Markov Lie Monoid Entropies as Network Metrics Joseph E. Johnson, PhD University of South Carolina
|
|
|
- Shanon McKenzie
- 5 years ago
- Views:
Transcription
1 Markov Lie Monoid Entropies as Network Metrics Joseph E. Johnson, PhD University of South Carolina A network of N nodes can be exactly described by a matrix of N 2 N non-negative off-diagonal values representing the connection weights among the N nodes. When a network is large and changing every second such as the Internet, then the resulting system has tens of millions of values every second. We have found a method for reducing this vast data into a few (2N and fewer) representative values (network entropy spectral functions, or metrics) in order to track the changing topology for attacks, failures and malicious processes. Our previous work showed that the general linear group, of transformations that are continuously connected to the identity in n dimensions GL(n,R), can be decomposed into two Lie groups 1 : (1) an n(n-1)-dimensional Markov-type Lie group M(n) that is defined by preserving the sum of the components of a vector, and (2) the n- dimensional Abelian Lie group, A(n), of scaling transformations of the coordinates. With the restriction of the Markov-type Lie algebra parameters to non-negative values, one obtains exactly all Markov transformations in n dimensions that are continuously connected to the identity. More precisely, this system is now a Markov Monoid (MM) as it is a group without an inverse. In our current work we show that every network, as defined by its connection matrix C ij, is in one to one correspondence to a single 1
2 element of the MM Lie algebra of the same dimensionality. It follows that any network matrix, C, is the generator of a continuous Markov transformation that can be interpreted as producing an irreversible flow of a conserved substance among the nodes of the corresponding network. The exponentiation of the MM algebra provides a continuous transformation with rows and columns that constitute normed probability distributions that encapsulate the topology of the network in all orders of expansion. This allows Shannon and generalized (Renyi) entropy functions to be defined on the column and row probability distributions. These (2N) generalized entropies (along with derivatives and functions of these entropies) for these Markov transformations become metrics for the topology of the corresponding network encapsulating all of the network topology in a more hierarchical way. Thus we have tightly connected the fields of Lie groups and algebras, Markov transformations, conserved flows, diffusion transformations, and generalized entropies, on the one hand, to network theory and network topology. We are specifically interested in applying these generalized entropies as metrics for the tracking of network topological changes such as one would expect under attacks and intrusions on internets. We will show our experimental results of monitoring these entropy spectral distributions using two internet tracking applications. 1 Introduction There is a broad spectrum of mathematical problems that involve the general theory of networks and the associated classification, optimization, and potentially even their dynamical evolution. By a network we mean a set of n nodes (points), some pairs of which are connected with a representative non-negative weight or strength of connection. Such a network can be represented by a connection (or connectivity, or adjancy) matrix C ij whose off-diagonal elements give the non-negative strength of the connection between nodes i and j in the network. Often that strength or weight is as simple as a 1 for a connection and a 0 otherwise. A network can be undirected or directed depending upon whether C ij is symmetric or not thus indicating respectively a symmetric or asymmetrical connection between i and j. There may or may not exist a metric distance 2
3 between the nodes or, equivalently, positions for the points in a metric space of some dimensionality, such as airports for airline networks, or substations for power or utility distribution networks. It is well known that the classification of different network topologies cannot be accomplished with just the eigenvalue spectra of the connectivity matrix as there are topologically different networks with as few as five nodes that have the same eigenvalue spectra. One root of the network problem is that although the network is exactly defined by the C matrix, there are n! different C matrices that correspond to the same topology because different C matrices result from different nodal numbering orders. Most network problems become computationally intractable for more than a few hundred nodes. The essential point here is that the n(n-1) off-diagonal non-negative values of C uniquely define a network. The n column values are arbitrary at this point and are undefined. We are interested in seeking useful metrics (functions of the C matrix) for the description of the topology of large networks such as sub-nets of the internet which might have from a hundred to a million nodes, and thus perhaps a trillion connection matrix values. To be useful, the metrics must be (a) rapidly computable (as compared to eigenvalue computations), (b) intuitively meaningful, (c) should holistically summarize the underlying topology with a few variables, (d) ideally would offer meaningful hierarchical expansions providing increasing levels of topological detail and (e) these metrics should be invariant under the permutation group on node numbering and thus reflect the intrinsic topology. We are specifically interested in the information flows of which originating node sends data to which destination node; and we are not initially interested in the underlying physical connectivity topology itself nor are we interested in the specific path which the information traverses nor associated distance metrics. Internet transmissions are extremely dynamic and thus to achieve some form of continuity, we envision constructing the C matrix using a summation of information transfers, or weights, over some time window t-δ/2 to t+δ/2, surrounding a time t as C(t, δ) thus representing the time evolution of the connection matrix. Given the number of connections, this problem resembles the representation of a physical gas in terms of thermodynamical variables 3
4 (such as temperature, volume, pressure, heat, and entropy). Generally, in such internet environments there is no meaningful location or position metric that gives insight into the topology and thus distance is not usefully defined. As such pressure and volume, do not have a clear meaning without a distance function. There is no general conserved quantity such as energy, and thus heat and temperature do not offer clear meanings. However, we will suggest below that the concept of entropy can be well defined and that it can be used to summarize the order and disorder in the underlying topological structure. Initially, how to define entropy on the connection matrix is not clear since both Shannon and Renyi entropies are defined as the log of the sum of the powers of the components of a vector, x i, representing probabilities: S = c log 2 (b(σx i a ) ) where Σ x i = 1 and where a, b, and c are constants. As such these entropies represent the disorder in the underlying probability distribution. The disorder is a maximum with an even probability distribution and is a minimum when all the probability is in one cell with others having a value of zero. But the connection matrix columns or rows cannot be used as probability distributions since the diagonal of C is totally arbitrary. Even if we make some arbitrary choice of the diagonal values of C and normalize the columns, it is not clear what underlying topological disorder we are measuring. Naturally one can take any set of non-negative numbers and normalize them to unity and compute the entropy of the distribution. But without an underlying mathematical and intuitive foundation for the meaning of this distribution it would follow that the resulting entropy calculation is likewise ambiguous. In this work, we utilize our past work on the decomposition of the general linear group in order to gain insight into how one might define these entropy metrics in useful ways that satisfy the requirements a-e above. Additionally we will utilize definitions of entropy (or equivalently information as negative entropy). The original argument by Shannon was that if the information of two independent systems is to be additive, and if the information is a function of the probability distribution, and since probabilities of independent systems is multiplicative, then it follows that information (or entropy) must be the log of a power of the probability. More precisely beginning with Shannon one has I = -log 2 (P) so that the probability P of a simple two 4
5 state system ( 1 or 0 ) is ½ for each thus giving I=1 bit of information. More generally with the work of Kolmogorov and Renyi one can consider a probability distribution x i among n cells (i=1,2, n) with Σx i =1 as I = a log 2 (n Σx i b ). In our work below, one can take any of the generalized Renyi entropies but we will choose a= 1 and b=2 giving I = log 2 (n Σx i 2 ). This can be shown to smoothly generalize the Shannon entropy as a boundary condition for two states. For example when x 1 = 1 and x 0 = 0 (or conversely) then n=2 and I = 1 for maximum information of one bit thus agreeing with Shannon. Then when there is equal probability and thus no information one has x 1 = x 0 = ½ thus I = 0. When a probability distribution is flat, the information function above becomes a minimum but when it peaks then the square of the probability becomes much larger and the information increases as the log of the sum of the squares of the values. In the following we will use information and entropy interchangeably as one is the negative of the other. 2 Background on Markov Lie Groups and Monoids We had previously shown 1 that the transformations in the general linear group in n dimensions, that are continuously connected to the identity, can be decomposed into two Lie groups: (1) an n(n-1) dimensional Markov type Lie group that is defined by preserving the sum of the components of a vector, and (2) the n dimensional Abelian Lie group, A(n), of scaling transformations of the coordinates. To construct the Markov type Lie group, consider the k,l matrix element of a matrix L ij as a basis for n x n matrices, with off-diagonal elements, as L ij kl = δ i k δ j l - δ j k δ j l with i =/= j. Thus the ij basis matrix has a 1 in position ij with a -1 in position jj on the diagonal. These n(n-1) matrices form a basis for the Lie algebra of all transformations that preserve the sum of the components of vector. With this particular choice of basis, we then showed that by restricting the parameter space to non-negative real values, λ ij >=0, one obtains exactly all Markov transformations in n dimensions that were continuously connected to the identity as M = exp (s λ ij L ij ) where we summarize over repeated indices and where s is a real parameter separated from λ ij to parameterize the continuous evolution of the transformation. In other words λ ij L ij consists of non-negative coefficients in a linear 5
