The Analysis of Microburst (Burstiness) on Virtual Switch
|
|
|
- Juliet Conley
- 5 years ago
- Views:
Transcription
1 The Analysis of Microburst (Burstiness) on Virtual Switch Chunghan Lee Fujitsu Laboratories Copyright 2016 FUJITSU LABORATORIES LIMITED
2 Background What is Network Function Virtualization (NFV)? NFV virtualizes network functions (e.g. Firewall, Load balancer) on IA servers The function is called as virtualized network function (VNF) Virtual switch is one of major components for virtual network on NFV Infrastructure (NFVI) QoS property is also important for NFV Virtual network* *Virtual switch is included in virtual network An image is from 1 Copyright 2014 FUJITSU LABORATORIES LIMITED
3 Microburst (1) What is microburst? Spikes in shot time period, but causing decreased performance Impact of microburst on network Although traffic with QoS property is generated, the spikes can be occurred by massive traffic in very short time period This phenomenon cannot catch the ordinary monitoring (SNMP) When packet drop is occurred by the spike, it is changed as the microburst SNMP (Coarse-grained) Spike Packet (Find-grained) Packet drop!! Sudden spikes in throughput 2 Copyright 2016 FUJITSU LABORATORIES LIMITED
4 Microburst (2) Impact of microburst on NFVI Although traffic with QoS property is generated on VNF, the sudden spikes would be occurred due to resource state Packet loss can be occurred by the spikes (microbursts) Traffic with QoS Sudden spikes!! NFVI (tx) NFVI (rx) 3 Copyright 2016 FUJITSU LABORATORIES LIMITED
5 Problem Microburst on NFVI Ordinary application measurement cannot catch the microbursts on NFVI There are queues and buffers between NFVIs A deep understanding of packet processing issued by virtual switch and Linux kernel is required to clarify the cause of microburst Traffic with QoS Sudden spikes!! NFVI (tx) NFVI (rx) 4 Copyright 2016 FUJITSU LABORATORIES LIMITED
6 GOAL Investigate the occurrence of microburst on NFVI Find the cause of microbursts on NFVI 5 Copyright 2014 FUJITSU LABORATORIES LIMITED
7 Approach Prepare two types of UDP traffic to observe the microbursts on an OvS bridge Foreground : Target with QoS property Background : Occur a lack of CPU resource at kernel Generate fore/background traffic and capture their packets with tcpdump Analyze them in packet-level to observe the microburst Profile kernel functions to clarify the cause of microbursts 6 Copyright 2016 FUJITSU LABORATORIES LIMITED
8 Overview of testbed Foreground traffic (UDP) Sending rate : 2Gbps [Datagram size : 1400 bytes (No fragmentation)] vport tx queue : default value (0), UDP buffer : default value (200 KBytes) Background traffic (UDP) 8 vports are used on the same OVS bridge iperf using UDP mode with 10 parallel flows per vport (iperf option p) Sending rate of UDP flow : 1Gbps (configured bandwidth by iperf) 7 Copyright 2016 FUJITSU LABORATORIES LIMITED
9 Server and switch spec. Overview of spec. All servers have the same spec. Server type : Fujitsu RX100S7 CPU (4 cores) Intel(R) Xeon(R) CPU 3.10GHz Memory 16GB (Speed: 1333 MHz) OS CentOS 7.2 Kernel version NIC 10G:Intel X710 iperf Open vswitch (release version) vport queue Default value (txqueuelen : 0) UDP buffer Default value (200 Kbytes) Switch spec. Fujitsu SR-X 526 (10G switch) 8 Copyright 2016 FUJITSU LABORATORIES LIMITED
10 Investigation of microburst 9 Copyright 2016 FUJITSU LABORATORIES LIMITED
11 Measurement points 6 throughput measurement points Sender : iperf, Entering OVS, Leaving OVS Receiver : iperf, Entering OVS, Leaving OVS iperf (TX) iperf Entering OVS (tcpdump) OVS (bridge) iperf (RX) iperf User Kernel Leaving OVS (tcpdump) OVS (bridge) Leaving OVS (tcpdump) NIC driver Network NIC driver Entering OVS (tcpdump) < Sender > < Receiver > Throughput measurement points 10 Copyright 2016 FUJITSU LABORATORIES LIMITED
12 Throughput at 6 measurement points Throughput of foreground per second Leaving OVS (sender), the throughput is decreased At receiver, the throughput is also decreased at iperf (RX) < Sender > Decreased throughput < Receiver > Decreased throughput 11 Copyright 2016 FUJITSU LABORATORIES LIMITED
13 Throughput of foreground at sender Throughput of foreground per 1 millisecond Entering OVS, the sending rate is fluctuated due to a lack of CPU Leaving OVS, sudden spikes in throughput are found Throughput with QoS property is changed Unit time : 1 millisecond < Entering OVS > < Sender > iperf < Leaving OVS > Entering OVS OVS (bridge) Leaving OVS NIC driver Network 12 Copyright 2016 FUJITSU LABORATORIES LIMITED
14 Packet drop and throughput at receiver A relation between throughput and packet drop The timing of packet drop is similar to the timing of sudden spikes in throughput at receiver The overflow of socket buffer is frequently occurred by the sudden spikes (spikes microbursts) < Receiver > < Packet drop at socket > iperf Leaving OVS Socket OVS (bridge) < Leaving OVS > NIC driver Network 13 Copyright 2016 FUJITSU LABORATORIES LIMITED
15 Packet drop and spacing at receiver A relation between packet drop and packet spacing The packet spacing with moving average (MA)* is decreased while the number of drop packets on socket buffer is increased Microburst Packet spacing Burstiness Packet loss < Receiver > iperf Leaving OVS Socket OVS (bridge) NIC driver *MA leg : 1000 Network 14 Copyright 2016 FUJITSU LABORATORIES LIMITED
16 Cause of microburst 15 Copyright 2016 FUJITSU LABORATORIES LIMITED
17 Find the cause of microburst Profiling kernel functions using perf Profiling rate (sampling rate) is 1 millisecond Focus on process (iperf with 2Gbps) only for the profiling Profiling Kernel by perf 16 Copyright 2016 FUJITSU LABORATORIES LIMITED
18 Common function call graph Packet processing at Linux kernel Net I/F Enqueue (qdisc, tx-ring) From OVS to qdisc OVS (bridge) From vport to OVS IP layer (TX) TCP/UDP layer (TX) Copy data iperf Kernel User 17 Copyright 2016 FUJITSU LABORATORIES LIMITED
19 Measurement points with TCP/IP stack Leaving OVS, the packet capture is occurred after qdisc Entering OVS Leaving OVS Entering OVS Leaving OVS Throughput measurement points 18 Copyright 2016 FUJITSU LABORATORIES LIMITED
20 Summary Throughput of foreground per second Leaving OVS (sender), the throughput is decreased At receiver, the throughput is also decreased at iperf (RX) < Sender > Packet drop at qdisc < Receiver > Packet drop at socket buffer by microbursts 19 Copyright 2016 FUJITSU LABORATORIES LIMITED
21 Conclusion We investigated the occurrence of microbursts on NFVI A major cause of microburst is packet queuing on qdisc, and the packet loss at socket buffer on receiver is occurred by the microbursts At qdisc, the throughput is decreased to 63% and the queue size is not enough to absorb the packets At socket buffer (rx), the throughput is decreased to 41% and the buffer capacity is also not enough We found the cause of microbursts using kernel profiling Although the total sending rate is 10 Gbps, qdisc at the sender is frequently full 20 Copyright 2016 FUJITSU LABORATORIES LIMITED
22 Future work Clarify the cause why qdisc is frequently full although the total sending rate is 10 Gbps Analyze the profiling results with kernel trace Modify Linux kernel to change the packet capture point Extend the experiments Without OVS (Clarify the overhead of OVS) With TCP, DPDK OVS, VMs based on vhost 21 Copyright 2016 FUJITSU LABORATORIES LIMITED
23 22 Copyright 2015 FUJITSU LABORATORIES LIMITED
Boost UDP Transaction Performance
 Boost UDP Transaction Performance Toshiaki Makita NTT Open Source Software Center Today's topics Background Basic technologies for network performance How to improve UDP performance 2 Who is Toshiaki Makita?
