Estimation and Computation with Matrices Over Finite Fields. Brian Philip Corr
|
|
|
- Jody Hensley
- 5 years ago
- Views:
Transcription
1 Estimation and Computation with Matrices Over Finite Fields Brian Philip Corr This thesis is presented for the degree of Doctor of Philosophy of The University of Western Australia Department of Mathematics. January, 2014
2 ii
3 iii Abstract The Matrix Group Recognition Project is a worldwide effort to produce efficient algorithms for working with arbitrary matrix groups over finite fields. Such groups are potentially very large in comparison to the input length, and dealing with them using deterministic methods is impractical. When a generating set for a group is input into a computer, a constructive recognition algorithm names the group, and finds an efficient mapping between the input generators and a set of standard generators, which allow various important questions to be answered quickly. Constructive recognition is a major, natural goal in computational group theory. To recognise an arbitrary group, there are two tasks to perform: the first is to decompose the group into smaller components if possible, and work recursively. The second is to deal with irreducible cases, which in this case are the Finite Simple Groups. This thesis addresses constructive recognition of matrix groups from both ends : on the one hand, we give an improved analysis of the Norton irreducibility test, part of the MEAT-AXE algorithm, by providing a lower bound of the form a 1 a 2 q bc for the proportion of Primary Cyclic matrices in Mc, q b, where a 1, a 2 are constants depending only on q, b. To achieve this, we generalise the Kung-Stong Cycle Index to compute a generating function for the proportion. At the other end, we solve a particular family of base cases for the constructive recognition recursion, by extending the work of Magaard, O Brien and Seress to provide a Las Vegas algorithm for constructive recognition of Classical Groups in irreducible representations of moderate degree. When the degree of the representation is large, existing black-box methods are effective, and when the degree is equal to the natural degree there are specific methods to address the problem. The algorithms presented in this thesis address the middle ground: working algorithms dealing with the case d < n d 2, where d is the natural degree, are presented, analysed and implemented in GAP. We present a Las Vegas algorithm to rewrite elements of a classical group over F q, represented as an irreducible subgroup of GLn, q with exceptions in some small cases, as elements of GLd, q, as follows: i The procedure Initialise, which must be run once to set up a data structure, is a Las Vegas algorithm with complexity O ξ H d 2 log 2 q log ɛ 1 + ρ q d 9 log d log log d log q + d 8 log d log log d log 3 q log ɛ 1, where ξ H is the cost of choosing a random element of H, and ρ q is the cost of a field operation in F q, and ɛ is the acceptable probability of failure. ii The procedure FindImage, which computes the image of g in a representation of natural degree d, is a Las Vegas algorithm with complexity O ξ H + ρ q d 8 log d log log d log q log ɛ 1.
4 iv Since n = Od 2, these algorithms efficiency in terms of the input length N = n 2 log q are of the order ON 9/2, ON 4 respectively. To analyse these algorithms we use the Quokka theory of Niemeyer and Praeger, which we also extend to deal with sets of matrices which may be singular, and apply this new theory to a second count of Primary Cyclic Matrices.
5 v Contents Abstract Acknowledgements iii vii 1 Background and Results The Basic Questions in Computational Group Theory Approaches to Matrix Group Algorithms Randomised Algorithms Black Box Algorithms Aschbacher s Theorem and the Geometric Approach The MEAT-AXE Algorithms and Their Analysis The Parker MEAT-AXE and Holt-Rees MEAT-AXE Glasby & Praeger s Analysis of Primary Cyclic Matrices Irreducible Subalgebras of Mn, q Decompositions Based On Aschbacher s Theorem All Roads Lead to Almost Simple Groups Constructive Recognition of Almost Simple Groups Nonconstructive Recognition Naming G The Cyclic Groups of Prime Order The Alternating Groups The Sporadic Groups The Exceptional Groups of Lie Type Classical Groups of Lie Type Black Box Methods Representations in Cross-Characteristic The Natural Representation The Moderate Degree Representations Finding Random Elements Counting With Quokka Theory The Quokka Theory of Niemeyer & Praeger Results Summary of Major Results Navigation Preliminary Results Modules and Representations Tensor Products Extension Fields Characteristic and Minimal Polynomials, Eigenvalues and Eigenvectors The Symmetric and Alternating Squares Related Bases and Their Effect on Matrices Computation and Complexity Randomised Algorithms
6 vi Complexity and Big-Oh Notation Complexity and Random Elements Factoring Polynomials Estimation for Quokka Theory Permutation Groups Counting In Abelian Groups Arithmetic The MEAT-AXE and Primary Cyclic Matrices Minimal and Characteristic Polynomials of X bc,q, X c,q b A Generalised Cycle Index for Matrix Algebras Counting Finding the Generating Function PCBII, u, q b Results Asymptotics as c Asymptotics as q b The Method of Wall The Setup and Strategy for Recognition of Classical Groups The Modules Irreducible submodules of S 2 V and 2 V The Linear Case A r and Unitary Case 2 A r The Symplectic Case C r The Orthogonal Cases B r, D r, 2 D r q odd The Orthogonal Cases q even Summary Constructive Recognition of F G-modules The Groups The Procedure Initialise The Procedure FindPreimage Special Elements and their Eigenstructure Special Elements and their Eigenstructure on V K Singer Cycles and ppd-elements in GLd, q The Eigenstructure of Singer Cycles and ppd-elements in V K Special Elements in Classical Groups The Eigenstructure of Special Elements on V V K Coincident Eigenvalues l ij The Action of a Special Element on the Symmetric Square S 2 V K The Action of a Special Element on the Alternating Square 2 V K Using Special Elements Quokka Theory and Nilpotent-Independent Sets of Matrices Quokka Sets in Matrix Groups F -Stable Maximal Tori and the Weyl Group W The Case A r The General Linear Groups The Case 2 A r The Unitary Groups
7 vii The Case B r The Odd-Dimensional Orthogonal Groups The Case C r The Symplectic Groups The Case D r The Orthogonal Groups of Positive Type The Case 2 D r The Orthogonal Groups of Negative Type Nilpotent-Independent Sets and Counting in Matrix Algebras Some General Lower Bounds for N An Application of NI-Theory to Primary Cyclic Matrices and the MEAT-AXE The Common Steps of Initialise and FindPreimage Finding the Special Element Testing ppd-ness Avoiding Division By Zero The Symmetric Square Case The Alternating Square Case The Change of Basis Matrix B The Symmetric Square Case Labelling the Eigenvalues l ij The Case d = d The Case d = d The Case d = d Finding the Constants c ij Relations Between the Values κ ij,kl, c ij, a ij The Procedure FindPreImage The Alternating Square Case Labelling the Eigenvalues l ij The Case d = d The Case d = d The Case d = d Finding the Constants c ij The Procedure FindPreImage The Top-Left Corner of a ij Tying Up Loose Ends d < d Implementation, Results and Further Work Example Runtimes for Initialise and FindPreimage Evidence for Conjectures & Accessing The Code Further Research Bibliography 173
8 viii
9 ix Acknowledgements It is only with the support of a vast array of people that I have been able to complete this thesis: there are far too many people whose support has been of critical importance than I can possibly fit in this short space, and so this list is far from exhaustive. First and foremost, to my coordinating supervisor and long-time mentor, Cheryl Praeger: I began this project with an entirely different perspective on life and on mathematics than the perspective I hold today. Your influence on me has been deep, and will be lasting. To my co-supervisor, the late Ákos Seress: your influence on my mathematics and life was entirely different to Cheryl s, but no less significant. It brings me great sadness that you are not here to read this thesis. Your attitude to mathematics and to life made a great impression on me in the relatively short time we worked together. To Eamonn O Brien, for your hospitality and help in the implementation of the recognition algorithms in Magma. To Shreya, Phil, Neil, Michael, Joanne, James, Benny, Steve, Dmitri, Chris, Dave, Sylvia, Dave, Dan, Mark, Chris, Ryan, and all of those I have missed: thank you for your moral, mathematical and even physical support over the years. You have made life excellent to live. To Alice Niemeyer, John Bamberg, Cai Heng Li, Gordon Royle, Alice Devillers and Michael Giudici: your guidance and mentoring has been invaluable, and is why UWA and the CMSC is such a wonderful community. To Rebecca Loo: you have been too nice to me throughout. To the University of Western Australia, the Faculty of Engineering, Computing & Mathematics, and the School of Mathematics & Statistics: the opportunity to work and study here for so long is a privilege that I do not intend to waste. Finally, to my family: my parents, brothers and beyond, your contribution to this work is impossible to measure. Thank you for all of your support through my entire life.
10 x
11 CHAPTER 1 1 Background and Results 1.1 The Basic Questions in Computational Group Theory The fundamental problem of Computational Group Theory CGT is simply stated: given a group G, by either a presentation, or a generating set of permutations or matrices, quickly and accurately determine qualitative and quantitative information about G. For example, find the order of G after deciding if G is finite or infinite, determine whether G is soluble, or construct a composition series for G. In particular, we frequently wish to solve, given an unknown group represented in a computer, the recognition problem: Question Suppose we are given a set X GLn, q generating a group G. Is G a simple group? If so, what is the isomorphism type of G? This is the so-called nonconstructive version of the recognition problem, and in some sense it includes many common questions about G for example, knowing the name of G usually requires or reveals its order. This question also forms a vital part of the more general question of computing a composition series for an arbitrary group. It is not unreasonable, however, to want further information: knowing the isomorphism type of G is not as useful as knowing an explicit isomorphism between G and some standard copy of the group. This need gives rise to the constructive recognition problem: Definition Given a set X GLn, q of matrices generating a simple group G, the recognition problem asks for the name i.e. the isomorphism type of G =. The constructive recognition problem asks, in addition, for an explicit isomorphism ϕ : C G, where C is a standard copy of G, in the sense that we provide a new generating set Y for G, and for each x X, a straight line program in Y reaching x see Definition below. Moreover, we require that, given h G, we can quickly and efficiently compute ϕ 1 h: that is, we can compute a straight line program in X reaching ϕ 1 h C. Note that we often treat nonconstructive recognition and constructive recognition as separate problems, and so when tackling the question of producing an isomorphism ϕ, for practical purposes we may assume knowledge of the isomorphism type of G. The goal of computational group theory is to answer questions such as these with procedures whose runtimes are close to optimal in the length of the algorithm s input see Section 2.2. The input length varies according to the way in which G is represented within the computer. In the case of matrix groups, G is given by a generating set X GLn, q, so the input length is N = X n 2 log q. In constructive recognition, we use the concept of a Straight Line Program to describe a procedure for efficiently writing words in the generators X. Definition Let X GLn, q. Then a straight line program SLP in X reaching g GLn, q of length r is a sequence of expressions w 1,..., w r such that, for each i, one of the following holds:
12 2 Chapter 1. Background and Results i w i is a symbol representing one of the generators in X; ii w i = w j, 1 for some j < i; or iii w i = w j, w k for some j, k < i; and such that w r, when evaluated, is equal to g. By evaluate we mean the following: in case i, we evaluate w i as the generator represented; in case ii we evaluate w i as the inverse of the evaluated value of w j, and in case iii we evaluate w i as the product of the evaluated values of w j, w k. A straight-line program formalises the idea of writing g as a word in the generators X, but with each operation, we retain the result in memory in case it is efficient to use it later: for example, one can produce the 10th power of a matrix g by computing g 10 = g g 2, and so reach the result a word of length 10 in just 4 steps. This speedup comes at the cost of using more memory: however we do not store the evaluation of each expression in memory any longer than we have to the SLP itself is stored merely as a sequence of steps, and evaluated when needed. In this thesis we do not explicitly use SLPs: by necessity, we deal with more concrete representations of group elements. However, the procedures we provide form part of a larger framework for constructive recognition, whose efficiency depends upon the concept. The benefits of constructive recognition are far-reaching: knowing the name of a group, of course, often allows us to apply existing theory to answer fundamental questions such as solubility and order for free. Solving the constructive recognition problem permits us to take a recursive approach to the problem: by breaking a group down into subgroups and quotients we reduce the recognition problems to several smaller cases. Constructive recognition is the process by which we manage this decomposition: in this sense, constructive recognition can be brought to bear on any computational problem which will benefit from a recursive approach. In this thesis we deal with algorithms for matrix groups over finite fields, including a subclass of the constructive recognition problem, namely for certain important representations of classical groups. We also address and analyse a specific implementation of the MEAT-AXE procedure, which provides an important first step in the process of recognising a matrix group: we analyse Glasby & Praeger s [33] primary cyclic MEAT-AXE in the case of an irreducible but not absolutely irreducible matrix algebra using two new general methods for estimation. 1.2 Approaches to Matrix Group Algorithms One of the major problems in computational group theory is the potential for the group G = X to be exponentially large in comparison with the input the full general linear group GLn, q has size q n 1q n q q n q n 1, roughly q n2, which is exponential in the input size X n 2 log q. The same problem arises in the field of permutation groups. There the Schreier-Sims method see for example [81] of finding a base for G and computing a stabiliser chain provides a tool for computing with groups which is highly efficient except for the giants the full alternating and symmetric groups, where a base is too large, and special procedures are needed to achieve efficiency. In the matrix group setting, we require a similar method for decomposing G into
13 1.2. Approaches to Matrix Group Algorithms 3 its fundamental pieces analogous to the giants, and special procedures for dealing with these base cases. In the matrix groups setting, the base cases are the Almost Simple Groups Randomised Algorithms Due to the inefficiency of deterministic algorithms for matrix groups, we rely on algorithms which may make random selections from the input group, and whose determinism is thus compromised. Such algorithms are either not guaranteed to return a correct result Monte Carlo algorithms, or are guaranteed to be correct when they assert results, but may fail to do so Las Vegas algorithms. The runtime and correctness of a randomised algorithm are related: by allowing a Monte Carlo algorithm to run longer, we may be more confident in the correctness of its answer. Likewise allowing a Las Vegas algorithm to run longer will increase its chances of returning an answer other than FAIL. For this reason, these algorithms take an extra input ɛ, a positive real number less than 1, which represents a user-specified upper bound on the probability of an incorrect answer in the Monte Carlo setting, or a bound on the probability of failure in the Las Vegas setting. Suppose that G = X is known to lie within some fixed ambient group A for example, a matrix group always lies within GLn, q. Then for some other subgroup H of A, we may wish to test whether G contains H. A typical one-sided Monte Carlo algorithm for such a test has the following structure: i Identify a type of element or a set of elements which occurs only in H or groups containing H; ii Search G = X for elements of that type. iii If the search is successful, return TRUE asserting that H G; if not, return FALSE asserting that H G. For example, the first recognition algorithm for matrix groups and genesis of the Matrix Group Recognition Project was the Neumann-Praeger SLd, q-recognition algorithm [70]. The algorithm is a one-sided monte carlo algorithm for answering the following question: Question Given X GLn, q, does G := X contain SLn, q as a subgroup? The algorithm uses random search to seek a pair of elements of the group: an element whose order is divisible by a primitive prime divisor see Section of q d 1, and another whose order is divisible by a primitive prime divisor of q d 1 1. Neumann & Praeger proved in [70] that only overgroups of SLd, q contain such a pair of elements with mild additional properties, and so if they are found, we have incontrovertible evidence that SLn, q G, and so an answer of TRUE is guaranteed to be correct. If SLn, q G, then no such pair will be found, and the answer of FALSE is correct, but in the case that SLn, q G and no pair is found, the reported result of FALSE is incorrect. Thus any answer of FALSE is a potential false negative, and to analyse the probability of the algorithm failing in this way, we must analyse the group SLn, q, as well as our search procedure, to determine the probability that a search in some G containing SLn, q would fail to produce an appropriate pair of elements.
14 4 Chapter 1. Background and Results Thus a crucial component of any randomised algorithm is a lower bound on the proportion of the kind of element sought in the search by determining the probability ɛ T of failure to produce the required elements after checking T random elements, we may tailor our algorithm namely the parameter T to ensure that the probability of a false negative in this case, or returning FAIL in the Las Vegas setting is below the user-specified bound ɛ see Section for more detail. Randomised algorithms have been used successfully in the field of computational matrix group theory, leading to algorithms of impressive and unexpected power Black Box Algorithms The first of the two common approaches to dealing with matrix groups essentially eschews the matrix structure altogether, and opts for a much more general approach. In a Black Box setting introduced by Babai & Szemerédi in [8], group elements are encoded, not necessarily uniquely, as strings of bounded length over some alphabet in practice, usually in binary, for obvious reasons, and we are equipped with a Black Box, which can perform the following operations: i Given a string representing g G, return a string representing g 1 ; ii Given strings representing g, h G, return a string representing gh; iii Given a string representing g G, decide whether g = 1. Note that our ability to recognise elements here is limited: we may test whether g = h for any strings representing h and g G, but we cannot in general check whether an arbitrary string lies in G without further effort. In the Black Box setting, only the group structure matters, and not the geometry of the underlying vector space the advantage of this is that a Black Box algorithm then applies to many groups concretely realised in a computer, whether represented as matrices, permutations or in another way in particular, the Black Box approach is often applied when dealing with a quotient group G/N: in this case operation iii is a membership test for N. The cost, or complexity, of a Black Box algorithm is measured as the number of Black Box operations i-iii used. Much attention is paid to computing a particular chain of subgroups of G, namely 1 O G Soc G PkerG G see for example [52], [6], which essentially breaks the problem into a series of smaller Black Box groups and some permutation groups. The Black Box approach has yielded a great deal of progress in constructive recognition, some of which will be mentioned below Aschbacher s Theorem and the Geometric Approach The Black Box approach to matrix group recognition may seem, at first glance, wasteful. This view is not without merit while Black Box algorithms are completely general and hence may be applied to varied situations, the cost of this versatility is the disposal of information. The opposite approach is to exploit in every way possible the geometry of the group s action on a vector space. In this thesis we rely heavily on the eigenstructure of elements of our group, and so our algorithms are decidedly non-black Box. The key to exploiting this geometry is Aschbacher s Theorem [4], which states that a maximal subgroup of GLn, q must fall into at least one of several categories the so-called Aschbacher
15 1.3. The MEAT-AXE Algorithms and Their Analysis 5 classes: the group either stabilises some geometric structure on the underlying vector space V, or is an almost simple group modulo scalars. For example, the Aschbacher class C 1 consists of groups which stabilise a proper nontrivial subspace U of V the reducible groups. Identifying such a subspace using, for example, the MEAT-AXE see Section 1.3 below or Chapter 3 for more details yields two linear groups, one acting on U and another on the quotient space V/U, together with a radical fixing both U and V/U pointwise. 1.3 The MEAT-AXE Algorithms and Their Analysis The first natural step in recognition of an arbitrary matrix group G GLV in a computational context is to ask whether or not G stabilises a proper nontrivial subspace U of V : if so, we can break V and G into pieces and deal with the pieces separately. Then given an arbitrary group, our first action is to run a MEAT-AXE procedure, so named for its ability to cut the space in this way. There is more than one MEAT-AXE procedure, but all work on essentially the same principle: search in the group for elements whose characteristic and minimal polynomials have some special feature, and if they are found, use them to either produce an invariant subspace or proof that the group acts irreducibly The Parker MEAT-AXE and Holt-Rees MEAT-AXE The very first MEAT-AXE was described by Richard Parker in [78], limited to groups over small fields, and was generalised and extended by Derek Holt and Sarah Rees in [45]. The principle behind the Parker MEAT-AXE is to search randomly for an element in G = X with a small nontrivial nullspace, and attempt to use it to find a proper nontrivial G-invariant subspace of V, or a proof that no such subspace exists. The Holt-Rees procedure refines this process: by applying a certain irreducible factor of the characteristic polynomial to a matrix, we can produce elements whose nullspace is low-dimensional, thus reducing the likely search time. In [45], the procedure is analysed using a lower bound for the proportion of those elements whose characteristic polynomial has a linear factor of multiplicity 1 see [45, p.8]: in our analysis of Primary Cyclic matrices in Chapter 3 we provide an analogous estimate in irreducible subalgebras by considering elements not with a linear factor, but with an irreducible factor of minimal possible degree Glasby & Praeger s Analysis of Primary Cyclic Matrices In [34], Glasby introduced the f-cyclic matrices : those X Mn, q whose characteristic polynomial c X t has an irreducible divisor with multiplicity in c X t equal to its multiplicity in the minimal polynomial m X t. Such matrices, which we call Primary Cyclic matrices after the fact that their action on a primary component is cyclic are the matrices used in the Norton Irreducibility test a key part of the Holt-Rees MEAT-AXE in [45]. In [33], Glasby & Praeger show that primary cyclic matrices are abundant in Mn, q: their proportion lies inside the interval 1 c 1 q n, 1 c 2 q n, for constants c 1, c 2. Note that the MEAT-AXE procedures are generally defined in terms of subalgebras of Mn, q, and not subgroups of GLn, q. In general, the group generated by X and the algebra generated by X are dealt with interchangeably, and algorithms are described in their preferred setting.
16 6 Chapter 1. Background and Results Irreducible Subalgebras of Mn, q In Chapter 3 and later in Section 6.3 we address the problem of determining the size of the set of primary cyclic matrices in an irreducible, but not absolutely irreducible, subalgebra of Mn, q. Such subalgebras are all equivalent to the algebra Mc, q b, for bc = n, and so we may treat their elements as c c matrices over F q b see Section for details. In [71], Neumann & Praeger estimate the proportion of cyclic matrices in such irreducible matrix algebras. In Chapter 3, we determine a necessary and sufficient condition for a matrix X Mc, q b to be primary cyclic as an element of Mn, q, and generalise the Cycle Index Theorem of Kung [56] and Stong [84] to find lower bounds for the proportion of a subfamily of these elements a family analagous to one analysed by Holt & Rees in [45]. In Chapter 6 we use Quokka theory described in [76] and the new theory of Nilpotent-Independent sets to enumerate a different subfamily see Section 1.8 below. While our results on Primary Cyclic matrices do not have great practical significance they do not provide any real improvement over existing bounds, in both cases we apply new general techniques to obtain usable results. 1.4 Decompositions Based On Aschbacher s Theorem The Geometric Approach to matrix group algorithms hinges upon answering the question to which Aschbacher classes does the group G belong? which gives rise to a reduction of some sort, except in the almost simple case. Thus we deconstruct a group into its almost simple parts by testing for membership of each of the Aschbacher classes. The MEAT-AXE procedure see Section 1.3 above decides if G is reducible, and the SMASH algorithm [43] and primitivity algorithm [44] of Holt et al. deal with several cases involving a normal subgroup of G. Leedham-Green & O Brien use geometric methods [60] to produce an algorithm which detects whether G preserves a tensor product decomposition in [59], and in [35], with Glasby they describe an algorithm for deciding whether G is definable over a subfield modulo scalars. Niemeyer [73] and Brooksbank, Niemeyer & Seress [14] deal with the case of G having an extraspecial normal subgroup, and Leedham-Green & O Brien [61] detect when G is tensorinduced. This leaves only two cases: either G normalises a Classical group in its natural representation, or G is almost simple modulo scalars All Roads Lead to Almost Simple Groups The geometric and Black Box approaches may seem at odds, but they are, in fact, complementary. In both approaches, the goal is essentially the same identify a normal subgroup N of G, and split the problem into smaller problems, those of dealing with the pieces, that is, the normal subgroup N and quotient G/N, separately while keeping track of how the pieces fit together. The normal subgroup N is again a matrix group, and the quotient G/N may be treated as a matrix, permutation or finitely presented group, as appropriate to the situation. Repetition of this process yields a tree-like data structure, with each node either splitting into children, or being almost simple modulo scalars. The process of splitting a group into its children while retaining the necessary data for reconstructing the original group is summarised in [58],[72], and is implemented in both GAP and MAGMA, the two leading computer algebra systems in Computational Group Theory. The main results of this thesis form part of the solution to the problem of constructively recognising the almost simple groups the leaves of the
17 1.5. Constructive Recognition of Almost Simple Groups 7 composition tree. This composition tree method is analogous to the Schreier-Sims method for computing with permutation groups. In that case, a permutation group is decomposed into smaller pieces recursively, until we are left with a group with a base too large in comparison to its permutation degree for the method to work effectively, at which point specialised algorithms are used for dealing with large base groups see [81, Chapter 10]. In the case of matrix groups, we attempt to find a normal subgroup which permits a decomposition into groups of smaller rank, and stop when no such subgroup can be found and again, specialised algorithms are needed to deal with the base cases. In the case of matrix groups, the base cases are Almost Simple groups. 1.5 Constructive Recognition of Almost Simple Groups If we assume that we may, using the tree structure described above, reduce the recognition problem to the case of Almost Simple Groups that is, groups G such that T G Aut T for some simple group T, we turn to the famous Classification of Finite Simple Groups, and treat each case separately. Many cases of constructive recognition have been completed, and some are easier than others. Theorem Let T be a finite simple group. Then T belongs to one of the following families: i The Cyclic Groups Z p of prime order p; ii The Alternating Groups A n, for n 5; iii The Classical Groups A r q, 2 A r q, B r q, C r q, D r q and 2 D r q, for r Z +, q a prime power; iv The Exceptional Groups of Lie Type; and v The 26 Sporadic Simple Groups. The Classification of Finite Simple Groups needs no introduction, and is impossible to adequately reference: see for example [36] for more detail. Groups from each family of finite simple groups may arise as the leaves of the composition tree: thus in each case, we seek recognition and constructive recognition. For the most part, the problem of constructive recognition is performed after a nonconstructive recognition algorithm has safely confirmed the isomorphism type of the group Nonconstructive Recognition Naming G The Neumann-Praeger approach of [70] can be generalised and applied to more groups than simply SLd, q: Celler & Leedham- Green [23] and Niemeyer & Praeger [75] describe procedures to recognise Classical groups in their natural representation, and in [7], Babai et al. nonconstructively recognise any simple Black Box group of Lie Type using similar ppd-element ideas, given only the characteristic p of the group representation which can be determined quickly in the same setting by algorithms of Liebeck & O Brien [64] and Seress [53]. The combined result of these algorithms is that we may, generally speaking, assume that when attempting to constructively recognise G, we know its name.
18 8 Chapter 1. Background and Results The Cyclic Groups of Prime Order Constructive recognition of Cyclic groups is well-studied, though it is not easy. The problem is precisely the Discrete Logarithm Problem, of finding, given a and b, the solution x to the equation a x b mod p. The discrete logarithm problem arises in many computational contexts: it is a hard problem, and often we simply ignore it in the sense that we assume we are given an oracle which solves it in a fixed time, and we try to minimise the number of calls to the oracle in the same way that a Black Box group algorithm ignores the question of precisely how the group is represented, and in the same way that we treat field operations and random selections as fundamental units : see Section 2.2. Then in practice we use whichever discrete logarithm algorithm is most suitable as our oracle: the most efficient algorithms run in sub-exponential time that is, they are not polynomial, but they are significantly faster than exponential: see for example [65],[83]. A great many algorithms for matrix groups depend upon these discrete log oracles The Alternating Groups In [9], Babai and Beals answered the question of constructive recognition of almost simple groups with alternating groups as their Socle providing, in the Black Box setting, a polynomial time Las Vegas algorithm giving an explicit isomorphism from the given group to the standard permutation representation of A d or S d. Bratus and Pak [13] gave a faster procedure, albeit one depending on an order oracle for G and assuming the Goldbach Conjecture. Finally in [10], Beals et al. present a polynomial time Las Vegas procedure for constructive recognition. However, this procedure is polynomial as a Black Box procedure, and so its complexity is dependent on how efficiently Black Box operations may be performed in comparison to the input length, which is dependent on the degree n of the representation of the group G {A d, S d } either as matrices or as permutations. It works efficiently when the dimension of the matrix representation is at least d 2. For the smallest dimensional representation on the deleted permutation module of dimension d 1 or d 2 a more efficient constructive recognition algorithm is given in [11] The Sporadic Groups In [1], Ambrose et al. constructively recognise several sporadics using generalised sifting : a generalisation of the Schreier-Sims method in a Black Box setting. In [88], Wilson introduced the notion of standard generators for sporadic groups the ATLAS website [87] provides a great deal of information about the sporadic groups, often in terms of these standard generators. Using known subgroup chains written in terms of these standard generators, modified versions of the Schreier-Sims method can be used to constructively recognise all Sporadic groups see [89],[69],[42] The Exceptional Groups of Lie Type The Exceptional Groups, by their very nature, require specialised algorithms for recognition. In [51], Kantor & Magaard, in a Black Box setting, constructively recognise the Exceptional Groups of Lie Type, with the exception of the Tits group 2 F 4 q and groups of rank 1.
19 1.6. Classical Groups of Lie Type Classical Groups of Lie Type In contrast to the Exceptional and Sporadic groups, the Classical Groups arise for infinitely many values of the rank r and field size q there are infinitely many Exceptional groups, but their rank is bounded. For this reason, they must be treated with a more general approach than the Exceptional Groups and especially the Sporadics. Moreover, the existence of Classical Groups for arbitrarily large rank and field size means that any recognition algorithms have complexity depending on the parameters r and q see Section This creates an interesting interplay, in a Black Box context, between the way in which the group is input into the computer and the complexity of the algorithm: if a Classical group Classd, q is represented as a subgroup of GLn, q, with n d k then the input length of the Black Box algorithm is N = On 2 log q = Od 2k log q. Then any algorithm whose runtime is dependent on d, will be faster relative to N for larger values of k. Thus for very efficient representations of a group G i.e. representations of small degree over a not-too-large field, Black Box algorithms are less effective. This mirrors the Alternating case above, where the algorithm in [10] is effective for representations of A d, S d of large degree, and a specialised algorithm [11] is used to deal with the small-degree case. We describe this in more detail below Black Box Methods The breakthrough Black Box algorithm for Classical groups came in [25], when Cooperman, Finkelstein & Linton presented a constructive recognition algorithm for a Black Box GLn, 2. This algorithm inspired Black Box recognition algorithms for all Classical groups see [52]: however, these algorithms are not polynomial. Brooksbank & Kantor in [18] present a Black Box procedure for constructive recognition of PSLd, q, and Brooksbank s procedures do the same for the Unitary [16], Orthogonal [19] with Kantor, and Symplectic [17] cases: these are polynomial-time algorithms subject to the existence of an oracle dealing with PSL2, q. These algorithms essentially isolate the obstruction to a polynomial-time algorithm to the oracle. In [24] Conder, Leedham-Green & O Brien produce such an oracle by constructively recognising PSL2, q we note that this algorithm is not a Black Box algorithm, but a matrix group algorithm, and in natural characteristic depends upon a discrete log oracle. Much of the analysis of these algorithms is done in terms of d and q: for example, the Kantor- Brooksbank PSL-recognition algorithm is polynomial in d, log q, ξ G, χ : after initialising, it recognises elements in time O log dξ G + χd + log q + µd log 2 q + d 5 log q, where ξ G is the cost of generating a random element in G, χ is the cost of a call to the PSL2, q oracle, and µ is the cost of a group operation. These are the only parts of the algorithm that depend on the input length N which is dependent on the representation of the group in the computer. When n is large relative to d, this procedure is faster in terms of its input length: we can see that if d is small relative to n, there are relatively few calls to the SL2, q-oracle, and the term µ, which in a matrix group setting is On 3 ρ q, dominates as d fades into the background.
20 10 Chapter 1. Background and Results Representations in Cross-Characteristic Recall that using the algorithms in [64] and [53], we may assume knowledge of the natural characteristic of the input group G. In the case that the natural characteristic is different from the input characteristic the so-called cross-characteristic case, Landazuri & Seitz [57] and later Seitz & Zalesskii [80] provide lower bounds on the degree of any faithful representation of a classical group, showing that the degree of a cross-characteristic representation is large : it is polynomial in the size of the defining characteristic rather than its logarithm. Thus the input size in this case is sufficiently large in terms of the natural parameters d, q that Black Box algorithms are polynomial The Natural Representation The smallest n of all is the natural representation, when n = d. Of course, knowing that G is represented in the degree equal to its natural degree is a great deal more information than we have in a Black Box context, and so recognition algorithms can use this geometrical information to their advantage. Celler & Leedham-Green in [21] constructively recognise SLd, q in its natural representation with an algorithm requiring Od 4 q field operations note that this is not polynomial in the input length for a matrix group, which usually involves log q, and Brooksbank in [15] constructively recognises the other classical groups in their natural representation in polynomial time assuming the existence of a discrete log oracle. Practically speaking, these algorithms are the most important due to the frequency with which they arise in the general composition tree setting The Moderate Degree Representations Between the natural representations the small n and those representations of degree so large that Black Box methods are very effective the large n, lie the moderate degree representations. The natural degree is rich with linear algebra to exploit, and while the structure in moderate degree is not as natural, there is a lot of information that a Black Box algorithm leaves on the table. In [67], Magaard, O Brien & Seress provide a reduction algorithm for SLn, q, where d < n < d 2. This procedure exploits the tensor product structure of these representations to provide a scheme for rewriting the group in its natural dimension note that this procedure does not provide the natural representation in the sense that we seek a standard copy, but having reduced to dimension d, existing recognition algorithms mentioned above can finish the job, and thus constructively recognise the group. In a main result of this thesis, we improve, clarify and adapt the algorithms in [67], so that every irreducible representation of a d-dimensional classical group of degree n d 2 2 can be efficiently rewritten as a representation of dimension d with exceptions in certain cases when d or q is small, where the methods fail, and appear unadaptable: the exceptions to the arithmetic results of Section 2.4 are the source of these failures. See Section 1.9 or Chapter 4 below for more detail. 1.7 Finding Random Elements A crucial aspect of the procedures we present, and any probabilistic algorithm, is the assumption that we can make random selections of a certain kind in most cases, including ours, we assume the existence of an oracle which returns, in time ξ H, uniformly distributed random elements of the group H generated by a set X GLn, q. It is not always easy to do such a thing: in particular, when a group H is input into a computer as a set of generating matrices X, we have no knowledge of even the order of H: selecting an element at random when the structure or even size of the group is unknown seems an impossible
21 1.8. Counting With Quokka Theory 11 task. For example, consider the simple problem of choosing a random element from the set {1,..., n} without knowledge of the value of n! In spite of this, Babai in [5] devised a method for producing nearly uniformly distributed elements of G in the sense that the probability of a given element in G being chosen is 1 G 1 ± ɛ, and which runs in Olog n, where n is an upper bound for G. Later, Celler et al. [22] produced the highly practical product replacement algorithm, which is implemented in GAP and MAGMA, and whose randomness and complexity was analysed by Pak [77]. In this thesis, we do not consider the problem of choosing random elements to be a great concern: we take it for granted that we may choose random elements of H at will, and denote by ξ H the cost of choosing a random element of a group H we treat this cost as a fundamental unit of our procedures; see Remark below. 1.8 Counting With Quokka Theory In [76], Niemeyer & Praeger, inspired by the work of Lehrer [62] and of Isaacs, Kantor & Spaltenstein [49], introduce the notion of a Quokka set and develop Quokka Theory, a powerful and wide-reaching tool for enumerating subsets of GLn, q The Quokka Theory of Niemeyer & Praeger A Quokka set is a subset Q of a classical group G which is closed under conjugacy, and for which membership depends only on the semisimple part of the multiplicative Jordan decomposition of its elements. In [76], Niemeyer & Praeger present a framework for reducing the problem of estimating the size of Quokka sets to two usually easier problems in subsets of permutation groups and abelian groups. Chapter 6 is devoted to using Quokka sets to enumerate subsets of classical groups crucial to the analysis of the recognition algorithms for classical groups in moderate dimension, as well as introducing a new combinatorial technique the theory of Nilpotent-Independent sets for conversion of estimates in GLn, q to the full matrix algebra Mn, q due to its dependence on the multiplicative Jordan decomposition, Quokka theory is not compatible with noninvertible matrices. Note that while the theory of Nilpotent-Independent sets was motivated by the desire to transfer estimates made with Quokka theory from GLn, q to Mn, q, the theory applies to all estimates in GLn, q no matter the method used to obtain them. In Section 6.4, we use Quokka theory to find a lower bound for the proportion of primary cyclic matrices in GLc, q b GLn, q, and apply the theory of Nilpotent-Independent sets to this estimate to produce a lower bound on the proportion of primary cyclic matrices in Mc, q b Mn, q as described in Section above.
