Gibbard Satterthwaite Games
|
|
|
- Cleopatra Boyd
- 6 years ago
- Views:
Transcription
1 Proceedings of the Twenty-Fourth International Joint Conference on Artificial Intelligence (IJCAI 2015) Gibbard Satterthwaite Games Edith Elkind University of Oxford United Kingdom Umberto Grandi University of Toulouse France Francesca Rossi University of Padova and Harvard University Arkadii Slinko University of Auckland New Zealand Abstract The Gibbard-Satterthwaite theorem implies the ubiquity of manipulators voters who could change the election outcome in their favor by unilaterally modifying their vote In this paper, we ask what happens if a given profile admits several such voters We model strategic interactions among Gibbard Satterthwaite manipulators as a normal-form game We classify the 2-by-2 games that can arise in this setting for two simple voting rules, namely Plurality and Borda, and study the complexity of determining whether a given manipulative vote weakly dominates truth-telling, as well as existence of Nash equilibria 1 Introduction Voting is a common method of preference aggregation, which enables the participating agents to identify the best candidate given the individual agents rankings of the candidates However, a common concern of electoral designers is that no reasonable voting rule is immune to manipulation: as shown by Gibbard [1973] and Satterthwaite [1975], for three or more candidates, every onto, non-dictatorial voting rule admits a preference profile (a collection of voters rankings) where some voter would be better off by submitting a ranking that differs from his truthful one This cornerstone result is partially mitigated by the observation, developed in the last decade in the research area of computational social choice [Brandt et al, 2015], that voters will not necessary respond to an incentive of manipulation, in case such an action presents heavy computational costs An additional factor that may prevent strategic behavior in voters is that would-be manipulators must interact between themselves The analysis of this interaction has been a very active area of research in political science, where several theoretical works have attempted to describe the micrologic behind strategic voting (eg, [Cain, 1978; Cox, 1997; Myatt, 2007]) Most of these works concerns elections using the Plurality rule; for other voting rules the situation may be even more complex On the one hand, some voters may not be able to manipulate on their own, but have an opportunity to take a defensive action which will destroy somebody s opportunity to manipulate On the other hand, such countermanipulators are uncertain whether the manipulation, which they are going to counter, will take place or not The voters in most elections are typically acting independently and in the absence of communication, hence strategic voters must play a simultaneous one-shot game in a non-cooperative setting 1 Apart from the practical difficulties of manipulating, some voters may be ideological and interested in stating their preference no matter what Practical observations suggest that the number of ideological voters is significant For instance, in the famous Florida vote (2000), where Bush won over Gore by just 537 votes, 97,488 Nader supporters voted for Nader even though in such a close election every strategic voter should have voted either for Gore or for Bush, and the overwhelming majority of Nader supporters preferred Gore to Bush At the other end of the spectrum, truly strategic voters are interested in optimizing the outcome of the election and may or may not submit their insincere vote depending on strategic considerations It is very hard to detect the number of strategic voters in a given election, but the percentage of those who actually manipulated may be easier to obtain For instance, [Kawai and Watanabe, 2013] estimate the number of such voters in Japanese elections between 2,5% and 5,5% Moreover, [Benjamin et al, 2013] show that preference misrepresentation is related to cognitive skills, and [Choi et al, 2014] demonstrate that decision-making ability in laboratory experiments correlates strongly with socio-economic status and wealth Therefore, it is reasonable to assume that only a small fraction of voters in an election would act strategically when given an opportunity to do so The goal of our paper is to develop a basic understanding of how multiple manipulators can help or hurt each other by acting simultaneously, under some simple voting rules In our model non-manipulators do not act strategically, since we assume that the strategic behavior of voters is prompted by the possibility of manipulating see, however, our Exam- 1 [Forsythe et al, 1993] found in laboratory that strategic voting is, indeed, more likely to occur if pre-election coordination devices such as polls and shared voting histories are available; in the model of [Myerson and Weber, 1993], which assume such coordination devices in the form of a common prior, the set of voting equilibria is always nonempty 533
2 ple 7, where we show that countermanipulations can make the game much more complex We model the interaction among the manipulators as a normal-form game, where the players called GS-manipulators are a subset of the manipulators in a given profile, each player s set of actions consists of her truthful vote and a subset of her manipulative votes, and players preferences over action profiles are determined by who wins in the resulting elections (see Section 3 for formal definitions) We call such games the GS-games The paper is organized as follows Section 2 presents some basic concepts of voting theory In Section 3 we formally define the Gibbard Satterthwaite games Section 4 focuses on 2-by-2 games Section 5 deals with computing weakly dominant strategies Section 6 presents our results on the existence of Nash equilibria Section 7 concludes Some proofs are omitted due to space constraints Related Work There is a substantial body of research dating back to [Farquharson, 1969] that analyzes non-truthful voting as a strategic game; see, eg, [Moulin, 1979; Myerson and Weber, 1993; Dhillon and Lockwood, 2004; Feddersen et al, 1990] The algorithmic aspects of such models have recently received some attention as well [Desmedt and Elkind, 2010; Xia and Conitzer, 2010; Thompson et al, 2013; Obraztsova et al, 2013], with a strong focus on the problem of equilibrium selection Indeed, a major difficulty in the study of general voting games is that they admit undesirable Nash equilibria such as, for instance, a situation in which all voters vote for the same candidate which none of them likes Our analysis can also be seen from this perspective: by limiting the set of players, and restricting their action spaces, we eliminate counterintuitive behaviors Voting dynamics is a closely related topic, where players change their votes one by one in response to the current outcome [Meir et al, 2010; Lev and Rosenschein, 2012; Reijngoud and Endriss, 2012; Reyhaneh and Wilson, 2012; Obraztsova et al, 2015; Rabinovich et al, 2015] With the exception of [Meir et al, 2010], in all of these papers the set of players consists of all voters, ie, a player is allowed to vote non-truthfully even if he would be unable to manipulate the election on his own Note that a convergence result in voting dynamics implies the existence of a Nash equilibrium in a GS-game, and indeed our Theorem 13 can be obtained as a consequence of a result by [Meir et al, 2010] Our work can also be viewed as an extension of the model of safe strategic voting proposed by Slinko and White [2008; 2014] However, unlike us, Slinko and White focus on a subset of GS-manipulators who (a) all have identical preferences and (b) choose between truthtelling and using a specific manipulative vote, and on the existence of weakly dominant nontruthful votes in this setting (such votes are called safe strategic votes) In contrast, we allow manipulators to have diverse preferences and to use strategy sets that contain more than one non-truthful vote 2 Preliminaries We consider n-voter elections over a candidate set C = {c 1,, c m } An election is defined by a preference profile V = (v 1,, v n ), where each v i, i = 1,, n, is a total order over C; we refer to v i as the vote, or preferences, of voter i For two candidates c 1, c 2 C we write c 1 i c 2 if voter i ranks c 1 above c 2 ; if this is the case, we say that voter i prefers c 1 to c 2 For brevity we will sometimes write ab z to represent a full ordering of the candidates v i with a i b i i z We denote by top k (v i ) the set of top k candidates in v i, and abbreviate top 1 (v i ) to top(v i ) Given a preference profile V = (v 1,, v n ), we denote by (V i, v i ) the preference profile obtained from V by replacing v i with v i Given two lists of candidates X = (x 1,, x l ), Y = (y 1,, y l ) we denote by v[x; Y ] the vote obtained by swapping x j with y j for j = 1,, l in vote v If X and Y are singletons, ie, X = (x), Y = (y), we omit the parentheses, and simply write v[x; y] A voting rule is a mapping R that, given a profile V, outputs a candidate R(V ) C We consider the following voting rules in this paper k-approval, 1 k m 1: under this rule, each candidate receives one point from each voter that ranks her in top k positions; 1-approval is also known as Plurality Borda: under this rule, each candidate gets m j points from each voter that ranks her in position j Under both rules, the score of a candidate is the total number of points she receives, and the winner is the candidate with the highest score Ties are broken according to a fixed order > over C We denote the k-approval score of c in a profile V by sc k (c, V ), and c s Borda score in V by sc B (c, V ) We say that two votes v and v over the same candidate set C are equivalent with respect to a voting rule R if R(V i, v) = R(V i, v ) for every profile V It is easy to see that v and v are equivalent with respect to k-approval if and only if top k (v) = top k (v ), and v and v are equivalent with respect to Borda if and only if v = v 3 The Model Our goal is to investigate strategic situations that arise when one or more voters could improve the outcome of the election from their perspective by unilaterally changing their votes We will now define such situations formally Definition 1 We say that a voter i is a Gibbard Satterthwaite manipulator, or a GS-manipulator, in a profile V = (v 1,, v n ) with respect to a voting rule R if there exists a vote v i v i such that i prefers R(V i, v i ) to R(V ) We denote the set of all GS-manipulators in a profile V with respect to a voting rule R by N(V, R) A vote v i is called a GS-manipulation of voter i if i prefers R(V i, v i ) to R(V ), and, moreover, for every v i it holds that either R(V i, v i ) = R(V i, v i ) or i prefers R(V i, v i ) to R(V i, v i ) We say that i manipulates in favor of p by submitting a vote v i v i if p is the winner in R(V i, v i ) Note that a voter can manipulate in favor of several different candidates; however, in the definition of a GS-manipulation we require the voter to focus on her most preferred candidate among the ones she can make the election winner Recall that a normal-form game is defined by a set of players N, and, for each i N, a set of actions A i and a preference relation i defined on the space of action profiles, 534
