Cisco [ advertises 64K cells output buers per link for its LightStream 00 ATM switch. Stratacom provides 64K cells
|
|
|
- Gervais Morris Newton
- 5 years ago
- Views:
Transcription
1 Analysis of Queueing Displacement Using Switch Port Speedup Israel Cidon y Department of Electrical Engineering Technion - Israel Institute of Technology Haifa 3000, Israel cidon@ee.technion.ac.il Moshe Sidi z Department of Electrical Engineering Technion - Israel Institute of Technology Haifa 3000, Israel moshe@ee.technion.ac.il Asad Khamisy SUN Microsystems Labs 550 Garcia Avenue Mountain View, CA 94043, U.S.A. asad@eng.sun.com Abstract Current high-speed packet switching systems, ATM in particular, have large port buering requirements. The use of highly integrated ASIC technology for implementing high-degree and high-speed switch fabrics is facing a technology mismatch in the sense that today's chip technology does not allow to integrate on-chip the high-speed switching fabric with the large buering requirements. Consequently, many designs are based on the principles of queueing displacement, i.e., they attempt to move the queueing point o-chip. This is usually done by considerably speeding-up the on-chip switch output ports and placing a second external stage of buering between the switch fabric and the outgoing link circuitry. Such designs are very popular and are used by many current ATM switch vendors. While such schemes are widely used, no rigorous analysis has so far been oered to evaluate the design trade-os and to quantify the design points. The model we use to analyze the performance ofthe above system is a two-node tandem queueing system. The rst node in the tandem corresponds to the internal buer while the second node in the tandem corresponds to the external buer. It is assumed that the internal buer is capable to transfer c cells per time unit to the external buer, while the external buer is served at a lower rate of c cells per time unit. The work of I. Cidon and M. Sidi was partially supported by Intel, Israel and by the Fund for the Promotion of Research at the Technion. y also with SUN Microsystems Labs, 550 Garcia Avenue, Mountain View, CA 94043, U.S.A. z Part of the work of this author was done while visiting SUN Microsystems Labs, Mountain View CA, U.S.A. Introduction This paper addresses basic design and performance issues in the architecture of hardware based fast packet switches. The ability to implement cost-eective high-speed switches in silicon is (along with the advance of ber-optic technologies) the enabling technology behind the recent rise of broadband integrated networks, in particular the ATM architecture [,, 3, 4, 5, 6]. Fast hardware based switches have also been at the core of the emerging switched LAN (also termed switching hubs) products as well as the new generation of Gigabit routers [ Current switching system designs in high-speed packet-switching networks and in particular the emerging ATM market have large and consistently growing port buering requirements. This trend follows the expected use of ATM networks for bursty data applications, the use of reactive ow control over ever increasing link speeds and the separation of dierent QoS classes and connection groups to dedicated buers. While in the past ATM vendors have frequently oered switches with less than a hundred cell (5Kbytes) buers, the numbers today have grown typically to more than 0K cell buers. These numbers are expected to continue to grow with the speed of links, with the geographical distances, as well as with the use of more sophisticated buer scheduling mechanisms. For example, Fore System [ html] advertises buer sizes of 53K cells (almost 3Mbytes) and K cells (Mbytes) for its AS- 00 and AS-000 ATM switches, respectively /97 $ IEEE
2 Cisco [ advertises 64K cells output buers per link for its LightStream 00 ATM switch. Stratacom provides 64K cells per port at its BP switch [ The GTE [ span4000.html] SPANet 4000 ATM switch is designed with a buer size of 6K cells. Most hardware based switch designs rely on the new generation of CMOS ASICs which are very popular within products which require fast turn-around and at the same time high integration and high performance. (Nevertheless, these following statements are also correct for today)s fully custom VLSI designs.) The use of highly integrated ASIC technology for implementing high-degree and high-speed switch fabrics (88 to 33 with 55-6Mbps) is facing a technology mismatch in the sense that today)s technology does not allow tointegrate within the same ASIC the high-speed switching fabric logic of many ports with the large amount of fast memory required to buer all switch output ports. Switch Fabric ASIC Figure : Speedup used to extend the memory in an ASIC based switch Consequently, many designs are based on the principles of queueing displacement, i.e., the attempt to move the queueing point o-chip and implement the main buer using standard RAM technology. This is usually done by considerably speeding-up the integrated switch output ports (compared to the actual link speed supported) and placing a second stage (external to the switch) of buering between the switch fabric and the outgoing link. The much higher speed at which the internal buer is o-loaded, considerably reduces its memory requirements for a given overow probability design point. Such a design is very popular and is used by many current C C ATM switch vendors (usually termed as speedup). In particular, the ones which base their buering design on output queueing techniques. (Other designs are also possible, for example, pure input queueing or a shared memory design based exclusively on o-the-shelf RAM.) Figure depicts an ASIC with a limited on-chip buer at the switching fabric being extended with an external memory using the speedup technique. For example, the IBM switch-on-a-chip Prizma chip is limited by the number of on-chip buers and employs speedup technique [ and [8]. Bay Networks, uses speedup in its Lattice Cell switch design to increase the eective amount of buers in its multi-stage switching fabric. While speedup schemes are widely used, no rigorous analysis has so far been oered to evaluate the design trade-os and to quantify the design points. The designer would like toevaluate the size of the internal and external buers required for a certain design point aswell as the speed of the path connecting them together. In particular, it is attractive to map (or lower bound) such dual stage designs to the performance of an \ideal" output queueing design in order to be able to compare dierent switches of different design points. The following works have addressed the speedup problem or have used queueing models which are related to our problem. In [0], the speedup eect was explored using a tandem system model composed of an M/M/C queue feeding a dependent M/M/ queue. This model was investigated by extensive simulation and no rigorous analysis was carried out for the speedup problem. In the relevant tandem queues models only limited results are available. In [9] a tandem of two single server discrete-time queues with independent and identically distributed external arrival processes, where the output of one queue is fed as an additional input for the other queue is solved. This is a special case of our solution when no speedup exists and the server can serve only a single cell at a time slot. In [, ] Boxma analyzes two exponential single server queues in series where the rst queue has a Poisson arrival process and the second is fed by the output of the rst. In both queues the same customers have the same service times. In this case, again, the system in question has no speedup. In [3] a tandem of multiple queues in which message sizes are preserved is considered. Several properties of the joint work load distribution (but no full solution) are presented and proved for such a system. The model we use to analyze the performance of the system with speed-up is a two-node tandem discrete /97 $ IEEE
3 time queueing system. The rst node in the tandem corresponds to the internal (in-asic) buer while the second node in the tandem corresponds to the external buer. We begin the analysis of this system assuming that the external buer can output at most one cell per slot and derive the generating function of the joint probability distribution of the lengths of the two buers. Moments of the queue lengths are then derived. In addition, we introduce an explicit recursion to compute the joint probability distribution. From this we are able to compute tail probabilities that enable us to dimension the length of the buers required to guarantee small loss probabilities when the buers are nite. Speedup of two has special implementation importance as it is a very common and convenient speedup to design and use. It usually does not require tricky clock resynchronizations as either one clock is derived from the other or the path that connects the two buer stages is of double width. Intuitively, with such speedup, the load on the rst buer stage is only half the load on the output port. In a well controlled network, no link should be overloaded (on the average) and hence the rst port has a load limitation of 0.5. This rather low load should enable us to use very few buers at the internal rst stage. Our main numerical conclusion supports this intuition and shows that the internal buer can be kept small without damaging the performance of the whole system. We extend the analysis to more general models in which the external buer can output several cells per slot, and again obtain the generating function of the joint probability distribution of the lengths of the two buers and the moments. The conclusions obtained are similar to the above. The Model The model we use to analyze the performance of the system with speed-up is a two-node tandem discretetime queueing system. The rst node in the tandem corresponds to the internal (in-asic) buer while the second node in the tandem corresponds to the external buer. Time is slotted into xed size slots. It is assumed that during each slot the internal buer is capable to transfer c cells to the external buer, while the external buer is capable to output from the system c cells. Since the internal buer is faster than the external buer, c >c. Note that when c = wehaveintegral speedups (c : ), while for a general c we can have any rational speedup (c : c ). Let A (n) and A (n) be the number of new cells arriving (from outside the system) during slot n to the rst node and the second node, respectively. The arrival process of these new cells at the system is assumed to be an independent and identically distributed (in each slot) process, namely, fa (n) ;A(n) g is independent of fa (k) ;A(k) g for any n 6= k, and Prob(A (n) = i; A P (n) = j) = a i;j is independent of n. Let A(z ;z )= P a i;jz i zj be the joint generating function of the arrival processes to the two nodes. Note that arrivals to the two buers in P the same slot may be correlated. We let r l = i =0P i i =0 la i;i ;z )=@z l j z=z= be the arrival rate of cells to node l (l =;). For the sake of the analysis, we assume that both buers are of in- nite size. We will later discuss how this assumption can be dealt with to attain the performance of realistic switches. (Note that the speedup based output port system corresponds to the case with no external arrivals to the second node, i.e., a i;j =0; j >0.) 