Game interpretation of Kolmogorov complexity
|
|
|
- Daniela Collins
- 6 years ago
- Views:
Transcription
1 Game interpretation of Kolmogorov complexity Andrej A. Muchnik, Ilya Mezhirov, Alexander Shen, Nikolay Vereshchagin Abstract arxiv: v1 [math.lo] 24 Mar 2010 The Kolmogorov complexity function K can be relativized using any oracle A, and most properties of K remain true for relativized versions K A. In section 1 we provide an explanation for this observation by giving a game-theoretic interpretation and showing that all natural properties are either true for all K A or false for all K A if we restrict ourselves to sufficiently powerful oracles A. This result is a simple consequence of Martin s determinacy theorem, but its proof is instructive: it shows how one can prove statements about Kolmogorov complexity by constructing a special game and a winning strategy in this game. 1 Game interpretation Consider all functions defined on the set of binary strings and having non-negative integer values, i.e., the set F =N {0,1}. Let α be a property of such a function (i.e., a subset of F ). We say that α is O(1)-stable if f 1 α f 2 α for any two functions f 1, f 2 F such that f 1 (x)= f 2 (x)+o(1), i.e., the difference f 1 (x) f 2 (x) is bounded. Let A be an oracle (a set of strings). By K A (x) we denote the Kolmogorov complexity of a string x relativized to oracle A, i.e., the length of the shortest description for x if the decompressor is allowed to use A as an oracle. (See [3] or [10] for more details; we may use either plain complexity (denoted usually by C or KS) or prefix complexity (denoted usually by K or KP) though the game interpretation would be slightly different; see below.) For a given A the function K A is defined up to an O(1) additive term, therefore an O(1)- stable property α is well defined for K A (does not depend on the specific version of K A ). So α(k A ) becomes a property of the oracle A. It may be true for some oracles and false for other ones. For example, if w n is a n-bit prefix of Chaitin s random real Ω, the (O(1)-stable) property K A (w n ) > 0.5n+O(1) is true for trivial oracle A = 0 and false for A = 0. The following result (a special case of a classical result of D. Martin [4], see the discussion below) shows, however, that for usual α the property α(k A ) is either true for all sufficiently large A or false for all sufficiently large A. The game interpretation considered in this paper was suggested by Andrej Muchnik ( ) in his talks at Kolmogorov seminar (Moscow Lomonosov Univerisity). The examples are added and text is prepared by I. Mezhirov (mezhirov@gmail.com, University of Kaiserslautern), A. Shen (alexander.shen@lif.univ-mrs.fr, LIF Marseille, CNRS & University Aix Marseille, on leave from IITP, RAS, Moscow) and N. Vereshchagin (nikolay.vereshchagin@gmail.com, Moscow State Lomonosov University) who are responsible for all errors and omissions. Preparation of this paper was supported in part by ANR Sycomore and NAFIT ANR-08-EMER-008-0[1,2] grants and RFBR grant. 1
2 Proposition. Let α be a Borel property. Then there exists an oracle A 0 such that either α(k A ) is true for all A T A 0 or α(k A ) is false for all A T A 0. Here T stands for Turing reducibility. The statement is true for different versions of complexity (plain complexity, prefix complexity, decision complexity, a priori complexity, monotone complexity etc.). We provide the proof for plain complexity C and there describe the changes needed for other versions. Proof. Consider the following infinite game with full information. Two players called (as usual) Alice and Bob enumerate graphs of two functions A and B respectively; arguments and values of A and B are binary strings. The players moves alternate; at each move player may add finitely many pairs to the graph of her/his function but cannot delete the pairs that are already there (so the values of A and B that are already defined remain unchanged). The winner is declared as follows. Let K A and K B be the complexity functions that correspond to decompressors A and B, i.e., K A (x)=min{l(p) A(p)=x} where l(p) stands for the length of p; the function K B is defined in a similar way. Let us agree that Alice wins if the function K(x)=min(K A (x),k B (x)) satisfies α. If not, Bob wins. (A technical correction: functions K A and K B may have infinite values; we assume that α is somehow extended to such functions, e.g., is false for all functions with infinite values.) Lemma. If Alice has a computable winning strategy in this game, then α(c) is true for (plain) complexity function C; if Bob has a computable winning strategy, then α(c) is false. Proof of the Lemma is straightforward. Assume that Alice has a computable winning strategy. Let her use this strategy against the enumeration of the graph of optimal decompressor function (so K B (x) = C(x) for all x). Note that in fact Bob ignores the moves of Alice and enumerates the graph of B at its own pace. Since both playes use computable strategies, the game is computable. Therefore K A K B + O(1) due to the optimality of B, and min(k A (x),k B (x))=k B (x)+o(1)=c(x)+o(1). Since Alice wins and α is O(1)-stable, the function C has property α. The same argument (with exchanged roles of Alice and Bob) can be used if Bob has a winning strategy. The statement and the proof of the lemma can be relativized: if Alice/Bob has a winning strategy that is A-computable for some oracle A, then α(c A ) is true/false. Now recall Martin s theorem on the determinacy of Borel games: the winning condition of the game described is a Borel set (since α has this property), so either Alice or Bob has a winning strategy in the game. So if the oracle A is powerful enough (is above the strategy in the hiearchy of T -degrees), the property α(k A ) is true (if Alice has a winning A-computable strategy) or false (if Bob has a winning A-computable strategy). Theorem is proven. 2
3 2 Discussion Let us make several remarks. As we have said, this proposition is a consequence of an old general result proved by Martin. Lemma on p. 688 of [4] together with Borel determinacy [5, 6] guarantees that for every Borel Turing-invariant property Φ of infinite binary sequences either Φ is true for all sequences in some upper cone (in the degrees semilattice), or Φ is false for all sequences in some upper cone. It remains to note that the property ϕ(a)=α(k A ) is a Turing-invariant Borel property. The proof in [4] uses a different (and simpler) game: two players alternate adding bits to a sequence, and the referee checks whether the resulting infinite sequence satisfies Φ. The advantage of our game is that it is more tailored to the definition of Kolmogorov complexity and therefore can be used as a prototype of games needed to prove some specific statements about Kolmogorov complexity. Note that not all theorems in algorithmic information theory are O(1)-stable. For example, most of the results about algorithmic properties of complexity function are not stable. (The non-computablity of the complexity function or its upper semicomputablity is not a stable property, while the non-existence of a nontrivial computable lower bound is stable. Also the Turing-completeness of C is a non-stable assertion though the stronger claim any function that is O(1)-close to C can be used as an oracle to decide halting problem is stable.) The other assumption (Borel property) seems less restrictive: it is hard to imagine a theorem about Kolmogorov complexity where the property in question won t be a Borel one by construction. One may ask whether the statement of our theorem can be used as a practical tool to prove the properties of Kolmogorov complexity. The answer is yes and no at the same time. Indeed, it is convenient to use some kind of game while proving results about Kolmogorov complexity, and usually the argument goes in the same way: we let the winning strategy play against the default strategy of the opponent and the fact that the winning strategy wins implies the statement in question. However, it is convenient to consider more special games. For example, proving the inequality C(x,y) C(x)+C(y x) O(logn) (for strings x and y of length at most n), we would consider a game where Alice wins if K B (x,y) < k+ l implies that either K A (x) < k+o(logn) or K A (y x) < l+ O(logn) for every n,k,l and for all strings x,y of length at most n. This example motivates the following version of the main theorem. Let α be a property of two functions in F, i.e., a subset of F F. Assume that α is monotone in the following sense: if α( f,g) is true, f (x) f(x)+o(1), and g (x) g(x) O(1), then α( f,g ) is true, too. Consider the version of the game when Alice wins if α(k A,K B ) is true. If Alice has a computable winning strategy, then α(c, C) is true; if Bob has a computable winning strategy, then α(c,c) is false. (The proof remains essentially the same.) We provide several examples where game interpretation is used to prove statements about Kolmogorov complexity in Section 3; other examples can be found in [9] and in the survey [12]. Going in the other direction, one would like to extend this result to arbitrary results of computablility theory not necessarily related to Kolmogorov complexity. One of the results 3
4 (Martin s theorem) was already mentioned. Even more general (in some sense) extension is discussed in [8]. It is easy to modify the proof to cover different versions of Kolmogorov complexity. For example, for prefix complexity we may consider prefix-stable decompressors where F(p) = x implies F(p )=x for every p that has prefix p; similar modifications work for monotone and decision complexity. For a priori complexity the players should specify lower approximations to a semimeasure. One may change the rules of the game and let Alice and Bob directly provide upper bounds KA and KB instead of enumerating graphs for A and B. Initially KA(x) = KB(x) = + for every x; at each step the player may decrease finitely many values of the corresponding function. The restriction (that goes back to Levin [2]) is that for every n there is at most 2 n strings x such that KA(x)<n (the same restriction for KB). This approach works for prefix and decision complexities (but not for the monotone one). 3 Examples Conditional complexity and total programs Let x and y be two strings. The conditional complexity C(x y) of x when y is known can be defined as the length of the shortest program that transforms y into x (assuming the programming language is optimal). What if we require this program to be total (i.e., defined everywhere)? It turns out that this requirement can change the situation drastically: there exist two strings x and y of length n such that C(x y)=o(logn) but any total program that transforms y to x has complexity (and length) n O(logn). (Note that a total program that maps everything to x has complexity at most n+o(1), so the bound is quite tight.) To prove this statement, we use the following game. Fix some n. We enumerate a graph of some function f : B n B n (at each move we add some pairs to that graph). The opponent enumerates a list of at most 2 n 1 total functions g 1,g 2,... (at each move the opponent may add some functions to this list). We win the game if there exist strings x,y B n such that f(y)=x but g i (y) x for all i. Why we can win in this game: First we choose some x and y and declare that f(y) = x. After every (non-trivial) move of the opponent we choose some y where f is still undefined and declare f(y)=x where x is different from currently known g 1 (y),g 2 (y),... The number of opponent s moves is less than 2 n, therefore an unused y still exists (we use only one point for every move of the opponent) and a value x different from all g i (y) exists. Why the statement is true: Let us use our strategy against the following opponent strategy: enumerate all total functions B n B n that have complexity less than n. (Each function is considered here as a list of its values.) This strategy is computable (given n) and therefore the game is computable. Therefore, for the winning pair (x,y) we have C(x y)=o(logn) since n is enough to describe the process and therefore to compute function f. On the other hand, any total function that maps y to x has complexity n O(1), otherwise the list of its values would appear in the enumeration. So if we denote by C(x y) the length of the shortest program for a total function that maps y to x, we get a (non-computable) upper bound for C(x y) that sometimes differs significantly from C: it is possible that C(x y) is about n while C is O(logn) (for strings x and y of length n). 4