3 ie, tuples of the form (a 1,, a n ), where a i A i for all i N (while one could define normal-form games in terms of utility functions or in terms of preference relations, the latter approach is more suitable for our setting, as we only have ordinal information about the voters preferences) For each preference profile V and voting rule R, we consider a family of normal-form games defined as follows Recall that N(V, R) is the set of GS-manipulators for V and R Definition 2 Given a preference profile V and a voting rule R, a GS-game for V and R is a normal-form game N, {A i } i N, { i } i N where: N = N(V, R); for each player i, his set of actions A i consists of his truthful vote and a subset of his GS-manipulations; the preference relation of player i is determined by the outcome of R on the preference profile that corresponds to a given action profile Given an action profile V = (v i ) i N, let (V N, V ) = (v 1,, v n) be the preference profile such that v i = v i for i N and v i = v i for i N Given two action profiles V and V, we write V i V if and only if player i prefers R(V N, V ) to R(V N, V ) or R(V N, V ) = R(V N, V ) Observe that different choices of the actions sets A i correspond to different games in the family Denote the set of all GS-games for V and R by GS(V, R) All games in GS(V, R) have the same set of players, namely, N(V, R), so an individual game in GS(V, R) is fully determined by the players sets of actions, ie, (A i ) i N(V,R) Thus, in what follows, we write G = (V, R, (A i ) i N(V,R) ); when V and R are clear from the context, we simply write G = (A i ) i N We refer to an action profile in a GS-game as a GS-profile; we will sometimes identify the GS-profile V = (vi ) i N with the preference profile (V N, V ) We denote the set of all GS-profiles in a game G by GSP(G) Discussion We emphasize a number of important features of this definition First, we restrict the set of players to Gibbard Satterthwaite manipulators That is, we assume that, if a player cannot benefit from voting non-truthfully in the original profile, he will not be interested in exploring the possible benefits of strategic behavior when other voters manipulate as well This attitude appears to be quite plausible: a voter may only be attracted to investigating the strategic aspects of the situation if manipulative behavior is profitable Second, we allow the players to limit themselves to subsets of their GS-manipulations, rather than consider a single game where each player s set of actions consists of his truthful vote and all of his GS-manipulations There are several reasons for that First, the space of all GS-manipulations for a given voter can be very large, and a player may be unable to identify all such votes Second, the player may use a specific algorithm, such as that of Bartholdi et al [1989], to find a GS-manipulation; in this case, her set of actions would consist of her truthful vote and the output of this algorithm Third, the player may choose to ignore manipulations that are (weakly) dominated by others Finally, a player may prefer not to change his vote beyond what is necessary to make his (i) (iv) (ii) (v) (iii) (vi) Figure 1: Diagrams for 2-by-2 GS-games target candidate the election winner, because he does not enjoy lying [Obraztsova and Elkind, 2012], or fears unintended consequences of his actions in the complex environment of the game 4 2-by-2 GS Games In this section, we investigate which 2-by-2 games (ie, games with two players and two actions per player) can be represented as GS-games To address this question, we need a suitable classification of 2-by-2 games Note first that every such game corresponds to 4 action profiles, and is fully described by giving both players preferences over these profiles By considering all possible pairs of preference relations over domains of size 4, Fraser and Kilgour [1986] show that there are 724 distinct 2-by-2 games However, this classification is too fine-grained for our purposes Instead, we represent every 2-by-2 game by a diagram with 4 vertices and 4 directed edges, where an edge is directed from a less preferred profile to a more preferred profile (a bidirectional edge indicates indifference) For each player, let s denote his truthful vote and let i denote his manipulative vote; thus, the vertices of our diagram are,,, and For two edges of this diagram their direction is determined by the fact that i is a GS-manipulation: namely, both of the edges adjacent to are directed away from Thus, by renaming the players if necessary, we can represent any 2-by-2 GS-game by one of the 6 diagrams in Figure 1 Observe that an action profile in a 2-by-2 game is a Nash equilibrium if and only if the corresponding vertex in the diagram of the game has two incoming edges The following proposition is immediate from Figure 1 Proposition 3 Every 2-by-2 GS-game has at least one Nash equilibrium in pure strategies Example 4 Consider the GS-game for the preference profile (abc, bac, cab, cba) under the Plurality voting rule, with ties broken according to a > b > c In this game players 1 and 2 are the GS-manipulators; we can assume that their GSmanipulations are v 1 = v 1 [a; b] and v 2 = v 2 [b; a], respectively Note that if both GS-manipulators vote insincerely, c 535
4 remains the election winner Thus, this game corresponds to diagram (ii) in Figure 1 We say that diagram D is realizable by voting rule R if there exist a profile V and a 2-by-2 game G GS(V, R) such that D is the diagram for G Our next goal is to study which diagrams are realizable by common voting rules Theorem 5 The only diagrams realizable by Plurality are (ii), (iii), (iv) and (v) Proof Consider a profile V, and assume that voters 1 and 2 are the GS-manipulators in V Suppose that the Plurality winner in V is w, voter 1 manipulates in favor of a, and voter 2 manipulates in favor of b Since voters 1 and 2 are GSmanipulators, we have w top(v 1 ) and w top(v 2 ) Thus, we can assume that their GS-manipulations are given by v 1 = v 1 [top(v 1 ); a], v 2 = v 2 [top(v 2 ); b] Let V 1 = (V 1, v 1), V 2 = (V 2, v 2), V 12 = (v 1, v 2) The winner in V 12 can be w, a, or b, and the case where it is w corresponds to diagram (ii) Further, if a = b, then a is the winner at V 1, V 2, and V 12, corresponding to diagram (iii) Now, suppose that a b As the winner at V 12 is either a or b, one of the arrows adjacent to must be bidirectional, ruling out diagrams (i), (ii) and (vi) for this case We have argued that diagrams (i) and (vi) are not realizable by Plurality Example 4 realizes diagram (ii) We omit the examples for the remaining two cases due to lack of space Note that Theorem 5 implies that the Prisoner s dilemma is not realizable by Plurality In contrast, for Borda all six diagrams are realizable Theorem 6 Diagrams (i) (vi) are all realizable by Borda Proof We provide an example for diagram (i), the remaining cases are omitted Assume that ties are broken alphabetically Let V = (dbcae, dbcae, acebd, acebd) The Borda winner in V is a The first two voters are the GS-manipulators, and for each of them the vote v = bdcea is a GS-manipulation in favor of c Further, in (v, v, v 3, v 4 ) the Borda winner is b To conclude the section, let us introduce the possibility of counter-manipulation, ie, let us expand the notion of GSgames by letting sincere players respond to hypothetic manipulations by strategic voters Example 7 We show that a 2-by-2 game with one manipulator and one counter-manipulator may not have a Nash equilibrium Suppose that the voting rule is 2-approval and the profile is V = (adcb, bdca) with ties broken according to a > b > c > d For voter 1 switching c and d is a manipulation in favor of a To counter-manipulate, voter 2 can also switch c and d, making c win But then voter 1 would be better off switching c and d back, after which the same move will be beneficial for voter 2 5 Weak Dominance In this section, we consider the complexity of checking whether a given GS-manipulation is always at least as good as the truthful vote This problem is captured by the gametheoretic notion of weak dominance Definition 8 Given a GS-game G = (V, R, (A i ) i N(V,R) ) and two strategies vi, v i A i, we say that vi weakly dominates vi if for every profile V GSP(G) either R(V i, v i ) = R(V i, v i ) or voter i prefers R(V i, v i ) to R(V i, v i ) We say that vi is weakly dominant if v i weakly dominates vi for every vi A i In what follows, we will mostly be interested in determining whether a given GS-manipulation vi weakly dominates the truthful vote v i A related problem is whether vi is weakly dominant However, in the context of GS-games the former problem appears to be more relevant than the latter Indeed, the main issue faced by a GS-manipulator is whether to manipulate or not, and if a certain vote can always ensure an outcome that is no worse than that of truthful voting, then this is a strong incentive to use it, even if another non-truthful vote may sometimes be better Our approach is consistent with the one taken in the study of safe manipulation [Slinko and White, 2008; 2014], where different manipulations are not compared to each other either Preliminary Observations In the rest of the paper, we limit our attention to k-approval rules We will now state some definitions and observations that apply to this class Note first that under k-approval any GS-manipulation of voter i is equivalent to a vote of the form v i [X; Y ], where X top k (v i ), Y C \ top k (v i ) Consider a GSmanipulation v i [X; Y ] of voter i in V under k-approval; we say that v i [X; Y ] is minimal if for every other GSmanipulation v i of voter i it holds that v i = v i[x ; Y ], where X X That is, a GS-manipulation is minimal if it performs as few swaps as possible Consider a profile V such that the k-approval winner in V is w, and sc k (w, V ) = t Recall that > is the tie-breaking order over candidates Let S 1 (V, k) = {c C sc k (c, V ) = t, w > c}, S 2 (V, k) = {c C sc k (c, V ) = t 1, w < c}, and set S(V, k) = S 1 (V, k) S 2 (V, k) We say that a candidate c is k-competitive in V if c S(V, k) Consider a GSmanipulator i who has a GS-manipulation in favor of some candidate p As i prefers p to w, it cannot be the case that, by submitting a non-truthful vote, he both decreases the score of w and increases the score of p Thus, his manipulation increases the score of p or decreases the score of w, but not both It follows that under k-approval every GS-manipulation in V is in favor of some candidate p S(V, k); in particular, if V admits a GS-manipulator under k-approval, then S(V, k) is not empty There are two types of GS-manipulators: those who rank w in top k positions, and those who do not The GSmanipulators of the first type can only manipulate in favor of candidates they already approve of, so in their manipulation they rank w in position k + 1 or lower; we will refer to such voters as demoters The GS-manipulators of the second type manipulate by promoting some candidate they rank above w into top k positions; we refer to such voters as promoters We say that a candidate c is k-plausible for i in V if there exists a promoter j i and a GS-manipulation vj such that c is the k-approval winner in (V j, vj ); we denote the set of all 536