3 Analysis We begin our analysis with c =, namely, a single cell can be transmitted by the second node and leave the system during a slot. Note that when c =,our system is identical to the system analyzed in [9]. In our analysis we are interested in computing the steadystate probabilities of the lengths of the two nodes. Since at most one cell can leave the system during a slot, steady-state exists if r r <. Assume that departures take place at the end of slots and arrivals within slots. Let Q (n) and Q (n) denote the lengths of the rst node and the second node at the end of slot n, respectively. Let p (n) i;j = Prob(Q P (n) = i ; Q (n) = j) and G (n) (z ;z )= P p(n) i;j zi zj be the generating function of the joint queue length distribution at both nodes. We let p i;j = lim n! p (n) i;j and G(z ;z ) = lim n! G (n) (z ;z ). The evolution equation of the queue lengths for n 0 is given by Q (n) = (Q (n) c ) A (n) Q (n) = (Q (n) ) min(q (n) ;c )A (n) () From which we have in steady-state (n!), c G(z ;z )=A(z ;z )fp 0;0 p i;0 z i z i zi i= j= j= i= p i;j z i zj z i zi p 0;j z j z p i;0 z i z c z c i=c /97 $ IEEE
4 i=c j= p i;j z i zj z c z c g () Simple algebraic manipulations yield the following, B(z ;z ) G(z ;z )=A(z ;z ) z c z z c A(z ;z ) where B(z ;z )= P c [p i;0(z ) g i (z )](z c z i zc )G(z ; 0)z c (z ) and g i (z )= i! i (z ;z i (3) z =0. In (3), we encounter a common phenomenon in dependent queues, namely, that the generating functions G(z ;z ) is expressed in terms of several boundary functions. In order to uniquely determine G(z ;z ) we will have to determine the boundary functions, G(z ; 0) and g i (z ); 0 i c. In what follows, we develop the method for obtaining these boundary functions. Along this process we mainly use the analytic properties of the generating functions G(z ;z ) in the disk jz i j < ; i =;. We begin by letting z! 0 in () to obtain G(z ; 0) = A(z ; 0)[p 0;0 p 0; ]. When z =0wehave that p 0;0 = a 0;0 (p 0;0 p 0; ) (4) Therefore we can express G(z ; 0) (and the corresponding probabilities p i;0 ; i ) in terms of the constant p 0;0 as follows, G(z ; 0) = A(z ; 0) p 0;0 a 0;0 ; p i;0 = a i;0 p 0;0 a 0;0 i (5) To determine g i (z ); 0 i c, we use the fact that for any jz j <, the denominator z c z z c A(z ;z ) of (3) has exactly c roots within the unit disk jz j < (the proof is based on Rouche`s Theorem). Let these roots be denoted by l (z ); l c. Since G(z ;z ) is an analytic function in the disk jz i j < ; i =;, the nominator of (3) must vanish at each of these roots, i.e., B( l (z );z ) = 0 ; l c (6) where in the above we use p i;0 from (5) and G( l (z ); 0) = A( l (z ); 0)p 0;0 =a 0;0. Expression (6) is a set of c (linear) equations that determines the functions g i (z ); 0 i c up to the constant p 0;0. To complete the derivation of the generating function we need to compute that constant. To that end, let z = z = z in (3) to obtain, G(z;0)(z ) G(z; z) = A(z; z) z A(z; z) = A(z; z) A(z;0)p 0;0(z ) a 0;0 [z A(z; z)] at (7) Letting z! in the above and assuming that the steady-state condition r r < holds, we obtain by using L)H^opital)s law, p 0;0 = a 0;0( r r ) A(; 0) (8) This completes the derivation of the joint generating function of the queue-length probability distribution. Using the generating function we can obtain the average number of cells in node i (i =;), denoted by L i. Letting z = in (3) we have G(z ;) = A(z ; ) g i ()(z c z i ) z c A(z ; ) Taking the derivative of the above expression with respect to z and letting z! we obatin, L = r g i ()(c i )r c ^A (c r ) (9) where ^A = d A(z; )=dz j z=. Taking the derivative of (7) with respect to z and letting z! we obatin (using (8)), d A(z;z) dz j z= da(z; 0) L L = r r j z= dz ( r r ) (0) Subtracting (9) from (0) we obtain the average number of cells in the second node L. 4 The Probability Distribution The joint generating function derived in the previous section allows us to compute p 0;0 and the average quantities easily. However, the computation of the probabilities themselves is dicult. In this section we develop a recursion for the computation of the steadystate probabilities p n;n.from equation (4) we obtain p 0; = p 0;0 ( a 0;0 )=a 0;0.Together with equations (5) and (8) wehave the initial conditions for the recursion, i.e., we know p i;0 ; i0 and p 0;. Next, we compute the probabilities p n;n for n 0 and n c (except for p 0; that is known already). In order to have n ; n c ; cells in the second queue, the number of cells in the rst queue at the end of the previous slot have to be less or equal to n. Assume the number of cells in the rst queue is i; 0 i c ; then in order to have n cells in the rst queue, all n cells have to arrive from the external source. Further, assuming that j cells arrive to the second queue from the external source, /97 $ IEEE
5 the total number of cells that arrive to the second queue is i j. If the second queue is not empty at the end of the previous slot, then in order to have n cells, the number of cells at the end of the previous slot have to be n i j, where the plus accounts for the cell that must have departed the second queue. We have for n 0; n c that p n;n = n n n p i;0 a n;n i i p i;n i ja n;j () where the rst sum corresponds to the case where the second queue is empty at the end of the previous slot. Note that n appears in the right hand side of equation () only in a n;l for some l (and does not appear in any ofthep)s). In equation () we compute the probabilities p n;n in increasing order of n as follows. We assume that p i;j for i 0; 0 j n aswell as p 0;n are known (initially, for n = this is true as explained at the beginning of this section). Next, we compute p 0;n ; p ;n by solving two equations with two unknowns. These equations correspond to equation () with p 0;n and p ;n in the left hand side. Note that the unknown p 0;n appears only in the right hand side of (), while the unknown p ;n appears also in the left hand side. After some simple algebra we obtain the solution for p 0;n ; p ;n as, p 0;n = ( ;n ()a 0;0 ;n (0)(a ;0 ))=a 0;0 p ;n = ( ;n (0)a ;0 ;n ()a 0;0 )=a 0;0 () where we dene ;n (l) =fl=0gp 0;n min(c ;(n )) n i min(c ;(n )) i= j= p i;n i ja l;j fj=n ig p i;n ia l;0 l =0; (3) Now the probabilities p n;n for n are computed directly from equation (). Recursing this procedure completes the computation of the probabilities p n;n for n 0 and n c. Next, we compute the probabilities p n;n for n 0 and n c. There are two cases to consider in the recursion, the rst is when the number of cells in the rst queue is less than c in which case all cells move to the second queue, and the case where the number of cells in the rst queue is greater or equal to c in which case only c cells move from the rst queue to the second queue. Similar to the previous recursion, we have for n 0;n c, p n;n = p i;0 a n;n n i n c i p i;n i ja n;j i=c p i;0 a nc i;n c n c n c i=c p i;n c ja nc i;j(4) In the same way as before, we write two equations for p 0;n and p ;n, from which we obtain the probabilities p 0;n ; p ;n. Then we use equation (4) to compute the probabilities p n;n for n. The solution for p 0;n ; p ;n in this case is given by: p 0;n = ( ;n ()a 0;0 ;n (0)(a ;0 ))=a 0;0 p ;n = ( ;n (0)a ;0 ;n ()a 0;0 )=a 0;0 (5) Where we dene ;n (0) = ;n (0) and ;n () P n = ;n () c p c;n c ja 0;j fj=n c g. Now the probabilities p n;n for n are computed directly from equation (4). This completes the computation of the probabilities p n;n for n 0 and n c. The computation complexity of the probabilities p n;n for 0 n N and 0 n N is in the order of O(N N ). 4. Overow Probability Since we use innite buers in our model, we approximate the cell loss probability by the buer over- ow probability. The rst (second) node is in overow state when the number of cells in the buer exceeds N (N ). If the state upon arrival is (n ;n ), then the the number of cells in the second queue in front of this cell, when this cell arrives to the second queue, will P d(n)=c e i= A (i) d(n )=c e, where be n n A (i) denotes the number of cells that arrive to the second queue in slot number i (the slot of arrival of the cell is marked as slot number ). This is true since. The cell will arrive at the second queue d(n )=c e slots after it arrived to the system, and. c > and hence the second queue will not empty in the next d(n )=c e slots after the arrival of this cell. Correspondingly, we dene the overow probability in the system as the probability that the number of /97 $ IEEE
6 cells in the rst and second nodes at slot boundaries full the relation (n ;n )f(n ;n ) j n >N ; n n d(n )=c e >N g. Next, we consider a system without external arrivals to the second queue, i.e., a i;j =0;j>0. Then, the overow probability in the system is equal to P overflow = N n =0 N d(n )=c e n p n;n (6) n =0 5 The case c > We now consider a system with c >, namely, several cells (c ) can be transmitted by the second node and leave the system during a slot. As before, we are interested in computing the steady-state probabilities of the lengths of the two nodes. Since c > cells can leave the system during a slot, steady-state exists if r r <c. With the same notations as in Section 3 the evolution equation of the queue lengths for n 0 is given by Q (n) = (Q (n) c ) A (n) Q (n) = (Q (n) c ) min(q (n) ;c )A (n) (7) Similar to the method for obtaining (), we obtain in this case, G(z ;z ) = A(z ;z )f i=c i=c p i;j z i zj z i j=c p i;j z i zj z i zi j zi c p i;j z i zj z c z c j j=c p i;j z i zj z c c c z and after simple algebraic manipulations we get, B(z ;z ) G(z ;z )=A(z ;z ) z c zc z c A(z ;z ) where B(z ;z ) = z i )g i(z )](z c zi z i zc ) c c c [ g (8) p i;j (z c (9) f j (z )z c (zc z j ) and g i (z i (z ;z ) j z=0, f i j (z j (z ;z ) j z=0. j In order to uniquely determine G(z ;z )we will have to determine the boundary functions, f j (z ); 0 j c and g i (z ); 0 i c. In what follows, we demonstrate the method for obtaining these boundary functions. Along this process we mainly use the analytic properties of the generating functions G(z ;z ) in the disk jz i j < ; i =;. We begin by taking the l-th derivative (0 l c ) of both sides of (8) with respect to z and let z! 0 to obtain, f l (z )= l k=0 A l k (z ) u k (l k)! (0) where A i (z ) i (z ;z )=@zj i z=0, and u k = P P c p k k;j p j;c k j. Consequently, f l (z ) (and the corresponding probabilities p i;l ; i0) are expressed in terms of the constants u k ; 0 k l. To determine these constants, we let z = z = z in (9) to obtain, ^B(z) G(z; z) =A(z; z) () z c A(z; z) where ^B(z) = P P c (zc z j j ) k=0 A j k(z) u k =(j k)!. Letting z! in the above and assuming that the steady-state condition r r <c holds, we obtain c r r = (c j) j k=0 A j k () u k (j k)! () Furthermore, the denominator z c A(z; z) of () has one root at z = and exactly c roots within the unit disk jzj < (the proof is based on Rouche`s Theorem). Let these roots be denoted by l ; l c. Since G(z; z) is an analytic function in the disk jzj <, the nominator of () must vanish at each of these roots, i.e., for l c, ( c l j l ) j k=0 A j k ( l ) u k (j k)! =0 (3) Equation () together with (3) is a set of c (linear) equations that determines the constants u k ; 0 k c, and hence the boundary functions f j (z ); 0 j c are determined (using (0)). From f j (z ) we can obtain p i;j ;j0by taking the i-th derivative of f j (z ) with respect to z and letting z! 0. To determine g i (z ); 0 i c, we use the same procedure described in Section 3. In particular, we note that for any jz j <, the denominator z c zc z c A(z ;z ) of (9) has exactly c roots within the /97 $ IEEE