Boost UDP Transaction Performance Toshiaki Makita NTT Open Source Software Center Today's topics Background Basic technologies for network performance How to improve UDP performance 2 Who is Toshiaki Makita?
These are special traffic patterns that create more stress on a switch
 Myths about Microbursts What are Microbursts? Microbursts are traffic patterns where traffic arrives in small bursts. While almost all network traffic is bursty to some extent, storage traffic usually
Myths about Microbursts What are Microbursts? Microbursts are traffic patterns where traffic arrives in small bursts. While almost all network traffic is bursty to some extent, storage traffic usually
Che-Wei Chang Department of Computer Science and Information Engineering, Chang Gung University
 Che-Wei Chang chewei@mail.cgu.edu.tw Department of Computer Science and Information Engineering, Chang Gung University } 2017/11/15 Midterm } 2017/11/22 Final Project Announcement 2 1. Introduction 2.
Che-Wei Chang chewei@mail.cgu.edu.tw Department of Computer Science and Information Engineering, Chang Gung University } 2017/11/15 Midterm } 2017/11/22 Final Project Announcement 2 1. Introduction 2.
A Different Kind of Flow Analysis. David M Nicol University of Illinois at Urbana-Champaign
 A Different Kind of Flow Analysis David M Nicol University of Illinois at Urbana-Champaign 2 What Am I Doing Here??? Invite for ICASE Reunion Did research on Peformance Analysis Supporting Supercomputing
A Different Kind of Flow Analysis David M Nicol University of Illinois at Urbana-Champaign 2 What Am I Doing Here??? Invite for ICASE Reunion Did research on Peformance Analysis Supporting Supercomputing
Weather Research and Forecasting (WRF) Performance Benchmark and Profiling. July 2012
 Weather Research and Forecasting (WRF) Performance Benchmark and Profiling July 2012 Note The following research was performed under the HPC Advisory Council activities Participating vendors: Intel, Dell,
Weather Research and Forecasting (WRF) Performance Benchmark and Profiling July 2012 Note The following research was performed under the HPC Advisory Council activities Participating vendors: Intel, Dell,
Congestion Control. Need to understand: What is congestion? How do we prevent or manage it?
 Congestion Control Phenomenon: when too much traffic enters into system, performance degrades excessive traffic can cause congestion Problem: regulate traffic influx such that congestion does not occur
Congestion Control Phenomenon: when too much traffic enters into system, performance degrades excessive traffic can cause congestion Problem: regulate traffic influx such that congestion does not occur
End-to-end Estimation of the Available Bandwidth Variation Range
 1 End-to-end Estimation of the Available Bandwidth Variation Range Manish Jain Georgia Tech jain@cc.gatech.edu Constantinos Dovrolis Georgia Tech dovrolis@cc.gatech.edu Abstract The available bandwidth
1 End-to-end Estimation of the Available Bandwidth Variation Range Manish Jain Georgia Tech jain@cc.gatech.edu Constantinos Dovrolis Georgia Tech dovrolis@cc.gatech.edu Abstract The available bandwidth
NICTA Short Course. Network Analysis. Vijay Sivaraman. Day 1 Queueing Systems and Markov Chains. Network Analysis, 2008s2 1-1
 NICTA Short Course Network Analysis Vijay Sivaraman Day 1 Queueing Systems and Markov Chains Network Analysis, 2008s2 1-1 Outline Why a short course on mathematical analysis? Limited current course offering
NICTA Short Course Network Analysis Vijay Sivaraman Day 1 Queueing Systems and Markov Chains Network Analysis, 2008s2 1-1 Outline Why a short course on mathematical analysis? Limited current course offering
Capturing Network Traffic Dynamics Small Scales. Rolf Riedi
 Capturing Network Traffic Dynamics Small Scales Rolf Riedi Dept of Statistics Stochastic Systems and Modelling in Networking and Finance Part II Dependable Adaptive Systems and Mathematical Modeling Kaiserslautern,
Capturing Network Traffic Dynamics Small Scales Rolf Riedi Dept of Statistics Stochastic Systems and Modelling in Networking and Finance Part II Dependable Adaptive Systems and Mathematical Modeling Kaiserslautern,
Administrivia. Course Objectives. Overview. Lecture Notes Week markem/cs333/ 2. Staff. 3. Prerequisites. 4. Grading. 1. Theory and application
 Administrivia 1. markem/cs333/ 2. Staff 3. Prerequisites 4. Grading Course Objectives 1. Theory and application 2. Benefits 3. Labs TAs Overview 1. What is a computer system? CPU PC ALU System bus Memory
Administrivia 1. markem/cs333/ 2. Staff 3. Prerequisites 4. Grading Course Objectives 1. Theory and application 2. Benefits 3. Labs TAs Overview 1. What is a computer system? CPU PC ALU System bus Memory
A Mathematical Model of the Skype VoIP Congestion Control Algorithm
 A Mathematical Model of the Skype VoIP Congestion Control Algorithm Luca De Cicco, S. Mascolo, V. Palmisano Dipartimento di Elettrotecnica ed Elettronica, Politecnico di Bari 47th IEEE Conference on Decision
A Mathematical Model of the Skype VoIP Congestion Control Algorithm Luca De Cicco, S. Mascolo, V. Palmisano Dipartimento di Elettrotecnica ed Elettronica, Politecnico di Bari 47th IEEE Conference on Decision
Computer Networks ( Classroom Practice Booklet Solutions)
 Computer Networks ( Classroom Practice Booklet Solutions). Concept Of Layering 0. Ans: (b) Sol: Data Link Layer is responsible for decoding bit stream into frames. 0. Ans: (c) Sol: Network Layer has the
Computer Networks ( Classroom Practice Booklet Solutions). Concept Of Layering 0. Ans: (b) Sol: Data Link Layer is responsible for decoding bit stream into frames. 0. Ans: (c) Sol: Network Layer has the
Reducing Noisy-Neighbor Impact with a Fuzzy Affinity- Aware Scheduler
 Reducing Noisy-Neighbor Impact with a Fuzzy Affinity- Aware Scheduler L U I S T O M Á S A N D J O H A N T O R D S S O N D E PA R T M E N T O F C O M P U T I N G S C I E N C E U M E Å U N I V E R S I T
Reducing Noisy-Neighbor Impact with a Fuzzy Affinity- Aware Scheduler L U I S T O M Á S A N D J O H A N T O R D S S O N D E PA R T M E N T O F C O M P U T I N G S C I E N C E U M E Å U N I V E R S I T
Congestion Control. Phenomenon: when too much traffic enters into system, performance degrades excessive traffic can cause congestion
 Congestion Control Phenomenon: when too much traffic enters into system, performance degrades excessive traffic can cause congestion Problem: regulate traffic influx such that congestion does not occur
Congestion Control Phenomenon: when too much traffic enters into system, performance degrades excessive traffic can cause congestion Problem: regulate traffic influx such that congestion does not occur
TDDB68 Concurrent programming and operating systems. Lecture: CPU Scheduling II
 TDDB68 Concurrent programming and operating systems Lecture: CPU Scheduling II Mikael Asplund, Senior Lecturer Real-time Systems Laboratory Department of Computer and Information Science Copyright Notice:
TDDB68 Concurrent programming and operating systems Lecture: CPU Scheduling II Mikael Asplund, Senior Lecturer Real-time Systems Laboratory Department of Computer and Information Science Copyright Notice:
Modelling an Isolated Compound TCP Connection
 Modelling an Isolated Compound TCP Connection Alberto Blanc and Denis Collange Orange Labs 905 rue Albert Einstein Sophia Antipolis, France {Email: alberto.blanc,denis.collange}@orange-ftgroup.com Konstantin
Modelling an Isolated Compound TCP Connection Alberto Blanc and Denis Collange Orange Labs 905 rue Albert Einstein Sophia Antipolis, France {Email: alberto.blanc,denis.collange}@orange-ftgroup.com Konstantin
Min Congestion Control for High- Speed Heterogeneous Networks. JetMax: Scalable Max-Min
 JetMax: Scalable Max-Min Min Congestion Control for High- Speed Heterogeneous Networks Yueping Zhang Joint work with Derek Leonard and Dmitri Loguinov Internet Research Lab Department of Computer Science
JetMax: Scalable Max-Min Min Congestion Control for High- Speed Heterogeneous Networks Yueping Zhang Joint work with Derek Leonard and Dmitri Loguinov Internet Research Lab Department of Computer Science
cs/ee/ids 143 Communication Networks
 cs/ee/ids 143 Communication Networks Chapter 4 Transport Text: Walrand & Parakh, 2010 Steven Low CMS, EE, Caltech Agenda Internetworking n Routing across LANs, layer2-layer3 n DHCP n NAT Transport layer
cs/ee/ids 143 Communication Networks Chapter 4 Transport Text: Walrand & Parakh, 2010 Steven Low CMS, EE, Caltech Agenda Internetworking n Routing across LANs, layer2-layer3 n DHCP n NAT Transport layer
Socket Programming. Daniel Zappala. CS 360 Internet Programming Brigham Young University
 Socket Programming Daniel Zappala CS 360 Internet Programming Brigham Young University Sockets, Addresses, Ports Clients and Servers 3/33 clients request a service from a server using a protocol need an
Socket Programming Daniel Zappala CS 360 Internet Programming Brigham Young University Sockets, Addresses, Ports Clients and Servers 3/33 clients request a service from a server using a protocol need an
PIQI-RCP: Design and Analysis of Rate-Based Explicit Congestion Control
 PIQI-RCP: Design and Analysis of Rate-Based Explicit Congestion Control Saurabh Jain Joint work with Dr. Dmitri Loguinov June 21, 2007 1 Agenda Introduction Analysis of RCP QI-RCP PIQI-RCP Comparison Wrap
PIQI-RCP: Design and Analysis of Rate-Based Explicit Congestion Control Saurabh Jain Joint work with Dr. Dmitri Loguinov June 21, 2007 1 Agenda Introduction Analysis of RCP QI-RCP PIQI-RCP Comparison Wrap
TDDI04, K. Arvidsson, IDA, Linköpings universitet CPU Scheduling. Overview: CPU Scheduling. [SGG7] Chapter 5. Basic Concepts.
![TDDI04, K. Arvidsson, IDA, Linköpings universitet CPU Scheduling. Overview: CPU Scheduling. [SGG7] Chapter 5. Basic Concepts. TDDI04, K. Arvidsson, IDA, Linköpings universitet CPU Scheduling. Overview: CPU Scheduling. [SGG7] Chapter 5. Basic Concepts.](/thumbs/79/80204297.jpg) TDDI4 Concurrent Programming, Operating Systems, and Real-time Operating Systems CPU Scheduling Overview: CPU Scheduling CPU bursts and I/O bursts Scheduling Criteria Scheduling Algorithms Multiprocessor
TDDI4 Concurrent Programming, Operating Systems, and Real-time Operating Systems CPU Scheduling Overview: CPU Scheduling CPU bursts and I/O bursts Scheduling Criteria Scheduling Algorithms Multiprocessor
CPU Scheduling. CPU Scheduler
 CPU Scheduling These slides are created by Dr. Huang of George Mason University. Students registered in Dr. Huang s courses at GMU can make a single machine readable copy and print a single copy of each
CPU Scheduling These slides are created by Dr. Huang of George Mason University. Students registered in Dr. Huang s courses at GMU can make a single machine readable copy and print a single copy of each
P214 Efficient Computation of Passive Seismic Interferometry
 P214 Efficient Computation of Passive Seismic Interferometry J.W. Thorbecke* (Delft University of Technology) & G.G. Drijkoningen (Delft University of Technology) SUMMARY Seismic interferometry is from
P214 Efficient Computation of Passive Seismic Interferometry J.W. Thorbecke* (Delft University of Technology) & G.G. Drijkoningen (Delft University of Technology) SUMMARY Seismic interferometry is from
Advanced Topicson Network Socket Programming
 Advanced Topics on Network Socket Programming Computer Science Department, University of Crete Manolis Surligas surligas@csduocgr October 18, 2017 Manolis Surligas (CSD, UoC) Advanced Topicson Network
Advanced Topics on Network Socket Programming Computer Science Department, University of Crete Manolis Surligas surligas@csduocgr October 18, 2017 Manolis Surligas (CSD, UoC) Advanced Topicson Network
CS418 Operating Systems
 CS418 Operating Systems Lecture 14 Queuing Analysis Textbook: Operating Systems by William Stallings 1 1. Why Queuing Analysis? If the system environment changes (like the number of users is doubled),
CS418 Operating Systems Lecture 14 Queuing Analysis Textbook: Operating Systems by William Stallings 1 1. Why Queuing Analysis? If the system environment changes (like the number of users is doubled),
Lecture 23: Illusiveness of Parallel Performance. James C. Hoe Department of ECE Carnegie Mellon University
 18 447 Lecture 23: Illusiveness of Parallel Performance James C. Hoe Department of ECE Carnegie Mellon University 18 447 S18 L23 S1, James C. Hoe, CMU/ECE/CALCM, 2018 Your goal today Housekeeping peel
18 447 Lecture 23: Illusiveness of Parallel Performance James C. Hoe Department of ECE Carnegie Mellon University 18 447 S18 L23 S1, James C. Hoe, CMU/ECE/CALCM, 2018 Your goal today Housekeeping peel
Performance Evaluation of Scientific Applications on POWER8
 Performance Evaluation of Scientific Applications on POWER8 2014 Nov 16 Andrew V. Adinetz 1, Paul F. Baumeister 1, Hans Böttiger 3, Thorsten Hater 1, Thilo Maurer 3, Dirk Pleiter 1, Wolfram Schenck 4,
Performance Evaluation of Scientific Applications on POWER8 2014 Nov 16 Andrew V. Adinetz 1, Paul F. Baumeister 1, Hans Böttiger 3, Thorsten Hater 1, Thilo Maurer 3, Dirk Pleiter 1, Wolfram Schenck 4,
CHAPTER 5 - PROCESS SCHEDULING
 CHAPTER 5 - PROCESS SCHEDULING OBJECTIVES To introduce CPU scheduling, which is the basis for multiprogrammed operating systems To describe various CPU-scheduling algorithms To discuss evaluation criteria
CHAPTER 5 - PROCESS SCHEDULING OBJECTIVES To introduce CPU scheduling, which is the basis for multiprogrammed operating systems To describe various CPU-scheduling algorithms To discuss evaluation criteria
VMware VMmark V1.1 Results
 Vendor and Hardware Platform: IBM System x3950 M2 Virtualization Platform: VMware ESX 3.5.0 U2 Build 110181 Performance VMware VMmark V1.1 Results Tested By: IBM Inc., RTP, NC Test Date: 2008-09-20 Performance
Vendor and Hardware Platform: IBM System x3950 M2 Virtualization Platform: VMware ESX 3.5.0 U2 Build 110181 Performance VMware VMmark V1.1 Results Tested By: IBM Inc., RTP, NC Test Date: 2008-09-20 Performance
Module 5: CPU Scheduling
 Module 5: CPU Scheduling Basic Concepts Scheduling Criteria Scheduling Algorithms Multiple-Processor Scheduling Real-Time Scheduling Algorithm Evaluation 5.1 Basic Concepts Maximum CPU utilization obtained
