Doubly Aggressive Selective Sampling Algorithms for Classification
|
|
|
- Kathleen Fitzgerald
- 5 years ago
- Views:
Transcription
1 Doubly Aggressive Selective Sampling Algorithms for Classification Koby Crammer Department of Electrical Engneering, Technion - Israel Institute of Technology, Haifa 3, Israel Abstract Online selective sampling algorithms learn to perform binary classification, and additionally they decided whether to ask, or query, for a label of any given example. We introduce two stochastic linear algorithms and analyze them in the worst-case mistake-bound framework. Even though stochastic, for some inputs, our algorithms query with probability and make an update even if there is no mistake, yet the margin is small, hence they are doubly aggressive. We prove bounds in the worst-case settings, which may be lower than previous bounds in some settings. Experiments with 33 document classification datasets, some with Ks examples, show the superiority of doubly-aggressive algorithms both in performance and number of queries. Introduction In many real world problems, input examples are cheap and easy to collect, while labeling them is a long and an expensive process. Today, one can easily access an enormous amount of text, audio, images and video, on the web. Nevertheless, much effort is needed to provide correct output for each input. We study online selective sampling in which algorithms are fed with a sequence of inputs and ask or query labels only for a subset of the inputs. Unlike the well studied area of active-learning, an algorithm has access to one input at a time, and it can query its label only at that time, with no ability to store examples which possibly will be queried in the future. Another motivation for a selective sampling technique is to reduce the size of kernel-based models built online, such as the Perceptron algorithm combined with kernels. This is because the size of the model is bounded by the number of queried labels, which may be small for selective sampling. Appearing in Proceedings of the 7 th International Conference on Artificial Intelligence and Statistics (AISTATS), Reykjavik, Iceland. JMLR: W&CP volume 33. Copyright by the authors. Many algorithms for selective sampling, that build on linear models, query for a label of an input x, if the absolute value of the margin is small, w x (e.g. [, ]). However, this quantity may be small in one of two cases: () when only few labels are observed (i.e. uncertainty due to a small sample, and there is a real need to query); () if there is labeling noise for x (uncertainty due to noise, and there is no real need to query). Previous algorithms are not distinguishing between these cases, and thus are not focusing their queries in the first case. We revisit the design of selective sampling with linear models based on this observation. As a by product, our algorithms query more aggressively in early rounds where the uncertainty is large. We introduce doubly aggressive algorithms for selective sampling (DAGGER), which query for a label based both on margin and a notion of confidence (intervals) (e.g. []). We present two algorithms that integrate both quantities to decide whether to query. One algorithm builds on the work of Cesa-Bianchi et al [], and the other on a recently introduced algorithm for online regression of Moroshko and Crammer []. We analyze the theoretical properties of both algorithms, showing bounds that may be lower than bounds of other algorithms in some settings. Extensive evaluation on 33 datasets, with hundred of thousand examples, demonstrate the superiority of our algorithms, which achieve lower test error with less number of queries. Finally, all figures in the paper are best viewed in color. Problem Setting Linear selective-sampling online algorithms maintain a weight vector w i and work in rounds. On the ith round an algorithm receives an input x i R d and outputs a binary label ŷ i = sign(x i w i ) {±}. The algorithm then makes (a possibly) stochastic decision if to ask (or query) for the true label y i {±}. If indeed the label is asked for, the algorithm may use y i to update its prediction model to w i. Otherwise, no change is performed, w i = w i, and it proceeds to the next round. Algorithms have two complementary goals, to make few prediction mistakes and to ask, or query, small amount of labels. The decision of the algorithm is represented by a binary
2 Doubly Aggressive Selective Sampling Algorithms for Classification variable Q i, where Q i = iff the label y i was queried on the ith round. Note, the algorithm is evaluated on all examples, even those not queered. The two goals above are to have both i Q i (queries) and i [[y i ŷ i ]] (mistakes) small. Algorithms will be analyzed in the worst-case setting, bounding the expected number of mistakes using the cumulative hinge loss, inter alia, defined by, l ( y i v ) ( x i where l yv x ) = max {, yv x }. i The bounds we describe below are of expected number of mistakes. Expectation of a quantity defined at round i is with respect to all events at prior (and present) of the query, and are independent of future times. 3 Algorithms We focus in second-order algorithms that are adapted to classification from regression, and specifically, the Aggregating Algorithm for regression (AAR) of Vovk [5], which was also described by Forster [8], and is related to the work of Azoury and Warmuth [3]. On each iteration, these algorithms solve (recursively) a time-dependent batch regression problem. The resulting prediction function depends on two quantities, a vector b i = j x jy j and a matrix A i = I + j x jx j. Cesa-Bianchi et al [9] proposed to adapt the online ridge-regression (squared loss and Euclidean regularization) to online binary classification. Given a new example, the second-order perceptron predicts the sign of the margin, ˆp i = x ( ) i A i b i. () A selective-sampling algorithm is required to make two choices, the first choice is if to query a label or not. Consider the case that the absolute margin is large ˆp i. This may be interpreted that the example lies far from the decision boundary, and thus it will not be useful to query the label, as even if the current model is not the optimal one, but only close to it, still it makes the same prediction as the optimal model. The hidden assumption is that the current model is indeed not far from the optimal one, but this clearly is not the case in early rounds. Thus, there is a need to employ an additional quantity that is used to differentiate between these two cases of large absolute margin ˆp i : () computed with a model after observing already examples close (or similar) to the input x i ; (b) computed with a model after seeing only few, if any, examples close (or similar) to the input x i. In the former case, in fact, there will not be a need to query, while in the later, the quality of the estimator ˆp i is not good, and there is a need to query. A useful quantity which is used below is the projection of an input x i on the inverse of the matrix A i (conceptually, it is a covariance-like matrix), r i = x i A i x i, () which can be thought of the confidence in the prediction. Indeed, confidence-weighted (CW) linear prediction algorithms [3] employ a similar formal model, and in CW, r i is exactly the variance in prediction, under a Gaussian distribution. Some algorithms, including AAR, use a related quantity that incorporates also the input x i itself. From Woodbury equality we have, x i A i x i = x i A r i i xi = +x i A i xi +r i. We will use this quantity exactly for the purpose of differentiating between these two cases. Low values of r i represent low uncertainty (as many examples close to x i were already observed), while large values of r i reflect high-uncertainty, as only few, if any, examples similar to x i were observed. In the extreme case, when x i is orthogonal to all previous examples, we have r i =. The second choice an algorithm should make is how to update the model given the input x i and the queried label y i. Previous linear algorithms for selective-sampling [, ] are based on the Perceptron update which is passive (or conservative), i.e. it updates only when mistakes occur. Yet, it is known that aggressive updates yield algorithms that perform better (e.g. the second order preceptron [9] vs AROW [], the latter is aggressive and performs better). The algorithms we describe below couples these two decisions. When they query aggressively (ie with probability ), they also perform an aggressive update when the signed margin is small, according to a rule of the form y i ˆp i f(r i ), where f(r i ) is a decreasing function. Hence, they are doubly aggressive, as they query- and update aggressively simultaneously. (Most aggressive algorithms, i.e. PA [], employ a constant function f(x) =.) Intuitively, a stochastic choice to query, means that the algorithm is confident about its own prediction, and thus there is no need for a large or aggressive update. Similarly, a query with probability (i.e. deterministic, which we call below an aggressive query), means that the algorithm is not confident about its own prediction, and the model is not converged yet. Thus, an aggressive update is needed. We design two selective-sampling algorithms that make a stochastic decision based both on ˆp i and r i. Both algorithms below flip a coin with bias, c/ (c + max{, F ( ˆp i, r i )}), (3) where F (ˆp i, r i ) is some function increasing in ˆp i and c > is a positive parameter. If F (ˆp i, r i ) is negative, a query will be issued aggressively, and otherwise, it will be issued if the margin ˆp i is close to zero, or r i is large, namely, there were only few past inputs similar to the current input x i. To summarize, on each iteration, after receiving x i, both algorithms compute ˆp i and r i. They then have one of two alternatives. First, draw a coin with bias defined in (3), each with a specific value of bias, and use the outcome of the draw to decide if to query. If indeed the label is queried, a conservative update is performed, i.e. an update is per-
