Computing Maximum Likelihood Estimates in Log-Linear Models
|
|
|
- Tobias Banks
- 6 years ago
- Views:
Transcription
1 Computing Maximum Likelihood Estimates in Log-Linear Models Stephen E. Fienberg Center for Automated Learning and Discovery and Cylab Carnegie Mellon University Alessandro Rinaldo Department of Statistics Carnegie Mellon University Abstract We develop computational strategies for extended maximum likelihood estimation, as defined in Rinaldo (26), for general classes of log-linear models of widespred use, under Poisson and product-multinomial sampling schemes. We derive numerically efficient procedures for generating and manipulating design matrices and we propose various algorithms for computing the extended maximum likelihood estimates of the expectations of the cell counts. These algorithms allow to identify the set of estimable cell means for any given observable table and can be used for modifying traditional goodness-of-fit tests to accommodate for a nonexistent MLE. We describe and take advantage of the connections between extended maximum likelihood estimation in hierarchical log-linear models and graphical models. Contents 1 Introduction Notation Contingency Tables and Maximum Likelihood Estimation Sampling Schemes and Log-likelihood functions Poisson Sampling Scheme Product Multinomial Sampling Scheme Existence of the MLE Literature Review Recent Results fienberg@stat.cmu.edu arinaldo@stat.cmu.edu 1
2 3 Log-Linear Models Subspaces Combinatorial Derivation Matrix Algebra Derivation Bases for U h : Contrast Bases Bases for W h : Marginal Bases Group Theoretic Derivation Appendix Incorporating Sampling Constraints Generation of U h, W h and V h A Combinatorial Lemma Computing Extended Maximum Likelihood Estimates Determination of the Facial Sets Linear Programming Newton-Raphson Procedure Existence of the MLE and Markov Bases Maximizing the Log-Likelihood Function Poisson Sampling Scheme Product-Multinomial Sampling Scheme Efficient Algorithms to Compute `L, r`l and r 2`L Manipulation and Computations on Design Matrices A Basis for M N for the Product-Multinomial Case Detecting Rank Degeneracy Cholesky Decomposition with Pivoting Gaussian Elimination, Gauss-Jordan Elimination with Full Pivoting and Reduced Row Echelon Form LU Factorization Appendix A: Alternative Methods for Determining Facial Sets Maximum Entropy Approach Maximum Entropy and Newton-Raphson Facial Sets and Gale Transform Matroids and Graver Basis Appendix B: The Newton-Raphson Method Appendix C: Theorems of Alternatives Graph Theory and Extended Maximum Likelihood Estimation Reducible Models Decomposing Simplicial Complexes Decomposable Models The Iterative Proportional Fitting Algorithm IPF and Perfect Orderings Deciding the Decomposability of a Hypergraph Table Collapsing and the Extended MLE Testing for Goodness of Fit 73 2
3 7 Tables of Pseudo-Codes 78 1 Introduction Log-linear models are a powerful statistical tool for the analysis of categorical data and their use has increased greatly over the past two decades with the compilation and distribution of large, and very often sparse, data bases, in the social and medical sciences as well as in machine learning applications. The growing interest in analyzing massive, sparse databases has dramatically exposed a critical and, until very recently, unresolved issue with log-linear modeling: the possibility that the presence of sampling zeros compromises the feasibility and correctness of statistical inference. Sampling zeros, i.e. cells containing zero counts, arise as a consequence of the random nature of the sampling mechanism itself and occur frequently, but not exclusively, in tables with a relatively large number of cells compared to the sample size. Sampling zeros may be thought of as missing bits of information. When they occur in specific patterns inside the table, the maximum of the likelihood function occurs at the boundary of the parameter space where some subset of the expected values are also zero. In such cases, we say that the Maximum Likelihood Estimate (MLE) of the cell mean vector does not exist. The MLE of the expected value of the vector of observed counts plays a fundamental role for assessment of fit, model selection and interpretation. The existence of the MLE is essential for the usual derivation of large sample 2 approximations to numerous measures of goodness of fit (Bishop et al., 1975; Cressie and Read, 1988; Agresti, 22) which are used in testing and model selection. If the distribution of the goodness-of-fit statistic is instead derived from the exact distribution, i.e., the conditional distribution given the sufficient statistics, namely the margins, it is still necessary in most cases to have an MLE or some similar type of estimator in order to quantify the discrepancy of the the observed data from the fitted values. In addition, the existence of the MLE is essential to the derivation of the limiting distribution in the double-asymptotic approximations for the likelihood ratio and Pearson s 2 statistics for tables in which both the sample size and the number of cells are allowed to grow unbounded (Cressie and Read, 1988). If the MLE is not defined, the inferential procedures mentioned above may not be applicable or, at a minimum, require adjusting the degrees of freedom. The problem of nonexistence of the MLE has long been known to be related to the presence of zero cell counts in the observed table (see, in particular, Haberman, 1974; Bishop et al., 1975). Even if a zero entry in the margins is a sufficient condition for the nonexistence of the MLE, little has been known about other pathological cases of tables with positive margins but where the MLE still does not exist. The most famous, and until recently, the only published example of this kind is the 2 3 table and the model of no-second-order interaction described by Haberman (1974) (see Examples 2.7a) and 6.1 below). Although Haberman (1974) gave necessary and sufficient conditions for the existence of the MLE, his characterization is nonconstructive in the sense that it does not directly lead to implementable numerical procedures and also fails to suggest alternative methods of inference for the case of an undefined MLE. Despite these deficiencies, Haberman s results have not been improved or extended in the published statistical literature. Furthermore, to our knowledge, no numerical procedure specifically designed to check for existence of the MLE has been developed yet. As a result, the possibility of the nonexistence of the MLE, even though well known, is rarely a concern for practitioners and is largely ignored, so that results and decisions stemming from the statistical analysis of tables containing zero counts are based on a possibly 3
4 incorrect, faulty methodology. See the examples in Fienberg and Rinaldo (26) and Example 6.5 below. Identifying the cases in which the MLE is not defined has immediate practical implications and is crucial for modifying traditional procedures of model selection based on both asymptotic and exact approximations of test statistics and, more generally, for developing new inferential methodologies to deal with sparse tables. Recent advances in the field of algebraic statistics (Pistone et al., 2; Diaconis and Sturmfels, 1998; Pachter and Sturmfels, 25) have provided novel and broader mathematical tools for the analysis of categorical data. Their application has led to a series of theoretical results providing a complete, constructive characterization of the conditions for the existence of the MLE and proposing modifications to existing methods of inference for tables that do not have an MLE. These findings are contained in Eriksson et al. (26), Rinaldo (25) and Rinaldo (26) and include (1) combinatorial and geometric characterization of the all possible patterns of sampling zeros leading to non-existence of the MLE; (2) design of a LP-based polynomial time algorithm for detecting non-existence; (3) theoretical derivation of the extended MLE and of its properties. Arising as a natural extension of the MLE, the extended MLE exhibits, in fact, all the defining features of the MLE and allows to identify boundary log-linear models for modelling sparse data that are informative only for some parameters of interest but not for all. This document describes efficient and scalable computational strategies for extended maximum likelihood estimation, as described in Rinaldo (26). The material presented here is taken, for the most part, from (Rinaldo, 25, Chapter 6). We would like to acknowledge Stephen Fienberg, Mike Meyer and Pete Stewart for many of the results presented in Section 3.2 and 3.4 and for some of the pseudo codes of Section 7, which were derived from their unpublished work referenced as Fienberg et al. (198). This document is organized as follows. In Section 2 we give a technical background on maximum likelihood estimation for log-linear models for the Poisson and product-multinomial sampling schemes. Relevant results about existence of the MLE available in the statistical literature are reviewed and discussed. In particular, we summarize the most recent findings linking maximum likelihood estimation in log-linear models to extended exponential families and to polyhedral and algebraic geometry, contained in Rinaldo (26). In Section 3 we offer a combinatorial, linear algebra and group-theoretical representation of the class of log-linear subspaces we are concerned in this work as a direct sum of orthogonal subspaces. We devise various ways of generating and manipulating the corresponding design matrices, which are computationally efficient and particularly suited for large problems. In Section 4, we derive a variety of numerical procedures for computing the extended MLE. Part of the section is devoted to the identification of those cells whose mean values cannot be determined by maximizing the likelihood because of insufficient information in the data. We also describe optimization procedure for the log-likelihood functions that are computationally efficient and take advantage of the algorithms from Section 3. We explore the connections between extended MLE and graphical models in Section 5. In particular, we will relate analytical factorization properties of the cell mean vectors with the combinatorial and graph-theoretical notions of reducibility and decomposability and we show how to take advantage of these features for the purpose of computing the extended MLE. In Section 6 we show by means of examples how to use the extended MLE for modifying, in a straightforward way, traditional 2 tests for goodness of fit and model selection. The pseudo codes for the algorithms we propose are in Section 7. 4
5 1.1 Notation We introduce here the general, non-tabular notation for contingency tables and related quantities of interest that will be used throughout the document. Consider K categorical random variables X 1,...,X K, each taking values on a finite set of labels, I k = {1,...,I k }, with I k 2 N +, k =1,...,K. Their cross-classification generates a set of label combinations, each called a cell, which is represented by the product set I = N K k=1 I k. Every cell is uniquely identified by a K-dimensional multi-index (i 1,...,i K )=i 2I, whose k-th coordinate indicates the value taken on by the k-th variable. To simplify the notation, the set of cells I will be represented as an lexicographically ordered linear list. This ordering is obtained through the bijection from I into 1, 2,..., Q o K k=1 I k given by KX 1 < i >=< i 1,...,i K >! i K + (i k k=1 KY j=k+1 I j 1 A, (1) so that each K-tuple i will be unambiguously identified with its image i =< i > under the map (1). See Table 6 and Table 7 for the pseudo-codes implementing (1) and its inverse. Example 1.1. Consider the 3-way table with levels I j = {1, 2, 3}, 1 apple j apple 3. The table may be represented in tabular form as and the corresponding numbering of the cells, according to Equation (1), is Any set operation involving i will be expressed using the corresponding index i; for example, for S I, i 2Swill be written i 2S. Adopting this convention, I can be more conveniently thought of as the coordinate vector of R I, the vector space of real-valued functions defined on I. Then, the value of any x 2 R I corresponding to the cell combination i 2Iwill be indicated as x(i) or x i, where i =< i > is defined in (1). The standard inner product on R I is denoted by (x, y) = P i2i x iy i, with x, y 2 R I. If s {1,...,K}, then the coordinate projection of i onto I s = N k2s I k is the ordered list i s = {i k : k 2 s}, and will be written, using (1) again, as i s =< i s >. The s-margin of x 2 R I is the real-valued function on I s with coordinate vector {i s : i 2I}=< I s > obtained as x(i s )= X x(j), j2i : j s=i s and x(i s ) will be called the i s -slice of x. Similarly, for S I, the restriction of x on S will be indicated with x S. The support of a vector x 2 R I is defined to be the set {i 2 I: x i 6= } and is denoted supp(x). The set of vectors in R I with non-negative coordinates will be denoted by R I. Matrices with coordinates indexed by subsets of I can be represented using the same convention and ordering. The column range of a matrix A will be denoted by R(A) and the. 5