7 unit disk jz j < (the proof is based on Rouche`s Theorem). Let these roots be denoted by l (z ); l c. Since G(z ;z ) is an analytic function in the disk jz i j < ; i =;, the nominator of (9) must vanish at each of these roots, i.e., B( l (z );z ) = 0 l c (4) Expression (4) is a set of c (linear) equations that determines the functions g i (z ); 0 i c. This completes the derivation of the joint generating function of the queue-length probability distribution. In [4] we provide the procedure for computing the joint probability distribution in this case. Using the generating function we can obtain the average number of cells in node i (i =;), denoted by L i,aswas done in Section 3. In fact, the average number of cells in the rst node does not change with c, hence is identical to (9). Taking the derivative of () with respect to z and letting z! we obatin, L L = r r where ^A = ^A c (c ) (c r r ) j k=0 d A(z;z) dz j z= (c r r ) u k (j k)! f[c (c ) j(j (5) )]A j k ()(c j)da j k (z)=dzj z= g. Subtracting (9) from (5) we obtain the average number of cells in the second node L. 6 Numerical Results In the rst example cells arrive to the system (through the rst node only) according to a Poisson process with rate. We set c = and c =. In Figure we plot the overow probability in the system versus the internal buer size for external buer size of 80 cells and load of =0:9. We also plot the overow probability in the internal buer, external buer and in an \ideal" output buer switch with c =. From Figure we notice that for internal buer size greater or equal to 5, the overow probability in the system is less than the overow probability in the \ideal" system. Also, the main contribution to the total overow probability for small (large) internal buer sizes comes from the internal (external) overow probability. Notice that the internal buer reduces the burstiness of the input process to the external buer by limiting the maximum number of cells that can arrive to the external buer to c =, and hence the overow probability in the system and in the external buer is smaller than the overow probability in the \ideal" system. We obtained numerical results for dierent external buer sizes and loads where the overow probability in the \ideal" system was kept at 0 7. In all examples, an internal buer size between and 4 cells was sucient to bring the overow probability in the system below 0 7. The same phenomena described in Figure were observed in all examples. Overflow Probability System Overflow Probability _._._ Internal Overflow Probability... External Overflow Probability Ideal Overflow Probability Internal Buffer Size Figure : Overow probability versus internal buer size for load of 0.9 and external buer size of 80 cells. More numerical results are provided in Figure 3 where we plot the overow probability versus the average load for internal buer size of 5 and external buer size of 40. We see again that internal buer size of 5 is enough to achieve smaller overow probability in the system compared to the \ideal" system, for average load of 0.75 or larger (for the range of 0 9 overow probability this is the relevant load range). Numerical results for the case c > are provided in [4]. Overflow Probability Total Overflow Probability _._._ Internal Overflow Probability... External Overflow Probability Ideal Overflow Probability Average Load Figure 3: Overow probability versus average load for internal buer size of 5 and external buer size of /97 $ IEEE
8 We also simulated a system with bursty trac model that corresponds to VBR trac class. Here we used three groups of sources. Each group consists of 0 identical sources. Each source corresponds to Interrupted Poisson Process (IPP) model, with sources in the rst group having an average ON period of 00 slots and average OFF period of 00 slots. The second and third group sources have average (ON, OFF) periods of (00, 300) and (00, 900), respectively. The average load in the system is termed "VBR Load" and the total load of each group is "VBR Load"/3. Table 6 contains the overow probability in the \ideal" system and in the system versus "VBR Load" for dierent internal buer sizes. The conclusions are similar to the Poisson model. [6] J. Hui, "A broadband packet switch for multirate services," Proc. of International Conference on Comm. (ICC'87): 78{788, June 987. [7] AT(T Microelectronics, Microelectronic Products Selection Guide, AT(T Microelectronics, Jan [8] W. E. Denzel, A. P. J. Engbersen, I. Iliadis, and G. Karlsson, "A highly modular packet switch for GB/S rates," Proc. of International Switching Symposium, :A8.3, Oct. 99. [9] J. A. Morrison, "Two discrete-time queues in tandem," IEEE Trans. on Comm., COM-7:563{ 573, 979. VBR Load Ideal IB = 8 IB = 0 IB=5 IB = 0 0:6 : : : : : :66 7: : : : : :70 : :8 0 3 : : : :74 3: : : : : :78 6: : : : : :8 :04 0 :06 0 :04 0 :03 0 :03 0 Table : Overow probability versus VBR Load for external buer size of 00. References [] J. S. Turner, "Design of an integrated services packet network," IEEE Journal on Selected Areas in Comm., SAC-4:373{380, Nov [] I. Cidon and I. S. Gopal, "PARIS: An approach to integrated high-speed private networks," International Journal of Digital and Analog Cabled Systems, ():77{85, April 988. [3] J. N. Giacopelli and et al, "Sunshine: A high-performance self-routing broadband packet switch architecture," IEEE Journal on Selected Areas in Comm., SAC-9:89{98, Oct. 99. [4] P. Newman, "A fast packet switch for the integrated services backbone network," IEEE Journal on Selected Areas in Comm., SAC-6:468{ 479, 988. [5] Y. S. Yeh, M. G. Hluchyj, and A. S. Acampora, "The knockout switch: A simple, modular architecture for high performance packet switching," IEEE Journal on Selected Areas in Comm.,SAC- 5:74{83, Oct [0] J. S. C. Chen and T. E. Stern, "Throughput analysis, optimal buer allocation, and trac imbalance study of a generic nonblocking packet switch," IEEE Journal on Selected Areas in Comm., SAC-9, 3:439{449, 99. [] O. J. Boxma, "On a tandem queueing model with identical service times at both counters, I," Adv. Appl. Prob., ():66{643, November 979. [] O. J. Boxma, "On a tandem queueing model with identical service times at both counters, II," Adv. Appl. Prob., ():644{659, November 979. [3] S. B. Calo, "Message delays in repeated-service tandem connections," IEEE Trans. on Comm., COM-9:670{678, May 98. [4] I. Cidon, A. Khamisy and M. Sidi, "Analysis of Queueing Displacement Using Switch Port Speedup," CC PUB 70, October /97 $ IEEE
Multiplicative Multifractal Modeling of. Long-Range-Dependent (LRD) Trac in. Computer Communications Networks. Jianbo Gao and Izhak Rubin
 Multiplicative Multifractal Modeling of Long-Range-Dependent (LRD) Trac in Computer Communications Networks Jianbo Gao and Izhak Rubin Electrical Engineering Department, University of California, Los Angeles
Multiplicative Multifractal Modeling of Long-Range-Dependent (LRD) Trac in Computer Communications Networks Jianbo Gao and Izhak Rubin Electrical Engineering Department, University of California, Los Angeles
Fast Evaluation of Ensemble Transients of Large IP Networks. University of Maryland, College Park CS-TR May 11, 1998.
 Fast Evaluation of Ensemble Transients of Large IP Networks Catalin T. Popescu cpopescu@cs.umd.edu A. Udaya Shankar shankar@cs.umd.edu Department of Computer Science University of Maryland, College Park
Fast Evaluation of Ensemble Transients of Large IP Networks Catalin T. Popescu cpopescu@cs.umd.edu A. Udaya Shankar shankar@cs.umd.edu Department of Computer Science University of Maryland, College Park
queue KTH, Royal Institute of Technology, Department of Microelectronics and Information Technology
 Analysis of the Packet oss Process in an MMPP+M/M/1/K queue György Dán, Viktória Fodor KTH, Royal Institute of Technology, Department of Microelectronics and Information Technology {gyuri,viktoria}@imit.kth.se
Analysis of the Packet oss Process in an MMPP+M/M/1/K queue György Dán, Viktória Fodor KTH, Royal Institute of Technology, Department of Microelectronics and Information Technology {gyuri,viktoria}@imit.kth.se
2 optimal prices the link is either underloaded or critically loaded; it is never overloaded. For the social welfare maximization problem we show that
 1 Pricing in a Large Single Link Loss System Costas A. Courcoubetis a and Martin I. Reiman b a ICS-FORTH and University of Crete Heraklion, Crete, Greece courcou@csi.forth.gr b Bell Labs, Lucent Technologies
1 Pricing in a Large Single Link Loss System Costas A. Courcoubetis a and Martin I. Reiman b a ICS-FORTH and University of Crete Heraklion, Crete, Greece courcou@csi.forth.gr b Bell Labs, Lucent Technologies
Environment (E) IBP IBP IBP 2 N 2 N. server. System (S) Adapter (A) ACV
 The Adaptive Cross Validation Method - applied to polling schemes Anders Svensson and Johan M Karlsson Department of Communication Systems Lund Institute of Technology P. O. Box 118, 22100 Lund, Sweden
The Adaptive Cross Validation Method - applied to polling schemes Anders Svensson and Johan M Karlsson Department of Communication Systems Lund Institute of Technology P. O. Box 118, 22100 Lund, Sweden
A discrete-time priority queue with train arrivals
 A discrete-time priority queue with train arrivals Joris Walraevens, Sabine Wittevrongel and Herwig Bruneel SMACS Research Group Department of Telecommunications and Information Processing (IR07) Ghent
A discrete-time priority queue with train arrivals Joris Walraevens, Sabine Wittevrongel and Herwig Bruneel SMACS Research Group Department of Telecommunications and Information Processing (IR07) Ghent
[4] T. I. Seidman, \\First Come First Serve" is Unstable!," tech. rep., University of Maryland Baltimore County, 1993.