6 combination of L ij matrics. This non-negativity restriction on the parameter space removed the group inverses and resulted in a continuous Markov monoid, MM(n), a group without an inverse, in n dimensions. The basis elements for the MM algebra is a complete basis for n x n matrices that are defined by their off-diagonal terms. The n dimensional Abelian scaling Lie algebra can be defined by L ii kl = δ i k δ i l thus consisting of a 1 on the i,i diagonal position. When exponentiated, A(s) = exp (s λ ii L ii ), this simply multiplies that coordinate by e s giving a scaling transformation. The Lie algebra that results from the sum of the Abelian and Markov Lie generators is sufficient to generate the entire general linear group that is connected to the identity. 3 Connecting Markov Monoids to Network Metrics We can begin with the simple observation that (1) since the nonnegative off diagonal elements of an n x n matrix exactly define a network (via C) and its topology with that node numbering, and (2) since a Markov monoid basis is complete in spanning all off-diagonal n x n matrices, then it follows that such networks are in one to one correspondence with the elements of the Markov monoids. The Lie Markov matrix that results is exactly the C matrix where the diagonal elements are set equal to the negative of the sum of all other elements in that column. Thus each such altered connection matrix is the infinitesimal generator of a continuous Markov transformation and conversely. This observation connects networks and their topology with the Lie groups and algebras and Markov transformations in a unique way. Since the Markov generators must have the diagonal elements set to the negative of the sum of the other elements in that column, this requirement fixes the otherwise arbitrary diagonal of the connection matrix to that value also (sometimes referred to as the Lagrangian) It now follows that this diagonal setting of C generates a Markov transformation by M= e λc. One recalls that the action of a Markov matrix on a vector of probabilities (an n-dimensional set of nonnegative real values whose sum is unity), will map that vector again 6
7 into such a vector (non-negative values with unit sum). The next observation is that by taking λ as infinitesimal, than one can write M = I + λc by ignoring higher order infinitesimals. Here one sees that the value or weight of the connection matrix between two nodes, gives the M matrix element as the relative infinitesimal transition rate between those two components of the vector. Thus it follows that given a probability distribution x i distributed over the n nodes of a network, then M gives the Markov transition (flow) rates of each probability from one node to another. Thus it follows that the connection matrix gives the infinitesimal transition rates between nodes with the weight reflecting that exact topology. Specifically, if the hypothetical initial probability vector is x i = (1,0,0,0 0) then the vector at a time dt later will be equal to the first column of the M matrix, M = I + dt C. Thus the first column of M is the probability distribution after an infinitesimal time of that part of the probability that began on node 1 and likewise for all other nodes thus giving a probability interpretation to each of the columns of M as the transfer to that node. Thus each column of M can be treated as a probability distribution associated with the topology connected to that associated node and will support an unambiguous definition of an associated entropy function that reflects the inherent disorder (or order) after a flow dt. Thus the columns of M support a meaningful definition of Renyi entropies which in turn reflect the Markov transformation towards disorder of the topological flow to the node for that column. Thus this Renyi entropy on this column can be said to summarize the disorder of the topology of the connections to that node to that order of the expansion. It follows that the spectra of all nodes reflects in some sense the disorder of the entire network. We recall that the numbering of the nodes is arbitrary and thus we can now renumber the nodes without affecting the underlying topology We thus sort the N values of the nodal entropy in descending order which gives a spectral curve independent of nodal ordering and thus independent of the permutations on nodal numbering (except possibly for some degeneracy which we address below). That spectral curve can be summarized by the total value for the entropy of all columns (since entropy is additive and the column values are totally independent 7
8 If the connection matrix is symmetric then the graph (network) is said to be undirected, but if there is some asymmetry, then the graph is at least partially directed where the flow from i to j is less or greater than the converse flow. If the connection matrix is not symmetrized then one can capture this asymmetry by resetting the diagonal values of C to be equal to the negative of all other row values in that row. Then upon expansion of M = I + λc, the rows are automatically normalized probabilities that in turn support entropy functions for each row. These row entropy values form a spectrum which could be sorted by the same nodal values (in order) that is used to order the column values. This will result in a different spectral curve that is not necessarily in nondecreasing order for the row entropies. One also can compute the total row entropy as we have done for columns. If two columns have the same entropy then one can remove some of the numbering degeneracy by using the values of the associated row entropies by using a rank ordering as we did with column values. 4 Practical and Computational Considerations The work here has both purely mathematical and practical aspects pertaining to applications to real networks. If one only has a single C matrix and time is not involved then the following discussion on time windows does not apply. It will then be assumed that one has a data flow with records with the fields: (a) network type, (b) time, (c) node i, (d) node j, (e) weight. These might be SNORT captures of internet traffic between IP addresses, financial transitions between bank accounts, power transfers among electrical grid substations, or passengers flown between two airports. The C(t,δ) matrix is constructed by summing the weights into the appropriate cells (renumbered with integers as i, j = 1, 2, N) during a time period δ centered about time t. It is obvious that one must have a period δ which allows a representative accumulation of values for the disagrigation size N. If C is too sparse, then one must choose longer time windows or one must collapse the matrix nodes by some natural methodology such as IP sectors, or flights between states and not airports. In some cases one may wish to combine several network types using a linear combination of the contributions determined by the first parameter. In some considerations, one might wish to modify the 8
9 weight of the contribution such as using the log of the financial transfer. The software we have built contains loaders with such adjustable parameters. The result of this process is a C(t) with no diagonal terms. We then put this in the form of a Lie Monoid generator by setting the diagonal terms equal to the negative of the other terms in that column (and later row). We then find it useful to normalize the entire matrix to have a fixed trace of -1 or N as this allows better control over the subsequent expansion into the Markov matrix. The expansion M(t) = e λc(t) although mathematically guaranteed to converge, have non-negative terms and generally be Markovian, must be executed with a small number of terms if C is large. The parameter λ gives a weighting of the higher terms in the expansion where one might choose to sum up through k terms. The number of such terms is the extent to which M feels out the connections to the connections etc. as weighted by the parameter λ. These two must work hand in hand since it is meaningless to have a very large λ while only expanding to the first order in C. Conversely, it is meaningless to expand to many powers, k, of C while using a nearly infinitesimal value of λ since higher orders of λ will make such higher powers of C vanish. The next consideration is that although the M matrix has only positive terms when the full expansion is executed, in practice one can choose k and λ which, due to the negative diagonals of C, can give negative terms for truncated expansions. Thus the software must have error checks to make the appropriate corrections in the expansion. Now having the M(t) matrix for that instant, one computes the E j c =log 2 (N(Σ i M ij 2 )) ie the log of the sums of squares of each column to get the entropy (information) for that column representing the transfers into that node by the Markov matrix. The spectra is computed by sorting these by value while keeping a lookup table for which node goes to which original position. A similar computation is done to compute the entropies of the rows E j r where the same sort order is used except for removing potential degeneracies (where the column values are the same and thus not distinguished by order). These two spectral curves, or histograms, are computed for each successive time window and overlaid graphically to compare the row and column entropy 9
10 profiles over time. A critical point is to realize that it does not matter that the nodes are renumbered with each window, but rather we are interested in whether the profile of order and disorder of the underlying topology is about the same. Naturally some profiles for networks change from late Sunday night to rush hours at 9AM Monday. Likewise, power grids depend upon the temperature as well as the time of day. Thus for a given time of day, day of week, and if necessary for that network, weather pattern in temperature, one must learn the profile of what is normal (i.e. profile one standard deviation) for the network under consideration and then to overlay the instantaneous network spectra on this and graphically display it. One can sum all of the row entropies into a single value Er(t) and likewise for the columns. Then one might sum the squares of deviations from normal to obtain a single value representing the total deviation of column entropies from normal (and likewise for the rows). Our software performs these computations and displays along with the overall network amplitude which is the trace of the original C matrix. This gives us three curves that we can monitor over time as well as watching the current row and column entropy spectra displayed overlaid upon the normal distribution for those circumstances. One must then be able to identify where anomalies are occurring in the network for example by clicking on the associated spectral curve anomaly area. The system then finds the node identification in the lookup table thus identifying the anomalous nodes and subnets. We will present results of our monitoring internet networks at two universities. 5 Interpretation and Discussion We emphasize again that the flows that are modeled by M(t) = e λc have nothing at all to do with the dynamical evolution of the network. These metrics are used to monitor the network state and dynamical behavior but not to predict it. Rather the evolution generated by M(λ) is an imaginary dynamical flow that would occur if a conserved fluid (probability, money, population ) were to move among the nodes at the rates indicated by the C matrix of connected weights. Thus the value of M(λ) is that the associated entropies can be used to summarize the order or disorder of the incoming or outgoing topological connectivity of the (static) network at one given instant of time. The 10