6 orthogonal complement of a vector subspace M of R I will be written as M?. Functions and relations on vectors will be taken component-wise, unless otherwise specified. For example, for x 2 R I, exp x = {exp x i : i 2I}and x means x i for all i. The cardinality of a set B will be denoted by B. 2 Contingency Tables and Maximum Likelihood Estimation Log-linear model analysis is concerned with the representation and study the joint distribution of the K variables (X 1,...,X K ). Data consists of a sequence of N independent realization, simultaneous realizations of the K factors and take the form of an unordered random sequence of labels (L 1,...,L N ), with L j 2Ifor each j =1,...,N, where N itself can be random. A contingency table n is a sufficient statistic for the parameters of the underlying joint distribution of (X 1,...,X K ) in the form of cell counts. Definition 2.1. A contingency table is a random function n 2 R I given by n(i) =#{j : L j = i}. The log-linear modeling approach hinges upon the representation of the cell mean vector m = E[n], which is assumed to be strictly positive, by means of a linear subspace M of R I containing µ = log m, to the extent that log-linear models themselves can in fact be defined by such subspaces. Namely, by fixing M, it follows that the logarithms of the cell mean vectors must satisfy specific linear constraints, which completely characterize the underlying joint probability distribution. The defining subspace M will be called log-linear subspace. The distribution of the cell counts is determined not only by the log-linear subspace, but also by the type of sampling scheme utilized in the collection of the data. A sampling scheme is a set of constraints on the observable cell counts induced by the sampling procedure. In this work, we will consider only sampling schemes defined by systems of linear forms. Formally, let N Mbe a linear subspace. The sampling restrictions dictated by N are of the form ( j, n) =c j, j =1,...,m, where (c 1,...,c m ) are known constants and ( 1,..., m) are vectors spanning N. In particular, we will be focusing on the Poisson and product-multinomial sampling schemes, which are of widespread use. We remark that the log-linear framework allows for more general linear sampling designs, known as conditional Poisson schemes. Because a closed form expression for the probability mass function of these models is typically not available and inference is oftentimes infeasible, we chose not to treat them here. We refer to Haberman (1974) and Rinaldo (26) for background and results on these general models. We also point out that our results can be applied in a straightforward way to the mixed Poisson-multinomial models described by Lang (24). 2.1 Sampling Schemes and Log-likelihood functions Poisson Sampling Scheme Under the Poisson sampling scheme, N is the trivial subspace {} and the sampling is unconstrained. Note that the number of data points N must then be random. As a result, the components of n are independent Poisson random variables with E[n i ]=m i, for i 2I. The log-likelihood function `P, as a function of µ 2M, is X X `P(µ) =(n, µ) exp µ i log n i!. (2) i2i i2i 6
7 2.1.2 Product Multinomial Sampling Scheme Under the product-multinomial sampling scheme, the observed vector of counts consists of one or more independent multinomial random vectors. Let I = r] j=1 be a partition of the set I into r classes, where ] denotes disjoint union. For each partitioning set B j let j 2 R I be its indicator function, which is given by B j 1 if i 2Bj j(i) = otherwise, (3) and define N to be the r-dimensional subspace spanned by the orthogonal vectors ( 1,..., r). The product-multinomial sampling constraints require that (n, j) =(m, j) =N j for fixed positive integers N j so that the joint distribution of the cell counts is the product of r independent multinomial distributions with sizes N j, each supported on the set B j. Typically, the spanning vectors of N are defined in a more intuitive way using indicator functions of slices of R I. Specifically, let b {1,...,K} and I b = N k2b I k and, for each j 2I b, define B j = {i 2I: i b = j}. By construction I = U j2i b B j and N is the r-dimensional subspace spanned by the orthogonal vectors { j } j2ib, where j are defined as in (3) and r = I b. For some authors, e.g. Lauritzen (1996), this is in fact taken to be the definition of the product-multinomial scheme. The log-likelihood function at a point µ 2Mis (see Haberman, 1974, Equation 1.51) 1 rx `L(µ) X m i n i log (m, j=1 j) + log N X j! log n i! A, (4) i2bj i2b j where the cell mean vector is m = exp µ. For the trivial partition with only one class, there is only one constraint, namely (1 I, n) =N, and the distribution of the cell counts is multinomial with size N. Because of the sampling constraints, the log-likelihood (4) is well defined only on the subset fm of M given by fm = {µ 2M:( j, exp µ )=N j,j =1,...,r}. (5) Note that f M is neither a vector space nor a convex set. A more convenient parametrization for `L leading to a more manageable parameter space can be obtained as follows. Let M N = M\N?. Lemma 2.2. The following injective function on M N `L( )=(n, ) rx N j log(exp, j) j=1 X log n i!, 8 2M N. (6) i2i parametrizes the log-likelihood function for the product-multinomial model. This re-parametrization is essentially equivalent to reduction to minimal form of the underlying exponential family of distributions for the cell counts via sufficiency (Theorem 3.5 in Rinaldo, 26) and offers considerable computational advantages, which will be exploited in Section 4. 7
8 Proof. We first show that there is a one-to-one correspondence between M N and M. f It is clear that to any point µ there corresponds a unique point = M N µ 2M N and a unique point = N µ 2Nsuch that µ = +. To show the converse, let 2M N. Next, notice that if 2N, then = P r j=1 c j j for some constants c 1,...,c r and, because supp( j ) \ supp( k )=;, for j 6= k, it must be that (i) =c j, for all i 2B j. Then, For each j, let ĉ j = log exp c j (exp, N j (exp, j )! X j) =exp c j i2b j exp i = (exp +, j). (7) (notice that these coefficients depend on only) and let = P r j=1 ĉj j 2N. Then, equation (7) implies that + 2 M. f Therefore, for each µ 2 M, f µ = +, where is obtained by equating (7) to N j. Hence, ( µ, n) =(n, ) Using (4), direct calculation shows that and the proof is complete. 2.2 Existence of the MLE. `L( µ) =(n, µ) kx N j log(exp, j=1 rx N j log N j j=1 j)+ rx N j log N j. j=1 X n i!=`l( ), Consider, for convenience, the parametrization of the log-likelihood functions `P and `L in terms of points of M and f M, respectively. The MLE of µ = log m is the set for the Poisson likelihood and the set i2i {µ 2M: `P(µ )= sup µ2m `P(µ)} {µ 2 M: f `M(µ )= sup `M( µ)} µ2 M f for the product-multinomial likelihood. The MLE is said to be nonexistent if the supremum is not attained at any point in the appropriate log-linear sub-space, i.e. if the above set is empty. With a slight abuse of language, since, in the present problem, the MLE is shown to be always a single point rather than a set, we will always speak of the MLE as a vector rather than a set. Note that, under both sampling schemes, when the MLE of µ exists, the MLE of m is a strictly positive vector. As noted in Haberman (1974), both the log-likelihood functions `P and `M are concave and bounded from above, so that the nonexistence of the MLE is caused by the behavior of the likelihoods at the boundary of the parameter space. In fact, the main result described later is that nonexistence of the MLE can be characterized by sequences of points in the domain of the log-likelihood function that realize the supremum in the limit but, at the same time, have norms exploding to infinity. 8
9 The directions of recession along any of such sequences will correspond to non-estimable natural parameters and non-estimable cell mean counts. As a result, when the MLE of m does not exist, the optimization of the log-likelihoods will lead to an estimated cell mean vector with some zero coordinates. The possibility of identifying the coordinates that correspond to the non-estimable parameters given the data, along with their statistical interpretation, is one the contributions in this work Literature Review We give here a brief history of the main contributions to the theory of maximum likelihood estimation in log-linear models. For a more detailed account see Fienberg and Rinaldo (26). Birch (1963) conducted the first rigorous study of the conditions for existence of the maximum likelihood estimate of the cell mean vector in log-linear models. The author considered hierarchical log-linear models and showed that, under the assumption n >, the maximum likelihood estimate of m exists uniquely and satisfies P M n =P M m, where P M is the projection matrix onto the loglinear subspace M (although the author did not formalize his result in this fashion). In addition, Birch (1963) showed that, if P N n =P N m, the MLE is the same for both Poisson and multinomial sampling schemes. Birch (1963) s findings were greatly generalized by Haberman (1974), whose results have represented the most thorough and advanced treatment on this subject for many years and are reproduced for completeness below, without proof. Haberman (1974), Theorem 2.1. Under Poisson scheme, if a maximum likelihood estimate bµ exists, then it is unique and satisfies P M n =P M bm, (8) where bm = exp bµ. Conversely, if for some bµ 2Mand bm = exp bµ Equation (8) is satisfied, then bm is the maximum likelihood estimate of m. Haberman (1974), Theorem 2.2. Under Poisson scheme, the maximum likelihood estimate of m exists if and only if there exists a 2M? such that n + >. Haberman (1974), Theorem 2.3. Under Poisson scheme, the maximum likelihood estimate of m exists if and only if there does not exist any µ 2Msuch that µ and (n, µ) =. Haberman (1974), Theorem 2.4. Provided, N M, the maximum likelihood estimate of m under Poisson sampling scheme exists if and only if it exists under product-multinomial sampling scheme. If they exist, they coincide. Theorem 2.2 in Haberman (1974) formalizes the intuition that the MLE is defined whenever it is possible to eliminate the zero cells in the table by adding and subtracting appropriate quantities to the observed table n. These results not only explain why the MLE is non-existent if one of the margins is null but also allowed Haberman to give an example of a table for which the MLE is not defined and the margins are positive, describe in Example 2.7, a case termed pathological. Despite the concerned raised by some authors (see Bishop et al., 1975) about the potential deleterious 9
10 effect of pathological configurations of zeros in large and sparse tables, Example 2.7 has been, up until very recently, the only published example of a contingency table with such feature. This was largely due to the fact that, though very intuitive, Haberman s characterization is non-constructive and ultimately impractical, in the sense that it does not lead to efficient algorithms for checking the existence of the MLE. Finally, Haberman (1974, Appendix B) noted by means of examples that, when the MLE is not defined, the maximization of the log-likelihood function produce a sequence of points converging to a unique maximizer bm e, some of whose coordinates, typically a subset of the zero cells, are. Such estimate was then heuristically called extended MLE. In an unpublished manuscript, Fienberg et al. (198) offered a different derivation of Haberman (1974) s results for the Poisson and product-multinomial sampling schemes and provided a formal definition of the extended MLE. The main goal in their work was the development of efficient algorithms for identifying cases of nonexistent MLE and computing the extended MLE. Their approach can be described as follows. For a given observed table n, let I + := supp(n) and I := I\supp(n) be the set of cells with positive and zero counts, respectively. Define the critical set C to be be the subset of I with maximal cardinality such that there exists a µ 2Mwith µ C < but µ C c =, where C c = I \C. Vectors satisfying these conditions are called critical vectors. Next, let M denote the sequential closure in R I of the set {exp µ : µ 2 M}. Theorem 2.3 (Fienberg et al. (198)). The maximum likelihood estimate bm of m exists if and only if C = ;. If C6= ;, then the unique extended maximum likelihood estimate bm e, identical for both the Poisson and product-multinomial sampling scheme, exists and satisfies these two defining conditions: 1. bm e C =, 2. bm e is the only vector in M such that P M n =P M bm e. Note that the condition for the existence of the MLE is a restatement of Haberman s Theorem 2.2. In fact, if C6= ;, then there exists µ 2Msuch that (n, µ) =, µ. On the other hand, if there exists a µ 2Msuch that (n, µ) =, µ, then C {i2i: µ i < } 6= ;. The novelty in the contribution of Fienberg et al. (198) lies in the characterization of the critical set and in the consequent formal definition of the extended MLE as the unique maximizer of the log-likelihood function. Furthermore, and quite importantly, the extended MLE is shown to be always defined, no matter how sparse a table is, and to possess properties mirroring the ones of the ordinary MLE. Gloneck et al. (1988) proved, by means of counter-examples, that positivity of the margins is a necessary and sufficient conditions for existence of the MLE if and only if the model is decomposable. Lauritzen (1996) used a slightly different approach to maximum likelihood estimation in hierarchical log-linear models. In fact, rather than the log-linear subspace M, its sequential closure M is taken to be the appropriate parameter space and hence the domain of the Poisson and productmultinomial log-likelihood functions (2) and (4). Because of this enlarged parameter space, Lauritzen (1996) referred to log-linear models as extended log-linear models. In Theorem 4.8 and Theorem 4.11 the author summarized this characterization of the MLE, which is, as far as existence and uniqueness are concerned, virtually identical to the one for extended MLE offered by Fienberg et al. (198). However, Lauritzen (1996) s results remain overall non-constructive and of limited practical use. Furthermore the author does not make an explicit distinction between MLE and extended MLE is made, and does not offer any interpretation of the MLE obtained in an extended sense. 1
