variables Pavan Kumar Venigella Follow this and additional works at: http://scholarsmine.mst.edu/masters_theses
1 Using standard errors when comparing estimated values
 MLPR Assignment Part : General comments Below are comments on some recurring issues I came across when marking the second part of the assignment, which I thought it would help to explain in more detail
MLPR Assignment Part : General comments Below are comments on some recurring issues I came across when marking the second part of the assignment, which I thought it would help to explain in more detail
Linear Models 1. Isfahan University of Technology Fall Semester, 2014
 Linear Models 1 Isfahan University of Technology Fall Semester, 2014 References: [1] G. A. F., Seber and A. J. Lee (2003). Linear Regression Analysis (2nd ed.). Hoboken, NJ: Wiley. [2] A. C. Rencher and
Linear Models 1 Isfahan University of Technology Fall Semester, 2014 References: [1] G. A. F., Seber and A. J. Lee (2003). Linear Regression Analysis (2nd ed.). Hoboken, NJ: Wiley. [2] A. C. Rencher and
σ(a) = a N (x; 0, 1 2 ) dx. σ(a) = Φ(a) =
 Until now we have always worked with likelihoods and prior distributions that were conjugate to each other, allowing the computation of the posterior distribution to be done in closed form. Unfortunately,
Until now we have always worked with likelihoods and prior distributions that were conjugate to each other, allowing the computation of the posterior distribution to be done in closed form. Unfortunately,
INFORMATION TO USERS
 INFORMATION TO USERS The most advanced technology has been used to photograph and reproduce this manuscript from the microfilm master. UMI films the text directly from the original or copy submitted. Thus,
INFORMATION TO USERS The most advanced technology has been used to photograph and reproduce this manuscript from the microfilm master. UMI films the text directly from the original or copy submitted. Thus,
IMPROVEMENT OF TIME REVERSAL PROCESSING IN TITANIUM INSPECTIONS
 IMPROVEMENT OF TIME REVERSAL PROCESSING IN TITANIUM INSPECTIONS Veronique Miette Mathias Fink Franyois Wu Laboratoire Ondes et Acoustique ESPCI, University Paris VII, 755 Paris, France INTRODUCTION We
IMPROVEMENT OF TIME REVERSAL PROCESSING IN TITANIUM INSPECTIONS Veronique Miette Mathias Fink Franyois Wu Laboratoire Ondes et Acoustique ESPCI, University Paris VII, 755 Paris, France INTRODUCTION We
ULTRASONIC ATTENUATION RESULTS OF THERMOPLASTIC RESIN COMPOSITES UNDERGOING THERMAL AND FATIGUE LOADING
 1 ULTRASONIC ATTENUATION RESULTS OF THERMOPLASTIC RESIN COMPOSITES UNDERGOING THERMAL AND FATIGUE LOADING Eric I. Madaras NASA Langley Research Center MS 231 Hampton,. VA 23681-0001 INTRODUCTION Before
1 ULTRASONIC ATTENUATION RESULTS OF THERMOPLASTIC RESIN COMPOSITES UNDERGOING THERMAL AND FATIGUE LOADING Eric I. Madaras NASA Langley Research Center MS 231 Hampton,. VA 23681-0001 INTRODUCTION Before
Effectiveness of the hybrid Levine equipercentile and modified frequency estimation equating methods under the common-item nonequivalent groups design
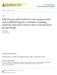 University of Iowa Iowa Research Online Theses and Dissertations 27 Effectiveness of the hybrid Levine equipercentile and modified frequency estimation equating methods under the common-item nonequivalent
University of Iowa Iowa Research Online Theses and Dissertations 27 Effectiveness of the hybrid Levine equipercentile and modified frequency estimation equating methods under the common-item nonequivalent
Generalized Linear. Mixed Models. Methods and Applications. Modern Concepts, Walter W. Stroup. Texts in Statistical Science.
