Search Algorithms. Analysis of Algorithms. John Reif, Ph.D. Prepared by
|
|
|
- Amos Fox
- 6 years ago
- Views:
Transcription
1 Search Algorithms Analysis of Algorithms Prepared by John Reif, Ph.D.
2 Search Algorithms a) Binary Search: average case b) Interpolation Search c) Unbounded Search (Advanced material)
3 Readings Reading Selection: CLR, Chapter 12
4 Binary Search Trees (in sorted Table of) keys k 0,, k n-1 Binary Search Tree property: at each node x key (x) > key (y) # y nodes on left subtree of x key (x) < key (z) # z nodes on right subtree of x
5 Binary Search Trees (cont d)
6 Binary Search Trees (cont d) Assume 1) Keys inserted into tree in random order 2) Search with all keys equally likely length = # of edges n + 1 = number of leaves Internal path length I = sum of lengths of all internal paths of length > 1 (from root to nonleaves)
7 Binary Search Trees (cont d) External path length E = sum of lengths of all external paths (from root to leaves) = I + 2n
8 Successful Search Expected # comparisons C = 1 + (I/n) n! n-1 " # i + $ % i= 0 & = (C' 1) / n
9 Unsuccessful Search Expected # comparisons C' = E/(n+1) = (I+2n)/(n+1) n = (n C n +n)/(n+1) n-1! " # i + $ % i=0 & = (C' 2) / (n+1) n 2 = 2 ln(n) (i+1) i=0 = log n
10 Model of Random Real Inputs over an Interval Input Set S of n keys each independently randomly chosen over real interval L,U for 0 < L < U Operations Comparison operations +, -, *, % operations: r =largest integer below or equal to r r = smallest integer above of equal to r
11 Sorting and Selection with Random Real Inputs Results 1) Sorting in 0(n) expected time 2) Selection in 0(loglogn) expected time
12 Bucket Sorting with Random Inputs Input set of n keys, S randomly chosen over [L,U] Algorithm BUCKEY-SORT(S): begin end for i = 1 to n do B[i] empty list for to do for $ n(x -L) % ' &! (U-L)! " '" i i = 1 n add x i to B & + 1 i output = 1 to n do sort (B[i]) B[1] B[2] B[n]
13 Bucket Sorting with Random Inputs (cont d) Theorem The expected time T of BUCKET-SORT is 0(n) Proof B[i] is upper bounded by a Binomial 1 variable with parameters n, p = n Hence c>1 i,j Prob { B[i] > j} < c n -j So T n c (jlogj) = O(n) j=0 Generalizes to case keys have nonuniform distribution -j
14 Random Search Table Table X = (x 0 < x 1 < < x n < x n+1 ) where x 1,, x n random reals chosen independently from interval (x 0, x n+1 ) Selection Problem Input key Y Problem find index k* with X k* = Y Note k* has Binomial distribution with parameters n,p = (Y-X 0 )/(X n+1 -X 0 )
15 Algorithm PSEUDO INTERPOLATION-SEARCH (X,Y) Random Table X = (X 0, X 1,, X n, X n+1 ) Algorithm pseudo interpolation search (X,Y) [0] k pn where p = (Y-X 0 )/(X n+1 -X 0 ) [1] if Y = X k then return k
16 Algorithm PSEUDO INTERPOLATION- SEARCH (X,Y) (cont d) [2] If Y > X k then for if k' = k, k+ n, k+2 n,... Y < X then exit with " k'+ n! output pseudo interpolation search (X,Y) where X' = (X k',...,x ) k'+ n
17 Algorithm PSEUDO INTERPOLATION- SEARCH (X,Y) (cont d) [3] Else if Y < X k then for if k' = k, k- n, k-2 n,... Y > X then exit with output pseudo interpolation search (X,Y) where " k'- n! X" = (X,..., X ) k'- n k'
18 Probability Distribution of Pseudo Interpolation Search
19 Probabilistic Analysis of Pseudo Interpolation Search k* is Binomial with mean pn variance σ 2 = p(1-p)n So * k Hence " # pn σ approximates normal as n grows * " # $ % k pn Prob * Z Ψ(Z)/Z σ +, - where Ψ(Z) = 2 -Z 2 e 2π
20 Probabilistic Analysis of Pseudo Interpolation Search (cont d) So Prob ( < i probes used in given call) *! " < Prob( k pn > (i - 2) n ) Ψ(Z )/Z where i i (i - 2) n (i - 2) Z i = = 2(i - 2) σ p(i-p) since p(1-p) 1 4
21 Probabilistic Analysis of Pseudo Interpolation Search (cont d) Lemma C 2.03 where C = expected number of probes in given call proof C = i>1 i>1 i Prob(i probes used) = Prob( i probes used) 2 + Ψ(Z )/Z 2.03 i 3 i i
22 Probabilistic Analysis of Pseudo Interpolation Search (cont d) Theorem Pseudo Interpolation Search has expected time T(n) C loglogn proof T(n) C + T( n ) C loglogn
23 Algorithm INTERPOLATION-SEARCH (X,Y) 1) Initialize k = np comment k = E(k*) 1) If X k = Y then return k 2) If X k < Y then output INTERPOLATION-SEARCH (X,Y) where X = (x k,, x n+1 ) 3) Else X k > Y and output INTERPOLATION-SEARCH (X,Y) where X = (x 0,, x k )
24 Probability Distribution of INTERPOLATION-SEARCH (X,Y)
25 Advanced Material: Probabilistic Analysis of Interpolation Search Lemma Prob( k * " pn # 0( nlogn)) 1 n a where a is a constant Proof Since k* is Binomial with parameters p,n 2 -Z Prob( k * pn Za) 2 e 2 Z 2π 1 n a for σ 2 = p(1-p)n and Z = 0( logn )
26 Probabilistic Analysis of Interpolation Search (cont d) Theorem The expected number of comparisons of Interpolation Search is T(n) loglogn + c (logloglogn) 1 2
27 Probabilistic Analysis of Interpolation Search (cont d) Proof! T(n) 1+ (1-1 n ) T (O( n log n )) + n #! # " a n a $ 1+ loglog n log n + c 1 logloglog n log n ) 2 + o(1) & 1+ log( 1 ' 2 logn ) + + c 1 (logloglogn) 2 * loglogn + c 1 (logloglogn) 2 since log2=1
28 Advance Material: Unbounded Search Input table X[1], X[2], where for j = 1, 2, X[j] =! 0 j < n " $ 1 j n Unbounded Search Problem Find n such that X[n-1] = 0 and X[n]=1 Cost for algorithm A: C A (n)=m if algorithm A uses m evaluations to determine that n is the solution to the unbounded search problem
29 Applications of Unbounded Search 1) Table Look-up in an ordered, infinite table 2) Binary encoding of integers if S n represents integer n, then S n is not a prefix of any S j for n > j {S 1, S 2, } called a prefix set Idea: use S n (b 1, b 2,, b CA (n) ) where b m = 1 if the m th evaluation of X is 1 in algorithm A for unbounded search
30 Unary Unbounded Search Algorithm Algorithm B 0 Try X[1], X[2],, until X[n] = 1 Cost C B0 (n) = n
31 Binary Unbounded Search Algorithm Algorithm B 1 1st stage i try X[2-1] for i=1,2,...,m m until X[2-1]=1 m-1 m ( cost m = logn + 1 where 2 n 2 1)! " m-1 2 nd stage binary search over 2 elements cost log(2 m-1 ) = m-1= logn! " Total Cost C (n) = 2 logn + 1! " B 1
32 Binary Unbounded Search Algorithm (cont d)
33 Double Unbounded Search Search Algorithm B 2 1st stage 1 m1 (2 1) (2 1) try X[2-1],..., X[2 ] = 1 where m = logn (cost is C (m ) = 2 logm + 1) B 1 " 1# 1 " # 2 nd stage same as 2nd stage of B after m was found. Total Cost Cost is C B 0 (n) = m-1= logn C (n) = C (m ) + C (n) B B 1 B = 2( log ( logn+1) + 1 ) + logn 1 " # " " # # " #