11 philosophy here is that the entropy values will capture the most essential aspects of the structure of the column and row probability distributions, and thus the topology, to that level of expansion of the parameter λ. By expanding to higher powers of C, with larger values of λ, the entropy metrics capture increasing levels of the connections to the connections etc. Also by utilizing other Renyi entropies, one obtains other spectra and values that measure other moments of the probability distributions. One can also consider alternative diagonal values of the C matrix by adding the Abelian scaling group transformation generators to the diagonal values of C. These transformations destroy the conservation of the modeled flow (such as probability) and thus the resulting transformation is no long Markovian. These altered diagonal transformations are equivalent to adding sources and sinks of the modeled fluid at the associated nodes. It is straight forward to prove that the entropy value E(t) = log 2 (N<x(t) x(t)>) when taken to only the third level of expansion, can, with its partial derivatives with respect to such sources and sinks at the node j, for different initial conditions for the flow x(0)> at node i, formally obtain the entire C matrix thus showing that the entire topology of the network is contained in the entropy functions and its derivatives. When C is diagonalized, with the values leading to the Markov transformations, or to the more general values of the diagonals of the last paragraph, one automatically gets a diagonalization of the M matrix. The interpretation of the eigenvectors is now totally obvious as those linear combinations of nodal flows that give a single eigenvalue (decrease when the transformation is Markov) of the associated probability, for that eigenvector. This follows from the fact that all Markov eigenvalues are negative except the one value for equilibrium which has eigenvalue unity for equilibrium. That means that each of these negative eigenvalues of C reflect the decreasing exponential rates of decrease of the associated eigenvector as the system approaches equilibrium as λ approaches infinity in M= e λc. This insight allows us to see that all of the Renyi entropy values are increasing as the system approaches equilibrium, which is normally the state of all nodes having the same value of this hypothetical probability. The use here of this 11
12 artificial flow of probability under M provides us with more than just a method of encapsulating the topology with generalized entropy values, it also gives an intuitive model for the eigenvectors and eigenvalues for C and sheds light on the graph isomerism problem (different topologies having the same eigenvalue spectra). Of course it does not resolve any graph isomerism issue associated with degeneracy of multiple topologies for a single eigenvalue spectra without altering the C matrix by the Abelian transformations. Based upon the arguments above, we suggest that for real networks such as the internet, that the appropriate connection matrix be formed, from source and destination information transfers, where both asymmetry and levels of connection are to be maintained in the C(t) matrix values during that window of time about that time instant. Specifically, this means that if a connection is made multiple times in that time interval, then that C element should reflect the appropriate weight of connectivity as this adds substantial value to the entropy functions. We then suggest that at each instant, the column and row entropy spectra be computed along with the total row and column entropy and that this be done for lower order Renyi entropies as well as lower order values in the expansion of the Markov parameter λ that includes higher order connectivity of the topology. We are currently performing tests to see how effective these entropy metrics are in detecting abnormal changes in topologies that could be associated with attacks, intrusions, malicious processes, and system failures. The patterns (from our simulations) of specific topologies such as rings, trees, clusters, and other structures have interesting entropy spectra. We are performing these experiments on both mathematical simulations of networks with changing topologies in known ways, and also on real network data both in raw forms and in forms simulated from raw data. The objective is to see if these metrics can be useful in the practical sense of monitoring sections of the internet and other computer networks. It is important to note that one can obtain these same metrics for subnetworks of the original network. The subnetwork would be chosen as that portion of the topology that has incoming or outgoing entropy changes that are anomalous. Thus this technique allows an automated reduction or hierarchical expansion methodology to drill into the network to monitor those subnets that are most dynamically aberrant. 12
13 6 Results of Monitoring Internet Traffic The mathematical and computational techniques defined above along with the associated Markov entropy network metrics can be used to analyze the static and track the dynamic behavior of any type of network structure. This includes electrical grids, natural gas pipelines, communications networks, financial transactions, disease networks and social networks. But the network tracking that we have performed to date concentrated totally on internet traffic as defined by Snort data capture at servers of information that is sent from one IP address to another IP address. Our objective is to identify anomalies, and abnormal behavior relative to normal traffic patterns by monitoring the total column (incoming traffic) and row (outgoing traffic) second order Renyi entropy along with the traffic volume which is independent of the traffic topology. This is similar to separating the buying pattern of financial investments from the volume of transactions on the market as two separate indicators. The associated graph shows the total incoming and outgoing entropy as a function of time for a server at a university of 30,000 students and faculty. The major anomalies were identified at certain times and these were expanded to see the full entropy spectra at those times over the network thus identifying the specific nodes that had aberrant behavior. It was determined that these particular anomalies in entropy occurred for nodes that at certain times were used to upload and download large volumes of audio and video files. 13
14 7 Conclusions We have proposed network metrics which are generalized entropy functions of the Markov monoid matrix M generated by an altered connection matrix C. When sorted, the associated entropy spectra for the columns and rows of C monitor the state and time evolution of the incoming and outgoing entropy at network nodes. These well defined functions satisfy our original criteria of being fast to compute (compared to eigenvalues), intuitive in interpretation, and hierarchical in revealing sequentially detained network information. They can be used to dynamically monitor networks relative to such normal metrical values thus identifying when the network statistically alters its intrinsic patterns of connectivity. 14
15 1. J. Math. Phys. 26 (2) 1985, Markov-type Lie groups in GL(n,R), Joseph E. Johnson Acknowledgements Extensive calculations and creation of the associated computer code, Internet data capture, and extensive technical support was performed by Ms. Nayeong Jeong and Mr. John William Campbell. Without their help, the experimental portions of this work could not have been accomplished. 15
No class on Thursday, October 1. No office hours on Tuesday, September 29 and Thursday, October 1.
 Stationary Distributions Monday, September 28, 2015 2:02 PM No class on Thursday, October 1. No office hours on Tuesday, September 29 and Thursday, October 1. Homework 1 due Friday, October 2 at 5 PM strongly
Stationary Distributions Monday, September 28, 2015 2:02 PM No class on Thursday, October 1. No office hours on Tuesday, September 29 and Thursday, October 1. Homework 1 due Friday, October 2 at 5 PM strongly
Markov Chains and Spectral Clustering
 Markov Chains and Spectral Clustering Ning Liu 1,2 and William J. Stewart 1,3 1 Department of Computer Science North Carolina State University, Raleigh, NC 27695-8206, USA. 2 nliu@ncsu.edu, 3 billy@ncsu.edu
Markov Chains and Spectral Clustering Ning Liu 1,2 and William J. Stewart 1,3 1 Department of Computer Science North Carolina State University, Raleigh, NC 27695-8206, USA. 2 nliu@ncsu.edu, 3 billy@ncsu.edu
Lab 8: Measuring Graph Centrality - PageRank. Monday, November 5 CompSci 531, Fall 2018
 Lab 8: Measuring Graph Centrality - PageRank Monday, November 5 CompSci 531, Fall 2018 Outline Measuring Graph Centrality: Motivation Random Walks, Markov Chains, and Stationarity Distributions Google
Lab 8: Measuring Graph Centrality - PageRank Monday, November 5 CompSci 531, Fall 2018 Outline Measuring Graph Centrality: Motivation Random Walks, Markov Chains, and Stationarity Distributions Google
Degenerate Perturbation Theory. 1 General framework and strategy
 Physics G6037 Professor Christ 12/22/2015 Degenerate Perturbation Theory The treatment of degenerate perturbation theory presented in class is written out here in detail. The appendix presents the underlying
Physics G6037 Professor Christ 12/22/2015 Degenerate Perturbation Theory The treatment of degenerate perturbation theory presented in class is written out here in detail. The appendix presents the underlying
Algebraic Representation of Networks
 Algebraic Representation of Networks 0 1 2 1 1 0 0 1 2 0 0 1 1 1 1 1 Hiroki Sayama sayama@binghamton.edu Describing networks with matrices (1) Adjacency matrix A matrix with rows and columns labeled by
Algebraic Representation of Networks 0 1 2 1 1 0 0 1 2 0 0 1 1 1 1 1 Hiroki Sayama sayama@binghamton.edu Describing networks with matrices (1) Adjacency matrix A matrix with rows and columns labeled by
Background on Chevalley Groups Constructed from a Root System
 Background on Chevalley Groups Constructed from a Root System Paul Tokorcheck Department of Mathematics University of California, Santa Cruz 10 October 2011 Abstract In 1955, Claude Chevalley described
Background on Chevalley Groups Constructed from a Root System Paul Tokorcheck Department of Mathematics University of California, Santa Cruz 10 October 2011 Abstract In 1955, Claude Chevalley described
6.207/14.15: Networks Lecture 12: Generalized Random Graphs
 6.207/14.15: Networks Lecture 12: Generalized Random Graphs 1 Outline Small-world model Growing random networks Power-law degree distributions: Rich-Get-Richer effects Models: Uniform attachment model
6.207/14.15: Networks Lecture 12: Generalized Random Graphs 1 Outline Small-world model Growing random networks Power-law degree distributions: Rich-Get-Richer effects Models: Uniform attachment model
Definition A finite Markov chain is a memoryless homogeneous discrete stochastic process with a finite number of states.