5 candidates that are k-plausible for i in V by S + i (V, k), and set S + (V, k) = i N S + i (V, k) Plurality Consider a GS-manipulator i in a profile V under Plurality, and let vi be his GS-manipulation Note that i is necessarily a promoter Let p i be i s favorite candidate in S(V, k) \ {top(v i )} It is clear that vi is equivalent to v i [top(v i ); p i ] and p i is the winner in (V i, vi ), ie, all GS-manipulations of voter i in V are equivalent to each other Hence, there is essentially a unique GSgame that corresponds to V, namely, the one where A i = {v i, v i [top(v i ); p i ]} for each player i; we will denote this game by G 1(V ) We will now characterize GS-manipulations that are weakly dominant in this game (as each player i has two strategies, her GS-manipulation vi is weakly dominant if and only if it weakly dominates v i ) Theorem 9 Let vi be the GS-manipulation of voter i in G 1(V ), and let c = top(v i ) Then vi is weakly dominant in G 1(V ) if and only if c S + i (V, 1) Proof Suppose that c S + i, ie, there exists a promoter j i with GS-manipulation vj such that c wins in V 1 = (V j, vj ) Note that c = top 1(vj ) Consider the profile V 2 = (V i 1, v i ) In this profile both c and the initial winner w have the same score as in V, so c loses to w As c = top(v i ), this shows that vi is not weakly dominant Conversely, suppose that c S + i Then for any profile V = (v 1,, v n) GSP(G 1(V )) such that v i = v i we have sc 1 (c, V ) sc 1 (c, V ) On the other hand, since no GSmanipulator ranks w first, we have sc 1 (w, V ) = sc 1 (w, V ) Thus, c is not the Plurality winner in V Let w be the Plurality winner in V ; note that w {w} S Let V = (V i, v i ) Suppose that vi = v[c; p] It is easy to see that this implies that the Plurality winner in V is either p or w Since i weakly prefers p to every other candidate in {w} S, it follows that vi is weakly dominant Theorem 9 illustrates that every GS-game for Plurality in the absence of dominant strategies is essentially a coordination game: the GS-manipulators have to coordinate to ensure that their efforts do not cancel out We obtain the following: Corollary 10 There is a polynomial-time algorithm for checking whether a given GS-manipulation v i of voter i weakly dominates his truthful vote v i in G 1(V ) 2-Approval: An Algorithm We will now focus on the 2- approval rule Let w be the 2-approval winner in V, and recall that p is the candidate in S that beats every other candidate in S in profile V under 2-approval It can be shown that all demoters rank the same candidate p first, and have the same set of GS-manipulations Now, suppose that w top 2 (v i ), ie, i is a promoter Then i can raise the scores of some candidates in C \top 2 (v i ) by moving these candidates into top two positions; note that i can do that for two candidates simultaneously Clearly, a promoter s vote is a GS-manipulation if and only if one of the promoted candidates is i s most preferred candidate in S \ top 2 (v i ) (let us denote this candidate by p) and the other promoted candidate p is such that promoting p does not prevent p from becoming a winner We emphasize that p is not necessarily i s most preferred 2-competitive candidate: it may be the case that i ranks another 2-competitive candidate in top two positions Given a profile V, let G 2(V ) be the GS-game where each player s set of actions consists of his truthful vote and all his minimal manipulations The argument above shows that for demoters the minimality assumption imposes no additional constraints, whereas for promoters it excludes manipulations where two candidates are swapped into top two positions simultaneously We can now state the main result of this section, whose proof is omitted in the interest of space Theorem 11 There is a polynomial-time algorithm for checking whether a given GS-manipulation v i of voter i weakly dominates his truthful vote v i in G 2(V ) 4-Approval: A Hardness Proof We were unable to determine the complexity of checking whether a given GS-manipulation weakly dominates truthtelling under 3- approval We conjecture that this problem is computationally hard Indeed, this is the case for 4-approval: there is a way to select one manipulative action per player so that for the resulting game this problem is conp-complete We reduce from the classic NP-complete problem EXACT COVER BY 3-SETS (X3C) An instance of this problem is given by a ground set Γ = {g 1,, g 3ν } and a collection Σ = {σ 1,, σ µ } of 3-element subsets of Γ It is a yes - instance if there is a subcollection Σ Σ with Σ = ν such that σ Σ σ = Γ, and a no -instance otherwise Theorem 12 The problem of deciding whether a given strategy vi weakly dominates truthtelling in a GS-game (V, 4-App, (A i ) i N(V,4-App) ) is conp-complete Proof sketch It is immediate that this problem is in conp To prove conp-hardness, consider an instance I = (Γ, Σ) of X3C with Γ = 3ν, Σ = µ We can assume without loss of generality that σ 1 = {g 1, g 2, g 3 } and no other set in Σ contains g 1 ; if this is not the case, we can modify I by adding three new elements and a single set containing them We will now construct an instance of our problem In what follows, when writing X Y in describing an order, we mean that all elements of X are ranked above all elements of Y, but the order of elements within X and within Y can be arbitrary There is a set of candidates C = {c 1,, c 3ν } that correspond to elements of Γ, three special candidates w, p, and c, and a set of dummy candidates D = µ i=0 D i, where D i = 4 for i = 0,, µ We define the order > by setting w > c > p > c 1 > > c 3ν > D For each set σ i Σ we construct a vote v i of the form D i σ i c, where candidates in σ i are ordered according to >, and set v 0 = D 0 p c 1 c C \ {c 1 } We also construct additional voters so that in the resulting profile V we have sc 4 (w, V ) = sc 4 (p, V ) = ν + 1, sc 4 (c i, V ) = ν + 1 for all i = 1,, 3ν, sc 4 (c, V ) = 1, the 4-approval score of each candidate in D is at most 1, and the only GS-manipulators in V are voters 0, 1,, µ 537
6 Note that w is the 4-approval winner in V, and S = C {p} We now define a GS-game for this profile by constructing the players sets of actions as follows Let D 0 = {d 1, d 2, d 3, d 4 } Then v0 = v 0 [{d 1, d 2 }; {p, c}] is a GS-manipulation for voter 0, which makes p the winner with ν + 2 points Similarly, for each i = 1,, µ the vote vi = v i[d i ; σ i {c}] is a GS-manipulation which makes i s top candidate in σ i the winner with ν + 2 points (note that i orders σ i in the same way > does, so tie-breaking favors i s most preferred candidate in σ i ) We set A i = {v i, vi } for i = 0,, µ This completes the description of our game Clearly, we can construct the profile V and the players sets of strategies in polynomial time given I It can be shown that v0 weakly dominates v 0 if and only if we started with a no -instance of X3C; we omit the proof 6 Nash Equilibrium In this section, we study existence and uniqueness of Nash equilibria in GS-games for k-approval with k = 1, 2, 3, 4 In what follows, when considering a GS-game, we assume that its set of GS-manipulators is not empty, since otherwise a Nash equilibrium exists trivially We will first show that for Plurality, a Nash equilibrium always exists Theorem 13 For any profile V the game G 1(V ) has a Nash equilibrium in pure strategies Proof Consider the set S + (V, 1), and let p be the candidate with the highest score in this set (using the tie-breaking order eventually) Let i be some voter whose GS-manipulation is in favor of p, and let v i = v i[top(v i ); p] Then (V i, v i ) is a Nash equilibrium with winner p However, many preference profiles admit multiple Nash equilibria under Plurality For instance, if there are three voters i, j, l such that v r [top(v r ); c] A r for each r {i, j, l} and some candidate c, then there is a NE where these three voters manipulate and everyone else votes truthfully; if there are several candidates for whom such a triple of voters exists, any of them could win in a Nash equilibrium For 2-approval, we can prove existence of Nash equilibria as long as every manipulator has at least one minimal GSmanipulation in her action set Theorem 14 Any game G = (V, 2-App, (A i ) i N(V,2-App) ), where for each i N(V, 2-App) the set A i contains some minimal manipulation of voter i, has a Nash equilibrium Proof We can assume that N(V, 2-App) Let w be the current winner of the election Assume first that the set of promoters in G is not empty Let p + be the 2-plausible candidate that beats all other candidates in S + (V, 2) Let i be a promoter who manipulates in favor of p +, and let vi be some minimal GS-manipulation of i Then V = (V i, vi ) is a Nash equilibrium with winner p + Indeed, by minimality of vi we know that only the score of p+ has increased in V Hence, to prevent p + from winning in V, a manipulator j would have to lower p + s score, and he could only do that if p + top 2 (v j ) If j is a promoter, then he prefers p + to any candidate that he could make a winner in this way On the other hand, if j is a demoter then p + is his top candidate, hence he does not have incentives to change the outcome If all GS-manipulators are demoters, then a profile where any demoter, say j, submits a