Reachability Results for Timed Automata with Unbounded Data Structures
|
|
|
- Jordan Bishop
- 5 years ago
- Views:
Transcription
1 Acta Informatica manuscript No. (will be inserted by the editor) Reachability Results for Timed Automata with Unbounded Data Structures Ruggero Lanotte Andrea Maggiolo-Schettini Angelo Troina Received: date / Accepted: date Abstract Systems of Data Management Timed Automata (SDMTAs) are networks of communicating timed automata with structures to store messages and functions to manipulate them. We prove the decidability of the reachability problem for a subclass of SDMTAs which assumes an unbounded knowledge, and we analyze the expressiveness of the model and the considered subclass. In particular, while SDMTAs can simulate a Turing machine, and hence the reachability problem is in general undecidable, the subclass for which reachability is decidable, when endowed with a concept of recognized language, accepts languages that are not regular. As an application, we model and analyze a variation of the Yahalom protocol. Keywords Timed Automata Vector Addition Systems Unbounded Data Structures 1 Introduction Automata based formalisms have been successfully used to describe concurrent and distributed systems and analyze their properties. Basic formalisms allow describing the nondeterministic behaviour of a system. This is enough to model the functionality of systems, and hence to capture the qualitative behaviour of a system, but if one wants to capture also time-dependent behaviour, formalisms must be extended with real-time features. Alur and Dill have proposed Timed Automata [4]. In general, timed automata models have an infinite state space. However the region automaton construction shows Ruggero Lanotte Dipartimento di Informatica e Comunicazione, Università dell Insubria Via Carloni 78, Como, Italy ruggero.lanotte@uninsubria.it Andrea Maggiolo-Schettini Dipartimento di Informatica, Università di Pisa Largo B. Pontecorvo 3, Pisa, Italy maggiolo@di.unipi.it Angelo Troina Dipartimento di Informatica, Università di Torino Corso Svizzera 185, Torino, Italy troina@di.unito.it
2 2 that this infinite state space can be mapped to an automaton with a finite number of equivalence classes (regions) as states, and finite-state model checking techniques can be applied to the reduced finite region automaton. Among the model checkers for timed automata we quote Kronos [25] and UPPAAL [5]. Systems of communicating agents can be described by automata composed in parallel and sharing synchronization channels. Transitions labelled with complementary channel names can be taken at the same moment and data transmission is typically modelled by a synchronization, where global variables are updated [10]. In this paper we define Systems of Data Management Timed Automata (SDMTAs). An SDMTA has a finite set of elementary messages, a finite set of functions to elaborate them, and a finite set of Data Management Timed Automata (DMTAs). Each DMTA has a finite set of channel labels, a finite set of clocks, a finite set of states (one of them is the initial state), and a finite set of transitions. Transitions from state to state of a DMTA represent either an internal move with the computation of a term (which enriches the knowledge of the automaton) or the input or the output of a term on a channel. The execution of a transition is conditioned by the fulfillment of a constraint. Two DMTAs of a system may perform a communication step modeling the communication of a term through a channel. Time elapsing is modelled by a time step of the automata of the system. Both the term domain (which may include any natural value) and the store of a DMTA are unbounded. We show that SDMTAs can simulate Turing machines, hence the reachability problem for SDMTAs is, in general, undecidable. However, we consider a subclass of SDM- TAs called 1-SDMTAs (where only one integer variable can occur) for which we are able to show that the reachability problem is decidable. Since we cannot simulate unbounded knowledge with a finite state machine, we prove the decidability result by reducing 1-SDMTAs to Vector Addition Systems (VASs). As we are dealing with a dense time model and exponential reductions to VASs, large 1-SDMTAs we will hardly be practically amenable for automated verification techniques. Moreover, we prove that our formalism extends the formalism of [21] in order to deal with a general class of distributed communicating systems with data structures. Actually, the formalism of [21] assumes bounded knowledge and has the power of regular languages, while the decidable class of 1-SDMTAs assumes an unbounded knowledge and, when endowed with a concept of recognized language, accepts languages that are not regular. With the purpose of modeling general systems, we consider the most general time model, hence the dense time model. The results in this paper hold also if one considers a discrete-time model. Actually, the undecidability result does not depend on the choice of the time model. Moreover, decidability results for a dense-time model imply decidability of the discrete time model. Finally, the problem still has the same complexity, since changing from dense to discrete time does not simplify the construction. Our purpose is to lay the foundations of a general model where features of time and information storage are considered. The applications of SDMTAs in the modelling and verification of realistic systems can be applied in any context where it is important to keep track of the timing behaviour of a system or of the information it may store. The first field that comes to mind is that of security analysis, where the information circulating on the network and the knowledge of the adversary should be modelled. Actually, time aspects can influence the flow of messages during the execution of a protocol. For instance, if a message does not arrive in a certain time interval, retransmissions or other behaviour should be considered and, in this case, the protocol specification should model these implementation details. Time information can also be
3 3 used within a protocol in order to enrich the information contained in a message (for example by constructing timestamps). Finally, the timing of the message flow may be exploited by an adversary to violate the security of the protocol. As an example we model and analyze with SDMTAs a version of the well-known Yahalom protocol adapted to take timeouts and retransmissions into account. 1.1 Related Works A preliminary version of this paper appeared in [19]. Among the frameworks which aim at describing timed systems with data structures, we may cite the following ones. In [21] the authors propose a model of communicating automata tailored for describing and analyzing protocols with timing constraints and verifying their security. Each participant in the protocol is described by a state transition diagram where transitions are labelled by events which represent the sending of a structured message along a channel. The performance of a transition is conditioned by the trigger of a communication event and by the temporal constraints imposed by a delay and/or timeout. Communication is synchronous. Primitive messages (public/private keys, identities, nonces, etc.) can be composed by using cryptographic primitives (encryption, hashing, signature, etc.). An initial evidence function assigns each initial state the set of evidence that is known by each participant at the beginning. Such evidence can be augmented by receiving messages from other participants and is reset to the initial conditions every time an input state is reached. The semantics of these descriptions is given in terms of Timed Automata, thus obtaining a specification on which properties can be verified. Our formalism extends the formalism of [21] to deal with a general class of distributed communicating systems with data structures. Note that the formalism of [21] assumes a bounded memory and has the power of regular languages, while our formalism assumes an unbound memory and, when endowed with a concept of recognized language, does accept languages which are not regular. Differently with respect to [21], we define a direct operational semantics of SDMTAs in terms of steps and runs, and we prove the decidability of the reachability. This allows proving properties expressible in terms of reached states. In [12], a model of Pushdown Timed Automata, i.e. Timed Automata augmented with a pushdown stack, is considered and a decidable characterization for reachability is given. In [8], the authors study the class of Pushdown Counter Linear Hybrid Systems, i.e. linear hybrid systems equipped with a stack and integer counters. Decidability of invariance/reachability properties of some subclasses of this model are proved. The considered subclasses are Timed Automata equipped with a stack and integer monotonic variables. In [15], similar results for Timed Automata with discrete clocks are proved. In [18], the author considers the class of Hybrid Systems (i.e. Timed Automata where variables can evolve by following general evolution laws) equipped with arrays. For this kind of systems the reachability problem is undecidable. However, an algorithm based on predicate transformation is provided for computing the successor operator (which implies the semidecidability of the reachability problem). Moreover, more
4 4 general data-structures can be handled since, by using arrays, one can simulate stacks, queues, etc.. Communicating Timed Automata (CTAs) are systems of Timed Automata that can send/receive messages exchanged via unbounded FIFO channels [17]. While CTAs with two (or more) channels have the power of Turing machines, state reachability is decidable for CTAs with just one channel (as it happens for 1-SDMTAs). Among the differences between the model of CTAs and the model of SDMTAs introduced in the present paper (whose preliminary version appeared in [19]) is that in CTAs the local store is not unbounded, namely, even if channels are not bounded, the Communicating Timed Automata can only operate on the head of a channel buffer. Moreover, the domain of the messages that could be sent/received by CTAs is finite. In [2] a method for deciding reachability properties of networks of timed processes is presented. Such a network consists of an arbitrary set of identical timed automata, each with a single real-valued clock. Their systems are infinite state in two directions. They contain an arbitrary set of processes, and they use infinite data structures, namely real valued clocks. In [3] data structures and real time features are studied in an original combination of three well established formal techniques for the specification of concurrent processes: Hoare s CSP, Object-Z [23] and the Duration Calculus [26]. 2 Basic Notions Let us assume a set X of positive real variables x called clocks. A valuation over a set of clocks is a mapping v : X IR 0 assigning real values to clocks. For a valuation v and a time value t IR 0, let v +t denote the valuation such that (v +t)(x) = v(x)+t, for each clock x X. Let C = {C 1,..., C m} be a finite set of disjoint sets where C i denotes a finite set of elementary messages. By an elementary message we mean a non composed/manipulated message (i.e., names are elementary messages, lists of elementary messages are not). Let us assume a set Υ of message variables µ that can take values in ( m j=1 C j) IN. Given a finite set of message variables, an instance I relates a message variable µ to a value in ( m j=1 C j) IN. Namely, I : Υ ( m j=1 C j) IN. Let Ω = {f 1,..., f n} denote a finite set of function symbols. Given a finite set of message variables Υ, the set of terms T (Υ ) is defined as: τ ::= c w µ f(τ 1,..., τ k ) where c C i for some i, w IN, µ Υ is a message variable, f is a function in Ω with arity k. We use C and Ω to represent a set of data structures and a set of functions to manipulate such structures. In general, C may be any set of data structures of different types and Ω may be any set of functions representing operations on such structures. Example 1 Consider C = {m 1, m 2,...} a set of basic messages (i.e. a set of plaintext messages represented by bitstrings of a fixed length). In a framework where agents exchange messages, we want to describe concatenations of messages and the possibility of distinguishing two messages sent at different
5 5 instants of time (this is done usually with a time stamp or a nonce in a security protocol). Hence we assume Ω = {P air, Occurrence}. P air(τ 1, τ 2 ) denotes the concatenation of the terms τ 1 and τ 2, and, Occurrence(τ, n), with n IN, associates with τ a natural number in such a way that Occurrence(τ, n) and Occurrence(τ, n ) with n n are distinguishable. With V ar(τ) we denote the message variables appearing in the term τ. For example, we have that V ar(p air(µ 1, Occurrence(µ 2, 100)) = {µ 1, µ 2 }. We say that two terms τ and τ in T (Υ ) are reducible (written τ τ ) if they have the same structure, namely τ τ if there exist variables µ 1,..., µ n and µ 1,..., µ n Υ such that τ = τ [µ 1 /µ 1 ]... [µ n /µ n ]. Finally, with K we denote a knowledge. A knowledge K T (Υ ) is a finite set of terms τ such that V ar(τ) =. Given a finite set of clocks X and a finite set of message variables Υ, we define the set Φ(X, Υ ) of formulae as follows: φ ::= true τ K τ = τ µ IN x c x y + c φ φ 1 φ 2 φ 1 φ 2 where φ, φ 1, φ 2 Φ(X, Υ ), τ, τ T (Υ ), µ Υ, x, y X, {<,, =,, >} and c Q (note that for decidability results c cannot be a real number). The difference between K and K is that K is a metavariable occurring in the conditions Φ(X, Υ ) and K (or K i with i = 1,..., m when we have a parallel compositions of m components) is a knowledge instance of K. This is necessary, since using the same notation could be ambiguous. We will write τ τ for (τ = τ ), µ IN for (µ IN), and τ {τ 1,..., τ k } for τ = τ 1... τ = τ k. As an example, with τ C i, for some i, we denote the formula m C i τ = m. Given a term τ and an instance I, we define the instantiation of τ as I(τ) = τ, where τ is the term resulting after each µ syntactically occurring in τ is replaced with I(µ). Example 2 Given the instance I such that I(µ 1 ) = 10 and I(µ 2 ) = msg for an elementary message msg C, then: I(P air(µ 1, Occurrence(µ 2, 100))) = P air(10, Occurence(msg, 100)). We recall that since a message variable cannot be instantiated with a term, there is no instance I such that I (P air(µ 1, µ 2 )) = P air(10, Occurrence(msg, 100)). Actually, I cannot assign the term Occurrence(msg, 100) to µ 2. Let φ Φ(X, Υ ), I be an instance, v a valuation of clocks, and K a knowledge; we say that I, v and K satisfy φ, written I, v, K = φ, in the following cases: I, v, K = true I, v, K = τ K iff I(τ) K I, v, K = τ = τ iff I(τ) = I(τ ) I, v, K = µ IN iff I(µ) IN I, v, K = x c iff v(x) c I, v, K = x y iff v(x) v(y) I, v, K = φ 1 iff I, v, K = φ 1 I, v, K = φ 1 φ 2 iff either I, v, K = φ 1 or I, v, K = φ 2 I, v, K = φ 1 φ 2 iff both I, v, K = φ 1 and I, v, K = φ 2.