 Chapter 8 Finite Markov Chains A discrete system is characterized by a set V of states and transitions between the states. V is referred to as the state space. We think of the transitions as occurring
Chapter 8 Finite Markov Chains A discrete system is characterized by a set V of states and transitions between the states. V is referred to as the state space. We think of the transitions as occurring
MATH 320, WEEK 11: Eigenvalues and Eigenvectors
 MATH 30, WEEK : Eigenvalues and Eigenvectors Eigenvalues and Eigenvectors We have learned about several vector spaces which naturally arise from matrix operations In particular, we have learned about the
MATH 30, WEEK : Eigenvalues and Eigenvectors Eigenvalues and Eigenvectors We have learned about several vector spaces which naturally arise from matrix operations In particular, we have learned about the
Chapter 7 Network Flow Problems, I
 Chapter 7 Network Flow Problems, I Network flow problems are the most frequently solved linear programming problems. They include as special cases, the assignment, transportation, maximum flow, and shortest
Chapter 7 Network Flow Problems, I Network flow problems are the most frequently solved linear programming problems. They include as special cases, the assignment, transportation, maximum flow, and shortest
Markov Chains, Random Walks on Graphs, and the Laplacian
 Markov Chains, Random Walks on Graphs, and the Laplacian CMPSCI 791BB: Advanced ML Sridhar Mahadevan Random Walks! There is significant interest in the problem of random walks! Markov chain analysis! Computer
Markov Chains, Random Walks on Graphs, and the Laplacian CMPSCI 791BB: Advanced ML Sridhar Mahadevan Random Walks! There is significant interest in the problem of random walks! Markov chain analysis! Computer
Queens College, CUNY, Department of Computer Science Numerical Methods CSCI 361 / 761 Spring 2018 Instructor: Dr. Sateesh Mane.
 Queens College, CUNY, Department of Computer Science Numerical Methods CSCI 361 / 761 Spring 2018 Instructor: Dr. Sateesh Mane c Sateesh R. Mane 2018 8 Lecture 8 8.1 Matrices July 22, 2018 We shall study
Queens College, CUNY, Department of Computer Science Numerical Methods CSCI 361 / 761 Spring 2018 Instructor: Dr. Sateesh Mane c Sateesh R. Mane 2018 8 Lecture 8 8.1 Matrices July 22, 2018 We shall study
In these chapter 2A notes write vectors in boldface to reduce the ambiguity of the notation.
 1 2 Linear Systems In these chapter 2A notes write vectors in boldface to reduce the ambiguity of the notation 21 Matrix ODEs Let and is a scalar A linear function satisfies Linear superposition ) Linear
1 2 Linear Systems In these chapter 2A notes write vectors in boldface to reduce the ambiguity of the notation 21 Matrix ODEs Let and is a scalar A linear function satisfies Linear superposition ) Linear
Monitoring of Network Topology Dynamics
 Monitoring of Network Topology Dynamics Dr. Vladimir Gudkov / Dr. Joseph E. Johnson Department of Physics and Astronomy University of South Carolina, Columbia, SC 29208 USA Email: gudkov@sc.edu / jjohnson@sc.edu
Monitoring of Network Topology Dynamics Dr. Vladimir Gudkov / Dr. Joseph E. Johnson Department of Physics and Astronomy University of South Carolina, Columbia, SC 29208 USA Email: gudkov@sc.edu / jjohnson@sc.edu
Network Analysis and Cluster Detection Using Markov Theory. John William Campbell
 Network Analysis and Cluster Detection Using Markov Theory by John William Campbell Bachelor of Science Wofford College 1994 Bachelor of Arts Wofford College 1994 Submitted in Partial Fulfillment of the
Network Analysis and Cluster Detection Using Markov Theory by John William Campbell Bachelor of Science Wofford College 1994 Bachelor of Arts Wofford College 1994 Submitted in Partial Fulfillment of the
Deep Learning Book Notes Chapter 2: Linear Algebra
 Deep Learning Book Notes Chapter 2: Linear Algebra Compiled By: Abhinaba Bala, Dakshit Agrawal, Mohit Jain Section 2.1: Scalars, Vectors, Matrices and Tensors Scalar Single Number Lowercase names in italic
Deep Learning Book Notes Chapter 2: Linear Algebra Compiled By: Abhinaba Bala, Dakshit Agrawal, Mohit Jain Section 2.1: Scalars, Vectors, Matrices and Tensors Scalar Single Number Lowercase names in italic
Distributed Randomized Algorithms for the PageRank Computation Hideaki Ishii, Member, IEEE, and Roberto Tempo, Fellow, IEEE
 IEEE TRANSACTIONS ON AUTOMATIC CONTROL, VOL. 55, NO. 9, SEPTEMBER 2010 1987 Distributed Randomized Algorithms for the PageRank Computation Hideaki Ishii, Member, IEEE, and Roberto Tempo, Fellow, IEEE Abstract
IEEE TRANSACTIONS ON AUTOMATIC CONTROL, VOL. 55, NO. 9, SEPTEMBER 2010 1987 Distributed Randomized Algorithms for the PageRank Computation Hideaki Ishii, Member, IEEE, and Roberto Tempo, Fellow, IEEE Abstract
Incompatibility Paradoxes
 Chapter 22 Incompatibility Paradoxes 22.1 Simultaneous Values There is never any difficulty in supposing that a classical mechanical system possesses, at a particular instant of time, precise values of
Chapter 22 Incompatibility Paradoxes 22.1 Simultaneous Values There is never any difficulty in supposing that a classical mechanical system possesses, at a particular instant of time, precise values of
Kernels of Directed Graph Laplacians. J. S. Caughman and J.J.P. Veerman
 Kernels of Directed Graph Laplacians J. S. Caughman and J.J.P. Veerman Department of Mathematics and Statistics Portland State University PO Box 751, Portland, OR 97207. caughman@pdx.edu, veerman@pdx.edu
Kernels of Directed Graph Laplacians J. S. Caughman and J.J.P. Veerman Department of Mathematics and Statistics Portland State University PO Box 751, Portland, OR 97207. caughman@pdx.edu, veerman@pdx.edu
Statistics 992 Continuous-time Markov Chains Spring 2004
 Summary Continuous-time finite-state-space Markov chains are stochastic processes that are widely used to model the process of nucleotide substitution. This chapter aims to present much of the mathematics
Summary Continuous-time finite-state-space Markov chains are stochastic processes that are widely used to model the process of nucleotide substitution. This chapter aims to present much of the mathematics
Elementary Linear Algebra
 Matrices J MUSCAT Elementary Linear Algebra Matrices Definition Dr J Muscat 2002 A matrix is a rectangular array of numbers, arranged in rows and columns a a 2 a 3 a n a 2 a 22 a 23 a 2n A = a m a mn We
Matrices J MUSCAT Elementary Linear Algebra Matrices Definition Dr J Muscat 2002 A matrix is a rectangular array of numbers, arranged in rows and columns a a 2 a 3 a n a 2 a 22 a 23 a 2n A = a m a mn We
1 Searching the World Wide Web
 Hubs and Authorities in a Hyperlinked Environment 1 Searching the World Wide Web Because diverse users each modify the link structure of the WWW within a relatively small scope by creating web-pages on
Hubs and Authorities in a Hyperlinked Environment 1 Searching the World Wide Web Because diverse users each modify the link structure of the WWW within a relatively small scope by creating web-pages on
This section is an introduction to the basic themes of the course.
