Game Characterizations and the PSPACE-Completeness of Tree Resolution Space
|
|
|
- Emerald Holmes
- 5 years ago
- Views:
Transcription
1 Game Characterizations and the PSPACE-Completeness of Tree Resolution Space Alexander Hertel & Alasdair Urquhart June 18, 2007 Abstract The Prover/Delayer game is a combinatorial game that can be used to prove upper and lower bounds on the size of Tree Resolution proofs, and also perfectly characterizes the space needed to compute them. As a proof system, Tree Resolution forms the underpinnings of all DPLL-based SAT solvers, so it is of interest not only to proof complexity researchers, but also to those in the area of propositional reasoning. In this paper, we prove the PSPACE-Completeness of the Prover/Delayer game as well as the problem of predicting Tree Resolution space requirements, where space is the number of clauses that must be kept in memory simultaneously during the computation of a refutation. Since in practice memory is often a limiting resource, researchers developing SAT solvers may wish to know ahead of time how much memory will be required for solving a certain formula, but the present result shows that predicting this is at least as hard as it would be to simply find a refutation. 1 Introduction & Motivation The Tree Resolution (T-RES) proof system has been studied extensively, and is understood quite well. Its algorithmic incarnation, DPLL, forms the basis of many SAT-solvers including clause learning algorithms. Any lower bounds proved for T-RES immediately imply lower bounds for real-world DPLL algorithms. However, compared with Resolution proof size, the amount of space needed to compute a proof has not been studied nearly as extensively. The usual definition of a Resolution proof is that it is a simple sequence of clauses, but we can redefine this so that only a small number of clauses are stored in a working memory space, typically much smaller than the size of the proof itself. The problem of determining the space required for Resolution proofs seems to have been suggested for the first time by Armin Haken in 1998, and was explored in a paper by Alekhnovich, Ben-Sasson, Razborov and Wigderson [1] and independently by Esteban and Torán [7]; Ben-Sasson proved an important tradeoff between Resolution size and space in [3]. In addition, a number of other results relating Resolution space and width are known [2, 11]. rom a practical point of view, DPLL and clause learning algorithms have been highly successful at solving SAT and SAT-related problems. The main limiting factor on these algorithms is space, namely the size of the cache used for memoization. This has inspired much research into methods for pruning space in a Resolution search. Thus there are both practical and theoretical motivations for understanding Resolution space as a resource. The authors gratefully acknowledge NSERC and the University of Toronto Department of Computer Science for supporting this research. 1
2 In this paper we prove that for T-RES, determining clause space requirements is PSPACE-Complete, which unfortunately implies that computing the T-RES space requirements for a formula is at least as hard as actually refuting it, and shows that it is therefore probably not feasible for researchers working with DPLL-based SAT solvers to predict a formula s memory needs. In addition, there are many formulas on which these SAT solvers fail, and it would be very useful to be able to tell ahead of time if this will be the case. If there was any hope of using T-RES space bounds to predict this, then the present result casts some serious doubt on that plan. The key to our main theorem is the intimate connection between Resolution space and games, and we combine three previous results and ideas in order to prove that both the Prover/Delayer game and T-RES clause space problem are PSPACE-Complete. The high-level idea behind this paper is as follows: rom [7], Prover/Delayer number is known to equal T-RES clause space, and from [10], pebbling Lingas circuits is known to be PSPACE-Complete. But the former deals with formulas, and the latter uses circuits, so we use pebbling contradiction formulas to bridge this gap. Specifically, we give tight bounds relating the black pebbling number of any Lingas circuit C to the Prover/Delayer number of the formula P eb 2 (C), thereby proving the PSPACE-Completeness of the Prover/Delayer game (and T-RES clause space by the equivalence from [7]). 2 Definitions We assume that the reader is familiar with basic proof complexity, circuit complexity, general complexity theory, and use [5] as our standard reference. By a DAG we mean a directed acyclic graph in which all nodes except source nodes have fan-in two, but unbounded fan-out, and there is a unique node (the sink, target or output node) with fan-out zero. A monotone circuit is defined as a DAG in which all nodes except the sources are labelled with AND or OR. 2.1 Resolution Space The definition of T-RES clause space requires a non-standard definition of T-RES proof that depends on the notion of configuration: Definition 2.1 (Configuration-Style T-RES Proof). A configuration C is a set of clauses. The sequence of configurations π = C 0, C 1,..., C k is a T-RES proof of C from the formula if C 0 =, C C k, and for each i < k, C i+1 is obtained from C i by deleting one or more of its clauses, adding the resolvent of two clauses of C i and deleting both parent clauses, or adding one or more of the clauses of (initial clauses). This leads us to our definition of space. Intuitively, space is the amount of memory required in order to compute π: Definition 2.2 (Clause Space). Let be a set of clauses and π be a configuration-style T-RES proof of clause C from. The tree clause space of π, denoted T CS(π) is the maximum number of clauses in any configuration of π. The tree clause space of resolving C from, denoted T CS( T-RES C), is the minimum T CS(π) over all T-RES proofs π of C from. 2.2 Pebbling Circuits & Games The investigation of Resolution space is closely associated with the well-known pebbling game and pebbling number of a DAG, originally explored in [6] as a means of investigating bounds on storage requirements. 2
3 We define the generalized black pebbling game as a single-player game in which the goal is to pebble the target node of a monotone circuit C. The game has the following rules: It starts with no pebbles on the circuit. At any point, the player may place a pebble onto any source node, or remove a pebble from any node. or any AND gate v, if both of v s immediate predecessors have pebbles on them, then the player may place a pebble on v, or slide a pebble from a predecessor to v. Similarly, for any OR gate v, if at least one of v s immediate predecessors has a pebble on it, then the player may place a pebble on v, or slide a pebble from a predecessor to v. The game ends once the target node has a pebble on it. Most of the black pebble games found in the literature can be viewed as restricted versions of this generalization. In particular, if all gates in the circuit are AND gates, then this game is equivalent to the original pebbling game on DAGs defined by Cook and Sethi [6]. Definition 2.3 (Black Pebbling Number of a Monotone Circuit). The black pebbling number of a monotone circuit C, denoted B-P eb(c), is the minimum number of pebbles needed in order to pebble C s target node using the above rules. Each version of the pebbling game can either be defined with or without sliding; for the purposes of this paper, we shall always allow sliding. 2.3 Pebbling Contradictions The formulas we call pebbling contradictions are based on the various forms of the pebbling game. Ben-Sasson gives a brief history of these formulas in [3]. The particular contradictory formulas we employ here are a generalization of those used by Ben-Sasson, Impagliazzo and Wigderson to give a near-optimal separation of tree-like and general resolution [4]. They can be interpreted as making the following contradictory claim: The input nodes of a monotone circuit C are all set to true, but the output node is set to false., where we represent node v is set to true by the disjunction v 0 v 1. Definition 2.4 (Pebbling Contradictions Based on Circuits). Let C be a monotone circuit. The set of clauses P eb 2 (C) contains the following clauses: 1. or each source node s, the clause {s 0, s 1 }; 2. or each AND node c with immediate predecessors a and b, four propagation clauses { a 0, b 0, c 0, c 1 }, { a 0, b 1, c 0, c 1 }, { a 1, b 0, c 0, c 1 }, and { a 1, b 1, c 0, c 1 }; 3. or each OR node c with immediate predecessors a and b, four propagation clauses { a 0, c 0, c 1 }, { b 0, c 0, c 1 }, { a 1, c 0, c 1 }, and { b 1, c 0, c 1 }; 4. or the target node t, two singleton clauses { t 0 } and { t 1 }. 2.4 The Prover/Delayer Game The Prover/Delayer game (P/D game), described in [4, 12], is a combinatorial game between two players, the Prover, and the Delayer, and is played on an unsatisfiable CN formula. The goal of the Prover is to falsify some initial clause of. Since the formula is unsatisfiable, this is inevitable. The game proceeds in rounds. Each round starts with the Prover querying the value of a variable. The Delayer can give one of three answers: True, alse, or You Choose. If the Delayer says You Choose, then the Prover gets to decide the value of that variable, and the Delayer wins one point. This is the only way in which points can be scored. The game finishes when any clause has been falsified. The Delayer s aim is to win as many points as possible, while the Prover aims to minimize this quantity. 3
4 Definition 2.5. Let be an unsatisfiable CN formula. The Prover/Delayer number of, denoted P D( ), is the greatest number of points the Delayer can score on with the Prover playing optimally. 3 Results Related to Resolution Space 3.1 Space & Games The pebbling game is closely related to Resolution clause space. Let be any arbitrary unsatisfiable formula, π a configuration-style RES refutation of, and G the DAG underlying the structure of π. The clause space used in computing π is exactly equal to B-P eb(g). More specifically, CS( RES ) is equal to the pebbling number of the DAG with the smallest pebbling number of all DAGs underlying valid RES refutations of. Of course, the analogous idea holds for T-RES and tree clause space. Esteban & Torán proved that the tree clause space of any unsatisfiable formula is essentially the same as its Prover/Delayer number: Theorem 3.1 ([8]). or any unsatisfiable CN formula, T CS( T-RES ) = P D( ) + 1. In addition to doing some of the pioneering research in the area of Resolution space, Esteban & Torán also showed that an upper bound on tree clause space yields an upper bound on the size of T-RES proofs [7]. Combining this with Theorem 3.1 and a little extra work shows that an upper bound on the number of points scored by the Prover immediately gives an upper bound on T-RES size: Corollary 3.2. If is a contradictory formula with P D( ) k, then has a T-RES proof of size ( n k+1). The P/D game can also be used to give a lower bound on T-RES size; in [4], Ben-Sasson, Impagliazzo and Wigderson prove that lower bounds on P D( ) can be used to prove lower bounds on the size of T-RES proofs: Theorem 3.3 ([4]). If the Delayer has a strategy guaranteed to win > k points on, then every T-RES refutation of has size > 2 k. In other words, upper and lower bounds on P D( ) not only immediately imply tightly corresponding upper and lower bounds on T CS( T-RES ), but they also imply upper and lower bounds for T-RES proof size, showing not only that the P/D game is intimately connected to the T-RES proof system, but also that T-RES size and space are closely related. 3.2 Complexity of Pebbling A number of complexity results involving pebbling are known. following: In 1978, Andrzej Lingas proved the Theorem 3.4 ([10]). Given a monotone circuit C and an integer k, the problem of determining if C can be black-pebbled with k pebbles is PSPACE-Complete. Gilbert, Lengauer and Tarjan extended this result to DAGs in 1980: Theorem 3.5 ([9]). Given a DAG G and an integer k, the problem of determining if G can be blackpebbled with k pebbles is PSPACE-Complete. These results are particularly interesting because the pebbling game only has one player, whereas most PSPACE-Complete games have two. 4
