Probabilistic Methods in Concurrency. Lecture 4
|
|
|
- Thomasine Park
- 6 years ago
- Views:
Transcription
1 Probabilistic Methods in oncurrency Lecture 4 Problems in distributed systems for which only randomized solutions exist atuscia Palamidessi catuscia@lix.polytechnique.fr Page of the course:
2 (1) The dining philosophers Each philosopher needs exactly two forks Each fork is shared by exactly two philosophers philosopher can access only one fork at the time Pisa, 1 July 2004 Prob methods in oncurrency 2
3 Intended properties of solution Deadlock freedom (aka progress): if there is a hungry philosopher, a philosopher will eventually eat Starvation freedom: every hungry philosopher will eventually eat (but we won t consider this property here) Robustness wrt a large class of adversaries: dversaries decide who does the next move (schedulers) Fully distributed: no centralized control or memory Symmetric: ll philosophers run the same code and are in the same initial state The same holds for the forks Pisa, 1 July 2004 Prob methods in oncurrency 3
4 Non-existence of a deterministic solution Lehman and Rabin have shown that there does not exist a deterministic (i.e. non-probabilistic) solution to the dining philosophers, satisfying all properties listed in previous slide. The proof proceeds by proving that for every possible program we can define an adversary (scheduler) which preserves the initial symmetry Note: Francez and Rodeh did propose a deterministic solution using SP. The solution to this apparent contradiction is that SP cannot be implemented in a fully distributed way Pisa, 1 July 2004 Prob methods in oncurrency 4
5 The algorithm of Lehmann and Rabin 1. Think 2. randomly choose fork in {left,right} %commit 3. if taken(fork) then goto 3 4. else take(fork) 5. if taken(other(fork)) then {release(fork); goto 2} 6. else take(other(fork)) 7. eat 8. release(other(fork)) 9. release(fork) 10. goto 1 Pisa, 1 July 2004 Prob methods in oncurrency 5
6 orrectness of the algorithm of Lehmann and Rabin Theorem: for every fair adversary, if a philosopher becomes hungry, then a philosopher (not necessarily the same) will eventually eat with probability 1. Question: why the fairness requirement? an we write a variant of the algorithm which does not require fairness? Pisa, 1 July 2004 Prob methods in oncurrency 6
7 (2) The committee coordination problem Description of the problem: In a certain university, professors have organized themselves into committees. Each committee has a fixed membership roster of two or more professors. From time to time a professor may decide to attend a committee meeting. He then starts waiting and continues to wait until a meeting of a committee in which he is member is established. Requirements: Mutual exclusion: No two committees meet simultaneously if they have a common member Weak Interaction Fairness (WIF) : if all professors of a committee are waiting (i.e. the committee meeting is enabled), then eventually some professor will attend a committee meeting (not necessarily the same). or Strong Interaction Fairness (SIF): committee meetig that is enabled infinitely often will be established infinitely often Pisa, 1 July 2004 Prob methods in oncurrency 7
8 The committee coordination problem Question: for which requirement among WIF and SIF do we have a correspondence with the synchronization mechanisms used in process calculi, like (the theory of) SP and π? General case equivalent to multiway synchronization, like the mechanism used in (the Theory of) SP inary case equivalent to the synchronization among two partners, like in S and π Pisa, 1 July 2004 Prob methods in oncurrency 8
9 The algorithm of Joung and Smolka 1. while waiting do { 2. randomly choose a committee M ; 3. if TEST&OP( M,inc,inc) = n M 1 4. then % a committee meeting is established 5. attend the meeting M 6. else { wait δ M time ; 7. if TEST&OP( M,no-op,dec) = 0 8. then % a committee meeting is established 9. attend the meeting M 10. % else try another committee } Pisa, 1 July 2004 Prob methods in oncurrency 9
10 orrectness of the algoritm ssumption: δ M > max prof {time 2-3 (M,prof)} Theorem: if a committee is enabled then a professor will eventually attend a meeting with probability 1 (WIF) Theorem: if a professor s transition from thinking to waiting does not depend on the random draws performed by other professors, then a committee meeting which is enabled infinitely often will eventually be established (SIF) Pisa, 1 July 2004 Prob methods in oncurrency 10
11 Importance of the assumption on δ The assumption on δ M is an assumption about the degree of synchronism (in the sense of cooperation) of the system. In Distributed lgorithms there are three models of cooperation: 1. Partially synchronous 2. synchronous 3. Synchronous (lockstep) This assumption corresponds to (2) Hence this algorithm would not be suitable for implementing the synchronization mechanism of SP or S in a fully distributed setting, since we need an asynchronous cooperation model. Pisa, 1 July 2004 Prob methods in oncurrency 11
12 lgorithm of Joung and Smolka: Example of a livelock in absence of the assumption on δ The states at the beginning of Lines 3, 5 and 6 are represented with a filled circle. The states at the beginning of Line 1, 2 and 8 are represented with a white circle. Lines 4 and 7 are never reached Pisa, 1 July 2004 Prob methods in oncurrency 12
On the generalized dining philosophers problem
 On the generalized dining philosophers problem Oltea Mihaela Herescu Catuscia Palamidessi Department of Computer Science and Engineering, The Pennsylvania State University Pond Lab, University Park, PA
On the generalized dining philosophers problem Oltea Mihaela Herescu Catuscia Palamidessi Department of Computer Science and Engineering, The Pennsylvania State University Pond Lab, University Park, PA
Correctness of Concurrent Programs
 Correctness of Concurrent Programs Trifon Ruskov ruskov@tu-varna.acad.bg Technical University of Varna - Bulgaria Correctness of Concurrent Programs Correctness of concurrent programs needs to be formalized:
Correctness of Concurrent Programs Trifon Ruskov ruskov@tu-varna.acad.bg Technical University of Varna - Bulgaria Correctness of Concurrent Programs Correctness of concurrent programs needs to be formalized:
On Randomization versus Synchronization in Distributed Systems
 On Randomization versus Synchronization in Distributed Systems Hagen Völzer Institut für Theoretische Informatik Universität zu Lübeck Germany July 14, 2004 ICALP 2004, Turku 0 Outline two new impossibility
On Randomization versus Synchronization in Distributed Systems Hagen Völzer Institut für Theoretische Informatik Universität zu Lübeck Germany July 14, 2004 ICALP 2004, Turku 0 Outline two new impossibility
Verification of. Probabilistic Programs. Seminar on. Federico Olmedo. Pr[n = k] = 1 2
![Verification of. Probabilistic Programs. Seminar on. Federico Olmedo. Pr[n = k] = 1 2 Verification of. Probabilistic Programs. Seminar on. Federico Olmedo. Pr[n = k] = 1 2](/thumbs/88/116213861.jpg) Seminar on Verification of n := 0; repeat n := n + 1; c := coin flip(0.5) until (c=heads); return n Probabilistic Programs Pr[n = k] = 1 2 k Federico Olmedo federico.olmedo@cs.rwth-aachen.de 1 Seminar