 Chapter 1 Matrices and Graphs 1.1 The Adjacency Matrix This section is an introduction to the basic themes of the course. Definition 1.1.1. A simple undirected graph G = (V, E) consists of a non-empty
Chapter 1 Matrices and Graphs 1.1 The Adjacency Matrix This section is an introduction to the basic themes of the course. Definition 1.1.1. A simple undirected graph G = (V, E) consists of a non-empty
Designing Information Devices and Systems I Spring 2018 Lecture Notes Note Introduction to Linear Algebra the EECS Way
 EECS 16A Designing Information Devices and Systems I Spring 018 Lecture Notes Note 1 1.1 Introduction to Linear Algebra the EECS Way In this note, we will teach the basics of linear algebra and relate
EECS 16A Designing Information Devices and Systems I Spring 018 Lecture Notes Note 1 1.1 Introduction to Linear Algebra the EECS Way In this note, we will teach the basics of linear algebra and relate
Majorizations for the Eigenvectors of Graph-Adjacency Matrices: A Tool for Complex Network Design
 Majorizations for the Eigenvectors of Graph-Adjacency Matrices: A Tool for Complex Network Design Rahul Dhal Electrical Engineering and Computer Science Washington State University Pullman, WA rdhal@eecs.wsu.edu
Majorizations for the Eigenvectors of Graph-Adjacency Matrices: A Tool for Complex Network Design Rahul Dhal Electrical Engineering and Computer Science Washington State University Pullman, WA rdhal@eecs.wsu.edu
MAT 2037 LINEAR ALGEBRA I web:
 MAT 237 LINEAR ALGEBRA I 2625 Dokuz Eylül University, Faculty of Science, Department of Mathematics web: Instructor: Engin Mermut http://kisideuedutr/enginmermut/ HOMEWORK 2 MATRIX ALGEBRA Textbook: Linear
MAT 237 LINEAR ALGEBRA I 2625 Dokuz Eylül University, Faculty of Science, Department of Mathematics web: Instructor: Engin Mermut http://kisideuedutr/enginmermut/ HOMEWORK 2 MATRIX ALGEBRA Textbook: Linear
6.207/14.15: Networks Lecture 7: Search on Networks: Navigation and Web Search
 6.207/14.15: Networks Lecture 7: Search on Networks: Navigation and Web Search Daron Acemoglu and Asu Ozdaglar MIT September 30, 2009 1 Networks: Lecture 7 Outline Navigation (or decentralized search)
6.207/14.15: Networks Lecture 7: Search on Networks: Navigation and Web Search Daron Acemoglu and Asu Ozdaglar MIT September 30, 2009 1 Networks: Lecture 7 Outline Navigation (or decentralized search)
Spectral Graph Theory and You: Matrix Tree Theorem and Centrality Metrics
 Spectral Graph Theory and You: and Centrality Metrics Jonathan Gootenberg March 11, 2013 1 / 19 Outline of Topics 1 Motivation Basics of Spectral Graph Theory Understanding the characteristic polynomial
Spectral Graph Theory and You: and Centrality Metrics Jonathan Gootenberg March 11, 2013 1 / 19 Outline of Topics 1 Motivation Basics of Spectral Graph Theory Understanding the characteristic polynomial
Decision-Making with the AHP: Why is The Principal Eigenvector Necessary
 Decision-Making with the AHP: Why is The Principal Eigenvector Necessary Thomas L. Saaty Keywords: complex order, consistent, near consistent, priority, principal eigenvector Summary: We will show here
Decision-Making with the AHP: Why is The Principal Eigenvector Necessary Thomas L. Saaty Keywords: complex order, consistent, near consistent, priority, principal eigenvector Summary: We will show here
Regular finite Markov chains with interval probabilities
 5th International Symposium on Imprecise Probability: Theories and Applications, Prague, Czech Republic, 2007 Regular finite Markov chains with interval probabilities Damjan Škulj Faculty of Social Sciences
5th International Symposium on Imprecise Probability: Theories and Applications, Prague, Czech Republic, 2007 Regular finite Markov chains with interval probabilities Damjan Škulj Faculty of Social Sciences
13 : Variational Inference: Loopy Belief Propagation and Mean Field
 10-708: Probabilistic Graphical Models 10-708, Spring 2012 13 : Variational Inference: Loopy Belief Propagation and Mean Field Lecturer: Eric P. Xing Scribes: Peter Schulam and William Wang 1 Introduction
10-708: Probabilistic Graphical Models 10-708, Spring 2012 13 : Variational Inference: Loopy Belief Propagation and Mean Field Lecturer: Eric P. Xing Scribes: Peter Schulam and William Wang 1 Introduction
Uncertainty and Randomization
 Uncertainty and Randomization The PageRank Computation in Google Roberto Tempo IEIIT-CNR Politecnico di Torino tempo@polito.it 1993: Robustness of Linear Systems 1993: Robustness of Linear Systems 16 Years
Uncertainty and Randomization The PageRank Computation in Google Roberto Tempo IEIIT-CNR Politecnico di Torino tempo@polito.it 1993: Robustness of Linear Systems 1993: Robustness of Linear Systems 16 Years
MASSACHUSETTS INSTITUTE OF TECHNOLOGY Chemistry 5.76 Revised February, 1982 NOTES ON MATRIX METHODS
 MASSACHUSETTS INSTITUTE OF TECHNOLOGY Chemistry 5.76 Revised February, 198 NOTES ON MATRIX METHODS 1. Matrix Algebra Margenau and Murphy, The Mathematics of Physics and Chemistry, Chapter 10, give almost
MASSACHUSETTS INSTITUTE OF TECHNOLOGY Chemistry 5.76 Revised February, 198 NOTES ON MATRIX METHODS 1. Matrix Algebra Margenau and Murphy, The Mathematics of Physics and Chemistry, Chapter 10, give almost
6.842 Randomness and Computation March 3, Lecture 8
 6.84 Randomness and Computation March 3, 04 Lecture 8 Lecturer: Ronitt Rubinfeld Scribe: Daniel Grier Useful Linear Algebra Let v = (v, v,..., v n ) be a non-zero n-dimensional row vector and P an n n
6.84 Randomness and Computation March 3, 04 Lecture 8 Lecturer: Ronitt Rubinfeld Scribe: Daniel Grier Useful Linear Algebra Let v = (v, v,..., v n ) be a non-zero n-dimensional row vector and P an n n
A Random Dot Product Model for Weighted Networks arxiv: v1 [stat.ap] 8 Nov 2016
![A Random Dot Product Model for Weighted Networks arxiv: v1 [stat.ap] 8 Nov 2016 A Random Dot Product Model for Weighted Networks arxiv: v1 [stat.ap] 8 Nov 2016](/thumbs/79/79491591.jpg) A Random Dot Product Model for Weighted Networks arxiv:1611.02530v1 [stat.ap] 8 Nov 2016 Daryl R. DeFord 1 Daniel N. Rockmore 1,2,3 1 Department of Mathematics, Dartmouth College, Hanover, NH, USA 03755
A Random Dot Product Model for Weighted Networks arxiv:1611.02530v1 [stat.ap] 8 Nov 2016 Daryl R. DeFord 1 Daniel N. Rockmore 1,2,3 1 Department of Mathematics, Dartmouth College, Hanover, NH, USA 03755
Chapter Two Elements of Linear Algebra
 Chapter Two Elements of Linear Algebra Previously, in chapter one, we have considered single first order differential equations involving a single unknown function. In the next chapter we will begin to
Chapter Two Elements of Linear Algebra Previously, in chapter one, we have considered single first order differential equations involving a single unknown function. In the next chapter we will begin to
EIGENVALUES AND EIGENVECTORS 3
 EIGENVALUES AND EIGENVECTORS 3 1. Motivation 1.1. Diagonal matrices. Perhaps the simplest type of linear transformations are those whose matrix is diagonal (in some basis). Consider for example the matrices
EIGENVALUES AND EIGENVECTORS 3 1. Motivation 1.1. Diagonal matrices. Perhaps the simplest type of linear transformations are those whose matrix is diagonal (in some basis). Consider for example the matrices
Quantum Mechanics- I Prof. Dr. S. Lakshmi Bala Department of Physics Indian Institute of Technology, Madras
 Quantum Mechanics- I Prof. Dr. S. Lakshmi Bala Department of Physics Indian Institute of Technology, Madras Lecture - 6 Postulates of Quantum Mechanics II (Refer Slide Time: 00:07) In my last lecture,
Quantum Mechanics- I Prof. Dr. S. Lakshmi Bala Department of Physics Indian Institute of Technology, Madras Lecture - 6 Postulates of Quantum Mechanics II (Refer Slide Time: 00:07) In my last lecture,
Week 4. (1) 0 f ij u ij.