5 4 Main Results 4.1 An Easy Case of the Pebbling Game Although pebbling circuits is PSPACE-Complete in general, in this section we define an interesting set of binary DAGs whose pebbling numbers can be computed in polynomial time. To this end, we first need to define the concept of the pebbling number of a vertex in a graph: Definition 4.1 (Pebbling Number of a Vertex). In a DAG, the pebbling number of a vertex x, Peb(x), is the pebbling number of the subgraph rooted at x, with x set to be the target node. A source node has a pebbling number of 1, while if c has predecessors a and b, then Peb(c) max(peb(a), Peb(b)) + 1. This is because we can always pebble c with the following strategy: Assuming that Peb(a) Peb(b), first pebble b using Peb(b) pebbles, then remove all the pebbles except the one on b, next pebble a using Peb(a) extra pebbles, then slide the pebble on a to c. Definition 4.2 (Increasing DAGs). G I = {G G is a DAG such that there is no c V (G) with predecessors a and b with a, b, and c all having the same pebbling number} Although the pebbling game on binary DAGs is PSPACE-Complete in general, when we restrict ourselves to inputs from G I, the problem becomes much easier: Theorem 4.3. Given a binary DAG G G I pebbled using at most k pebbles is in P. and integer k, the problem of determining if G can be Proof: Since the pebbling number of each node in G is uniquely determined by those of its predecessors, simply start at the source nodes and set their pebbling numbers to 1. Then find a vertex x for which the pebbling numbers of both predecessors have been determined (since G is a DAG, such a node always exists), and set x s pebbling number. Repeat until the target node s number has been determined. Clearly this can be done in polynomial time. This gives some insight into why the pebbling game is so difficult. An inspection of the constructions from both [9] and [10] shows that the graphs resulting from the reductions contain a large number of vertices that have the same pebbling numbers as their predecessors, so the obvious algorithm above fails. 4.2 Prover Strategy for the G I DAGs In this section we describe an efficient Prover strategy for the G I graphs: Lemma 4.4. or any binary DAG G G I with pebbling number k, the Prover has a strategy limiting the Delayer to at most k = B-P eb(g) points playing on the formula P eb 2 (G). Proof: In the interests of concision, we omit a detailed proof, and instead provide the following proof sketch: The Prover first labels each node in G with its pebbling number, and first queries the variables associated with the target. The Delayer must set them both to alse, or else the game is over. The Prover then follows a path towards the source nodes, forcing the Delayer to set both variables c 0 and c 1 associated with each node c on the path to alse. Given any node c on the path, let us suppose that it has both variables c 0 and c 1 set to alse, and that the predecessors of c are a and b. In all cases, it is possible for the Prover to query the variables associated with a and b in such a way that sets both a 0 and a 1, or b 0 and b 1 to alse while giving up at most one point every time the pebbling number decreases. Eventually the path will reach a node with 5
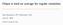
6 two source nodes as its children, in which case it is easy to see that the Delayer can win at most 2 more points. Since the Delayer wins at most 1 point every time the pebbling number decreases, and since only 2 points can be won in the base case, the Prover limits the Delayer to at most B-P eb(g) points, as required. 4.3 Prover Strategy for the Lingas Circuits Lingas 1978 paper [10] shows that the black pebbling game on monotone circuits is PSPACE-Complete by reducing from the 3-QB problem with alternating quantifiers. This is done by taking a formula and outputting a binary circuit C and integer k such that is true if and only if C has a pebbling number of at most k. The reduction builds a number of widgets based on. The original example from [10] can be seen below in igure 1. The construction includes one widget for each quantifier, literal, and clause, as well as one pyramid graph that acts as a conjunction between the clauses. Each clause widget is incident on the widgets corresponding to the literals contained in the clause. The literal widgets are shown using shorthand notation; they are the pyramid graphs from [6], and an example is given in the upper corner of the diagram. The pebbling number output by the reduction is k = 2U + E + M, where U, E, and M are the respective number of universal quantifiers, existential quantifiers, and clauses in. Intuitively, the reduction works by forcing any pebbling to simulate a brute force QB proof system. or each universal quantifier, the pebbling must travel up both sides, requiring that the entire circuit below that point be re-pebbled, thereby ensuring that is true. We refer to the circuits corresponding to true QB formulas as the Lingas circuits, defined formally as follows: Definition 4.5 (Lingas Circuits). C L = {C a true 3-QB formula with alternating quantifiers such that applying Lingas s reduction to yields the circuit C} We shall make use of the PSPACE-Completeness of the Lingas circuits to prove the PSPACE- Completeness of the P/D game as well as the T-RES clause space problem. To this end we must first prove that for any Lingas circuit C, when playing on P eb 2 (C), the Prover has a strategy limiting the Delayer to at most B-P eb(c) points. The strategy is quite simple: the Prover first forces the Delayer to admit that both variables associated with the target node must be alse. As with the G I DAGs, the Prover then proceeds to propagate this Double alse setting downwards. We show that it is possible to traverse each existential widget while giving up at most one point, each universal widget while giving up at most two, and finally that it is possible to traverse the conjunctive pyramid and derive the ultimate contradictions while giving up at most M points, where M is the number of clauses in the formula underlying the circuit. Each of these steps shall be proven by giving a decision tree showing the order in which the Prover queries variables. Each branch in this tree shall terminate with the Delayer scoring no more than B- P eb(c) points. A contradiction can be obtained (thereby ending the game) by falsifying an initial clause of P eb 2 (C). The Prover s strategy is interesting in that whenever the Delayer responds You Choose to a query, the Prover shall always respond with True. Note that the Delayer has the choice of three different responses after each variable is queried, but our decision tree only needs to be binary, because if the Prover is willing to give the Delayer one point by responding to the Delayer s You Choose answer, then there is no sense in exploring the path in which the Delayer gives the same answer without winning a point. 6
7 Target Node t b i Literal Widget b i Widget q 0 q 0 b 0 b d 0 d 0 c 1 c 1 The pebbling number of each pyramid is indicated in the shorthand version. q 1 Widget o 1 q 1 b 1 b w 1 c 2 d 1 d 1 c 2 b 2 b2 Widget q 2 q d 4 d 2 d 2 c 3 b 3 b3 c 3 q 3 Widget o 3 q w 3 d 3 d 3 c 4 c 4 Widget b 4 b4 q 4 q Quantifier Widgets Literal Widgets Clause Widgets Conjunctive Pyramid Graph igure 1: The monotone circuit resulting from applying Lingas s reduction to the true formula = x 0 x 1 x 2 x 3 x 4 (x 0 x 1 x 2 ) ( x 1 x 2 x 3 ) ( x 0 x 3 x 4 ) ( x 2 x 3 x 4 ). An example of a pyramid graph is shown in the upper corner. In this case k = = 11, but if were false, then the circuit would require k + 1 pebbles and could not be pebbled using only k. Theorem 4.6. or any binary circuit C C L with pebbling number k, when playing on the formula P eb 2 (C), the Prover has a strategy limiting the Delayer to at most k = B-P eb(c) points. Proof. The Prover s strategy proceeds as follows: first query t 0 and then t 1. The Delayer must set these variables to alse, or else the game is over. The Delayer has therefore scored no points, and we enter 7
8 the first quantifier widget with k points remaining. Next the Prover inductively traverses the quantifier widgets in order, propagating the Double alse setting downwards towards the conjunctive pyramid. The Prover has a strategy that gives up at most one point while traversing an existential widget, and at most two points when traversing a universal widget. The existential widget and the Prover s strategy for traversing it are shown in igure 2. We assume that we have j points remaining before the Delayer reaches k points, and that both variables associated with either the node d i 1 or d i 1 have been set to alse. Decision tree edges are labelled with the different possibilities at each step during the P/D game; represents the case when the Delayer says You Choose, and the Prover replies True, and represents the case when the Delayer says alse. Leaves are labelled in the P/D game outcomes which they lead to; those labelled with numbers represent situations in which the game is over since an initial clause has been falsified, and the number indicates how many points were scored. Although we said that the Prover may give up at most 1 point while traversing this widget, some leaves end with the Delayer scoring 2 points. This is not a problem because even if this is the final quantifier widget, the formula has at least one clause, so we have at least one extra point s leeway. The leaf corresponding to both of b i s variables being set to alse corresponds to the game entering the pyramid graph associated with variable b i that has pebbling number j. Since each pyramid graph belongs to the G I family, the Delayer can score at most j points on it by Lemma 4.4. The remaining leaf is the one in which the widget has been traversed with only 1 point scored. Note that this decision tree corresponds to the strategy in which the Prover traversed the widget while setting one of the variables