GS-manipulation and everyone else votes truthfully is a Nash equilibrium with winner top(v j ) Indeed, a demoter can only manipulate in favor of her top candidate by decreasing the score of w Hence all demoters manipulate in favor of the same candidate A similar result holds for 3-approval, though under stronger assumptions Given a voter i and a set of candidates Z,we denote by bot i (Z) the least preferred candidate of i in Z A manipulative vote v i [X; Y ] is called greedy if it is minimal and for every other minimal strategy v i [X; Y ] it holds that i prefers bot i (Y ) to bot i (Y ) Clearly, there is a unique greedy manipulation for each manipulator i Theorem 15 The game G = (V, 3-App, (A i ) i N(V,3-App) ) where for each i N(V, 3-App) the set A i consists of i s truthful vote and her greedy GS-manipulation has a Nash equilibrium The restriction to greedy strategies in Theorem 15 is essential Moreover, for 4-approval the existence of Nash equilibria is not guaranteed; we conjecture that this result extends to k- approval with k > 4 Theorem 16 Under 3-approval, there exists a game G = (V, 3-App, (A i ) i N(V,3-App) ), where for each player i N(V, 3-App) the set A i consists of i s truthful vote and some minimal manipulations, st G has no Nash equilibrium Theorem 16 holds even if we restrict the set of strategies of each player to her greedy manipulations: Theorem 17 Under 4-approval, there exists a game G = (V, 4-App, (A i ) i N(V,4-App) ), where for each player i N(V, 4-App) the set A i consists of i s truthful vote and her greedy GS-manipulation, st G has no Nash equilibrium 7 Conclusions In this paper we have studied the strategic interaction of manipulators in an electoral situation, providing a formal model in the form of a class of strategic-form games, which we called GS-games, and showing that these games may require extensive communication and a non-trivial computational effort to be played, which may serve as a barrier against manipulation In particular, we have shown that for Plurality these games exhibit a fairly simple structure, which still allows for situations as complex as a coordination game For Borda and k-approval, with k > 1, GS-games are quite complicated, and it may therefore be difficult for the players to coordinate their actions: indeed, for large enough k a Nash equilibrium may fail to exist, and even if it exists, it is not necessarily unique Many questions concerning GS-games remain open The most immediate of them is to fully understand the role of minimality assumptions in our proofs Further afield, it would be interesting to extend our study to other voting rules, and to identify reasonable restrictions on the manipulators strategy spaces that lead to existence and uniqueness of Nash equilibria, and make it easy to compute manipulations that weakly dominate truthtelling 538
7 Acknowledgements Part of this work was done when Arkadii Slinko was visiting the Institute for Mathematical Sciences (Singapore) and the University of Padova (Italy) Francesca Rossi and Umberto Grandi were partially supported by the strategic project KIDNEY - Incorporating patients preferences in kidney transplant decision protocols of the University of Padova References [Bartholdi et al, 1989] J Bartholdi, C A Tovey, and M A Trick The computational difficulty of manipulating an election Social Choice and Welfare, 6: , 1989 [Benjamin et al, 2013] D J Benjamin, S A Brown, and J M Shapiro Who is behavioral? cognitive ability and anomalous preferences Journal of the European Economic Association, 11: , 2013 [Brandt et al, 2015] Felix Brandt, Vincent Conitzer, Ulle Endriss, Jérôme Lang, and Ariel Procaccia, editors Handbook of Computational Social Choice Cambridge University Press, 2015 [Cain, 1978] BE Cain Strategic voting in britain American Journal of Political Science, 22: , 1978 [Choi et al, 2014] S Choi, S Kariv, W Muller, and D Silverman Who is (more) rational? American Economic Review, 104: , 2014 [Cox, 1997] GW Cox Making Votes Count Cambridge University Press, 1997 [Desmedt and Elkind, 2010] Y Desmedt and E Elkind Equilibria of plurality voting with abstentions In ACM EC 10, pages , 2010 [Dhillon and Lockwood, 2004] A Dhillon and B Lockwood When are plurality rule voting games dominancesolvable? Games and Economic Behavior, 46:55 75, 2004 [Farquharson, 1969] R Farquharson Theory of Voting Yale University Press, 1969 [Feddersen et al, 1990] T J Feddersen, I Sened, and S G Wright Rational voting and candidate entry under plurality rule American Journal of Political Science, 34(4): , 1990 [Forsythe et al, 1993] R Forsythe, R B Myerson, T A Rietz, and R J Weber An experiment on coordination in multi-candidate elections: The importance of polls and election histories Social Choice and Welfare, 10: , 1993 [Fraser and Kilgour, 1986] NM Fraser and DM Kilgour Non-strict ordinal 2x2 games: A comprehensive computer-assisted analysis of the 726 possibilities Theory and Decision, 20(2):99 121, 1986 [Gibbard, 1973] A Gibbard Manipulation of voting schemes: A general result Econometrica, 41(4): , 1973 [Kawai and Watanabe, 2013] K Kawai and Y Watanabe Inferring strategic voting American Economic Review, 103: , 2013 [Lev and Rosenschein, 2012] O Lev and J S Rosenschein Convergence of iterative voting In AAMAS 12, pages , 2012 [Meir et al, 2010] R Meir, M Polukarov, J S Rosenschein, and N R Jennings Convergence to equilibria of plurality voting In AAAI 10, pages , 2010 [Moulin, 1979] H Moulin Dominance solvable voting schemes Econometrica, 47: , 1979 [Myatt, 2007] David P Myatt On the theory of strategic voting The Review of Economic Studies, 74: , 2007 [Myerson and Weber, 1993] R Myerson and R Weber A theory of voting equilibria American Political Science Review, 87(1): , 1993 [Obraztsova and Elkind, 2012] S Obraztsova and E Elkind Optimal manipulation of voting rules In AAMAS 12, pages , 2012 [Obraztsova et al, 2013] S Obraztsova, E Markakis, and D R M Thompson Plurality voting with truth-biased agents In SAGT 13, 2013 [Obraztsova et al, 2015] S Obraztsova, E Markakis, M Polukarov, Z Rabinovich, and N Jennings On the convergence of iterative voting: How restrictive should restricted dynamics be? In AAAI 15, 2015 [Rabinovich et al, 2015] Z Rabinovich, S Obraztsova, O Lev, E Markakis, and J S Rosenschein Analysis of equilibria in iterative voting schemes In AAAI 15, 2015 [Reijngoud and Endriss, 2012] A Reijngoud and U Endriss Voter response to iterated poll information In AAMAS 12, pages , 2012 [Reyhaneh and Wilson, 2012] R Reyhaneh and M Wilson Best reply dynamics for scoring rules In ECAI 12, pages , 2012 [Satterthwaite, 1975] M A Satterthwaite Strategyproofness and Arrow s conditions: Existence and correspondence theorems for voting procedures and social welfare functions Journal of Economic Theory, 10(2): , 1975 [Slinko and White, 2008] A Slinko and S White Nondictatorial social choice rules are safely manipulable? In COMSOC 08, pages , 2008 [Slinko and White, 2014] A Slinko and S White Is it ever safe to vote strategically? Social Choice and Welfare, 43(2): , 2014 [Thompson et al, 2013] D R M Thompson, O Lev, K Leyton-Brown, and J S Rosenschein Empirical analysis of plurality election equilibria In AAMAS 13, pages , 2013 [Xia and Conitzer, 2010] L Xia and V Conitzer Stackelberg voting games: Computational aspects and paradoxes In AAAI 10, pages ,
Trembling Hand Equilibria of Plurality Voting
 Trembling Hand Equilibria of Plurality Voting Svetlana Obraztsova Hebrew University of Jerusalem Israel Zinovi Rabinovich Mobileye Vision Technologies Ltd. Israel Edith Elkind University of Oxford United
Trembling Hand Equilibria of Plurality Voting Svetlana Obraztsova Hebrew University of Jerusalem Israel Zinovi Rabinovich Mobileye Vision Technologies Ltd. Israel Edith Elkind University of Oxford United
An NTU Cooperative Game Theoretic View of Manipulating Elections
 An NTU Cooperative Game Theoretic View of Manipulating Elections Michael Zuckerman 1, Piotr Faliszewski 2, Vincent Conitzer 3, and Jeffrey S. Rosenschein 1 1 School of Computer Science and Engineering,
An NTU Cooperative Game Theoretic View of Manipulating Elections Michael Zuckerman 1, Piotr Faliszewski 2, Vincent Conitzer 3, and Jeffrey S. Rosenschein 1 1 School of Computer Science and Engineering,
How Bad is Selfish Voting?
 How Bad is Selfish Voting? Simina Brânzei Aarhus University simina@cs.au.dk Ioannis Caragiannis University of Patras caragian@ceid.upatras.gr Jamie Morgenstern Carnegie Mellon University jamiemmt@cs.cmu.edu
How Bad is Selfish Voting? Simina Brânzei Aarhus University simina@cs.au.dk Ioannis Caragiannis University of Patras caragian@ceid.upatras.gr Jamie Morgenstern Carnegie Mellon University jamiemmt@cs.cmu.edu
Best reply dynamics for scoring rules
 Best reply dynamics for scoring rules R. Reyhani M.C Wilson Department of Computer Science University of Auckland 3rd Summer workshop of CMSS, 20-22 Feb 2012 Introduction Voting game Player (voter) action
Best reply dynamics for scoring rules R. Reyhani M.C Wilson Department of Computer Science University of Auckland 3rd Summer workshop of CMSS, 20-22 Feb 2012 Introduction Voting game Player (voter) action
Ties Matter: Complexity of Voting Manipulation Revisited
 Proceedings of the Twenty-Second International Joint Conference on Artificial Intelligence Ties Matter: Complexity of Voting Manipulation Revisited Svetlana Obraztsova Edith Elkind School of Physical and
Proceedings of the Twenty-Second International Joint Conference on Artificial Intelligence Ties Matter: Complexity of Voting Manipulation Revisited Svetlana Obraztsova Edith Elkind School of Physical and
Convergence to Equilibria in Plurality Voting
 Convergence to Equilibria in Plurality Voting Reshef Meir, Maria Polukarov, Jeffrey S. Rosenschein, and Nicholas R. Jennings Abstract Multi-agent decision problems, in which independent agents have to
Convergence to Equilibria in Plurality Voting Reshef Meir, Maria Polukarov, Jeffrey S. Rosenschein, and Nicholas R. Jennings Abstract Multi-agent decision problems, in which independent agents have to
Stackelberg Voting Games: Computational Aspects and Paradoxes
 Stackelberg Voting Games: Computational Aspects and Paradoxes Lirong Xia Department of Computer Science Duke University Durham, NC 7708, USA lxia@cs.duke.edu Vincent Conitzer Department of Computer Science
Stackelberg Voting Games: Computational Aspects and Paradoxes Lirong Xia Department of Computer Science Duke University Durham, NC 7708, USA lxia@cs.duke.edu Vincent Conitzer Department of Computer Science
Multiple Equilibria in the Citizen-Candidate Model of Representative Democracy.