Module 5: CPU Scheduling Basic Concepts Scheduling Criteria Scheduling Algorithms Multiple-Processor Scheduling Real-Time Scheduling Algorithm Evaluation 5.1 Basic Concepts Maximum CPU utilization obtained
Congestion Control. Topics
 Congestion Control Topics Congestion control what & why? Current congestion control algorithms TCP and UDP Ideal congestion control Resource allocation Distributed algorithms Relation current algorithms
Congestion Control Topics Congestion control what & why? Current congestion control algorithms TCP and UDP Ideal congestion control Resource allocation Distributed algorithms Relation current algorithms
Effective Bandwidth for Traffic Engineering
 Brigham Young University BYU ScholarsArchive All Faculty Publications 2-5- Effective Bandwidth for Traffic Engineering Mark J. Clement clement@cs.byu.edu Rob Kunz See next page for additional authors Follow
Brigham Young University BYU ScholarsArchive All Faculty Publications 2-5- Effective Bandwidth for Traffic Engineering Mark J. Clement clement@cs.byu.edu Rob Kunz See next page for additional authors Follow
Introduction to Markov Chains, Queuing Theory, and Network Performance
 Introduction to Markov Chains, Queuing Theory, and Network Performance Marceau Coupechoux Telecom ParisTech, departement Informatique et Réseaux marceau.coupechoux@telecom-paristech.fr IT.2403 Modélisation
Introduction to Markov Chains, Queuing Theory, and Network Performance Marceau Coupechoux Telecom ParisTech, departement Informatique et Réseaux marceau.coupechoux@telecom-paristech.fr IT.2403 Modélisation
CS276 Homework 1: ns-2
 CS276 Homework 1: ns-2 Erik Peterson October 28, 2006 1 Part 1 - Fairness between TCP variants 1.1 Method After learning ns-2, I wrote a script (Listing 3) that runs a simulation of one or two tcp flows
CS276 Homework 1: ns-2 Erik Peterson October 28, 2006 1 Part 1 - Fairness between TCP variants 1.1 Method After learning ns-2, I wrote a script (Listing 3) that runs a simulation of one or two tcp flows
Lecture 7: Simulation of Markov Processes. Pasi Lassila Department of Communications and Networking
 Lecture 7: Simulation of Markov Processes Pasi Lassila Department of Communications and Networking Contents Markov processes theory recap Elementary queuing models for data networks Simulation of Markov
Lecture 7: Simulation of Markov Processes Pasi Lassila Department of Communications and Networking Contents Markov processes theory recap Elementary queuing models for data networks Simulation of Markov
Compound TCP with Random Losses
 Compound TCP with Random Losses Alberto Blanc 1, Konstantin Avrachenkov 2, Denis Collange 1, and Giovanni Neglia 2 1 Orange Labs, 905 rue Albert Einstein, 06921 Sophia Antipolis, France {alberto.blanc,denis.collange}@orange-ftgroup.com
Compound TCP with Random Losses Alberto Blanc 1, Konstantin Avrachenkov 2, Denis Collange 1, and Giovanni Neglia 2 1 Orange Labs, 905 rue Albert Einstein, 06921 Sophia Antipolis, France {alberto.blanc,denis.collange}@orange-ftgroup.com
Homework 1 - SOLUTION
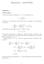 Homework - SOLUTION Problem M/M/ Queue ) Use the fact above to express π k, k > 0, as a function of π 0. π k = ( ) k λ π 0 µ 2) Using λ < µ and the fact that all π k s sum to, compute π 0 (as a function
Homework - SOLUTION Problem M/M/ Queue ) Use the fact above to express π k, k > 0, as a function of π 0. π k = ( ) k λ π 0 µ 2) Using λ < µ and the fact that all π k s sum to, compute π 0 (as a function
Approximate Fairness with Quantized Congestion Notification for Multi-tenanted Data Centers
 Approximate Fairness with Quantized Congestion Notification for Multi-tenanted Data Centers Abdul Kabbani Stanford University Joint work with: Mohammad Alizadeh, Masato Yasuda, Rong Pan, and Balaji Prabhakar
Approximate Fairness with Quantized Congestion Notification for Multi-tenanted Data Centers Abdul Kabbani Stanford University Joint work with: Mohammad Alizadeh, Masato Yasuda, Rong Pan, and Balaji Prabhakar
Capacity management for packet-switched networks with heterogeneous sources. Linda de Jonge. Master Thesis July 29, 2009.
 Capacity management for packet-switched networks with heterogeneous sources Linda de Jonge Master Thesis July 29, 2009 Supervisors Dr. Frank Roijers Prof. dr. ir. Sem Borst Dr. Andreas Löpker Industrial
Capacity management for packet-switched networks with heterogeneous sources Linda de Jonge Master Thesis July 29, 2009 Supervisors Dr. Frank Roijers Prof. dr. ir. Sem Borst Dr. Andreas Löpker Industrial
Compound TCP with Random Losses
 Compound TCP with Random Losses Alberto Blanc 1, Konstantin Avrachenkov 2, Denis Collange 1, and Giovanni Neglia 2 1 Orange Labs, 905 rue Albert Einstein, 06921 Sophia Antipolis, France {alberto.blanc,denis.collange}@orange-ftgroup.com
Compound TCP with Random Losses Alberto Blanc 1, Konstantin Avrachenkov 2, Denis Collange 1, and Giovanni Neglia 2 1 Orange Labs, 905 rue Albert Einstein, 06921 Sophia Antipolis, France {alberto.blanc,denis.collange}@orange-ftgroup.com
Dynamic Scheduling for Work Agglomeration on Heterogeneous Clusters
 Dynamic Scheduling for Work Agglomeration on Heterogeneous Clusters Jonathan Lifflander, G. Carl Evans, Anshu Arya, Laxmikant Kale University of Illinois Urbana-Champaign May 25, 2012 Work is overdecomposed
Dynamic Scheduling for Work Agglomeration on Heterogeneous Clusters Jonathan Lifflander, G. Carl Evans, Anshu Arya, Laxmikant Kale University of Illinois Urbana-Champaign May 25, 2012 Work is overdecomposed
Queueing Theory I Summary! Little s Law! Queueing System Notation! Stationary Analysis of Elementary Queueing Systems " M/M/1 " M/M/m " M/M/1/K "
 Queueing Theory I Summary Little s Law Queueing System Notation Stationary Analysis of Elementary Queueing Systems " M/M/1 " M/M/m " M/M/1/K " Little s Law a(t): the process that counts the number of arrivals
Queueing Theory I Summary Little s Law Queueing System Notation Stationary Analysis of Elementary Queueing Systems " M/M/1 " M/M/m " M/M/1/K " Little s Law a(t): the process that counts the number of arrivals
CSE 380 Computer Operating Systems
 CSE 380 Computer Operating Systems Instructor: Insup Lee & Dianna Xu University of Pennsylvania, Fall 2003 Lecture Note 3: CPU Scheduling 1 CPU SCHEDULING q How can OS schedule the allocation of CPU cycles
CSE 380 Computer Operating Systems Instructor: Insup Lee & Dianna Xu University of Pennsylvania, Fall 2003 Lecture Note 3: CPU Scheduling 1 CPU SCHEDULING q How can OS schedule the allocation of CPU cycles
Operational Laws Raj Jain
 Operational Laws 33-1 Overview What is an Operational Law? 1. Utilization Law 2. Forced Flow Law 3. Little s Law 4. General Response Time Law 5. Interactive Response Time Law 6. Bottleneck Analysis 33-2
Operational Laws 33-1 Overview What is an Operational Law? 1. Utilization Law 2. Forced Flow Law 3. Little s Law 4. General Response Time Law 5. Interactive Response Time Law 6. Bottleneck Analysis 33-2
Experimental evaluation of DDoS detection and prevention using opensource and commodity hardware