22 12 Chapter 1. Background and Results 1.9 Results Owing to the slightly disjointed nature of this thesis, which addresses the problems of matrix group recognition from both ends the MEAT-AXE at the top of the tree, and the Classical groups at the leaves, this document requires some explaining. The dependency of one chapter on another is not necessarily obvious, and depending on the reader s interests, they need not read this document linearly Summary of Major Results The main results of this thesis can be sorted into two groups: those relating to estimating the proportion of Primary Cyclic matrices in irreducible subalgebras of Mn, q and those addressing constructive recognition of the moderate degree representations of classical groups. In Chapter 6 these two worlds overlap, as we apply Quokka Theory to the analysis of both the MEAT-AXE and to our recognition algorithms. Estimation and Primary Cyclic Matrices The Kung-Stong Cycle Index Theorem [56],[84] is a tool for investigating the structure of generating functions for the proportion of subsets of Mn, q, where the subsets are defined according to properties of the divisors of the characteristic polynomials of their elements. In Chapter 3, we generalise this in Theorem 3.2.6, the I-Cycle Index Theorem, to allow the consideration of whether or not specific irreducible polynomials divide the characteristic polynomial of elements. We then apply the new I-Cycle Index Theorem to provide an explicit, closed-form expression in Theorem for the generating function PCBu, q b = i=1 P M c, q b u c, where P M c, q b is the proportion of matrices X Mc, q b Mbc, q which are f-primary cyclic as elements of Mbc, q for some monic irreducible f F [t] of degree b. In Theorem , we apply complex analytic techniques to prove that lim c P M c, q b exists and equals P M, q b := lim P M c, q b bq b Nb q = 1 1 c 1 q b 2 ω1, qb b, where ω1, q b = i=1 1 q bi and N b q is the number of monic irreducible polynomials of degree b over F q. In Proposition , we prove that PM, q b 1 e 1 < 4e 1 bq b/2. Moreover, we use the method of Wall see [86],[29] to show that there exists a constant kq, b 2, such that, if c then max{b 1,q b /b} log3/4 P M c, q b P M, q b < kq, bq bc. In Section 6.3, we introduce the notion of a Nilpotent-Independent Subset NI-Subset of Md, q; namely a set for which membership depends only upon the nilpotent part of its elements. We prove in Theorem that, for an NI-Subset N of Md, q, we have N d GLV = i=0 q d i ωd i, q N i GLV i, where for each i, N i is a subset of GLi, q uniquely determined by N. We demonstrate that this theory has practical value by using it to find an alternative lower bound for the primary cyclic matrices: in Theorem , we find that the proportion P N c, q b of matrices X Mc, q b
23 1.9. Results 13 which are f-primary cyclic for some f of large degree where large here means that it is more than half of the dimension of the invertible part of X: see Definition satisfies P N c, q b > 1 2q b/2 log 2 log c Constructive Recognition of Moderate Degree Representations of Classical Groups In Chapter 4 we describe the procedures Initialise and FindPreimage, which together form a constructive recognition procedure: Theorem Let X GLn, q be a set of matrices generating a classical group G = Classd, q, such that the module W defined by the action of H = X is either the Reduced Symmetric Square Module or the Reduced Alternating Square Module as in Table Let d be as in Table Suppose that G {Spd, 3, SO ɛ d, 3} in the Symmetric Square case, and G {Spd, 2, SO ɛ d, 2} in the Alternating Square case. Then assuming that Conjecture holds in the Symmetric Square case, and Conjecture holds in the Alternating Square case, and excluding some small values of d see Table , there exists a Las Vegas algorithm which, with probability at least 1 ɛ, sets up a data structure for rewriting H as a projective representation in its natural dimension, with complexity O ξ H d 2 log 2 q log ɛ 1 + ρ q d 9 log d log log d log q + d 8 log d log log d log 3 q log ɛ 1, where ξ H is the cost of choosing a random element of H, and ρ q is the cost of a field operation in F q. Once the initialisation procedure is complete, there is a Las Vegas algorithm for rewriting a group element that is, returning a d d matrix with complexity O ξ H + ρ q d 8 log d log log d log q log ɛ 1. Theorem follows immediately from Theorems and In Section 10.2 we discuss strong computational evidence for both of the Conjectures & The recognition algorithms we describe in this thesis are polynomial-time Las Vegas algorithms for recognising the irreducible representations of a Classical Group of smallest degree other than the natural degree d. They are implemented in GAP and MAGMA, and code is available online or by contacting the author directly. Taking the input length to be N = n 2 log q = Od 4 log q, we have that the runtime of FindPreimage is roughly that is, modulo logarithmic terms O ξ H N 2 + ρ q N 2.25 log ɛ 1, and the runtime of FindPreimage is roughly O ξ H + ρ q N 2 log ɛ 1. This quadratic runtime is comparable to Black Box runtimes, but without the reliance on d calls to an SL2, q-oracle see In practice, our procedures perform much better than existing implementations of Black Box algorithms see Chapter 10 for runtime comparisons Navigation Chapter 2 addresses preliminary results, beginning with the theory of F G-modules that is, group actions which respect the structure of vector spaces, before some necessary results in permutation group theory, a discussion of computation, complexity, and analysis of Las Vegas algorithms, and some preliminary arithmètic results. Chapter 3 addresses Primary Cyclic matrices after presenting a necessary and sufficient condition for a matrix X Mc, q b to be primary cyclic when viewed as an element of a larger
24 14 Chapter 1. Background and Results algebra Mbc, q, we present a generalisation of the Kung-Stong Cycle Index, and apply this to enumerating a subfamily of such matrices. This Chapter is largely self-contained, although later we apply Quokka theory and Nilpotent-Independent sets to a different subfamily. In Chapter 4, we construct the modules we aim to constructively recognise, and present a top-down view of our recognition procedure. In Chapter 5 we define and analyse Special Elements of Classical Groups, and determine exactly their eigenstructure on the modules with which we concern ourselves. In Chapter 6 we introduce the Quokka theory of Niemeyer & Praeger [76], and apply it to enumerating special elements in all cases for the analysis of Initialise and FindPreimage. We go on to present the new theory of Nilpotent-Independent sets and present a proof-of-concept application, using Quokka Theory to count a different subfamily of Primary Cyclic matrices than the family in Chapter 3. Chapter 7 is devoted to those aspects of our procedure which apply to all cases, while Chapters 8 and 9 deal with the two main cases where separation is necessary. Chapter 10 discusses the implementation and practical results we have achieved, and provides instructions for downloading and using the currently available GAP code for the Recognition Algorithms described in Chapters 7, 8 & 9.
25 CHAPTER 2 15 Preliminary Results 2.1 Modules and Representations This thesis concerns itself, at its core, with the idea of a group action. A group G is said to act upon a set Ω if every g G induces a permutation of Ω we denote the image of α Ω under the action of g by α g such that, for every g, h G and α Ω, we have α g h = α gh. We often require the action of G to respect some geometric structure on Ω: if, for example, Ω is an F -vector space, group actions which leave invariant the vector space structure are called F G-modules. Definition Let G be a group, and V a vector space over a field F. Then V is called an F G-module if G acts on V in a way that respects the vector space structure of V : that is, such that the following relations hold: i for every g G, v, w V, we have v + w g = v g + w g ; and ii for every g G, v V, a F, we have av g = av g. With this definition, for any subgroup G GLV, the vector space V is automatically an F G-module relative to the usual G-action. The concept of a module provides a means to discuss the target space of a linear group while keeping the group action in mind. Definition Let V be an F G-module. A subspace W of V which is fixed setwise by the action of G is called an F G-submodule or simply a submodule of V. In particular, the zero subspace is called the trivial F G-submodule, and a nontrivial module with no proper nontrivial submodules is said to be irreducible. The kernel N := {g G v g = v, v V } of the action of G on V is a normal subgroup of G we denote this by N as we reserve the letter K for fields. The vector space V is called the underlying vector space of the module, and the subgroup of GLV induced by the action of G on V is denoted G V so G V = G/N. Let V and W be F G-modules. Then a homomorphism of F G-modules is an F -linear map ν : V W such that, for every v V, g G, we have νv g = νv g. If in addition ν is a bijection then ν is called an isomorphism of F G-modules, and V and W are said to be isomorphic. Note that two different even nonisomorphic F G-modules may have the same underlying vector space. A group element g G induces a linear transformation of any F G-module: we introduce some notation for dealing with the different perspectives from which we may view g. Notation Let V be an F G-module, and let B be a basis for V. Then for g G, we write g V as the transformation in GLV induced by the action of g, and we write G V := {g V g G} GLV. Moreover, for each g G and for each basis element b B, we can express b g uniquely as a linear combination of the basis vectors in B: b g = g bb b. b B
26 16 Chapter 2. Preliminary Results We define g b,b or, if there is no ambiguity, g bb as the unique element of F determined by the triple g, b, b in this way: that is, g bb is the coefficient of b in the unique expansion of b g as a linear combination of the basis vectors in B. Moreover, if a basis B of V is indexed by some ordered set I as is common for ordered bases: say B = {v i i I}, then we may simply write g ij in place of g vi,v j. Then for g G, the matrix of g with respect to the basis B is the matrix g ij i,j I where the subscript denotes that i and j are indexed by I. We denote this matrix g B. The set G B := {g B g G} of such matrices forms a subgroup of GLd, q which we regard as a group of matrices, while thinking of G V GLV as a group of linear transformations of V. Definition Let G be a group. A representation of G is a homomorphism ρ : G GLV. Any representation of G gives rise to an F G-module, and for any F G-module V the map G G V is a representation of G. That is to say, representations and F G-modules are simply two approaches for studying the same objects. By fixing a basis of V, we fix a correspondence between G and a subgroup of GLd, q. By modifying the basis, we modify this correspondence. Thus the matrices of g G in its action on related bases are themselves related: relationships of this kind are the main tool in our recognition algorithms. We describe a few such relationships below in Section Tensor Products The Tensor Product of two F -vector spaces V and W is often abstractly defined as a quotient of the direct product V W : the largest space such that products are bilinear. In this thesis we use a more practical, simpler definition which is equivalent in the finite case it differs only in its requirement that we choose bases for the spaces, which we assume that we can do: after all, we are provided one intrinsically in a computational context. Definition Let V, W be vector spaces over F, with bases {v 1,..., v d1 }, {w 1,..., w d2 } respectively. Then the Tensor Product space V W is the F -span of {v i w j 1 i d 1, 1 j d 2 }, where v i w j is a formal symbol, called the tensor product of v i and w j. If there are several fields under discussion we may write V F W where clarity is necessary. For each v = d 1 i=1 a iv i V, w = d 2 j=1 b jw j W, we define the tensor product of v and w: d 1 d 2 v w = a i b j v i w j. i=1 j=1 While all elements of the form v w lie in V W, the converse is not true in general. Vectors as above are called the simple tensors of V W. Each element of V W can be written as a sum of simple tensors. The minimal number of simple tensors required, though not the actual expression, is uniquely determined. The tensor product V W has dimension d 1 d 2, and the simple tensors satisfy the following bilinearity relations for any v, v V, w, w W, a F : v + v w + w = v w + v w + v w + v w av w = av w = v aw. Up to isomorphism, the tensor product V W does not depend on the choice of bases for V, W.
27 2.1. Modules and Representations 17 Definition Let F = F q, and let V be an F G-module. Then G acts on the tensor product V V by v w g := v g w g for g G, extended linearly for arbitrary elements, and so V V is an F G-module. F G-modules are most often defined by the actions of subgroups G of the General Linear Group GLV, which we often consider when a basis B has been fixed interchangeably with the matrix groups G B GLd, q under the action of right multiplication. With this action V forms an F G-module, called the natural module of G Extension Fields We frequently use the idea of extension fields in this thesis: for a detailed treatment of finite fields and an excellent reference book, see [63]. Definition Let F = F q be a finite field. Then a field K is an extension field of F sometimes denoted K/F if we want to emphasise the relationship between K and F if K contains F as a subfield. A finite extension field K is isomorphic to F q d, for some integer d 1: this integer d is called the degree of the extension K/F. The map σ : K K : x x q is an automorphism of K of order d, with Fix σ := {a K a σ = a} = F ; σ is called the Frobenius automorphism of K/F. The cyclic group generated by σ is called the Galois Group of K/F, denoted GalK/F. Note that the Galois group and Frobenius automorphism depend on both K and F. The Frobenius map σ induces an action on any K-vector space with a prescribed basis by acting individually on each coordinate of row vectors, and acts on matrices with entries in K by raising entries to their qth power. A natural example of an infinite extension field is the field of complex numbers C, which is a quadratic degree 2 extension of the real numbers R: the analogue of the Frobenius map σ is the operation of complex conjugation. Complex numbers allow the creation of roots of polynomials irreducible over R: a similar idea holds for finite fields. Definition Let F = F q be a field. Then denote by F [t] the ring of polynomials with coefficients in F, where multiplication and addition are defined in the natural way. The degree of f F [t] is the highest power of t with a nonzero coefficient. If that highest coefficient is 1, then f is called monic. For f, g F [t], we say that g divides f denoted g f if there exists h F [t] with f = gh. A polynomial is called irreducible if it has no proper divisors of degree at least 1. The set of monic irreducible polynomials over F is denoted IrrF = Irrq; and the set of monic irreducibles of degree b is denoted Irr b F = Irr b q. We denote by N b F = N b q the number Irr b q of monic irreducibles of degree b over F. The following is an immediate consequence of [63, Lemma 2.14]. Lemma Let F = F q, and let f Irr q b. For an extension field K = F q b of F, each coefficient of f lies, in particular, in K, and so f may be regarded as a polynomial over K; and as an element of K[t], f has b distinct linear divisors, namely b f = t λ qi 1, i=1
28 18 Chapter 2. Preliminary Results for some λ K with {λ, λ q,..., λ qb 1 } all distinct. In particular, for any x F, there exists at least one bth root of x in K. Definition Let b be an integer. Then for any integer i, we define res b i as the unique integer k such that 1 k b and k i mod d. It follows immediately from the definition that if λ K = F q b, and l i := λ qi 1 for i Z, then for any integer i we have l i = l resb i. We now present two methods for considering a vector space over two different fields: one makes a transition to a subfield, and the other to an extension field. Definition Let q be a prime power, let F = F q, let b 1, let K = F q b. An element α K is called a primitive element of K if α generates the multiplicative group K of K. Then K forms an F -vector space K F of dimension b, with basis {1, α, α 2,..., α b 1 }, where α is a primitive element of K. Similarly, suppose that V := V c, q b is a c-dimensional K-vector space with basis {v 1,..., v c }. Then V may be regarded as an F -vector space, with basis {α i 1 v j 1 i b, 1 j c}, and addition and multiplication inherited from the K-vector space structure, isomorphic to the space V bc, q of bc-dimensional row vectors over F. We use the notation V bc, q when we are discussing V as an F -vector space, and if it is ambiguous, we use V c, q b to denote the original K-vector space. For V = V c, q b, any linear transformation X EndV induces a linear transformation of V bc, q, which we denote as usual by X bc,q. If there is ambiguity we denote the transformation of V c, q b by X c,q b. Suppose now that V is a d-dimensional F -vector space there is no good reason why V should admit additional structure as a K-vector space, but here we describe a means to embed V naturally and intuitively inside a K-vector space, in the way that we might seek complex eigenvectors of a linear transformation of a real vector space. Note that this is not any kind of inverse operation to the concept of forgetting the K-vector space structure in Definition above. Definition Let F = F q and let V be an F -vector space with basis {v 1,..., v d }. Let K = F q d be an extension of F, and let α be a primitive element of K. Then the tensor product V F K F is an F -vector space of dimension dd, with basis {v j α i 1 1 i d, 1 j d}. Moreover, the space V F K F can be given the structure of a K-vector space with the following definition of scalar multiplication: for any a K, define av j α i 1 := v j aα i 1,
29 2.1. Modules and Representations 19 V F Dimension d Order q d Extend Scalars V K := V F K F Dimension d Order q d d V bc, q Dimension bc Order q bc Restrict to Subfield V c, q b Dimension c Order q bc Figure : Two ways of considering vector spaces over different fields. and extend linearly to all elements of V F K F. With this definition, V F K F satisfies all of the axioms of a K-vector space, and has basis {v j 1 j d}. Moreover, for every simple tensor v V, a K, we have that v a = av 1. The mapping V V F K F : v v 1 is a natural embedding of V in V F K F, and so we consider this to be the canonical way of considering an arbitrary F -vector space V over the larger field K. For this reason, we use the notation V K to denote this space. That is, V K := V F K F. Definition Let F = F q, let K = F q d, and let V = F d be an F G-module. Then for d 1, the group G acts on V K according to v 1 g := v g 1, for all v V, g G, and extending by linearity. Thus V K has the structure of a KG-module. We must take great care with notation here: we have defined two different ways in which we may consider a vector space V over multiple fields see fig The process of extending scalars to produce V K := V F K is analagous to regarding a real vector space as a complex vector space by simply permitting the coordinates to take complex values, and thus producing C n from R n. This produces a larger in the finite case, not in the Real case vector space, in the sense that there are more vectors overall, but preserves dimension. The second method, as in Definition , is more akin to producing R 2n from C n by forgetting a complex structure. This method leaves constant the cardinality of the space by producing a higher-dimensional space over a smaller field Characteristic and Minimal Polynomials, Eigenvalues and Eigenvectors One of the concepts that pervades this thesis is that the action of G on a vector space should be exploited wherever it is useful to do so; neither the constructive recognition algorithms of Chapters 7, 8 & 9, nor the MEAT-AXE procedure we analyse in Chapters 3 & 6, are Black Box algorithms. In both cases, the characteristic and minimal polynomial of g G in its action on an F G-module V are of critical importance. However, as these definitions apply to both invertible and noninvertible linear transformations of a vector space V, we introduce them for elements of the matrix algebra MV.
30 20 Chapter 2. Preliminary Results Definition Let V be an F -vector space, and let X MV. polynomial c X,V t is the polynomial The characteristic c X,V t := detx ti, where I is the identity transformation of V, and X is viewed as an n n matrix over F the characteristic polynomial is independent of the choice of basis. The characteristic polynomial is monic of degree n, and has coefficients in F. The minimal polynomial m X,V t is the monic polynomial of minimal degree such that m X,V X = 0. Note that the inclusion of V in the notation c X,V t is technically unnecessary, for the field is implicit in X: it serves as a reminder of our setting. We frequently wish to relate the polynomials associated with a linear transformation X := X c,q b of a K-vector space V c, q b with the linear transformation X bc,q induced by X c,q b on the F -vector space V bc, q as in Definition , or the characteristic polynomial of X in its action on V K as in Definition These polynomials are closely related, as we observe in Lemmas , below. Remark We may equivalently view the minimal polynomial as the unique monic polynomial which divides any polynomial for which X MV is a zero. By the Cayley-Hamilton theorem [31, p. 83], c X,V X = 0, and so we have m X,V t c X,V t: in particular, the set of irreducible divisors of these two polynomials are the same, although the multiplicities of the irreducible factors may differ. Definition Let X MV, for an F -vector space V. Then λ F is an eigenvalue of X if t λ is a divisor of c X,V t. Equivalently, λ is an eigenvalue of X if and only if there exists a nonzero vector v V such that v X = λv. Such vectors v are called λ-eigenvectors of X in V. The set of λ-eigenvectors of X forms an X-invariant subspace of V, called the λ-eigenspace of X. It is well known that if V has a basis of eigenvectors for X, then V has an X-invariant decomposition as a direct sum of the eigenspaces of X: this notion is generalised by the X- primary decomposition of V : Definition Let X MV for an F -vector space V = V F, and suppose that m X,V = r i=1 f αi i, with each f i Irrq recall Definition , and α i > 0. The X-primary decomposition see [40, Theorem 11.8] is V F = V f1 V fr, where the subspace V fi, called the f i -primary component of X on V, has the property that f i does not divide the minimal polynomial of the restriction of X to j i V fj, and the minimal polynomial of X Vfi is f αi i. If an irreducible f does not divide c X,V t we say the f-primary component is trivial and define V f = {0}. Definition A matrix X MV is called cyclic if m X,V t = c X,V t, and, for f Irrq, X is f-primary cyclic if V f is nontrivial and X Vf is cyclic. Also, X is primary cyclic if it is f-primary cyclic for some f Irrq. We note that X is f-primary cyclic if and only if the nullspace Null fx is an irreducible F X -submodule of V.
31 2.1. Modules and Representations 21 Lemma Let g G, and let V be an F G-module. Then the characteristic polynomials of g V and g VK are equal. Proof. Let {v i 1 i d} be a basis for V. Then {v i 1 i d} is a basis for V K, and since g acts by v 1 g = v g 1 g = v g 1, the matrix of g V with respect to the basis {v i } is exactly the same as the matrix of g VK with respect to the basis {v i 1}. Thus the two have the same characteristic polynomial. Remark Though the characteristic polynomials of g V and g VK are equal, they are polynomials over different fields, and so, for example, it may be possible to factorise the characteristic polynomial into linear factors over K but not F. Thus the eigenvalues of g V may differ from those of g VK. In particular, by Lemma , if c X,V t is irreducible of degree b, then setting K = F q b, c X,VK t has b distinct linear factors, and so X VK has b distinct eigenvalues. We often use the phrase over K when discussing the eigenvalues of g VK as distinct from g V. This is no different from the common practice of considering the eigenvalues over C of a real-valued matrix. The following relationship between the characteristic polynomials of a linear transformation X in its actions on V c, q b, V bc, q is proved in [71, Lemma 5.1]: Lemma Let F = F q, K = F q b, let X Mc, q b, and let c X,V c,q b, m X,V c,q b be the characteristic and minimal polynomials of X in its action on V c, q b. Then the characteristic and minimal polynomials of X in its action on V bc, q are c X,V bc,q t = τ GalK/F c τ X,V c,q b ; m X,V bc,q t = lcm{m τ X,V c,q b τ GalK/F }. Note that the result of Lemma ensures that the characteristic polynomial of X bc,q has degree bc which it must, and that the minimal polynomial has degree at least deg m X,V c,qb and at most b deg m X,V c,q. This change in degree reflects the change in dimension when b embedding V c, q b V bc, q The Symmetric and Alternating Squares We now define an action of GLV on a more familiar space, and prove in Lemma that the F G-module produced is isomorphic to V F V. Definition Let Md, q be the space of all d d matrices over F = F q considered as an F -vector space, and define E ij as the d d matrix with a 1 in the i, j position and zeroes elsewhere. Then {E ij 1 i, j d} is a basis for Md, q. Moreover, define an action GLd, q on Md, q by for any g GLd, q, A Md, q. A ϕg := g T Ag The map ϕ defines a group action on Md, q since, for all g, h GLd, q, we have gh T Agh = h T g T Agh.
32 22 Chapter 2. Preliminary Results Lemma Let F = F q, let G GLV, where V is the F -space of d-dimensional row vectors with basis {v 1,..., v d }, and consider Md, q as in Definition above. Define ρ : V F V Md, q by ρ : a ij v i v j a ij i,j [1...d], i,j Then ρ is an isomorphism of F G-modules. Proof. By definition, v i v j ρ = E ij = v T i v j for all i, j and for each g G, we have v i v j ρ ϕg = E ϕg ij = g T E ij g = g T v T i v j g = v i g T v j g = v i g v j g ρ = v i v j g ρ. A routine matrix calculation yields the following useful lemma: Lemma Let A GLd, q, and let a ij denote the i, j-entry of A. Then for every i, j we have A T E ij A = a ik a jl E kl k,l Lemma The kernel of the action of GLV on V V is the subgroup {±I} GLV. Proof. Let g = a ij GLd, q. Then g ker ρ implies, by , that E ij = g T E ij g = a ik a jl E kl, k,l and so if k, l i, j then we have a ik a jl = 0. Now fix j: then since g is invertible, it has no zero rows and hence there exists l such that a jl 0. If j l, then implies that for every pair i, k we have a ik = 0, which is a contradiction. Hence l = j and so g is a diagonal matrix diaga 11,..., a dd. Since the action of g fixes all matrices, it fixes the identity I, and so g T Ig = I, and so g 2 = I since g is diagonal. This forces a 2 11 = 1 and so a 11 = ±1. Then for every j, setting i = 1 in and inspecting the coefficient of E 1j, we have a 1k a jl = 1 with k = 1, l = j, and so a 11 a jj = 1, and so a jj = a 11 since a 11 = ±1. Thus g = diaga 11,..., a 11 = a 11 I, for a 11 {±1} as required. Definition Let V = v 1,..., v d be an F G-module. The Symmetric Square S 2 V of V is the subspace of V F V spanned by {v i v j + v j v i 1 i < j d} {v i v i 1 i d}.
33 2.1. Modules and Representations 23 The Symmetric Square has dimension d+1 2. The Alternating Square 2 V of V is the subspace of V F V spanned by The Alternating Square has dimension d 2. {v i v j v j v i 1 i < j d}. We have defined S 2 V and 2 V as subspaces of V F V, and we see below that they are, in fact, F G-submodules. Lemma Let G GLV. Then both the Symmetric Square S 2 V and Alternating Square 2 V as defined in Definition are invariant under the action of G, and so are F G-submodules of V F V. If q is odd then V F V = S 2 V 2 V. If q is even, then 2 V S 2 V. Proof. We use the F G-module isomorphism ρ defined in Lemma with respect to the G-action on Md, q given in Definition The image of S 2 V under the isomorphism ρ is E ij + E ji 1 i j d E ii 1 i d, that is, the space of symmetric matrices, so S 2 V ρ = {A Md, q A = A T }. This subspace of Md, q is G-invariant, as A = A T implies g T Ag = g T A T g T = g T Ag T. Similarly, the image of 2 V under the isomorphism ρ is E ij E ji 1 i < j d. To see that 2 V is G-invariant, for any q, observe that using Lemma , g T E ij E ji g = g T E ij g g T E ji g = g ik g jr g jk g ir E kr k,r = k<r g ik g jr E kr E rk 2 V ρ, and so 2 V ρ and hence 2 V is G-invariant. Suppose that q is odd. Then this is the space of skew-symmetric matrices: 2 V ρ = {A Md, q A = A T }. Let X Md, q. Then X sym := 2 1 X + X T is a symmetric matrix, X alt := 2 1 X X T is skew-symmetric, and X = X sym +X alt. Hence any matrix in Md, q can be written uniquely as a sum of a symmetric and a skew-symmetric matrix when q is odd. That is, V = S 2 V 2 V. Now suppose that q is even. Then 2 V S 2 V, since the given basis for 2 V is a subset of the basis for S 2 V given in Definition
34 24 Chapter 2. Preliminary Results Notation Let G GLV = GLd, q. By Lemma , the Symmetric and Alternating squares are F G-submodules of V F V, and so we may use the notation S 2 V, 2 V to refer to either the vector subspace or F G-module according to the context. We will frequently refer to actions of an element g GLV on various modules. Recall that the notation g W denotes the action of g on an F G-module W. Our primary method is the analysis of the eigenvalues and eigenspaces of a group element: if, for v V, we have that v g = λv for some λ F, then we say that λ is an eigenvalue of g in V, and v is an eigenvector. We refer to the set of all eigenvalues and eigenvectors of g G as the eigenstructure of g on V. Since the eigenstructure of a group element depends on its action on a vector space, an element g will usually have different eigenstructures, depending on whether we consider g V, g V V, g S2 V, g 2 V or an action on another module, and also depending on the underlying field. We now describe the relationship between the eigenstructures of g G in its actions on various modules. Lemma Suppose λ 1, λ 2 are eigenvalues of g GLV, with eigenvectors v 1, v 2 respectively. Then λ 1 λ 2 is an eigenvalue of g in its action on V F V, and v 1 v 2, v 2 v 1 are λ 1 λ 2 -eigenvectors. Proof. We have v g 1 = λ 1v 1, v g 2 = λ 2v 2. Hence v 1 v 2 g = v g 1 vg 2 = λ 1v 1 λ 2 v 2 = λ 1 λ 2 v 1 v 2, and so v 1 v 2 is a λ 1 λ 2 -eigenvector. The same argument applies to v 2 v 1. Corollary Let F = F q, let K = F q d for some integer d, let V = F d, and suppose that g GLd, q has d not necessarily distinct eigenvalues {λ i 1 i d} in its action on V K, and there exists a basis {v 1,..., v d } for V K of g-eigenvectors so that for each i, v i g = λ i v i. Then the eigenvalues of g in its action on V F V K are {λ i λ j 1 i j d}, and for each i, j, both v i v j and v j v i are λ i λ j -eigenvectors in V F V K. Moreover, these are the only eigenvalues of g in V V K. Proof. That v i v j, v j v i are λ i λ j -eigenvectors follows directly from Lemma Since {v i v j 1 i, j d} is a basis for V F V K, we have a basis of eigenvectors and so no other eigenvalues are possible. Lemma Let g GLV, and suppose that g has eigenvalues λ 1,..., λ d in its action on V, and that {v 1,..., v d } is a basis for V such that for all i, v i is a λ i -eigenvector for g V. Let v Sym ij = v i v j + v j v i when i j, and v Sym ii = v i v i. Then {v Sym ij 1 i j d} is a basis for S 2 V, such that for every i, j, v Sym ij S 2 V. is a λ i λ j -eigenvector for g in its action on Let v Alt ij = v i v j v j v i for i < j, we have that {v Alt ij 1 i < j d}
35 2.1. Modules and Representations 25 is a basis for 2 V, such that for every i, j, vij Alt 2 V. is a λ i λ j -eigenvector for g in its action on Proof. By Lemma , both v i v j, v j v i are λ i λ j -eigenvectors of g V V, and so any linear combination of the two is itself a λ i λ j -eigenvector. That these sets form bases is clear by comparing dimensions Related Bases and Their Effect on Matrices In this section we describe the ways in which different bases of the same space, and related bases for different spaces, give rise to relationships among different representations of a group G. Lemma Let V be an F G-module, and let B := {b i 1 i d}, B = {b i 1 i d} be bases for V, such that for every i, there exists c i F := F \ {0} such that b i = c ib i. Then for every g G and for all i, j, we have g b i b j = c i c j g bib j. Proof. On the one hand, for every i we have b i g = d j=1 g b i b b j j = d j=1 g b c jb i b j j. On the other hand, b i g = c i b g i = c i and the result follows. d j=1 g b ib j b j. It follows that for all i, j, we have g b i b j c j = c i g bib j, Lemma Suppose that V, W are F G-modules, suppose that ϕ : V W is an isomorphism of F G-modules, and suppose that V is a basis for V. Then V ϕ is a basis for W, and for all v, w V, g G, we have g v ϕ w ϕ = g vw. Proof. For all v V, g G, we have ϕ v ϕ g = v g ϕ = g vw w = g vw w ϕ, w V w V and so the coefficient of w ϕ in v g ϕ is g vw : that is, g vϕ w ϕ = g vw. Lemma Suppose that V is an F G-module, and suppose that W is a G-invariant subspace of V. Then the quotient space V/W := {v + W v V } is an F G-module of dimension dim V dim W, with the action of g G defined by v + W g = v g + W. Moreover, suppose that quo W : V V/W is the natural quotient map v v + W, and e, f V are basis vectors such that e, f W = {0}. Then for every g G, we have that g e,f = g quoe,quof. Proof. Since W g = W, the action of g on V/W is well defined. Moreover, we may choose a basis V for V containing e, f, such that V contains a basis W for W. Then e + W g = e g + W = g ev v + W = v V g ev v + W = g ev v + W. v V \W v V \W Since f V \ W, the coefficient of quof in quoe g is g ef as required.