34 Double Unbounded Search Algorithm (cont d)
35 Ultimate Unbounded Search Algorithm
36 Search Algorithms Analysis of Algorithms Prepared by John Reif, Ph.D.
ALG 2.2 Search Algorithms
 Algorithms Professor Joh Reif ALG 2.2 Search Algorithms (a Biary Search: average case (b Biary Search with Errors (homework (c Iterpolatio Search (d Ubouded Search Biary Search Trees (i sorted Table of
Algorithms Professor Joh Reif ALG 2.2 Search Algorithms (a Biary Search: average case (b Biary Search with Errors (homework (c Iterpolatio Search (d Ubouded Search Biary Search Trees (i sorted Table of
Data structures Exercise 1 solution. Question 1. Let s start by writing all the functions in big O notation:
 Data structures Exercise 1 solution Question 1 Let s start by writing all the functions in big O notation: f 1 (n) = 2017 = O(1), f 2 (n) = 2 log 2 n = O(n 2 ), f 3 (n) = 2 n = O(2 n ), f 4 (n) = 1 = O
Data structures Exercise 1 solution Question 1 Let s start by writing all the functions in big O notation: f 1 (n) = 2017 = O(1), f 2 (n) = 2 log 2 n = O(n 2 ), f 3 (n) = 2 n = O(2 n ), f 4 (n) = 1 = O
Design and Analysis of Algorithms
 CSE 101, Winter 2018 Design and Analysis of Algorithms Lecture 5: Divide and Conquer (Part 2) Class URL: http://vlsicad.ucsd.edu/courses/cse101-w18/ A Lower Bound on Convex Hull Lecture 4 Task: sort the
CSE 101, Winter 2018 Design and Analysis of Algorithms Lecture 5: Divide and Conquer (Part 2) Class URL: http://vlsicad.ucsd.edu/courses/cse101-w18/ A Lower Bound on Convex Hull Lecture 4 Task: sort the
Data Structures and Algorithms
 Data Structures and Algorithms Spring 2017-2018 Outline 1 Sorting Algorithms (contd.) Outline Sorting Algorithms (contd.) 1 Sorting Algorithms (contd.) Analysis of Quicksort Time to sort array of length
Data Structures and Algorithms Spring 2017-2018 Outline 1 Sorting Algorithms (contd.) Outline Sorting Algorithms (contd.) 1 Sorting Algorithms (contd.) Analysis of Quicksort Time to sort array of length
Outline. Computer Science 331. Cost of Binary Search Tree Operations. Bounds on Height: Worst- and Average-Case
 Outline Computer Science Average Case Analysis: Binary Search Trees Mike Jacobson Department of Computer Science University of Calgary Lecture #7 Motivation and Objective Definition 4 Mike Jacobson (University
Outline Computer Science Average Case Analysis: Binary Search Trees Mike Jacobson Department of Computer Science University of Calgary Lecture #7 Motivation and Objective Definition 4 Mike Jacobson (University
Analysis of Approximate Quickselect and Related Problems
 Analysis of Approximate Quickselect and Related Problems Conrado Martínez Univ. Politècnica Catalunya Joint work with A. Panholzer and H. Prodinger LIP6, Paris, April 2009 Introduction Quickselect finds
Analysis of Approximate Quickselect and Related Problems Conrado Martínez Univ. Politècnica Catalunya Joint work with A. Panholzer and H. Prodinger LIP6, Paris, April 2009 Introduction Quickselect finds
Fundamental Algorithms
 Chapter 2: Sorting, Winter 2018/19 1 Fundamental Algorithms Chapter 2: Sorting Jan Křetínský Winter 2018/19 Chapter 2: Sorting, Winter 2018/19 2 Part I Simple Sorts Chapter 2: Sorting, Winter 2018/19 3
Chapter 2: Sorting, Winter 2018/19 1 Fundamental Algorithms Chapter 2: Sorting Jan Křetínský Winter 2018/19 Chapter 2: Sorting, Winter 2018/19 2 Part I Simple Sorts Chapter 2: Sorting, Winter 2018/19 3
Fundamental Algorithms
 Fundamental Algorithms Chapter 2: Sorting Harald Räcke Winter 2015/16 Chapter 2: Sorting, Winter 2015/16 1 Part I Simple Sorts Chapter 2: Sorting, Winter 2015/16 2 The Sorting Problem Definition Sorting
Fundamental Algorithms Chapter 2: Sorting Harald Räcke Winter 2015/16 Chapter 2: Sorting, Winter 2015/16 1 Part I Simple Sorts Chapter 2: Sorting, Winter 2015/16 2 The Sorting Problem Definition Sorting
Randomized Sorting Algorithms Quick sort can be converted to a randomized algorithm by picking the pivot element randomly. In this case we can show th
 CSE 3500 Algorithms and Complexity Fall 2016 Lecture 10: September 29, 2016 Quick sort: Average Run Time In the last lecture we started analyzing the expected run time of quick sort. Let X = k 1, k 2,...,
CSE 3500 Algorithms and Complexity Fall 2016 Lecture 10: September 29, 2016 Quick sort: Average Run Time In the last lecture we started analyzing the expected run time of quick sort. Let X = k 1, k 2,...,
Design and Analysis of Algorithms
 CSE 101, Winter 2018 Design and Analysis of Algorithms Lecture 4: Divide and Conquer (I) Class URL: http://vlsicad.ucsd.edu/courses/cse101-w18/ Divide and Conquer ( DQ ) First paradigm or framework DQ(S)
CSE 101, Winter 2018 Design and Analysis of Algorithms Lecture 4: Divide and Conquer (I) Class URL: http://vlsicad.ucsd.edu/courses/cse101-w18/ Divide and Conquer ( DQ ) First paradigm or framework DQ(S)
Fundamental Algorithms
 Fundamental Algorithms Chapter 5: Searching Michael Bader Winter 2014/15 Chapter 5: Searching, Winter 2014/15 1 Searching Definition (Search Problem) Input: a sequence or set A of n elements (objects)
Fundamental Algorithms Chapter 5: Searching Michael Bader Winter 2014/15 Chapter 5: Searching, Winter 2014/15 1 Searching Definition (Search Problem) Input: a sequence or set A of n elements (objects)
PROBABILITY AND STATISTICS IN COMPUTING. III. Discrete Random Variables Expectation and Deviations From: [5][7][6] German Hernandez
![PROBABILITY AND STATISTICS IN COMPUTING. III. Discrete Random Variables Expectation and Deviations From: [5][7][6] German Hernandez PROBABILITY AND STATISTICS IN COMPUTING. III. Discrete Random Variables Expectation and Deviations From: [5][7][6] German Hernandez](/thumbs/89/97686901.jpg) Conditional PROBABILITY AND STATISTICS IN COMPUTING III. Discrete Random Variables and Deviations From: [5][7][6] Page of 46 German Hernandez Conditional. Random variables.. Measurable function Let (Ω,
Conditional PROBABILITY AND STATISTICS IN COMPUTING III. Discrete Random Variables and Deviations From: [5][7][6] Page of 46 German Hernandez Conditional. Random variables.. Measurable function Let (Ω,
Randomized Load Balancing:The Power of 2 Choices
 Randomized Load Balancing: The Power of 2 Choices June 3, 2010 Balls and Bins Problem We have m balls that are thrown into n bins, the location of each ball chosen independently and uniformly at random
Randomized Load Balancing: The Power of 2 Choices June 3, 2010 Balls and Bins Problem We have m balls that are thrown into n bins, the location of each ball chosen independently and uniformly at random
Sorting algorithms. Sorting algorithms