 Experimental evaluation of DDoS detection and prevention using opensource and commodity hardware Meklit Elfiyos Dekita Master of Science in Telematics - Communication Networks and Networked Submission
Experimental evaluation of DDoS detection and prevention using opensource and commodity hardware Meklit Elfiyos Dekita Master of Science in Telematics - Communication Networks and Networked Submission
A flow-based model for Internet backbone traffic
 A flow-based model for Internet backbone traffic Chadi Barakat, Patrick Thiran Gianluca Iannaccone, Christophe iot Philippe Owezarski ICA - SC - EPFL Sprint Labs LAAS-CNRS {Chadi.Barakat,Patrick.Thiran}@epfl.ch
A flow-based model for Internet backbone traffic Chadi Barakat, Patrick Thiran Gianluca Iannaccone, Christophe iot Philippe Owezarski ICA - SC - EPFL Sprint Labs LAAS-CNRS {Chadi.Barakat,Patrick.Thiran}@epfl.ch
Wavelet and SiZer analyses of Internet Traffic Data
 Wavelet and SiZer analyses of Internet Traffic Data Cheolwoo Park Statistical and Applied Mathematical Sciences Institute Fred Godtliebsen Department of Mathematics and Statistics, University of Tromsø
Wavelet and SiZer analyses of Internet Traffic Data Cheolwoo Park Statistical and Applied Mathematical Sciences Institute Fred Godtliebsen Department of Mathematics and Statistics, University of Tromsø
QUEUING SYSTEM. Yetunde Folajimi, PhD
 QUEUING SYSTEM Yetunde Folajimi, PhD Part 2 Queuing Models Queueing models are constructed so that queue lengths and waiting times can be predicted They help us to understand and quantify the effect of
QUEUING SYSTEM Yetunde Folajimi, PhD Part 2 Queuing Models Queueing models are constructed so that queue lengths and waiting times can be predicted They help us to understand and quantify the effect of
Correlating the Perceived Quality of Networked Games to Broadband Cable Network Design Parameters. Project Update: 7/20/2011
 Correlating the Perceived Quality of Networked Games to Broadband Cable Network Design Parameters Project Update: 7/20/2011 Networking Team: Rahul Amin, Jim Martin School of Computing HCI Team: Dr Juan
Correlating the Perceived Quality of Networked Games to Broadband Cable Network Design Parameters Project Update: 7/20/2011 Networking Team: Rahul Amin, Jim Martin School of Computing HCI Team: Dr Juan
Process Scheduling. Process Scheduling. CPU and I/O Bursts. CPU - I/O Burst Cycle. Variations in Bursts. Histogram of CPU Burst Times
 Scheduling The objective of multiprogramming is to have some process running all the time The objective of timesharing is to have the switch between processes so frequently that users can interact with
Scheduling The objective of multiprogramming is to have some process running all the time The objective of timesharing is to have the switch between processes so frequently that users can interact with
Analysis of Software Artifacts
 Analysis of Software Artifacts System Performance I Shu-Ngai Yeung (with edits by Jeannette Wing) Department of Statistics Carnegie Mellon University Pittsburgh, PA 15213 2001 by Carnegie Mellon University
Analysis of Software Artifacts System Performance I Shu-Ngai Yeung (with edits by Jeannette Wing) Department of Statistics Carnegie Mellon University Pittsburgh, PA 15213 2001 by Carnegie Mellon University
Operational Laws 33-1
 Operational Laws Raj Jain Washington University in Saint Louis Jain@eecs.berkeley.edu or Jain@wustl.edu A Mini-Course offered at UC Berkeley, Sept-Oct 2012 These slides and audio/video recordings are available
Operational Laws Raj Jain Washington University in Saint Louis Jain@eecs.berkeley.edu or Jain@wustl.edu A Mini-Course offered at UC Berkeley, Sept-Oct 2012 These slides and audio/video recordings are available
Network Traffic Characteristic
 Network Traffic Characteristic Hojun Lee hlee02@purros.poly.edu 5/24/2002 EL938-Project 1 Outline Motivation What is self-similarity? Behavior of Ethernet traffic Behavior of WAN traffic Behavior of WWW
Network Traffic Characteristic Hojun Lee hlee02@purros.poly.edu 5/24/2002 EL938-Project 1 Outline Motivation What is self-similarity? Behavior of Ethernet traffic Behavior of WAN traffic Behavior of WWW
A Data Communication Reliability and Trustability Study for Cluster Computing
 A Data Communication Reliability and Trustability Study for Cluster Computing Speaker: Eduardo Colmenares Midwestern State University Wichita Falls, TX HPC Introduction Relevant to a variety of sciences,
A Data Communication Reliability and Trustability Study for Cluster Computing Speaker: Eduardo Colmenares Midwestern State University Wichita Falls, TX HPC Introduction Relevant to a variety of sciences,
An XG-PON Module for the NS-3 Network Simulator: the Manual
 An XG-PON Module for the NS-3 Network Simulator: the Manual Xiuchao Wu, Kenneth N. Brown, Cormac J. Sreenan, Jerome Arokkiam Department of Computer Science, University College Cork, Ireland {xw2, k.brown,
An XG-PON Module for the NS-3 Network Simulator: the Manual Xiuchao Wu, Kenneth N. Brown, Cormac J. Sreenan, Jerome Arokkiam Department of Computer Science, University College Cork, Ireland {xw2, k.brown,
Wavelet and Time-Domain Modeling of Multi-Layer VBR Video Traffic
 Wavelet and Time-Domain Modeling of Multi-Layer VBR Video Traffic Min Dai, Dmitri Loguinov Texas A&M University 1 Agenda Background Importance of traffic modeling Goals of traffic modeling Preliminary
Wavelet and Time-Domain Modeling of Multi-Layer VBR Video Traffic Min Dai, Dmitri Loguinov Texas A&M University 1 Agenda Background Importance of traffic modeling Goals of traffic modeling Preliminary
CPU scheduling. CPU Scheduling
 EECS 3221 Operating System Fundamentals No.4 CPU scheduling Prof. Hui Jiang Dept of Electrical Engineering and Computer Science, York University CPU Scheduling CPU scheduling is the basis of multiprogramming
EECS 3221 Operating System Fundamentals No.4 CPU scheduling Prof. Hui Jiang Dept of Electrical Engineering and Computer Science, York University CPU Scheduling CPU scheduling is the basis of multiprogramming
Chapter 6: CPU Scheduling
 Chapter 6: CPU Scheduling Basic Concepts Scheduling Criteria Scheduling Algorithms Multiple-Processor Scheduling Real-Time Scheduling Algorithm Evaluation 6.1 Basic Concepts Maximum CPU utilization obtained
Chapter 6: CPU Scheduling Basic Concepts Scheduling Criteria Scheduling Algorithms Multiple-Processor Scheduling Real-Time Scheduling Algorithm Evaluation 6.1 Basic Concepts Maximum CPU utilization obtained
Networking = Plumbing. Queueing Analysis: I. Last Lecture. Lecture Outline. Jeremiah Deng. 29 July 2013
 Networking = Plumbing TELE302 Lecture 7 Queueing Analysis: I Jeremiah Deng University of Otago 29 July 2013 Jeremiah Deng (University of Otago) TELE302 Lecture 7 29 July 2013 1 / 33 Lecture Outline Jeremiah
Networking = Plumbing TELE302 Lecture 7 Queueing Analysis: I Jeremiah Deng University of Otago 29 July 2013 Jeremiah Deng (University of Otago) TELE302 Lecture 7 29 July 2013 1 / 33 Lecture Outline Jeremiah
A Methodology for Clock Benchmarking
