On Efficient Decoding of Polar Codes with Large Kernels
|
|
|
- Clinton Powell
- 5 years ago
- Views:
Transcription
1 On Efficient Decoding of Poar Codes with Large Kernes Sarit Buzago, Arman Fazei, Pau H. Siege, Veeresh Taranai, andaexander Vardy University of Caifornia San Diego, La Joa, CA 92093, USA {sbuzago, afazeic, psiege, vtaranai, Abstract Defined through a certain 2 2 matrix caed Arikan s kerne, poar codes are known to achieve the symmetric capacity of binary-input discrete memoryess channes under the successive canceation (SC) decoder. Yet, for short bockengths, poar codes fai to deiver a compeing performance under the ow compexity SC decoding scheme. Recent studies provide evidence for improved performance when Arikan s kerne is repaced with arger kernes that have smaer scaing exponents. However,for kernes the time compexity of the SC decoding increases by a factor of 2. In this paper we study a specia type of kernes caed permuted kernes. The advantage of these kernes is that the SC decoder for the corresponding poar codes can be viewed as a permuted version of the SC decoder for the conventiona poar codes that are ined through Arikan s kerne. This permuted successive canceation (PSC) decoder outputs its decisions on the input bits according to a permuted order of their indices. We introduce an efficient PSC decoding agorithm and show simuations for two permuted kernes that have better scaing exponents than Arikan s kerne. I. INTRODUCTION Introduced by Arikan [1], poar codes are the first codes that were proved to achieve the symmetric capacity of a binary-input discrete memoryess channe (B-DMC) W. Poar codes can be viewed as part of a much arger famiy of codes that are generated according to the 2 2 matrix F 2 ( ). These ength n 2 m codes are cosets of a inear subspace that is spanned by some k rows of F2 m,themth Kronecker power of F 2. One important exampe of such codes are Reed- Muer codes, for which the spanning k rows correspond to the k rows of F m 2 that have maximum Hamming weight. The genius of Arikan s construction ies in the fact that the seection of the k spanning rows depends on the channe. Each row of F m 2 is associated with a synthesized channe caed a bit channe, which is ined through F 2 and the channe W. The seected k rows correspond to the k east noisy bit channes, where the noisiness of the channe is measured by its Bhattacharyya parameter (see [1] for more information on the Bhattacharyya parameter). A remarkabe property of F 2 is that as n grows, the bit channes exhibit a poarization phenomenon: some of the bit channes become very noisy, whie the rest of the bit channes become amost noiseess. Moreover, the fraction of channes that are amost noiseess approaches the symmetric capacity of the channe, I(W). As a resut, for every R<I(W) and for sufficienty arge n there exists a rate R poar code for which the probabiity of error under a successive canceation (SC) decoder is O(n 1 2+ε ), where ε>0 is arbitrariy sma. Despite their impressive asymptotic behavior, empirica resuts indicate ess impressive performance of the SC decoder for poar codes of short bock-engths, e.g. compared to LDPC codes. To improve performance, different decoders were suggested, e.g., beief propagation decoding [2], [5], [8], decoding with ook-ahead [15], and ist successive canceation decoding [12] improved SC decoding [4]. Combined with cycic redundancy check (CRC) pre-coding, the ist successive canceation decoder provides the best performance for poar codes up-to date. Meanwhie, a series of works pursued the same goa by repacing F 2 with arger matrices caed kernes that may induce a faster poarization of the bit channes [6], [7], [9], [10], [11], [14]. To estimate how poarizing a kerne is, two figures of merit were proposed. The first is the error exponent [3], [10] which quantifies the exponentia decay of the error probabiity with respect to the bock-ength n, for a fixed rate R. The second is the scaing exponent [6], [9] which refects the dependence between the ength of the code and its rate, for a fixed probabiity of error P e. More precisey, a scaing exponent μ is a constant that depends ony on the kerne K and the channe W for which n Θ(I(W) R) μ, where the sum of the Bhattacharyya parameters of the nr east noisy bit channes is at most P e. No method is known to compute the scaing exponent for genera channes. In fact, it is not even cear whether or not the scaing exponent exists. Hassani et. a. [9] introduced a numerica method to compute the scaing exponent for the binary erasure channe (BEC) and found that μ 3.627, where the kerne is F 2. Fazei and Vardy [6] presented an 8 8 kerne K 8 with μ and showed that this is optima for kernes of size 8. They aso suggested a heuristic construction through which they found a kerne K 16 with μ However, the time compexity of a SC decoding of poar codes with kernes scaes as 2 n og n. The goa of this paper is to achieve both good performance and efficient SC decoding. To this end we propose to use a specia type of kernes caed permuted kernes. These kernes are formed by permuting the rows of F2. One exampe of a permuted kerne is the kerne K 8 from [6]. On the other hand, the kerne K 16 ined in [6] is not a permuted kerne. Whie a successive canceation decoder for a poar code with the kerne F 2 and of dimension k decides on the n input bits u 0 u 1...u n 1 (n uncoded bits, n k of them are known to the decoder) one after the other according to the sequentia order /17/$ IEEE
2 from 0 to n 1, a SC decoder for poar codes with permuted kernes decides on the input bits according to a permuted order of their indices. Therefore, we ca the SC decoder for a poar code with a permuted kerne a permuted successive canceation (PSC) decoder. By expoiting the connection, we introduce a more efficient impementation of the PSC decoder. Due to page imitations, we ony describe our PSC decoding agorithm for ength- poar codes. A more detaied presentation of the agorithm wi be given in the fu version of this paper. We aso propose two new permuted kernes and show simuation resuts for their performance. The rest of this paper is organized as foows. In Section II, we present notation and initions that are used throughout the paper and review the basic concepts of poar codes. In Section III we discuss the connection between the bit between permuted kernes and F 2 channes of a permuted kerne and the bit channes of F 2. Our PSC decoding agorithm for bock-ength decoder is presented in Section IV. Time compexity of the agorithm is discussed in Section V aong with some simuation resuts. II. PRELIMINARIES In this section we introduce notation and initions used throughout the paper and review the basic concepts for poar codes. For a positive integer n, denote by [n] the set of n integers {0, 1,...,n 1}. For two integers a<b, denote by [a, b] the set of b a integers {a, a +1,...,b 1}. For a positive integer and for a r [], denote by [n] r the set of a eements in [n] that are equa to r moduo, where shoud be cear from the context. A binary vector of ength n is denoted by u n 1 0 u 0 u 1...u n 1.ForA [n], denote by u A the subvector of u n 1 0 that is specified according to indices from A. In particuar, if divides n and r [] then u [n]r u r u +r...u n +r. A operations on vectors and matrices in this paper are carried out over the fied GF (2). The componentwise addition moduo-2 of two binary vectors u n 1 0 and v0 n 1 is denoted by u n 1 0 v0 n 1. For an matrix K, denote by K m the mth Kronecker power of K. Throughout this paper W : X Y is a generic B- DMC with input aphabet X {0, 1}, output aphabet Y, and transition probabiities W(y x), where for a x X and y Y, W(y x) is the conditiona probabiity that the channe output is y given that the transmitted input is x. For a positive integer n, denote by W n : X n Y n the channe that corresponds to transmission over n independent copies of W. Hence, for every x n 1 0 X n and y0 n 1 Y n,the transition probabiity W n (y n 1 0 x n 1 0 ) is given by W n (y0 n 1 x n 1 0 ) n 1 W(y i x i ). i0 For an n n matrix G, aseta [n] of size k, and a vector z0 n k 1,etC be the code that encodes a ength n input vector u n 1 0,forwhichu [n] A z0 n k 1, to the codeword x n 1 0 u0 n 1 G. Ifi [n] A, then u i is caed a frozen bit. For a i [n], theith bit channe with respect to G, G : X Y n X i, is ined by the transition probabiities G (yn 1 0,u i 1 0 u i ) u n 1 i+1 X n i n 1 W G(y n 1 0 u n 1 0 G). (1) A successive canceation (SC) decoder for C outputs a decision vector ˆu n 1 0 in n steps, where at the ith step the decoder decides on the vaue of ˆu i according to the foowing rue. If i [n] A then ˆu i is set to the vaue of the frozen bit u i. Otherwise, the decoder cacuates the pair of probabiities P i [0] G (yn 1 0, ˆu i 1 0 u i 0), (2) P i [1] G (yn 1 0, ˆu i 1 0 u i 1). and sets ˆu i to the more ikey vaue according to these probabiities, i.e., { 0, Pi [0] P ˆu i i [1] 1, otherwise. Notice that, in genera, the compexity of the SC decoder may be exponentia in n, since the cacuation of P i [0],P i [1] requires a summation of 2 n i 1 terms. Let n 2 m and et G n B n F2 m, where B n is the bitreversa permutation matrix (see [1] for the inition of B n ). For G G n, a poar code with Arikan s kerne is ined by setting A to be the set of k indices corresponding to the bit-channes with the owest Bhattacharyya parameters 1. Due to the structure of G n,thesc decoder for poar codes admits an efficient impementation that runs in O(n og n). This foows from the fact that for this choice of G, there is a recursive expression for the transition probabiities of the ith bit channe. That is, for a i [n], ifi 2φ then G n (y0 n 1,u i 1 0 u i ) 1 2 W(φ) G n/2 (y n/2 1 0,u [2φ]0 u [2φ]1 u 2φ u 2φ+1 ) u 2φ+1 W (i/2) G n/2 (y n 1 n/2,u [2φ] 1 u 2φ+1 ), and if i 2φ +1 then G n (y0 n 1,u i 1 0 u i ) 1 2 W(φ) G n/2 (y n/2 1 0,u [2φ]0 u [2φ]1 u 2φ u 2φ+1 ) W ( i/2 ) G n/2 (y n 1 n/2,u [2φ] 1 u 2φ+1 ). W. Notice that, for r {0, 1}, [2φ] r is the set of a eements in [2π] that are equa to r moduo 2. A kerne K is an invertibe matrix. As mentioned above, one can improve the performance of poar codes by repacing Arikan s kerne with arger kernes that admit better W (0) G 1 1 By the inition of poar codes, the vaues of the frozen bits are aso required. If the channe is symmetric, then the frozen bits are a taken to be zero. For asymmetric channes, an assignment of the frozen bits that guarantees a vanishing probabiity of error is known to exist, however no practica method that finds such an assignment is known. (3) (4)