 Properties of sorting algorithms A sorting algorithm is Comparison based If it works by pairwise key comparisons. In place If only a constant number of elements of the input array are ever stored outside
Properties of sorting algorithms A sorting algorithm is Comparison based If it works by pairwise key comparisons. In place If only a constant number of elements of the input array are ever stored outside
Random Variable. Pr(X = a) = Pr(s)
 Random Variable Definition A random variable X on a sample space Ω is a real-valued function on Ω; that is, X : Ω R. A discrete random variable is a random variable that takes on only a finite or countably
Random Variable Definition A random variable X on a sample space Ω is a real-valued function on Ω; that is, X : Ω R. A discrete random variable is a random variable that takes on only a finite or countably
The Separating Words Problem
 The Separating Words Problem Jeffrey Shallit School of Computer Science University of Waterloo Waterloo, Ontario N2L 3G1 Canada shallit@cs.uwaterloo.ca https://www.cs.uwaterloo.ca/~shallit 1/54 The Simplest
The Separating Words Problem Jeffrey Shallit School of Computer Science University of Waterloo Waterloo, Ontario N2L 3G1 Canada shallit@cs.uwaterloo.ca https://www.cs.uwaterloo.ca/~shallit 1/54 The Simplest
Sorting. Chapter 11. CSE 2011 Prof. J. Elder Last Updated: :11 AM
 Sorting Chapter 11-1 - Sorting Ø We have seen the advantage of sorted data representations for a number of applications q Sparse vectors q Maps q Dictionaries Ø Here we consider the problem of how to efficiently
Sorting Chapter 11-1 - Sorting Ø We have seen the advantage of sorted data representations for a number of applications q Sparse vectors q Maps q Dictionaries Ø Here we consider the problem of how to efficiently
Coding of memoryless sources 1/35
 Coding of memoryless sources 1/35 Outline 1. Morse coding ; 2. Definitions : encoding, encoding efficiency ; 3. fixed length codes, encoding integers ; 4. prefix condition ; 5. Kraft and Mac Millan theorems
Coding of memoryless sources 1/35 Outline 1. Morse coding ; 2. Definitions : encoding, encoding efficiency ; 3. fixed length codes, encoding integers ; 4. prefix condition ; 5. Kraft and Mac Millan theorems
Algorithms PART II: Partitioning and Divide & Conquer. HPC Fall 2007 Prof. Robert van Engelen
 Algorithms PART II: Partitioning and Divide & Conquer HPC Fall 2007 Prof. Robert van Engelen Overview Partitioning strategies Divide and conquer strategies Further reading HPC Fall 2007 2 Partitioning
Algorithms PART II: Partitioning and Divide & Conquer HPC Fall 2007 Prof. Robert van Engelen Overview Partitioning strategies Divide and conquer strategies Further reading HPC Fall 2007 2 Partitioning
Probability Theory Overview and Analysis of Randomized Algorithms
 Probability Theory Overview and Analysis of Randomized Algorithms Analysis of Algorithms Prepared by John Reif, Ph.D. Probability Theory Topics a) Random Variables: Binomial and Geometric b) Useful Probabilistic
Probability Theory Overview and Analysis of Randomized Algorithms Analysis of Algorithms Prepared by John Reif, Ph.D. Probability Theory Topics a) Random Variables: Binomial and Geometric b) Useful Probabilistic
CS Data Structures and Algorithm Analysis
 CS 483 - Data Structures and Algorithm Analysis Lecture VII: Chapter 6, part 2 R. Paul Wiegand George Mason University, Department of Computer Science March 22, 2006 Outline 1 Balanced Trees 2 Heaps &
CS 483 - Data Structures and Algorithm Analysis Lecture VII: Chapter 6, part 2 R. Paul Wiegand George Mason University, Department of Computer Science March 22, 2006 Outline 1 Balanced Trees 2 Heaps &
Data Compression Techniques (Spring 2012) Model Solutions for Exercise 2
 582487 Data Compression Techniques (Spring 22) Model Solutions for Exercise 2 If you have any feedback or corrections, please contact nvalimak at cs.helsinki.fi.. Problem: Construct a canonical prefix
582487 Data Compression Techniques (Spring 22) Model Solutions for Exercise 2 If you have any feedback or corrections, please contact nvalimak at cs.helsinki.fi.. Problem: Construct a canonical prefix
R ij = 2. Using all of these facts together, you can solve problem number 9.
 Help for Homework Problem #9 Let G(V,E) be any undirected graph We want to calculate the travel time across the graph. Think of each edge as one resistor of 1 Ohm. Say we have two nodes: i and j Let the
Help for Homework Problem #9 Let G(V,E) be any undirected graph We want to calculate the travel time across the graph. Think of each edge as one resistor of 1 Ohm. Say we have two nodes: i and j Let the
Legendre s Equation. PHYS Southern Illinois University. October 18, 2016
 Legendre s Equation PHYS 500 - Southern Illinois University October 18, 2016 PHYS 500 - Southern Illinois University Legendre s Equation October 18, 2016 1 / 11 Legendre s Equation Recall We are trying
Legendre s Equation PHYS 500 - Southern Illinois University October 18, 2016 PHYS 500 - Southern Illinois University Legendre s Equation October 18, 2016 1 / 11 Legendre s Equation Recall We are trying
Advanced Implementations of Tables: Balanced Search Trees and Hashing
 Advanced Implementations of Tables: Balanced Search Trees and Hashing Balanced Search Trees Binary search tree operations such as insert, delete, retrieve, etc. depend on the length of the path to the
Advanced Implementations of Tables: Balanced Search Trees and Hashing Balanced Search Trees Binary search tree operations such as insert, delete, retrieve, etc. depend on the length of the path to the
Automata Theory CS Complexity Theory I: Polynomial Time
 Automata Theory CS411-2015-17 Complexity Theory I: Polynomial Time David Galles Department of Computer Science University of San Francisco 17-0: Tractable vs. Intractable If a problem is recursive, then
Automata Theory CS411-2015-17 Complexity Theory I: Polynomial Time David Galles Department of Computer Science University of San Francisco 17-0: Tractable vs. Intractable If a problem is recursive, then
Entropy Coding. Connectivity coding. Entropy coding. Definitions. Lossles coder. Input: a set of symbols Output: bitstream. Idea
 Connectivity coding Entropy Coding dd 7, dd 6, dd 7, dd 5,... TG output... CRRRLSLECRRE Entropy coder output Connectivity data Edgebreaker output Digital Geometry Processing - Spring 8, Technion Digital
Connectivity coding Entropy Coding dd 7, dd 6, dd 7, dd 5,... TG output... CRRRLSLECRRE Entropy coder output Connectivity data Edgebreaker output Digital Geometry Processing - Spring 8, Technion Digital
Cluster Validity. Oct. 28, Cluster Validity 10/14/ Erin Wirch & Wenbo Wang. Outline. Hypothesis Testing. Relative Criteria.