 A Methodology for Clock Benchmarking Julien Ridoux j.ridoux@ee.unimelb.edu.au Darryl Veitch d.veitch@ee.unimelb.edu.au ARC Special Research Centre for Ultra-Broadband Information Networks THE UNIVERSITY
A Methodology for Clock Benchmarking Julien Ridoux j.ridoux@ee.unimelb.edu.au Darryl Veitch d.veitch@ee.unimelb.edu.au ARC Special Research Centre for Ultra-Broadband Information Networks THE UNIVERSITY
DIMENSIONING BANDWIDTH FOR ELASTIC TRAFFIC IN HIGH-SPEED DATA NETWORKS
 Submitted to IEEE/ACM Transactions on etworking DIMESIOIG BADWIDTH FOR ELASTIC TRAFFIC I HIGH-SPEED DATA ETWORKS Arthur W. Berger * and Yaakov Kogan Abstract Simple and robust engineering rules for dimensioning
Submitted to IEEE/ACM Transactions on etworking DIMESIOIG BADWIDTH FOR ELASTIC TRAFFIC I HIGH-SPEED DATA ETWORKS Arthur W. Berger * and Yaakov Kogan Abstract Simple and robust engineering rules for dimensioning
An Optimal Index Policy for the Multi-Armed Bandit Problem with Re-Initializing Bandits
 An Optimal Index Policy for the Multi-Armed Bandit Problem with Re-Initializing Bandits Peter Jacko YEQT III November 20, 2009 Basque Center for Applied Mathematics (BCAM), Bilbao, Spain Example: Congestion
An Optimal Index Policy for the Multi-Armed Bandit Problem with Re-Initializing Bandits Peter Jacko YEQT III November 20, 2009 Basque Center for Applied Mathematics (BCAM), Bilbao, Spain Example: Congestion
CS 700: Quantitative Methods & Experimental Design in Computer Science
 CS 700: Quantitative Methods & Experimental Design in Computer Science Sanjeev Setia Dept of Computer Science George Mason University Logistics Grade: 35% project, 25% Homework assignments 20% midterm,
CS 700: Quantitative Methods & Experimental Design in Computer Science Sanjeev Setia Dept of Computer Science George Mason University Logistics Grade: 35% project, 25% Homework assignments 20% midterm,
MPTCP is not Pareto-Optimal: Performance Issues and a Possible Solution
 MPTCP is not Pareto-Optimal: Performance Issues and a Possible Solution Ramin Khalili, Nicolas Gast, Miroslav Popovic, Jean-Yves Le Boudec To cite this version: Ramin Khalili, Nicolas Gast, Miroslav Popovic,
MPTCP is not Pareto-Optimal: Performance Issues and a Possible Solution Ramin Khalili, Nicolas Gast, Miroslav Popovic, Jean-Yves Le Boudec To cite this version: Ramin Khalili, Nicolas Gast, Miroslav Popovic,
Fuzzy Logic Based Robust Control of Queue Management and Optimal Treatment of Traffic over TCP/IP Networks
 Fuzzy Logic Based Robust Control of Queue Management and Optimal Treatment of Traffic over TCP/IP Networks Zhi Li BSc(Sci), MSc(Eng) Department of Mathematics and Computing The University of Southern Queensland
Fuzzy Logic Based Robust Control of Queue Management and Optimal Treatment of Traffic over TCP/IP Networks Zhi Li BSc(Sci), MSc(Eng) Department of Mathematics and Computing The University of Southern Queensland
PC Based Precision Timing Without GPS
 PC Based Precision Timing Without GPS Attila Pásztor EMULab at the Department of Electrical & Electronic Engineering The University of Melbourne, Victoria 31, Australia and Ericsson Hungary R&D a.pasztor@ee.mu.oz.au
PC Based Precision Timing Without GPS Attila Pásztor EMULab at the Department of Electrical & Electronic Engineering The University of Melbourne, Victoria 31, Australia and Ericsson Hungary R&D a.pasztor@ee.mu.oz.au
A Hysteresis-Based Energy-Saving Mechanism for Data Centers Christian Schwartz, Rastin Pries, Phuoc Tran-Gia www3.informatik.uni-wuerzburg.
 Institute of Computer Science Chair of Communication Networks Prof. Dr.-Ing. P. Tran-Gia A Hysteresis-Based Energy-Saving Mechanism for Data Centers Christian Schwartz, Rastin Pries, Phuoc Tran-Gia www3.informatik.uni-wuerzburg.de
Institute of Computer Science Chair of Communication Networks Prof. Dr.-Ing. P. Tran-Gia A Hysteresis-Based Energy-Saving Mechanism for Data Centers Christian Schwartz, Rastin Pries, Phuoc Tran-Gia www3.informatik.uni-wuerzburg.de
CPU SCHEDULING RONG ZHENG
 CPU SCHEDULING RONG ZHENG OVERVIEW Why scheduling? Non-preemptive vs Preemptive policies FCFS, SJF, Round robin, multilevel queues with feedback, guaranteed scheduling 2 SHORT-TERM, MID-TERM, LONG- TERM
CPU SCHEDULING RONG ZHENG OVERVIEW Why scheduling? Non-preemptive vs Preemptive policies FCFS, SJF, Round robin, multilevel queues with feedback, guaranteed scheduling 2 SHORT-TERM, MID-TERM, LONG- TERM
IMPROVING BANDWIDTH ALLOCATION IN CLOUD COMPUTING ENVIRONMENTS VIA "BANDWIDTH AS A SERVICE" PARTITIONING SCHEME. Anthony Amaro Jr
 IMPROVING BANDWIDTH ALLOCATION IN CLOUD COMPUTING ENVIRONMENTS VIA "BANDWIDTH AS A SERVICE" PARTITIONING SCHEME by Anthony Amaro Jr A thesis submitted to the Graduate College of Texas State University
IMPROVING BANDWIDTH ALLOCATION IN CLOUD COMPUTING ENVIRONMENTS VIA "BANDWIDTH AS A SERVICE" PARTITIONING SCHEME by Anthony Amaro Jr A thesis submitted to the Graduate College of Texas State University
A discrete wavelet transform traffic model with application to queuing critical time scales
 University of Roma ÒLa SapienzaÓ Dept. INFOCOM A discrete wavelet transform traffic model with application to queuing critical time scales Andrea Baiocchi, Andrea De Vendictis, Michele Iarossi University
University of Roma ÒLa SapienzaÓ Dept. INFOCOM A discrete wavelet transform traffic model with application to queuing critical time scales Andrea Baiocchi, Andrea De Vendictis, Michele Iarossi University
A Virtual Queue Approach to Loss Estimation
 A Virtual Queue Approach to Loss Estimation Guoqiang Hu, Yuming Jiang, Anne Nevin Centre for Quantifiable Quality of Service in Communication Systems Norwegian University of Science and Technology, Norway
A Virtual Queue Approach to Loss Estimation Guoqiang Hu, Yuming Jiang, Anne Nevin Centre for Quantifiable Quality of Service in Communication Systems Norwegian University of Science and Technology, Norway
Extended Ethernet Congestion Management (E 2 CM): Per Path ECM - A Hybrid Proposal
 Extended Ethernet Congestion Management (E 2 CM): Per Path ECM - A Hybrid Proposal M. Gusat, C. Minkenberg and R. Luijten IBM Research GmbH, Zurich March 14 th 2007 Outline Status at 802.1 Critique Analysis
Extended Ethernet Congestion Management (E 2 CM): Per Path ECM - A Hybrid Proposal M. Gusat, C. Minkenberg and R. Luijten IBM Research GmbH, Zurich March 14 th 2007 Outline Status at 802.1 Critique Analysis
Mininet on OpenBSD. Using rdomains for Interactive SDN Testing and Development. Ayaka Koshibe. AsiaBSDCon
 Mininet on OpenBSD Using rdomains for Interactive SDN Testing and Development Ayaka Koshibe akoshibe@openbsd.org AsiaBSDCon 2018 SDN? Network split into programmable nodes that handle traffic and entities
Mininet on OpenBSD Using rdomains for Interactive SDN Testing and Development Ayaka Koshibe akoshibe@openbsd.org AsiaBSDCon 2018 SDN? Network split into programmable nodes that handle traffic and entities
Mininet on OpenBSD. Using rdomains for Interactive SDN Testing and Development. Ayaka Koshibe. BSDCan
 Mininet on OpenBSD Using rdomains for Interactive SDN Testing and Development Ayaka Koshibe akoshibe@openbsd.org BSDCan 2018 SDN? Anything you want it to mean... Or rather, a way to logically centralize
