Equivalence. Two networks can look different but be the same. They can also appear similar, but be different. For example:
|
|
|
- Brook Johnston
- 5 years ago
- Views:
Transcription
1 Equivalence Two networks can look different but be the same. They can also appear similar, but be different. For example: All of the networks below are banyans. The networks have other similarities and differences EE 7725 Lecture Transparency. Formatted 11:57, 8 June 2001 from lsli
2 Equivalence Definitions Types of Equivalence Descriptively Equivalent (DE): Drawn the same. (Link and cell numbers match.) Without a doubt, identical. Terminal Equivalent (TE): Same cell and link connections when input and output numbers preserved but cells and links possibly renamed. Identical, even though they may be drawn differently. Topologically Equivalent (OE): Same cell and link connections when input and output numbers ignored. Can satisfy same connection assignments if inputs renamed. Functionally Equivalent (FE): Can satisfy same connections assignments. Two networks do the same thing but have different topologies. 6-2 EE 7725 Lecture Transparency. Formatted 11:57, 8 June 2001 from lsli
3 Descriptive Equivalence Two networks are descriptively equivalent (DE) when there is a one-to-one correspondence between cells, links, and their labels, (including positions), when the networks are rendered in their usual way. The relational operator DE = indicates terminal equivalence, A DE = B means A is descriptively equivalence to B. Informally, this type of equivalence is a no-brainer. The following two networks are not descriptively equivalent: 6-3 EE 7725 Lecture Transparency. Formatted 11:57, 8 June 2001 from lsli
4 Terminal Equivalence Two networks are terminal equivalent (TE) if their LGM representations are identical for some renaming of vertices in V (I O). The relational operator TE = indicates terminal equivalence; A TE = B means A is terminal equivalent to B. The following two networks are terminal equivalent: 6-4 EE 7725 Lecture Transparency. Formatted 11:57, 8 June 2001 from lsli
5 Terminal Equivalence Examples These two networks are TE Each of the two below is not TE to any of the others: 6-5 EE 7725 Lecture Transparency. Formatted 11:57, 8 June 2001 from lsli
6 Determining if Two Networks are TE Let A =(I A,O A,V A,E A ) and B =(I B,O B,V B,E B ) be network LGMs. Easy cases: Two networks are not TE if: or Either I A I B, O A O B, V A V B,or E A E B. (The number of inputs, outputs, cells, and links must be identical for TE.) Either I A I B or O A O B. (Input and output labels must be identical for TE.) Other cases will need a mapping function EE 7725 Lecture Transparency. Formatted 11:57, 8 June 2001 from lsli
7 Mapping Function Tool needed to show equivalence: mapping function. Maps one set of labels onto another. Notation: f X Y, symbols in X mapped to Y. Example: X = {One, Two, Three} Y = {2, 1, 3} { 1, if x = One; f(x) = 2, if x =Two; 3, if x = Three. If f(x) =y then y is called x s image under f; In the function above, 1 is the image of One. 6-7 EE 7725 Lecture Transparency. Formatted 11:57, 8 June 2001 from lsli
8 Mapping Function Bijective Functions Mapping function must be bijective, id est, each element of X must be mapped to exactly one element of Y and vice versa. The function above is bijective. The following mapping function is not bijective: X = {mouth, hand, foot} Y = {paw, snout, tail} { paw, if x = hand; f(x) = paw, if x = foot; snout, if x = mouth. Numerical example: Y = X = mk, f(x) =σ m,k (x). 6-8 EE 7725 Lecture Transparency. Formatted 11:57, 8 June 2001 from lsli
9 Notation for Mapping Function Let X = {One, Two, Three} and Y = {2, 1, 3} f(x) = { 1, if x = One; 2, if x =Two; 3, if x = Three. Usual notation: f(one) = EE 7725 Lecture Transparency. Formatted 11:57, 8 June 2001 from lsli
10 Notation for Mapping Function Mapping can be applied to sets: f(a) ={ f(a) a A }. For example: f(x) =Y and f({one, Two, Three}) ={f(one),f(two),f(three)} = {1, 2, 3}. Mapping can be applied to tuples: f((a, B, C))=(f(A),f(B),f(C)). Tuples can be network LGMs, (I,O,V,E), edges, (a, b), or anything else EE 7725 Lecture Transparency. Formatted 11:57, 8 June 2001 from lsli
11 Equivalence Proofs To Prove That Two Networks Are TE Using Mapping Functions Let A =(I A,O A,V A,E A ) and B =(I B,O B,V B,E B ) be network LGMs. Network A TE = B iff I A = I B and O A = O B and there exists a bijection f V A V B such that f(a) =B EE 7725 Lecture Transparency. Formatted 11:57, 8 June 2001 from lsli
12 Equivalence Proof Simple Example Prove that these two networks are identical: Input and output labels are same for both networks (or they wouldn t be TE). I A = I B = {I, 0, I, 1, I, 2, I, 3} O A = O B = {O, 0, O, 1, O, 2, O, 3} Edge labels are different, of course: E A = {(I, 0, 0, 0)(I, 1, 0, 0)(I, 2, 0, 1)(I, 3, 0, 1), (0, 0, 2, 0), (0, 0, 1, 0), (0, 1, 1, 0), (0, 1, 2, 1), (1, 0, 2, 0), (1, 0, 2, 1), (2, 0, O, 0), (2, 0, O, 1), (2, 1, O, 2), (2, 1, O, 3)} E B = {(I, 0, 0, 0), (I, 1, 0, 0), (I, 2, 0, 1), (I, 3, 0, 1), (0, 0, 1, 0), (0, 0, 2, 1), (0, 1, 1, 0), (0, 1, 2, 0), (1, 0, 2, 0), (1, 0, 2, 1), (2, 0, O, 2), (2, 0, O, 3), (2, 1, O, 0), (2, 1, O, 1)} 6-12 EE 7725 Lecture Transparency. Formatted 11:57, 8 June 2001 from lsli
13 Equivalence Proof Simple Example Mapping Function for this Simple Example The easy part: Because (I, 0, 0, 0) E A, and (I, 0, 0, 0) E B : f(0, 0) =0, 0 For similar reasons f(0, 1) =0, 1 Because (2, 0, O, 0) E A, and (2, 1, O, 0) E B : f(2, 0) =2, 1 For similar reasons f(2, 1) =2, 0 As always for TE f(i, i) =I, i and f(o, i) =O, i EE 7725 Lecture Transparency. Formatted 11:57, 8 June 2001 from lsli
14 Equivalence Proof Simple Example The part that would be hard (if the network were more complicated). We need to find a mapping for the one remaining cell. Since the map must be bijective, we have only one choice: f(1, 0) =1, 0 Now that we have a mapping function, we can find f(a) 6-14 EE 7725 Lecture Transparency. Formatted 11:57, 8 June 2001 from lsli
15 Use of Mapping Function in the Simple Example Starting, f(a) =(I A,O A,f(V A ),f(e A ))? = B To show A TE = B must show that f(a) =B. Clearly, f(v A )=V B. Check f(e A ): f(e A )={(f(i, 0),f(0, 0)), (f(i, 1),f(0, 0)), (f(i, 2),f(0, 1)), (f(i, 3),f(0, 1)), (f(0, 0),f(2, 0)), (f(0, 0),f(1, 0)), (f(0, 1),f(1, 0)), (f(0, 1),f(2, 1)), (f(1, 0),f(2, 0)), (f(1, 0),f(2, 1)), (f(2, 0),f(O, 0)), (f(2, 0),f(O, 1)), (f(2, 1),f(O, 2)), (f(2, 1),f(O, 3)) } = { (I, 0, 0, 0), (I, 1, 0, 0), (I, 2, 0, 1), (I, 3, 0, 1), (0, 0, 2, 1), (0, 0, 1, 0), (0, 1, 1, 0), (0, 1, 2, 0), (1, 0, 2, 1), (1, 0, 2, 0), (2, 1, O, 0), (2, 1, O, 1), (2, 0, O, 2), (2, 0, O, 3) } = E B Therefore, the two networks are TE EE 7725 Lecture Transparency. Formatted 11:57, 8 June 2001 from lsli
16 Exhaustive Procedure for Determining if Two Networks are TE: Let A =(I A,O A,V A,E A ) and B =(I B,O B,V B,E B ) be network LGMs. 1: Return not TE if either I A I B, O A O B, V A V B,or E A E B. 2: Otherwise, let C A = V A I A O A and C B = V B I B O B, the cell labels. There are C A! bijective mapping functions f C A C B. Let the functions be numbered and let f i denote function i, for0 i< C A!. 3: Set i =0. 4: Loop: Create LGM A by applying f i to each cell label of A. 5: If A = B then return A and B are TE. 6: Set i = i +1. 7: If i< C A! then goto Loop 8: Return LGM A and B are not TE EE 7725 Lecture Transparency. Formatted 11:57, 8 June 2001 from lsli
17 Efficient Procedures for Determining if Two Networks are TE: Fact which will be exploited: Mapping of first- and last-stage cells is unique. Let A =(I A,O A,V A,E A ) and B =(I B,O B,V B,E B ) be network LGMs. Consider only networks in which each input and output is connected to exactly one cell. If A TE = B then: For all I, i I A, and (I, i, x, j) E A, and (I, i, x,j ) E B : f(x, j) =x,j (1) In words: For TE networks A and B, if input i connects to cell x, j in network A, and input i connects to cell x,j in network B, then cell x, j maps to cell x,j EE 7725 Lecture Transparency. Formatted 11:57, 8 June 2001 from lsli