5 The conditional complexity defined is this way was considered also by Bruno Bauwens [1] (who used a different notation). Extracting randomness requires Ω(logn) additional bits Let us consider a question that can be considered as Kolmogorov-complexity version of randomness extraction (though the similarity is superficial). Assume that a string x is weakly random in the following sense: its complexity is high (at least n) but still can be much smaller than its length, which is polynomial in n. We want to extract randomness out of x, i.e., to get a string y such that y is random (=incompressible: its length is close to its complexity) using few additional bits, i.e., C(y x) should be small. When is it possible? The natural approach: take the shortest program for x as y. Then y is indeed incompressible (C(y)=l(y)+O(1); here l(y) stands for the length of y). And the complexity of y when x is known is O(logn): knowing x and the length of a shortest program for x, we can find (at least some) shortest program for x. Taking the first n bit of this shortest program, we get a string of length n, complexity n + O(log n) and O(log n) conditional complexity relative to x. What if we put a stronger requirement and requiere C(y x) to be O(1) or o(logn)? It turns that randomness extraction in this stronger sense is not always possible: there exists a string x of length n 2 that has complexity at least n such that every string y of length n that has conditional complexity C(y x) less than 0.5 log n has unconditional complexity O(log n) (i.e., is highly compressible). (The same result is true for all strings y of length less than n, so we cannot extract even n/2 good random bits using o(logn) advice bits.) To prove this statement, consider the following game. There are two sets L = B n ( left part ) and R=B n2 ( right part ). The opponent at each move may choose two elements l L and r R and add an edge between them (declaring l to be a neighbor of r). The restriction is that every element in R should have at most d = n neighbors. We may mark some elements of L as simple. We win if there is at least 2 n elements in R that have the following property: all their neighbors are marked. Why the statement is true if we can win the game (using a computable strategy): Let the opponent declare x Lto be a neighbor of y R if C(x y)<0.5logn. Then every y has at most d neighbors. The process is computable, so the game can be effectively simulated. Therefore, all x declared as simple indeed have complexity O(logn) since each x can be described by n and its ordinal number in the enumeration of simple elements (the latter requires 0.5 logn bits). Among 2 n elements in R that have the winning property there is one that has complexity at least n, and this is exactly what we claimed. How to win the game: We do nothing while there are 2 n (or more) elements in R that have no neighbors in L (since this implies the required property). After 2 n2 2 n elements get neighbors in L, we mark the neighbor that is used most often. It is a neighbor of at least(2 n2 2 n )/2 n = 2 n2 n 1 > 2 n2 2n elements in R, and we restrict our attention to these selected elements ignoring all other elements of R. Then we do nothing while at least 2 n of selected elements have no second neighbor. After that we mark the most used second neighbor and have at least (2 n2 2n 2 n )/2 n > 2 n2 4n elements that have two marked neighbors. In this way we either wait indefinitely at some step (and in this case we have at least 2 n elements that have only marked neighbors) or finally get 2 n2 2dn > 2 n elements who have d marked neighbors and therefore cannot have non-marked ones, so we win. 5
6 Note that we could change the game allowing the opponent to declare 2 n elements in R as simple and requiring in the winning condition that there is a non-simple element in R that has no non-simple neighbors. This would make the game closer to original statement about Kolmogorov complexity but a bit more complicated. This example is adapted from [11]. The compexity of a bijection For any two strings x and y one may look for a shortest program for a bijective function that maps x to y. Evidently, it is not shorter than a shortest program for a total function that maps x to y, therefore we get a lower bound C(y x) O(1) for a length (and complexity) of such a program. Since bijection can be effectively reversed, the bound can be made symmetric and we conclude that the length of a program for a bijection that maps x to y is at least max(c(x y), C(y x)) O(1). What about upper bounds? Imagine there exists a simple total function that maps x to y and other simple total function that maps y to x. Can we guarantee that there exists a simple bijective total function that maps x to y? To simplify the discussion, let us assume that x and y are of length n, the bijection should be length-preserving and n is known (used as a condition in all the complexities). This question corresponds to a game. Our opponent produces some total functions f 1, f 2,... : B n B n and g 1,g 2,... : B n B n claiming that one of f i maps x to y, and one of g j maps y to x. Knowing this functions (but not x,y), we have to produce bijections h 1,h 2,... : B n B n and guarantee that one of them maps x to y. (More precisely, the opponent wins if there exist x, y, i and j such that f i (x)=y and g j (y)=x but h k (x) y for all k.) The question now is: how many bijections do we need to beat the opponent that can produce at most m bijections of each type? At first it seems that m bijections are enough. Indeed, let us consider a bipartite graph where x and y are connected by an edge if f i (x)=y and g j (y)=x for some i and j. This graph has degree at most m at both sides (e.g., x can be connected only to f 1 (x),..., f m (x)). Each bipartite graph where each vertex has degree at most m and both parts are of the same size, can be covered by m bijection graphs (we add edges to get degrees exactly m and then use Hall s criterion for matchings). This argument, if correct, would imply the upper bound max(c(x y), C(y x)) + O(log n) for the minimal complexity of the program that computes a bijection that maps x to y. (Here O(logn) is added to take into account that we need to know n for all our constructions.) Indeed, let the opponent to enumerate all the total functionsb n B n that have complexity at most u=max(c(x y),c(y x)). It is a computable process that involves at most 2 u functions. Beating this strategy of the opponent, we computably generate at most 2 u bijections (as we have assumed) and each bijection can be encoded by its ordinal number (at most u bits) and n (this requires O(log n) bits). Winning condition guarantees that one of these bijections maps x to y. 6
7 However, this argument (and the result itself) is wrong. The problem is that the opponent does not tell us all its mappings at once but gives them one by one and we have to react immediately (otherwise we lose if the opponent does not make anything else). So we need to repeat this procedure after each move of the opponent, which gives Θ(m 2 ) bijection if opponent makes m moves. And this bound can be obtained by a much more simple strategy: for every f i and g j consider a bijection h i j that extents a partial matching x y f i (x)=yand g j (y)=x. This strategy gives upper bound C(x y) + C(y x) + O(log n). The main point of this example is that game arguments work in both directions: the absense of the winning strategy for us (and the existence of the winning strategy for the opponent) implies that the upper bound we wanted to prove is not true at all. For example, the winning strategy in our game (for us) exists only if the number of our bijections is Ω(m 2 ) where m is the maximal number of opponent s moves. It can be shown as follows. Let us assume that all the opponent s functions are constant functions (i.e., map all the elements of B n into one element). In other terms, the opponent just selects vertices at both sides of the graph, and our goal is to provide bijections between each pair of selected vertices. It is easy to see that we would need Ω(m 2 ) bijections: indeed, if the opponent at each move selects a vertex that is not connected yet to vertices selected earlier (which is always possible if the number of vertices is large compared to m 2 ) then we need Ω(m) new bijections to provide these new connections. Translating this observation into Kolmogorov complexity language, we get the following statement: for every k and n such that n>2k there exist two strings x and y of length n such that C(x),C(y) k+o(logn) but any bijection that maps x to y has complexity 2k O(1). To show this, use the trivial strategy at our side (we list all programs of length less than 2k that turn out to define a bijection B n B n ; this property is enumerable) and let the opponent use the winning strategy described above (choosing elements not connected to already chosen elements by known bijections; the inequality n>2k guarantees that Ω(2 k ) steps are possible, since (2 k ) 2 = 2 2k < 2 n ). All chosen elements have complexity at most k+ O(logn) and by the winning condition they are some of them not connected by a bijection of complexity less than 2k. Contrasting prefix and plain complexity Here we give a game-based proof of J. Miller s result [7]. (The original proof in [7] uses a different scheme and involves the Kleene fixed-point theorem.) Let Q be a co-enumerable set of strings (i.e., its complement is enumerable) that for every n contains at least one string of length n. Then for every c there exists n and x of length n such that K(x)<n+K(n) c. Here K stands for prefix complexity; the contrast with the plain complexity arises because for plain complexity the set of incompressible strings (that have maximal possible complexity) is co-enumberable. (Note also that the maximal value of K(x) for strings of length n is K(n)+O(1).) To prove this statement, let us consider the following game specified by a natural number C and a finite family of disjoint finite sets S 1,...,S N. During the game each element s S= 7