 Texts in Statistical Science Generalized Linear Mixed Models Modern Concepts, Methods and Applications Walter W. Stroup CRC Press Taylor & Francis Croup Boca Raton London New York CRC Press is an imprint
Texts in Statistical Science Generalized Linear Mixed Models Modern Concepts, Methods and Applications Walter W. Stroup CRC Press Taylor & Francis Croup Boca Raton London New York CRC Press is an imprint
A Simulation Study on Confidence Interval Procedures of Some Mean Cumulative Function Estimators
 Statistics Preprints Statistics -00 A Simulation Study on Confidence Interval Procedures of Some Mean Cumulative Function Estimators Jianying Zuo Iowa State University, jiyizu@iastate.edu William Q. Meeker
Statistics Preprints Statistics -00 A Simulation Study on Confidence Interval Procedures of Some Mean Cumulative Function Estimators Jianying Zuo Iowa State University, jiyizu@iastate.edu William Q. Meeker
The Bayesian Approach to Multi-equation Econometric Model Estimation
 Journal of Statistical and Econometric Methods, vol.3, no.1, 2014, 85-96 ISSN: 2241-0384 (print), 2241-0376 (online) Scienpress Ltd, 2014 The Bayesian Approach to Multi-equation Econometric Model Estimation
Journal of Statistical and Econometric Methods, vol.3, no.1, 2014, 85-96 ISSN: 2241-0384 (print), 2241-0376 (online) Scienpress Ltd, 2014 The Bayesian Approach to Multi-equation Econometric Model Estimation
Ultrasonic Testing and Entropy
 Ultrasonic Testing and Entropy Alex Karpelson Kinectrics Inc.; Toronto, Canada; e-mail: alex.karpelson@kinectrics.com Abstract Attempt is described to correlate results of the UT inspection of the object
Ultrasonic Testing and Entropy Alex Karpelson Kinectrics Inc.; Toronto, Canada; e-mail: alex.karpelson@kinectrics.com Abstract Attempt is described to correlate results of the UT inspection of the object
Learning Gaussian Process Models from Uncertain Data
 Learning Gaussian Process Models from Uncertain Data Patrick Dallaire, Camille Besse, and Brahim Chaib-draa DAMAS Laboratory, Computer Science & Software Engineering Department, Laval University, Canada
Learning Gaussian Process Models from Uncertain Data Patrick Dallaire, Camille Besse, and Brahim Chaib-draa DAMAS Laboratory, Computer Science & Software Engineering Department, Laval University, Canada
CHAPTER 2 Estimating Probabilities
 CHAPTER 2 Estimating Probabilities Machine Learning Copyright c 2017. Tom M. Mitchell. All rights reserved. *DRAFT OF September 16, 2017* *PLEASE DO NOT DISTRIBUTE WITHOUT AUTHOR S PERMISSION* This is
CHAPTER 2 Estimating Probabilities Machine Learning Copyright c 2017. Tom M. Mitchell. All rights reserved. *DRAFT OF September 16, 2017* *PLEASE DO NOT DISTRIBUTE WITHOUT AUTHOR S PERMISSION* This is
Estimating terminal half life by non-compartmental methods with some data below the limit of quantification
 Paper SP08 Estimating terminal half life by non-compartmental methods with some data below the limit of quantification Jochen Müller-Cohrs, CSL Behring, Marburg, Germany ABSTRACT In pharmacokinetic studies
Paper SP08 Estimating terminal half life by non-compartmental methods with some data below the limit of quantification Jochen Müller-Cohrs, CSL Behring, Marburg, Germany ABSTRACT In pharmacokinetic studies
Comparing Group Means When Nonresponse Rates Differ
 UNF Digital Commons UNF Theses and Dissertations Student Scholarship 2015 Comparing Group Means When Nonresponse Rates Differ Gabriela M. Stegmann University of North Florida Suggested Citation Stegmann,
UNF Digital Commons UNF Theses and Dissertations Student Scholarship 2015 Comparing Group Means When Nonresponse Rates Differ Gabriela M. Stegmann University of North Florida Suggested Citation Stegmann,