11 2.2.2 Recent Results In this section we summarize the latest results on maximum likelihood estimation for log-linear models. Both the methodology and the results were largely inspired by recent advances in the field of algebraic statistics (Pistone et al., 2; Diaconis and Sturmfels, 1998; Pachter and Sturmfels, 25), which have indicated a more general approach to the study of log-linear models that takes advantage of the tolls and formalism of algebraic and polyhedral geometry. Eriksson et al. (26) used Theorem 2.1 in Haberman (1974) to provide geometric conditions for the existence of the MLE in Poisson and product-multinomial schemes for hierarchical log-linear models. Their characterization is relatively simple, as it relies on basic results form polyhedral geometry, but, at the same time, proved itself quite powerful and suited for numerical implementation. In order to describe their results, basic notions from polyhedral geometry will be introduced here, which will be used throughout the paper. See, in particular, Ziegler (1998). For a given log-linear subspace M, let A be the corresponding d I design matrix whose row span is M. We don t require A to be of full rank, i.e. d may be bigger than rank(a), and we will always assume that the entries of A are integral, a hypothesis that is hardly restrictive and naturally satisfied by the log-linear subspaces we study in Section 3. Consider the polyhedral cone generated by the columns of the matrix A, C A = { : =Ax, x 2 R I }, which is called the marginal cone. Eriksson et al. (26) showed that, provided that N M, the MLE of the cell mean vector under both Poisson and product-multinomial schemes exists if and only if An 2 ri(c A ). The d-dimensional integer vector t =Anis minimal sufficient statistic for the vector of parameters µ, so the condition for the existence of the MLE reduces to the study of the geometric properties of the sufficient statistics. This result was further generalized by Rinaldo (26) who studied maximum likelihood estimation for log-linear models using the theory of exponential families, polyhedral and algebraic geometry. The remainder of the section summarizes these findings. A face of C A is a set F = { 2 C A :(, F )=}, for some F 2 R d such that (, F ) apple for all 2 C A. Note that the polyhedral cone C A has a finite number of faces and that C A is a face of itself, termed improper. To every face F of C A there corresponds a subset F of I such that (a i, F )=, for all i 2Fand (a i, F ) < for all i 2F c = I\F. In words, the set F consists of the cell indexes of the columns of A whose conic hull is precisely F. Conversely, if there exists a vector that defines a set F Iwith the above properties, then determines the supporting hyperplane H F = {x 2 R d :(, x) =} for F, i.e. F =C A \ H F. The set F is called the facial set of F (Geiger et al., 26). For any 2 C A there exists only one (possibly improper) face F containing in its relative interior, i.e. such that t is a linear combination with positive coefficients of the columns of A with indexes in F. This implies that, for any 2 C A, there is one facial set F such that =Ax, for some x 2 R I with supp(x) =F. The facial sets provide a combinatorial representation of the face lattice of C A and play a fundamental role in identifying the set of cells for which an MLE of the expected count is not defined. In particular, for a given table n, we will be concerned with determining the (random) facial set corresponding to the sufficient statistics t =An (see Section 4.1). The next result is a generalization of Theorem Fienberg et al. (198) showing that critical sets are in fact facial sets. The proof is a simplified version of arguments described in detail in Rinaldo (26). 11
12 Theorem 2.4. Assume N Mand let F be the facial set associated to t. The MLE bm of the cell mean vector exists, is unique and identical under Poisson and product-multinomial if and only if F = I. If F ( I, there exists one point bm e in M such that bm e = lim n exp{µ n }, where {µ} n Mis a sequence for which lim n `P(µ n )=supµ2m `P(µ) and lim n `L(µ n )=sup µ2 f M `L( µ). Furthermore, supp( bm e )=F and P M n =P M bm e. Proof. We show that, under both Poisson and product multinomial scheme, the MLE exists unique and is identical in both cases if and only if t =Anis a point in the relative interior of C A. If t belongs to the relative interior of a face F, then both the log-likelihoods realize their suprema along sequences of points µ n Mfor which the limit exp µ n = bm is unique, satisfies the moment equations P M n =P M bn and supp( bm) =F. P First, we consider the problem of maximizing the log-likelihood `P(µ) =(n,µ) i2i expµ i under Poisson sampling scheme. Suppose t =Anlies inside the relative interior of a proper face F of C A. Then, there exists a z F 2 kernel(a) such that the vector x F = n + z F P satisfies t =Ax F and supp(n + z F ) gives the corresponding facial set F. Then, `P(µ) =(x F,µ) i2i expµ i, since, for µ 2M, (z F,µ)=. Let F : R I! R F and F c : R I! R F c be the coordinate projection maps from I into F and F c, respectively. Define `F and `F c to be P the restriction of `P on P F (M) and F c(m), respectively. Explicitly, `F(µ) =(x F, F (µ)) i2f expµ i =(x F,µ) i2f expµ i P and `F c(µ) = i2f c expµ i. Therefore, `P(µ) =`F(µ) +`F c(µ). The function `F is continuous and strictly concave on F (M) and is bounded from above, since limµ: F (µ)!1 `F(µ) = 1. Therefore, `F achieves its supremum at a point in F (M) with finite coordinates. The function `F c is negative and strictly decreasing in each coordinate of its argument and supµ2m `F c(µ) =. Conclude that supµ2m `P(µ) =supµ2m `F(µ). Pick any sequence { n } n Mfor which lim n `F( n )=supµ2m `F(µ) (note that necessarily F ( ) = lim n F ( n ) belongs to F (M) and has finite norm.) Next, choose a sequence { n } n M n such that lim (i) n =for all i 62 F and lim n(i) n n (i) = 1 for all i 2Fand n (i) =for all n and i 62 F. Since F is a facial set, sequences with these properties exist. Then, lim n `F c( n + n ) = lim n `F c( n )== sup Consider now the new sequence {µ n } n M, where µ n = µ2m `F c(µ). n + n. Then lim n `P(µ n ) = lim n (`F( n + n )+`F c( n + n )) = lim n `F( n ) + lim n `F c( n ) = supµ2m `F(µ)+supµ2M `F c(µ) = supµ2m `F(µ) = supµ2m `P(µ) Let bm = lim n exp µ n. Then bm is a non-negative vector with support F such that F ( bm) = exp{ F ( )}. Furthermore, since `F admits a unique maximizer, the optimum bm must be unique. Next, since = lim n n maximizes `F, the first order conditions on the differential of `F (see Haberman, 1974, Chapter 2) gives ( F ( ), exp{ F ( )}) =( F ( ), F (x F )) = (, n), 12
13 for all 2M, where the last equality stems from the fact that F c(x F )=. But this, in turn, implies that, exp µ =(, n) for all 2M, where µ = lim n µ n, and hence P M bm =P M n. (9) If instead the log-likelihood function `L under product-multinomial sampling is to be maximized, it is necessary to consider only the points µ inside f M as in Equation (5). Fortunately, this restriction is inconsequential. In fact, first note that, by (9) and because N M, the limit µ satisfies the constraints {( j, exp µ )=N j,j =1,...,r}. Next, since `L and `P differ by a constant on f M and f M M, we have that `L(µ ) = sup `L( µ). µ2 M f Conclude that the log-likelihood functions under both the Poisson and product multinomial model have the same maximizer bm. Finally, notice that if t 2 ri(c A ), so that F = I, the arguments simplify. Explicitly, there exists a point µ 2 f M Msuch that supµ2m `P(µ) = `P(µ ) sup µ2 M f `L( µ) = `L(µ ). The previous theorem shows that, for any observed table n, one maximizer bm e of the loglikelihood functions can always be found and it exhibits the same features as the ordinary MLE. Definition 2.5. The vector bm e from Theorem 2.4 is the extended MLE of m. In fact, bm e is the MLE of the cell mean vector for a boundary log-linear model in the closure parameter space, under mean-value parametrization. More generally, extended MLEs arise as regular MLEs for an the extended exponential family of distributions supported on the facial sets of C A and that the MLE is just a special case of extended MLE induced by observed sufficient statistics in the interior of the marginal cone rather than on its boundary. The additional distributions making up for the extended exponential family have cell mean vectors supported on the facial sets and are derived by closing appropriately the parameter space, as described below. The results stated in Theorem 2.4 are derived using only analytic arguments focusing on the maximization of the log-likelihood function. Rinaldo (26) gives a different derivation, based on further geometric properties of log-linear models. This approach, which relies on notion from algebraic geometry (see, e.g., Cox et al., 1996), is particularly convenient because it provides an explicit representation for the closure of the parameter space under mean-value parametrization. Specifically, consider the set V A, = nx 2 R I : x z+ = x z, 8z 2 kernel(a) \ Z Io consisting of the real-valued non-negative solutions of a system of polynomial equations specified by the lattice points in the orthogonal complement of M. The set V A, is called a toric variety 13
14 (Sturmfels, 1996; Diaconis and Sturmfels, 1998) and defines a closed, smooth hyper-surface of point in the non-negative orthant of R I. The most notable example of toric varieties arising from hierarchical log-linear models is the surface of independence for a 2 2 and the model of independence (Fienberg and Gilbert, 197). The set V A, offers a more advantageous description of the parameter space under mean value parametrization than the natural parametrization or the u-term representation, which parametrize only log-linear models for which the cell mean vector has strictly positive coordinates. In contrasts, points in V A, with some zero coordinates correspond to boundary log-linear models, i.e. statistical models described by probability distributions expressible in exponential form whose cell mean vectors belong to the boundary of M. To complete the geometric characterization of log-linear models and extended maximum likelihood estimation, we introduce another geometric object that plays a fundamental role in the geometry of log-linear model, namely the polytope P t = x 2 R I : t =Ax, consisting of the set of all possible cell mean values whose margin match the observed sufficient statistics t. The set of lattice points inside P t, called the fiber at t, corresponds to the support of the conditional distribution of the the tables given the value t for the sufficient statistics, often known as the exact distribution. Since both the MLE and extended MLE satisfy the moment equations, bm e is a point of P t (in fact, it is a point in the relative interior of P t ). The marginal cone C A, the variety V A, and the polytope P t are the three main geometric object that fully describe the geometry of log-linear models and their closure. Their relationships are summarized in the following theorem. See Rinaldo (26) and Geiger et al. (26) for the proofs of these statements. Theorem 2.6. i. M =V A, ; ii. V A, and C A are homeomorphic and, for any m 2 V A,, supp(m) is a facial set of C A ; iii. for any t =An, { bm e } =V A, \ P t and bm e 2 ri(p t ). The first results says that the toric variety consists exactly of the set of all cell mean vectors for the log-linear model specified by the row range of A and its point-wise limit closure (i.e. the boundary models). The second results says that there exists a one-to-one correspondence between the expected values of the sufficient statistics and the cell mean vectors. This implies that, for any observable value of the margins t =An, there exists one and only one point bm in V A, such that An =Abm. This point is the MLE if t is in the interior of C A, in which case supp( bm) =I or the extended MLE if t is on the boundary of the marginal cone, in which case supp( bm) =F, with F being the facial set determined by t. The conditions on the support of the points in V A, implies that the additional distributions parametrized, in a mean value sense, by the boundary of V A, (and hence of C A ) are supported on facial sets of the marginal cone. The last statement is a geometrical representation of the result that the (extended) MLE is the only point in M that satisfies the moment equations. Overall, the results described in this section allow to identify boundary log-linear models in many fashions: analytically by maximizing the log-likelihood function, geometrically by describing points on the boundary of both V A, and C A and combinatorially through the facial sets of the 14
15 marginal cone. Not only do they provide useful theoretical characterizations of extended exponential families and extended MLE but also they give a full description of all possible patterns of sampling zeros leading to a nonexistent MLE and the proposal of alternative inferential procedure to deal with tables with a nonexistent MLE (see Section 6). In fact, the condition that the MLE exists if and only if t 2 relint(c A ) can be translated into the equivalent statement that the MLE does not exists if and only if supp(n) Ffor some facial set F of C A. In other words, the forbidden configurations of sampling zeros causing the MLE to be undefined are precisely the complements of the facial set. We call these configurations of zero counts likelihood zeros. Examples of likelihood zeros for different log-linear models are presented in Example 2.7 (see also Eriksson et al., 26). The number of likelihood zero configurations is directly related to the combinatorial complexity of the marginal cone which, for most log-linear models, appears to grow super-exponentially with the number of variable K and the number of categories I k, k =1,...,K, (see the computational study in Eriksson et al., 26). In Section 4 we will address this problem and derive efficient methods for computing the likelihood zeros, the extended MLE and the dimension of the statistical model identified by it. Example 2.7 (Rinaldo (26)). The polyhedral characterization of the conditions for the existence of the MLE permits to generate novel examples of patterns of sampling zeros causing non-existence of the MLE without producing null margins. The examples presented below were obtained using polymake (Gawrilow, 2), a software for the algorithmic treatment of convex polyhedra. These examples suggest that the combinatorial complexity of hierarchical log-linear models can be quite significant. Below we denote the generating class of a hierarchical log-linear model on K variables as represented as a class of subsets of {1,...,K}. a) 2 3 table and the model {{1, 2}, {2, 3}, {1, 3}} of no-second-order interaction (Haberman, 1974). The MLE is not defined because the pattern zeros exposes one of the 16 facets of the marginal cone. See Table 1 in Eriksson et al. (26) and Section 5 in Fienberg and Rinaldo (26) for a more general result concerning binary variables and log-linear models of no-(k 1)st interaction. This example has been for a long time the only published instance of pathological (Bishop et al., 1975, page 115) tables with positive margins and non-existent MLE. b) 3 3 table and the model {{1, 2}, {2, 3}, {1, 3}}. The MLE is not defined because the pattern of zeros exposes one of the 27 facets of the marginal cone. Another facet of the same marginal cone is given by 15
16 In this third and final example, two sampling zero in the left table are not reported in the right table because they don t affect the existence of the MLE and, in fact, correspond to positive cell mean values for the extended MLE. The table on the right exposes a facet of the marginal cone. =) c) table and the model {{1, 2}, {2, 3}, {1, 3}}. The MLE is not defined because the pattern of zeros exposes one of 153,858 facets of the marginal cone. d) 2 4 table and the non-graphical model {{1, 2}, {2, 3}, {3, 4}, {1, 4}, {1, 3}, {2, 3}}. The MLE is not defined because the pattern of zeros exposes one of the 56 facets of the marginal cone. e) 2 4 table and the 4-cycle model {{1, 2}, {2, 3}, {3, 4}, {1, 4}}. The MLE is not defined because the pattern of zeros exposes one of the 24 facets of the marginal cone. f) 3 4 table and the 4-cycle model {{1, 2}, {2, 3}, {3, 4}, {1, 4}}. The MLE is not defined because the pattern of zeros exposes one of the 1,116 facets of the marginal cone. 16