Seminar on Verification of n := 0; repeat n := n + 1; c := coin flip(0.5) until (c=heads); return n Probabilistic Programs Pr[n = k] = 1 2 k Federico Olmedo federico.olmedo@cs.rwth-aachen.de 1 Seminar
1 Lamport s Bakery Algorithm
 Com S 6 Spring Semester 2009 Algorithms for Multiprocessor Synchronization Lecture 3: Tuesday, 27th January 2009 Instructor: Soma Chaudhuri Scribe: Neeraj Khanolkar Lamport s Bakery Algorithm Algorithm
Com S 6 Spring Semester 2009 Algorithms for Multiprocessor Synchronization Lecture 3: Tuesday, 27th January 2009 Instructor: Soma Chaudhuri Scribe: Neeraj Khanolkar Lamport s Bakery Algorithm Algorithm
Clojure Concurrency Constructs, Part Two. CSCI 5828: Foundations of Software Engineering Lecture 13 10/07/2014
 Clojure Concurrency Constructs, Part Two CSCI 5828: Foundations of Software Engineering Lecture 13 10/07/2014 1 Goals Cover the material presented in Chapter 4, of our concurrency textbook In particular,
Clojure Concurrency Constructs, Part Two CSCI 5828: Foundations of Software Engineering Lecture 13 10/07/2014 1 Goals Cover the material presented in Chapter 4, of our concurrency textbook In particular,
Verifying Randomized Distributed Algorithms with PRISM
 Verifying Randomized Distributed Algorithms with PRISM Marta Kwiatkowska, Gethin Norman, and David Parker University of Birmingham, Birmingham B15 2TT, United Kingdom {M.Z.Kwiatkowska,G.Norman,D.A.Parker}@cs.bham.ac.uk
Verifying Randomized Distributed Algorithms with PRISM Marta Kwiatkowska, Gethin Norman, and David Parker University of Birmingham, Birmingham B15 2TT, United Kingdom {M.Z.Kwiatkowska,G.Norman,D.A.Parker}@cs.bham.ac.uk
Methods for the specification and verification of business processes MPB (6 cfu, 295AA)
 Methods for the specification and verification of business processes MPB (6 cfu, 295AA) Roberto Bruni http://www.di.unipi.it/~bruni 08 - Petri nets basics 1 Object Formalization of the basic concepts of
Methods for the specification and verification of business processes MPB (6 cfu, 295AA) Roberto Bruni http://www.di.unipi.it/~bruni 08 - Petri nets basics 1 Object Formalization of the basic concepts of
THE WEAKEST FAILURE DETECTOR FOR SOLVING WAIT-FREE, EVENTUALLY BOUNDED-FAIR DINING PHILOSOPHERS. A Dissertation YANTAO SONG
 THE WEAKEST FAILURE DETECTOR FOR SOLVING WAIT-FREE, EVENTUALLY BOUNDED-FAIR DINING PHILOSOPHERS A Dissertation by YANTAO SONG Submitted to the Office of Graduate Studies of Texas A&M University in partial
THE WEAKEST FAILURE DETECTOR FOR SOLVING WAIT-FREE, EVENTUALLY BOUNDED-FAIR DINING PHILOSOPHERS A Dissertation by YANTAO SONG Submitted to the Office of Graduate Studies of Texas A&M University in partial
Asynchronous Models For Consensus
 Distributed Systems 600.437 Asynchronous Models for Consensus Department of Computer Science The Johns Hopkins University 1 Asynchronous Models For Consensus Lecture 5 Further reading: Distributed Algorithms
Distributed Systems 600.437 Asynchronous Models for Consensus Department of Computer Science The Johns Hopkins University 1 Asynchronous Models For Consensus Lecture 5 Further reading: Distributed Algorithms
TERMINATION OF PROBABILISTIC CONCURRENT PROGRAMS. (Extended Abstract) Sergiu Hart, Micha Sharir Tel Aviv University
 TERMINATION OF PROBABILISTIC CONCURRENT PROGRAMS (Extended Abstract) Sergiu Hart, Micha Sharir Tel Aviv University Amir Pnueli Weizmann Institute of Science Abstract. The asynchronous execution behavior
TERMINATION OF PROBABILISTIC CONCURRENT PROGRAMS (Extended Abstract) Sergiu Hart, Micha Sharir Tel Aviv University Amir Pnueli Weizmann Institute of Science Abstract. The asynchronous execution behavior
INF 4140: Models of Concurrency Series 3
 Universitetet i Oslo Institutt for Informatikk PMA Olaf Owe, Martin Steffen, Toktam Ramezani INF 4140: Models of Concurrency Høst 2016 Series 3 14. 9. 2016 Topic: Semaphores (Exercises with hints for solution)
Universitetet i Oslo Institutt for Informatikk PMA Olaf Owe, Martin Steffen, Toktam Ramezani INF 4140: Models of Concurrency Høst 2016 Series 3 14. 9. 2016 Topic: Semaphores (Exercises with hints for solution)
CS505: Distributed Systems
 Cristina Nita-Rotaru CS505: Distributed Systems. Required reading for this topic } Michael J. Fischer, Nancy A. Lynch, and Michael S. Paterson for "Impossibility of Distributed with One Faulty Process,
Cristina Nita-Rotaru CS505: Distributed Systems. Required reading for this topic } Michael J. Fischer, Nancy A. Lynch, and Michael S. Paterson for "Impossibility of Distributed with One Faulty Process,
A modular approach to shared-memory consensus, with applications to the probabilistic-write model
 A modular approach to shared-memory consensus, with applications to the probabilistic-write model James Aspnes Yale University July 28th, 2010 Randomized consensus Problem definition Known bounds Probabilistic-write
A modular approach to shared-memory consensus, with applications to the probabilistic-write model James Aspnes Yale University July 28th, 2010 Randomized consensus Problem definition Known bounds Probabilistic-write
Improper Nesting Example
 Improper Nesting Example One of the limits on the use of parbegin/parend, and any related constructs, is that the program involved must be properly nested. Not all programs are. For example, consider the
Improper Nesting Example One of the limits on the use of parbegin/parend, and any related constructs, is that the program involved must be properly nested. Not all programs are. For example, consider the
An Introduction to Temporal Logics
 An Introduction to Temporal Logics c 2001,2004 M. Lawford Outline Motivation: Dining Philosophers Safety, Liveness, Fairness & Justice Kripke structures, LTS, SELTS, and Paths Linear Temporal Logic Branching
An Introduction to Temporal Logics c 2001,2004 M. Lawford Outline Motivation: Dining Philosophers Safety, Liveness, Fairness & Justice Kripke structures, LTS, SELTS, and Paths Linear Temporal Logic Branching
fakultät für informatik informatik 12 technische universität dortmund Petri nets Peter Marwedel Informatik 12 TU Dortmund Germany
 12 Petri nets Peter Marwedel Informatik 12 TU Dortmund Germany Introduction Introduced in 1962 by Carl Adam Petri in his PhD thesis. Focus on modeling causal dependencies; no global synchronization assumed
12 Petri nets Peter Marwedel Informatik 12 TU Dortmund Germany Introduction Introduced in 1962 by Carl Adam Petri in his PhD thesis. Focus on modeling causal dependencies; no global synchronization assumed
Introduction to Self-Stabilization. Maria Potop-Butucaru, Franck Petit and Sébastien Tixeuil LiP6/UPMC
 Introduction to Self-Stabilization Maria Potop-Butucaru, Franck Petit and Sébastien Tixeuil LiP6/UPMC Self-stabilization 101 Example U 0 = a U n+1 = U n 2 if U n is even U n+1 = 3U n+1 2 if U n is odd
Introduction to Self-Stabilization Maria Potop-Butucaru, Franck Petit and Sébastien Tixeuil LiP6/UPMC Self-stabilization 101 Example U 0 = a U n+1 = U n 2 if U n is even U n+1 = 3U n+1 2 if U n is odd
Directed Topology and Concurrency Theory.