36 26 Chapter 2. Preliminary Results Lemma Suppose that V is an n-dimensional F G-module, and W is a 1-dimensional F G-submodule of V fixed pointwise by the action of G. Let N = {g G g V/W = 1} be the kernel of the action of G on V/W. Then N is isomorphic to a subgroup of the additive group of an n 1-dimensional F -vector space. In particular, if F = F q, then N is an elementary abelian group with order a power of the characteristic charf of F. Proof. Let 0 w W, and suppose that {w, v 1,..., v n 1 } is a basis for V. Then {quov i = v i + W 1 i n 1} is a basis for V/W, and since W is fixed pointwise by G, we have that for every g G, g ww = 1, g wvi = 0, and g viv j = g quovi,quov j for all i, j n 1. Thus if g V/W = 1, then the values of g ww, g wvi, g viv j are known for all i, j, and the values of g viw may take any value in F, and so the matrix of g with respect to the basis {w, v 1,..., v n 1 } is r I n 1.. where r F n 1 is an arbitrary column vector. It is easily verified that multiplying two matrices of this form results in addition of the corresponding vectors r, and so the kernel N is contained in the additive group of an F -vector space of dimension n 1: when F = F q is finite, this is an elementary abelian group of order q n 1. Lemma Suppose that V is an F G-module, and suppose that V is a basis for V. Suppose that W is a G-invariant subspace of V, and suppose that e, f V are basis vectors such that e, f W. Then for every g G, we have that g ef = g W ef. Proof. This follows from the fact that the action of g when restricting to a subspace is unchanged. Lemma Suppose that V is an F G-module of dimension n, where F = F q, and W is an F G-submodule of V of dimension n 1, and let N = ker ι, where ι is the restriction map ι : G V G W : g V g W. Then N is isomorphic to a subgroup of a group of order q 1q n 1. If in addition G V SLV, K is isomorphic to a subgroup of an elementary abelian group of order q n 1. Proof. Let {v, w 1,..., w n 1 } be a basis for V such that {w 1,..., w n 1 } is a basis for W. Then by Lemma , and since W is G-invariant, we have that, for all 1 i, j n 1, g wiw j = ιg wiw j, and g wiv = 0. Thus if ιg = 1, the matrix of g with respect to the basis {v, w 1,..., w n 1 } has the form z 0 0. r I d 1. where r F n 1 is a column vector, and z F. Note that since g is invertible, z 0. Thus there are exactly q 1 choices for z, and q n 1 choices for r. In the case that G = GLV,
37 2.1. Modules and Representations 27 all such choices are valid. If G SLV, then z = 1 and the result follows as in the proof of Lemma Just as we may seek normal subgroups of groups by defining homomorphisms and inspecting their kernels, we will construct submodules of F G-modules by considering the nullspaces of certain maps: Lemma Let V be an F G-module. Then a linear form on V is a linear map T : V F. The form T is called G-invariant if, for every v V, g G, we have T v = T v g. Define the kernel of the form T as the set ker T := {v V T v = 0}. The kernel of a linear form is a subspace of V, and the kernel of a G-invariant linear form is an F G-submodule of V. Proof. This follows since, for every v ker T, we have that T v g = T v = 0, and so v g ker T. Lemma Let G be a group, W be an F G-module, and let T be a G-invariant linear form on W that is, a linear map W F, and let g G. If g W has an eigenvalue λ 1 in F, then the λ-eigenspace of g is contained in the kernel of T. Proof. Let v be a λ-eigenvector: then since T is g-invariant and linear, we have T v = T v g = T vλ = λt v, and since λ 1, this forces T v = 0 as required. Given the matrix of a group element g G in its action on a module V with respect to a fixed basis as is always the case when dealing with a computer representation of a group, we may easily construct corresponding matrices for the actions of g on V V, S 2 V, 2 V : Lemma Let G GLV, and let V := {v i 1 i d} be a basis for V. Let g G, and write g ij = g viv j. Define v Sym ij, vij Alt as in Lemma Then i g vi v j,v k v l = g ik g jl, for any i, j, k, l [1... d]; ii for 1 i j d, 1 k l d, we have iii for 1 i < j d, 1 k < l d, we have Proof. By definition we have g v Sym ij,v Sym = g ik g jl + 1 δ kl g il g jk. kl g v Alt = g ij,valt kl ik g jl g il g jk. v i v j g = v g i vg j d d = g ik v k g jl v l k=1 d = k=1 l=1 l=1 d g ik g jl v k v l,
38 28 Chapter 2. Preliminary Results and i follows. For ii, observe that, for i j, we have v i v j + v j v i g = v g i vg j + vg j vg i d d = g ik g jl + g jk g il v k v l k=1 l=1 Since switching k, l does not change the value of g ik g jl + g jk g il, we have d v i v j + v j v i g = g ik g jl + g jk g il v k v l + v l v k. k=1 l k The proof when i = j, and of iii, follows by an identical argument. 2.2 Computation and Complexity In this Section we introduce the fundamentals of computational complexity, the techniques by which we analyse the theoretical quality of our procedures, and the basic functions we require for analysing the algorithms Initialise and FindPreimage to be given in Chapters 7-9. In short, in this section we describe the theoretical setting for our procedures Randomised Algorithms In some Computational Group Theory settings, deterministic algorithms are feasible: for simple tasks, like constructing the orbits of a permutation group, one can write programs that, for a given input, always return correct answers, always return the same answer, and always take the same time to run. Other tasks require the use of random number generators to run in a reasonable time, and so their output may change for different runs on the same input. There are three ways in which different executions of the same randomised algorithm with the same input may produce different output: i The output of one or both executions may be incorrect, or one may return FAIL. ii Two different, correct outputs may be returned for example, if a group G acts reducibly on a vector space V, the MEAT-AXE procedure returns when correct one G-invariant subspace of V. Two runs may return different subspaces. iii Even if the outputs match, the runtimes may be different. We now formalise the notion of an algorithm which may have nondeterministic output. Definition i A two-sided Monte Carlo algorithm is one which takes as part of its input a positive real number ɛ < 1, and whose output is correct with probability at least 1 ɛ; ii A One-Sided Monte Carlo algorithm is a Monte Carlo algorithm with parameter ɛ for which the output of one type for example, TRUE is guaranteed to be correct, and all other types are correct with probability at least 1 ɛ; and iii A Las Vegas algorithm is one which takes as part of its input a positive real number ɛ < 1, and whose output is always correct, though it may return FAIL with probability at most ɛ.
39 2.2. Computation and Complexity 29 We have defined the three most common types of randomised algorithms in order of least to most desirable : in the case of a Las Vegas algorithm, we can be completely confident in our answer, so long as one is returned. In many cases, we can upscale two-sided Monte Carlo procedures to one-sided Monte Carlo or Las Vegas procedures if we have the ability to check our output quickly. The MEAT-AXE procedure is an example of a Las Vegas algorithm: it may return FAIL, but if it does return an answer, it returns a certificate proving that the answer is correct Complexity and Big-Oh Notation Although there are many ways of analysing an algorithm s complexity and even more so when dealing with Monte Carlo and Las Vegas algorithms, it is conventional in Computational Group Theory to consider the worst case. We do this in both possible senses: when considering runtimes, we analyse the slowest possible runtime of our procedure rather than an average or best-possible; and when analysing the random aspects of our algorithms, we find lower bounds on the probability of failure rather than think about expectation. Definition Let Proc be a procedure. Then the runtime complexity of Proc is a function f : Z + Z + such that, for every N Z +, fn is the maximum time taken in terms of some basic unit of time for Proc to complete, for all inputs of length N. If Proc is a randomised algorithm one of the three types in Definition , then the runtime of Proc is a function f : Z + 0, 1 Z + such that, for every N, ɛ Z + 0, 1, fn, ɛ is the maximum time taken for Proc to complete, for all inputs of length N, such that probability of an incorrect result or a result of FAIL in the Las Vegas case is less than ɛ. In practice, we do not often find the precise runtime of a function, but find an upper bound for simplicity. In particular, we mostly concern ourselves with the growth rate of the runtime as the input length N grows. To describe growth rates, we use Big-Oh notation, which we introduce here briefly and use throughout to describe the asymptotic behaviour of our procedures. For more on computational complexity, we refer the reader to the excellent introductory textbook of Graham, Knuth & Patashnik [37, Chapter 9]. Definition Let n 1, and let f : Z Z be a function. Then we define Of as the set of functions defined as follows: a function g : Z Z lies in Of if there exist constants c R, N Z such that, for n N, we have gn cfn. If g Of, we may say that g is Big-Oh of f, that g is Of, or even and this is a considerable abuse of notation that g = Of. If in addition g is the runtime of a procedure Proc, then we may say that Proc is Of, that Proc runs in Of time or most often in our case that Proc has complexity Of. The definition of Of is similar in spirit to the definition of limits of functions: a function g is Of if there exists a constant c such that cf dominates g. Intuitively, g is Of if g grows no faster than f.
40 30 Chapter 2. Preliminary Results Remark The following are well known facts about the growth rates of functions. Logarithmic functions grow more slowly than polynomials, which in turn grow more slowly than exponentials. Functions of the form fn = n a for a fixed a are called polynomial even if a is not an integer, and grow faster as a grows. That is, n 2 On 3, but n 3 On 2. While it makes good sense to discuss the runtime of an algorithm in terms of its input length that is, its runtime with respect to a single variable, considering its runtime with respect to aspects of its input is also of use to us especially in a black-box setting, where the input length is dependent on the representation of the group. In particular, in a computational group theory setting, the input length N is often a function of the input group G. For example, the usual representation of a matrix group G GLn, q has input length dependent on d and q, and so an analysis of an algorithm s complexity in terms of these parameters is quite reasonable. For this reason, we require a broader definition of runtime, which allows us to define the runtime in terms of some set X of relevant parameters : Definition Let I be the set of inputs to a procedure Proc, and let g : I X be a function from I to an arbitrary set X the parameter space. Then the runtime of Proc is a function f : X Z, such that for each x X, fx is defined to be the maximum time taken by Proc to complete, for all inputs in the preimage g 1 x. For example, in a constructive recognition algorithm for a matrix group, the set I contains our usual inputs such as the generating matrices and the acceptable probability of failure ɛ, as well as some implicit inputs for example, a certain algorithm to be used for matrix multiplication, a discrete log oracle, or instructions for choosing random elements. The function g then takes such an input and returns parameters on which the runtime depends see below for examples of such parameters. With Definition , we may safely discuss the runtime of a function whose input has more characteristics than just a length. Similarly, we must generalise the Big-Oh notation to permit functions of several variables, and to account for the fact that ɛ is fixed rather than growing. These are definitions we do not address in detail, for they are intricate in ways which have little relevance for our work. In particular, note that, while our definition of Big-Oh notation is for functions of positive integers, we assume that it has been extended to functions of real variables, and to functions of several variables. Not only do we analyse our procedures in terms of the features of the group G, but we also consider other variables which may depend upon our setting. Recall that the notion of runtime contains both in its definition and as a subword the rather mysterious notion of time: we avoid this question by defining our runtimes in terms of the runtimes of certain basic functions, or units. Definition We define the following units of cost for our procedures: i Let F be a finite field of order q. Then denote by ρ q or ρ F an upper bound for the cost of performing any field operation addition, multiplication, inversion in F ; ii Let X be a set. Then denote by ξ X an upper bound for the cost of constructing we may casually refer to this as choosing a uniformly distributed random element of X.
41 2.2. Computation and Complexity 31 Remark i We use both ρ q and ξ X as units of runtime rather than considering in detail the intricacies of their implementation, as is conventional in the field of matrix group recognition. For example, in practice, field addition is faster than field multiplication, for finite fields are most often regarded as equivalence classes of polynomials, and so multiplication requires a lot more work it is more costly to multiply two polynomials than to add them, even before considering the reduction to a canonical representative of the class. Note that ξ X may be a function of ρ q among other things. ii The precise meaning of what it is to construct a random element of X may depend upon the setting: often we produce words or straight line programs in X, but in a matrix group setting we often construct random elements as matrices. iii We may use the product replacement algorithm of Celler et al. [22], which is implemented in both GAP and MAGMA, to produce random elements in a matrix group given as straight line programs in the input generators. iv Note that in the analyses of our procedures, we consider computations other than field operations such as the manipulation of simple data structures or integers and floatingpoint numbers as having negligible cost, and we do not analyse explicitly the memory requirements of our procedures. All of the procedures we present in this thesis are analysed in terms of these parameters. Moreover, we make use of several existing algorithms not only in the context of our procedures being a part of the matrix group recognition project, but also in the manipulation of common objects like matrices and polynomials. We summarise the functions we require, and their typical runtimes, below. In general, we will consider matrix multiplication to come at a cost of On 3 field operations, although there exist fast matrix multiplication algorithms for example, the aforementioned Strassen s algorithm, which runs in On log 2 7. It is customary to use ω to denote the exponent of n in the cost of matrix multiplication. In choosing which algorithms to use for our analysis, we err on the side of simplicity when discussing procedures which are not bottlenecks that is, we do not spend undue effort speeding up sections of our algorithm in ways that do not affect the overall performance or complexity. Lemma i The characteristic polynomial of an n n matrix with entries in F q can be computed by the LU-Krylov algorithm [27, Algorithm 2.2] in Oρ q n 3 time; or by the algorithm of Keller and Gehrig [54] in Oρ q n ω log n time; ii For an eigenvalue λ of an n n matrix X with entries in F q, the computation of a λ- eigenvector of X can be completed by computing the nullspace of X λ using Gaussian elimination, in Oρ q n 3 see for example [28]. When n = Od 2, we can hence find an eigenvector in Oρ q d 6. iii We often make computations over extension fields: let K = F q d be an extension field of F = F q of degree d : then following [67, Lemma 4.1], there exists a Las Vegas algorithm which can construct K in Oρ q d 2 log 2 d time as polynomials over F, and in this framework we have that field multiplications in K can be performed in Oρ q d log d log log d = Oρ q d log d log log d time, and the inverse of a nonzero field element in K can be computed in Oρ q d 2 log d log log d = Oρ q d 2 log d log log d. Taking the worst case, we have ρ q d = Oρ qd 2 log d log log d
42 32 Chapter 2. Preliminary Results iv Finding the square root of c F can be treated as factoring the quadratic polynomial x 2 c, and so using the approach of [85, 14.14] can be completed in Oρ q log q time. Over the extension field K = F q d of F we can therefore produce square roots in Oρ q d log qd = Oρ q d d log q time Complexity and Random Elements The complexity of a Las Vegas procedure depends upon the value ɛ, input by the user, which represents the acceptable probability of returning FAIL. Almost every algorithm in this thesis requires, in the worst case, the consideration that random elements chosen may be unsuitable for use. In Section 7.1, we require a Las Vegas procedure to be nested within another: we randomly search our input group H for elements suitable for our algorithms by choosing a sample from the group and testing each element separately: if no suitable elements are found, we return FAIL. However, the suitability test is itself a Las Vegas algorithm: the following result provides a means to determine the overall complexity of a typical random search-based procedure such as this one. We denote by x the ceiling operation, which returns the least integer greater than or equal to x. Definition Let X be a set, and let S X. Suppose that Test is a Las Vegas procedure which has as input an x X and ɛ 0, 1, and returns TRUE if x S, and FALSE otherwise but may return FAIL with probability ɛ. Suppose that r ɛ is the runtime of Test which is dependent upon ɛ, suppose that P is a lower bound for S X, and define a Las Vegas algorithm FindSuitableElementT as follows where T 0 is an integer: i Choose T independent, uniformly distributed random elements of X. ii For each chosen element x, if Testx, 1 2 returns TRUE, then return x. iii If no element x in the sample passes this test, return FAIL. The procedure FindSuitableElement is a natural way to search in practice, instead of choosing T elements at random and testing each one, we test each randomly selected element before choosing the next, unless parallel computing is available to us, in which case we can test all T elements at once without great difficulty. Lemma The Procedure FindSuitableElement log ɛ log1 P/2 returns FAIL with probability at most ɛ, and has complexity log ɛ 1 OT ξ X + r 1/2 = O ξ X + r 1/2 log1 P/2 1 as in Definition Proof. There are two ways in which, for a randomly chosen x X, the procedure Test fails to return TRUE: namely, if x S, or if x X and Test returns FAIL. Thus the probability of one iteration of Test fails to return TRUE is bounded above by 1 P + P ɛ = 1 P 1 ɛ. where ɛ is the probability of failure for Test. Set ɛ = 1/2: then FindSuitableElement fails only if this occurs T times independently: that is, with probability at most P FAIL = 1 P/2 T = 1 P/2 ɛ log1 P/2 1 P/2 log ɛ log1 P/2 = 1 P/2 log 1 P/2 ɛ = ɛ..
43 2.2. Computation and Complexity 33 In the worst case, we choose T elements from X at random, and run Test on each with ɛ = 1/2: the runtime of FindSuitableElement is therefore since log a/ log b = log a/ log b = loga 1 / logb 1 log ɛ 1 OT ξ X + r 1/2 = Oξ X + r 1/2 log1 P/2 1. The complexity given in Lemma is rather ugly. Intuitively, if the probability of finding what we seek is P, then we expect to need 1/P random selections however, our analysis requires not only the expected number of choices, but sufficiently many that we can ensure a probability of failure less than ɛ. In Lemma below, we find an upper bound on the number of choices we must make which rather simplifies the analysis, but has a minimal effect on runtime. The result is based on the following: Lemma For any x > 1, we have log1 + x x. Proof. Let fx = x log1 + x. Then f x = x = x 1+x. Since 1 + x is positive for all x > 1, we have that f x has the same sign as x: that is, the function f is decreasing for x < 0, and increasing for x > 0. At 0, we have fx = 0 log 1 = 0. It follows that fx is nowhere negative for x > 1, proving the inequality. Lemma Let X be a set, and let S X. Suppose that Test is a Las Vegas procedure which has as input an x X and ɛ 0, 1, and returns TRUE if x S, and FALSE otherwise but may FAIL with probability ɛ. Suppose that r ɛ is the runtime of Test which is dependent upon ɛ, suppose that 0 P S X, and define a Las Vegas algorithm FindSuitableElement as in Definition Then FindSuitableElement 2 P log ɛ 1 is a Las Vegas algorithm with complexity O ξ X + r 1/2 1P log ɛ 1. Proof. Since P 1, we have P/2 > 1, and so by Lemma with x = P/2 log1 P/2 P/2. 1 Since both of these numbers are negative, we have log1 P/2 2 P, and so the probability of failure of FindSuitableElement 2 P log ɛ 1 is less than ɛ since we test more elements than in Lemma ; and by the same argument as in the proof of Lemma , its complexity is and the result follows. O T ξ X + r 1/2 = O ξ X + r 1/2 2P log ɛ 1, Factoring Polynomials The problem of factorising an arbitrary polynomial over a finite field is difficult: in [82], Shoup describes an algorithm which can factor a degree n polynomial deterministically with complexity worse than Oρ q n 2. However, randomised methods can do better: Kaltofen & Shoup [50] present a Las Vegas procedure with much better runtime. In the procedure Initialise, we do not require such a general result: we only need to check whether or not a polynomial has a certain form, and find its roots if so. With that in mind, we can selectively use parts of the Kaltofen-Shoup algorithm to solve the problem deterministically in subquadratic time that is, better than On 2, and then move on to the problem of finding roots where we need. The following definitions follow Kaltofen & Shoup in [50]:
44 34 Chapter 2. Preliminary Results Definition the tuple f 1,..., f r such that i Let f F [t]. Then the square-free factorisation of f over F = F q is f = f 1 f f r r = r fi i. ii Let f F [t] be square-free. Then the distinct-degree factorisation of f over F = F q is the tuple f [1],..., f [r] such that f = f [1] f [2]... f [r] = i=1 r f [i], and for each i, f [i] is a product of monic irreducible polynomials of degree i over F. Ultimately, when searching for suitable elements of H in our procedure Initialise, we require the complete factorisation of the characteristic polynomial of a candidate element: however, using the square-free and distinct-degree factorisations, we may eliminate unsuitable elements without doing so. Lemma Let F = F q, and let f F [t] be a polynomial of degree n. Then: i The square-free factorisation of f over F can be found in Oρ q n 3/2 + n log q time, by the algorithm of Yun see Knuth [55, Section 4.6] for a detailed description. ii If f is square-free, then the distinct-degree factorisation of f can be found in O ρ q n ω+1/2+1 βω 1/2 + n 1+β+o1 log q for any 0 β 1 where ω is dependent on the cost of matrix multiplication On ω, using the algorithm of Kaltofen & Shoup [50, Algorithm D]. If we use classical matrix multiplication ω = 3, then setting β = 1/2, the procedure has complexity less than Oρ q n 2.5 log q: if we use fast matrix multiplication ω < , then this procedure has complexity Oρ q n log q. iii The distinct linear factors of f[t] can be found by a Las Vegas algorithm, adapted from the Kaltofen-Shoup algorithm by Beals et al. in [11, Lemma 4.6], with complexity i=1 O ρ q n log 2 n lognq log log n log ɛ 1. Note that the first two algorithms cited in Lemma are deterministic: it is in factoring each of the f [i] that a nondeterministic procedure is needed to reduce the complexity. Remark Ultimately, the only factorisation algorithm which has any impact on our recognition procedure in Section 7.1 is the algorithm of Beals et al. iii, for we must apply it in the worst case note that while it may appear that algorithm iii runs more quickly than the others, we will be applying it to the linear factors of a polynomial over an extension field F q d, and so these runtimes are deceptive. However, we would be remiss not to mention these speedups which can be used to carve time off the algorithm in more typical cases we may determine, for example, that a matrix is not usable by finding that its square-free factorisation proves that it is not suited to our needs. In particular, we find comfort in removing the possibility of our procedures returning FAIL wherever possible, and seek to use randomised algorithms only as a last resort.
45 2.3. Estimation for Quokka Theory Estimation for Quokka Theory The Quokka Theory equation of Niemeyer & Praeger, introduced in Chapter 6 below, reduces the problem of enumerating certain subsets of classical groups to two notionally easier questions: enumeration in permutation groups and in abelian groups. In this section we present briefly the required results for estimating the proportions of matrices which we use in this thesis Permutation Groups Let Ω be a finite set, and let n = Ω. A permutation of Ω is a bijection from Ω to itself: under function composition, the set of all permutations of Ω forms a group, called the symmetric group Sym Ω of Ω. If Ω = Ω n := {1,..., n}, then we write S n := Sym Ω n, and often use the notation S n to denote the symmetric group on any set of size n where there is no ambiguity. A subgroup of Sym Ω is called a permutation group on Ω. Let G Sym Ω, and let α Ω. The orbit α G of α under G or the G-orbit of α is the set {α g g G}. The set of G-orbits forms a partition of Ω. If G has only one orbit then it is called transitive. A partition is a nonincreasing sequence λ = λ 1, λ 2,... such that λ = i=1 λ i is an integer that is, λ has only finitely many nonzero terms. If n = λ, we say that λ is a partition of n. For any permutation τ S n, we define the cycle type or cycle structure of τ as the partition of n into the set of orbit lengths ordered from longest to shortest of τ. Using cycle notation, this structure is easily seen. For example, the cycle structure of 1235 = S 5 is 2, 2, 1: we observe the convention that points omitted in our cycle notation 4 in this example are fixed by the permutation. Conjugacy classes in S n are precisely the subsets of S n having a given cycle structure: for a partition a of n we denote by C a the conjugacy class of S n of elements with cycle structure a. We are mostly concerned with determining the number of permutations in S n having long cycles. Lemma Let X be the set of n-cycles in S n. Then X S n = 1 n. Proof. Suppose we write an n-cycle τ in cycle notation, beginning with 1: then any choice of ordering of {2,..., n} gives a unique n-cycle, and every n-cycle can be written uniquely in this way. There are exactly n 1! ways to order {2,..., n} and so X n 1! = = 1 S n n! n. Corollary Let t > n/2, and let X be the set of permutations in S n containing an t-cycle. Then X S n = 1 t. Proof. We use a simple counting argument: there are exactly n t choices for the orbit of length t, t 1! possible t-cycles on that orbit, and n t! choices for the action of the permutation n! n! on the other elements of Ω. Multiplying gives a total of t!n t! t 1!n t! = t choices: since t > n/2, there is no possibility of overcounting, for no permutation can contain more than one t-cycle.
46 36 Chapter 2. Preliminary Results Let n = 2r, and consider the subgroup W = S 2 S r of the symmetric group S 2r acting on the set Ω = {1, 1, 2, 2,..., r, r}, and preserving the partition into pairs {i, ī}. Then W = Z r 2 S r, and there is a projection of W onto S r, namely the image of its action on the pairs. Call this projection ϕ: then ϕ has a kernel of size 2 r this group W arises as a Weyl group in Section 6.1 below. Now consider the preimage of a t-cycle in S r under ϕ. This preimage has size 2 r, and consists of precisely 2 r 1 elements containing a 2t-cycle in S 2r and 2 r 1 elements containing a product of 2 disjoint t-cycles in S 2r : for example when r = 3 we have ϕ 1 12 = {ab a {12 1 2, , , }, b {1, 3 3}}. That is to say, any element of the preimage of a t-cycle is the product of a and b, where a is either a 2t-cycle or a pair of t-cycles, and b acts by swapping some of the pairs {i, ī}, where i Fix a. Precisely half of these permutations contain a product of two t-cycles: the other half contain 2t-cycles. As long cycles in S n are of particular importance to us, the half containing 2t-cycles is of interest. Definition Let W = S 2 S r, and let τ W. Then τ is called a W, t-cycle if ϕτ is a t-cycle of S r. If in addition the W, t-cycle τ contains a 2t-cycle in S 2r, then τ is called a positive W, t-cycle, and if the W, t-cycle τ contains a pair of t-cycles in S 2r, then τ is called a negative W, t-cycle. Thus by the arguments above, the preimage ϕ 1 τ of a t-cycle τ S r has size 2 r, and consists of exactly 2 r 1 positive W, t-cycles and 2 r 1 negative W, t-cycles in W. Lemma Let n = 2r, t > r, and let X be the set of permutations in W = S 2 S r containing a t-cycle. Then X W W 1 t if t is even, = 0 if t is odd. This is precisely the proportion of negative t/2-cycles in W. Proof. If t is odd, then t W, since it cannot preserve the partition into pairs {i, ī}, and so X W =. If t is even then the t-cycles in S n are precisely the negative W, t/2-cycles in W. Each t/2-cycle in ϕw = S r corresponds to 2 r 1 negative W, t/2-cycles, and so by Corollary , we have and since W = 2 r r!, the result follows. X W = r! t/2.2r 1 = 1 t.2r r!, Counting In Abelian Groups Let G be a finite abelian group: then by the relevant fundamental theorem see for example the excellent reference [26, Theorem 9.17], G has the form G = Z a1 Z a2... Z ar, for integers a 1,... a r. Thus G has natural projections onto each of these r constituent cyclic subgroups note that this representation is not unique: we seek to answer questions about elements whose projections have certain properties, and so to begin we restrict our discussion to cyclic groups.
47 2.4. Arithmetic 37 Lemma Let a be a positive integer, let G = Z a, and let X be the set of elements of G of order a. Then X = ϕa > a 3 log a, where ϕ is Euler s Totient Function which counts the number of positive integers strictly less than a which are coprime to a. Proof. Let t be a divisor of a. The proportion of elements of Z a having order exactly t is ϕt, and the second inequality which we have simplified from ϕa > since log 2 > 2 3 log 2 2 a log a can be found in [68, I.1.5] citing [41], which has proved difficult for the author to source. Lemma Let a 1, a 2 be positive integers, let G = Z a1 Z a2. Let π 1, π 2 respectively be the natural projections from G onto the subgroups Z a1 1, 1 Z a2, and let X 1, X 2 be subsets of Z a1, Z a2 respectively. Let X be the set {g G i, π i g X i }. Then X G = X 1 X 2. G Proof. This follows immediately from the fact that the set X in question is precisely the set X 1 X 2, which has order X 1 X Arithmetic In this section we prove a series of results in modular arithmetic which will be used in Section 5.2 below. By Lemma , the multiset of eigenvalues of a special element of a classical group G in its action on the tensor product V F V K is the multiset Σ := {l ij i, j {1,..., d}}, where each l ij is an element of K = F q d, and is the product of a pair of eigenvalues of s in its action on V K as described in Lemma below note that the details of this are not required for the results in this section, except as motivation. This multiset has size d 2, but contains repeated values: in all cases, for example, we have l ij = l ji. The following series of results is required to prove that, for almost all values of q and d, most of the eigenspaces of a special element s in its action on V F V K are 1- or 2-dimensional and so the eigenspaces in its action on S 2 V K, 2 V K are 1-dimensional, and to characterise precisely when this condition fails to hold. The central issue in determining this is whether or not the values l ij might be the same for different choices of i, j. These results are crucial to proving Lemma , a result critical to our recognition algorithms. Note that this section proceeds with little motivation for the specifics of the results: they exist only as preliminaries for the results in Section 5.2 below. Proposition Suppose q is a prime power, that d Z with d 4, and suppose there exists j, m, n Z, with 1 j d /2, 1 m < n d and satisfying Then m, n = 1, j. 1 + q j 1 q m 1 q n 1 0 mod qd q 1
48 38 Chapter 2. Preliminary Results Proof. For all such j, m, n, we have and on the other hand, 1 + q j 1 q m 1 q n q d / = 1 + q d /2 < qd 1 q 1, 1 + q j 1 q m 1 q n 1 2 q d 1 q d 2 = qd q d q q 1 > qd 1 q 1 and so we have equality in 2.4.1, not just equivalence modulo qd 1 q 1. Thus 1 + q j 1 = q m 1 + q n 1 and reducing modulo q we have that m = 1, from which it immediately follows that n = j. We now address the hard case, where d is even and oλ is q d / We seek solutions to the equation 1 + q j 1 + ɛ m q m 1 + ɛ n q n 1 = tq d / for integer values of j, m, n, ɛ m, ɛ n, t with 1 j, m, n d /2, ɛ m, ɛ n { 1, 1}. We make an important distinction here: due to the fact that the Symmetric Square module contains the Alternating Square module when q is even see Lemma , we need not consider the case that j = 1 when q is even this corresponds to the eigenvalue l 11, which is not present in the 2 V case, by Lemma below. Lemma Suppose q is a prime power, that d Z is even with d 6, and suppose that j, m, n, ɛ m, ɛ n, t Z, with 1 j, m, n d /2, ɛ m, ɛ n {±1}, and m, ɛ m n, ɛ n, satisfy Then t {0, 1}, and if t = 1 then q = 2. Proof. Since m, ɛ m n, ɛ n, we have 2 q d /2 1 q d / q j 1 + ɛ m q m 1 + ɛ n q n q d / q d /2 1, and so 2 q d /2 1 q d /2 2 tq d / q d / q d /2 1, implying 2 q d /2 1 q d /2 2 q d /2 + 1 t 1 + /2 2 qd + 2q d /2 1. q d /2 + 1 Since the left hand side is negative and the right hand side is positive, reducing the size of the denominator, which increases the magnitude of both quantities, moves the bounds on t outwards, and hence 2 q d /2 1 q d /2 2 q d /2 < t < 1 + /2 2 qd + 2q d / q d /2
49 2.4. Arithmetic 39 The left inequality of implies Since t is an integer, this ensures t 0. t > qd /2 1 + q d /2 2 q d /2 = 1 q 1 q > 1. Similarly, the right inequality in is t < 1 + qd / q d /2 1 q d /2 = 2 q + 1 q q d / = 13 8 < 2. Since t is an integer, we have t 1, and so t {0, 1}. Moreover, if q 3 then and so if t = 1, then q = 2. t < = < 1, Lemma Suppose q is a prime power, and suppose that j, m, n, ɛ m, ɛ n Z, with 1 j, m, n d /2, ɛ m, ɛ n {±1}, and m, ɛ m n, ɛ n, satisfy for t = 1. Then, up to switching m, n, we have that q = 2, j = d 2 1, ɛ m = 1, m = d 2 1, ɛ n = 1, n = d 2. Proof. By Lemma 2.4.2, we have q = 2 we will continue to write q, though we keep in mind that 2q i = q i+1 for every i, and is 1 + q j 1 + ɛ m q m 1 + ɛ n q n 1 = q d / Now the largest value the left hand side can take is when j = d /2, ɛ m = ɛ n = 1, m = d /2 1, n = d /2, and in this case we have 1 + q j 1 + ɛ m q m 1 + ɛ n q n 1 = 1 + 2q d /2 1 + q d /2 2 = 1 + q d /2 + q d /2 2 > 1 + q d /2. The next-largest value is attained when j = d /2 1, ɛ m = ɛ n = 1, m = d /2 1, n = d /2: in this case 1 + q j 1 + ɛ m q m 1 + ɛ n q n 1 = 1 + 2q d /2 2 + q d /2 1 = 1 + 2q d /2 1 = 1 + q d /2. This is precisely the solution given. All other combinations of j, ɛ m, m, ɛ n, n give smaller values for the left hand side, and so cannot yield solutions. Lemma Suppose q is a prime power, and suppose that j, m, n, ɛ m, ɛ n Z, with 1 j, m, n d /2, ɛ m, ɛ n {±1}, and m, ɛ m n, ɛ n, satisfy for t = 0. Then one of the following holds up to switching m, n: i ɛ m = ɛ n = 1 and {1, j} = {m, n } the trivial solution 1 + q j 1 1 q j 1 = 0;
50 40 Chapter 2. Preliminary Results ii q = 3, j = 1, m = ɛ m = 1, n = 2, ɛ n = 1 that is, = 0; or iii q = 2, j = 2, m = ɛ m = 1, n = 3, ɛ n = 1 that is, = 0. Proof. Reducing modulo q for t = 0, we have 1 + q j 1 + ɛ m q m 1 + ɛ n q n 1 0 mod q Since m, ɛ m n, ɛ n implies ɛ m q m 1 ɛ n q n 1, they cannot both be 1 nor both 1, and so the left hand side of 2.4.4, when reduced modulo q, is equal to 0, 1, 2 or 3. Since q 2, only the values 0, 2 and 3 can possibly be equivalent to 0 modulo q. We treat each case separately, and refer to the value of the left hand side of after it has been reduced modulo q as the reduced left hand side of If the reduced left hand side of is 3, then q = 3, j = 1 and exactly one of ɛ m q m 1, ɛ n q n 1 = 1, say m = ɛ m = 1 and n > 1. Then yields 3 + ɛ n q n 1 = 0, forcing ɛ n = 1, n = 2: This is solution ii. If the reduced left hand side of is 2, then q = 2 and one of the terms in the left hand side is 1, say ɛ m q m 1 = 1 noting that when q is even we have j > 1. Then is 2 + q j 1 + ɛ n q n 1 = 0, forcing ɛ n = 1, and so 2 + q j 1 = q n 1. There is only one way in which 2 plus a power of 2 can equal a power of 2: namely = 4, and so j = 2, n = 3. This is solution iii. Finally, if the reduced left hand side of is zero, then j 2 and one of ɛ m q m 1, ɛ n q n 1 = 1, say m = 1, ɛ m = 1 and n > 1. Then reduces to q j 1 + ɛ n q n 1 = 0, and so ɛ n = 1, n = j. Thus m = 1, j = n, ɛ m = ɛ n = 1, the trivial solution. having exhausted all of the possible values of t given in Lemma 2.4.2, we have found every solution of equation 2.4.2: Proposition Suppose q is a prime power, that d Z is even with d 6, and suppose that j, m, n, ɛ m, ɛ n Z, with 1 j, m, n d /2, ɛ m, ɛ n {±1}, and m, ɛ m n, ɛ n, satisfy Then one of the following holds: 1 + q j 1 + ɛ m q m 1 + ɛ n q n 1 0 mod q d / i ɛ m = ɛ n = 1 and {1, j} = {m, n } the trivial solution; ii q = 2, j = d 2 1, ɛ m = 1, m = d 2 1, ɛ n = 1, n = d 2.
51 2.4. Arithmetic 41 iii q = 3, j = 1, m = ɛ m = 1, n = 2, ɛ n = 1; or iv q = 2, j = 2, m = ɛ m = 1, n = 3, ɛ n = 1. Proof. This follows immediately by combining Lemmas 2.4.2, and In the case G = SUd, q, we have that q is a square, and λ has smaller order than q d /2 + 1, and so we must treat it separately though we use similar methods, and we must solve the following equation, which bears a strong similarity to 2.4.2: note that in the Unitary case, we have d odd. 1 + q j 1 + ɛ m q m 1 + ɛ n q n 1 = t q d + 1 q Lemma Suppose q is a square prime power, that d Z is odd with d 3, and suppose that j, m, n, ɛ m, ɛ n, t Z, with 1 j, m, n d 1/2, ɛ m {±1}, ɛ n {0, ±1}, and m, ɛ m n, ɛ n, satisfy Then t = 0. Proof. Since m, ɛ m n, ɛ n, we have 2 q d 1/2 1 q d 1/ q j 1 + ɛ m q m 1 + ɛ n q n q d 1/ q d 1/2 1, and so 2 q d 1/2 1 q d 1/2 2 t q d / q d 1/ q d 1/2 1, q 1/2 + 1 implying q 1/ q d 1/2 1 q d 1/2 2 t q1/ q d 1/ q d 1/2 1. q d /2 + 1 q d /2 + 1 Since the left hand side is negative and the right hand side is positive, and we have that q 1/2 +1 < q1/2 q d /2 +1 q d /2, we have 2 q d 1/2 1 q d 1/2 2 q d /2 1/2 < t < 1 + 1/ q qd d 1/ q d /2 1/2 The left inequality of implies recall that since q is a square, we have q 4 t > qd 1/2 1 q d 1/2 2 q d 1/2 = 1 q 1 q > 1. Since t is an integer, this ensures t 0. On the other hand, the right inequality in is Since t is an integer, we have t 0. t < 1 + qd 1/ q d 1/2 1 q d 1/2 = 2 q + 1 q q d 1/ = < 1.