associated with b i to True and both of the variables associated with d i+1 to alse, thereby leading to the next widget. The case in which the Prover traverses the widget while setting one of the variables associated with b i to True and both of the variables associated with d i+1 to alse is completely symmetrical. In other words, the Prover has complete control over which of the literal widgets is set to True. This is important because it allows the Prover to set the literal widgets in such a way so as to make the formula underlying the circuit true. The universal widget and the Prover s strategy for traversing it are shown in igure 2. We have j points remaining before the Delayer reaches k points, and both variables associated with either the node d i or d i have been set to alse. Once again, some paths lead to the Delayer scoring 3 points, but this is all right even if this is the final quantifier widget, since we have at least one point s leeway. Also as before, the pyramid graphs corresponding to both the literal widgets and the o i widget belong to the G I family, so by Lemma 4.4, the Delayer can score at most j 1, j 1, and j points on them, respectively. Note the two leaves in which the widget has been traversed with only 2 points scored. In one case, one of the variables associated with b i is set to True and both variables associated with d i+1 are set to alse, and in the other case one of the variables associated with b i is set to True, and both of the variables associated with d i+1 are set to alse, thereby leading to the next widget. We now show how the Prover traverses the conjunctive pyramid graph. The apex of the conjunctive pyramid is part of the final quantifier widget, so both of its variables have been set to alse. Since the formula underlying the Lingas circuit has M clauses and we have successfully traversed all of the clause widgets while giving up only the minimum number of points, we still have M points remaining. The conjunctive pyramid required to join M clauses has M 1 AND gates on its base, and therefore has pebbling number M 1. Let us assume for a moment that the leaves of the conjunctive pyramid have no children. Since the pyramid belongs to the G I family, the Prover has a strategy limiting the Delayer to at most M 1 points. However, since each of the conjunctive pyramid s leaves does have two children, we must explore the decision tree rooted at the possibility that the two variables associated with a leaf l are both set to alse. Since the Delayer did not say You Choose on either of l s variables, the number of points scored in setting them both to alse is at most M 2. This is the worst-case scenario branching 8
9 Previous Widget b i,0 d i d i Literal Widgets q i,0 b i,1 Widget q i q i b i j b i j q i,1 j Points rom Pyramid d i+1,0 d i+1 d i+1 d i+1,1 Next Widget Widget Traversed 1 Point, b i set to T Previous Widget d i d i Widget q i q i o i w i j d i+1 d i+1 Next Widget Literal Widgets b i j-1 b i j-1 q i,0 q i, 0 b i,0 o i,1 q i, 1 w i,0 b i,1 j Points rom b i,0 Pyramid w i,1 3 Pts. 1 Pt. + j - 1 Pts. rom d i+1, 0 b i,1 Pyramid d i+1,0 3 Pts. d i+1, 1 3 Pts. 1 Pt. + j - 1 Pts. rom d i+1,1 Pyramid 3 Pts. 3 Pts. Widget Traversed 2 Points, b i set to T q i,1 o i,0 3 Pts. Widget Traversed 2 Points, b i set to T c i, 0 l Clause Widgets c i c i c i+1 c 6 i+1 5 c i+1, 0 c i, 1 c i+1, 1 c i,0 c i+1,0 c i,1 1 Pt. c i+1,1 1 Pt. 0 Pts. 1 Pt. igure 2: The different widgets from Lingas s construction together with the decision trees showing the prover s strategies for traversing them. Duplicate subtrees are indicated by having multiple parents. down the conjunctive pyramid, so the number of points scored on all other paths to leaves is strictly less than M 2. We therefore have at least 2 points left with which to derive a contradiction within the clause widgets, and shall show how to force a contradiction given a conjunction pyramid leaf l that has had both of its 9
10 associated variables set to alse. This strategy is shown in igure 2. A key observation to make is that it is possible for the Prover to traverse the quantifier widgets such that the literal widgets that are attached to the existential widgets are set to True in any arbitrary way. Since the formula which the overall circuit is based on is a true QB formula, it is therefore possible to set them so that each clause widget is incident on at least one literal widget that has been set to True. This ensures that the Prover s strategy given by the decision tree in igure 2 will always work. Note that the subtrees in the Prover s strategy labelled with may or may not be necessary, depending on which literal widgets were set to True. Since each existential and universal widgets can be traversed while only giving up 1 and 2 points respectively, the conjunctive pyramid can be traversed while only giving up M 2 points, and a final contradiction can always be derived within the clause widgets while giving up at most 2 points, it follows that all of the above decision trees can be combined to show that the Prover has a strategy limiting the Delayer to at most B-P eb(c) points, as required. 4.4 Delayer Strategy for Monotone Circuits We now show that for any binary monotone circuit C, when playing the P/D game on P eb 2 (C), the Delayer has a strategy that will always win at least B-P eb(c) points. In [4] the authors give a Delayer strategy that wins at least B-P eb(g) 3 points, where B-P eb(g) is defined without sliding. We improve this argument to show that the Delayer has a strategy that is guaranteed to win at least B-P eb(g) points, defined with sliding. In [4], the Delayer maintains a DAG G, with certain nodes marked as source nodes, and other nodes marked as target nodes. In the improved strategy, which applies to the more general case of monotone circuits, the Delayer also maintains such a marked monotone circuit C, but in addition, certain source nodes have pebbles on them. Thus at each stage of the game, the Delayer maintains a structure of the form C, S, T, P, where C is a monotone circuit, S and T are disjoint subsets of C, and P S. By Peb(C, S, T, P ), we mean the pebbling number of the marked, pebbled circuit C, S, T, P, where the pebbles on the nodes in P can be used as free pebbles. The Delayer s strategy proceeds as follows: at the start of the game, P is empty, S is the set of source nodes of the circuit C, and T contains the unique target node of C. At the start of each round in the game, the Prover queries a variable v i, associated with a vertex v in the circuit C. The Delayer s strategy consists of two stages. In the first stage, the Delayer updates the sets S and T ; in the second stage, the Delayer answers the Prover s query, and updates P. In the first stage, assume that the marked, pebbled circuit at the start of the round is C, S, T, P ; the Delayer updates S and T to S and T as follows: Case 1a: If v S T, then set S := S, and T := T. Case 1b: If v S T, and Peb(C, S, T, P ) = Peb(C, S, T {v}, P ), then set S := S and T := T {v}. Case 1c: If v S T, and Peb(C, S, T, P ) > Peb(C, S, T {v}, P ), then set S := S {v} and T := T. In the second stage of the Delayer s strategy, the Delayer updates P to P, and responds to the Prover s query. Case 2a: If v S, and v has no pebble on it, then respond You Choose, and place a pebble on v (i.e. P := P {v}). If v has a pebble on it, then set the queried variable the value True. Case 2b: If v T, then set the queried variable to alse, and set P := P. 10
11 Lemma 4.7. When the game terminates, Peb(C, S, T, P ) = 0. Proof. When the game terminates, an initial clause is falsified. Because of the strategy followed by the Delayer in the second stage of each round, this clause cannot be a clause associated with one of the initial source nodes of C, nor can it be the clause associated with the target node of C. Consequently, it must be a propagation clause associated with a vertex v and its immediate predecessors u 1, u 2 if v is an gate, or just one of its immediate predecessors if v is an gate. Let us assume that v is an gate. Then both variables associated with v must be set to alse, from which it follows that v T, by Case 2a. If u i is one of the immediate predecessors of v, one of the two variables associated with u i must be set to True. By Case 2b, u i cannot be in T, so u i S. It follows from this that there must be a pebble on u i. Hence, we can pebble C, S, T, P by sliding the pebble on u i to v, showing that Peb(C, S, T, P ) = 0. The second case, where v is an gate, proceeds by essentially the same argument. Lemma 4.8. If C, S, T, P is a marked, pebbled circuit, and v a vertex in C, then P eb(c, S, T, P ) max{peb(c, S, T {v}, P ), Peb(C, S {v}, T, P {v}) + 1}. Proof. We employ the following strategy to pebble T from S, using only the free pebbles in P. irst, pebble T {v} from S, using Peb(G, S, T {v}, P ) pebbles. If the result is a pebble in T, then we are through, otherwise the final configuration has a pebble on v. Simply remove the other pebbles, then pebble T from S {v}; this final step uses a total of Peb(C, S {v}, T, P {v}) + 1 pebbles. Theorem 4.9. If at the beginning of a round in the game, the marked, pebbled circuit is C, S, T, P, then the Delayer can score at least Peb(C, S, T, P ) more points in the game. Proof: We argue by induction on the depth of the game tree. Lemma 4.7 settles the base case. Assume that the theorem holds for a subtree in which the marked, pebbled circuit is C, S, T, P ; we wish to show that it holds also for its immediate supertree, associated with the marked, pebbled circuit C, S, T, P. If Peb(C, S, T, P ) = Peb(C, S, T, P ), then there is nothing to prove, so we can assume that Peb(C, S, T, P ) > Peb(C, S, T, P ). By Lemma 4.8, Peb(C, S, T, P ) = Peb(C, S, T, P ) + 1. Now consider the round of the game in which the Delayer s initial circuit is C, S, T, P, and the final circuit is C, S, T, P, and the variable queried was v i. If v were in T, or if v had a pebble on it at the start of the round, then Peb(C, S, T, P ) = Peb(C, S, T, P ). It follows from this that v is in S, but does not have a pebble on it at the start of the round, so the Delayer scores a point during this round. This proves that the condition of the Theorem also holds for the supertree. Corollary or any monotone circuit C, when playing on the formula P eb 2 (C), the Delayer has a strategy that wins at least B-P eb(c) points. 4.5 PSPACE-Completeness of TCSP & P/D Game This section contains our main result, namely the PSPACE-Completeness of the T-RES clause space problem as well as the P/D game. The T-RES clause space problem (T CSP ) asks: Given a formula and integer k, does have a T-RES refutation with clause space at most k The Prover Delayer game Problem (P DGAME) asks: Given a formula and integer k, is P D( ) at most k The results from the previous sections allow us to prove the PSPACE-Completeness of T CSP and P DGAM E via a straightforward reduction from the PSPACE-Complete problem of pebbling Lingas circuits. However, before proving this result we must first give a PSPACE algorithm for them these problems which uses following Lemma: Lemma Every unsatisfiable CN formula has a T-RES refutation with clause space at most n + 1, where n is the number of distinct variables in. 11