 1 Testing Oct. 28, 2010 2 Testing Testing Agenda 3 Testing Review of Testing Testing Review of Testing 4 Test a parameter against a specific value Begin with H 0 and H 1 as the null and alternative hypotheses
1 Testing Oct. 28, 2010 2 Testing Testing Agenda 3 Testing Review of Testing Testing Review of Testing 4 Test a parameter against a specific value Begin with H 0 and H 1 as the null and alternative hypotheses
Optimal Bounds for the Predecessor Problem and Related Problems
 Optimal Bounds for the Predecessor Problem and Related Problems Paul Beame Computer Science and Engineering University of Washington Seattle, WA, USA 98195-2350 beame@cs.washington.edu Faith E. Fich Department
Optimal Bounds for the Predecessor Problem and Related Problems Paul Beame Computer Science and Engineering University of Washington Seattle, WA, USA 98195-2350 beame@cs.washington.edu Faith E. Fich Department
Models of Computation
 Models of Computation Analysis of Algorithms Week 1, Lecture 2 Prepared by John Reif, Ph.D. Distinguished Professor of Computer Science Duke University Models of Computation (RAM) a) Random Access Machines
Models of Computation Analysis of Algorithms Week 1, Lecture 2 Prepared by John Reif, Ph.D. Distinguished Professor of Computer Science Duke University Models of Computation (RAM) a) Random Access Machines
CMPT 307 : Divide-and-Conqer (Study Guide) Should be read in conjunction with the text June 2, 2015
 CMPT 307 : Divide-and-Conqer (Study Guide) Should be read in conjunction with the text June 2, 2015 1 Introduction The divide-and-conquer strategy is a general paradigm for algorithm design. This strategy
CMPT 307 : Divide-and-Conqer (Study Guide) Should be read in conjunction with the text June 2, 2015 1 Introduction The divide-and-conquer strategy is a general paradigm for algorithm design. This strategy
An instantaneous code (prefix code, tree code) with the codeword lengths l 1,..., l N exists if and only if. 2 l i. i=1
 Kraft s inequality An instantaneous code (prefix code, tree code) with the codeword lengths l 1,..., l N exists if and only if N 2 l i 1 Proof: Suppose that we have a tree code. Let l max = max{l 1,...,
Kraft s inequality An instantaneous code (prefix code, tree code) with the codeword lengths l 1,..., l N exists if and only if N 2 l i 1 Proof: Suppose that we have a tree code. Let l max = max{l 1,...,
Average Case Analysis of QuickSort and Insertion Tree Height using Incompressibility
 Average Case Analysis of QuickSort and Insertion Tree Height using Incompressibility Tao Jiang, Ming Li, Brendan Lucier September 26, 2005 Abstract In this paper we study the Kolmogorov Complexity of a
Average Case Analysis of QuickSort and Insertion Tree Height using Incompressibility Tao Jiang, Ming Li, Brendan Lucier September 26, 2005 Abstract In this paper we study the Kolmogorov Complexity of a
Mathematical Induction Assignments
 1 Mathematical Induction Assignments Prove the Following using Principle of Mathematical induction 1) Prove that for any positive integer number n, n 3 + 2 n is divisible by 3 2) Prove that 1 3 + 2 3 +
1 Mathematical Induction Assignments Prove the Following using Principle of Mathematical induction 1) Prove that for any positive integer number n, n 3 + 2 n is divisible by 3 2) Prove that 1 3 + 2 3 +
COS597D: Information Theory in Computer Science October 19, Lecture 10
 COS597D: Information Theory in Computer Science October 9, 20 Lecture 0 Lecturer: Mark Braverman Scribe: Andrej Risteski Kolmogorov Complexity In the previous lectures, we became acquainted with the concept
COS597D: Information Theory in Computer Science October 9, 20 Lecture 0 Lecturer: Mark Braverman Scribe: Andrej Risteski Kolmogorov Complexity In the previous lectures, we became acquainted with the concept
ICS141: Discrete Mathematics for Computer Science I
 ICS141: Discrete Mathematics for Computer Science I Dept. Information & Computer Sci., Jan Stelovsky based on slides by Dr. Baek and Dr. Still Originals by Dr. M. P. Frank and Dr. J.L. Gross Provided by
ICS141: Discrete Mathematics for Computer Science I Dept. Information & Computer Sci., Jan Stelovsky based on slides by Dr. Baek and Dr. Still Originals by Dr. M. P. Frank and Dr. J.L. Gross Provided by
Multiple Choice Tries and Distributed Hash Tables
 Multiple Choice Tries and Distributed Hash Tables Luc Devroye and Gabor Lugosi and Gahyun Park and W. Szpankowski January 3, 2007 McGill University, Montreal, Canada U. Pompeu Fabra, Barcelona, Spain U.
Multiple Choice Tries and Distributed Hash Tables Luc Devroye and Gabor Lugosi and Gahyun Park and W. Szpankowski January 3, 2007 McGill University, Montreal, Canada U. Pompeu Fabra, Barcelona, Spain U.
Lecture 7: Dynamic Programming I: Optimal BSTs
 5-750: Graduate Algorithms February, 06 Lecture 7: Dynamic Programming I: Optimal BSTs Lecturer: David Witmer Scribes: Ellango Jothimurugesan, Ziqiang Feng Overview The basic idea of dynamic programming
5-750: Graduate Algorithms February, 06 Lecture 7: Dynamic Programming I: Optimal BSTs Lecturer: David Witmer Scribes: Ellango Jothimurugesan, Ziqiang Feng Overview The basic idea of dynamic programming
Binary Search Trees. Motivation
 Binary Search Trees Motivation Searching for a particular record in an unordered list takes O(n), too slow for large lists (databases) If the list is ordered, can use an array implementation and use binary
Binary Search Trees Motivation Searching for a particular record in an unordered list takes O(n), too slow for large lists (databases) If the list is ordered, can use an array implementation and use binary
THE REAL NUMBERS Chapter #4
 FOUNDATIONS OF ANALYSIS FALL 2008 TRUE/FALSE QUESTIONS THE REAL NUMBERS Chapter #4 (1) Every element in a field has a multiplicative inverse. (2) In a field the additive inverse of 1 is 0. (3) In a field
FOUNDATIONS OF ANALYSIS FALL 2008 TRUE/FALSE QUESTIONS THE REAL NUMBERS Chapter #4 (1) Every element in a field has a multiplicative inverse. (2) In a field the additive inverse of 1 is 0. (3) In a field
4.4 Recurrences and Big-O
 4.4. RECURRENCES AND BIG-O 91 4.4 Recurrences and Big-O In this section, we will extend our knowledge of recurrences, showing how to solve recurrences with big-o s in them, recurrences in which n b k,
4.4. RECURRENCES AND BIG-O 91 4.4 Recurrences and Big-O In this section, we will extend our knowledge of recurrences, showing how to solve recurrences with big-o s in them, recurrences in which n b k,
CSC236H Lecture 2. Ilir Dema. September 19, 2018
 CSC236H Lecture 2 Ilir Dema September 19, 2018 Simple Induction Useful to prove statements depending on natural numbers Define a predicate P(n) Prove the base case P(b) Prove that for all n b, P(n) P(n
CSC236H Lecture 2 Ilir Dema September 19, 2018 Simple Induction Useful to prove statements depending on natural numbers Define a predicate P(n) Prove the base case P(b) Prove that for all n b, P(n) P(n
k-protected VERTICES IN BINARY SEARCH TREES
 k-protected VERTICES IN BINARY SEARCH TREES MIKLÓS BÓNA Abstract. We show that for every k, the probability that a randomly selected vertex of a random binary search tree on n nodes is at distance k from
k-protected VERTICES IN BINARY SEARCH TREES MIKLÓS BÓNA Abstract. We show that for every k, the probability that a randomly selected vertex of a random binary search tree on n nodes is at distance k from
Ch 01. Analysis of Algorithms
 Ch 01. Analysis of Algorithms Input Algorithm Output Acknowledgement: Parts of slides in this presentation come from the materials accompanying the textbook Algorithm Design and Applications, by M. T.