17 g) 3 3 table and the model {{1, 2}, {2, 3}, {1, 3}} (Fienberg and Rinaldo, 26). The MLE is defined, despite the table being very sparse, because no facet of the marginal cone is exposed. 3 Log-Linear Models Subspaces Although log-linear models are defined by generic linear manifolds of R I, in practice it is customary to consider only certain, rather constrained, classes of linear subspaces. These subspaces, which are also characteristic of ANOVA models and experimental design, present considerable advantages in terms of interpretability and ease of computation. In this section we describe various, equivalent characterizations of the factor-interaction subspaces and the subspaces of interactions described in Darroch and Speed (1983) using combinatorics, linear algebra and group theory. We will also present algorithms for optimal sparse representations of the relevant design matrices that will prove useful in the next section for efficient computation of the extended MLE and of the number of estimable parameters. Let K = {1, 2,...,K} the set of labels of the variables of interest and let 2 K be the power set of K. There is a natural partial order in 2 K induced by the operation of taking subset inclusion which makes 2 K into a boolean lattice. A hypergraph H on the finite base set K is a subset of 2 K consisting of a class of subsets of K called hyperedges. An abstract simplicial complex on K is a hypergraph on K such that h d for some d 2 implies h 2. An antichain is a subset A of 2 K such that, for any a i,a j 2A, a i 6 a j. Since K is finite, there is a one-to-one correspondence between antichains and simplicial complexes of 2 K. Namely, for any simplicial complex, the set of all maximal hyperedges of forms an antichain. Conversely, given any antichain A, the class of sets ={d K: d a, for some a 2A} forms a simplicial complex. Because of this correspondence, any simplicial complex will be identified with the associated antichain of maximal hyperedges, called the facets of, while the non-maximal hyperedges will be called its faces. The definition of log-linear models given below is essentially based on the combinatorial structure of the power set 2 K and provides a formal justification of the traditional notation (see, for 17
18 example, Bishop et al., 1975, Chapter 3) of identifying log-linear models, and in particular hierarchical log-linear models, with classes of subsets of K, often called generating classes. Such characterizations are virtually identical to analysis of variance models, a connection that has been known for a long time (see for example Haberman, 1974; Bishop et al., 1975), so that the loglinear subspaces derived here are the same orthogonal decompositions of R I defined by Darroch and Speed (1983). In fact, the contents of Section 3.1 of the present chapter can be considered as an alternative derivation of some results of Darroch and Speed (1983). Definition 3.1. A log-linear model is a hypergraph H on K and a hierarchical log-linear model is a simplicial complex on K. Graphical models form a subclass of hierarchical log-linear models (Whittaker, 199; Lauritzen, 1996). To each hypergraph H on K, it is always possible to associate its 2-section G(H) (see, e.g., Berge, 1989), which is a graph with vertex set V = {1,...,K} and edge set consisting of all unordered pairs (i, j) V such that (i, j) h for some h 2H. In the statistical literature, the 2-section graph is also called interaction graph. A hypergraph H is called graphical if its hyperedges are the cliques of its 2-section G(H). Definition 3.2. A hierarchical log-linear model is graphical if the facets of form a graphical hypergraph. The log-linear subspace M associated to a hierarchical log-linear model will be indicated as M and, similarly, M H will denote the log-linear subspace corresponding to a generic loglinear model specified by the hypergraph H. Unless otherwise specified, we will always assume that, for a generic log-linear model H, S h2h = K, so that all the K factors are always included. Each hyperedge of H will be given straightforward interpretation, using the language of analysis of variance. Specifically, the hyperedges h are called h -factor interaction term or interaction term of order h 1. If h =1, then h is a main effect. If h =, then h is the grand mean. In this document, for a hierarchical log-linear model on K factors, the generating classes will be represented by a list of factors enclosed in squared brackets, i.e. [1] indicates the main effect for the factor labeled as 1 and [12] the interaction between factor 1 and 2. This notation is consistent with the one used in the statistical literature (e.g. Bishop et al., 1975; Fienberg, 198). Example 3.3 (Hierarchical log-linear models). = [1][2][3] is the model of mutual independence of the three factors and = [12][23] denotes the model of conditional independence of factor 1 and 3 given factor 2 (a decomposable model; see Section 5.2). The simplest non-graphical model is the model of no-3-factor effect = [12][23][13], which will be used as a test set for many examples here. In fact, for a K-way table, the largest hierarchical log-linear model is the model of no-k-factor effect, represented by the simplicial complex on K nodes whose K 1 facets form the set of all possible distinct subsets of K with cardinality K 1. The simplest example of a graphical non-decomposable (and non-reducible) model is the 4-cycle model on 4 factors, = [12][23][34][14]. For a log-linear model H, we will represent the log-linear subspace M H as the direct sum of orthogonal subspaces of R I, each determined by a subset of K, M H = M h2h M h, (1) 18
19 where M h?m h for h, h K with h 6= h. For a hierarchical log-linear model, the above expression specializes to M M = M h. (11) {h d: d2 } In the remainder of the section various equivalent constructions of the subspaces involved in Equations (1) and (11) are provided. These constructions will lead to the same class of subspaces described in Darroch and Speed (1983). 3.1 Combinatorial Derivation In this section we derive log-linear model subspaces is obtained by establishing multiple correspondences among the combinatorial structure of the subsets of K, the properties of certain classes of partitions of I and the decomposition of R I into direct sums of orthogonal linear subspaces. The techniques and most of the results utilized here are adapted from Bailey (24). Let h Kand define the equivalence relation h on I given by i h j () i h = j h, for all i, j 2I. The equivalence classes of h in turn define a partition p(h) of I into d h = Q k2h I k subsets of equal cardinality n h = Q k62h I k = I d h. Explicitly, the equivalence classes are the sets {H j : j 2I h }, where H j = {i 2I: i h = j} and I h = N k2h I k, so that I = ] j2ih H j. It should be noted that an identical partitioning argument is utilized for computing an orthogonal basis of the sampling subspace for the product-multinomial sampling scheme in Section 2. In fact, d h is the number of entries of the h-margins of any function x 2 R I and n h is the number of cells to be summed over in order to compute each such entry. Partitions whose classes have constant size are said to be uniform. All the partitions defined in the way described above are, by construction, uniform. For any such partition p(h), the relation matrix R h 2 R I I is the incidence matrix of the equivalence classes of h over I and is defined as ( R h (i, j) = 1 if i h j (12) otherwise. The relation matrix R h has the explicit form, of easy verification, R h = KO k=1 Ik if k 2 h J k if k 62 h, where I k is the I k -dimensional identity matrix and J k the I k -dimensional matrix containing all 1 s. Associated to each p(h) is the subspace W h R I consisting of all functions on the multi-index set I that depend on i 2Ionly through i h, i.e. n o W h = f 2 R I : f(i) =f(j) if i h j, (13) where W ; = 1 and W K = R I. In Darroch and Speed (1983) such spaces are called factor-interaction subspaces. Let P h be the orthogonal projection onto W h. Then, for any x 2 R I, y =P h x is a vector 19
20 whose i h -margins are constant and equal to the average of the corresponding coordinates of x, i.e. y(i) = 1 X x(j). n h {j2i : i h j} As a consequence of the uniformity of the classes of p(h), the projection matrix P h has a very simple form, obtained as P h = 1 KO Ik if k 2 h R h = (14) n h otherwise. k=1 Let P K = {p(h): h 2 2 K }, where p(;) consists of the entire set I, and p(k) has as many classes as cells. For different partitions p(h) and p(h ), write p(h) 4 p(h ) if every p(h)-class is a subset of some p(h )-class. The relation 4 satisfies the properties of reflexivity, antisymmetry and transitivity, so that P K is a poset with respect to the relation 4. Similarly, let W K = {W h : h 2 2 K }, where the subspaces are defined as in (13). By construction, W K is partially ordered by inclusion, hence it is a poset with respect to the inclusion operator. 1 I k J k Lemma 3.4. The three posets W K, 2 K and P K are isomorphic lattices: for all h, h 2 2 K. W h W h () h h () p(h ) < p(h) (15) Proof. The equivalences follow by construction. Using (15) and the fact that 2 K is a lattice or direct verification, it follows that both P K and W K are lattices. As indicated in the equivalence (15), the relation 4 on P K the is the opposite of the inclusion relation on both 2 K and W K ; in fact, subsets of h and linear subspaces of W h in W K induce coarser partitions than p(h). The ˆ and ˆ1 elements of P K are p(;) and p(k), respectively, while ˆ and ˆ1 elements of W K are 1 I and R I, respectively. Furthermore, the relations of the next Corollary can be verified for the least upper bound and biggest lower bound on P K. Corollary 3.5. For any h 1,h 2,h K : W h3 = W h1 + W h2 () h 3 = h 1 [ h 2 () p(h 3 )=p(h 1 ) ^ p(h 1 ) W h3 = W h1 \W h2 () h 3 = h 1 \ h 2 () p(h 3 )=p(h 1 ) _ p(h 1 ) (16) Because of the isomorphism of Lemma 3.4, combinatorial properties of P K and 2 K translates into geometric properties of the subspaces in W K. In order to illustrate these properties we will use the correspondence between orthogonal partitions and geometric orthogonality. Specifically, two partitions p(h) and p(h ) are said to be orthogonal if P h P h =P h P h. Linear subspaces whose projection matrices commute, like the ones associated with orthogonal partitions, are called geometrically orthogonal. As it turns out, orthogonality of all the partitions making up P K is precisely the required feature to obtain a combinatorial decomposition of R I into orthogonal subspaces indexed by elements of 2 K, as in Equations (1) and (11). Lemma 3.6. For any h, h 2 2 K : 2
21 1. p(h) and p(h ) are orthogonal, hence W h and W h are geometrically orthogonal; 2. W h \ W p(h)_p(h )? is orthogonal to Wh. Proof. Lemma 6.4 and Lemma 9.1 in Bailey (24). The geometric orthogonality of the vector spaces W h, h 2 2 K, allows for a recursive decomposition of every W h into orthogonal subspaces computed by intersecting W h itself with the orthogonal complement of all the smaller subspaces it contains. Theorem 3.7. For any h 2 2 K, define: U h = W h X {h 22 K : p(h ) p(h)} W h 1 A?. (17) Then: 1. for any h, h 2 2 K, with h 6= h the subspaces U h and U h are orthogonal to each other; 2. for each h 2 2 K W h = Proof. Theorem 6.7 in Bailey (24). M {h 22 K : p(h )<p(h)} U h. (18) In virtue of (15), {h 2 2 K : p(h ) < p(h)} = {h 2 2 K : h h}, so that equation (18), along with W K = R I, gives: Corollary 3.8. For any h 2 2 K : In particular: W h = M h h U h. (19) R I = M h K U h. (2) The orthogonal subspaces U h decomposing the W h s are the subspaces of interactions in Darroch and Speed (1983) (see also Lauritzen, 1996, Appendix B). Bailey (24) calls them strata instead. In the rest of the section, the combinatorial structure of P K will be exploited We will take advantage of the combinatorial structure of P K to derive formulas for the projection matrices onto the factor subspaces and, consequently, a fully description of the subspaces of interactions. For any two partitions p(h) and p(h ) in the lattice P K, define in R P K P K the zeta function p(h),p(h ) = 1 if p(h) 4 p(h ) otherwise. Since P K is finite, it is possible to assign an ordering to its elements in such a way that p(h) comes before p(h ) if p(h) 4 p(h ). The zeta function belongs to the incidence algebra (see, for example, Stanley, 1997) of P K, which is isomorphic to the algebra of upper triangular matrices. Provided such an ordering of the elements of P K has been fixed once and for all, the zeta function can 21
22 be represented as an upper triangular matrix with diagonal entries all equal to 1. The inverse of such a matrix is therefore well defined and is isomorphic to another function in the corresponding incidence algebra, called the Möbius function µ of the poset P K, 4. Using the Möbius function it is possible to obtain a combinatorial representation of both the projector and the dimension of the subspaces of interactions U h, h 2 2 K. Theorem 3.9. For h 2 2 K, the projector S h onto the subspace U h defined in (17) is given by S h = X h 22 K µ p(h),p(h ) P h (21) and the dimension of S h is dim(u h )= X h 22 K µ p(h),p(h ) d h. Proof. This result follows from Theorem 6.9 in Bailey (24) after noting that each p(h) form an orthogonal block structure (Bailey, 24, Chapter 6). Using the last theorem it is possible to derive a formula for S h. Corollary 3.1. where S h k = ( Ik 1 S h = O k2k S h k (22) I j J k 1 Ij J k if k 2 h otherwise. Note that the last equation match the formulas for the log-linear models of a 3-way table found in Knuiman and Speed (1988). Proof. Because there is an order-reversing correspondence between the lattices 2 K, and P K, 4, as indicated in (15), µ (p(h),p(h )) = µ(h,h), where it is clear that the first Möbius function refers to P K and the second to 2 K. Next, the Möbius function for the lattice 2 K is (see Stanley, 1997, page 118) µ(h ( 1) h\h if h,h)= h otherwise. Hence, equation (21) becomes S h = X {h 22 K : h h} ( 1) h\h P h. (23) It is worth noting that the this is identical to Equation (4.3) in Darroch and Speed (1983) and Equation (B.15) in Lauritzen (1996). Next, assume for simplicity and without loss of generality that h = {1,..., h } (in fact, the whole construction is invariant under permutations of the K factors). Because of the linearity of the tensor product an induction argument can be used to show that N h k=1 I k 1 I k J k = P 2{,1} ( 1) P N h h k k k=1 = P h h ( 1) h N h k=1 22 ki k + (1 k) 1 I k J k ki k + (1 k) 1 I k J k.