12 Proof. Let be any arbitrary unsatisfiable CN formula. Simply take and choose some ordering for its n variables. Build a complete DPLL tree for, branching on this ordering. This tree can be viewed as a T-RES proof that can be pebbled with at most n + 1 pebbles, since any binary tree can be pebbled with h + 1 pebbles, where h is the height of the tree. These pebbles correspond to which clauses need to be kept in memory in order to verify the proof, showing that for any unsatisfiable, T CS( T-RES ) n + 1, as required. Lemma T CSP PSPACE and P DGAME PSPACE Proof: Given an input (, k) we first determine if is satisfiable. Since SAT N P and N P PSPACE, this is not a problem. If is satisfiable, then we reject. If it is unsatisfiable, then we look at k. If k n + 1, where n is the number of distinct variables in, then by Lemma 4.11 we simply accept. Otherwise is unsatisfiable and k n, so if has a (configuration style) T-RES refutation π with T CS( T-RES ) k, then each configuration contains at most k clauses. Since k n and each clause contains at most n variables, each configuration in π requires only polynomial space. Although we don t have access to π, we verify it as follows: Using a non-deterministic algorithm, start with a configuration C 0 =. Guess configuration C 1, check to ensure that it follows from C 0 by a legal tree resolution step, and erase configuration C 0. Next, guess configuration C 2, check to make sure that it follows from C 1, and erase configuration C 1. Continue this way until C k has been derived. At any time, there are only two configurations in memory, but since each configuration uses at most quadratic space, our computation is in N PSPACE. inally, we appeal to Savitch s theorem to show that the problem of determining whether or not has T-RES refutation π with T CS( T-RES ) k is in PSPACE, thereby completing our PSPACE algorithm. By Theorem 3.1, this immediately implies that P DGAM E PSPACE as well. We are now ready to prove our main result: Theorem P DGAME and T CSP are both PSPACE-Complete. Proof: By Lemma 4.12, we know that P DGAME PSPACE. Next we show that P DGAME is PSPACE-Hard by reducing from black pebbling the Lingas circuits C L, which proceeds by simply taking the input (C, k), and outputting (P eb 2 (C), k). Clearly this is a polytime reduction, and it is easy to see that it is correct by showing that (C, k) C L if and only if (P eb 2 (C), k) P DGAME: If (C, k) C L, then B-P eb(c) k, so by Theorem 4.6, P D(P eb 2 (C)) k, and (P eb 2 (C), k) P DGAME. On the other hand, if (C, k) / C L, then B-P eb(c) > k, so by Corollary 4.10, P D(P eb 2 (C)) > k, and (P eb 2 (C), k) / P DGAME. Therefore P DGAME is PSPACE-Complete, and by Theorem 3.1 it is easy to design a PSPACE- Hardness reduction from P DGAME to T CSP as well. References [1] M. Alekhnovich, E. Ben-Sasson, A.A. Razborov, and A. Wigderson. Space Complexity in Propositional Calculus. SIAM J. of Comp., V.31,No.4: , [2] A. Atserias and V. Dalmau. A Combinatorial Characterization of Resolution Width. Proc. of the 18th IEEE Conference on Computational Complexity, [3] E. Ben-Sasson. Size Space Tradeoffs or Resolution. Proceedings of the 34th ACM Symposium on the Theory of Computing, pages ,
13 [4] E. Ben-Sasson, R. Impagliazzo, and A. Wigderson. Near Optimal Separation of Tree-like and General Resolution. Combinatorica, Vol. 24, No. 4: , [5] P. Clote and E. Kranakis. Boolean unctions and Computation Models. Springer-Verlag, Berlin, [6] S. Cook and R. Sethi. Storage Requirements for Deterministic Polynomial Time Recognizable Languages. J. of Computer & System Sciences, pages 25 37, [7] J. Esteban and J. Torán. Space Bounds for Resolution. Information and Computation, 171:84 97, [8] J. Esteban and J. Torán. A Combinatorial Characterization of Treelike Resolution Space. Information Processing Letters, 87: , [9] J. R. Gilbert, T. Lengauer, and R. E. Tarjan. The Pebbling Problem is Complete in Polynomial Space. SIAM Journal of Computing, Vol. 9, No. 3: , [10] A. Lingas. A PSPACE-Complete Problem Related to a Pebble Game. In Proceedings of the ifth Colloquium on Automata, Languages and Programming, pages , London, UK, Springer- Verlag. [11] J. Nordström. Narrow Proofs May Be Spacious: Separating Space and Width in Resolution. Proc. of the 38th ACM Symposium on the Theory of Computing, [12] P. Pudlák and Russell Impagliazzo. Lower Bounds for DLL Algorithms for k-sat. Proceedings of SODA 2000,
Resolution and Pebbling Games
 Resolution and Pebbling Games Nicola Galesi and Neil Thapen Abstract. We define a collection of Prover-Delayer games to characterise some subsystems of propositional resolution. We give some natural criteria
Resolution and Pebbling Games Nicola Galesi and Neil Thapen Abstract. We define a collection of Prover-Delayer games to characterise some subsystems of propositional resolution. We give some natural criteria
Research Proposal & Progress Report
 Research Proposal & Progress Report Alexander Hertel July 5, 2006 1 Introduction This paper has two purposes. The first purpose is to provide a progress report describing research and results completed
Research Proposal & Progress Report Alexander Hertel July 5, 2006 1 Introduction This paper has two purposes. The first purpose is to provide a progress report describing research and results completed
INSTITUTE OF MATHEMATICS THE CZECH ACADEMY OF SCIENCES. A trade-off between length and width in resolution. Neil Thapen
 INSTITUTE OF MATHEMATICS THE CZECH ACADEMY OF SCIENCES A trade-off between length and width in resolution Neil Thapen Preprint No. 59-2015 PRAHA 2015 A trade-off between length and width in resolution
INSTITUTE OF MATHEMATICS THE CZECH ACADEMY OF SCIENCES A trade-off between length and width in resolution Neil Thapen Preprint No. 59-2015 PRAHA 2015 A trade-off between length and width in resolution
A note on monotone real circuits
 A note on monotone real circuits Pavel Hrubeš and Pavel Pudlák March 14, 2017 Abstract We show that if a Boolean function f : {0, 1} n {0, 1} can be computed by a monotone real circuit of size s using
A note on monotone real circuits Pavel Hrubeš and Pavel Pudlák March 14, 2017 Abstract We show that if a Boolean function f : {0, 1} n {0, 1} can be computed by a monotone real circuit of size s using
Space and Nondeterminism
 CS 221 Computational Complexity, Lecture 5 Feb 6, 2018 Space and Nondeterminism Instructor: Madhu Sudan 1 Scribe: Yong Wook Kwon Topic Overview Today we ll talk about space and non-determinism. For some
CS 221 Computational Complexity, Lecture 5 Feb 6, 2018 Space and Nondeterminism Instructor: Madhu Sudan 1 Scribe: Yong Wook Kwon Topic Overview Today we ll talk about space and non-determinism. For some
On the Automatizability of Resolution and Related Propositional Proof Systems
 On the Automatizability of Resolution and Related Propositional Proof Systems Albert Atserias and María Luisa Bonet Departament de Llenguatges i Sistemes Informàtics Universitat Politècnica de Catalunya
On the Automatizability of Resolution and Related Propositional Proof Systems Albert Atserias and María Luisa Bonet Departament de Llenguatges i Sistemes Informàtics Universitat Politècnica de Catalunya
Propositional and Predicate Logic - V
 Propositional and Predicate Logic - V Petr Gregor KTIML MFF UK WS 2016/2017 Petr Gregor (KTIML MFF UK) Propositional and Predicate Logic - V WS 2016/2017 1 / 21 Formal proof systems Hilbert s calculus
Propositional and Predicate Logic - V Petr Gregor KTIML MFF UK WS 2016/2017 Petr Gregor (KTIML MFF UK) Propositional and Predicate Logic - V WS 2016/2017 1 / 21 Formal proof systems Hilbert s calculus
Proof Complexity of Intuitionistic Propositional Logic
 Proof Complexity of Intuitionistic Propositional Logic Alexander Hertel & Alasdair Urquhart November 29, 2006 Abstract We explore the proof complexity of intuitionistic propositional logic (IP L) The problem
Proof Complexity of Intuitionistic Propositional Logic Alexander Hertel & Alasdair Urquhart November 29, 2006 Abstract We explore the proof complexity of intuitionistic propositional logic (IP L) The problem
The NP-hardness of finding a directed acyclic graph for regular resolution
 The NP-hardness of finding a directed acyclic graph for regular resolution Samuel R. Buss Department of Mathematics University of California, San Diego La Jolla, CA 92093-0112, USA sbuss@math.ucsd.edu
The NP-hardness of finding a directed acyclic graph for regular resolution Samuel R. Buss Department of Mathematics University of California, San Diego La Jolla, CA 92093-0112, USA sbuss@math.ucsd.edu
RESOLUTION OVER LINEAR EQUATIONS AND MULTILINEAR PROOFS
 RESOLUTION OVER LINEAR EQUATIONS AND MULTILINEAR PROOFS RAN RAZ AND IDDO TZAMERET Abstract. We develop and study the complexity of propositional proof systems of varying strength extending resolution by
RESOLUTION OVER LINEAR EQUATIONS AND MULTILINEAR PROOFS RAN RAZ AND IDDO TZAMERET Abstract. We develop and study the complexity of propositional proof systems of varying strength extending resolution by
Parameterized Complexity of DPLL Search Procedures
 Parameterized Complexity of DPLL Search Procedures Olaf Beyersdorff 1, Nicola Galesi 2, and Massimo Lauria 2 1 Institut für Theoretische Informatik, Leibniz Universität Hannover, Germany 2 Dipartimento
Parameterized Complexity of DPLL Search Procedures Olaf Beyersdorff 1, Nicola Galesi 2, and Massimo Lauria 2 1 Institut für Theoretische Informatik, Leibniz Universität Hannover, Germany 2 Dipartimento
LOGIC PROPOSITIONAL REASONING
 LOGIC PROPOSITIONAL REASONING WS 2017/2018 (342.208) Armin Biere Martina Seidl biere@jku.at martina.seidl@jku.at Institute for Formal Models and Verification Johannes Kepler Universität Linz Version 2018.1
LOGIC PROPOSITIONAL REASONING WS 2017/2018 (342.208) Armin Biere Martina Seidl biere@jku.at martina.seidl@jku.at Institute for Formal Models and Verification Johannes Kepler Universität Linz Version 2018.1
CS Introduction to Complexity Theory. Lecture #11: Dec 8th, 2015
 CS 2401 - Introduction to Complexity Theory Lecture #11: Dec 8th, 2015 Lecturer: Toniann Pitassi Scribe Notes by: Xu Zhao 1 Communication Complexity Applications Communication Complexity (CC) has many
CS 2401 - Introduction to Complexity Theory Lecture #11: Dec 8th, 2015 Lecturer: Toniann Pitassi Scribe Notes by: Xu Zhao 1 Communication Complexity Applications Communication Complexity (CC) has many
On the Relative Strength of Pebbling and Resolution (Extended Abstract)
 On the Relative Strength of Pebbling and Resolution (Extended Abstract) Jakob Nordström Computer Science and Artificial Intelligence Laboratory Massachusetts Institute of Technology Cambridge, MA 02139,
On the Relative Strength of Pebbling and Resolution (Extended Abstract) Jakob Nordström Computer Science and Artificial Intelligence Laboratory Massachusetts Institute of Technology Cambridge, MA 02139,
Lecture 8. MINDNF = {(φ, k) φ is a CNF expression and DNF expression ψ s.t. ψ k and ψ is equivalent to φ}