6 6 Example 3 The formula µ 1 µ 2 µ 1 K µ 2 K says that in the knowledge K there are at least two elementary messages. 3 Data Management Timed Automata Given a finite set of clocks X and a finite set of message variables Υ, with X and Υ we denote new sets of clocks and message variables such that x X and µ Υ iff x X and µ Υ, respectively. A System of Data Management Timed Automata (SDMTA) is a tuple expressed by A = (C, Ω, A 1,..., A m), where: C = {C 1,..., C k } is a set of elementary messages; Ω = {f 1,..., f n } is a set of functions; A 1,..., A m are Data Management Timed Automata (DMTAs). A DMTA is a tuple A = (Σ, X, Υ, Q, q 0, δ), where: Σ is a finite set of channel labels; X is a finite set of clocks; Υ is a finite set of message variables; Q is a finite set of states with q 0 Q initial state; δ is a finite set of transitions. Each transition is a tuple (q, α, φ, q ), where q, q Q are the source and the target states respectively, for a Σ, α {ɛ(τ), a?(τ), a!(τ)} represents, respectively, an internal move producing the term τ, which enriches the knowledge of A, or the input or the output of the term τ T (Υ ) on channel a, φ is a formula in Φ(X X, Υ Υ ). Variables in X Υ and in X Υ represent the value of variables before and after the firing of the transition, respectively. An example transition is (q 0, a!(f(µ)), x < 5 µ K x = x µ IN, q 1 ), stating that from the initial state q 0 the DMTA may reach state q 1 and output a message f(µ) when µ K and x < 5. The condition x = x means that the transition does not change the clock x, and the condition µ IN means that the variable µ nondeterministically assumes a natural number as value after the transition. Given an SDMTA A = (C, Ω, A 1,..., A m ), the states of A are represented by tuples (q 1,..., q m), where q i Q i, where Q i is the set of states of A i. 3.1 Semantics Given two valuations v 1, v 2 over X, with v 1 v 2 we denote the valuation on X X such that for any x X, (v 1 v 2 )(x) = v 1 (x) and (v 1 v 2 )(x ) = v 2 (x). The idea is the the operator is to split the valuation on X X in two parts, one arguing on the actual values of the clocks and one arguing on the values of the clocks after the step (hence the value of clocks in X ). In a similar manner we can define the same operator for the instances. Actually, given two instances I 1, I 2 over Υ, with I 1 I 2 we denote the instance over Υ Υ such that for any µ Υ, (I 1 I 2 )(µ) = I 1 (µ) and (I 1 I 2 )(µ ) = I 2 (µ). A configuration of an SDMTA A = (C, Ω, A 1,..., A m) with DMTAs defined as A i = (Σ i, X i, Υ i, Q i, q i 0, φi 0, Ki 0, δi ), is a tuple (s 1,..., s m ) such that s i = (q, v, I, K) is
7 7 a configuration of the DMTA A i with q Q i a state of A i, v a valuation over X i, I an instance over Υ i and K a knowledge. We have three kinds of steps: ɛ-transition steps, communication transition steps and time steps. An ɛ-transition step is performed by one only component when a transition labeled with ɛ is performable. A communication transition step consists in a synchronization with message exchange between two components. Time steps represent the elapsing of time. Given two configurations s = (s 1,..., s m ) and s = (s 1,..., s m) such that s i = (q i, v i, I i, K i ) and s i = (q i, v i, I i, K i ), we have that: there is an ɛ-transition step from s to s (denoted s τ s ) if there exists an index i and a transition e = (q i, ɛ(τ 1 ), φ, q i ) δi such that I i (τ 1 ) = τ, (I i I i ), (v i v i ), K i = φ, K i = K i {τ} and, for all j i, s j = s j; there is a communication transition step from s to s on channel a with term τ (denoted s a(τ) s ) if there exist two different indexes i and j, (q i, a!(τ 1 ), φ 1, q i ) δ i and (q j, a?(τ 2 ), φ 2, q j ) δj such that: τ 1 τ 2 and I i (τ 1 ) = I j (τ 2 ) = τ; (I i I i ), (v i v i ), K i = φ 1 and (I j I j ), (v j v j ), K j = φ 2, K i = K i {τ} and K j = K j {τ}; for all k {i, j}, it holds that s k = s k; there is a time step from s to s with delay t IR >0, written s t s, if, for any i, q i = q i, v i = (v i + t), I i = I i, and K i = K i. With the ɛ-transition step we model the internal data manipulation executed by a DMTA without communication. For example, given a configuration (q, v, I, K), transition (q, ɛ(µ 1 ), φ, q ), where φ = P air(µ 1, µ 2 ) K, states that if (I I ), (v v ), K = φ, the DMTA may enrich its knowledge with the left part of a concatenated message. A communication transition step a(τ) models the communication of term τ on channel a. There is a synchronization between two DMTAs, and they both change their configuration by following the formula in the transition and by augmenting their knowledge. If variables appear in the output and input terms (τ 1 and τ 2, respectively), they should be reducible for transmission. Hence, we require that τ τ and that I i (τ 1 ) = I j (τ 2 ) (also see Example 4). The DMTAs of the system not involved in the communication remain in their respective original configurations. Although it is often the case that the parties involved in a communication send data which are already present in their knowledge, our semantics allows a component to send a message even if this is not within its knowledge. As a consequence, components are able to provide new messages. This is necessary when fresh terms (for example nonces or keys in cryptographic protocols) should be created. On the other hand, one can always impose that a term to be exchanged is within the knowledge of the sending component by imposing it on the transition guard (i.e. through the formula τ K). Finally, a time step models time elapsing. When time elapses we assume that each DMTA A i in the system performs a time step by changing its valuation v i. Sometimes, an initial condition and, in our case, also an initial knowledge could be introduced in the definition. The purpose of these conditions is to initialize the variables and the knowledge. It is obvious that, if one wants to simulate an initial knowledge and initial values for clocks and variables, it is sufficient to create a sequence of new initial states linked by new transitions initializing knowledge, clocks and variables.
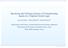
8 8 A 1 A 2 q 1 a!(k) q 0 a!(occurrence(b, 10)) x > 5 q 2 r 1 a?(occurrence(µ 1, µ 2 )) a?(µ) r 0 r 2 a?(occurrence(c, µ 1 )) r 3 Fig. 1 A System of Data Management Timed Automata. Example 4 Consider the DMTAs A 1 and A 2 in Figure 1, where q 0 and r 0 are the initial states of A 1 and A 2, respectively. The only communications that may happen between A 1 and A 2 through synchronization steps of matching terms are either a(occurrence(b, 10)) (synchronizing with the transition from r 0 to r 1 when x has value greater than 5) or a(k) (synchronizing with the transition from r 0 to r 2 ). In the first case, variable µ 1 is instantiated with value b and variable µ 2 with the natural number value 10, in the second case, variable µ assumes the value k. In both cases, the knowledge of A 2 is augmented with the term received by A 1. Given a DMTA A = (Σ, X, Υ, Q, q 0, δ), a configuration s = (q 0, v, I, K) of A is initial if I(µ) = 0, for any µ, v(x) = 0, for any x, and, K =. Given an SDMTA A = (C, Ω, A 1,..., A m), we say that the configuration s = (s 1,..., s m) of A is initial iff s i is an initial configuration of the DMTA A i for all i [1, m]. A run of an SDMTA A is a finite sequence of steps σ = s 0 α1 s 1 α2... αl s l, where s 0 is an initial configuration of A, s j is a configuration of A and α j {τ, a(τ)} IR >0 for each j [1, l]. A state q = (q 1,..., q m ) of an SDMTA A is reachable iff there is a run σ = (s 1 0,..., sm 0 ) α 1... αl (s 1 l,..., sm l ) of A such that, for any i, if s i l = (q, v, I, K), then q = q i. A state q of a DMTA A i in the SDMTA A is reachable iff there is a run σ = (s 1 0,..., sm 0 ) α 1... αl (s 1 l,..., sm l ) of A such that s i l = (q, v, I, K), for some v, I, K. 3.2 n-sdmtas We define the class of n-sdmtas. The idea is that an n-sdmta can store in its knowledge an unbounded number of occurrences of instances of a term τ by varying in an unbounded manner at most n arguments of τ. As an example the term f(2) has a finite number of instances, while f(µ) has an unbounded number of instances (and hence in the knowledge we can have an unbounded number of occurrences of instances of f(µ)) if µ can be a natural number.
9 9 If we consider the term g(µ 1, 5, µ 2 ), then also in this case the term has an unbounded number of instances but the degrees of freedom are double with respect f(µ). Actually in g(µ 1, 5, µ 2 ) we have two possible natural variables against the one of f(µ). The idea is that the class n-sdmtas has n different natural variables appearing contemporarily in the same term. With the purpose of defining the class of n-sdmtas we define a function natv ar. Given a term τ and a set of instances I, with natv ar(τ, I) we denote the maximum number of natural number variables that can appear in τ w.r.t. instances in I, namely, max I I {µ µ V ar(τ) and I(µ) IN}. We can extend this definition on φ as follows: natv ar(true, I), µ IN, x c and x y is equal to 0; natv ar(τ K, I) is equal to natv ar(τ, I); natv ar(τ = τ, I) is equal to the maximum between natv ar(τ, I) and natv ar(τ, I); natv ar(φ 1 φ 2, I) and natv ar(φ 1 φ 2, I) is equal to the maximum between natv ar(φ 1, I) and natv ar(φ 2, I); natv ar( φ 1, I) is equal to natv ar(φ 1, I). When we omit the set of instances I we consider the case in which I = {I I = φ}. Hence, with natv ar(φ) we denote the maximum number of natural number variables that can appear simultaneously in a term in φ. Namely, natv ar(φ) = natv ar(φ, {I I = φ}). As an example, natv ar(f(µ, µ ) K) = 2 and natv ar(f(µ, µ ) K µ IN) = 1. In the condition f(µ, µ ) K both µ and µ can assume contemporarily natural number values. On the contrary, in the condition f(µ, µ ) K µ IN only µ can assume natural number values thanks to the subformula µ IN. With F orm(a) we denote the set of formulas φ appearing in the transitions of A. Finally, we can extend this definition to SDMTAs and DMTAs. Definition 1 With n-sdmtas (resp. n-dmtas) we denote the class of automata A such that ( max φ F orm(a) natv ar(φ) ) = n. 3.3 n-standard Form for n-sdmtas We define an n-standard form for SDMTAs and we prove that the reachability problem for n-sdmtas can be translated into the reachability problem for n-sdmtas in n- standard form. Our purpose is to simplify the definition of SDMTA in order to simplify the construction of the proof showing the decidability of the reachability problem. Hence, the n-standard form allows: only one component; only natural number variables that are at the beginning pairwise equal; 0 as starting values of the clocks; as starting value of the knowledge; only terms of the form f(µ 1,..., µ n) (which we will call n-simple). Thus, the first step is to transform an n-sdmta with more components into an n-sdmta with just one component.