Reliability prediction based on complicated data and dynamic data
 Graduate Theses and Dissertations Graduate College 2009 Reliability prediction based on complicated data and dynamic data Yili Hong Iowa State University Follow this and additional works at: http://lib.dr.iastate.edu/etd
Graduate Theses and Dissertations Graduate College 2009 Reliability prediction based on complicated data and dynamic data Yili Hong Iowa State University Follow this and additional works at: http://lib.dr.iastate.edu/etd
Short Note: Naive Bayes Classifiers and Permanence of Ratios
 Short Note: Naive Bayes Classifiers and Permanence of Ratios Julián M. Ortiz (jmo1@ualberta.ca) Department of Civil & Environmental Engineering University of Alberta Abstract The assumption of permanence
Short Note: Naive Bayes Classifiers and Permanence of Ratios Julián M. Ortiz (jmo1@ualberta.ca) Department of Civil & Environmental Engineering University of Alberta Abstract The assumption of permanence
Statistical Methods for Handling Incomplete Data Chapter 2: Likelihood-based approach
 Statistical Methods for Handling Incomplete Data Chapter 2: Likelihood-based approach Jae-Kwang Kim Department of Statistics, Iowa State University Outline 1 Introduction 2 Observed likelihood 3 Mean Score
Statistical Methods for Handling Incomplete Data Chapter 2: Likelihood-based approach Jae-Kwang Kim Department of Statistics, Iowa State University Outline 1 Introduction 2 Observed likelihood 3 Mean Score
Probabilistic Graphical Models
 Probabilistic Graphical Models David Sontag New York University Lecture 4, February 16, 2012 David Sontag (NYU) Graphical Models Lecture 4, February 16, 2012 1 / 27 Undirected graphical models Reminder
Probabilistic Graphical Models David Sontag New York University Lecture 4, February 16, 2012 David Sontag (NYU) Graphical Models Lecture 4, February 16, 2012 1 / 27 Undirected graphical models Reminder
6.867 Machine Learning
 6.867 Machine Learning Problem Set 2 Due date: Wednesday October 6 Please address all questions and comments about this problem set to 6867-staff@csail.mit.edu. You will need to use MATLAB for some of
6.867 Machine Learning Problem Set 2 Due date: Wednesday October 6 Please address all questions and comments about this problem set to 6867-staff@csail.mit.edu. You will need to use MATLAB for some of
Restricted and Unrestricted Coverings of Complete Bipartite Graphs with Hexagons
 East Tennessee State University Digital Commons @ East Tennessee State University Electronic Theses and Dissertations 5-2013 Restricted and Unrestricted Coverings of Complete Bipartite Graphs with Hexagons
East Tennessee State University Digital Commons @ East Tennessee State University Electronic Theses and Dissertations 5-2013 Restricted and Unrestricted Coverings of Complete Bipartite Graphs with Hexagons
Forecasting Wind Ramps
 Forecasting Wind Ramps Erin Summers and Anand Subramanian Jan 5, 20 Introduction The recent increase in the number of wind power producers has necessitated changes in the methods power system operators
Forecasting Wind Ramps Erin Summers and Anand Subramanian Jan 5, 20 Introduction The recent increase in the number of wind power producers has necessitated changes in the methods power system operators
Contents. Acknowledgments. xix
 Table of Preface Acknowledgments page xv xix 1 Introduction 1 The Role of the Computer in Data Analysis 1 Statistics: Descriptive and Inferential 2 Variables and Constants 3 The Measurement of Variables
Table of Preface Acknowledgments page xv xix 1 Introduction 1 The Role of the Computer in Data Analysis 1 Statistics: Descriptive and Inferential 2 Variables and Constants 3 The Measurement of Variables
Machine Learning, Fall 2009: Midterm