 Directed Topology and Concurrency Theory. Lisbeth Fajstrup Department of Mathematics alborg University Denmark Sapporo 2017 Directed Topology/Concurrency Take home message: Models of concurrency geometry/topology
Directed Topology and Concurrency Theory. Lisbeth Fajstrup Department of Mathematics alborg University Denmark Sapporo 2017 Directed Topology/Concurrency Take home message: Models of concurrency geometry/topology
Algorithmic verification
 Algorithmic verification Ahmed Rezine IDA, Linköpings Universitet Hösttermin 2018 Outline Overview Model checking Symbolic execution Outline Overview Model checking Symbolic execution Program verification
Algorithmic verification Ahmed Rezine IDA, Linköpings Universitet Hösttermin 2018 Outline Overview Model checking Symbolic execution Outline Overview Model checking Symbolic execution Program verification
Lecture 16: Computation Tree Logic (CTL)
 Lecture 16: Computation Tree Logic (CTL) 1 Programme for the upcoming lectures Introducing CTL Basic Algorithms for CTL CTL and Fairness; computing strongly connected components Basic Decision Diagrams
Lecture 16: Computation Tree Logic (CTL) 1 Programme for the upcoming lectures Introducing CTL Basic Algorithms for CTL CTL and Fairness; computing strongly connected components Basic Decision Diagrams
Deadlock. CSE 2431: Introduction to Operating Systems Reading: Chap. 7, [OSC]
![Deadlock. CSE 2431: Introduction to Operating Systems Reading: Chap. 7, [OSC] Deadlock. CSE 2431: Introduction to Operating Systems Reading: Chap. 7, [OSC]](/thumbs/80/80503727.jpg) Deadlock CSE 2431: Introduction to Operating Systems Reading: Chap. 7, [OSC] 1 Outline Resources Deadlock Deadlock Prevention Deadlock Avoidance Deadlock Detection Deadlock Recovery 2 Review: Synchronization
Deadlock CSE 2431: Introduction to Operating Systems Reading: Chap. 7, [OSC] 1 Outline Resources Deadlock Deadlock Prevention Deadlock Avoidance Deadlock Detection Deadlock Recovery 2 Review: Synchronization
The Weakest Failure Detector for Wait-Free Dining under Eventual Weak Exclusion
 The Weakest Failure Detector for Wait-Free Dining under Eventual Weak Exclusion Srikanth Sastry Computer Science and Engr Texas A&M University College Station, TX, USA sastry@cse.tamu.edu Scott M. Pike
The Weakest Failure Detector for Wait-Free Dining under Eventual Weak Exclusion Srikanth Sastry Computer Science and Engr Texas A&M University College Station, TX, USA sastry@cse.tamu.edu Scott M. Pike
CS162 Operating Systems and Systems Programming Lecture 7 Semaphores, Conditional Variables, Deadlocks"
 CS162 Operating Systems and Systems Programming Lecture 7 Semaphores, Conditional Variables, Deadlocks" September 19, 2012! Ion Stoica! http://inst.eecs.berkeley.edu/~cs162! Recap: Monitors" Monitors represent
CS162 Operating Systems and Systems Programming Lecture 7 Semaphores, Conditional Variables, Deadlocks" September 19, 2012! Ion Stoica! http://inst.eecs.berkeley.edu/~cs162! Recap: Monitors" Monitors represent
Petri Nets and Model Checking. Natasa Gkolfi. University of Oslo. March 31, 2017
 University of Oslo March 31, 2017 Petri Nets Petri Nets : mathematically founded formalism concurrency synchronization modeling distributed systems Petri Nets Petri Nets : mathematically founded formalism
University of Oslo March 31, 2017 Petri Nets Petri Nets : mathematically founded formalism concurrency synchronization modeling distributed systems Petri Nets Petri Nets : mathematically founded formalism
GAMES: MIXED STRATEGIES
 Prerequisites Almost essential Game Theory: Strategy and Equilibrium GAMES: MIXED STRATEGIES MICROECONOMICS Principles and Analysis Frank Cowell April 2018 Frank Cowell: Mixed Strategy Games 1 Introduction
Prerequisites Almost essential Game Theory: Strategy and Equilibrium GAMES: MIXED STRATEGIES MICROECONOMICS Principles and Analysis Frank Cowell April 2018 Frank Cowell: Mixed Strategy Games 1 Introduction
CS 453 Operating Systems. Lecture 7 : Deadlock
 CS 453 Operating Systems Lecture 7 : Deadlock 1 What is Deadlock? Every New Yorker knows what a gridlock alert is - it s one of those days when there is so much traffic that nobody can move. Everything
CS 453 Operating Systems Lecture 7 : Deadlock 1 What is Deadlock? Every New Yorker knows what a gridlock alert is - it s one of those days when there is so much traffic that nobody can move. Everything
Embedded Systems 6 REVIEW. Place/transition nets. defaults: K = ω W = 1
 Embedded Systems 6-1 - Place/transition nets REVIEW Def.: (P, T, F, K, W, M 0 ) is called a place/transition net (P/T net) iff 1. N=(P,T,F) is a net with places p P and transitions t T 2. K: P (N 0 {ω})
Embedded Systems 6-1 - Place/transition nets REVIEW Def.: (P, T, F, K, W, M 0 ) is called a place/transition net (P/T net) iff 1. N=(P,T,F) is a net with places p P and transitions t T 2. K: P (N 0 {ω})
Foundations of Cryptography
 - 111 - Foundations of Cryptography Notes of lecture No. 10B & 11 (given on June 11 & 18, 1989) taken by Sergio Rajsbaum Summary In this lecture we define unforgeable digital signatures and present such
- 111 - Foundations of Cryptography Notes of lecture No. 10B & 11 (given on June 11 & 18, 1989) taken by Sergio Rajsbaum Summary In this lecture we define unforgeable digital signatures and present such
CS505: Distributed Systems
 Department of Computer Science CS505: Distributed Systems Lecture 10: Consensus Outline Consensus impossibility result Consensus with S Consensus with Ω Consensus Most famous problem in distributed computing
Department of Computer Science CS505: Distributed Systems Lecture 10: Consensus Outline Consensus impossibility result Consensus with S Consensus with Ω Consensus Most famous problem in distributed computing
Communicating Parallel Processes. Stephen Brookes
 Communicating Parallel Processes Stephen Brookes Carnegie Mellon University Deconstructing CSP 1 CSP sequential processes input and output as primitives named parallel composition synchronized communication