18 Similarly, if A TE = B then: For all O, i O A, and (x, j, O, i) E A, and (x,j, O, i) E B : f(x, j) =x,j (2) In words: For TE networks A and B, if output i connects to cell x, j in network A, and output i connects to cell x,j in network B, then cell x, j maps to cell x,j. Therefore, when choosing the f i, select only those that satisfy equations (1,2) 6-18 EE 7725 Lecture Transparency. Formatted 11:57, 8 June 2001 from lsli
19 Proving Terminal Equivalence of Omega and Recursive Omega Introducing the recursive omega network: Structure of an n-stage m m-cell recursive omega network: Each stage has m n 1 cells. Network inputs connect to stage-0 cells with an m, m n 1 shuffle. Stage-x cell outputs connect to stage-(x+1) cell inputs with a n x 1 butterfly, for 0 x<n 1. Stage-(n 1) cell outputs connect to like-numbered network outputs EE 7725 Lecture Transparency. Formatted 11:57, 8 June 2001 from lsli
20 Butterfly Function for Recursive Omega The radix-m, n-digit, i butterfly function, β (i) m n m n is given by x (n 1:2) x (0) x (1), if i =1; β (i) (x) = x (n 1:i+1) x (0) x (i 1:1) x (i), if 1 <i<n 1; x (0) x (n 2:1) x (n 1), if i = n 1; for 0 <i<nand 0 x<m n. In words: digits 0 and i are swapped. Three examples, radix-2, 4-digit: 3 butterfly, 2 butterfly, and 1 butterfly EE 7725 Lecture Transparency. Formatted 11:57, 8 June 2001 from lsli
21 LGM of Recursive Omega (RΩ): Let k = m n 1,asusual. I RΩ = {I, i 0 i<mk} O RΩ = {O, i 0 i<mk} V RΩ = I RΩ O RΩ {x, i 0 x<n, 0 i<k} So far, just like an omega network; links set them apart: { } E RΩ = (I, i, 0, imod k) 0 i<mk {( ) } β(n x 1) (mi+ d) x, i, x +1, 0 d<m, 0 i<k, 0 x<n 1 m { (n 1, i, O, mi+ j) 0 j<m,0 i<k} Non-input/output links can also be written as: { ( x, i, ) x +1,i (n 2) i (n 3)...i (n x 1) di (n x 3)...i (0) 0 d<m, 0 i<k, 1 x<n 1 } 6-21 EE 7725 Lecture Transparency. Formatted 11:57, 8 June 2001 from lsli
22 LGM of an(n, m) Omega Network (For Review) Let k = m n 1. I Ω = {I, i 0 i<mk} O Ω = {O, i 0 i<mk} V Ω = I Ω O Ω {x, i 0 x<n, 0 i<k} E Ω ={ (I, i, 0, imod k) 0 i<mk} { (x, i, x +1,mi+ j mod k) 0 j<m,0 i<k, 0 x<n 1 } { (n 1, i, O, mi+ j) 0 j<m,0 i<k} 6-22 EE 7725 Lecture Transparency. Formatted 11:57, 8 June 2001 from lsli
23 Outline of Proof that Recursive Omega is TE to Omega Prove that the input and output labels are identical. (Easy) Find part of the mapping function for first- and last-stage cells. (Easy) (This part of the mapping function could be used to show that two networks are not TE.) Find the remainder of the mapping function. (Interesting) Proof That Input and Output Labels Identical By definition of the networks. Mapping Function for First- and Last-Stage Cells The first and last stages in the two networks are identical. Therefore, f(0, i) =0, i and f(n 1, i) =n 1, i for 0 i<m n EE 7725 Lecture Transparency. Formatted 11:57, 8 June 2001 from lsli
24 Mapping Function for Stage-1 Cells Consider a link from stage-0 cell i to stage 1 for both networks: In graph notation: ( 0,i(n 2) i (n 3)...i (0), 1,i(n 3) i (n 4)...i (0) d ) E Ω ( 0,i(n 2) i (n 3)...i (0), 1,di(n 3)...i (0) ) ERΩ In path notation 1 Ω RΩ 0,i(n 2) i (n 3)...i (0) 0,i(n 2) i (n 3)...i (0) for 0 d<m. 1,i(n 3) i (n 4)...i (0) d 1,di (n 3)...i (0) Mapping function for these stage-1 cells: f (1, i) =f ( ) 1,i (n 2) i (n 3)...i (0) = 1,i(0) i (n 2)...i (1) = 1,σ m n 2,m(i) 1 Note: The notation shows the links from stage-0 cell i. Similar notation has been used for showing the links taken by a request (e.g., (a, α)). Regardless of the stage, cell i s radix-m representation is i (n 2) i (n 3)...i (0) EE 7725 Lecture Transparency. Formatted 11:57, 8 June 2001 from lsli
25 Using the mapping function: The mapping function (from the previous transparency): f (1, i) =f ( ) 1,i (n 2) i (n 3)...i (0) = 1,i(0) i (n 2)...i (1) = 1,σ m n 2,m(i) The links in the two networks (also from the previous transparency): ( 0,i(n 2) i (n 3)...i (0), 1,i(n 3) i (n 4)...i (0) d ) E Ω for 0 d<m. ( 0,i(n 2) i (n 3)...i (0), 1,di(n 3)...i (0) ) ERΩ The mapping function used on Ω to (hopefully) obtain RΩ: ( f( 0,i(n 2) i (n 3)...i (0) ),f( 1,i(n 3) i (n 4)...i (0) d ) ) f(e Ω ) ( 0,i(n 2) i (n 3)...i (0), 1,di(n 3)...i (0) ) E RΩ Thus, we have chosen so that links between stage 0 and 1 in the two networks will match EE 7725 Lecture Transparency. Formatted 11:57, 8 June 2001 from lsli
26 Mapping Function for Stage-2 Cells Link from stage-1 cell i to stage 2 for the omega network: ( 1,i(n 2) i (n 3)...i (0), 2,i(n 3) i (n 4)...i (0) d ) E Ω for 0 d<m. In the recursive omega consider f (1, i), cell i s image: f ( ) 1,i (n 2) i (n 3)...i (0) = 1,i(0) i (n 2)...i (1) The link from this cell to stage 2 in the RΩ: ( 1,i(0) i (n 2) i (n 3)...i (1), 2,i(0) di (n 3)...i (1) ) ERΩ for 0 d<m. To show Ω TE = RΩ we must find maps between these stage-2 cells: f(2, i) =f ( ) 2,i (n 2) i (n 3)...i (0) = 2,i(1) i (0) i (n 2)...i (2) = 2,σ m n 3,m 2(i) Using this function: ( f( 1,i(n 2) i (n 3)...i (0) ),f( 2,i(n 3) i (n 4)...i (0) d ) ) f(e Ω ) ( ) 1,i(0) i (n 2) i (n 3)...i (1), 2,i(0) di (n 3)...i (1) E RΩ 6-26 EE 7725 Lecture Transparency. Formatted 11:57, 8 June 2001 from lsli
27 Mapping Function for Stage-x + 1 Cells Link from stage-x cell i to stage x + 1 for the omega network: ( x, i(n 2) i (n 3)...i (0), x +1,i(n 3) i (n 4)...i (0) d ) E Ω for 0 d<m Assume that the mapping for cells in stages x has been found. (See below.) Then in the recursive omega consider f (x, i), cell i s image. f ( ) x, i (n 2) i (n 3)...i (0) = x, i(x 1)...i (0) i (n 2)...i (x) The link from this cell to stage x +1: ( x, i(x 1)...i (0) i (n 2) i (n 3)...i (x), x +1,i(x 1)...i (0) di (n 3)...i (x) ) E RΩ for 0 d<m 6-27 EE 7725 Lecture Transparency. Formatted 11:57, 8 June 2001 from lsli
28 To show Ω TE = RΩ we must find maps between these stage-x + 1 cells: f(x +1,i) = f ( x +1,i (n 2) i (n 3)...i (0) ) = x +1,i(x 1)...i (0) i (n 2)...i (x) Using the function: = x +1,σ m n x 1,m x(i) f ( x, i (n 2) i (n 3)...i (0), x +1,i(n 3) i (n 4)...i (0) d ) f(e Ω ) ( x, i(x 1)...i (0) i (n 2) i (n 3)...i (x), x +1,i(x 1)...i (0) di (n 3)...i (x) ) E RΩ 6-28 EE 7725 Lecture Transparency. Formatted 11:57, 8 June 2001 from lsli
29 Wrapup of Proof Determination of Mapping Function Found explicitly for stages 0, 1, and 2. It was assumed that a mapping function was found for stages 3...x<n 1. Using this assumption one could find the mapping for stage x +1. By induction, mapping can be found for all stages. Since mapping functions found for all cells, networks are TE EE 7725 Lecture Transparency. Formatted 11:57, 8 June 2001 from lsli
30 Proof that Inverse Omega (IΩ) is not TE to Omega An inverse omega network The mirror-image of the omega network. Structure of an n-stage m m-cell inverse omega network: Each stage has m n 1 cells. Network inputs connect to like-numbered stage-0 cell inputs. Stage-x cell outputs connect to stage-(x + 1) cell inputs with a m n 1,m shuffle, for 0 x<n 1. Stage-(n 1) cell outputs connect to network outputs with a m n 1,m shuffle. Routing: To route request (a, α) use cell output α (x) in stage x EE 7725 Lecture Transparency. Formatted 11:57, 8 June 2001 from lsli
31 Inverse omega network LGM: Let k = m n 1. I IΩ = {I, i 0 i<mk} O IΩ = {O, i 0 i<mk} V IΩ = I IΩ O IΩ {x, i 0 x<n, 0 i<k} E IΩ = {( ) } i I, i, 0, 0 i<mk m {( ) } i x, i, x +1, + jm n 2 0 j<m,0 i<k, 0 x<n 1 m {( n 1, i, O,i+ jm n 2 ) 0 j<m,0 i<k } 6-31 EE 7725 Lecture Transparency. Formatted 11:57, 8 June 2001 from lsli