![[4] T. I. Seidman, \\First Come First Serve is Unstable!, tech. rep., University of Maryland Baltimore County, 1993. [4] T. I. Seidman, \\First Come First Serve is Unstable!, tech. rep., University of Maryland Baltimore County, 1993.](/thumbs/86/93513281.jpg) [2] C. J. Chase and P. J. Ramadge, \On real-time scheduling policies for exible manufacturing systems," IEEE Trans. Automat. Control, vol. AC-37, pp. 491{496, April 1992. [3] S. H. Lu and P. R. Kumar,
[2] C. J. Chase and P. J. Ramadge, \On real-time scheduling policies for exible manufacturing systems," IEEE Trans. Automat. Control, vol. AC-37, pp. 491{496, April 1992. [3] S. H. Lu and P. R. Kumar,
G-networks with synchronized partial ushing. PRi SM, Universite de Versailles, 45 av. des Etats Unis, Versailles Cedex,France
 G-networks with synchronized partial ushing Jean-Michel FOURNEAU ;a, Dominique VERCH ERE a;b a PRi SM, Universite de Versailles, 45 av. des Etats Unis, 78 05 Versailles Cedex,France b CERMSEM, Universite
G-networks with synchronized partial ushing Jean-Michel FOURNEAU ;a, Dominique VERCH ERE a;b a PRi SM, Universite de Versailles, 45 av. des Etats Unis, 78 05 Versailles Cedex,France b CERMSEM, Universite
Efficient Nonlinear Optimizations of Queuing Systems
 Efficient Nonlinear Optimizations of Queuing Systems Mung Chiang, Arak Sutivong, and Stephen Boyd Electrical Engineering Department, Stanford University, CA 9435 Abstract We present a systematic treatment
Efficient Nonlinear Optimizations of Queuing Systems Mung Chiang, Arak Sutivong, and Stephen Boyd Electrical Engineering Department, Stanford University, CA 9435 Abstract We present a systematic treatment
RUNNING ADDER NETWORK DUMMY ADDRESS ENCODER BANYAN NUMBER
 Integral Expressions for the Numerical Evaluation of Product Form Expressions Over Irregular Multidimensional Integer State Spaces D. Manjunath Biplab Sikdar Department of Electrical Engg. Department of
Integral Expressions for the Numerical Evaluation of Product Form Expressions Over Irregular Multidimensional Integer State Spaces D. Manjunath Biplab Sikdar Department of Electrical Engg. Department of
Introduction This paper is motivated by the question of whether a predictor of future packet arrivals could improve switch performance. This is a two-
 Future Information in Input Queueing Timothy X Brown Electrical & Computer Engineering timxb@colorado.edu Hal Gabow Computer Science hal@cs.colorado.edu University of Colorado Boulder, CO 80309-0425 Abstract
Future Information in Input Queueing Timothy X Brown Electrical & Computer Engineering timxb@colorado.edu Hal Gabow Computer Science hal@cs.colorado.edu University of Colorado Boulder, CO 80309-0425 Abstract
A POPULATION-MIX DRIVEN APPROXIMATION FOR QUEUEING NETWORKS WITH FINITE CAPACITY REGIONS
 A POPULATION-MIX DRIVEN APPROXIMATION FOR QUEUEING NETWORKS WITH FINITE CAPACITY REGIONS J. Anselmi 1, G. Casale 2, P. Cremonesi 1 1 Politecnico di Milano, Via Ponzio 34/5, I-20133 Milan, Italy 2 Neptuny
A POPULATION-MIX DRIVEN APPROXIMATION FOR QUEUEING NETWORKS WITH FINITE CAPACITY REGIONS J. Anselmi 1, G. Casale 2, P. Cremonesi 1 1 Politecnico di Milano, Via Ponzio 34/5, I-20133 Milan, Italy 2 Neptuny
Batch Arrival Queuing Models with Periodic Review
 Batch Arrival Queuing Models with Periodic Review R. Sivaraman Ph.D. Research Scholar in Mathematics Sri Satya Sai University of Technology and Medical Sciences Bhopal, Madhya Pradesh National Awardee
Batch Arrival Queuing Models with Periodic Review R. Sivaraman Ph.D. Research Scholar in Mathematics Sri Satya Sai University of Technology and Medical Sciences Bhopal, Madhya Pradesh National Awardee
Any Work-conserving Policy Stabilizes the Ring with Spatial Reuse
 Any Work-conserving Policy Stabilizes the Ring with Spatial Reuse L. assiulas y Dept. of Electrical Engineering Polytechnic University Brooklyn, NY 20 leandros@olympos.poly.edu L. Georgiadis IBM. J. Watson
Any Work-conserving Policy Stabilizes the Ring with Spatial Reuse L. assiulas y Dept. of Electrical Engineering Polytechnic University Brooklyn, NY 20 leandros@olympos.poly.edu L. Georgiadis IBM. J. Watson
In Proceedings of the 13th U.K. Workshop on Performance Engineering of Computer. and Telecommunication Systems (UKPEW'97), July 1997, Ilkley, U.K.
 In Proceedings of the 13th U.K. Workshop on Performance Engineering of Computer and Telecommunication Systems (UKPEW'97), July 1997, Ilkley, U.K. Investigation of Cell Scale and Burst Scale Eects on the
In Proceedings of the 13th U.K. Workshop on Performance Engineering of Computer and Telecommunication Systems (UKPEW'97), July 1997, Ilkley, U.K. Investigation of Cell Scale and Burst Scale Eects on the
Trac of an ATM-SMX in the NCIH. Tung Ouyang and Arne A. Nilsson. Center for Advanced Computing and Communication
 Departure Process for Periodic Real-Time Trac of an ATM-SMX in the NCIH Tung Ouyang and Arne A. Nilsson Center for Advanced Computing and Communication Department of Electrical and Computer Engineering
Departure Process for Periodic Real-Time Trac of an ATM-SMX in the NCIH Tung Ouyang and Arne A. Nilsson Center for Advanced Computing and Communication Department of Electrical and Computer Engineering
I 2 (t) R (t) R 1 (t) = R 0 (t) B 1 (t) R 2 (t) B b (t) = N f. C? I 1 (t) R b (t) N b. Acknowledgements
 Proc. 34th Allerton Conf. on Comm., Cont., & Comp., Monticello, IL, Oct., 1996 1 Service Guarantees for Window Flow Control 1 R. L. Cruz C. M. Okino Department of Electrical & Computer Engineering University
Proc. 34th Allerton Conf. on Comm., Cont., & Comp., Monticello, IL, Oct., 1996 1 Service Guarantees for Window Flow Control 1 R. L. Cruz C. M. Okino Department of Electrical & Computer Engineering University
These are special traffic patterns that create more stress on a switch
 Myths about Microbursts What are Microbursts? Microbursts are traffic patterns where traffic arrives in small bursts. While almost all network traffic is bursty to some extent, storage traffic usually
Myths about Microbursts What are Microbursts? Microbursts are traffic patterns where traffic arrives in small bursts. While almost all network traffic is bursty to some extent, storage traffic usually
IEEE Journal of Selected Areas in Communication, special issue on Advances in the Fundamentals of Networking ( vol. 13, no. 6 ), Aug
 IEEE Journal of Selected Areas in Communication, special issue on Advances in the Fundamentals of Networking ( vol. 13, no. 6 ), Aug. 1995. Quality of Service Guarantees in Virtual Circuit Switched Networks
IEEE Journal of Selected Areas in Communication, special issue on Advances in the Fundamentals of Networking ( vol. 13, no. 6 ), Aug. 1995. Quality of Service Guarantees in Virtual Circuit Switched Networks
Carry-Over Round Robin: A Simple Cell Scheduling Mechanism. for ATM Networks. Abstract
 Carry-Over Round Robin: A Simple Cell Scheduling Mechanism for ATM Networks Debanjan Saha y Sarit Mukherjee z Satish K. Tripathi x Abstract We propose a simple cell scheduling mechanism for ATM networks.
Carry-Over Round Robin: A Simple Cell Scheduling Mechanism for ATM Networks Debanjan Saha y Sarit Mukherjee z Satish K. Tripathi x Abstract We propose a simple cell scheduling mechanism for ATM networks.
A Queueing System with Queue Length Dependent Service Times, with Applications to Cell Discarding in ATM Networks
 A Queueing System with Queue Length Dependent Service Times, with Applications to Cell Discarding in ATM Networks by Doo Il Choi, Charles Knessl and Charles Tier University of Illinois at Chicago 85 South
A Queueing System with Queue Length Dependent Service Times, with Applications to Cell Discarding in ATM Networks by Doo Il Choi, Charles Knessl and Charles Tier University of Illinois at Chicago 85 South
Submitted to IEEE Transactions on Computers, June Evaluating Dynamic Failure Probability for Streams with. (m; k)-firm Deadlines
 Submitted to IEEE Transactions on Computers, June 1994 Evaluating Dynamic Failure Probability for Streams with (m; k)-firm Deadlines Moncef Hamdaoui and Parameswaran Ramanathan Department of Electrical
Submitted to IEEE Transactions on Computers, June 1994 Evaluating Dynamic Failure Probability for Streams with (m; k)-firm Deadlines Moncef Hamdaoui and Parameswaran Ramanathan Department of Electrical
One billion+ terminals in voice network alone
 Traffic Engineering Traffic Engineering One billion+ terminals in voice networ alone Plus data, video, fax, finance, etc. Imagine all users want service simultaneously its not even nearly possible (despite
Traffic Engineering Traffic Engineering One billion+ terminals in voice networ alone Plus data, video, fax, finance, etc. Imagine all users want service simultaneously its not even nearly possible (despite
Inequality Comparisons and Traffic Smoothing in Multi-Stage ATM Multiplexers
 IEEE Proceedings of the International Conference on Communications, 2000 Inequality Comparisons and raffic Smoothing in Multi-Stage AM Multiplexers Michael J. Neely MI -- LIDS mjneely@mit.edu Abstract
IEEE Proceedings of the International Conference on Communications, 2000 Inequality Comparisons and raffic Smoothing in Multi-Stage AM Multiplexers Michael J. Neely MI -- LIDS mjneely@mit.edu Abstract
TRANSIENT ANALYSIS OF A DISCRETE-TIME PRIORITY QUEUE
 RANSIEN ANALYSIS OF A DISCREE-IME PRIORIY QUEUE Joris Walraevens Dieter Fiems Herwig Bruneel SMACS Research Group Department of elecommunications and Information Processing (W7) Ghent University - UGent
RANSIEN ANALYSIS OF A DISCREE-IME PRIORIY QUEUE Joris Walraevens Dieter Fiems Herwig Bruneel SMACS Research Group Department of elecommunications and Information Processing (W7) Ghent University - UGent
M/G/FQ: STOCHASTIC ANALYSIS OF FAIR QUEUEING SYSTEMS
 M/G/FQ: STOCHASTIC ANALYSIS OF FAIR QUEUEING SYSTEMS MOHAMMED HAWA AND DAVID W. PETR Information and Telecommunications Technology Center University of Kansas, Lawrence, Kansas, 66045 email: {hawa, dwp}@ittc.ku.edu
M/G/FQ: STOCHASTIC ANALYSIS OF FAIR QUEUEING SYSTEMS MOHAMMED HAWA AND DAVID W. PETR Information and Telecommunications Technology Center University of Kansas, Lawrence, Kansas, 66045 email: {hawa, dwp}@ittc.ku.edu
A Retrial Queueing model with FDL at OBS core node
 A Retrial Queueing model with FDL at OBS core node Chuong Dang Thanh a, Duc Pham Trung a, Thang Doan Van b a Faculty of Information Technology, College of Sciences, Hue University, Hue, Viet Nam. E-mail:
A Retrial Queueing model with FDL at OBS core node Chuong Dang Thanh a, Duc Pham Trung a, Thang Doan Van b a Faculty of Information Technology, College of Sciences, Hue University, Hue, Viet Nam. E-mail:
System occupancy of a two-class batch-service queue with class-dependent variable server capacity
 System occupancy of a two-class batch-service queue with class-dependent variable server capacity Jens Baetens 1, Bart Steyaert 1, Dieter Claeys 1,2, and Herwig Bruneel 1 1 SMACS Research Group, Dept.