 6.841 Advanced Complexity Theory February 28, 2005 Lecture 8 Lecturer: Madhu Sudan Scribe: Arnab Bhattacharyya 1 A New Theme In the past few lectures, we have concentrated on non-uniform types of computation
6.841 Advanced Complexity Theory February 28, 2005 Lecture 8 Lecturer: Madhu Sudan Scribe: Arnab Bhattacharyya 1 A New Theme In the past few lectures, we have concentrated on non-uniform types of computation
Regular Resolution Lower Bounds for the Weak Pigeonhole Principle
 Regular Resolution Lower Bounds for the Weak Pigeonhole Principle Toniann Pitassi Department of Computer Science University of Toronto toni@cs.toronto.edu Ran Raz Department of Computer Science Weizmann
Regular Resolution Lower Bounds for the Weak Pigeonhole Principle Toniann Pitassi Department of Computer Science University of Toronto toni@cs.toronto.edu Ran Raz Department of Computer Science Weizmann
Resolution Lower Bounds for the Weak Pigeonhole Principle
 Electronic Colloquium on Computational Complexity, Report No. 21 (2001) Resolution Lower Bounds for the Weak Pigeonhole Principle Ran Raz Weizmann Institute, and The Institute for Advanced Study ranraz@wisdom.weizmann.ac.il
Electronic Colloquium on Computational Complexity, Report No. 21 (2001) Resolution Lower Bounds for the Weak Pigeonhole Principle Ran Raz Weizmann Institute, and The Institute for Advanced Study ranraz@wisdom.weizmann.ac.il
Worst-Case Upper Bound for (1, 2)-QSAT
 Worst-Case Upper Bound for (1, 2)-QSAT Minghao Yin Department of Computer, Northeast Normal University, Changchun, China, 130117 ymh@nenu.edu.cn Abstract. The rigorous theoretical analysis of the algorithm
Worst-Case Upper Bound for (1, 2)-QSAT Minghao Yin Department of Computer, Northeast Normal University, Changchun, China, 130117 ymh@nenu.edu.cn Abstract. The rigorous theoretical analysis of the algorithm
From Small Space to Small Width in Resolution
 From Small Space to Small Width in Resolution Yuval Filmus 1, Massimo Lauria 2, Mladen Mikša 2, Jakob Nordström 2, and Marc Vinyals 2 1 Simons Institute for the Theory of Computing, University of California,
From Small Space to Small Width in Resolution Yuval Filmus 1, Massimo Lauria 2, Mladen Mikša 2, Jakob Nordström 2, and Marc Vinyals 2 1 Simons Institute for the Theory of Computing, University of California,
Propositional Logic: Evaluating the Formulas
 Institute for Formal Models and Verification Johannes Kepler University Linz VL Logik (LVA-Nr. 342208) Winter Semester 2015/2016 Propositional Logic: Evaluating the Formulas Version 2015.2 Armin Biere
Institute for Formal Models and Verification Johannes Kepler University Linz VL Logik (LVA-Nr. 342208) Winter Semester 2015/2016 Propositional Logic: Evaluating the Formulas Version 2015.2 Armin Biere
Clause/Term Resolution and Learning in the Evaluation of Quantified Boolean Formulas
 Journal of Artificial Intelligence Research 1 (1993) 1-15 Submitted 6/91; published 9/91 Clause/Term Resolution and Learning in the Evaluation of Quantified Boolean Formulas Enrico Giunchiglia Massimo
Journal of Artificial Intelligence Research 1 (1993) 1-15 Submitted 6/91; published 9/91 Clause/Term Resolution and Learning in the Evaluation of Quantified Boolean Formulas Enrico Giunchiglia Massimo
First-order resolution for CTL
 First-order resolution for Lan Zhang, Ullrich Hustadt and Clare Dixon Department of Computer Science, University of Liverpool Liverpool, L69 3BX, UK {Lan.Zhang, U.Hustadt, CLDixon}@liverpool.ac.uk Abstract
First-order resolution for Lan Zhang, Ullrich Hustadt and Clare Dixon Department of Computer Science, University of Liverpool Liverpool, L69 3BX, UK {Lan.Zhang, U.Hustadt, CLDixon}@liverpool.ac.uk Abstract
A Lower Bound of 2 n Conditional Jumps for Boolean Satisfiability on A Random Access Machine
 A Lower Bound of 2 n Conditional Jumps for Boolean Satisfiability on A Random Access Machine Samuel C. Hsieh Computer Science Department, Ball State University July 3, 2014 Abstract We establish a lower
A Lower Bound of 2 n Conditional Jumps for Boolean Satisfiability on A Random Access Machine Samuel C. Hsieh Computer Science Department, Ball State University July 3, 2014 Abstract We establish a lower
On extracting computations from propositional proofs (a survey)
 On extracting computations from propositional proofs (a survey) Pavel Pudlák September 16, 2010 Abstract This paper describes a project that aims at showing that propositional proofs of certain tautologies
On extracting computations from propositional proofs (a survey) Pavel Pudlák September 16, 2010 Abstract This paper describes a project that aims at showing that propositional proofs of certain tautologies
Lecture 11: Proofs, Games, and Alternation
 IAS/PCMI Summer Session 2000 Clay Mathematics Undergraduate Program Basic Course on Computational Complexity Lecture 11: Proofs, Games, and Alternation David Mix Barrington and Alexis Maciel July 31, 2000
IAS/PCMI Summer Session 2000 Clay Mathematics Undergraduate Program Basic Course on Computational Complexity Lecture 11: Proofs, Games, and Alternation David Mix Barrington and Alexis Maciel July 31, 2000
A Duality between Clause Width and Clause Density for SAT
 A Duality between Clause Width and Clause Density for SAT Chris Calabro, Russell Impagliazzo, Ramamohan Paturi University of California, San Diego 9500 Gilman Drive, La Jolla, CA 92093 ccalabro,russell,paturi
A Duality between Clause Width and Clause Density for SAT Chris Calabro, Russell Impagliazzo, Ramamohan Paturi University of California, San Diego 9500 Gilman Drive, La Jolla, CA 92093 ccalabro,russell,paturi
On the Computational Hardness of Graph Coloring
 On the Computational Hardness of Graph Coloring Steven Rutherford June 3, 2011 Contents 1 Introduction 2 2 Turing Machine 2 3 Complexity Classes 3 4 Polynomial Time (P) 4 4.1 COLORED-GRAPH...........................
On the Computational Hardness of Graph Coloring Steven Rutherford June 3, 2011 Contents 1 Introduction 2 2 Turing Machine 2 3 Complexity Classes 3 4 Polynomial Time (P) 4 4.1 COLORED-GRAPH...........................
CSC 2429 Approaches to the P vs. NP Question and Related Complexity Questions Lecture 2: Switching Lemma, AC 0 Circuit Lower Bounds
 CSC 2429 Approaches to the P vs. NP Question and Related Complexity Questions Lecture 2: Switching Lemma, AC 0 Circuit Lower Bounds Lecturer: Toniann Pitassi Scribe: Robert Robere Winter 2014 1 Switching
CSC 2429 Approaches to the P vs. NP Question and Related Complexity Questions Lecture 2: Switching Lemma, AC 0 Circuit Lower Bounds Lecturer: Toniann Pitassi Scribe: Robert Robere Winter 2014 1 Switching
Essential facts about NP-completeness:
 CMPSCI611: NP Completeness Lecture 17 Essential facts about NP-completeness: Any NP-complete problem can be solved by a simple, but exponentially slow algorithm. We don t have polynomial-time solutions
CMPSCI611: NP Completeness Lecture 17 Essential facts about NP-completeness: Any NP-complete problem can be solved by a simple, but exponentially slow algorithm. We don t have polynomial-time solutions
Geometric Steiner Trees
 Geometric Steiner Trees From the book: Optimal Interconnection Trees in the Plane By Marcus Brazil and Martin Zachariasen Part 3: Computational Complexity and the Steiner Tree Problem Marcus Brazil 2015
Geometric Steiner Trees From the book: Optimal Interconnection Trees in the Plane By Marcus Brazil and Martin Zachariasen Part 3: Computational Complexity and the Steiner Tree Problem Marcus Brazil 2015
Lecture Notes on SAT Solvers & DPLL
 15-414: Bug Catching: Automated Program Verification Lecture Notes on SAT Solvers & DPLL Matt Fredrikson André Platzer Carnegie Mellon University Lecture 10 1 Introduction In this lecture we will switch
15-414: Bug Catching: Automated Program Verification Lecture Notes on SAT Solvers & DPLL Matt Fredrikson André Platzer Carnegie Mellon University Lecture 10 1 Introduction In this lecture we will switch
Complexity Bounds for Muller Games 1
 Complexity Bounds for Muller Games 1 Paul Hunter a, Anuj Dawar b a Oxford University Computing Laboratory, UK b University of Cambridge Computer Laboratory, UK Abstract We consider the complexity of infinite
Complexity Bounds for Muller Games 1 Paul Hunter a, Anuj Dawar b a Oxford University Computing Laboratory, UK b University of Cambridge Computer Laboratory, UK Abstract We consider the complexity of infinite
Resolution and the Weak Pigeonhole Principle
 Resolution and the Weak Pigeonhole Principle Sam Buss 1 and Toniann Pitassi 2 1 Departments of Mathematics and Computer Science University of California, San Diego, La Jolla, CA 92093-0112. 2 Department
Resolution and the Weak Pigeonhole Principle Sam Buss 1 and Toniann Pitassi 2 1 Departments of Mathematics and Computer Science University of California, San Diego, La Jolla, CA 92093-0112. 2 Department
Lower bounds for width-restricted clause learning on small width formulas
 Electronic Colloquium on Computational Complexity, Report No. 85 (2010) Lower bounds for width-restricted clause learning on small width formulas Eli Ben-Sasson 1 and Jan Johannsen 2 1 Computer Science
Electronic Colloquium on Computational Complexity, Report No. 85 (2010) Lower bounds for width-restricted clause learning on small width formulas Eli Ben-Sasson 1 and Jan Johannsen 2 1 Computer Science
Warm-Up Problem. Is the following true or false? 1/35
 Warm-Up Problem Is the following true or false? 1/35 Propositional Logic: Resolution Carmen Bruni Lecture 6 Based on work by J Buss, A Gao, L Kari, A Lubiw, B Bonakdarpour, D Maftuleac, C Roberts, R Trefler,
Warm-Up Problem Is the following true or false? 1/35 Propositional Logic: Resolution Carmen Bruni Lecture 6 Based on work by J Buss, A Gao, L Kari, A Lubiw, B Bonakdarpour, D Maftuleac, C Roberts, R Trefler,
SAT Solvers: Theory and Practice
 Summer School on Verification Technology, Systems & Applications, September 17, 2008 p. 1/98 SAT Solvers: Theory and Practice Clark Barrett barrett@cs.nyu.edu New York University Summer School on Verification
Summer School on Verification Technology, Systems & Applications, September 17, 2008 p. 1/98 SAT Solvers: Theory and Practice Clark Barrett barrett@cs.nyu.edu New York University Summer School on Verification
A New 3-CNF Transformation by Parallel-Serial Graphs 1
 A New 3-CNF Transformation by Parallel-Serial Graphs 1 Uwe Bubeck, Hans Kleine Büning University of Paderborn, Computer Science Institute, 33098 Paderborn, Germany Abstract For propositional formulas we
A New 3-CNF Transformation by Parallel-Serial Graphs 1 Uwe Bubeck, Hans Kleine Büning University of Paderborn, Computer Science Institute, 33098 Paderborn, Germany Abstract For propositional formulas we
Complexity Theory VU , SS The Polynomial Hierarchy. Reinhard Pichler
 Complexity Theory Complexity Theory VU 181.142, SS 2018 6. The Polynomial Hierarchy Reinhard Pichler Institut für Informationssysteme Arbeitsbereich DBAI Technische Universität Wien 15 May, 2018 Reinhard
Complexity Theory Complexity Theory VU 181.142, SS 2018 6. The Polynomial Hierarchy Reinhard Pichler Institut für Informationssysteme Arbeitsbereich DBAI Technische Universität Wien 15 May, 2018 Reinhard
Outline. Complexity Theory EXACT TSP. The Class DP. Definition. Problem EXACT TSP. Complexity of EXACT TSP. Proposition VU 181.