3 Koby Crammer Algorithm DAGGER-algorithms Input: parameter c > (b > wemm) (Tab. line ) Initialize b =, A = I (ridge) or A = bi (wemm) (Tab. line ) for i =,..., m do Get instance x i R d, x i Compute ˆp i (Tab. line 3) Predict y i = sign(ˆp i ) Compute r i = x i A i x i () if F ( ˆp i, r i ) (Tab. line ) then Draw a Bernoulli random variable Q i {, } with c probability c+f ( ˆp i,r i) if Q i = then Receive label y i {±} Set Z i = if y i ŷ i (and Z i = otherwise) end if else Set Q i = (i.e. Q i = with probability ). Receive label y i {±} Set Z i =. end if {If Q i = the rhs of both equations below is zero.} Set a i (Tab. line 5) b i = b i + a i Z i Q i x i y i A i = A i + a i Z i Q i x i x i end for formed only if y i ˆp i. Second, when an aggressive query is performed, the update is also aggressive, it is performed when y i ˆp i f(r i ) for some non-decreasing non-negative function f(r i ). We conclude et al [, Alg. 3] is a special case for which F ( ˆp i, r i ) = ˆp i (always stochastic) and f(r i ) =. We refer to this algorithm by the initials of the authors, namely CBGZ-ridge, where the suffix indicates the underlying regression algorithm. An illustration of this query and update schema is shown in Fig. (a) for c =.. The bias of querying is fixed with respect to r i and thus the colored lines are parallel to the y-axis. Clearly, the probability drops fast when ˆp i gets larger, it is.5 when the margin is about.3. Also, the left half-plane is shaded indicating an update if the margin is negative, ignoring the uncertainty r i. 3. DAGGER: Doubly AGGREssive algorithms Our first algorithm, builds on the work of Cesa-Bianchi et al [] and employs the following function in the denominator of (3). It is motivated from the analysis in Thm.. Θ( ˆp i, r i ) = ( + r i )ˆp i + ˆp i r i + r i. () To better understand the query rule, we compute under what conditions a query will be issued aggressively. The function Θ( ˆp i, r i ) is quadratic in ˆp i, and attains negative Table : Settings for DAGGER-ridge and DAGGER-wemm Algorithm DAGGER-ridge DAGGER-wemm Parameters c > c >, b > A I bi ( ) 3 ˆp i x i Ai + x ix i bi x i A i bi F ( ˆp i, r i) Θ( ˆp i, r i) () Γ( ˆp i, r i) (7) 5 a i r i (6) values in a closed interval. Solving for ˆp i we get, Θ( ˆp i, r i ) ˆp i θ(r i ) = + + r i + r i. (5) That is, there is a first order phase transition point of the bias that depends on r i. For margin values ˆp i less than θ(r i ), a query will always be issued, while for margin values above this threshold, it will be issued only with some probability strictly less than. This upper bound is decreasing with the uncertainty r i. If the uncertainty is maximal r i =, then a query will be issued if the margin is less than ( )/.. While if the algorithm observe the same example (or linear combination of it) many times, that is, r i, than only if the margin is zero, ˆp i =, a query will be issued aggressively (with probability ). If a stochastic query is made (i.e. with probability less than one, when Θ( ˆp i, r i ) ), then a conservative update is made, that is only when a mistake is performed. Otherwise, if a deterministic query is made (i.e. with probability, called aggressive-query), then also an aggressive update is performed y i ˆp i θ(r i ) (see (5)), when the margin is negative or small. We call this algorithm DAGGER-ridge, for a Doubly AG- GRessive based on (online) ridge-regression, as an algorithm that (sometimes) is aggressive simultaneously in querying (deterministic, probability ) and in its update. Pseudocode of DAGGER-ridge is given in Alg. and the left column of Tab.. An illustration of this query and update schema are shown in Fig. (b) for c =.. For large uncertainty r i, the bias is (deterministic, or aggressive query) even if the absolute margin is far from zero, ˆp i. As the uncertainty r i increases, the interval of absolute values with deterministic bias shrinks, until it is a point ( ˆp i =, as in CBGZridge). Also, the left half-plane and the red (middle) area are shaded, indicating that an update is performed if the margin is negative or if an aggressive query was performed. 3. DAGGER-wemm Our next algorithm builds on a recent online regression algorithm of Crammer and Moroshko [] called WEMM. The algorithm is a last-step min-max online regression algorithm, as the one of Forster [8], yet it weights the loss
4 Doubly Aggressive Selective Sampling Algorithms for Classification r (uncertainty). r (uncertainty).9.3 r (uncertainty) p (a) CBGZ-ridge p (b) DAGGER-ridge p (c) DAGGER-wemm Figure : Bias vs. p and r for 3 algorithms. Updates are performed for pairs (p i, r) which are shaded with black dots. occur more on early rounds of the run. Thus, we expect these algorithms to query more on early stages. Additionally, DAGGER algorithms update aggressively (on selected cases) as opposed to CBGZ-ridge, which is conservative. term of the ith example with, ai = x i Ai xi =. ri (6) On each round, the algorithm finds the minimizer of bi + i aj yj w xj, for some parameter b >. It was j shown to have sub-logarithmic regret, and has an aggressive update (for regression). The sequence of weights ai is effectively giving higher weights to new examples, or directions in space, making it an ideal basis for a new aggressive selective sampling algorithm. For example, if the algorithm receives the same input x again and again, the weights ai will decrease from a value larger of a, to, in the limit. The bias function we use for this algorithm is, ri + p i + p i /ai, (7) Γ( p i, ri ) = + ri Analysis We now analyze both algorithms in the worst-case mistake bound model, starting with DAGGER-ridge. We denote for convenience the matrix, m Zi Qi x i x (9) Av = I + i. i= The bound partitions the inputs into two disjoint sets of indices, S = { i : Θ( p i, ri ) }, A{ i : Θ( p i, ri ) < }. The set S is of examples for which a stochastic query was made, and the other set A is when there is an aggressive query. Additionally, denote by M the set of example indices for which the algorithm makes a mistake (that is, where p i ) and let M = M. Similarly, denote by U the set of example indices for which there is an update but not a mistake ( < p i θ(ri )) and let U = U. The remaining examples, for which the algorithm had a large margin (θ(ri ) < p i ), do not affect the behavior of the algorithm and can be ignored. Theorem. Let (x, y ),..., (xm, ym ) be an arbitrary input sequence, where xi. Assume DAGGER-ridge (Alg. and left column of Tab.) is run on the sequence with parameter c >. Then, for all v Rd, E [M ] cv E [Av ] v + E Z i Q i yi v x i i ri E [U ]. () + E c + ri which, as before, its specific form is motivated from an analysis, summarized in Thm.. The main difference is the multiplicative factor of /ai = ( ri ). Thus, even if there is no aggressive update (Γ( p i, ri ) ), the bias (probability of update) is close to as ri is close to, i.e. where there were only few examples similar to xi. As before we compute the point of phase transition, ri, (8) Γ( p i, ri ) p i γ(ri ) = ri and update conservatively if Γ( p i, ri ) and aggressively (yi p i γ(ri )) otherwise. We call this algorithm DAGGER-wemm, since it is based on the WEMM algorithm. A pseudocode appears in Alg. and the right column of Tab.. Finally, an illustration of this query and update schema is shown in Fig. (c) for c =.. It has similar properties as DAGGER-ridge, with two differences: for large uncertainty, the probability of query is very close to unit, effectively ignoring the margin p i, and the area for which Γ( p i, ri ) is negative is slightly smaller. To conclude both DAGGER algorithms have high probability rate where there is uncertainty, which naturally i A Additionally, the expected number of queries is upper c bounded by E A + i S c+θ( p i,ri }. ri Remark. The last term of the bound, E i A +ri 3 E [U ] is strictly lower than the corresponding term of CesaBianchi et al [, Thm. 3] for two First, itricon reasons. ri tains a sum over less examples, i A +r i +ri i
5 Koby Crammer k log( + λ k), where λ k are the eigenvalues of A v. Second, the expected number of times the algorithm makes an update when no mistakes occur (E [U]) is subtracted from it. Nevertheless, the bounds are not comparable as both contain quantities that depend on a specific run of each. Remark. The exact value of the bound depends explicitly on the choice of parameter c. The optimal value of c can be compute easily, c = E[ i A ] r i +r i v E[A v]v, yielding a bound similar to Cesa-Bianchi et al [, Thm. 3], which may be lower due to Remark. Note that there is no real optimal parameter as we trade-off between accuracy and number of queries. Additionally, from the experiments below, we see that both DAGGER algorithms perform reasonably well for a large range of values for c, and in fact they outperform other algorithms we evaluated for all values of c used. The proof appears in App. A. (supplementary material). We conclude by noting that the set A is not too large. Consider the simple case in which examples are restricted to some basis, e.g. x i {e... e d }. Since examples are orthogonal they do no affect each other. When e is observed for the first time we have ˆp i = and r i = and thus it will be queried aggressively and be used for an update. Now, if it is seen again, we have ˆp i = and r i =, and thus Θ(, ) >, i.e., it will not belong to A again. We now turn to analyze DAGGER-wemm. We emphasize that weights of WEMM a i defined in (6) are random variables depending on the specific outcomes of the algorithm s randomization. We define S = {i : Γ( ˆp i, r i ) } and A{i : Γ( ˆp i, r i ) < }, analogously to (9), we denote, A a v = bi + m a i Z i Q i x i x i. () i= Theorem. Let (x, y ),..., (x m, y m ) be arbitrary input sequence, where x i. Assume DAGGER-wemm ( Alg. and right column of Tab. ) is run on the sequence with parameter b > and c >. Then for all v R d, [ E [M] cv E [A a v] v + b b E Z i Q i l ( y i v ) ] x i i ( ( + ) [ ] b r i + ) E E [U]. c b + r i i M U Additionally, [ the expected number of queries is upper bounded by E A + ] i S. c c+γ( ˆp i,r i} The proof appears in App. A.3 (supplementary material). Remark 3. Both Remarks and also apply for this theorem. Its last term, is lower than the last term of Cesa- Bianchi et al [, Thm. 3], and one can compute the optimal parameter c. Nevertheless, the three terms may be higher than the previous bound, as A v A a v, and b >. Table : Properties of datasets. Data Generated Examples Features Fraction of smaller class NG vs-rest 8K 6K % RCV vs-rest 685K 68K 8-3% RCV 6 vs K K-53K -6% Amazon 3 Rank 769K (.5K) 6M 6-33% Still, the bounds are not comparable, as they depend on the exact updates of the user, which may yield this bound to be lower than the previous one, as DAGGER-wemm may update more aggressively during the beginning of its exception, but much less later. 5 Empirical Evaluation We evaluate our algorithms on a range of binary document classification problems. We selected three tasks and generated 33 binary classification problems, by either predicting one class against the rest (vs-rest), or taking pairs of classes (vs). We used five-fold cross validation. Newsgroups corpus contains messages partitioned across different newsgroups []. We generated vsrest binary problems, yielding datasets with about 8K examples and 6K features. These datasets are highly unbalanced with about 5% positive examples. The Reuters Corpus (RCV-v/LYRL) contains manually categorized newswire stories []. Each article contains one or more labels describing its general topic, industry and region. We used the four most general labels (E-, G-, C-, M-CAT) and generated datasets: four vs-rest (with about 685K examples and 68K features) and six vs sets. Details on document preparation and feature extraction are given by Lewis et al []. Amazon reviews were used to predict sentiment. We used a larger version of the multi-domain data set of Blitzer et al [6] used by Dredze et al [7, ]. This data consists of product reviews. The goal in each domain is to classify a product review as either positive or negative. Feature extraction creates unigram and bigram features using counts following Blitzer et al [6]. We induced three binary datasets with 769K training examples,.5k test examples, and 6M features. The task in the first dataset was to predict if the number of stars associated with a review is one or more. For the second dataset, it s to predict if the score is two or less, vs more than two. Finally, for the third one, is it four or less, or five. We followed previous preprocessing and omitted all reviews with three stars, as they are very noisy. Properties of all datasets are summarized in Tab.. We evaluated five algorithms: DAGGER-ridge, DAGGER-wemm (with a fixed value of b =.) (both algorithms are in Alg. and Tab. ), CBGZ-ridge of Cesa-Bianchi et al [, Alg. 3] (performed best in their evaluation), of Orabona et al [] and om sampling. Since the data is of high-dimension (up to