23 Then, using the previous equality and the tensor product form of the projection matrices P h given in (14), a more explicit representation of (23) can be obtained as S h = P {h h} ( 1) h\h P h = P {h h} ( 1) h P h\h h P = h h ( 1) h N h k=1 = N 1 N k2h I k I k J k k> h ki k + (1 k) 1 I k J k i N k> h 1 I k J k, 1 I k J k which gives, possibly accounting for permutations of the factors, Equation (22). Formulas for the dimension of the subspaces U h, which again utilizes the Möbius function, will be derived later in Corollary By setting M h = U h for each h K, the desired representation of Equations (1) and (11) is obtained. Definition The log-linear subspace associated to a log-linear model H is defined to be M H = M h2h U h. (24) As for hierarchical log-linear models, Equation (19) allows for the following refinement of the previous definition: Definition The log-linear subspace associated to a hierarchical log-linear model with generating classes is M = X M W d = U h. (25) d2 3.2 Matrix Algebra Derivation {h d: d2 } This section provides efficient algorithms for building design matrices for the factor-interaction subspaces W h and the subspaces of interactions U h, h 2 2 K. The columns of such matrices will span vector subspaces satisfying the defining Equations (24) and (25) of log-linear and hierarchical log-linear models, respectively. A significant portion of the material is derived from Fienberg et al. (198) Bases for U h : Contrast Bases Given a log-linear model H, bases for the subspaces U h = M h, with h 2Hwill be defined and computed. The term contrast bases is appropriate because they indeed correspond to contrasts in models of analysis of variance. Using Birch s notation (see, in particular, Bishop et al., 1975), the design matrix for U h will encode to the u-terms corresponding to the h -order interactions among the factors in h. For each term h Kand factor k 2K, define the matrix U h k = Zk if k 2 h 1 k if k 62 h, 23
24 where Z k is a I k (I k 1) matrix with entries Z k =, (26) B A... 1 and 1 k is the I k -dimensional column vector of 1 s. Let KO U h = U h k. (27) k=1 Since the elements of U h k are 1, and 1, U h has entries that can only be 1, and 1. Additional properties of the design matrices U h and hence of the subspaces spanned by their columns are given in the next Lemma. Lemma i. For every h, h 2 2 K, with h 6= h, the columns of U h are linearly independent and U > h U h =; ii. R I = L h22 K R(U h); iii. for any h 2 2 K, R(U h )=U h, where U h is the subspace of interactions for the factors in h. Proof. Part i.: the first statement follows from the fact that the columns of Z h k are independent QK for each k and h and U h has dimension k=1 k I. As for the second statement, without loss of generality, we can assume that there exists a factor k such that k 2 h and k 62 h. Then, Z h k =C k and Z h k = 1 k, so (Z h k )> Z h k =, hence the result. Part ii.: by i., the subspaces R(U h ), are orthogonal (hence the direct sum notation is well defined) and dimr(u h )= Q j2h (I j 1). Therefore: 1 M R(U h ) A = X Y j 1) = h22 j2h(i Y I k, K k2k h22 K where the last equality follows from Lemma 3.18 and the fact that, for h = ;, dim(u h )=1since U ; = 1 I. Part iii.: it suffices to show S h U h =U h and S h U h =for h 6= h, where S h is the projection matrix onto U h as in Equation (22). This implies R(U h ) U h and the results follow from the fact that the inclusion cannot be strict because of the orthogonal decompositions of R I as in ii. and Equation (2). It is easy to see that S h k Uh k =Uh k and, for any h 6= h with k 2 h \h, S h k U h k =S h k U h k =. Therefore, for any h 6= h. S h U h = KO S h k Uh k =U h and S h U h = k=1 24 KO k=1 S h k Uh k =
25 Note that part ii. yields a decomposition of R I analogous to Equation (2). An alternative way of computing the contrast basis, which might be advantageous from the computational viewpoint, is to replace the matrix Z k in (26) by the equivalent matrix, having the same dimension, C k =. (28) B.... A... 1 It is immediate to see that R(Z k )=R(C k ) and hence part.i and ii. of Lemma 3.13 still hold. It is possible to generate the contrast bases design matrices in computationally efficient ways, which is especially useful when dealing with very high-dimensional problems. Section in the Appendix gives algorithms for generating the matrices U h one row at a time and also for storing them with minimal memory allocation requirements Bases for W h : Marginal Bases Although bases for hierarchical models can be computed using contrast bases, there is a different construction for the hierarchical log-linear subspaces which produces sparse, redundant bases called marginal bases. The use of marginal bases is very common, mainly because of ease of interpretability: such bases in fact induce minimal sufficient statistics which coincides the marginal table sums. In addition, as it is shown in Section 5.2, design matrices defined with marginal basis allow to identify quite straightforwardly some cases in which the MLE is undefined. and For any h 2 2 K let Wk h = IIk if k 2 h 1 k if k 62 h, W h = KO Wk h, (29) k=1 where I Ik denotes the I k -dimensional identity matrix. Let I h = Q k2h I k, so that I h contains the indexes for the columns of W h, where the usual QK lexicographic ordering introduced in Section 1.1 is assumed. The -1 k=1 k I Q k2h I k - dimensional matrix W h enjoys the following properties, which can be easily verified: 1. it is full-column-rank: rank(w h )= Q k2h I k ; 2. for each j 2I h, the column indexed by j have zero entries except in the coordinates i 2I such that i h = j. 3. W > h W h =; 25
26 4. 1 I W > h = 1 hn h, where 1 h is the d h -dimensional vector containing only 1 s, with n h and d h defined at the beginning of Section 3.1. It is straightforward to see that, by construction, R(W h ) = W h, with W h being the factorinteraction subspace defined as in (13). Notice also, that, for x 2 R I, the linear transformation W > h x returns the h-margins of x. For this reason, the columns of design matrix W h are said to form the marginal basis for W h. Contrast bases and marginal bases are related to each other in a very simple way (see also Theorem 3.7). Lemma R(W h )= L h : h h R(U h ) Proof. The proof is a direct consequence of Equation (19) and part iii. of Lemma An alternative proof, using directly the properties of the contrasts and marginal design matrices is given below. Let B h = L h : h 6 h U h. By Lemma 3.13 part ii. and Part 2. of Lemma 3.13, the column range of B h spans the null space of L h : h h R(U h). Therefore, the claim is proved if it is showed that the columns of B h form a basis for the kernel of W h >. By construction, for every h 6 h, U > h W h =, since there exists a k 2 h but k 62 h so that 1 > k Uh k = (see the proof of Lemma 3.13, Part 2.). Therefore, W h > B h =. Next, rank(w h )= Q P Q i2h I k, which, by Lemma 3.18, is equal to h h k2h (I k 1), the co-dimension of B h. Hence rank(b h ) = dim kernel(w h > ). Using Lemma 3.14 it is possible to compute the dimension of the subspaces W h and V h (see also Theorem 3.9). Corollary Let H, be log-linear models and M H, M R I be the associated subspaces. Then dim(m H )= X Y (I k 1) (3) h2h k2h and dim(m )=! KY I j k=1 with the convention that, for h = ;, Q k2h (I k 1) = 1. X {h22 K : h6 d, d2 } Y (I k 1), (31) k2h Proof. Equation (3) follows from the orthogonality properties of the design matrices U h, h 2 H, indicated in Lemma As for equation (31), since M = S d2 R(W d), where d ranges among S the facets of the simplicial complex, then, by Lemma 3.14, its orthogonal complement is {h22 K : h62 } R(U h). By orthogonality again, the dimension of this subspace is X h22 K : h62 Y (I k 1), k2h hence the result. 26
27 Figure 1: 3 3 table and the hierarchical model = [12][13][23]. a): W design matrix ( entries in white and +1 entries in black). b): U design matrix ( entries in gray, 1 entries in back and +1 entries in white). c): B matrix, with columns spanning M? ( entries in gray, 1 entries in back and +1 entries in white). 27
28 The proof of the Lemma requires a well-known combinatorial result, given in Section which uses the Möbius function in exactly the same way as indicated by Theorem 3.9. Equation 31 is given also in Lauritzen (22), without derivation. A very similar but more involved expression for B is derived by Hosten and Sullivant (24) using the notion of adjacent minors. Although the matrices defining the marginal basis are sparse, it is possible to find an even sparser representation of M h for hierarchical models. Specifically, let E n by the first n 1 columns of the identity matrix I n. For any h 2H, let V h k = Ek if k 2 h 1 k if k 62 h and V h = KO Vk h. k=1 The matrices V h have the same properties of the matrices U h listed in Lemma 3.13, even if R(V h ) differs from R(U h ), for any h Kwith h 6= ;. However, it is possible to show that M R(V h )=R(W h )= M R(U h ). (32) h : h h h : h h Similar to the contrast design matrices U h, efficient ways of generating W h and V h row-wise and of storing them in a very compact form are devised and described in Section These algorithms take advantage of the sparsity of both W h and V h as well. For matrices A 1,...,A n with the same number of rows r and number of columns c 1,...,c n, respectively, we will denote the operation of adjoining them into one matrix of dimension r P k c k with nm A k =[A 1...A n ]. Using this notation, we conclude that k=1 U H = M h2h U h is a design matrix for the log-linear model H and both W = M d2 W d and V = M d2 V d (33) are design matrices for the hierarchical log-linear model. In addition, the columns of the matrices M B H = {h22 K : h62h} and M B = U h (34) U h {h22 K : h6 d, d2 } form a basis for M? H and M?, respectively. 28
29 Figure 2: 3 5 table and the random hierarchical model = [145][25][135][345][123]. a): W design matrix ( entries in white and +1 entries in black). b): U design matrix ( entries in gray, 1 entries in back and +1 entries in white). 29
30 Figure 3: 3 5 table and the hierarchical model = [2345][1345][1245][1235][1234] ( entries in white and +1 entries in black). a): W design matrix. b): U design matrix ( entries in gray, 1 entries in back and +1 entries in white). 3
Computing Maximum Likelihood Estimates in Log-Linear Models
 Computing Maximum Likelihood Estimates in Log-Linear Models Alessandro Rinaldo Department of Statistics Carnegie Mellon University June, 2006 Abstract We develop computational strategies for extended maximum
Computing Maximum Likelihood Estimates in Log-Linear Models Alessandro Rinaldo Department of Statistics Carnegie Mellon University June, 2006 Abstract We develop computational strategies for extended maximum
Polyhedral Conditions for the Nonexistence of the MLE for Hierarchical Log-linear Models
 Polyhedral Conditions for the Nonexistence of the MLE for Hierarchical Log-linear Models Nicholas Eriksson Department of Mathematics University of California, Berkeley Alessandro Rinaldo Department of
Polyhedral Conditions for the Nonexistence of the MLE for Hierarchical Log-linear Models Nicholas Eriksson Department of Mathematics University of California, Berkeley Alessandro Rinaldo Department of
arxiv:math/ v1 [math.co] 4 May 2004
![arxiv:math/ v1 [math.co] 4 May 2004 arxiv:math/ v1 [math.co] 4 May 2004](/thumbs/93/111346405.jpg) Polyhedral Conditions for the Nonexistence of the MLE for Hierarchical Log-linear Models arxiv:math/0405044v1 [math.co] 4 May 2004 Nicholas Eriksson a Stephen E. Fienberg b,c Alessandro Rinaldo b Seth
Polyhedral Conditions for the Nonexistence of the MLE for Hierarchical Log-linear Models arxiv:math/0405044v1 [math.co] 4 May 2004 Nicholas Eriksson a Stephen E. Fienberg b,c Alessandro Rinaldo b Seth
Polyhedral conditions for the nonexistence of the MLE for hierarchical log-linear models
 Journal of Symbolic Computation 41 (2006) 222 233 www.elsevier.com/locate/jsc Polyhedral conditions for the nonexistence of the MLE for hierarchical log-linear models Nicholas Eriksson a,stephene.fienberg
Journal of Symbolic Computation 41 (2006) 222 233 www.elsevier.com/locate/jsc Polyhedral conditions for the nonexistence of the MLE for hierarchical log-linear models Nicholas Eriksson a,stephene.fienberg
Maximum Likelihood Estimation in Loglinear Models
 in Loglinear Models Alessandro Rinaldo Carnegie Mellon University joint work with Steve Fienberg April 18, 2012 Workshop on Graphical Models: Mathematics, Statistics and Computer Sciences Fields Institute
in Loglinear Models Alessandro Rinaldo Carnegie Mellon University joint work with Steve Fienberg April 18, 2012 Workshop on Graphical Models: Mathematics, Statistics and Computer Sciences Fields Institute
3. Linear Programming and Polyhedral Combinatorics
 Massachusetts Institute of Technology 18.433: Combinatorial Optimization Michel X. Goemans February 28th, 2013 3. Linear Programming and Polyhedral Combinatorics Summary of what was seen in the introductory
Massachusetts Institute of Technology 18.433: Combinatorial Optimization Michel X. Goemans February 28th, 2013 3. Linear Programming and Polyhedral Combinatorics Summary of what was seen in the introductory
Maximum Likelihood Estimation in Latent Class Models for Contingency Table Data
 Maximum Likelihood Estimation in Latent Class Models for Contingency Table Data Stephen E. Fienberg Department of Statistics, Machine Learning Department, Cylab Carnegie Mellon University May 20, 2008
Maximum Likelihood Estimation in Latent Class Models for Contingency Table Data Stephen E. Fienberg Department of Statistics, Machine Learning Department, Cylab Carnegie Mellon University May 20, 2008
arxiv: v2 [stat.ot] 10 Nov 2011
![arxiv: v2 [stat.ot] 10 Nov 2011 arxiv: v2 [stat.ot] 10 Nov 2011](/thumbs/90/102853071.jpg) Maximum Likelihood Estimation in Network Models arxiv:1105.6145v2 [stat.ot] 10 Nov 2011 Alessandro Rinaldo Department of Statistics Carnegie Mellon University Pittsburgh, PA, 15213-3890 USA Sonja Petrović
Maximum Likelihood Estimation in Network Models arxiv:1105.6145v2 [stat.ot] 10 Nov 2011 Alessandro Rinaldo Department of Statistics Carnegie Mellon University Pittsburgh, PA, 15213-3890 USA Sonja Petrović
Toric statistical models: parametric and binomial representations
 AISM (2007) 59:727 740 DOI 10.1007/s10463-006-0079-z Toric statistical models: parametric and binomial representations Fabio Rapallo Received: 21 February 2005 / Revised: 1 June 2006 / Published online:
AISM (2007) 59:727 740 DOI 10.1007/s10463-006-0079-z Toric statistical models: parametric and binomial representations Fabio Rapallo Received: 21 February 2005 / Revised: 1 June 2006 / Published online:
Linear Algebra March 16, 2019
 Linear Algebra March 16, 2019 2 Contents 0.1 Notation................................ 4 1 Systems of linear equations, and matrices 5 1.1 Systems of linear equations..................... 5 1.2 Augmented
Linear Algebra March 16, 2019 2 Contents 0.1 Notation................................ 4 1 Systems of linear equations, and matrices 5 1.1 Systems of linear equations..................... 5 1.2 Augmented
Tree sets. Reinhard Diestel
 1 Tree sets Reinhard Diestel Abstract We study an abstract notion of tree structure which generalizes treedecompositions of graphs and matroids. Unlike tree-decompositions, which are too closely linked
1 Tree sets Reinhard Diestel Abstract We study an abstract notion of tree structure which generalizes treedecompositions of graphs and matroids. Unlike tree-decompositions, which are too closely linked
PRIMARY DECOMPOSITION FOR THE INTERSECTION AXIOM
 PRIMARY DECOMPOSITION FOR THE INTERSECTION AXIOM ALEX FINK 1. Introduction and background Consider the discrete conditional independence model M given by {X 1 X 2 X 3, X 1 X 3 X 2 }. The intersection axiom
PRIMARY DECOMPOSITION FOR THE INTERSECTION AXIOM ALEX FINK 1. Introduction and background Consider the discrete conditional independence model M given by {X 1 X 2 X 3, X 1 X 3 X 2 }. The intersection axiom
Boolean Inner-Product Spaces and Boolean Matrices
 Boolean Inner-Product Spaces and Boolean Matrices Stan Gudder Department of Mathematics, University of Denver, Denver CO 80208 Frédéric Latrémolière Department of Mathematics, University of Denver, Denver
Boolean Inner-Product Spaces and Boolean Matrices Stan Gudder Department of Mathematics, University of Denver, Denver CO 80208 Frédéric Latrémolière Department of Mathematics, University of Denver, Denver
Linear Algebra. The analysis of many models in the social sciences reduces to the study of systems of equations.