32 TE Ω = IΩ Proof In omega network: I, 0 I Ω and (I, 0, 0, 0) E Ω. In inverse omega network: I, 0 I IΩ and (I, 0, 0, 0) E IΩ. Therefore, f (0, 0) =0, 0. But ( I,m n 1, 0, 0 ) E Ω and (I, 1, 0, 0) E IΩ. Since ( I,m n 1, 0, 0 ) (I, 1, 0, 0) E IΩ, TE Ω =IΩ. That s it EE 7725 Lecture Transparency. Formatted 11:57, 8 June 2001 from lsli
33 Topological Equivalence Two networks are topologically equivalent (OE) if their LGM representations are identical for some renaming of vertices in V. The relational operator OE = indicates topological equivalence; A OE = B means A is topologically equivalent to B. Mathematically, A OE = B (f V A V B ) f(a) =B, where A =(I A,O A,V A,E A ) and B =(I B,O B,V B,E B ) are network LGMs. The following two networks are topologically equivalent: 6-33 EE 7725 Lecture Transparency. Formatted 11:57, 8 June 2001 from lsli
34 Topological Equivalence Examples These two networks (from previous slide) are topologically equivalent: The one below is not OE to either of the two above: 6-34 EE 7725 Lecture Transparency. Formatted 11:57, 8 June 2001 from lsli
35 Proof Methods Let A =(I A,O A,V A,E A ) and B =(I B,O B,V B,E B ) be network LGMs. Easy cases: The two networks are not OE if: Either I A I B, O A O B, V A V B,or E A E B. (The number of inputs, outputs, cells, and links must be identical for OE.) Hard cases: find the mapping function, f. For many networks f can be either quickly found or can be shown to not exist. For others an exhaustive method must be used. Differences From TE Proofs No unique naming of input- and output-stage cells. Mapping function for input and output terminals must also be found EE 7725 Lecture Transparency. Formatted 11:57, 8 June 2001 from lsli
36 Proof That Omega is OE to Inverse Omega Proof Plan: Guess a mapping function for input labels. (The first guess presented will be wrong.) Compare links in the two networks that connect to the same input. Based on this, find mapping for first-stage cells, if possible. (If it is not possible we have to choose a different mapping for the input labels. If a different mapping cannot be found then the networks are not OE.) Continue to outputs. (Backtracking, when necessary.) 6-36 EE 7725 Lecture Transparency. Formatted 11:57, 8 June 2001 from lsli
37 (Incorrect) Input Mapping Function f (I, i) = I,σ m,m n 1(i) Given this mapping function: First find link to stage 0 in Ω: ( I,i(n 1) i (n 2)...i (0), 0,i(n 2) i (n 3)...i (0) ) EΩ The analogous link in the inverse omega: ( I,i(n 2) i (n 3)...i (0) i (n 1), 0,i(n 2) i (n 3)...i (0) ) EIΩ The map for the stage-0 cells couldn t be easier: f(0, i) =0, i 6-37 EE 7725 Lecture Transparency. Formatted 11:57, 8 June 2001 from lsli
38 Using (Incorrect) Input Mapping Function For stage 1: ( 0,i(n 2) i (n 3)...i (0), 1,i(n 3) i (n 4)...i (0) d ) E Ω The analogous link in the inverse omega: ( 0,i(n 2) i (n 3)...i (0), 1,di(n 2) i (n 3)...i (1) ) EIΩ The map for the stage-1 cells is impossible since no function could map 1,i (n 3) i (n 4)...i (0) d to 1,di (n 2) i (n 3)...i (1). (Because, for one reason, i (n 2) appears in only one) EE 7725 Lecture Transparency. Formatted 11:57, 8 June 2001 from lsli
39 Using (Correct) Input Mapping Function (Correct) input mapping will convert input number using the n-digit, radix-m, bit reverse function, ρ m n m n : ρ(i (n 1) i (n 2)...i (0) )=i (0) i (1)...i (n 1) In words, ρ reverse digits in radix-m representation. The (correct) input mapping function: f (I, i) =I, ρ(i) Using this mapping function find link to stage 0 in Ω: ( I,i(n 1) i (n 2)...i (0), 0,i(n 2) i (n 3)...i (0) ) EΩ The analogous link in the inverse omega: ( I,i(0) i (1)...i (n 2) i (n 1), 0,i(0) i (1)...i (n 3) i (n 2) ) EIΩ The map for the stage-0 cells is familiar: f(0, i) =0, ρ(i) 6-39 EE 7725 Lecture Transparency. Formatted 11:57, 8 June 2001 from lsli
40 For stage 1: ( 0,i(n 2) i (n 3)...i (0), 1,i(n 3) i (n 4)...i (0) d ) E Ω The analogous link in the inverse omega: ( 0,i(0) i (1)...i (n 2), 1,di(0) i (1)...i (n 3) ) EIΩ The map for the stage-1 cells is also familiar: f(1, i) =1, ρ(i) It can easily be shown that all nodes are mapped using ρ. Therefore, Ω OE =IΩ EE 7725 Lecture Transparency. Formatted 11:57, 8 June 2001 from lsli
41 Functional Equivalence Two networks are functionally equivalent (FE) if the sets of connection assignments each can satisfy are identical. Proof of functional equivalence: Find a set of connection assignments that each network can satisfy. Show that the two sets are identical. This is tedious using LGMs, CGMs, and similar graph notation. It is much easier to do using sets-of-permutation models, to be covered soon EE 7725 Lecture Transparency. Formatted 11:57, 8 June 2001 from lsli
Chapter 5. Finite Automata
 Chapter 5 Finite Automata 5.1 Finite State Automata Capable of recognizing numerous symbol patterns, the class of regular languages Suitable for pattern-recognition type applications, such as the lexical
Chapter 5 Finite Automata 5.1 Finite State Automata Capable of recognizing numerous symbol patterns, the class of regular languages Suitable for pattern-recognition type applications, such as the lexical
CSE 200 Lecture Notes Turing machine vs. RAM machine vs. circuits
 CSE 200 Lecture Notes Turing machine vs. RAM machine vs. circuits Chris Calabro January 13, 2016 1 RAM model There are many possible, roughly equivalent RAM models. Below we will define one in the fashion
CSE 200 Lecture Notes Turing machine vs. RAM machine vs. circuits Chris Calabro January 13, 2016 1 RAM model There are many possible, roughly equivalent RAM models. Below we will define one in the fashion
(x 1 +x 2 )(x 1 x 2 )+(x 2 +x 3 )(x 2 x 3 )+(x 3 +x 1 )(x 3 x 1 ).
 CMPSCI611: Verifying Polynomial Identities Lecture 13 Here is a problem that has a polynomial-time randomized solution, but so far no poly-time deterministic solution. Let F be any field and let Q(x 1,...,
CMPSCI611: Verifying Polynomial Identities Lecture 13 Here is a problem that has a polynomial-time randomized solution, but so far no poly-time deterministic solution. Let F be any field and let Q(x 1,...,
Mathematical Structures Combinations and Permutations
 Definitions: Suppose S is a (finite) set and n, k 0 are integers The set C(S, k) of k - combinations consists of all subsets of S that have exactly k elements The set P (S, k) of k - permutations consists
Definitions: Suppose S is a (finite) set and n, k 0 are integers The set C(S, k) of k - combinations consists of all subsets of S that have exactly k elements The set P (S, k) of k - permutations consists
Slides 3: Random Numbers
 Slides 3: Random Numbers We previously considered a few examples of simulating real processes. In order to mimic real randomness of events such as arrival times we considered the use of random numbers
Slides 3: Random Numbers We previously considered a few examples of simulating real processes. In order to mimic real randomness of events such as arrival times we considered the use of random numbers
n n P} is a bounded subset Proof. Let A be a nonempty subset of Z, bounded above. Define the set
 1 Mathematical Induction We assume that the set Z of integers are well defined, and we are familiar with the addition, subtraction, multiplication, and division. In particular, we assume the following
1 Mathematical Induction We assume that the set Z of integers are well defined, and we are familiar with the addition, subtraction, multiplication, and division. In particular, we assume the following
ELEG 305: Digital Signal Processing
 ELEG 5: Digital Signal Processing Lecture 6: The Fast Fourier Transform; Radix Decimatation in Time Kenneth E. Barner Department of Electrical and Computer Engineering University of Delaware Fall 8 K.
ELEG 5: Digital Signal Processing Lecture 6: The Fast Fourier Transform; Radix Decimatation in Time Kenneth E. Barner Department of Electrical and Computer Engineering University of Delaware Fall 8 K.