Ch 01. Analysis of Algorithms Input Algorithm Output Acknowledgement: Parts of slides in this presentation come from the materials accompanying the textbook Algorithm Design and Applications, by M. T.
CSE 613: Parallel Programming. Lecture 9 ( Divide-and-Conquer: Partitioning for Selection and Sorting )
 CSE 613: Parallel Programming Lecture 9 ( Divide-and-Conquer: Partitioning for Selection and Sorting ) Rezaul A. Chowdhury Department of Computer Science SUNY Stony Brook Spring 2012 Parallel Partition
CSE 613: Parallel Programming Lecture 9 ( Divide-and-Conquer: Partitioning for Selection and Sorting ) Rezaul A. Chowdhury Department of Computer Science SUNY Stony Brook Spring 2012 Parallel Partition
Input Decidable Language -- Program Halts on all Input Encoding of Input -- Natural Numbers Encoded in Binary or Decimal, Not Unary
 Complexity Analysis Complexity Theory Input Decidable Language -- Program Halts on all Input Encoding of Input -- Natural Numbers Encoded in Binary or Decimal, Not Unary Output TRUE or FALSE Time and Space
Complexity Analysis Complexity Theory Input Decidable Language -- Program Halts on all Input Encoding of Input -- Natural Numbers Encoded in Binary or Decimal, Not Unary Output TRUE or FALSE Time and Space
Lecture 16. Error-free variable length schemes (contd.): Shannon-Fano-Elias code, Huffman code
 Lecture 16 Agenda for the lecture Error-free variable length schemes (contd.): Shannon-Fano-Elias code, Huffman code Variable-length source codes with error 16.1 Error-free coding schemes 16.1.1 The Shannon-Fano-Elias
Lecture 16 Agenda for the lecture Error-free variable length schemes (contd.): Shannon-Fano-Elias code, Huffman code Variable-length source codes with error 16.1 Error-free coding schemes 16.1.1 The Shannon-Fano-Elias
1 Circuit Complexity. CS 6743 Lecture 15 1 Fall Definitions
 CS 6743 Lecture 15 1 Fall 2007 1 Circuit Complexity 1.1 Definitions A Boolean circuit C on n inputs x 1,..., x n is a directed acyclic graph (DAG) with n nodes of in-degree 0 (the inputs x 1,..., x n ),
CS 6743 Lecture 15 1 Fall 2007 1 Circuit Complexity 1.1 Definitions A Boolean circuit C on n inputs x 1,..., x n is a directed acyclic graph (DAG) with n nodes of in-degree 0 (the inputs x 1,..., x n ),
SIMPLE RANDOM WALKS: IMPROBABILITY OF PROFITABLE STOPPING
 SIMPLE RANDOM WALKS: IMPROBABILITY OF PROFITABLE STOPPING EMILY GENTLES Abstract. This paper introduces the basics of the simple random walk with a flair for the statistical approach. Applications in biology
SIMPLE RANDOM WALKS: IMPROBABILITY OF PROFITABLE STOPPING EMILY GENTLES Abstract. This paper introduces the basics of the simple random walk with a flair for the statistical approach. Applications in biology
Cardinality Networks: a Theoretical and Empirical Study
 Constraints manuscript No. (will be inserted by the editor) Cardinality Networks: a Theoretical and Empirical Study Roberto Asín, Robert Nieuwenhuis, Albert Oliveras, Enric Rodríguez-Carbonell Received:
Constraints manuscript No. (will be inserted by the editor) Cardinality Networks: a Theoretical and Empirical Study Roberto Asín, Robert Nieuwenhuis, Albert Oliveras, Enric Rodríguez-Carbonell Received:
CSI Mathematical Induction. Many statements assert that a property of the form P(n) is true for all integers n.
 CSI 2101- Mathematical Induction Many statements assert that a property of the form P(n) is true for all integers n. Examples: For every positive integer n: n! n n Every set with n elements, has 2 n Subsets.
CSI 2101- Mathematical Induction Many statements assert that a property of the form P(n) is true for all integers n. Examples: For every positive integer n: n! n n Every set with n elements, has 2 n Subsets.
4.8 Huffman Codes. These lecture slides are supplied by Mathijs de Weerd
 4.8 Huffman Codes These lecture slides are supplied by Mathijs de Weerd Data Compression Q. Given a text that uses 32 symbols (26 different letters, space, and some punctuation characters), how can we
4.8 Huffman Codes These lecture slides are supplied by Mathijs de Weerd Data Compression Q. Given a text that uses 32 symbols (26 different letters, space, and some punctuation characters), how can we
Y fli log (1/fli)+ ce log (1/at) is the entropy of the frequency distribution. This
 SIAM J. COMPUT. Vol. 6, No. 2, June 1977 A BEST POSSIBLE BOUND FOR THE WEIGHTED PATH LENGTH OF BINARY SEARCH TREES* KURT MEHLHORN Abstract. The weighted path length of optimum binary search trees is bounded
SIAM J. COMPUT. Vol. 6, No. 2, June 1977 A BEST POSSIBLE BOUND FOR THE WEIGHTED PATH LENGTH OF BINARY SEARCH TREES* KURT MEHLHORN Abstract. The weighted path length of optimum binary search trees is bounded
An algorithm for the satisfiability problem of formulas in conjunctive normal form
 Journal of Algorithms 54 (2005) 40 44 www.elsevier.com/locate/jalgor An algorithm for the satisfiability problem of formulas in conjunctive normal form Rainer Schuler Abt. Theoretische Informatik, Universität
Journal of Algorithms 54 (2005) 40 44 www.elsevier.com/locate/jalgor An algorithm for the satisfiability problem of formulas in conjunctive normal form Rainer Schuler Abt. Theoretische Informatik, Universität
Ch01. Analysis of Algorithms
 Ch01. Analysis of Algorithms Input Algorithm Output Acknowledgement: Parts of slides in this presentation come from the materials accompanying the textbook Algorithm Design and Applications, by M. T. Goodrich
Ch01. Analysis of Algorithms Input Algorithm Output Acknowledgement: Parts of slides in this presentation come from the materials accompanying the textbook Algorithm Design and Applications, by M. T. Goodrich
Proofs Not Based On POMI
 s Not Based On POMI James K. Peterson Department of Biological Sciences and Department of Mathematical Sciences Clemson University February 1, 018 Outline Non POMI Based s Some Contradiction s Triangle
s Not Based On POMI James K. Peterson Department of Biological Sciences and Department of Mathematical Sciences Clemson University February 1, 018 Outline Non POMI Based s Some Contradiction s Triangle
Exercises with solutions (Set B)
 Exercises with solutions (Set B) 3. A fair coin is tossed an infinite number of times. Let Y n be a random variable, with n Z, that describes the outcome of the n-th coin toss. If the outcome of the n-th
Exercises with solutions (Set B) 3. A fair coin is tossed an infinite number of times. Let Y n be a random variable, with n Z, that describes the outcome of the n-th coin toss. If the outcome of the n-th
Practical Session #3 - Recursions
 Practical Session #3 - Recursions Substitution method Guess the form of the solution and prove it by induction Iteration Method Convert the recurrence into a summation and solve it Tightly bound a recurrence
Practical Session #3 - Recursions Substitution method Guess the form of the solution and prove it by induction Iteration Method Convert the recurrence into a summation and solve it Tightly bound a recurrence