 Week 4 1 Network Flow Chapter 7 of the book is about optimisation problems on networks. Section 7.1 gives a quick introduction to the definitions of graph theory. In fact I hope these are already known
Week 4 1 Network Flow Chapter 7 of the book is about optimisation problems on networks. Section 7.1 gives a quick introduction to the definitions of graph theory. In fact I hope these are already known
Designing Information Devices and Systems I Fall 2018 Lecture Notes Note Introduction to Linear Algebra the EECS Way
 EECS 16A Designing Information Devices and Systems I Fall 018 Lecture Notes Note 1 1.1 Introduction to Linear Algebra the EECS Way In this note, we will teach the basics of linear algebra and relate it
EECS 16A Designing Information Devices and Systems I Fall 018 Lecture Notes Note 1 1.1 Introduction to Linear Algebra the EECS Way In this note, we will teach the basics of linear algebra and relate it
Statistics 202: Data Mining. c Jonathan Taylor. Week 2 Based in part on slides from textbook, slides of Susan Holmes. October 3, / 1
 Week 2 Based in part on slides from textbook, slides of Susan Holmes October 3, 2012 1 / 1 Part I Other datatypes, preprocessing 2 / 1 Other datatypes Document data You might start with a collection of
Week 2 Based in part on slides from textbook, slides of Susan Holmes October 3, 2012 1 / 1 Part I Other datatypes, preprocessing 2 / 1 Other datatypes Document data You might start with a collection of
13 : Variational Inference: Loopy Belief Propagation
 10-708: Probabilistic Graphical Models 10-708, Spring 2014 13 : Variational Inference: Loopy Belief Propagation Lecturer: Eric P. Xing Scribes: Rajarshi Das, Zhengzhong Liu, Dishan Gupta 1 Introduction
10-708: Probabilistic Graphical Models 10-708, Spring 2014 13 : Variational Inference: Loopy Belief Propagation Lecturer: Eric P. Xing Scribes: Rajarshi Das, Zhengzhong Liu, Dishan Gupta 1 Introduction
Part I. Other datatypes, preprocessing. Other datatypes. Other datatypes. Week 2 Based in part on slides from textbook, slides of Susan Holmes
 Week 2 Based in part on slides from textbook, slides of Susan Holmes Part I Other datatypes, preprocessing October 3, 2012 1 / 1 2 / 1 Other datatypes Other datatypes Document data You might start with
Week 2 Based in part on slides from textbook, slides of Susan Holmes Part I Other datatypes, preprocessing October 3, 2012 1 / 1 2 / 1 Other datatypes Other datatypes Document data You might start with
QR FACTORIZATIONS USING A RESTRICTED SET OF ROTATIONS
 QR FACTORIZATIONS USING A RESTRICTED SET OF ROTATIONS DIANNE P. O LEARY AND STEPHEN S. BULLOCK Dedicated to Alan George on the occasion of his 60th birthday Abstract. Any matrix A of dimension m n (m n)
QR FACTORIZATIONS USING A RESTRICTED SET OF ROTATIONS DIANNE P. O LEARY AND STEPHEN S. BULLOCK Dedicated to Alan George on the occasion of his 60th birthday Abstract. Any matrix A of dimension m n (m n)
Computing and Communicating Functions over Sensor Networks
 Computing and Communicating Functions over Sensor Networks Solmaz Torabi Dept. of Electrical and Computer Engineering Drexel University solmaz.t@drexel.edu Advisor: Dr. John M. Walsh 1/35 1 Refrences [1]
Computing and Communicating Functions over Sensor Networks Solmaz Torabi Dept. of Electrical and Computer Engineering Drexel University solmaz.t@drexel.edu Advisor: Dr. John M. Walsh 1/35 1 Refrences [1]
Lie algebraic quantum control mechanism analysis
 Lie algebraic quantum control mechanism analysis June 4, 2 Existing methods for quantum control mechanism identification do not exploit analytic features of control systems to delineate mechanism (or,
Lie algebraic quantum control mechanism analysis June 4, 2 Existing methods for quantum control mechanism identification do not exploit analytic features of control systems to delineate mechanism (or,
Lecture: Local Spectral Methods (1 of 4)
 Stat260/CS294: Spectral Graph Methods Lecture 18-03/31/2015 Lecture: Local Spectral Methods (1 of 4) Lecturer: Michael Mahoney Scribe: Michael Mahoney Warning: these notes are still very rough. They provide
Stat260/CS294: Spectral Graph Methods Lecture 18-03/31/2015 Lecture: Local Spectral Methods (1 of 4) Lecturer: Michael Mahoney Scribe: Michael Mahoney Warning: these notes are still very rough. They provide
Using Markov Chains To Model Human Migration in a Network Equilibrium Framework
 Using Markov Chains To Model Human Migration in a Network Equilibrium Framework Jie Pan Department of Mathematics and Computer Science Saint Joseph s University Philadelphia, PA 19131 Anna Nagurney School
Using Markov Chains To Model Human Migration in a Network Equilibrium Framework Jie Pan Department of Mathematics and Computer Science Saint Joseph s University Philadelphia, PA 19131 Anna Nagurney School
This appendix provides a very basic introduction to linear algebra concepts.
 APPENDIX Basic Linear Algebra Concepts This appendix provides a very basic introduction to linear algebra concepts. Some of these concepts are intentionally presented here in a somewhat simplified (not
APPENDIX Basic Linear Algebra Concepts This appendix provides a very basic introduction to linear algebra concepts. Some of these concepts are intentionally presented here in a somewhat simplified (not
communication networks
 Positive matrices associated with synchronised communication networks Abraham Berman Department of Mathematics Robert Shorten Hamilton Institute Douglas Leith Hamilton Instiute The Technion NUI Maynooth
Positive matrices associated with synchronised communication networks Abraham Berman Department of Mathematics Robert Shorten Hamilton Institute Douglas Leith Hamilton Instiute The Technion NUI Maynooth
CS 664 Segmentation (2) Daniel Huttenlocher
 CS 664 Segmentation (2) Daniel Huttenlocher Recap Last time covered perceptual organization more broadly, focused in on pixel-wise segmentation Covered local graph-based methods such as MST and Felzenszwalb-Huttenlocher
CS 664 Segmentation (2) Daniel Huttenlocher Recap Last time covered perceptual organization more broadly, focused in on pixel-wise segmentation Covered local graph-based methods such as MST and Felzenszwalb-Huttenlocher
Introduction to Group Theory
 Chapter 10 Introduction to Group Theory Since symmetries described by groups play such an important role in modern physics, we will take a little time to introduce the basic structure (as seen by a physicist)
Chapter 10 Introduction to Group Theory Since symmetries described by groups play such an important role in modern physics, we will take a little time to introduce the basic structure (as seen by a physicist)
Qualifying Examination Winter 2017
 Qualifying Examination Winter 2017 Examination Committee: Anne Greenbaum, Hong Qian, Eric Shea-Brown Day 1, Tuesday, December 12, 9:30-12:30, LEW 208 You have three hours to complete this exam. Work all
Qualifying Examination Winter 2017 Examination Committee: Anne Greenbaum, Hong Qian, Eric Shea-Brown Day 1, Tuesday, December 12, 9:30-12:30, LEW 208 You have three hours to complete this exam. Work all
A Note on Google s PageRank
 A Note on Google s PageRank According to Google, google-search on a given topic results in a listing of most relevant web pages related to the topic. Google ranks the importance of webpages according to
A Note on Google s PageRank According to Google, google-search on a given topic results in a listing of most relevant web pages related to the topic. Google ranks the importance of webpages according to
Some Notes on Linear Algebra
 Some Notes on Linear Algebra prepared for a first course in differential equations Thomas L Scofield Department of Mathematics and Statistics Calvin College 1998 1 The purpose of these notes is to present
Some Notes on Linear Algebra prepared for a first course in differential equations Thomas L Scofield Department of Mathematics and Statistics Calvin College 1998 1 The purpose of these notes is to present
Capacity of a Two-way Function Multicast Channel
 Capacity of a Two-way Function Multicast Channel 1 Seiyun Shin, Student Member, IEEE and Changho Suh, Member, IEEE Abstract We explore the role of interaction for the problem of reliable computation over
Capacity of a Two-way Function Multicast Channel 1 Seiyun Shin, Student Member, IEEE and Changho Suh, Member, IEEE Abstract We explore the role of interaction for the problem of reliable computation over
1 Mathematical preliminaries
 1 Mathematical preliminaries The mathematical language of quantum mechanics is that of vector spaces and linear algebra. In this preliminary section, we will collect the various definitions and mathematical
1 Mathematical preliminaries The mathematical language of quantum mechanics is that of vector spaces and linear algebra. In this preliminary section, we will collect the various definitions and mathematical
14 Singular Value Decomposition
 14 Singular Value Decomposition For any high-dimensional data analysis, one s first thought should often be: can I use an SVD? The singular value decomposition is an invaluable analysis tool for dealing
14 Singular Value Decomposition For any high-dimensional data analysis, one s first thought should often be: can I use an SVD? The singular value decomposition is an invaluable analysis tool for dealing
Central Groupoids, Central Digraphs, and Zero-One Matrices A Satisfying A 2 = J
 Central Groupoids, Central Digraphs, and Zero-One Matrices A Satisfying A 2 = J Frank Curtis, John Drew, Chi-Kwong Li, and Daniel Pragel September 25, 2003 Abstract We study central groupoids, central
Central Groupoids, Central Digraphs, and Zero-One Matrices A Satisfying A 2 = J Frank Curtis, John Drew, Chi-Kwong Li, and Daniel Pragel September 25, 2003 Abstract We study central groupoids, central
Oblivious Equilibrium: A Mean Field Approximation for Large-Scale Dynamic Games
 Oblivious Equilibrium: A Mean Field Approximation for Large-Scale Dynamic Games Gabriel Y. Weintraub, Lanier Benkard, and Benjamin Van Roy Stanford University {gweintra,lanierb,bvr}@stanford.edu Abstract
Oblivious Equilibrium: A Mean Field Approximation for Large-Scale Dynamic Games Gabriel Y. Weintraub, Lanier Benkard, and Benjamin Van Roy Stanford University {gweintra,lanierb,bvr}@stanford.edu Abstract
Computationally, diagonal matrices are the easiest to work with. With this idea in mind, we introduce similarity:
 Diagonalization We have seen that diagonal and triangular matrices are much easier to work with than are most matrices For example, determinants and eigenvalues are easy to compute, and multiplication
Diagonalization We have seen that diagonal and triangular matrices are much easier to work with than are most matrices For example, determinants and eigenvalues are easy to compute, and multiplication
Applications of Randomized Methods for Decomposing and Simulating from Large Covariance Matrices
 Applications of Randomized Methods for Decomposing and Simulating from Large Covariance Matrices Vahid Dehdari and Clayton V. Deutsch Geostatistical modeling involves many variables and many locations.
Applications of Randomized Methods for Decomposing and Simulating from Large Covariance Matrices Vahid Dehdari and Clayton V. Deutsch Geostatistical modeling involves many variables and many locations.