6 Doubly Aggressive Selective Sampling Algorithms for Classification x 5 (a) Amazon x 5 (b) Amazon x 5 (c) Amazon x 5 (d) CCAT x 5 (e) GCAT (f) MCAT-GCAT x (g) rec sport hockey (h) sci space (i) comp windows x Figure : Error vs no of queries labels for 9 datasets: Amazon (first row), vs-rest and vs RCV (second row), and NG vs-rest (third row). Figure best viewed in color M) we diagonalized A i after processing each example. (Synthetic simulations with full matrices showed similar results as shown below.) Each algorithm was executed with values of the constant c having one pass over the training data, recording the number of queried labels and the test error. We report averages over all folds. Results for 9 representative datasets appear in Fig. (more results are in Fig. and Fig. 5 in the supplementary material). Each panel summarizes the results for a single dataset, where the first row shows the results for all Amazon datasets, second for two (out of four) vs-rest RCV and one (out of six) vs RCV, and third for three (out of twenty) vs-rest NG. Each panel plots five lines connecting markers, one line per algorithm. Each marker shows the average (test) error vs average number of updates for a run with a specific choice of the parameter c. A line shows the tradeoff between number of queries (x-axis) and error (y-axis) for some algorithm. Error bars indicate 95% confidence intervals. The horizontal dashed gray line indicates the performance of AROW [5], a state-of-the-art online algorithm, a possible skyline that always makes a query. In most cases CBGZ-ridge (green-circles) shows a large range of the tradeoff, with the ability to query very little (points at left) to very much (points at right). In some cases om is worse than, and in other cases, the other way around. Note that has strong assumptions about the label generating process, and furthermore it ignores the labels when deciding to query. DAGGER algorithms perform best than the other algorithms, where in general, DAGGER-ridge outperforms DAGGER-wemm. We were not able to drive them to query 5
7 Koby Crammer Table 3: Average number of queries and test error Results for six algorithms for -vs-rest binary classification problems based on the NG dataset, where the maximal number of allowed queries is, 5 (st block) and, 5. queries< 5 queries< 6 CBGZ-ridge DAGGER-ridge DAGGER-wemm AROW queries error queries error queries error queries error queries error queries error rec.sport.hockey (.5) (.3),96.5 (.3),36. (.3),9. (.) 5,9.89 (.3) rec.sport.baseball, 6. (.9) (.78),8.5 (.7),7.6 (.39),33.85 (.9) 5,9.7 (.5) sci.electronics,7 8.7 (3.76) 3.33 (.6), (.37) (.6),36.5 (.) 5,9 3. (.8) sci.crypt () (.3), (.7),335. (),6.86 (.) 5,9.8 (.3) sci.space, 5.7 (.) (.9),5 3.5 (.7),8.5 (.3), (.6) 5,9.5 (.) sci.med (.9) (.3),399. (.38) 85.6 (.73),89.78 (.7) 5,9.68 (.3) talk.politics.guns, 5.3 (.69) (.3),36. (.7),96 3. (.93),9.9 (.35) 5,9.9 (.) soc.religion.christian (.85) (.86),8 5. (.),75 3. (.),7 3.3 (.) 5,9. (.7) talk.politics.misc,.39 (.39) (6),36. (.73) (.35), (.36) 5,9. (.7) talk.politics.mideast (3.63) (.38), (.78) 98.3 (.),37. (.) 5,9.6 (.6) talk.religion.misc,5 5.8 (.56) (.66), (), (.3), (.37) 5,9.75 (.39) alt.atheism (.) 7.5 (.),39. (.),7 3.3 (), (.5) 5,9.7 (.39) comp.os.ms-windows.misc,3 6. (.8) (.9),98.9 (.39),6 3.6 (.6), (.) 5,9.7 (.8) comp.graphics, 6. (.67) 6 6. (.3), (3.6), (.85), (.37) 5,9 3. (.3) comp.sys.mac.hardware (.8) (.96), (.8) 98.9 (.89),3 3.6 (.3) 5,9.5 (.3) comp.sys.ibm.pc.hardware (3.) 7.33 (.9),5 6. (.37) 95.7 (.6),3.3 (.3) 5,9 3.5 (.7) misc.forsale (.) (.76), 3. (.3),38.8 (.),33.98 (.) 5,9.8 (.5) comp.windows.x, 5.78 (.6) (.9),7.7 (.8),99.69 (.3),3.66 (.9) 5,9.7 (.) rec.motorcycles 997. (.38) (.5), (.67),6.3 (.39),3.5 (.) 5,9.7 (.3) rec.autos,7. (3.) (.6), (.85), 3.5 (.69),33.6 (.9) 5,9. (.3) rec.sport.hockey 5,56.3 (.6) 5,5.73 (.39) 5, (.39) 5,6.79 (.6) 5,65.9 (.) 5,9.89 (.3) rec.sport.baseball 5, (.), (.8) 5,75. (.) 5,53.38 (.6) 5,36. (.) 5,9.7 (.5) sci.electronics 5,99.96 () 5,7 5.6 (.3) 5,976. (.69) 5,99 3. (.3) 5, (.8) 5,9 3. (.8) sci.crypt 5, (.57), (.3) 5,9.79 (.86) 5,786. (.3) 5,66.5 (.) 5,9.8 (.3) sci.space 5, (.97), (.37) 5,6.5 (.8) 5,3.35 (.9),63.5 (.3) 5,9.5 (.) sci.med 5,5 3.7 (5), (.9) 5,7.6 (.6),7.5 (.3),737.6 (.) 5,9.68 (.3) talk.politics.guns 5,8. (.3) 5,57.5 (.36) 5, (.38),9.5 (.) 5,3. (.3) 5,9.9 (.) soc.religion.christian 5, (3.69) 5,6.8 () 5, () 5,57. (.6) 5,.5 (.3) 5,9. (.7) talk.politics.misc 5, (8) 5, (.9) 5, (.85) 5,79.8 (.33) 5,6.35 (.) 5,9. (.7) talk.politics.mideast 5,5.3 (.7) 5, () 5,83.78 (.7) 5,57.95 (.) 5,8. (.) 5,9.6 (.6) talk.religion.misc 5,557.6 (.76) 5,36 5. (.9) 5, () 5,3.76 (.9) 5,6.68 (.) 5,9.75 (.39) alt.atheism 5,9 3.8 (.87) 5,.5 (.69) 5, (.8) 5,65.9 (.) 5,.6 (.8) 5,9.7 (.39) comp.os.ms-windows.misc 5,53 5. (.83) 3, (3.9) 5,5 5.7 (.5) 5,.75 (.8),75 3. (.6) 5,9.7 (.8) comp.graphics 5,7 6.9 (.75) 3,666.9 (.6) 5,68.98 (.89),83.96 (.33) 5,8 3.7 (.38) 5,9 3. (.3) comp.sys.mac.hardware 5,5.97 (.93) 3,89.9 (.67) 5,75.78 (.3),898.6 (.3) 5,95.6 (.39) 5,9.5 (.3) comp.sys.ibm.pc.hardware 5,9 5.5 (.8) 3, (.36) 5,57.6 (3) 5, (.), (.37) 5,9 3.5 (.7) misc.forsale, (.8),5 3.8 (.3) 5,7.3 (.3),38.75 (.9),99.3 (.) 5,9.8 (.5) comp.windows.x 5, (.8) 3,75. (.9) 5,6 3.5 (.78) 5,. (.6) 5,598. (.3) 5,9.7 (.) rec.motorcycles 5,6.55 (.), (.3) 5,86.9 (.3) 5,65. (.) 5,7.37 (.) 5,9.7 (.3) rec.autos 5, (.68),97. (.39) 5, (.3) 5,.3 (.3) 5,339.5 (.35) 5,9. (.3) only a very few labels, despite low values of c used. This is due to the phase transition of the bias which is set to for some values of the margin. This phenomena is more evident in the Amazon (top row) and less in the RCV and NG datasets. We hypothesize that it is correlated with the dimension, as it is higher, more examples needed to be observed before Θ(, ) or Γ(, ) will not be negative. Also, both DAGGER algorithms perform better than AROW on the NG datasets, and close to it on the sentiment datasets, even though they query at most third than AROW. Interestingly, in some datasets (e.g. Amazon in Fig. (a)), the test error is increasing when more labels are observed. For less than K examples, it is reduced from about 6% to 5%, then when more labels are observed (up to 7K), the test error goes up to about 5.6%. We now focus in the twenty NG datasets using Tab. 3 (more results are in Tab. and Tab. 5 in the supplementary material) where we specify the number of queries and the average test error for all five algorithms (and AROW) for selected runs. For the first block we set the value of the parameter c such that the number of queries for CBGZ-ridge does not exceed, 5, and the number of queries for all other algorithms does not exceed the number of queries of CBGZ-ridge per dataset. In other words, per dataset, CBGZ-ridge uses the maximum number of queries compared to the other selective sampling algorithms. The error of the best performing selective sampling algorithm is emphasized in bold fonts. DAGGER-wemm is the best algorithm for 7 datasets, and DAGGER-ridge for the remaining 3 datasets. Also, these algorithms have a lower confidence interval than CBGZridge. The second block shows the results where the number of queries for CBGZ-ridge is limited to 6, (out of about 5K examples). Now DAGGER-ridge is the best for 6 datasets, and as before both DAGGER algorithms are better than the other algorithms, and both have a performance closer to the performance of AROW than of the performance of CBGZ-ridge. We illustrate the difference of CBGZ-ridge and DAGGER in Fig. 3. We used the comp.windows.x dataset (line 8 in the second block of Tab. 3; dataset name and number of updates are underlined). Fig. 3(a) shows the cumulative number of queries for all three algorithms, CBGZridge made 5, 6 queries, DAGGER-ridge 5, and DAGGER-wemm 5, 598. Fig. 3(b) shows the difference of cumulative number of queries of both DAGGER algorithms with respect to the CBGZ-ridge algorithm. Note 6
8 Doubly Aggressive Selective Sampling Algorithms for Classification Cumulative Number of Queries 3 3 Input Index (a) comp.windows.x-cumsum Differance of Cumulative Number of Queries vs vs 3 Input Index (b) comp.windows.x - diff Cumulative Number of Queries 3 Input Index (c) ECAT vs rest - cumsum Differance of Cumulative Number of Queries vs vs Input Index (d) ECAT vs rest - diff Figure 3: Cumulative number of queries (a,c) and difference of the DAGGER algorithms and CBGZ-ridge (b,d), for comp.windows.x dataset (a,b), and ECAT-vs-rest (c,d). x-axis is plotted is log-scale, and y-axis of (a,c) also in log-scale. the log scale used. observe the run, and in a higher rate than of CBGZ-ridge; and DAGGER-ridge queries more than CBGZ-ridge, in very early stages. Fig. 3(b) shows that until about 3, examples the DAGGER algorithms query more and more aggressively than the CBGZ-ridge algorithm. After that point, both DAGGER algorithms query less aggressively, until they even make less queries than CBGZ-ridge. Figs. 3(c),3(b) show similar trends with ECAT-vs-rest dataset (row 8 of Tab. ). To conclude, both DAGGER algorithms query more aggressively in earlier rounds, where the wemm based version is more aggressive. 6 Related Work Selective sampling and active learning, such as query-bycommittee [9] and apple tasting [], were studied in the past decades. Clearly, we can not cover all that work. Recent papers [, 5] discuss stochastic query decisions for active learning. Their methods are designed for general PAC-learnable classes. We focus in linear methods, and use natural quantities such as margin ˆp i and confidence r i. Cesa-Bianchi et al [] and Orabona et al [3] developed algorithms for selective sampling in the stochastic setting. The decisions of their algorithms are based on a quantity r i (aka upper confidence interval). If r i is small there is no need to query, and if it is large, there is. Intuitively, if x i lies in the span of the preceding examples (computed via A i ) the algorithm has enough knowledge from previous examples about the direction of x i, and there is no need to query. These algorithms are in fact ignoring the margin ˆp i, and have a domestic query rule, although the authors mention that stochastic queries are possible. Much of recent work on linear functions is based on a quantity called the margin. It is used in active learning [], perceptron active learning [6], and SVMs for selective sampling is also based on the margin [7, 8] (also use a finite period of non-stop querying and later sporadic querying). The work of Cesa-Bianchi et al [] is the closest to our work, and has a stochastic rule with the same form as (3) with F ( ˆp i, r i ) = ˆp i and f(r i ) = (conservative). Each of these quantities lacks information (separately). Consider for example the case of an input x i for which ˆp i is small and r i is large. Methods that focus only in ˆp i will decide to query (as the margin is close to zero), even though it could be the case that enough samples like x i were already observed, yet there is large label noise at this region. Here, ˆp i would be small, so there is no need to query for this input. This information could be inferred from the fact that r i is not large, which means that indeed x i was observed many times. On the other hand, a medium value of r i means that x i was observed a few times already, and thus methods that consider only this quantity would decide not to query, even though it might be the case that this example lies in a region with inputs hard to predict (as ˆp i is small), and thus it is valuable to query. We take the best of these two approaches by considering both quantities. Finally, recently, few works were published about second order algorithms for classification, e.g. the second order Preceptorn [9], confidence weighted classifiers [3], and adaptive regulariztion of weights (AROW) [5]. 