Markov Model. Model representing the different resident states of a system, and the transitions between the different states
 Markov Model Model representing the different resident states of a system, and the transitions between the different states (applicable to repairable, as well as non-repairable systems) System behavior
Markov Model Model representing the different resident states of a system, and the transitions between the different states (applicable to repairable, as well as non-repairable systems) System behavior
Expected heights in heaps. Jeannette M. de Graaf and Walter A. Kosters
 Expected heights in heaps Jeannette M. de Graaf and Walter A. Kosters Department of Mathematics and Computer Science Leiden University P.O. Box 951 300 RA Leiden The Netherlands Abstract In this paper
Expected heights in heaps Jeannette M. de Graaf and Walter A. Kosters Department of Mathematics and Computer Science Leiden University P.O. Box 951 300 RA Leiden The Netherlands Abstract In this paper
Similarity Search in High Dimensions II. Piotr Indyk MIT
 Similarity Search in High Dimensions II Piotr Indyk MIT Approximate Near(est) Neighbor c-approximate Nearest Neighbor: build data structure which, for any query q returns p P, p-q cr, where r is the distance
Similarity Search in High Dimensions II Piotr Indyk MIT Approximate Near(est) Neighbor c-approximate Nearest Neighbor: build data structure which, for any query q returns p P, p-q cr, where r is the distance
CS151 Complexity Theory
 Introduction CS151 Complexity Theory Lecture 5 April 13, 2004 Power from an unexpected source? we know PEXP, which implies no polytime algorithm for Succinct CVAL poly-size Boolean circuits for Succinct
Introduction CS151 Complexity Theory Lecture 5 April 13, 2004 Power from an unexpected source? we know PEXP, which implies no polytime algorithm for Succinct CVAL poly-size Boolean circuits for Succinct
MARKING A BINARY TREE PROBABILISTIC ANALYSIS OF A RANDOMIZED ALGORITHM
 MARKING A BINARY TREE PROBABILISTIC ANALYSIS OF A RANDOMIZED ALGORITHM XIANG LI Abstract. This paper centers on the analysis of a specific randomized algorithm, a basic random process that involves marking
MARKING A BINARY TREE PROBABILISTIC ANALYSIS OF A RANDOMIZED ALGORITHM XIANG LI Abstract. This paper centers on the analysis of a specific randomized algorithm, a basic random process that involves marking
Growth of Functions (CLRS 2.3,3)
 Growth of Functions (CLRS 2.3,3) 1 Review Last time we discussed running time of algorithms and introduced the RAM model of computation. Best-case running time: the shortest running time for any input
Growth of Functions (CLRS 2.3,3) 1 Review Last time we discussed running time of algorithms and introduced the RAM model of computation. Best-case running time: the shortest running time for any input
ENCODING ARGUMENTS. Pat Morin, Wolfgang Mulzer, and Tommy Reddad. Abstract.
 1 ENCODING ARGUMENTS 2 Pat Morin, Wolfgang Mulzer, and Tommy Reddad 3 4 5 6 7 8 9 10 11 12 13 14 Abstract. This expository article surveys encoding arguments. In its most most basic form an encoding argument
1 ENCODING ARGUMENTS 2 Pat Morin, Wolfgang Mulzer, and Tommy Reddad 3 4 5 6 7 8 9 10 11 12 13 14 Abstract. This expository article surveys encoding arguments. In its most most basic form an encoding argument
EXPLICIT INVERSE OF THE PASCAL MATRIX PLUS ONE
 EXPLICIT INVERSE OF THE PASCAL MATRIX PLUS ONE SHENG-LIANG YANG AND ZHONG-KUI LIU Received 5 June 005; Revised September 005; Accepted 5 December 005 This paper presents a simple approach to invert the
EXPLICIT INVERSE OF THE PASCAL MATRIX PLUS ONE SHENG-LIANG YANG AND ZHONG-KUI LIU Received 5 June 005; Revised September 005; Accepted 5 December 005 This paper presents a simple approach to invert the
Smart Home Health Analytics Information Systems University of Maryland Baltimore County
 Smart Home Health Analytics Information Systems University of Maryland Baltimore County 1 IEEE Expert, October 1996 2 Given sample S from all possible examples D Learner L learns hypothesis h based on
Smart Home Health Analytics Information Systems University of Maryland Baltimore County 1 IEEE Expert, October 1996 2 Given sample S from all possible examples D Learner L learns hypothesis h based on
Taylor and Maclaurin Series
 Taylor and Maclaurin Series MATH 211, Calculus II J. Robert Buchanan Department of Mathematics Spring 2018 Background We have seen that some power series converge. When they do, we can think of them as
Taylor and Maclaurin Series MATH 211, Calculus II J. Robert Buchanan Department of Mathematics Spring 2018 Background We have seen that some power series converge. When they do, we can think of them as
1 Probability Review. CS 124 Section #8 Hashing, Skip Lists 3/20/17. Expectation (weighted average): the expectation of a random quantity X is:
 CS 24 Section #8 Hashing, Skip Lists 3/20/7 Probability Review Expectation (weighted average): the expectation of a random quantity X is: x= x P (X = x) For each value x that X can take on, we look at
CS 24 Section #8 Hashing, Skip Lists 3/20/7 Probability Review Expectation (weighted average): the expectation of a random quantity X is: x= x P (X = x) For each value x that X can take on, we look at
Introduction. I Dynamic programming is a technique for solving optimization problems. I Key element: Decompose a problem into subproblems, solve them
 ntroduction Computer Science & Engineering 423/823 Design and Analysis of Algorithms Lecture 03 Dynamic Programming (Chapter 15) Stephen Scott and Vinodchandran N. Variyam Dynamic programming is a technique
ntroduction Computer Science & Engineering 423/823 Design and Analysis of Algorithms Lecture 03 Dynamic Programming (Chapter 15) Stephen Scott and Vinodchandran N. Variyam Dynamic programming is a technique
The Knapsack Problem. 28. April /44
 The Knapsack Problem 20 10 15 20 W n items with weight w i N and profit p i N Choose a subset x of items Capacity constraint i x w i W wlog assume i w i > W, i : w i < W Maximize profit i x p i 28. April
The Knapsack Problem 20 10 15 20 W n items with weight w i N and profit p i N Choose a subset x of items Capacity constraint i x w i W wlog assume i w i > W, i : w i < W Maximize profit i x p i 28. April
13 Dynamic Programming (3) Optimal Binary Search Trees Subset Sums & Knapsacks
 13 Dynamic Programming (3) Optimal Binary Search Trees Subset Sums & Knapsacks Average-case analysis Average-case analysis of algorithms and data structures: Input is generated according to a known probability
13 Dynamic Programming (3) Optimal Binary Search Trees Subset Sums & Knapsacks Average-case analysis Average-case analysis of algorithms and data structures: Input is generated according to a known probability
Module 1: Analyzing the Efficiency of Algorithms
 Module 1: Analyzing the Efficiency of Algorithms Dr. Natarajan Meghanathan Professor of Computer Science Jackson State University Jackson, MS 39217 E-mail: natarajan.meghanathan@jsums.edu What is an Algorithm?