Big O 2/14/13. Administrative. Does it terminate? David Kauchak cs302 Spring 2013
 /4/3 Administrative Big O David Kauchak cs3 Spring 3 l Assignment : how d it go? l Assignment : out soon l CLRS code? l Videos Insertion-sort Insertion-sort Does it terminate? /4/3 Insertion-sort Loop
/4/3 Administrative Big O David Kauchak cs3 Spring 3 l Assignment : how d it go? l Assignment : out soon l CLRS code? l Videos Insertion-sort Insertion-sort Does it terminate? /4/3 Insertion-sort Loop
An Algebraic Approach to Network Coding
 An Algebraic Approach to July 30 31, 2009 Outline 1 2 a 3 Linear 4 Digital Communication Digital communication networks are integral parts of our lives these days; so, we want to know how to most effectively
An Algebraic Approach to July 30 31, 2009 Outline 1 2 a 3 Linear 4 Digital Communication Digital communication networks are integral parts of our lives these days; so, we want to know how to most effectively
Algorithm Design CS 515 Fall 2015 Sample Final Exam Solutions
 Algorithm Design CS 515 Fall 2015 Sample Final Exam Solutions Copyright c 2015 Andrew Klapper. All rights reserved. 1. For the functions satisfying the following three recurrences, determine which is the
Algorithm Design CS 515 Fall 2015 Sample Final Exam Solutions Copyright c 2015 Andrew Klapper. All rights reserved. 1. For the functions satisfying the following three recurrences, determine which is the
Lecture Notes On THEORY OF COMPUTATION MODULE -1 UNIT - 2
 BIJU PATNAIK UNIVERSITY OF TECHNOLOGY, ODISHA Lecture Notes On THEORY OF COMPUTATION MODULE -1 UNIT - 2 Prepared by, Dr. Subhendu Kumar Rath, BPUT, Odisha. UNIT 2 Structure NON-DETERMINISTIC FINITE AUTOMATA
BIJU PATNAIK UNIVERSITY OF TECHNOLOGY, ODISHA Lecture Notes On THEORY OF COMPUTATION MODULE -1 UNIT - 2 Prepared by, Dr. Subhendu Kumar Rath, BPUT, Odisha. UNIT 2 Structure NON-DETERMINISTIC FINITE AUTOMATA
ICS141: Discrete Mathematics for Computer Science I
 ICS141: Discrete Mathematics for Computer Science I Dept. Information & Computer Sci., Jan Stelovsky based on slides by Dr. Baek and Dr. Still Originals by Dr. M. P. Frank and Dr. J.L. Gross Provided by
ICS141: Discrete Mathematics for Computer Science I Dept. Information & Computer Sci., Jan Stelovsky based on slides by Dr. Baek and Dr. Still Originals by Dr. M. P. Frank and Dr. J.L. Gross Provided by
Lecture #3. Review: Power
 Lecture #3 OUTLINE Power calculations Circuit elements Voltage and current sources Electrical resistance (Ohm s law) Kirchhoff s laws Reading Chapter 2 Lecture 3, Slide 1 Review: Power If an element is
Lecture #3 OUTLINE Power calculations Circuit elements Voltage and current sources Electrical resistance (Ohm s law) Kirchhoff s laws Reading Chapter 2 Lecture 3, Slide 1 Review: Power If an element is
Algorithms and Data Structures 2016 Week 5 solutions (Tues 9th - Fri 12th February)
 Algorithms and Data Structures 016 Week 5 solutions (Tues 9th - Fri 1th February) 1. Draw the decision tree (under the assumption of all-distinct inputs) Quicksort for n = 3. answer: (of course you should
Algorithms and Data Structures 016 Week 5 solutions (Tues 9th - Fri 1th February) 1. Draw the decision tree (under the assumption of all-distinct inputs) Quicksort for n = 3. answer: (of course you should
Multi-coloring and Mycielski s construction
 Multi-coloring and Mycielski s construction Tim Meagher Fall 2010 Abstract We consider a number of related results taken from two papers one by W. Lin [1], and the other D. C. Fisher[2]. These articles
Multi-coloring and Mycielski s construction Tim Meagher Fall 2010 Abstract We consider a number of related results taken from two papers one by W. Lin [1], and the other D. C. Fisher[2]. These articles
Turing Machines Part III
 Turing Machines Part III Announcements Problem Set 6 due now. Problem Set 7 out, due Monday, March 4. Play around with Turing machines, their powers, and their limits. Some problems require Wednesday's
Turing Machines Part III Announcements Problem Set 6 due now. Problem Set 7 out, due Monday, March 4. Play around with Turing machines, their powers, and their limits. Some problems require Wednesday's
MATH 2200 Final LC Review
 MATH 2200 Final LC Review Thomas Goller April 25, 2013 1 Final LC Format The final learning celebration will consist of 12-15 claims to be proven or disproven. It will take place on Wednesday, May 1, from
MATH 2200 Final LC Review Thomas Goller April 25, 2013 1 Final LC Format The final learning celebration will consist of 12-15 claims to be proven or disproven. It will take place on Wednesday, May 1, from
Juggling card sequences
 Juggling card sequences Steve Butler Fan Chung Jay Cummings Ron Graham Abstract Juggling patterns can be described by a sequence of cards which keep track of the relative order of the balls at each step.
Juggling card sequences Steve Butler Fan Chung Jay Cummings Ron Graham Abstract Juggling patterns can be described by a sequence of cards which keep track of the relative order of the balls at each step.
Name (please print) Mathematics Final Examination December 14, 2005 I. (4)
 Mathematics 513-00 Final Examination December 14, 005 I Use a direct argument to prove the following implication: The product of two odd integers is odd Let m and n be two odd integers Since they are odd,
Mathematics 513-00 Final Examination December 14, 005 I Use a direct argument to prove the following implication: The product of two odd integers is odd Let m and n be two odd integers Since they are odd,
1 Pheasant Lane December 1990 Ithaca, NY (607) AN INTUITIVE APPROACH TO FFT ALGORITHMS
 APPLICATION NOTE NO. Pheasant Lane December Ithaca, NY ()-- AN INTUITIVE APPROACH TO FFT ALGORITHMS Most readers are probably familiar with the general notion of an FFT (Fast Fourier Transform). An FFT
APPLICATION NOTE NO. Pheasant Lane December Ithaca, NY ()-- AN INTUITIVE APPROACH TO FFT ALGORITHMS Most readers are probably familiar with the general notion of an FFT (Fast Fourier Transform). An FFT
Mathematical Induction
 Mathematical Induction MAT231 Transition to Higher Mathematics Fall 2014 MAT231 (Transition to Higher Math) Mathematical Induction Fall 2014 1 / 21 Outline 1 Mathematical Induction 2 Strong Mathematical
Mathematical Induction MAT231 Transition to Higher Mathematics Fall 2014 MAT231 (Transition to Higher Math) Mathematical Induction Fall 2014 1 / 21 Outline 1 Mathematical Induction 2 Strong Mathematical
Queens College, CUNY, Department of Computer Science Numerical Methods CSCI 361 / 761 Spring 2018 Instructor: Dr. Sateesh Mane.
 Queens College, CUNY, Department of Computer Science Numerical Methods CSCI 361 / 761 Spring 2018 Instructor: Dr. Sateesh Mane c Sateesh R. Mane 2018 3 Lecture 3 3.1 General remarks March 4, 2018 This
Queens College, CUNY, Department of Computer Science Numerical Methods CSCI 361 / 761 Spring 2018 Instructor: Dr. Sateesh Mane c Sateesh R. Mane 2018 3 Lecture 3 3.1 General remarks March 4, 2018 This
Functions and cardinality (solutions) sections A and F TA: Clive Newstead 6 th May 2014
 Functions and cardinality (solutions) 21-127 sections A and F TA: Clive Newstead 6 th May 2014 What follows is a somewhat hastily written collection of solutions for my review sheet. I have omitted some
Functions and cardinality (solutions) 21-127 sections A and F TA: Clive Newstead 6 th May 2014 What follows is a somewhat hastily written collection of solutions for my review sheet. I have omitted some
5 Quiver Representations
 5 Quiver Representations 5. Problems Problem 5.. Field embeddings. Recall that k(y,..., y m ) denotes the field of rational functions of y,..., y m over a field k. Let f : k[x,..., x n ] k(y,..., y m )
5 Quiver Representations 5. Problems Problem 5.. Field embeddings. Recall that k(y,..., y m ) denotes the field of rational functions of y,..., y m over a field k. Let f : k[x,..., x n ] k(y,..., y m )
Mathematical Induction
 Mathematical Induction MAT30 Discrete Mathematics Fall 018 MAT30 (Discrete Math) Mathematical Induction Fall 018 1 / 19 Outline 1 Mathematical Induction Strong Mathematical Induction MAT30 (Discrete Math)
Mathematical Induction MAT30 Discrete Mathematics Fall 018 MAT30 (Discrete Math) Mathematical Induction Fall 018 1 / 19 Outline 1 Mathematical Induction Strong Mathematical Induction MAT30 (Discrete Math)
8.1 Polynomial Threshold Functions
 CS 395T Computational Learning Theory Lecture 8: September 22, 2008 Lecturer: Adam Klivans Scribe: John Wright 8.1 Polynomial Threshold Functions In the previous lecture, we proved that any function over
CS 395T Computational Learning Theory Lecture 8: September 22, 2008 Lecturer: Adam Klivans Scribe: John Wright 8.1 Polynomial Threshold Functions In the previous lecture, we proved that any function over
Assignment 3 with Solutions
 Discrete Mathematics (Math 27), Spring 2004 Assignment 3 with Solutions. Recall the definition of functions, one-to-one functions, and onto functions. (a) Consider the function f : R R with f(x) x x. i.