7 Conclusion We presented two new online learning selective sampling algorithms, that may query a label of each input example. Our algorithms use both margin and a notion of uncertainty (or variance), to stochastically decide if to query. The algorithms are doubly aggressive, both for querying and updating. We analyzed the algorithms in the worst-case mistake bound setting, and showed that under proper choice of the learning parameter c, they may work as well as algorithms that observe all labels. Experiments with 33 datasets coming from three document classification tasks show that our algorithms perform best compared to the other algorithms, and occasionally, outperform algorithms that observes all the input labels. DAGGER-wemm seems outperform DAGGER-ridge when only few inputs are queried, either by being able to query a few input (see Tab.,Tab. 5) or having low errors (see Tab. 3). We plan to extend the algorithms for multi-class problems and other settings. Acknowledgments This research was funded in part by the Intel Collaborative Research Institute for Computational Intelligence (ICRI- CI), and in part by the Israeli Science Foundation grant ISF- 567/. 7
9 Koby Crammer References [] jrennie/newsgroups/. [] mdredze/ datasets/sentiment/. [3] Katy S. Azoury and Manfred K. Warmuth. Relative loss bounds for on-line density estimation with the exponential family of distributions. Machine Learning, 3(3): 6,. [] Alina Beygelzimer, Sanjoy Dasgupta, and John Langford. Importance weighted active learning. In ICML 9: Proceedings of the 6th Annual International Conference on Machine Learning, pages 9 56, 9. [5] Alina Beygelzimer, Daniel Hsu, John Langford, and Zhang Tong. Agnostic active learning without constraints. In J. Lafferty, C. K. I. Williams, J. Shawe- Taylor, R.S. Zemel, and A. Culotta, editors, Advances in Neural Information Processing Systems 3, pages [6] John Blitzer, Mark Dredze, and Fernando Pereira. Biographies, bollywood, boom-boxes and blenders: Domain adaptation for sentiment classification. In Association for Computational Linguistics (ACL), 7. [7] Giovanni Cavallanti, Nicolò Cesa-Bianchi, and Claudio Gentile. Learning noisy linear classifiers via adaptive and selective sampling. Machine Learning, 83():7,. [8] Nicolò Cesa-Bianchi, Alex Conconi, and Claudio Gentile. Learning probabilistic linear-threshold classifiers via selective sampling. In COLT, pages , 3. [9] Nicolo Cesa-Bianchi, Alex Conconi, and Claudio Gentile. A second-order perceptron algorithm. Siam Journal of Commutation, 3(3):6 668, 5. [] Nicolò Cesa-Bianchi, Claudio Gentile, and Francesco Orabona. Robust bounds for classification via selective sampling. In ICML, page 6, 9. [] Nicolò Cesa-Bianchi, Claudio Gentile, and Luca Zaniboni. Worst-case analysis of selective sampling for linear classification. Journal of Machine Learning Research, 7:5 3, 6. [3] Koby Crammer, Mark Dredze, and Fernando Pereira. Confidence-weighted linear classification for text categorization. J. Mach. Learn. Res., 98888:89 96, June. [] Koby Crammer and Claudio Gentile. Multiclass classification with bandit feedback using adaptive regularization. Machine Learning, 9(3):37 383, 3. [5] Koby Crammer, Alex Kulesza, and Mark Dredze. Adaptive regularization of weight vectors. Machine Learning, 9():55 87, 3. [6] Sanjoy Dasgupta, Adam Tauman Kalai, and Claire Monteleoni. Analysis of perceptron-based active learning. In COLT, pages 9 63, 5. [7] Mark Dredze, Alex Kulesza, and Koby Crammer. Multi-domain learning by confidence-weighted parameter combination. Machine Learning, 79(- ):3 9,. [8] Jurgen Forster. On relative loss bounds in generalized linear regression. In FCT, 999. [9] Y. Freund, H.S. Seung, E. Shamir, and N. Tishby. Selective sampling using the Query By Committee algorirhm. Machine Learning, 8:33 68, 997. [] David P. Helmbold, Nick Littlestone, and Philip M. Long. Apple tasting. Inf. Comput., 6():85 39,. [] David D. Lewis, Yiming Yang, Tony G. Rose, and Fan Li. Rcv: A new benchmark collection for text categorization research. Journal of Machine Learning Research (JMLR), 5:36 397,. [] Edward Moroshko and Koby Crammer. Weighted last-step min-max algorithm with improved sublogarithmic regret. In ALT, pages 5 59,. [3] Francesco Orabona and Nicolò Cesa-Bianchi. Better algorithms for selective sampling. In ICML, pages 33,. [] Simon Tong and Daphne Koller. Support vector machine active learning with application sto text classification. In ICML, pages 999 6,. [5] Volodya Vovk. Competitive on-line statistics. International Statistical Review, 69,. [] K. Crammer, O. Dekel, J. Keshet, S. Shalev-Shwartz, and Y. Singer. Online passive-aggressive algorithms. JMLR, 7:55 585, 6. 8
COMP 551 Applied Machine Learning Lecture 5: Generative models for linear classification
 COMP 55 Applied Machine Learning Lecture 5: Generative models for linear classification Instructor: (jpineau@cs.mcgill.ca) Class web page: www.cs.mcgill.ca/~jpineau/comp55 Unless otherwise noted, all material
COMP 55 Applied Machine Learning Lecture 5: Generative models for linear classification Instructor: (jpineau@cs.mcgill.ca) Class web page: www.cs.mcgill.ca/~jpineau/comp55 Unless otherwise noted, all material
Co-training and Learning with Noise
 Co-training and Learning with Noise Wee Sun Lee LEEWS@COMP.NUS.EDU.SG Department of Computer Science and Singapore-MIT Alliance, National University of Singapore, Singapore 117543, Republic of Singapore
Co-training and Learning with Noise Wee Sun Lee LEEWS@COMP.NUS.EDU.SG Department of Computer Science and Singapore-MIT Alliance, National University of Singapore, Singapore 117543, Republic of Singapore
Adaptive Sampling Under Low Noise Conditions 1
 Manuscrit auteur, publié dans "41èmes Journées de Statistique, SFdS, Bordeaux (2009)" Adaptive Sampling Under Low Noise Conditions 1 Nicolò Cesa-Bianchi Dipartimento di Scienze dell Informazione Università
Manuscrit auteur, publié dans "41èmes Journées de Statistique, SFdS, Bordeaux (2009)" Adaptive Sampling Under Low Noise Conditions 1 Nicolò Cesa-Bianchi Dipartimento di Scienze dell Informazione Università
Better Algorithms for Selective Sampling
 Francesco Orabona Nicolò Cesa-Bianchi DSI, Università degli Studi di Milano, Italy francesco@orabonacom nicolocesa-bianchi@unimiit Abstract We study online algorithms for selective sampling that use regularized
Francesco Orabona Nicolò Cesa-Bianchi DSI, Università degli Studi di Milano, Italy francesco@orabonacom nicolocesa-bianchi@unimiit Abstract We study online algorithms for selective sampling that use regularized
Practical Agnostic Active Learning
 Practical Agnostic Active Learning Alina Beygelzimer Yahoo Research based on joint work with Sanjoy Dasgupta, Daniel Hsu, John Langford, Francesco Orabona, Chicheng Zhang, and Tong Zhang * * introductory
Practical Agnostic Active Learning Alina Beygelzimer Yahoo Research based on joint work with Sanjoy Dasgupta, Daniel Hsu, John Langford, Francesco Orabona, Chicheng Zhang, and Tong Zhang * * introductory
Multi-Class Confidence Weighted Algorithms
 Multi-Class Confidence Weighted Algorithms Koby Crammer Department of Computer and Information Science University of Pennsylvania Philadelphia, PA 19104 Mark Dredze Alex Kulesza Human Language Technology
Multi-Class Confidence Weighted Algorithms Koby Crammer Department of Computer and Information Science University of Pennsylvania Philadelphia, PA 19104 Mark Dredze Alex Kulesza Human Language Technology
Online Passive-Aggressive Algorithms
 Online Passive-Aggressive Algorithms Koby Crammer Ofer Dekel Shai Shalev-Shwartz Yoram Singer School of Computer Science & Engineering The Hebrew University, Jerusalem 91904, Israel {kobics,oferd,shais,singer}@cs.huji.ac.il
Online Passive-Aggressive Algorithms Koby Crammer Ofer Dekel Shai Shalev-Shwartz Yoram Singer School of Computer Science & Engineering The Hebrew University, Jerusalem 91904, Israel {kobics,oferd,shais,singer}@cs.huji.ac.il
Online multiclass learning with bandit feedback under a Passive-Aggressive approach
 ESANN 205 proceedings, European Symposium on Artificial Neural Networks, Computational Intelligence and Machine Learning. Bruges (Belgium), 22-24 April 205, i6doc.com publ., ISBN 978-28758704-8. Online
ESANN 205 proceedings, European Symposium on Artificial Neural Networks, Computational Intelligence and Machine Learning. Bruges (Belgium), 22-24 April 205, i6doc.com publ., ISBN 978-28758704-8. Online
Ruslan Salakhutdinov Joint work with Geoff Hinton. University of Toronto, Machine Learning Group
 NON-LINEAR DIMENSIONALITY REDUCTION USING NEURAL NETORKS Ruslan Salakhutdinov Joint work with Geoff Hinton University of Toronto, Machine Learning Group Overview Document Retrieval Present layer-by-layer
NON-LINEAR DIMENSIONALITY REDUCTION USING NEURAL NETORKS Ruslan Salakhutdinov Joint work with Geoff Hinton University of Toronto, Machine Learning Group Overview Document Retrieval Present layer-by-layer
On the Generalization Ability of Online Strongly Convex Programming Algorithms
 On the Generalization Ability of Online Strongly Convex Programming Algorithms Sham M. Kakade I Chicago Chicago, IL 60637 sham@tti-c.org Ambuj ewari I Chicago Chicago, IL 60637 tewari@tti-c.org Abstract
On the Generalization Ability of Online Strongly Convex Programming Algorithms Sham M. Kakade I Chicago Chicago, IL 60637 sham@tti-c.org Ambuj ewari I Chicago Chicago, IL 60637 tewari@tti-c.org Abstract
New bounds on the price of bandit feedback for mistake-bounded online multiclass learning
 Journal of Machine Learning Research 1 8, 2017 Algorithmic Learning Theory 2017 New bounds on the price of bandit feedback for mistake-bounded online multiclass learning Philip M. Long Google, 1600 Amphitheatre
Journal of Machine Learning Research 1 8, 2017 Algorithmic Learning Theory 2017 New bounds on the price of bandit feedback for mistake-bounded online multiclass learning Philip M. Long Google, 1600 Amphitheatre
Multiclass Classification with Bandit Feedback using Adaptive Regularization
 Multiclass Classification with Bandit Feedback using Adaptive Regularization Koby Crammer The Technion, Department of Electrical Engineering, Haifa, 3000, Israel Claudio Gentile Universita dell Insubria,
Multiclass Classification with Bandit Feedback using Adaptive Regularization Koby Crammer The Technion, Department of Electrical Engineering, Haifa, 3000, Israel Claudio Gentile Universita dell Insubria,
