Non-Bayesian decision making
|
|
|
- Lionel Dennis
- 5 years ago
- Views:
Transcription
1 Non-Bayesian decision making 1/47 Václav Hlaváč Czech Technical University in Prague Czech Institute of Informatics, Robotics and Cybernetics Prague 6, Jugoslávských partyzánů 1580/3, Czech Republic also Center for Machine Perception, Lecture plan Penalties and probabilities which do not suffice for Bayesian task. Task formulation of prototype non-bayesian tasks. Unified formalism leading to a solution the pair of dual tasks of linear programming. Solution to non-bayesian tasks. Courtesy: Vojtěch Franc.
2 Bayesian task (rehearsal) 2/47 Bayesian task of statistical decision making seeks for sets X, Y and D, statistical model, i.e joint probability function as a function of two variables p XY : X Y R penalty function W : Y D R Bayesian strategy Q: X D, which minimizes the Bayesian risk R(Q) = x X y Y p XY (x, y) W (y, Q(x)). Typical use: minimizing the probability of a wrong classification.
3 Bayesian approach, limitations 3/47 Despite the generality of Bayesian approach, there are many tasks, which cannot be expressed within Bayesian framework. Why? It is difficult to establish a penalty function. E.g., it does not assume values from the totally ordered set. A priori probabilities pk(y), y Y, are not known or cannot be known because y is not a random event. Conditional probabilities p(x y) are difficult to express.
4 Non-Bayesian formulations can be natural for practical tasks 4/47 Even is the case, in which events are random and all involved probabilities are known, it is sometimes of advantage to approach the problem as a non-bayesian one. In practical tasks, it can be more intuitive for a customer to express desired classifier properties as the acceptable rate of false positives (false alarms) and false negatives (overlooked danger). Example: In a quality check of electronic components (e.g., in a tantalum capacitors production), it is common for the customers to express allowed number of rejects (false negatives, overlooked danger) in erroneous pieces per million (ppm).
5 Way out (only in a few special cases): Non-Bayesian formulations 5/47 Good news There are several practically useful non-bayesian tasks, for which a solution similar to Bayesian tasks exist. These non-bayesian tasks can be expressed in a general framework of linear programming, in which the solution is easy and intuitive. Bad news The class of non-bayesian tasks covers only a small subset of possible tasks. Analogy: a few known positive islands in a sea of unknown. Nothing can be said about the task and its solution if it does not belong to non-bayesian tasks.
6 Penalty function in Bayesian decision making 6/47 The decision is rated by a real number, which corresponds to a penalty function value. The quality of the decision has to be expressed in compatible units. Values of a penalty function have to constitute an ordered set. The addition and multiplication has exist for this set.
7 Problems due to penalty function Minimization of the mathematical expectation of the penalty requires that the penalty assumes the value in the totally ordered set (by relation < or ) and the multiplication by a real number and the addition are defined. An example from a Russian fairy tale: A hero comes to the place where he must make a decision. When the hero turns to the left, he loses his horse, when he turns to the right, he loses his sword, and when he turns back, he loses his beloved girl. Is the sum of p 1 horses and p 2 swords is less or more than p 3 beloved girls? 7/47 Often various losses cannot be measured by the same unit even in a single application. The penalty for the false positive (false alarm) and the false negative (overlooked danger) might be incomparable.
8 Example: Decisions when curing a patient 8/47 x X, i.e. observable parameters (features, observations) measured on a patient y Y, i.e. hidden parameters = {healthy, seriously sick} d D, i.e. decisions = {do not cure, apply a drug} Penalty function W : Y D R Y \ D do not cure apply a drug healthy correct decision small health damage seriously sick death possible correct decision This examples illustrates the difficulty with assigning a penalty (real number) to a decision. Note: Health insurance companies overcome this problem by assessing everything by money.
9 Troubles with a priori probability of situations It can be difficult to find a priori probabilities p Y (y), y Y, which are needed in Bayesian formulation. Recall p(x, y) = p(x y) p(y). Reasons: 1. Hidden state is random but a priori probabilities p Y (y), y Y, are unknown. An object has not been analyzed sufficiently. The hint has two options: (a) Do not formulate the task in the Bayesian framework but in another one that does not require statistical properties of the object, which are unknown. (b) Start analyzing the object thoroughly and get a priori probabilities, which are inevitable for the Bayesian solution. 2. Hidden state is not random. Consequently, the a priori probabilities p Y (y), y Y, do not exist. It is impossible to discover them by an arbitrary detailed exploration of the object. The hint is to check if one of non-bayesian methods can be used. 9/47
10 An example: Enemy or allied airplane? 10/47 Observation x describes the observed airplane, e.g. in a radar signal. Two hidden states { y = 1 allied airplane, y = 2 enemy airplane. The conditional probability px Y (x y) might depend on the observation x in a complicated manner. Nevertheless, it exists and describes the dependence of the observation x on the situation y correctly. A priori probabilities py (y) are not known. They even cannot be known in principle because it is impossible to say about any number α, 0 α 1, that α is the probability of the enemy plane occurrence. Consequently py (y) do not exist since the frequency of the experiment result does not converge to any number, which can be named the probability. The hidden state y is not a random event.
11 Beware of a pseudosolution 11/47 Refers to the airplane example. If a priori probabilities are unknown, the situation is avoided wrongly by supposing that a priori probabilities are the same for all possible situations, e.g., the occurrence of the enemy plane has the same probability as the occurrence of the allied one. It is obvious that the supposition does not correspond to the reality even if we assume that the occurrence of a plane is a random event. Missing logical arguments are quickly substituted by a pseudo-argument as referencing, e.g., to C. Shannon and to the widely known property that the uniform probability distribution has the highest entropy. It is happening even if C. Shannon s result does not concern the studied problem in any way.
12 Conditional probabilities of observations 12/47 Motivating example: Recognizing characters written by three persons Given: X is a set of pictures of hand written characters x. y is a name (label) of a character, y Y. z Z = {1, 2, 3} identifies the writer (this info is not known it is an unobservable intervention). Task: Recognize, which character is written in the picture x? We can talk about the penalty function W (y, d) and a priori probabilities p Y (y) of individual characters. We cannot talk about conditional probabilities p X Y (x y) because the appearance x of a character does not depend only on the character label but also on a non-random intervention (i.e., who wrote it).
13 Example: Recognizing characters written by three persons (2) We can speak only about conditional probabilities px Y,Z(x y, z), i.e., how a character looks provided it was written by a certain person. 13/47 If the intervention z would be random and pz(z) would be known for each z then it would be possible to speak also about probabilities p X Y (x y) = 3 z=1 p Z (z) p X Y,Z (x y, z). However, we do not know how often it will be necessary to recognize pictures handwritten by this or that person. Under such uncertain statistical conditions, the algorithm ought to be created that will secure the required recognition quality of pictures independently of who wrote the letter. The concept of a priori probabilities p Z (z) of the variable z cannot be used because z is not random and a probability is not defined for it.
14 Formulations of Non-Bayesian tasks Introduction 14/47 Let us introduce several known non-bayesian tasks (and several original extensions of them by M. I. Schlesinger). The whole class of solvable non-bayesian tasks has two common features: 1. There is one formalism for expressing tasks and their solution (dual tasks of linear programming). 2. Similarly to Bayesian tasks: The decision strategy divides the space of probabilities into convex cones.
15 Basic concepts; Female detection example (1) 15/47 A person is characterized by the: Observed parameters, the height and the weight in our case, x X = {short, average, tall} }{{} height {lean, light, average, heavy} }{{} weight Class label = sex, i.e. y Y = {male, female}. A priori probabilities are unknown. Conditional probabilities are known, e.g.:
16 Basic concepts; Female detection example (2) 16/47 Goal: Find a decision strategy q Q: X Y allowing to detect females among persons based on the observed height and weight. The decision strategy q splits the set X of observations into two subsets: X male = {x Q(x) = male} X female = {x Q(x) = female} } such that { Xmale X female = X, X male X female =. short female female female male Example of one possible strategy Q(x) y average tall female female male male male male male male lean light average heavy
17 Basic concepts; Female detection example (3) The decision strategy q Q: X Y is characterized by the probability of: ω(fp) = p X Y (x male)... false positive, (also false alarm or x X female Type 2 error i.e. a male recognized wrongly as a female). ω(fn) = p X Y (x female)... false negative (also overlooked danger or x X male Type 1 error, i.e. a female recognized wrongly as a male). Conditional probablities repeated from slide 15. The color label female (red) or male (blue) was added for one possible strategy the for the illustration. 17/47 (female) (male) short short average average tall tall lean light average heavy lean light average heavy
18 Neyman Pearson task, two classes only (1) 18/47 Proposed by Jerzy Neyman and Egon Pearson in the paper On the Problem of the Most Efficient Tests of Statistical Hypotheses in Observation x X, two states: { y = 1... the normal state, y = 2... the dangerous state. The probability distribution of the observation x depends on the state y, into which the object belongs. x X, y Y. p X Y (x y) are known. The set X is to be divided into two such subsets X1 (normal states) and X 2 (dangerous states), X = X 1 X 2, X = X 1 X 2 =. Given observation x, the task is to decide if the object is in the normal or dangerous state.