 Complexity Theory Complexity Theory Outline Complexity Theory VU 181.142, SS 2018 6. The Polynomial Hierarchy Reinhard Pichler Institut für Informationssysteme Arbeitsbereich DBAI Technische Universität
Complexity Theory Complexity Theory Outline Complexity Theory VU 181.142, SS 2018 6. The Polynomial Hierarchy Reinhard Pichler Institut für Informationssysteme Arbeitsbereich DBAI Technische Universität
Detecting Backdoor Sets with Respect to Horn and Binary Clauses
 Detecting Backdoor Sets with Respect to Horn and Binary Clauses Naomi Nishimura 1,, Prabhakar Ragde 1,, and Stefan Szeider 2, 1 School of Computer Science, University of Waterloo, Waterloo, Ontario, N2L
Detecting Backdoor Sets with Respect to Horn and Binary Clauses Naomi Nishimura 1,, Prabhakar Ragde 1,, and Stefan Szeider 2, 1 School of Computer Science, University of Waterloo, Waterloo, Ontario, N2L
On the correlation of parity and small-depth circuits
 Electronic Colloquium on Computational Complexity, Report No. 137 (2012) On the correlation of parity and small-depth circuits Johan Håstad KTH - Royal Institute of Technology November 1, 2012 Abstract
Electronic Colloquium on Computational Complexity, Report No. 137 (2012) On the correlation of parity and small-depth circuits Johan Håstad KTH - Royal Institute of Technology November 1, 2012 Abstract
Limiting Negations in Non-Deterministic Circuits
 Limiting Negations in Non-Deterministic Circuits Hiroki Morizumi Graduate School of Information Sciences, Tohoku University, Sendai 980-8579, Japan morizumi@ecei.tohoku.ac.jp Abstract The minimum number
Limiting Negations in Non-Deterministic Circuits Hiroki Morizumi Graduate School of Information Sciences, Tohoku University, Sendai 980-8579, Japan morizumi@ecei.tohoku.ac.jp Abstract The minimum number
U.C. Berkeley CS278: Computational Complexity Professor Luca Trevisan August 30, Notes for Lecture 1
 U.C. Berkeley CS278: Computational Complexity Handout N1 Professor Luca Trevisan August 30, 2004 Notes for Lecture 1 This course assumes CS170, or equivalent, as a prerequisite. We will assume that the
U.C. Berkeley CS278: Computational Complexity Handout N1 Professor Luca Trevisan August 30, 2004 Notes for Lecture 1 This course assumes CS170, or equivalent, as a prerequisite. We will assume that the
Organization. Informal introduction and Overview Informal introductions to P,NP,co-NP and themes from and relationships with Proof complexity
 15-16/08/2009 Nicola Galesi 1 Organization Informal introduction and Overview Informal introductions to P,NP,co-NP and themes from and relationships with Proof complexity First Steps in Proof Complexity
15-16/08/2009 Nicola Galesi 1 Organization Informal introduction and Overview Informal introductions to P,NP,co-NP and themes from and relationships with Proof complexity First Steps in Proof Complexity
The Strength of Multilinear Proofs
 The Strength of Multilinear Proofs Ran Raz Iddo Tzameret December 19, 2006 Abstract We introduce an algebraic proof system that manipulates multilinear arithmetic formulas. We show that this proof system
The Strength of Multilinear Proofs Ran Raz Iddo Tzameret December 19, 2006 Abstract We introduce an algebraic proof system that manipulates multilinear arithmetic formulas. We show that this proof system
Bounded-width QBF is PSPACE-complete
 Bounded-width QBF is PSPACE-complete Albert Atserias Universitat Politècnica de Catalunya Barcelona, Spain atserias@lsi.upc.edu Sergi Oliva Universitat Politècnica de Catalunya Barcelona, Spain oliva@lsi.upc.edu
Bounded-width QBF is PSPACE-complete Albert Atserias Universitat Politècnica de Catalunya Barcelona, Spain atserias@lsi.upc.edu Sergi Oliva Universitat Politècnica de Catalunya Barcelona, Spain oliva@lsi.upc.edu
Pebbling Meets Coloring : Reversible Pebble Game On Trees
 Electronic Colloquium on Computational Complexity, Report No. 67 (206) Pebbling Meets Coloring : Reversible Pebble Game On Trees Balagopal Komarath Jayalal Sarma Saurabh Sawlani Department of Computer
Electronic Colloquium on Computational Complexity, Report No. 67 (206) Pebbling Meets Coloring : Reversible Pebble Game On Trees Balagopal Komarath Jayalal Sarma Saurabh Sawlani Department of Computer
Realization Plans for Extensive Form Games without Perfect Recall
 Realization Plans for Extensive Form Games without Perfect Recall Richard E. Stearns Department of Computer Science University at Albany - SUNY Albany, NY 12222 April 13, 2015 Abstract Given a game in
Realization Plans for Extensive Form Games without Perfect Recall Richard E. Stearns Department of Computer Science University at Albany - SUNY Albany, NY 12222 April 13, 2015 Abstract Given a game in
1 Circuit Complexity. CS 6743 Lecture 15 1 Fall Definitions
 CS 6743 Lecture 15 1 Fall 2007 1 Circuit Complexity 1.1 Definitions A Boolean circuit C on n inputs x 1,..., x n is a directed acyclic graph (DAG) with n nodes of in-degree 0 (the inputs x 1,..., x n ),
CS 6743 Lecture 15 1 Fall 2007 1 Circuit Complexity 1.1 Definitions A Boolean circuit C on n inputs x 1,..., x n is a directed acyclic graph (DAG) with n nodes of in-degree 0 (the inputs x 1,..., x n ),
6.841/18.405J: Advanced Complexity Wednesday, February 12, Lecture Lecture 3
 6.841/18.405J: Advanced Complexity Wednesday, February 12, 2003 Lecture Lecture 3 Instructor: Madhu Sudan Scribe: Bobby Kleinberg 1 The language MinDNF At the end of the last lecture, we introduced the
6.841/18.405J: Advanced Complexity Wednesday, February 12, 2003 Lecture Lecture 3 Instructor: Madhu Sudan Scribe: Bobby Kleinberg 1 The language MinDNF At the end of the last lecture, we introduced the
On Complexity gaps for Resolution-based proof systems
 On omplexity gaps for Resolution-based proof systems Stefan Dantchev and Søren Riis Dept of Mathematics and omputer Science University of eicester dantchevmcsleacuk Dept of omputer Science Queen Mary University
On omplexity gaps for Resolution-based proof systems Stefan Dantchev and Søren Riis Dept of Mathematics and omputer Science University of eicester dantchevmcsleacuk Dept of omputer Science Queen Mary University
ALGEBRAIC PROOFS OVER NONCOMMUTATIVE FORMULAS
 Electronic Colloquium on Computational Complexity, Report No. 97 (2010) ALGEBRAIC PROOFS OVER NONCOMMUTATIVE FORMULAS IDDO TZAMERET Abstract. We study possible formulations of algebraic propositional proof
Electronic Colloquium on Computational Complexity, Report No. 97 (2010) ALGEBRAIC PROOFS OVER NONCOMMUTATIVE FORMULAS IDDO TZAMERET Abstract. We study possible formulations of algebraic propositional proof
On the Relative Efficiency of DPLL and OBDDs with Axiom and Join
 On the Relative Efficiency of DPLL and OBDDs with Axiom and Join Matti Järvisalo University of Helsinki, Finland September 16, 2011 @ CP M. Järvisalo (U. Helsinki) DPLL and OBDDs September 16, 2011 @ CP
On the Relative Efficiency of DPLL and OBDDs with Axiom and Join Matti Järvisalo University of Helsinki, Finland September 16, 2011 @ CP M. Järvisalo (U. Helsinki) DPLL and OBDDs September 16, 2011 @ CP
An Algebraic View of the Relation between Largest Common Subtrees and Smallest Common Supertrees
 An Algebraic View of the Relation between Largest Common Subtrees and Smallest Common Supertrees Francesc Rosselló 1, Gabriel Valiente 2 1 Department of Mathematics and Computer Science, Research Institute
An Algebraic View of the Relation between Largest Common Subtrees and Smallest Common Supertrees Francesc Rosselló 1, Gabriel Valiente 2 1 Department of Mathematics and Computer Science, Research Institute
Clique is hard on average for regular resolution
 Clique is hard on average for regular resolution Ilario Bonacina, UPC Barcelona Tech July 27, 2018 Oxford Complexity Day Talk based on a joint work with: A. Atserias S. de Rezende J. Nordstro m M. Lauria
Clique is hard on average for regular resolution Ilario Bonacina, UPC Barcelona Tech July 27, 2018 Oxford Complexity Day Talk based on a joint work with: A. Atserias S. de Rezende J. Nordstro m M. Lauria
1 PSPACE-Completeness
 CS 6743 Lecture 14 1 Fall 2007 1 PSPACE-Completeness Recall the NP-complete problem SAT: Is a given Boolean formula φ(x 1,..., x n ) satisfiable? The same question can be stated equivalently as: Is the
CS 6743 Lecture 14 1 Fall 2007 1 PSPACE-Completeness Recall the NP-complete problem SAT: Is a given Boolean formula φ(x 1,..., x n ) satisfiable? The same question can be stated equivalently as: Is the
Tableau-based decision procedures for the logics of subinterval structures over dense orderings
 Tableau-based decision procedures for the logics of subinterval structures over dense orderings Davide Bresolin 1, Valentin Goranko 2, Angelo Montanari 3, and Pietro Sala 3 1 Department of Computer Science,
Tableau-based decision procedures for the logics of subinterval structures over dense orderings Davide Bresolin 1, Valentin Goranko 2, Angelo Montanari 3, and Pietro Sala 3 1 Department of Computer Science,
Upper and Lower Bounds for Tree-like. Cutting Planes Proofs. Abstract. In this paper we study the complexity of Cutting Planes (CP) refutations, and
 Upper and Lower Bounds for Tree-like Cutting Planes Proofs Russell Impagliazzo Toniann Pitassi y Alasdair Urquhart z UCSD UCSD and U. of Pittsburgh University of Toronto Abstract In this paper we study
Upper and Lower Bounds for Tree-like Cutting Planes Proofs Russell Impagliazzo Toniann Pitassi y Alasdair Urquhart z UCSD UCSD and U. of Pittsburgh University of Toronto Abstract In this paper we study
INAPPROX APPROX PTAS. FPTAS Knapsack P
 CMPSCI 61: Recall From Last Time Lecture 22 Clique TSP INAPPROX exists P approx alg for no ε < 1 VertexCover MAX SAT APPROX TSP some but not all ε< 1 PTAS all ε < 1 ETSP FPTAS Knapsack P poly in n, 1/ε
CMPSCI 61: Recall From Last Time Lecture 22 Clique TSP INAPPROX exists P approx alg for no ε < 1 VertexCover MAX SAT APPROX TSP some but not all ε< 1 PTAS all ε < 1 ETSP FPTAS Knapsack P poly in n, 1/ε
NP-completeness. Chapter 34. Sergey Bereg
 NP-completeness Chapter 34 Sergey Bereg Oct 2017 Examples Some problems admit polynomial time algorithms, i.e. O(n k ) running time where n is the input size. We will study a class of NP-complete problems
NP-completeness Chapter 34 Sergey Bereg Oct 2017 Examples Some problems admit polynomial time algorithms, i.e. O(n k ) running time where n is the input size. We will study a class of NP-complete problems
THE COMPLEXITY OF PROVING THAT A GRAPH IS RAMSEY
 COMBINATORICA Bolyai Society Springer-Verlag Combinatorica 37 (2) (2017) 253 268 DOI: 10.1007/s00493-015-3193-9 THE COMPLEXITY OF PROVING THAT A GRAPH IS RAMSEY MASSIMO LAURIA, PAVEL PUDLÁK, VOJTĚCH RÖDL,
COMBINATORICA Bolyai Society Springer-Verlag Combinatorica 37 (2) (2017) 253 268 DOI: 10.1007/s00493-015-3193-9 THE COMPLEXITY OF PROVING THAT A GRAPH IS RAMSEY MASSIMO LAURIA, PAVEL PUDLÁK, VOJTĚCH RÖDL,
The exam is closed book, closed calculator, and closed notes except your one-page crib sheet.