8 N j=1 S j is labeled by two non-negative rational numbers A(s) and B(s) called Alice weight and Bob s weight. Initially all weights are zeros. Alice and Bob make alternate moves. On each move each player may increase her/his weight of several elements s S. Both players must obey the following total weight restrictions: s S A(s) 1 and B(s) 1. s S In addition, Bob must be fair : for every j Bob s weights of all s S j must be equal. That means that basically Bob assigns weights to j {1,...,N} and Bob s weight B( j) of j is then evenly distributed among all s S j so that B(s)=B( j)/#s j for all s S j. Alice need not be fair. This extra requirement is somehow compensated by allowing Bob to disable certain s S. Once an s is disabled it cannot be enabled any more. Alice cannot disable or enable anything. For every j Bob is not allowed to disable all s S j : every set S j should contain at least one element that is enabled (=not disabled). The game is infinite. Alice wins if at the end of the game (or, better to say, in the limit) there exists an enabled s S such that A(s) B(s) C. Now we have (as usual) to explain two things: why Alice has a (computable) winning strategy in the game (with some assumptions on the parameters of the game) and why this implies Miller s theorem. Lemma. Alice has a computable winning strategy if N 2 8C and #S j 8C for all j N. Let us show first why this statement implies the theorem. Let Let us take the sets of all strings of length C=2 c and N = 2 8C = 2 2c+3 log8c+ 1,...,log8C+ N as S 1,...,S N. Then S j consists of 2 j 8C elements; the conditions of the lemma are satisfied and hence Alice has a computable winning strategy. Consider the following Bob s strategy in this game: he enumerates the complement of Q and disables all its elements; in parallel, he approximates the prefix complexity from above and once he finds out that K(n) does not exceed some l, he increases the weights of all 2 n strings of length n up to 2 l n. Thus at the end of the game B(x)=2 K(n) n for all s S that have length n (i.e., for s S j where j=n log8c). Alice s limit weight function x A(x) is lower semi-computable given c, as both Alice s and Bob s strategies are computable given c. Therefore (since prefix complexity is equal to the logarithm of a priori probability) K(s c) loga(s)+o(1) 8
9 for all s S. As Alice wins, there exists a string s Q of some length n N + log 8C such that A(s)/B(s) C, i.e., loga(s) logb(s) c=k(n)+n c. This implies that and K(s c) K(n)+n c+o(1), K(s) K(n)+n c+2logc+o(1). This is a bit weaker statement that we need: we wanted K(s)<K(n)+n c. To fix this, apply this argument to c = c+3logc in place of c. For all large enough c we then have K(s)<K(n)+n c. It remains to prove the Lemma by showing a winning strategy for Alice. Proof of the Lemma. The strategy is rather straighforward. The main idea is that playing with one S i, Alice can force Bob to spend twice more weight than she does. Then she switches to next S i and so on until Bob s weight is exhausted while she has solid reserves. To achieve her goal on one set of M elements, Alice assigns sequentially weights 1/2 M,1/2 M 1,...,1/2 1 and after each move waits until Bob increases his weight or disables the corresponding element. Since he cannot disable all elements and is forced to use the same weights for all elements while Alice puts more than half of the weight on the last element, Alice has factor M/2 as a handicap, and we may assume that M beats C-factor that Bob has in his favor. Now the formal details. Assume first that #S j = M = 4C for all j and N = 2 M. (We will show later how to adjust the proof to the case when S j 8C and N 2 8C.) Alice picks an element x 1 S 1 and assigns the weight 1/2 M to x 1. Bob (to avoid losing the entire game) has either to assign a weight of more than 1/C2 M to all elements in S 1, or to disable x 1. In the second case Alice picks another element x 2 S 1 and assigns a (twice bigger) weight of 2/2 M to it. Again Bob has a dilemma: either to increase the weight for all elements of S 1 up to 2/C2 M, or to disable x 2. In the second case Alice picks x 3, assigns a weight of 4/2 M to it, and so on. (If this process continues long enough, the last weight would be 2 M 1 /2 M = 1/2.) As Bob cannot disable all the elements of S 1, at some step i the first case occurs, and Bob assigns a weight greater than 2 i /C2 M to all the elements of S 1. Then Alice stops playing with S 1. Note that the total Alice s weight of S 1 (let us call it β) is the sum of the geometric sequence: β = 1/2 M + 2/2 M + +2 i 1 /2 M < 2 i /2 M 1. Thus Alice obeys the rules. Note that total Bob s weight of S 1 is more than M2 i 1 /C2 M = 2 i+1 /2 M, which exceeds at least two times the total Alice s weight spent on S 1. This implies, in particular, that Bob cannot beat Alice s weight for the last element if the game comes to this stage (and Alice wins the game in this case.) Then Alice proceeds to the second set S 2 and repeats the procedure. However this time she uses weights α/2 M,2α/2 M,..., where α = 1 β is the weight still available for Alice. Again she forces Bob to use twice more weight than she does. Then Alice repeats the procedure for the third set S 3 with the remaining weight etc. Let β j is the the total weight Alice spent on the sets S 1,...,S j, and α j = 1 β j the weight remaining after the first j iterations. By construction, Bob s total weight spent on sets S 1,...,S j 9
10 is greater than 2β j, so we have 2β j < 1 and hence α j > 1/2. Consequently, Alice s total weight of each S j is more than 1/2 M+1. Hence after at most N = 2 M iterations Alice wins. If the size of S j are large but different, we need to make some modification. (We cannot use the same approach starting with 1/2 M where M is the size of the set: if Bob beats the first element with factor C, he spends twice more weight than Alice but still a small amount, so we do not have enough sets for a contradiction.) However, the modification is easy. If the number of elements in S j is a multiple of 4C (which is the case we use), we can split elements of S j into 4C groups of equal size, and treat all members of each group G as one element. This means that if the above algorithm asks to assign to an element (group) G a weight w, Alice distributes the weight w uniformly among members of G and waits until either Bob disables all elements of the group or assigns 4C-bigger weight to all elements of S j. If S j is not a multiple of 4C, the groups are not equal (the worst case is when some groups have one element while other have two elements), so to compensate for this we heed to use 8C instead of 4C. Note that excess in the number of groups (when N is bigger than required 8C) does not matter at all, we just ignore some groups. Note that this proof provides also some bound for n (the length of the string); this bound is (almost) the same as given in Theorem 6.1 in [7]. Note also that instead of classifying strings according to their length, we could split them (effectively) into arbitrary finite sets G n whose cardinalities monotonically increase and are unbounded. Then for every string x G n we have K(x) #G n + KP(n)+O(1) and for every co-enumerable set Q that intersects every G n there exists n and x G N Q such that K(x) #G n + K(n) c (for the same reasons). References [1] Bruno Bauwens, personal communication. [2] Leonid Levin, Various measures of complexity for finite objects, Soviet Math. Dokl., 17(2), p (1976). See for a corrected translation. [3] Ming Li, Paul Vitanyi, An Introduction to Kolmogorov Complexity and Its Applications. 3rd ed., Springer, [4] Donald A. Martin, The axiom of determinateness and reduction principles in the analytical hierarchy, Bull. Amer. Math. Soc., 74: (1968). [5] Donald A. Martin, Borel Determinacy, The Annals of Mathematics, 2nd Ser., 102(2): (Sept. 1975). [6] Donald A. Martin, A purely inductive proof of Borel determinacy, Recursion theory, Proceedings of the AMS ASL summer institute held in Ithaca, New York, 1982, p [7] Joseph S. Miller, Contrasting plain and prefix-free complexities. Preprint available at 10
11 [8] Andrej Muchnik, On the basic structures of the descriptive theory of algorithms, Soviet Math. Dokl., 32, p (1985). [9] Andrej Muchnik, Alexander Shen, Mikhail Ustinov, Nikolai K. Vereshchagin, Michael V. Vyugin, Non-reducible descriptions for conditional Kolmogorov complexity, Theoretical Computer Science, 384 (1), p (2007). [10] Alexander Shen, Algorithmic Information Theory and Kolmogorov Complexity, Lecture notes of a course taught at the Uppsala University. Available as Technical Report at [11] Nikolay Vereshchagin, Mikhail Vyugin, Independent minimum length programs to translate between given strings, Theoretical Computer Science, 271 (1 2), p (2002). [12] Nikolay Vereshchagin, Kolmogorov complexity and Games, Bulletin of the European Association for Theoretical Computer Science, 94, Feb. 2008, p
Game arguments in computability theory and algorithmic information theory
 Game arguments in computability theory and algorithmic information theory Andrej Muchnik Alexander Shen Mikhail Vyugin September 10, 2012 Abstract We provide some examples showing how game-theoretic arguments
Game arguments in computability theory and algorithmic information theory Andrej Muchnik Alexander Shen Mikhail Vyugin September 10, 2012 Abstract We provide some examples showing how game-theoretic arguments
Limit Complexities Revisited
 DOI 10.1007/s00224-009-9203-9 Limit Complexities Revisited Laurent Bienvenu Andrej Muchnik Alexander Shen Nikolay Vereshchagin Springer Science+Business Media, LLC 2009 Abstract The main goal of this article
DOI 10.1007/s00224-009-9203-9 Limit Complexities Revisited Laurent Bienvenu Andrej Muchnik Alexander Shen Nikolay Vereshchagin Springer Science+Business Media, LLC 2009 Abstract The main goal of this article
On approximate decidability of minimal programs 1
 On approximate decidability of minimal programs 1 Jason Teutsch June 12, 2014 1 Joint work with Marius Zimand How not to estimate complexity What s hard about Kolmogorov complexity? the case of functions
On approximate decidability of minimal programs 1 Jason Teutsch June 12, 2014 1 Joint work with Marius Zimand How not to estimate complexity What s hard about Kolmogorov complexity? the case of functions