10 10 Proposition 1 Given an n-sdmta A and a state q = (q 1,..., q m ) of A, an n- SDMTA A composed of only one n-dmta with a state ˆq can be constructed such that q is reachable in A iff ˆq is reachable in A. Proof. It is sufficient to consider the cartesian product of the sequential components of A. Now, a configuration fixes, for each component, its knowledge. Therefore if a component A i checks for the condition τ K, this is checked in the knowledge of A i. If we consider the cartesian product, the knowledge is unique. This is a problem because in the cartesian product of the parallel composition of a set of components, the presence in the knowledge of a term τ is ambiguous, actually, is not clear which component knows τ. Therefore, when a term enters into the whole knowledge, we must mark it with the index of components knowing this term. Now, for the parallel composition, there are three manners for introducing a term τ in the knowledge: τ is sent to another component, τ is received from another component, and, τ is inserted by an ɛ-transition. Hence, the cartesian product of the parallel composition simulates the steps of the parallel composition and therefore it must update its knowledge when simulating these three cases. For a simple and uniform construction, we consider a new function triple. The idea is that, the term triple(i, j, τ) is in the knowledge of the cartesian product of the parallel components for expressing that τ is in the knowledge of the i th and j th components thanks to a communication between i and j. To express the ɛ-transition, we consider the special term triple(i, i, τ) expressing the fact that τ is in the knowledge of the i th component thanks to an ɛ-transition step. Hence a communication step or an ɛ-step of the parallel composition over the term τ is simulated by the cartesian product by an ɛ step that update the knowledge with the term τ marked with the index of the component knowing it. Before formalizing the construction, we define the construction of a formula φ(i) that simulates in the cartesian product the condition φ appearing in the component i th of the parallel composition. As exposed before, if the component i th checks for τ K, then the cartesian product must checks whether in its knowledge there is: or triple(i, j, τ) for some j i, namely component i th knows τ because it sent it to component j th ; or triple(j, i, τ) for some j i, namely component i th knows τ because it received it from component j th ; or triple(i, i, τ), namely component i th knows τ because it stored it in its knowledge by an ɛ-step. Formally, given a formula φ, with( φ(i) we denote the formula φ where each formula of K) the form τ K is replaced with j [1,m] triple(i, j, τ) K triple(j, i, τ). We now formalize the construction of the cartesian product. Given the SDMTA A = (C, Ω, A 1,..., A m ), where A i = (Σ i, X i, Υ i, Q i, q0 i, δi ) for i = 1,..., m, we construct A = (C, Ω, A), where Ω = Ω {triple} and A = (Σ, X, Υ, Q, q 0, δ). The set Σ = does not contain any channel label, and the sets X = i Xi, Υ = i Υ i. The set of states Q = Q 1... Q m is given by the cartesian product of the set of states of each A i with q 0 = (q0 1,..., qm 0 ) the initial state. The set of transitions δ is defined as follows. In A we introduce a transition ((q 1,..., q,... q m ), ɛ(triple(i, i, τ)), φ(i), (q 1,..., q,... q m ))
11 11 if there exists a transition (q, ɛ(τ), φ, q ) of the i th component of A. In A we introduce a transition ((q 1,..., q,..., q,... q m ), ɛ(triple(i, j, τ)), φ(i) φ (j) φ, (q 1,..., q,..., q,..., q m )) if there exist two transitions (q, α 1, φ, q ) and (q, α 2, φ, q ) of the i th and j th components, respectively, such that {α 1, α 2 } = {a!(τ), a?(τ )} and φ expresses the set of instances I and I such that I(τ) = I (τ ). Obviously, this construction does not change the value of natv ar of the system. We prove now the correctness of our construction. Given a configuration s = (s 1,..., s m ) of A with s i = (q i, I i, v i, K i ) and a configuration s = (q, I, v, K ) of A, s simulates s if it holds that: 1. q = (q 1,..., q m); 2. I (µ) = I i (µ) if µ Υ i ; 3. v (x) = v i if x X i ; 4. For any triple(i, j, τ) K, it holds that τ K i and τ K j ; 5. For any τ K i, there exists j such that triple(i, j, τ) K or triple(j, i, τ) K. We prove now that, given s simulating s, if s s is a step of A, then s s is a step of A and s simulates s. Consider the configurations s = (s 1,..., s m) with s i = (q i, I i, v i, K i ), and s = (s 1,..., s m) with s i = (q i, I i, v i, K i ), and let s = (q, I, v, K) and s = (q, I, v, K ). If is a time step, then, for any i, it holds that q i = q i, I i = I i, K i = K i and there exists t such that v i = v i + t. Hence, in A we can perform the same time steps and hence s simulates s. If is an ɛ-transition step, then there exist i and a transition e = (q i, ɛ(τ), φ, q i ) such that (I i I i ), (v i v i ), K i = φ, K = K {I i (τ)}. Moreover, for any j i, it holds that I j = I j, v j = v j and K j = K j. Therefore, there exists a transition ((q 1,..., q,... q m ), ɛ(triple(i, i, τ)), φ(i), (q 1,..., q,... q m )) of A. By 2, 3 and 5 and since φ(i) is φ where each formula of the form τ K is replaced with j [1,m] (triple(i, j, τ) K triple(j, i, τ) K), we have that (I I ), (v v ), K = φ(i). Therefore the transition is performable and K = K {triple(i, i, I(τ))}. This implies that s simulates s. The last case in which is a communication step can be proves similarly. Hence we have that, if s s is a step of A, then s s is a step of A and s simulates s. Symmetrically one can prove that if s s is a step of A, then s s is a step of A and s simulates s. Hence, since the initial configuration of A simulates the initial configuration of A, by induction on the length of the runs we have the thesis. Actually s is reachable by A iff s is reachable by A where s simulates s. A term τ is n-simple for a set of message variables Υ if τ = f(µ 1,..., µ n ) with µ i Υ. As an example, f(µ 1, µ 2 ) is 2-simple but non 1-simple, while f(µ 1, f(µ 2, µ)) and f(1, µ 2 ) are not n-simple, for any n. Now, we show that an n-sdmta can always be transformed into an n-standard form that preserves reachability of states.
12 12 Definition 2 An n-sdmta A is in n-standard form iff A = (C, Ω, (Σ, X, Υ, Q, q 0, δ)) is composed by only one DMTA such that: C = ; for any (q, ɛ(τ), φ, q ) δ, it holds that τ is n-simple for Υ and each term τ appearing in φ is n-simple for Υ. For an SDMTA in n standard form, message variables can assume only natural number values (C = ). Finally, the conditions on formulas and on terms appearing in the transitions guarantee that an SDMTA in n-standard form only operates on n- simple terms. Thus, every term appearing in an n-sdmta in n-standard form has the form f(µ 1,..., µ n) for some f Ω and µ Υ, with I(µ) IN for all I. We prove now that any n-sdmta can be translated into an n-sdmta in n- standard form. Proposition 2 Given an n-sdmta A and a state q = (q 1,..., q m ) of A, an n- SDMTA A in n-standard form with a state ˆq can be constructed such that q is reachable in A iff ˆq is reachable in A. Proof. By Proposition 1 we can assume that A = (C, Ω, (Σ, X, Υ, Q, q 0, δ)). We construct an n-sdmta A = (C, Ω, (Σ, X, Υ, Q, q 0, δ )) in n-standard form. The construction needs three steps. The first step deletes each occurrence of natural values from the terms appearing in the SDMTA. The second step ensures that all message variable can assume only natural values. The third step transform each term in a n-simple term. Step 1 Now, we delete the natural numbers appearing in the terms. Given a term τ, with Nat(τ) we denote the set of natural numbers appearing in τ. If K is a knowledge, with Nat(K) we denote the set τ K Nat(τ). Now, we delete the natural numbers in Nat(A). If Nat(A) = {n 1,..., n k }, then we consider c 1,..., c k new constants and we substitute each n i with c i. Moreover, we replace each occurrence of n i with c i, and µ IN with µ IN µ {c 1,..., c k }, for any µ Υ Υ. Moreover, in each formula we add the formula µ Υ Υ µ {n 1,..., n k }. We prove that I, v, K = φ iff I, v, K = φ where: I(µ) = n i iff I (µ) = c i I(µ) Nat(A) implies I (µ) = I(µ) v = v Let τ be a term and τ is τ where each n i is substituted with c i. It holds that τ K iff τ K. The formula µ Υ Υ µ {n 1,..., n k } ensures that the terms added to the knowledge of A and the instance I do not contain values in {n 1,..., n k }. Therefore the property holds since µ IN is substituted with µ IN µ {c 1,..., c k } and we have substituted each occurrence of n i in a term with c i. Actually, this guarantees that I, v, K = µ IN iff I, v, K = µ IN µ {c 1,..., c k }, and, I, v, K = τ K iff I, v, K = τ K where τ is τ where each n i is substituted with c i. This property, implies the correctness of the construction by induction on the length of the run. Actually, the property holds for the initial configuration, and by definition
13 13 of step and by construction, this property still holds also after a step. Step 2 Now, we must guarantee that all variables can assume only natural values. Hence, for any µ, if {I(µ) IN I = φ} is not empty, then let H = {I(µ) IN I = φ}; we can substitute φ with µ IN ( (φ) ( c H φ[c/µ])). It is trivial that, if I(µ) IN, then I(τ) is equal to I (τ[i(µ)/µ]), for any I such that I (µ) = I(µ) if µ µ and I (µ) IN otherwise. Moreover, this implies that I, v, K = φ iff I, v, K = µ IN ((φ) φ[i(µ)/µ]). Step 3 Finally, we want all terms to be in the form f(µ 1,..., µ n). Let T be the set of terms appearing in the SDMTA after the previous transformations. We can partition T in T 1,..., T h such that, for any τ, τ T, it holds that τ τ iff τ, τ T i for some i. We then take Ω = {f 1,..., f h }, and, for any τ T i, we replace τ with the simple term f i (µ i1,..., µ ik ), where µ i1,..., µ ik is the sequence of variables occurring in τ from left to right without repetition. Now we prove that I, v, K = φ iff I, v, K = φ where: 1. I = I. 2. v = v. 3. for any τ T i and instance I, we have that I(τ) K iff I(f i (µ i1,..., µ ik )) K where µ i1,..., µ ik is the sequence of variables occurring in τ from left to right without repetition. 4. φ is φ where, for any τ T i, we replace τ with the simple term f i (µ i1,..., µ ik ), where µ i1,..., µ ik is the sequence of variables occurring in τ from left to right without repetition. Since I = I and v = v, the only case we must check is I, v, K = τ K iff I, v, K = f i (µ i1,..., µ ik ) K. But this holds by item 3. This implies the correctness of the construction by induction on the length of the run. Actually, since this property holds for the initial configuration and, by definition of step and by item 4, this property still holds also after a step. Now, since A is a n-sdmta, all terms are in the form f(µ 1,..., µ h ) with h n (note that constants can be viewed as the term f(µ 1,..., µ h ) with h = 0). If h is strictly less than n (h < n), it is sufficient to add n h new variables µ 1,..., µ n h to the system to replace f(µ 1,..., µ h ) with f(µ 1,..., µ h, µ 1,..., µ n h ), and to add in each transition the condition j [1,n h] µ j = µ j (namely µ 1,..., µ n h have a fixed value given non deterministically at the beginning). With such a construction defined in four steps, we guarantee that a state q Q can be reached in A iff the same can be reached also in A. Again, this construction does not change the value of natv ar of the system. 3.4 Decidability of Reachability for 1-SDMTAs We recall the definitions of clock equivalence [4]. Clock equivalence is a finite index equivalence relation allowing to group sets of valuations.
14 14 Let A be a DMTA and X A be the greatest constant appearing in a condition involving clocks and appearing in A. Let us consider the equivalence relation over clock valuations containing precisely the pairs (v, v ) such that: for each clock x, either v(x) = v (x), or both v(x) and v (x) are greater than X A ; for each pair of clocks x and y with v(x) X A and v(y) X A it holds that fract(v(x)) fract(v(y)) iff fract(v (x)) fract(v (y)) (where fract( ) is the fractional part); for each clock x with v(x) X A, fract(v(x)) = 0 iff fract(v (x)) = 0. Let [v] denote the equivalence class {v v v }. The set of equivalence classes {[v] v is a valuation} is finite, and with V we denote its cardinality. Known properties of the equivalence classes are summarized in the following theorem [4]. Theorem 1 Given a DMTA A, let c < X A and v and v be two valuations; v [v ] implies that v = x c iff v = x c, where {<,, =,, >}. Moreover, given a class [v], the set {[v + t] t IR 0 } is computable. In order to check the reachability problem, in [4], Timed Automata are reduced to finite state machines. In our case, however, we cannot simulate an unbounded knowledge with a finite state machine. Hence, we prove the decidability of the reachability problem for 1-SDMTAs by reducing the problem to the reachability problem for Vector Addition Systems (VASs). We briefly recall the model of VASs. Given two vectors w, w ZZ n, with w i we denote the i th component of w and with w + w we denote the vector w such that w i = w i + w i, for any i [1, n]. Definition 3 A Vector Addition System (VAS) of dimension n is a tuple S = (Q, δ) such that Q is a finite set of states and δ Q ZZ n Q. A configuration is a pair (q, w) with q Q and w IN n. There exists a step from configuration (q, w) to configuration (q, w ) (denoted with (q, w) (q, w )) if (q, w, q ) δ such that w = w + w. Note that while vectors w appearing in configurations can only assume positive natural values (w IN n ), vectors w δ may assume any integer value (w ZZ n ). The following theorem is proved in [16]. Theorem 2 Given two configurations (q, w) and (q, w ) of a VAS S, the problem of checking whether there exists a sequence of steps (q, w)... (q, w ) is decidable and EXPSPACE hard. Before proving the reduction result from 1-SDMTAs to VASs, we briefly discuss about the complexity of this problem. Since the number of clock zones of a region automaton is exponential w.r.t. the number of clocks of a timed automaton, the VAS corresponding to a 1-SDMTA has a size that is at least exponential w.r.t. the number of clocks. Moreover, to simulate message variables, structured messages and knowledge, the VAS needs a number of states that is exponential w.r.t. the number of function symbols in Ω and message variables in Υ. Hence, the VAS resulting from a 1-SDMTA will have an exponential size w.r.t. the size of the 1-SDMTA.