52 42 Chapter 2. Preliminary Results The result of Lemma permits us to apply Lemma to the Unitary case: Proposition Suppose q is a square prime power, that d Z with d 3, and suppose that j, m, n, ɛ m, ɛ n Z, with 1 j, m, n d 1/2, ɛ m, ɛ n {±1}, and m, ɛ m n, ɛ n, satisfy 1 + q j 1 + ɛ m q m 1 + ɛ n q n 1 0 mod Then ɛ m = ɛ n = 1 and {1, j} = {m, n }. Proof. This follows immediately by Lemmas and q d + 1 q In the case G = SO + d, q, we must, in proving Lemma below, solve a different equation 1 + q j 1 + ɛ m q m 1 q + 1 = tq d / The procedure is similar to the approach used above for solving 2.4.2: we bound the value of t and address each case separately. Lemma Suppose q is a prime power, that d 8, and suppose that j, m, ɛ m Z, with 1 j, m d /2, ɛ m, {±1}, satisfy Then t { 1, 0, 1}. Proof. By the conditions on j, m, ɛ m, we have the bounds and so implying q + 12 q d / q j 1 + ɛ m q m 1 q q d /2 1, q + 12 q d /2 1 tq d /2 + 1 q q d /2 1. q q d /2 1 t q q d /2 1. q d /2 + 1 q d /2 + 1 Now the left hand side is negative since q d /2 1 q 3 > 2 and the right hand side is positive, and so reducing the size of the denominator, which increases the magnitude of both quantities, weakens the bounds on t. Thus the following holds: q qd q d /2 The left inequality of implies /2 1 t q + 1 q d /2 t > 2q + 2 qd /2 q d /2 1 q d /2 > qd /2 q d /2 1 q d /2 > 1 1 q > qd / Since t is an integer, we have that t 1. Now the right inequality of gives t < q qd /2 + q d /2 1 q d /2 = q d /2+1 + q d / q < q + 1 q q < 2. Since t is an integer, we have that t 1 as required.
53 2.4. Arithmetic 43 We now treat the three cases t = 1, 0, 1 separately. Lemma Suppose q is a prime power, that d 8, and suppose that j, m, ɛ m Z, with 1 j, m d /2, ɛ m, {±1}, satisfy with t = 1. Then q = 2, d = 10, j = 3, ɛ m = 1, m = 5. Proof. If t = 1, then is 1 + q j 1 + ɛ m q m 1 q + 1 = q d /2 1. The minimum value that ɛ m q m 1 may take is q d /2 1. If this minimum is not attained, then ɛ m q m 1 q d /2 2, and 1 + q j 1 + ɛ m q m 1 q q d /2 2 q + 1 = 2q + 2 q d /2 1 q d /2 2 > q d /2 1 q d /2 2 > q d /2 1, contradiction. Hence ɛ m q m 1 = q d /2 1, and so ɛ m = 1, m = d /2, and gives 1 + q j 1 q + 1 = q d /2 1 q + 1 q d /2 1 = q d / Thus the following equation holds: q j + q j 1 + q + 2 = q d / If j = 1, then 2q + 3 = q d /2 1 and since q must divide both sides of this equation, we have q = 3 and 9 = q d /2 1, so d = 6, contradicting d 8. If j = 2, then q 2 + 2q + 2 = q d /2 1, and so again since q must divide both sides we have q = 2, which yields 10 = q d /2 1, which is a contradiction. If j > 3, then reducing modulo q 3, we have q mod q 3 which is a contradiction, and so j = 3. Then becomes q 3 + q 2 + q + 2 = q d /2 1. Since q must divide both sides, we have q = 2, and q 3 + q 2 + q + 2 = = 16 = 2 4 and so d /2 = 5, and this is the solution given corresponding to the solution = 33 = of
54 44 Chapter 2. Preliminary Results Lemma Suppose q is a prime power, that d 8, and suppose that j, m, ɛ m Z, with 1 j, m d /2, ɛ m, {±1}, satisfy with t = 0. Then q = 2, j = 1, ɛ m = 1, m = 2. Proof. If t = 0, then is 1 + q j 1 + ɛ m q m 1 q + 1 = 0, and so 1 + q j 1 + ɛ m q m 1 = 0. This forces ɛ m = 1 or else the left hand side is positive, and hence 1 + q j 1 = q m 1. The only possible solution to this that is, the only way 1 plus a power of q can itself be a power of q, is when q = 2, j = 1, m = 2 that is, when = 2. This is the solution given. Lemma Let t be an integer. Then if t is odd, we have q t t q + 1 = 1 i q t i = q t 1 q t If t is even, then q + 1 q t + 1. Proof. If t is odd, then the result is easily seen by expansion: q + 1 If t is even, then t 1 i=1 t 1 1 i q t i = 1 i q t i + q t i+1 i=1 i=1 t 2 = q t + 1 i q t i + 1 i+1 q t i + 1 i=1 = q t + 1. q t + 1 = q t q t 1 + q t = q t 1 q 1 + q t Since q + 1 q t 1 + 1, and since q + 1 does not divide q t 1 q 1, we have that q + 1 does not divide q t + 1 as required. Lemma Suppose q is a prime power, that d 8, and suppose that j, m, ɛ m Z, with 1 j, m d /2, ɛ m, {±1}, satisfy with t = 1. Then q = 2, d = 10, ɛ m = 1, {j, m } = {2, 4}. Proof. If t = 1, then is 1 + q j 1 + ɛ m q m 1 q + 1 = q d / Thus q + 1 q d /2 + 1, and so by Lemma we have that d /2 is odd and 1 + q j 1 + ɛ m q m 1 = q d /2 1 q d / ,
55 2.4. Arithmetic 45 Rearranging, we have q j 1 + ɛ m q m 1 = q d /2 1 q d / q 2 q = q 2 q d /2 3 q d / q = q 2 q d / q q + 1 and so q + q j 1 + ɛ m q m 1 = q 2 q d / q + 1 Reducing modulo q 2 yields the following equation: q + q j 1 + ɛ m q m 1 0 mod q The left hand side of this equation, when reduced modulo q 2, can take only the values 0, q 1, q, q + 1, q + 2, 2q, 1 + 2q, 3q. The only cases where any of these values can be equivalent to 0 modulo q 2 are 0; q + 2 or 2q when q = 2; and 3q when q = 3. We treat each case separately. When the reduced left hand side of is 0, we have that ɛ m = 1, m = 2, and so gives q j 1 = q 2 q d / q + 1 This can hold only if the right hand side is a power of q, which is possible only if d /2 2 = 1, which is a contradiction. When the reduced left hand side of is q + 2 or 2q, we have that q = 2, and either j = m = ɛ m = 1; or one of j, m = 2. In the former case, is 9 = q + 1 = q d /2 + 1, which implies that d /2 = 3, contradicting d 8. In the latter case, suppose that j = 2. Then is 1 + q + ɛ m q m 1 3 = q d /2 + 1 and so 8 + 3ɛ m q m 1 = q d /2. The only possible choices which yield a power of 2 on the right hand side are 8 6 = 2 leading to d /2 = 1, contradicting d 8 or = 32, which comes from the given solution j = 2, ɛ m = 1, m = 4, d = 10: switching j, m gives the second solution. When the reduced left hand side of is 3q, we have that q = 3, and j = m = 2, ɛ m = 1, and is 28 = 1 + q + qq + 1 = q d /2 + 1, and so d /2 = 3, contradicting d 8.
56 46 Chapter 2. Preliminary Results We have now exhausted all values of t, and so we have the following: Proposition Suppose q is a prime power, that d 8, and suppose that t, j, m, ɛ m Z, with 1 j, m d /2, ɛ m, {±1}, satisfy 1 + q j 1 + ɛ m q m 1 0 mod q d / Then q = 2, and one of the following holds: i d = 10, j = 3, ɛ m = 1, m = 5 that is, = 32 1; ii j = 1, ɛ m = 1, m = 2 that is, = 0; or iii d = 10, ɛ m = 1, {j, m } = {2, 4} that is, = Proof. This follows immediately by application of Lemmas 2.4.8, 2.4.9, and Proposition solves the issue of whether eigenvalues of the form l ij, l s m t can be equal, in the case d = d 2 below. In the case d = d 1, we must compare eigenvalues of the form l ij, l m : the following corollary solves this hence our addressing the harder case d = d 2 first: Corollary Suppose q is a prime power, that d 8, and suppose that j, m, ɛ m Z, with 1 j, m d /2, ɛ m {±1}, satisfy 1 + q j 1 + ɛ m q m 1 0 mod q d / Then q = 2, j = 1, ɛ m = 1, m = 2. Proof. Multiplying by q+1 implies that holds for some t, and so the result immediately follows by testing the solutions found in Proposition : of these, only ii satisfies Once again we must treat the Unitary case separately: however, we can do so in one fell swoop by combining some previous results: Corollary Suppose q is a square prime power, that d 5. Then there is no j, m, ɛ m Z, with 1 j, m d 1/2, ɛ m {±1}, satisfying 1 + q j 1 + ɛ m q m 1 0 mod q d + 1 q Proof. By Lemma with ɛ n = 0, we have that equality holds not just equivalence, that is, 1 + q j 1 + ɛ m q m 1 = 0. Then the result follows by Lemma since q is a square, the solution to Lemma when q = 2 is not included here.
57 CHAPTER 3 47 The MEAT-AXE and Primary Cyclic Matrices Given an algebra A Mn, q acting on V = F n = F n q, the irreducibility test in the MEAT-AXE algorithm, originally due to Simon Norton see [78], tests whether or not G leaves invariant a proper nontrivial subspace of V that is, if V has any proper nontrivial submodules. The more robust version of the test used by Holt and Rees in [45] does so by randomly searching for primary cyclic matrices and analysing their action on V : for the analysis, then, it is crucial to know how abundant primary cyclic matrices are. Holt and Rees in [45, pp.7-8] obtain a positive constant lower bound on the proportion of primary cyclic matrices in the full matrix algebra Mn, F, and in [33] Glasby & Praeger show that the proportion of primary cyclic matrices in Mn, F lies in the interval 1 c1 q n, 1 c2 q n for positive constants c 1, c 2. Here we focus on irreducible subalgebras of Mn, F : any such subalgebra can be identified with the full matrix algebra Mc, K over some extension field K = F q b of F, where n = bc. We prove an analogous result to the Holt-Rees estimate for these subalgebras. In this chapter we treat the case of fixed degree extensions K := F q b of a field F := F q as the dimensions c, bc in question grow unboundedly. Let P M c, q b be the proportion of matrices in Mc, q b which are primary cyclic in Mn, q relative to some irreducible polynomial f of degree b over F note that by Corollary below, this is the minimal possible degree of such an f: then P M c, q b is a lower bound for the proportion of primary cyclic matrices in Mc, q b. We begin by recalling some notation: see Section 2.1 for more detail. Notation 3.1. Let F = F q and let K be an extension field of F of degree b. The Galois group G = GalK/F Aut K is cyclic of order b, generated by the Frobenius automorphism σ : x x q, and has the F as its fixed point set. Let V = F n denote the space of n-dimensional row vectors over F, with basis {v 1,..., v n }, and let Mn, q = MV denote the full endomorphism ring of V, with elements written as n n matrices with entries in F. For a divisor b of n say n = bc, we can embed the algebra Mc, q b as an irreducible subalgebra of Mn, q = Mbc, q as in Definition Where there is ambiguity, we denote the F -vector space by V bc, q and the K-vector space by V c, q b, and we denote the action of X Mc, q b Mbc, q on V c, q b by X c,q b, and the action on V bc, q by X bc,q. 3.1 Minimal and Characteristic Polynomials of X bc,q, X c,q b We aim to count matrices X in the subalgebra Mc, q b of Mbc, q such that X bc,q is primary cyclic. To do so we derive necessary and sufficient conditions for this property which are intrinsic to their action on K c : that is to say, conditions on X c,q b. Our analysis follows that of [71, Section 5] and relies on results in Section 2.1. We investigate the relationship between the characteristic and minimal polynomials of a matrix X over the two different fields F and K. We call two polynomials g, g in K[t] conjugate if there exists τ G = GalK/F such that g τ = g. Recall from Lemma that the characteristic polynomial of X bc,q is the product of the conjugates of the characteristic polynomial of X c,q b,
58 48 Chapter 3. The MEAT-AXE and Primary Cyclic Matrices and the minimal polynomial of X bc,q minimal polynomial of X c,q b. is the least common multiple of the conjugates of the Lemma Let f Irr d q, let b 2, and let G = σ = GalK/F. Suppose that g Irrq is a divisor of f in K[t]. Then the following hold: i deg g = d/gcdb, d; ii f = lcm{g σi 1 1 i b} = gcdb,d i=1 g σi 1 ; iii g = g σi if and only if i 0 mod gcdb, d; iv f is the unique element of Irrq divisible by g in K[t]. Proof. Part i follows immediately from [63, Theorem 3.46]. For ii and iii, observe that since σ fixes the field F, the image g σ divides f σ = f, and similarly, for every i we have g σi f, so lcm{g σi 1 1 i b} divides f. Since the set {g σi 1 1 i b} is permuted under the action of σ, its least common multiple is fixed by σ, and so lies in F [t]. Then by the irreducibility of f, they are equal. Since deg f = d = gcdb, d deg g, it follows that {g σi 1 1 i b} has size gcdb, d, and the stabiliser of each g σi 1 in G is σ gcdb,d. This implies part iii and the last assertion of ii. Part iv follows from part ii. The following is an immediate consequence of Lemma Corollary Let f, b, d, G, g be as in Lemma 3.1.1, and suppose that b d. following hold: Then the i deg g = d/b; b ii f = lcm{g σi 1 1 i b} = g σi 1 ; i=1 iii For every nontrivial τ G, g g τ. We now give a description of f-primary cyclic matrices in terms of their representations over the field K. The following result uses ideas and information from the proof of [71, Lemma 5.1]. Proposition Let f Irrq, let G = GalK/F, and let X Mc, q b such that f divides c X,V bc,q t. Then X bc,q is f-primary cyclic if and only if b deg f and the following hold for some divisor g K[t] of f of degree deg f/b: i X c,q b is g-primary cyclic; and ii for every nontrivial τ G, we have that g τ g and g τ does not divide c X,V c,qb t. Proof. Let d = deg f, r = gcdd, b, and g Irrq b such that g f. Let g i = g σi 1 for 1 i r. Then by Lemma 3.1.1, f = r i=1 g i and deg g = d/r. Consider the X bc,q -invariant decomposition of V bc, q: V bc, q = V f V,
59 3.1. Minimal and Characteristic Polynomials of X bc,q, X c,q b 49 where V f is the f-primary component of V bc, q and the minimal polynomial of X bc,q Vf f α. Comparing this to the X c,q b-invariant decomposition r V c, q b = V 1 V 2 = V gi V 2, i=1 is where for each i, the minimal polynomial of X c,q b restricted to V gi is g αi i for some nonnegative integer α i, and the minimal polynomial of X c,q b restricted to V 2 is not divisible by any g i, we see that V 1 bc, q = V f, since by Lemma 3.1.1iv, the g i are the only divisors of f. By [71, Lemma 5.1], the minimal polynomial m of X bc,q restricted to V 1 bc, q is r lcm{ i=1 g αi i τ τ G} By Lemma 3.1.1ii, for each i, we have lcm{gi τ τ G} = f, and it follows that m = f max αi, where max α i = max{α i 1 i r}. Then since V f = V 1 bc, q, we have max α i = α. Now suppose X bc,q is f-primary cyclic. Recall from Definition that this is true if and only if the minimal polynomial of X Vf bc,q has degree equal to dim V f. Then αd = dim V f = dimv 1 bc, q. Suppose that more than one of the α i is positive. Then r αd b = dimv f bc, q = dimv 1 c, q b deg g αi i = degg i α i, b i=1 and so, using the fact that each degg i = d/ gcdd, b by Lemma 3.1.1, we have i=1 αd b > d gcdd, b max α dα i = gcdd, b dα b, which is impossible. Hence only one of the α i is nonzero, and so exactly one of the g i divides c X,V c,q t, say g = g b 1, so α = α 1 and V f = V g bc, q. Then αd d b = gcdd,b α, implying that b d. It follows from Corollary that r = b, r i=1 g i = τ G gτ 1, and g τ g for all τ G. Thus ii holds. Now dimv g bc, q = dim V f, and as we observed above, this equals αd. Hence dimv g c, q b = αd/b = deg g α, and so X c,q b is g-primary cyclic so i also holds. The converse is easier: if b d and g is the only divisor of f dividing c X,V c,qb t, then V f = V g bc, q, and if also X c,q b is g-primary cyclic and the minimal polynomial of X Vg bc,q is g α, then by the minimal polynomial m of X Vf bc,q is lcm{g τ α τ G}. Since g τ g for all nontrivial τ G, m = τ G gτ α, with degree αb degg = αd. On the other hand, since V g c, q b is cyclic, it has dimension equal to the degree of the minimal polynomial g α, namely α degg = αd b. Thus dimv gbc, q = αd = degm, so V f is cyclic. The next corollary follows immediately from Lemmas and 3.1.1iii. Corollary Let X Mc, q b Mn, q, where n = bc, let G = GalK/F, and let I = {f 1,..., f k } Irr b q. Then X bc,q is f i -primary cyclic for every i if and only if there exists a set I = {g 1,..., g k } Irr 1 q b with I = k satisfying the following for each i {1,..., k}:
60 50 Chapter 3. The MEAT-AXE and Primary Cyclic Matrices i g i f i, and X c,q b is g i -primary cyclic; ii for every nontrivial τ G, we have g τ i g i, and g τ i does not divide m X,V c,q b t. 3.2 A Generalised Cycle Index for Matrix Algebras Our main tool in enumerating matrices is the cycle index of the matrix algebra Mn, q, introduced by Kung [56] and developed further by Stong [84], and based on Polya s cycle index see for example [79] of a permutation group. We continue to use Notation 3.1. To each pair h, λ, with h Irrq and λ a partition of a nonnegative integer, denoted λ, with λ [0, n], assign an indeterminate x h,λ. Then the cycle index of Mn, q is the multivariate polynomial Z Mn,q x := 1 GLn, q X Mn,q h Div X x h,λx,h where x is a vector representing the set of indeterminates x h,λ occuring, Div X is the set of irreducible polynomials dividing c X,V c,qb t and λx, h is a partition of an integer uniquely determined by the structure of the action of X on the primary component V h as described in Definition below., In this section we generalise the Cycle Index of Kung and Stong to include variables associated with a finite number of irreducible polynomials which do not divide c X,V bc,q t. We will apply this more general version in our study of primary cyclic matrices. We begin by presenting the original Cycle Index Theorem: we omit the proof, for it will follow immediately from our generalised version below. In this section V = F c is viewed solely as a F -space, where F = F q. Definition Let X Mn, q, h Irrq, and let α h be the multiplicity of h in c X,V bc,q t. Then X acts on the h-primary component V h of V F with characteristic polynomial h α h, and α h deg h = dimv h F so α h = 0 if V h = 0. There is a direct sum decomposition of V h into F X-modules V h = V λ1 V λr with each V λi cyclic, such that the restriction of X to V λi has minimal polynomial h λi, and λ i λ i+1 for all i. The λ i are uniquely determined by X see [40, Theorem 11.19]. Define the partition λx, h as the ordered tuple λx, h := λ 1, λ 2,..., λ r, 0, 0,.... Then λx, h is a partition of dim V h = α h deg h, and as this partition is non-increasing, we often omit the trailing zeroes and write λ 1,..., λ r if V h {0} and := 0, 0,... if V h = {0}. The partition λx, h is the empty partition of the integer zero if h Div X, and otherwise is determined by the sizes of the blocks in the Frobenius Normal Form of X Vh. For more information on the cyclic and primary decompositions, and on λx, h, see [40]. Lemma follows immediately from the definition of λx, h: Lemma Let X Mn, q, h Irrq, and λ = λx, h. Then the following hold: i h Div X if and only if λx, h =. In particular, deg h > n implies λx, h = ; ii h Div X and X is h-primary cyclic if and only if λx, h is λ 1, with λ 1 > 0, and in this case deg h λ 1 and λ 1 / deg h is the multiplicity of h in c X,V bc,q t; and
61 3.2. A Generalised Cycle Index for Matrix Algebras 51 iii h Div X and X is not h-primary cyclic if and only if λx, h has at least two nonzero parts. Definition Let λ be a partition of an integer λ, let h Irrq, and let s = λ deg h. If λ = then define cλ, deg h, q = 1. If λ 1 then there exists a matrix X := X λ,h Ms, q b such that c X,V c,q b t = h λ, and the cyclic decomposition of K s described in Definition determines the partition λ. In this case we define cλ, deg h, q := C GLs,q X, the number of matrices in GLs, q which commute with X. This quantity depends only on deg h and λ, since all such matrices are conjugate under elements of GLs, q see again [40, GLs,q Theorem 11.19]. The number of such matrices X is cλ,deg h,q, and this holds also for λ = if we take GL0, q as the trivial group. Theorem Cycle Index Theorem. The generating function for the Cycle Index of a matrix algebra Mn, q satisfies 1 + Z Mn,q xu n = n=1 h Irrq 1 + λ x h,λh λ degh u cλ, deg h, q where cλ, deg h, q is as in Definition 3.2.3, and the sum is over all partitions λ. The Kung-Stong Cycle Index assigns, to every X Mn, q, the monomial h Div X x h,λx,h and sums over Mn, q. Given a finite subset I Irrq, we generalise by forcing, for every h I, the term x h,λx,h to appear in every expression assigned, whether or not h divides c X,V bc,q t. The reason for this generalisation will become apparent when we apply this to the proof of Lemma in Section 3.3: it permits us to ask questions about whether some fixed f Irrq divides c X t. Definition Let I Irrq be finite, and let λx, h be defined as in Definition Then the I-Cycle Index of Mn, q is defined as or equivalently Z I Mn,q x := 1 GLn, q Z I Mn,q x := 1 GLn, q X Mn,q X Mn,q h Div X h Div X I x h,λx,h x h,λx,h h I\Div X,, x h, The Kung-Stong Cycle Index is precisely the I-Cycle Index with I =. We now prove the I-Cycle Index Theorem. Theorem The I-Cycle Index Theorem. For a finite subset I Irrq and λx, h as in Definition 3.2.1, the generating function for the I-Cycle Index of Mn, q satisfies x h, + Z I Mn,q xun = 1 + λ degh u x h,λ cλ, deg h, q h I n=1 h Irrq b \I λ h I x h, + λ x h,λ λ degh u, cλ, deg h, q 3.2.3
62 52 Chapter 3. The MEAT-AXE and Primary Cyclic Matrices where the function cλ, deg h, q is as in Definition 3.2.3, and the sums on the right hand side are over all partitions λ. Proof. Our proof is an adaptation of Stong s original proof in [84]. We consider the quantities in as power series in the variables x h,λ, and treat u as a constant. Note that since I is finite, and for X Mn, q the set Div X is finite, each Z I Mn,q x on the left hand side of 3.2.3, when expressed as in 3.2.2, is clearly a sum of products of finitely many of the x h,λ. Recall that c, deg h, q = 1 for all h Irrq, and so 0. deg h u x h, = x h, c, deg h, q. Let {h i 1 i t} Irrq, and let {λ i 1 i t} be a multiset of partitions such that λ i may be if h i I, and otherwise λ i. For each i, let n i = λ i deg h i, and let n = t i=1 n i.the coefficient of t i=1 x h i,λ i on the right hand side of is t 1 u n cλ i, deg h i, q i=1 On the other hand, the coefficient of n i=1 x h i,λ i on the left hand side of is equal to 1 if n = 0, and otherwise is times the number of matrices X Mn, q having characteristic u n GLn,q polynomial t i=1 h λi i, with λx, h i = λ i for each i. Each of these matrices X is uniquely determined by the following data: i Its Primary Decomposition V = V h1 V hn has dim V hi = n i, noting that we may have λx, h i = if h i I; and ii for each primary component V hi, the partition λ i = λx hi, h i. There are exactly GLn, q n i=1 GLn i, q direct sum decompositions of V with the appropriate dimensions, and on each part V hi, there are exactly GLn i, q /cλ i, h i, q matrices X hi with λx hi, h i = λ i, as noted in Definition Thus the coefficient of t i=1 x h i,λ i on the left hand side of is which equals u n GLn, q GLn, q 1 i t GLn i, q 1 i t 3.3 Counting GLn i, q cλ i, h i, q = 1 i t 1 cλ i, h i, q un, By evaluating in Theorem for different values of x, we can enumerate subsets of Mc, q b having certain properties based on their minimal polynomials. In particular, we wish to count matrices in Mc, q b Mn, q which are f-primary cyclic for some f Irr b q by Proposition 3.1.3, b is the smallest degree for which such an f exists. We begin this section by introducing some quantities which will simplify our rather complicated calculations. Note that while the I-Cycle Index Theorem was presented for the full matrix algebra Mn, q, it may be applied directly to the irreducible subalgebra Mc, q b, provided that we treat Mc, q b in its own right, rather than as a subalgebra of Mbc, q the results in Section 3.1 permit us to do so.
63 3.3. Counting 53 Definition Define the following quantities: ω n u, q := ωu, q := n 1 uq i for {u C : u < q}; i=1 1 uq i for {u C : u < q}; i=1 Gu, q, n := 1 + λ P u, q := 1 + Su, q := n=1 n=1 u λ cλ, n, q u n ω n 1, q u n q n 1 q 1 for {u C : u < 1}; for {u C : u < 1}; for {u C : u < q}; where cλ, n, q is as defined in Definition and the sum for Gu, q, n runs over all partitions GLn, q GLn, q λ. Note that ω n 1, q =, and ω1, q = lim exists. Mn, q n Mn, q These definitions function to simplify our rather complicated calculations below. The following results will be used to help with manipulation of the generating functions: Lemma The following relations hold between the quantities in Definition 3.3.1, for u < 1, and in case iii for u < q: i ii Gu, q, 1 = P uq 1, q; h Irrq Gudeg h, q, deg h = P u, q; iii P u, q = 1 1 u P uq 1, q = i=0 1 uq i 1 ; iv Su, q b 1 u = q b 1 1 uq b ; Proof. For i, in set I =, and for all λ, set x h,λ = 0 if h t 1 and x t 1,λ = 1. Using we see that the right hand side of is equal to Gu, q, 1, while the left hand side is 1 + # unipotent elements in Mn, q u n GLn, q n=1 which by Steinberg s Theorem [20, Theorem 6.6.1] is equal to 1+ u n q nn 1 n=1 GLn,q and this equals P uq 1, q. For ii, The left hand side of the equation in ii is equal to the right hand side of if we set I = and all the x h,λ = 1. Thus by 3.2.3, using also and Definition 3.3.1, this is equal to 1 + Mn,q n=1 GLn,q un = P u, q. iii In [3, p.19] we find the equality, for u < q, 1 uq r 1 u n q nn 1/2 = 1 + n i=1 qi 1 r=1 the right hand side of which is equal to P uq 1, q. This proves the second equality of iii, and the first equality follows on substituting u for uq 1 into the second equality. Part iv is a routine geometric series calculation. n=1
64 54 Chapter 3. The MEAT-AXE and Primary Cyclic Matrices Definition i For nonempty I Irr b q, define ii Define pcbc, q b := pcbii, c, q b := {X Mc, q b X bc,q is f-primary cyclic for all f I}; I Irr b q I pcbii, c, q b ; iii Define generating functions for pcbii, c, q b and pcbc, q b : PCBII, u, q b := 1 + PCBu, q b := 1 + c=1 c=1 pcbii, c, q b GLc, q b u c pcbc, q b GLc, q b uc. Note that pcbc, q b is the set of matrices X Mc, q b such that X bc,q is f-primary cyclic for some f Irr b q: hence the name primary cyclic, degree b. Our end goal is to find and investigate PCBu, q b : to do so we compute a formula for PCBII, u, q b, depending only on the size of I and the parameters q, b, and a relationship between the functions PCB, PCBI Finding the Generating Function PCBII, u, q b Lemma Let I = {f 1,..., f k } Irr b q, with I = k, and let PCBII, u, q b be as defined in Definition Then for u < 1, we have PCBII, u, q b = P u, q b Hu, q b k, where Hu, q b := bp u, q b b 1 u b Su, q b, with P u, q b, Su, q b as in Definition Proof. Let G = GalK/F. By Corollary 3.1.4, a matrix X bc,q is f i -primary cyclic for all i if and only if there exist divisors g i of f i for each i k such that I = {g 1,..., g k } Irr 1 q b has size I = k, for each i, the g i -primary component of X c,q b is cyclic, and for 1 τ G, g τ i does not divide m X,V c,q. Fix a subset I and set b 0 if h I, and either λ = or λ λ, 0,..., with λ > 0; 0 if for some nontrivial τ G, h τ I ; x h,λ = 1 if h I, λ = λ, 0,... with λ > 0; and 1 if h τ G I τ. Let X Mc, q b : then X contributes 1 to the I -Cycle Index 3.2.1, evaluated at x, if and only if, for every g i I, λx, g i = λ, 0,..., with λ > 0, and λx, gi τ = for all nontrivial τ G; and X contributes zero otherwise. This is precisely the set of matrices which, for every g i I and nontrivial τ, are g i -primary cyclic and g τ i m X,V c,q b t. Arguing as in the proof of Theorem and in particular noting 3.2.4, the number of matrices X which contribute 1 to the I -cycle index is the same for each choice of the k-element set I. By Corollary 3.1.4, each member of pcbii, c, q b contributes 1 for a unique choice of I. Since there are b k possible I corresponding to I, the number of X Mc, q b for which evaluates to 1 with the above assignment of the x h,λ is therefore pcbii, c, q b /b k. Set
65 3.4. Results 55 I = τ G I τ. Then since by Corollary we have g τ g for every nontrivial τ G, we have I = bk. Hence, by Theorem 3.2.6, we have PCBIu, q b = b k 1 + λ degh u cλ, deg h, q b h Irrq b \I λ λ degh u cλ, deg h, q b. h I λ= λ,0,... Now since every polynomial in I is linear, and by [33, Table 1] we have that c λ, 0,..., 1, q b = q λ b 1 q b, it follows that h I λ= λ,0,... λ deg h u cλ, deg h, q b = u α q αb 1 q b h I α=1 = Su, q b k. Then by Definition and Lemma 3.3.2, and since I = bk, PCBIu, q b = b k Su, q b k Gu deg h, q b, deg h and the result follows. = b k Su, q b k h Irrq b \I h Irrq b = b k Su, q b k P u, q b P uq b, q b bk = b k Su, q b k P u, q b 1 up u, q b bk = P u, q b bsu, q b 1 u b P u, q b b k Gu deg h, q b, deg h Gu, q b, 1 h I 3.4 Results The function PCBII, u, q b counts the number of elements of Mc, q b which are f-primary cyclic for at least I distinct irreducibles of degree b in I as elements of the larger algebra Mbc, q. We seek the proportion of matrices which are f-primary cyclic for some f Irr b q. The Inclusion-Exclusion Principle yields the first main result of this Chapter, namely an explicit closed form for PCBu, q b : Theorem For any q, b, let Hu, q b = bp u, q b b 1 u b Su, q b, where Su, q b, P u, q b are as defined in Definition Then we have PCBu, q b = P u, q b 1 1 Hu, q b N bq, where N b q = Irr b q. Proof. Any X Mc, q b which is primary cyclic as an element of Mn, q relative to some element of Irr b q lies in pcbii, c, q b for at least one nonempty subset I of Irr b q. Thus for every c, pcbc, q b = I Irrq b pcbii, c, q b, 1
66 56 Chapter 3. The MEAT-AXE and Primary Cyclic Matrices and by the inclusion-exclusion principle, N pcbc, q b = 1 i+1 I Irr b q, I =i i=1 I Irr b q, I =i pcbii, c, q b, where N = Irr b q. By Lemma , the value of pcbii, c, q b depends only on I. Thus N pcbii, c, q b = pcbii i, c, q b, i for some fixed i-element subset I i of Irr b q. Hence pcbc, q b = N N 1 i+1 i i=1 pcbii i, c, q b. Since this relationship is a linear combination, the same holds for the generating functions: PCBu, q b = N N 1 i+1 i i=1 PCBII i, u, q b, and so by Lemma , writing P = P u, q b and H = Hu, q b, we have N N PCBu, q b = P 1 P i+1 H i i i=1 N N = P 1 1 H i i i as required. i=0 = P 1 1 H N Theorem allows us to easily compute using, for example, the Mathematica system [48] the Taylor coefficients of PCBu, q b, and hence values of pcbc,qb Mc,q b for small c. We summarise some small cases in Table Asymptotics as c The data suggests that the proportion has a nonzero constant term, so for every triple c, q, b the proportion is nontrivial. We turn to complex analysis to determine what happens as c. The following appears, for example, in [29], as Lemma 1.3.3: Lemma Suppose gu = a n u n and gu = fu/1 u for u < 1. If fu is analytic with a radius of convergence R > 1, then a n f1, and a n f1 = Od n for any d < R. We apply this Lemma to PCBu, q b to obtain our second main result for the chapter, namely the limit P M, q b : Theorem Let q be a prime power, and b, c positive integers with b > 1. lim c P M c, q b exists and equals P M, q b := lim P M c, q b bq b Nb q = 1 1 c 1 q b 2 ω1, qb b, Then where ω1, q b = i=1 1 q bi and N b q is the number of monic irreducible polynomials of degree b over F q.