2 Plain Kolmogorov Complexity
 2 Plain Kolmogorov Complexity In this section, we introduce plain Kolmogorov Complexity, prove the invariance theorem - that is, the complexity of a string does not depend crucially on the particular model
2 Plain Kolmogorov Complexity In this section, we introduce plain Kolmogorov Complexity, prove the invariance theorem - that is, the complexity of a string does not depend crucially on the particular model
Kolmogorov complexity and its applications
 CS860, Winter, 2010 Kolmogorov complexity and its applications Ming Li School of Computer Science University of Waterloo http://www.cs.uwaterloo.ca/~mli/cs860.html We live in an information society. Information
CS860, Winter, 2010 Kolmogorov complexity and its applications Ming Li School of Computer Science University of Waterloo http://www.cs.uwaterloo.ca/~mli/cs860.html We live in an information society. Information
The sum 2 KM(x) K(x) over all prefixes x of some binary sequence can be infinite
 The sum 2 KM(x) K(x) over all prefixes x of some binary sequence can be infinite Mikhail Andreev, Akim Kumok arxiv:40.467v [cs.it] 7 Jan 204 January 8, 204 Abstract We consider two quantities that measure
The sum 2 KM(x) K(x) over all prefixes x of some binary sequence can be infinite Mikhail Andreev, Akim Kumok arxiv:40.467v [cs.it] 7 Jan 204 January 8, 204 Abstract We consider two quantities that measure
Kolmogorov complexity and its applications
 Spring, 2009 Kolmogorov complexity and its applications Paul Vitanyi Computer Science University of Amsterdam http://www.cwi.nl/~paulv/course-kc We live in an information society. Information science is
Spring, 2009 Kolmogorov complexity and its applications Paul Vitanyi Computer Science University of Amsterdam http://www.cwi.nl/~paulv/course-kc We live in an information society. Information science is
Algorithmic statistics revisited
 Algorithmic statistics revisited Nikolay Vereshchagin and Alexander Shen Abstract The mission of statistics is to provide adequate statistical hypotheses (models) for observed data. But what is an adequate
Algorithmic statistics revisited Nikolay Vereshchagin and Alexander Shen Abstract The mission of statistics is to provide adequate statistical hypotheses (models) for observed data. But what is an adequate
Layerwise computability and image randomness
 Layerwise computability and image randomness Laurent Bienvenu Mathieu Hoyrup Alexander Shen arxiv:1607.04232v1 [math.lo] 14 Jul 2016 Abstract Algorithmic randomness theory starts with a notion of an individual
Layerwise computability and image randomness Laurent Bienvenu Mathieu Hoyrup Alexander Shen arxiv:1607.04232v1 [math.lo] 14 Jul 2016 Abstract Algorithmic randomness theory starts with a notion of an individual
CISC 876: Kolmogorov Complexity
 March 27, 2007 Outline 1 Introduction 2 Definition Incompressibility and Randomness 3 Prefix Complexity Resource-Bounded K-Complexity 4 Incompressibility Method Gödel s Incompleteness Theorem 5 Outline
March 27, 2007 Outline 1 Introduction 2 Definition Incompressibility and Randomness 3 Prefix Complexity Resource-Bounded K-Complexity 4 Incompressibility Method Gödel s Incompleteness Theorem 5 Outline
Random Reals à la Chaitin with or without prefix-freeness
 Random Reals à la Chaitin with or without prefix-freeness Verónica Becher Departamento de Computación, FCEyN Universidad de Buenos Aires - CONICET Argentina vbecher@dc.uba.ar Serge Grigorieff LIAFA, Université
Random Reals à la Chaitin with or without prefix-freeness Verónica Becher Departamento de Computación, FCEyN Universidad de Buenos Aires - CONICET Argentina vbecher@dc.uba.ar Serge Grigorieff LIAFA, Université
Complexity Theory VU , SS The Polynomial Hierarchy. Reinhard Pichler
 Complexity Theory Complexity Theory VU 181.142, SS 2018 6. The Polynomial Hierarchy Reinhard Pichler Institut für Informationssysteme Arbeitsbereich DBAI Technische Universität Wien 15 May, 2018 Reinhard
Complexity Theory Complexity Theory VU 181.142, SS 2018 6. The Polynomial Hierarchy Reinhard Pichler Institut für Informationssysteme Arbeitsbereich DBAI Technische Universität Wien 15 May, 2018 Reinhard
Outline. Complexity Theory EXACT TSP. The Class DP. Definition. Problem EXACT TSP. Complexity of EXACT TSP. Proposition VU 181.
 Complexity Theory Complexity Theory Outline Complexity Theory VU 181.142, SS 2018 6. The Polynomial Hierarchy Reinhard Pichler Institut für Informationssysteme Arbeitsbereich DBAI Technische Universität
Complexity Theory Complexity Theory Outline Complexity Theory VU 181.142, SS 2018 6. The Polynomial Hierarchy Reinhard Pichler Institut für Informationssysteme Arbeitsbereich DBAI Technische Universität
Probabilistic Constructions of Computable Objects and a Computable Version of Lovász Local Lemma.
 Probabilistic Constructions of Computable Objects and a Computable Version of Lovász Local Lemma. Andrei Rumyantsev, Alexander Shen * January 17, 2013 Abstract A nonconstructive proof can be used to prove
Probabilistic Constructions of Computable Objects and a Computable Version of Lovász Local Lemma. Andrei Rumyantsev, Alexander Shen * January 17, 2013 Abstract A nonconstructive proof can be used to prove
Kolmogorov-Loveland Randomness and Stochasticity
 Kolmogorov-Loveland Randomness and Stochasticity Wolfgang Merkle 1 Joseph Miller 2 André Nies 3 Jan Reimann 1 Frank Stephan 4 1 Institut für Informatik, Universität Heidelberg 2 Department of Mathematics,
Kolmogorov-Loveland Randomness and Stochasticity Wolfgang Merkle 1 Joseph Miller 2 André Nies 3 Jan Reimann 1 Frank Stephan 4 1 Institut für Informatik, Universität Heidelberg 2 Department of Mathematics,
Symmetry of Information: A Closer Look
 Symmetry of Information: A Closer Look Marius Zimand. Department of Computer and Information Sciences, Towson University, Baltimore, MD, USA Abstract. Symmetry of information establishes a relation between
Symmetry of Information: A Closer Look Marius Zimand. Department of Computer and Information Sciences, Towson University, Baltimore, MD, USA Abstract. Symmetry of information establishes a relation between
COS597D: Information Theory in Computer Science October 19, Lecture 10
 COS597D: Information Theory in Computer Science October 9, 20 Lecture 0 Lecturer: Mark Braverman Scribe: Andrej Risteski Kolmogorov Complexity In the previous lectures, we became acquainted with the concept
COS597D: Information Theory in Computer Science October 9, 20 Lecture 0 Lecturer: Mark Braverman Scribe: Andrej Risteski Kolmogorov Complexity In the previous lectures, we became acquainted with the concept
The Metamathematics of Randomness
 The Metamathematics of Randomness Jan Reimann January 26, 2007 (Original) Motivation Effective extraction of randomness In my PhD-thesis I studied the computational power of reals effectively random for
The Metamathematics of Randomness Jan Reimann January 26, 2007 (Original) Motivation Effective extraction of randomness In my PhD-thesis I studied the computational power of reals effectively random for
Randomness Beyond Lebesgue Measure
 Randomness Beyond Lebesgue Measure Jan Reimann Department of Mathematics University of California, Berkeley November 16, 2006 Measures on Cantor Space Outer measures from premeasures Approximate sets from
Randomness Beyond Lebesgue Measure Jan Reimann Department of Mathematics University of California, Berkeley November 16, 2006 Measures on Cantor Space Outer measures from premeasures Approximate sets from
The axiomatic power of Kolmogorov complexity
 The axiomatic power of Kolmogorov complexity Laurent Bienvenu 1, Andrei Romashchenko 2, Alexander Shen 2, Antoine Taveneaux 1, and Stijn Vermeeren 3 1 LIAFA, CNRS & Université Paris 7 2 LIRMM, CNRS & Université
The axiomatic power of Kolmogorov complexity Laurent Bienvenu 1, Andrei Romashchenko 2, Alexander Shen 2, Antoine Taveneaux 1, and Stijn Vermeeren 3 1 LIAFA, CNRS & Université Paris 7 2 LIRMM, CNRS & Université
CS 6820 Fall 2014 Lectures, October 3-20, 2014
 Analysis of Algorithms Linear Programming Notes CS 6820 Fall 2014 Lectures, October 3-20, 2014 1 Linear programming The linear programming (LP) problem is the following optimization problem. We are given
Analysis of Algorithms Linear Programming Notes CS 6820 Fall 2014 Lectures, October 3-20, 2014 1 Linear programming The linear programming (LP) problem is the following optimization problem. We are given
Notes for Lecture Notes 2
 Stanford University CS254: Computational Complexity Notes 2 Luca Trevisan January 11, 2012 Notes for Lecture Notes 2 In this lecture we define NP, we state the P versus NP problem, we prove that its formulation
Stanford University CS254: Computational Complexity Notes 2 Luca Trevisan January 11, 2012 Notes for Lecture Notes 2 In this lecture we define NP, we state the P versus NP problem, we prove that its formulation
STRUCTURES WITH MINIMAL TURING DEGREES AND GAMES, A RESEARCH PROPOSAL
 STRUCTURES WITH MINIMAL TURING DEGREES AND GAMES, A RESEARCH PROPOSAL ZHENHAO LI 1. Structures whose degree spectrum contain minimal elements/turing degrees 1.1. Background. Richter showed in [Ric81] that
STRUCTURES WITH MINIMAL TURING DEGREES AND GAMES, A RESEARCH PROPOSAL ZHENHAO LI 1. Structures whose degree spectrum contain minimal elements/turing degrees 1.1. Background. Richter showed in [Ric81] that
CSE 4111/5111/6111 Computability Jeff Edmonds Assignment 3: Diagonalization & Halting Problem Due: One week after shown in slides
 CSE 4111/5111/6111 Computability Jeff Edmonds Assignment 3: Diagonalization & Halting Problem Due: One week after shown in slides First Person: Second Person: Family Name: Family Name: Given Name: Given
CSE 4111/5111/6111 Computability Jeff Edmonds Assignment 3: Diagonalization & Halting Problem Due: One week after shown in slides First Person: Second Person: Family Name: Family Name: Given Name: Given
1 Computational Problems
 Stanford University CS254: Computational Complexity Handout 2 Luca Trevisan March 31, 2010 Last revised 4/29/2010 In this lecture we define NP, we state the P versus NP problem, we prove that its formulation
Stanford University CS254: Computational Complexity Handout 2 Luca Trevisan March 31, 2010 Last revised 4/29/2010 In this lecture we define NP, we state the P versus NP problem, we prove that its formulation
Universal probability-free conformal prediction
 Universal probability-free conformal prediction Vladimir Vovk and Dusko Pavlovic March 20, 2016 Abstract We construct a universal prediction system in the spirit of Popper s falsifiability and Kolmogorov
Universal probability-free conformal prediction Vladimir Vovk and Dusko Pavlovic March 20, 2016 Abstract We construct a universal prediction system in the spirit of Popper s falsifiability and Kolmogorov
Sophistication Revisited
 Sophistication Revisited Luís Antunes Lance Fortnow August 30, 007 Abstract Kolmogorov complexity measures the ammount of information in a string as the size of the shortest program that computes the string.