19 Neyman Pearson task (2) 19/47 The observation x can belong either to normal state or to dangerous state. There is no faultless strategy. The strategy is characterized by two numbers ω(fp), ω(fn): Probability of the false positive (false alarm) ω(fp) = x X 2 p X Y (x 1). Probability of the false negative (overlooked danger) ω(fn) = x X 1 p X Y (x 2).
20 Neyman Pearson task (3) A strategy is sought in the Neyman Pearson task, i.e., a decomposition of X into X 1 X, X 1 X 2 = X, X 2 X, X 1 X 2 =, such that: 1. The conditional probability of the false negative is not larger than the prescribed limit (threshold) ε, 0 < ε < 1, on the probability of the false negative (overlooked danger). This yields eligible strategies. ω(fn) = x X 1 p X Y (x 2) ε. 20/47 2. A strategy q is sought among eligible strategies, which has the conditional probability of the false positive is the smallest. q = argmin ω(fp) = argmin p X Y (x 1) subject to the condition q:x Y q:x Y x X 2 ω(fn) = x X 1 p X Y (x 2) ε.
21 Trivial example: men/women by weight only (1) 21/47 We start the explanation even with a simpler example using only one observation: weight. The person height is not taken into account for a moment. The Females detection example by the weight only formulation: The observation x (weight of the person), x X = {lean, leight, average, heavy}. The hidden state y Y = {male, female}. ε = 0.2 meaning that the prescribed probability of the false negative (overlooking a female) is 20% at most. The decision strategy q has to be the Neyman-Pearson strategy. The number of all possible strategies is 2 X = 16.
22 Trivial example: men/women by weight only (2) p(x y = male) p(x y = female) 22/47 lean leight average heavy lean leight average heavy under the condition min p(x y = male) x X female x X male p(x y = female) 0.20 i.e., false alarm i.e., overlooked female eligible solutions{ optimal solution lean light average heavy overlooked false alarm female 1 female female female female female female female male female female male female female female male male female male female female male male male male
23 Neyman Pearson task; the solution (4) 23/47 The solution is by J. Neyman and E. Pearson (1928, 1933). The optimal strategy q separates the observation sets X1 and X2 according to the threshold θ on the likelihood ratio L(x) value. The optimal strategy q is obtained by selecting the minimal θ, for which q = (x 1) y = 1 (normal state) if L(x) = p X Y p X Y (x 2) > θ, y = 2 (dangerous state) othewise. The rule is the special case of the division of a space of probabilities into convex cones, i.e., it corresponds to Bayesian strategy. It was explained in the Bayesian lecture.
24 Female detection example, Neyman-Pearson (4) 24/47 Taking into account known conditional probabilities (Table A and Table B), the likelihood ratio L(x) is calculated. It yields Table C. We order likelihood ratios L(x) from the smallest one to the biggest one. The appropriate rank as shown in Table D. There are 12 possible strategies. Let us set the threshold θ values for the strategies. The value θ for the particular strategy lies in between the two limit values L(x) in Table C corresponding to neighboring ranks. Let us set θ as the average of limit values L(x) corresponding to the pair of neighboring ranks. Let us label strategies by the higher rank number of the pair.
25 Female detection example, Neyman-Pearson (5) 25/47 In this example, different likelihood ratios L(x) produce 11 possible strategies out of 12 L(x) entries. Strategy #12 is not possible and is shown as empty in the tables. We display these 11 possible strategies. Table entry colors (female=red; male=blue) denote a particular strategy. If L(x) of the entry is above the threshold θ then the entry is labeled as female. The next job is to select the optimal strategy.
26 Female detection example, Neyman-Pearson (6) For each possible strategy, we calculated ω(f P ) and ω(f N). We selected from eligible strategies (ω(f P ) 0.2) the optimal strategy #5 because of the minimal ω(f N). 26/47
27 Solving Non-Bayesian tasks using linear programming (LP) 27/47 Decision strategies Q: X Y can be equivalently represented by a function α: X Y {1, 0} satisfying y Y α(x, y) = 1, x X, α(x, y) {0, 1}, x X, y Y. Values of α for the Female detection example, cf. slide 15: (x, male) (x, female) short short average average tall tall lean light average heavy lean light average heavy
28 Neyman-Pearson task solved by LP To avoid integer programming, the relaxed stochastic strategy α: X Y 0, 1 is introduced, which satisfies α(x, 1) + α(x, 2) = 1, x X, α(x, y) 0, x X, y {1, 2}. Linear programming relaxation Original formulation 28/47 α = argmin α subject to x X α(x, 2) p X Y (x 1), subject to Q = argmin X 1,X 2 x X 2 p X Y (x 1), x X α(x, 1)p X Y (x, 2) ε, x X 1 p X Y (x 2) ε. α(x, 1) + α(x, 2) = 1, x X, α(x, 1) 0, x X, α(x, 2) 0, x X.
29 Neyman-Pearson task as LP (2) 29/47 The dual formulation of the Neyman-Pearson task ( ) (t(x), τ ) = argmax t(x),τ x X t(x) ε τ subject to t(x) τ p X Y (x 2) 0, x X, t(x) p X Y (x 1) 0, x X, τ 0.
30 Female detection example, Neyman-Pearson (1) 30/47 The decision strategy q : x y is characterized by two probabilities ω(male), ω(female) and the likelihood ratio threshold θ; θ = 0.2 in this example. ω(female) = p(x male) x X female ω(male) = p(x female) x X male... false positive We seek the decision strategy q : x {male, female} q = argmin X male,x female... false negative (overlooked girl) x X female p(x male) under the condition x X male p(x female) 0.2
31 Generalised Neyman-Pearson task for two dangerous states 31/47 y = 1 corresponds to the set X1; y = 2 or y = 3 correspond to the set X23. We seek a strategy with the conditional probability of the false positives (overlooked dangerous states) both y = 2 and y = 3 is not larger than a value ε given in advance. Simultaneously, the strategy minimizes the false negatives (false alarms), x X 23 p X Y (x 1) under the conditions x X 1 p X Y (x 2) ε, x X 1 p X Y (x 3) ε, X 1 X 23 =, X 1 X 23 = X. The formulated optimization task will be solved later in a single constructive framework.
32 Minimax task, introduction Selects the strategy according to the worst case scenario. 32/47 Observations X are decomposed into subsets X(y), y Y, such that they minimize the number max y Y ω(y). Consider a customer who demands that the PR algorithm will be evaluated by two tests in advance: Preliminary test (performed by the customer himself) checks the probability of a wrong decision ω(y) for all states y. The customer selects the worst state y = argmax y Y ω(y). Final test checks only those objects which are in the worst state. The result of the final test will be written in the protocol and the final evaluation depends on the protocol content. The algorithm designer aims to achieve the best result in the final test. The problem has not been widely known for the more general case, i.e., for the arbitrary number of object states.
33 Minimax task (2) 33/47 x X are observable parameters. y Y are hidden states. Q: X Y is the sought strategy given by the decomposition X = X 1 X 2... X Y Each strategy is characterized by Y numbers ω(y) = x/ X(y) p(x y), i.e., conditional probabilities of a wrong decision under the condition that the correct hidden state is y.
34 Minimax task (3) 34/47 Minimax task formulation A strategy q is sought which minimizes max y Y ω(y) The solution decomposes the space of probabilities into convex cones. Notice that the case Y = 2 is the Neyman-Pearson task in which convex cones degenerate to 1D case a likelihood ratio. Notice that the strategy belongs to the Bayesian family.
35 Wald task (motivation) 35/47 A tiny part of Wald sequential analysis (1947). Neyman-Pearson task lacks symmetry with respect to states of the recognized object. The conditional probability of the false negative (overlooked danger) must be small, which is the principal requirement. The conditional probability of the false positive (false alarm) is a subsidiary requirement. It can be only demanded to be as small as possible even if this minimum can be even big. It would be excellent if such a strategy were found for which both probabilities would not exceed a predefined value ε. These demands can be antagonistic and that is why the task could not be accomplished by using such a formulation.
36 Wald task (2) 36/47 Classification in three subsets X 0, X 1 and X 2 with the following meaning: if x X1, then y = 1 is chosen; if x X2, then y = 2 is chosen; and finally if x X0 it is decided that the observation x does not provide enough information for a safe decision about the state y.
37 Wald task (3) 37/47 A strategy of this kind will be characterized by four numbers: ω(1) is a conditional probability of a wrong decision about the state y = 1, ω(1) = x X 2 p X Y (x 1), ω(2) is a conditional probability of a wrong decision about the state y = 2, ω(2) = x X 1 p X Y (x 2). χ(1) is a conditional probability of a indecisive situation under the condition that the object is in the state y = 1, χ(1) = x X 0 p X Y (x 1). χ(2) is a conditional probability of the indecisive situation under the condition that the object is in the state y = 2, χ(2) = x X 0 p X Y (x 2).