 Multiple Equilibria in the Citizen-Candidate Model of Representative Democracy. Amrita Dhillon and Ben Lockwood This version: March 2001 Abstract De Sinopoli and Turrini (1999) present an example to show
Multiple Equilibria in the Citizen-Candidate Model of Representative Democracy. Amrita Dhillon and Ben Lockwood This version: March 2001 Abstract De Sinopoli and Turrini (1999) present an example to show
How Bad is Selfish Voting?
 How Bad is Selfish Voting? Simina Brânzei Aarhus University simina@cs.au.dk Ioannis Caragiannis University of Patras caragian@ceid.upatras.gr Jamie Morgenstern Carnegie Mellon University jamiemmt@cs.cmu.edu
How Bad is Selfish Voting? Simina Brânzei Aarhus University simina@cs.au.dk Ioannis Caragiannis University of Patras caragian@ceid.upatras.gr Jamie Morgenstern Carnegie Mellon University jamiemmt@cs.cmu.edu
Social Algorithms. Umberto Grandi University of Toulouse. IRIT Seminar - 5 June 2015
 Social Algorithms Umberto Grandi University of Toulouse IRIT Seminar - 5 June 2015 Short presentation PhD from Universiteit van Amsterdam, 2012 Institute for Logic, Language and Computation Supervisor:
Social Algorithms Umberto Grandi University of Toulouse IRIT Seminar - 5 June 2015 Short presentation PhD from Universiteit van Amsterdam, 2012 Institute for Logic, Language and Computation Supervisor:
6.207/14.15: Networks Lecture 24: Decisions in Groups
 6.207/14.15: Networks Lecture 24: Decisions in Groups Daron Acemoglu and Asu Ozdaglar MIT December 9, 2009 1 Introduction Outline Group and collective choices Arrow s Impossibility Theorem Gibbard-Satterthwaite
6.207/14.15: Networks Lecture 24: Decisions in Groups Daron Acemoglu and Asu Ozdaglar MIT December 9, 2009 1 Introduction Outline Group and collective choices Arrow s Impossibility Theorem Gibbard-Satterthwaite
APPLIED MECHANISM DESIGN FOR SOCIAL GOOD
 APPLIED MECHANISM DESIGN FOR SOCIAL GOOD JOHN P DICKERSON Lecture #3 09/06/2016 CMSC828M Tuesdays & Thursdays 12:30pm 1:45pm REMINDER: SEND ME TOP 3 PRESENTATION PREFERENCES! I LL POST THE SCHEDULE TODAY
APPLIED MECHANISM DESIGN FOR SOCIAL GOOD JOHN P DICKERSON Lecture #3 09/06/2016 CMSC828M Tuesdays & Thursdays 12:30pm 1:45pm REMINDER: SEND ME TOP 3 PRESENTATION PREFERENCES! I LL POST THE SCHEDULE TODAY
CMU Social choice 2: Manipulation. Teacher: Ariel Procaccia
 CMU 15-896 Social choice 2: Manipulation Teacher: Ariel Procaccia Reminder: Voting Set of voters Set of alternatives Each voter has a ranking over the alternatives means that voter prefers to Preference
CMU 15-896 Social choice 2: Manipulation Teacher: Ariel Procaccia Reminder: Voting Set of voters Set of alternatives Each voter has a ranking over the alternatives means that voter prefers to Preference
APPLIED MECHANISM DESIGN FOR SOCIAL GOOD
 APPLIED MECHANISM DESIGN FOR SOCIAL GOOD JOHN P DICKERSON Lecture #21 11/8/2016 CMSC828M Tuesdays & Thursdays 12:30pm 1:45pm IMPOSSIBILITY RESULTS IN VOTING THEORY / SOCIAL CHOICE Thanks to: Tuomas Sandholm
APPLIED MECHANISM DESIGN FOR SOCIAL GOOD JOHN P DICKERSON Lecture #21 11/8/2016 CMSC828M Tuesdays & Thursdays 12:30pm 1:45pm IMPOSSIBILITY RESULTS IN VOTING THEORY / SOCIAL CHOICE Thanks to: Tuomas Sandholm
Combining Voting Rules Together
 Combining Voting Rules Together Nina Narodytska and Toby Walsh and Lirong Xia 3 Abstract. We propose a simple method for combining together voting rules that performs a run-off between the different winners
Combining Voting Rules Together Nina Narodytska and Toby Walsh and Lirong Xia 3 Abstract. We propose a simple method for combining together voting rules that performs a run-off between the different winners
Algorithmic Game Theory Introduction to Mechanism Design
 Algorithmic Game Theory Introduction to Mechanism Design Makis Arsenis National Technical University of Athens April 216 Makis Arsenis (NTUA) AGT April 216 1 / 41 Outline 1 Social Choice Social Choice
Algorithmic Game Theory Introduction to Mechanism Design Makis Arsenis National Technical University of Athens April 216 Makis Arsenis (NTUA) AGT April 216 1 / 41 Outline 1 Social Choice Social Choice
Coalitional Structure of the Muller-Satterthwaite Theorem
 Coalitional Structure of the Muller-Satterthwaite Theorem Pingzhong Tang and Tuomas Sandholm Computer Science Department Carnegie Mellon University {kenshin,sandholm}@cscmuedu Abstract The Muller-Satterthwaite
Coalitional Structure of the Muller-Satterthwaite Theorem Pingzhong Tang and Tuomas Sandholm Computer Science Department Carnegie Mellon University {kenshin,sandholm}@cscmuedu Abstract The Muller-Satterthwaite
Complexity of unweighted coalitional manipulation under some common voting rules
 Complexity of unweighted coalitional manipulation under some common voting rules Lirong Xia, Vincent Conitzer, Ariel D. Procaccia, and Jeffrey S. Rosenschein Abstract In this paper, we study the computational
Complexity of unweighted coalitional manipulation under some common voting rules Lirong Xia, Vincent Conitzer, Ariel D. Procaccia, and Jeffrey S. Rosenschein Abstract In this paper, we study the computational
Approximation Algorithms and Mechanism Design for Minimax Approval Voting 1
 Approximation Algorithms and Mechanism Design for Minimax Approval Voting 1 Ioannis Caragiannis, Dimitris Kalaitzis, and Evangelos Markakis Abstract We consider approval voting elections in which each
Approximation Algorithms and Mechanism Design for Minimax Approval Voting 1 Ioannis Caragiannis, Dimitris Kalaitzis, and Evangelos Markakis Abstract We consider approval voting elections in which each
Approximation Algorithms and Mechanism Design for Minimax Approval Voting
 Approximation Algorithms and Mechanism Design for Minimax Approval Voting Ioannis Caragiannis RACTI & Department of Computer Engineering and Informatics University of Patras, Greece caragian@ceid.upatras.gr
Approximation Algorithms and Mechanism Design for Minimax Approval Voting Ioannis Caragiannis RACTI & Department of Computer Engineering and Informatics University of Patras, Greece caragian@ceid.upatras.gr
Efficient Algorithms for Hard Problems on Structured Electorates
 Aspects of Computation 2017 Efficient Algorithms for Hard Problems on Structured Electorates Neeldhara Misra The standard Voting Setup and some problems that we will encounter. The standard Voting Setup
Aspects of Computation 2017 Efficient Algorithms for Hard Problems on Structured Electorates Neeldhara Misra The standard Voting Setup and some problems that we will encounter. The standard Voting Setup
Dominating Manipulations in Voting with Partial Information
 Dominating Manipulations in Voting with Partial Information Vincent Conitzer Department of Computer Science Duke University Durham, NC 27708, USA conitzer@cs.duke.edu Toby Walsh NICTA and UNSW Sydney,
Dominating Manipulations in Voting with Partial Information Vincent Conitzer Department of Computer Science Duke University Durham, NC 27708, USA conitzer@cs.duke.edu Toby Walsh NICTA and UNSW Sydney,
Complexity of Unweighted Coalitional Manipulation Under Some Common Voting Rules
 Complexity of Unweighted Coalitional Manipulation Under Some Common Voting Rules Lirong Xia Michael Zuckerman Ariel D. Procaccia Vincent Conitzer Jeffrey S. Rosenschein Department of Computer Science,
Complexity of Unweighted Coalitional Manipulation Under Some Common Voting Rules Lirong Xia Michael Zuckerman Ariel D. Procaccia Vincent Conitzer Jeffrey S. Rosenschein Department of Computer Science,
Game Theory: Spring 2017
 Game Theory: Spring 2017 Ulle Endriss Institute for Logic, Language and Computation University of Amsterdam Ulle Endriss 1 Plan for Today In this second lecture on mechanism design we are going to generalise
Game Theory: Spring 2017 Ulle Endriss Institute for Logic, Language and Computation University of Amsterdam Ulle Endriss 1 Plan for Today In this second lecture on mechanism design we are going to generalise
Approval Voting: Three Examples
 Approval Voting: Three Examples Francesco De Sinopoli, Bhaskar Dutta and Jean-François Laslier August, 2005 Abstract In this paper we discuss three examples of approval voting games. The first one illustrates
Approval Voting: Three Examples Francesco De Sinopoli, Bhaskar Dutta and Jean-François Laslier August, 2005 Abstract In this paper we discuss three examples of approval voting games. The first one illustrates
Recap Social Choice Fun Game Voting Paradoxes Properties. Social Choice. Lecture 11. Social Choice Lecture 11, Slide 1
 Social Choice Lecture 11 Social Choice Lecture 11, Slide 1 Lecture Overview 1 Recap 2 Social Choice 3 Fun Game 4 Voting Paradoxes 5 Properties Social Choice Lecture 11, Slide 2 Formal Definition Definition
Social Choice Lecture 11 Social Choice Lecture 11, Slide 1 Lecture Overview 1 Recap 2 Social Choice 3 Fun Game 4 Voting Paradoxes 5 Properties Social Choice Lecture 11, Slide 2 Formal Definition Definition
CPS 173 Mechanism design. Vincent Conitzer
 CPS 173 Mechanism design Vincent Conitzer conitzer@cs.duke.edu edu Mechanism design: setting The center has a set of outcomes O that she can choose from Allocations of tasks/resources, joint plans, Each
CPS 173 Mechanism design Vincent Conitzer conitzer@cs.duke.edu edu Mechanism design: setting The center has a set of outcomes O that she can choose from Allocations of tasks/resources, joint plans, Each
Equilibrium Refinement through Negotiation in Binary Voting
 Proceedings of the Twenty-Fourth International Joint Conference on Artificial Intelligence (IJCAI 2015) Equilibrium Refinement through Negotiation in Binary Voting Umberto Grandi University of Toulouse
Proceedings of the Twenty-Fourth International Joint Conference on Artificial Intelligence (IJCAI 2015) Equilibrium Refinement through Negotiation in Binary Voting Umberto Grandi University of Toulouse
Possible Winners When New Alternatives Join: New Results Coming Up!