15 15 Theorem 3 Given an 1-SDMTA A and a state q of A, there exists a VAS S of exponential size w.r.t. A and two states q and q of S such that A reaches q iff there exists a sequence of steps (q, (0,..., 0))... (q, (0,..., 0)) of S. Before proving the theorem, we consider an extension of VASs. If S = (Q, δ) we assume δ Q 2 [1,n] ZZ n Q. There exists a step from the configuration (q, w) to the configuration (q, w ) if (q, In, w, q ) δ such that w = w + w and w i > 0 for any i In. It is easy to see that, given an extended VAS, we can construct an equivalent VAS with size polynomial w.r.t. the original one. Actually, it is sufficient to substitute any transition (q, In, w, q ) with two transitions (q, w w, ˆq), (ˆq, w, q ), where ˆq is a new state and w i = 1 if i In and w i = 0 otherwise. Note that, by definition, the values of w, for any configuration (q, w), could not be smaller than 0. Therefore, the two transitions introduced above guarantee that the values corresponding to indexes in In will be kept greater than 0. Proof. The proof can be divided into two main parts. In the first part we introduce the construction of an extended VAS for a given 1-SDMTA, in the second part we show that for a sequence of steps performed by the 1-SDMTA, there is an analogous step in the corresponding VAS leading to a special state q T. Part I: Thanks to Propositions 2, we can suppose that A is in n-standard form. Let Ω = {f 1,..., f k }, Q, Υ and X be the set of function symbols, the set of states, the set of message variables, and the set of clocks of A, respectively. A state of the VAS S is constructed as a tuple (q, [v], (A 1, T 1 ),..., (A p, T p)) such that q Q, v is a valuation on X, and = A i Υ and T i Ω, for any i, and {A 1,..., A p} is a partition of Υ. The idea is that (A 1, T 1 ),..., (A p, T p ) express the instance I such that: I(µ 1 ) = I(µ 2 ) iff µ 1, µ 2 A i, for some i; f(µ) K is true iff µ A i and f T i, for some i. The dimension of S, denoted by U = 2 Ω 1, is given by the number of possible sets T Ω such that T. Since an instance that does not use any constant appearing in the knowledge is always definable, we do not consider the empty set. Let g be a bijective function assigning a coordinate of the vector to each set T Ω such that T. The configuration ((q, [v], (A 1, T 1 ),..., (A p, T p)), w) of S expresses the configuration (q, v, I, K) of A such that q = q, v [v], (A 1, T 1 ),..., (A p, T p ) define the instance I as shown before, and w IN U represents the knowledge K. More precisely, let T Ω; if the g(t )-th coordinate of w is equal to h, then there exist c 1,..., c h distinct values in IN such that, for any j and for any f T, it holds that f(c j ) is in the knowledge. Summing up, we will write that a configuration ((q, [v], (A 1, T 1 ),..., (A p, T p )), w) represents a configuration (q, v, I, K) of A if q = q ; v [v]; I(µ 1 ) = I(µ 2 ) iff µ 1, µ 2 A i, for some i; f(µ) K is true iff µ A i and f T i, for some i;
16 16 for any T Ω, it holds that, if w g(t ) = h, then there exist c 1,..., c h distinct values in IN such that, for any j and for any f T, it holds that f(c j ) is in the knowledge. The set of transitions of S is constructed as follows. To model time steps of A, we add in S transitions of the form (q, In, w, q ), where In =, w = (0,..., 0), q = (q, [v], (A 1, T 1 ),..., (A p, T p )), for some q, [v], A i and T i, and q = (q, [v + t], (A 1, T 1 ),..., (A p, T p )) for some t IR 0. Moreover, there is a transition in S from the state (q, [v], (A 1, T 1 ),..., (A p, T p)) to the state (q, [v ], (A 1, T 1 ),..., (A r, T r)) with label (In, w) if there exists a transition (q, ɛ(f(µ), φ, q ) of A such that the following conditions hold: There exists (A 1, T 1 ),..., (A z, T z ) representing the relations between actual and new values of message variables, where: for any h, T h Ω; {A 1,..., A z } is a partition of Υ Υ ; for any h [1, p], there exists k such that A h = A k Υ and T h = T h ; namely, the sequence (A 1, T 1 ),..., (A z, T z ) preserves the relationships linking the actual values of the variables and the conditions that are satisfied by the actual instance and knowledge; for any h [1, r], there exists k such that A h = {µ µ A k Υ } and if µ A h then T h = T k {f} otherwise if µ A h then T h = T k (recall f(µ) is the term injected into the knowledge), namely, the sequence (A 1, T 1 preserves the relationships linking the new values of the variables and the conditions that will be satisfied by the target instance and knowledge; φ is true when evaluating: each clock x with (v v )(x), each µ IN as true, µ 1 = µ 2 as true iff, for some h, it holds that µ 1, µ 2 A h, ),..., (A z, T z ) f(µ) K is true iff for some h, it holds that µ A h and f T h ; hence, condition φ holds for the valuations v and v and when considering instances and conditions expressed by (A 1, T 1 ),..., (A z, T z ). In = {g(t i ) T i and i = 1,..., r}. This condition expresses the presence in the knowledge of the terms f(µ) where f T i and µ A i, namely ensures that f T i iff f(µ) is in the knowledge. Note that this implies that the starting state is coherent with the knowledge. Therefore the coherence of a state with the knowledge is guaranteed in the successive step. Moreover, an instance that does not use any constant appearing in the knowledge is always definable, hence, it is not necessary to check T i such that T i =. Let h be such that µ A h ; if f T h, then w = (0,..., 0), otherwise 1 if g 1 (j) = T h w j = 1 if g 1 (j) = {f} T h 0 otherwise. This a condition expresses the fact that, if f(µ) is in the knowledge (namely, f T h and µ A h ), then the knowledge does not change (namely, w = (0,..., 0)). Otherwise, the insertion of f(µ) creates new relations among the terms in the knowledge. Actually, the natural numbers appearing in f(µ) can appear in other terms in the knowledge. The terms that become related when f(µ) is inserted are those expressed by T h with µ A h. Hence, the case w j = 1 means that the set T h, represented by coordinate j (namely, g 1 (j) = T h ) that has relations with
17 17 f(µ), cannot still be activated by any instance. Actually, f(µ) does not introduce new relations. The case w j = 1 means that the set of terms expressed by {f} T h, represented by coordinate j and expressing the new relations, can be activated by some instance. Hence, we have a transition in S for any step of A. Each transition updates the values of the vector in the configuration by following the changes of the knowledge due to the step of A. Note that, if a transition of S models a time step of A, the knowledge is left unchanged. Our construction checks for the coherence of the state with the knowledge in the successive step. Actually, as explained before, the set In checks the coherence of the source state and not of the target state. So, we add a new state q T to S and transitions with label (In, (0,..., 0)) and target q T from each state ((q, [v], (A 1, T 1 ),..., (A m, T m)) with In = {g(t i ) i = 1,..., m}. So when arriving at the state q T all states have been checked for coherence. Part II: We prove that, given a sequence of steps of A, there exists a sequence of steps of the extended VAS ending with q T where every crossed state of A is represented by the states crossed by the VAS. We prove this fact by induction on the length of the sequence of steps. The base case is obvious, so we consider the inductive step. We consider a run σ = (q, v, I, K) (q, v, I, K ).... By induction, the thesis holds for the sequence σ = (q, v, I, K )... and there exists a sequence of steps ((q, [v ], (A 1, T 1 ),..., (A r, T r)), w )... (q T, w ), for some w. Hence we prove that the thesis holds for the first step of σ. More precisely, we prove that (q, v, I, K) (q, v, I, K ) implies that there exists a step in S of the form ((q, [v], (A 1, T 1 ),..., (A p, T p )), w) ((q, [v ], (A 1, T 1 ),..., (A r, T r)), w ), for some ((q, [v], (A 1, T 1 ),..., (A p, T p)), w) representing (q, v, I, K) (note that by induction ((q, [v ], (A 1, T 1 ),..., (A p, T r)), w ) represents (q, v, I, K )). The step performed by A may be of two types: it could be a time step or it could be an ɛ-transition step. We start with the case of a time step. If (q, v, I, K) t (q, v, I, K ) then we have that q = q, v = (v + t), I = I, and K = K. Let ((q, [v], (A 1, T 1 ),..., (A p, T p )), w) represent the configuration (q, v, I, K). By construction of S we have a transition (((q, [v], (A 1, T 1 ),..., (A p, T p )), w), In, (0,..., 0), ((q, [v+t], (A 1, T 1 ),..., (A p, T p )), w)) with In = {g(t 1 ),..., g(t p)}. Since the state ((q, [v], (A 1, T 1 ),..., (A p, T p)), w) represents (q, v, I, K), then, for any i, it holds that w g(ti ) > 0, therefore the step can be taken. We now prove the case of an ɛ-transition step. If (q, v, I, K) τ (q, v, I, K ) then there exists a transition e = (q, ɛ(f(µ)), φ, q ) such that the following holds: I(τ) = f(µ), (I I ), (v v ), K = φ, K = K {f(µ)}. Let the state ((q, [v], (A 1, T 1 ),..., (A p, T p )), w) represent (q, v, I, K), and let the state ((q, [v ], (A 1, T 1 ),..., (A r, T r)), w ) represent (q, v, I, K ). It is now sufficient to prove that there exists a transition from state (q, [v], (A 1, T 1 ),..., (A p, T p)) to state (q, [v ], (A 1, T 1 ),..., (A r, T r)) with label (In, w ) such that w i > 0 if i In [1, n] and w = w + w. This holds due to the following facts: 1. We prove the relations between the old and the new values of message variables:
Dense-Timed Pushdown Automata
 Dense-Timed Pushdown Automata Parosh Aziz Abdulla Uppsala University Sweden Mohamed Faouzi Atig Uppsala University Sweden Jari Stenman Uppsala University Sweden Abstract We propose a model that captures
Dense-Timed Pushdown Automata Parosh Aziz Abdulla Uppsala University Sweden Mohamed Faouzi Atig Uppsala University Sweden Jari Stenman Uppsala University Sweden Abstract We propose a model that captures
Design and Verification of Long Running Transactions in a Timed Framework
 Design and Verification of Long Running Transactions in a Timed Framework Ruggero Lanotte a, Andrea Maggiolo Schettini b, Paolo Milazzo b, Angelo Troina c, a Dipartimento di Scienze della Cultura, Politiche
Design and Verification of Long Running Transactions in a Timed Framework Ruggero Lanotte a, Andrea Maggiolo Schettini b, Paolo Milazzo b, Angelo Troina c, a Dipartimento di Scienze della Cultura, Politiche
Timed Automata VINO 2011
 Timed Automata VINO 2011 VeriDis Group - LORIA July 18, 2011 Content 1 Introduction 2 Timed Automata 3 Networks of timed automata Motivation Formalism for modeling and verification of real-time systems.
Timed Automata VINO 2011 VeriDis Group - LORIA July 18, 2011 Content 1 Introduction 2 Timed Automata 3 Networks of timed automata Motivation Formalism for modeling and verification of real-time systems.