38 Wald task (4) 38/47 For such strategies, the requirements ω(1) ε and ω(2) ε are not contradictory for an arbitrary non-negative value ε because the strategy X 0 = X, X 1 =, X 2 = belongs to the class of allowed strategies too. Each strategy fulfilling ω(1) ε and ω(2) ε is characterized by how often the strategy is reluctant to decide, i.e., by the number max ( χ(1), χ(2) ). The strategy q which minimizes max (χ(1), χ(2)) is sought.
39 Wald task (5) 39/47 Solution (without proof) of this task for two states only is based on the calculation of the likelihood ratio γ(x) = p X Y (x 1) p X Y (x 2). Based on comparison to two thresholds θ 1, θ 2, θ 1 θ 2 it is decided for class 1, class 2 or the solution is undecided. In the SH10 book, there the generalization for > 2 states is explained.
40 Wald task, example Men, women, weight, height 40/47
41 Wald task, example (2) Men, women, weight, height 41/47
42 Linnik tasks = decisions with non-random interventions 42/47 In previous non-bayesian tasks, either the penalty function or a priori probabilities of the states do not make sense. In Linnik tasks, even the conditional probabilities px Y (x y) do not exist. Proposed by the Russian mathematician J.V. Linnik in Random observation x depends on the object state and on an additional unobservable parameter z. The user is not interested in z and thus it need not be estimated. However, the parameter z must be taken into account because conditional probabilities p X Y (x y) are not defined. Conditional probabilities px Y,Z(x y, z) do exist.
43 Linnik tasks (2) 43/47 Other names used for Linnik tasks: Statistical decisions with non-random interventions. Evaluations of complex hypotheses. Let us mention two examples from many possibilities: Testing of complex hypotheses with random state and with non-random intervention Testing of complex hypotheses with non-random state and with non-random interventions.
44 Linnik task with random state and non-random interventions (1) 44/47 X, Y, Z are finite sets of possible observation x, state y and intervention z. p K (y) be the a priori probability of the state y. px Y,Z(x y, z) be the conditional probability of the observation x under the condition of the state y and intervention z. X(y), y y decomposes X according to some strategy determining states y. The probability of the incorrect decision (quality) depends on z ω(z) = y Y p Y (y) x/ X(y) p X Y,Z (x y, z).
45 Linnik task with random state and non-random interventions (2) 45/47 The quality ω of a strategy (X(y), y Y ) is defined as the probability of the incorrect decision obtained in the case of the worst intervention z for this strategy, that is ω = max z Z ω(z). ω is minimised, i.e., ( X (y), y Y ) = argmin (X(y),y Y ) max z Z y Y p Y (y) x/ X(y) p X Y,Z (x y, z).
46 Linnik task with non-random state and non-random interventions (1) 46/47 Neither the state y nor intervention z can be considered as a random variable and consequently a priori probabilities p Y (y) are not defined. Quality ω depends not only on the intervention z but also on the state y ω(y, z) = x/ X(y) p X Y,Z (x y, z).
47 Linnik task with non-random state and non-random interventions (2) 47/47 The quality ω ω = max y Y max z Z ω(y, z), The task is formulated as a search for the best strategy in this sense, i.e., as a search for decomposition ( X (y), y Y ) = argmin (X(y),y Y ) max y Y max z Z x/ X(y) p X Y,Z (x y, z).
Bayesian decision making
 Bayesian decision making Václav Hlaváč Czech Technical University in Prague Czech Institute of Informatics, Robotics and Cybernetics 166 36 Prague 6, Jugoslávských partyzánů 1580/3, Czech Republic http://people.ciirc.cvut.cz/hlavac,
Bayesian decision making Václav Hlaváč Czech Technical University in Prague Czech Institute of Informatics, Robotics and Cybernetics 166 36 Prague 6, Jugoslávských partyzánů 1580/3, Czech Republic http://people.ciirc.cvut.cz/hlavac,
Intelligent Systems Statistical Machine Learning
 Intelligent Systems Statistical Machine Learning Carsten Rother, Dmitrij Schlesinger WS2015/2016, Our model and tasks The model: two variables are usually present: - the first one is typically discrete
Intelligent Systems Statistical Machine Learning Carsten Rother, Dmitrij Schlesinger WS2015/2016, Our model and tasks The model: two variables are usually present: - the first one is typically discrete
Intelligent Systems Statistical Machine Learning
 Intelligent Systems Statistical Machine Learning Carsten Rother, Dmitrij Schlesinger WS2014/2015, Our tasks (recap) The model: two variables are usually present: - the first one is typically discrete k
Intelligent Systems Statistical Machine Learning Carsten Rother, Dmitrij Schlesinger WS2014/2015, Our tasks (recap) The model: two variables are usually present: - the first one is typically discrete k
Bayesian Decision Theory
 Bayesian Decision Theory 1/27 lecturer: authors: Jiri Matas, matas@cmp.felk.cvut.cz Václav Hlaváč, Jiri Matas Czech Technical University, Faculty of Electrical Engineering Department of Cybernetics, Center
Bayesian Decision Theory 1/27 lecturer: authors: Jiri Matas, matas@cmp.felk.cvut.cz Václav Hlaváč, Jiri Matas Czech Technical University, Faculty of Electrical Engineering Department of Cybernetics, Center
Probability and statistics; Rehearsal for pattern recognition
 Probability and statistics; Rehearsal for pattern recognition Václav Hlaváč Czech Technical University in Prague Czech Institute of Informatics, Robotics and Cybernetics 166 36 Prague 6, Jugoslávských
Probability and statistics; Rehearsal for pattern recognition Václav Hlaváč Czech Technical University in Prague Czech Institute of Informatics, Robotics and Cybernetics 166 36 Prague 6, Jugoslávských
Classifier performance evaluation
 Classifier performance evaluation Václav Hlaváč Czech Technical University in Prague Czech Institute of Informatics, Robotics and Cybernetics 166 36 Prague 6, Jugoslávských partyzánu 1580/3, Czech Republic
Classifier performance evaluation Václav Hlaváč Czech Technical University in Prague Czech Institute of Informatics, Robotics and Cybernetics 166 36 Prague 6, Jugoslávských partyzánu 1580/3, Czech Republic
Pattern Recognition and Machine Learning Course: Introduction. Bayesian Decision Theory.
 Pattern Recognition and Machine Learning Course: Introduction. Bayesian Decision Theory. lecturer: authors: Jiří Matas, matas@cmp.felk.cvut.cz Václav Hlaváč, Jiří Matas, Ondřej Drbohlav Czech Technical
Pattern Recognition and Machine Learning Course: Introduction. Bayesian Decision Theory. lecturer: authors: Jiří Matas, matas@cmp.felk.cvut.cz Václav Hlaváč, Jiří Matas, Ondřej Drbohlav Czech Technical
LEARNING & LINEAR CLASSIFIERS
 LEARNING & LINEAR CLASSIFIERS 1/26 J. Matas Czech Technical University, Faculty of Electrical Engineering Department of Cybernetics, Center for Machine Perception 121 35 Praha 2, Karlovo nám. 13, Czech
LEARNING & LINEAR CLASSIFIERS 1/26 J. Matas Czech Technical University, Faculty of Electrical Engineering Department of Cybernetics, Center for Machine Perception 121 35 Praha 2, Karlovo nám. 13, Czech
Pattern Recognition and Machine Learning Course: Introduction. Bayesian Decision Theory.