67 3.4. Results 57 c P M c, q b 1 1 qq b b q b b2 bq2 q2 + q + 2 q 2b bq2 q q 3b + qq 4b q 4 q b b 2 b2 6 + q bq q 2b b2 3 bq 2 + b2 q 6 q2 + bq2 2 q3 q 3b b2 3 + q 2 bq + b2 q 3 q2 + bq 2 q3 q 4b b 2 b2 6 bq 2 + b2 q q 5b + bq 2 + b2 q 6 + q2 + bq2 2 q bq2 q3 3 q 6b q 2 q 7b qq 8b Table 3.4.1: The proportion of Primary Cyclic matrices for some f of degree b in Mc, q b. Observe that as q b grows, the proportions rapidly approach positive constant values. Proof. By Theorem 3.4.1, we have, writing N = N b q = Irr b q, PCBu, q b = P u, q b 1 1 Hu, q b N. Set Lu, q b = 1 u PCBu, q b. By Lemma 3.3.2iii and Definition we have Lu, q b = ω1, q b Hu, q b N. Now by Lemma 3.3.2, writing S = Su, q b and P = P u, q b for brevity, Hu, q b = bp b 1 u b S = b u q b 1 1 uq b 1 uq bi b and the infinite product is convergent for all u < q b. In particular, H1, q b exists, and It follows that H1, q b = i=1 bq b 1 q b 2 ω1, qb b L1, q b = ω1, q b H1, q b N. By Lemma , we have lim c pcbc,q b GLc,q b = L1, qb, and so and the result is proved. pcbc, q b lim c Mc, q b = ω1, q b pcbc, q b lim c GLc, q b = 1 1 H1, qb N, Asymptotics as q b Having determined the limiting proportion P M c, q b as the dimension c grows, we turn our attention briefly to the asymptotic behaviour of P M, q b as the field size grows. Throughout we assume that c is already infinity, and so we do not consider the idea that c, q b may grow together in some quirky or unpredictable way: we simply concern ourselves with the limit of P M, q b as in Theorem as q b grows. Lemma i For any x [0, 1/4, we have 1 x > 1 x x 2 > 1/2. i=1
68 58 Chapter 3. The MEAT-AXE and Primary Cyclic Matrices ii For any integer b 1 and for x [0, 1 2 ], we have that 1 2bx 1 x x 2 b. iii For any x > 1, we have x log x > x1/2. iv For any x 0, 1 2, we have 1 1 x < 1 + x + 2x2. Proof. i By the Pentagonal Number Theorem [2], we have 1 x = 1 k x k3k 1/2 i=1 k= = 1 x x 2 + x 5 + x 7 x 12 > 1 x x 2 + x 5 + x 7 x j. Now the geometric series gives j=12 xj = x12 1 x, and this is clearly less than x5 + x 7, since x < 1/4 implies x 12 1 x < 2x12 < x 5 + x 7. Hence the difference i=1 1 x 1 x x2 is positive. The second inequality follows immediately. ii Fix b 1, and let fx := 1 x x 2 b 1 2bx: we seek to prove that f is nonnegative for x [0, 1 2 ]. Now f x = b1 x x 2 b 1 1 2x + 2b = b x1 x x 2 b 1. Since x [0, 1 2 ], we have 1 + 2x 2, and 0 < 1 x x2 b 1 1, and so their product is at most 2. Thus f x 0 for all x [0, 1 2 ], and so fx is nondecreasing. Since f0 = 0, it follows that fx is nonnegative. iii Let fx = x1/2 log x. Then f x = log x 2 2x 1/2 log x 2, which, for x > 1, is zero if and only if x = e 2. Since lim x 1 + fx =, and fe 2 = e/2, and fe 4 = e 2 /4, f is decreasing for 1 < x < e 2, and increasing for x > e 2. fx fe 2 = e/2 > 1 for all x > 1, and the result follows. j=12 Thus iv Since x < 1/2, the result is equivalent to 1 < 1 x1 + x + 2x 2 = 1 + x 2 2x 3, which holds if and only if 0 < x 2 1 2x, and this last inequality holds for all x 0, }, t Lemma Let t 1, 0 < ɛ < 1. Then for all c such that c > max{1, log1 ɛ we have that c t 1 ɛ c. Proof. The result holds if and only if t log c c log1 ɛ,
69 3.4. Results 59 and so, since log c > 0 and since 0 < 1 ɛ < 1 implies log1 ɛ < 0, this is true if and only if t log1 ɛ c log c. Since, by Lemma iv, c/ log c > c 1/2 for all c > 1, if also c 1/2 t/ log1 ɛ then this inequality holds. Proposition Let P M, q b = lim c pcbc, q b Mc, q b, where b 2. Then 4b eq < P b/2 M, q b 1 e 1 < 1 + b 21 + b2 eq b + eq 2b, so that P M, q b 1 e 1 < 4e 1 bq b/2. Proof. By Theorem , we have P M, q b = 1 1 H1, q b N, with H1, q b as in above. We consider the behaviour of 1 H1, q b N as q and b grow. Since ω1, q b = i=1 1 q bi, and since q b 1/4, by Lemma i, we have Applying Lemma ii with x = q b gives Now as N := N b q = 1 b 1 q b q 2b < ω1, q b < 1 q b. 1 2bq b < ω1, q b b < 1 q b d b µdqd/b, we have 1 b qb 2q b/2 N b q qb b. Thus 1 H1, q b 1 b qb 1 H1, q b N 1 H1, q b 1 b qb 2q b/2, and so with H denoting H1, q b for simplicity: q b b log1 H N log1 H 1 b qb 2q b/2 log1 H. Using the inequality 1 1 x log x x 1, which holds for all x > 0, we have q b b H H 1 N log1 H 1 b qb 2q b/2 H. Substituting for H using and rearranging gives bq b ω1, q b b 1 q b 2 bq b ω1, q b b N log1 H 1 b qb 2q b/2 1 q b 2 ω1, qb b. Using the right inequality of and observing a geometric series gives ω1, q b b 1 q b 2 bq b ω1, q b b > 1 q b 1 q b 2 bq b 1 q b 1 = 1 q b bq b 1 = bq b, and applying Lemma iii with x = 1 + bq b gives N log1 H > bq b 21 + b 2 q 2b.
70 60 Chapter 3. The MEAT-AXE and Primary Cyclic Matrices On the other hand, we have, using the left inequality in , and since q b > 4 implies that 1 1 q b 2 < 1 3/4 2 = 16/9 < 2, that 1 b qb 2q b/2 bq b 1 q b 2 ω1, qb b = 1 2q b/2 ω1, qb b 1 q b 2 < 1 2q b/2 1 2bq b 1 q b 2 = 1 + 2q b/2 + 2b 1q b 4bq 3b/2 + q 2b 1 q b 2 < q b/2 + 2b 1q b 4bq 3b/2 + q 2b. Since 4bq 3b/2 is negative, and 2q b > q 2b, this is less than 1 + 4q b/2 + 4bq b. Thus we have proved that bq b 21 + b 2 q 2b < N log1 H < 1 + 4q b/2 + 4bq b, and so exponentiating, exp bq b 21 + b 2 q 2b < 1 H N < exp 1 + 4q b/2 + 4bq b. Now for 0 x 1 we have e x 1 + x x2 and e x > 1 x see for example [39, Lemma 2.3]. The first inequality implies that 1 H N < e q b/2 + 4bq b q b/2 + 4bq b 2 = e 1 + 4e 1 q b/2 + 4e 1 b + 3q b + 24e 1 bq 3b/2 + 12e 1 b 2 q 2b < e 1 + 4be 1 q b/2, and the second inequality gives 1 H N > e bq b 21 + b 2 q 2b = e 1 e bq b 2e b 2 q 2b. Recalling that P M, q b = 1 1 H N, the first inequality in the statement is proved by subtracting these two values from 1. The second inequality follows immediately from the first The Method of Wall We now return to the behaviour of P M c, q b as c grows: in particular we seek the rate at which it approaches the limiting value found in Theorem We apply the method of Wall see [29] to Mc, q b to prove the final main result of the chapter, which gives a useful lower bound on pcbc,qb Mc,q b for sufficiently large c, namely, the following: Theorem Let q, b > 1. Then there exists a constant kq, b such that, if c is at least max{b 1,q b /b} log3/4 2, then P M c, q b P M, q b < kq, bq bc. Moreover, we have that kq, b 8 bq b q b /b 31 q b q b 1 22b q 2b 2.
71 3.4. Results 61 Theorem shows that, for fixed q, b, the quantity P M c, q b approaches its limiting value exponentially quickly. We prove Theorem over the course of this section. The inequality we require is proved in Proposition We introduce the following notation, following Fulman in [30]: for a function Xu of a complex variable, we denote by [u c ]X the coefficient of u c in the Maclaurin Series of X. Lemma Let Xu be an analytic function of a complex variable, and let t be a positive integer. Then i for all c 1, we have [u c ] Xu = 1 u c [u i ]Xu. i=0 ii Suppose there exist constants a 1, a 2 such that [u c ]Xu a 1 a c 2, for all c 0. Then for all c 0, we have [u c ]Xu t a t 1c + 1 t 1 a c 2. Proof. i Let x i := [u i ]Xu. Then Xu 1 u = x 0 + x 1 u u + u 2 + = x 0 + x 0 + x 1 u + x 0 + x 1 + x 2 u 2 + and i follows. ii We proceed by induction on t. The result holds for t = 1 by assumption. Let x ij := [u j ]Xu i, and suppose that t 2 and that part ii holds for Xu t 1. Then Xu t = Xu t 1 Xu = x t 1,0 + x t 1,1 u + x 10 + x 11 u + c = x t 1,i x 1,c i u c, c=0 i=0 and so by induction [u c ]Xu t c = x t 1,i x 1,c i i=0 c a t 1 1 i + 1 t 2 a i 2.a 1a c i 2 i=0 = a t 1 c i + 1 t 2 a c 2 i=0 a t 1c + 1 t 1 a c 2, since c+1 j=1 jt 2 c + 1 t 1, and the result follows by induction. Lemma Let Ju, q b = 1 uq b PCBuq b, q b. Then for c 2, we have pcbc, q [u c ]Ju, q b b = Mc, q b pcbc 1, qb Mc 1, q b q bc.
72 62 Chapter 3. The MEAT-AXE and Primary Cyclic Matrices Proof. By definition of Ju, q b we have Ju, q b = 1 uq b c=1 = pcb1, qb M1, q b uqb + pcbc, q b Mc, q b uqb c c=2 pcbc, q b Mc, q b pcbc 1, qb Mc 1, q b q bc u c. The remainder of this section is devoted to finding an upper bound on [u c ]Ju, q b, and using this to prove Theorem Lemma Define Lu, q b := i=1 1 uq bi = P u, q b 1 u 1, and suppose b > 1. Then and for all c 1, we have where a L = 2q b. Lu, q b = u c=1 [u c ]Lu, q b a L q bc, 1 c q bc u c c i=1 qbi 1 Proof. The first assertion follows from [3, Corollary 2.2]. For the second, observe that [u c ]L = 1 + c k=1 1 k q bk k i=1 qbi 1 = 1 + = 1 + c k=1 1 k q bk 1 k i=1 qbi k k i=1 qbi 1 c k=1 = k k 1 i=1 qbi 1 + 1k k i=1 qbi 1 1 c c i=1 qbi 1 = 1c q bcc 1/2 c i=1 1 q bi, as all but the first and last terms of the alternating sum cancel. Now for all c, we have both q bcc 1 q b.q bc, and c i=1 1 q bi > i=1 1 q bi > 1/2 by Lemma i, and so [u c ]L 2q b.q bc. Lemma Let Ju, q b be as defined in Lemma , and suppose that b > 1. Let M q b = max{b 1,q b /b} 2: log3/4 then for c Mq b, and a J = 8 bq b 3 q b 1 2b 2q b b q b2 q b b we have [u c ]Ju, q b < a J, and hence pcbc + 1, q b Mc + 1, q b pcbc, qb Mc, q b < a Jq bc. Proof. Using Theorem 3.4.1, the observation that P uq b, q b = P u, q b 1 uq b 1, the definition of Huq b, q b from the right hand side of and Lemma 3.3.2iii, we have with
73 3.4. Results 63 N = Irr b q Ju, q b = 1 uq b P uq b, q b 1 1 Huq b, q b N [ ] = P u, q b 1 1 bqb u q b 1 uq b bi b N 1 1 u i=1 [ ] = P u, q b 1 1 bqb u q b 1 uq bi b N 1 1 u i=0 ] = P u, q b [1 1 bqb u q b 1 1 u P u, qb b N [ N ] = P u, q b 1 1 bqb q b 1 u1 ub 1 Lu, q b b, since Lu, q b = 1 up u, q b 1 by definition. By Lemma , [u c ]L a L q bc, where a L = 2q b, and hence by Lemma ii, [u c ]L b is bounded above by a b L c + 1b 1 q bc. Then [u c ] 1 u b 1 L b b b a b k Lc k + 1 b 1 q bc k k=0 b b < a b k Lc + 1 b 1 q bc b k=0 b b = a b Lc + 1 b 1 q bc b k k=0 = 2 b a b Lq b2 c + 1 b 1 q bc. Multiplication by u shifts the coefficients, so that c is replaced with c 1: that is, [u c ] u1 u b 1 Lu, q b b < 2 b a b Lq b2 +b c b 1 q bc. It follows that bq b [uc ] q b 1 u1 ub 1 Lu, q b b < bq2b q b 1 2b a b Lq b 2 c b 1 q bc, and since subtracting the function from 1 has no effect on the absolute value of any coefficients when c 1, we have for c > 1 that [uc ] 1 bqb q b 1 u1 ub 1 Lu, q b b < bqb q b 1 2b a b Lq b 2 c b 1 q bc, 2 b 1 and so by Lemma with t = b 1, ɛ = 1/4, we have, for c log3/4 and hence c > 1, [uc ] 1 bqb q b 1 u1 ub 1 Lu, q b b < bqb q b 1 2b a b Lq b 2 3q b c. 4 Again applying Lemma ii, with t = N, and since by inspection of the formula in [63, Theorem 3.25], N q b /b, we have N [uc ] 1 bqb bq q b 1 u1 ub 1 Lu, q b b b 2 qb < q b 1 2b a b Lq b b c + 1 q b b 3q b c. 4
74 64 Chapter 3. The MEAT-AXE and Primary Cyclic Matrices bq b q Then setting a J = 8 3 q b 1 2b a b L qb2 b of c and t = q b /b, we have, for c > and so b and again applying Lemma with c + 1 in place 2, that c + 1 q b /b < 1 1/4 c 1 = 4 3 3/4 c, q b b log3/4 N [uc ] 1 bqb q b 1 u1 ub 1 Lu, q b b < 3a J q b 16 c = a J 2 9q b c. 16 Now by , we may attain an expression for Ju, q b by multiplying the above equation by P u, q b : doing so, and recalling that by definition [u c ]P u, q b = ωc, q b 1 = c j=1 1 q bj, gives since c i=0 9q b 16 [u c ]Ju, q b < i < 2 when q b 4. c c 1 q bj a J 9q b 2 16 c 9q b i i=0 j=i < a J 2 < a J, i=0 The second assertion follows directly from Lemma Proposition Suppose b 2, and let a J, M q b for c > M q b, we have pcbc, q b Mc, q b Proof. By Lemma , we have M q b we have pcbc, q b Mc, q b lim n pcbc, qb Mc, q b 16 pcbc, q b Mc, q b pcbc+1,qb Mc+1,q b pcbc,qb Mc,q b c 1 < m=c c 1 m=c i be as defined in Lemma Then a J 1 q b q bc. pcbm + 1, q b Mm + 1, q b a J q bm = q bc a J < a J q bc, and so for every c > c > c c 1 q bm m=0 < q bc a J q bm m=0 = q bc 1 a J 1 q b. pcbm, qb Mm, q b Theorem follows immediately from Proposition Thus we have, for sufficiently large c, both the value P M, q b as well as a bound on the difference between this value which is roughly 1 e 1 for large fields and P M c, q b. Between this and the direct computation using the generating functions as in Table 3.4.1, we have the methods to prove that for all values of
75 3.4. Results 65 c, q, b, there is a significant proportion of primary cyclic matrices, and so the MEAT-AXE procedure is not searching in vain. This concludes our investigation of the subfamily of Primary Cyclics consisting of those matrices which are f-primary cyclic for an irreducible polynomial f of degree b that is, of least possible degree. In Chapter 6, we return to Primary Cyclics, but in that case we apply Quokka Theory and the theory of Nilpotent-Independent sets to investigate the f-primary cyclic matrices for f of large degree.
76 66 Chapter 3. The MEAT-AXE and Primary Cyclic Matrices
77 CHAPTER 4 67 The Setup and Strategy for Recognition of Classical Groups 4.1 The Modules Irreducible submodules of S 2 V and 2 V Recall from Section 2.1 that when G = GLV, both S 2 V and 2 V are irreducible F G-modules. When G is an arbitrary classical group, however, we find that in some cases, G acts reducibly. In this section we describe explicitly the irreducible F G-submodules and quotients of S 2 V and 2 V, referring frequently to Lübeck s list of irreducible representations of degree less than d 2 see [66], and describe in each case an explicit construction of the module in terms of our identification of V V with Md, q. A list of all irreducible F G-modules of degree less than d 2, in terms of our view of V V as matrices over F, for each classical group G, is given in Table Each of the modules in question, up to isomorphism, takes one of the following forms: i The Symmetric or Alternating Square Module; ii A submodule of the Symmetric or Alternating Square consisting of the zeroes of a G- invariant linear form; or iii A quotient of one of i or ii by a 1-dimensional subspace fixed pointwise by the action of G. The goal of this Section is to prove that in all cases we may pretend that our module W is, in fact, the Symmetric or Alternating Square, in the sense that we prove that any such module takes one of the above forms, and hence by Lemmas , and , almost all of the equations which govern the action of a group element on S 2 V, 2 V hold for W. Remark We do not, prove explicitly that the F G-modules we construct are, in fact, irreducible: this is proved by Lübeck in [66, Theorem 5.1]. In the proof of this theorem, Lübeck constructs explicitly the same irreducible modules we do in this section: we provide the constructions for illustrative purposes. Remark Note that in the paper of Magaard, O Brien and Seress [67], the adjoint module, a submodule of V V where V is the dual space is considered. In all but the Linear and Unitary cases, the module V is self-adjoint, and so this case is contained within the case we consider, namely submodules and quotients of V V. In most cases where the adjoint module arises and has irreducible constituents not considered here, the Magaard-O Brien-Seress algorithm is sufficient. Only in Unitary case with d even does it not. Moreover, in [67], the twisted module V V τ is considered, where τ represents the twisting of the action of g by a field automorphism. We do not consider these case here, and consider only the modules of dimension strictly less than d 2 1, that is, the Alternating and Symmetric cases. Notation Throughout this section we will use the following notation: Let F = F q, let p be the characteristic of F, and recall for G GLV the F G-module isomorphism
78 68 Chapter 4. The Setup and Strategy for Recognition of Classical Groups ρ : V V Md, q with respect to the action A g T Ag for g G as described in Section In each case we consider a standard copy of G, defined as the subgroup of GLd, q stabilising a specific bilinear or quadratic form on V. Recall that {E ij 1 i, j d}, where E ij is the matrix with a 1 in the i, j position and zeroes elsewhere, forms a basis of Md, q = V F V ρ. Recall from the proof of Lemma that S 2 V ρ is the set of all symmetric matrices in Md, q, and 2 V ρ is the set of skew-symmetric matrices when q is odd, and the set of symmetric matrices with zeroes on the main diagonal when q is even The Linear Case A r and Unitary Case 2 A r Lemma In the linear case G = SLd, q and the unitary case G = SUd, q 2, both S 2 V and 2 V are irreducible submodules of V V. Proof. This follows directly from the 3rd and 4th lines of [66, Table 2] and by [66, Theorem 5.1] The Symplectic Case C r Definition Let d = 2r and let d/2 J Sp = E i,d i+1 E d i+1,i. i=1 For example, when r = 2, we have J Sp = The standard copy of the Symplectic Group of rank r or of dimension d is defined Spd, q := {g SLd, q g T J Sp g = J Sp }. That is, Spd, q is the stabiliser Stab SLd,q J Sp of J Sp in the action of SLd, q on Md, q described in Definition Recall that 2 V ρ is the space of matrices A Md, q with zeroes on the main diagonal satisfying A = A T. Lemma The subspace J Sp Md, q is contained in 2 V ρ, and is fixed pointwise under the action of G = Spd, q. Proof. Since J Sp is a skew-symmetric matrix with zeroes on its main diagonal when q = 2, J Sp is also symmetric, J Sp 2 V ρ. The invariance follows immediately from the definition of Spd, q: for every g G, we have J g Sp = gt J Sp g = J Sp. Lemma Let G = Spd, q. Then g G if and only if g T G.
79 4.1. The Modules 69 Proof. Since J 2 Sp = I 2r, we have J 1 Sp = J Sp, and so Since G is inverse-closed we have g T G. g G g T J Sp g = J Sp g 1 J 1 Sp g T = J 1 Sp g 1 J Sp g T = J Sp g T G. Lemma Let g = g ij be a matrix in GLd, q. Then g Spd, q if and only if the following hold for all i, j: d/2 1 if l = d k + 1, k < l, g ki g l,d i+1 g k,d i+1 g li = 1 if l = d k + 1, k > l, i=1 0 otherwise. Proof. We expand the following using Lemma : d/2 J Sp = g T J Sp g = g T E i,d i+1 E d i+1,i g d/2 i=1 = g T E i,d i+1 g g T E d i+1,i g i=1 d/2 = g ik g d i+1,l g d i+1,k g il E kl i=1 = k,l k,l d/2 g ik g d i+1,l g d i+1,k g il E kl. i= Comparing coefficients with J Sp = d/2 i=1 E i,d i+1 E d i+1,i, we have that g ij Spd, q if and only if the following holds for all k, l: d/2 1 if l = d k + 1, k < l, g ik g d i+1,l g d i+1,k g il = 1 if l = d k + 1, k > l, i=1 0 otherwise. By Lemma , g T reversed, and the Lemma is proved. We exhibit another F G-submodule of 2 V ρ. Spd, q and so the same equations hold when the subscripts are Lemma Let V = F d, let G = SpV, and define the map T Sp : 2 V ρ F by d/2 T Sp A = a k,d k+1. k=1 Then T Sp is a G-invariant F -linear form on 2 V, and hence N Sp := ker T Sp is an F G-submodule of 2 V ρ, of dimension d 2 1.
80 70 Chapter 4. The Setup and Strategy for Recognition of Classical Groups Proof. Since by Lemma , g T Ag = i,j,k,l a ijg ik g jl E kl, we have d/2 T Sp g T Ag = a ij g is g j,d s+1 s=1 i,j = d/2 a ij g is g j,d s+1 i,j s=1 = d/2 a ij g is g j,d s+1 g js g i,d s+1. i<j s=1 By , most terms are zero, and we are left with d/2 T Sp g T Ag = a i,d i+1 a d i+1,i = T Sp A. i=1 Thus T Sp invariant under the action of G. It is also clearly F -linear, so by Lemma , the kernel N Sp of T Sp is G-invariant. The map T Sp has rank 1 its image is F, and so its kernel N Sp is a codimension 1 subspace of 2 V ρ, and hence has dimension d 2 1. Lemma Let V = F d, let G = Spd, q, let p = charf, and let J Sp, N Sp be as defined in Lemma and Definition respectively. Then J Sp N Sp if and only if p r. Proof. Recall that J Sp = d/2 i=1 E i,d i+1 E d i+1,i. By definition of T Sp, we have 1 when i d/2, j = d i + 1; T Sp E ij = 0 otherwise. It follows that T Sp J Sp = d/2 i=1 1 0 = d/2 = r, and this is zero if and only if p r. Lemma Let G = Spd, q, let r = d/2, let p = charf, and let J Sp, N Sp be the F G- modules defined in Lemma and Definition respectively. Then the irreducible F G-modules which are submodules and/or quotients of Md, q of dimension strictly greater than 1 are, up to isomorphism, the following: i The Symmetric Square Module S 2 V := S 2 V ρ, of dimension d+1 2 ; ii The Reduced Alternating Square Module 2 V := N Sp /N Sp J Sp, of dimension d 2 2, when p r, and d 2 1, when p r. Proof. This follows by inspection lines 14, 15 of Table 2 in [66], and by the proof of [66, Theorem 5.1] The Orthogonal Cases B r, D r, 2 D r q odd Suppose that q is odd. We treat the three Orthogonal cases together: the treatment is similar to the Symplectic case above, though the results differ.
81 4.1. The Modules 71 Definition For each r 2 there are three Orthogonal Groups, one for each value of ɛ {, +, }, defined as follows. Let α be a primitive element of the field F = F q. Then if ɛ =, set d = 2r + 1 and x = 1. If ɛ = ±, then set d = 2r, and set x ɛ as follows: 1 if q 1 mod 4 and 1 if q 3 mod 4 and x + = x = α otherwise. α otherwise. Now define J O,ɛ := x 1 ɛ = E 12 + E x 1 ɛ E 33 + d 2 1 E ii. i=4 Note that since q is odd, 2 has an inverse in the field F. Then the Orthogonal Group of Rank r and Type ɛ is defined O ɛ d, q := {g GLd, q g T J O,ɛ g = J O,ɛ }. That is, O ɛ d, q is the stabiliser of J O,ɛ in the action of GLd, q on Md, q. Orthogonal Group of Rank r and Type ɛ is defined The Special SO ɛ d, q = O ɛ d, q SLd, q. Lemma Let G = O ɛ d, q, and let g GLd, q. Then g G if and only if gj 1 g T = J 1. Proof. Since G is a group, g G if and only if g 1 G, or equivalently g T Jg 1 = J. Then taking the inverse of both sides gives g T Jg 1 1 = J 1 which is equivalent to gj 1 g T = J 1. We derive from this, as in the symplectic case, a condition on the entries of g. Lemma Let ɛ {0, +, }, let G = O ɛ d, q, and let g = g ij GLd, q. Then g G if and only if 1 if {k, l} = {1, 2}, d 2x ɛ if k = l = 3, g k1 g l2 + g k2 g l1 + 2x ɛ g k3 g l3 + 2g ki g li = i=4 2 if k = l 4, 0 otherwise. Proof. It is straightforward to see that J 1 O,ɛ := 0 0 2x ɛ = E 12 + E x ɛ E 33 + d 2E ii. i=4
82 72 Chapter 4. The Setup and Strategy for Recognition of Classical Groups Hence gj 1 O,ɛ gt = g E 12 + E x ɛ E 33 + d 2E ii i=4 = ge 12 g T + ge 21 g T + 2x ɛ ge 33 g T + 2 = d k=1 r=1 g T d ge ii g T i=4 d g k1 g r2 + g k2 g r1 + 2x ɛ g k3 g r3 + 2 d g ki g ri E kr. i=4 By Lemma , we have gj 1 O,ɛ gt = J 1 O,ɛ, and the result follows immediately by comparing the coefficients of E kr. Once again we define a form T on Md, q, and show that its zeroes form a G-invariant subspace of Md, q. Lemma Let ɛ {0, +, }, let G = O ɛ d, q, and define a form T O,ɛ : Md, q F by T O,ɛ A = a 12 + a x ɛ a 33 + d 2a ii, where A = a ij. Then T O,ɛ is a G-invariant F -linear form on Md, q, and the subspace i=4 N O,ɛ := ker T O,ɛ = {A Md, q T O,ɛ A = 0} is an F G-submodule of Md, q of dimension d 2 1. Proof. For any g G we have g T Ag = a ij g ik g jl e kl. So the coefficient of e kl in g T Ag is i,j a ijg ik g jl. Hence T O,ɛ g T Ag = i,j i,j,k,l a ij g i1 g j2 + g i2 g j1 + g i3 g j3 + d 2g is g js. Then each term in the sum is precisely a ij multiplied by the left hand side of , and so using Lemma we have T O,ɛ g T Ag = a 12 + a 21 2x ɛ a 33 + s=4 d 2a ss, and this is precisely the definition of T O,ɛ A. Hence T O,ɛ is G-invariant. s=4 As N O,ɛ is the set of zeroes of a single linear equation, it is the kernel of a rank 1 map, and so its dimension is d 2 1. Thus by Lemma , since q is odd and hence V V = S 2 V 2 V, it suffices to show that 2 V N O,ɛ so that the missing dimension comes from S 2 V. Let A be a skew-symmetric matrix. Then the diagonal entries of A are zero, and hence d T O,ɛ A = a 12 + a x ɛ a a ii = a 12 + a 21. Since A is skew-symmetric, we have a 12 + a 21 = 0, and so T O,ɛ A = 0 and 2 V N O,ɛ as required. i=4
83 4.1. The Modules 73 Lemma Let ɛ {0, +, }, let G = O ɛ d, q, let p = charf, and let J O,ɛ, N O,ɛ be as defined above. Then J O,ɛ N O,ɛ if and only if p d. Proof. Let J ij denote the i, j-entry of J O,ɛ. Then recalling the definition of J O,ɛ from Definition , we have T O,ɛ N O,ɛ = J 12 + J x ɛ J 33 + d i=4 = x ɛ 2 1 x 1 ɛ + = 3 + and hence T O,ɛ J O,ɛ = 0 if and only if p d. d 1 = d, 4 2J ii d 22 1 i=4 Lemma Let ɛ {0, 1, 1}, let q be an odd prime power, let r 2, let d = 2r + 1 if ɛ = 0 and 2r otherwise, and let G = SO ɛ d, q. Let J O,ɛ, N O,ɛ be the F G-modules defined in Lemma and Definition respectively. Then the irreducible F G-submodules of Md, q of dimension strictly greater than 1 are, up to isomorphism, the following: i The Reduced Symmetric Square Module S 2 V := N O,ɛ N O,ɛ J O,ɛ, of dimension d+1 2 2, when p r, and d+1 2 1, when p r. ii The Alternating Square Module 2 V := 2 V ρ, of dimension d 2. Proof. This follows by inspection of lines 8, 9, 10, 20, 22, 23 of Table 2 in [66] and by [66, Theorem 5.1] The Orthogonal Cases q even When q is even, the Alternating Square 2 V is an irreducible submodule of the Symmetric Square S 2 V, and so we consider only submodules of 2 V. Note that if d is odd, then we have SOd, q = Spd 1, q see for example [38, Theorem 14.2], and so we omit this case. When d is even, we may still recycle our work in the Symplectic case, although we do not quite have isomorphism. The Orthogonal Group O ɛ 2r, q is defined as the stabiliser of a quadratic form Q ɛ : V F q : that is, O ɛ 2r, q = {g GL2r, q x V, Q ɛ x = Q ɛ xg}. There are two choices, up to equivalence, for the form Q ɛ, one for each ɛ { 1, +1}. The standard copies in GAP of the Orthogonal groups are the stabilisers of the forms Q ɛ, defined
84 74 Chapter 4. The Setup and Strategy for Recognition of Classical Groups by Q ɛ x = xj ɛ x T, where J 1 = J 1 = α α where α is a primitive element of the field F. That is, J 1 := r i=1 E 2i 1,2i, J 1 = J 1 + αe 33 + αe 44. In both cases, the quadratic form Q ɛ gives rise to a symmetric bilinear form x, y = Q ɛ xy Q ɛ x Q ɛ y, which is left invariant by G. That is to say, SO ɛ d, q is contained in a Symplectic Group note that as we have defined the groups, the Symplectic Group in which SO ɛ is contained is not the Symplectic Group defined above, but a conjugate. Thus, by Lemma , there is a G-invariant linear form T O,ɛ on V V. Thus we have proved the following: Lemma Let G = SO ɛ d, q, for d, q even, let r = d/2, let p = charf, and let J Sp, N Sp be the F G-modules defined in Lemma and Definition respectively. Let φ be the module isomorphism taking the natural module of Spd, q to the module containing the natural module of G. Then the Reduced Alternating Square Module φ 2 V N Sp :=, N Sp J Sp of dimension d 2 2, when p r, and d 2 1, when p r, is up to isomorphism the unique irreducible F G-module of dimension strictly between d and d Summary We summarise the results of Lemmas , , & in Table The following result plays a crucial role in our procedures. Case d G q S 2 V dims 2 V 2 V dim 2 V A r r + 1 SLd, q any S 2 V d V d 2 2 A r r + 1 SUd, q any S 2 V d V d 2 B r 2r + 1 SO N d, q odd O d+1 N O J O,ɛ 2 1 δp r 2 V d 2 C r 2r Spd, q any S 2 V d+1 N Sp d 2 N Sp J Sp 2 1 δp r D r 2r SO + N d, q odd O d+1 N O J O,ɛ 2 1 δp r 2 V d 2 φ N d even Sp N Sp J Sp 2 1 δp r 2 D r 2r SO N d, q odd O d+1 N O J O,ɛ 2 1 δp r 2 V d 2 φ N d even Sp N Sp J Sp 2 1 δp r Table : Irreducible F G-Modules of Moderate Degree Proposition Let G be a Classical group, and let W be one of the F G-modules listed in Table Then the kernel of the action of G on W is {±1}.
85 4.2. Constructive Recognition of F G-modules 75 Proof. By Lemma , the kernel of the action of G on V V is {±1}, and the induced actions on S 2 V, 2 V have the same kernel {±1} by only a slight modification of the proof of Lemma Now any W listed in Table is constructed from S 2 V or 2 V by either the restriction to a submodule or a quotient by a 1-dimensional fixed-point space. Then by Lemmas , , the kernel of the action of G on W is an abelian normal subgroup of order a power of charf ; our Classical groups have no such subgroup other than the trivial subgroup. 4.2 Constructive Recognition of F G-modules In this section we describe the precise form our constructive recognition procedure for an F G-module listed in Table will take, for some Classical group G over F. In broad terms, our goal is to produce a scheme for rewriting an arbitrary n n matrix g H = X as a d d matrix ϕ 1 g, an element of the preimage of g under a homomorphism ϕ from a copy of G inside GLd, q into H. and a subgroup of GLd, q, where d is the dimension of the natural module of G. In this section we describe explicitly our input, our output, an outline of the procedure with subroutines described, but details omitted, and all assumptions made, and provide a summary of notation. Note that this section may contain forward references and lack detail; it is intended as a motivational summary of what is to come. Our procedure comes in two components: Initialise and FindPreimage, which differ in the detail from case to case but retain similar structure and goals. See Table for a summary of the components of Initialise and FindPreimage as well as forward references to the details of each component The Groups The groups we consider are the Classical Groups over finite fields. Specifically, we deal with subgroups of the Special Linear Group SLd, q which stabilise a form on V = F d. These groups are described in detail in Sections 4.1 and 6.2. In summary, the groups we consider are the Special Linear Group SLd, q, the Special Unitary Groups SUd, q, the Symplectic Groups Spd, q, and the Special Orthogonal Groups SO ɛ d, q for ɛ { 1, 0, 1} The Procedure Initialise Here we give a summary of Initialise. The basic input of Initialise is motivated by the conventions of recognition algorithms, and is as follows: i A set X of n n matrices with entries in F = F q, such that H := X is isomorphic to a classical group G with natural dimension d, where the action of H on W := F n is isomorphic to one of the modules S 2 V, 2 V as in Table ; and ii An acceptable probability ɛ 0, 1 of failure. In addition, we assume the existence of an oracle which returns, in constant time ξ H, a random element of H, and we assume that we can perform several standard functions as in Lemma , such as matrix multiplication over any finite field; computation of the characteristic polynomial of a matrix and finding its irreducible linear factors over any finite field; and computing the eigenvalues and eigenvectors of a matrix including over field extensions as in Definition The procedure Initialise will not run for certain small values of d, since there is not enough
86 76 Chapter 4. The Setup and Strategy for Recognition of Classical Groups Name Input Output Deterministic? Section FindSpecialElement X s, Σ LV 7.1 LabelEigenvalues s, Σ F W Yes 8.1, 9.1 FindConstants F W C LV 8.2, 9.2 FindChangeOfBasisMatrix F W, C B LV 7.3 FindPreimage F W, C, g, B a ij LV 8.3, 9.3 Table : The Pieces of Initialise and FindPreimage G Symmetric Square Alternating Square Conditions SLd, q 3 3 SUd, q 3 5 d odd 4 6 d even Spd, q 6 8 d even SO d, q 6 8 d even SO d, q 7 9 d odd SO + d, q 8 10 d even Table : Minimum values of d for Initialise information coarsely speaking, we produce a system of d 4 equations and d 2 unknowns, and for small values of d, this system cannot be solved. Table provides the minimum value of d for which the procedures can run in each case. The blockage in these cases and in certain cases for small q for certain modules is caused by the exceptions to the arithmetic results in Section 2.4. In practice, we use existing usually black box algorithms to handle these cases. The output of Initialise is the following a data structure which provides necessary input for FindPreimage. Specifically: i A basis F W of W K satisfying the conditions of Lemma in the Symmetric Square case, or of Lemma in the Alternating Square case; ii A set C of constants c ij as in the conclusion of Lemma in the Symmetric Square case, or of Lemma in the Alternating Square case; and iii A Change-Of-Basis matrix B as described in Section 7.3. Initialise is a Las Vegas algorithm, and so it may return FAIL, with probability less than ɛ. We break the procedure into several natural subroutines, namely FindSpecialElement, LabelEigenvalues and FindConstants. Table provides a summary of their input, output, and runtime. The basic structure of Initialise is as follows. i Search in H = X for a special element s, as described in Chapter 5. If no special element is found, return FAIL. ii Compute a labelling of the eigenvalues of s in its action on W K in accordance with the
87 4.2. Constructive Recognition of F G-modules 77 structure described in Lemmas 5.3.1, 5.4.1, and from this labelling choose a basis of W K of eigenvectors satisfying the conditions of Lemma or iii Choose a random g H satisfying certain conditions described in Section 7.2, and use it to find the constants c ij. Theorem Let X GLn, q be a set of matrices generating a classical group G = Classd, q, such that the module W defined by the action of H is either the Reduced Symmetric Square Module or the Reduced Alternating Square Module as in Table Let d be as in Table , and suppose that d is at least the minimum value given in Table Suppose that G {Spd, 3, SO ɛ d, 3} in the Symmetric Square case, and G {Spd, 2, SO ɛ d, 2} in the Alternating Square case. Define the procedure Initialise as follows, for ɛ 0, 1: i Let s be the special element output by FindSpecialElement Algorithm 7.1, and Σ its eigenvalues; ii Using the procedure LabelEigenvalues the appropriate choice of Algorithm 8.1, 8.2, 8.3, 9.1, 9.2, or 8.3 depending on the case and the value of d, label the eigenvalues Σ and produce the basis F W ; iii Using the procedure FindConstants Algorithm 8.4 in the Symmetric Square Case, or Algorithm 9.4 in the Alternating Square Case, produce the constants C ; iv Produce the change-of-basis matrix B as in Section 7.3. Then assuming that Conjecture holds in the Symmetric Square case, and Conjecture holds in the Alternating Square case, Initialise returns a special element s H, basis F W, a set C of constants in L as described in Lemma in the Symmetric Square Case, or in Lemma in the Alternating Square Case, and a change-of-basis matrix B; or FAIL with probability less than ɛ; and has complexity O ξ H d 2 log 2 q log ɛ 1 + ρ q d 8 log 3 q log ɛ 1 + ρ q d d 7 log q + d 6 log 3 q log ɛ 1. In particular, using the relationship ρ q d has complexity = Oρ qd 2 log d log log d as in , Initialise O ξ H d 2 log 2 q log ɛ 1 + ρ q d 9 log d log log d log q + d 8 log d log log d log 3 q log ɛ 1. Proof. By Lemma , the procedure FindSpecialElement is a Las Vegas algorithm with complexity O ξ H + ρ q d 3 d 3 + log q + ρ q d d3 log 2 d logdq d 2 log 2 q log ɛ 1. By the appropriate Proposition , , , , or , the procedure LabelEigenvalues is a deterministic algorithm with complexity O ρ q d d4 d 3 + log q. By Proposition in the Symmetric Square case, and Proposition in the Alternating Square case, the procedure FindConstants is a Las Vegas algorithm with complexity O ξ H + ρ q d dd5 + log q log ɛ 1.