Sophistication Revisited Luís Antunes Lance Fortnow August 30, 007 Abstract Kolmogorov complexity measures the ammount of information in a string as the size of the shortest program that computes the string.
A necessary and sufficient condition for the existence of a spanning tree with specified vertices having large degrees
 A necessary and sufficient condition for the existence of a spanning tree with specified vertices having large degrees Yoshimi Egawa Department of Mathematical Information Science, Tokyo University of
A necessary and sufficient condition for the existence of a spanning tree with specified vertices having large degrees Yoshimi Egawa Department of Mathematical Information Science, Tokyo University of
We are going to discuss what it means for a sequence to converge in three stages: First, we define what it means for a sequence to converge to zero
 Chapter Limits of Sequences Calculus Student: lim s n = 0 means the s n are getting closer and closer to zero but never gets there. Instructor: ARGHHHHH! Exercise. Think of a better response for the instructor.
Chapter Limits of Sequences Calculus Student: lim s n = 0 means the s n are getting closer and closer to zero but never gets there. Instructor: ARGHHHHH! Exercise. Think of a better response for the instructor.
Stochasticity in Algorithmic Statistics for Polynomial Time
 Stochasticity in Algorithmic Statistics for Polynomial Time Alexey Milovanov 1 and Nikolay Vereshchagin 2 1 National Research University Higher School of Economics, Moscow, Russia almas239@gmail.com 2
Stochasticity in Algorithmic Statistics for Polynomial Time Alexey Milovanov 1 and Nikolay Vereshchagin 2 1 National Research University Higher School of Economics, Moscow, Russia almas239@gmail.com 2
Computability Theory
 Computability Theory Cristian S. Calude May 2012 Computability Theory 1 / 1 Bibliography M. Sipser. Introduction to the Theory of Computation, PWS 1997. (textbook) Computability Theory 2 / 1 Supplementary
Computability Theory Cristian S. Calude May 2012 Computability Theory 1 / 1 Bibliography M. Sipser. Introduction to the Theory of Computation, PWS 1997. (textbook) Computability Theory 2 / 1 Supplementary
1 Basic Game Modelling
 Max-Planck-Institut für Informatik, Winter 2017 Advanced Topic Course Algorithmic Game Theory, Mechanism Design & Computational Economics Lecturer: CHEUNG, Yun Kuen (Marco) Lecture 1: Basic Game Modelling,
Max-Planck-Institut für Informatik, Winter 2017 Advanced Topic Course Algorithmic Game Theory, Mechanism Design & Computational Economics Lecturer: CHEUNG, Yun Kuen (Marco) Lecture 1: Basic Game Modelling,
Prefix-like Complexities and Computability in the Limit
 Prefix-like Complexities and Computability in the Limit Alexey Chernov 1 and Jürgen Schmidhuber 1,2 1 IDSIA, Galleria 2, 6928 Manno, Switzerland 2 TU Munich, Boltzmannstr. 3, 85748 Garching, München, Germany
Prefix-like Complexities and Computability in the Limit Alexey Chernov 1 and Jürgen Schmidhuber 1,2 1 IDSIA, Galleria 2, 6928 Manno, Switzerland 2 TU Munich, Boltzmannstr. 3, 85748 Garching, München, Germany
Notes on induction proofs and recursive definitions
 Notes on induction proofs and recursive definitions James Aspnes December 13, 2010 1 Simple induction Most of the proof techniques we ve talked about so far are only really useful for proving a property
Notes on induction proofs and recursive definitions James Aspnes December 13, 2010 1 Simple induction Most of the proof techniques we ve talked about so far are only really useful for proving a property
Incomplete version for students of easllc2012 only. 94 First-Order Logic. Incomplete version for students of easllc2012 only. 6.5 The Semantic Game 93
 65 The Semantic Game 93 In particular, for every countable X M there is a countable submodel N of M such that X N and N = T Proof Let T = {' 0, ' 1,} By Proposition 622 player II has a winning strategy
65 The Semantic Game 93 In particular, for every countable X M there is a countable submodel N of M such that X N and N = T Proof Let T = {' 0, ' 1,} By Proposition 622 player II has a winning strategy
Chaitin Ω Numbers and Halting Problems
 Chaitin Ω Numbers and Halting Problems Kohtaro Tadaki Research and Development Initiative, Chuo University CREST, JST 1 13 27 Kasuga, Bunkyo-ku, Tokyo 112-8551, Japan E-mail: tadaki@kc.chuo-u.ac.jp Abstract.
Chaitin Ω Numbers and Halting Problems Kohtaro Tadaki Research and Development Initiative, Chuo University CREST, JST 1 13 27 Kasuga, Bunkyo-ku, Tokyo 112-8551, Japan E-mail: tadaki@kc.chuo-u.ac.jp Abstract.
RMT 2014 Power Round Solutions February 15, 2014
 Introduction This Power Round develops the many and varied properties of the Thue-Morse sequence, an infinite sequence of 0s and 1s which starts 0, 1, 1, 0, 1, 0, 0, 1,... and appears in a remarkable number
Introduction This Power Round develops the many and varied properties of the Thue-Morse sequence, an infinite sequence of 0s and 1s which starts 0, 1, 1, 0, 1, 0, 0, 1,... and appears in a remarkable number
On the Complexity of Computing an Equilibrium in Combinatorial Auctions
 On the Complexity of Computing an Equilibrium in Combinatorial Auctions Shahar Dobzinski Hu Fu Robert Kleinberg April 8, 2014 Abstract We study combinatorial auctions where each item is sold separately
On the Complexity of Computing an Equilibrium in Combinatorial Auctions Shahar Dobzinski Hu Fu Robert Kleinberg April 8, 2014 Abstract We study combinatorial auctions where each item is sold separately
Does the Polynomial Hierarchy Collapse if Onto Functions are Invertible?
 Does the Polynomial Hierarchy Collapse if Onto Functions are Invertible? Harry Buhrman 1, Lance Fortnow 2, Michal Koucký 3, John D. Rogers 4, and Nikolay Vereshchagin 5 1 CWI, Amsterdam, buhrman@cwi.nl
Does the Polynomial Hierarchy Collapse if Onto Functions are Invertible? Harry Buhrman 1, Lance Fortnow 2, Michal Koucký 3, John D. Rogers 4, and Nikolay Vereshchagin 5 1 CWI, Amsterdam, buhrman@cwi.nl
Limitations of Efficient Reducibility to the Kolmogorov Random Strings
 Limitations of Efficient Reducibility to the Kolmogorov Random Strings John M. HITCHCOCK 1 Department of Computer Science, University of Wyoming Abstract. We show the following results for polynomial-time
Limitations of Efficient Reducibility to the Kolmogorov Random Strings John M. HITCHCOCK 1 Department of Computer Science, University of Wyoming Abstract. We show the following results for polynomial-time
Kernelization Lower Bounds: A Brief History
 Kernelization Lower Bounds: A Brief History G Philip Max Planck Institute for Informatics, Saarbrücken, Germany New Developments in Exact Algorithms and Lower Bounds. Pre-FSTTCS 2014 Workshop, IIT Delhi
Kernelization Lower Bounds: A Brief History G Philip Max Planck Institute for Informatics, Saarbrücken, Germany New Developments in Exact Algorithms and Lower Bounds. Pre-FSTTCS 2014 Workshop, IIT Delhi
Some Properties of Antistochastic Strings. Alexey Milovanov. Theory of Computing Systems ISSN
 Some Properties of Antistochastic Strings Alexey Milovanov Theory of Computing Systems ISSN 1432-4350 DOI 10.1007/s00224-016-9695-z 1 23 Your article is protected by copyright and all rights are held exclusively
Some Properties of Antistochastic Strings Alexey Milovanov Theory of Computing Systems ISSN 1432-4350 DOI 10.1007/s00224-016-9695-z 1 23 Your article is protected by copyright and all rights are held exclusively
Randomness. What next?