System occupancy of a two-class batch-service queue with class-dependent variable server capacity Jens Baetens 1, Bart Steyaert 1, Dieter Claeys 1,2, and Herwig Bruneel 1 1 SMACS Research Group, Dept.
ENTROPY OF ATM TRAFFIC STREAMS: A. Dublin Applied Probability Group. Dublin City University, Dublin 9, Ireland. 10 Burlington Road, Dublin 4
 ENTROPY OF ATM TRAFFIC STREAMS: A TOOL FOR ESTIMATING QoS PARAMETERS N.G.Dueld 1;2, J.T.Lewis 2, Neil O'Connell 2, Raymond Russell 2 and Fergal Toomey 2 Dublin Applied Probability Group 1 School of Mathematical
ENTROPY OF ATM TRAFFIC STREAMS: A TOOL FOR ESTIMATING QoS PARAMETERS N.G.Dueld 1;2, J.T.Lewis 2, Neil O'Connell 2, Raymond Russell 2 and Fergal Toomey 2 Dublin Applied Probability Group 1 School of Mathematical
On Queues with Inter-Arrival Times Proportional to Service Times
 On Queues with Inter-Arrival Times Proportional to Service Times Israel Cidon* Department of Electrical Engineering Technion, Haifa 32000, Israel Asad Khamisyt Department of Electrical Engineering Technion,
On Queues with Inter-Arrival Times Proportional to Service Times Israel Cidon* Department of Electrical Engineering Technion, Haifa 32000, Israel Asad Khamisyt Department of Electrical Engineering Technion,
NICTA Short Course. Network Analysis. Vijay Sivaraman. Day 1 Queueing Systems and Markov Chains. Network Analysis, 2008s2 1-1
 NICTA Short Course Network Analysis Vijay Sivaraman Day 1 Queueing Systems and Markov Chains Network Analysis, 2008s2 1-1 Outline Why a short course on mathematical analysis? Limited current course offering
NICTA Short Course Network Analysis Vijay Sivaraman Day 1 Queueing Systems and Markov Chains Network Analysis, 2008s2 1-1 Outline Why a short course on mathematical analysis? Limited current course offering
Delay characteristics in discrete-time GI-G-1 queues with non-preemptive priority queueing discipline
 Delay characteristics in discrete-time GI-G-1 queues with non-preemptive priority queueing discipline Joris Walraevens, Bart Steyaert, Herwig Bruneel SMACS Research Group, University of Ghent, Vakgroep
Delay characteristics in discrete-time GI-G-1 queues with non-preemptive priority queueing discipline Joris Walraevens, Bart Steyaert, Herwig Bruneel SMACS Research Group, University of Ghent, Vakgroep
Stochastic Network Calculus
 Stochastic Network Calculus Assessing the Performance of the Future Internet Markus Fidler joint work with Amr Rizk Institute of Communications Technology Leibniz Universität Hannover April 22, 2010 c
Stochastic Network Calculus Assessing the Performance of the Future Internet Markus Fidler joint work with Amr Rizk Institute of Communications Technology Leibniz Universität Hannover April 22, 2010 c
Bounded Delay for Weighted Round Robin with Burst Crediting
 Bounded Delay for Weighted Round Robin with Burst Crediting Sponsor: Sprint Kert Mezger David W. Petr Technical Report TISL-0230-08 Telecommunications and Information Sciences Laboratory Department of
Bounded Delay for Weighted Round Robin with Burst Crediting Sponsor: Sprint Kert Mezger David W. Petr Technical Report TISL-0230-08 Telecommunications and Information Sciences Laboratory Department of
Intro Refresher Reversibility Open networks Closed networks Multiclass networks Other networks. Queuing Networks. Florence Perronnin
 Queuing Networks Florence Perronnin Polytech Grenoble - UGA March 23, 27 F. Perronnin (UGA) Queuing Networks March 23, 27 / 46 Outline Introduction to Queuing Networks 2 Refresher: M/M/ queue 3 Reversibility
Queuing Networks Florence Perronnin Polytech Grenoble - UGA March 23, 27 F. Perronnin (UGA) Queuing Networks March 23, 27 / 46 Outline Introduction to Queuing Networks 2 Refresher: M/M/ queue 3 Reversibility
Homework 1 - SOLUTION
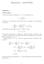 Homework - SOLUTION Problem M/M/ Queue ) Use the fact above to express π k, k > 0, as a function of π 0. π k = ( ) k λ π 0 µ 2) Using λ < µ and the fact that all π k s sum to, compute π 0 (as a function
Homework - SOLUTION Problem M/M/ Queue ) Use the fact above to express π k, k > 0, as a function of π 0. π k = ( ) k λ π 0 µ 2) Using λ < µ and the fact that all π k s sum to, compute π 0 (as a function
THE HEAVY-TRAFFIC BOTTLENECK PHENOMENON IN OPEN QUEUEING NETWORKS. S. Suresh and W. Whitt AT&T Bell Laboratories Murray Hill, New Jersey 07974
 THE HEAVY-TRAFFIC BOTTLENECK PHENOMENON IN OPEN QUEUEING NETWORKS by S. Suresh and W. Whitt AT&T Bell Laboratories Murray Hill, New Jersey 07974 ABSTRACT This note describes a simulation experiment involving
THE HEAVY-TRAFFIC BOTTLENECK PHENOMENON IN OPEN QUEUEING NETWORKS by S. Suresh and W. Whitt AT&T Bell Laboratories Murray Hill, New Jersey 07974 ABSTRACT This note describes a simulation experiment involving
Optimal Rejuvenation for. Tolerating Soft Failures. Andras Pfening, Sachin Garg, Antonio Puliato, Miklos Telek, Kishor S. Trivedi.
 Optimal Rejuvenation for Tolerating Soft Failures Andras Pfening, Sachin Garg, Antonio Puliato, Miklos Telek, Kishor S. Trivedi Abstract In the paper we address the problem of determining the optimal time
Optimal Rejuvenation for Tolerating Soft Failures Andras Pfening, Sachin Garg, Antonio Puliato, Miklos Telek, Kishor S. Trivedi Abstract In the paper we address the problem of determining the optimal time
Dynamic Power Allocation and Routing for Time Varying Wireless Networks
 Dynamic Power Allocation and Routing for Time Varying Wireless Networks X 14 (t) X 12 (t) 1 3 4 k a P ak () t P a tot X 21 (t) 2 N X 2N (t) X N4 (t) µ ab () rate µ ab µ ab (p, S 3 ) µ ab µ ac () µ ab (p,
Dynamic Power Allocation and Routing for Time Varying Wireless Networks X 14 (t) X 12 (t) 1 3 4 k a P ak () t P a tot X 21 (t) 2 N X 2N (t) X N4 (t) µ ab () rate µ ab µ ab (p, S 3 ) µ ab µ ac () µ ab (p,
Effective Bandwidth for Traffic Engineering
 Brigham Young University BYU ScholarsArchive All Faculty Publications 2-5- Effective Bandwidth for Traffic Engineering Mark J. Clement clement@cs.byu.edu Rob Kunz See next page for additional authors Follow
Brigham Young University BYU ScholarsArchive All Faculty Publications 2-5- Effective Bandwidth for Traffic Engineering Mark J. Clement clement@cs.byu.edu Rob Kunz See next page for additional authors Follow
IP Packet Level vbns Trac. fjbgao, vwani,
 IP Packet Level vbns Trac Analysis and Modeling Jianbo Gao a,vwani P. Roychowdhury a, Ronn Ritke b, and Izhak Rubin a a Electrical Engineering Department, University of California, Los Angeles, Los Angeles,
IP Packet Level vbns Trac Analysis and Modeling Jianbo Gao a,vwani P. Roychowdhury a, Ronn Ritke b, and Izhak Rubin a a Electrical Engineering Department, University of California, Los Angeles, Los Angeles,
CDA5530: Performance Models of Computers and Networks. Chapter 4: Elementary Queuing Theory
 CDA5530: Performance Models of Computers and Networks Chapter 4: Elementary Queuing Theory Definition Queuing system: a buffer (waiting room), service facility (one or more servers) a scheduling policy
CDA5530: Performance Models of Computers and Networks Chapter 4: Elementary Queuing Theory Definition Queuing system: a buffer (waiting room), service facility (one or more servers) a scheduling policy
CHAPTER 4. Networks of queues. 1. Open networks Suppose that we have a network of queues as given in Figure 4.1. Arrivals
 CHAPTER 4 Networks of queues. Open networks Suppose that we have a network of queues as given in Figure 4.. Arrivals Figure 4.. An open network can occur from outside of the network to any subset of nodes.