88 78 Chapter 4. The Setup and Strategy for Recognition of Classical Groups Finding the change-of-basis matrix B requires, in the worst case, the use of the algorithm of Glasby, Leedham-Green & O Brien, which runs much more quickly than any of the other steps see [35]. The result follows by adding these complexities note that in combining these complexities we weaken our estimates in the name of simplicity: for example, we might simplify Od 2 + d log q to Od 2 log q The Procedure FindPreimage This procedure finds the inverse of the group homomorphism ϕ defined by the procedure Initialise and the special element s found therein: given g H and the data returned by an instance of Initialise, it returns an element a of the preimage ϕ 1 g ϕ 1 H GLV the full preimage is {±a}, having size 2 when q is odd. Input: A basis F W for W K, and a set {c ij } of constants in F q d, satisfying certain conditions, a change of basis matrix B as described in Section 7.3, a matrix g GLW, and an acceptable probability of failure ɛ. Output: An element a of the preimage ϕ 1 g GLV, or FAIL. In short, FindPreimage takes the output of Initialise, and a matrix g GLW, and rewrites g in its action on a d-dimensional F -vector space. Then existing algorithms for recognition in the natural dimension may be used to recognise the results in the sense that we can find a straight-line program reaching ϕg from standard generators of G GLV. Theorem Let X GLn, q be a set of matrices generating a classical group G = Classd, q, such that the module W defined by the action of H is either the Reduced Symmetric Square Module or the Reduced Alternating Square Module as in Table Let d be as in Table , and suppose that in the Linear and Unitary cases, we have d 4; in the remaining cases with d = d we have d 6; and in the remaining cases with d = d 1, d 2 we have d 8. Suppose that G {Spd, 3, SO ɛ d, 3} in the Symmetric Square case, and G {Spd, 2, SO ɛ d, 2} in the Alternating Square case. Define the procedure FindPreimage as follows, for g H, ɛ 0, 1: i Find the matrix a ij or a ij using Algorithm 8.5 in the Symmetric Square case, or 9.6 in the Alternating Square case; ii Return the conjugate a ij B. Then assuming that Conjecture holds in the Symmetric Square case, and Conjecture holds in the Alternating Square case, FindPreimage returns, for a fixed homomorphism ϕ from a conjugate of the standard copy of G in GLd, q, an element of the preimage ϕ 1 g; and is a Las Vegas algorithm with complexity O ξ H + ρ q d d6 log q log ɛ 1. In particular, using the relationship ρ q d = Oρ qd 2 log d log log d as in , FindPreimage has complexity O ξ H + ρ q d 8 log d log log d log q log ɛ 1. Proof. By Proposition in the Symmetric Square case, and Proposition in the Alternating Square case, finding a ij can be performed by a Las Vegas algorithm with complexity O ξ H + ρ q d d2 d 4 + log q log ɛ 1,
89 4.2. Constructive Recognition of F G-modules 79 and conjugation by B is equivalent to matrix multiplication of d d matrices over F q d : taking classical matrix multiplication we have a cost of Oρ q d d3, and so this does not add to the overall complexity.
90 80 Chapter 4. The Setup and Strategy for Recognition of Classical Groups
91 CHAPTER 5 81 Special Elements and their Eigenstructure 5.1 Special Elements and their Eigenstructure on V K In this section we define precisely what we mean by a Special Element of a Classical Group it differs slightly in each case, though the general idea is the same, and detail the properties we exploit for our recognition procedure. All special elements are ppdd, q, d -elements of G see Definition below for some d, and so we begin, after fixing some notation which is used for the rest of the section without further reference, with a description of ppd-elements and some of their important properties. Notation Let q be a prime power, and let F = F q. Let G be a classical group of rank r over F with natural dimension d. For d d fixed and given specifically in Table , let K = F q d, and let σ be the generator of GalK/F which raises elements to their qth power. Let V be the natural F G-module of d-dimensional row vectors over F, and let V K = V F K as in Definition Singer Cycles and ppd-elements in GLd, q A Singer Cycle in GLd, q is an element s 0 of order q d 1: this is the largest order possible [12]. Singer Cycles are well studied objects: the cyclic subgroups of GLd, q generated by Singer Cycles are all conjugate and the centraliser of a Singer Cycle s 0 is C GLd,q s 0 = s 0. While classical groups do not always contain Singer Cycles, they do contain elements which behave in similar ways. To discuss these elements we require the notion of a primitive prime divisor: Definition Suppose q is a prime power, and d an integer. Then a prime r is called a primitive prime divisor of q d 1 if the following hold: i r q d 1; and ii for 1 e < d, we have r q e 1. Remark Note that the definition of a primitive prime divisor of q d 1 is slightly ambiguous: the primitivity of a prime divisor of q d 1 depends upon the pair q, d, and not only on the integer q d 1. For example, 13 is a primitive prime divisor of 9 3 1, for 13 divides = 728, but divides neither = 81 nor = 8. However, 13 is not a primitive prime divisor of 3 6 1, since = 26 = To wit, primitive prime divisors of q ab 1 are always primitive prime divisors of q a b 1, but the converse is not true in general. By a theorem of Zsigmondy [90], there is a primitive prime divisor of q d 1 for every pair d, q, except when d, q = 6, 2 or 2, p for p a Mersenne prime. To deal with those cases, we say that 9 is a ppd of 2 6 1, and that 4 is a ppd of p 2 1 for a Mersenne prime p. For details, see for example [75, Section 2.2]. Lemma Suppose that r is a primitive prime divisor of q d 1. If r q t 1, then d t. Proof. This follows immediately from [74, Lemma 4.1i]. Definition Let s G GLd, q, and let d d. Then s is called a ppdd, q; d - element of G if os is divisible by a primitive prime divisor of q d 1.
92 82 Chapter 5. Special Elements and their Eigenstructure Many of the useful properties of Singer Cycles are inherited by ppdd, q; d-elements: indeed, each such element s is a power of a Singer Cycle s 0, and we have C GLd,q s = s 0 [47, Satz II.7.3]. Moreover, a ppdd, q; d -element s, for d < d, restricts to a ppdd, q; d -element in its action on a unique s-invariant d -dimensional subspace of F d note that in all cases we consider, we have d > d/2. For our purposes, the most important property of ppd-elements is the following, which is proved in [75, Lemma 5.1]: Lemma Let G GLd, q, let d/2 < d d, and let s G be a ppdd, q; d -element. Then there is a unique s-invariant subspace U of V such that the restriction s U is irreducible, and the characteristic polynomial of s has a unique irreducible divisor of degree d The Eigenstructure of Singer Cycles and ppd-elements in V K While a Singer Cycle has no eigenvalues in F by Lemma , its characteristic polynomial is irreducible of degree d, the eigenstructure of its action on V K is rich. In this case we are dealing with the full group GLd, q, and so we have d = d. Recall that res d i is the unique integer j such that j i mod d and 1 j d. Lemma If s GLd, q acts irreducibly on V, then the eigenvalues of s on V K are {l i = λ qi 1 1 i d} for some λ K with oλ = os, and there exists a basis E s, V := {e i 1 i d} of V K such that for all i, we have that e i is the eigenspace of l i, and e σ i = e i+1 for every i [1... d 1], and e σ d = e 1. That is, we have e σ i = e res d i+1, for all i. Proof. By Lemma , since the characteristic polynomial of s is irreducible of degree d over F, the eigenvalues of s in V K which are precisely the roots in K of the characteristic polynomial of s are as asserted and the l i are distinct. Thus there are d eigenspaces of dimension 1 in V K. Fix an eigenvector e 1 of l 1, such that the first nonzero entry of e 1 is 1, and for each i with 2 i d, set e i := e σi 1 1. Then for each i, since s GLV F and is therefore fixed under the action of σ: e s i = e σi 1 s 1 = e 1 s σi 1 = l 1 e 1 σi 1 = l qi 1 1 e i = l i e i, and so e i is an l i -eigenvector for s as required. Moreover, since l q d = λqd = λ = l 1, we have that e σ d e 1, that is, e σ d is a scalar multiple of e 1. Since e 1 has its first nonzero coordinate equal to 1, and since the action of σ fixes this coordinate, we have e σ d = e 1. We may write e σ i = e i+1 with indices computed modulo d to denote the kind of cyclic permutation arrangement found in Lemma : that is, to indicate that e σ i = e res d i+1. If we are restricted to a Classical Group G GLV, we cannot always find an element acting irreducibly on V : our solution is to search for elements in G which act irreducibly on a largedimension subspace as in table below. The following corollary follows immediately: Corollary Let s GLd, q, and suppose that there exists a d -dimensional s-invariant subspace U of V, such that s acts irreducibly on U. Then s U has d eigenspaces of dimension 1 in U K, and there exists a basis E = {e i 1 i d } for U K such that e σ i = e res d i+1.
93 5.1. Special Elements and their Eigenstructure on V K 83 Case d G d os U os U Conditions q d 1 A r r + 1 SLd, q d q 1 q d A r r + 1 SUd, q d d odd, q square q + 1 d 1 q d + 1 q d even, q square B r 2r + 1 SOd, q d 1 q d / C r 2r Spd, q d q d/2 + 1 D r 2r SO + d, q d 2 q d /2 + 1 q D r 2r SO d, q d q d/2 + 1 Table : Properties of Special Elements of Classical Groups Special Elements in Classical Groups In this section we define rigorously special elements of classical groups of each type, and describe the eigenstructures of their actions on the natural module with extended scalars V K see Definition In particular, we outline the structure of a well-behaved basis E s, V K for V K associated with a special element of G an extension of the the basis E of Corollary The definitions vary from case to case, although the spirit is the same: we seek elements with as many 1-dimensional eigenspaces in their actions on S 2 V K and 2 V K as possible. Recall by Lemma that the eigenvalues of s on S 2 V K, 2 V K are the products of the eigenvalues on V K : thus we seek ppdd, q; d -elements with d as large as possible in the group, and with sufficiently large order that the transition to the tensor product does not result in the loss of too many eigenvalues that is, large enough order that the set of products l ij = l i l j does not contain too many repeated values. Definition Let G be a classical group of rank r as in one of the lines of Table Let d be as in the 4th column of the corresponding line of Table Then an element s G is a special element if s is a ppdd, q; d -element, and there exists an s-invariant decomposition V = U U such that dim U = d ; and os U is a multiple of the value in the 5th column of the appropriate line of Table ; and if d < d, then os U is equal to the value in the 6th column of the appropriate line of Table Remark We frequently refer to our procedure Initialise searching for special elements, but this is not strictly true. Special elements, as in Definition , are merely a subset of the elements that Initialise can use: in practice we may use elements with smaller order than the values in Table i.e. certain powers of special elements, but the proof that such elements are suitable is neither interesting nor illuminating, and adds no value to the analysis of our algorithms. In practice we may essentially replace the appearances of q d /2 + 1 in Table with q d /2 +1 gcdq+1,q d /2 +1. The subspace U in Definition is uniquely determined by s as in Lemma , and s acts irreducibly on U; if d < d, then s also acts irreducibly on U as a consequence of the condition on os U. Our ultimate goal is a basis for V L, where L is an extension field of F satisfying certain conditions: we define these conditions below.
94 84 Chapter 5. Special Elements and their Eigenstructure Definition Let G be a classical group over F, let V be the natural F G-module, and let σ be the Frobenius automorphism of K/F, where K is an extension of F of degree d as given in Table Let F := {f i 1 i d} be a basis for V : then we say F satisfies the almost-σ-relations for V if the following hold: i for 1 i d 1, we have that fi σ = f i+1, and fd σ f 1 ; ii if d = d 1, then fd σ = f d; and iii if d = d 2, then fd 1 σ = f d and fd σ = f d 1. If, in addition, we have fd σ = f 1, then we say F satisfies the σ-relations for V. We now describe explicitly the eigenstructure of a special element on V K : Lemma Let G be a classical group of rank r, let d be as in Table , and let s G be a special element. Let K = F q d, and let U, U be as in Definition Then the eigenvalues of s in its action on V K are {l i 1 i d}, where λ qi 1 for 1 i d, l i = µ qi d 1 for d < i d, for λ, µ K satisfying oλ = os U, oµ = os U as in the 5th and 6th entry respectively in the appropriate line of Table Moreover, there exists a basis E := E s, V := {e i := e s,v,i 1 i d} such that E satisfies the σ-relations for V as in Definition Proof. If d = d then the result follows immediately from If d = d 1, then by definition we have os U = 1, and so s acts trivially on U : that is, l d = 1 is an eigenvalue of s, and the result follows from this fact and Corollary , since s acts irreducibly on both U and U. If d = d 2, then s U GL2, q has order q + 1, and hence acts irreducibly on U since all proper nontrivial subspaces of U are 1-dimensional, and the result follows by applying Corollary separately to U and U. 5.2 The Eigenstructure of Special Elements on V V K In this section we determine the precise eigenstructure of a special element s G in its action on V V K, which will enable us to determine the eigenstructure of s in its action on both S 2 V K and 2 V K. This eigenstructure is the crux of the procedures Initialise and FindPreimage. The results in this Section depend heavily on the arithmetic results in Section 2.4. Recall from Definition that res d i is the unique integer j such that 1 j d and j i mod d.
95 5.2. The Eigenstructure of Special Elements on V V K Coincident Eigenvalues l ij There are two ways in which eigenvalues l ij may coincide: there are cases where l ij = 1 leading to a nontrivial fixed-point space of s, or where two eigenvalues are not 1, but coincide anyway. Lemma Let λ K, let l i = λ qi 1 for 1 i d, and let l ij = l i l j for 1 i j d. Suppose that the order of λ is divisible by a primitive prime divisor r of q d 1, and suppose for some integer t, not divisible by r, we have l t ij = 1. Then d is even, and j i = d /2. Proof. If l t ij = 1 then 1 = +q j 1 λtqi 1 = λ tqi 1 1+q j i, so r divides tq i q j i. Since r does not divide q or t, and r is prime, it follows that r 1 + q j i, and so r divides q 2j i 1. Since r is a primitive prime divisor of q d 1, by Lemma , it follows that d 2j i, and since 0 < j i < d, we have 0 < 2j i < 2d and so 2j i = d. Lemma , with t = 1, is crucial in determining when a special element s has an eigenvalue 1. Note that Lemma provides only a necessary condition, and not a sufficient condition: in some cases, the eigenvalue l 1,d /2+1 may be different from 1 this is dependent on the order of λ. The existence of a fixed-point space of s in its action on V V K may seem unfortunate in the sense that it guarantees that not all of the eigenspaces can be 1-dimensional. However, in Section 4.1 we observe that, in all but the Unitary and Linear cases, G has fixed points in its action on MV = V V, and so these products equalling 1 is inevitable we cannot hope to find an element in G with no fixed points. We now address coincidences among the l ij other than those corresponding to fixed points: we seek pairs i, j, m, n such that l ij = l mn. We begin by exploiting the symmetry of the problem under the action of σ as much as we can. Lemma Suppose q is a prime power, and d an even integer with d 6. Let K = F q d, let λ K, and suppose that oλ is divisible by a primitive prime divisor r of q d 1. Let l i = λ qi 1, for 1 i d, and let l ij = l i l j for 1 i, j d. Suppose that there exist integers i, j, m, n {1,..., d }, satisfying Then at least one of the following holds: i {i, j} = {m, n}; l ij = l mn. ii d is even, and res d j i = res d n m = d /2; iii There exist integers k, s, t, α, with 1 k d /2, and 1 s < t d, such that l 1k = l st, and l ij = l qα 1k. Proof. Suppose that res d j i = res d n m. Then setting t = res d i m, we have res d m + t = i, and res d n + t = res d n m + i = res d j i + i = j, and so l qt mn = l m+t,n+t = l ij = l mn. Thus l qt 1 mn = 1. If t = d then m = i, j = n and we are in case i. Assume t < d : then since r is a primitive prime divisor of q d 1, r does not divide q t 1. Then by Lemma with t = q t 1, we have res d n m = res d j i = d /2.
96 86 Chapter 5. Special Elements and their Eigenstructure Suppose, then, that res d j i res d n m and so at least one of res d j i, res d n m is distinct from d /2, and at least one is distinct from d. If res d j i = d /2, or if res d n m = d then we switch {i, j} with {m, n}: then we may assume that res d n m d and res d j i d /2. If res d j i < d /2, then setting k = res d j i + 1, and α = res d i 1, we have = l q i+1 ij = l 1,j i+1 = l 1k. Set {s, t} = {res d m i + 1, res d n i + 1}, with s, t ordered so that s < t. Note that since res d n m d we have m n, implying that s t. l qd α ij Then l ij = l qα 1k, l 1k = l qd α mn = l q i+1 mn = l m i+1,n i+1 = l st, and k = res d j i + 1 < d /2 + 1, and so k d /2 as required. On the other hand, if res d j i > d /2, then res d i j < d /2. Then setting k = res d i j + 1, and α = res d j 1, we have l qd α ij = l q j+1 ij = l i j+1,1 = l 1k. Set {s, t} = {res d m j + 1, res d n j + 1} with s, t again ordered so that s < t. Then we have l ij = l qα 1k, l 1k = l st, and again k d /2 as required. The upshot of Lemma is that in our search for coincidences l ij = l mn among our eigenvalues, we may assume without loss of generality that i = 1, j d /2 and m n. The first case we deal with is the Linear Case, where the order of λ is largest: Lemma Suppose q is a prime power, and d an integer with d 4. Let λ K have order a multiple of qd 1 q 1. Let l i = λ qi 1, for 1 i d, and let l ij = l i l j for 1 i j d. Suppose there exist integers j, m, n such that l 1j = l mn, with 1 j d /2 and 1 m < n d, with j 1 if q is even. Then 1, j = m, n. Proof. If l 1j = l mn then λ 1+qj 1 q m 1 q n 1 = 1, and hence 1 + q j 1 q m 1 q n 1 0 mod qd 1 q 1. This is a solution of equation 2.4.1, and the result then follows from Proposition In all other cases things are more difficult, and most of Section 2.4 is devoted to aspects of the proof that the l ij rarely coincide. Lemma Suppose q is a prime power, and d an integer with d 6. Let λ K have order q d / Let l i = λ qi 1, for 1 i d, and let l ij = l i l j for 1 i j d. Suppose there exist integers j, m, n such that l 1j = l mn, with 1 j d /2 and 1 m < n d, with j 1 if q is even. Then one of the following holds: i {1, j} = {m, n} the trivial coincidence; ii q = 2, j = d /2 1, m = d 1, n = d; iii q = 2, j = 2, m = d /2, and n = 3; iv q = 3, j = 1, m = 2, and n = d /2 + 1.
97 5.2. The Eigenstructure of Special Elements on V V K 87 Proof. Solutions to l 1j = l mn are integer solutions to the equation 1 + q j 1 q m 1 q n 1 0 mod oλ, for 1 j d /2, and 1 m n d. Now if m > d /2, then q m 1 = q m d /2 1 q d /2 + 1 q m d /2 1, and so q m 1 q m d /2 1 mod q d / The same argument holds if n > d /2, and so we have 1 + q j 1 + ɛ m q m 1 + ɛ n q n 1 0 mod q d /2 + 1, where m m when m d /2 = m d /2 when m > d /2, 1 when m d /2 and ɛ m = +1 when m > d /2, and n, ɛ n are defined likewise. Note that while m may be equal to n, since m < n, we have ɛ m, m ɛ n, n, and all of j, m, n lie between 1 and d /2. That is, j, m, ɛ m, n, ɛ n is a set of solutions to equation 1 + q j 1 + ɛ m q m 1 + ɛ n q n 1 0 mod q d / This is precisely in Section 2.4, and the result follows by Proposition Note here that the solutions ii, iii in Lemma are essentially the same coincidence: one can be obtained from the other by switching 1, j with m, n and cycling under the action of σ. We now address the Unitary case: note here that d is always odd see Table , and so d /2 is not an integer. Thus when Lemma allows us to assume that j d /2, we may strengthen this to assume that j d 1/2. Lemma Suppose q is square a prime power, and d an odd integer with d 3. Let λ K have order q d +1 q+1. Let l i = λ qi 1, for 1 i d, and let l ij = l i l j for 1 i j d. Suppose there exist integers j, m, n such that l 1j = l mn, with 1 j d 1/2 and 1 m < n d, with j 1 if q is even. Then 1, j = m, n. Proof. Define ɛ m, m, ɛ n, n as in the proof of Lemma above: then by an identical argument, since oλ q d /2 + 1 where q d /2 denotes q d, we have that q m 1 ɛ m q m 1 modulo oλ, and so a solution to l 1j = l mn corresponds to a solution to 1 + q j 1 + ɛ m q m 1 + ɛ n q n 1 0 mod q d + 1 q + 1. This is precisely equation in Proposition 2.4.7, and the result follows. We now address the possibility of coincidence which are specific to the cases d = d 2, d 1. Lemma Suppose q is a prime power, and d an even integer with d /2 3. Let K = F q d, let λ K, and let µ K have order q + 1. Let l i = λ qi 1, for 1 i d, let
98 88 Chapter 5. Special Elements and their Eigenstructure m 1 = µ, m 2 = µ q, and let l ij = l i l j for 1 i, j d. Suppose that there exist integers i, j, k {1,..., d }, and t {1, 2}, satisfying l ij = l k m t. Then there exist integers r, s, n, α, with 1 r d /2, 1 s d, 1 n 2, such that l 1r = l s m n, and l ij = l qα 1r. Proof. Set r = min{res d j i + 1, res d i j + 1}: if r = res d j i + 1, then we have l qi 1 1k = l 1+i 1,k+i 1 = l ij, and so setting α = d i + 1, we have that l 1k = l qα ij, and l 1k = l qα ij = l km t qα = l resd k+αm res2t+α. Then setting s = res d k + α, n = res 2 t + α, the result holds. When r = res d i j + 1, the result holds by an identical argument, with α = d j + 1. Lemma Suppose q is a prime power, and d an even integer with d /2 3. Let λ K have order q d /2 + 1, and let µ K have order q + 1. Let l i = λ qi 1, for 1 i d, let m i = µ qi 1 for 1 i 2, and let l ij = l i l j for 1 i j d. Suppose there exist integers j, s, t such that l 1j = l s m t, with 1 j, s d and 1 t 2, with j 1 if q is even. Then q = 2, and one of the following holds: i d = 10, j = 3, ɛ m = 1, m = 5; ii j = 1, ɛ m = 1, m = 2; or iii d = 10, ɛ m = 1, {j, m } = {2, 4}. Proof. Since oµ = q + 1, we have that l q+1 1j = l s m t q+1 = l q+1 s, and so λ 1+qj 1 q+1 = λ qs 1 q+1 : that is, 1 + q j 1 q s 1 q mod q d / As in the proof of Lemma , set s s when s d /2 = s d /2 when s > d /2, 1 when s d /2 and ɛ s = +1 when s > d /2, and we have that ɛ s q s 1 q s 1 modulo q d /2 + 1, implying 1 + q j 1 + ɛ s q s q 0 mod q d / This is precisely equation , and the result follows by Proposition Lemma Suppose q is a prime power, and d an even integer with d /2 3. Let K = F q d, and let λ K. Let l i = λ qi 1, for 1 i d, let m 1 = µ, m 2 = µ q, and let l ij = l i l j for 1 i, j d. Suppose that there exist integers i, j, k {1,..., d }, satisfying l ij = l k. Then there exist integers r, s, α, with 1 r d /2, 1 s d, such that l 1r = l s, and l ij = l qα 1r. Proof. This follows immediately by the same proof as Lemma , replacing µ with 1.
99 5.2. The Eigenstructure of Special Elements on V V K 89 Lemma Suppose q is a prime power, and that d is an even integer with d 6. Suppose that λ K has order q d /2 + 1, let l i = λ qi 1 for 1 i d, and let l ij = l i l j. Suppose there exist integers j, s, t such that l 1j = l s, with 1 j d /2, 1 s d, with j 1 if q is even. Then q = 2, j = 1, ɛ m = 1, m = 2. Proof. By an identical argument to the proof of Lemma above without raising to the q + 1st power, we have that 1 + q j 1 + ɛ s q s 1 0 mod q d /2 + 1 where s, ɛ s are as defined in the proof of Lemma Then j, ɛ s, s, q, d are solutions to the equation in Section 2.4. Then the result follows from Corollary Once again we must treat the Unitary case separately. Lemma Suppose q is a square prime power, and that d is an odd integer with d 3. Suppose that λ K has order a multiple of q d +1 q+1, let l i = λ qi 1 for 1 i d, and let l ij = l i l j. Then there do not exist integers j, s, t such that l 1j = l s, with 1 j d 1/2, 1 s d. Proof. Again by an identical argument to the proof of Lemma , we have that 1 + q j 1 + ɛ s q s 1 0 mod q d + 1 q + 1 where s, ɛ s are as defined in the proof of Lemma Then j, ɛ s, s, q, d are solutions to the equation in Section 2.4. Then the result follows from Corollary Lemma Let G be a classical group as in one of the lines of Table , and let s G be a special element as defined in Definition , with eigenvalues {l i 1 i d} as in Lemma , and let E s, V = {e i 1 i d} be as defined in Lemma Suppose that in the Linear and Unitary cases, we have d 4; in the remaining cases with d = d we have d 6; in the cases d = d 1, d 2 we have d 8. Then the eigenvalues of s in its action on V V K are {l ij := l i l j 1 i j d}, and the following hold: i if l ij = 1 then either d = d 1 and i = j = d; or d = d 2 and {i, j} = {d 1, d}; or i d, j d, res d j i = d /2, and G is Symplectic or Orthogonal; ii for each pair i, j with 1 i j d, the l ij -eigenspace of s in its action on V V K contains the tensor products e i e j, e j e i ; and iii the l ij -eigenspace of s in its action on V V K is precisely e i e j, e j e i, except when l ij = 1 and G {Spd, q, SO ɛ d, q; or when G {Spd, 3, SO ɛ d, 3}, and res d j i {d, d /2 + 1}; or when G {Spd, 2, SO ɛ d, 2} and res d j i {1, d /2 2}.
100 90 Chapter 5. Special Elements and their Eigenstructure Proof. i By Lemma , if l ij = 1 and 1 i j d then d is even and res d j i = d /2. Since when d = d 2 for µ K of order q + 1 we have that µ 2 1, the only other possible pairs giving l ij = 1 are those listed. In the Linear case we have that os > qd 1 q 1, and so l 1,d /2+1 = λ qd /2 +1 1, and so 1 is not an eigenvalue. In the Unitary case, we have that d is odd, and so l ij = 1 only if i = j = d, and so in this case the eigenspace of 1 is precisely e d e d. In all other cases when l ij = 1, the eigenspace of 1 has dimension greater than 1. ii This follows from Lemma ; and iii This follows from i, and from Lemma and Lemma in the Linear case; Lemma and Lemmas , in non-linear cases with d = d; Lemma and Lemmas , when d = d 1; and Lemma and Lemma when d = d The Action of a Special Element on the Symmetric Square S 2 V K Having completely described the action of a special element on V V K, we turn to the submodules S 2 V, 2 V as defined in Section The eigenstructure of a special element s action on S 2 V K and 2 V K can be read directly from Lemma using Lemma : the remainder of this chapter is devoted to providing concrete links between the action of an arbitrary g G on various bases for the modules with which we concern ourselves. Lemma Let G be a Classical Group as in one of the lines of Table , and let s G be a special element as defined in Definition , with eigenvalues {l i 1 i d} as in Lemma , and let E s, V = {e i 1 i d} be as defined in Lemma Define where E s, S 2 V = {e s,s2 V,ij 1 i j d}, e s,s 2 V,ij = e i e j + 1 δ ij e j e i. Suppose that in the Linear and Unitary cases, we have d 4; in the remaining cases with d = d we have d 6; and in the remaining cases with d = d 1, d 2 we have d 8. Then the eigenvalues of s in its action on S 2 V K are {l ij := l i l j 1 i j d}, and the following hold: i if l ij = 1 then i d, j d and the condition in the 5th column of the appropriate line of Table holds; ii for each pair i, j, the l ij -eigenspace of s contains e s,s2 V,ij; and iii the l ij -eigenspace of s is precisely e s,s 2 V,ij, except when either l ij {Spd, q, SO ɛ d, q}; or G {Spd, 3, SO ɛ d, 3}. = 1 and G Proof. This follows immediately from Lemma and note that the exceptional cases in Lemma for q = 2 do not apply here as q is odd.