3 scaing exponents, and hence are considered to be more poarizing. Next, we describe the matrix G G n,k through which a poar code with kerne K is generated. Let n m and et R n be the permutation matrix for which u0 n 1 R n u [n]0 u [n]1...u [n] 1, for a u n 1 0 X n. For an kerne K (K r,s ), ine the matrix G n,k recursivey by G,K K and G n,k (I n/ K)R n (I G n/,k ). For ease of notation we denote the ith bit channe with respect to G n,k by n,k. The recursive structure of the matrix G n,k induces recursive formuas for the bit channes as foows. Lemma 1. Let K be an kerne that can be obtained by permuting the rows and coumns of some ower trianguar matrix. For a i [n], ifi φ + ρ for some φ [n/] and ρ [] then n,k (yn 1 0,u i 1 0 u i ) W (φ) n/,k (y(s+1)n/ 1 sn/ u (φ+1) 1 φ+ρ+1 1 s0,t (s) (u [φ] ) r0 1 K r,s u φ+r ), where T (s) (u [φ] ) r0 1 K r,s u [φ]r. Notice that u [φ]r is a vector of ength φ and K r,s GF (2), hence T (s) (u [φ] ) is a vector of ength φ as required by the inition of the φth bit channe. The term r0 1 K r,s u φ+r is simpy the inner product of u (φ+1) 1 φ with the sth coumn of K. Aso notice that for 2,the expression in Lemma 1 reduces to the recursive formuas (3) and (4). From Lemma 1, it foows that a SC decoding agorithm at the kerne eve, i.e., for a ength- poar code with G K, that has time compexity t can be extended to a SC decoding agorithm for a ength-n poar code with kerne K that has time compexity O(tn og n). In particuar, there exists an impementation for the SC decoder that runs in O(2 n og n). In practice, this time compexity may be too arge even for reativey sma vaues of. For this reason we propose to use a specia type of kernes that can simutaneousy reduce the time compexity of the SC decoder and achieve better scaing exponents. These kernes are caed permuted kernes since they are ined by a row permutation of the matrix G B F2 L, 2 L. III. PERMUTED KERNELS In this section, we focus our discussion on poar codes of ength 2 L, where the matrix G is an permuted kerne. We wi express the bit channes of these codes in terms of the bit channes of G. The discussion in this section motivates the SC decoding agorithm that is formaized in Section IV. A permutation π of ength is a bijection π :[] []. For a permutation π, the matrix permutation corresponding to π is denoted by M π and ined by (M π ) r,s { 1, if s π(r) 0, otherwise, i.e., u 1 0 M π v 1 0, where v π(r) u r, for a r []. A permuted kerne with respect to π is ined by M π G M π B F2 L. Let C π be the poar code that is generated by G K π. For i [], etd i {π(0),π(1),...,π(i 1),π(i)} and et d i max{d i }. For ease of notation, for a i [n] we denote the ith bit channe with respect to G n,kπ and G n by W n,π (i) and W n (i), respectivey. K π Lemma 2. For a i [], theith bit channe with respect to K π is equa to,π (y 1 0,u i 1 0 u i ) W (di) (y0 1,v di 1 0 v di ), v [di +1] D i where v0 1 u0 1 M π, i.e., for a r [], v π(r) u r. Proof. By inition of the ith bit channe (1), we have that,k (y 1 0,u i 1 0 u i ) u 1 i u 1 i W (y 1 0 u 1 0 K π ) W (y 1 0 (u 1 0 M π )G ) v [] Di W (y 1 v [di +1] D i W (di) v [di +1] D i v 1 d i +1 0 v 1 0 G ) W () (y 1 0 v 1 0 G ) (y 1 0,v di 1 0 v di ). By Lemma 2, the ith bit channe with respect to K π can be expressed in terms of the d i th bit channe with respect to G. In particuar, using a SC decoder for the ength- poar code with Arikan s kerne, one can ine a SC decoder for the code C π as foows. For a i [], to decode ˆu i,given the previous decoded bits ˆu i 1 0, the transition probabiities W (di) (y0 1,v di 1 0 v di ) are cacuated for a possibe choices of v s, s [d i +1] D i, where v sπ(r) ˆu r if r [i]. Thus, 2 di+1 i transition probabiities for the ith bit channe of G are cacuated in order to cacuate the ith pair of probabiities ined in (2). IV. FORMALIZATION OF SC DECODER FOR PERMUTED KERNELS In this section we formaize our SC decoder for a ength- code C π ined by a permuted kerne K π. As mentioned above, SC decoding for C π is equivaent to SC decoding of a ength- poar code with kerne F 2 that decides on the input bits in a permuted order according to π. For this reason, we ca our SC decoding scheme permuted successive canceation (PSC) decoding. We present an impementation of PSC decoding for any permutation π, which requires significanty ess computationa power compared to the conventiona SC decoder at the kerne eve. Anaysis of the time compexity is aso presented.
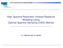
4 For i [], etˆu i 1 0 be the bits decoded so far. Reca that in the ith step, the SC decoder cacuates the pair of probabiities ined in (2). Denote these probabiities by 16, 16 For v i 0,et Q i [0],π (y 1 0, ˆu i 1 0 u i 0), Q i [1],π (y 1 0, ˆu i 1 0 u i 1). P i [v0] i (y0 1,v0 i 1 v i ). Reca that D i {π(0),π(1),...,π(i)} and d i is the maximum over D i.thedecoding window in the ith step is denoted by DW i [d i +1] D i. By Lemma 2, Q i [b] P di [v di 0 ], (5) v s: s DW i where v π(i) u i b and for a r [i], v π(r) ˆu r. The PSC decoding utiizes the conventiona recursive SC decoder for the cacuation of P di [v di 0 ] with different settings (corresponding to a choices for v s, s DW i ) so that it can generate the desired pair of probabiities Q i [b], b {0, 1}. The decoding window DW π (i), refers to the indices of the input bits in v di 0 that are not decoded yet, and hence have to be set temporariy before execution of an instance of the traditiona SC decoder. However, the origina (and efficient) recursive agorithm requires that {π(0), π(1),, π(i)} {0, 1,,i}, which may not be the case for many i []. To overcome this probem, the SC decoder must aso cacuate P j [v j 0 ] for a j [τ i +1,d i +1], where τ i { min(dw i ) 1, i 1, if DW i otherwise. In other words, τ i denotes the argest index j such that v 0,v 1,,v j have a been decoded before cacuating the pair of probabiities associated with u i v π(i). To better understand the importance of this parameter, we reca that the conventiona SC decoding agorithm requires memory, in which it stores both cacuated probabiities and decoded vaues associated with the previous bit channes and bit channes in inner-ayer nodes. Utiizing this memory, the agorithm avoids dupicate cacuations and achieves O(n og(n)) overa compexity in decoding a of the bit channes. This od information, i.e., probabiities and decoded vaues of the previous bit channes, is ony hepfu if it can be propagated back through the poarization ayers and revea unknown inner nodes. However, that is ony possibe when the indices of the aready-decoded bits form a consecutive set. The parameter τ i determines the argest subset of consecutive indices of the aready-decoded bits and hence acts as the starting point for the recursive SC decoding. For simpicity, we ca the sets [τ i +1] and [τ i +1,d i +1] the decoding tai and decoding ookahead of u i, respectivey. Note that, depending on π, forsomei [] we may have DW i, which is equivaent to {π(0),,π(i)} {0, 1,,i} and hence ony a singe instance of the traditiona SC decoder is required. Fig. 1: Structure of the permuted kerne K π from Exampe 1. The recursive structure of G 16 is expoited by the PSC decoder for this kerne. Exampe 1. Consider the permuted binary kerne K π G 16,π, shown in Figure 1, where π (0, 1, 2, 4, 8, 3, 5, 6, 9, 12, 7, 11, 13, 14, 15). The scaing exponent of this kerne for BEC is μ(k π ) To decode u 0,u 1, and u 2 we can simpy ca the traditiona recursive SC decoder. However, to decode u 3, one needs to cacuate the pair of probabiities Q 3 [b] P 4 [ˆv 0ˆv 1ˆv 2 0b]+P 4 [ˆv 0ˆv 1ˆv 2 1b], (6) where ˆv π(r) denotes the decoded bit ˆu r. By inition, we have that D 3 {0, 1, 2, 4}, DW 3 {3}, and τ 3 2. Each term in the right-hand side can be cacuated using the recursive SC decoder with input parameters y0 15, ˆv 0,v and y0 1, ˆv 0,v However, in order to cacuate P 4 [ˆv 0ˆv 1ˆv 2 v 3 v 4 ], the recursive SC must first cacuate P 3 [ˆv 0ˆv 1 ˆv 2 v 3 ]. Moving forward, to decode the next unknown bit u 4,itis desired to output the probabiity pair Q 4 [b] P 8 [ˆv 0ˆv 1ˆv 2 v 3ˆv 4 v5b] 7 (7) v 3v 5v 6v 7 which consists of terms. In this case, D 4 {0, 1, 2, 4, 8}, DW 4 {3, 5, 6, 7}, and τ 3 2. Again, in order to cacuate P 8 [ˆv 0ˆv 1ˆv 2 v 3ˆv 4 v5b], 7 the recursive SC must first cacuate P j [ˆv 0ˆv 1 ˆv 2 v j 3 ], for a j [τ 3 +1, 7]. Surprisingy, the decoding of u 5 formuation to (7), as Q 5 [b] foows a very simiar v 5v 6v 7 P 8 [ˆv 0ˆv 1ˆv 2 bˆv 4 v 7 5ˆv 8 ]. (8)
5 and enters a nested chain of for-oops which aternate between a 2 DWi initiaizations for the unknown bits in the decoding window of u i. At each such initiaization, the agorithm runs the traditiona successive canceation for a j [τ i +1,d i +1] with input parameters y0 1, ˆv j 1 0, where s [j], ˆv s is given either from the previousy decoded vaues ˆu i 1 0, or the temporary initiaization of the eements in the decoding window. It is observed that both the size of the decoding window and the size of the decoding ookahead have a significant roe in determining the time compexity of the decoding agorithm. In the next section, we present the simuations resuts for mutipe permutations, aong with a more detaied comparison on the compexity increase for each permutation. V. SIMULATION RESULTS Fig. 2: Structure of the agorithm that cacuates the transition probabiities of the ith bit channe,π (y 1 0, ˆu i 1 0 u i) for PSC decoding. Accordingy, u 5 can be decoded by simuating the conventiona SC at the same bit channe 2. An overview of the genera PSC decoder is given in Figure 2. The diagram is sef-expanatory. We add a few comments here to carify some of the instructions. The reader is encouraged to read the fu version of the paper for the detaied decoding agorithm (simiar to source code) at both the kerne and the fu-ength eve, where more detais about efficient memory addressing, and dupicationfree cacuations are presented. The agorithm starts by checking updates on the decoding tai. The decoding tai (and its propagated vaues) correspond to the fixed inner-ayer nodes in the decoder structure, and hence by storing their corresponding probabiities/hardvaues in memory we can avoid dupicate cacuations. Next, the agorithm moves to the first unknown node, i.e., τ i, 2 It is possibe to expoit this fact by storing a of the terms in (7) in an auxiiary memory to avoid dupicate cacuations in the future stages (decoding u 5,u 6, and u 7 ). We refer the reader to the fu version of the paper, where we expain this extension in detai, its improvement in throughput, and the extra required memory. In this section, we discuss the compexity increase in more detai and compare the performance of the poar codes based upon different permuted kernes with respect to their overa decoding compexity. As expained earier, the computationa compexity of the permuted SC decoder for the ith bit channe in the permuted kerne may be more than the corresponding ith bit channe in the traditiona kerne. This is mainy because computing Q i [b] requires a summation over 2 DWi terms, where each term can be computed by running d i τ i instances of the conventiona SC decoder; see (8). However, not a such instances consume the same amount of computationa power. Hence, to arrive at an expicit formuation of the computationa compexity for the proposed agorithm, we need to anayze each instance separatey. It is to be noted that time compexity and space compexity are the two main notions of computationa compexity. This paper focuses on improving the decoder speed (throughput) and ignores the efficiency of the memory management. In the fu version, we propose agorithms that sacrifice space efficiency for utimate throughput, or vice versa. The speed of a successive canceation decoder is usuay imited to the number of mathematica operations that have to be executed sequentiay. This sequence in the conventiona SC decoder consists of a doube visit for each of n og(n) nodes in the decoder structure; the first visit is to output a pair of probabiities for the nodes on their eft (coser to u i s), and the second visit is to cacuate and update the probabiities for the nodes on the right side (coser to y i s). Let us ine the normaized compexity fraction at bit channe i, ρ i,tobe the fraction of the tota 2n og(n) computationa power that is spent on decoding W i,gn. It is easy to track the number of nodes contributing to reveaing each v i, and hence a simpe program can derive the expicit vaues of ρ i s. Tabe I shows the evauation of ρ i s for K π from Exampe 1. i odd {2, 6, 10, 14} {4, 12} {8} {0} ρ i 0.008% 0.039% 0.101% 0.226% 0.351% TABLE I: Tabe of normaized compexity fractions for 4 th power or Arikan s kerne. ρ i 2 16 og(16) the number of visits (out of 2 16 og(16)) the reguar SC decoder makes on the inner nodes whie decoding the ith bit channe.