Discrete Mathematics (Math 27), Spring 2004 Assignment 3 with Solutions. Recall the definition of functions, one-to-one functions, and onto functions. (a) Consider the function f : R R with f(x) x x. i.
Foundations of Mathematics MATH 220 FALL 2017 Lecture Notes
 Foundations of Mathematics MATH 220 FALL 2017 Lecture Notes These notes form a brief summary of what has been covered during the lectures. All the definitions must be memorized and understood. Statements
Foundations of Mathematics MATH 220 FALL 2017 Lecture Notes These notes form a brief summary of what has been covered during the lectures. All the definitions must be memorized and understood. Statements
1 + lim. n n+1. f(x) = x + 1, x 1. and we check that f is increasing, instead. Using the quotient rule, we easily find that. 1 (x + 1) 1 x (x + 1) 2 =
 Chapter 5 Sequences and series 5. Sequences Definition 5. (Sequence). A sequence is a function which is defined on the set N of natural numbers. Since such a function is uniquely determined by its values
Chapter 5 Sequences and series 5. Sequences Definition 5. (Sequence). A sequence is a function which is defined on the set N of natural numbers. Since such a function is uniquely determined by its values
Binary Decision Diagrams
 Binary Decision Diagrams Binary Decision Diagrams (BDDs) are a class of graphs that can be used as data structure for compactly representing boolean functions. BDDs were introduced by R. Bryant in 1986.
Binary Decision Diagrams Binary Decision Diagrams (BDDs) are a class of graphs that can be used as data structure for compactly representing boolean functions. BDDs were introduced by R. Bryant in 1986.
CSCE 222 Discrete Structures for Computing. Review for the Final. Hyunyoung Lee
 CSCE 222 Discrete Structures for Computing Review for the Final! Hyunyoung Lee! 1 Final Exam Section 501 (regular class time 8:00am) Friday, May 8, starting at 1:00pm in our classroom!! Section 502 (regular
CSCE 222 Discrete Structures for Computing Review for the Final! Hyunyoung Lee! 1 Final Exam Section 501 (regular class time 8:00am) Friday, May 8, starting at 1:00pm in our classroom!! Section 502 (regular
Codes on Graphs. Telecommunications Laboratory. Alex Balatsoukas-Stimming. Technical University of Crete. November 27th, 2008
 Codes on Graphs Telecommunications Laboratory Alex Balatsoukas-Stimming Technical University of Crete November 27th, 2008 Telecommunications Laboratory (TUC) Codes on Graphs November 27th, 2008 1 / 31
Codes on Graphs Telecommunications Laboratory Alex Balatsoukas-Stimming Technical University of Crete November 27th, 2008 Telecommunications Laboratory (TUC) Codes on Graphs November 27th, 2008 1 / 31
Math 396. Quotient spaces
 Math 396. Quotient spaces. Definition Let F be a field, V a vector space over F and W V a subspace of V. For v, v V, we say that v v mod W if and only if v v W. One can readily verify that with this definition
Math 396. Quotient spaces. Definition Let F be a field, V a vector space over F and W V a subspace of V. For v, v V, we say that v v mod W if and only if v v W. One can readily verify that with this definition
On Detecting Multiple Faults in Baseline Interconnection Networks
 On Detecting Multiple Faults in Baseline Interconnection Networks SHUN-SHII LIN 1 AND SHAN-TAI CHEN 2 1 National Taiwan Normal University, Taipei, Taiwan, ROC 2 Chung Cheng Institute of Technology, Tao-Yuan,
On Detecting Multiple Faults in Baseline Interconnection Networks SHUN-SHII LIN 1 AND SHAN-TAI CHEN 2 1 National Taiwan Normal University, Taipei, Taiwan, ROC 2 Chung Cheng Institute of Technology, Tao-Yuan,
Definition: Let S and T be sets. A binary relation on SxT is any subset of SxT. A binary relation on S is any subset of SxS.
 4 Functions Before studying functions we will first quickly define a more general idea, namely the notion of a relation. A function turns out to be a special type of relation. Definition: Let S and T be
4 Functions Before studying functions we will first quickly define a more general idea, namely the notion of a relation. A function turns out to be a special type of relation. Definition: Let S and T be
EE263 Review Session 1
 EE263 Review Session 1 October 5, 2018 0.1 Importing Variables from a MALAB.m file If you are importing variables given in file vars.m, use the following code at the beginning of your script. close a l
EE263 Review Session 1 October 5, 2018 0.1 Importing Variables from a MALAB.m file If you are importing variables given in file vars.m, use the following code at the beginning of your script. close a l
Decidable Subsets of CCS
 Decidable Subsets of CCS based on the paper with the same title by Christensen, Hirshfeld and Moller from 1994 Sven Dziadek Abstract Process algebra is a very interesting framework for describing and analyzing
Decidable Subsets of CCS based on the paper with the same title by Christensen, Hirshfeld and Moller from 1994 Sven Dziadek Abstract Process algebra is a very interesting framework for describing and analyzing
Chapter Generating Functions
 Chapter 8.1.1-8.1.2. Generating Functions Prof. Tesler Math 184A Fall 2017 Prof. Tesler Ch. 8. Generating Functions Math 184A / Fall 2017 1 / 63 Ordinary Generating Functions (OGF) Let a n (n = 0, 1,...)
Chapter 8.1.1-8.1.2. Generating Functions Prof. Tesler Math 184A Fall 2017 Prof. Tesler Ch. 8. Generating Functions Math 184A / Fall 2017 1 / 63 Ordinary Generating Functions (OGF) Let a n (n = 0, 1,...)
Section 1.8 Matrices as Linear Transformations
 Section.8 Matrices as Linear Transformations Up to this point in the course, we have thought of matrices as stand alone constructions, objects of interest in their own right. We have learned multiple matrix
Section.8 Matrices as Linear Transformations Up to this point in the course, we have thought of matrices as stand alone constructions, objects of interest in their own right. We have learned multiple matrix
Solutions, 2004 NCS/MAA TEAM COMPETITION
 Solutions, 004 NCS/MAA TEAM COMPETITION Each problem number is followed by an 11-tuple (a 10, a 9, a 8, a 7, a 6, a 5, a 4, a 3, a, a 1, a 0 ), where a k is the number of teams that scored k points on
Solutions, 004 NCS/MAA TEAM COMPETITION Each problem number is followed by an 11-tuple (a 10, a 9, a 8, a 7, a 6, a 5, a 4, a 3, a, a 1, a 0 ), where a k is the number of teams that scored k points on
Math 231E, Lecture 25. Integral Test and Estimating Sums
 Math 23E, Lecture 25. Integral Test and Estimating Sums Integral Test The definition of determining whether the sum n= a n converges is:. Compute the partial sums s n = a k, k= 2. Check that s n is a convergent
Math 23E, Lecture 25. Integral Test and Estimating Sums Integral Test The definition of determining whether the sum n= a n converges is:. Compute the partial sums s n = a k, k= 2. Check that s n is a convergent
Chapter 3 HW Solution
 Chapter 3 HW Solution Problem 3.6: I placed an xy coordinate system at a convenient point (origin doesn t really matter). y 173 x The positions of both planes are given by r B = v B ti + 173j mi (1) r
Chapter 3 HW Solution Problem 3.6: I placed an xy coordinate system at a convenient point (origin doesn t really matter). y 173 x The positions of both planes are given by r B = v B ti + 173j mi (1) r
CHAPTER 2 NUMBER SYSTEMS
 CHAPTER 2 NUMBER SYSTEMS The Decimal Number System : We begin our study of the number systems with the familiar decimal number system. The decimal system contains ten unique symbol 0, 1, 2, 3, 4, 5, 6,
CHAPTER 2 NUMBER SYSTEMS The Decimal Number System : We begin our study of the number systems with the familiar decimal number system. The decimal system contains ten unique symbol 0, 1, 2, 3, 4, 5, 6,
MODEL ANSWERS TO THE SEVENTH HOMEWORK. (b) We proved in homework six, question 2 (c) that. But we also proved homework six, question 2 (a) that
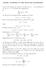 MODEL ANSWERS TO THE SEVENTH HOMEWORK 1. Let X be a finite set, and let A, B and A 1, A 2,..., A n be subsets of X. Let A c = X \ A denote the complement. (a) χ A (x) = A. x X (b) We proved in homework
MODEL ANSWERS TO THE SEVENTH HOMEWORK 1. Let X be a finite set, and let A, B and A 1, A 2,..., A n be subsets of X. Let A c = X \ A denote the complement. (a) χ A (x) = A. x X (b) We proved in homework
CS103 Handout 08 Spring 2012 April 20, 2012 Problem Set 3
 CS103 Handout 08 Spring 2012 April 20, 2012 Problem Set 3 This third problem set explores graphs, relations, functions, cardinalities, and the pigeonhole principle. This should be a great way to get a
CS103 Handout 08 Spring 2012 April 20, 2012 Problem Set 3 This third problem set explores graphs, relations, functions, cardinalities, and the pigeonhole principle. This should be a great way to get a
Linear Codes, Target Function Classes, and Network Computing Capacity
 Linear Codes, Target Function Classes, and Network Computing Capacity Rathinakumar Appuswamy, Massimo Franceschetti, Nikhil Karamchandani, and Kenneth Zeger IEEE Transactions on Information Theory Submitted:
Linear Codes, Target Function Classes, and Network Computing Capacity Rathinakumar Appuswamy, Massimo Franceschetti, Nikhil Karamchandani, and Kenneth Zeger IEEE Transactions on Information Theory Submitted:
Designing Information Devices and Systems I Spring 2018 Lecture Notes Note 11
 EECS 16A Designing Information Devices and Systems I Spring 2018 Lecture Notes Note 11 11.1 Context Our ultimate goal is to design systems that solve people s problems. To do so, it s critical to understand
EECS 16A Designing Information Devices and Systems I Spring 2018 Lecture Notes Note 11 11.1 Context Our ultimate goal is to design systems that solve people s problems. To do so, it s critical to understand
Practice Exam 1 CIS/CSE 607, Spring 2009
 Practice Exam 1 CIS/CSE 607, Spring 2009 Problem 1) Let R be a reflexive binary relation on a set A. Prove that R is transitive if, and only if, R = R R. Problem 2) Give an example of a transitive binary
Practice Exam 1 CIS/CSE 607, Spring 2009 Problem 1) Let R be a reflexive binary relation on a set A. Prove that R is transitive if, and only if, R = R R. Problem 2) Give an example of a transitive binary
MATH 61-02: PRACTICE PROBLEMS FOR FINAL EXAM
 MATH 61-02: PRACTICE PROBLEMS FOR FINAL EXAM (FP1) The exclusive or operation, denoted by and sometimes known as XOR, is defined so that P Q is true iff P is true or Q is true, but not both. Prove (through
MATH 61-02: PRACTICE PROBLEMS FOR FINAL EXAM (FP1) The exclusive or operation, denoted by and sometimes known as XOR, is defined so that P Q is true iff P is true or Q is true, but not both. Prove (through
Writing Circuit Equations
 2 C H A P T E R Writing Circuit Equations Objectives By the end of this chapter, you should be able to do the following: 1. Find the complete solution of a circuit using the exhaustive, node, and mesh
2 C H A P T E R Writing Circuit Equations Objectives By the end of this chapter, you should be able to do the following: 1. Find the complete solution of a circuit using the exhaustive, node, and mesh
One-to-one functions and onto functions
 MA 3362 Lecture 7 - One-to-one and Onto Wednesday, October 22, 2008. Objectives: Formalize definitions of one-to-one and onto One-to-one functions and onto functions At the level of set theory, there are
MA 3362 Lecture 7 - One-to-one and Onto Wednesday, October 22, 2008. Objectives: Formalize definitions of one-to-one and onto One-to-one functions and onto functions At the level of set theory, there are
Abstract Algebra I. Randall R. Holmes Auburn University. Copyright c 2012 by Randall R. Holmes Last revision: November 11, 2016
 Abstract Algebra I Randall R. Holmes Auburn University Copyright c 2012 by Randall R. Holmes Last revision: November 11, 2016 This work is licensed under the Creative Commons Attribution- NonCommercial-NoDerivatives
Abstract Algebra I Randall R. Holmes Auburn University Copyright c 2012 by Randall R. Holmes Last revision: November 11, 2016 This work is licensed under the Creative Commons Attribution- NonCommercial-NoDerivatives
JUST THE MATHS UNIT NUMBER 5.3. GEOMETRY 3 (Straight line laws) A.J.Hobson
 JUST THE MATHS UNIT NUMBER 5.3 GEOMETRY 3 (Straight line laws) by A.J.Hobson 5.3.1 Introduction 5.3.2 Laws reducible to linear form 5.3.3 The use of logarithmic graph paper 5.3.4 Exercises 5.3.5 Answers
JUST THE MATHS UNIT NUMBER 5.3 GEOMETRY 3 (Straight line laws) by A.J.Hobson 5.3.1 Introduction 5.3.2 Laws reducible to linear form 5.3.3 The use of logarithmic graph paper 5.3.4 Exercises 5.3.5 Answers
Turing Machine Variants
 CS311 Computational Structures Turing Machine Variants Lecture 12 Andrew Black Andrew Tolmach 1 The Church-Turing Thesis The problems that can be decided by an algorithm are exactly those that can be decided
CS311 Computational Structures Turing Machine Variants Lecture 12 Andrew Black Andrew Tolmach 1 The Church-Turing Thesis The problems that can be decided by an algorithm are exactly those that can be decided
Group. Orders. Review. Orders: example. Subgroups. Theorem: Let x be an element of G. The order of x divides the order of G
 Victor Adamchik Danny Sleator Great Theoretical Ideas In Computer Science Algebraic Structures: Group Theory II CS 15-251 Spring 2010 Lecture 17 Mar. 17, 2010 Carnegie Mellon University Group A group G
Victor Adamchik Danny Sleator Great Theoretical Ideas In Computer Science Algebraic Structures: Group Theory II CS 15-251 Spring 2010 Lecture 17 Mar. 17, 2010 Carnegie Mellon University Group A group G
Introduction to Computer Science Lecture 5: Algorithms
 Introduction to Computer Science Lecture 5: Algorithms Tian-Li Yu Taiwan Evolutionary Intelligence Laboratory (TEIL) Department of Electrical Engineering National Taiwan University tianliyu@cc.ee.ntu.edu.tw
Introduction to Computer Science Lecture 5: Algorithms Tian-Li Yu Taiwan Evolutionary Intelligence Laboratory (TEIL) Department of Electrical Engineering National Taiwan University tianliyu@cc.ee.ntu.edu.tw
LINDSTRÖM S THEOREM SALMAN SIDDIQI
 LINDSTRÖM S THEOREM SALMAN SIDDIQI Abstract. This paper attempts to serve as an introduction to abstract model theory. We introduce the notion of abstract logics, explore first-order logic as an instance
LINDSTRÖM S THEOREM SALMAN SIDDIQI Abstract. This paper attempts to serve as an introduction to abstract model theory. We introduce the notion of abstract logics, explore first-order logic as an instance
Number Theory. Zachary Friggstad. Programming Club Meeting
 Number Theory Zachary Friggstad Programming Club Meeting Outline Factoring Sieve Multiplicative Functions Greatest Common Divisors Applications Chinese Remainder Theorem Throughout, problems to try are
Number Theory Zachary Friggstad Programming Club Meeting Outline Factoring Sieve Multiplicative Functions Greatest Common Divisors Applications Chinese Remainder Theorem Throughout, problems to try are
SRI RAMAKRISHNA INSTITUTE OF TECHNOLOGY COIMBATORE Discrete Mathematics Functions
 1 SRI RAMAKRISHNA INSTITUTE OF TECHNOLOGY COIMBATORE 641010 Discrete Mathematics Functions 1. Define function. Let X and Y be any two sets. A relation f from X to Y is called a function if for every x
1 SRI RAMAKRISHNA INSTITUTE OF TECHNOLOGY COIMBATORE 641010 Discrete Mathematics Functions 1. Define function. Let X and Y be any two sets. A relation f from X to Y is called a function if for every x
Reduced Ordered Binary Decision Diagrams
 Reduced Ordered Binary Decision Diagrams Lecture #13 of Advanced Model Checking Joost-Pieter Katoen Lehrstuhl 2: Software Modeling & Verification E-mail: katoen@cs.rwth-aachen.de June 5, 2012 c JPK Switching
Reduced Ordered Binary Decision Diagrams Lecture #13 of Advanced Model Checking Joost-Pieter Katoen Lehrstuhl 2: Software Modeling & Verification E-mail: katoen@cs.rwth-aachen.de June 5, 2012 c JPK Switching
Bandwidth of op amps. R 1 R 2 1 k! 250 k!
 Bandwidth of op amps An experiment - connect a simple non-inverting op amp and measure the frequency response. From the ideal op amp model, we expect the amp to work at any frequency. Is that what happens?
Bandwidth of op amps An experiment - connect a simple non-inverting op amp and measure the frequency response. From the ideal op amp model, we expect the amp to work at any frequency. Is that what happens?
Chapter 7 Random Numbers
 Chapter 7 Random Numbers February 15, 2010 7 In the following random numbers and random sequences are treated as two manifestations of the same thing. A series of random numbers strung together is considered
Chapter 7 Random Numbers February 15, 2010 7 In the following random numbers and random sequences are treated as two manifestations of the same thing. A series of random numbers strung together is considered
CS Lecture 3. More Bayesian Networks
 CS 6347 Lecture 3 More Bayesian Networks Recap Last time: Complexity challenges Representing distributions Computing probabilities/doing inference Introduction to Bayesian networks Today: D-separation,
CS 6347 Lecture 3 More Bayesian Networks Recap Last time: Complexity challenges Representing distributions Computing probabilities/doing inference Introduction to Bayesian networks Today: D-separation,
Lecture 1: Asymptotics, Recurrences, Elementary Sorting
 Lecture 1: Asymptotics, Recurrences, Elementary Sorting Instructor: Outline 1 Introduction to Asymptotic Analysis Rate of growth of functions Comparing and bounding functions: O, Θ, Ω Specifying running
Lecture 1: Asymptotics, Recurrences, Elementary Sorting Instructor: Outline 1 Introduction to Asymptotic Analysis Rate of growth of functions Comparing and bounding functions: O, Θ, Ω Specifying running
Combinatorial algorithms
 Combinatorial algorithms computing subset rank and unrank, Gray codes, k-element subset rank and unrank, computing permutation rank and unrank Jiří Vyskočil, Radek Mařík 2012 Combinatorial Generation definition:
Combinatorial algorithms computing subset rank and unrank, Gray codes, k-element subset rank and unrank, computing permutation rank and unrank Jiří Vyskočil, Radek Mařík 2012 Combinatorial Generation definition:
download instant at
 2 CRYPTOGRAPHY AND NUMBER THEORY 2.1 CRYPTOGRAPHY AND MODULAR ARITHMETIC Pages 54 to 56 Problem 1 Problem 2 Problem 3 Problem 4 14 mod 9 = 5; 1 mod 9 = 8; 11 mod 9 = 7. KHUH LV D PHVVDJH. EBOB FP X JBPPXDB.