 Possible Winners When New Alternatives Join: New Results Coming Up! Lirong Xia Dept. of Computer Science Duke University Durham, NC 7708, USA lxia@cs.duke.edu Jérôme Lang Jérôme Monnot LAMSADE Université
Possible Winners When New Alternatives Join: New Results Coming Up! Lirong Xia Dept. of Computer Science Duke University Durham, NC 7708, USA lxia@cs.duke.edu Jérôme Lang Jérôme Monnot LAMSADE Université
13 Social choice B = 2 X X. is the collection of all binary relations on X. R = { X X : is complete and transitive}
 13 Social choice So far, all of our models involved a single decision maker. An important, perhaps the important, question for economics is whether the desires and wants of various agents can be rationally
13 Social choice So far, all of our models involved a single decision maker. An important, perhaps the important, question for economics is whether the desires and wants of various agents can be rationally
"Arrow s Theorem and the Gibbard-Satterthwaite Theorem: A Unified Approach", by Phillip Reny. Economic Letters (70) (2001),
 February 25, 2015 "Arrow s Theorem and the Gibbard-Satterthwaite Theorem: A Unified Approach", by Phillip Reny. Economic Letters (70) (2001), 99-105. Also recommended: M. A. Satterthwaite, "Strategy-Proof
February 25, 2015 "Arrow s Theorem and the Gibbard-Satterthwaite Theorem: A Unified Approach", by Phillip Reny. Economic Letters (70) (2001), 99-105. Also recommended: M. A. Satterthwaite, "Strategy-Proof
Social Choice and Mechanism Design - Part I.2. Part I.2: Social Choice Theory Summer Term 2011
 Social Choice and Mechanism Design Part I.2: Social Choice Theory Summer Term 2011 Alexander Westkamp April 2011 Introduction Two concerns regarding our previous approach to collective decision making:
Social Choice and Mechanism Design Part I.2: Social Choice Theory Summer Term 2011 Alexander Westkamp April 2011 Introduction Two concerns regarding our previous approach to collective decision making:
Approximation algorithms and mechanism design for minimax approval voting
 Approximation algorithms and mechanism design for minimax approval voting Ioannis Caragiannis Dimitris Kalaitzis University of Patras Vangelis Markakis Athens University of Economics and Business Outline
Approximation algorithms and mechanism design for minimax approval voting Ioannis Caragiannis Dimitris Kalaitzis University of Patras Vangelis Markakis Athens University of Economics and Business Outline
Teams in Online Scheduling Polls: Game-Theoretic Aspects
 Proceedings of the Thirty-First AAAI Conference on Artificial Intelligence (AAAI-17) Teams in Online Scheduling Polls: Game-Theoretic Aspects Robert Bredereck, 1 Jiehua Chen, 2 Rolf Niedermeier 2 1 University
Proceedings of the Thirty-First AAAI Conference on Artificial Intelligence (AAAI-17) Teams in Online Scheduling Polls: Game-Theoretic Aspects Robert Bredereck, 1 Jiehua Chen, 2 Rolf Niedermeier 2 1 University
Finite Dictatorships and Infinite Democracies
 Finite Dictatorships and Infinite Democracies Iian B. Smythe October 20, 2015 Abstract Does there exist a reasonable method of voting that when presented with three or more alternatives avoids the undue
Finite Dictatorships and Infinite Democracies Iian B. Smythe October 20, 2015 Abstract Does there exist a reasonable method of voting that when presented with three or more alternatives avoids the undue
Probabilistic Possible Winner Determination
 Probabilistic Possible Winner Determination Yoram Bachrach Microsoft Research Ltd. Cambridge, UK Nadja Betzler Institut für Informatik Friedrich-Schiller-Universität Jena Jena, Germany Piotr Faliszewski
Probabilistic Possible Winner Determination Yoram Bachrach Microsoft Research Ltd. Cambridge, UK Nadja Betzler Institut für Informatik Friedrich-Schiller-Universität Jena Jena, Germany Piotr Faliszewski
Ties Matter: Complexity of Manipulation when Tie-breaking with a Random Vote
 Ties Matter: Complexity of Manipulation when Tie-breaking with a Random Vote Haris Aziz, Serge Gaspers, Nicholas Mattei, Nina Narodytska, and Toby Walsh NICTA and UNSW Sydney, Australia {haris.aziz, serge.gaspers,
Ties Matter: Complexity of Manipulation when Tie-breaking with a Random Vote Haris Aziz, Serge Gaspers, Nicholas Mattei, Nina Narodytska, and Toby Walsh NICTA and UNSW Sydney, Australia {haris.aziz, serge.gaspers,
Mechanism Design for Bounded Agents
 Chapter 8 Mechanism Design for Bounded Agents Any fool can tell the truth, but it requires a man of some sense to know how to lie well. Samuel Butler Mechanism design has traditionally taken the conservative
Chapter 8 Mechanism Design for Bounded Agents Any fool can tell the truth, but it requires a man of some sense to know how to lie well. Samuel Butler Mechanism design has traditionally taken the conservative
Complexity of Shift Bribery in Hare, Coombs, Baldwin, and Nanson Elections
 Complexity of Shift Bribery in Hare, Coombs, Baldwin, and Nanson Elections Cynthia Maushagen, Marc Neveling, Jörg Rothe, and Ann-Kathrin Selker Institut für Informatik Heinrich-Heine-Universität Düsseldorf
Complexity of Shift Bribery in Hare, Coombs, Baldwin, and Nanson Elections Cynthia Maushagen, Marc Neveling, Jörg Rothe, and Ann-Kathrin Selker Institut für Informatik Heinrich-Heine-Universität Düsseldorf
Repeated Downsian Electoral Competition
 Repeated Downsian Electoral Competition John Duggan Department of Political Science and Department of Economics University of Rochester Mark Fey Department of Political Science University of Rochester
Repeated Downsian Electoral Competition John Duggan Department of Political Science and Department of Economics University of Rochester Mark Fey Department of Political Science University of Rochester
Volume 31, Issue 1. Manipulation of the Borda rule by introduction of a similar candidate. Jérôme Serais CREM UMR 6211 University of Caen
 Volume 31, Issue 1 Manipulation of the Borda rule by introduction of a similar candidate Jérôme Serais CREM UMR 6211 University of Caen Abstract In an election contest, a losing candidate a can manipulate
Volume 31, Issue 1 Manipulation of the Borda rule by introduction of a similar candidate Jérôme Serais CREM UMR 6211 University of Caen Abstract In an election contest, a losing candidate a can manipulate
Introduction to Game Theory Lecture Note 2: Strategic-Form Games and Nash Equilibrium (2)
 Introduction to Game Theory Lecture Note 2: Strategic-Form Games and Nash Equilibrium (2) Haifeng Huang University of California, Merced Best response functions: example In simple games we can examine
Introduction to Game Theory Lecture Note 2: Strategic-Form Games and Nash Equilibrium (2) Haifeng Huang University of California, Merced Best response functions: example In simple games we can examine
Mechanism Design for Multiagent Systems
 Mechanism Design for Multiagent Systems Vincent Conitzer Assistant Professor of Computer Science and Economics Duke University conitzer@cs.duke.edu Introduction Often, decisions must be taken based on
Mechanism Design for Multiagent Systems Vincent Conitzer Assistant Professor of Computer Science and Economics Duke University conitzer@cs.duke.edu Introduction Often, decisions must be taken based on
CMU Social choice: Advanced manipulation. Teachers: Avrim Blum Ariel Procaccia (this time)
 CMU 15-896 Social choice: Advanced manipulation Teachers: Avrim Blum Ariel Procaccia (this time) Recap A Complexity-theoretic barrier to manipulation Polynomial-time greedy alg can successfully decide
CMU 15-896 Social choice: Advanced manipulation Teachers: Avrim Blum Ariel Procaccia (this time) Recap A Complexity-theoretic barrier to manipulation Polynomial-time greedy alg can successfully decide
Social Dichotomy Functions (extended abstract)
 Social Dichotomy Functions (extended abstract) Conal Duddy, Nicolas Houy, Jérôme Lang, Ashley Piggins, and William S. Zwicker February 22, 2014 1 What is a Social Dichotomy Function? A dichotomy A = (A
Social Dichotomy Functions (extended abstract) Conal Duddy, Nicolas Houy, Jérôme Lang, Ashley Piggins, and William S. Zwicker February 22, 2014 1 What is a Social Dichotomy Function? A dichotomy A = (A
Possible Winners when New Candidates Are Added: The Case of Scoring Rules
 Proceedings of the Twenty-Fourth AAAI Conference on Artificial Intelligence (AAAI-0) Possible Winners when New Candidates Are Added: The Case of Scoring Rules Yann Chevaleyre and Jérôme Lang and Nicolas
Proceedings of the Twenty-Fourth AAAI Conference on Artificial Intelligence (AAAI-0) Possible Winners when New Candidates Are Added: The Case of Scoring Rules Yann Chevaleyre and Jérôme Lang and Nicolas