 Randomness What next? Random Walk Attribution These slides were prepared for the New Jersey Governor s School course The Math Behind the Machine taught in the summer of 2012 by Grant Schoenebeck Large
Randomness What next? Random Walk Attribution These slides were prepared for the New Jersey Governor s School course The Math Behind the Machine taught in the summer of 2012 by Grant Schoenebeck Large
Essential facts about NP-completeness:
 CMPSCI611: NP Completeness Lecture 17 Essential facts about NP-completeness: Any NP-complete problem can be solved by a simple, but exponentially slow algorithm. We don t have polynomial-time solutions
CMPSCI611: NP Completeness Lecture 17 Essential facts about NP-completeness: Any NP-complete problem can be solved by a simple, but exponentially slow algorithm. We don t have polynomial-time solutions
Shift-complex Sequences
 University of Wisconsin Madison March 24th, 2011 2011 ASL North American Annual Meeting Berkeley, CA What are shift-complex sequences? K denotes prefix-free Kolmogorov complexity: For a string σ, K(σ)
University of Wisconsin Madison March 24th, 2011 2011 ASL North American Annual Meeting Berkeley, CA What are shift-complex sequences? K denotes prefix-free Kolmogorov complexity: For a string σ, K(σ)
U.C. Berkeley CS278: Computational Complexity Professor Luca Trevisan August 30, Notes for Lecture 1
 U.C. Berkeley CS278: Computational Complexity Handout N1 Professor Luca Trevisan August 30, 2004 Notes for Lecture 1 This course assumes CS170, or equivalent, as a prerequisite. We will assume that the
U.C. Berkeley CS278: Computational Complexity Handout N1 Professor Luca Trevisan August 30, 2004 Notes for Lecture 1 This course assumes CS170, or equivalent, as a prerequisite. We will assume that the
1 Randomized Computation
 CS 6743 Lecture 17 1 Fall 2007 1 Randomized Computation Why is randomness useful? Imagine you have a stack of bank notes, with very few counterfeit ones. You want to choose a genuine bank note to pay at
CS 6743 Lecture 17 1 Fall 2007 1 Randomized Computation Why is randomness useful? Imagine you have a stack of bank notes, with very few counterfeit ones. You want to choose a genuine bank note to pay at
Constructions with ruler and compass.
 Constructions with ruler and compass. Semyon Alesker. 1 Introduction. Let us assume that we have a ruler and a compass. Let us also assume that we have a segment of length one. Using these tools we can
Constructions with ruler and compass. Semyon Alesker. 1 Introduction. Let us assume that we have a ruler and a compass. Let us also assume that we have a segment of length one. Using these tools we can
CS Communication Complexity: Applications and New Directions
 CS 2429 - Communication Complexity: Applications and New Directions Lecturer: Toniann Pitassi 1 Introduction In this course we will define the basic two-party model of communication, as introduced in the
CS 2429 - Communication Complexity: Applications and New Directions Lecturer: Toniann Pitassi 1 Introduction In this course we will define the basic two-party model of communication, as introduced in the
2 P vs. NP and Diagonalization
 2 P vs NP and Diagonalization CS 6810 Theory of Computing, Fall 2012 Instructor: David Steurer (sc2392) Date: 08/28/2012 In this lecture, we cover the following topics: 1 3SAT is NP hard; 2 Time hierarchies;
2 P vs NP and Diagonalization CS 6810 Theory of Computing, Fall 2012 Instructor: David Steurer (sc2392) Date: 08/28/2012 In this lecture, we cover the following topics: 1 3SAT is NP hard; 2 Time hierarchies;
The Heine-Borel and Arzela-Ascoli Theorems
 The Heine-Borel and Arzela-Ascoli Theorems David Jekel October 29, 2016 This paper explains two important results about compactness, the Heine- Borel theorem and the Arzela-Ascoli theorem. We prove them
The Heine-Borel and Arzela-Ascoli Theorems David Jekel October 29, 2016 This paper explains two important results about compactness, the Heine- Borel theorem and the Arzela-Ascoli theorem. We prove them
MORE ON CONTINUOUS FUNCTIONS AND SETS
 Chapter 6 MORE ON CONTINUOUS FUNCTIONS AND SETS This chapter can be considered enrichment material containing also several more advanced topics and may be skipped in its entirety. You can proceed directly
Chapter 6 MORE ON CONTINUOUS FUNCTIONS AND SETS This chapter can be considered enrichment material containing also several more advanced topics and may be skipped in its entirety. You can proceed directly
a 2 = ab a 2 b 2 = ab b 2 (a + b)(a b) = b(a b) a + b = b
 Discrete Structures CS2800 Fall 204 Final Solutions. Briefly and clearly identify the errors in each of the following proofs: (a) Proof that is the largest natural number: Let n be the largest natural
Discrete Structures CS2800 Fall 204 Final Solutions. Briefly and clearly identify the errors in each of the following proofs: (a) Proof that is the largest natural number: Let n be the largest natural
Lecture 4: Constructing the Integers, Rationals and Reals
 Math/CS 20: Intro. to Math Professor: Padraic Bartlett Lecture 4: Constructing the Integers, Rationals and Reals Week 5 UCSB 204 The Integers Normally, using the natural numbers, you can easily define
Math/CS 20: Intro. to Math Professor: Padraic Bartlett Lecture 4: Constructing the Integers, Rationals and Reals Week 5 UCSB 204 The Integers Normally, using the natural numbers, you can easily define
1 Primals and Duals: Zero Sum Games
 CS 124 Section #11 Zero Sum Games; NP Completeness 4/15/17 1 Primals and Duals: Zero Sum Games We can represent various situations of conflict in life in terms of matrix games. For example, the game shown
CS 124 Section #11 Zero Sum Games; NP Completeness 4/15/17 1 Primals and Duals: Zero Sum Games We can represent various situations of conflict in life in terms of matrix games. For example, the game shown
Kolmogorov complexity
 Kolmogorov complexity In this section we study how we can define the amount of information in a bitstring. Consider the following strings: 00000000000000000000000000000000000 0000000000000000000000000000000000000000
Kolmogorov complexity In this section we study how we can define the amount of information in a bitstring. Consider the following strings: 00000000000000000000000000000000000 0000000000000000000000000000000000000000
Cone Avoidance of Some Turing Degrees
 Journal of Mathematics Research; Vol. 9, No. 4; August 2017 ISSN 1916-9795 E-ISSN 1916-9809 Published by Canadian Center of Science and Education Cone Avoidance of Some Turing Degrees Patrizio Cintioli
Journal of Mathematics Research; Vol. 9, No. 4; August 2017 ISSN 1916-9795 E-ISSN 1916-9809 Published by Canadian Center of Science and Education Cone Avoidance of Some Turing Degrees Patrizio Cintioli
Notes for Lecture 3... x 4
 Stanford University CS254: Computational Complexity Notes 3 Luca Trevisan January 18, 2012 Notes for Lecture 3 In this lecture we introduce the computational model of boolean circuits and prove that polynomial
Stanford University CS254: Computational Complexity Notes 3 Luca Trevisan January 18, 2012 Notes for Lecture 3 In this lecture we introduce the computational model of boolean circuits and prove that polynomial
Solutions to the 74th William Lowell Putnam Mathematical Competition Saturday, December 7, 2013
 Solutions to the 74th William Lowell Putnam Mathematical Competition Saturday, December 7, 213 Kiran Kedlaya and Lenny Ng A1 Suppose otherwise. Then each vertex v is a vertex for five faces, all of which
Solutions to the 74th William Lowell Putnam Mathematical Competition Saturday, December 7, 213 Kiran Kedlaya and Lenny Ng A1 Suppose otherwise. Then each vertex v is a vertex for five faces, all of which
arxiv: v1 [math.co] 7 Jul 2014
![arxiv: v1 [math.co] 7 Jul 2014 arxiv: v1 [math.co] 7 Jul 2014](/thumbs/92/110910633.jpg) Sum-ratio estimates over arbitrary finite fields Oliver Roche-Newton arxiv:1407.1654v1 [math.co] 7 Jul 2014 July 11, 2018 Abstract The aim of this note is to record a proof that the estimate max{ A+A,
Sum-ratio estimates over arbitrary finite fields Oliver Roche-Newton arxiv:1407.1654v1 [math.co] 7 Jul 2014 July 11, 2018 Abstract The aim of this note is to record a proof that the estimate max{ A+A,
Lecture 14 - P v.s. NP 1
 CME 305: Discrete Mathematics and Algorithms Instructor: Professor Aaron Sidford (sidford@stanford.edu) February 27, 2018 Lecture 14 - P v.s. NP 1 In this lecture we start Unit 3 on NP-hardness and approximation
CME 305: Discrete Mathematics and Algorithms Instructor: Professor Aaron Sidford (sidford@stanford.edu) February 27, 2018 Lecture 14 - P v.s. NP 1 In this lecture we start Unit 3 on NP-hardness and approximation
Continuity. Chapter 4
 Chapter 4 Continuity Throughout this chapter D is a nonempty subset of the real numbers. We recall the definition of a function. Definition 4.1. A function from D into R, denoted f : D R, is a subset of