6 As expained in the previous section, the PSC decoder executes the instances of traditiona SC at each index i mutipe times. Let us ine the frequencies, f i, by the tota number of cas made by PSC on traditiona SC at index i. The foowing theorem gives an expicit formua for the computationa compexity of PSC decoder at the kerne eve. Theorem 1. The normaized computationa compexity of the PSC decoder at kerne eve, CC(K,π ), is given by 1 CC(K,π ) f i ρ i. (9) i0 The proof is straightforward and thus it is omitted. Note that the overa decoding compexity at the fu-ength aso scaes with the same scaar as in (9). Tabe II tabuates the evauation of f i s for the permuted kerne in Exampe 1. Utiizing (9), we have CC(K 16,π )7.03. i f i i f i TABLE II: The frequency tabe for K π from Exampe 1. Exampe 2. Consider a different permuted binary kerne K σ, ined by the permutation σ (0, 1, 2, 3, 4, 6, 8, 10, 5, 9, 7, 11, 12, 13, 14, 15). The scaing exponent of K σ for the binary erasure channe is given by μ 3.541, which is again smaer than μ(f 2 ). Hence one woud expect a performance improvement upon conventiona poar codes. However, since σ(i) i, for a i [15] {5, 6, 7, 8, 9, 10}, it is aso expected to observe a smaer increase in computation compexity. We can verify this by foowing the formuation in (9), and show CC(K σ ) 3.2. We eave the discussion on space compexity to the fu version of the paper, where we aso introduce even faster decoding agorithms which can increase the throughput even further at the cost of extra memory. Figure 3 depicts the performance comparison of three poar codes at ength n 2 8 over binary erasure channes. Two of these codes are constructed via K σ and K π, respectivey, and the other one is the conventiona Arikan s poar code, constructed from the 2 2 kerne F 2. It is observed that the poar code constructed from K π, and decoded with PSC, outperforms both the conventiona poar code and the code constructed by K σ. The atter outperforms the conventiona poar code. The resuts are in agreement with the convention that the smaer the scaing exponent, the better the poar code performance. Notice that for some erasure channes the poar code constructed from K π outperforms Arikan s poar code even with the ML decoder. It is to be noted that the conventiona construction agorithms such as [13] cannot be appied directy for the kernes with 4 due to the exponentia increase in the number of bit channe outputs. In this paper, we utiized a Monte- Caro construction agorithm, which may be improved by Frame Error Rate (FER) SC Decoder for F 2 Permuted SC Decoder for K π Permuted SC Decoder for K σ ML Bound for F Erasure Probabiity Fig. 3: Frame-error-rate comparison of three poar codes over binary erasure channes. The tree codes are constructed with F 2, K σ,and K π, respectivey, at code ength n 2 8, and decoded with SC and PSC agorithms. A codes are optimized for the channe BEC(0.2) and rate R 3. The ML bound on performance of the F2 poar 5 code is aso given, based upon methods in [12]. using a arger number of iterations. We eave the study of ow-compexity construction agorithms for future work. REFERENCES [1] E. Arikan, Channe poarization: A method for constructing capacityachieving codes for symmetric binary-input memoryess channes, IEEE Trans. on Inform. Theory, vo. 55, pp , Juy [2] E. Arikan, A performance comparison of poar codes and Reed-Muer codes, IEEE Commun. Letters, vo.12, pp , June [3] E. Arikan and E. Teatar, On the rate of channe poarization, Proc. IEEE Int. Symp. Inform. Theory, pp , Seaou, South Korea, Juy [4] K. Chen, N. Kai, and L. Jiaru, Improved successive canceation decoding of poar codes, IEEE Trans. on Commun., vo. 61, pp , August [5] U. U. Fayyaz and J. R. Bany, Poar codes for partia response channes, Proc. IEEE Int. Conf. Commun., Budapest, Hungary, pp , June [6] A. Fazei and A. Vardy. On the scaing exponent of binary poarization kernes, Proc. Aerton Conf. on Commun., Contro, and Computing, October [7] T. C. Gucu, M. Ye, and A. Barg, Construction of poar codes for arbitrary discrete memoryess channes, Proc. IEEE Symp. Inform. Theory, pp , Barceona, Spain, Juy [8] J. Guo, M. Qin, A. G Fàbregas, and P. H. Siege, Enhanced beief propagation decoding of poar codes through concatenation, Proc. IEEE Int. Symp. Inform. Theory, pp , Honouu, Hawaii, Juy [9] H. S. Hassani, K. Aishahi, and R. L. Urbanke, Finite-ength scaing of poar codes, IEEE Trans. on Inform. Theory, vo.60, pp , Juy [10] S. B. Korada, E. Sasogu, and R. L. Urbanke, Poar codes: Characterization of exponent, bounds, and constructions, IEEE Trans. on Inform. Theory, vo. 56, pp , December [11] V. Miosavskaya, and P. Trifonov, Sequentia decoding of poar codes with arbitrary binary kerne, Proc. IEEE Information Theory Workshop, pp , San Diego, February [12] I. Ta and A. Vardy, List decoding of poar codes, IEEE Trans. on Inform. Theory, vo. 61, pp , May [13] I. Ta and A. Vardy, How to construct poar codes, IEEE Trans. on Inform. Theory, vo. 59, pp , October [14] P. Trifonov, Efficient design and decoding of poar codes, IEEE Trans. on Commun., vo. 60, pp , November [15] P. Trifonov, Binary successive canceation decoding of poar codes with Reed-Soomon kerne, Proc. IEEE Int. Symp. Inform. Theory, pp , Honouu, Hawaii, Juy 2014.
Sequential Decoding of Polar Codes with Arbitrary Binary Kernel
 Sequentia Decoding of Poar Codes with Arbitrary Binary Kerne Vera Miosavskaya, Peter Trifonov Saint-Petersburg State Poytechnic University Emai: veram,petert}@dcn.icc.spbstu.ru Abstract The probem of efficient
Sequentia Decoding of Poar Codes with Arbitrary Binary Kerne Vera Miosavskaya, Peter Trifonov Saint-Petersburg State Poytechnic University Emai: veram,petert}@dcn.icc.spbstu.ru Abstract The probem of efficient
A Brief Introduction to Markov Chains and Hidden Markov Models
 A Brief Introduction to Markov Chains and Hidden Markov Modes Aen B MacKenzie Notes for December 1, 3, &8, 2015 Discrete-Time Markov Chains You may reca that when we first introduced random processes,
A Brief Introduction to Markov Chains and Hidden Markov Modes Aen B MacKenzie Notes for December 1, 3, &8, 2015 Discrete-Time Markov Chains You may reca that when we first introduced random processes,
Turbo Codes. Coding and Communication Laboratory. Dept. of Electrical Engineering, National Chung Hsing University
 Turbo Codes Coding and Communication Laboratory Dept. of Eectrica Engineering, Nationa Chung Hsing University Turbo codes 1 Chapter 12: Turbo Codes 1. Introduction 2. Turbo code encoder 3. Design of intereaver
Turbo Codes Coding and Communication Laboratory Dept. of Eectrica Engineering, Nationa Chung Hsing University Turbo codes 1 Chapter 12: Turbo Codes 1. Introduction 2. Turbo code encoder 3. Design of intereaver
Cryptanalysis of PKP: A New Approach
 Cryptanaysis of PKP: A New Approach Éiane Jaumes and Antoine Joux DCSSI 18, rue du Dr. Zamenhoff F-92131 Issy-es-Mx Cedex France eiane.jaumes@wanadoo.fr Antoine.Joux@ens.fr Abstract. Quite recenty, in
Cryptanaysis of PKP: A New Approach Éiane Jaumes and Antoine Joux DCSSI 18, rue du Dr. Zamenhoff F-92131 Issy-es-Mx Cedex France eiane.jaumes@wanadoo.fr Antoine.Joux@ens.fr Abstract. Quite recenty, in
Iterative Decoding Performance Bounds for LDPC Codes on Noisy Channels
 Iterative Decoding Performance Bounds for LDPC Codes on Noisy Channes arxiv:cs/060700v1 [cs.it] 6 Ju 006 Chun-Hao Hsu and Achieas Anastasopouos Eectrica Engineering and Computer Science Department University
Iterative Decoding Performance Bounds for LDPC Codes on Noisy Channes arxiv:cs/060700v1 [cs.it] 6 Ju 006 Chun-Hao Hsu and Achieas Anastasopouos Eectrica Engineering and Computer Science Department University
Expectation-Maximization for Estimating Parameters for a Mixture of Poissons
 Expectation-Maximization for Estimating Parameters for a Mixture of Poissons Brandon Maone Department of Computer Science University of Hesini February 18, 2014 Abstract This document derives, in excrutiating
Expectation-Maximization for Estimating Parameters for a Mixture of Poissons Brandon Maone Department of Computer Science University of Hesini February 18, 2014 Abstract This document derives, in excrutiating
Fast Blind Recognition of Channel Codes
 Fast Bind Recognition of Channe Codes Reza Moosavi and Erik G. Larsson Linköping University Post Print N.B.: When citing this work, cite the origina artice. 213 IEEE. Persona use of this materia is permitted.