The Power of Selective Memory: Self-Bounded Learning of Prediction Suffix Trees
 The Power of Selective Memory: Self-Bounded Learning of Prediction Suffix Trees Ofer Dekel Shai Shalev-Shwartz Yoram Singer School of Computer Science & Engineering The Hebrew University, Jerusalem 91904,
The Power of Selective Memory: Self-Bounded Learning of Prediction Suffix Trees Ofer Dekel Shai Shalev-Shwartz Yoram Singer School of Computer Science & Engineering The Hebrew University, Jerusalem 91904,
Efficient and Principled Online Classification Algorithms for Lifelon
 Efficient and Principled Online Classification Algorithms for Lifelong Learning Toyota Technological Institute at Chicago Chicago, IL USA Talk @ Lifelong Learning for Mobile Robotics Applications Workshop,
Efficient and Principled Online Classification Algorithms for Lifelong Learning Toyota Technological Institute at Chicago Chicago, IL USA Talk @ Lifelong Learning for Mobile Robotics Applications Workshop,
ECE521 week 3: 23/26 January 2017
 ECE521 week 3: 23/26 January 2017 Outline Probabilistic interpretation of linear regression - Maximum likelihood estimation (MLE) - Maximum a posteriori (MAP) estimation Bias-variance trade-off Linear
ECE521 week 3: 23/26 January 2017 Outline Probabilistic interpretation of linear regression - Maximum likelihood estimation (MLE) - Maximum a posteriori (MAP) estimation Bias-variance trade-off Linear
Active Learning Class 22, 03 May Claire Monteleoni MIT CSAIL
 Active Learning 9.520 Class 22, 03 May 2006 Claire Monteleoni MIT CSAIL Outline Motivation Historical framework: query learning Current framework: selective sampling Some recent results Open problems Active
Active Learning 9.520 Class 22, 03 May 2006 Claire Monteleoni MIT CSAIL Outline Motivation Historical framework: query learning Current framework: selective sampling Some recent results Open problems Active
Linear Classification and Selective Sampling Under Low Noise Conditions
 Linear Classification and Selective Sampling Under Low Noise Conditions Giovanni Cavallanti DSI, Università degli Studi di Milano, Italy cavallanti@dsi.unimi.it Nicolò Cesa-Bianchi DSI, Università degli
Linear Classification and Selective Sampling Under Low Noise Conditions Giovanni Cavallanti DSI, Università degli Studi di Milano, Italy cavallanti@dsi.unimi.it Nicolò Cesa-Bianchi DSI, Università degli
Online Passive-Aggressive Algorithms
 Online Passive-Aggressive Algorithms Koby Crammer Ofer Dekel Shai Shalev-Shwartz Yoram Singer School of Computer Science & Engineering The Hebrew University, Jerusalem 91904, Israel {kobics,oferd,shais,singer}@cs.huji.ac.il
Online Passive-Aggressive Algorithms Koby Crammer Ofer Dekel Shai Shalev-Shwartz Yoram Singer School of Computer Science & Engineering The Hebrew University, Jerusalem 91904, Israel {kobics,oferd,shais,singer}@cs.huji.ac.il
Robust Selective Sampling from Single and Multiple Teachers
 Robust Selective Sampling from Single and Multiple Teachers Ofer Dekel Microsoft Research oferd@microsoftcom Claudio Gentile DICOM, Università dell Insubria claudiogentile@uninsubriait Karthik Sridharan
Robust Selective Sampling from Single and Multiple Teachers Ofer Dekel Microsoft Research oferd@microsoftcom Claudio Gentile DICOM, Università dell Insubria claudiogentile@uninsubriait Karthik Sridharan
Learning Multiple Tasks in Parallel with a Shared Annotator
 Learning Multiple Tasks in Parallel with a Shared Annotator Haim Cohen Department of Electrical Engeneering The Technion Israel Institute of Technology Haifa, 3000 Israel hcohen@tx.technion.ac.il Koby
Learning Multiple Tasks in Parallel with a Shared Annotator Haim Cohen Department of Electrical Engeneering The Technion Israel Institute of Technology Haifa, 3000 Israel hcohen@tx.technion.ac.il Koby
 This article was published in an Elsevier journal. The attached copy is furnished to the author for non-commercial research and education use, including for instruction at the author s institution, sharing
This article was published in an Elsevier journal. The attached copy is furnished to the author for non-commercial research and education use, including for instruction at the author s institution, sharing
The Forgetron: A Kernel-Based Perceptron on a Fixed Budget
 The Forgetron: A Kernel-Based Perceptron on a Fixed Budget Ofer Dekel Shai Shalev-Shwartz Yoram Singer School of Computer Science & Engineering The Hebrew University, Jerusalem 91904, Israel {oferd,shais,singer}@cs.huji.ac.il
The Forgetron: A Kernel-Based Perceptron on a Fixed Budget Ofer Dekel Shai Shalev-Shwartz Yoram Singer School of Computer Science & Engineering The Hebrew University, Jerusalem 91904, Israel {oferd,shais,singer}@cs.huji.ac.il
Margin-Based Algorithms for Information Filtering
 MarginBased Algorithms for Information Filtering Nicolò CesaBianchi DTI University of Milan via Bramante 65 26013 Crema Italy cesabianchi@dti.unimi.it Alex Conconi DTI University of Milan via Bramante
MarginBased Algorithms for Information Filtering Nicolò CesaBianchi DTI University of Milan via Bramante 65 26013 Crema Italy cesabianchi@dti.unimi.it Alex Conconi DTI University of Milan via Bramante
Efficient Bandit Algorithms for Online Multiclass Prediction
 Efficient Bandit Algorithms for Online Multiclass Prediction Sham Kakade, Shai Shalev-Shwartz and Ambuj Tewari Presented By: Nakul Verma Motivation In many learning applications, true class labels are
Efficient Bandit Algorithms for Online Multiclass Prediction Sham Kakade, Shai Shalev-Shwartz and Ambuj Tewari Presented By: Nakul Verma Motivation In many learning applications, true class labels are
LEARNING AND REASONING ON BACKGROUND NETS FOR TEXT CATEGORIZATION WITH CHANGING DOMAIN AND PERSONALIZED CRITERIA
 International Journal of Innovative Computing, Information and Control ICIC International c 2013 ISSN 1349-4198 Volume 9, Number 1, January 2013 pp. 47 67 LEARNING AND REASONING ON BACKGROUND NETS FOR
International Journal of Innovative Computing, Information and Control ICIC International c 2013 ISSN 1349-4198 Volume 9, Number 1, January 2013 pp. 47 67 LEARNING AND REASONING ON BACKGROUND NETS FOR
Multiclass classification with bandit feedback using adaptive regularization
 Mach Learn 013 90:347 383 DOI 10.1007/s10994-01-531-8 Multiclass classification with bandit feedback using adaptive regularization Koby Crammer Claudio Gentile Received: 8 August 011 / Accepted: 5 September
Mach Learn 013 90:347 383 DOI 10.1007/s10994-01-531-8 Multiclass classification with bandit feedback using adaptive regularization Koby Crammer Claudio Gentile Received: 8 August 011 / Accepted: 5 September
Learning the Semantic Correlation: An Alternative Way to Gain from Unlabeled Text
 Learning the Semantic Correlation: An Alternative Way to Gain from Unlabeled Text Yi Zhang Machine Learning Department Carnegie Mellon University yizhang1@cs.cmu.edu Jeff Schneider The Robotics Institute
Learning the Semantic Correlation: An Alternative Way to Gain from Unlabeled Text Yi Zhang Machine Learning Department Carnegie Mellon University yizhang1@cs.cmu.edu Jeff Schneider The Robotics Institute
Evaluation requires to define performance measures to be optimized
 Evaluation Basic concepts Evaluation requires to define performance measures to be optimized Performance of learning algorithms cannot be evaluated on entire domain (generalization error) approximation
Evaluation Basic concepts Evaluation requires to define performance measures to be optimized Performance of learning algorithms cannot be evaluated on entire domain (generalization error) approximation
SUPPORT VECTOR MACHINE
 SUPPORT VECTOR MACHINE Mainly based on https://nlp.stanford.edu/ir-book/pdf/15svm.pdf 1 Overview SVM is a huge topic Integration of MMDS, IIR, and Andrew Moore s slides here Our foci: Geometric intuition
SUPPORT VECTOR MACHINE Mainly based on https://nlp.stanford.edu/ir-book/pdf/15svm.pdf 1 Overview SVM is a huge topic Integration of MMDS, IIR, and Andrew Moore s slides here Our foci: Geometric intuition
Bayesian Learning. Remark on Conditional Probabilities and Priors. Two Roles for Bayesian Methods. [Read Ch. 6] [Suggested exercises: 6.1, 6.2, 6.
![Bayesian Learning. Remark on Conditional Probabilities and Priors. Two Roles for Bayesian Methods. [Read Ch. 6] [Suggested exercises: 6.1, 6.2, 6. Bayesian Learning. Remark on Conditional Probabilities and Priors. Two Roles for Bayesian Methods. [Read Ch. 6] [Suggested exercises: 6.1, 6.2, 6.](/thumbs/95/125781605.jpg) Machine Learning Bayesian Learning Bayes Theorem Bayesian Learning [Read Ch. 6] [Suggested exercises: 6.1, 6.2, 6.6] Prof. Dr. Martin Riedmiller AG Maschinelles Lernen und Natürlichsprachliche Systeme
Machine Learning Bayesian Learning Bayes Theorem Bayesian Learning [Read Ch. 6] [Suggested exercises: 6.1, 6.2, 6.6] Prof. Dr. Martin Riedmiller AG Maschinelles Lernen und Natürlichsprachliche Systeme
Evaluation. Andrea Passerini Machine Learning. Evaluation
 Andrea Passerini passerini@disi.unitn.it Machine Learning Basic concepts requires to define performance measures to be optimized Performance of learning algorithms cannot be evaluated on entire domain
Andrea Passerini passerini@disi.unitn.it Machine Learning Basic concepts requires to define performance measures to be optimized Performance of learning algorithms cannot be evaluated on entire domain
Reducing Multiclass to Binary: A Unifying Approach for Margin Classifiers
 Reducing Multiclass to Binary: A Unifying Approach for Margin Classifiers Erin Allwein, Robert Schapire and Yoram Singer Journal of Machine Learning Research, 1:113-141, 000 CSE 54: Seminar on Learning
Reducing Multiclass to Binary: A Unifying Approach for Margin Classifiers Erin Allwein, Robert Schapire and Yoram Singer Journal of Machine Learning Research, 1:113-141, 000 CSE 54: Seminar on Learning
CSE 417T: Introduction to Machine Learning. Final Review. Henry Chai 12/4/18
 CSE 417T: Introduction to Machine Learning Final Review Henry Chai 12/4/18 Overfitting Overfitting is fitting the training data more than is warranted Fitting noise rather than signal 2 Estimating! "#$
CSE 417T: Introduction to Machine Learning Final Review Henry Chai 12/4/18 Overfitting Overfitting is fitting the training data more than is warranted Fitting noise rather than signal 2 Estimating! "#$
The Online Approach to Machine Learning
 The Online Approach to Machine Learning Nicolò Cesa-Bianchi Università degli Studi di Milano N. Cesa-Bianchi (UNIMI) Online Approach to ML 1 / 53 Summary 1 My beautiful regret 2 A supposedly fun game I
The Online Approach to Machine Learning Nicolò Cesa-Bianchi Università degli Studi di Milano N. Cesa-Bianchi (UNIMI) Online Approach to ML 1 / 53 Summary 1 My beautiful regret 2 A supposedly fun game I
Online Passive- Aggressive Algorithms
 Online Passive- Aggressive Algorithms Jean-Baptiste Behuet 28/11/2007 Tutor: Eneldo Loza Mencía Seminar aus Maschinellem Lernen WS07/08 Overview Online algorithms Online Binary Classification Problem Perceptron
Online Passive- Aggressive Algorithms Jean-Baptiste Behuet 28/11/2007 Tutor: Eneldo Loza Mencía Seminar aus Maschinellem Lernen WS07/08 Overview Online algorithms Online Binary Classification Problem Perceptron
Machine Learning. Bayesian Learning.