A Borda Count for Collective Sentiment Analysis
 A Borda Count for Collective Sentiment Analysis Umberto Grandi Department of Mathematics University of Padova 10 February 2014 Joint work with Andrea Loreggia (Univ. Padova), Francesca Rossi (Univ. Padova)
A Borda Count for Collective Sentiment Analysis Umberto Grandi Department of Mathematics University of Padova 10 February 2014 Joint work with Andrea Loreggia (Univ. Padova), Francesca Rossi (Univ. Padova)
Possible and necessary winners in voting trees: majority graphs vs. profiles
 Possible and necessary winners in voting trees: majority graphs vs. profiles Maria Silvia Pini University of Padova Padova, Italy mpini@math.unipd.it Francesca Rossi University of Padova Padova, Italy
Possible and necessary winners in voting trees: majority graphs vs. profiles Maria Silvia Pini University of Padova Padova, Italy mpini@math.unipd.it Francesca Rossi University of Padova Padova, Italy
arxiv: v1 [cs.gt] 29 Mar 2014
![arxiv: v1 [cs.gt] 29 Mar 2014 arxiv: v1 [cs.gt] 29 Mar 2014](/thumbs/86/93672035.jpg) Testing Top Monotonicity Haris Aziz NICTA and UNSW Australia, Kensington 2033, Australia arxiv:1403.7625v1 [cs.gt] 29 Mar 2014 Abstract Top monotonicity is a relaxation of various well-known domain restrictions
Testing Top Monotonicity Haris Aziz NICTA and UNSW Australia, Kensington 2033, Australia arxiv:1403.7625v1 [cs.gt] 29 Mar 2014 Abstract Top monotonicity is a relaxation of various well-known domain restrictions
Multiwinner Elections Under Preferences that Are Single-Peaked on a Tree
 Proceedings of the Twenty-Third International Joint Conference on Artificial Intelligence Multiwinner Elections Under Preferences that Are Single-Peaked on a Tree Lan Yu 1, Hau Chan 2, and Edith Elkind
Proceedings of the Twenty-Third International Joint Conference on Artificial Intelligence Multiwinner Elections Under Preferences that Are Single-Peaked on a Tree Lan Yu 1, Hau Chan 2, and Edith Elkind
On the Dimensionality of Voting Games
 Proceedings of the Twenty-Third AAAI Conference on Artificial Intelligence (2008) On the Dimensionality of Voting Games Edith Elkind Electronics & Computer Science University of Southampton Southampton
Proceedings of the Twenty-Third AAAI Conference on Artificial Intelligence (2008) On the Dimensionality of Voting Games Edith Elkind Electronics & Computer Science University of Southampton Southampton
Lower Bound Issues in Computational Social Choice
 Lower Bound Issues in Computational Social Choice Rolf Niedermeier Fakultät IV, Institut für Softwaretechnik und Theoretische Informatik, TU Berlin www.akt.tu-berlin.de Rolf Niedermeier (TU Berlin) Lower
Lower Bound Issues in Computational Social Choice Rolf Niedermeier Fakultät IV, Institut für Softwaretechnik und Theoretische Informatik, TU Berlin www.akt.tu-berlin.de Rolf Niedermeier (TU Berlin) Lower
The Axiomatic Method in Social Choice Theory:
 The Axiomatic Method in Social Choice Theory: Preference Aggregation, Judgment Aggregation, Graph Aggregation Ulle Endriss Institute for Logic, Language and Computation University of Amsterdam Ulle Endriss
The Axiomatic Method in Social Choice Theory: Preference Aggregation, Judgment Aggregation, Graph Aggregation Ulle Endriss Institute for Logic, Language and Computation University of Amsterdam Ulle Endriss
Improved Heuristic for Manipulation of Second-order Copeland Elections
 EPiC Series in Computing Volume 50, 017, Pages 16 174 GCAI 017. 3rd Global Conference on Artificial Intelligence Improved Heuristic for Manipulation of Second-order Copeland Elections Ramoni O. Lasisi
EPiC Series in Computing Volume 50, 017, Pages 16 174 GCAI 017. 3rd Global Conference on Artificial Intelligence Improved Heuristic for Manipulation of Second-order Copeland Elections Ramoni O. Lasisi
Economics Bulletin, 2012, Vol. 32 No. 1 pp Introduction. 2. The preliminaries
 1. Introduction In this paper we reconsider the problem of axiomatizing scoring rules. Early results on this problem are due to Smith (1973) and Young (1975). They characterized social welfare and social
1. Introduction In this paper we reconsider the problem of axiomatizing scoring rules. Early results on this problem are due to Smith (1973) and Young (1975). They characterized social welfare and social
What do you do when you can t use money to solve your problems?
 Markets without money What do you do when you can t use money to solve your problems? Matching: heterosexual men and women marrying in a small town, students matching to universities, workers to jobs where
Markets without money What do you do when you can t use money to solve your problems? Matching: heterosexual men and women marrying in a small town, students matching to universities, workers to jobs where
Game Theory and Algorithms Lecture 2: Nash Equilibria and Examples
 Game Theory and Algorithms Lecture 2: Nash Equilibria and Examples February 24, 2011 Summary: We introduce the Nash Equilibrium: an outcome (action profile) which is stable in the sense that no player
Game Theory and Algorithms Lecture 2: Nash Equilibria and Examples February 24, 2011 Summary: We introduce the Nash Equilibrium: an outcome (action profile) which is stable in the sense that no player
Complexity of Winner Determination and Strategic Manipulation in Judgment Aggregation
 Complexity of Winner Determination and Strategic Manipulation in Judgment Aggregation Ulle Endriss, Umberto Grandi and Daniele Porello Abstract Judgment aggregation is an area of social choice theory that
Complexity of Winner Determination and Strategic Manipulation in Judgment Aggregation Ulle Endriss, Umberto Grandi and Daniele Porello Abstract Judgment aggregation is an area of social choice theory that
Introduction to Formal Epistemology Lecture 5
 Introduction to Formal Epistemology Lecture 5 Eric Pacuit and Rohit Parikh August 17, 2007 Eric Pacuit and Rohit Parikh: Introduction to Formal Epistemology, Lecture 5 1 Plan for the Course Introduction,
Introduction to Formal Epistemology Lecture 5 Eric Pacuit and Rohit Parikh August 17, 2007 Eric Pacuit and Rohit Parikh: Introduction to Formal Epistemology, Lecture 5 1 Plan for the Course Introduction,
A Note on the McKelvey Uncovered Set and Pareto Optimality
 Noname manuscript No. (will be inserted by the editor) A Note on the McKelvey Uncovered Set and Pareto Optimality Felix Brandt Christian Geist Paul Harrenstein Received: date / Accepted: date Abstract
Noname manuscript No. (will be inserted by the editor) A Note on the McKelvey Uncovered Set and Pareto Optimality Felix Brandt Christian Geist Paul Harrenstein Received: date / Accepted: date Abstract
Fault Tolerant Implementation
 Review of Economic Studies (2002) 69, 589 610 0034-6527/02/00230589$02.00 c 2002 The Review of Economic Studies Limited Fault Tolerant Implementation KFIR ELIAZ New York University First version received
Review of Economic Studies (2002) 69, 589 610 0034-6527/02/00230589$02.00 c 2002 The Review of Economic Studies Limited Fault Tolerant Implementation KFIR ELIAZ New York University First version received
How Credible is the Prediction of a Party-Based Election?
 How Credible is the Prediction of a Party-Based Election? Jiong Guo Shandong University School of Computer Science and Technology SunHua Road 1500, 250101 Jinan, China. jguo@mmci.unisaarland.de Yash Raj
How Credible is the Prediction of a Party-Based Election? Jiong Guo Shandong University School of Computer Science and Technology SunHua Road 1500, 250101 Jinan, China. jguo@mmci.unisaarland.de Yash Raj
Recognizing Top-Monotonic Preference Profiles in Polynomial Time
 Recognizing Top-Monotonic Preference Profiles in Polynomial Time Krzysztof Magiera and Piotr Faliszewski AGH University, Krakow, Poland krzys.magiera@gmail.com, faliszew@agh.edu.pl Abstract We provide
Recognizing Top-Monotonic Preference Profiles in Polynomial Time Krzysztof Magiera and Piotr Faliszewski AGH University, Krakow, Poland krzys.magiera@gmail.com, faliszew@agh.edu.pl Abstract We provide
Survey of Voting Procedures and Paradoxes
 Survey of Voting Procedures and Paradoxes Stanford University ai.stanford.edu/ epacuit/lmh Fall, 2008 :, 1 The Voting Problem Given a (finite) set X of candidates and a (finite) set A of voters each of
Survey of Voting Procedures and Paradoxes Stanford University ai.stanford.edu/ epacuit/lmh Fall, 2008 :, 1 The Voting Problem Given a (finite) set X of candidates and a (finite) set A of voters each of
Coalitionally strategyproof functions depend only on the most-preferred alternatives.