 Pattern Recognition and Machine Learning Course: Introduction. Bayesian Decision Theory. lecturer: authors: Jiří Matas, matas@cmp.felk.cvut.cz Václav Hlaváč, Jiří Matas, Ondřej Drbohlav Czech Technical
Pattern Recognition and Machine Learning Course: Introduction. Bayesian Decision Theory. lecturer: authors: Jiří Matas, matas@cmp.felk.cvut.cz Václav Hlaváč, Jiří Matas, Ondřej Drbohlav Czech Technical
Topic 3: Hypothesis Testing
 CS 8850: Advanced Machine Learning Fall 07 Topic 3: Hypothesis Testing Instructor: Daniel L. Pimentel-Alarcón c Copyright 07 3. Introduction One of the simplest inference problems is that of deciding between
CS 8850: Advanced Machine Learning Fall 07 Topic 3: Hypothesis Testing Instructor: Daniel L. Pimentel-Alarcón c Copyright 07 3. Introduction One of the simplest inference problems is that of deciding between
Nonparametric probability density estimation
 A temporary version for the 2018-04-11 lecture. Nonparametric probability density estimation Václav Hlaváč Czech Technical University in Prague Czech Institute of Informatics, Robotics and Cybernetics
A temporary version for the 2018-04-11 lecture. Nonparametric probability density estimation Václav Hlaváč Czech Technical University in Prague Czech Institute of Informatics, Robotics and Cybernetics
Lecture 7 Introduction to Statistical Decision Theory
 Lecture 7 Introduction to Statistical Decision Theory I-Hsiang Wang Department of Electrical Engineering National Taiwan University ihwang@ntu.edu.tw December 20, 2016 1 / 55 I-Hsiang Wang IT Lecture 7
Lecture 7 Introduction to Statistical Decision Theory I-Hsiang Wang Department of Electrical Engineering National Taiwan University ihwang@ntu.edu.tw December 20, 2016 1 / 55 I-Hsiang Wang IT Lecture 7
 http://www.math.uah.edu/stat/hypothesis/.xhtml 1 of 5 7/29/2009 3:14 PM Virtual Laboratories > 9. Hy pothesis Testing > 1 2 3 4 5 6 7 1. The Basic Statistical Model As usual, our starting point is a random
http://www.math.uah.edu/stat/hypothesis/.xhtml 1 of 5 7/29/2009 3:14 PM Virtual Laboratories > 9. Hy pothesis Testing > 1 2 3 4 5 6 7 1. The Basic Statistical Model As usual, our starting point is a random
Problem Set 2. MAS 622J/1.126J: Pattern Recognition and Analysis. Due: 5:00 p.m. on September 30
 Problem Set MAS 6J/1.16J: Pattern Recognition and Analysis Due: 5:00 p.m. on September 30 [Note: All instructions to plot data or write a program should be carried out using Matlab. In order to maintain
Problem Set MAS 6J/1.16J: Pattern Recognition and Analysis Due: 5:00 p.m. on September 30 [Note: All instructions to plot data or write a program should be carried out using Matlab. In order to maintain
Sequential Procedure for Testing Hypothesis about Mean of Latent Gaussian Process
 Applied Mathematical Sciences, Vol. 4, 2010, no. 62, 3083-3093 Sequential Procedure for Testing Hypothesis about Mean of Latent Gaussian Process Julia Bondarenko Helmut-Schmidt University Hamburg University
Applied Mathematical Sciences, Vol. 4, 2010, no. 62, 3083-3093 Sequential Procedure for Testing Hypothesis about Mean of Latent Gaussian Process Julia Bondarenko Helmut-Schmidt University Hamburg University
CSCI-567: Machine Learning (Spring 2019)
 CSCI-567: Machine Learning (Spring 2019) Prof. Victor Adamchik U of Southern California Mar. 19, 2019 March 19, 2019 1 / 43 Administration March 19, 2019 2 / 43 Administration TA3 is due this week March
CSCI-567: Machine Learning (Spring 2019) Prof. Victor Adamchik U of Southern California Mar. 19, 2019 March 19, 2019 1 / 43 Administration March 19, 2019 2 / 43 Administration TA3 is due this week March
Mathematics-I Prof. S.K. Ray Department of Mathematics and Statistics Indian Institute of Technology, Kanpur. Lecture 1 Real Numbers
 Mathematics-I Prof. S.K. Ray Department of Mathematics and Statistics Indian Institute of Technology, Kanpur Lecture 1 Real Numbers In these lectures, we are going to study a branch of mathematics called
Mathematics-I Prof. S.K. Ray Department of Mathematics and Statistics Indian Institute of Technology, Kanpur Lecture 1 Real Numbers In these lectures, we are going to study a branch of mathematics called
Machine Learning. Lecture 9: Learning Theory. Feng Li.
 Machine Learning Lecture 9: Learning Theory Feng Li fli@sdu.edu.cn https://funglee.github.io School of Computer Science and Technology Shandong University Fall 2018 Why Learning Theory How can we tell
Machine Learning Lecture 9: Learning Theory Feng Li fli@sdu.edu.cn https://funglee.github.io School of Computer Science and Technology Shandong University Fall 2018 Why Learning Theory How can we tell
Bayesian Decision Theory
 Introduction to Pattern Recognition [ Part 4 ] Mahdi Vasighi Remarks It is quite common to assume that the data in each class are adequately described by a Gaussian distribution. Bayesian classifier is
Introduction to Pattern Recognition [ Part 4 ] Mahdi Vasighi Remarks It is quite common to assume that the data in each class are adequately described by a Gaussian distribution. Bayesian classifier is
Information measures in simple coding problems
 Part I Information measures in simple coding problems in this web service in this web service Source coding and hypothesis testing; information measures A(discrete)source is a sequence {X i } i= of random
Part I Information measures in simple coding problems in this web service in this web service Source coding and hypothesis testing; information measures A(discrete)source is a sequence {X i } i= of random
MIDTERM: CS 6375 INSTRUCTOR: VIBHAV GOGATE October,
 MIDTERM: CS 6375 INSTRUCTOR: VIBHAV GOGATE October, 23 2013 The exam is closed book. You are allowed a one-page cheat sheet. Answer the questions in the spaces provided on the question sheets. If you run
MIDTERM: CS 6375 INSTRUCTOR: VIBHAV GOGATE October, 23 2013 The exam is closed book. You are allowed a one-page cheat sheet. Answer the questions in the spaces provided on the question sheets. If you run
PATTERN RECOGNITION AND MACHINE LEARNING
 PATTERN RECOGNITION AND MACHINE LEARNING Slide Set 3: Detection Theory January 2018 Heikki Huttunen heikki.huttunen@tut.fi Department of Signal Processing Tampere University of Technology Detection theory
PATTERN RECOGNITION AND MACHINE LEARNING Slide Set 3: Detection Theory January 2018 Heikki Huttunen heikki.huttunen@tut.fi Department of Signal Processing Tampere University of Technology Detection theory
Lecture 9: PGM Learning
 13 Oct 2014 Intro. to Stats. Machine Learning COMP SCI 4401/7401 Table of Contents I Learning parameters in MRFs 1 Learning parameters in MRFs Inference and Learning Given parameters (of potentials) and
13 Oct 2014 Intro. to Stats. Machine Learning COMP SCI 4401/7401 Table of Contents I Learning parameters in MRFs 1 Learning parameters in MRFs Inference and Learning Given parameters (of potentials) and
Lecture 8: Information Theory and Statistics
 Lecture 8: Information Theory and Statistics Part II: Hypothesis Testing and Estimation I-Hsiang Wang Department of Electrical Engineering National Taiwan University ihwang@ntu.edu.tw December 22, 2015
Lecture 8: Information Theory and Statistics Part II: Hypothesis Testing and Estimation I-Hsiang Wang Department of Electrical Engineering National Taiwan University ihwang@ntu.edu.tw December 22, 2015
Error Rates. Error vs Threshold. ROC Curve. Biometrics: A Pattern Recognition System. Pattern classification. Biometrics CSE 190 Lecture 3
 Biometrics: A Pattern Recognition System Yes/No Pattern classification Biometrics CSE 190 Lecture 3 Authentication False accept rate (FAR): Proportion of imposters accepted False reject rate (FRR): Proportion
Biometrics: A Pattern Recognition System Yes/No Pattern classification Biometrics CSE 190 Lecture 3 Authentication False accept rate (FAR): Proportion of imposters accepted False reject rate (FRR): Proportion
ECE521 Lecture7. Logistic Regression
 ECE521 Lecture7 Logistic Regression Outline Review of decision theory Logistic regression A single neuron Multi-class classification 2 Outline Decision theory is conceptually easy and computationally hard
ECE521 Lecture7 Logistic Regression Outline Review of decision theory Logistic regression A single neuron Multi-class classification 2 Outline Decision theory is conceptually easy and computationally hard