Undecidability Results for Timed Automata with Silent Transitions
 Fundamenta Informaticae XXI (2001) 1001 1025 1001 IOS Press Undecidability Results for Timed Automata with Silent Transitions Patricia Bouyer LSV, ENS Cachan, CNRS, France bouyer@lsv.ens-cachan.fr Serge
Fundamenta Informaticae XXI (2001) 1001 1025 1001 IOS Press Undecidability Results for Timed Automata with Silent Transitions Patricia Bouyer LSV, ENS Cachan, CNRS, France bouyer@lsv.ens-cachan.fr Serge
Angelo Troina. Joint work with: Ruggero Lanotte (University of Insubria at Como) Andrea Maggiolo Schettini (University of Pisa)
 Angelo Troina Dipartimento di Informatica, Università di Pisa, Italy Probabilistic Joint work with: Ruggero Lanotte (University of Insubria at Como) Andrea Maggiolo Schettini (University of Pisa) 1/23
Angelo Troina Dipartimento di Informatica, Università di Pisa, Italy Probabilistic Joint work with: Ruggero Lanotte (University of Insubria at Como) Andrea Maggiolo Schettini (University of Pisa) 1/23
for System Modeling, Analysis, and Optimization
 Fundamental Algorithms for System Modeling, Analysis, and Optimization Stavros Tripakis UC Berkeley EECS 144/244 Fall 2013 Copyright 2013, E. A. Lee, J. Roydhowdhury, S. A. Seshia, S. Tripakis All rights
Fundamental Algorithms for System Modeling, Analysis, and Optimization Stavros Tripakis UC Berkeley EECS 144/244 Fall 2013 Copyright 2013, E. A. Lee, J. Roydhowdhury, S. A. Seshia, S. Tripakis All rights
Recent results on Timed Systems
 Recent results on Timed Systems Time Petri Nets and Timed Automata Béatrice Bérard LAMSADE Université Paris-Dauphine & CNRS berard@lamsade.dauphine.fr Based on joint work with F. Cassez, S. Haddad, D.
Recent results on Timed Systems Time Petri Nets and Timed Automata Béatrice Bérard LAMSADE Université Paris-Dauphine & CNRS berard@lamsade.dauphine.fr Based on joint work with F. Cassez, S. Haddad, D.
Timo Latvala. March 7, 2004
 Reactive Systems: Safety, Liveness, and Fairness Timo Latvala March 7, 2004 Reactive Systems: Safety, Liveness, and Fairness 14-1 Safety Safety properties are a very useful subclass of specifications.
Reactive Systems: Safety, Liveness, and Fairness Timo Latvala March 7, 2004 Reactive Systems: Safety, Liveness, and Fairness 14-1 Safety Safety properties are a very useful subclass of specifications.
The Minimal Cost Reachability Problem in Priced Timed Pushdown Systems
 The Minimal Cost Reachability Problem in Priced Timed Pushdown Systems Parosh Aziz Abdulla, Mohamed Faouzi Atig, and Jari Stenman Uppsala University, Sweden Abstract. This paper introduces the model of
The Minimal Cost Reachability Problem in Priced Timed Pushdown Systems Parosh Aziz Abdulla, Mohamed Faouzi Atig, and Jari Stenman Uppsala University, Sweden Abstract. This paper introduces the model of
Time-Bounding Needham-Schroeder Public Key Exchange Protocol
 Time-Bounding Needham-Schroeder Public Key Exchange Protocol Max Kanovich, Queen Mary, University of London, UK University College London, UCL-CS, UK Tajana Ban Kirigin, University of Rijeka, HR Vivek
Time-Bounding Needham-Schroeder Public Key Exchange Protocol Max Kanovich, Queen Mary, University of London, UK University College London, UCL-CS, UK Tajana Ban Kirigin, University of Rijeka, HR Vivek
Decentralized Control of Discrete Event Systems with Bounded or Unbounded Delay Communication 1
 Decentralized Control of Discrete Event Systems with Bounded or Unbounded Delay Communication 1 Stavros Tripakis 2 VERIMAG Technical Report TR-2004-26 November 2004 Abstract We introduce problems of decentralized
Decentralized Control of Discrete Event Systems with Bounded or Unbounded Delay Communication 1 Stavros Tripakis 2 VERIMAG Technical Report TR-2004-26 November 2004 Abstract We introduce problems of decentralized
DISTINGUING NON-DETERMINISTIC TIMED FINITE STATE MACHINES
 DISTINGUING NON-DETERMINISTIC TIMED FINITE STATE MACHINES Maxim Gromov 1, Khaled El-Fakih 2, Natalia Shabaldina 1, Nina Yevtushenko 1 1 Tomsk State University, 36 Lenin Str.. Tomsk, 634050, Russia gromov@sibmail.com,
DISTINGUING NON-DETERMINISTIC TIMED FINITE STATE MACHINES Maxim Gromov 1, Khaled El-Fakih 2, Natalia Shabaldina 1, Nina Yevtushenko 1 1 Tomsk State University, 36 Lenin Str.. Tomsk, 634050, Russia gromov@sibmail.com,
Abstracting real-valued parameters in parameterised boolean equation systems
 Department of Mathematics and Computer Science Formal System Analysis Research Group Abstracting real-valued parameters in parameterised boolean equation systems Master Thesis M. Laveaux Supervisor: dr.
Department of Mathematics and Computer Science Formal System Analysis Research Group Abstracting real-valued parameters in parameterised boolean equation systems Master Thesis M. Laveaux Supervisor: dr.
Models for Efficient Timed Verification
 Models for Efficient Timed Verification François Laroussinie LSV / ENS de Cachan CNRS UMR 8643 Monterey Workshop - Composition of embedded systems Model checking System Properties Formalizing step? ϕ Model
Models for Efficient Timed Verification François Laroussinie LSV / ENS de Cachan CNRS UMR 8643 Monterey Workshop - Composition of embedded systems Model checking System Properties Formalizing step? ϕ Model
TESTING is one of the most important parts of the
 IEEE TRANSACTIONS 1 Generating Complete Controllable Test Suites for Distributed Testing Robert M. Hierons, Senior Member, IEEE Abstract A test suite is m-complete for finite state machine (FSM) M if it
IEEE TRANSACTIONS 1 Generating Complete Controllable Test Suites for Distributed Testing Robert M. Hierons, Senior Member, IEEE Abstract A test suite is m-complete for finite state machine (FSM) M if it
Lecture 11: Timed Automata
 Real-Time Systems Lecture 11: Timed Automata 2014-07-01 11 2014-07-01 main Dr. Bernd Westphal Albert-Ludwigs-Universität Freiburg, Germany Contents & Goals Last Lecture: DC (un)decidability This Lecture:
Real-Time Systems Lecture 11: Timed Automata 2014-07-01 11 2014-07-01 main Dr. Bernd Westphal Albert-Ludwigs-Universität Freiburg, Germany Contents & Goals Last Lecture: DC (un)decidability This Lecture:
Alan Bundy. Automated Reasoning LTL Model Checking
 Automated Reasoning LTL Model Checking Alan Bundy Lecture 9, page 1 Introduction So far we have looked at theorem proving Powerful, especially where good sets of rewrite rules or decision procedures have
Automated Reasoning LTL Model Checking Alan Bundy Lecture 9, page 1 Introduction So far we have looked at theorem proving Powerful, especially where good sets of rewrite rules or decision procedures have
Verification of Probabilistic Systems with Faulty Communication
 Verification of Probabilistic Systems with Faulty Communication P. A. Abdulla 1, N. Bertrand 2, A. Rabinovich 3, and Ph. Schnoebelen 2 1 Uppsala University, Sweden 2 LSV, ENS de Cachan, France 3 Tel Aviv
Verification of Probabilistic Systems with Faulty Communication P. A. Abdulla 1, N. Bertrand 2, A. Rabinovich 3, and Ph. Schnoebelen 2 1 Uppsala University, Sweden 2 LSV, ENS de Cachan, France 3 Tel Aviv
Decentralized Control of Discrete Event Systems with Bounded or Unbounded Delay Communication
 Decentralized Control of Discrete Event Systems with Bounded or Unbounded Delay Communication Stavros Tripakis Abstract We introduce problems of decentralized control with communication, where we explicitly
Decentralized Control of Discrete Event Systems with Bounded or Unbounded Delay Communication Stavros Tripakis Abstract We introduce problems of decentralized control with communication, where we explicitly
Database Theory VU , SS Complexity of Query Evaluation. Reinhard Pichler
 Database Theory Database Theory VU 181.140, SS 2018 5. Complexity of Query Evaluation Reinhard Pichler Institut für Informationssysteme Arbeitsbereich DBAI Technische Universität Wien 17 April, 2018 Pichler
Database Theory Database Theory VU 181.140, SS 2018 5. Complexity of Query Evaluation Reinhard Pichler Institut für Informationssysteme Arbeitsbereich DBAI Technische Universität Wien 17 April, 2018 Pichler
Real-Time Systems. Lecture 10: Timed Automata Dr. Bernd Westphal. Albert-Ludwigs-Universität Freiburg, Germany main
 Real-Time Systems Lecture 10: Timed Automata 2013-06-04 10 2013-06-04 main Dr. Bernd Westphal Albert-Ludwigs-Universität Freiburg, Germany Contents & Goals Last Lecture: PLC, PLC automata This Lecture:
Real-Time Systems Lecture 10: Timed Automata 2013-06-04 10 2013-06-04 main Dr. Bernd Westphal Albert-Ludwigs-Universität Freiburg, Germany Contents & Goals Last Lecture: PLC, PLC automata This Lecture:
Cryptographic Protocols Notes 2
 ETH Zurich, Department of Computer Science SS 2018 Prof. Ueli Maurer Dr. Martin Hirt Chen-Da Liu Zhang Cryptographic Protocols Notes 2 Scribe: Sandro Coretti (modified by Chen-Da Liu Zhang) About the notes:
ETH Zurich, Department of Computer Science SS 2018 Prof. Ueli Maurer Dr. Martin Hirt Chen-Da Liu Zhang Cryptographic Protocols Notes 2 Scribe: Sandro Coretti (modified by Chen-Da Liu Zhang) About the notes:
Zone-Based Reachability Analysis of Dense-Timed Pushdown Automata
 IT 12 034 Examensarbete 15 hp Juli 2012 Zone-Based Reachability Analysis of Dense-Timed Pushdown Automata Kristiina Ausmees Institutionen för informationsteknologi Department of Information Technology
IT 12 034 Examensarbete 15 hp Juli 2012 Zone-Based Reachability Analysis of Dense-Timed Pushdown Automata Kristiina Ausmees Institutionen för informationsteknologi Department of Information Technology
The algorithmic analysis of hybrid system
 The algorithmic analysis of hybrid system Authors: R.Alur, C. Courcoubetis etc. Course teacher: Prof. Ugo Buy Xin Li, Huiyong Xiao Nov. 13, 2002 Summary What s a hybrid system? Definition of Hybrid Automaton
The algorithmic analysis of hybrid system Authors: R.Alur, C. Courcoubetis etc. Course teacher: Prof. Ugo Buy Xin Li, Huiyong Xiao Nov. 13, 2002 Summary What s a hybrid system? Definition of Hybrid Automaton
Notes on BAN Logic CSG 399. March 7, 2006
 Notes on BAN Logic CSG 399 March 7, 2006 The wide-mouthed frog protocol, in a slightly different form, with only the first two messages, and time stamps: A S : A, {T a, B, K ab } Kas S B : {T s, A, K ab
Notes on BAN Logic CSG 399 March 7, 2006 The wide-mouthed frog protocol, in a slightly different form, with only the first two messages, and time stamps: A S : A, {T a, B, K ab } Kas S B : {T s, A, K ab
MPRI 1-22 Introduction to Verification January 4, TD 6: Petri Nets
 TD 6: Petri Nets 1 Modeling Using Petri Nets Exercise 1 (Traffic Lights). Consider again the traffic lights example from the lecture notes: r r ry y r y ry g g y g 1. How can you correct this Petri net
TD 6: Petri Nets 1 Modeling Using Petri Nets Exercise 1 (Traffic Lights). Consider again the traffic lights example from the lecture notes: r r ry y r y ry g g y g 1. How can you correct this Petri net
Complexity Issues in Automated Addition of Time-Bounded Liveness Properties 1
 Complexity Issues in Automated Addition of Time-Bounded Liveness Properties 1 Borzoo Bonakdarpour and Sandeep S. Kulkarni Software Engineering and Network Systems Laboratory, Department of Computer Science
Complexity Issues in Automated Addition of Time-Bounded Liveness Properties 1 Borzoo Bonakdarpour and Sandeep S. Kulkarni Software Engineering and Network Systems Laboratory, Department of Computer Science
Real-Time Systems. Lecture 15: The Universality Problem for TBA Dr. Bernd Westphal. Albert-Ludwigs-Universität Freiburg, Germany
 Real-Time Systems Lecture 15: The Universality Problem for TBA 2013-06-26 15 2013-06-26 main Dr. Bernd Westphal Albert-Ludwigs-Universität Freiburg, Germany Contents & Goals Last Lecture: Extended Timed
Real-Time Systems Lecture 15: The Universality Problem for TBA 2013-06-26 15 2013-06-26 main Dr. Bernd Westphal Albert-Ludwigs-Universität Freiburg, Germany Contents & Goals Last Lecture: Extended Timed
Timed Automata. Chapter Clocks and clock constraints Clock variables and clock constraints
 Chapter 10 Timed Automata In the previous chapter, we have discussed a temporal logic where time was a discrete entities. A time unit was one application of the transition relation of an LTS. We could
Chapter 10 Timed Automata In the previous chapter, we have discussed a temporal logic where time was a discrete entities. A time unit was one application of the transition relation of an LTS. We could