 Machine Learning Bayesian Learning Prof. Dr. Martin Riedmiller AG Maschinelles Lernen und Natürlichsprachliche Systeme Institut für Informatik Technische Fakultät Albert-Ludwigs-Universität Freiburg Martin.Riedmiller@uos.de
Machine Learning Bayesian Learning Prof. Dr. Martin Riedmiller AG Maschinelles Lernen und Natürlichsprachliche Systeme Institut für Informatik Technische Fakultät Albert-Ludwigs-Universität Freiburg Martin.Riedmiller@uos.de
Machine Learning. Bayesian Learning. Acknowledgement Slides courtesy of Martin Riedmiller
 Machine Learning Bayesian Learning Dr. Joschka Boedecker AG Maschinelles Lernen und Natürlichsprachliche Systeme Institut für Informatik Technische Fakultät Albert-Ludwigs-Universität Freiburg jboedeck@informatik.uni-freiburg.de
Machine Learning Bayesian Learning Dr. Joschka Boedecker AG Maschinelles Lernen und Natürlichsprachliche Systeme Institut für Informatik Technische Fakultät Albert-Ludwigs-Universität Freiburg jboedeck@informatik.uni-freiburg.de
Multiclass Classification-1
 CS 446 Machine Learning Fall 2016 Oct 27, 2016 Multiclass Classification Professor: Dan Roth Scribe: C. Cheng Overview Binary to multiclass Multiclass SVM Constraint classification 1 Introduction Multiclass
CS 446 Machine Learning Fall 2016 Oct 27, 2016 Multiclass Classification Professor: Dan Roth Scribe: C. Cheng Overview Binary to multiclass Multiclass SVM Constraint classification 1 Introduction Multiclass
Bounded Kernel-Based Online Learning
 Journal of Machine Learning Research 10 (2009) 2643-2666 Submitted 12/08; Revised 9/09; Published 11/09 Bounded Kernel-Based Online Learning Francesco Orabona Joseph Keshet Barbara Caputo Idiap Research
Journal of Machine Learning Research 10 (2009) 2643-2666 Submitted 12/08; Revised 9/09; Published 11/09 Bounded Kernel-Based Online Learning Francesco Orabona Joseph Keshet Barbara Caputo Idiap Research
Minimax Fixed-Design Linear Regression
 JMLR: Workshop and Conference Proceedings vol 40:1 14, 2015 Mini Fixed-Design Linear Regression Peter L. Bartlett University of California at Berkeley and Queensland University of Technology Wouter M.
JMLR: Workshop and Conference Proceedings vol 40:1 14, 2015 Mini Fixed-Design Linear Regression Peter L. Bartlett University of California at Berkeley and Queensland University of Technology Wouter M.
Optimal and Adaptive Online Learning
 Optimal and Adaptive Online Learning Haipeng Luo Advisor: Robert Schapire Computer Science Department Princeton University Examples of Online Learning (a) Spam detection 2 / 34 Examples of Online Learning
Optimal and Adaptive Online Learning Haipeng Luo Advisor: Robert Schapire Computer Science Department Princeton University Examples of Online Learning (a) Spam detection 2 / 34 Examples of Online Learning
The Decision List Machine
 The Decision List Machine Marina Sokolova SITE, University of Ottawa Ottawa, Ont. Canada,K1N-6N5 sokolova@site.uottawa.ca Nathalie Japkowicz SITE, University of Ottawa Ottawa, Ont. Canada,K1N-6N5 nat@site.uottawa.ca
The Decision List Machine Marina Sokolova SITE, University of Ottawa Ottawa, Ont. Canada,K1N-6N5 sokolova@site.uottawa.ca Nathalie Japkowicz SITE, University of Ottawa Ottawa, Ont. Canada,K1N-6N5 nat@site.uottawa.ca
Online Learning Class 12, 20 March 2006 Andrea Caponnetto, Sanmay Das
 Online Learning 9.520 Class 12, 20 March 2006 Andrea Caponnetto, Sanmay Das About this class Goal To introduce the general setting of online learning. To describe an online version of the RLS algorithm
Online Learning 9.520 Class 12, 20 March 2006 Andrea Caponnetto, Sanmay Das About this class Goal To introduce the general setting of online learning. To describe an online version of the RLS algorithm
Learning noisy linear classifiers via adaptive and selective sampling
 Mach Learn (2011) 83: 71 102 DOI 10.1007/s10994-010-5191-x Learning noisy linear classifiers via adaptive and selective sampling Giovanni Cavallanti Nicolò Cesa-Bianchi Claudio Gentile Received: 13 January
Mach Learn (2011) 83: 71 102 DOI 10.1007/s10994-010-5191-x Learning noisy linear classifiers via adaptive and selective sampling Giovanni Cavallanti Nicolò Cesa-Bianchi Claudio Gentile Received: 13 January
Exploiting Feature Covariance in High-Dimensional Online Learning
 Justin Ma Alex Kulesza Mark Dredze UC San Diego University of Pennsylvania Johns Hopkins University jtma@cs.ucsd.edu kulesza@cis.upenn.edu mdredze@cs.jhu.edu Koby Crammer Lawrence K. Saul Fernando Pereira
Justin Ma Alex Kulesza Mark Dredze UC San Diego University of Pennsylvania Johns Hopkins University jtma@cs.ucsd.edu kulesza@cis.upenn.edu mdredze@cs.jhu.edu Koby Crammer Lawrence K. Saul Fernando Pereira
Analysis of perceptron-based active learning
 Analysis of perceptron-based active learning Sanjoy Dasgupta 1, Adam Tauman Kalai 2, and Claire Monteleoni 3 1 UCSD CSE 9500 Gilman Drive #0114, La Jolla, CA 92093 dasgupta@csucsdedu 2 TTI-Chicago 1427
Analysis of perceptron-based active learning Sanjoy Dasgupta 1, Adam Tauman Kalai 2, and Claire Monteleoni 3 1 UCSD CSE 9500 Gilman Drive #0114, La Jolla, CA 92093 dasgupta@csucsdedu 2 TTI-Chicago 1427
The No-Regret Framework for Online Learning
 The No-Regret Framework for Online Learning A Tutorial Introduction Nahum Shimkin Technion Israel Institute of Technology Haifa, Israel Stochastic Processes in Engineering IIT Mumbai, March 2013 N. Shimkin,
The No-Regret Framework for Online Learning A Tutorial Introduction Nahum Shimkin Technion Israel Institute of Technology Haifa, Israel Stochastic Processes in Engineering IIT Mumbai, March 2013 N. Shimkin,
Support vector machines Lecture 4
 Support vector machines Lecture 4 David Sontag New York University Slides adapted from Luke Zettlemoyer, Vibhav Gogate, and Carlos Guestrin Q: What does the Perceptron mistake bound tell us? Theorem: The
Support vector machines Lecture 4 David Sontag New York University Slides adapted from Luke Zettlemoyer, Vibhav Gogate, and Carlos Guestrin Q: What does the Perceptron mistake bound tell us? Theorem: The
Perceptron Mistake Bounds
 Perceptron Mistake Bounds Mehryar Mohri, and Afshin Rostamizadeh Google Research Courant Institute of Mathematical Sciences Abstract. We present a brief survey of existing mistake bounds and introduce
Perceptron Mistake Bounds Mehryar Mohri, and Afshin Rostamizadeh Google Research Courant Institute of Mathematical Sciences Abstract. We present a brief survey of existing mistake bounds and introduce
Instance-based Domain Adaptation via Multi-clustering Logistic Approximation
 Instance-based Domain Adaptation via Multi-clustering Logistic Approximation FENG U, Nanjing University of Science and Technology JIANFEI YU, Singapore Management University RUI IA, Nanjing University
Instance-based Domain Adaptation via Multi-clustering Logistic Approximation FENG U, Nanjing University of Science and Technology JIANFEI YU, Singapore Management University RUI IA, Nanjing University
CS 188: Artificial Intelligence. Outline
 CS 188: Artificial Intelligence Lecture 21: Perceptrons Pieter Abbeel UC Berkeley Many slides adapted from Dan Klein. Outline Generative vs. Discriminative Binary Linear Classifiers Perceptron Multi-class
CS 188: Artificial Intelligence Lecture 21: Perceptrons Pieter Abbeel UC Berkeley Many slides adapted from Dan Klein. Outline Generative vs. Discriminative Binary Linear Classifiers Perceptron Multi-class
Online Sparse Passive Aggressive Learning with Kernels
 Online Sparse Passive Aggressive Learning with Kernels Jing Lu Peilin Zhao Steven C.H. Hoi Abstract Conventional online kernel methods often yield an unbounded large number of support vectors, making them
Online Sparse Passive Aggressive Learning with Kernels Jing Lu Peilin Zhao Steven C.H. Hoi Abstract Conventional online kernel methods often yield an unbounded large number of support vectors, making them
PAC-learning, VC Dimension and Margin-based Bounds
 More details: General: http://www.learning-with-kernels.org/ Example of more complex bounds: http://www.research.ibm.com/people/t/tzhang/papers/jmlr02_cover.ps.gz PAC-learning, VC Dimension and Margin-based
More details: General: http://www.learning-with-kernels.org/ Example of more complex bounds: http://www.research.ibm.com/people/t/tzhang/papers/jmlr02_cover.ps.gz PAC-learning, VC Dimension and Margin-based
Efficient Semi-supervised and Active Learning of Disjunctions
 Maria-Florina Balcan ninamf@cc.gatech.edu Christopher Berlind cberlind@gatech.edu Steven Ehrlich sehrlich@cc.gatech.edu Yingyu Liang yliang39@gatech.edu School of Computer Science, College of Computing,
Maria-Florina Balcan ninamf@cc.gatech.edu Christopher Berlind cberlind@gatech.edu Steven Ehrlich sehrlich@cc.gatech.edu Yingyu Liang yliang39@gatech.edu School of Computer Science, College of Computing,
Active Online Classification via Information Maximization
 Proceedings of the Twenty-Second International Joint Conference on Artificial Intelligence Active Online Classification via Information Maimization Noam Slonim IBM Haifa Research Lab Haifa, Israel noams@il.ibm.com
Proceedings of the Twenty-Second International Joint Conference on Artificial Intelligence Active Online Classification via Information Maimization Noam Slonim IBM Haifa Research Lab Haifa, Israel noams@il.ibm.com
Sample and Computationally Efficient Active Learning. Maria-Florina Balcan Carnegie Mellon University
 Sample and Computationally Efficient Active Learning Maria-Florina Balcan Carnegie Mellon University Machine Learning is Shaping the World Highly successful discipline with lots of applications. Computational
Sample and Computationally Efficient Active Learning Maria-Florina Balcan Carnegie Mellon University Machine Learning is Shaping the World Highly successful discipline with lots of applications. Computational
Bandit Online Learning on Graphs via Adaptive Optimization
 Bandit Online Learning on Graphs via Adaptive Optimization Peng Yang, Peilin Zhao 2,3 and Xin Gao King Abdullah University of Science and Technology, Saudi Arabia 2 South China University of Technology,