Supplementary Information: Construction of Hypothetical MOFs using a Graph Theoretical Approach. Peter G. Boyd and Tom K. Woo*
 Electronic Supplementary Material ESI) for CrystEngComm. This journal is The Royal Society of Chemistry 2016 Supplementary Information: Construction of Hypothetical MOFs using a Graph Theoretical Approach
Electronic Supplementary Material ESI) for CrystEngComm. This journal is The Royal Society of Chemistry 2016 Supplementary Information: Construction of Hypothetical MOFs using a Graph Theoretical Approach
MATH 5524 MATRIX THEORY Pledged Problem Set 2
 MATH 5524 MATRIX THEORY Pledged Problem Set 2 Posted Tuesday 25 April 207 Due by 5pm on Wednesday 3 May 207 Complete any four problems, 25 points each You are welcome to complete more problems if you like,
MATH 5524 MATRIX THEORY Pledged Problem Set 2 Posted Tuesday 25 April 207 Due by 5pm on Wednesday 3 May 207 Complete any four problems, 25 points each You are welcome to complete more problems if you like,
Calculating Web Page Authority Using the PageRank Algorithm
 Jacob Miles Prystowsky and Levi Gill Math 45, Fall 2005 1 Introduction 1.1 Abstract In this document, we examine how the Google Internet search engine uses the PageRank algorithm to assign quantitatively
Jacob Miles Prystowsky and Levi Gill Math 45, Fall 2005 1 Introduction 1.1 Abstract In this document, we examine how the Google Internet search engine uses the PageRank algorithm to assign quantitatively
Analysis of Algorithms. Unit 5 - Intractable Problems
 Analysis of Algorithms Unit 5 - Intractable Problems 1 Intractable Problems Tractable Problems vs. Intractable Problems Polynomial Problems NP Problems NP Complete and NP Hard Problems 2 In this unit we
Analysis of Algorithms Unit 5 - Intractable Problems 1 Intractable Problems Tractable Problems vs. Intractable Problems Polynomial Problems NP Problems NP Complete and NP Hard Problems 2 In this unit we
Detailed Proof of The PerronFrobenius Theorem
 Detailed Proof of The PerronFrobenius Theorem Arseny M Shur Ural Federal University October 30, 2016 1 Introduction This famous theorem has numerous applications, but to apply it you should understand
Detailed Proof of The PerronFrobenius Theorem Arseny M Shur Ural Federal University October 30, 2016 1 Introduction This famous theorem has numerous applications, but to apply it you should understand
Mini-project in scientific computing
 Mini-project in scientific computing Eran Treister Computer Science Department, Ben-Gurion University of the Negev, Israel. March 7, 2018 1 / 30 Scientific computing Involves the solution of large computational
Mini-project in scientific computing Eran Treister Computer Science Department, Ben-Gurion University of the Negev, Israel. March 7, 2018 1 / 30 Scientific computing Involves the solution of large computational
EE731 Lecture Notes: Matrix Computations for Signal Processing
 EE731 Lecture Notes: Matrix Computations for Signal Processing James P. Reilly c Department of Electrical and Computer Engineering McMaster University September 22, 2005 0 Preface This collection of ten
EE731 Lecture Notes: Matrix Computations for Signal Processing James P. Reilly c Department of Electrical and Computer Engineering McMaster University September 22, 2005 0 Preface This collection of ten
Agreement algorithms for synchronization of clocks in nodes of stochastic networks
 UDC 519.248: 62 192 Agreement algorithms for synchronization of clocks in nodes of stochastic networks L. Manita, A. Manita National Research University Higher School of Economics, Moscow Institute of
UDC 519.248: 62 192 Agreement algorithms for synchronization of clocks in nodes of stochastic networks L. Manita, A. Manita National Research University Higher School of Economics, Moscow Institute of
AUTOMATIC CONTROL. Andrea M. Zanchettin, PhD Spring Semester, Introduction to Automatic Control & Linear systems (time domain)
 1 AUTOMATIC CONTROL Andrea M. Zanchettin, PhD Spring Semester, 2018 Introduction to Automatic Control & Linear systems (time domain) 2 What is automatic control? From Wikipedia Control theory is an interdisciplinary
1 AUTOMATIC CONTROL Andrea M. Zanchettin, PhD Spring Semester, 2018 Introduction to Automatic Control & Linear systems (time domain) 2 What is automatic control? From Wikipedia Control theory is an interdisciplinary
Fiedler s Theorems on Nodal Domains
 Spectral Graph Theory Lecture 7 Fiedler s Theorems on Nodal Domains Daniel A Spielman September 9, 202 7 About these notes These notes are not necessarily an accurate representation of what happened in
Spectral Graph Theory Lecture 7 Fiedler s Theorems on Nodal Domains Daniel A Spielman September 9, 202 7 About these notes These notes are not necessarily an accurate representation of what happened in
LIMITING PROBABILITY TRANSITION MATRIX OF A CONDENSED FIBONACCI TREE
 International Journal of Applied Mathematics Volume 31 No. 18, 41-49 ISSN: 1311-178 (printed version); ISSN: 1314-86 (on-line version) doi: http://dx.doi.org/1.173/ijam.v31i.6 LIMITING PROBABILITY TRANSITION
International Journal of Applied Mathematics Volume 31 No. 18, 41-49 ISSN: 1311-178 (printed version); ISSN: 1314-86 (on-line version) doi: http://dx.doi.org/1.173/ijam.v31i.6 LIMITING PROBABILITY TRANSITION
! 4 4! o! +! h 4 o=0! ±= ± p i And back-substituting into the linear equations gave us the ratios of the amplitudes of oscillation:.»» = A p e i! +t»»
 Topic 6: Coupled Oscillators and Normal Modes Reading assignment: Hand and Finch Chapter 9 We are going to be considering the general case of a system with N degrees of freedome close to one of its stable
Topic 6: Coupled Oscillators and Normal Modes Reading assignment: Hand and Finch Chapter 9 We are going to be considering the general case of a system with N degrees of freedome close to one of its stable
Structure in Data. A major objective in data analysis is to identify interesting features or structure in the data.
 Structure in Data A major objective in data analysis is to identify interesting features or structure in the data. The graphical methods are very useful in discovering structure. There are basically two
Structure in Data A major objective in data analysis is to identify interesting features or structure in the data. The graphical methods are very useful in discovering structure. There are basically two
Mathematical Methods wk 2: Linear Operators
 John Magorrian, magog@thphysoxacuk These are work-in-progress notes for the second-year course on mathematical methods The most up-to-date version is available from http://www-thphysphysicsoxacuk/people/johnmagorrian/mm
John Magorrian, magog@thphysoxacuk These are work-in-progress notes for the second-year course on mathematical methods The most up-to-date version is available from http://www-thphysphysicsoxacuk/people/johnmagorrian/mm
Chapter 2. Linear Algebra. rather simple and learning them will eventually allow us to explain the strange results of
 Chapter 2 Linear Algebra In this chapter, we study the formal structure that provides the background for quantum mechanics. The basic ideas of the mathematical machinery, linear algebra, are rather simple
Chapter 2 Linear Algebra In this chapter, we study the formal structure that provides the background for quantum mechanics. The basic ideas of the mathematical machinery, linear algebra, are rather simple
Spectral clustering. Two ideal clusters, with two points each. Spectral clustering algorithms
 A simple example Two ideal clusters, with two points each Spectral clustering Lecture 2 Spectral clustering algorithms 4 2 3 A = Ideally permuted Ideal affinities 2 Indicator vectors Each cluster has an
A simple example Two ideal clusters, with two points each Spectral clustering Lecture 2 Spectral clustering algorithms 4 2 3 A = Ideally permuted Ideal affinities 2 Indicator vectors Each cluster has an
The 1+1-dimensional Ising model
 Chapter 4 The 1+1-dimensional Ising model The 1+1-dimensional Ising model is one of the most important models in statistical mechanics. It is an interacting system, and behaves accordingly. Yet for a variety
Chapter 4 The 1+1-dimensional Ising model The 1+1-dimensional Ising model is one of the most important models in statistical mechanics. It is an interacting system, and behaves accordingly. Yet for a variety
Select/Special Topics in Atomic Physics Prof. P. C. Deshmukh Department of Physics Indian Institute of Technology, Madras
 Select/Special Topics in Atomic Physics Prof. P. C. Deshmukh Department of Physics Indian Institute of Technology, Madras Lecture - 9 Angular Momentum in Quantum Mechanics Dimensionality of the Direct-Product
Select/Special Topics in Atomic Physics Prof. P. C. Deshmukh Department of Physics Indian Institute of Technology, Madras Lecture - 9 Angular Momentum in Quantum Mechanics Dimensionality of the Direct-Product
Module 1: Signals & System
 Module 1: Signals & System Lecture 6: Basic Signals in Detail Basic Signals in detail We now introduce formally some of the basic signals namely 1) The Unit Impulse function. 2) The Unit Step function
Module 1: Signals & System Lecture 6: Basic Signals in Detail Basic Signals in detail We now introduce formally some of the basic signals namely 1) The Unit Impulse function. 2) The Unit Step function
Statistical Geometry Processing Winter Semester 2011/2012
 Statistical Geometry Processing Winter Semester 2011/2012 Linear Algebra, Function Spaces & Inverse Problems Vector and Function Spaces 3 Vectors vectors are arrows in space classically: 2 or 3 dim. Euclidian
Statistical Geometry Processing Winter Semester 2011/2012 Linear Algebra, Function Spaces & Inverse Problems Vector and Function Spaces 3 Vectors vectors are arrows in space classically: 2 or 3 dim. Euclidian
Review of Controllability Results of Dynamical System
 IOSR Journal of Mathematics (IOSR-JM) e-issn: 2278-5728, p-issn: 2319-765X. Volume 13, Issue 4 Ver. II (Jul. Aug. 2017), PP 01-05 www.iosrjournals.org Review of Controllability Results of Dynamical System
IOSR Journal of Mathematics (IOSR-JM) e-issn: 2278-5728, p-issn: 2319-765X. Volume 13, Issue 4 Ver. II (Jul. Aug. 2017), PP 01-05 www.iosrjournals.org Review of Controllability Results of Dynamical System
Problem set 2. Math 212b February 8, 2001 due Feb. 27
 Problem set 2 Math 212b February 8, 2001 due Feb. 27 Contents 1 The L 2 Euler operator 1 2 Symplectic vector spaces. 2 2.1 Special kinds of subspaces....................... 3 2.2 Normal forms..............................