Communicating Parallel Processes Stephen Brookes Carnegie Mellon University Deconstructing CSP 1 CSP sequential processes input and output as primitives named parallel composition synchronized communication
The Weakest Failure Detector to Solve Mutual Exclusion
 The Weakest Failure Detector to Solve Mutual Exclusion Vibhor Bhatt Nicholas Christman Prasad Jayanti Dartmouth College, Hanover, NH Dartmouth Computer Science Technical Report TR2008-618 April 17, 2008
The Weakest Failure Detector to Solve Mutual Exclusion Vibhor Bhatt Nicholas Christman Prasad Jayanti Dartmouth College, Hanover, NH Dartmouth Computer Science Technical Report TR2008-618 April 17, 2008
MPRI Course on Concurrency. Lecture 14. Application of probabilistic process calculi to security
 MPRI Course on Concurrency Lecture 14 Application of probabilistic process calculi to security Catuscia Palamidessi LIX, Ecole Polytechnique kostas@lix.polytechnique.fr www.lix.polytechnique.fr/~catuscia
MPRI Course on Concurrency Lecture 14 Application of probabilistic process calculi to security Catuscia Palamidessi LIX, Ecole Polytechnique kostas@lix.polytechnique.fr www.lix.polytechnique.fr/~catuscia
Further discussion of Turing machines
 Further discussion of Turing machines In this lecture we will discuss various aspects of decidable and Turing-recognizable languages that were not mentioned in previous lectures. In particular, we will
Further discussion of Turing machines In this lecture we will discuss various aspects of decidable and Turing-recognizable languages that were not mentioned in previous lectures. In particular, we will
Wait-Free Dining Under Eventual Weak Exclusion
 Wait-Free Dining Under Eventual Weak Exclusion Scott M. Pike, Yantao Song, and Srikanth Sastry Texas A&M University Department of Computer Science College Station, TX 77843-3112, USA {pike,yantao,sastry}@cs.tamu.edu
Wait-Free Dining Under Eventual Weak Exclusion Scott M. Pike, Yantao Song, and Srikanth Sastry Texas A&M University Department of Computer Science College Station, TX 77843-3112, USA {pike,yantao,sastry}@cs.tamu.edu
Petri nets. s 1 s 2. s 3 s 4. directed arcs.
 Petri nets Petri nets Petri nets are a basic model of parallel and distributed systems (named after Carl Adam Petri). The basic idea is to describe state changes in a system with transitions. @ @R s 1
Petri nets Petri nets Petri nets are a basic model of parallel and distributed systems (named after Carl Adam Petri). The basic idea is to describe state changes in a system with transitions. @ @R s 1
Valency Arguments CHAPTER7
 CHAPTER7 Valency Arguments In a valency argument, configurations are classified as either univalent or multivalent. Starting from a univalent configuration, all terminating executions (from some class)
CHAPTER7 Valency Arguments In a valency argument, configurations are classified as either univalent or multivalent. Starting from a univalent configuration, all terminating executions (from some class)
Implementing Uniform Reliable Broadcast with Binary Consensus in Systems with Fair-Lossy Links
 Implementing Uniform Reliable Broadcast with Binary Consensus in Systems with Fair-Lossy Links Jialin Zhang Tsinghua University zhanggl02@mails.tsinghua.edu.cn Wei Chen Microsoft Research Asia weic@microsoft.com
Implementing Uniform Reliable Broadcast with Binary Consensus in Systems with Fair-Lossy Links Jialin Zhang Tsinghua University zhanggl02@mails.tsinghua.edu.cn Wei Chen Microsoft Research Asia weic@microsoft.com
March 19 - Solving Linear Systems
 March 19 - Solving Linear Systems Welcome to linear algebra! Linear algebra is the study of vectors, vector spaces, and maps between vector spaces. It has applications across data analysis, computer graphics,
March 19 - Solving Linear Systems Welcome to linear algebra! Linear algebra is the study of vectors, vector spaces, and maps between vector spaces. It has applications across data analysis, computer graphics,
Design of Distributed Systems Melinda Tóth, Zoltán Horváth
 Design of Distributed Systems Melinda Tóth, Zoltán Horváth Design of Distributed Systems Melinda Tóth, Zoltán Horváth Publication date 2014 Copyright 2014 Melinda Tóth, Zoltán Horváth Supported by TÁMOP-412A/1-11/1-2011-0052
Design of Distributed Systems Melinda Tóth, Zoltán Horváth Design of Distributed Systems Melinda Tóth, Zoltán Horváth Publication date 2014 Copyright 2014 Melinda Tóth, Zoltán Horváth Supported by TÁMOP-412A/1-11/1-2011-0052
Livelock example. p 1. Assume this as initial marking. t 1 R. t 2. t 4. t 3. t 6. t 5. t 7. t 8. (taken from Fundamentals of SE by C.
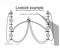 p 1 Livelock example (taken from Fundamentals of SE by C. Ghezzi) p 1 Assume this as initial marking. t 1 R t 3 t 4 t 5 t 6 t 7 t 8 Slide No.106 Livelock example analysis The tokens in R cannot be divided
p 1 Livelock example (taken from Fundamentals of SE by C. Ghezzi) p 1 Assume this as initial marking. t 1 R t 3 t 4 t 5 t 6 t 7 t 8 Slide No.106 Livelock example analysis The tokens in R cannot be divided
Unary negation: T F F T
 Unary negation: ϕ 1 ϕ 1 T F F T Binary (inclusive) or: ϕ 1 ϕ 2 (ϕ 1 ϕ 2 ) T T T T F T F T T F F F Binary (exclusive) or: ϕ 1 ϕ 2 (ϕ 1 ϕ 2 ) T T F T F T F T T F F F Classical (material) conditional: ϕ 1
Unary negation: ϕ 1 ϕ 1 T F F T Binary (inclusive) or: ϕ 1 ϕ 2 (ϕ 1 ϕ 2 ) T T T T F T F T T F F F Binary (exclusive) or: ϕ 1 ϕ 2 (ϕ 1 ϕ 2 ) T T F T F T F T T F F F Classical (material) conditional: ϕ 1
Stéphane Lafortune. August 2006
 UNIVERSITY OF MICHIGAN DEPARTMENT OF ELECTRICAL ENGINEERING AND COMPUTER SCIENCE LECTURE NOTES FOR EECS 661 CHAPTER 1: INTRODUCTION TO DISCRETE EVENT SYSTEMS Stéphane Lafortune August 2006 References for
UNIVERSITY OF MICHIGAN DEPARTMENT OF ELECTRICAL ENGINEERING AND COMPUTER SCIENCE LECTURE NOTES FOR EECS 661 CHAPTER 1: INTRODUCTION TO DISCRETE EVENT SYSTEMS Stéphane Lafortune August 2006 References for
Dealing with Uncertainty. CS 331: Artificial Intelligence Probability I. Outline. Random Variables. Random Variables.