Bandit Online Learning on Graphs via Adaptive Optimization Peng Yang, Peilin Zhao 2,3 and Xin Gao King Abdullah University of Science and Technology, Saudi Arabia 2 South China University of Technology,
Undirected Graphical Models
 Outline Hong Chang Institute of Computing Technology, Chinese Academy of Sciences Machine Learning Methods (Fall 2012) Outline Outline I 1 Introduction 2 Properties Properties 3 Generative vs. Conditional
Outline Hong Chang Institute of Computing Technology, Chinese Academy of Sciences Machine Learning Methods (Fall 2012) Outline Outline I 1 Introduction 2 Properties Properties 3 Generative vs. Conditional
Online Passive-Aggressive Algorithms. Tirgul 11
 Online Passive-Aggressive Algorithms Tirgul 11 Multi-Label Classification 2 Multilabel Problem: Example Mapping Apps to smart folders: Assign an installed app to one or more folders Candy Crush Saga 3
Online Passive-Aggressive Algorithms Tirgul 11 Multi-Label Classification 2 Multilabel Problem: Example Mapping Apps to smart folders: Assign an installed app to one or more folders Candy Crush Saga 3
Coactive Learning for Locally Optimal Problem Solving
 Coactive Learning for Locally Optimal Problem Solving Robby Goetschalckx, Alan Fern, Prasad adepalli School of EECS, Oregon State University, Corvallis, Oregon, USA Abstract Coactive learning is an online
Coactive Learning for Locally Optimal Problem Solving Robby Goetschalckx, Alan Fern, Prasad adepalli School of EECS, Oregon State University, Corvallis, Oregon, USA Abstract Coactive learning is an online
Lecture Support Vector Machine (SVM) Classifiers
 Introduction to Machine Learning Lecturer: Amir Globerson Lecture 6 Fall Semester Scribe: Yishay Mansour 6.1 Support Vector Machine (SVM) Classifiers Classification is one of the most important tasks in
Introduction to Machine Learning Lecturer: Amir Globerson Lecture 6 Fall Semester Scribe: Yishay Mansour 6.1 Support Vector Machine (SVM) Classifiers Classification is one of the most important tasks in
A Generalization of Principal Component Analysis to the Exponential Family
 A Generalization of Principal Component Analysis to the Exponential Family Michael Collins Sanjoy Dasgupta Robert E. Schapire AT&T Labs Research 8 Park Avenue, Florham Park, NJ 7932 mcollins, dasgupta,
A Generalization of Principal Component Analysis to the Exponential Family Michael Collins Sanjoy Dasgupta Robert E. Schapire AT&T Labs Research 8 Park Avenue, Florham Park, NJ 7932 mcollins, dasgupta,
A New Perspective on an Old Perceptron Algorithm
 A New Perspective on an Old Perceptron Algorithm Shai Shalev-Shwartz 1,2 and Yoram Singer 1,2 1 School of Computer Sci & Eng, The Hebrew University, Jerusalem 91904, Israel 2 Google Inc, 1600 Amphitheater
A New Perspective on an Old Perceptron Algorithm Shai Shalev-Shwartz 1,2 and Yoram Singer 1,2 1 School of Computer Sci & Eng, The Hebrew University, Jerusalem 91904, Israel 2 Google Inc, 1600 Amphitheater
Computational and Statistical Learning Theory
 Computational and Statistical Learning Theory TTIC 31120 Prof. Nati Srebro Lecture 17: Stochastic Optimization Part II: Realizable vs Agnostic Rates Part III: Nearest Neighbor Classification Stochastic
Computational and Statistical Learning Theory TTIC 31120 Prof. Nati Srebro Lecture 17: Stochastic Optimization Part II: Realizable vs Agnostic Rates Part III: Nearest Neighbor Classification Stochastic
Introduction to Machine Learning Lecture 13. Mehryar Mohri Courant Institute and Google Research
 Introduction to Machine Learning Lecture 13 Mehryar Mohri Courant Institute and Google Research mohri@cims.nyu.edu Multi-Class Classification Mehryar Mohri - Introduction to Machine Learning page 2 Motivation
Introduction to Machine Learning Lecture 13 Mehryar Mohri Courant Institute and Google Research mohri@cims.nyu.edu Multi-Class Classification Mehryar Mohri - Introduction to Machine Learning page 2 Motivation
Atutorialonactivelearning
 Atutorialonactivelearning Sanjoy Dasgupta 1 John Langford 2 UC San Diego 1 Yahoo Labs 2 Exploiting unlabeled data Alotofunlabeleddataisplentifulandcheap,eg. documents off the web speech samples images
Atutorialonactivelearning Sanjoy Dasgupta 1 John Langford 2 UC San Diego 1 Yahoo Labs 2 Exploiting unlabeled data Alotofunlabeleddataisplentifulandcheap,eg. documents off the web speech samples images
Littlestone s Dimension and Online Learnability
 Littlestone s Dimension and Online Learnability Shai Shalev-Shwartz Toyota Technological Institute at Chicago The Hebrew University Talk at UCSD workshop, February, 2009 Joint work with Shai Ben-David
Littlestone s Dimension and Online Learnability Shai Shalev-Shwartz Toyota Technological Institute at Chicago The Hebrew University Talk at UCSD workshop, February, 2009 Joint work with Shai Ben-David
Two Roles for Bayesian Methods
 Bayesian Learning Bayes Theorem MAP, ML hypotheses MAP learners Minimum description length principle Bayes optimal classifier Naive Bayes learner Example: Learning over text data Bayesian belief networks
Bayesian Learning Bayes Theorem MAP, ML hypotheses MAP learners Minimum description length principle Bayes optimal classifier Naive Bayes learner Example: Learning over text data Bayesian belief networks
6.036 midterm review. Wednesday, March 18, 15
 6.036 midterm review 1 Topics covered supervised learning labels available unsupervised learning no labels available semi-supervised learning some labels available - what algorithms have you learned that
6.036 midterm review 1 Topics covered supervised learning labels available unsupervised learning no labels available semi-supervised learning some labels available - what algorithms have you learned that
Worst-Case Analysis of the Perceptron and Exponentiated Update Algorithms
 Worst-Case Analysis of the Perceptron and Exponentiated Update Algorithms Tom Bylander Division of Computer Science The University of Texas at San Antonio San Antonio, Texas 7849 bylander@cs.utsa.edu April
Worst-Case Analysis of the Perceptron and Exponentiated Update Algorithms Tom Bylander Division of Computer Science The University of Texas at San Antonio San Antonio, Texas 7849 bylander@cs.utsa.edu April
Machine learning comes from Bayesian decision theory in statistics. There we want to minimize the expected value of the loss function.
 Bayesian learning: Machine learning comes from Bayesian decision theory in statistics. There we want to minimize the expected value of the loss function. Let y be the true label and y be the predicted
Bayesian learning: Machine learning comes from Bayesian decision theory in statistics. There we want to minimize the expected value of the loss function. Let y be the true label and y be the predicted
From Bandits to Experts: A Tale of Domination and Independence
 From Bandits to Experts: A Tale of Domination and Independence Nicolò Cesa-Bianchi Università degli Studi di Milano N. Cesa-Bianchi (UNIMI) Domination and Independence 1 / 1 From Bandits to Experts: A
From Bandits to Experts: A Tale of Domination and Independence Nicolò Cesa-Bianchi Università degli Studi di Milano N. Cesa-Bianchi (UNIMI) Domination and Independence 1 / 1 From Bandits to Experts: A
A simpler unified analysis of Budget Perceptrons
 Ilya Sutskever University of Toronto, 6 King s College Rd., Toronto, Ontario, M5S 3G4, Canada ILYA@CS.UTORONTO.CA Abstract The kernel Perceptron is an appealing online learning algorithm that has a drawback:
Ilya Sutskever University of Toronto, 6 King s College Rd., Toronto, Ontario, M5S 3G4, Canada ILYA@CS.UTORONTO.CA Abstract The kernel Perceptron is an appealing online learning algorithm that has a drawback:
Online Bayesian Passive-Aggressive Learning
 Online Bayesian Passive-Aggressive Learning Full Journal Version: http://qr.net/b1rd Tianlin Shi Jun Zhu ICML 2014 T. Shi, J. Zhu (Tsinghua) BayesPA ICML 2014 1 / 35 Outline Introduction Motivation Framework
Online Bayesian Passive-Aggressive Learning Full Journal Version: http://qr.net/b1rd Tianlin Shi Jun Zhu ICML 2014 T. Shi, J. Zhu (Tsinghua) BayesPA ICML 2014 1 / 35 Outline Introduction Motivation Framework
Efficient Bandit Algorithms for Online Multiclass Prediction
 Sham M. Kakade Shai Shalev-Shwartz Ambuj Tewari Toyota Technological Institute, 427 East 60th Street, Chicago, Illinois 60637, USA sham@tti-c.org shai@tti-c.org tewari@tti-c.org Keywords: Online learning,
Sham M. Kakade Shai Shalev-Shwartz Ambuj Tewari Toyota Technological Institute, 427 East 60th Street, Chicago, Illinois 60637, USA sham@tti-c.org shai@tti-c.org tewari@tti-c.org Keywords: Online learning,
Qualifying Exam in Machine Learning
 Qualifying Exam in Machine Learning October 20, 2009 Instructions: Answer two out of the three questions in Part 1. In addition, answer two out of three questions in two additional parts (choose two parts
Qualifying Exam in Machine Learning October 20, 2009 Instructions: Answer two out of the three questions in Part 1. In addition, answer two out of three questions in two additional parts (choose two parts
Gaussian processes. Chuong B. Do (updated by Honglak Lee) November 22, 2008
 Gaussian processes Chuong B Do (updated by Honglak Lee) November 22, 2008 Many of the classical machine learning algorithms that we talked about during the first half of this course fit the following pattern:
Gaussian processes Chuong B Do (updated by Honglak Lee) November 22, 2008 Many of the classical machine learning algorithms that we talked about during the first half of this course fit the following pattern:
10/05/2016. Computational Methods for Data Analysis. Massimo Poesio SUPPORT VECTOR MACHINES. Support Vector Machines Linear classifiers
 Computational Methods for Data Analysis Massimo Poesio SUPPORT VECTOR MACHINES Support Vector Machines Linear classifiers 1 Linear Classifiers denotes +1 denotes -1 w x + b>0 f(x,w,b) = sign(w x + b) How
Computational Methods for Data Analysis Massimo Poesio SUPPORT VECTOR MACHINES Support Vector Machines Linear classifiers 1 Linear Classifiers denotes +1 denotes -1 w x + b>0 f(x,w,b) = sign(w x + b) How
6.867 Machine learning
 6.867 Machine learning Mid-term eam October 8, 6 ( points) Your name and MIT ID: .5.5 y.5 y.5 a).5.5 b).5.5.5.5 y.5 y.5 c).5.5 d).5.5 Figure : Plots of linear regression results with different types of