2 CRYPTOGRAPHY AND NUMBER THEORY 2.1 CRYPTOGRAPHY AND MODULAR ARITHMETIC Pages 54 to 56 Problem 1 Problem 2 Problem 3 Problem 4 14 mod 9 = 5; 1 mod 9 = 8; 11 mod 9 = 7. KHUH LV D PHVVDJH. EBOB FP X JBPPXDB.
Temporal Constraint Networks
 Ch. 5b p.1/24 Temporal Constraint Networks Addition to Chapter 5 Ch. 5b p.2/24 Outline Qualitative networks The interval algebra The point algebra Quantitative temporal networks Reference: Chapter 12 of
Ch. 5b p.1/24 Temporal Constraint Networks Addition to Chapter 5 Ch. 5b p.2/24 Outline Qualitative networks The interval algebra The point algebra Quantitative temporal networks Reference: Chapter 12 of
A product of γ-sets which is not Menger.
 A product of γ-sets which is not Menger. A. Miller Dec 2009 Theorem. Assume CH. Then there exists γ-sets A 0, A 1 2 ω such that A 0 A 1 is not Menger. We use perfect sets determined by Silver forcing (see
A product of γ-sets which is not Menger. A. Miller Dec 2009 Theorem. Assume CH. Then there exists γ-sets A 0, A 1 2 ω such that A 0 A 1 is not Menger. We use perfect sets determined by Silver forcing (see
Project Management Prof. Raghunandan Sengupta Department of Industrial and Management Engineering Indian Institute of Technology Kanpur
 Project Management Prof. Raghunandan Sengupta Department of Industrial and Management Engineering Indian Institute of Technology Kanpur Module No # 07 Lecture No # 35 Introduction to Graphical Evaluation
Project Management Prof. Raghunandan Sengupta Department of Industrial and Management Engineering Indian Institute of Technology Kanpur Module No # 07 Lecture No # 35 Introduction to Graphical Evaluation
#29: Logarithm review May 16, 2009
 #29: Logarithm review May 16, 2009 This week we re going to spend some time reviewing. I say re- view since you ve probably seen them before in theory, but if my experience is any guide, it s quite likely
#29: Logarithm review May 16, 2009 This week we re going to spend some time reviewing. I say re- view since you ve probably seen them before in theory, but if my experience is any guide, it s quite likely
Math 3361-Modern Algebra Lecture 08 9/26/ Cardinality
 Math 336-Modern Algebra Lecture 08 9/26/4. Cardinality I started talking about cardinality last time, and you did some stuff with it in the Homework, so let s continue. I said that two sets have the same
Math 336-Modern Algebra Lecture 08 9/26/4. Cardinality I started talking about cardinality last time, and you did some stuff with it in the Homework, so let s continue. I said that two sets have the same
Symbolic Model Checking with ROBDDs
 Symbolic Model Checking with ROBDDs Lecture #13 of Advanced Model Checking Joost-Pieter Katoen Lehrstuhl 2: Software Modeling & Verification E-mail: katoen@cs.rwth-aachen.de December 14, 2016 c JPK Symbolic
Symbolic Model Checking with ROBDDs Lecture #13 of Advanced Model Checking Joost-Pieter Katoen Lehrstuhl 2: Software Modeling & Verification E-mail: katoen@cs.rwth-aachen.de December 14, 2016 c JPK Symbolic
CSE 211. Pushdown Automata. CSE 211 (Theory of Computation) Atif Hasan Rahman
 CSE 211 Pushdown Automata CSE 211 (Theory of Computation) Atif Hasan Rahman Lecturer Department of Computer Science and Engineering Bangladesh University of Engineering & Technology Adapted from slides
CSE 211 Pushdown Automata CSE 211 (Theory of Computation) Atif Hasan Rahman Lecturer Department of Computer Science and Engineering Bangladesh University of Engineering & Technology Adapted from slides
Complexity Results for Deciding Networks of Evolutionary Processors 1
 Complexity Results for Deciding Networks of Evolutionary Processors 1 Florin Manea Institut für Informatik, Christian-Albrechts-Universität zu Kiel, D-24098 Kiel, Germany, and Faculty of Mathematics and
Complexity Results for Deciding Networks of Evolutionary Processors 1 Florin Manea Institut für Informatik, Christian-Albrechts-Universität zu Kiel, D-24098 Kiel, Germany, and Faculty of Mathematics and
MAT115A-21 COMPLETE LECTURE NOTES
 MAT115A-21 COMPLETE LECTURE NOTES NATHANIEL GALLUP 1. Introduction Number theory begins as the study of the natural numbers the integers N = {1, 2, 3,...}, Z = { 3, 2, 1, 0, 1, 2, 3,...}, and sometimes
MAT115A-21 COMPLETE LECTURE NOTES NATHANIEL GALLUP 1. Introduction Number theory begins as the study of the natural numbers the integers N = {1, 2, 3,...}, Z = { 3, 2, 1, 0, 1, 2, 3,...}, and sometimes
König s Lemma and Kleene Tree
 König s Lemma and Kleene Tree Andrej Bauer May 3, 2006 Abstract I present a basic result about Cantor space in the context of computability theory: the computable Cantor space is computably non-compact.
König s Lemma and Kleene Tree Andrej Bauer May 3, 2006 Abstract I present a basic result about Cantor space in the context of computability theory: the computable Cantor space is computably non-compact.
Lecture 10 Polynomial interpolation
 Lecture 10 Polynomial interpolation Weinan E 1,2 and Tiejun Li 2 1 Department of Mathematics, Princeton University, weinan@princeton.edu 2 School of Mathematical Sciences, Peking University, tieli@pku.edu.cn
Lecture 10 Polynomial interpolation Weinan E 1,2 and Tiejun Li 2 1 Department of Mathematics, Princeton University, weinan@princeton.edu 2 School of Mathematical Sciences, Peking University, tieli@pku.edu.cn
Week 2: Defining Computation
 Computational Complexity Theory Summer HSSP 2018 Week 2: Defining Computation Dylan Hendrickson MIT Educational Studies Program 2.1 Turing Machines Turing machines provide a simple, clearly defined way
Computational Complexity Theory Summer HSSP 2018 Week 2: Defining Computation Dylan Hendrickson MIT Educational Studies Program 2.1 Turing Machines Turing machines provide a simple, clearly defined way
APPLICATIONS OF INTEGRATION
 6 APPLICATIONS OF INTEGRATION APPLICATIONS OF INTEGRATION 6.5 Average Value of a Function In this section, we will learn about: Applying integration to find out the average value of a function. AVERAGE
6 APPLICATIONS OF INTEGRATION APPLICATIONS OF INTEGRATION 6.5 Average Value of a Function In this section, we will learn about: Applying integration to find out the average value of a function. AVERAGE
Prime Labeling of Small Trees with Gaussian Integers
 Rose-Hulman Undergraduate Mathematics Journal Volume 17 Issue 1 Article 6 Prime Labeling of Small Trees with Gaussian Integers Hunter Lehmann Seattle University Andrew Park Seattle University Follow this
Rose-Hulman Undergraduate Mathematics Journal Volume 17 Issue 1 Article 6 Prime Labeling of Small Trees with Gaussian Integers Hunter Lehmann Seattle University Andrew Park Seattle University Follow this
ECS 120 Lesson 18 Decidable Problems, the Halting Problem
 ECS 120 Lesson 18 Decidable Problems, the Halting Problem Oliver Kreylos Friday, May 11th, 2001 In the last lecture, we had a look at a problem that we claimed was not solvable by an algorithm the problem
ECS 120 Lesson 18 Decidable Problems, the Halting Problem Oliver Kreylos Friday, May 11th, 2001 In the last lecture, we had a look at a problem that we claimed was not solvable by an algorithm the problem
15.1 Proof of the Cook-Levin Theorem: SAT is NP-complete
 CS125 Lecture 15 Fall 2016 15.1 Proof of the Cook-Levin Theorem: SAT is NP-complete Already know SAT NP, so only need to show SAT is NP-hard. Let L be any language in NP. Let M be a NTM that decides L
CS125 Lecture 15 Fall 2016 15.1 Proof of the Cook-Levin Theorem: SAT is NP-complete Already know SAT NP, so only need to show SAT is NP-hard. Let L be any language in NP. Let M be a NTM that decides L
BDD Based Upon Shannon Expansion
 Boolean Function Manipulation OBDD and more BDD Based Upon Shannon Expansion Notations f(x, x 2,, x n ) - n-input function, x i = or f xi=b (x,, x n ) = f(x,,x i-,b,x i+,,x n ), b= or Shannon Expansion
Boolean Function Manipulation OBDD and more BDD Based Upon Shannon Expansion Notations f(x, x 2,, x n ) - n-input function, x i = or f xi=b (x,, x n ) = f(x,,x i-,b,x i+,,x n ), b= or Shannon Expansion
3 FUNCTIONS. 3.1 Definition and Basic Properties. c Dr Oksana Shatalov, Fall