Probabilistic classification CE-717: Machine Learning Sharif University of Technology. M. Soleymani Fall 2016
 Probabilistic classification CE-717: Machine Learning Sharif University of Technology M. Soleymani Fall 2016 Topics Probabilistic approach Bayes decision theory Generative models Gaussian Bayes classifier
Probabilistic classification CE-717: Machine Learning Sharif University of Technology M. Soleymani Fall 2016 Topics Probabilistic approach Bayes decision theory Generative models Gaussian Bayes classifier
Multiplex network inference
 (using hidden Markov models) University of Cambridge Bioinformatics Group Meeting 11 February 2016 Words of warning Disclaimer These slides have been produced by combining & translating two of my previous
(using hidden Markov models) University of Cambridge Bioinformatics Group Meeting 11 February 2016 Words of warning Disclaimer These slides have been produced by combining & translating two of my previous
Generative Techniques: Bayes Rule and the Axioms of Probability
 Intelligent Systems: Reasoning and Recognition James L. Crowley ENSIMAG 2 / MoSIG M1 Second Semester 2016/2017 Lesson 8 3 March 2017 Generative Techniques: Bayes Rule and the Axioms of Probability Generative
Intelligent Systems: Reasoning and Recognition James L. Crowley ENSIMAG 2 / MoSIG M1 Second Semester 2016/2017 Lesson 8 3 March 2017 Generative Techniques: Bayes Rule and the Axioms of Probability Generative
EEL 851: Biometrics. An Overview of Statistical Pattern Recognition EEL 851 1
 EEL 851: Biometrics An Overview of Statistical Pattern Recognition EEL 851 1 Outline Introduction Pattern Feature Noise Example Problem Analysis Segmentation Feature Extraction Classification Design Cycle
EEL 851: Biometrics An Overview of Statistical Pattern Recognition EEL 851 1 Outline Introduction Pattern Feature Noise Example Problem Analysis Segmentation Feature Extraction Classification Design Cycle
SYDE 372 Introduction to Pattern Recognition. Probability Measures for Classification: Part I
 SYDE 372 Introduction to Pattern Recognition Probability Measures for Classification: Part I Alexander Wong Department of Systems Design Engineering University of Waterloo Outline 1 2 3 4 Why use probability
SYDE 372 Introduction to Pattern Recognition Probability Measures for Classification: Part I Alexander Wong Department of Systems Design Engineering University of Waterloo Outline 1 2 3 4 Why use probability
Mathematical Statistics
 Mathematical Statistics MAS 713 Chapter 8 Previous lecture: 1 Bayesian Inference 2 Decision theory 3 Bayesian Vs. Frequentist 4 Loss functions 5 Conjugate priors Any questions? Mathematical Statistics
Mathematical Statistics MAS 713 Chapter 8 Previous lecture: 1 Bayesian Inference 2 Decision theory 3 Bayesian Vs. Frequentist 4 Loss functions 5 Conjugate priors Any questions? Mathematical Statistics
CSCI3390-Lecture 6: An Undecidable Problem
 CSCI3390-Lecture 6: An Undecidable Problem September 21, 2018 1 Summary The language L T M recognized by the universal Turing machine is not decidable. Thus there is no algorithm that determines, yes or
CSCI3390-Lecture 6: An Undecidable Problem September 21, 2018 1 Summary The language L T M recognized by the universal Turing machine is not decidable. Thus there is no algorithm that determines, yes or
Real Analysis Prof. S.H. Kulkarni Department of Mathematics Indian Institute of Technology, Madras. Lecture - 13 Conditional Convergence
 Real Analysis Prof. S.H. Kulkarni Department of Mathematics Indian Institute of Technology, Madras Lecture - 13 Conditional Convergence Now, there are a few things that are remaining in the discussion
Real Analysis Prof. S.H. Kulkarni Department of Mathematics Indian Institute of Technology, Madras Lecture - 13 Conditional Convergence Now, there are a few things that are remaining in the discussion
LECTURE NOTE #3 PROF. ALAN YUILLE
 LECTURE NOTE #3 PROF. ALAN YUILLE 1. Three Topics (1) Precision and Recall Curves. Receiver Operating Characteristic Curves (ROC). What to do if we do not fix the loss function? (2) The Curse of Dimensionality.
LECTURE NOTE #3 PROF. ALAN YUILLE 1. Three Topics (1) Precision and Recall Curves. Receiver Operating Characteristic Curves (ROC). What to do if we do not fix the loss function? (2) The Curse of Dimensionality.
What does Bayes theorem give us? Lets revisit the ball in the box example.
 ECE 6430 Pattern Recognition and Analysis Fall 2011 Lecture Notes - 2 What does Bayes theorem give us? Lets revisit the ball in the box example. Figure 1: Boxes with colored balls Last class we answered
ECE 6430 Pattern Recognition and Analysis Fall 2011 Lecture Notes - 2 What does Bayes theorem give us? Lets revisit the ball in the box example. Figure 1: Boxes with colored balls Last class we answered
University of Cambridge Engineering Part IIB Module 3F3: Signal and Pattern Processing Handout 2:. The Multivariate Gaussian & Decision Boundaries
 University of Cambridge Engineering Part IIB Module 3F3: Signal and Pattern Processing Handout :. The Multivariate Gaussian & Decision Boundaries..15.1.5 1 8 6 6 8 1 Mark Gales mjfg@eng.cam.ac.uk Lent
University of Cambridge Engineering Part IIB Module 3F3: Signal and Pattern Processing Handout :. The Multivariate Gaussian & Decision Boundaries..15.1.5 1 8 6 6 8 1 Mark Gales mjfg@eng.cam.ac.uk Lent
Detection and Estimation Chapter 1. Hypothesis Testing
 Detection and Estimation Chapter 1. Hypothesis Testing Husheng Li Min Kao Department of Electrical Engineering and Computer Science University of Tennessee, Knoxville Spring, 2015 1/20 Syllabus Homework:
Detection and Estimation Chapter 1. Hypothesis Testing Husheng Li Min Kao Department of Electrical Engineering and Computer Science University of Tennessee, Knoxville Spring, 2015 1/20 Syllabus Homework:
Computability Crib Sheet
 Computer Science and Engineering, UCSD Winter 10 CSE 200: Computability and Complexity Instructor: Mihir Bellare Computability Crib Sheet January 3, 2010 Computability Crib Sheet This is a quick reference
Computer Science and Engineering, UCSD Winter 10 CSE 200: Computability and Complexity Instructor: Mihir Bellare Computability Crib Sheet January 3, 2010 Computability Crib Sheet This is a quick reference
Machine Learning (CS 567) Lecture 2
 Machine Learning (CS 567) Lecture 2 Time: T-Th 5:00pm - 6:20pm Location: GFS118 Instructor: Sofus A. Macskassy (macskass@usc.edu) Office: SAL 216 Office hours: by appointment Teaching assistant: Cheol
Machine Learning (CS 567) Lecture 2 Time: T-Th 5:00pm - 6:20pm Location: GFS118 Instructor: Sofus A. Macskassy (macskass@usc.edu) Office: SAL 216 Office hours: by appointment Teaching assistant: Cheol
Statistical methods in recognition. Why is classification a problem?
 Statistical methods in recognition Basic steps in classifier design collect training images choose a classification model estimate parameters of classification model from training images evaluate model
Statistical methods in recognition Basic steps in classifier design collect training images choose a classification model estimate parameters of classification model from training images evaluate model
In this initial chapter, you will be introduced to, or more than likely be reminded of, a
 1 Sets In this initial chapter, you will be introduced to, or more than likely be reminded of, a fundamental idea that occurs throughout mathematics: sets. Indeed, a set is an object from which every mathematical
1 Sets In this initial chapter, you will be introduced to, or more than likely be reminded of, a fundamental idea that occurs throughout mathematics: sets. Indeed, a set is an object from which every mathematical
ORF 245 Fundamentals of Statistics Chapter 9 Hypothesis Testing
 ORF 245 Fundamentals of Statistics Chapter 9 Hypothesis Testing Robert Vanderbei Fall 2014 Slides last edited on November 24, 2014 http://www.princeton.edu/ rvdb Coin Tossing Example Consider two coins.
ORF 245 Fundamentals of Statistics Chapter 9 Hypothesis Testing Robert Vanderbei Fall 2014 Slides last edited on November 24, 2014 http://www.princeton.edu/ rvdb Coin Tossing Example Consider two coins.