Problem set 2 Math 212b February 8, 2001 due Feb. 27 Contents 1 The L 2 Euler operator 1 2 Symplectic vector spaces. 2 2.1 Special kinds of subspaces....................... 3 2.2 Normal forms..............................
Solution Set 7, Fall '12
 Solution Set 7, 18.06 Fall '12 1. Do Problem 26 from 5.1. (It might take a while but when you see it, it's easy) Solution. Let n 3, and let A be an n n matrix whose i, j entry is i + j. To show that det
Solution Set 7, 18.06 Fall '12 1. Do Problem 26 from 5.1. (It might take a while but when you see it, it's easy) Solution. Let n 3, and let A be an n n matrix whose i, j entry is i + j. To show that det
CS249: ADVANCED DATA MINING
 CS249: ADVANCED DATA MINING Graph and Network Instructor: Yizhou Sun yzsun@cs.ucla.edu May 31, 2017 Methods Learnt Classification Clustering Vector Data Text Data Recommender System Decision Tree; Naïve
CS249: ADVANCED DATA MINING Graph and Network Instructor: Yizhou Sun yzsun@cs.ucla.edu May 31, 2017 Methods Learnt Classification Clustering Vector Data Text Data Recommender System Decision Tree; Naïve
MTH 2032 Semester II
 MTH 232 Semester II 2-2 Linear Algebra Reference Notes Dr. Tony Yee Department of Mathematics and Information Technology The Hong Kong Institute of Education December 28, 2 ii Contents Table of Contents
MTH 232 Semester II 2-2 Linear Algebra Reference Notes Dr. Tony Yee Department of Mathematics and Information Technology The Hong Kong Institute of Education December 28, 2 ii Contents Table of Contents
MITOCW watch?v=rf5sefhttwo
 MITOCW watch?v=rf5sefhttwo The following content is provided under a Creative Commons license. Your support will help MIT OpenCourseWare continue to offer high-quality educational resources for free. To
MITOCW watch?v=rf5sefhttwo The following content is provided under a Creative Commons license. Your support will help MIT OpenCourseWare continue to offer high-quality educational resources for free. To
H ψ = E ψ. Introduction to Exact Diagonalization. Andreas Läuchli, New states of quantum matter MPI für Physik komplexer Systeme - Dresden
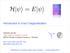 H ψ = E ψ Introduction to Exact Diagonalization Andreas Läuchli, New states of quantum matter MPI für Physik komplexer Systeme - Dresden http://www.pks.mpg.de/~aml laeuchli@comp-phys.org Simulations of
H ψ = E ψ Introduction to Exact Diagonalization Andreas Läuchli, New states of quantum matter MPI für Physik komplexer Systeme - Dresden http://www.pks.mpg.de/~aml laeuchli@comp-phys.org Simulations of
arxiv: v2 [cs.it] 4 Mar 2019
![arxiv: v2 [cs.it] 4 Mar 2019 arxiv: v2 [cs.it] 4 Mar 2019](/thumbs/96/127504310.jpg) Capacity-Achieving Private Information Retrieval Codes with Optimal Message Size and Upload Cost Chao Tian Hua Sun Jun Chen arxiv:1808.07536v2 [cs.it] 4 Mar 2019 March 6, 2019 Abstract We propose a new
Capacity-Achieving Private Information Retrieval Codes with Optimal Message Size and Upload Cost Chao Tian Hua Sun Jun Chen arxiv:1808.07536v2 [cs.it] 4 Mar 2019 March 6, 2019 Abstract We propose a new
Some Background Material
 Chapter 1 Some Background Material In the first chapter, we present a quick review of elementary - but important - material as a way of dipping our toes in the water. This chapter also introduces important
Chapter 1 Some Background Material In the first chapter, we present a quick review of elementary - but important - material as a way of dipping our toes in the water. This chapter also introduces important
Reading for Lecture 13 Release v10
 Reading for Lecture 13 Release v10 Christopher Lee November 15, 2011 Contents 1 Evolutionary Trees i 1.1 Evolution as a Markov Process...................................... ii 1.2 Rooted vs. Unrooted Trees........................................
Reading for Lecture 13 Release v10 Christopher Lee November 15, 2011 Contents 1 Evolutionary Trees i 1.1 Evolution as a Markov Process...................................... ii 1.2 Rooted vs. Unrooted Trees........................................
From Non-Negative Matrix Factorization to Deep Learning
 The Math!! From Non-Negative Matrix Factorization to Deep Learning Intuitions and some Math too! luissarmento@gmailcom https://wwwlinkedincom/in/luissarmento/ October 18, 2017 The Math!! Introduction Disclaimer
The Math!! From Non-Negative Matrix Factorization to Deep Learning Intuitions and some Math too! luissarmento@gmailcom https://wwwlinkedincom/in/luissarmento/ October 18, 2017 The Math!! Introduction Disclaimer
Lecture 10: A (Brief) Introduction to Group Theory (See Chapter 3.13 in Boas, 3rd Edition)
 Lecture 0: A (Brief) Introduction to Group heory (See Chapter 3.3 in Boas, 3rd Edition) Having gained some new experience with matrices, which provide us with representations of groups, and because symmetries
Lecture 0: A (Brief) Introduction to Group heory (See Chapter 3.3 in Boas, 3rd Edition) Having gained some new experience with matrices, which provide us with representations of groups, and because symmetries
MATH3200, Lecture 31: Applications of Eigenvectors. Markov Chains and Chemical Reaction Systems
 Lecture 31: Some Applications of Eigenvectors: Markov Chains and Chemical Reaction Systems Winfried Just Department of Mathematics, Ohio University April 9 11, 2018 Review: Eigenvectors and left eigenvectors
Lecture 31: Some Applications of Eigenvectors: Markov Chains and Chemical Reaction Systems Winfried Just Department of Mathematics, Ohio University April 9 11, 2018 Review: Eigenvectors and left eigenvectors
Process Modelling. Table of Contents
 Process Modelling 1 Process Modelling prepared by Wm. J. Garland, Professor, Department of Engineering Physics, McMaster University, Hamilton, Ontario, Canada More about this document Summary: The general
Process Modelling 1 Process Modelling prepared by Wm. J. Garland, Professor, Department of Engineering Physics, McMaster University, Hamilton, Ontario, Canada More about this document Summary: The general
MATH 521, WEEK 2: Rational and Real Numbers, Ordered Sets, Countable Sets
 MATH 521, WEEK 2: Rational and Real Numbers, Ordered Sets, Countable Sets 1 Rational and Real Numbers Recall that a number is rational if it can be written in the form a/b where a, b Z and b 0, and a number
MATH 521, WEEK 2: Rational and Real Numbers, Ordered Sets, Countable Sets 1 Rational and Real Numbers Recall that a number is rational if it can be written in the form a/b where a, b Z and b 0, and a number
Inference in Bayesian Networks
 Andrea Passerini passerini@disi.unitn.it Machine Learning Inference in graphical models Description Assume we have evidence e on the state of a subset of variables E in the model (i.e. Bayesian Network)
Andrea Passerini passerini@disi.unitn.it Machine Learning Inference in graphical models Description Assume we have evidence e on the state of a subset of variables E in the model (i.e. Bayesian Network)
6 Evolution of Networks
 last revised: March 2008 WARNING for Soc 376 students: This draft adopts the demography convention for transition matrices (i.e., transitions from column to row). 6 Evolution of Networks 6. Strategic network
last revised: March 2008 WARNING for Soc 376 students: This draft adopts the demography convention for transition matrices (i.e., transitions from column to row). 6 Evolution of Networks 6. Strategic network
Chapter 2 Fourier Series Phase Object Spectra
 PhD University of Edinburgh 99 Phase-Only Optical Information Processing D. J. Potter Index Chapter 3 4 5 6 7 8 9 Chapter Fourier Series Phase Object Spectra In chapter one, it was noted how one may describe
PhD University of Edinburgh 99 Phase-Only Optical Information Processing D. J. Potter Index Chapter 3 4 5 6 7 8 9 Chapter Fourier Series Phase Object Spectra In chapter one, it was noted how one may describe