 c Dr Oksana Shatalov, Fall 2014 1 3 FUNCTIONS 3.1 Definition and Basic Properties DEFINITION 1. Let A and B be nonempty sets. A function f from A to B is a rule that assigns to each element in the set
c Dr Oksana Shatalov, Fall 2014 1 3 FUNCTIONS 3.1 Definition and Basic Properties DEFINITION 1. Let A and B be nonempty sets. A function f from A to B is a rule that assigns to each element in the set
Handout 2 (Correction of Handout 1 plus continued discussion/hw) Comments and Homework in Chapter 1
 22M:132 Fall 07 J. Simon Handout 2 (Correction of Handout 1 plus continued discussion/hw) Comments and Homework in Chapter 1 Chapter 1 contains material on sets, functions, relations, and cardinality that
22M:132 Fall 07 J. Simon Handout 2 (Correction of Handout 1 plus continued discussion/hw) Comments and Homework in Chapter 1 Chapter 1 contains material on sets, functions, relations, and cardinality that
Mathematical Background. Unsigned binary numbers. Powers of 2. Logs and exponents. Mathematical Background. Today, we will review:
 Mathematical Background Mathematical Background CSE 373 Data Structures Today, we will review: Logs and eponents Series Recursion Motivation for Algorithm Analysis 5 January 007 CSE 373 - Math Background
Mathematical Background Mathematical Background CSE 373 Data Structures Today, we will review: Logs and eponents Series Recursion Motivation for Algorithm Analysis 5 January 007 CSE 373 - Math Background
CS 6110 Lecture 35 Solving Domain Equations 19 April 2013 Lecturer: Andrew Myers
 CS 6110 Lecture 35 Solving Domain Equations 19 April 2013 Lecturer: Andrew Myers To develop a denotational semantics for a language with recursive types, or to give a denotational semantics for the untyped
CS 6110 Lecture 35 Solving Domain Equations 19 April 2013 Lecturer: Andrew Myers To develop a denotational semantics for a language with recursive types, or to give a denotational semantics for the untyped
Main topics for the First Midterm Exam
 Main topics for the First Midterm Exam The final will cover Sections.-.0, 2.-2.5, and 4.. This is roughly the material from first three homeworks and three quizzes, in addition to the lecture on Monday,
Main topics for the First Midterm Exam The final will cover Sections.-.0, 2.-2.5, and 4.. This is roughly the material from first three homeworks and three quizzes, in addition to the lecture on Monday,
MITOCW MIT18_01SCF10Rec_24_300k
 MITOCW MIT18_01SCF10Rec_24_300k JOEL LEWIS: Hi. Welcome back to recitation. In lecture, you've been doing related rates problems. I've got another example for you, here. So this one's a really tricky one.
MITOCW MIT18_01SCF10Rec_24_300k JOEL LEWIS: Hi. Welcome back to recitation. In lecture, you've been doing related rates problems. I've got another example for you, here. So this one's a really tricky one.
ACS2: Decidability Decidability
 Decidability Bernhard Nebel and Christian Becker-Asano 1 Overview An investigation into the solvable/decidable Decidable languages The halting problem (undecidable) 2 Decidable problems? Acceptance problem
Decidability Bernhard Nebel and Christian Becker-Asano 1 Overview An investigation into the solvable/decidable Decidable languages The halting problem (undecidable) 2 Decidable problems? Acceptance problem
a = a i 2 i a = All such series are automatically convergent with respect to the standard norm, but note that this representation is not unique: i<0
 p-adic Numbers K. Sutner v0.4 1 Modular Arithmetic rings integral domains integers gcd, extended Euclidean algorithm factorization modular numbers add Lemma 1.1 (Chinese Remainder Theorem) Let a b. Then
p-adic Numbers K. Sutner v0.4 1 Modular Arithmetic rings integral domains integers gcd, extended Euclidean algorithm factorization modular numbers add Lemma 1.1 (Chinese Remainder Theorem) Let a b. Then
b + O(n d ) where a 1, b > 1, then O(n d log n) if a = b d d ) if a < b d O(n log b a ) if a > b d
 CS161, Lecture 4 Median, Selection, and the Substitution Method Scribe: Albert Chen and Juliana Cook (2015), Sam Kim (2016), Gregory Valiant (2017) Date: January 23, 2017 1 Introduction Last lecture, we
CS161, Lecture 4 Median, Selection, and the Substitution Method Scribe: Albert Chen and Juliana Cook (2015), Sam Kim (2016), Gregory Valiant (2017) Date: January 23, 2017 1 Introduction Last lecture, we
Circuits. Lecture 11 Uniform Circuit Complexity
 Circuits Lecture 11 Uniform Circuit Complexity 1 Recall 2 Recall Non-uniform complexity 2 Recall Non-uniform complexity P/1 Decidable 2 Recall Non-uniform complexity P/1 Decidable NP P/log NP = P 2 Recall
Circuits Lecture 11 Uniform Circuit Complexity 1 Recall 2 Recall Non-uniform complexity 2 Recall Non-uniform complexity P/1 Decidable 2 Recall Non-uniform complexity P/1 Decidable NP P/log NP = P 2 Recall
1 Basic Combinatorics
 1 Basic Combinatorics 1.1 Sets and sequences Sets. A set is an unordered collection of distinct objects. The objects are called elements of the set. We use braces to denote a set, for example, the set
1 Basic Combinatorics 1.1 Sets and sequences Sets. A set is an unordered collection of distinct objects. The objects are called elements of the set. We use braces to denote a set, for example, the set
The well-known Fibonacci sequence is defined by a recurrence. Specifically,letF i denote the ith number. Then, we have:
 Week 4 Recurrences (I) 4.1 The Fibonacci Sequence The well-known Fibonacci sequence is defined by a recurrence. Specifically,letF i denote the ith number. Then, we have: F 0 =0 (4.1) F 1 =1 (4.2) F n =
Week 4 Recurrences (I) 4.1 The Fibonacci Sequence The well-known Fibonacci sequence is defined by a recurrence. Specifically,letF i denote the ith number. Then, we have: F 0 =0 (4.1) F 1 =1 (4.2) F n =
Review 3. Andreas Klappenecker
 Review 3 Andreas Klappenecker Final Exam Friday, May 4, 2012, starting at 12:30pm, usual classroom Topics Topic Reading Algorithms and their Complexity Chapter 3 Logic and Proofs Chapter 1 Logic and Proofs
Review 3 Andreas Klappenecker Final Exam Friday, May 4, 2012, starting at 12:30pm, usual classroom Topics Topic Reading Algorithms and their Complexity Chapter 3 Logic and Proofs Chapter 1 Logic and Proofs
CS21 Decidability and Tractability
 CS21 Decidability and Tractability Lecture 3 January 9, 2017 January 9, 2017 CS21 Lecture 3 1 Outline NFA, FA equivalence Regular Expressions FA and Regular Expressions January 9, 2017 CS21 Lecture 3 2
CS21 Decidability and Tractability Lecture 3 January 9, 2017 January 9, 2017 CS21 Lecture 3 1 Outline NFA, FA equivalence Regular Expressions FA and Regular Expressions January 9, 2017 CS21 Lecture 3 2
CS 154, Lecture 4: Limitations on DFAs (I), Pumping Lemma, Minimizing DFAs
 CS 154, Lecture 4: Limitations on FAs (I), Pumping Lemma, Minimizing FAs Regular or Not? Non-Regular Languages = { w w has equal number of occurrences of 01 and 10 } REGULAR! C = { w w has equal number
CS 154, Lecture 4: Limitations on FAs (I), Pumping Lemma, Minimizing FAs Regular or Not? Non-Regular Languages = { w w has equal number of occurrences of 01 and 10 } REGULAR! C = { w w has equal number
Deterministic Finite Automata (DFAs)
 CS/ECE 374: Algorithms & Models of Computation, Fall 28 Deterministic Finite Automata (DFAs) Lecture 3 September 4, 28 Chandra Chekuri (UIUC) CS/ECE 374 Fall 28 / 33 Part I DFA Introduction Chandra Chekuri
CS/ECE 374: Algorithms & Models of Computation, Fall 28 Deterministic Finite Automata (DFAs) Lecture 3 September 4, 28 Chandra Chekuri (UIUC) CS/ECE 374 Fall 28 / 33 Part I DFA Introduction Chandra Chekuri
In this lecture, we will consider how to analyse an electrical circuit by applying KVL and KCL. As a result, we can predict the voltages and currents
 In this lecture, we will consider how to analyse an electrical circuit by applying KVL and KCL. As a result, we can predict the voltages and currents around an electrical circuit. This is a short lecture,
In this lecture, we will consider how to analyse an electrical circuit by applying KVL and KCL. As a result, we can predict the voltages and currents around an electrical circuit. This is a short lecture,