New Complexity Results for Some Linear Counting Problems Using Minimal Solutions to Linear Diophantine Equations
 New Complexity Results for Some Linear Counting Problems Using Minimal Solutions to Linear Diophantine Equations (Extended Abstract) Gaoyan Xie, Cheng Li and Zhe Dang School of Electrical Engineering and
New Complexity Results for Some Linear Counting Problems Using Minimal Solutions to Linear Diophantine Equations (Extended Abstract) Gaoyan Xie, Cheng Li and Zhe Dang School of Electrical Engineering and
Kybernetika. Daniel Reidenbach; Markus L. Schmid Automata with modulo counters and nondeterministic counter bounds
 Kybernetika Daniel Reidenbach; Markus L. Schmid Automata with modulo counters and nondeterministic counter bounds Kybernetika, Vol. 50 (2014), No. 1, 66 94 Persistent URL: http://dml.cz/dmlcz/143764 Terms
Kybernetika Daniel Reidenbach; Markus L. Schmid Automata with modulo counters and nondeterministic counter bounds Kybernetika, Vol. 50 (2014), No. 1, 66 94 Persistent URL: http://dml.cz/dmlcz/143764 Terms
Closure under the Regular Operations
 Closure under the Regular Operations Application of NFA Now we use the NFA to show that collection of regular languages is closed under regular operations union, concatenation, and star Earlier we have
Closure under the Regular Operations Application of NFA Now we use the NFA to show that collection of regular languages is closed under regular operations union, concatenation, and star Earlier we have
540 IEEE TRANSACTIONS ON AUTOMATIC CONTROL, VOL. 43, NO. 4, APRIL Algorithmic Analysis of Nonlinear Hybrid Systems
 540 IEEE TRANSACTIONS ON AUTOMATIC CONTROL, VOL. 43, NO. 4, APRIL 1998 Algorithmic Analysis of Nonlinear Hybrid Systems Thomas A. Henzinger, Pei-Hsin Ho, Howard Wong-Toi Abstract Hybrid systems are digital
540 IEEE TRANSACTIONS ON AUTOMATIC CONTROL, VOL. 43, NO. 4, APRIL 1998 Algorithmic Analysis of Nonlinear Hybrid Systems Thomas A. Henzinger, Pei-Hsin Ho, Howard Wong-Toi Abstract Hybrid systems are digital
TIMED automata, introduced by Alur and Dill in [3], have
![TIMED automata, introduced by Alur and Dill in [3], have TIMED automata, introduced by Alur and Dill in [3], have](/thumbs/90/103710352.jpg) 1 Language Inclusion Checking of Timed Automata with Non-Zenoness Xinyu Wang, Jun Sun, Ting Wang, and Shengchao Qin Abstract Given a timed automaton P modeling an implementation and a timed automaton S
1 Language Inclusion Checking of Timed Automata with Non-Zenoness Xinyu Wang, Jun Sun, Ting Wang, and Shengchao Qin Abstract Given a timed automaton P modeling an implementation and a timed automaton S
Bounded Model Checking with SAT/SMT. Edmund M. Clarke School of Computer Science Carnegie Mellon University 1/39
 Bounded Model Checking with SAT/SMT Edmund M. Clarke School of Computer Science Carnegie Mellon University 1/39 Recap: Symbolic Model Checking with BDDs Method used by most industrial strength model checkers:
Bounded Model Checking with SAT/SMT Edmund M. Clarke School of Computer Science Carnegie Mellon University 1/39 Recap: Symbolic Model Checking with BDDs Method used by most industrial strength model checkers:
Model Checking Restricted Sets of Timed Paths
 Model Checking Restricted Sets of Timed Paths Nicolas Markey a Jean-François Raskin b a Lab. Spécification et Vérification ENS Cachan & CNRS UMR8643 61, avenue Président Wilson 94235 Cachan Cedex France
Model Checking Restricted Sets of Timed Paths Nicolas Markey a Jean-François Raskin b a Lab. Spécification et Vérification ENS Cachan & CNRS UMR8643 61, avenue Président Wilson 94235 Cachan Cedex France
TWO-VARIABLE LOGIC WITH COUNTING AND A LINEAR ORDER
 Logical Methods in Computer Science Vol. 12(2:8)2016, pp. 1 31 www.lmcs-online.org Submitted Nov. 2, 2015 Published Jun. 23, 2016 TWO-VARIABLE LOGIC WITH COUNTING AND A LINEAR ORDER WITOLD CHARATONIK AND
Logical Methods in Computer Science Vol. 12(2:8)2016, pp. 1 31 www.lmcs-online.org Submitted Nov. 2, 2015 Published Jun. 23, 2016 TWO-VARIABLE LOGIC WITH COUNTING AND A LINEAR ORDER WITOLD CHARATONIK AND
A Sample State Machine
 A Sample State Machine Environment Signatures An environment signature is a triple of sets of guards, actions, and messages. H = (G H, A H, M H ) Guards: formulas in some logical language, e.g. OCL. Actions
A Sample State Machine Environment Signatures An environment signature is a triple of sets of guards, actions, and messages. H = (G H, A H, M H ) Guards: formulas in some logical language, e.g. OCL. Actions
Undecidable Problems. Z. Sawa (TU Ostrava) Introd. to Theoretical Computer Science May 12, / 65
 Undecidable Problems Z. Sawa (TU Ostrava) Introd. to Theoretical Computer Science May 12, 2018 1/ 65 Algorithmically Solvable Problems Let us assume we have a problem P. If there is an algorithm solving
Undecidable Problems Z. Sawa (TU Ostrava) Introd. to Theoretical Computer Science May 12, 2018 1/ 65 Algorithmically Solvable Problems Let us assume we have a problem P. If there is an algorithm solving
 Introduction: Computer Science is a cluster of related scientific and engineering disciplines concerned with the study and application of computations. These disciplines range from the pure and basic scientific
Introduction: Computer Science is a cluster of related scientific and engineering disciplines concerned with the study and application of computations. These disciplines range from the pure and basic scientific
The efficiency of identifying timed automata and the power of clocks
 The efficiency of identifying timed automata and the power of clocks Sicco Verwer a,b,1,, Mathijs de Weerdt b, Cees Witteveen b a Eindhoven University of Technology, Department of Mathematics and Computer
The efficiency of identifying timed automata and the power of clocks Sicco Verwer a,b,1,, Mathijs de Weerdt b, Cees Witteveen b a Eindhoven University of Technology, Department of Mathematics and Computer
Let us first give some intuitive idea about a state of a system and state transitions before describing finite automata.
 Finite Automata Automata (singular: automation) are a particularly simple, but useful, model of computation. They were initially proposed as a simple model for the behavior of neurons. The concept of a
Finite Automata Automata (singular: automation) are a particularly simple, but useful, model of computation. They were initially proposed as a simple model for the behavior of neurons. The concept of a
arxiv:cs/ v1 [cs.lo] 8 Dec 2005
![arxiv:cs/ v1 [cs.lo] 8 Dec 2005 arxiv:cs/ v1 [cs.lo] 8 Dec 2005](/thumbs/71/66059156.jpg) Alternating Timed Automata S lawomir Lasota 1 and Igor Walukiewicz 2 1 Institute of Informatics, Warsaw University Banacha 2, 02-097 Warszawa arxiv:cs/0512031v1 [cs.lo] 8 Dec 2005 2 LaBRI, Université Bordeaux-1
Alternating Timed Automata S lawomir Lasota 1 and Igor Walukiewicz 2 1 Institute of Informatics, Warsaw University Banacha 2, 02-097 Warszawa arxiv:cs/0512031v1 [cs.lo] 8 Dec 2005 2 LaBRI, Université Bordeaux-1
Diagnosis of Repeated/Intermittent Failures in Discrete Event Systems
 Diagnosis of Repeated/Intermittent Failures in Discrete Event Systems Shengbing Jiang, Ratnesh Kumar, and Humberto E. Garcia Abstract We introduce the notion of repeated failure diagnosability for diagnosing
Diagnosis of Repeated/Intermittent Failures in Discrete Event Systems Shengbing Jiang, Ratnesh Kumar, and Humberto E. Garcia Abstract We introduce the notion of repeated failure diagnosability for diagnosing
Final exam study sheet for CS3719 Turing machines and decidability.
 Final exam study sheet for CS3719 Turing machines and decidability. A Turing machine is a finite automaton with an infinite memory (tape). Formally, a Turing machine is a 6-tuple M = (Q, Σ, Γ, δ, q 0,
Final exam study sheet for CS3719 Turing machines and decidability. A Turing machine is a finite automaton with an infinite memory (tape). Formally, a Turing machine is a 6-tuple M = (Q, Σ, Γ, δ, q 0,
}w!"#$%&'()+,-./012345<ya FI MU. Decidable Race Condition for HMSC. Faculty of Informatics Masaryk University Brno
 }w!"#$%&'()+,-./012345
}w!"#$%&'()+,-./012345
Chapter 1. Automata over infinite alphabets
 Chapter 1 Automata over infinite alphabets Amaldev Manuel and R. Ramanujam Institute of Mathematical Sciences, C.I.T campus, Taramani, Chennai - 600113. In many contexts such as validation of XML data,
Chapter 1 Automata over infinite alphabets Amaldev Manuel and R. Ramanujam Institute of Mathematical Sciences, C.I.T campus, Taramani, Chennai - 600113. In many contexts such as validation of XML data,
arxiv: v1 [cs.pl] 3 Jul 2017
![arxiv: v1 [cs.pl] 3 Jul 2017 arxiv: v1 [cs.pl] 3 Jul 2017](/thumbs/73/69387137.jpg) Checking Linearizability of Concurrent Priority Queues Ahmed Bouajjani 1, Constantin Enea 1, and Chao Wang 1 1 Institut de Recherche en Informatique Fondamentale, {abou,cenea,wangch}@irif.fr arxiv:1707.00639v1
Checking Linearizability of Concurrent Priority Queues Ahmed Bouajjani 1, Constantin Enea 1, and Chao Wang 1 1 Institut de Recherche en Informatique Fondamentale, {abou,cenea,wangch}@irif.fr arxiv:1707.00639v1
An optimal tableau-based decision algorithm for Propositional Neighborhood Logic
 An optimal tableau-based decision algorithm for Propositional Neighborhood Logic Davide Bresolin, Angelo Montanari, and Pietro Sala Department of Mathematics and Computer Science, University of Udine,
An optimal tableau-based decision algorithm for Propositional Neighborhood Logic Davide Bresolin, Angelo Montanari, and Pietro Sala Department of Mathematics and Computer Science, University of Udine,
Specifying and Verifying Systems of Communicating Agents in a Temporal Action Logic
 Specifying and Verifying Systems of Communicating Agents in a Temporal Action Logic Laura Giordano 1, Alberto Martelli 2, Camilla Schwind 3 1 Dipartimento di Informatica, Università del Piemonte Orientale,
Specifying and Verifying Systems of Communicating Agents in a Temporal Action Logic Laura Giordano 1, Alberto Martelli 2, Camilla Schwind 3 1 Dipartimento di Informatica, Università del Piemonte Orientale,
Automata, Logic and Games: Theory and Application
 Automata, Logic and Games: Theory and Application 1. Büchi Automata and S1S Luke Ong University of Oxford TACL Summer School University of Salerno, 14-19 June 2015 Luke Ong Büchi Automata & S1S 14-19 June
Automata, Logic and Games: Theory and Application 1. Büchi Automata and S1S Luke Ong University of Oxford TACL Summer School University of Salerno, 14-19 June 2015 Luke Ong Büchi Automata & S1S 14-19 June
Time(d) Petri Net. Serge Haddad. Petri Nets 2016, June 20th LSV ENS Cachan, Université Paris-Saclay & CNRS & INRIA
 Time(d) Petri Net Serge Haddad LSV ENS Cachan, Université Paris-Saclay & CNRS & INRIA haddad@lsv.ens-cachan.fr Petri Nets 2016, June 20th 2016 1 Time and Petri Nets 2 Time Petri Net: Syntax and Semantic
Time(d) Petri Net Serge Haddad LSV ENS Cachan, Université Paris-Saclay & CNRS & INRIA haddad@lsv.ens-cachan.fr Petri Nets 2016, June 20th 2016 1 Time and Petri Nets 2 Time Petri Net: Syntax and Semantic
Deciding Safety and Liveness in TPTL
 Deciding Safety and Liveness in TPTL David Basin a, Carlos Cotrini Jiménez a,, Felix Klaedtke b,1, Eugen Zălinescu a a Institute of Information Security, ETH Zurich, Switzerland b NEC Europe Ltd., Heidelberg,
Deciding Safety and Liveness in TPTL David Basin a, Carlos Cotrini Jiménez a,, Felix Klaedtke b,1, Eugen Zălinescu a a Institute of Information Security, ETH Zurich, Switzerland b NEC Europe Ltd., Heidelberg,
Complexity Issues in Automated Addition of Time-Bounded Liveness Properties 1
 Complexity Issues in Automated Addition of Time-Bounded Liveness Properties 1 Borzoo Bonakdarpour and Sandeep S. Kulkarni Software Engineering and Network Systems Laboratory, Department of Computer Science
Complexity Issues in Automated Addition of Time-Bounded Liveness Properties 1 Borzoo Bonakdarpour and Sandeep S. Kulkarni Software Engineering and Network Systems Laboratory, Department of Computer Science
Diagnosis of Dense-Time Systems using Digital-Clocks
 Diagnosis of Dense-Time Systems using Digital-Clocks Shengbing Jiang GM R&D and Planning Mail Code 480-106-390 Warren, MI 48090-9055 Email: shengbing.jiang@gm.com Ratnesh Kumar Dept. of Elec. & Comp. Eng.