101 5.3. The Action of a Special Element on the Symmetric Square S 2 V K 91 Lemma Let G be a classical group, let W be an F G-module isomorphic to S 2 V, and let App W be the set of pairs i, j of integers such that, for any special element s G, the l ij -eigenspace of s in its action on W has dimension 1. Then: i if G {SLd, q, SUd, q}, then d = d and App W = {i, j 1 i j d}; ii if G {Spd, q, SO d, q}, q 5, then d = d and i, j App W if and only if 1 i j d, and j i d/2; iii if G {SO d, q for d odd}, q 5, then d = d 1 and i, j App W if and only if either 1 i j d, and j i d /2; or 1 i d and j = d; iv if G = SO + d, q, q 5, then d = d 2 and i, j App W if and only if either 1 i j d, and j i d /2; or 1 i d and d < j d; or d < i d and j = i. Note that in all cases, if 1 i j d, j i d /2, we have i, j App W. Proof. This follows immediately from Lemma Note that while the eigenvalues and eigenvectors depend upon s, the set of pairs i, j App W does not. While the notation e s,s2 V,ij is cumbersome, there are very many modules and bases to consider, and it is sometimes needed for clarity. We will often simply write e ij when there is no ambiguity. Definition Let G be a classical group as in one of the lines of Table , let s G be a special element as in Definition , and for 1 i j d, let e ij := e s,s2 V,ij be as defined in Lemma Let σ be the Frobenius automorphism of the extension K/F. Suppose that F = {f ij 1 i j d} is a basis for S 2 V K. Then F is said to satisfy the σ-relations for S 2 V if the following hold: i for 1 i j d 1, fij σ = f i+1,j+1; ii for 1 i d 1, fid σ = f 1,i+1, and f σ d d = f 11; iii if d = d 1 then, for 1 i d, fi,d σ = f i+1,d, and fdd σ = f dd; iv if d = d 2 then, for 1 i d, fi,d 1 σ = f res d i+1,d, fi,d σ = f res d i+1,d 1, and fd 1,d 1 σ = f dd, fd 1,d σ = f d 1,d, and fdd σ = f d 1,d 1. If F has a partial labelling {f ij i, j App W } F, then we say that F satisfies the σ-relations for App W if the relations hold for all i, j App W. Lemma Let G be a classical group as in one of the lines of Table , let s G be a special element as defined in Definition , and let E s, S 2 V = {e ij := e s,s2 V,ij 1 i j d} as defined in Lemma Then E s, S 2 V satisfies the σ-relations for S 2 V. Proof. The relations follow immediately from the fact that, by Lemma , the σ-relations for V as in Definition hold for {e i 1 i d}. Lemma Let G be a classical group as in one of the lines of Table , let s G be a special element as defined in Definition , let W = S 2 V, and let E = E s, S 2 V = {e ij 1 i j d} be as in Definition
102 92 Chapter 5. Special Elements and their Eigenstructure Suppose that there exists a basis F S2 V := F s, S 2 V, E := {f ij := f s,v,e,ij 1 i j d} for W K such that, for every pair i, j with 1 i j d, we have that f s,v,e,ij e ij, and F S2 V satisfies the σ-relations for S 2 V as defined in Lemma Then there exists an extension field L of K of degree at most 2, a basis F V = F s, V, F S 2 V := {f i 1 i d} for V L, and a set C = C s, F S2 V, F V := {c ij 1 i j d} L, such that F V satisfies the almost-σ-relations for V, and for 1 i j d, we have f ij = c ij f i f j + 1 δ ij f j f i. Moreover, we have that c 11 = 1; and if d < d, we have c 1j = 1 for j > d. Proof. Let E V := {e i } be as defined in Lemma Then since each f ij is a scalar multiple of e ij, there exist constants c ij K such that f ij = c ij e ij. Suppose that for every i, we set f i = a i e i, for a i L. Then for every i, j, we have that f i f j = a i e i a j e j = a i a j e i e j, and so f i f j + 1 δ ij f j f i = a i a j e i e j + 1 δ ij e j e i = a i a j e ij. For 1 i j d, set c ij := c ij a ia j 1 L: then c ij f i f j + 1 δ ij f j f i = c ije ij = f ij. This holds for all choices of {a i }, and so we have a great deal of freedom. By Lemma , we may choose a square root x of c 11 in the extension field L/K. For 1 i d, set a i = x qi 1 : then a 2 1 = x 2 = c 11, and so c 11 = c 11a 2 1 = 1, and when i < d, we have fi σ = a i e i σ = x qi 1 q e i+1 = a i+1 e i+1 = f i+1. When i = d, we have that e σ d = e 1, and so fi σ = a q d f 1 f 1, and so the almost-σ-relations hold for i < d. The other relations follow in a similar way. If d < d, then for j > d, set a j = c 1j a 1 1 : then a 1a j = c 1j, and we have c 1j = c 1j a 1 a j 1 = 1 as required. The purpose of Lemma is to allow a safe transition between an action of g G on S 2 V K to an action on V L although we will later show that this action remains within the confines of V K. However, it depends on our ability to find the constants c ij, and this is not necessarily possible. There is, at one point in the procedure, a square root to be taken, and so a choice must be made, and a sign ambiguity introduced. The following result permits us to choose either path without regret. Lemma Let G be a classical group as in one of the lines of Table , let s G be a special element as defined in Definition , let W = S 2 V, and let E S2 V = {e ij 1 i j d} be as defined in Lemma Suppose that there exists F S 2 V := {f s,v,e,ij 1 i j d}, L, F V := {f i 1 i d}, C s, F S2 V, F V = {c ij 1 i j d} as defined in Lemma Then define a basis F V := {f i 1 i d} and a set of constants C = C s, F S2 V, F V := {c ij 1 i j d} L, as follows:
103 5.3. The Action of a Special Element on the Symmetric Square S 2 V K 93 i for 1 i d, let f i = 1 i+1 f i ; and for i > d let f i = f i ; and ii for 1 i j d, let c ij := 1j i c ij ; for 1 i d, j > d, let c ij := 1i+1 c ij ; and for all other i, j let c ij := c ij. Then for 1 i j d, we have f ij = c ij Proof. Observe that, for 1 i j d, we have c ij f i f j + 1 δ ij f j f i f i f j + 1 δ ij f j f i = 1 2j+2 c ij f i f j + 1 δ ij f j f i, and since 2j + 2 is even, this is precisely f ij. When i d, j > d, we have c ij f i f j + 1 δ ij f j f i = 1 2i+1 c ij f i f j + 1 δ ij f j f i, which again is equal to f ij since 2i + 1 is even. If d < i j d then the assertion holds trivially by the definitions. Lemma allows us to err in our search for the values of the c ij, so long as we accidentally find c ij : in that case, FindPreimage will return the action of g G with respect to F V instead of F V, a mistake which is irrelevant to us, and by Lemma above, is unavoidable. Note that we are only permitted to make one mistake: we must compute all of either C or C, and we cannot mix and match. Lemma Let G be a classical group as in one of the lines of Table , let s G be a special element as defined in Definition , let W = S 2 V. Let E S2 V = {e ij 1 i j d} be as defined in Lemma 5.3.1, and let F V, C be defined as in Lemma 5.3.5, and let F V, C be as defined in Lemma Then for 1 i j d 1, we have c q ij = c i+1,j+1 and c ij q = c i+1,j+1, and hence for 1 i d, we have c ii = c ii = 1. Moreover, for every g G, and for all pairs i, j, k, l App W, we have the following, where κ ij,kl := g fijf kl, a ij = g fif j, a ij = g f i f j : i The Basic Equations in the Symmetric Square Case hold for κ ij,kl, C, a ij, C, a ij : κ ij,kl = c ij a ik a jl + 1 δ ij a il a jk = c ij c kl c a ik a jl + 1 δ ija il a jk kl ii for 1 i, j d 1, we have a q ij = a i+1,j+1, a ij q = a i+1,j+1. Proof. Since fi σ = f i+1 for all 1 i d 1, and since δ ij = δ i+1,j+1, we have, for 1 i j d 1, that = c ij f i f j + 1 δ ij f j f i σ f σ ij = c q ij f i+1 f j δ i+1,j+1 f j+1 f i+1 = c q ij c 1 i+1,j+1 f i+1,j+1, and so c q ij = c i+1,j+1 since, by definition, we have that f σ ij = f i+1,j+1. Since, by Lemma 5.3.5, c 11 = 1, we have that c ii = 1 for all i. The relations on c ij follow immediately since
104 94 Chapter 5. Special Elements and their Eigenstructure c ij = 1j i c ij. i follows immediately from Lemmas and For ii, since f σ i = f i+1 for 1 i d 1, and since f σ i f 2,..., f d for i d, we have that f gσ i = d a ij f j j=1 for some v f 2,..., f d. On the other hand f σg σ = d 1 j=1 a q ij f j+1 + v, d i = f g i+1 = d 1 a i+1,j f j = a i+1,j+1 f j+1, j=1 and so, since f gσ i = f σg i, by equating coefficients of f j+1 for 1 j d 1, we have a q ij = a i+1,j+1 as required. A similar argument shows that the relations hold among the a ij, since f i σ = 1 i+1 σ f σ i = 1 i+1 f i+1 = f i+1. Lemma Let G be a Classical Group, let V be the natural F G-module, and let W be an F G-module such that W = S 2 V ϕ, where S 2 V j=0 is as in Table , and ϕ is an isomorphism of F G-modules, and let ν be a homomorphism of F G-modules such that S 2 V S 2 V ν. Let s G be a special element, as in Definition , let {l ij 1 i j d } be the eigenvalues of s in S 2 V K, as in Lemma Suppose that F W = {f W,ij i, j App W } F is a basis of W K such that, for every i, j App W, we have that f W,ij is an l ij -eigenvector for s in W K, and F W satisfies the σ-relations for S 2 V for all i, j App W as in Definition Then there exists a basis F S 2 V = { ˆf ij 1 i j d} of S 2 V K such that F S 2 V satisfies the σ-relations for S 2 V, and for every i, j App W, the following hold: i ˆf ν ij S2 V ; ii ˆf νϕ ij = f ij ; and iii for every g G and for all i, j, k, l App W, we have that g ˆfij ˆfkl = g fijf kl. Proof. Note first that ν is either the identity map, or the projection of S 2 V onto a quotient by a subspace fixed pointwise by G see Section 4.1 for details. For each 1, j App W, choose a preimage of f ϕ 1 1j under ν, and set ˆf 1j to be this preimage. Then for i, j App W with 2 i j d, set ˆf σi 1 ij := ˆf i 1,j 1. If d = d 1, then for 2 i d, set ˆf id := ˆf σ i 1,d. If d = d 2, then for 2 i d, set ˆf id := ˆf σ i 1,d 1, and set ˆf i,d 1 := ˆf σ i 1,d. preimage of f ϕ 1 d 1,d 1 under ν, set ˆf d 1,d 1 to be this preimage, and set ˆf dd = ˆf σ d 1,d 1. Choose a Then ˆf ij has been defined for all pairs i, j App W : for the remaining pairs with 1 i j d, choose ˆf ij such that they satisfy the σ-relations for S 2 V.
105 5.4. The Action of a Special Element on the Alternating Square 2 V K 95 Now for all 1 i j d, we have that ˆf ij is an l ij -eigenvector for s in its action on S 2 V, since the maps ν, ϕ preserve eigenstructure, and since the action of σ maps l ij -eigenvectors to l q ij -eigenvectors. By Lemma 5.3.1, for every i, j App W, either G = SUd, q, or l ij 1. In the former case, ν is the identity map, and so ˆf ν ij S2 V. In the latter case, ˆfij is an l ij -eigenvector for l ij 1, and so is not fixed by the action of s, and so since S 2 V is the kernel a linear form T see Section 4.1, we have, by Lemma , that ˆf ν ij S2 V. Since σ commutes with ϕ, ν, we have, for i, j App W with 2 i j d, that ij = ˆf i 1,j 1 σ νϕ νϕ = ˆf i 1,j 1 σ = fi 1,j 1 σ = f νϕ ij. By the same argument we have that ˆf ij = f ij for the remaining i, j App W, and so ii holds. iii then follows by Lemmas and Lemma lifts us from a basis of W K to a basis of S 2 V K : combining this with Lemma decomposes into one of two bases for V L for which the Basic Equation holds whenever i, j, k, l App W. This set of equations is the tool for constructive recognition. Corollary Let G be a Classical Group, let V be the natural F G-module, and let W be an F G-module such that W = S 2 V ϕ, where S 2 V is as in Table , and ϕ is an isomorphism of F G-modules. ˆf νϕ Let s G be a special element, as in Definition , let {l ij 1 i j d } be the eigenvalues of s in S 2 V K, as in Lemma Suppose that F W = {f W,ij i, j App W } F is a basis of W K satisfying the conditions in Lemma Then there exists a field extension L of K of degree at most 2, a basis F V = F s, V, F W = {f V,i 1 i d} of V L, a set of constants C = {c ij i, j App W }, a basis F V = {f V,i 1 i d} and constants C = {c ij i, j App W } as defined in Lemma 5.3.6, such that, for every i, j, k, l App W and for every g G, the following hold, where κ ij,kl = g fw,ij f W,kl, a ij = g fv,i f V,j, a ij = g f V,i f : V,j i The Basic Equation holds; and ii for 1 i, j d 1, we have a q ij = a i+1,j+1. Moreover, we have c ii = c ii = 1 for 1 i d, and if d < d, we have c 1j = 1 for d < j d. Proof. By Lemma 5.3.8, the basis F W gives rise to a basis F of S 2 V satisfying the conditions of Lemma 5.3.7: combining these two results, the result follows. 5.4 The Action of a Special Element on the Alternating Square 2 V K The analysis for the Alternating Square case mirrors that of the Symmetric Square, although there are some minor differences, and in particular there is no need for a second basis F. Unfortunately while this may seem to indicate that the 2 V case is easier, it reflects only that the difficulties which arise must be dealt with later in Chapter 9. Lemma Let G be a classical group as in one of the lines of Table , and let s G be a special element as defined in Definition , with eigenvalues {l i 1 i d} as in Lemma , and let E s, V = {e i 1 i d} be as defined in Lemma
106 96 Chapter 5. Special Elements and their Eigenstructure Define where E s, 2 V = {e s, 2 V,ij 1 i < j d}, e s, 2 V,ij = e i e j e j e i. Suppose that in the Linear and Unitary cases, we have d 4; in the remaining cases with d = d we have d 6; and in the remaining cases with d = d 1, d 2 we have d 8. Then the eigenvalues of s in its action on 2 V K are {l ij := l i l j 1 i < j d}, and the following hold: i if l ij = 1 then i d, j d and the condition in the 5th column of the appropriate line of Table holds; ii for each pair i, j, the l ij -eigenspace of s contains e s, 2 V,ij; and iii the l ij -eigenspace of s is precisely e s, 2 V,ij, except when either l ij {Spd, q, SO ɛ d, q}; or G {Spd, 2, SO ɛ d, 2}. = 1 and G Proof. This follows immediately from Lemma and note that the exceptional cases in Lemma for q = 3 do not apply here since we do not have i = j in the Alternating Square case. As in the S 2 V case above, we often write e ij := e s, 2 V,ij when there is no ambiguity. Lemma Let G be a classical group, let W be an F G-module isomorphic to 2 V, and let App W be the set of pairs i, j of integers such that, for any special element s G, the l ij -eigenspace of s in its action on W has dimension 1. Then: i if G {SLd, q, SUd, q}, then App W = {i, j 1 i < j d}; ii if G {Spd, q, SO d, q}, q 5, then d = d and i, j App W if and only if 1 i < j d, and j i d/2; iii if G {SO d, q}, q 5, then d = d 1 and i, j App W if and only if either 1 i < j d, and j i d /2; or 1 i d and j = d; iv if G = SO + d, q, q 5, then d = d 2 and i, j App W if and only if either 1 i < j d, and j i d /2; or 1 i d and d < j d. Note that in all cases, if 1 i < j d, j i d /2, we have i, j App W. Proof. This follows immediately from Lemma Definition Suppose that F = {f ij 1 i < j d} is a basis for 2 V K. Then F is said to satisfy the σ-relations for 2 V if the following hold: i for 1 i < j d 1, fij σ = f i+1,j+1; ii when d = d 1, we have that for 1 i d, fi,d σ = f i+1,d; and
107 5.4. The Action of a Special Element on the Alternating Square 2 V K 97 iii when d = d 2, we have that for 1 i d 1, fi,d 1 σ = f i+1,d. If F has a partial labelling {f ij i, j App W } F, then we say that F satisfies the σ-relations for App W if the relations hold for all i, j App W. We weaken the σ-relations in this case when wrapping around from d to 1 this is a result of the fact that switching i with j in e ij := e i e j e j e i results in a sign change. Although we could include this as a condition for example, we might require that e σ 1d = e 12, it would complicate matters needlessly. Lemma Let G be a classical group as in one of the lines of Table , let s G be a special element as defined in Definition , and let E s, 2 V = {e ij := e s, 2 V,ij 1 i < j d} as defined in Lemma Then E s, 2 V satisfies the σ-relations for 2 V. Proof. As in Lemma 5.3.4, the relations follow immediately from the σ-relations on {e i 1 i d}, which hold by Lemma Lemma Let G be a classical group as in one of the lines of Table , let s G be a special element as defined in Definition , let W = 2 V, and let E := E s, 2 V = {e ij 1 i < j d} be as defined in Lemma Suppose that there exists a basis F 2 V := F s, 2 V, E := {f ij := f s,v,e,ij 1 i < j d} for W K such that, for every pair i, j with 1 i < j d, we have that f s,v,e,ij e ij, and F 2 V satisfies the σ-relations for 2 V as defined in Lemma Then there exists an extension field L/K of degree at most q+1, a basis F V = F s, V, F 2 V := {f i 1 i d} for V L, and a set C = C s, F 2 V, F V := {c ij 1 i < j d} L, such that F V satisfies the almost-σ-relations for V, and for 1 i < j d, we have f ij = c ij f i f j f j f i. Moreover, we have that c 12 = 1; and if d < d, we have c 1j = 1 for j > d. Proof. Let E V := {e i 1 i d} be as defined in Lemma Then since each f ij is a scalar multiple of e ij, there exist constants c ij K such that f ij = c ij e ij. Suppose that for every i, we set f i = a i e i, for a i L. Then for every i, j, we have that f i f j = a i e i a j e j = a i a j e i e j, and so f i f j f j f i = a i a j e i e j e j e i = a i a j e ij. For 1 i < j d, set c ij = c ij a ia j 1 L. Then c ij f i f j f j f i = c ije ij = f ij. This holds for all choices of {a i }. By Lemma , we may choose a q + 1st root x of c 12 in an extension field L/K of degree at most q + 1. For 1 i d, set a i = x qi 1 : then a q+1 1 = x q+1 = c 12, and so c 12 = c 12a q+1 1 = 1, and when i < d, we have f σ i = a i e i σ = x qi 1 q e i+1 = a i+1 e i+1. When i = d, we have that e σ d = e 1, and so f σ i = a q d f 1 f 1, and so the almost-σ-relations hold for i < d. The other relations follow in a similar way.
108 98 Chapter 5. Special Elements and their Eigenstructure If d < d, then for j > d, set a j = c 1j a 1 1 : then a 1a j = c 1j, and we have c 1j = c 1j a 1 a j 1 = 1 as required. Lemma Let G be a classical group as in one of the lines of Table , let s G be a special element as defined in Definition , let W = 2 V. Let E 2 V = {e ij 1 i j d} be as defined in Lemma 5.4.1, and let F V, C := {c ij 1 i j d} be defined as in Lemma Then for 1 i j d 1, we have c q ij = c i+1,j+1 and hence for 1 i d 1, we have c i,i+1 = 1. Moreover, for every g G, and for all pairs i, j, k, l App W, we have the following hold, where κ ij,kl := g fijf kl, a ij = g fif j : i The Basic Equation in the Alternating Square Case holds for κ ij,kl, a ij, C : ii for 1 i, j d 1, we have a q ij = a i+1,j+1. κ ij,kl = c ij c kl a ik a jl a il a jk ; Proof. Since f σ i = f i+1 for all 1 i d 1 we have, for 1 i j d 1, that f σ ij = c ij f i f j f j f i σ = c q ij f i+1 f j+1 f j+1 f i+1 = c q ij c 1 i+1,j+1 f i+1,j+1, and so c q ij = c i+1,j+1 since we have that f σ ij = f i+1,j+1. Since by Lemma c 12 = 1, we have that c i,i+1 = 1 for 1 i d 1. i follows immediately from Lemmas and For ii, since for 1 i d 1, we have fi σ = f i+1, and since, for i d we have fi σ f 2,..., f d, we have that σ d d 1 f gσ i = a ij f j = a q ij f j+1 + v, j=1 where v f 2,..., f d. On the other hand, we have and so, since f gσ i as required. f σg j=1 d i = f g i+1 = d 1 a i+1,j f j = a i+1,j+1 f j+1, j=1 j=0 = f σg i, by equating coefficients of f j+1 for 1 j d 1, we have a q ij = a i+1,j+1 Lemma Let G be a Classical Group, let V be the natural F G-module, and let W be an F G-module such that W = 2 V ϕ, where 2 V is as in Table , and ϕ is an isomorphism of F G-modules, and let ν be a homomorphism of F G-modules such that 2 V 2 V ν. Let s G be a special element, as in Definition , let {l ij 1 i j d } be the eigenvalues of s in S 2 V K, as in Lemma Suppose that F W = {f W,ij i, j App W } F is
109 5.5. Using Special Elements 99 a basis of W K such that, for every i, j App W, we have that f W,ij is an l ij -eigenvector for s in W K, and F W satisfies the σ-relations for S 2 V as in Lemma for all i, j App W. Then there exists a basis F 2 V = { ˆf ij 1 i j d} of 2 V K such that F 2 V satisfies the σ-relations for 2 V, and for every i, j App W, the following hold: i ˆf ν ij 2 V ; ii ˆf νϕ ij = f ij ; and iii for every g G and for all i, j, k, l App W, we have that g ˆfij, ˆf kl = g fij,f kl. Proof. This follows by an identical argument to the proof of Lemma Corollary Let G be a Classical Group, let V be the natural F G-module, and let W be an F G-module such that W = 2 V ϕ, where 2 V is as in Table , and ϕ is an isomorphism of F G-modules. Let s G be a special element, as in Definition , let {l ij 1 i j d } be the eigenvalues of s in 2 V K, as in Lemma Suppose that F W = {f W,ij i, j App W } F is a basis of W K satisfying the conditions in Lemma Then there exists a field extension L of K, a basis F V = F s, V, F W = {f V,i 1 i d} of V L, and a set of constants C = {c ij i, j App W } such that, for every i, j, k, l App W, g G, the following hold, where κ ij,kl = g fw,ij f W,kl, a ij = g fv,i f V,j : i The Basic Equation κ ij,kl = cij c kl a ik a jl a il a jk holds; and ii for 1 i, j d 1, we have a q ij = a i+1,j+1. Proof. By Lemma 5.4.7, the basis F W gives rise to a basis F of 2 V satisfying the conditions of Lemma 5.4.6: combining the two results, the equations hold. 5.5 Using Special Elements The key results in this chapter are Corollaries and 5.4.8: the plan for Initialise is to produce a special element s in its action on W, and from there produce a basis F W for W K satisfying the conditions of the corollary appropriate for the case: this yields, then, a basis F V for V L and a set of Basic Equations satisfied by the known coefficients of g G in its action on F W, the unknown constants C, and the unknown coefficients of g in its action on F V. The final difficult step of Initialise is to choose a random element g G, and use those equations to turn the unknown constants C into known constants. With these in hand, the procedure FindPreimage can then attack the problem of producing the unknowns a ij := g fif j for an arbitrary g G.
110 100 Chapter 5. Special Elements and their Eigenstructure
111 CHAPTER Quokka Theory and Nilpotent-Independent Sets of Matrices The Quokka Theory of Niemeyer and Praeger as described in [76] is a powerful tool in estimating proportions in classical groups, reducing the question of estimating the size of a subset of a classical group to a pair of simpler questions: one of estimating proportions in F -stable maximal Tori that is, in abelian groups, and another of estimating proportions in Weyl groups that is, in permutation groups. This method was introduced by Lehrer [62] for computing with the characters of Lie type groups. Each of these tasks estimation in abelian and permutation groups is generally much easier than the corresponding task in the Classical group. Quokka Theory s usefulness is limited to sets satisfying certain conditions on their structure: however is is often possible to estimate the size of a non-quokka set X G by finding a large enough quokka set Q contained in X. Then the size of Q is a lower bound for the size of X. This approach can expand the scope of Quokka theory beyond its apparent limits. 6.1 Quokka Sets in Matrix Groups Let G = GLd, q. Then for each g G, there exists a unique decomposition g = su = us, called the Multiplicative Jordan-Chevalley Decomposition, such that s is a semisimple element of G that is, the minimal polynomial of s is square-free, and u is a unipotent element that is, the minimal polynomial of u is a power of t 1. For more information on this decomposition, see for example [46, Chapter VI]. Definition A nonempty subset Q of a classical group G is said to have the Quokka Property and is called a Quokka Set if the following conditions hold: i Q is closed under conjugation by elements of G; and ii for all g G, we have g Q if and only if the semisimple part s of the Jordan-Chevalley decomposition of g = su = us is in Q. In other words, i Q is a union of conjugacy classes in G; and ii membership of Q depends only on the semisimple part of its elements. Quokka sets are extremely useful due to the following Theorem [76, Thm 1.3]. Note that this statement contains some forward references, which will be explained in due course:
Recognition of Classical Groups of Lie Type
 Recognition of Classical Groups of Lie Type Alice Niemeyer UWA, RWTH Aachen Alice Niemeyer (UWA, RWTH Aachen) Matrix Groups Sommerschule 2011 1 / 60 Linear groups Let q = p a for some prime p and F = F
Recognition of Classical Groups of Lie Type Alice Niemeyer UWA, RWTH Aachen Alice Niemeyer (UWA, RWTH Aachen) Matrix Groups Sommerschule 2011 1 / 60 Linear groups Let q = p a for some prime p and F = F
An Algorithm for Projective Representations of some Matrix Groups.
 An Algorithm for Projective Representations of some Matrix Groups Kübra GÜL 1, Abdullah ÇAĞMAN 2, Nurullah ANKARALIOĞLU 1 1 Mathematics Department, Faculty of Science, Ataturk University, 25240, Erzurum,
An Algorithm for Projective Representations of some Matrix Groups Kübra GÜL 1, Abdullah ÇAĞMAN 2, Nurullah ANKARALIOĞLU 1 1 Mathematics Department, Faculty of Science, Ataturk University, 25240, Erzurum,
A biased overview of computational algebra
 A biased overview of computational algebra Peter Brooksbank Bucknell University Linear Algebra and Matrix Theory: connections, applications and computations NUI Galway (December 3, 2012) Lecture Outline
A biased overview of computational algebra Peter Brooksbank Bucknell University Linear Algebra and Matrix Theory: connections, applications and computations NUI Galway (December 3, 2012) Lecture Outline
A unified approach to computations with permutation and matrix groups
 A unified approach to computations with permutation and matrix groups Ákos Seress Abstract. We survey algorithms to compute with large finite permutation and matrix groups. Particular attention will be
A unified approach to computations with permutation and matrix groups Ákos Seress Abstract. We survey algorithms to compute with large finite permutation and matrix groups. Particular attention will be
Probabilistic and Non-Deterministic Computations in Finite Groups
 Probabilistic and Non-Deterministic Computations in Finite Groups A talk at the ICMS Workshop Model-Theoretic Algebra and Algebraic Models of Computation Edinburgh, 4 15 September 2000 Alexandre Borovik
Probabilistic and Non-Deterministic Computations in Finite Groups A talk at the ICMS Workshop Model-Theoretic Algebra and Algebraic Models of Computation Edinburgh, 4 15 September 2000 Alexandre Borovik
Algorithms for Permutation groups
 Algorithms for Permutation groups Alice Niemeyer UWA, RWTH Aachen Alice Niemeyer (UWA, RWTH Aachen) Perm Groups Sommerschule 2011 1 / 36 Permutation Groups Permutation Groups The Symmetric Group Let Ω
Algorithms for Permutation groups Alice Niemeyer UWA, RWTH Aachen Alice Niemeyer (UWA, RWTH Aachen) Perm Groups Sommerschule 2011 1 / 36 Permutation Groups Permutation Groups The Symmetric Group Let Ω
Finding the characteristic of a group of Lie type
 Finding the characteristic of a group of Lie type Martin W. Liebeck Department of Mathematics Imperial College London SW7 2BZ England E.A. O Brien Department of Mathematics University of Auckland Auckland
Finding the characteristic of a group of Lie type Martin W. Liebeck Department of Mathematics Imperial College London SW7 2BZ England E.A. O Brien Department of Mathematics University of Auckland Auckland
Subspace stabilizers and maximal subgroups of exceptional groups of Lie type
 Subspace stabilizers and maximal subgroups of exceptional groups of Lie type David A. Craven June 7, 2016 Abstract In 1998, Liebeck and Seitz introduced a constant t(g), dependent on the root system of
Subspace stabilizers and maximal subgroups of exceptional groups of Lie type David A. Craven June 7, 2016 Abstract In 1998, Liebeck and Seitz introduced a constant t(g), dependent on the root system of
Testing matrix groups for primitivity
 Testing matrix groups for primitivity Derek F. Holt, Charles R. Leedham-Green, E.A. O Brien and Sarah Rees Derek F. Holt Mathematics Institute University of Warwick Coventry CV4 7AL Great Britain E-mail:
Testing matrix groups for primitivity Derek F. Holt, Charles R. Leedham-Green, E.A. O Brien and Sarah Rees Derek F. Holt Mathematics Institute University of Warwick Coventry CV4 7AL Great Britain E-mail:
Primitive groups and maximal subgroups
 Dartmouth Colloquium 3 December 2009 Main Goal of Finite Group Theory? Classify all finite groups Determine list L containing all finite groups, and for each isomorphism class of groups describe all ways
Dartmouth Colloquium 3 December 2009 Main Goal of Finite Group Theory? Classify all finite groups Determine list L containing all finite groups, and for each isomorphism class of groups describe all ways
Maximal subgroups of exceptional groups: representing groups in groups
 Maximal subgroups of exceptional groups: representing groups in groups David A. Craven University of Birmingham Representations of Finite and Algebraic Groups, Les Houches. 9th February, 2015. Joint with
Maximal subgroups of exceptional groups: representing groups in groups David A. Craven University of Birmingham Representations of Finite and Algebraic Groups, Les Houches. 9th February, 2015. Joint with
THERE IS NO Sz(8) IN THE MONSTER
 THERE IS NO Sz(8) IN THE MONSTER ROBERT A. WILSON Abstract. As a contribution to an eventual solution of the problem of the determination of the maximal subgroups of the Monster we show that there is no
THERE IS NO Sz(8) IN THE MONSTER ROBERT A. WILSON Abstract. As a contribution to an eventual solution of the problem of the determination of the maximal subgroups of the Monster we show that there is no
ON THE ORDERS OF AUTOMORPHISM GROUPS OF FINITE GROUPS
 Submitted exclusively to the London Mathematical Society DOI: 0./S0000000000000000 ON THE ORDERS OF AUTOMORPHISM GROUPS OF FINITE GROUPS JOHN N. BRAY and ROBERT A. WILSON Abstract In the Kourovka Notebook,
Submitted exclusively to the London Mathematical Society DOI: 0./S0000000000000000 ON THE ORDERS OF AUTOMORPHISM GROUPS OF FINITE GROUPS JOHN N. BRAY and ROBERT A. WILSON Abstract In the Kourovka Notebook,
Computing with matrix groups
 Computing with matrix groups William M. Kantor and Ákos Seress 1 Introduction A group is usually input into a computer by specifying the group either using a presentation or using a generating set of permutations
Computing with matrix groups William M. Kantor and Ákos Seress 1 Introduction A group is usually input into a computer by specifying the group either using a presentation or using a generating set of permutations
LOCALLY ELUSIVE CLASSICAL GROUPS. 1. Introduction
 LOCALLY ELUSIVE CLASSICAL GROUPS TIMOTHY C. BURNESS AND MICHAEL GIUDICI Abstract. Let G be a transitive permutation group of degree n with point stabiliser H and let r be a prime divisor of n. We say that
LOCALLY ELUSIVE CLASSICAL GROUPS TIMOTHY C. BURNESS AND MICHAEL GIUDICI Abstract. Let G be a transitive permutation group of degree n with point stabiliser H and let r be a prime divisor of n. We say that
Regular permutation groups. and Cayley graphs. Cheryl E Praeger. University of Western Australia
 Regular permutation groups and Cayley graphs Cheryl E Praeger University of Western Australia 1 What are Cayley graphs? Group : G with generating set S = {s, t, u,... } Group elements: words in S stu 1
Regular permutation groups and Cayley graphs Cheryl E Praeger University of Western Australia 1 What are Cayley graphs? Group : G with generating set S = {s, t, u,... } Group elements: words in S stu 1
Bases of primitive permutation groups
 Bases of primitive permutation groups Martin W. Liebeck and Aner Shalev 1 Introduction Let G be a permutation group on a finite set Ω of size n. A subset of Ω is said to be a base for G if its pointwise
Bases of primitive permutation groups Martin W. Liebeck and Aner Shalev 1 Introduction Let G be a permutation group on a finite set Ω of size n. A subset of Ω is said to be a base for G if its pointwise
Maximal Subgroups of Finite Groups
 Groups St Andrews 2009 in Bath Colva M. Roney-Dougal University of St Andrews In honour of John Cannon and Derek Holt 11 August 2009 Primitive permutation groups Mostly definitions Old stuff Newer stuff
Groups St Andrews 2009 in Bath Colva M. Roney-Dougal University of St Andrews In honour of John Cannon and Derek Holt 11 August 2009 Primitive permutation groups Mostly definitions Old stuff Newer stuff
Finding 47:23 in the Baby Monster
 Submitted exclusively to the London Mathematical Society doi:10.1112/0000/000000 Finding 47:23 in the Baby Monster John N. Bray, Richard A. Parker and Robert A. Wilson Abstract In this paper we describe
Submitted exclusively to the London Mathematical Society doi:10.1112/0000/000000 Finding 47:23 in the Baby Monster John N. Bray, Richard A. Parker and Robert A. Wilson Abstract In this paper we describe
THE SEMISIMPLE SUBALGEBRAS OF EXCEPTIONAL LIE ALGEBRAS
 Trudy Moskov. Matem. Obw. Trans. Moscow Math. Soc. Tom 67 (2006) 2006, Pages 225 259 S 0077-1554(06)00156-7 Article electronically published on December 27, 2006 THE SEMISIMPLE SUBALGEBRAS OF EXCEPTIONAL
Trudy Moskov. Matem. Obw. Trans. Moscow Math. Soc. Tom 67 (2006) 2006, Pages 225 259 S 0077-1554(06)00156-7 Article electronically published on December 27, 2006 THE SEMISIMPLE SUBALGEBRAS OF EXCEPTIONAL
Characters and triangle generation of the simple Mathieu group M 11
 SEMESTER PROJECT Characters and triangle generation of the simple Mathieu group M 11 Under the supervision of Prof. Donna Testerman Dr. Claude Marion Student: Mikaël Cavallin September 11, 2010 Contents
SEMESTER PROJECT Characters and triangle generation of the simple Mathieu group M 11 Under the supervision of Prof. Donna Testerman Dr. Claude Marion Student: Mikaël Cavallin September 11, 2010 Contents
Sporadic and related groups. Lecture 11 Matrices over finite fields J 4
 Sporadic and related groups. Lecture 11 Matrices over finite fields J 4 Original aim of the meat-axe. Find the (degrees of the) 13 irreducible representations of M 24 mod 2. Gordon James found 12 of them
Sporadic and related groups. Lecture 11 Matrices over finite fields J 4 Original aim of the meat-axe. Find the (degrees of the) 13 irreducible representations of M 24 mod 2. Gordon James found 12 of them
Representation Theory. Ricky Roy Math 434 University of Puget Sound
 Representation Theory Ricky Roy Math 434 University of Puget Sound May 2, 2010 Introduction In our study of group theory, we set out to classify all distinct groups of a given order up to isomorphism.
Representation Theory Ricky Roy Math 434 University of Puget Sound May 2, 2010 Introduction In our study of group theory, we set out to classify all distinct groups of a given order up to isomorphism.
arxiv: v1 [math.gr] 20 Jul 2015
![arxiv: v1 [math.gr] 20 Jul 2015 arxiv: v1 [math.gr] 20 Jul 2015](/thumbs/90/101197499.jpg) arxiv:1507.05671v1 [math.gr] 20 Jul 2015 A LAS VEGAS REWRITING ALGORITHM FOR THE SYMMETRIC SQUARE REPRESENTATION OF CLASSICAL GROUPS BRIAN P. CORR Dedicated to the memory of Àkos Seress, who provided a
arxiv:1507.05671v1 [math.gr] 20 Jul 2015 A LAS VEGAS REWRITING ALGORITHM FOR THE SYMMETRIC SQUARE REPRESENTATION OF CLASSICAL GROUPS BRIAN P. CORR Dedicated to the memory of Àkos Seress, who provided a
ON BASE SIZES FOR ALGEBRAIC GROUPS
 ON BASE SIZES FOR ALGEBRAIC GROUPS TIMOTHY C. BURNESS, ROBERT M. GURALNICK, AND JAN SAXL Abstract. For an algebraic group G and a closed subgroup H, the base size of G on the coset variety of H in G is
ON BASE SIZES FOR ALGEBRAIC GROUPS TIMOTHY C. BURNESS, ROBERT M. GURALNICK, AND JAN SAXL Abstract. For an algebraic group G and a closed subgroup H, the base size of G on the coset variety of H in G is
6 Cosets & Factor Groups
 6 Cosets & Factor Groups The course becomes markedly more abstract at this point. Our primary goal is to break apart a group into subsets such that the set of subsets inherits a natural group structure.
6 Cosets & Factor Groups The course becomes markedly more abstract at this point. Our primary goal is to break apart a group into subsets such that the set of subsets inherits a natural group structure.
Rank 3 permutation groups
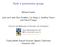 Rank 3 permutation groups Michael Giudici joint work with Alice Devillers, Cai Heng Li, Geoffrey Pearce and Cheryl Praeger Centre for the Mathematics of Symmetry and Computation Twenty-Ninth Annual Victorian
Rank 3 permutation groups Michael Giudici joint work with Alice Devillers, Cai Heng Li, Geoffrey Pearce and Cheryl Praeger Centre for the Mathematics of Symmetry and Computation Twenty-Ninth Annual Victorian
Classification of semisimple Lie algebras
 Chapter 6 Classification of semisimple Lie algebras When we studied sl 2 (C), we discovered that it is spanned by elements e, f and h fulfilling the relations: [e, h] = 2e, [ f, h] = 2 f and [e, f ] =
Chapter 6 Classification of semisimple Lie algebras When we studied sl 2 (C), we discovered that it is spanned by elements e, f and h fulfilling the relations: [e, h] = 2e, [ f, h] = 2 f and [e, f ] =
STEINBERG PRESENTATIONS OF BLACK BOX CLASSICAL GROUPS IN SMALL CHARACTERISTICS
 STEINBERG PRESENTATIONS OF BLACK BOX CLASSICAL GROUPS IN SMALL CHARACTERISTICS ALEXANDRE BOROVIK AND ŞÜKRÜ YALÇINKAYA Abstract. The main component of (constructive) recognition algorithms for black box
STEINBERG PRESENTATIONS OF BLACK BOX CLASSICAL GROUPS IN SMALL CHARACTERISTICS ALEXANDRE BOROVIK AND ŞÜKRÜ YALÇINKAYA Abstract. The main component of (constructive) recognition algorithms for black box
1 Fields and vector spaces
 1 Fields and vector spaces In this section we revise some algebraic preliminaries and establish notation. 1.1 Division rings and fields A division ring, or skew field, is a structure F with two binary
1 Fields and vector spaces In this section we revise some algebraic preliminaries and establish notation. 1.1 Division rings and fields A division ring, or skew field, is a structure F with two binary
The Major Problems in Group Representation Theory
 The Major Problems in Group Representation Theory David A. Craven 18th November 2009 In group representation theory, there are many unsolved conjectures, most of which try to understand the involved relationship
The Major Problems in Group Representation Theory David A. Craven 18th November 2009 In group representation theory, there are many unsolved conjectures, most of which try to understand the involved relationship
Solving an arbitrary permutation puzzle
 T.C. Brouwer Solving an arbitrary permutation puzzle Bachelor thesis, June 18, 2016 Supervisor: Dr. R.M. van Luijk Mathematisch Instituut, Universiteit Leiden Contents 1 Introduction 2 Mathematical formulation
T.C. Brouwer Solving an arbitrary permutation puzzle Bachelor thesis, June 18, 2016 Supervisor: Dr. R.M. van Luijk Mathematisch Instituut, Universiteit Leiden Contents 1 Introduction 2 Mathematical formulation
MIT Algebraic techniques and semidefinite optimization May 9, Lecture 21. Lecturer: Pablo A. Parrilo Scribe:???