CHAPTER 4 Networks of queues. Open networks Suppose that we have a network of queues as given in Figure 4.. Arrivals Figure 4.. An open network can occur from outside of the network to any subset of nodes.
Stability of the Maximum Size Matching
 Stability of the Maximum Size Matching Mohsen Bayati Dept. of Electrical Engineering Stanford University Stanford, CA 9405-950 bayati@stanford.edu Neda Beheshti Dept. of Electrical Engineering Stanford
Stability of the Maximum Size Matching Mohsen Bayati Dept. of Electrical Engineering Stanford University Stanford, CA 9405-950 bayati@stanford.edu Neda Beheshti Dept. of Electrical Engineering Stanford
Sensitivity Analysis for Discrete-Time Randomized Service Priority Queues
 Sensitivity Analysis for Discrete-Time Randomized Service Priority Queues George Kesidis 1, Takis Konstantopoulos 2, Michael Zazanis 3 1. Elec. & Comp. Eng. Dept, University of Waterloo, Waterloo, ON,
Sensitivity Analysis for Discrete-Time Randomized Service Priority Queues George Kesidis 1, Takis Konstantopoulos 2, Michael Zazanis 3 1. Elec. & Comp. Eng. Dept, University of Waterloo, Waterloo, ON,
Asymptotic Delay Distribution and Burst Size Impact on a Network Node Driven by Self-similar Traffic
 Èíôîðìàöèîííûå ïðîöåññû, Òîì 5, 1, 2005, ñòð. 4046. c 2004 D'Apice, Manzo. INFORMATION THEORY AND INFORMATION PROCESSING Asymptotic Delay Distribution and Burst Size Impact on a Network Node Driven by
Èíôîðìàöèîííûå ïðîöåññû, Òîì 5, 1, 2005, ñòð. 4046. c 2004 D'Apice, Manzo. INFORMATION THEORY AND INFORMATION PROCESSING Asymptotic Delay Distribution and Burst Size Impact on a Network Node Driven by
The Entropy of Cell Streams as a. Trac Descriptor in ATM Networks
 1 The Entropy of Cell Streams as a Trac Descriptor in ATM Networks N. T. Plotkin SRI International 333 Ravenswood Avenue Menlo Park, CA 94025, USA ninatp@erg.sri.com and C. Roche Laboratoire MASI Universite
1 The Entropy of Cell Streams as a Trac Descriptor in ATM Networks N. T. Plotkin SRI International 333 Ravenswood Avenue Menlo Park, CA 94025, USA ninatp@erg.sri.com and C. Roche Laboratoire MASI Universite
Strong Performance Guarantees for Asynchronous Buffered Crossbar Schedulers
 Strong Performance Guarantees for Asynchronous Buffered Crossbar Schedulers Jonathan Turner Washington University jon.turner@wustl.edu January 30, 2008 Abstract Crossbar-based switches are commonly used
Strong Performance Guarantees for Asynchronous Buffered Crossbar Schedulers Jonathan Turner Washington University jon.turner@wustl.edu January 30, 2008 Abstract Crossbar-based switches are commonly used
A Data Communication Reliability and Trustability Study for Cluster Computing
 A Data Communication Reliability and Trustability Study for Cluster Computing Speaker: Eduardo Colmenares Midwestern State University Wichita Falls, TX HPC Introduction Relevant to a variety of sciences,
A Data Communication Reliability and Trustability Study for Cluster Computing Speaker: Eduardo Colmenares Midwestern State University Wichita Falls, TX HPC Introduction Relevant to a variety of sciences,
Burst Scheduling Based on Time-slotting and Fragmentation in WDM Optical Burst Switched Networks
 Burst Scheduling Based on Time-slotting and Fragmentation in WDM Optical Burst Switched Networks G. Mohan, M. Ashish, and K. Akash Department of Electrical and Computer Engineering National University
Burst Scheduling Based on Time-slotting and Fragmentation in WDM Optical Burst Switched Networks G. Mohan, M. Ashish, and K. Akash Department of Electrical and Computer Engineering National University
On the Performance of an Eective Bandwidths Formula. Costas Courcoubetis, George Fouskas. and Richard Weber y. Abstract
 On the Performance of an Eective Bandwidths Formula Costas Courcoubetis, George Fouskas and Richard Weber y Abstract At a buered switch in an ATM (asynchronous transfer mode) network it is important to
On the Performance of an Eective Bandwidths Formula Costas Courcoubetis, George Fouskas and Richard Weber y Abstract At a buered switch in an ATM (asynchronous transfer mode) network it is important to
An Admission Control Mechanism for Providing Service Differentiation in Optical Burst-Switching Networks
 An Admission Control Mechanism for Providing Service Differentiation in Optical Burst-Switching Networks Igor M. Moraes, Daniel de O. Cunha, Marco D. D. Bicudo, Rafael P. Laufer, and Otto Carlos M. B.
An Admission Control Mechanism for Providing Service Differentiation in Optical Burst-Switching Networks Igor M. Moraes, Daniel de O. Cunha, Marco D. D. Bicudo, Rafael P. Laufer, and Otto Carlos M. B.
Networking = Plumbing. Queueing Analysis: I. Last Lecture. Lecture Outline. Jeremiah Deng. 29 July 2013
 Networking = Plumbing TELE302 Lecture 7 Queueing Analysis: I Jeremiah Deng University of Otago 29 July 2013 Jeremiah Deng (University of Otago) TELE302 Lecture 7 29 July 2013 1 / 33 Lecture Outline Jeremiah
Networking = Plumbing TELE302 Lecture 7 Queueing Analysis: I Jeremiah Deng University of Otago 29 July 2013 Jeremiah Deng (University of Otago) TELE302 Lecture 7 29 July 2013 1 / 33 Lecture Outline Jeremiah
A packet switch with a priority. scheduling discipline: performance. analysis
 A packet switch with a priority scheduling discipline: performance analysis Joris Walraevens, Bart Steyaert and Herwig Bruneel SMACS Research Group Ghent University, Department TELIN (TW07) Sint-Pietersnieuwstraat
A packet switch with a priority scheduling discipline: performance analysis Joris Walraevens, Bart Steyaert and Herwig Bruneel SMACS Research Group Ghent University, Department TELIN (TW07) Sint-Pietersnieuwstraat
Stability, Queue Length and Delay of Deterministic and Stochastic Queueing Networks Cheng-Shang Chang IBM Research Division T.J. Watson Research Cente
 Stability, Queue Length and Delay of Deterministic and Stochastic Queueing Networks Cheng-Shang Chang IBM Research Division T.J. Watson Research Center P.O. Box 704 Yorktown Heights, NY 10598 cschang@watson.ibm.com
Stability, Queue Length and Delay of Deterministic and Stochastic Queueing Networks Cheng-Shang Chang IBM Research Division T.J. Watson Research Center P.O. Box 704 Yorktown Heights, NY 10598 cschang@watson.ibm.com
1 Introduction Future high speed digital networks aim to serve integrated trac, such as voice, video, fax, and so forth. To control interaction among
 On Deterministic Trac Regulation and Service Guarantees: A Systematic Approach by Filtering Cheng-Shang Chang Dept. of Electrical Engineering National Tsing Hua University Hsinchu 30043 Taiwan, R.O.C.
On Deterministic Trac Regulation and Service Guarantees: A Systematic Approach by Filtering Cheng-Shang Chang Dept. of Electrical Engineering National Tsing Hua University Hsinchu 30043 Taiwan, R.O.C.