 POLI 7 - Mathematical and Statistical Foundations Prof S Saiegh Fall Lecture Notes - Class 4 October 4, Linear Algebra The analysis of many models in the social sciences reduces to the study of systems
POLI 7 - Mathematical and Statistical Foundations Prof S Saiegh Fall Lecture Notes - Class 4 October 4, Linear Algebra The analysis of many models in the social sciences reduces to the study of systems
3. Linear Programming and Polyhedral Combinatorics
 Massachusetts Institute of Technology 18.453: Combinatorial Optimization Michel X. Goemans April 5, 2017 3. Linear Programming and Polyhedral Combinatorics Summary of what was seen in the introductory
Massachusetts Institute of Technology 18.453: Combinatorial Optimization Michel X. Goemans April 5, 2017 3. Linear Programming and Polyhedral Combinatorics Summary of what was seen in the introductory
Normal Fans of Polyhedral Convex Sets
 Set-Valued Analysis manuscript No. (will be inserted by the editor) Normal Fans of Polyhedral Convex Sets Structures and Connections Shu Lu Stephen M. Robinson Received: date / Accepted: date Dedicated
Set-Valued Analysis manuscript No. (will be inserted by the editor) Normal Fans of Polyhedral Convex Sets Structures and Connections Shu Lu Stephen M. Robinson Received: date / Accepted: date Dedicated
EE731 Lecture Notes: Matrix Computations for Signal Processing
 EE731 Lecture Notes: Matrix Computations for Signal Processing James P. Reilly c Department of Electrical and Computer Engineering McMaster University September 22, 2005 0 Preface This collection of ten
EE731 Lecture Notes: Matrix Computations for Signal Processing James P. Reilly c Department of Electrical and Computer Engineering McMaster University September 22, 2005 0 Preface This collection of ten
A Parametric Simplex Algorithm for Linear Vector Optimization Problems
 A Parametric Simplex Algorithm for Linear Vector Optimization Problems Birgit Rudloff Firdevs Ulus Robert Vanderbei July 9, 2015 Abstract In this paper, a parametric simplex algorithm for solving linear
A Parametric Simplex Algorithm for Linear Vector Optimization Problems Birgit Rudloff Firdevs Ulus Robert Vanderbei July 9, 2015 Abstract In this paper, a parametric simplex algorithm for solving linear
Appendix PRELIMINARIES 1. THEOREMS OF ALTERNATIVES FOR SYSTEMS OF LINEAR CONSTRAINTS
 Appendix PRELIMINARIES 1. THEOREMS OF ALTERNATIVES FOR SYSTEMS OF LINEAR CONSTRAINTS Here we consider systems of linear constraints, consisting of equations or inequalities or both. A feasible solution
Appendix PRELIMINARIES 1. THEOREMS OF ALTERNATIVES FOR SYSTEMS OF LINEAR CONSTRAINTS Here we consider systems of linear constraints, consisting of equations or inequalities or both. A feasible solution
Algebraic Statistics for a Directed Random Graph Model with Reciprocation
 Algebraic Statistics for a Directed Random Graph Model with Reciprocation Sonja Petrović, Alessandro Rinaldo, and Stephen E. Fienberg Abstract. The p 1 model is a directed random graph model used to describe
Algebraic Statistics for a Directed Random Graph Model with Reciprocation Sonja Petrović, Alessandro Rinaldo, and Stephen E. Fienberg Abstract. The p 1 model is a directed random graph model used to describe
Chapter 1. Preliminaries
 Introduction This dissertation is a reading of chapter 4 in part I of the book : Integer and Combinatorial Optimization by George L. Nemhauser & Laurence A. Wolsey. The chapter elaborates links between
Introduction This dissertation is a reading of chapter 4 in part I of the book : Integer and Combinatorial Optimization by George L. Nemhauser & Laurence A. Wolsey. The chapter elaborates links between
Learning with Submodular Functions: A Convex Optimization Perspective
 Foundations and Trends R in Machine Learning Vol. 6, No. 2-3 (2013) 145 373 c 2013 F. Bach DOI: 10.1561/2200000039 Learning with Submodular Functions: A Convex Optimization Perspective Francis Bach INRIA
Foundations and Trends R in Machine Learning Vol. 6, No. 2-3 (2013) 145 373 c 2013 F. Bach DOI: 10.1561/2200000039 Learning with Submodular Functions: A Convex Optimization Perspective Francis Bach INRIA
Some Properties of Convex Hulls of Integer Points Contained in General Convex Sets
 Some Properties of Convex Hulls of Integer Points Contained in General Convex Sets Santanu S. Dey and Diego A. Morán R. H. Milton Stewart School of Industrial and Systems Engineering, Georgia Institute
Some Properties of Convex Hulls of Integer Points Contained in General Convex Sets Santanu S. Dey and Diego A. Morán R. H. Milton Stewart School of Industrial and Systems Engineering, Georgia Institute
The cocycle lattice of binary matroids
 Published in: Europ. J. Comb. 14 (1993), 241 250. The cocycle lattice of binary matroids László Lovász Eötvös University, Budapest, Hungary, H-1088 Princeton University, Princeton, NJ 08544 Ákos Seress*
Published in: Europ. J. Comb. 14 (1993), 241 250. The cocycle lattice of binary matroids László Lovász Eötvös University, Budapest, Hungary, H-1088 Princeton University, Princeton, NJ 08544 Ákos Seress*
Toric Varieties in Statistics
 Toric Varieties in Statistics Daniel Irving Bernstein and Seth Sullivant North Carolina State University dibernst@ncsu.edu http://www4.ncsu.edu/~dibernst/ http://arxiv.org/abs/50.063 http://arxiv.org/abs/508.0546
Toric Varieties in Statistics Daniel Irving Bernstein and Seth Sullivant North Carolina State University dibernst@ncsu.edu http://www4.ncsu.edu/~dibernst/ http://arxiv.org/abs/50.063 http://arxiv.org/abs/508.0546
Facets for Node-Capacitated Multicut Polytopes from Path-Block Cycles with Two Common Nodes
 Facets for Node-Capacitated Multicut Polytopes from Path-Block Cycles with Two Common Nodes Michael M. Sørensen July 2016 Abstract Path-block-cycle inequalities are valid, and sometimes facet-defining,
Facets for Node-Capacitated Multicut Polytopes from Path-Block Cycles with Two Common Nodes Michael M. Sørensen July 2016 Abstract Path-block-cycle inequalities are valid, and sometimes facet-defining,
Topological properties
 CHAPTER 4 Topological properties 1. Connectedness Definitions and examples Basic properties Connected components Connected versus path connected, again 2. Compactness Definition and first examples Topological
CHAPTER 4 Topological properties 1. Connectedness Definitions and examples Basic properties Connected components Connected versus path connected, again 2. Compactness Definition and first examples Topological
MAT2342 : Introduction to Applied Linear Algebra Mike Newman, fall Projections. introduction
 MAT4 : Introduction to Applied Linear Algebra Mike Newman fall 7 9. Projections introduction One reason to consider projections is to understand approximate solutions to linear systems. A common example
MAT4 : Introduction to Applied Linear Algebra Mike Newman fall 7 9. Projections introduction One reason to consider projections is to understand approximate solutions to linear systems. A common example
Unless otherwise specified, V denotes an arbitrary finite-dimensional vector space.
 MAT 90 // 0 points Exam Solutions Unless otherwise specified, V denotes an arbitrary finite-dimensional vector space..(0) Prove: a central arrangement A in V is essential if and only if the dual projective
MAT 90 // 0 points Exam Solutions Unless otherwise specified, V denotes an arbitrary finite-dimensional vector space..(0) Prove: a central arrangement A in V is essential if and only if the dual projective
DISCRETIZED CONFIGURATIONS AND PARTIAL PARTITIONS
 DISCRETIZED CONFIGURATIONS AND PARTIAL PARTITIONS AARON ABRAMS, DAVID GAY, AND VALERIE HOWER Abstract. We show that the discretized configuration space of k points in the n-simplex is homotopy equivalent
DISCRETIZED CONFIGURATIONS AND PARTIAL PARTITIONS AARON ABRAMS, DAVID GAY, AND VALERIE HOWER Abstract. We show that the discretized configuration space of k points in the n-simplex is homotopy equivalent
Cutting planes from extended LP formulations
 Cutting planes from extended LP formulations Merve Bodur University of Wisconsin-Madison mbodur@wisc.edu Sanjeeb Dash IBM Research sanjeebd@us.ibm.com March 7, 2016 Oktay Günlük IBM Research gunluk@us.ibm.com
Cutting planes from extended LP formulations Merve Bodur University of Wisconsin-Madison mbodur@wisc.edu Sanjeeb Dash IBM Research sanjeebd@us.ibm.com March 7, 2016 Oktay Günlük IBM Research gunluk@us.ibm.com
Recoverabilty Conditions for Rankings Under Partial Information
 Recoverabilty Conditions for Rankings Under Partial Information Srikanth Jagabathula Devavrat Shah Abstract We consider the problem of exact recovery of a function, defined on the space of permutations
Recoverabilty Conditions for Rankings Under Partial Information Srikanth Jagabathula Devavrat Shah Abstract We consider the problem of exact recovery of a function, defined on the space of permutations
6-1 The Positivstellensatz P. Parrilo and S. Lall, ECC
 6-1 The Positivstellensatz P. Parrilo and S. Lall, ECC 2003 2003.09.02.10 6. The Positivstellensatz Basic semialgebraic sets Semialgebraic sets Tarski-Seidenberg and quantifier elimination Feasibility
6-1 The Positivstellensatz P. Parrilo and S. Lall, ECC 2003 2003.09.02.10 6. The Positivstellensatz Basic semialgebraic sets Semialgebraic sets Tarski-Seidenberg and quantifier elimination Feasibility
Stat 5101 Lecture Notes
 Stat 5101 Lecture Notes Charles J. Geyer Copyright 1998, 1999, 2000, 2001 by Charles J. Geyer May 7, 2001 ii Stat 5101 (Geyer) Course Notes Contents 1 Random Variables and Change of Variables 1 1.1 Random
Stat 5101 Lecture Notes Charles J. Geyer Copyright 1998, 1999, 2000, 2001 by Charles J. Geyer May 7, 2001 ii Stat 5101 (Geyer) Course Notes Contents 1 Random Variables and Change of Variables 1 1.1 Random
Qualifying Exam in Machine Learning
 Qualifying Exam in Machine Learning October 20, 2009 Instructions: Answer two out of the three questions in Part 1. In addition, answer two out of three questions in two additional parts (choose two parts
Qualifying Exam in Machine Learning October 20, 2009 Instructions: Answer two out of the three questions in Part 1. In addition, answer two out of three questions in two additional parts (choose two parts
Optimization WS 13/14:, by Y. Goldstein/K. Reinert, 9. Dezember 2013, 16: Linear programming. Optimization Problems
 Optimization WS 13/14:, by Y. Goldstein/K. Reinert, 9. Dezember 2013, 16:38 2001 Linear programming Optimization Problems General optimization problem max{z(x) f j (x) 0,x D} or min{z(x) f j (x) 0,x D}
Optimization WS 13/14:, by Y. Goldstein/K. Reinert, 9. Dezember 2013, 16:38 2001 Linear programming Optimization Problems General optimization problem max{z(x) f j (x) 0,x D} or min{z(x) f j (x) 0,x D}
Preliminaries and Complexity Theory
 Preliminaries and Complexity Theory Oleksandr Romanko CAS 746 - Advanced Topics in Combinatorial Optimization McMaster University, January 16, 2006 Introduction Book structure: 2 Part I Linear Algebra
Preliminaries and Complexity Theory Oleksandr Romanko CAS 746 - Advanced Topics in Combinatorial Optimization McMaster University, January 16, 2006 Introduction Book structure: 2 Part I Linear Algebra
Lecture 5. Theorems of Alternatives and Self-Dual Embedding
 IE 8534 1 Lecture 5. Theorems of Alternatives and Self-Dual Embedding IE 8534 2 A system of linear equations may not have a solution. It is well known that either Ax = c has a solution, or A T y = 0, c
IE 8534 1 Lecture 5. Theorems of Alternatives and Self-Dual Embedding IE 8534 2 A system of linear equations may not have a solution. It is well known that either Ax = c has a solution, or A T y = 0, c
arxiv: v1 [cs.cc] 5 Dec 2018
![arxiv: v1 [cs.cc] 5 Dec 2018 arxiv: v1 [cs.cc] 5 Dec 2018](/thumbs/91/106499182.jpg) Consistency for 0 1 Programming Danial Davarnia 1 and J. N. Hooker 2 1 Iowa state University davarnia@iastate.edu 2 Carnegie Mellon University jh38@andrew.cmu.edu arxiv:1812.02215v1 [cs.cc] 5 Dec 2018
Consistency for 0 1 Programming Danial Davarnia 1 and J. N. Hooker 2 1 Iowa state University davarnia@iastate.edu 2 Carnegie Mellon University jh38@andrew.cmu.edu arxiv:1812.02215v1 [cs.cc] 5 Dec 2018
Probabilistic Graphical Models
 Probabilistic Graphical Models Lecture 11 CRFs, Exponential Family CS/CNS/EE 155 Andreas Krause Announcements Homework 2 due today Project milestones due next Monday (Nov 9) About half the work should
Probabilistic Graphical Models Lecture 11 CRFs, Exponential Family CS/CNS/EE 155 Andreas Krause Announcements Homework 2 due today Project milestones due next Monday (Nov 9) About half the work should
3 Integration and Expectation
 3 Integration and Expectation 3.1 Construction of the Lebesgue Integral Let (, F, µ) be a measure space (not necessarily a probability space). Our objective will be to define the Lebesgue integral R fdµ
3 Integration and Expectation 3.1 Construction of the Lebesgue Integral Let (, F, µ) be a measure space (not necessarily a probability space). Our objective will be to define the Lebesgue integral R fdµ
Vector Space Concepts
 Vector Space Concepts ECE 174 Introduction to Linear & Nonlinear Optimization Ken Kreutz-Delgado ECE Department, UC San Diego Ken Kreutz-Delgado (UC San Diego) ECE 174 Fall 2016 1 / 25 Vector Space Theory
Vector Space Concepts ECE 174 Introduction to Linear & Nonlinear Optimization Ken Kreutz-Delgado ECE Department, UC San Diego Ken Kreutz-Delgado (UC San Diego) ECE 174 Fall 2016 1 / 25 Vector Space Theory
Linear Algebra, Summer 2011, pt. 2
 Linear Algebra, Summer 2, pt. 2 June 8, 2 Contents Inverses. 2 Vector Spaces. 3 2. Examples of vector spaces..................... 3 2.2 The column space......................... 6 2.3 The null space...........................
Linear Algebra, Summer 2, pt. 2 June 8, 2 Contents Inverses. 2 Vector Spaces. 3 2. Examples of vector spaces..................... 3 2.2 The column space......................... 6 2.3 The null space...........................