Chapter 4 Continuity Throughout this chapter D is a nonempty subset of the real numbers. We recall the definition of a function. Definition 4.1. A function from D into R, denoted f : D R, is a subset of
MTAT Complexity Theory October 13th-14th, Lecture 6
 MTAT.07.004 Complexity Theory October 13th-14th, 2011 Lecturer: Peeter Laud Lecture 6 Scribe(s): Riivo Talviste 1 Logarithmic memory Turing machines working in logarithmic space become interesting when
MTAT.07.004 Complexity Theory October 13th-14th, 2011 Lecturer: Peeter Laud Lecture 6 Scribe(s): Riivo Talviste 1 Logarithmic memory Turing machines working in logarithmic space become interesting when
A An Overview of Complexity Theory for the Algorithm Designer
 A An Overview of Complexity Theory for the Algorithm Designer A.1 Certificates and the class NP A decision problem is one whose answer is either yes or no. Two examples are: SAT: Given a Boolean formula
A An Overview of Complexity Theory for the Algorithm Designer A.1 Certificates and the class NP A decision problem is one whose answer is either yes or no. Two examples are: SAT: Given a Boolean formula
Lecture 2: Connecting the Three Models
 IAS/PCMI Summer Session 2000 Clay Mathematics Undergraduate Program Advanced Course on Computational Complexity Lecture 2: Connecting the Three Models David Mix Barrington and Alexis Maciel July 18, 2000
IAS/PCMI Summer Session 2000 Clay Mathematics Undergraduate Program Advanced Course on Computational Complexity Lecture 2: Connecting the Three Models David Mix Barrington and Alexis Maciel July 18, 2000
MTAT Complexity Theory October 20th-21st, Lecture 7
 MTAT.07.004 Complexity Theory October 20th-21st, 2011 Lecturer: Peeter Laud Lecture 7 Scribe(s): Riivo Talviste Polynomial hierarchy 1 Turing reducibility From the algorithmics course, we know the notion
MTAT.07.004 Complexity Theory October 20th-21st, 2011 Lecturer: Peeter Laud Lecture 7 Scribe(s): Riivo Talviste Polynomial hierarchy 1 Turing reducibility From the algorithmics course, we know the notion
Critical Reading of Optimization Methods for Logical Inference [1]
![Critical Reading of Optimization Methods for Logical Inference [1] Critical Reading of Optimization Methods for Logical Inference [1]](/thumbs/95/124347829.jpg) Critical Reading of Optimization Methods for Logical Inference [1] Undergraduate Research Internship Department of Management Sciences Fall 2007 Supervisor: Dr. Miguel Anjos UNIVERSITY OF WATERLOO Rajesh
Critical Reading of Optimization Methods for Logical Inference [1] Undergraduate Research Internship Department of Management Sciences Fall 2007 Supervisor: Dr. Miguel Anjos UNIVERSITY OF WATERLOO Rajesh
REU 2007 Transfinite Combinatorics Lecture 9
 REU 2007 Transfinite Combinatorics Lecture 9 Instructor: László Babai Scribe: Travis Schedler August 10, 2007. Revised by instructor. Last updated August 11, 3:40pm Note: All (0, 1)-measures will be assumed
REU 2007 Transfinite Combinatorics Lecture 9 Instructor: László Babai Scribe: Travis Schedler August 10, 2007. Revised by instructor. Last updated August 11, 3:40pm Note: All (0, 1)-measures will be assumed
On Computing Boolean Connectives of Characteristic Functions
 On Computing Boolean Connectives of Characteristic Functions Richard Chang Computer Science Department Cornell University Ithaca, NY 14853 Jim Kadin Computer Science Department University of Maine Orono,
On Computing Boolean Connectives of Characteristic Functions Richard Chang Computer Science Department Cornell University Ithaca, NY 14853 Jim Kadin Computer Science Department University of Maine Orono,
1 Topology Definition of a topology Basis (Base) of a topology The subspace topology & the product topology on X Y 3
 Index Page 1 Topology 2 1.1 Definition of a topology 2 1.2 Basis (Base) of a topology 2 1.3 The subspace topology & the product topology on X Y 3 1.4 Basic topology concepts: limit points, closed sets,
Index Page 1 Topology 2 1.1 Definition of a topology 2 1.2 Basis (Base) of a topology 2 1.3 The subspace topology & the product topology on X Y 3 1.4 Basic topology concepts: limit points, closed sets,
The Minesweeper game: Percolation and Complexity
 The Minesweeper game: Percolation and Complexity Elchanan Mossel Hebrew University of Jerusalem and Microsoft Research March 15, 2002 Abstract We study a model motivated by the minesweeper game In this
The Minesweeper game: Percolation and Complexity Elchanan Mossel Hebrew University of Jerusalem and Microsoft Research March 15, 2002 Abstract We study a model motivated by the minesweeper game In this
Math 320-2: Final Exam Practice Solutions Northwestern University, Winter 2015
 Math 30-: Final Exam Practice Solutions Northwestern University, Winter 015 1. Give an example of each of the following. No justification is needed. (a) A closed and bounded subset of C[0, 1] which is
Math 30-: Final Exam Practice Solutions Northwestern University, Winter 015 1. Give an example of each of the following. No justification is needed. (a) A closed and bounded subset of C[0, 1] which is
Kolmogorov Complexity with Error
 Kolmogorov Complexity with Error Lance Fortnow 1, Troy Lee 2, and Nikolai Vereshchagin 3, 1 University of Chicago, 1100 E. 58th Street, Chicago, IL, USA 60637. fortnow@cs.uchicago.edu, http://people.cs.uchicago.edu/~fortnow
Kolmogorov Complexity with Error Lance Fortnow 1, Troy Lee 2, and Nikolai Vereshchagin 3, 1 University of Chicago, 1100 E. 58th Street, Chicago, IL, USA 60637. fortnow@cs.uchicago.edu, http://people.cs.uchicago.edu/~fortnow
Exercise Sheet #1 Solutions, Computer Science, A M. Hallett, K. Smith a k n b k = n b + k. a k n b k c 1 n b k. a k n b.
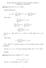 Exercise Sheet #1 Solutions, Computer Science, 308-251A M. Hallett, K. Smith 2002 Question 1.1: Prove (n + a) b = Θ(n b ). Binomial Expansion: Show O(n b ): (n + a) b = For any c 1 > b = O(n b ). Show
Exercise Sheet #1 Solutions, Computer Science, 308-251A M. Hallett, K. Smith 2002 Question 1.1: Prove (n + a) b = Θ(n b ). Binomial Expansion: Show O(n b ): (n + a) b = For any c 1 > b = O(n b ). Show
Extension of continuous functions in digital spaces with the Khalimsky topology
 Extension of continuous functions in digital spaces with the Khalimsky topology Erik Melin Uppsala University, Department of Mathematics Box 480, SE-751 06 Uppsala, Sweden melin@math.uu.se http://www.math.uu.se/~melin
Extension of continuous functions in digital spaces with the Khalimsky topology Erik Melin Uppsala University, Department of Mathematics Box 480, SE-751 06 Uppsala, Sweden melin@math.uu.se http://www.math.uu.se/~melin
3 Self-Delimiting Kolmogorov complexity
 3 Self-Delimiting Kolmogorov complexity 3. Prefix codes A set is called a prefix-free set (or a prefix set) if no string in the set is the proper prefix of another string in it. A prefix set cannot therefore
3 Self-Delimiting Kolmogorov complexity 3. Prefix codes A set is called a prefix-free set (or a prefix set) if no string in the set is the proper prefix of another string in it. A prefix set cannot therefore
Decentralized Control of Discrete Event Systems with Bounded or Unbounded Delay Communication
 Decentralized Control of Discrete Event Systems with Bounded or Unbounded Delay Communication Stavros Tripakis Abstract We introduce problems of decentralized control with communication, where we explicitly
Decentralized Control of Discrete Event Systems with Bounded or Unbounded Delay Communication Stavros Tripakis Abstract We introduce problems of decentralized control with communication, where we explicitly
Game Theory and Rationality
 April 6, 2015 Notation for Strategic Form Games Definition A strategic form game (or normal form game) is defined by 1 The set of players i = {1,..., N} 2 The (usually finite) set of actions A i for each
April 6, 2015 Notation for Strategic Form Games Definition A strategic form game (or normal form game) is defined by 1 The set of players i = {1,..., N} 2 The (usually finite) set of actions A i for each
Kolmogorov-Loveland Randomness and Stochasticity
 Kolmogorov-Loveland Randomness and Stochasticity Wolfgang Merkle 1, Joseph Miller 2, André Nies 3, Jan Reimann 1, and Frank Stephan 4 1 Universität Heidelberg, Heidelberg, Germany 2 Indiana University,
Kolmogorov-Loveland Randomness and Stochasticity Wolfgang Merkle 1, Joseph Miller 2, André Nies 3, Jan Reimann 1, and Frank Stephan 4 1 Universität Heidelberg, Heidelberg, Germany 2 Indiana University,
4 Choice axioms and Baire category theorem
 Tel Aviv University, 2013 Measure and category 30 4 Choice axioms and Baire category theorem 4a Vitali set....................... 30 4b No choice....................... 31 4c Dependent choice..................
Tel Aviv University, 2013 Measure and category 30 4 Choice axioms and Baire category theorem 4a Vitali set....................... 30 4b No choice....................... 31 4c Dependent choice..................