Mininet on OpenBSD Using rdomains for Interactive SDN Testing and Development Ayaka Koshibe akoshibe@openbsd.org BSDCan 2018 SDN? Anything you want it to mean... Or rather, a way to logically centralize
Dynamic resource sharing
 J. Virtamo 38.34 Teletraffic Theory / Dynamic resource sharing and balanced fairness Dynamic resource sharing In previous lectures we have studied different notions of fair resource sharing. Our focus
J. Virtamo 38.34 Teletraffic Theory / Dynamic resource sharing and balanced fairness Dynamic resource sharing In previous lectures we have studied different notions of fair resource sharing. Our focus
Dynamic Silicon Firewall
 Dynamic Silicon Firewall A Thesis Submitted to the College of Graduate Studies and Research in Partial Fulfillment of the Requirements for the degree of Master of Science in the Department of Electrical
Dynamic Silicon Firewall A Thesis Submitted to the College of Graduate Studies and Research in Partial Fulfillment of the Requirements for the degree of Master of Science in the Department of Electrical
Bounded Delay for Weighted Round Robin with Burst Crediting
 Bounded Delay for Weighted Round Robin with Burst Crediting Sponsor: Sprint Kert Mezger David W. Petr Technical Report TISL-0230-08 Telecommunications and Information Sciences Laboratory Department of
Bounded Delay for Weighted Round Robin with Burst Crediting Sponsor: Sprint Kert Mezger David W. Petr Technical Report TISL-0230-08 Telecommunications and Information Sciences Laboratory Department of
Thermal, Mechanical & Networking Issues. Dave Bailey University of Manchester
 Thermal, Mechanical & Networking Issues Dave Bailey University of Manchester Outline Thermal Simulations Mechanical Issues Long-term studies of conductive glue Automated assembly Few words on 10 Gig Ethernet
Thermal, Mechanical & Networking Issues Dave Bailey University of Manchester Outline Thermal Simulations Mechanical Issues Long-term studies of conductive glue Automated assembly Few words on 10 Gig Ethernet
Operational Laws. Operational Laws. Overview. Operational Quantities
 Operational Laws Raj Jain Washington University in Saint Louis Jain@eecs.berkeley.edu or Jain@wustl.edu Mini-Course offered at UC erkeley, Sept-Oct 2012 These slides and audio/video recordings are available
Operational Laws Raj Jain Washington University in Saint Louis Jain@eecs.berkeley.edu or Jain@wustl.edu Mini-Course offered at UC erkeley, Sept-Oct 2012 These slides and audio/video recordings are available
Distributed Systems Fundamentals
 February 17, 2000 ECS 251 Winter 2000 Page 1 Distributed Systems Fundamentals 1. Distributed system? a. What is it? b. Why use it? 2. System Architectures a. minicomputer mode b. workstation model c. processor
February 17, 2000 ECS 251 Winter 2000 Page 1 Distributed Systems Fundamentals 1. Distributed system? a. What is it? b. Why use it? 2. System Architectures a. minicomputer mode b. workstation model c. processor
Energy-efficient Mapping of Big Data Workflows under Deadline Constraints
 Energy-efficient Mapping of Big Data Workflows under Deadline Constraints Presenter: Tong Shu Authors: Tong Shu and Prof. Chase Q. Wu Big Data Center Department of Computer Science New Jersey Institute
Energy-efficient Mapping of Big Data Workflows under Deadline Constraints Presenter: Tong Shu Authors: Tong Shu and Prof. Chase Q. Wu Big Data Center Department of Computer Science New Jersey Institute
A Generalized Processor Sharing Approach to Flow Control in Integrated Services Networks: The Single Node Case. 1
 A Generalized Processor Sharing Approach to Flow Control in Integrated Services Networks: The Single Node Case 1 Abhay K Parekh 2 3 and Robert G Gallager 4 Laboratory for Information and Decision Systems
A Generalized Processor Sharing Approach to Flow Control in Integrated Services Networks: The Single Node Case 1 Abhay K Parekh 2 3 and Robert G Gallager 4 Laboratory for Information and Decision Systems
2/5/07 CSE 30341: Operating Systems Principles
 page 1 Shortest-Job-First (SJR) Scheduling Associate with each process the length of its next CPU burst. Use these lengths to schedule the process with the shortest time Two schemes: nonpreemptive once
page 1 Shortest-Job-First (SJR) Scheduling Associate with each process the length of its next CPU burst. Use these lengths to schedule the process with the shortest time Two schemes: nonpreemptive once
Microeconomic Algorithms for Flow Control in Virtual Circuit Networks (Subset in Infocom 1989)
 Microeconomic Algorithms for Flow Control in Virtual Circuit Networks (Subset in Infocom 1989) September 13th, 1995 Donald Ferguson*,** Christos Nikolaou* Yechiam Yemini** *IBM T.J. Watson Research Center
Microeconomic Algorithms for Flow Control in Virtual Circuit Networks (Subset in Infocom 1989) September 13th, 1995 Donald Ferguson*,** Christos Nikolaou* Yechiam Yemini** *IBM T.J. Watson Research Center
PIQI-RCP: Design and Analysis of Rate-Based Explicit Congestion Control
 PIQI-RCP: Design and Analysis of Rate-Based Explicit Congestion Control Saurabh Jain and Dmitri Loguinov Texas A&M University, College Station, TX 77843 Email: saujain@tamu.edu, dmitri@cs.tamu.edu Abstract
PIQI-RCP: Design and Analysis of Rate-Based Explicit Congestion Control Saurabh Jain and Dmitri Loguinov Texas A&M University, College Station, TX 77843 Email: saujain@tamu.edu, dmitri@cs.tamu.edu Abstract
ESTIMATION OF THE BURST LENGTH IN OBS NETWORKS
 ESTIMATION OF THE BURST LENGTH IN OBS NETWORKS Pallavi S. Department of CSE, Sathyabama University Chennai, Tamilnadu, India pallavi.das12@gmail.com M. Lakshmi Department of CSE, Sathyabama University
ESTIMATION OF THE BURST LENGTH IN OBS NETWORKS Pallavi S. Department of CSE, Sathyabama University Chennai, Tamilnadu, India pallavi.das12@gmail.com M. Lakshmi Department of CSE, Sathyabama University
Continuous-time hidden Markov models for network performance evaluation
 Performance Evaluation 49 (2002) 129 146 Continuous-time hidden Markov models for network performance evaluation Wei Wei, Bing Wang, Don Towsley Department of Computer Science, University of Massachusetts,
Performance Evaluation 49 (2002) 129 146 Continuous-time hidden Markov models for network performance evaluation Wei Wei, Bing Wang, Don Towsley Department of Computer Science, University of Massachusetts,
Rate adaptation, Congestion Control and Fairness: A Tutorial. JEAN-YVES LE BOUDEC Ecole Polytechnique Fédérale de Lausanne (EPFL)
 Rate adaptation, Congestion Control and Fairness: A Tutorial JEAN-YVES LE BOUDEC Ecole Polytechnique Fédérale de Lausanne (EPFL) December 2000 2 Contents 31 Congestion Control for Best Effort: Theory 1
Rate adaptation, Congestion Control and Fairness: A Tutorial JEAN-YVES LE BOUDEC Ecole Polytechnique Fédérale de Lausanne (EPFL) December 2000 2 Contents 31 Congestion Control for Best Effort: Theory 1
2 k Factorial Designs Raj Jain
 2 k Factorial Designs Raj Jain Washington University in Saint Louis Saint Louis, MO 63130 Jain@cse.wustl.edu These slides are available on-line at: http://www.cse.wustl.edu/~jain/cse567-06/ 17-1 Overview!