 10-601 Machine Learning, Fall 009: Midterm Monday, November nd hours 1. Personal info: Name: Andrew account: E-mail address:. You are permitted two pages of notes and a calculator. Please turn off all
10-601 Machine Learning, Fall 009: Midterm Monday, November nd hours 1. Personal info: Name: Andrew account: E-mail address:. You are permitted two pages of notes and a calculator. Please turn off all
Part II. Probability, Design and Management in NDE
 Part II Probability, Design and Management in NDE Probability Distributions The probability that a flaw is between x and x + dx is p( xdx ) x p( x ) is the flaw size is the probability density pxdx ( )
Part II Probability, Design and Management in NDE Probability Distributions The probability that a flaw is between x and x + dx is p( xdx ) x p( x ) is the flaw size is the probability density pxdx ( )
Integrated reliable and robust design
 Scholars' Mine Masters Theses Student Research & Creative Works Spring 011 Integrated reliable and robust design Gowrishankar Ravichandran Follow this and additional works at: http://scholarsmine.mst.edu/masters_theses
Scholars' Mine Masters Theses Student Research & Creative Works Spring 011 Integrated reliable and robust design Gowrishankar Ravichandran Follow this and additional works at: http://scholarsmine.mst.edu/masters_theses
Introduction to Maximum Likelihood Estimation
 Introduction to Maximum Likelihood Estimation Eric Zivot July 26, 2012 The Likelihood Function Let 1 be an iid sample with pdf ( ; ) where is a ( 1) vector of parameters that characterize ( ; ) Example:
Introduction to Maximum Likelihood Estimation Eric Zivot July 26, 2012 The Likelihood Function Let 1 be an iid sample with pdf ( ; ) where is a ( 1) vector of parameters that characterize ( ; ) Example:
A Note on Bayesian Inference After Multiple Imputation
 A Note on Bayesian Inference After Multiple Imputation Xiang Zhou and Jerome P. Reiter Abstract This article is aimed at practitioners who plan to use Bayesian inference on multiplyimputed datasets in
A Note on Bayesian Inference After Multiple Imputation Xiang Zhou and Jerome P. Reiter Abstract This article is aimed at practitioners who plan to use Bayesian inference on multiplyimputed datasets in
Part 8: GLMs and Hierarchical LMs and GLMs
 Part 8: GLMs and Hierarchical LMs and GLMs 1 Example: Song sparrow reproductive success Arcese et al., (1992) provide data on a sample from a population of 52 female song sparrows studied over the course
Part 8: GLMs and Hierarchical LMs and GLMs 1 Example: Song sparrow reproductive success Arcese et al., (1992) provide data on a sample from a population of 52 female song sparrows studied over the course
VALUES FOR THE CUMULATIVE DISTRIBUTION FUNCTION OF THE STANDARD MULTIVARIATE NORMAL DISTRIBUTION. Carol Lindee
 VALUES FOR THE CUMULATIVE DISTRIBUTION FUNCTION OF THE STANDARD MULTIVARIATE NORMAL DISTRIBUTION Carol Lindee LindeeEmail@netscape.net (708) 479-3764 Nick Thomopoulos Illinois Institute of Technology Stuart
VALUES FOR THE CUMULATIVE DISTRIBUTION FUNCTION OF THE STANDARD MULTIVARIATE NORMAL DISTRIBUTION Carol Lindee LindeeEmail@netscape.net (708) 479-3764 Nick Thomopoulos Illinois Institute of Technology Stuart
Introduction to Logistic Regression and Support Vector Machine
 Introduction to Logistic Regression and Support Vector Machine guest lecturer: Ming-Wei Chang CS 446 Fall, 2009 () / 25 Fall, 2009 / 25 Before we start () 2 / 25 Fall, 2009 2 / 25 Before we start Feel
Introduction to Logistic Regression and Support Vector Machine guest lecturer: Ming-Wei Chang CS 446 Fall, 2009 () / 25 Fall, 2009 / 25 Before we start () 2 / 25 Fall, 2009 2 / 25 Before we start Feel
n =10,220 observations. Smaller samples analyzed here to illustrate sample size effect.