 Dealing with Uncertainty CS 331: Artificial Intelligence Probability I We want to get to the point where we can reason with uncertainty This will require using probability e.g. probability that it will
Dealing with Uncertainty CS 331: Artificial Intelligence Probability I We want to get to the point where we can reason with uncertainty This will require using probability e.g. probability that it will
Design and Analysis of Distributed Interacting Systems
 Design and Analysis of Distributed Interacting Systems Organization Prof. Dr. Joel Greenyer April 11, 2013 Organization Lecture: Thursdays, 10:15 11:45, F 128 Tutorial: Thursdays, 13:00 13:45, G 323 first
Design and Analysis of Distributed Interacting Systems Organization Prof. Dr. Joel Greenyer April 11, 2013 Organization Lecture: Thursdays, 10:15 11:45, F 128 Tutorial: Thursdays, 13:00 13:45, G 323 first
Recognizing Safety and Liveness by Alpern and Schneider
 Recognizing Safety and Liveness by Alpern and Schneider Calvin Deutschbein 17 Jan 2017 1 Intro 1.1 Safety What is safety? Bad things do not happen For example, consider the following safe program in C:
Recognizing Safety and Liveness by Alpern and Schneider Calvin Deutschbein 17 Jan 2017 1 Intro 1.1 Safety What is safety? Bad things do not happen For example, consider the following safe program in C:
Chapter 13: Model Checking Linear-Time Properties of Probabilistic Systems
 Chapter 13: Model Checking Linear-Time Properties of Probabilistic Systems Christel Baier, Marcus Größer, and Frank Ciesinski Technische Universität Dresden, Fakultät Informatik, Institut für Theoretische
Chapter 13: Model Checking Linear-Time Properties of Probabilistic Systems Christel Baier, Marcus Größer, and Frank Ciesinski Technische Universität Dresden, Fakultät Informatik, Institut für Theoretische
Mathematical Logic Prof. Arindama Singh Department of Mathematics Indian Institute of Technology, Madras. Lecture - 15 Propositional Calculus (PC)
 Mathematical Logic Prof. Arindama Singh Department of Mathematics Indian Institute of Technology, Madras Lecture - 15 Propositional Calculus (PC) So, now if you look back, you can see that there are three
Mathematical Logic Prof. Arindama Singh Department of Mathematics Indian Institute of Technology, Madras Lecture - 15 Propositional Calculus (PC) So, now if you look back, you can see that there are three
Impossibility of Distributed Consensus with One Faulty Process
 Impossibility of Distributed Consensus with One Faulty Process Journal of the ACM 32(2):374-382, April 1985. MJ Fischer, NA Lynch, MS Peterson. Won the 2002 Dijkstra Award (for influential paper in distributed
Impossibility of Distributed Consensus with One Faulty Process Journal of the ACM 32(2):374-382, April 1985. MJ Fischer, NA Lynch, MS Peterson. Won the 2002 Dijkstra Award (for influential paper in distributed
Chapter Learning Objectives. Random Experiments Dfiii Definition: Dfiii Definition:
 Chapter 2: Probability 2-1 Sample Spaces & Events 2-1.1 Random Experiments 2-1.2 Sample Spaces 2-1.3 Events 2-1 1.4 Counting Techniques 2-2 Interpretations & Axioms of Probability 2-3 Addition Rules 2-4
Chapter 2: Probability 2-1 Sample Spaces & Events 2-1.1 Random Experiments 2-1.2 Sample Spaces 2-1.3 Events 2-1 1.4 Counting Techniques 2-2 Interpretations & Axioms of Probability 2-3 Addition Rules 2-4
AGREEMENT PROBLEMS (1) Agreement problems arise in many practical applications:
 AGREEMENT PROBLEMS (1) AGREEMENT PROBLEMS Agreement problems arise in many practical applications: agreement on whether to commit or abort the results of a distributed atomic action (e.g. database transaction)
AGREEMENT PROBLEMS (1) AGREEMENT PROBLEMS Agreement problems arise in many practical applications: agreement on whether to commit or abort the results of a distributed atomic action (e.g. database transaction)
Foundations of
 91.304 Foundations of (Theoretical) Computer Science Chapter 3 Lecture Notes (Section 3.2: Variants of Turing Machines) David Martin dm@cs.uml.edu With some modifications by Prof. Karen Daniels, Fall 2012
91.304 Foundations of (Theoretical) Computer Science Chapter 3 Lecture Notes (Section 3.2: Variants of Turing Machines) David Martin dm@cs.uml.edu With some modifications by Prof. Karen Daniels, Fall 2012
Round-Efficient Multi-party Computation with a Dishonest Majority
 Round-Efficient Multi-party Computation with a Dishonest Majority Jonathan Katz, U. Maryland Rafail Ostrovsky, Telcordia Adam Smith, MIT Longer version on http://theory.lcs.mit.edu/~asmith 1 Multi-party
Round-Efficient Multi-party Computation with a Dishonest Majority Jonathan Katz, U. Maryland Rafail Ostrovsky, Telcordia Adam Smith, MIT Longer version on http://theory.lcs.mit.edu/~asmith 1 Multi-party
Coordination. Failures and Consensus. Consensus. Consensus. Overview. Properties for Correct Consensus. Variant I: Consensus (C) P 1. v 1.
 Coordination Failures and Consensus If the solution to availability and scalability is to decentralize and replicate functions and data, how do we coordinate the nodes? data consistency update propagation
Coordination Failures and Consensus If the solution to availability and scalability is to decentralize and replicate functions and data, how do we coordinate the nodes? data consistency update propagation
Impagliazzo s Hardcore Lemma
 Average Case Complexity February 8, 011 Impagliazzo s Hardcore Lemma ofessor: Valentine Kabanets Scribe: Hoda Akbari 1 Average-Case Hard Boolean Functions w.r.t. Circuits In this lecture, we are going
Average Case Complexity February 8, 011 Impagliazzo s Hardcore Lemma ofessor: Valentine Kabanets Scribe: Hoda Akbari 1 Average-Case Hard Boolean Functions w.r.t. Circuits In this lecture, we are going
Lecture Examples of problems which have randomized algorithms
 6.841 Advanced Complexity Theory March 9, 2009 Lecture 10 Lecturer: Madhu Sudan Scribe: Asilata Bapat Meeting to talk about final projects on Wednesday, 11 March 2009, from 5pm to 7pm. Location: TBA. Includes
6.841 Advanced Complexity Theory March 9, 2009 Lecture 10 Lecturer: Madhu Sudan Scribe: Asilata Bapat Meeting to talk about final projects on Wednesday, 11 March 2009, from 5pm to 7pm. Location: TBA. Includes
What languages are Turing-decidable? What languages are not Turing-decidable? Is there a language that isn t even Turingrecognizable?