 MIT 6.972 Algebraic techniques and semidefinite optimization May 9, 2006 Lecture 2 Lecturer: Pablo A. Parrilo Scribe:??? In this lecture we study techniques to exploit the symmetry that can be present
MIT 6.972 Algebraic techniques and semidefinite optimization May 9, 2006 Lecture 2 Lecturer: Pablo A. Parrilo Scribe:??? In this lecture we study techniques to exploit the symmetry that can be present
Automorphism group computation and isomorphism testing in finite groups
 Article Submitted to Journal of Symbolic Computation Automorphism group computation and isomorphism testing in finite groups John J. Cannon 1 and Derek F. Holt 2 1 School of Mathematics, University of
Article Submitted to Journal of Symbolic Computation Automorphism group computation and isomorphism testing in finite groups John J. Cannon 1 and Derek F. Holt 2 1 School of Mathematics, University of
Algorithmic construction of Chevalley bases Magaard, Kay; Wilson, Robert
 Algorithmic construction of Chevalley bases Magaard, Kay; Wilson, Robert DOI: 10.1112/S1461157012001180 License: None: All rights reserved Document Version Publisher's PDF, also known as Version of record
Algorithmic construction of Chevalley bases Magaard, Kay; Wilson, Robert DOI: 10.1112/S1461157012001180 License: None: All rights reserved Document Version Publisher's PDF, also known as Version of record
THE TRANSITIVE AND CO TRANSITIVE BLOCKING SETS IN P 2 (F q )
 Volume 3, Number 1, Pages 47 51 ISSN 1715-0868 THE TRANSITIVE AND CO TRANSITIVE BLOCKING SETS IN P 2 (F q ) ANTONIO COSSIDENTE AND MARIALUISA J. DE RESMINI Dedicated to the centenary of the birth of Ferenc
Volume 3, Number 1, Pages 47 51 ISSN 1715-0868 THE TRANSITIVE AND CO TRANSITIVE BLOCKING SETS IN P 2 (F q ) ANTONIO COSSIDENTE AND MARIALUISA J. DE RESMINI Dedicated to the centenary of the birth of Ferenc
Math 594. Solutions 5
 Math 594. Solutions 5 Book problems 6.1: 7. Prove that subgroups and quotient groups of nilpotent groups are nilpotent (your proof should work for infinite groups). Give an example of a group G which possesses
Math 594. Solutions 5 Book problems 6.1: 7. Prove that subgroups and quotient groups of nilpotent groups are nilpotent (your proof should work for infinite groups). Give an example of a group G which possesses
0.2 Vector spaces. J.A.Beachy 1
 J.A.Beachy 1 0.2 Vector spaces I m going to begin this section at a rather basic level, giving the definitions of a field and of a vector space in much that same detail as you would have met them in a
J.A.Beachy 1 0.2 Vector spaces I m going to begin this section at a rather basic level, giving the definitions of a field and of a vector space in much that same detail as you would have met them in a
2 Permutation Groups
 2 Permutation Groups Last Time Orbit/Stabilizer algorithm: Orbit of a point. Transversal of transporter elements. Generators for stabilizer. Today: Use in a ``divide-and-conquer approach for permutation
2 Permutation Groups Last Time Orbit/Stabilizer algorithm: Orbit of a point. Transversal of transporter elements. Generators for stabilizer. Today: Use in a ``divide-and-conquer approach for permutation
arxiv:math/ v1 [math.gr] 15 Apr 2003
![arxiv:math/ v1 [math.gr] 15 Apr 2003 arxiv:math/ v1 [math.gr] 15 Apr 2003](/thumbs/94/122107851.jpg) ICM 2002 Vol. III 1 3 arxiv:math/0304207v1 [math.gr] 15 Apr 2003 Permutation Groups and Normal Subgroups Cheryl E. Praeger Abstract Various descending chains of subgroups of a finite permutation group
ICM 2002 Vol. III 1 3 arxiv:math/0304207v1 [math.gr] 15 Apr 2003 Permutation Groups and Normal Subgroups Cheryl E. Praeger Abstract Various descending chains of subgroups of a finite permutation group
REPRESENTATION THEORY OF S n
 REPRESENTATION THEORY OF S n EVAN JENKINS Abstract. These are notes from three lectures given in MATH 26700, Introduction to Representation Theory of Finite Groups, at the University of Chicago in November
REPRESENTATION THEORY OF S n EVAN JENKINS Abstract. These are notes from three lectures given in MATH 26700, Introduction to Representation Theory of Finite Groups, at the University of Chicago in November
Cubefree. Construction Algorithm for Cubefree Groups. A GAP4 Package. Heiko Dietrich
 Cubefree Construction Algorithm for Cubefree Groups A GAP4 Package by Heiko Dietrich School of Mathematical Sciences Monash University Clayton VIC 3800 Australia email: heiko.dietrich@monash.edu September
Cubefree Construction Algorithm for Cubefree Groups A GAP4 Package by Heiko Dietrich School of Mathematical Sciences Monash University Clayton VIC 3800 Australia email: heiko.dietrich@monash.edu September
Irreducible subgroups of algebraic groups
 Irreducible subgroups of algebraic groups Martin W. Liebeck Department of Mathematics Imperial College London SW7 2BZ England Donna M. Testerman Department of Mathematics University of Lausanne Switzerland
Irreducible subgroups of algebraic groups Martin W. Liebeck Department of Mathematics Imperial College London SW7 2BZ England Donna M. Testerman Department of Mathematics University of Lausanne Switzerland
VARIATIONS ON THE BAER SUZUKI THEOREM. 1. Introduction
 VARIATIONS ON THE BAER SUZUKI THEOREM ROBERT GURALNICK AND GUNTER MALLE Dedicated to Bernd Fischer on the occasion of his 75th birthday Abstract. The Baer Suzuki theorem says that if p is a prime, x is
VARIATIONS ON THE BAER SUZUKI THEOREM ROBERT GURALNICK AND GUNTER MALLE Dedicated to Bernd Fischer on the occasion of his 75th birthday Abstract. The Baer Suzuki theorem says that if p is a prime, x is
Constructing All Composition Series of a Finite Group
 Constructing All Composition Series of a Finite Group Alexander Hulpke Department of Mathematics Colorado State University 1874 Campus Delivery Fort Collins, CO, 80523-1874, USA hulpke@math.colostate.edu
Constructing All Composition Series of a Finite Group Alexander Hulpke Department of Mathematics Colorado State University 1874 Campus Delivery Fort Collins, CO, 80523-1874, USA hulpke@math.colostate.edu
Math 145. Codimension
 Math 145. Codimension 1. Main result and some interesting examples In class we have seen that the dimension theory of an affine variety (irreducible!) is linked to the structure of the function field in
Math 145. Codimension 1. Main result and some interesting examples In class we have seen that the dimension theory of an affine variety (irreducible!) is linked to the structure of the function field in
AUTOMORPHISM GROUPS AND SPECTRA OF CIRCULANT GRAPHS
 AUTOMORPHISM GROUPS AND SPECTRA OF CIRCULANT GRAPHS MAX GOLDBERG Abstract. We explore ways to concisely describe circulant graphs, highly symmetric graphs with properties that are easier to generalize
AUTOMORPHISM GROUPS AND SPECTRA OF CIRCULANT GRAPHS MAX GOLDBERG Abstract. We explore ways to concisely describe circulant graphs, highly symmetric graphs with properties that are easier to generalize
Liouvillian solutions of third order differential equations
 Article Submitted to Journal of Symbolic Computation Liouvillian solutions of third order differential equations Felix Ulmer IRMAR, Université de Rennes, 0 Rennes Cedex, France felix.ulmer@univ-rennes.fr
Article Submitted to Journal of Symbolic Computation Liouvillian solutions of third order differential equations Felix Ulmer IRMAR, Université de Rennes, 0 Rennes Cedex, France felix.ulmer@univ-rennes.fr
Total Ordering on Subgroups and Cosets
 Total Ordering on Subgroups and Cosets Alexander Hulpke Department of Mathematics Colorado State University 1874 Campus Delivery Fort Collins, CO 80523-1874 hulpke@math.colostate.edu Steve Linton Centre
Total Ordering on Subgroups and Cosets Alexander Hulpke Department of Mathematics Colorado State University 1874 Campus Delivery Fort Collins, CO 80523-1874 hulpke@math.colostate.edu Steve Linton Centre
Algebra Questions. May 13, Groups 1. 2 Classification of Finite Groups 4. 3 Fields and Galois Theory 5. 4 Normal Forms 9
 Algebra Questions May 13, 2013 Contents 1 Groups 1 2 Classification of Finite Groups 4 3 Fields and Galois Theory 5 4 Normal Forms 9 5 Matrices and Linear Algebra 10 6 Rings 11 7 Modules 13 8 Representation
Algebra Questions May 13, 2013 Contents 1 Groups 1 2 Classification of Finite Groups 4 3 Fields and Galois Theory 5 4 Normal Forms 9 5 Matrices and Linear Algebra 10 6 Rings 11 7 Modules 13 8 Representation
(1) A frac = b : a, b A, b 0. We can define addition and multiplication of fractions as we normally would. a b + c d
 The Algebraic Method 0.1. Integral Domains. Emmy Noether and others quickly realized that the classical algebraic number theory of Dedekind could be abstracted completely. In particular, rings of integers
The Algebraic Method 0.1. Integral Domains. Emmy Noether and others quickly realized that the classical algebraic number theory of Dedekind could be abstracted completely. In particular, rings of integers
SOME DESIGNS AND CODES FROM L 2 (q) Communicated by Alireza Abdollahi
 Transactions on Combinatorics ISSN (print): 2251-8657, ISSN (on-line): 2251-8665 Vol. 3 No. 1 (2014), pp. 15-28. c 2014 University of Isfahan www.combinatorics.ir www.ui.ac.ir SOME DESIGNS AND CODES FROM
Transactions on Combinatorics ISSN (print): 2251-8657, ISSN (on-line): 2251-8665 Vol. 3 No. 1 (2014), pp. 15-28. c 2014 University of Isfahan www.combinatorics.ir www.ui.ac.ir SOME DESIGNS AND CODES FROM
L(C G (x) 0 ) c g (x). Proof. Recall C G (x) = {g G xgx 1 = g} and c g (x) = {X g Ad xx = X}. In general, it is obvious that
 ALGEBRAIC GROUPS 61 5. Root systems and semisimple Lie algebras 5.1. Characteristic 0 theory. Assume in this subsection that chark = 0. Let me recall a couple of definitions made earlier: G is called reductive
ALGEBRAIC GROUPS 61 5. Root systems and semisimple Lie algebras 5.1. Characteristic 0 theory. Assume in this subsection that chark = 0. Let me recall a couple of definitions made earlier: G is called reductive
STRING C-GROUPS AS TRANSITIVE SUBGROUPS OF S n
 STRING C-GROUPS AS TRANSITIVE SUBGROUPS OF S n PETER J. CAMERON, MARIA ELISA FERNANDES, DIMITRI LEEMANS, AND MARK MIXER Abstract. If Γ is a string C-group which is isomorphic to a transitive subgroup of
STRING C-GROUPS AS TRANSITIVE SUBGROUPS OF S n PETER J. CAMERON, MARIA ELISA FERNANDES, DIMITRI LEEMANS, AND MARK MIXER Abstract. If Γ is a string C-group which is isomorphic to a transitive subgroup of
Spanning and Independence Properties of Finite Frames
 Chapter 1 Spanning and Independence Properties of Finite Frames Peter G. Casazza and Darrin Speegle Abstract The fundamental notion of frame theory is redundancy. It is this property which makes frames
Chapter 1 Spanning and Independence Properties of Finite Frames Peter G. Casazza and Darrin Speegle Abstract The fundamental notion of frame theory is redundancy. It is this property which makes frames
On a question of B.H. Neumann
 On a question of B.H. Neumann Robert Guralnick Department of Mathematics University of Southern California E-mail: guralnic@math.usc.edu Igor Pak Department of Mathematics Massachusetts Institute of Technology
On a question of B.H. Neumann Robert Guralnick Department of Mathematics University of Southern California E-mail: guralnic@math.usc.edu Igor Pak Department of Mathematics Massachusetts Institute of Technology
THE CHEBOTAREV INVARIANT OF A FINITE GROUP
 THE CHOBATAREV INVARIANT OF A FINITE GROUP Andrea Lucchini Università di Padova, Italy ISCHIA GROUP THEORY 2016 March, 29th - April, 2nd Let G be a nontrivial finite group and let x = (x n ) n N be a sequence
THE CHOBATAREV INVARIANT OF A FINITE GROUP Andrea Lucchini Università di Padova, Italy ISCHIA GROUP THEORY 2016 March, 29th - April, 2nd Let G be a nontrivial finite group and let x = (x n ) n N be a sequence
GALOIS THEORY: LECTURE 20
 GALOIS THEORY: LECTURE 0 LEO GOLDMAKHER. REVIEW: THE FUNDAMENTAL LEMMA We begin today s lecture by recalling the Fundamental Lemma introduced at the end of Lecture 9. This will come up in several places
GALOIS THEORY: LECTURE 0 LEO GOLDMAKHER. REVIEW: THE FUNDAMENTAL LEMMA We begin today s lecture by recalling the Fundamental Lemma introduced at the end of Lecture 9. This will come up in several places
Notes on D 4 May 7, 2009
 Notes on D 4 May 7, 2009 Consider the simple Lie algebra g of type D 4 over an algebraically closed field K of characteristic p > h = 6 (the Coxeter number). In particular, p is a good prime. We have dim
Notes on D 4 May 7, 2009 Consider the simple Lie algebra g of type D 4 over an algebraically closed field K of characteristic p > h = 6 (the Coxeter number). In particular, p is a good prime. We have dim
Representations of quivers
 Representations of quivers Gwyn Bellamy October 13, 215 1 Quivers Let k be a field. Recall that a k-algebra is a k-vector space A with a bilinear map A A A making A into a unital, associative ring. Notice
Representations of quivers Gwyn Bellamy October 13, 215 1 Quivers Let k be a field. Recall that a k-algebra is a k-vector space A with a bilinear map A A A making A into a unital, associative ring. Notice
The Gelfand-Tsetlin Basis (Too Many Direct Sums, and Also a Graph)
 The Gelfand-Tsetlin Basis (Too Many Direct Sums, and Also a Graph) David Grabovsky June 13, 2018 Abstract The symmetric groups S n, consisting of all permutations on a set of n elements, naturally contain
The Gelfand-Tsetlin Basis (Too Many Direct Sums, and Also a Graph) David Grabovsky June 13, 2018 Abstract The symmetric groups S n, consisting of all permutations on a set of n elements, naturally contain
TESTING MODULES OF GROUPS OF EVEN ORDER FOR SIMPLICITY
 TESTING MODULES OF GROUPS OF EVEN ORDER FOR SIMPLICITY GERHARD O. MICHLER AND ØYVIND SOLBERG Abstract. In this paper we exhibit an intimate relationship between the simplicity of an F G-module V of a finite
TESTING MODULES OF GROUPS OF EVEN ORDER FOR SIMPLICITY GERHARD O. MICHLER AND ØYVIND SOLBERG Abstract. In this paper we exhibit an intimate relationship between the simplicity of an F G-module V of a finite
Comprehensive Introduction to Linear Algebra
 Comprehensive Introduction to Linear Algebra WEB VERSION Joel G Broida S Gill Williamson N = a 11 a 12 a 1n a 21 a 22 a 2n C = a 11 a 12 a 1n a 21 a 22 a 2n a m1 a m2 a mn a m1 a m2 a mn Comprehensive
Comprehensive Introduction to Linear Algebra WEB VERSION Joel G Broida S Gill Williamson N = a 11 a 12 a 1n a 21 a 22 a 2n C = a 11 a 12 a 1n a 21 a 22 a 2n a m1 a m2 a mn a m1 a m2 a mn Comprehensive
THREE CASES AN EXAMPLE: THE ALTERNATING GROUP A 5
 THREE CASES REPRESENTATIONS OF FINITE GROUPS OF LIE TYPE LECTURE II: DELIGNE-LUSZTIG THEORY AND SOME APPLICATIONS Gerhard Hiss Lehrstuhl D für Mathematik RWTH Aachen University Summer School Finite Simple
THREE CASES REPRESENTATIONS OF FINITE GROUPS OF LIE TYPE LECTURE II: DELIGNE-LUSZTIG THEORY AND SOME APPLICATIONS Gerhard Hiss Lehrstuhl D für Mathematik RWTH Aachen University Summer School Finite Simple
Generation of finite classical groups by pairs of elements with large fixed point spaces
 Journal of Algebra 421 (2015) 56 101 Contents lists available at ScienceDirect Journal of Algebra www.elsevier.com/locate/jalgebra Generation of finite classical groups by pairs of elements with large
Journal of Algebra 421 (2015) 56 101 Contents lists available at ScienceDirect Journal of Algebra www.elsevier.com/locate/jalgebra Generation of finite classical groups by pairs of elements with large
HUPPERT S CONJECTURE FOR F i 23
 HUPPERT S CONJECTURE FOR F i 23 S. H. ALAVI, A. DANESHKAH, H. P. TONG-VIET, AND T. P. WAKEFIELD Abstract. Let G denote a finite group and cd(g) the set of irreducible character degrees of G. Bertram Huppert
HUPPERT S CONJECTURE FOR F i 23 S. H. ALAVI, A. DANESHKAH, H. P. TONG-VIET, AND T. P. WAKEFIELD Abstract. Let G denote a finite group and cd(g) the set of irreducible character degrees of G. Bertram Huppert
COURSE SUMMARY FOR MATH 504, FALL QUARTER : MODERN ALGEBRA
 COURSE SUMMARY FOR MATH 504, FALL QUARTER 2017-8: MODERN ALGEBRA JAROD ALPER Week 1, Sept 27, 29: Introduction to Groups Lecture 1: Introduction to groups. Defined a group and discussed basic properties
COURSE SUMMARY FOR MATH 504, FALL QUARTER 2017-8: MODERN ALGEBRA JAROD ALPER Week 1, Sept 27, 29: Introduction to Groups Lecture 1: Introduction to groups. Defined a group and discussed basic properties
TRANSITIVE PERMUTATION GROUPS IN WHICH ALL DERANGEMENTS ARE INVOLUTIONS
 TRANSITIVE PERMUTATION GROUPS IN WHICH ALL DERANGEMENTS ARE INVOLUTIONS I. M. Isaacs Department of Mathematics, University of Wisconsin Madison, WI 53706 USA e-mail: isaacs@math.wisc.edu Thomas Michael
TRANSITIVE PERMUTATION GROUPS IN WHICH ALL DERANGEMENTS ARE INVOLUTIONS I. M. Isaacs Department of Mathematics, University of Wisconsin Madison, WI 53706 USA e-mail: isaacs@math.wisc.edu Thomas Michael
2. The center of G, denoted by Z(G), is the abelian subgroup which commutes with every elements of G. The center always contains the unit element e.
 Chapter 2 Group Structure To be able to use groups in physics, or mathematics, we need to know what are the important features distinguishing one group from another. This is under the heading of group
Chapter 2 Group Structure To be able to use groups in physics, or mathematics, we need to know what are the important features distinguishing one group from another. This is under the heading of group
Computational Approaches to Finding Irreducible Representations
 Computational Approaches to Finding Irreducible Representations Joseph Thomas Research Advisor: Klaus Lux May 16, 2008 Introduction Among the various branches of algebra, linear algebra has the distinctions
Computational Approaches to Finding Irreducible Representations Joseph Thomas Research Advisor: Klaus Lux May 16, 2008 Introduction Among the various branches of algebra, linear algebra has the distinctions
6 Orthogonal groups. O 2m 1 q. q 2i 1 q 2i. 1 i 1. 1 q 2i 2. O 2m q. q m m 1. 1 q 2i 1 i 1. 1 q 2i. i 1. 2 q 1 q i 1 q i 1. m 1.
 6 Orthogonal groups We now turn to the orthogonal groups. These are more difficult, for two related reasons. First, it is not always true that the group of isometries with determinant 1 is equal to its
6 Orthogonal groups We now turn to the orthogonal groups. These are more difficult, for two related reasons. First, it is not always true that the group of isometries with determinant 1 is equal to its
Recognising nilpotent groups
 Recognising nilpotent groups A. R. Camina and R. D. Camina School of Mathematics, University of East Anglia, Norwich, NR4 7TJ, UK; a.camina@uea.ac.uk Fitzwilliam College, Cambridge, CB3 0DG, UK; R.D.Camina@dpmms.cam.ac.uk
Recognising nilpotent groups A. R. Camina and R. D. Camina School of Mathematics, University of East Anglia, Norwich, NR4 7TJ, UK; a.camina@uea.ac.uk Fitzwilliam College, Cambridge, CB3 0DG, UK; R.D.Camina@dpmms.cam.ac.uk
Symplectic representation theory and the Weyl algebra in positive characteristic
 Symplectic representation theory and the Weyl algebra in positive characteristic SPUR Final Paper, Summer 2016 Joseph Zurier Mentor: Augustus Lonergan Project Suggested by Roman Bezrukavnikov 3 August
Symplectic representation theory and the Weyl algebra in positive characteristic SPUR Final Paper, Summer 2016 Joseph Zurier Mentor: Augustus Lonergan Project Suggested by Roman Bezrukavnikov 3 August
ALGEBRA QUALIFYING EXAM SPRING 2012
 ALGEBRA QUALIFYING EXAM SPRING 2012 Work all of the problems. Justify the statements in your solutions by reference to specific results, as appropriate. Partial credit is awarded for partial solutions.
ALGEBRA QUALIFYING EXAM SPRING 2012 Work all of the problems. Justify the statements in your solutions by reference to specific results, as appropriate. Partial credit is awarded for partial solutions.
Notes on nilpotent orbits Computational Theory of Real Reductive Groups Workshop. Eric Sommers
 Notes on nilpotent orbits Computational Theory of Real Reductive Groups Workshop Eric Sommers 17 July 2009 2 Contents 1 Background 5 1.1 Linear algebra......................................... 5 1.1.1
Notes on nilpotent orbits Computational Theory of Real Reductive Groups Workshop Eric Sommers 17 July 2009 2 Contents 1 Background 5 1.1 Linear algebra......................................... 5 1.1.1
Linear Algebra. Min Yan
 Linear Algebra Min Yan January 2, 2018 2 Contents 1 Vector Space 7 1.1 Definition................................. 7 1.1.1 Axioms of Vector Space..................... 7 1.1.2 Consequence of Axiom......................
Linear Algebra Min Yan January 2, 2018 2 Contents 1 Vector Space 7 1.1 Definition................................. 7 1.1.1 Axioms of Vector Space..................... 7 1.1.2 Consequence of Axiom......................
Math 210B. Artin Rees and completions
 Math 210B. Artin Rees and completions 1. Definitions and an example Let A be a ring, I an ideal, and M an A-module. In class we defined the I-adic completion of M to be M = lim M/I n M. We will soon show
Math 210B. Artin Rees and completions 1. Definitions and an example Let A be a ring, I an ideal, and M an A-module. In class we defined the I-adic completion of M to be M = lim M/I n M. We will soon show
Properties of Generating Sets of Finite Groups
 Cornell SPUR 2018 1 Group Theory Properties of Generating Sets of Finite Groups by R. Keith Dennis We now provide a few more details about the prerequisites for the REU in group theory, where to find additional
Cornell SPUR 2018 1 Group Theory Properties of Generating Sets of Finite Groups by R. Keith Dennis We now provide a few more details about the prerequisites for the REU in group theory, where to find additional
Exercises on chapter 1
 Exercises on chapter 1 1. Let G be a group and H and K be subgroups. Let HK = {hk h H, k K}. (i) Prove that HK is a subgroup of G if and only if HK = KH. (ii) If either H or K is a normal subgroup of G
Exercises on chapter 1 1. Let G be a group and H and K be subgroups. Let HK = {hk h H, k K}. (i) Prove that HK is a subgroup of G if and only if HK = KH. (ii) If either H or K is a normal subgroup of G
Overgroups of Irreducible Quasisimple Subgroups in Finite Classical Groups
 Overgroups of Irreducible Quasisimple Subgroups in Finite Classical Groups K. Magaard University of Birmingham January 14, 2017 Theorem [Aschbacher-Scott 1985] To settle the maximal subgroup problem for
Overgroups of Irreducible Quasisimple Subgroups in Finite Classical Groups K. Magaard University of Birmingham January 14, 2017 Theorem [Aschbacher-Scott 1985] To settle the maximal subgroup problem for
School of Mathematics and Statistics. MT5824 Topics in Groups. Problem Sheet I: Revision and Re-Activation
 MRQ 2009 School of Mathematics and Statistics MT5824 Topics in Groups Problem Sheet I: Revision and Re-Activation 1. Let H and K be subgroups of a group G. Define HK = {hk h H, k K }. (a) Show that HK
MRQ 2009 School of Mathematics and Statistics MT5824 Topics in Groups Problem Sheet I: Revision and Re-Activation 1. Let H and K be subgroups of a group G. Define HK = {hk h H, k K }. (a) Show that HK
Rings and groups. Ya. Sysak
 Rings and groups. Ya. Sysak 1 Noetherian rings Let R be a ring. A (right) R -module M is called noetherian if it satisfies the maximum condition for its submodules. In other words, if M 1... M i M i+1...
Rings and groups. Ya. Sysak 1 Noetherian rings Let R be a ring. A (right) R -module M is called noetherian if it satisfies the maximum condition for its submodules. In other words, if M 1... M i M i+1...
Primality Testing. 1 Introduction. 2 Brief Chronology of Primality Testing. CS265/CME309, Fall Instructor: Gregory Valiant
 CS265/CME309, Fall 2018. Instructor: Gregory Valiant Primality Testing [These notes may not be distributed outside this class without the permission of Gregory Valiant.] 1 Introduction Prime numbers are
CS265/CME309, Fall 2018. Instructor: Gregory Valiant Primality Testing [These notes may not be distributed outside this class without the permission of Gregory Valiant.] 1 Introduction Prime numbers are
Topics in linear algebra
 Chapter 6 Topics in linear algebra 6.1 Change of basis I want to remind you of one of the basic ideas in linear algebra: change of basis. Let F be a field, V and W be finite dimensional vector spaces over
Chapter 6 Topics in linear algebra 6.1 Change of basis I want to remind you of one of the basic ideas in linear algebra: change of basis. Let F be a field, V and W be finite dimensional vector spaces over
List of topics for the preliminary exam in algebra
 List of topics for the preliminary exam in algebra 1 Basic concepts 1. Binary relations. Reflexive, symmetric/antisymmetryc, and transitive relations. Order and equivalence relations. Equivalence classes.
List of topics for the preliminary exam in algebra 1 Basic concepts 1. Binary relations. Reflexive, symmetric/antisymmetryc, and transitive relations. Order and equivalence relations. Equivalence classes.
Math 396. Quotient spaces
 Math 396. Quotient spaces. Definition Let F be a field, V a vector space over F and W V a subspace of V. For v, v V, we say that v v mod W if and only if v v W. One can readily verify that with this definition
Math 396. Quotient spaces. Definition Let F be a field, V a vector space over F and W V a subspace of V. For v, v V, we say that v v mod W if and only if v v W. One can readily verify that with this definition
Simple groups and the classification of finite groups
 Simple groups and the classification of finite groups 1 Finite groups of small order How can we describe all finite groups? Before we address this question, let s write down a list of all the finite groups
Simple groups and the classification of finite groups 1 Finite groups of small order How can we describe all finite groups? Before we address this question, let s write down a list of all the finite groups
Algebraic aspects of Hadamard matrices
 Algebraic aspects of Hadamard matrices Padraig Ó Catháin University of Queensland 22 February 2013 Overview Difference set Relative difference set Symmetric Design Hadamard matrix Overview 1 Hadamard matrices
Algebraic aspects of Hadamard matrices Padraig Ó Catháin University of Queensland 22 February 2013 Overview Difference set Relative difference set Symmetric Design Hadamard matrix Overview 1 Hadamard matrices
On the Effectiveness of Symmetry Breaking
 On the Effectiveness of Symmetry Breaking Russell Miller 1, Reed Solomon 2, and Rebecca M Steiner 3 1 Queens College and the Graduate Center of the City University of New York Flushing NY 11367 2 University
On the Effectiveness of Symmetry Breaking Russell Miller 1, Reed Solomon 2, and Rebecca M Steiner 3 1 Queens College and the Graduate Center of the City University of New York Flushing NY 11367 2 University
Spherical varieties and arc spaces
 Spherical varieties and arc spaces Victor Batyrev, ESI, Vienna 19, 20 January 2017 1 Lecture 1 This is a joint work with Anne Moreau. Let us begin with a few notations. We consider G a reductive connected
Spherical varieties and arc spaces Victor Batyrev, ESI, Vienna 19, 20 January 2017 1 Lecture 1 This is a joint work with Anne Moreau. Let us begin with a few notations. We consider G a reductive connected
The primitive permutation groups of degree less than 2500
 The primitive permutation groups of degree less than 2500 Colva M. Roney-Dougal 8th November, 2004 School of Computer Science, University of St Andrews, North Haugh, St Andrews, Fife, KY16 9SS. Abstract
The primitive permutation groups of degree less than 2500 Colva M. Roney-Dougal 8th November, 2004 School of Computer Science, University of St Andrews, North Haugh, St Andrews, Fife, KY16 9SS. Abstract
DIGRAPHS WITH SMALL AUTOMORPHISM GROUPS THAT ARE CAYLEY ON TWO NONISOMORPHIC GROUPS
 DIGRAPHS WITH SMALL AUTOMORPHISM GROUPS THAT ARE CAYLEY ON TWO NONISOMORPHIC GROUPS LUKE MORGAN, JOY MORRIS, AND GABRIEL VERRET Abstract. Let Γ = Cay(G, S) be a Cayley digraph on a group G and let A =
DIGRAPHS WITH SMALL AUTOMORPHISM GROUPS THAT ARE CAYLEY ON TWO NONISOMORPHIC GROUPS LUKE MORGAN, JOY MORRIS, AND GABRIEL VERRET Abstract. Let Γ = Cay(G, S) be a Cayley digraph on a group G and let A =
Classification of root systems
 Classification of root systems September 8, 2017 1 Introduction These notes are an approximate outline of some of the material to be covered on Thursday, April 9; Tuesday, April 14; and Thursday, April
Classification of root systems September 8, 2017 1 Introduction These notes are an approximate outline of some of the material to be covered on Thursday, April 9; Tuesday, April 14; and Thursday, April
Transitive groups, derangements and related problems
 Transitive groups, derangements and related problems Tim Burness University of Bristol Algebraic Combinatorics and Group Actions Herstmonceux Castle July 11th 2016 Introduction Let G be a group acting
Transitive groups, derangements and related problems Tim Burness University of Bristol Algebraic Combinatorics and Group Actions Herstmonceux Castle July 11th 2016 Introduction Let G be a group acting
THE REPRESENTATION THEORY, GEOMETRY, AND COMBINATORICS OF BRANCHED COVERS
 THE REPRESENTATION THEORY, GEOMETRY, AND COMBINATORICS OF BRANCHED COVERS BRIAN OSSERMAN Abstract. The study of branched covers of the Riemann sphere has connections to many fields. We recall the classical
THE REPRESENTATION THEORY, GEOMETRY, AND COMBINATORICS OF BRANCHED COVERS BRIAN OSSERMAN Abstract. The study of branched covers of the Riemann sphere has connections to many fields. We recall the classical
ALGEBRAIC GROUPS J. WARNER
 ALGEBRAIC GROUPS J. WARNER Let k be an algebraically closed field. varieties unless otherwise stated. 1. Definitions and Examples For simplicity we will work strictly with affine Definition 1.1. An algebraic
ALGEBRAIC GROUPS J. WARNER Let k be an algebraically closed field. varieties unless otherwise stated. 1. Definitions and Examples For simplicity we will work strictly with affine Definition 1.1. An algebraic
ECEN 5022 Cryptography
 Elementary Algebra and Number Theory University of Colorado Spring 2008 Divisibility, Primes Definition. N denotes the set {1, 2, 3,...} of natural numbers and Z denotes the set of integers {..., 2, 1,
Elementary Algebra and Number Theory University of Colorado Spring 2008 Divisibility, Primes Definition. N denotes the set {1, 2, 3,...} of natural numbers and Z denotes the set of integers {..., 2, 1,
THE 2-MODULAR DECOMPOSITION MATRICES OF THE SYMMETRIC GROUPS S 15, S 16, AND S 17
 THE 2-MODULAR DECOMPOSITION MATRICES OF THE SYMMETRIC GROUPS S 15, S 16, AND S 17 Abstract. In this paper the 2-modular decomposition matrices of the symmetric groups S 15, S 16, and S 17 are determined
THE 2-MODULAR DECOMPOSITION MATRICES OF THE SYMMETRIC GROUPS S 15, S 16, AND S 17 Abstract. In this paper the 2-modular decomposition matrices of the symmetric groups S 15, S 16, and S 17 are determined
Galois Groups of CM Fields in Degrees 24, 28, and 30
 Lehigh University Lehigh Preserve Theses and Dissertations 2017 Galois Groups of CM Fields in Degrees 24, 28, and 30 Alexander P. Borselli Lehigh University Follow this and additional works at: http://preserve.lehigh.edu/etd
Lehigh University Lehigh Preserve Theses and Dissertations 2017 Galois Groups of CM Fields in Degrees 24, 28, and 30 Alexander P. Borselli Lehigh University Follow this and additional works at: http://preserve.lehigh.edu/etd
Quasi-reducible Polynomials
 Quasi-reducible Polynomials Jacques Willekens 06-Dec-2008 Abstract In this article, we investigate polynomials that are irreducible over Q, but are reducible modulo any prime number. 1 Introduction Let
Quasi-reducible Polynomials Jacques Willekens 06-Dec-2008 Abstract In this article, we investigate polynomials that are irreducible over Q, but are reducible modulo any prime number. 1 Introduction Let