 Chapter 7 Parametric Likelihood Fitting Concepts: Chapter 7 Parametric Likelihood Fitting Concepts: Objectives Show how to compute a likelihood for a parametric model using discrete data. Show how to compute
Chapter 7 Parametric Likelihood Fitting Concepts: Chapter 7 Parametric Likelihood Fitting Concepts: Objectives Show how to compute a likelihood for a parametric model using discrete data. Show how to compute
Principles of Bayesian Inference
 Principles of Bayesian Inference Sudipto Banerjee University of Minnesota July 20th, 2008 1 Bayesian Principles Classical statistics: model parameters are fixed and unknown. A Bayesian thinks of parameters
Principles of Bayesian Inference Sudipto Banerjee University of Minnesota July 20th, 2008 1 Bayesian Principles Classical statistics: model parameters are fixed and unknown. A Bayesian thinks of parameters
Using the negative log-gamma distribution for Bayesian system reliability assessment
 Graduate Theses and Dissertations Graduate College 2012 Using the negative log-gamma distribution for Bayesian system reliability assessment Roger Zoh Iowa State University Follow this and additional works
Graduate Theses and Dissertations Graduate College 2012 Using the negative log-gamma distribution for Bayesian system reliability assessment Roger Zoh Iowa State University Follow this and additional works
Contents. Part I: Fundamentals of Bayesian Inference 1
 Contents Preface xiii Part I: Fundamentals of Bayesian Inference 1 1 Probability and inference 3 1.1 The three steps of Bayesian data analysis 3 1.2 General notation for statistical inference 4 1.3 Bayesian
Contents Preface xiii Part I: Fundamentals of Bayesian Inference 1 1 Probability and inference 3 1.1 The three steps of Bayesian data analysis 3 1.2 General notation for statistical inference 4 1.3 Bayesian
Measurement error as missing data: the case of epidemiologic assays. Roderick J. Little
 Measurement error as missing data: the case of epidemiologic assays Roderick J. Little Outline Discuss two related calibration topics where classical methods are deficient (A) Limit of quantification methods
Measurement error as missing data: the case of epidemiologic assays Roderick J. Little Outline Discuss two related calibration topics where classical methods are deficient (A) Limit of quantification methods
Bayesian nonparametric estimation of finite population quantities in absence of design information on nonsampled units
 Bayesian nonparametric estimation of finite population quantities in absence of design information on nonsampled units Sahar Z Zangeneh Robert W. Keener Roderick J.A. Little Abstract In Probability proportional
Bayesian nonparametric estimation of finite population quantities in absence of design information on nonsampled units Sahar Z Zangeneh Robert W. Keener Roderick J.A. Little Abstract In Probability proportional
Assessing the Effect of Prior Distribution Assumption on the Variance Parameters in Evaluating Bioequivalence Trials
 Georgia State University ScholarWorks @ Georgia State University Mathematics Theses Department of Mathematics and Statistics 8--006 Assessing the Effect of Prior Distribution Assumption on the Variance
Georgia State University ScholarWorks @ Georgia State University Mathematics Theses Department of Mathematics and Statistics 8--006 Assessing the Effect of Prior Distribution Assumption on the Variance
Experimental Design and Data Analysis for Biologists
 Experimental Design and Data Analysis for Biologists Gerry P. Quinn Monash University Michael J. Keough University of Melbourne CAMBRIDGE UNIVERSITY PRESS Contents Preface page xv I I Introduction 1 1.1
Experimental Design and Data Analysis for Biologists Gerry P. Quinn Monash University Michael J. Keough University of Melbourne CAMBRIDGE UNIVERSITY PRESS Contents Preface page xv I I Introduction 1 1.1
Correlated and Interacting Predictor Omission for Linear and Logistic Regression Models
 Clemson University TigerPrints All Dissertations Dissertations 8-207 Correlated and Interacting Predictor Omission for Linear and Logistic Regression Models Emily Nystrom Clemson University, emily.m.nystrom@gmail.com