Algorithmic Information Theory and Kolmogorov Complexity
 Algorithmic Information Theory and Kolmogorov Complexity Alexander Shen, Uppsala University, Computing Science Department, Independent University of Moscow, shen@mccme.ru November 19, 2007 Abstract This
Algorithmic Information Theory and Kolmogorov Complexity Alexander Shen, Uppsala University, Computing Science Department, Independent University of Moscow, shen@mccme.ru November 19, 2007 Abstract This
Compression Complexity
 Compression Complexity Stephen Fenner University of South Carolina Lance Fortnow Georgia Institute of Technology February 15, 2017 Abstract The Kolmogorov complexity of x, denoted C(x), is the length of
Compression Complexity Stephen Fenner University of South Carolina Lance Fortnow Georgia Institute of Technology February 15, 2017 Abstract The Kolmogorov complexity of x, denoted C(x), is the length of
Measures of relative complexity
 Measures of relative complexity George Barmpalias Institute of Software Chinese Academy of Sciences and Visiting Fellow at the Isaac Newton Institute for the Mathematical Sciences Newton Institute, January
Measures of relative complexity George Barmpalias Institute of Software Chinese Academy of Sciences and Visiting Fellow at the Isaac Newton Institute for the Mathematical Sciences Newton Institute, January
Randomness, probabilities and machines
 1/20 Randomness, probabilities and machines by George Barmpalias and David Dowe Chinese Academy of Sciences - Monash University CCR 2015, Heildeberg 2/20 Concrete examples of random numbers? Chaitin (1975)
1/20 Randomness, probabilities and machines by George Barmpalias and David Dowe Chinese Academy of Sciences - Monash University CCR 2015, Heildeberg 2/20 Concrete examples of random numbers? Chaitin (1975)
Lecture 11: Proofs, Games, and Alternation
 IAS/PCMI Summer Session 2000 Clay Mathematics Undergraduate Program Basic Course on Computational Complexity Lecture 11: Proofs, Games, and Alternation David Mix Barrington and Alexis Maciel July 31, 2000
IAS/PCMI Summer Session 2000 Clay Mathematics Undergraduate Program Basic Course on Computational Complexity Lecture 11: Proofs, Games, and Alternation David Mix Barrington and Alexis Maciel July 31, 2000
CSCI3390-Lecture 6: An Undecidable Problem
 CSCI3390-Lecture 6: An Undecidable Problem September 21, 2018 1 Summary The language L T M recognized by the universal Turing machine is not decidable. Thus there is no algorithm that determines, yes or
CSCI3390-Lecture 6: An Undecidable Problem September 21, 2018 1 Summary The language L T M recognized by the universal Turing machine is not decidable. Thus there is no algorithm that determines, yes or
DR.RUPNATHJI( DR.RUPAK NATH )
 Contents 1 Sets 1 2 The Real Numbers 9 3 Sequences 29 4 Series 59 5 Functions 81 6 Power Series 105 7 The elementary functions 111 Chapter 1 Sets It is very convenient to introduce some notation and terminology
Contents 1 Sets 1 2 The Real Numbers 9 3 Sequences 29 4 Series 59 5 Functions 81 6 Power Series 105 7 The elementary functions 111 Chapter 1 Sets It is very convenient to introduce some notation and terminology
Introduction to Kolmogorov Complexity
 Introduction to Kolmogorov Complexity Marcus Hutter Canberra, ACT, 0200, Australia http://www.hutter1.net/ ANU Marcus Hutter - 2 - Introduction to Kolmogorov Complexity Abstract In this talk I will give
Introduction to Kolmogorov Complexity Marcus Hutter Canberra, ACT, 0200, Australia http://www.hutter1.net/ ANU Marcus Hutter - 2 - Introduction to Kolmogorov Complexity Abstract In this talk I will give
Discrete Mathematics and Probability Theory Spring 2014 Anant Sahai Note 20. To Infinity And Beyond: Countability and Computability
 EECS 70 Discrete Mathematics and Probability Theory Spring 014 Anant Sahai Note 0 To Infinity And Beyond: Countability and Computability This note ties together two topics that might seem like they have
EECS 70 Discrete Mathematics and Probability Theory Spring 014 Anant Sahai Note 0 To Infinity And Beyond: Countability and Computability This note ties together two topics that might seem like they have
Lecture 6: Oracle TMs, Diagonalization Limits, Space Complexity
 CSE 531: Computational Complexity I Winter 2016 Lecture 6: Oracle TMs, Diagonalization Limits, Space Complexity January 22, 2016 Lecturer: Paul Beame Scribe: Paul Beame Diagonalization enabled us to separate
CSE 531: Computational Complexity I Winter 2016 Lecture 6: Oracle TMs, Diagonalization Limits, Space Complexity January 22, 2016 Lecturer: Paul Beame Scribe: Paul Beame Diagonalization enabled us to separate
Kolmogorov-Loveland Randomness and Stochasticity
 Kolmogorov-Loveland Randomness and Stochasticity Wolfgang Merkle Institut für Informatik, Ruprecht-Karls-Universität Heidelberg Joseph S. Miller Department of Mathematics, University of Connecticut, Storrs
Kolmogorov-Loveland Randomness and Stochasticity Wolfgang Merkle Institut für Informatik, Ruprecht-Karls-Universität Heidelberg Joseph S. Miller Department of Mathematics, University of Connecticut, Storrs
The Turán number of sparse spanning graphs
 The Turán number of sparse spanning graphs Noga Alon Raphael Yuster Abstract For a graph H, the extremal number ex(n, H) is the maximum number of edges in a graph of order n not containing a subgraph isomorphic
The Turán number of sparse spanning graphs Noga Alon Raphael Yuster Abstract For a graph H, the extremal number ex(n, H) is the maximum number of edges in a graph of order n not containing a subgraph isomorphic
Basic counting techniques. Periklis A. Papakonstantinou Rutgers Business School
 Basic counting techniques Periklis A. Papakonstantinou Rutgers Business School i LECTURE NOTES IN Elementary counting methods Periklis A. Papakonstantinou MSIS, Rutgers Business School ALL RIGHTS RESERVED
Basic counting techniques Periklis A. Papakonstantinou Rutgers Business School i LECTURE NOTES IN Elementary counting methods Periklis A. Papakonstantinou MSIS, Rutgers Business School ALL RIGHTS RESERVED
2. Intersection Multiplicities
 2. Intersection Multiplicities 11 2. Intersection Multiplicities Let us start our study of curves by introducing the concept of intersection multiplicity, which will be central throughout these notes.
2. Intersection Multiplicities 11 2. Intersection Multiplicities Let us start our study of curves by introducing the concept of intersection multiplicity, which will be central throughout these notes.
CSC 5170: Theory of Computational Complexity Lecture 9 The Chinese University of Hong Kong 15 March 2010
 CSC 5170: Theory of Computational Complexity Lecture 9 The Chinese University of Hong Kong 15 March 2010 We now embark on a study of computational classes that are more general than NP. As these classes
CSC 5170: Theory of Computational Complexity Lecture 9 The Chinese University of Hong Kong 15 March 2010 We now embark on a study of computational classes that are more general than NP. As these classes
OPTION-CLOSED GAMES RICHARD J. NOWAKOWSKI AND PAUL OTTAWAY
 Volume 6, Number 1, Pages 142 153 ISSN 1715-0868 OPTION-CLOSED GAMES RICHARD J. NOWAKOWSKI AND PAUL OTTAWAY Abstract. We consider the class of combinatorial games with the property that each player s move
Volume 6, Number 1, Pages 142 153 ISSN 1715-0868 OPTION-CLOSED GAMES RICHARD J. NOWAKOWSKI AND PAUL OTTAWAY Abstract. We consider the class of combinatorial games with the property that each player s move
arxiv: v1 [cs.dm] 12 Jun 2016
![arxiv: v1 [cs.dm] 12 Jun 2016 arxiv: v1 [cs.dm] 12 Jun 2016](/thumbs/93/113276497.jpg) A Simple Extension of Dirac s Theorem on Hamiltonicity Yasemin Büyükçolak a,, Didem Gözüpek b, Sibel Özkana, Mordechai Shalom c,d,1 a Department of Mathematics, Gebze Technical University, Kocaeli, Turkey
A Simple Extension of Dirac s Theorem on Hamiltonicity Yasemin Büyükçolak a,, Didem Gözüpek b, Sibel Özkana, Mordechai Shalom c,d,1 a Department of Mathematics, Gebze Technical University, Kocaeli, Turkey
Journal of Computer and System Sciences
 Journal of Computer and System Sciences 77 (2011) 738 742 Contents lists available at ScienceDirect Journal of Computer and System Sciences www.elsevier.com/locate/jcss Nonapproximability of the normalized
Journal of Computer and System Sciences 77 (2011) 738 742 Contents lists available at ScienceDirect Journal of Computer and System Sciences www.elsevier.com/locate/jcss Nonapproximability of the normalized
Enumerations including laconic enumerators
 Enumerations including laconic enumerators Sanjay Jain National University of Singapore sanjay@comp.nus.edu.sg Jason Teutsch TrueBit Foundation jt@truebit.io June 19, 2017 Abstract We show that it is possible,
Enumerations including laconic enumerators Sanjay Jain National University of Singapore sanjay@comp.nus.edu.sg Jason Teutsch TrueBit Foundation jt@truebit.io June 19, 2017 Abstract We show that it is possible,
Mathematical Systems Theory 1996 Springer-Verlag New York Inc.
 Math. Systems Theory 29, 271 292 (1996) Mathematical Systems Theory 1996 Springer-Verlag New York Inc. Relations Between Varieties of Kolmogorov Complexities V. A. Uspensky 1 and A. Shen 2 1 Division of
Math. Systems Theory 29, 271 292 (1996) Mathematical Systems Theory 1996 Springer-Verlag New York Inc. Relations Between Varieties of Kolmogorov Complexities V. A. Uspensky 1 and A. Shen 2 1 Division of