Fast Bind Recognition of Channe Codes Reza Moosavi and Erik G. Larsson Linköping University Post Print N.B.: When citing this work, cite the origina artice. 213 IEEE. Persona use of this materia is permitted.
Practical Polar Code Construction Using Generalised Generator Matrices
 Practical Polar Code Construction Using Generalised Generator Matrices Berksan Serbetci and Ali E. Pusane Department of Electrical and Electronics Engineering Bogazici University Istanbul, Turkey E-mail:
Practical Polar Code Construction Using Generalised Generator Matrices Berksan Serbetci and Ali E. Pusane Department of Electrical and Electronics Engineering Bogazici University Istanbul, Turkey E-mail:
Improved Min-Sum Decoding of LDPC Codes Using 2-Dimensional Normalization
 Improved Min-Sum Decoding of LDPC Codes sing -Dimensiona Normaization Juntan Zhang and Marc Fossorier Department of Eectrica Engineering niversity of Hawaii at Manoa Honouu, HI 968 Emai: juntan, marc@spectra.eng.hawaii.edu
Improved Min-Sum Decoding of LDPC Codes sing -Dimensiona Normaization Juntan Zhang and Marc Fossorier Department of Eectrica Engineering niversity of Hawaii at Manoa Honouu, HI 968 Emai: juntan, marc@spectra.eng.hawaii.edu
Analysis of Emerson s Multiple Model Interpolation Estimation Algorithms: The MIMO Case
 Technica Report PC-04-00 Anaysis of Emerson s Mutipe Mode Interpoation Estimation Agorithms: The MIMO Case João P. Hespanha Dae E. Seborg University of Caifornia, Santa Barbara February 0, 004 Anaysis
Technica Report PC-04-00 Anaysis of Emerson s Mutipe Mode Interpoation Estimation Agorithms: The MIMO Case João P. Hespanha Dae E. Seborg University of Caifornia, Santa Barbara February 0, 004 Anaysis
Formulas for Angular-Momentum Barrier Factors Version II
 BNL PREPRINT BNL-QGS-06-101 brfactor1.tex Formuas for Anguar-Momentum Barrier Factors Version II S. U. Chung Physics Department, Brookhaven Nationa Laboratory, Upton, NY 11973 March 19, 2015 abstract A
BNL PREPRINT BNL-QGS-06-101 brfactor1.tex Formuas for Anguar-Momentum Barrier Factors Version II S. U. Chung Physics Department, Brookhaven Nationa Laboratory, Upton, NY 11973 March 19, 2015 abstract A
Partial permutation decoding for MacDonald codes
 Partia permutation decoding for MacDonad codes J.D. Key Department of Mathematics and Appied Mathematics University of the Western Cape 7535 Bevie, South Africa P. Seneviratne Department of Mathematics
Partia permutation decoding for MacDonad codes J.D. Key Department of Mathematics and Appied Mathematics University of the Western Cape 7535 Bevie, South Africa P. Seneviratne Department of Mathematics
MATH 172: MOTIVATION FOR FOURIER SERIES: SEPARATION OF VARIABLES
 MATH 172: MOTIVATION FOR FOURIER SERIES: SEPARATION OF VARIABLES Separation of variabes is a method to sove certain PDEs which have a warped product structure. First, on R n, a inear PDE of order m is
MATH 172: MOTIVATION FOR FOURIER SERIES: SEPARATION OF VARIABLES Separation of variabes is a method to sove certain PDEs which have a warped product structure. First, on R n, a inear PDE of order m is
Bayesian Learning. You hear a which which could equally be Thanks or Tanks, which would you go with?
 Bayesian Learning A powerfu and growing approach in machine earning We use it in our own decision making a the time You hear a which which coud equay be Thanks or Tanks, which woud you go with? Combine
Bayesian Learning A powerfu and growing approach in machine earning We use it in our own decision making a the time You hear a which which coud equay be Thanks or Tanks, which woud you go with? Combine
XSAT of linear CNF formulas
 XSAT of inear CN formuas Bernd R. Schuh Dr. Bernd Schuh, D-50968 Kön, Germany; bernd.schuh@netcoogne.de eywords: compexity, XSAT, exact inear formua, -reguarity, -uniformity, NPcompeteness Abstract. Open
XSAT of inear CN formuas Bernd R. Schuh Dr. Bernd Schuh, D-50968 Kön, Germany; bernd.schuh@netcoogne.de eywords: compexity, XSAT, exact inear formua, -reguarity, -uniformity, NPcompeteness Abstract. Open
Limited magnitude error detecting codes over Z q
 Limited magnitude error detecting codes over Z q Noha Earief choo of Eectrica Engineering and Computer cience Oregon tate University Corvais, OR 97331, UA Emai: earief@eecsorstedu Bea Bose choo of Eectrica
Limited magnitude error detecting codes over Z q Noha Earief choo of Eectrica Engineering and Computer cience Oregon tate University Corvais, OR 97331, UA Emai: earief@eecsorstedu Bea Bose choo of Eectrica
SUPPLEMENTARY MATERIAL TO INNOVATED SCALABLE EFFICIENT ESTIMATION IN ULTRA-LARGE GAUSSIAN GRAPHICAL MODELS
 ISEE 1 SUPPLEMENTARY MATERIAL TO INNOVATED SCALABLE EFFICIENT ESTIMATION IN ULTRA-LARGE GAUSSIAN GRAPHICAL MODELS By Yingying Fan and Jinchi Lv University of Southern Caifornia This Suppementary Materia
ISEE 1 SUPPLEMENTARY MATERIAL TO INNOVATED SCALABLE EFFICIENT ESTIMATION IN ULTRA-LARGE GAUSSIAN GRAPHICAL MODELS By Yingying Fan and Jinchi Lv University of Southern Caifornia This Suppementary Materia
Lecture Note 3: Stationary Iterative Methods
 MATH 5330: Computationa Methods of Linear Agebra Lecture Note 3: Stationary Iterative Methods Xianyi Zeng Department of Mathematica Sciences, UTEP Stationary Iterative Methods The Gaussian eimination (or
MATH 5330: Computationa Methods of Linear Agebra Lecture Note 3: Stationary Iterative Methods Xianyi Zeng Department of Mathematica Sciences, UTEP Stationary Iterative Methods The Gaussian eimination (or
A. Distribution of the test statistic
 A. Distribution of the test statistic In the sequentia test, we first compute the test statistic from a mini-batch of size m. If a decision cannot be made with this statistic, we keep increasing the mini-batch
A. Distribution of the test statistic In the sequentia test, we first compute the test statistic from a mini-batch of size m. If a decision cannot be made with this statistic, we keep increasing the mini-batch
Bayesian Unscented Kalman Filter for State Estimation of Nonlinear and Non-Gaussian Systems
 Bayesian Unscented Kaman Fiter for State Estimation of Noninear and Non-aussian Systems Zhong Liu, Shing-Chow Chan, Ho-Chun Wu and iafei Wu Department of Eectrica and Eectronic Engineering, he University
Bayesian Unscented Kaman Fiter for State Estimation of Noninear and Non-aussian Systems Zhong Liu, Shing-Chow Chan, Ho-Chun Wu and iafei Wu Department of Eectrica and Eectronic Engineering, he University
arxiv: v1 [math.co] 17 Dec 2018
![arxiv: v1 [math.co] 17 Dec 2018 arxiv: v1 [math.co] 17 Dec 2018](/thumbs/92/108562858.jpg) On the Extrema Maximum Agreement Subtree Probem arxiv:1812.06951v1 [math.o] 17 Dec 2018 Aexey Markin Department of omputer Science, Iowa State University, USA amarkin@iastate.edu Abstract Given two phyogenetic
On the Extrema Maximum Agreement Subtree Probem arxiv:1812.06951v1 [math.o] 17 Dec 2018 Aexey Markin Department of omputer Science, Iowa State University, USA amarkin@iastate.edu Abstract Given two phyogenetic
NEW DEVELOPMENT OF OPTIMAL COMPUTING BUDGET ALLOCATION FOR DISCRETE EVENT SIMULATION
 NEW DEVELOPMENT OF OPTIMAL COMPUTING BUDGET ALLOCATION FOR DISCRETE EVENT SIMULATION Hsiao-Chang Chen Dept. of Systems Engineering University of Pennsyvania Phiadephia, PA 904-635, U.S.A. Chun-Hung Chen
NEW DEVELOPMENT OF OPTIMAL COMPUTING BUDGET ALLOCATION FOR DISCRETE EVENT SIMULATION Hsiao-Chang Chen Dept. of Systems Engineering University of Pennsyvania Phiadephia, PA 904-635, U.S.A. Chun-Hung Chen
Uniprocessor Feasibility of Sporadic Tasks with Constrained Deadlines is Strongly conp-complete
 Uniprocessor Feasibiity of Sporadic Tasks with Constrained Deadines is Strongy conp-compete Pontus Ekberg and Wang Yi Uppsaa University, Sweden Emai: {pontus.ekberg yi}@it.uu.se Abstract Deciding the feasibiity
Uniprocessor Feasibiity of Sporadic Tasks with Constrained Deadines is Strongy conp-compete Pontus Ekberg and Wang Yi Uppsaa University, Sweden Emai: {pontus.ekberg yi}@it.uu.se Abstract Deciding the feasibiity
Problem set 6 The Perron Frobenius theorem.