Generating p-extremal graphs
 Generating p-extremal graphs Derrick Stolee Department of Mathematics Department of Computer Science University of Nebraska Lincoln s-dstolee1@math.unl.edu August 2, 2011 Abstract Let f(n, p be the maximum
Generating p-extremal graphs Derrick Stolee Department of Mathematics Department of Computer Science University of Nebraska Lincoln s-dstolee1@math.unl.edu August 2, 2011 Abstract Let f(n, p be the maximum
Closedness of Integer Hulls of Simple Conic Sets
 Closedness of Integer Hulls of Simple Conic Sets Diego A. Morán R., Santanu S. Dey June 7, 2013 Abstract Let C be a full-dimensional pointed closed convex cone in R m obtained by taking the conic hull
Closedness of Integer Hulls of Simple Conic Sets Diego A. Morán R., Santanu S. Dey June 7, 2013 Abstract Let C be a full-dimensional pointed closed convex cone in R m obtained by taking the conic hull
Maximum likelihood in log-linear models
 Graphical Models, Lecture 4, Michaelmas Term 2010 October 22, 2010 Generating class Dependence graph of log-linear model Conformal graphical models Factor graphs Let A denote an arbitrary set of subsets
Graphical Models, Lecture 4, Michaelmas Term 2010 October 22, 2010 Generating class Dependence graph of log-linear model Conformal graphical models Factor graphs Let A denote an arbitrary set of subsets
arxiv: v2 [math.ag] 24 Jun 2015
![arxiv: v2 [math.ag] 24 Jun 2015 arxiv: v2 [math.ag] 24 Jun 2015](/thumbs/94/118503236.jpg) TRIANGULATIONS OF MONOTONE FAMILIES I: TWO-DIMENSIONAL FAMILIES arxiv:1402.0460v2 [math.ag] 24 Jun 2015 SAUGATA BASU, ANDREI GABRIELOV, AND NICOLAI VOROBJOV Abstract. Let K R n be a compact definable set
TRIANGULATIONS OF MONOTONE FAMILIES I: TWO-DIMENSIONAL FAMILIES arxiv:1402.0460v2 [math.ag] 24 Jun 2015 SAUGATA BASU, ANDREI GABRIELOV, AND NICOLAI VOROBJOV Abstract. Let K R n be a compact definable set
Semidefinite Programming
 Semidefinite Programming Notes by Bernd Sturmfels for the lecture on June 26, 208, in the IMPRS Ringvorlesung Introduction to Nonlinear Algebra The transition from linear algebra to nonlinear algebra has
Semidefinite Programming Notes by Bernd Sturmfels for the lecture on June 26, 208, in the IMPRS Ringvorlesung Introduction to Nonlinear Algebra The transition from linear algebra to nonlinear algebra has
Sampling Contingency Tables
 Sampling Contingency Tables Martin Dyer Ravi Kannan John Mount February 3, 995 Introduction Given positive integers and, let be the set of arrays with nonnegative integer entries and row sums respectively
Sampling Contingency Tables Martin Dyer Ravi Kannan John Mount February 3, 995 Introduction Given positive integers and, let be the set of arrays with nonnegative integer entries and row sums respectively
Linear Algebra. Min Yan
 Linear Algebra Min Yan January 2, 2018 2 Contents 1 Vector Space 7 1.1 Definition................................. 7 1.1.1 Axioms of Vector Space..................... 7 1.1.2 Consequence of Axiom......................
Linear Algebra Min Yan January 2, 2018 2 Contents 1 Vector Space 7 1.1 Definition................................. 7 1.1.1 Axioms of Vector Space..................... 7 1.1.2 Consequence of Axiom......................
CHAPTER 11. A Revision. 1. The Computers and Numbers therein
 CHAPTER A Revision. The Computers and Numbers therein Traditional computer science begins with a finite alphabet. By stringing elements of the alphabet one after another, one obtains strings. A set of
CHAPTER A Revision. The Computers and Numbers therein Traditional computer science begins with a finite alphabet. By stringing elements of the alphabet one after another, one obtains strings. A set of
Minimal basis for connected Markov chain over 3 3 K contingency tables with fixed two-dimensional marginals. Satoshi AOKI and Akimichi TAKEMURA
 Minimal basis for connected Markov chain over 3 3 K contingency tables with fixed two-dimensional marginals Satoshi AOKI and Akimichi TAKEMURA Graduate School of Information Science and Technology University
Minimal basis for connected Markov chain over 3 3 K contingency tables with fixed two-dimensional marginals Satoshi AOKI and Akimichi TAKEMURA Graduate School of Information Science and Technology University
Section Notes 8. Integer Programming II. Applied Math 121. Week of April 5, expand your knowledge of big M s and logical constraints.
 Section Notes 8 Integer Programming II Applied Math 121 Week of April 5, 2010 Goals for the week understand IP relaxations be able to determine the relative strength of formulations understand the branch
Section Notes 8 Integer Programming II Applied Math 121 Week of April 5, 2010 Goals for the week understand IP relaxations be able to determine the relative strength of formulations understand the branch
Optimization methods NOPT048
 Optimization methods NOPT048 Jirka Fink https://ktiml.mff.cuni.cz/ fink/ Department of Theoretical Computer Science and Mathematical Logic Faculty of Mathematics and Physics Charles University in Prague
Optimization methods NOPT048 Jirka Fink https://ktiml.mff.cuni.cz/ fink/ Department of Theoretical Computer Science and Mathematical Logic Faculty of Mathematics and Physics Charles University in Prague
Likelihood Analysis of Gaussian Graphical Models
 Faculty of Science Likelihood Analysis of Gaussian Graphical Models Ste en Lauritzen Department of Mathematical Sciences Minikurs TUM 2016 Lecture 2 Slide 1/43 Overview of lectures Lecture 1 Markov Properties
Faculty of Science Likelihood Analysis of Gaussian Graphical Models Ste en Lauritzen Department of Mathematical Sciences Minikurs TUM 2016 Lecture 2 Slide 1/43 Overview of lectures Lecture 1 Markov Properties
Containment restrictions
 Containment restrictions Tibor Szabó Extremal Combinatorics, FU Berlin, WiSe 207 8 In this chapter we switch from studying constraints on the set operation intersection, to constraints on the set relation
Containment restrictions Tibor Szabó Extremal Combinatorics, FU Berlin, WiSe 207 8 In this chapter we switch from studying constraints on the set operation intersection, to constraints on the set relation
Lecture Notes 1: Vector spaces
 Optimization-based data analysis Fall 2017 Lecture Notes 1: Vector spaces In this chapter we review certain basic concepts of linear algebra, highlighting their application to signal processing. 1 Vector
Optimization-based data analysis Fall 2017 Lecture Notes 1: Vector spaces In this chapter we review certain basic concepts of linear algebra, highlighting their application to signal processing. 1 Vector
APPENDIX A. Background Mathematics. A.1 Linear Algebra. Vector algebra. Let x denote the n-dimensional column vector with components x 1 x 2.
 APPENDIX A Background Mathematics A. Linear Algebra A.. Vector algebra Let x denote the n-dimensional column vector with components 0 x x 2 B C @. A x n Definition 6 (scalar product). The scalar product
APPENDIX A Background Mathematics A. Linear Algebra A.. Vector algebra Let x denote the n-dimensional column vector with components 0 x x 2 B C @. A x n Definition 6 (scalar product). The scalar product
Linear Regression and Its Applications
 Linear Regression and Its Applications Predrag Radivojac October 13, 2014 Given a data set D = {(x i, y i )} n the objective is to learn the relationship between features and the target. We usually start
Linear Regression and Its Applications Predrag Radivojac October 13, 2014 Given a data set D = {(x i, y i )} n the objective is to learn the relationship between features and the target. We usually start
Auerbach bases and minimal volume sufficient enlargements
 Auerbach bases and minimal volume sufficient enlargements M. I. Ostrovskii January, 2009 Abstract. Let B Y denote the unit ball of a normed linear space Y. A symmetric, bounded, closed, convex set A in
Auerbach bases and minimal volume sufficient enlargements M. I. Ostrovskii January, 2009 Abstract. Let B Y denote the unit ball of a normed linear space Y. A symmetric, bounded, closed, convex set A in
1 Basic Combinatorics
 1 Basic Combinatorics 1.1 Sets and sequences Sets. A set is an unordered collection of distinct objects. The objects are called elements of the set. We use braces to denote a set, for example, the set
1 Basic Combinatorics 1.1 Sets and sequences Sets. A set is an unordered collection of distinct objects. The objects are called elements of the set. We use braces to denote a set, for example, the set
TORIC WEAK FANO VARIETIES ASSOCIATED TO BUILDING SETS
 TORIC WEAK FANO VARIETIES ASSOCIATED TO BUILDING SETS YUSUKE SUYAMA Abstract. We give a necessary and sufficient condition for the nonsingular projective toric variety associated to a building set to be
TORIC WEAK FANO VARIETIES ASSOCIATED TO BUILDING SETS YUSUKE SUYAMA Abstract. We give a necessary and sufficient condition for the nonsingular projective toric variety associated to a building set to be
Convex hull of two quadratic or a conic quadratic and a quadratic inequality
 Noname manuscript No. (will be inserted by the editor) Convex hull of two quadratic or a conic quadratic and a quadratic inequality Sina Modaresi Juan Pablo Vielma the date of receipt and acceptance should
Noname manuscript No. (will be inserted by the editor) Convex hull of two quadratic or a conic quadratic and a quadratic inequality Sina Modaresi Juan Pablo Vielma the date of receipt and acceptance should
Convex sets, conic matrix factorizations and conic rank lower bounds
 Convex sets, conic matrix factorizations and conic rank lower bounds Pablo A. Parrilo Laboratory for Information and Decision Systems Electrical Engineering and Computer Science Massachusetts Institute
Convex sets, conic matrix factorizations and conic rank lower bounds Pablo A. Parrilo Laboratory for Information and Decision Systems Electrical Engineering and Computer Science Massachusetts Institute
Combinatorial Optimization
 Combinatorial Optimization 2017-2018 1 Maximum matching on bipartite graphs Given a graph G = (V, E), find a maximum cardinal matching. 1.1 Direct algorithms Theorem 1.1 (Petersen, 1891) A matching M is
Combinatorial Optimization 2017-2018 1 Maximum matching on bipartite graphs Given a graph G = (V, E), find a maximum cardinal matching. 1.1 Direct algorithms Theorem 1.1 (Petersen, 1891) A matching M is
Structural and Multidisciplinary Optimization. P. Duysinx and P. Tossings
 Structural and Multidisciplinary Optimization P. Duysinx and P. Tossings 2018-2019 CONTACTS Pierre Duysinx Institut de Mécanique et du Génie Civil (B52/3) Phone number: 04/366.91.94 Email: P.Duysinx@uliege.be
Structural and Multidisciplinary Optimization P. Duysinx and P. Tossings 2018-2019 CONTACTS Pierre Duysinx Institut de Mécanique et du Génie Civil (B52/3) Phone number: 04/366.91.94 Email: P.Duysinx@uliege.be
A Brief Outline of Math 355
 A Brief Outline of Math 355 Lecture 1 The geometry of linear equations; elimination with matrices A system of m linear equations with n unknowns can be thought of geometrically as m hyperplanes intersecting
A Brief Outline of Math 355 Lecture 1 The geometry of linear equations; elimination with matrices A system of m linear equations with n unknowns can be thought of geometrically as m hyperplanes intersecting
Linear-Time Algorithms for Finding Tucker Submatrices and Lekkerkerker-Boland Subgraphs
 Linear-Time Algorithms for Finding Tucker Submatrices and Lekkerkerker-Boland Subgraphs Nathan Lindzey, Ross M. McConnell Colorado State University, Fort Collins CO 80521, USA Abstract. Tucker characterized
Linear-Time Algorithms for Finding Tucker Submatrices and Lekkerkerker-Boland Subgraphs Nathan Lindzey, Ross M. McConnell Colorado State University, Fort Collins CO 80521, USA Abstract. Tucker characterized
POLARS AND DUAL CONES
 POLARS AND DUAL CONES VERA ROSHCHINA Abstract. The goal of this note is to remind the basic definitions of convex sets and their polars. For more details see the classic references [1, 2] and [3] for polytopes.
POLARS AND DUAL CONES VERA ROSHCHINA Abstract. The goal of this note is to remind the basic definitions of convex sets and their polars. For more details see the classic references [1, 2] and [3] for polytopes.
Learning convex bodies is hard
 Learning convex bodies is hard Navin Goyal Microsoft Research India navingo@microsoft.com Luis Rademacher Georgia Tech lrademac@cc.gatech.edu Abstract We show that learning a convex body in R d, given
Learning convex bodies is hard Navin Goyal Microsoft Research India navingo@microsoft.com Luis Rademacher Georgia Tech lrademac@cc.gatech.edu Abstract We show that learning a convex body in R d, given
2.1.3 The Testing Problem and Neave s Step Method
 we can guarantee (1) that the (unknown) true parameter vector θ t Θ is an interior point of Θ, and (2) that ρ θt (R) > 0 for any R 2 Q. These are two of Birch s regularity conditions that were critical
we can guarantee (1) that the (unknown) true parameter vector θ t Θ is an interior point of Θ, and (2) that ρ θt (R) > 0 for any R 2 Q. These are two of Birch s regularity conditions that were critical
Summer School: Semidefinite Optimization
 Summer School: Semidefinite Optimization Christine Bachoc Université Bordeaux I, IMB Research Training Group Experimental and Constructive Algebra Haus Karrenberg, Sept. 3 - Sept. 7, 2012 Duality Theory
Summer School: Semidefinite Optimization Christine Bachoc Université Bordeaux I, IMB Research Training Group Experimental and Constructive Algebra Haus Karrenberg, Sept. 3 - Sept. 7, 2012 Duality Theory
Linear Algebra M1 - FIB. Contents: 5. Matrices, systems of linear equations and determinants 6. Vector space 7. Linear maps 8.