 CS 188 Fall 2015 Introduction to Artificial Intelligence Final You have approximately 2 hours and 50 minutes. The exam is closed book, closed calculator, and closed notes except your one-page crib sheet.
CS 188 Fall 2015 Introduction to Artificial Intelligence Final You have approximately 2 hours and 50 minutes. The exam is closed book, closed calculator, and closed notes except your one-page crib sheet.
MTAT Complexity Theory October 20th-21st, Lecture 7
 MTAT.07.004 Complexity Theory October 20th-21st, 2011 Lecturer: Peeter Laud Lecture 7 Scribe(s): Riivo Talviste Polynomial hierarchy 1 Turing reducibility From the algorithmics course, we know the notion
MTAT.07.004 Complexity Theory October 20th-21st, 2011 Lecturer: Peeter Laud Lecture 7 Scribe(s): Riivo Talviste Polynomial hierarchy 1 Turing reducibility From the algorithmics course, we know the notion
CS 5114: Theory of Algorithms. Tractable Problems. Tractable Problems (cont) Decision Problems. Clifford A. Shaffer. Spring 2014
 Department of Computer Science Virginia Tech Blacksburg, Virginia Copyright c 2014 by Clifford A. Shaffer : Theory of Algorithms Title page : Theory of Algorithms Clifford A. Shaffer Spring 2014 Clifford
Department of Computer Science Virginia Tech Blacksburg, Virginia Copyright c 2014 by Clifford A. Shaffer : Theory of Algorithms Title page : Theory of Algorithms Clifford A. Shaffer Spring 2014 Clifford
Mathematical Logic Part Three
 Mathematical Logic Part hree riday our Square! oday at 4:15PM, Outside Gates Announcements Problem Set 3 due right now. Problem Set 4 goes out today. Checkpoint due Monday, October 22. Remainder due riday,
Mathematical Logic Part hree riday our Square! oday at 4:15PM, Outside Gates Announcements Problem Set 3 due right now. Problem Set 4 goes out today. Checkpoint due Monday, October 22. Remainder due riday,
Understanding Space in Proof Complexity: Separations and Trade-offs via Substitutions (Extended Abstract)
 Innovations in Computer Science 2011 Understanding Space in Proof Complexity: Separations and Trade-offs via Substitutions (Extended Abstract) Eli Ben-Sasson 1 Jakob Nordström 2 1 Computer Science Department,
Innovations in Computer Science 2011 Understanding Space in Proof Complexity: Separations and Trade-offs via Substitutions (Extended Abstract) Eli Ben-Sasson 1 Jakob Nordström 2 1 Computer Science Department,
Notes on Complexity Theory Last updated: October, Lecture 6
 Notes on Complexity Theory Last updated: October, 2015 Lecture 6 Notes by Jonathan Katz, lightly edited by Dov Gordon 1 PSPACE and PSPACE-Completeness As in our previous study of N P, it is useful to identify
Notes on Complexity Theory Last updated: October, 2015 Lecture 6 Notes by Jonathan Katz, lightly edited by Dov Gordon 1 PSPACE and PSPACE-Completeness As in our previous study of N P, it is useful to identify
Branching. Teppo Niinimäki. Helsinki October 14, 2011 Seminar: Exact Exponential Algorithms UNIVERSITY OF HELSINKI Department of Computer Science
 Branching Teppo Niinimäki Helsinki October 14, 2011 Seminar: Exact Exponential Algorithms UNIVERSITY OF HELSINKI Department of Computer Science 1 For a large number of important computational problems
Branching Teppo Niinimäki Helsinki October 14, 2011 Seminar: Exact Exponential Algorithms UNIVERSITY OF HELSINKI Department of Computer Science 1 For a large number of important computational problems
On improving matchings in trees, via bounded-length augmentations 1
 On improving matchings in trees, via bounded-length augmentations 1 Julien Bensmail a, Valentin Garnero a, Nicolas Nisse a a Université Côte d Azur, CNRS, Inria, I3S, France Abstract Due to a classical
On improving matchings in trees, via bounded-length augmentations 1 Julien Bensmail a, Valentin Garnero a, Nicolas Nisse a a Université Côte d Azur, CNRS, Inria, I3S, France Abstract Due to a classical
arxiv: v1 [cs.cc] 10 Aug 2007
![arxiv: v1 [cs.cc] 10 Aug 2007 arxiv: v1 [cs.cc] 10 Aug 2007](/thumbs/95/123522020.jpg) RESOLUTION OVER LINEAR EQUATIONS AND MULTILINEAR PROOFS RAN RAZ AND IDDO TZAMERET arxiv:0708.1529v1 [cs.cc] 10 Aug 2007 Abstract. We develop and study the complexity of propositional proof systems of varying
RESOLUTION OVER LINEAR EQUATIONS AND MULTILINEAR PROOFS RAN RAZ AND IDDO TZAMERET arxiv:0708.1529v1 [cs.cc] 10 Aug 2007 Abstract. We develop and study the complexity of propositional proof systems of varying
Price: $25 (incl. T-Shirt, morning tea and lunch) Visit:
 Three days of interesting talks & workshops from industry experts across Australia Explore new computing topics Network with students & employers in Brisbane Price: $25 (incl. T-Shirt, morning tea and
Three days of interesting talks & workshops from industry experts across Australia Explore new computing topics Network with students & employers in Brisbane Price: $25 (incl. T-Shirt, morning tea and
arxiv: v1 [cs.cc] 5 Dec 2018
![arxiv: v1 [cs.cc] 5 Dec 2018 arxiv: v1 [cs.cc] 5 Dec 2018](/thumbs/91/106499182.jpg) Consistency for 0 1 Programming Danial Davarnia 1 and J. N. Hooker 2 1 Iowa state University davarnia@iastate.edu 2 Carnegie Mellon University jh38@andrew.cmu.edu arxiv:1812.02215v1 [cs.cc] 5 Dec 2018
Consistency for 0 1 Programming Danial Davarnia 1 and J. N. Hooker 2 1 Iowa state University davarnia@iastate.edu 2 Carnegie Mellon University jh38@andrew.cmu.edu arxiv:1812.02215v1 [cs.cc] 5 Dec 2018
Chapter 4: Computation tree logic
 INFOF412 Formal verification of computer systems Chapter 4: Computation tree logic Mickael Randour Formal Methods and Verification group Computer Science Department, ULB March 2017 1 CTL: a specification
INFOF412 Formal verification of computer systems Chapter 4: Computation tree logic Mickael Randour Formal Methods and Verification group Computer Science Department, ULB March 2017 1 CTL: a specification
Critical Reading of Optimization Methods for Logical Inference [1]
![Critical Reading of Optimization Methods for Logical Inference [1] Critical Reading of Optimization Methods for Logical Inference [1]](/thumbs/95/124347829.jpg) Critical Reading of Optimization Methods for Logical Inference [1] Undergraduate Research Internship Department of Management Sciences Fall 2007 Supervisor: Dr. Miguel Anjos UNIVERSITY OF WATERLOO Rajesh
Critical Reading of Optimization Methods for Logical Inference [1] Undergraduate Research Internship Department of Management Sciences Fall 2007 Supervisor: Dr. Miguel Anjos UNIVERSITY OF WATERLOO Rajesh
Parameterized Algorithms and Kernels for 3-Hitting Set with Parity Constraints
 Parameterized Algorithms and Kernels for 3-Hitting Set with Parity Constraints Vikram Kamat 1 and Neeldhara Misra 2 1 University of Warsaw vkamat@mimuw.edu.pl 2 Indian Institute of Science, Bangalore neeldhara@csa.iisc.ernet.in
Parameterized Algorithms and Kernels for 3-Hitting Set with Parity Constraints Vikram Kamat 1 and Neeldhara Misra 2 1 University of Warsaw vkamat@mimuw.edu.pl 2 Indian Institute of Science, Bangalore neeldhara@csa.iisc.ernet.in
CS6840: Advanced Complexity Theory Mar 29, Lecturer: Jayalal Sarma M.N. Scribe: Dinesh K.