Module 1: Analyzing the Efficiency of Algorithms Dr. Natarajan Meghanathan Professor of Computer Science Jackson State University Jackson, MS 39217 E-mail: natarajan.meghanathan@jsums.edu What is an Algorithm?
P,NP, NP-Hard and NP-Complete
 P,NP, NP-Hard and NP-Complete We can categorize the problem space into two parts Solvable Problems Unsolvable problems 7/11/2011 1 Halting Problem Given a description of a program and a finite input, decide
P,NP, NP-Hard and NP-Complete We can categorize the problem space into two parts Solvable Problems Unsolvable problems 7/11/2011 1 Halting Problem Given a description of a program and a finite input, decide
Another way of saying this is that amortized analysis guarantees the average case performance of each operation in the worst case.
 Amortized Analysis: CLRS Chapter 17 Last revised: August 30, 2006 1 In amortized analysis we try to analyze the time required by a sequence of operations. There are many situations in which, even though
Amortized Analysis: CLRS Chapter 17 Last revised: August 30, 2006 1 In amortized analysis we try to analyze the time required by a sequence of operations. There are many situations in which, even though
Computer Science & Engineering 423/823 Design and Analysis of Algorithms
 Computer Science & Engineering 423/823 Design and Analysis of Algorithms Lecture 03 Dynamic Programming (Chapter 15) Stephen Scott and Vinodchandran N. Variyam sscott@cse.unl.edu 1/44 Introduction Dynamic
Computer Science & Engineering 423/823 Design and Analysis of Algorithms Lecture 03 Dynamic Programming (Chapter 15) Stephen Scott and Vinodchandran N. Variyam sscott@cse.unl.edu 1/44 Introduction Dynamic
Analysis of Algorithms
 Analysis of Algorithms Section 4.3 Prof. Nathan Wodarz Math 209 - Fall 2008 Contents 1 Analysis of Algorithms 2 1.1 Analysis of Algorithms....................... 2 2 Complexity Analysis 4 2.1 Notation
Analysis of Algorithms Section 4.3 Prof. Nathan Wodarz Math 209 - Fall 2008 Contents 1 Analysis of Algorithms 2 1.1 Analysis of Algorithms....................... 2 2 Complexity Analysis 4 2.1 Notation
Fast Sorting and Selection. A Lower Bound for Worst Case
 Presentation for use with the textbook, Algorithm Design and Applications, by M. T. Goodrich and R. Tamassia, Wiley, 0 Fast Sorting and Selection USGS NEIC. Public domain government image. A Lower Bound
Presentation for use with the textbook, Algorithm Design and Applications, by M. T. Goodrich and R. Tamassia, Wiley, 0 Fast Sorting and Selection USGS NEIC. Public domain government image. A Lower Bound
Formulas and Tables by Mario F. Triola
 Copyright 010 Pearson Education, Inc. Ch. 3: Descriptive Statistics x f # x x f Mean 1x - x s - 1 n 1 x - 1 x s 1n - 1 s B variance s Ch. 4: Probability Mean (frequency table) Standard deviation P1A or
Copyright 010 Pearson Education, Inc. Ch. 3: Descriptive Statistics x f # x x f Mean 1x - x s - 1 n 1 x - 1 x s 1n - 1 s B variance s Ch. 4: Probability Mean (frequency table) Standard deviation P1A or
Where do pseudo-random generators come from?
 Computer Science 2426F Fall, 2018 St. George Campus University of Toronto Notes #6 (for Lecture 9) Where do pseudo-random generators come from? Later we will define One-way Functions: functions that are
Computer Science 2426F Fall, 2018 St. George Campus University of Toronto Notes #6 (for Lecture 9) Where do pseudo-random generators come from? Later we will define One-way Functions: functions that are
Lecture 3 (Notes) 1. The book Computational Complexity: A Modern Approach by Sanjeev Arora and Boaz Barak;
 Topics in Theoretical Computer Science March 7, 2016 Lecturer: Ola Svensson Lecture 3 (Notes) Scribes: Ola Svensson Disclaimer: These notes were written for the lecturer only and may contain inconsistent
Topics in Theoretical Computer Science March 7, 2016 Lecturer: Ola Svensson Lecture 3 (Notes) Scribes: Ola Svensson Disclaimer: These notes were written for the lecturer only and may contain inconsistent
Chapter 11. Min Cut Min Cut Problem Definition Some Definitions. By Sariel Har-Peled, December 10, Version: 1.
 Chapter 11 Min Cut By Sariel Har-Peled, December 10, 013 1 Version: 1.0 I built on the sand And it tumbled down, I built on a rock And it tumbled down. Now when I build, I shall begin With the smoke from
Chapter 11 Min Cut By Sariel Har-Peled, December 10, 013 1 Version: 1.0 I built on the sand And it tumbled down, I built on a rock And it tumbled down. Now when I build, I shall begin With the smoke from
Computational Intelligence Winter Term 2018/19
 Computational Intelligence Winter Term 2018/19 Prof. Dr. Günter Rudolph Lehrstuhl für Algorithm Engineering (LS 11) Fakultät für Informatik TU Dortmund Three tasks: 1. Choice of an appropriate problem
Computational Intelligence Winter Term 2018/19 Prof. Dr. Günter Rudolph Lehrstuhl für Algorithm Engineering (LS 11) Fakultät für Informatik TU Dortmund Three tasks: 1. Choice of an appropriate problem
6.1 The Pumping Lemma for CFLs 6.2 Intersections and Complements of CFLs
 CSC4510/6510 AUTOMATA 6.1 The Pumping Lemma for CFLs 6.2 Intersections and Complements of CFLs The Pumping Lemma for Context Free Languages One way to prove AnBn is not regular is to use the pumping lemma
CSC4510/6510 AUTOMATA 6.1 The Pumping Lemma for CFLs 6.2 Intersections and Complements of CFLs The Pumping Lemma for Context Free Languages One way to prove AnBn is not regular is to use the pumping lemma
MIDTERM I CMPS Winter 2013 Warmuth
 test I 1 MIDTERM I CMPS 101 - Winter 2013 Warmuth With Solutions NAME: Student ID: This exam is closed book, notes, computer and cell phone. Show partial solutions to get partial credit. Make sure you
test I 1 MIDTERM I CMPS 101 - Winter 2013 Warmuth With Solutions NAME: Student ID: This exam is closed book, notes, computer and cell phone. Show partial solutions to get partial credit. Make sure you
Ma/CS 117c Handout # 5 P vs. NP
 Ma/CS 117c Handout # 5 P vs. NP We consider the possible relationships among the classes P, NP, and co-np. First we consider properties of the class of NP-complete problems, as opposed to those which are
Ma/CS 117c Handout # 5 P vs. NP We consider the possible relationships among the classes P, NP, and co-np. First we consider properties of the class of NP-complete problems, as opposed to those which are
Lec 03 Entropy and Coding II Hoffman and Golomb Coding
 CS/EE 5590 / ENG 40 Special Topics Multimedia Communication, Spring 207 Lec 03 Entropy and Coding II Hoffman and Golomb Coding Zhu Li Z. Li Multimedia Communciation, 207 Spring p. Outline Lecture 02 ReCap
CS/EE 5590 / ENG 40 Special Topics Multimedia Communication, Spring 207 Lec 03 Entropy and Coding II Hoffman and Golomb Coding Zhu Li Z. Li Multimedia Communciation, 207 Spring p. Outline Lecture 02 ReCap