 Probem set 6 The Perron Frobenius theorem. Math 22a4 Oct 2 204, Due Oct.28 In a future probem set I want to discuss some criteria which aow us to concude that that the ground state of a sef-adjoint operator
Probem set 6 The Perron Frobenius theorem. Math 22a4 Oct 2 204, Due Oct.28 In a future probem set I want to discuss some criteria which aow us to concude that that the ground state of a sef-adjoint operator
MARKOV CHAINS AND MARKOV DECISION THEORY. Contents
 MARKOV CHAINS AND MARKOV DECISION THEORY ARINDRIMA DATTA Abstract. In this paper, we begin with a forma introduction to probabiity and expain the concept of random variabes and stochastic processes. After
MARKOV CHAINS AND MARKOV DECISION THEORY ARINDRIMA DATTA Abstract. In this paper, we begin with a forma introduction to probabiity and expain the concept of random variabes and stochastic processes. After
First-Order Corrections to Gutzwiller s Trace Formula for Systems with Discrete Symmetries
 c 26 Noninear Phenomena in Compex Systems First-Order Corrections to Gutzwier s Trace Formua for Systems with Discrete Symmetries Hoger Cartarius, Jörg Main, and Günter Wunner Institut für Theoretische
c 26 Noninear Phenomena in Compex Systems First-Order Corrections to Gutzwier s Trace Formua for Systems with Discrete Symmetries Hoger Cartarius, Jörg Main, and Günter Wunner Institut für Theoretische
BALANCING REGULAR MATRIX PENCILS
 BALANCING REGULAR MATRIX PENCILS DAMIEN LEMONNIER AND PAUL VAN DOOREN Abstract. In this paper we present a new diagona baancing technique for reguar matrix pencis λb A, which aims at reducing the sensitivity
BALANCING REGULAR MATRIX PENCILS DAMIEN LEMONNIER AND PAUL VAN DOOREN Abstract. In this paper we present a new diagona baancing technique for reguar matrix pencis λb A, which aims at reducing the sensitivity
CS229 Lecture notes. Andrew Ng
 CS229 Lecture notes Andrew Ng Part IX The EM agorithm In the previous set of notes, we taked about the EM agorithm as appied to fitting a mixture of Gaussians. In this set of notes, we give a broader view
CS229 Lecture notes Andrew Ng Part IX The EM agorithm In the previous set of notes, we taked about the EM agorithm as appied to fitting a mixture of Gaussians. In this set of notes, we give a broader view
Some Measures for Asymmetry of Distributions
 Some Measures for Asymmetry of Distributions Georgi N. Boshnakov First version: 31 January 2006 Research Report No. 5, 2006, Probabiity and Statistics Group Schoo of Mathematics, The University of Manchester
Some Measures for Asymmetry of Distributions Georgi N. Boshnakov First version: 31 January 2006 Research Report No. 5, 2006, Probabiity and Statistics Group Schoo of Mathematics, The University of Manchester
A Branch and Cut Algorithm to Design. LDPC Codes without Small Cycles in. Communication Systems
 A Branch and Cut Agorithm to Design LDPC Codes without Sma Cyces in Communication Systems arxiv:1709.09936v1 [cs.it] 28 Sep 2017 Banu Kabakuak 1, Z. Caner Taşkın 1, and Ai Emre Pusane 2 1 Department of
A Branch and Cut Agorithm to Design LDPC Codes without Sma Cyces in Communication Systems arxiv:1709.09936v1 [cs.it] 28 Sep 2017 Banu Kabakuak 1, Z. Caner Taşkın 1, and Ai Emre Pusane 2 1 Department of
Appendix of the Paper The Role of No-Arbitrage on Forecasting: Lessons from a Parametric Term Structure Model
 Appendix of the Paper The Roe of No-Arbitrage on Forecasting: Lessons from a Parametric Term Structure Mode Caio Ameida cameida@fgv.br José Vicente jose.vaentim@bcb.gov.br June 008 1 Introduction In this
Appendix of the Paper The Roe of No-Arbitrage on Forecasting: Lessons from a Parametric Term Structure Mode Caio Ameida cameida@fgv.br José Vicente jose.vaentim@bcb.gov.br June 008 1 Introduction In this
Efficient Generation of Random Bits from Finite State Markov Chains
 Efficient Generation of Random Bits from Finite State Markov Chains Hongchao Zhou and Jehoshua Bruck, Feow, IEEE Abstract The probem of random number generation from an uncorreated random source (of unknown
Efficient Generation of Random Bits from Finite State Markov Chains Hongchao Zhou and Jehoshua Bruck, Feow, IEEE Abstract The probem of random number generation from an uncorreated random source (of unknown
Forty-Seventh Annual Allerton Conference Allerton House, UIUC, Illinois, USA September 30 - October 2, 2009
 Forty-Seventh Annua Aerton Conference Aerton House, UIUC, Iinois, USA September 30 - October 2, 2009 On systematic design of universay capacity approaching rate-compatibe sequences of LDPC code ensembes
Forty-Seventh Annua Aerton Conference Aerton House, UIUC, Iinois, USA September 30 - October 2, 2009 On systematic design of universay capacity approaching rate-compatibe sequences of LDPC code ensembes
8 Digifl'.11 Cth:uits and devices
 8 Digif'. Cth:uits and devices 8. Introduction In anaog eectronics, votage is a continuous variabe. This is usefu because most physica quantities we encounter are continuous: sound eves, ight intensity,
8 Digif'. Cth:uits and devices 8. Introduction In anaog eectronics, votage is a continuous variabe. This is usefu because most physica quantities we encounter are continuous: sound eves, ight intensity,
Efficiently Generating Random Bits from Finite State Markov Chains
 1 Efficienty Generating Random Bits from Finite State Markov Chains Hongchao Zhou and Jehoshua Bruck, Feow, IEEE Abstract The probem of random number generation from an uncorreated random source (of unknown
1 Efficienty Generating Random Bits from Finite State Markov Chains Hongchao Zhou and Jehoshua Bruck, Feow, IEEE Abstract The probem of random number generation from an uncorreated random source (of unknown
Nearly Optimal Constructions of PIR and Batch Codes
 arxiv:700706v [csit] 5 Jun 07 Neary Optima Constructions of PIR and Batch Codes Hia Asi Technion - Israe Institute of Technoogy Haifa 3000, Israe shea@cstechnionaci Abstract In this work we study two famiies
arxiv:700706v [csit] 5 Jun 07 Neary Optima Constructions of PIR and Batch Codes Hia Asi Technion - Israe Institute of Technoogy Haifa 3000, Israe shea@cstechnionaci Abstract In this work we study two famiies
Reliability: Theory & Applications No.3, September 2006
 REDUNDANCY AND RENEWAL OF SERVERS IN OPENED QUEUING NETWORKS G. Sh. Tsitsiashvii M.A. Osipova Vadivosto, Russia 1 An opened queuing networ with a redundancy and a renewa of servers is considered. To cacuate
REDUNDANCY AND RENEWAL OF SERVERS IN OPENED QUEUING NETWORKS G. Sh. Tsitsiashvii M.A. Osipova Vadivosto, Russia 1 An opened queuing networ with a redundancy and a renewa of servers is considered. To cacuate
Asynchronous Control for Coupled Markov Decision Systems
 INFORMATION THEORY WORKSHOP (ITW) 22 Asynchronous Contro for Couped Marov Decision Systems Michae J. Neey University of Southern Caifornia Abstract This paper considers optima contro for a coection of
INFORMATION THEORY WORKSHOP (ITW) 22 Asynchronous Contro for Couped Marov Decision Systems Michae J. Neey University of Southern Caifornia Abstract This paper considers optima contro for a coection of
2M2. Fourier Series Prof Bill Lionheart
 M. Fourier Series Prof Bi Lionheart 1. The Fourier series of the periodic function f(x) with period has the form f(x) = a 0 + ( a n cos πnx + b n sin πnx ). Here the rea numbers a n, b n are caed the Fourier
M. Fourier Series Prof Bi Lionheart 1. The Fourier series of the periodic function f(x) with period has the form f(x) = a 0 + ( a n cos πnx + b n sin πnx ). Here the rea numbers a n, b n are caed the Fourier
Multilayer Kerceptron
 Mutiayer Kerceptron Zotán Szabó, András Lőrincz Department of Information Systems, Facuty of Informatics Eötvös Loránd University Pázmány Péter sétány 1/C H-1117, Budapest, Hungary e-mai: szzoi@csetehu,
Mutiayer Kerceptron Zotán Szabó, András Lőrincz Department of Information Systems, Facuty of Informatics Eötvös Loránd University Pázmány Péter sétány 1/C H-1117, Budapest, Hungary e-mai: szzoi@csetehu,
<C 2 2. λ 2 l. λ 1 l 1 < C 1
 Teecommunication Network Contro and Management (EE E694) Prof. A. A. Lazar Notes for the ecture of 7/Feb/95 by Huayan Wang (this document was ast LaT E X-ed on May 9,995) Queueing Primer for Muticass Optima
Teecommunication Network Contro and Management (EE E694) Prof. A. A. Lazar Notes for the ecture of 7/Feb/95 by Huayan Wang (this document was ast LaT E X-ed on May 9,995) Queueing Primer for Muticass Optima
In-plane shear stiffness of bare steel deck through shell finite element models. G. Bian, B.W. Schafer. June 2017
 In-pane shear stiffness of bare stee deck through she finite eement modes G. Bian, B.W. Schafer June 7 COLD-FORMED STEEL RESEARCH CONSORTIUM REPORT SERIES CFSRC R-7- SDII Stee Diaphragm Innovation Initiative
In-pane shear stiffness of bare stee deck through she finite eement modes G. Bian, B.W. Schafer June 7 COLD-FORMED STEEL RESEARCH CONSORTIUM REPORT SERIES CFSRC R-7- SDII Stee Diaphragm Innovation Initiative
Explicit overall risk minimization transductive bound
 1 Expicit overa risk minimization transductive bound Sergio Decherchi, Paoo Gastado, Sandro Ridea, Rodofo Zunino Dept. of Biophysica and Eectronic Engineering (DIBE), Genoa University Via Opera Pia 11a,
1 Expicit overa risk minimization transductive bound Sergio Decherchi, Paoo Gastado, Sandro Ridea, Rodofo Zunino Dept. of Biophysica and Eectronic Engineering (DIBE), Genoa University Via Opera Pia 11a,
Maximizing Sum Rate and Minimizing MSE on Multiuser Downlink: Optimality, Fast Algorithms and Equivalence via Max-min SIR
 1 Maximizing Sum Rate and Minimizing MSE on Mutiuser Downink: Optimaity, Fast Agorithms and Equivaence via Max-min SIR Chee Wei Tan 1,2, Mung Chiang 2 and R. Srikant 3 1 Caifornia Institute of Technoogy,