 } We ll now take a look at Turing Machines at a high level and consider what types of problems can be solved algorithmically and what types can t: What languages are Turing-decidable? What languages are
} We ll now take a look at Turing Machines at a high level and consider what types of problems can be solved algorithmically and what types can t: What languages are Turing-decidable? What languages are
Distributed Computing in Shared Memory and Networks
 Distributed Computing in Shared Memory and Networks Class 2: Consensus WEP 2018 KAUST This class Reaching agreement in shared memory: Consensus ü Impossibility of wait-free consensus 1-resilient consensus
Distributed Computing in Shared Memory and Networks Class 2: Consensus WEP 2018 KAUST This class Reaching agreement in shared memory: Consensus ü Impossibility of wait-free consensus 1-resilient consensus
Section 6 Fault-Tolerant Consensus
 Section 6 Fault-Tolerant Consensus CS586 - Panagiota Fatourou 1 Description of the Problem Consensus Each process starts with an individual input from a particular value set V. Processes may fail by crashing.
Section 6 Fault-Tolerant Consensus CS586 - Panagiota Fatourou 1 Description of the Problem Consensus Each process starts with an individual input from a particular value set V. Processes may fail by crashing.
The Decent Philosophers: An exercise in concurrent behaviour
 Fundamenta Informaticae 80 (2007) 1 9 1 IOS Press The Decent Philosophers: An exercise in concurrent behaviour Wolfgang Reisig Humboldt-Universität zu Berlin Institute of Informatics Unter den Linden 6,
Fundamenta Informaticae 80 (2007) 1 9 1 IOS Press The Decent Philosophers: An exercise in concurrent behaviour Wolfgang Reisig Humboldt-Universität zu Berlin Institute of Informatics Unter den Linden 6,
Lecture # 12. Agenda: I. Vector Program Relaxation for Max Cut problem. Consider the vectors are in a sphere. Lecturer: Prof.
 Lecture # 12 Lecturer: Prof. Allan Borodin Scribe: Yeleiny Bonilla Agenda: I. Finish discussion of Vector Program Relaxation for Max-Cut problem. II. Briefly discuss same approach for Max-2-Sat. III. The
Lecture # 12 Lecturer: Prof. Allan Borodin Scribe: Yeleiny Bonilla Agenda: I. Finish discussion of Vector Program Relaxation for Max-Cut problem. II. Briefly discuss same approach for Max-2-Sat. III. The
Decidability and Undecidability
 Decidability and Undecidability Major Ideas from Last Time Every TM can be converted into a string representation of itself. The encoding of M is denoted M. The universal Turing machine U TM accepts an
Decidability and Undecidability Major Ideas from Last Time Every TM can be converted into a string representation of itself. The encoding of M is denoted M. The universal Turing machine U TM accepts an
Introduction to mcrl2
 Introduction to mcrl2 Luís S. Barbosa DI-CCTC Universidade do Minho Braga, Portugal May, 2011 mcrl2: A toolset for process algebra mcrl2 provides: a generic process algebra, based on Acp (Bergstra & Klop,
Introduction to mcrl2 Luís S. Barbosa DI-CCTC Universidade do Minho Braga, Portugal May, 2011 mcrl2: A toolset for process algebra mcrl2 provides: a generic process algebra, based on Acp (Bergstra & Klop,
Temporal logics and model checking for fairly correct systems
 Temporal logics and model checking for fairly correct systems Hagen Völzer 1 joint work with Daniele Varacca 2 1 Lübeck University, Germany 2 Imperial College London, UK LICS 2006 Introduction Five Philosophers
Temporal logics and model checking for fairly correct systems Hagen Völzer 1 joint work with Daniele Varacca 2 1 Lübeck University, Germany 2 Imperial College London, UK LICS 2006 Introduction Five Philosophers
A Brief Introduction to Model Checking
 A Brief Introduction to Model Checking Jan. 18, LIX Page 1 Model Checking A technique for verifying finite state concurrent systems; a benefit on this restriction: largely automatic; a problem to fight:
A Brief Introduction to Model Checking Jan. 18, LIX Page 1 Model Checking A technique for verifying finite state concurrent systems; a benefit on this restriction: largely automatic; a problem to fight:
General Terms: Algorithms, Theory, Verification Additional Key Words and Phrases: Program analysis, Markov chains, ergodic sets
 Termination of Probabilistic Programs Concurrent SERGlU HART and MICHA SHARIR Tel Aviv University and AMIR PNUELI The Weizrnann Institute of Science The asynchronous execution behavior of several concurrent
Termination of Probabilistic Programs Concurrent SERGlU HART and MICHA SHARIR Tel Aviv University and AMIR PNUELI The Weizrnann Institute of Science The asynchronous execution behavior of several concurrent
Weighted Majority and the Online Learning Approach
 Statistical Techniques in Robotics (16-81, F12) Lecture#9 (Wednesday September 26) Weighted Majority and the Online Learning Approach Lecturer: Drew Bagnell Scribe:Narek Melik-Barkhudarov 1 Figure 1: Drew
Statistical Techniques in Robotics (16-81, F12) Lecture#9 (Wednesday September 26) Weighted Majority and the Online Learning Approach Lecturer: Drew Bagnell Scribe:Narek Melik-Barkhudarov 1 Figure 1: Drew
ROBUST & SPECULATIVE BYZANTINE RANDOMIZED CONSENSUS WITH CONSTANT TIME COMPLEXITY IN NORMAL CONDITIONS
 ROBUST & SPECULATIVE BYZANTINE RANDOMIZED CONSENSUS WITH CONSTANT TIME COMPLEXITY IN NORMAL CONDITIONS Bruno Vavala University of Lisbon, Portugal Carnegie Mellon University, U.S. Nuno Neves University
ROBUST & SPECULATIVE BYZANTINE RANDOMIZED CONSENSUS WITH CONSTANT TIME COMPLEXITY IN NORMAL CONDITIONS Bruno Vavala University of Lisbon, Portugal Carnegie Mellon University, U.S. Nuno Neves University
Communication and Concurrency: CCS
 Communication and Concurrency: CCS R. Milner, A Calculus of Communicating Systems, 1980 cours SSDE Master 1 Why calculi? Prove properties on programs and languages Principle: tiny syntax, small semantics,
Communication and Concurrency: CCS R. Milner, A Calculus of Communicating Systems, 1980 cours SSDE Master 1 Why calculi? Prove properties on programs and languages Principle: tiny syntax, small semantics,
Solving ANTS with Loneliness Detection and Constant Memory. Casey O Brien
 Solving ANTS with Loneliness Detection and Constant Memory by Casey O Brien B.S., Computer Science, B.S., Mathematics Massachusetts Institute of Technology (2014) Submitted to the Department of Electrical
Solving ANTS with Loneliness Detection and Constant Memory by Casey O Brien B.S., Computer Science, B.S., Mathematics Massachusetts Institute of Technology (2014) Submitted to the Department of Electrical
Lecture 8: Probability
 Lecture 8: Probability The idea of probability is well-known The flipping of a balanced coin can produce one of two outcomes: T (tail) and H (head) and the symmetry between the two outcomes means, of course,
Lecture 8: Probability The idea of probability is well-known The flipping of a balanced coin can produce one of two outcomes: T (tail) and H (head) and the symmetry between the two outcomes means, of course,
Decentralized Control of Discrete Event Systems with Bounded or Unbounded Delay Communication
 Decentralized Control of Discrete Event Systems with Bounded or Unbounded Delay Communication Stavros Tripakis Abstract We introduce problems of decentralized control with communication, where we explicitly