Diagnosis of Dense-Time Systems using Digital-Clocks Shengbing Jiang GM R&D and Planning Mail Code 480-106-390 Warren, MI 48090-9055 Email: shengbing.jiang@gm.com Ratnesh Kumar Dept. of Elec. & Comp. Eng.
Composability of Infinite-State Activity Automata
 & Composability of Infinite-State Activity Automata Zhe Dang, Oscar H. Ibarra, and Jianwen Su School of Electrical Engineering and Computer Science Washington State University Pullman, WA 99164, USA Department
& Composability of Infinite-State Activity Automata Zhe Dang, Oscar H. Ibarra, and Jianwen Su School of Electrical Engineering and Computer Science Washington State University Pullman, WA 99164, USA Department
DES. 4. Petri Nets. Introduction. Different Classes of Petri Net. Petri net properties. Analysis of Petri net models
 4. Petri Nets Introduction Different Classes of Petri Net Petri net properties Analysis of Petri net models 1 Petri Nets C.A Petri, TU Darmstadt, 1962 A mathematical and graphical modeling method. Describe
4. Petri Nets Introduction Different Classes of Petri Net Petri net properties Analysis of Petri net models 1 Petri Nets C.A Petri, TU Darmstadt, 1962 A mathematical and graphical modeling method. Describe
When are Timed Automata Determinizable?
 When are Timed Automata Determinizable? Christel Baier 1, Nathalie Bertrand 2, Patricia Bouyer 3, and Thomas Brihaye 4 1 Technische Universität Dresden, Germany 2 INRIA Rennes Bretagne Atlantique, France
When are Timed Automata Determinizable? Christel Baier 1, Nathalie Bertrand 2, Patricia Bouyer 3, and Thomas Brihaye 4 1 Technische Universität Dresden, Germany 2 INRIA Rennes Bretagne Atlantique, France
Automatic Synthesis of Distributed Protocols
 Automatic Synthesis of Distributed Protocols Rajeev Alur Stavros Tripakis 1 Introduction Protocols for coordination among concurrent processes are an essential component of modern multiprocessor and distributed
Automatic Synthesis of Distributed Protocols Rajeev Alur Stavros Tripakis 1 Introduction Protocols for coordination among concurrent processes are an essential component of modern multiprocessor and distributed
Pushdown timed automata:a binary reachability characterization and safety verication
 Theoretical Computer Science 302 (2003) 93 121 www.elsevier.com/locate/tcs Pushdown timed automata:a binary reachability characterization and safety verication Zhe Dang School of Electrical Engineering
Theoretical Computer Science 302 (2003) 93 121 www.elsevier.com/locate/tcs Pushdown timed automata:a binary reachability characterization and safety verication Zhe Dang School of Electrical Engineering
MONOTONIC ABSTRACTION (ON EFFICIENT VERIFICATION OF PARAMETERIZED SYSTEMS)
 International Journal of Foundations of Computer Science Vol. 20, No. 5 (2009) 779 801 c World Scientific Publishing Company MONOTONIC ABSTRACTION (ON EFFICIENT VERIFICATION OF PARAMETERIZED SYSTEMS) PAROSH
International Journal of Foundations of Computer Science Vol. 20, No. 5 (2009) 779 801 c World Scientific Publishing Company MONOTONIC ABSTRACTION (ON EFFICIENT VERIFICATION OF PARAMETERIZED SYSTEMS) PAROSH
Temporal logics and explicit-state model checking. Pierre Wolper Université de Liège
 Temporal logics and explicit-state model checking Pierre Wolper Université de Liège 1 Topics to be covered Introducing explicit-state model checking Finite automata on infinite words Temporal Logics and
Temporal logics and explicit-state model checking Pierre Wolper Université de Liège 1 Topics to be covered Introducing explicit-state model checking Finite automata on infinite words Temporal Logics and
Logical Time. 1. Introduction 2. Clock and Events 3. Logical (Lamport) Clocks 4. Vector Clocks 5. Efficient Implementation
 Logical Time Nicola Dragoni Embedded Systems Engineering DTU Compute 1. Introduction 2. Clock and Events 3. Logical (Lamport) Clocks 4. Vector Clocks 5. Efficient Implementation 2013 ACM Turing Award:
Logical Time Nicola Dragoni Embedded Systems Engineering DTU Compute 1. Introduction 2. Clock and Events 3. Logical (Lamport) Clocks 4. Vector Clocks 5. Efficient Implementation 2013 ACM Turing Award:
Theory of Computing Tamás Herendi
 Theory of Computing Tamás Herendi Theory of Computing Tamás Herendi Publication date 2014 Table of Contents 1 Preface 1 2 Formal languages 2 3 Order of growth rate 9 4 Turing machines 16 1 The definition
Theory of Computing Tamás Herendi Theory of Computing Tamás Herendi Publication date 2014 Table of Contents 1 Preface 1 2 Formal languages 2 3 Order of growth rate 9 4 Turing machines 16 1 The definition
Time and Timed Petri Nets
 Time and Timed Petri Nets Serge Haddad LSV ENS Cachan & CNRS & INRIA haddad@lsv.ens-cachan.fr DISC 11, June 9th 2011 1 Time and Petri Nets 2 Timed Models 3 Expressiveness 4 Analysis 1/36 Outline 1 Time
Time and Timed Petri Nets Serge Haddad LSV ENS Cachan & CNRS & INRIA haddad@lsv.ens-cachan.fr DISC 11, June 9th 2011 1 Time and Petri Nets 2 Timed Models 3 Expressiveness 4 Analysis 1/36 Outline 1 Time
Pairing Transitive Closure and Reduction to Efficiently Reason about Partially Ordered Events
 Pairing Transitive Closure and Reduction to Efficiently Reason about Partially Ordered Events Massimo Franceschet Angelo Montanari Dipartimento di Matematica e Informatica, Università di Udine Via delle
Pairing Transitive Closure and Reduction to Efficiently Reason about Partially Ordered Events Massimo Franceschet Angelo Montanari Dipartimento di Matematica e Informatica, Università di Udine Via delle
Intelligent Agents. Formal Characteristics of Planning. Ute Schmid. Cognitive Systems, Applied Computer Science, Bamberg University
 Intelligent Agents Formal Characteristics of Planning Ute Schmid Cognitive Systems, Applied Computer Science, Bamberg University Extensions to the slides for chapter 3 of Dana Nau with contributions by
Intelligent Agents Formal Characteristics of Planning Ute Schmid Cognitive Systems, Applied Computer Science, Bamberg University Extensions to the slides for chapter 3 of Dana Nau with contributions by
Negotiation Games. Javier Esparza and Philipp Hoffmann. Fakultät für Informatik, Technische Universität München, Germany
 Negotiation Games Javier Esparza and Philipp Hoffmann Fakultät für Informatik, Technische Universität München, Germany Abstract. Negotiations, a model of concurrency with multi party negotiation as primitive,
Negotiation Games Javier Esparza and Philipp Hoffmann Fakultät für Informatik, Technische Universität München, Germany Abstract. Negotiations, a model of concurrency with multi party negotiation as primitive,
What You Must Remember When Processing Data Words
 What You Must Remember When Processing Data Words Michael Benedikt, Clemens Ley, and Gabriele Puppis Oxford University Computing Laboratory, Park Rd, Oxford OX13QD UK Abstract. We provide a Myhill-Nerode-like
What You Must Remember When Processing Data Words Michael Benedikt, Clemens Ley, and Gabriele Puppis Oxford University Computing Laboratory, Park Rd, Oxford OX13QD UK Abstract. We provide a Myhill-Nerode-like
Theoretical Foundations of the UML
 Theoretical Foundations of the UML Lecture 17+18: A Logic for MSCs Joost-Pieter Katoen Lehrstuhl für Informatik 2 Software Modeling and Verification Group moves.rwth-aachen.de/teaching/ws-1718/fuml/ 5.
Theoretical Foundations of the UML Lecture 17+18: A Logic for MSCs Joost-Pieter Katoen Lehrstuhl für Informatik 2 Software Modeling and Verification Group moves.rwth-aachen.de/teaching/ws-1718/fuml/ 5.
arxiv:cs/ v2 [cs.lo] 24 Aug 2006
![arxiv:cs/ v2 [cs.lo] 24 Aug 2006 arxiv:cs/ v2 [cs.lo] 24 Aug 2006](/thumbs/78/77252892.jpg) Alternating Timed Automata S lawomir Lasota 1 and Igor Walukiewicz 2 arxiv:cs/0512031v2 [cs.lo] 24 Aug 2006 1 Institute of Informatics, Warsaw University Banacha 2, 02-097 Warszawa 2 LaBRI, Université
Alternating Timed Automata S lawomir Lasota 1 and Igor Walukiewicz 2 arxiv:cs/0512031v2 [cs.lo] 24 Aug 2006 1 Institute of Informatics, Warsaw University Banacha 2, 02-097 Warszawa 2 LaBRI, Université
ON MONADIC LOGIC OF RECURSIVE PROGRAMS WITH PARAMETERS
 Bulletin of the Section of Logic Volume 18/2 (1989), pp. 57 61 reedition 2006 [original edition, pp. 57 62] A. L. Rastsvetaev ON MONADIC LOGIC OF RECURSIVE PROGRAMS WITH PARAMETERS 1. Introduction The
Bulletin of the Section of Logic Volume 18/2 (1989), pp. 57 61 reedition 2006 [original edition, pp. 57 62] A. L. Rastsvetaev ON MONADIC LOGIC OF RECURSIVE PROGRAMS WITH PARAMETERS 1. Introduction The
Semantic Equivalences and the. Verification of Infinite-State Systems 1 c 2004 Richard Mayr
 Semantic Equivalences and the Verification of Infinite-State Systems Richard Mayr Department of Computer Science Albert-Ludwigs-University Freiburg Germany Verification of Infinite-State Systems 1 c 2004
Semantic Equivalences and the Verification of Infinite-State Systems Richard Mayr Department of Computer Science Albert-Ludwigs-University Freiburg Germany Verification of Infinite-State Systems 1 c 2004
A Uniformization Theorem for Nested Word to Word Transductions
 A Uniformization Theorem for Nested Word to Word Transductions Dmitry Chistikov and Rupak Majumdar Max Planck Institute for Software Systems (MPI-SWS) Kaiserslautern and Saarbrücken, Germany {dch,rupak}@mpi-sws.org
A Uniformization Theorem for Nested Word to Word Transductions Dmitry Chistikov and Rupak Majumdar Max Planck Institute for Software Systems (MPI-SWS) Kaiserslautern and Saarbrücken, Germany {dch,rupak}@mpi-sws.org
Symbolic Data Structure for sets of k-uples of integers
 Symbolic Data Structure for sets of k-uples of integers Pierre Ganty 1, Cédric Meuter 1, Laurent Van Begin 1, Gabriel Kalyon 1, Jean-François Raskin 1, and Giorgio Delzanno 2 1 Département d Informatique,
Symbolic Data Structure for sets of k-uples of integers Pierre Ganty 1, Cédric Meuter 1, Laurent Van Begin 1, Gabriel Kalyon 1, Jean-François Raskin 1, and Giorgio Delzanno 2 1 Département d Informatique,
Timed pushdown automata revisited
 Timed pushdown automata revisited Lorenzo Clemente University of Warsaw Sławomir Lasota University of Warsaw Abstract This paper contains two results on timed extensions of pushdown automata (PDA). As
Timed pushdown automata revisited Lorenzo Clemente University of Warsaw Sławomir Lasota University of Warsaw Abstract This paper contains two results on timed extensions of pushdown automata (PDA). As
X-machines - a computational model framework.