1 Maximizing Sum Rate and Minimizing MSE on Mutiuser Downink: Optimaity, Fast Agorithms and Equivaence via Max-min SIR Chee Wei Tan 1,2, Mung Chiang 2 and R. Srikant 3 1 Caifornia Institute of Technoogy,
Stochastic Complement Analysis of Multi-Server Threshold Queues. with Hysteresis. Abstract
 Stochastic Compement Anaysis of Muti-Server Threshod Queues with Hysteresis John C.S. Lui The Dept. of Computer Science & Engineering The Chinese University of Hong Kong Leana Goubchik Dept. of Computer
Stochastic Compement Anaysis of Muti-Server Threshod Queues with Hysteresis John C.S. Lui The Dept. of Computer Science & Engineering The Chinese University of Hong Kong Leana Goubchik Dept. of Computer
Stochastic Variational Inference with Gradient Linearization
 Stochastic Variationa Inference with Gradient Linearization Suppementa Materia Tobias Pötz * Anne S Wannenwetsch Stefan Roth Department of Computer Science, TU Darmstadt Preface In this suppementa materia,
Stochastic Variationa Inference with Gradient Linearization Suppementa Materia Tobias Pötz * Anne S Wannenwetsch Stefan Roth Department of Computer Science, TU Darmstadt Preface In this suppementa materia,
18-660: Numerical Methods for Engineering Design and Optimization
 8-660: Numerica Methods for Engineering esign and Optimization in i epartment of ECE Carnegie Meon University Pittsburgh, PA 523 Side Overview Conjugate Gradient Method (Part 4) Pre-conditioning Noninear
8-660: Numerica Methods for Engineering esign and Optimization in i epartment of ECE Carnegie Meon University Pittsburgh, PA 523 Side Overview Conjugate Gradient Method (Part 4) Pre-conditioning Noninear
Schedulability Analysis of Deferrable Scheduling Algorithms for Maintaining Real-Time Data Freshness
 1 Scheduabiity Anaysis of Deferrabe Scheduing Agorithms for Maintaining Rea-Time Data Freshness Song Han, Deji Chen, Ming Xiong, Kam-yiu Lam, Aoysius K. Mok, Krithi Ramamritham UT Austin, Emerson Process
1 Scheduabiity Anaysis of Deferrabe Scheduing Agorithms for Maintaining Rea-Time Data Freshness Song Han, Deji Chen, Ming Xiong, Kam-yiu Lam, Aoysius K. Mok, Krithi Ramamritham UT Austin, Emerson Process
Centralized Coded Caching of Correlated Contents
 Centraized Coded Caching of Correated Contents Qianqian Yang and Deniz Gündüz Information Processing and Communications Lab Department of Eectrica and Eectronic Engineering Imperia Coege London arxiv:1711.03798v1
Centraized Coded Caching of Correated Contents Qianqian Yang and Deniz Gündüz Information Processing and Communications Lab Department of Eectrica and Eectronic Engineering Imperia Coege London arxiv:1711.03798v1
Unconditional security of differential phase shift quantum key distribution
 Unconditiona security of differentia phase shift quantum key distribution Kai Wen, Yoshihisa Yamamoto Ginzton Lab and Dept of Eectrica Engineering Stanford University Basic idea of DPS-QKD Protoco. Aice
Unconditiona security of differentia phase shift quantum key distribution Kai Wen, Yoshihisa Yamamoto Ginzton Lab and Dept of Eectrica Engineering Stanford University Basic idea of DPS-QKD Protoco. Aice
The Binary Space Partitioning-Tree Process Supplementary Material
 The inary Space Partitioning-Tree Process Suppementary Materia Xuhui Fan in Li Scott. Sisson Schoo of omputer Science Fudan University ibin@fudan.edu.cn Schoo of Mathematics and Statistics University of
The inary Space Partitioning-Tree Process Suppementary Materia Xuhui Fan in Li Scott. Sisson Schoo of omputer Science Fudan University ibin@fudan.edu.cn Schoo of Mathematics and Statistics University of
(This is a sample cover image for this issue. The actual cover is not yet available at this time.)
 (This is a sampe cover image for this issue The actua cover is not yet avaiabe at this time) This artice appeared in a journa pubished by Esevier The attached copy is furnished to the author for interna
(This is a sampe cover image for this issue The actua cover is not yet avaiabe at this time) This artice appeared in a journa pubished by Esevier The attached copy is furnished to the author for interna
T.C. Banwell, S. Galli. {bct, Telcordia Technologies, Inc., 445 South Street, Morristown, NJ 07960, USA
 ON THE SYMMETRY OF THE POWER INE CHANNE T.C. Banwe, S. Gai {bct, sgai}@research.tecordia.com Tecordia Technoogies, Inc., 445 South Street, Morristown, NJ 07960, USA Abstract The indoor power ine network
ON THE SYMMETRY OF THE POWER INE CHANNE T.C. Banwe, S. Gai {bct, sgai}@research.tecordia.com Tecordia Technoogies, Inc., 445 South Street, Morristown, NJ 07960, USA Abstract The indoor power ine network
Recursive Constructions of Parallel FIFO and LIFO Queues with Switched Delay Lines
 Recursive Constructions of Parae FIFO and LIFO Queues with Switched Deay Lines Po-Kai Huang, Cheng-Shang Chang, Feow, IEEE, Jay Cheng, Member, IEEE, and Duan-Shin Lee, Senior Member, IEEE Abstract One
Recursive Constructions of Parae FIFO and LIFO Queues with Switched Deay Lines Po-Kai Huang, Cheng-Shang Chang, Feow, IEEE, Jay Cheng, Member, IEEE, and Duan-Shin Lee, Senior Member, IEEE Abstract One
2-loop additive mass renormalization with clover fermions and Symanzik improved gluons
 2-oop additive mass renormaization with cover fermions and Symanzik improved guons Apostoos Skouroupathis Department of Physics, University of Cyprus, Nicosia, CY-1678, Cyprus E-mai: php4as01@ucy.ac.cy
2-oop additive mass renormaization with cover fermions and Symanzik improved guons Apostoos Skouroupathis Department of Physics, University of Cyprus, Nicosia, CY-1678, Cyprus E-mai: php4as01@ucy.ac.cy
Stat 155 Game theory, Yuval Peres Fall Lectures 4,5,6
 Stat 155 Game theory, Yuva Peres Fa 2004 Lectures 4,5,6 In the ast ecture, we defined N and P positions for a combinatoria game. We wi now show more formay that each starting position in a combinatoria
Stat 155 Game theory, Yuva Peres Fa 2004 Lectures 4,5,6 In the ast ecture, we defined N and P positions for a combinatoria game. We wi now show more formay that each starting position in a combinatoria
MONTE CARLO SIMULATIONS
 MONTE CARLO SIMULATIONS Current physics research 1) Theoretica 2) Experimenta 3) Computationa Monte Caro (MC) Method (1953) used to study 1) Discrete spin systems 2) Fuids 3) Poymers, membranes, soft matter
MONTE CARLO SIMULATIONS Current physics research 1) Theoretica 2) Experimenta 3) Computationa Monte Caro (MC) Method (1953) used to study 1) Discrete spin systems 2) Fuids 3) Poymers, membranes, soft matter
Schedulability Analysis of Deferrable Scheduling Algorithms for Maintaining Real-Time Data Freshness
 1 Scheduabiity Anaysis of Deferrabe Scheduing Agorithms for Maintaining Rea- Data Freshness Song Han, Deji Chen, Ming Xiong, Kam-yiu Lam, Aoysius K. Mok, Krithi Ramamritham UT Austin, Emerson Process Management,
1 Scheduabiity Anaysis of Deferrabe Scheduing Agorithms for Maintaining Rea- Data Freshness Song Han, Deji Chen, Ming Xiong, Kam-yiu Lam, Aoysius K. Mok, Krithi Ramamritham UT Austin, Emerson Process Management,
DIGITAL FILTER DESIGN OF IIR FILTERS USING REAL VALUED GENETIC ALGORITHM
 DIGITAL FILTER DESIGN OF IIR FILTERS USING REAL VALUED GENETIC ALGORITHM MIKAEL NILSSON, MATTIAS DAHL AND INGVAR CLAESSON Bekinge Institute of Technoogy Department of Teecommunications and Signa Processing
DIGITAL FILTER DESIGN OF IIR FILTERS USING REAL VALUED GENETIC ALGORITHM MIKAEL NILSSON, MATTIAS DAHL AND INGVAR CLAESSON Bekinge Institute of Technoogy Department of Teecommunications and Signa Processing
Algorithms to solve massively under-defined systems of multivariate quadratic equations
 Agorithms to sove massivey under-defined systems of mutivariate quadratic equations Yasufumi Hashimoto Abstract It is we known that the probem to sove a set of randomy chosen mutivariate quadratic equations
Agorithms to sove massivey under-defined systems of mutivariate quadratic equations Yasufumi Hashimoto Abstract It is we known that the probem to sove a set of randomy chosen mutivariate quadratic equations
Melodic contour estimation with B-spline models using a MDL criterion
 Meodic contour estimation with B-spine modes using a MDL criterion Damien Loive, Ney Barbot, Oivier Boeffard IRISA / University of Rennes 1 - ENSSAT 6 rue de Kerampont, B.P. 80518, F-305 Lannion Cedex
Meodic contour estimation with B-spine modes using a MDL criterion Damien Loive, Ney Barbot, Oivier Boeffard IRISA / University of Rennes 1 - ENSSAT 6 rue de Kerampont, B.P. 80518, F-305 Lannion Cedex
Age of Information: The Gamma Awakening
 Age of Information: The Gamma Awakening Eie Najm and Rajai Nasser LTHI, EPFL, Lausanne, Switzerand Emai: {eie.najm, rajai.nasser}@epf.ch arxiv:604.086v [cs.it] 5 Apr 06 Abstract Status update systems is
Age of Information: The Gamma Awakening Eie Najm and Rajai Nasser LTHI, EPFL, Lausanne, Switzerand Emai: {eie.najm, rajai.nasser}@epf.ch arxiv:604.086v [cs.it] 5 Apr 06 Abstract Status update systems is
Introduction to Simulation - Lecture 13. Convergence of Multistep Methods. Jacob White. Thanks to Deepak Ramaswamy, Michal Rewienski, and Karen Veroy
 Introduction to Simuation - Lecture 13 Convergence of Mutistep Methods Jacob White Thans to Deepa Ramaswamy, Micha Rewiensi, and Karen Veroy Outine Sma Timestep issues for Mutistep Methods Loca truncation
Introduction to Simuation - Lecture 13 Convergence of Mutistep Methods Jacob White Thans to Deepa Ramaswamy, Micha Rewiensi, and Karen Veroy Outine Sma Timestep issues for Mutistep Methods Loca truncation
(f) is called a nearly holomorphic modular form of weight k + 2r as in [5].