 Linear Algebra M1 - FIB Contents: 5 Matrices, systems of linear equations and determinants 6 Vector space 7 Linear maps 8 Diagonalization Anna de Mier Montserrat Maureso Dept Matemàtica Aplicada II Translation:
Linear Algebra M1 - FIB Contents: 5 Matrices, systems of linear equations and determinants 6 Vector space 7 Linear maps 8 Diagonalization Anna de Mier Montserrat Maureso Dept Matemàtica Aplicada II Translation:
DS-GA 1002 Lecture notes 0 Fall Linear Algebra. These notes provide a review of basic concepts in linear algebra.
 DS-GA 1002 Lecture notes 0 Fall 2016 Linear Algebra These notes provide a review of basic concepts in linear algebra. 1 Vector spaces You are no doubt familiar with vectors in R 2 or R 3, i.e. [ ] 1.1
DS-GA 1002 Lecture notes 0 Fall 2016 Linear Algebra These notes provide a review of basic concepts in linear algebra. 1 Vector spaces You are no doubt familiar with vectors in R 2 or R 3, i.e. [ ] 1.1
COUNTING INTEGER POINTS IN POLYHEDRA. Alexander Barvinok
 COUNTING INTEGER POINTS IN POLYHEDRA Alexander Barvinok Papers are available at http://www.math.lsa.umich.edu/ barvinok/papers.html Let P R d be a polytope. We want to compute (exactly or approximately)
COUNTING INTEGER POINTS IN POLYHEDRA Alexander Barvinok Papers are available at http://www.math.lsa.umich.edu/ barvinok/papers.html Let P R d be a polytope. We want to compute (exactly or approximately)
7. Dimension and Structure.
 7. Dimension and Structure 7.1. Basis and Dimension Bases for Subspaces Example 2 The standard unit vectors e 1, e 2,, e n are linearly independent, for if we write (2) in component form, then we obtain
7. Dimension and Structure 7.1. Basis and Dimension Bases for Subspaces Example 2 The standard unit vectors e 1, e 2,, e n are linearly independent, for if we write (2) in component form, then we obtain
Properties and Classification of the Wheels of the OLS Polytope.
 Properties and Classification of the Wheels of the OLS Polytope. G. Appa 1, D. Magos 2, I. Mourtos 1 1 Operational Research Department, London School of Economics. email: {g.appa, j.mourtos}@lse.ac.uk
Properties and Classification of the Wheels of the OLS Polytope. G. Appa 1, D. Magos 2, I. Mourtos 1 1 Operational Research Department, London School of Economics. email: {g.appa, j.mourtos}@lse.ac.uk
Chapter 1. Preliminaries. The purpose of this chapter is to provide some basic background information. Linear Space. Hilbert Space.
 Chapter 1 Preliminaries The purpose of this chapter is to provide some basic background information. Linear Space Hilbert Space Basic Principles 1 2 Preliminaries Linear Space The notion of linear space
Chapter 1 Preliminaries The purpose of this chapter is to provide some basic background information. Linear Space Hilbert Space Basic Principles 1 2 Preliminaries Linear Space The notion of linear space
arxiv: v5 [math.ra] 17 Sep 2013
![arxiv: v5 [math.ra] 17 Sep 2013 arxiv: v5 [math.ra] 17 Sep 2013](/thumbs/89/97847948.jpg) UNIVERSAL GEOMETRIC CLUSTER ALGEBRAS NATHAN READING arxiv:1209.3987v5 [math.ra] 17 Sep 2013 Abstract. We consider, for each exchange matrix B, a category of geometric cluster algebras over B and coefficient
UNIVERSAL GEOMETRIC CLUSTER ALGEBRAS NATHAN READING arxiv:1209.3987v5 [math.ra] 17 Sep 2013 Abstract. We consider, for each exchange matrix B, a category of geometric cluster algebras over B and coefficient
Least squares regularized or constrained by L0: relationship between their global minimizers. Mila Nikolova
 Least squares regularized or constrained by L0: relationship between their global minimizers Mila Nikolova CMLA, CNRS, ENS Cachan, Université Paris-Saclay, France nikolova@cmla.ens-cachan.fr SIAM Minisymposium
Least squares regularized or constrained by L0: relationship between their global minimizers Mila Nikolova CMLA, CNRS, ENS Cachan, Université Paris-Saclay, France nikolova@cmla.ens-cachan.fr SIAM Minisymposium
Lecture 1 : Probabilistic Method
 IITM-CS6845: Theory Jan 04, 01 Lecturer: N.S.Narayanaswamy Lecture 1 : Probabilistic Method Scribe: R.Krithika The probabilistic method is a technique to deal with combinatorial problems by introducing
IITM-CS6845: Theory Jan 04, 01 Lecturer: N.S.Narayanaswamy Lecture 1 : Probabilistic Method Scribe: R.Krithika The probabilistic method is a technique to deal with combinatorial problems by introducing
Linear algebra for MATH2601: Theory
 Linear algebra for MATH2601: Theory László Erdős August 12, 2000 Contents 1 Introduction 4 1.1 List of crucial problems............................... 5 1.2 Importance of linear algebra............................
Linear algebra for MATH2601: Theory László Erdős August 12, 2000 Contents 1 Introduction 4 1.1 List of crucial problems............................... 5 1.2 Importance of linear algebra............................
MAT-INF4110/MAT-INF9110 Mathematical optimization
 MAT-INF4110/MAT-INF9110 Mathematical optimization Geir Dahl August 20, 2013 Convexity Part IV Chapter 4 Representation of convex sets different representations of convex sets, boundary polyhedra and polytopes:
MAT-INF4110/MAT-INF9110 Mathematical optimization Geir Dahl August 20, 2013 Convexity Part IV Chapter 4 Representation of convex sets different representations of convex sets, boundary polyhedra and polytopes:
Ahlswede Khachatrian Theorems: Weighted, Infinite, and Hamming
 Ahlswede Khachatrian Theorems: Weighted, Infinite, and Hamming Yuval Filmus April 4, 2017 Abstract The seminal complete intersection theorem of Ahlswede and Khachatrian gives the maximum cardinality of
Ahlswede Khachatrian Theorems: Weighted, Infinite, and Hamming Yuval Filmus April 4, 2017 Abstract The seminal complete intersection theorem of Ahlswede and Khachatrian gives the maximum cardinality of
This pre-publication material is for review purposes only. Any typographical or technical errors will be corrected prior to publication.
 This pre-publication material is for review purposes only. Any typographical or technical errors will be corrected prior to publication. Copyright Pearson Canada Inc. All rights reserved. Copyright Pearson
This pre-publication material is for review purposes only. Any typographical or technical errors will be corrected prior to publication. Copyright Pearson Canada Inc. All rights reserved. Copyright Pearson
Construction of a general measure structure
 Chapter 4 Construction of a general measure structure We turn to the development of general measure theory. The ingredients are a set describing the universe of points, a class of measurable subsets along
Chapter 4 Construction of a general measure structure We turn to the development of general measure theory. The ingredients are a set describing the universe of points, a class of measurable subsets along
NOTES on LINEAR ALGEBRA 1
 School of Economics, Management and Statistics University of Bologna Academic Year 207/8 NOTES on LINEAR ALGEBRA for the students of Stats and Maths This is a modified version of the notes by Prof Laura
School of Economics, Management and Statistics University of Bologna Academic Year 207/8 NOTES on LINEAR ALGEBRA for the students of Stats and Maths This is a modified version of the notes by Prof Laura
Chapter 1 The Real Numbers
 Chapter 1 The Real Numbers In a beginning course in calculus, the emphasis is on introducing the techniques of the subject;i.e., differentiation and integration and their applications. An advanced calculus
Chapter 1 The Real Numbers In a beginning course in calculus, the emphasis is on introducing the techniques of the subject;i.e., differentiation and integration and their applications. An advanced calculus
Claw-Free Graphs With Strongly Perfect Complements. Fractional and Integral Version.
 Claw-Free Graphs With Strongly Perfect Complements. Fractional and Integral Version. Part II. Nontrivial strip-structures Maria Chudnovsky Department of Industrial Engineering and Operations Research Columbia
Claw-Free Graphs With Strongly Perfect Complements. Fractional and Integral Version. Part II. Nontrivial strip-structures Maria Chudnovsky Department of Industrial Engineering and Operations Research Columbia
Maximum Likelihood Estimation in Latent Class Models For Contingency Table Data
 Maximum Likelihood Estimation in Latent Class Models For Contingency Table Data Stephen E. Fienberg Department of Statistics, Machine Learning Department and Cylab Carnegie Mellon University Pittsburgh,
Maximum Likelihood Estimation in Latent Class Models For Contingency Table Data Stephen E. Fienberg Department of Statistics, Machine Learning Department and Cylab Carnegie Mellon University Pittsburgh,
11. Learning graphical models
 Learning graphical models 11-1 11. Learning graphical models Maximum likelihood Parameter learning Structural learning Learning partially observed graphical models Learning graphical models 11-2 statistical
Learning graphical models 11-1 11. Learning graphical models Maximum likelihood Parameter learning Structural learning Learning partially observed graphical models Learning graphical models 11-2 statistical
A LINEAR PROGRAMMING BASED ANALYSIS OF THE CP-RANK OF COMPLETELY POSITIVE MATRICES
 Int J Appl Math Comput Sci, 00, Vol 1, No 1, 5 1 A LINEAR PROGRAMMING BASED ANALYSIS OF HE CP-RANK OF COMPLEELY POSIIVE MARICES YINGBO LI, ANON KUMMER ANDREAS FROMMER Department of Electrical and Information
Int J Appl Math Comput Sci, 00, Vol 1, No 1, 5 1 A LINEAR PROGRAMMING BASED ANALYSIS OF HE CP-RANK OF COMPLEELY POSIIVE MARICES YINGBO LI, ANON KUMMER ANDREAS FROMMER Department of Electrical and Information
Contents. O-minimal geometry. Tobias Kaiser. Universität Passau. 19. Juli O-minimal geometry
 19. Juli 2016 1. Axiom of o-minimality 1.1 Semialgebraic sets 2.1 Structures 2.2 O-minimal structures 2. Tameness 2.1 Cell decomposition 2.2 Smoothness 2.3 Stratification 2.4 Triangulation 2.5 Trivialization
19. Juli 2016 1. Axiom of o-minimality 1.1 Semialgebraic sets 2.1 Structures 2.2 O-minimal structures 2. Tameness 2.1 Cell decomposition 2.2 Smoothness 2.3 Stratification 2.4 Triangulation 2.5 Trivialization
Consistency Under Sampling of Exponential Random Graph Models
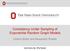 Consistency Under Sampling of Exponential Random Graph Models Cosma Shalizi and Alessandro Rinaldo Summary by: Elly Kaizar Remember ERGMs (Exponential Random Graph Models) Exponential family models Sufficient
Consistency Under Sampling of Exponential Random Graph Models Cosma Shalizi and Alessandro Rinaldo Summary by: Elly Kaizar Remember ERGMs (Exponential Random Graph Models) Exponential family models Sufficient
ARTICLE IN PRESS. Journal of Multivariate Analysis ( ) Contents lists available at ScienceDirect. Journal of Multivariate Analysis
 Journal of Multivariate Analysis ( ) Contents lists available at ScienceDirect Journal of Multivariate Analysis journal homepage: www.elsevier.com/locate/jmva Marginal parameterizations of discrete models
Journal of Multivariate Analysis ( ) Contents lists available at ScienceDirect Journal of Multivariate Analysis journal homepage: www.elsevier.com/locate/jmva Marginal parameterizations of discrete models
Integer Programming ISE 418. Lecture 12. Dr. Ted Ralphs
 Integer Programming ISE 418 Lecture 12 Dr. Ted Ralphs ISE 418 Lecture 12 1 Reading for This Lecture Nemhauser and Wolsey Sections II.2.1 Wolsey Chapter 9 ISE 418 Lecture 12 2 Generating Stronger Valid
Integer Programming ISE 418 Lecture 12 Dr. Ted Ralphs ISE 418 Lecture 12 1 Reading for This Lecture Nemhauser and Wolsey Sections II.2.1 Wolsey Chapter 9 ISE 418 Lecture 12 2 Generating Stronger Valid
arxiv: v1 [stat.ml] 30 Dec 2008
![arxiv: v1 [stat.ml] 30 Dec 2008 arxiv: v1 [stat.ml] 30 Dec 2008](/thumbs/82/85315013.jpg) On the Geometry of Discrete Exponential Families with Application to Exponential Random Graph Models arxiv:0901.0026v1 [stat.ml] 30 Dec 2008 Stephen E. Fienberg Department of Statistics, Machine Learning
On the Geometry of Discrete Exponential Families with Application to Exponential Random Graph Models arxiv:0901.0026v1 [stat.ml] 30 Dec 2008 Stephen E. Fienberg Department of Statistics, Machine Learning
Statistics 612: L p spaces, metrics on spaces of probabilites, and connections to estimation
 Statistics 62: L p spaces, metrics on spaces of probabilites, and connections to estimation Moulinath Banerjee December 6, 2006 L p spaces and Hilbert spaces We first formally define L p spaces. Consider
Statistics 62: L p spaces, metrics on spaces of probabilites, and connections to estimation Moulinath Banerjee December 6, 2006 L p spaces and Hilbert spaces We first formally define L p spaces. Consider
Foundations of Mathematics MATH 220 FALL 2017 Lecture Notes
 Foundations of Mathematics MATH 220 FALL 2017 Lecture Notes These notes form a brief summary of what has been covered during the lectures. All the definitions must be memorized and understood. Statements
Foundations of Mathematics MATH 220 FALL 2017 Lecture Notes These notes form a brief summary of what has been covered during the lectures. All the definitions must be memorized and understood. Statements
Maximum Likelihood Estimation in Latent Class Models For Contingency Table Data
 Maximum Likelihood Estimation in Latent Class Models For Contingency Table Data Stephen E. Fienberg Department of Statistics, Machine Learning Department and Cylab Carnegie Mellon University Pittsburgh,
Maximum Likelihood Estimation in Latent Class Models For Contingency Table Data Stephen E. Fienberg Department of Statistics, Machine Learning Department and Cylab Carnegie Mellon University Pittsburgh,