Recall from last time: Conditional probabilities. Lecture 2: Belief (Bayesian) networks. Bayes ball. Example (continued) Example: Inference problem
 Recall from last time: Conditional probabilities Our probabilistic models will compute and manipulate conditional probabilities. Given two random variables X, Y, we denote by Lecture 2: Belief (Bayesian)
Recall from last time: Conditional probabilities Our probabilistic models will compute and manipulate conditional probabilities. Given two random variables X, Y, we denote by Lecture 2: Belief (Bayesian)
Algorithmisches Lernen/Machine Learning
 Algorithmisches Lernen/Machine Learning Part 1: Stefan Wermter Introduction Connectionist Learning (e.g. Neural Networks) Decision-Trees, Genetic Algorithms Part 2: Norman Hendrich Support-Vector Machines
Algorithmisches Lernen/Machine Learning Part 1: Stefan Wermter Introduction Connectionist Learning (e.g. Neural Networks) Decision-Trees, Genetic Algorithms Part 2: Norman Hendrich Support-Vector Machines
EM Algorithm LECTURE OUTLINE
 EM Algorithm Lukáš Cerman, Václav Hlaváč Czech Technical University, Faculty of Electrical Engineering Department of Cybernetics, Center for Machine Perception 121 35 Praha 2, Karlovo nám. 13, Czech Republic
EM Algorithm Lukáš Cerman, Václav Hlaváč Czech Technical University, Faculty of Electrical Engineering Department of Cybernetics, Center for Machine Perception 121 35 Praha 2, Karlovo nám. 13, Czech Republic
Binary Logistic Regression
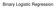 The coefficients of the multiple regression model are estimated using sample data with k independent variables Estimated (or predicted) value of Y Estimated intercept Estimated slope coefficients Ŷ = b
The coefficients of the multiple regression model are estimated using sample data with k independent variables Estimated (or predicted) value of Y Estimated intercept Estimated slope coefficients Ŷ = b
Decision Tree Learning Lecture 2
 Machine Learning Coms-4771 Decision Tree Learning Lecture 2 January 28, 2008 Two Types of Supervised Learning Problems (recap) Feature (input) space X, label (output) space Y. Unknown distribution D over
Machine Learning Coms-4771 Decision Tree Learning Lecture 2 January 28, 2008 Two Types of Supervised Learning Problems (recap) Feature (input) space X, label (output) space Y. Unknown distribution D over
On the errors introduced by the naive Bayes independence assumption
 On the errors introduced by the naive Bayes independence assumption Author Matthijs de Wachter 3671100 Utrecht University Master Thesis Artificial Intelligence Supervisor Dr. Silja Renooij Department of
On the errors introduced by the naive Bayes independence assumption Author Matthijs de Wachter 3671100 Utrecht University Master Thesis Artificial Intelligence Supervisor Dr. Silja Renooij Department of
Machine Learning for Signal Processing Bayes Classification and Regression
 Machine Learning for Signal Processing Bayes Classification and Regression Instructor: Bhiksha Raj 11755/18797 1 Recap: KNN A very effective and simple way of performing classification Simple model: For
Machine Learning for Signal Processing Bayes Classification and Regression Instructor: Bhiksha Raj 11755/18797 1 Recap: KNN A very effective and simple way of performing classification Simple model: For
Lecture 8: Information Theory and Statistics
 Lecture 8: Information Theory and Statistics Part II: Hypothesis Testing and I-Hsiang Wang Department of Electrical Engineering National Taiwan University ihwang@ntu.edu.tw December 23, 2015 1 / 50 I-Hsiang
Lecture 8: Information Theory and Statistics Part II: Hypothesis Testing and I-Hsiang Wang Department of Electrical Engineering National Taiwan University ihwang@ntu.edu.tw December 23, 2015 1 / 50 I-Hsiang
Lecture 1: Entropy, convexity, and matrix scaling CSE 599S: Entropy optimality, Winter 2016 Instructor: James R. Lee Last updated: January 24, 2016
 Lecture 1: Entropy, convexity, and matrix scaling CSE 599S: Entropy optimality, Winter 2016 Instructor: James R. Lee Last updated: January 24, 2016 1 Entropy Since this course is about entropy maximization,
Lecture 1: Entropy, convexity, and matrix scaling CSE 599S: Entropy optimality, Winter 2016 Instructor: James R. Lee Last updated: January 24, 2016 1 Entropy Since this course is about entropy maximization,
October 25, 2013 INNER PRODUCT SPACES
 October 25, 2013 INNER PRODUCT SPACES RODICA D. COSTIN Contents 1. Inner product 2 1.1. Inner product 2 1.2. Inner product spaces 4 2. Orthogonal bases 5 2.1. Existence of an orthogonal basis 7 2.2. Orthogonal
October 25, 2013 INNER PRODUCT SPACES RODICA D. COSTIN Contents 1. Inner product 2 1.1. Inner product 2 1.2. Inner product spaces 4 2. Orthogonal bases 5 2.1. Existence of an orthogonal basis 7 2.2. Orthogonal
CROSS-VALIDATION OF CONTROLLED DYNAMIC MODELS: BAYESIAN APPROACH
 CROSS-VALIDATION OF CONTROLLED DYNAMIC MODELS: BAYESIAN APPROACH Miroslav Kárný, Petr Nedoma,Václav Šmídl Institute of Information Theory and Automation AV ČR, P.O.Box 18, 180 00 Praha 8, Czech Republic
CROSS-VALIDATION OF CONTROLLED DYNAMIC MODELS: BAYESIAN APPROACH Miroslav Kárný, Petr Nedoma,Václav Šmídl Institute of Information Theory and Automation AV ČR, P.O.Box 18, 180 00 Praha 8, Czech Republic
Lecture notes on statistical decision theory Econ 2110, fall 2013
 Lecture notes on statistical decision theory Econ 2110, fall 2013 Maximilian Kasy March 10, 2014 These lecture notes are roughly based on Robert, C. (2007). The Bayesian choice: from decision-theoretic
Lecture notes on statistical decision theory Econ 2110, fall 2013 Maximilian Kasy March 10, 2014 These lecture notes are roughly based on Robert, C. (2007). The Bayesian choice: from decision-theoretic
Statistical Inference
 Statistical Inference Classical and Bayesian Methods Class 6 AMS-UCSC Thu 26, 2012 Winter 2012. Session 1 (Class 6) AMS-132/206 Thu 26, 2012 1 / 15 Topics Topics We will talk about... 1 Hypothesis testing
Statistical Inference Classical and Bayesian Methods Class 6 AMS-UCSC Thu 26, 2012 Winter 2012. Session 1 (Class 6) AMS-132/206 Thu 26, 2012 1 / 15 Topics Topics We will talk about... 1 Hypothesis testing
Linear and quadratic classification toolbox for Matlab
 Czech Pattern Recognition Workshop 2, Tomáš Svoboda (Ed.) Peršlák, Czech Republic, February 2 4, 2 Czech Pattern Recognition Society Linear and quadratic classification toolbox for Matlab Vojtěch Franc,
Czech Pattern Recognition Workshop 2, Tomáš Svoboda (Ed.) Peršlák, Czech Republic, February 2 4, 2 Czech Pattern Recognition Society Linear and quadratic classification toolbox for Matlab Vojtěch Franc,
Learning Theory. Ingo Steinwart University of Stuttgart. September 4, 2013
 Learning Theory Ingo Steinwart University of Stuttgart September 4, 2013 Ingo Steinwart University of Stuttgart () Learning Theory September 4, 2013 1 / 62 Basics Informal Introduction Informal Description
Learning Theory Ingo Steinwart University of Stuttgart September 4, 2013 Ingo Steinwart University of Stuttgart () Learning Theory September 4, 2013 1 / 62 Basics Informal Introduction Informal Description
Gaussian and Linear Discriminant Analysis; Multiclass Classification
 Gaussian and Linear Discriminant Analysis; Multiclass Classification Professor Ameet Talwalkar Slide Credit: Professor Fei Sha Professor Ameet Talwalkar CS260 Machine Learning Algorithms October 13, 2015
Gaussian and Linear Discriminant Analysis; Multiclass Classification Professor Ameet Talwalkar Slide Credit: Professor Fei Sha Professor Ameet Talwalkar CS260 Machine Learning Algorithms October 13, 2015
Bayesian Classifiers and Probability Estimation. Vassilis Athitsos CSE 4308/5360: Artificial Intelligence I University of Texas at Arlington
 Bayesian Classifiers and Probability Estimation Vassilis Athitsos CSE 4308/5360: Artificial Intelligence I University of Texas at Arlington 1 Data Space Suppose that we have a classification problem The
Bayesian Classifiers and Probability Estimation Vassilis Athitsos CSE 4308/5360: Artificial Intelligence I University of Texas at Arlington 1 Data Space Suppose that we have a classification problem The
Fuzzy Systems. Introduction
 Fuzzy Systems Introduction Prof. Dr. Rudolf Kruse Christian Moewes {kruse,cmoewes}@iws.cs.uni-magdeburg.de Otto-von-Guericke University of Magdeburg Faculty of Computer Science Department of Knowledge
Fuzzy Systems Introduction Prof. Dr. Rudolf Kruse Christian Moewes {kruse,cmoewes}@iws.cs.uni-magdeburg.de Otto-von-Guericke University of Magdeburg Faculty of Computer Science Department of Knowledge
Math 38: Graph Theory Spring 2004 Dartmouth College. On Writing Proofs. 1 Introduction. 2 Finding A Solution
 Math 38: Graph Theory Spring 2004 Dartmouth College 1 Introduction On Writing Proofs What constitutes a well-written proof? A simple but rather vague answer is that a well-written proof is both clear and
Math 38: Graph Theory Spring 2004 Dartmouth College 1 Introduction On Writing Proofs What constitutes a well-written proof? A simple but rather vague answer is that a well-written proof is both clear and
Chapter 2 Classical Probability Theories