![(f) is called a nearly holomorphic modular form of weight k + 2r as in [5]. (f) is called a nearly holomorphic modular form of weight k + 2r as in [5].](/thumbs/77/75192090.jpg) PRODUCTS OF NEARLY HOLOMORPHIC EIGENFORMS JEFFREY BEYERL, KEVIN JAMES, CATHERINE TRENTACOSTE, AND HUI XUE Abstract. We prove that the product of two neary hoomorphic Hece eigenforms is again a Hece eigenform
PRODUCTS OF NEARLY HOLOMORPHIC EIGENFORMS JEFFREY BEYERL, KEVIN JAMES, CATHERINE TRENTACOSTE, AND HUI XUE Abstract. We prove that the product of two neary hoomorphic Hece eigenforms is again a Hece eigenform
A Fundamental Storage-Communication Tradeoff in Distributed Computing with Straggling Nodes
 A Fundamenta Storage-Communication Tradeoff in Distributed Computing with Stragging odes ifa Yan, Michèe Wigger LTCI, Téécom ParisTech 75013 Paris, France Emai: {qifa.yan, michee.wigger} @teecom-paristech.fr
A Fundamenta Storage-Communication Tradeoff in Distributed Computing with Stragging odes ifa Yan, Michèe Wigger LTCI, Téécom ParisTech 75013 Paris, France Emai: {qifa.yan, michee.wigger} @teecom-paristech.fr
CS 331: Artificial Intelligence Propositional Logic 2. Review of Last Time
 CS 33 Artificia Inteigence Propositiona Logic 2 Review of Last Time = means ogicay foows - i means can be derived from If your inference agorithm derives ony things that foow ogicay from the KB, the inference
CS 33 Artificia Inteigence Propositiona Logic 2 Review of Last Time = means ogicay foows - i means can be derived from If your inference agorithm derives ony things that foow ogicay from the KB, the inference
STA 216 Project: Spline Approach to Discrete Survival Analysis
 : Spine Approach to Discrete Surviva Anaysis November 4, 005 1 Introduction Athough continuous surviva anaysis differs much from the discrete surviva anaysis, there is certain ink between the two modeing
: Spine Approach to Discrete Surviva Anaysis November 4, 005 1 Introduction Athough continuous surviva anaysis differs much from the discrete surviva anaysis, there is certain ink between the two modeing
C. Fourier Sine Series Overview
 12 PHILIP D. LOEWEN C. Fourier Sine Series Overview Let some constant > be given. The symboic form of the FSS Eigenvaue probem combines an ordinary differentia equation (ODE) on the interva (, ) with a
12 PHILIP D. LOEWEN C. Fourier Sine Series Overview Let some constant > be given. The symboic form of the FSS Eigenvaue probem combines an ordinary differentia equation (ODE) on the interva (, ) with a
Trapping Set Enumerators for Repeat Multiple Accumulate Code Ensembles
 Trapping Set Enumerators for Repeat Mutipe Accumuate Code Ensembes Christian Koer, Aexandre Grae i Amat, Jörg Kiewer, and Danie J. Costeo, Jr. Department of Eectrica Engineering, University of Notre Dame,
Trapping Set Enumerators for Repeat Mutipe Accumuate Code Ensembes Christian Koer, Aexandre Grae i Amat, Jörg Kiewer, and Danie J. Costeo, Jr. Department of Eectrica Engineering, University of Notre Dame,
Limits on Support Recovery with Probabilistic Models: An Information-Theoretic Framework
 Limits on Support Recovery with Probabiistic Modes: An Information-Theoretic Framewor Jonathan Scarett and Voan Cevher arxiv:5.744v3 cs.it 3 Aug 6 Abstract The support recovery probem consists of determining
Limits on Support Recovery with Probabiistic Modes: An Information-Theoretic Framewor Jonathan Scarett and Voan Cevher arxiv:5.744v3 cs.it 3 Aug 6 Abstract The support recovery probem consists of determining
arxiv:quant-ph/ v3 6 Jan 1995
 arxiv:quant-ph/9501001v3 6 Jan 1995 Critique of proposed imit to space time measurement, based on Wigner s cocks and mirrors L. Diósi and B. Lukács KFKI Research Institute for Partice and Nucear Physics
arxiv:quant-ph/9501001v3 6 Jan 1995 Critique of proposed imit to space time measurement, based on Wigner s cocks and mirrors L. Diósi and B. Lukács KFKI Research Institute for Partice and Nucear Physics
Control Chart For Monitoring Nonparametric Profiles With Arbitrary Design
 Contro Chart For Monitoring Nonparametric Profies With Arbitrary Design Peihua Qiu 1 and Changiang Zou 2 1 Schoo of Statistics, University of Minnesota, USA 2 LPMC and Department of Statistics, Nankai
Contro Chart For Monitoring Nonparametric Profies With Arbitrary Design Peihua Qiu 1 and Changiang Zou 2 1 Schoo of Statistics, University of Minnesota, USA 2 LPMC and Department of Statistics, Nankai
Supporting Information for Suppressing Klein tunneling in graphene using a one-dimensional array of localized scatterers
 Supporting Information for Suppressing Kein tunneing in graphene using a one-dimensiona array of ocaized scatterers Jamie D Was, and Danie Hadad Department of Chemistry, University of Miami, Cora Gabes,
Supporting Information for Suppressing Kein tunneing in graphene using a one-dimensiona array of ocaized scatterers Jamie D Was, and Danie Hadad Department of Chemistry, University of Miami, Cora Gabes,
HYDROGEN ATOM SELECTION RULES TRANSITION RATES
 DOING PHYSICS WITH MATLAB QUANTUM PHYSICS Ian Cooper Schoo of Physics, University of Sydney ian.cooper@sydney.edu.au HYDROGEN ATOM SELECTION RULES TRANSITION RATES DOWNLOAD DIRECTORY FOR MATLAB SCRIPTS
DOING PHYSICS WITH MATLAB QUANTUM PHYSICS Ian Cooper Schoo of Physics, University of Sydney ian.cooper@sydney.edu.au HYDROGEN ATOM SELECTION RULES TRANSITION RATES DOWNLOAD DIRECTORY FOR MATLAB SCRIPTS
BP neural network-based sports performance prediction model applied research
 Avaiabe onine www.jocpr.com Journa of Chemica and Pharmaceutica Research, 204, 6(7:93-936 Research Artice ISSN : 0975-7384 CODEN(USA : JCPRC5 BP neura networ-based sports performance prediction mode appied
Avaiabe onine www.jocpr.com Journa of Chemica and Pharmaceutica Research, 204, 6(7:93-936 Research Artice ISSN : 0975-7384 CODEN(USA : JCPRC5 BP neura networ-based sports performance prediction mode appied
Statistical Learning Theory: A Primer
 Internationa Journa of Computer Vision 38(), 9 3, 2000 c 2000 uwer Academic Pubishers. Manufactured in The Netherands. Statistica Learning Theory: A Primer THEODOROS EVGENIOU, MASSIMILIANO PONTIL AND TOMASO
Internationa Journa of Computer Vision 38(), 9 3, 2000 c 2000 uwer Academic Pubishers. Manufactured in The Netherands. Statistica Learning Theory: A Primer THEODOROS EVGENIOU, MASSIMILIANO PONTIL AND TOMASO
Primal and dual active-set methods for convex quadratic programming
 Math. Program., Ser. A 216) 159:469 58 DOI 1.17/s117-15-966-2 FULL LENGTH PAPER Prima and dua active-set methods for convex quadratic programming Anders Forsgren 1 Phiip E. Gi 2 Eizabeth Wong 2 Received:
Math. Program., Ser. A 216) 159:469 58 DOI 1.17/s117-15-966-2 FULL LENGTH PAPER Prima and dua active-set methods for convex quadratic programming Anders Forsgren 1 Phiip E. Gi 2 Eizabeth Wong 2 Received:
Random maps and attractors in random Boolean networks
 LU TP 04-43 Rom maps attractors in rom Booean networks Björn Samuesson Car Troein Compex Systems Division, Department of Theoretica Physics Lund University, Sövegatan 4A, S-3 6 Lund, Sweden Dated: 005-05-07)
LU TP 04-43 Rom maps attractors in rom Booean networks Björn Samuesson Car Troein Compex Systems Division, Department of Theoretica Physics Lund University, Sövegatan 4A, S-3 6 Lund, Sweden Dated: 005-05-07)
Precoding for the Sparsely Spread MC-CDMA Downlink with Discrete-Alphabet Inputs
 IEEE TRANSACTIONS ON VEHICULAR TECHNOLOGY, VOL.*, NO.*, MONTH 2016 1 Precoding for the Sparsey Spread MC-CDMA Downin with Discrete-Aphabet Inputs Min Li, Member, IEEE, Chunshan Liu, Member, IEEE, and Stephen
IEEE TRANSACTIONS ON VEHICULAR TECHNOLOGY, VOL.*, NO.*, MONTH 2016 1 Precoding for the Sparsey Spread MC-CDMA Downin with Discrete-Aphabet Inputs Min Li, Member, IEEE, Chunshan Liu, Member, IEEE, and Stephen
The EM Algorithm applied to determining new limit points of Mahler measures
 Contro and Cybernetics vo. 39 (2010) No. 4 The EM Agorithm appied to determining new imit points of Maher measures by Souad E Otmani, Georges Rhin and Jean-Marc Sac-Épée Université Pau Veraine-Metz, LMAM,
Contro and Cybernetics vo. 39 (2010) No. 4 The EM Agorithm appied to determining new imit points of Maher measures by Souad E Otmani, Georges Rhin and Jean-Marc Sac-Épée Université Pau Veraine-Metz, LMAM,
Target Location Estimation in Wireless Sensor Networks Using Binary Data
 Target Location stimation in Wireess Sensor Networks Using Binary Data Ruixin Niu and Pramod K. Varshney Department of ectrica ngineering and Computer Science Link Ha Syracuse University Syracuse, NY 344
Target Location stimation in Wireess Sensor Networks Using Binary Data Ruixin Niu and Pramod K. Varshney Department of ectrica ngineering and Computer Science Link Ha Syracuse University Syracuse, NY 344
Article An Efficient Method to Construct Parity-Check Matrices for Recursively Encoding Spatially Coupled LDPC Codes
 entropy Artice An Efficient Method to Construct Parity-Check Matrices for Recursivey Encoding Spatiay Couped LDPC Codes Zhongwei Si, Sijie Wang and Junyang Ma Key Laboratory of Universa Wireess Communications,
entropy Artice An Efficient Method to Construct Parity-Check Matrices for Recursivey Encoding Spatiay Couped LDPC Codes Zhongwei Si, Sijie Wang and Junyang Ma Key Laboratory of Universa Wireess Communications,
Scalable Spectrum Allocation for Large Networks Based on Sparse Optimization
 Scaabe Spectrum ocation for Large Networks ased on Sparse Optimization innan Zhuang Modem R&D Lab Samsung Semiconductor, Inc. San Diego, C Dongning Guo, Ermin Wei, and Michae L. Honig Department of Eectrica
Scaabe Spectrum ocation for Large Networks ased on Sparse Optimization innan Zhuang Modem R&D Lab Samsung Semiconductor, Inc. San Diego, C Dongning Guo, Ermin Wei, and Michae L. Honig Department of Eectrica
Uniformly Reweighted Belief Propagation: A Factor Graph Approach
 Uniformy Reweighted Beief Propagation: A Factor Graph Approach Henk Wymeersch Chamers University of Technoogy Gothenburg, Sweden henkw@chamers.se Federico Penna Poitecnico di Torino Torino, Itay federico.penna@poito.it
Uniformy Reweighted Beief Propagation: A Factor Graph Approach Henk Wymeersch Chamers University of Technoogy Gothenburg, Sweden henkw@chamers.se Federico Penna Poitecnico di Torino Torino, Itay federico.penna@poito.it
Improving the Accuracy of Boolean Tomography by Exploiting Path Congestion Degrees
 Improving the Accuracy of Booean Tomography by Expoiting Path Congestion Degrees Zhiyong Zhang, Gaoei Fei, Fucai Yu, Guangmin Hu Schoo of Communication and Information Engineering, University of Eectronic
Improving the Accuracy of Booean Tomography by Expoiting Path Congestion Degrees Zhiyong Zhang, Gaoei Fei, Fucai Yu, Guangmin Hu Schoo of Communication and Information Engineering, University of Eectronic
Tracking Control of Multiple Mobile Robots
 Proceedings of the 2001 IEEE Internationa Conference on Robotics & Automation Seou, Korea May 21-26, 2001 Tracking Contro of Mutipe Mobie Robots A Case Study of Inter-Robot Coision-Free Probem Jurachart
Proceedings of the 2001 IEEE Internationa Conference on Robotics & Automation Seou, Korea May 21-26, 2001 Tracking Contro of Mutipe Mobie Robots A Case Study of Inter-Robot Coision-Free Probem Jurachart
TitleCryptanalysis of the Quaternion Rai. IEICE Transactions on Fundamentals.