2 k Factorial Designs Raj Jain Washington University in Saint Louis Saint Louis, MO 63130 Jain@cse.wustl.edu These slides are available on-line at: http://www.cse.wustl.edu/~jain/cse567-06/ 17-1 Overview!
A Quantitative View: Delay, Throughput, Loss
 A Quantitative View: Delay, Throughput, Loss Antonio Carzaniga Faculty of Informatics University of Lugano September 27, 2017 Outline Quantitative analysis of data transfer concepts for network applications
A Quantitative View: Delay, Throughput, Loss Antonio Carzaniga Faculty of Informatics University of Lugano September 27, 2017 Outline Quantitative analysis of data transfer concepts for network applications
Performance Metrics & Architectural Adaptivity. ELEC8106/ELEC6102 Spring 2010 Hayden Kwok-Hay So
 Performance Metrics & Architectural Adaptivity ELEC8106/ELEC6102 Spring 2010 Hayden Kwok-Hay So What are the Options? Power Consumption Activity factor (amount of circuit switching) Load Capacitance (size
Performance Metrics & Architectural Adaptivity ELEC8106/ELEC6102 Spring 2010 Hayden Kwok-Hay So What are the Options? Power Consumption Activity factor (amount of circuit switching) Load Capacitance (size
COMP9334: Capacity Planning of Computer Systems and Networks
 COMP9334: Capacity Planning of Computer Systems and Networks Week 2: Operational analysis Lecturer: Prof. Sanjay Jha NETWORKS RESEARCH GROUP, CSE, UNSW Operational analysis Operational: Collect performance
COMP9334: Capacity Planning of Computer Systems and Networks Week 2: Operational analysis Lecturer: Prof. Sanjay Jha NETWORKS RESEARCH GROUP, CSE, UNSW Operational analysis Operational: Collect performance
EP2200 Course Project 2017 Project II - Mobile Computation Offloading
 EP2200 Course Project 2017 Project II - Mobile Computation Offloading 1 Introduction Queuing theory provides us a very useful mathematic tool that can be used to analytically evaluate the performance of
EP2200 Course Project 2017 Project II - Mobile Computation Offloading 1 Introduction Queuing theory provides us a very useful mathematic tool that can be used to analytically evaluate the performance of
Input-queued switches: Scheduling algorithms for a crossbar switch. EE 384X Packet Switch Architectures 1
 Input-queued switches: Scheduling algorithms for a crossbar switch EE 84X Packet Switch Architectures Overview Today s lecture - the input-buffered switch architecture - the head-of-line blocking phenomenon
Input-queued switches: Scheduling algorithms for a crossbar switch EE 84X Packet Switch Architectures Overview Today s lecture - the input-buffered switch architecture - the head-of-line blocking phenomenon
The conceptual view. by Gerrit Muller University of Southeast Norway-NISE
 by Gerrit Muller University of Southeast Norway-NISE e-mail: gaudisite@gmail.com www.gaudisite.nl Abstract The purpose of the conceptual view is described. A number of methods or models is given to use
by Gerrit Muller University of Southeast Norway-NISE e-mail: gaudisite@gmail.com www.gaudisite.nl Abstract The purpose of the conceptual view is described. A number of methods or models is given to use
Wireless Internet Exercises
 Wireless Internet Exercises Prof. Alessandro Redondi 2018-05-28 1 WLAN 1.1 Exercise 1 A Wi-Fi network has the following features: Physical layer transmission rate: 54 Mbps MAC layer header: 28 bytes MAC
Wireless Internet Exercises Prof. Alessandro Redondi 2018-05-28 1 WLAN 1.1 Exercise 1 A Wi-Fi network has the following features: Physical layer transmission rate: 54 Mbps MAC layer header: 28 bytes MAC
CS 550 Operating Systems Spring CPU scheduling I
 1 CS 550 Operating Systems Spring 2018 CPU scheduling I Process Lifecycle Ready Process is ready to execute, but not yet executing Its waiting in the scheduling queue for the CPU scheduler to pick it up.
1 CS 550 Operating Systems Spring 2018 CPU scheduling I Process Lifecycle Ready Process is ready to execute, but not yet executing Its waiting in the scheduling queue for the CPU scheduler to pick it up.
Processor Sharing Flows in the Internet
 STANFORD HPNG TECHNICAL REPORT TR4-HPNG4 Processor Sharing Flows in the Internet Nandita Dukkipati, Nick McKeown Computer Systems Laboratory Stanford University Stanford, CA 9434-93, USA nanditad, nickm
STANFORD HPNG TECHNICAL REPORT TR4-HPNG4 Processor Sharing Flows in the Internet Nandita Dukkipati, Nick McKeown Computer Systems Laboratory Stanford University Stanford, CA 9434-93, USA nanditad, nickm
A Starvation-free Algorithm For Achieving 100% Throughput in an Input- Queued Switch
 A Starvation-free Algorithm For Achieving 00% Throughput in an Input- Queued Switch Abstract Adisak ekkittikul ick ckeown Department of Electrical Engineering Stanford University Stanford CA 9405-400 Tel
A Starvation-free Algorithm For Achieving 00% Throughput in an Input- Queued Switch Abstract Adisak ekkittikul ick ckeown Department of Electrical Engineering Stanford University Stanford CA 9405-400 Tel
Queuing Networks. - Outline of queuing networks. - Mean Value Analisys (MVA) for open and closed queuing networks
 Queuing Networks - Outline of queuing networks - Mean Value Analisys (MVA) for open and closed queuing networks 1 incoming requests Open queuing networks DISK CPU CD outgoing requests Closed queuing networks
Queuing Networks - Outline of queuing networks - Mean Value Analisys (MVA) for open and closed queuing networks 1 incoming requests Open queuing networks DISK CPU CD outgoing requests Closed queuing networks