 Chapter 2. X-machines - a computational model framework. This chapter has three aims: To examine the main existing computational models and assess their computational power. To present the X-machines as
Chapter 2. X-machines - a computational model framework. This chapter has three aims: To examine the main existing computational models and assess their computational power. To present the X-machines as
A Tableau-Based Decision Procedure for Right Propositional Neighborhood Logic (RPNL )
 A Tableau-Based Decision Procedure for Right Propositional Neighborhood Logic (RPNL ) Davide Bresolin Angelo Montanari Dipartimento di Matematica e Informatica Università degli Studi di Udine {bresolin,
A Tableau-Based Decision Procedure for Right Propositional Neighborhood Logic (RPNL ) Davide Bresolin Angelo Montanari Dipartimento di Matematica e Informatica Università degli Studi di Udine {bresolin,
arxiv: v1 [cs.lo] 17 Jun 2014
![arxiv: v1 [cs.lo] 17 Jun 2014 arxiv: v1 [cs.lo] 17 Jun 2014](/thumbs/94/119175911.jpg) On MITL and alternating timed automata over infinite words Thomas Brihaye 1, Morgane Estiévenart 1, and Gilles Geeraerts 2 1 UMons, Belgium, 2 U.L.B., Belgium arxiv:1406.4395v1 [cs.lo] 17 Jun 2014 Abstract.
On MITL and alternating timed automata over infinite words Thomas Brihaye 1, Morgane Estiévenart 1, and Gilles Geeraerts 2 1 UMons, Belgium, 2 U.L.B., Belgium arxiv:1406.4395v1 [cs.lo] 17 Jun 2014 Abstract.
Serge Haddad Mathieu Sassolas. Verification on Interrupt Timed Automata. Research Report LSV-09-16
 Béatrice Bérard Serge Haddad Mathieu Sassolas Verification on Interrupt Timed Automata Research Report LSV-09-16 July 2009 Verification on Interrupt Timed Automata Béatrice Bérard 1, Serge Haddad 2, Mathieu
Béatrice Bérard Serge Haddad Mathieu Sassolas Verification on Interrupt Timed Automata Research Report LSV-09-16 July 2009 Verification on Interrupt Timed Automata Béatrice Bérard 1, Serge Haddad 2, Mathieu
Hubert Comon-Lundh Florent Jacquemard Nicolas Perrin. Tree Automata with Memory, Visibility and Structural Constraints. Research Report LSV-07-01
 Hubert Comon-Lundh Florent Jacquemard Nicolas Perrin Tree Automata with Memory, Visibility and Structural Constraints Research Report LSV-07-01 January 2007 Tree Automata with Memory, Visibility and Structural
Hubert Comon-Lundh Florent Jacquemard Nicolas Perrin Tree Automata with Memory, Visibility and Structural Constraints Research Report LSV-07-01 January 2007 Tree Automata with Memory, Visibility and Structural
Transducers for bidirectional decoding of prefix codes
 Transducers for bidirectional decoding of prefix codes Laura Giambruno a,1, Sabrina Mantaci a,1 a Dipartimento di Matematica ed Applicazioni - Università di Palermo - Italy Abstract We construct a transducer
Transducers for bidirectional decoding of prefix codes Laura Giambruno a,1, Sabrina Mantaci a,1 a Dipartimento di Matematica ed Applicazioni - Università di Palermo - Italy Abstract We construct a transducer
Dipartimento di Scienze dell Informazione
 UNIVERSITÀ DEGLI STUDI DI MILANO Dipartimento di Scienze dell Informazione RAPPORTO INTERNO N 313-07 Combination Methods for Satisfiability and Model-Checking of Infinite-State Systems Silvio Ghilardi,
UNIVERSITÀ DEGLI STUDI DI MILANO Dipartimento di Scienze dell Informazione RAPPORTO INTERNO N 313-07 Combination Methods for Satisfiability and Model-Checking of Infinite-State Systems Silvio Ghilardi,
Part I: Definitions and Properties
 Turing Machines Part I: Definitions and Properties Finite State Automata Deterministic Automata (DFSA) M = {Q, Σ, δ, q 0, F} -- Σ = Symbols -- Q = States -- q 0 = Initial State -- F = Accepting States
Turing Machines Part I: Definitions and Properties Finite State Automata Deterministic Automata (DFSA) M = {Q, Σ, δ, q 0, F} -- Σ = Symbols -- Q = States -- q 0 = Initial State -- F = Accepting States
On the Automatic Analysis of Recursive Security Protocols with XOR
 On the Automatic Analysis of Recursive Security Protocols with XOR Ralf Küsters 1 and Tomasz Truderung 2 1 ETH Zurich ralf.kuesters@inf.ethz.ch 2 University of Kiel, Wrocław University tomasz.truderung@ii.uni.wroc.pl
On the Automatic Analysis of Recursive Security Protocols with XOR Ralf Küsters 1 and Tomasz Truderung 2 1 ETH Zurich ralf.kuesters@inf.ethz.ch 2 University of Kiel, Wrocław University tomasz.truderung@ii.uni.wroc.pl
Introduction to Computers & Programming
 16.070 Introduction to Computers & Programming Theory of computation: What is a computer? FSM, Automata Prof. Kristina Lundqvist Dept. of Aero/Astro, MIT Models of Computation What is a computer? If you
16.070 Introduction to Computers & Programming Theory of computation: What is a computer? FSM, Automata Prof. Kristina Lundqvist Dept. of Aero/Astro, MIT Models of Computation What is a computer? If you
Languages, regular languages, finite automata
 Notes on Computer Theory Last updated: January, 2018 Languages, regular languages, finite automata Content largely taken from Richards [1] and Sipser [2] 1 Languages An alphabet is a finite set of characters,
Notes on Computer Theory Last updated: January, 2018 Languages, regular languages, finite automata Content largely taken from Richards [1] and Sipser [2] 1 Languages An alphabet is a finite set of characters,
Formal Verification of Mobile Network Protocols
 Dipartimento di Informatica, Università di Pisa, Italy milazzo@di.unipi.it Pisa April 26, 2005 Introduction Modelling Systems Specifications Examples Algorithms Introduction Design validation ensuring
Dipartimento di Informatica, Università di Pisa, Italy milazzo@di.unipi.it Pisa April 26, 2005 Introduction Modelling Systems Specifications Examples Algorithms Introduction Design validation ensuring
Integer Linear Programming Based Property Checking for Asynchronous Reactive Systems
 IEEE TRANSACTIONS ON SOFTWARE ENGINEERING 1 Integer Linear Programming Based Property Checking for Asynchronous Reactive Systems Stefan Leue Department of Computer and Information Science University of
IEEE TRANSACTIONS ON SOFTWARE ENGINEERING 1 Integer Linear Programming Based Property Checking for Asynchronous Reactive Systems Stefan Leue Department of Computer and Information Science University of
Variable Automata over Infinite Alphabets
 Variable Automata over Infinite Alphabets Orna Grumberg a, Orna Kupferman b, Sarai Sheinvald b a Department of Computer Science, The Technion, Haifa 32000, Israel b School of Computer Science and Engineering,
Variable Automata over Infinite Alphabets Orna Grumberg a, Orna Kupferman b, Sarai Sheinvald b a Department of Computer Science, The Technion, Haifa 32000, Israel b School of Computer Science and Engineering,
September 7, Formal Definition of a Nondeterministic Finite Automaton
 Formal Definition of a Nondeterministic Finite Automaton September 7, 2014 A comment first The formal definition of an NFA is similar to that of a DFA. Both have states, an alphabet, transition function,
Formal Definition of a Nondeterministic Finite Automaton September 7, 2014 A comment first The formal definition of an NFA is similar to that of a DFA. Both have states, an alphabet, transition function,
On the coinductive nature of centralizers
 On the coinductive nature of centralizers Charles Grellois INRIA & University of Bologna Séminaire du LIFO Jan 16, 2017 Charles Grellois (INRIA & Bologna) On the coinductive nature of centralizers Jan
On the coinductive nature of centralizers Charles Grellois INRIA & University of Bologna Séminaire du LIFO Jan 16, 2017 Charles Grellois (INRIA & Bologna) On the coinductive nature of centralizers Jan
Laboratoire Spécification & Vérification. Language Preservation Problems in Parametric Timed Automata. Étienne André and Nicolas Markey
 Language Preservation Problems in Parametric Timed Automata Étienne André and Nicolas Markey June 2015 Research report LSV-15-05 (Version 1) Laboratoire Spécification & Vérification École Normale Supérieure
Language Preservation Problems in Parametric Timed Automata Étienne André and Nicolas Markey June 2015 Research report LSV-15-05 (Version 1) Laboratoire Spécification & Vérification École Normale Supérieure
Unbounded, Fully Symbolic Model Checking of Timed Automata using Boolean Methods
 Unbounded, Fully Symbolic Model Checking of Timed Automata using Boolean Methods Sanjit A. Seshia and Randal E. Bryant Computer Science Department Carnegie Mellon University Verifying Timed Embedded Systems
Unbounded, Fully Symbolic Model Checking of Timed Automata using Boolean Methods Sanjit A. Seshia and Randal E. Bryant Computer Science Department Carnegie Mellon University Verifying Timed Embedded Systems
7 RC Simulates RA. Lemma: For every RA expression E(A 1... A k ) there exists a DRC formula F with F V (F ) = {A 1,..., A k } and
 7 RC Simulates RA. We now show that DRC (and hence TRC) is at least as expressive as RA. That is, given an RA expression E that mentions at most C, there is an equivalent DRC expression E that mentions
7 RC Simulates RA. We now show that DRC (and hence TRC) is at least as expressive as RA. That is, given an RA expression E that mentions at most C, there is an equivalent DRC expression E that mentions
Timed Automata. Semantics, Algorithms and Tools. Zhou Huaiyang
 Timed Automata Semantics, Algorithms and Tools Zhou Huaiyang Agenda } Introduction } Timed Automata } Formal Syntax } Operational Semantics } Verification Problems } Symbolic Semantics & Verification }
Timed Automata Semantics, Algorithms and Tools Zhou Huaiyang Agenda } Introduction } Timed Automata } Formal Syntax } Operational Semantics } Verification Problems } Symbolic Semantics & Verification }
Foundations of Informatics: a Bridging Course
 Foundations of Informatics: a Bridging Course Week 3: Formal Languages and Semantics Thomas Noll Lehrstuhl für Informatik 2 RWTH Aachen University noll@cs.rwth-aachen.de http://www.b-it-center.de/wob/en/view/class211_id948.html
Foundations of Informatics: a Bridging Course Week 3: Formal Languages and Semantics Thomas Noll Lehrstuhl für Informatik 2 RWTH Aachen University noll@cs.rwth-aachen.de http://www.b-it-center.de/wob/en/view/class211_id948.html
From Liveness to Promptness
 From Liveness to Promptness Orna Kupferman Hebrew University Nir Piterman EPFL Moshe Y. Vardi Rice University Abstract Liveness temporal properties state that something good eventually happens, e.g., every
From Liveness to Promptness Orna Kupferman Hebrew University Nir Piterman EPFL Moshe Y. Vardi Rice University Abstract Liveness temporal properties state that something good eventually happens, e.g., every
Foundations of the X-machine Theory for Testing
 Foundations of the X-machine Theory for Testing Research Report CS-02-06 J. Aguado and A. J. Cowling Department of Computer Science, Sheffield University Regent Court, 211 Portobello Street, Sheffield,
Foundations of the X-machine Theory for Testing Research Report CS-02-06 J. Aguado and A. J. Cowling Department of Computer Science, Sheffield University Regent Court, 211 Portobello Street, Sheffield,
Enhancing Active Automata Learning by a User Log Based Metric
 Master Thesis Computing Science Radboud University Enhancing Active Automata Learning by a User Log Based Metric Author Petra van den Bos First Supervisor prof. dr. Frits W. Vaandrager Second Supervisor
Master Thesis Computing Science Radboud University Enhancing Active Automata Learning by a User Log Based Metric Author Petra van den Bos First Supervisor prof. dr. Frits W. Vaandrager Second Supervisor