 TiteCryptanaysis of the Quaternion Rai Author(s Hashimoto, Yasufumi Citation IEICE Transactions on Fundamentas Communications and Computer Science Issue Date 205-0-0 URL http://hd.hande.net/20.500.2000/
TiteCryptanaysis of the Quaternion Rai Author(s Hashimoto, Yasufumi Citation IEICE Transactions on Fundamentas Communications and Computer Science Issue Date 205-0-0 URL http://hd.hande.net/20.500.2000/
Componentwise Determination of the Interval Hull Solution for Linear Interval Parameter Systems
 Componentwise Determination of the Interva Hu Soution for Linear Interva Parameter Systems L. V. Koev Dept. of Theoretica Eectrotechnics, Facuty of Automatics, Technica University of Sofia, 1000 Sofia,
Componentwise Determination of the Interva Hu Soution for Linear Interva Parameter Systems L. V. Koev Dept. of Theoretica Eectrotechnics, Facuty of Automatics, Technica University of Sofia, 1000 Sofia,
arxiv: v2 [cond-mat.stat-mech] 14 Nov 2008
![arxiv: v2 [cond-mat.stat-mech] 14 Nov 2008 arxiv: v2 [cond-mat.stat-mech] 14 Nov 2008](/thumbs/74/70733902.jpg) Random Booean Networks Barbara Drosse Institute of Condensed Matter Physics, Darmstadt University of Technoogy, Hochschustraße 6, 64289 Darmstadt, Germany (Dated: June 27) arxiv:76.335v2 [cond-mat.stat-mech]
Random Booean Networks Barbara Drosse Institute of Condensed Matter Physics, Darmstadt University of Technoogy, Hochschustraße 6, 64289 Darmstadt, Germany (Dated: June 27) arxiv:76.335v2 [cond-mat.stat-mech]
A proposed nonparametric mixture density estimation using B-spline functions
 A proposed nonparametric mixture density estimation using B-spine functions Atizez Hadrich a,b, Mourad Zribi a, Afif Masmoudi b a Laboratoire d Informatique Signa et Image de a Côte d Opae (LISIC-EA 4491),
A proposed nonparametric mixture density estimation using B-spine functions Atizez Hadrich a,b, Mourad Zribi a, Afif Masmoudi b a Laboratoire d Informatique Signa et Image de a Côte d Opae (LISIC-EA 4491),
K a,k minors in graphs of bounded tree-width *
 K a,k minors in graphs of bounded tree-width * Thomas Böhme Institut für Mathematik Technische Universität Imenau Imenau, Germany E-mai: tboehme@theoinf.tu-imenau.de and John Maharry Department of Mathematics
K a,k minors in graphs of bounded tree-width * Thomas Böhme Institut für Mathematik Technische Universität Imenau Imenau, Germany E-mai: tboehme@theoinf.tu-imenau.de and John Maharry Department of Mathematics
Data Mining Technology for Failure Prognostic of Avionics
 IEEE Transactions on Aerospace and Eectronic Systems. Voume 38, #, pp.388-403, 00. Data Mining Technoogy for Faiure Prognostic of Avionics V.A. Skormin, Binghamton University, Binghamton, NY, 1390, USA
IEEE Transactions on Aerospace and Eectronic Systems. Voume 38, #, pp.388-403, 00. Data Mining Technoogy for Faiure Prognostic of Avionics V.A. Skormin, Binghamton University, Binghamton, NY, 1390, USA
From Margins to Probabilities in Multiclass Learning Problems
 From Margins to Probabiities in Muticass Learning Probems Andrea Passerini and Massimiiano Ponti 2 and Paoo Frasconi 3 Abstract. We study the probem of muticass cassification within the framework of error
From Margins to Probabiities in Muticass Learning Probems Andrea Passerini and Massimiiano Ponti 2 and Paoo Frasconi 3 Abstract. We study the probem of muticass cassification within the framework of error
A Novel Learning Method for Elman Neural Network Using Local Search
 Neura Information Processing Letters and Reviews Vo. 11, No. 8, August 2007 LETTER A Nove Learning Method for Eman Neura Networ Using Loca Search Facuty of Engineering, Toyama University, Gofuu 3190 Toyama
Neura Information Processing Letters and Reviews Vo. 11, No. 8, August 2007 LETTER A Nove Learning Method for Eman Neura Networ Using Loca Search Facuty of Engineering, Toyama University, Gofuu 3190 Toyama
Applied Nuclear Physics (Fall 2006) Lecture 7 (10/2/06) Overview of Cross Section Calculation
 22.101 Appied Nucear Physics (Fa 2006) Lecture 7 (10/2/06) Overview of Cross Section Cacuation References P. Roman, Advanced Quantum Theory (Addison-Wesey, Reading, 1965), Chap 3. A. Foderaro, The Eements
22.101 Appied Nucear Physics (Fa 2006) Lecture 7 (10/2/06) Overview of Cross Section Cacuation References P. Roman, Advanced Quantum Theory (Addison-Wesey, Reading, 1965), Chap 3. A. Foderaro, The Eements
High Spectral Resolution Infrared Radiance Modeling Using Optimal Spectral Sampling (OSS) Method
 High Spectra Resoution Infrared Radiance Modeing Using Optima Spectra Samping (OSS) Method J.-L. Moncet and G. Uymin Background Optima Spectra Samping (OSS) method is a fast and accurate monochromatic
High Spectra Resoution Infrared Radiance Modeing Using Optima Spectra Samping (OSS) Method J.-L. Moncet and G. Uymin Background Optima Spectra Samping (OSS) method is a fast and accurate monochromatic
6.434J/16.391J Statistics for Engineers and Scientists May 4 MIT, Spring 2006 Handout #17. Solution 7
 6.434J/16.391J Statistics for Engineers and Scientists May 4 MIT, Spring 2006 Handout #17 Soution 7 Probem 1: Generating Random Variabes Each part of this probem requires impementation in MATLAB. For the
6.434J/16.391J Statistics for Engineers and Scientists May 4 MIT, Spring 2006 Handout #17 Soution 7 Probem 1: Generating Random Variabes Each part of this probem requires impementation in MATLAB. For the
Efficient Similarity Search across Top-k Lists under the Kendall s Tau Distance
 Efficient Simiarity Search across Top-k Lists under the Kenda s Tau Distance Koninika Pa TU Kaisersautern Kaisersautern, Germany pa@cs.uni-k.de Sebastian Miche TU Kaisersautern Kaisersautern, Germany smiche@cs.uni-k.de
Efficient Simiarity Search across Top-k Lists under the Kenda s Tau Distance Koninika Pa TU Kaisersautern Kaisersautern, Germany pa@cs.uni-k.de Sebastian Miche TU Kaisersautern Kaisersautern, Germany smiche@cs.uni-k.de
SASIMI: Sparsity-Aware Simulation of Interconnect-Dominated Circuits with Non-Linear Devices
 SASIMI: Sparsity-Aware Simuation of Interconnect-Dominated Circuits with Non-Linear Devices Jitesh Jain, Stephen Cauey, Cheng-Kok Koh, and Venkataramanan Baakrishnan Schoo of Eectrica and Computer Engineering
SASIMI: Sparsity-Aware Simuation of Interconnect-Dominated Circuits with Non-Linear Devices Jitesh Jain, Stephen Cauey, Cheng-Kok Koh, and Venkataramanan Baakrishnan Schoo of Eectrica and Computer Engineering
Math 124B January 31, 2012
 Math 124B January 31, 212 Viktor Grigoryan 7 Inhomogeneous boundary vaue probems Having studied the theory of Fourier series, with which we successfuy soved boundary vaue probems for the homogeneous heat
Math 124B January 31, 212 Viktor Grigoryan 7 Inhomogeneous boundary vaue probems Having studied the theory of Fourier series, with which we successfuy soved boundary vaue probems for the homogeneous heat