Link Models for Packet Switching
 Link Models for Packet Switching To begin our study of the performance of communications networks, we will study a model of a single link in a message switched network. The important feature of this model
Link Models for Packet Switching To begin our study of the performance of communications networks, we will study a model of a single link in a message switched network. The important feature of this model
COMP9334: Capacity Planning of Computer Systems and Networks
 COMP9334: Capacity Planning of Computer Systems and Networks Week 2: Operational analysis Lecturer: Prof. Sanjay Jha NETWORKS RESEARCH GROUP, CSE, UNSW Operational analysis Operational: Collect performance
COMP9334: Capacity Planning of Computer Systems and Networks Week 2: Operational analysis Lecturer: Prof. Sanjay Jha NETWORKS RESEARCH GROUP, CSE, UNSW Operational analysis Operational: Collect performance
A Packet Switch with a Priority Scheduling Discipline: Performance Analysis
 Telecommunication Systems 8:1, 53 77, 005 005 Springer Science + Business Media, Inc. Manufactured in The Netherlands. A Packet Switch with a Priority Scheduling Discipline: Performance Analysis JORIS
Telecommunication Systems 8:1, 53 77, 005 005 Springer Science + Business Media, Inc. Manufactured in The Netherlands. A Packet Switch with a Priority Scheduling Discipline: Performance Analysis JORIS
Online Companion for. Decentralized Adaptive Flow Control of High Speed Connectionless Data Networks
 Online Companion for Decentralized Adaptive Flow Control of High Speed Connectionless Data Networks Operations Research Vol 47, No 6 November-December 1999 Felisa J Vásquez-Abad Départment d informatique
Online Companion for Decentralized Adaptive Flow Control of High Speed Connectionless Data Networks Operations Research Vol 47, No 6 November-December 1999 Felisa J Vásquez-Abad Départment d informatique
CAC investigation for video and data
 CAC investigation for video and data E.Aarstad a, S.Blaabjerg b, F.Cerdan c, S.Peeters d and K.Spaey d a Telenor Research & Development, P.O. Box 8, N-7 Kjeller, Norway,egil.aarstad@fou.telenor.no b Tele
CAC investigation for video and data E.Aarstad a, S.Blaabjerg b, F.Cerdan c, S.Peeters d and K.Spaey d a Telenor Research & Development, P.O. Box 8, N-7 Kjeller, Norway,egil.aarstad@fou.telenor.no b Tele
`First Come, First Served' can be unstable! Thomas I. Seidman. Department of Mathematics and Statistics. University of Maryland Baltimore County
 revision2: 9/4/'93 `First Come, First Served' can be unstable! Thomas I. Seidman Department of Mathematics and Statistics University of Maryland Baltimore County Baltimore, MD 21228, USA e-mail: hseidman@math.umbc.edui
revision2: 9/4/'93 `First Come, First Served' can be unstable! Thomas I. Seidman Department of Mathematics and Statistics University of Maryland Baltimore County Baltimore, MD 21228, USA e-mail: hseidman@math.umbc.edui
in accordance with a window ow control protocol. Alternatively, the total volume of trac generated may in fact depend on the network feedback, as in a
 Proc. Allerton Conf. on Comm.,Control, and Comp., Monticello, IL. Sep t. 1998. 1 A Framework for Adaptive Service Guarantees Rajeev Agrawal ECE Department University of Wisconsin Madison, WI 53706-1691
Proc. Allerton Conf. on Comm.,Control, and Comp., Monticello, IL. Sep t. 1998. 1 A Framework for Adaptive Service Guarantees Rajeev Agrawal ECE Department University of Wisconsin Madison, WI 53706-1691
Equivalent Models and Analysis for Multi-Stage Tree Networks of Deterministic Service Time Queues
 Proceedings of the 38th Annual Allerton Conference on Communication, Control, and Computing, Oct. 2000. Equivalent Models and Analysis for Multi-Stage ree Networks of Deterministic Service ime Queues Michael
Proceedings of the 38th Annual Allerton Conference on Communication, Control, and Computing, Oct. 2000. Equivalent Models and Analysis for Multi-Stage ree Networks of Deterministic Service ime Queues Michael
Window Flow Control Systems with Random Service
 Window Flow Control Systems with Random Service Alireza Shekaramiz Joint work with Prof. Jörg Liebeherr and Prof. Almut Burchard April 6, 2016 1 / 20 Content 1 Introduction 2 Related work 3 State-of-the-art
Window Flow Control Systems with Random Service Alireza Shekaramiz Joint work with Prof. Jörg Liebeherr and Prof. Almut Burchard April 6, 2016 1 / 20 Content 1 Introduction 2 Related work 3 State-of-the-art
Time-dependent performance analysis of a discrete-time. priority queue
 ime-dependent performance analysis of a discrete-time priority queue Joris Walraevens, Dieter Fiems and Herwig Bruneel SMACS Research Group Department of elecommunications and Information Processing (IR07)
ime-dependent performance analysis of a discrete-time priority queue Joris Walraevens, Dieter Fiems and Herwig Bruneel SMACS Research Group Department of elecommunications and Information Processing (IR07)
The Rate-Based Execution Model
 University of Nebraska - Lincoln DigitalCommons@University of Nebraska - Lincoln CSE Technical reports Computer Science and Engineering, Department of 4-1-1999 The Rate-Based Execution Model Kevin Jeffay
University of Nebraska - Lincoln DigitalCommons@University of Nebraska - Lincoln CSE Technical reports Computer Science and Engineering, Department of 4-1-1999 The Rate-Based Execution Model Kevin Jeffay
Queue Response to Input Correlation Functions: Continuous Spectral Analysis. University of Texas at Austin. Austin, Texas
 Queue Response to Input Correlation Functions: Continuous Spectral Analysis San-i Li Chia-Lin Hwang Department of Electrical and Computer Engineering University of Texas at Austin Austin, Texas 78712 August
Queue Response to Input Correlation Functions: Continuous Spectral Analysis San-i Li Chia-Lin Hwang Department of Electrical and Computer Engineering University of Texas at Austin Austin, Texas 78712 August
Competitive Management of Non-Preemptive Queues with Multiple Values
 Competitive Management of Non-Preemptive Queues with Multiple Values Nir Andelman and Yishay Mansour School of Computer Science, Tel-Aviv University, Tel-Aviv, Israel Abstract. We consider the online problem
Competitive Management of Non-Preemptive Queues with Multiple Values Nir Andelman and Yishay Mansour School of Computer Science, Tel-Aviv University, Tel-Aviv, Israel Abstract. We consider the online problem
Baltzer Journals Received 7 January 1997; revised 16 April 1997 An Interpolation Approximation for the GI/G/1 Queue Based on Multipoint Pade Approxima
 Baltzer Journals Received 7 January 1997; revised 16 April 1997 An Interpolation Approximation for the GI/G/1 Queue Based on Multipoint Pade Approximation Muckai K Girish 1 and Jian-Qiang Hu 1 Telesis
Baltzer Journals Received 7 January 1997; revised 16 April 1997 An Interpolation Approximation for the GI/G/1 Queue Based on Multipoint Pade Approximation Muckai K Girish 1 and Jian-Qiang Hu 1 Telesis
ABSTRACT. We investigate the routing and performance of sparse crossbar packet concentrators
 ABSTRACT Title of Thesis: ON ROUTING AND PERFORMANCE EVALUATION OF BUFFERED SPARSE CROSSBAR CONCENTRA- TORS Degree candidate: Rahul Ratan Degree and year: Master of Science, 2002 Thesis directed by: Professor
ABSTRACT Title of Thesis: ON ROUTING AND PERFORMANCE EVALUATION OF BUFFERED SPARSE CROSSBAR CONCENTRA- TORS Degree candidate: Rahul Ratan Degree and year: Master of Science, 2002 Thesis directed by: Professor
A Direct Approach to Transient Queue-Size Distribution in a Finite-Buffer Queue with AQM
 Appl. Math. Inf. Sci. 7, No. 3, 99-915 (213) 99 Applied Mathematics & Information Sciences An International Journal A Direct Approach to Transient Queue-Size Distribution in a Finite-Buffer Queue with
Appl. Math. Inf. Sci. 7, No. 3, 99-915 (213) 99 Applied Mathematics & Information Sciences An International Journal A Direct Approach to Transient Queue-Size Distribution in a Finite-Buffer Queue with
The purpose of this paper is to demonstrate the exibility of the SPA
 TIPP and the Spectral Expansion Method I. Mitrani 1, A. Ost 2, and M. Rettelbach 2 1 University of Newcastle upon Tyne 2 University of Erlangen-Nurnberg Summary. Stochastic Process Algebras (SPA) like
TIPP and the Spectral Expansion Method I. Mitrani 1, A. Ost 2, and M. Rettelbach 2 1 University of Newcastle upon Tyne 2 University of Erlangen-Nurnberg Summary. Stochastic Process Algebras (SPA) like
A preemptive repeat priority queue with resampling: Performance analysis
 Ann Oper Res (2006) 46:89 202 DOI 0.007/s0479-006-0053-4 A preemptive repeat priority queue with resampling: Performance analysis Joris Walraevens Bart Steyaert Herwig Bruneel Published online: 6 July
Ann Oper Res (2006) 46:89 202 DOI 0.007/s0479-006-0053-4 A preemptive repeat priority queue with resampling: Performance analysis Joris Walraevens Bart Steyaert Herwig Bruneel Published online: 6 July
Lan Performance LAB Ethernet : CSMA/CD TOKEN RING: TOKEN
 Lan Performance LAB Ethernet : CSMA/CD TOKEN RING: TOKEN Ethernet Frame Format 7 b y te s 1 b y te 2 o r 6 b y te s 2 o r 6 b y te s 2 b y te s 4-1 5 0 0 b y te s 4 b y te s P r e a m b le S ta r t F r
Lan Performance LAB Ethernet : CSMA/CD TOKEN RING: TOKEN Ethernet Frame Format 7 b y te s 1 b y te 2 o r 6 b y te s 2 o r 6 b y te s 2 b y te s 4-1 5 0 0 b y te s 4 b y te s P r e a m b le S ta r t F r