Clemson University TigerPrints All Dissertations Dissertations 8-207 Correlated and Interacting Predictor Omission for Linear and Logistic Regression Models Emily Nystrom Clemson University, emily.m.nystrom@gmail.com
Discussion of Maximization by Parts in Likelihood Inference
 Discussion of Maximization by Parts in Likelihood Inference David Ruppert School of Operations Research & Industrial Engineering, 225 Rhodes Hall, Cornell University, Ithaca, NY 4853 email: dr24@cornell.edu
Discussion of Maximization by Parts in Likelihood Inference David Ruppert School of Operations Research & Industrial Engineering, 225 Rhodes Hall, Cornell University, Ithaca, NY 4853 email: dr24@cornell.edu
Evaluating the value of structural heath monitoring with longitudinal performance indicators and hazard functions using Bayesian dynamic predictions
 Evaluating the value of structural heath monitoring with longitudinal performance indicators and hazard functions using Bayesian dynamic predictions C. Xing, R. Caspeele, L. Taerwe Ghent University, Department
Evaluating the value of structural heath monitoring with longitudinal performance indicators and hazard functions using Bayesian dynamic predictions C. Xing, R. Caspeele, L. Taerwe Ghent University, Department
Parametric Techniques
 Parametric Techniques Jason J. Corso SUNY at Buffalo J. Corso (SUNY at Buffalo) Parametric Techniques 1 / 39 Introduction When covering Bayesian Decision Theory, we assumed the full probabilistic structure
Parametric Techniques Jason J. Corso SUNY at Buffalo J. Corso (SUNY at Buffalo) Parametric Techniques 1 / 39 Introduction When covering Bayesian Decision Theory, we assumed the full probabilistic structure
ANALYSIS OF ORDINAL SURVEY RESPONSES WITH DON T KNOW
 SSC Annual Meeting, June 2015 Proceedings of the Survey Methods Section ANALYSIS OF ORDINAL SURVEY RESPONSES WITH DON T KNOW Xichen She and Changbao Wu 1 ABSTRACT Ordinal responses are frequently involved
SSC Annual Meeting, June 2015 Proceedings of the Survey Methods Section ANALYSIS OF ORDINAL SURVEY RESPONSES WITH DON T KNOW Xichen She and Changbao Wu 1 ABSTRACT Ordinal responses are frequently involved
The extreme points of symmetric norms on R^2
 Graduate Theses and Dissertations Iowa State University Capstones, Theses and Dissertations 2008 The extreme points of symmetric norms on R^2 Anchalee Khemphet Iowa State University Follow this and additional
Graduate Theses and Dissertations Iowa State University Capstones, Theses and Dissertations 2008 The extreme points of symmetric norms on R^2 Anchalee Khemphet Iowa State University Follow this and additional
Charles E. McCulloch Biometrics Unit and Statistics Center Cornell University
 A SURVEY OF VARIANCE COMPONENTS ESTIMATION FROM BINARY DATA by Charles E. McCulloch Biometrics Unit and Statistics Center Cornell University BU-1211-M May 1993 ABSTRACT The basic problem of variance components
A SURVEY OF VARIANCE COMPONENTS ESTIMATION FROM BINARY DATA by Charles E. McCulloch Biometrics Unit and Statistics Center Cornell University BU-1211-M May 1993 ABSTRACT The basic problem of variance components
BOOK REVIEW Sampling: Design and Analysis. Sharon L. Lohr. 2nd Edition, International Publication,
 STATISTICS IN TRANSITION-new series, August 2011 223 STATISTICS IN TRANSITION-new series, August 2011 Vol. 12, No. 1, pp. 223 230 BOOK REVIEW Sampling: Design and Analysis. Sharon L. Lohr. 2nd Edition,
STATISTICS IN TRANSITION-new series, August 2011 223 STATISTICS IN TRANSITION-new series, August 2011 Vol. 12, No. 1, pp. 223 230 BOOK REVIEW Sampling: Design and Analysis. Sharon L. Lohr. 2nd Edition,
Regression-Discontinuity Analysis
 Page 1 of 11 Home» Analysis» Inferential Statistics» Regression-Discontinuity Analysis Analysis Requirements The basic RD Design is a two-group pretestposttest model as indicated in the design notation.
Page 1 of 11 Home» Analysis» Inferential Statistics» Regression-Discontinuity Analysis Analysis Requirements The basic RD Design is a two-group pretestposttest model as indicated in the design notation.