6.867 Machine learning Mid-term eam October 8, 6 ( points) Your name and MIT ID: .5.5 y.5 y.5 a).5.5 b).5.5.5.5 y.5 y.5 c).5.5 d).5.5 Figure : Plots of linear regression results with different types of
Gaussian Models
 Gaussian Models ddebarr@uw.edu 2016-04-28 Agenda Introduction Gaussian Discriminant Analysis Inference Linear Gaussian Systems The Wishart Distribution Inferring Parameters Introduction Gaussian Density
Gaussian Models ddebarr@uw.edu 2016-04-28 Agenda Introduction Gaussian Discriminant Analysis Inference Linear Gaussian Systems The Wishart Distribution Inferring Parameters Introduction Gaussian Density
Machine Learning, Fall 2012 Homework 2
 0-60 Machine Learning, Fall 202 Homework 2 Instructors: Tom Mitchell, Ziv Bar-Joseph TA in charge: Selen Uguroglu email: sugurogl@cs.cmu.edu SOLUTIONS Naive Bayes, 20 points Problem. Basic concepts, 0
0-60 Machine Learning, Fall 202 Homework 2 Instructors: Tom Mitchell, Ziv Bar-Joseph TA in charge: Selen Uguroglu email: sugurogl@cs.cmu.edu SOLUTIONS Naive Bayes, 20 points Problem. Basic concepts, 0
COMS 4771 Introduction to Machine Learning. Nakul Verma
 COMS 4771 Introduction to Machine Learning Nakul Verma Announcements HW1 due next lecture Project details are available decide on the group and topic by Thursday Last time Generative vs. Discriminative
COMS 4771 Introduction to Machine Learning Nakul Verma Announcements HW1 due next lecture Project details are available decide on the group and topic by Thursday Last time Generative vs. Discriminative
Mining Classification Knowledge
 Mining Classification Knowledge Remarks on NonSymbolic Methods JERZY STEFANOWSKI Institute of Computing Sciences, Poznań University of Technology COST Doctoral School, Troina 2008 Outline 1. Bayesian classification
Mining Classification Knowledge Remarks on NonSymbolic Methods JERZY STEFANOWSKI Institute of Computing Sciences, Poznań University of Technology COST Doctoral School, Troina 2008 Outline 1. Bayesian classification
Lecture 3: Multiclass Classification
 Lecture 3: Multiclass Classification Kai-Wei Chang CS @ University of Virginia kw@kwchang.net Some slides are adapted from Vivek Skirmar and Dan Roth CS6501 Lecture 3 1 Announcement v Please enroll in
Lecture 3: Multiclass Classification Kai-Wei Chang CS @ University of Virginia kw@kwchang.net Some slides are adapted from Vivek Skirmar and Dan Roth CS6501 Lecture 3 1 Announcement v Please enroll in
Comparison of Modern Stochastic Optimization Algorithms
 Comparison of Modern Stochastic Optimization Algorithms George Papamakarios December 214 Abstract Gradient-based optimization methods are popular in machine learning applications. In large-scale problems,
Comparison of Modern Stochastic Optimization Algorithms George Papamakarios December 214 Abstract Gradient-based optimization methods are popular in machine learning applications. In large-scale problems,
Imitation Learning by Coaching. Abstract
 Imitation Learning by Coaching He He Hal Daumé III Department of Computer Science University of Maryland College Park, MD 20740 {hhe,hal}@cs.umd.edu Abstract Jason Eisner Department of Computer Science
Imitation Learning by Coaching He He Hal Daumé III Department of Computer Science University of Maryland College Park, MD 20740 {hhe,hal}@cs.umd.edu Abstract Jason Eisner Department of Computer Science
A Bound on the Label Complexity of Agnostic Active Learning
 A Bound on the Label Complexity of Agnostic Active Learning Steve Hanneke March 2007 CMU-ML-07-103 School of Computer Science Carnegie Mellon University Pittsburgh, PA 15213 Machine Learning Department,
A Bound on the Label Complexity of Agnostic Active Learning Steve Hanneke March 2007 CMU-ML-07-103 School of Computer Science Carnegie Mellon University Pittsburgh, PA 15213 Machine Learning Department,
Linear smoother. ŷ = S y. where s ij = s ij (x) e.g. s ij = diag(l i (x))
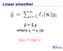 Linear smoother ŷ = S y where s ij = s ij (x) e.g. s ij = diag(l i (x)) 2 Online Learning: LMS and Perceptrons Partially adapted from slides by Ryan Gabbard and Mitch Marcus (and lots original slides by
Linear smoother ŷ = S y where s ij = s ij (x) e.g. s ij = diag(l i (x)) 2 Online Learning: LMS and Perceptrons Partially adapted from slides by Ryan Gabbard and Mitch Marcus (and lots original slides by
Nonparametric Bayesian Methods (Gaussian Processes)
 [70240413 Statistical Machine Learning, Spring, 2015] Nonparametric Bayesian Methods (Gaussian Processes) Jun Zhu dcszj@mail.tsinghua.edu.cn http://bigml.cs.tsinghua.edu.cn/~jun State Key Lab of Intelligent
[70240413 Statistical Machine Learning, Spring, 2015] Nonparametric Bayesian Methods (Gaussian Processes) Jun Zhu dcszj@mail.tsinghua.edu.cn http://bigml.cs.tsinghua.edu.cn/~jun State Key Lab of Intelligent
SVAN 2016 Mini Course: Stochastic Convex Optimization Methods in Machine Learning
 SVAN 2016 Mini Course: Stochastic Convex Optimization Methods in Machine Learning Mark Schmidt University of British Columbia, May 2016 www.cs.ubc.ca/~schmidtm/svan16 Some images from this lecture are
SVAN 2016 Mini Course: Stochastic Convex Optimization Methods in Machine Learning Mark Schmidt University of British Columbia, May 2016 www.cs.ubc.ca/~schmidtm/svan16 Some images from this lecture are
Online Passive-Aggressive Algorithms
 Online Passive-Aggressive Algorithms Koby Crammer Ofer Dekel Joseph Keshet Shai Shalev-Shwartz Yoram Singer School of Computer Science and Engineering The Hebrew University Jerusalem, 91904, Israel CRAMMER@CIS.UPENN.EDU
Online Passive-Aggressive Algorithms Koby Crammer Ofer Dekel Joseph Keshet Shai Shalev-Shwartz Yoram Singer School of Computer Science and Engineering The Hebrew University Jerusalem, 91904, Israel CRAMMER@CIS.UPENN.EDU
Foundations of Machine Learning On-Line Learning. Mehryar Mohri Courant Institute and Google Research
 Foundations of Machine Learning On-Line Learning Mehryar Mohri Courant Institute and Google Research mohri@cims.nyu.edu Motivation PAC learning: distribution fixed over time (training and test). IID assumption.
Foundations of Machine Learning On-Line Learning Mehryar Mohri Courant Institute and Google Research mohri@cims.nyu.edu Motivation PAC learning: distribution fixed over time (training and test). IID assumption.
Sparse Linear Contextual Bandits via Relevance Vector Machines
 Sparse Linear Contextual Bandits via Relevance Vector Machines Davis Gilton and Rebecca Willett Electrical and Computer Engineering University of Wisconsin-Madison Madison, WI 53706 Email: gilton@wisc.edu,
Sparse Linear Contextual Bandits via Relevance Vector Machines Davis Gilton and Rebecca Willett Electrical and Computer Engineering University of Wisconsin-Madison Madison, WI 53706 Email: gilton@wisc.edu,
Machine Learning Lecture 6 Note
 Machine Learning Lecture 6 Note Compiled by Abhi Ashutosh, Daniel Chen, and Yijun Xiao February 16, 2016 1 Pegasos Algorithm The Pegasos Algorithm looks very similar to the Perceptron Algorithm. In fact,
Machine Learning Lecture 6 Note Compiled by Abhi Ashutosh, Daniel Chen, and Yijun Xiao February 16, 2016 1 Pegasos Algorithm The Pegasos Algorithm looks very similar to the Perceptron Algorithm. In fact,
Online Learning, Mistake Bounds, Perceptron Algorithm
 Online Learning, Mistake Bounds, Perceptron Algorithm 1 Online Learning So far the focus of the course has been on batch learning, where algorithms are presented with a sample of training data, from which
Online Learning, Mistake Bounds, Perceptron Algorithm 1 Online Learning So far the focus of the course has been on batch learning, where algorithms are presented with a sample of training data, from which
Online and Stochastic Learning with a Human Cognitive Bias
 Proceedings of the Twenty-Eighth AAAI Conference on Artificial Intelligence Online and Stochastic Learning with a Human Cognitive Bias Hidekazu Oiwa The University of Tokyo and JSPS Research Fellow 7-3-1
Proceedings of the Twenty-Eighth AAAI Conference on Artificial Intelligence Online and Stochastic Learning with a Human Cognitive Bias Hidekazu Oiwa The University of Tokyo and JSPS Research Fellow 7-3-1
Active Learning: Disagreement Coefficient
 Advanced Course in Machine Learning Spring 2010 Active Learning: Disagreement Coefficient Handouts are jointly prepared by Shie Mannor and Shai Shalev-Shwartz In previous lectures we saw examples in which
Advanced Course in Machine Learning Spring 2010 Active Learning: Disagreement Coefficient Handouts are jointly prepared by Shie Mannor and Shai Shalev-Shwartz In previous lectures we saw examples in which
Neural Networks. CSE 6363 Machine Learning Vassilis Athitsos Computer Science and Engineering Department University of Texas at Arlington
 Neural Networks CSE 6363 Machine Learning Vassilis Athitsos Computer Science and Engineering Department University of Texas at Arlington 1 Perceptrons x 0 = 1 x 1 x 2 z = h w T x Output: z x D A perceptron
Neural Networks CSE 6363 Machine Learning Vassilis Athitsos Computer Science and Engineering Department University of Texas at Arlington 1 Perceptrons x 0 = 1 x 1 x 2 z = h w T x Output: z x D A perceptron
Linear Regression (continued)
 Linear Regression (continued) Professor Ameet Talwalkar Professor Ameet Talwalkar CS260 Machine Learning Algorithms February 6, 2017 1 / 39 Outline 1 Administration 2 Review of last lecture 3 Linear regression
Linear Regression (continued) Professor Ameet Talwalkar Professor Ameet Talwalkar CS260 Machine Learning Algorithms February 6, 2017 1 / 39 Outline 1 Administration 2 Review of last lecture 3 Linear regression
MIRA, SVM, k-nn. Lirong Xia
 MIRA, SVM, k-nn Lirong Xia Linear Classifiers (perceptrons) Inputs are feature values Each feature has a weight Sum is the activation activation w If the activation is: Positive: output +1 Negative, output
MIRA, SVM, k-nn Lirong Xia Linear Classifiers (perceptrons) Inputs are feature values Each feature has a weight Sum is the activation activation w If the activation is: Positive: output +1 Negative, output