Bucket-Sort. Have seen lower bound of Ω(nlog n) for comparisonbased. Some cheating algorithms achieve O(n), given certain assumptions re input
 Bucket-Sort Have seen lower bound of Ω(nlog n) for comparisonbased sorting algs Some cheating algorithms achieve O(n), given certain assumptions re input One example: bucket sort Assumption: input numbers
Bucket-Sort Have seen lower bound of Ω(nlog n) for comparisonbased sorting algs Some cheating algorithms achieve O(n), given certain assumptions re input One example: bucket sort Assumption: input numbers
Lecture 1 : Data Compression and Entropy
 CPS290: Algorithmic Foundations of Data Science January 8, 207 Lecture : Data Compression and Entropy Lecturer: Kamesh Munagala Scribe: Kamesh Munagala In this lecture, we will study a simple model for
CPS290: Algorithmic Foundations of Data Science January 8, 207 Lecture : Data Compression and Entropy Lecturer: Kamesh Munagala Scribe: Kamesh Munagala In this lecture, we will study a simple model for
Source Coding. Master Universitario en Ingeniería de Telecomunicación. I. Santamaría Universidad de Cantabria
 Source Coding Master Universitario en Ingeniería de Telecomunicación I. Santamaría Universidad de Cantabria Contents Introduction Asymptotic Equipartition Property Optimal Codes (Huffman Coding) Universal
Source Coding Master Universitario en Ingeniería de Telecomunicación I. Santamaría Universidad de Cantabria Contents Introduction Asymptotic Equipartition Property Optimal Codes (Huffman Coding) Universal
i=1 i B[i] B[i] + A[i, j]; c n for j n downto i + 1 do c n i=1 (n i) C[i] C[i] + A[i, j]; c n
![i=1 i B[i] B[i] + A[i, j]; c n for j n downto i + 1 do c n i=1 (n i) C[i] C[i] + A[i, j]; c n i=1 i B[i] B[i] + A[i, j]; c n for j n downto i + 1 do c n i=1 (n i) C[i] C[i] + A[i, j]; c n](/thumbs/76/73723628.jpg) Fundamental Algorithms Homework #1 Set on June 25, 2009 Due on July 2, 2009 Problem 1. [15 pts] Analyze the worst-case time complexity of the following algorithms,and give tight bounds using the Theta
Fundamental Algorithms Homework #1 Set on June 25, 2009 Due on July 2, 2009 Problem 1. [15 pts] Analyze the worst-case time complexity of the following algorithms,and give tight bounds using the Theta
arxiv: v1 [math.nt] 1 Sep 2014
![arxiv: v1 [math.nt] 1 Sep 2014 arxiv: v1 [math.nt] 1 Sep 2014](/thumbs/73/69605377.jpg) Integer Complexity: Experimental and Analytical Results II Juris Čerņenoks1, Jānis Iraids 1, Mārtiņš Opmanis 2, Rihards Opmanis 2, and Kārlis Podnieks 1 1 University of Latvia, Raiņa bulvāris 19, Riga,
Integer Complexity: Experimental and Analytical Results II Juris Čerņenoks1, Jānis Iraids 1, Mārtiņš Opmanis 2, Rihards Opmanis 2, and Kārlis Podnieks 1 1 University of Latvia, Raiņa bulvāris 19, Riga,
Exercise Sheet #1 Solutions, Computer Science, A M. Hallett, K. Smith a k n b k = n b + k. a k n b k c 1 n b k. a k n b.
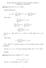 Exercise Sheet #1 Solutions, Computer Science, 308-251A M. Hallett, K. Smith 2002 Question 1.1: Prove (n + a) b = Θ(n b ). Binomial Expansion: Show O(n b ): (n + a) b = For any c 1 > b = O(n b ). Show
Exercise Sheet #1 Solutions, Computer Science, 308-251A M. Hallett, K. Smith 2002 Question 1.1: Prove (n + a) b = Θ(n b ). Binomial Expansion: Show O(n b ): (n + a) b = For any c 1 > b = O(n b ). Show
The divide-and-conquer strategy solves a problem by: 1. Breaking it into subproblems that are themselves smaller instances of the same type of problem
 Chapter 2. Divide-and-conquer algorithms The divide-and-conquer strategy solves a problem by: 1. Breaking it into subproblems that are themselves smaller instances of the same type of problem. 2. Recursively
Chapter 2. Divide-and-conquer algorithms The divide-and-conquer strategy solves a problem by: 1. Breaking it into subproblems that are themselves smaller instances of the same type of problem. 2. Recursively
Searching Algorithms. CSE21 Winter 2017, Day 3 (B00), Day 2 (A00) January 13, 2017
 Searching Algorithms CSE21 Winter 2017, Day 3 (B00), Day 2 (A00) January 13, 2017 Selection Sort (MinSort) Pseudocode Rosen page 203, exercises 41-42 procedure selection sort(a 1, a 2,..., a n : real numbers
Searching Algorithms CSE21 Winter 2017, Day 3 (B00), Day 2 (A00) January 13, 2017 Selection Sort (MinSort) Pseudocode Rosen page 203, exercises 41-42 procedure selection sort(a 1, a 2,..., a n : real numbers
Nearest Neighbor Search with Keywords: Compression
 Nearest Neighbor Search with Keywords: Compression Yufei Tao KAIST June 3, 2013 In this lecture, we will continue our discussion on: Problem (Nearest Neighbor Search with Keywords) Let P be a set of points
Nearest Neighbor Search with Keywords: Compression Yufei Tao KAIST June 3, 2013 In this lecture, we will continue our discussion on: Problem (Nearest Neighbor Search with Keywords) Let P be a set of points
P, NP, NP-Complete, and NPhard
 P, NP, NP-Complete, and NPhard Problems Zhenjiang Li 21/09/2011 Outline Algorithm time complicity P and NP problems NP-Complete and NP-Hard problems Algorithm time complicity Outline What is this course
P, NP, NP-Complete, and NPhard Problems Zhenjiang Li 21/09/2011 Outline Algorithm time complicity P and NP problems NP-Complete and NP-Hard problems Algorithm time complicity Outline What is this course
ALG 4.0 Number Theory Algorithms:
 Algorithms Professor John Reif ALG 4.0 Number Theory Algorithms: (a) GCD (b) Multiplicative Inverse (c) Fermat & Euler's Theorems (d) Public Key Cryptographic Systems (e) Primality Testing Greatest Common
Algorithms Professor John Reif ALG 4.0 Number Theory Algorithms: (a) GCD (b) Multiplicative Inverse (c) Fermat & Euler's Theorems (d) Public Key Cryptographic Systems (e) Primality Testing Greatest Common
Algorithmic Approach to Counting of Certain Types m-ary Partitions
 Algorithmic Approach to Counting of Certain Types m-ary Partitions Valentin P. Bakoev Abstract Partitions of integers of the type m n as a sum of powers of m (the so called m-ary partitions) and their
Algorithmic Approach to Counting of Certain Types m-ary Partitions Valentin P. Bakoev Abstract Partitions of integers of the type m n as a sum of powers of m (the so called m-ary partitions) and their
Fundamentals of Programming. Efficiency of algorithms November 5, 2017
 15-112 Fundamentals of Programming Efficiency of algorithms November 5, 2017 Complexity of sorting algorithms Selection Sort Bubble Sort Insertion Sort Efficiency of Algorithms A computer program should
15-112 Fundamentals of Programming Efficiency of algorithms November 5, 2017 Complexity of sorting algorithms Selection Sort Bubble Sort Insertion Sort Efficiency of Algorithms A computer program should