Decentralized Control of Discrete Event Systems with Bounded or Unbounded Delay Communication Stavros Tripakis Abstract We introduce problems of decentralized control with communication, where we explicitly
Last class: Today: Synchronization. Deadlocks
 Last class: Synchronization Today: Deadlocks Definition A set of processes is deadlocked if each process in the set is waiting for an event that only another process in the set can cause. An event could
Last class: Synchronization Today: Deadlocks Definition A set of processes is deadlocked if each process in the set is waiting for an event that only another process in the set can cause. An event could
Section 1.6. Functions
 Section 1.6 Functions Definitions Relation, Domain, Range, and Function The table describes a relationship between the variables x and y. This relationship is also described graphically. x y 3 2 4 1 5
Section 1.6 Functions Definitions Relation, Domain, Range, and Function The table describes a relationship between the variables x and y. This relationship is also described graphically. x y 3 2 4 1 5
A Self-Stabilizing Algorithm for Finding a Minimal Distance-2 Dominating Set in Distributed Systems
 JOURNAL OF INFORMATION SCIENCE AND ENGINEERING 24, 1709-1718 (2008) A Self-Stabilizing Algorithm for Finding a Minimal Distance-2 Dominating Set in Distributed Systems JI-CHERNG LIN, TETZ C. HUANG, CHENG-PIN
JOURNAL OF INFORMATION SCIENCE AND ENGINEERING 24, 1709-1718 (2008) A Self-Stabilizing Algorithm for Finding a Minimal Distance-2 Dominating Set in Distributed Systems JI-CHERNG LIN, TETZ C. HUANG, CHENG-PIN
1 Introduction. 1.1 The Problem Domain. Self-Stablization UC Davis Earl Barr. Lecture 1 Introduction Winter 2007
 Lecture 1 Introduction 1 Introduction 1.1 The Problem Domain Today, we are going to ask whether a system can recover from perturbation. Consider a children s top: If it is perfectly vertically, you can
Lecture 1 Introduction 1 Introduction 1.1 The Problem Domain Today, we are going to ask whether a system can recover from perturbation. Consider a children s top: If it is perfectly vertically, you can
CPSC 536N: Randomized Algorithms Term 2. Lecture 9
 CPSC 536N: Randomized Algorithms 2011-12 Term 2 Prof. Nick Harvey Lecture 9 University of British Columbia 1 Polynomial Identity Testing In the first lecture we discussed the problem of testing equality
CPSC 536N: Randomized Algorithms 2011-12 Term 2 Prof. Nick Harvey Lecture 9 University of British Columbia 1 Polynomial Identity Testing In the first lecture we discussed the problem of testing equality
Randomized Algorithms
 Randomized Algorithms Prof. Tapio Elomaa tapio.elomaa@tut.fi Course Basics A new 4 credit unit course Part of Theoretical Computer Science courses at the Department of Mathematics There will be 4 hours
Randomized Algorithms Prof. Tapio Elomaa tapio.elomaa@tut.fi Course Basics A new 4 credit unit course Part of Theoretical Computer Science courses at the Department of Mathematics There will be 4 hours
Review of Basic Probability Theory
 Review of Basic Probability Theory James H. Steiger Department of Psychology and Human Development Vanderbilt University James H. Steiger (Vanderbilt University) 1 / 35 Review of Basic Probability Theory
Review of Basic Probability Theory James H. Steiger Department of Psychology and Human Development Vanderbilt University James H. Steiger (Vanderbilt University) 1 / 35 Review of Basic Probability Theory
Notes on induction proofs and recursive definitions
 Notes on induction proofs and recursive definitions James Aspnes December 13, 2010 1 Simple induction Most of the proof techniques we ve talked about so far are only really useful for proving a property
Notes on induction proofs and recursive definitions James Aspnes December 13, 2010 1 Simple induction Most of the proof techniques we ve talked about so far are only really useful for proving a property
Atomic m-register operations
 Atomic m-register operations Michael Merritt Gadi Taubenfeld December 15, 1993 Abstract We investigate systems where it is possible to access several shared registers in one atomic step. We characterize
Atomic m-register operations Michael Merritt Gadi Taubenfeld December 15, 1993 Abstract We investigate systems where it is possible to access several shared registers in one atomic step. We characterize
Introduction to Algorithms / Algorithms I Lecturer: Michael Dinitz Topic: Intro to Learning Theory Date: 12/8/16
 600.463 Introduction to Algorithms / Algorithms I Lecturer: Michael Dinitz Topic: Intro to Learning Theory Date: 12/8/16 25.1 Introduction Today we re going to talk about machine learning, but from an
600.463 Introduction to Algorithms / Algorithms I Lecturer: Michael Dinitz Topic: Intro to Learning Theory Date: 12/8/16 25.1 Introduction Today we re going to talk about machine learning, but from an
Stabilizing Dining with Failure Locality 1
 Stabilizing Dining with Failure Locality 1 Hyun Chul Chung 1,, Srikanth Sastry 2,, and Jennifer L. Welch 1, 1 Texas A&M University, Department of Computer Science & Engineering {h0c8412,welch}@cse.tamu.edu
Stabilizing Dining with Failure Locality 1 Hyun Chul Chung 1,, Srikanth Sastry 2,, and Jennifer L. Welch 1, 1 Texas A&M University, Department of Computer Science & Engineering {h0c8412,welch}@cse.tamu.edu
CS 331: Artificial Intelligence Probability I. Dealing with Uncertainty
 CS 331: Artificial Intelligence Probability I Thanks to Andrew Moore for some course material 1 Dealing with Uncertainty We want to get to the point where we can reason with uncertainty This will require
CS 331: Artificial Intelligence Probability I Thanks to Andrew Moore for some course material 1 Dealing with Uncertainty We want to get to the point where we can reason with uncertainty This will require
Automata-Theoretic Model Checking of Reactive Systems
 Automata-Theoretic Model Checking of Reactive Systems Radu Iosif Verimag/CNRS (Grenoble, France) Thanks to Tom Henzinger (IST, Austria), Barbara Jobstmann (CNRS, Grenoble) and Doron Peled (Bar-Ilan University,
Automata-Theoretic Model Checking of Reactive Systems Radu Iosif Verimag/CNRS (Grenoble, France) Thanks to Tom Henzinger (IST, Austria), Barbara Jobstmann (CNRS, Grenoble) and Doron Peled (Bar-Ilan University,
The Mutual Visibility Problem for Oblivious Robots
 CCCG 201, Halifax, Nova Scotia, August 11 13, 201 The Mutual Visibility Problem for Oblivious Robots Giuseppe Antonio Di Luna Paola Flocchini Federico Poloni Nicola Santoro Giovanni Viglietta Abstract
CCCG 201, Halifax, Nova Scotia, August 11 13, 201 The Mutual Visibility Problem for Oblivious Robots Giuseppe Antonio Di Luna Paola Flocchini Federico Poloni Nicola Santoro Giovanni Viglietta Abstract
carroll/notes/ has a lot of good notes on GR and links to other pages. General Relativity Philosophy of general
 http://pancake.uchicago.edu/ carroll/notes/ has a lot of good notes on GR and links to other pages. General Relativity Philosophy of general relativity. As with any major theory in physics, GR has been
http://pancake.uchicago.edu/ carroll/notes/ has a lot of good notes on GR and links to other pages. General Relativity Philosophy of general relativity. As with any major theory in physics, GR has been
Probability and Independence Terri Bittner, Ph.D.