 Chapter 2 Classical Probability Theories In principle, those who are not interested in mathematical foundations of probability theory might jump directly to Part II. One should just know that, besides
Chapter 2 Classical Probability Theories In principle, those who are not interested in mathematical foundations of probability theory might jump directly to Part II. One should just know that, besides
Incompatibility Paradoxes
 Chapter 22 Incompatibility Paradoxes 22.1 Simultaneous Values There is never any difficulty in supposing that a classical mechanical system possesses, at a particular instant of time, precise values of
Chapter 22 Incompatibility Paradoxes 22.1 Simultaneous Values There is never any difficulty in supposing that a classical mechanical system possesses, at a particular instant of time, precise values of
Parameter Estimation, Sampling Distributions & Hypothesis Testing
 Parameter Estimation, Sampling Distributions & Hypothesis Testing Parameter Estimation & Hypothesis Testing In doing research, we are usually interested in some feature of a population distribution (which
Parameter Estimation, Sampling Distributions & Hypothesis Testing Parameter Estimation & Hypothesis Testing In doing research, we are usually interested in some feature of a population distribution (which
Scribe to lecture Tuesday March
 Scribe to lecture Tuesday March 16 2004 Scribe outlines: Message Confidence intervals Central limit theorem Em-algorithm Bayesian versus classical statistic Note: There is no scribe for the beginning of
Scribe to lecture Tuesday March 16 2004 Scribe outlines: Message Confidence intervals Central limit theorem Em-algorithm Bayesian versus classical statistic Note: There is no scribe for the beginning of
Ch. 5 Hypothesis Testing
 Ch. 5 Hypothesis Testing The current framework of hypothesis testing is largely due to the work of Neyman and Pearson in the late 1920s, early 30s, complementing Fisher s work on estimation. As in estimation,
Ch. 5 Hypothesis Testing The current framework of hypothesis testing is largely due to the work of Neyman and Pearson in the late 1920s, early 30s, complementing Fisher s work on estimation. As in estimation,
Introduction to Statistical Inference
 Structural Health Monitoring Using Statistical Pattern Recognition Introduction to Statistical Inference Presented by Charles R. Farrar, Ph.D., P.E. Outline Introduce statistical decision making for Structural
Structural Health Monitoring Using Statistical Pattern Recognition Introduction to Statistical Inference Presented by Charles R. Farrar, Ph.D., P.E. Outline Introduce statistical decision making for Structural
Introduction to Machine Learning. Introduction to ML - TAU 2016/7 1
 Introduction to Machine Learning Introduction to ML - TAU 2016/7 1 Course Administration Lecturers: Amir Globerson (gamir@post.tau.ac.il) Yishay Mansour (Mansour@tau.ac.il) Teaching Assistance: Regev Schweiger
Introduction to Machine Learning Introduction to ML - TAU 2016/7 1 Course Administration Lecturers: Amir Globerson (gamir@post.tau.ac.il) Yishay Mansour (Mansour@tau.ac.il) Teaching Assistance: Regev Schweiger
Pattern Classification
 Pattern Classification All materials in these slides were taken from Pattern Classification (2nd ed) by R. O. Duda, P. E. Hart and D. G. Stork, John Wiley & Sons, 2000 with the permission of the authors
Pattern Classification All materials in these slides were taken from Pattern Classification (2nd ed) by R. O. Duda, P. E. Hart and D. G. Stork, John Wiley & Sons, 2000 with the permission of the authors
Tutorial 6. By:Aashmeet Kalra
 Tutorial 6 By:Aashmeet Kalra AGENDA Candidate Elimination Algorithm Example Demo of Candidate Elimination Algorithm Decision Trees Example Demo of Decision Trees Concept and Concept Learning A Concept
Tutorial 6 By:Aashmeet Kalra AGENDA Candidate Elimination Algorithm Example Demo of Candidate Elimination Algorithm Decision Trees Example Demo of Decision Trees Concept and Concept Learning A Concept
Machine Learning
 Machine Learning 10-601 Tom M. Mitchell Machine Learning Department Carnegie Mellon University August 30, 2017 Today: Decision trees Overfitting The Big Picture Coming soon Probabilistic learning MLE,
Machine Learning 10-601 Tom M. Mitchell Machine Learning Department Carnegie Mellon University August 30, 2017 Today: Decision trees Overfitting The Big Picture Coming soon Probabilistic learning MLE,
Bayesian Methods in Artificial Intelligence
 WDS'10 Proceedings of Contributed Papers, Part I, 25 30, 2010. ISBN 978-80-7378-139-2 MATFYZPRESS Bayesian Methods in Artificial Intelligence M. Kukačka Charles University, Faculty of Mathematics and Physics,
WDS'10 Proceedings of Contributed Papers, Part I, 25 30, 2010. ISBN 978-80-7378-139-2 MATFYZPRESS Bayesian Methods in Artificial Intelligence M. Kukačka Charles University, Faculty of Mathematics and Physics,
Qualifier: CS 6375 Machine Learning Spring 2015
 Qualifier: CS 6375 Machine Learning Spring 2015 The exam is closed book. You are allowed to use two double-sided cheat sheets and a calculator. If you run out of room for an answer, use an additional sheet
Qualifier: CS 6375 Machine Learning Spring 2015 The exam is closed book. You are allowed to use two double-sided cheat sheets and a calculator. If you run out of room for an answer, use an additional sheet
Probability, Entropy, and Inference / More About Inference
 Probability, Entropy, and Inference / More About Inference Mário S. Alvim (msalvim@dcc.ufmg.br) Information Theory DCC-UFMG (2018/02) Mário S. Alvim (msalvim@dcc.ufmg.br) Probability, Entropy, and Inference
Probability, Entropy, and Inference / More About Inference Mário S. Alvim (msalvim@dcc.ufmg.br) Information Theory DCC-UFMG (2018/02) Mário S. Alvim (msalvim@dcc.ufmg.br) Probability, Entropy, and Inference
14 : Theory of Variational Inference: Inner and Outer Approximation
 10-708: Probabilistic Graphical Models 10-708, Spring 2014 14 : Theory of Variational Inference: Inner and Outer Approximation Lecturer: Eric P. Xing Scribes: Yu-Hsin Kuo, Amos Ng 1 Introduction Last lecture
10-708: Probabilistic Graphical Models 10-708, Spring 2014 14 : Theory of Variational Inference: Inner and Outer Approximation Lecturer: Eric P. Xing Scribes: Yu-Hsin Kuo, Amos Ng 1 Introduction Last lecture
8: Hypothesis Testing
 Some definitions 8: Hypothesis Testing. Simple, compound, null and alternative hypotheses In test theory one distinguishes between simple hypotheses and compound hypotheses. A simple hypothesis Examples:
Some definitions 8: Hypothesis Testing. Simple, compound, null and alternative hypotheses In test theory one distinguishes between simple hypotheses and compound hypotheses. A simple hypothesis Examples:
Previously on TT, Target Tracking: Lecture 2 Single Target Tracking Issues. Lecture-2 Outline. Basic ideas on track life
 REGLERTEKNIK Previously on TT, AUTOMATIC CONTROL Target Tracing: Lecture 2 Single Target Tracing Issues Emre Özan emre@isy.liu.se Division of Automatic Control Department of Electrical Engineering Linöping
REGLERTEKNIK Previously on TT, AUTOMATIC CONTROL Target Tracing: Lecture 2 Single Target Tracing Issues Emre Özan emre@isy.liu.se Division of Automatic Control Department of Electrical Engineering Linöping
Basic Concepts of Inference
 Basic Concepts of Inference Corresponds to Chapter 6 of Tamhane and Dunlop Slides prepared by Elizabeth Newton (MIT) with some slides by Jacqueline Telford (Johns Hopkins University) and Roy Welsch (MIT).
Basic Concepts of Inference Corresponds to Chapter 6 of Tamhane and Dunlop Slides prepared by Elizabeth Newton (MIT) with some slides by Jacqueline Telford (Johns Hopkins University) and Roy Welsch (MIT).
Probabilistic Graphical Models: MRFs and CRFs. CSE628: Natural Language Processing Guest Lecturer: Veselin Stoyanov
 Probabilistic Graphical Models: MRFs and CRFs CSE628: Natural Language Processing Guest Lecturer: Veselin Stoyanov Why PGMs? PGMs can model joint probabilities of many events. many techniques commonly
Probabilistic Graphical Models: MRFs and CRFs CSE628: Natural Language Processing Guest Lecturer: Veselin Stoyanov Why PGMs? PGMs can model joint probabilities of many events. many techniques commonly
A first model of learning
 A first model of learning Let s restrict our attention to binary classification our labels belong to (or ) We observe the data where each Suppose we are given an ensemble of possible hypotheses / classifiers
A first model of learning Let s restrict our attention to binary classification our labels belong to (or ) We observe the data where each Suppose we are given an ensemble of possible hypotheses / classifiers
Chapter 2. Mathematical Reasoning. 2.1 Mathematical Models
 Contents Mathematical Reasoning 3.1 Mathematical Models........................... 3. Mathematical Proof............................ 4..1 Structure of Proofs........................ 4.. Direct Method..........................
Contents Mathematical Reasoning 3.1 Mathematical Models........................... 3. Mathematical Proof............................ 4..1 Structure of Proofs........................ 4.. Direct Method..........................