 CS684: Advanced Complexity Theory Mar 29, 22 Lecture 46 : Size lower bounds for AC circuits computing Parity Lecturer: Jayalal Sarma M.N. Scribe: Dinesh K. Theme: Circuit Complexity Lecture Plan: Proof
CS684: Advanced Complexity Theory Mar 29, 22 Lecture 46 : Size lower bounds for AC circuits computing Parity Lecturer: Jayalal Sarma M.N. Scribe: Dinesh K. Theme: Circuit Complexity Lecture Plan: Proof
Cardinality Networks: a Theoretical and Empirical Study
 Constraints manuscript No. (will be inserted by the editor) Cardinality Networks: a Theoretical and Empirical Study Roberto Asín, Robert Nieuwenhuis, Albert Oliveras, Enric Rodríguez-Carbonell Received:
Constraints manuscript No. (will be inserted by the editor) Cardinality Networks: a Theoretical and Empirical Study Roberto Asín, Robert Nieuwenhuis, Albert Oliveras, Enric Rodríguez-Carbonell Received:
Propositional Logic. Methods & Tools for Software Engineering (MTSE) Fall Prof. Arie Gurfinkel
 Propositional Logic Methods & Tools for Software Engineering (MTSE) Fall 2017 Prof. Arie Gurfinkel References Chpater 1 of Logic for Computer Scientists http://www.springerlink.com/content/978-0-8176-4762-9/
Propositional Logic Methods & Tools for Software Engineering (MTSE) Fall 2017 Prof. Arie Gurfinkel References Chpater 1 of Logic for Computer Scientists http://www.springerlink.com/content/978-0-8176-4762-9/
Guarded resolution for Answer Set Programming
 Under consideration for publication in Theory and Practice of Logic Programming 1 Guarded resolution for Answer Set Programming V.W. Marek Department of Computer Science, University of Kentucky, Lexington,
Under consideration for publication in Theory and Practice of Logic Programming 1 Guarded resolution for Answer Set Programming V.W. Marek Department of Computer Science, University of Kentucky, Lexington,
A Parameterized Complexity of DPLL Search Procedures
 A Parameterized Complexity of DPLL Search Procedures OLAF BEYERSDORFF, University of Leeds NICOLA GALESI, Sapienza University Rome MASSIMO LAURIA, KTH Royal Institute of Technology We study the performance
A Parameterized Complexity of DPLL Search Procedures OLAF BEYERSDORFF, University of Leeds NICOLA GALESI, Sapienza University Rome MASSIMO LAURIA, KTH Royal Institute of Technology We study the performance
Exact and Approximate Equilibria for Optimal Group Network Formation
 Exact and Approximate Equilibria for Optimal Group Network Formation Elliot Anshelevich and Bugra Caskurlu Computer Science Department, RPI, 110 8th Street, Troy, NY 12180 {eanshel,caskub}@cs.rpi.edu Abstract.
Exact and Approximate Equilibria for Optimal Group Network Formation Elliot Anshelevich and Bugra Caskurlu Computer Science Department, RPI, 110 8th Street, Troy, NY 12180 {eanshel,caskub}@cs.rpi.edu Abstract.
ZZ On the Interplay Between Proof Complexity and SAT Solving
 ZZ On the Interplay Between Proof Complexity and SAT Solving JAKOB NORDSTRÖM, KTH Royal Institute of Technology This paper is intended as an informal and accessible survey of proof complexity for non-experts,
ZZ On the Interplay Between Proof Complexity and SAT Solving JAKOB NORDSTRÖM, KTH Royal Institute of Technology This paper is intended as an informal and accessible survey of proof complexity for non-experts,
Exponential Separations in a Hierarchy of Clause Learning Proof Systems
 Electronic Colloquium on Computational Complexity, Report No. 72 (2013) Exponential Separations in a Hierarchy of Clause Learning Proof Systems Jan Johannsen Institut fur Informatik Ludwig-Maximilians-Universitat
Electronic Colloquium on Computational Complexity, Report No. 72 (2013) Exponential Separations in a Hierarchy of Clause Learning Proof Systems Jan Johannsen Institut fur Informatik Ludwig-Maximilians-Universitat
Alpha-Beta Pruning: Algorithm and Analysis
 Alpha-Beta Pruning: Algorithm and Analysis Tsan-sheng Hsu tshsu@iis.sinica.edu.tw http://www.iis.sinica.edu.tw/~tshsu 1 Introduction Alpha-beta pruning is the standard searching procedure used for solving
Alpha-Beta Pruning: Algorithm and Analysis Tsan-sheng Hsu tshsu@iis.sinica.edu.tw http://www.iis.sinica.edu.tw/~tshsu 1 Introduction Alpha-beta pruning is the standard searching procedure used for solving
The Complexity of Resolution Refinements
 The Complexity of Resolution Refinements Joshua Buresh-Oppenheim Computer Science Department University of Toronto Toronto, ON bureshop@cs.toronto.edu Toniann Pitassi Computer Science Department University
The Complexity of Resolution Refinements Joshua Buresh-Oppenheim Computer Science Department University of Toronto Toronto, ON bureshop@cs.toronto.edu Toniann Pitassi Computer Science Department University
Lecture 2: Connecting the Three Models
 IAS/PCMI Summer Session 2000 Clay Mathematics Undergraduate Program Advanced Course on Computational Complexity Lecture 2: Connecting the Three Models David Mix Barrington and Alexis Maciel July 18, 2000
IAS/PCMI Summer Session 2000 Clay Mathematics Undergraduate Program Advanced Course on Computational Complexity Lecture 2: Connecting the Three Models David Mix Barrington and Alexis Maciel July 18, 2000
PROPOSITIONAL LOGIC. VL Logik: WS 2018/19
 PROPOSITIONAL LOGIC VL Logik: WS 2018/19 (Version 2018.2) Martina Seidl (martina.seidl@jku.at), Armin Biere (biere@jku.at) Institut für Formale Modelle und Verifikation BOX Game: Rules 1. The game board
PROPOSITIONAL LOGIC VL Logik: WS 2018/19 (Version 2018.2) Martina Seidl (martina.seidl@jku.at), Armin Biere (biere@jku.at) Institut für Formale Modelle und Verifikation BOX Game: Rules 1. The game board
NP-Complete Reductions 2
 x 1 x 1 x 2 x 2 x 3 x 3 x 4 x 4 12 22 32 CS 447 11 13 21 23 31 33 Algorithms NP-Complete Reductions 2 Prof. Gregory Provan Department of Computer Science University College Cork 1 Lecture Outline NP-Complete
x 1 x 1 x 2 x 2 x 3 x 3 x 4 x 4 12 22 32 CS 447 11 13 21 23 31 33 Algorithms NP-Complete Reductions 2 Prof. Gregory Provan Department of Computer Science University College Cork 1 Lecture Outline NP-Complete
P P P NP-Hard: L is NP-hard if for all L NP, L L. Thus, if we could solve L in polynomial. Cook's Theorem and Reductions
 Summary of the previous lecture Recall that we mentioned the following topics: P: is the set of decision problems (or languages) that are solvable in polynomial time. NP: is the set of decision problems
Summary of the previous lecture Recall that we mentioned the following topics: P: is the set of decision problems (or languages) that are solvable in polynomial time. NP: is the set of decision problems
The Size and Depth of Layered Boolean Circuits
 The Size and Depth of Layered Boolean Circuits Anna Gál a,1, Jing-Tang Jang a,2 a Dept. of Computer Science, University of Texas at Austin, Austin, TX 78712-1188, USA Abstract We consider the relationship
The Size and Depth of Layered Boolean Circuits Anna Gál a,1, Jing-Tang Jang a,2 a Dept. of Computer Science, University of Texas at Austin, Austin, TX 78712-1188, USA Abstract We consider the relationship
Towards an Understanding of Polynomial Calculus: New Separations and Lower Bounds
 Towards an Understanding of Polynomial Calculus: New Separations and Lower Bounds Yuval Filmus University of Toronto Mladen Mikša KTH Royal Institute of Technology Massimo Lauria KTH Royal Institute of
Towards an Understanding of Polynomial Calculus: New Separations and Lower Bounds Yuval Filmus University of Toronto Mladen Mikša KTH Royal Institute of Technology Massimo Lauria KTH Royal Institute of
Boolean circuits. Lecture Definitions
 Lecture 20 Boolean circuits In this lecture we will discuss the Boolean circuit model of computation and its connection to the Turing machine model. Although the Boolean circuit model is fundamentally
Lecture 20 Boolean circuits In this lecture we will discuss the Boolean circuit model of computation and its connection to the Turing machine model. Although the Boolean circuit model is fundamentally
Comp487/587 - Boolean Formulas
 Comp487/587 - Boolean Formulas 1 Logic and SAT 1.1 What is a Boolean Formula Logic is a way through which we can analyze and reason about simple or complicated events. In particular, we are interested
Comp487/587 - Boolean Formulas 1 Logic and SAT 1.1 What is a Boolean Formula Logic is a way through which we can analyze and reason about simple or complicated events. In particular, we are interested
Lecture 15 - NP Completeness 1
 CME 305: Discrete Mathematics and Algorithms Instructor: Professor Aaron Sidford (sidford@stanford.edu) February 29, 2018 Lecture 15 - NP Completeness 1 In the last lecture we discussed how to provide
CME 305: Discrete Mathematics and Algorithms Instructor: Professor Aaron Sidford (sidford@stanford.edu) February 29, 2018 Lecture 15 - NP Completeness 1 In the last lecture we discussed how to provide
Limitations of Algorithm Power
 Limitations of Algorithm Power Objectives We now move into the third and final major theme for this course. 1. Tools for analyzing algorithms. 2. Design strategies for designing algorithms. 3. Identifying
Limitations of Algorithm Power Objectives We now move into the third and final major theme for this course. 1. Tools for analyzing algorithms. 2. Design strategies for designing algorithms. 3. Identifying
CSC 5170: Theory of Computational Complexity Lecture 9 The Chinese University of Hong Kong 15 March 2010
 CSC 5170: Theory of Computational Complexity Lecture 9 The Chinese University of Hong Kong 15 March 2010 We now embark on a study of computational classes that are more general than NP. As these classes
CSC 5170: Theory of Computational Complexity Lecture 9 The Chinese University of Hong Kong 15 March 2010 We now embark on a study of computational classes that are more general than NP. As these classes
NP-Completeness of Refutability by Literal-Once Resolution
 NP-Completeness of Refutability by Literal-Once Resolution Stefan Szeider Institute of Discrete Mathematics Austrian Academy of Sciences Sonnenfelsgasse 19, 1010 Vienna, Austria stefan.szeider@oeaw.ac.at
NP-Completeness of Refutability by Literal-Once Resolution Stefan Szeider Institute of Discrete Mathematics Austrian Academy of Sciences Sonnenfelsgasse 19, 1010 Vienna, Austria stefan.szeider@oeaw.ac.at
Lecture 9 : PPAD and the Complexity of Equilibrium Computation. 1 Complexity Class PPAD. 1.1 What does PPAD mean?
 CS 599: Algorithmic Game Theory October 20, 2010 Lecture 9 : PPAD and the Complexity of Equilibrium Computation Prof. Xi Chen Scribes: Cheng Lu and Sasank Vijayan 1 Complexity Class PPAD 1.1 What does
CS 599: Algorithmic Game Theory October 20, 2010 Lecture 9 : PPAD and the Complexity of Equilibrium Computation Prof. Xi Chen Scribes: Cheng Lu and Sasank Vijayan 1 Complexity Class PPAD 1.1 What does
The Complexity of Constructing Evolutionary Trees Using Experiments
 The Complexity of Constructing Evolutionary Trees Using Experiments Gerth Stlting Brodal 1,, Rolf Fagerberg 1,, Christian N. S. Pedersen 1,, and Anna Östlin2, 1 BRICS, Department of Computer Science, University
The Complexity of Constructing Evolutionary Trees Using Experiments Gerth Stlting Brodal 1,, Rolf Fagerberg 1,, Christian N. S. Pedersen 1,, and Anna Östlin2, 1 BRICS, Department of Computer Science, University