 Probability and Independence Terri Bittner, Ph.D. The concept of independence is often confusing for students. This brief paper will cover the basics, and will explain the difference between independent
Probability and Independence Terri Bittner, Ph.D. The concept of independence is often confusing for students. This brief paper will cover the basics, and will explain the difference between independent
EDF Scheduling. Giuseppe Lipari May 11, Scuola Superiore Sant Anna Pisa
 EDF Scheduling Giuseppe Lipari http://feanor.sssup.it/~lipari Scuola Superiore Sant Anna Pisa May 11, 2008 Outline 1 Dynamic priority 2 Basic analysis 3 FP vs EDF 4 Processor demand bound analysis Generalization
EDF Scheduling Giuseppe Lipari http://feanor.sssup.it/~lipari Scuola Superiore Sant Anna Pisa May 11, 2008 Outline 1 Dynamic priority 2 Basic analysis 3 FP vs EDF 4 Processor demand bound analysis Generalization
Fall Math 140 Week-in-Review #5 courtesy: Kendra Kilmer (covering Sections 3.4 and 4.1) Section 3.4
 Section 3.4 A Standard Maximization Problem has the following properties: The objective function is to be maximized. All variables are non-negative. Fall 2017 Math 140 Week-in-Review #5 courtesy: Kendra
Section 3.4 A Standard Maximization Problem has the following properties: The objective function is to be maximized. All variables are non-negative. Fall 2017 Math 140 Week-in-Review #5 courtesy: Kendra
Lecture 9 - Symmetric Encryption
 0368.4162: Introduction to Cryptography Ran Canetti Lecture 9 - Symmetric Encryption 29 December 2008 Fall 2008 Scribes: R. Levi, M. Rosen 1 Introduction Encryption, or guaranteeing secrecy of information,
0368.4162: Introduction to Cryptography Ran Canetti Lecture 9 - Symmetric Encryption 29 December 2008 Fall 2008 Scribes: R. Levi, M. Rosen 1 Introduction Encryption, or guaranteeing secrecy of information,
Game Theory Lecture 10+11: Knowledge
 Game Theory Lecture 10+11: Knowledge Christoph Schottmüller University of Copenhagen November 13 and 20, 2014 1 / 36 Outline 1 (Common) Knowledge The hat game A model of knowledge Common knowledge Agree
Game Theory Lecture 10+11: Knowledge Christoph Schottmüller University of Copenhagen November 13 and 20, 2014 1 / 36 Outline 1 (Common) Knowledge The hat game A model of knowledge Common knowledge Agree
(Refer Slide Time: )
 Digital Signal Processing Prof. S. C. Dutta Roy Department of Electrical Engineering Indian Institute of Technology, Delhi FIR Lattice Synthesis Lecture - 32 This is the 32nd lecture and our topic for
Digital Signal Processing Prof. S. C. Dutta Roy Department of Electrical Engineering Indian Institute of Technology, Delhi FIR Lattice Synthesis Lecture - 32 This is the 32nd lecture and our topic for
Agreement Protocols. CS60002: Distributed Systems. Pallab Dasgupta Dept. of Computer Sc. & Engg., Indian Institute of Technology Kharagpur
 Agreement Protocols CS60002: Distributed Systems Pallab Dasgupta Dept. of Computer Sc. & Engg., Indian Institute of Technology Kharagpur Classification of Faults Based on components that failed Program
Agreement Protocols CS60002: Distributed Systems Pallab Dasgupta Dept. of Computer Sc. & Engg., Indian Institute of Technology Kharagpur Classification of Faults Based on components that failed Program
Discrete Bee Dance Algorithms for Pattern Formation on a Grid
 Discrete Bee Dance Algorithms for Pattern Formation on a Grid Noam Gordon, Israel A. Wagner and Alfred M. Bruckstein Center for Intelligent Systems, CS Department Technion Israel Institute of Technology
Discrete Bee Dance Algorithms for Pattern Formation on a Grid Noam Gordon, Israel A. Wagner and Alfred M. Bruckstein Center for Intelligent Systems, CS Department Technion Israel Institute of Technology
A Weakest Failure Detector for Dining Philosophers with Eventually Bounded Waiting and Failure Locality 1
 A Weakest Failure Detector for Dining Philosophers with Eventually Bounded Waiting and Failure Locality 1 Hyun Chul Chung, Jennifer L. Welch Department of Computer Science & Engineering Texas A&M University
A Weakest Failure Detector for Dining Philosophers with Eventually Bounded Waiting and Failure Locality 1 Hyun Chul Chung, Jennifer L. Welch Department of Computer Science & Engineering Texas A&M University
CSCI3390-Lecture 6: An Undecidable Problem
 CSCI3390-Lecture 6: An Undecidable Problem September 21, 2018 1 Summary The language L T M recognized by the universal Turing machine is not decidable. Thus there is no algorithm that determines, yes or
CSCI3390-Lecture 6: An Undecidable Problem September 21, 2018 1 Summary The language L T M recognized by the universal Turing machine is not decidable. Thus there is no algorithm that determines, yes or
18.01 Single Variable Calculus Fall 2006
 MIT OpenCourseWare http://ocw.mit.edu 8.0 Single Variable Calculus Fall 2006 For information about citing these materials or our Terms of Use, visit: http://ocw.mit.edu/terms. Lecture 0 8.0 Fall 2006 Lecture
MIT OpenCourseWare http://ocw.mit.edu 8.0 Single Variable Calculus Fall 2006 For information about citing these materials or our Terms of Use, visit: http://ocw.mit.edu/terms. Lecture 0 8.0 Fall 2006 Lecture
Model Checking. Boris Feigin March 9, University College London
 b.feigin@cs.ucl.ac.uk University College London March 9, 2005 Outline 1 2 Techniques Symbolic 3 Software 4 Vs. Deductive Verification Summary Further Reading In a nutshell... Model checking is a collection
b.feigin@cs.ucl.ac.uk University College London March 9, 2005 Outline 1 2 Techniques Symbolic 3 Software 4 Vs. Deductive Verification Summary Further Reading In a nutshell... Model checking is a collection
Standing on the Shoulders of a Giant
 Standing on the Shoulders of a Giant One Person s Experience of Turing s Impact David Harel The Weizmann Institute of Science If I have seen further, it is because I stand on the shoulders of giants (Isaac
Standing on the Shoulders of a Giant One Person s Experience of Turing s Impact David Harel The Weizmann Institute of Science If I have seen further, it is because I stand on the shoulders of giants (Isaac