I. INTRODUCTION. This work was supported by a Wakerly Stanford Graduate Fellowship and by the Powell Foundation.
 Analysis of scheduling algorithms that provide 100% throughput in input-queued switches Isaac Keslassy, Nick McKeown Computer Systems Laboratory, Stanford University Stanford, CA 94305-9030 {keslassy,
Analysis of scheduling algorithms that provide 100% throughput in input-queued switches Isaac Keslassy, Nick McKeown Computer Systems Laboratory, Stanford University Stanford, CA 94305-9030 {keslassy,
The M/G/1 FIFO queue with several customer classes
 The M/G/1 FIFO queue with several customer classes Boxma, O.J.; Takine, T. Published: 01/01/2003 Document Version Publisher s PDF, also known as Version of Record (includes final page, issue and volume
The M/G/1 FIFO queue with several customer classes Boxma, O.J.; Takine, T. Published: 01/01/2003 Document Version Publisher s PDF, also known as Version of Record (includes final page, issue and volume
Link Models for Circuit Switching
 Link Models for Circuit Switching The basis of traffic engineering for telecommunication networks is the Erlang loss function. It basically allows us to determine the amount of telephone traffic that can
Link Models for Circuit Switching The basis of traffic engineering for telecommunication networks is the Erlang loss function. It basically allows us to determine the amount of telephone traffic that can
ESTIMATION OF THE BURST LENGTH IN OBS NETWORKS
 ESTIMATION OF THE BURST LENGTH IN OBS NETWORKS Pallavi S. Department of CSE, Sathyabama University Chennai, Tamilnadu, India pallavi.das12@gmail.com M. Lakshmi Department of CSE, Sathyabama University
ESTIMATION OF THE BURST LENGTH IN OBS NETWORKS Pallavi S. Department of CSE, Sathyabama University Chennai, Tamilnadu, India pallavi.das12@gmail.com M. Lakshmi Department of CSE, Sathyabama University
ADVANCES in dense wavelength division multiplexing
 JOURNAL OF LIGHTWAVE TECHNOLOGY, VOL. 25, NO. 8, AUGUST 2007 1883 Optimal Burst Scheduling in Optical Burst Switched Networks Yuhua Chen, Member, IEEE, Jonathan S. Turner, Fellow, IEEE, and Pu-Fan Mo Abstract
JOURNAL OF LIGHTWAVE TECHNOLOGY, VOL. 25, NO. 8, AUGUST 2007 1883 Optimal Burst Scheduling in Optical Burst Switched Networks Yuhua Chen, Member, IEEE, Jonathan S. Turner, Fellow, IEEE, and Pu-Fan Mo Abstract
An engineering approximation for the mean waiting time in the M/H 2 b /s queue
 An engineering approximation for the mean waiting time in the M/H b /s queue Francisco Barceló Universidad Politécnica de Catalunya c/ Jordi Girona, -3, Barcelona 08034 Email : barcelo@entel.upc.es Abstract
An engineering approximation for the mean waiting time in the M/H b /s queue Francisco Barceló Universidad Politécnica de Catalunya c/ Jordi Girona, -3, Barcelona 08034 Email : barcelo@entel.upc.es Abstract
Buzen s algorithm. Cyclic network Extension of Jackson networks
 Outline Buzen s algorithm Mean value analysis for Jackson networks Cyclic network Extension of Jackson networks BCMP network 1 Marginal Distributions based on Buzen s algorithm With Buzen s algorithm,
Outline Buzen s algorithm Mean value analysis for Jackson networks Cyclic network Extension of Jackson networks BCMP network 1 Marginal Distributions based on Buzen s algorithm With Buzen s algorithm,
Exercises Stochastic Performance Modelling. Hamilton Institute, Summer 2010
 Exercises Stochastic Performance Modelling Hamilton Institute, Summer Instruction Exercise Let X be a non-negative random variable with E[X ]
Exercises Stochastic Performance Modelling Hamilton Institute, Summer Instruction Exercise Let X be a non-negative random variable with E[X ]
Resource Allocation for Video Streaming in Wireless Environment
 Resource Allocation for Video Streaming in Wireless Environment Shahrokh Valaee and Jean-Charles Gregoire Abstract This paper focuses on the development of a new resource allocation scheme for video streaming
Resource Allocation for Video Streaming in Wireless Environment Shahrokh Valaee and Jean-Charles Gregoire Abstract This paper focuses on the development of a new resource allocation scheme for video streaming
A Starvation-free Algorithm For Achieving 100% Throughput in an Input- Queued Switch
 A Starvation-free Algorithm For Achieving 00% Throughput in an Input- Queued Switch Abstract Adisak ekkittikul ick ckeown Department of Electrical Engineering Stanford University Stanford CA 9405-400 Tel
A Starvation-free Algorithm For Achieving 00% Throughput in an Input- Queued Switch Abstract Adisak ekkittikul ick ckeown Department of Electrical Engineering Stanford University Stanford CA 9405-400 Tel
TCOM 501: Networking Theory & Fundamentals. Lecture 6 February 19, 2003 Prof. Yannis A. Korilis
 TCOM 50: Networking Theory & Fundamentals Lecture 6 February 9, 003 Prof. Yannis A. Korilis 6- Topics Time-Reversal of Markov Chains Reversibility Truncating a Reversible Markov Chain Burke s Theorem Queues
TCOM 50: Networking Theory & Fundamentals Lecture 6 February 9, 003 Prof. Yannis A. Korilis 6- Topics Time-Reversal of Markov Chains Reversibility Truncating a Reversible Markov Chain Burke s Theorem Queues
Introduction to Markov Chains, Queuing Theory, and Network Performance
 Introduction to Markov Chains, Queuing Theory, and Network Performance Marceau Coupechoux Telecom ParisTech, departement Informatique et Réseaux marceau.coupechoux@telecom-paristech.fr IT.2403 Modélisation
Introduction to Markov Chains, Queuing Theory, and Network Performance Marceau Coupechoux Telecom ParisTech, departement Informatique et Réseaux marceau.coupechoux@telecom-paristech.fr IT.2403 Modélisation
e-05
 Empirical Eective Bandwidths M. Falkner, M. Devetsikiotis, I. Lambadaris Department of Systems and Computer Engineering Carleton University 25 Colonel By Drive Ottawa, Ontario KS 5B6, Canada S. Tartarelli,
Empirical Eective Bandwidths M. Falkner, M. Devetsikiotis, I. Lambadaris Department of Systems and Computer Engineering Carleton University 25 Colonel By Drive Ottawa, Ontario KS 5B6, Canada S. Tartarelli,
A Virtual Queue Approach to Loss Estimation
 A Virtual Queue Approach to Loss Estimation Guoqiang Hu, Yuming Jiang, Anne Nevin Centre for Quantifiable Quality of Service in Communication Systems Norwegian University of Science and Technology, Norway
A Virtual Queue Approach to Loss Estimation Guoqiang Hu, Yuming Jiang, Anne Nevin Centre for Quantifiable Quality of Service in Communication Systems Norwegian University of Science and Technology, Norway
Contents 1 Introduction 3 2 Continuous time rate based control Network and Queue Models The Rate Control M
 SP-EPRCA: an ATM Rate Based Congestion Control Scheme based on a Smith Predictor D. Cavendish, S. Mascolo, M. Gerla dirceu@cs.ucla.edu, mascolo@poliba.it, gerla@cs.ucla.edu Abstract This report presents
SP-EPRCA: an ATM Rate Based Congestion Control Scheme based on a Smith Predictor D. Cavendish, S. Mascolo, M. Gerla dirceu@cs.ucla.edu, mascolo@poliba.it, gerla@cs.ucla.edu Abstract This report presents
VARIANCE REDUCTION IN SIMULATIONS OF LOSS MODELS
 VARIANCE REDUCTION IN SIMULATIONS OF LOSS MODELS by Rayadurgam Srikant 1 and Ward Whitt 2 October 20, 1995 Revision: September 26, 1996 1 Coordinated Science Laboratory, University of Illinois, 1308 W.
VARIANCE REDUCTION IN SIMULATIONS OF LOSS MODELS by Rayadurgam Srikant 1 and Ward Whitt 2 October 20, 1995 Revision: September 26, 1996 1 Coordinated Science Laboratory, University of Illinois, 1308 W.
Lecture 11. Advanced Dividers
 Lecture 11 Advanced Dividers Required Reading Behrooz Parhami, Computer Arithmetic: Algorithms and Hardware Design Chapter 15 Variation in Dividers 15.3, Combinational and Array Dividers Chapter 16, Division
Lecture 11 Advanced Dividers Required Reading Behrooz Parhami, Computer Arithmetic: Algorithms and Hardware Design Chapter 15 Variation in Dividers 15.3, Combinational and Array Dividers Chapter 16, Division
SDL Constructions of FIFO, LIFO and Absolute Contractors
 SDL Constructions of FIFO, LIFO and Absolute Contractors Cheng-Shang Chang, Jay Cheng, Duan-Shin Lee Institute of Communications Engineering National Tsing Hua University Hsinchu 3003, Taiwan, R.O.C. Email:
SDL Constructions of FIFO, LIFO and Absolute Contractors Cheng-Shang Chang, Jay Cheng, Duan-Shin Lee Institute of Communications Engineering National Tsing Hua University Hsinchu 3003, Taiwan, R.O.C. Email:
Lecture 10: Semi-Markov Type Processes
 Lecture 1: Semi-Markov Type Processes 1. Semi-Markov processes (SMP) 1.1 Definition of SMP 1.2 Transition probabilities for SMP 1.3 Hitting times and semi-markov renewal equations 2. Processes with semi-markov
Lecture 1: Semi-Markov Type Processes 1. Semi-Markov processes (SMP) 1.1 Definition of SMP 1.2 Transition probabilities for SMP 1.3 Hitting times and semi-markov renewal equations 2. Processes with semi-markov
IEEE TRANSACTIONS ON AUTOMATIC CONTROL, VOL. 43, NO. 3, MARCH
 IEEE TRANSACTIONS ON AUTOMATIC CONTROL, VOL. 43, NO. 3, MARCH 1998 315 Asymptotic Buffer Overflow Probabilities in Multiclass Multiplexers: An Optimal Control Approach Dimitris Bertsimas, Ioannis Ch. Paschalidis,
IEEE TRANSACTIONS ON AUTOMATIC CONTROL, VOL. 43, NO. 3, MARCH 1998 315 Asymptotic Buffer Overflow Probabilities in Multiclass Multiplexers: An Optimal Control Approach Dimitris Bertsimas, Ioannis Ch. Paschalidis,
A tutorial on some new methods for. performance evaluation of queueing networks. P. R. Kumar. Coordinated Science Laboratory. University of Illinois
 A tutorial on some new methods for performance evaluation of queueing networks P. R. Kumar Dept. of Electrical and Computer Engineering, and Coordinated Science Laboratory University of Illinois 1308 West
A tutorial on some new methods for performance evaluation of queueing networks P. R. Kumar Dept. of Electrical and Computer Engineering, and Coordinated Science Laboratory University of Illinois 1308 West
Convexity Properties of Loss and Overflow Functions
 Convexity Properties of Loss and Overflow Functions Krishnan Kumaran?, Michel Mandjes y, and Alexander Stolyar? email: kumaran@lucent.com, michel@cwi.nl, stolyar@lucent.com? Bell Labs/Lucent Technologies,
Convexity Properties of Loss and Overflow Functions Krishnan Kumaran?, Michel Mandjes y, and Alexander Stolyar? email: kumaran@lucent.com, michel@cwi.nl, stolyar@lucent.com? Bell Labs/Lucent Technologies,
Non Markovian Queues (contd.)
 MODULE 7: RENEWAL PROCESSES 29 Lecture 5 Non Markovian Queues (contd) For the case where the service time is constant, V ar(b) = 0, then the P-K formula for M/D/ queue reduces to L s = ρ + ρ 2 2( ρ) where
MODULE 7: RENEWAL PROCESSES 29 Lecture 5 Non Markovian Queues (contd) For the case where the service time is constant, V ar(b) = 0, then the P-K formula for M/D/ queue reduces to L s = ρ + ρ 2 2( ρ) where
Input-queued switches: Scheduling algorithms for a crossbar switch. EE 384X Packet Switch Architectures 1
 Input-queued switches: Scheduling algorithms for a crossbar switch EE 84X Packet Switch Architectures Overview Today s lecture - the input-buffered switch architecture - the head-of-line blocking phenomenon
Input-queued switches: Scheduling algorithms for a crossbar switch EE 84X Packet Switch Architectures Overview Today s lecture - the input-buffered switch architecture - the head-of-line blocking phenomenon
Technion - Computer Science Department - Technical Report CS On Centralized Smooth Scheduling
 On Centralized Smooth Scheduling Ami Litman January 25, 2005 Abstract Shiri Moran-Schein This paper studies evenly distributed sets of natural numbers and their applications to scheduling in a centralized
On Centralized Smooth Scheduling Ami Litman January 25, 2005 Abstract Shiri Moran-Schein This paper studies evenly distributed sets of natural numbers and their applications to scheduling in a centralized