CISC 4090: Theory of Computation Chapter 1 Regular Languages. Section 1.1: Finite Automata. What is a computer? Finite automata
 CISC 4090: Theory of Computation Chapter Regular Languages Xiaolan Zhang, adapted from slides by Prof. Werschulz Section.: Finite Automata Fordham University Department of Computer and Information Sciences
CISC 4090: Theory of Computation Chapter Regular Languages Xiaolan Zhang, adapted from slides by Prof. Werschulz Section.: Finite Automata Fordham University Department of Computer and Information Sciences
Computational Integer Programming. Lecture 2: Modeling and Formulation. Dr. Ted Ralphs
 Computational Integer Programming Lecture 2: Modeling and Formulation Dr. Ted Ralphs Computational MILP Lecture 2 1 Reading for This Lecture N&W Sections I.1.1-I.1.6 Wolsey Chapter 1 CCZ Chapter 2 Computational
Computational Integer Programming Lecture 2: Modeling and Formulation Dr. Ted Ralphs Computational MILP Lecture 2 1 Reading for This Lecture N&W Sections I.1.1-I.1.6 Wolsey Chapter 1 CCZ Chapter 2 Computational
Bayesian decision theory Introduction to Pattern Recognition. Lectures 4 and 5: Bayesian decision theory
 Bayesian decision theory 8001652 Introduction to Pattern Recognition. Lectures 4 and 5: Bayesian decision theory Jussi Tohka jussi.tohka@tut.fi Institute of Signal Processing Tampere University of Technology
Bayesian decision theory 8001652 Introduction to Pattern Recognition. Lectures 4 and 5: Bayesian decision theory Jussi Tohka jussi.tohka@tut.fi Institute of Signal Processing Tampere University of Technology
ORIGINS OF STOCHASTIC PROGRAMMING
 ORIGINS OF STOCHASTIC PROGRAMMING Early 1950 s: in applications of Linear Programming unknown values of coefficients: demands, technological coefficients, yields, etc. QUOTATION Dantzig, Interfaces 20,1990
ORIGINS OF STOCHASTIC PROGRAMMING Early 1950 s: in applications of Linear Programming unknown values of coefficients: demands, technological coefficients, yields, etc. QUOTATION Dantzig, Interfaces 20,1990
CS 350 Algorithms and Complexity
 1 CS 350 Algorithms and Complexity Fall 2015 Lecture 15: Limitations of Algorithmic Power Introduction to complexity theory Andrew P. Black Department of Computer Science Portland State University Lower
1 CS 350 Algorithms and Complexity Fall 2015 Lecture 15: Limitations of Algorithmic Power Introduction to complexity theory Andrew P. Black Department of Computer Science Portland State University Lower
Problem Set 2. MAS 622J/1.126J: Pattern Recognition and Analysis. Due: 5:00 p.m. on September 30
 Problem Set 2 MAS 622J/1.126J: Pattern Recognition and Analysis Due: 5:00 p.m. on September 30 [Note: All instructions to plot data or write a program should be carried out using Matlab. In order to maintain
Problem Set 2 MAS 622J/1.126J: Pattern Recognition and Analysis Due: 5:00 p.m. on September 30 [Note: All instructions to plot data or write a program should be carried out using Matlab. In order to maintain
Detection theory. H 0 : x[n] = w[n]
![Detection theory. H 0 : x[n] = w[n] Detection theory. H 0 : x[n] = w[n]](/thumbs/89/98950636.jpg) Detection Theory Detection theory A the last topic of the course, we will briefly consider detection theory. The methods are based on estimation theory and attempt to answer questions such as Is a signal
Detection Theory Detection theory A the last topic of the course, we will briefly consider detection theory. The methods are based on estimation theory and attempt to answer questions such as Is a signal
Algorithms Exam TIN093 /DIT602
 Algorithms Exam TIN093 /DIT602 Course: Algorithms Course code: TIN 093, TIN 092 (CTH), DIT 602 (GU) Date, time: 21st October 2017, 14:00 18:00 Building: SBM Responsible teacher: Peter Damaschke, Tel. 5405
Algorithms Exam TIN093 /DIT602 Course: Algorithms Course code: TIN 093, TIN 092 (CTH), DIT 602 (GU) Date, time: 21st October 2017, 14:00 18:00 Building: SBM Responsible teacher: Peter Damaschke, Tel. 5405
Fuzzy Systems. Introduction
 Fuzzy Systems Introduction Prof. Dr. Rudolf Kruse Christoph Doell {kruse,doell}@iws.cs.uni-magdeburg.de Otto-von-Guericke University of Magdeburg Faculty of Computer Science Department of Knowledge Processing
Fuzzy Systems Introduction Prof. Dr. Rudolf Kruse Christoph Doell {kruse,doell}@iws.cs.uni-magdeburg.de Otto-von-Guericke University of Magdeburg Faculty of Computer Science Department of Knowledge Processing
Stochastic Realization of Binary Exchangeable Processes
 Stochastic Realization of Binary Exchangeable Processes Lorenzo Finesso and Cecilia Prosdocimi Abstract A discrete time stochastic process is called exchangeable if its n-dimensional distributions are,
Stochastic Realization of Binary Exchangeable Processes Lorenzo Finesso and Cecilia Prosdocimi Abstract A discrete time stochastic process is called exchangeable if its n-dimensional distributions are,
Statistics for the LHC Lecture 1: Introduction
 Statistics for the LHC Lecture 1: Introduction Academic Training Lectures CERN, 14 17 June, 2010 indico.cern.ch/conferencedisplay.py?confid=77830 Glen Cowan Physics Department Royal Holloway, University
Statistics for the LHC Lecture 1: Introduction Academic Training Lectures CERN, 14 17 June, 2010 indico.cern.ch/conferencedisplay.py?confid=77830 Glen Cowan Physics Department Royal Holloway, University
2 Upper-bound of Generalization Error of AdaBoost
 COS 511: Theoretical Machine Learning Lecturer: Rob Schapire Lecture #10 Scribe: Haipeng Zheng March 5, 2008 1 Review of AdaBoost Algorithm Here is the AdaBoost Algorithm: input: (x 1,y 1 ),...,(x m,y
COS 511: Theoretical Machine Learning Lecturer: Rob Schapire Lecture #10 Scribe: Haipeng Zheng March 5, 2008 1 Review of AdaBoost Algorithm Here is the AdaBoost Algorithm: input: (x 1,y 1 ),...,(x m,y
This exam contains 13 pages (including this cover page) and 10 questions. A Formulae sheet is provided with the exam.
 Probability and Statistics FS 2017 Session Exam 22.08.2017 Time Limit: 180 Minutes Name: Student ID: This exam contains 13 pages (including this cover page) and 10 questions. A Formulae sheet is provided
Probability and Statistics FS 2017 Session Exam 22.08.2017 Time Limit: 180 Minutes Name: Student ID: This exam contains 13 pages (including this cover page) and 10 questions. A Formulae sheet is provided
Affine Normalization of Symmetric Objects
 Affine Normalization of Symmetric Objects Tomáš Suk and Jan Flusser Institute of Information Theory and Automation, Academy of Sciences of the Czech Republic, Pod vodárenskou věží 4, 182 08 Prague 8, Czech
Affine Normalization of Symmetric Objects Tomáš Suk and Jan Flusser Institute of Information Theory and Automation, Academy of Sciences of the Czech Republic, Pod vodárenskou věží 4, 182 08 Prague 8, Czech
Pattern Recognition and Machine Learning. Learning and Evaluation of Pattern Recognition Processes
 Pattern Recognition and Machine Learning James L. Crowley ENSIMAG 3 - MMIS Fall Semester 2016 Lesson 1 5 October 2016 Learning and Evaluation of Pattern Recognition Processes Outline Notation...2 1. The
Pattern Recognition and Machine Learning James L. Crowley ENSIMAG 3 - MMIS Fall Semester 2016 Lesson 1 5 October 2016 Learning and Evaluation of Pattern Recognition Processes Outline Notation...2 1. The
CS246 Final Exam, Winter 2011
 CS246 Final Exam, Winter 2011 1. Your name and student ID. Name:... Student ID:... 2. I agree to comply with Stanford Honor Code. Signature:... 3. There should be 17 numbered pages in this exam (including
CS246 Final Exam, Winter 2011 1. Your name and student ID. Name:... Student ID:... 2. I agree to comply with Stanford Honor Code. Signature:... 3. There should be 17 numbered pages in this exam (including
Nondeterministic finite automata
 Lecture 3 Nondeterministic finite automata This lecture is focused on the nondeterministic finite automata (NFA) model and its relationship to the DFA model. Nondeterminism is an important concept in the
Lecture 3 Nondeterministic finite automata This lecture is focused on the nondeterministic finite automata (NFA) model and its relationship to the DFA model. Nondeterminism is an important concept in the
CS 188: Artificial Intelligence Spring Today
 CS 188: Artificial Intelligence Spring 2006 Lecture 9: Naïve Bayes 2/14/2006 Dan Klein UC Berkeley Many slides from either Stuart Russell or Andrew Moore Bayes rule Today Expectations and utilities Naïve
CS 188: Artificial Intelligence Spring 2006 Lecture 9: Naïve Bayes 2/14/2006 Dan Klein UC Berkeley Many slides from either Stuart Russell or Andrew Moore Bayes rule Today Expectations and utilities Naïve