 Coalitionally strategyproof functions depend only on the most-preferred alternatives. H. Reiju Mihara reiju@ec.kagawa-u.ac.jp Economics, Kagawa University, Takamatsu, 760-8523, Japan April, 1999 [Social
Coalitionally strategyproof functions depend only on the most-preferred alternatives. H. Reiju Mihara reiju@ec.kagawa-u.ac.jp Economics, Kagawa University, Takamatsu, 760-8523, Japan April, 1999 [Social
Game Theory: Spring 2017
 Game Theory: Spring 207 Ulle Endriss Institute for Logic, Language and Computation University of Amsterdam Ulle Endriss Plan for Today We have seen that every normal-form game has a Nash equilibrium, although
Game Theory: Spring 207 Ulle Endriss Institute for Logic, Language and Computation University of Amsterdam Ulle Endriss Plan for Today We have seen that every normal-form game has a Nash equilibrium, although
Approximate Nash Equilibria with Near Optimal Social Welfare
 Proceedings of the Twenty-Fourth International Joint Conference on Artificial Intelligence (IJCAI 015) Approximate Nash Equilibria with Near Optimal Social Welfare Artur Czumaj, Michail Fasoulakis, Marcin
Proceedings of the Twenty-Fourth International Joint Conference on Artificial Intelligence (IJCAI 015) Approximate Nash Equilibria with Near Optimal Social Welfare Artur Czumaj, Michail Fasoulakis, Marcin
Group Activity Selection on Social Networks
 Proceedings of the Thirty-First AAAI Conference on Artificial Intelligence (AAAI-17) Group Activity Selection on Social Networks Ayumi Igarashi, Dominik Peters, Edith Elkind Department of Computer Science
Proceedings of the Thirty-First AAAI Conference on Artificial Intelligence (AAAI-17) Group Activity Selection on Social Networks Ayumi Igarashi, Dominik Peters, Edith Elkind Department of Computer Science
Sequential Bidding in the Bailey-Cavallo Mechanism
 Sequential Bidding in the Bailey-Cavallo Mechanism Krzysztof R. Apt 1,2 and Evangelos Markakis 2 1 CWI, Science Park 123, 1098 XG Amsterdam 2 Institute of Logic, Language and Computation, University of
Sequential Bidding in the Bailey-Cavallo Mechanism Krzysztof R. Apt 1,2 and Evangelos Markakis 2 1 CWI, Science Park 123, 1098 XG Amsterdam 2 Institute of Logic, Language and Computation, University of
Clone Structures in Voters Preferences
 Clone Structures in Voters Preferences Edith Elkind 1, Piotr Faliszewski 2, and Arkadii Slinko 3 1 School of Physical and Math. Sciences, Nanyang Tech. Univ., Singapore 2 AGH University of Science and
Clone Structures in Voters Preferences Edith Elkind 1, Piotr Faliszewski 2, and Arkadii Slinko 3 1 School of Physical and Math. Sciences, Nanyang Tech. Univ., Singapore 2 AGH University of Science and
Matching Theory. Mihai Manea. Based on slides by Fuhito Kojima. MIT
 Matching Theory Mihai Manea MIT Based on slides by Fuhito Kojima. Market Design Traditional economics focuses mostly on decentralized markets. Recently, economists are helping to design economic institutions
Matching Theory Mihai Manea MIT Based on slides by Fuhito Kojima. Market Design Traditional economics focuses mostly on decentralized markets. Recently, economists are helping to design economic institutions
Single-peaked consistency and its complexity
 Bruno Escoffier, Jérôme Lang, Meltem Öztürk Abstract A common way of dealing with the paradoxes of preference aggregation consists in restricting the domain of admissible preferences. The most well-known
Bruno Escoffier, Jérôme Lang, Meltem Öztürk Abstract A common way of dealing with the paradoxes of preference aggregation consists in restricting the domain of admissible preferences. The most well-known
Lower Bound Issues in Computational Social Choice
 Lower Bound Issues in Computational Social Choice Rolf Niedermeier Fakultät IV, Institut für Softwaretechnik und Theoretische Informatik, TU Berlin www.akt.tu-berlin.de Rolf Niedermeier (TU Berlin) Lower
Lower Bound Issues in Computational Social Choice Rolf Niedermeier Fakultät IV, Institut für Softwaretechnik und Theoretische Informatik, TU Berlin www.akt.tu-berlin.de Rolf Niedermeier (TU Berlin) Lower
Approval Voting for Committees: Threshold Approaches
 Approval Voting for Committees: Threshold Approaches Peter Fishburn Aleksandar Pekeč WORKING DRAFT PLEASE DO NOT CITE WITHOUT PERMISSION Abstract When electing a committee from the pool of individual candidates,
Approval Voting for Committees: Threshold Approaches Peter Fishburn Aleksandar Pekeč WORKING DRAFT PLEASE DO NOT CITE WITHOUT PERMISSION Abstract When electing a committee from the pool of individual candidates,
Political Economy of Institutions and Development. Lectures 2 and 3: Static Voting Models
 14.773 Political Economy of Institutions and Development. Lectures 2 and 3: Static Voting Models Daron Acemoglu MIT February 7 and 12, 2013. Daron Acemoglu (MIT) Political Economy Lectures 2 and 3 February
14.773 Political Economy of Institutions and Development. Lectures 2 and 3: Static Voting Models Daron Acemoglu MIT February 7 and 12, 2013. Daron Acemoglu (MIT) Political Economy Lectures 2 and 3 February
Computational Aspects of Strategic Behaviour in Elections with Top-Truncated Ballots
 Computational Aspects of Strategic Behaviour in Elections with Top-Truncated Ballots by Vijay Menon A thesis presented to the University of Waterloo in fulfillment of the thesis requirement for the degree
Computational Aspects of Strategic Behaviour in Elections with Top-Truncated Ballots by Vijay Menon A thesis presented to the University of Waterloo in fulfillment of the thesis requirement for the degree
SYSU Lectures on the Theory of Aggregation Lecture 2: Binary Aggregation with Integrity Constraints
 SYSU Lectures on the Theory of Aggregation Lecture 2: Binary Aggregation with Integrity Constraints Ulle Endriss Institute for Logic, Language and Computation University of Amsterdam [ http://www.illc.uva.nl/~ulle/sysu-2014/
SYSU Lectures on the Theory of Aggregation Lecture 2: Binary Aggregation with Integrity Constraints Ulle Endriss Institute for Logic, Language and Computation University of Amsterdam [ http://www.illc.uva.nl/~ulle/sysu-2014/
Thema Working Paper n Université de Cergy Pontoise, France
 Thema Working Paper n 2010-02 Université de Cergy Pontoise, France Sincere Scoring Rules Nunez Matias May, 2010 Sincere Scoring Rules Matías Núñez May 2010 Abstract Approval Voting is shown to be the unique
Thema Working Paper n 2010-02 Université de Cergy Pontoise, France Sincere Scoring Rules Nunez Matias May, 2010 Sincere Scoring Rules Matías Núñez May 2010 Abstract Approval Voting is shown to be the unique
Strategic Behavior when Allocating Indivisible Goods Sequentially
 Strategic Behavior when Allocating Indivisible Goods Sequentially Thomas Kalinowski University of Rostock Germany Nina Narodytska and Toby Walsh NICTA and UNSW Australia Lirong Xia CRCS, Harvard University
Strategic Behavior when Allocating Indivisible Goods Sequentially Thomas Kalinowski University of Rostock Germany Nina Narodytska and Toby Walsh NICTA and UNSW Australia Lirong Xia CRCS, Harvard University
Mechanism Design without Money
 Mechanism Design without Money MSc Thesis (Afstudeerscriptie) written by Sylvia Boicheva (born December 27th, 1986 in Sofia, Bulgaria) under the supervision of Prof Dr Krzysztof Apt, and submitted to the
Mechanism Design without Money MSc Thesis (Afstudeerscriptie) written by Sylvia Boicheva (born December 27th, 1986 in Sofia, Bulgaria) under the supervision of Prof Dr Krzysztof Apt, and submitted to the
Incentive-Compatible Voting Rules with Positively Correlated Beliefs
 Incentive-Compatible Voting Rules with Positively Correlated Beliefs Mohit Bhargava, Dipjyoti Majumdar and Arunava Sen August 13, 2014 Abstract We study the consequences of positive correlation of beliefs
Incentive-Compatible Voting Rules with Positively Correlated Beliefs Mohit Bhargava, Dipjyoti Majumdar and Arunava Sen August 13, 2014 Abstract We study the consequences of positive correlation of beliefs
Participation Incentives in Randomized Social Choice
 Participation Incentives in Randomized Social Choice Haris Aziz Data61 and UNSW, Sydney, Australia arxiv:1602.02174v2 [cs.gt] 8 Nov 2016 Abstract When aggregating preferences of agents via voting, two
Participation Incentives in Randomized Social Choice Haris Aziz Data61 and UNSW, Sydney, Australia arxiv:1602.02174v2 [cs.gt] 8 Nov 2016 Abstract When aggregating preferences of agents via voting, two
The Condorcet Jur(ies) Theorem
 The Condorcet Jur(ies) Theorem David S. Ahn University of California, Berkeley Santiago Oliveros Haas School of Business, UC Berkeley September 2010 Abstract Two issues can be decided in a single election
The Condorcet Jur(ies) Theorem David S. Ahn University of California, Berkeley Santiago Oliveros Haas School of Business, UC Berkeley September 2010 Abstract Two issues can be decided in a single election
EC3224 Autumn Lecture #03 Applications of Nash Equilibrium
 Reading EC3224 Autumn Lecture #03 Applications of Nash Equilibrium Osborne Chapter 3 By the end of this week you should be able to: apply Nash equilibrium to oligopoly games, voting games and other examples.
Reading EC3224 Autumn Lecture #03 Applications of Nash Equilibrium Osborne Chapter 3 By the end of this week you should be able to: apply Nash equilibrium to oligopoly games, voting games and other examples.
CONNECTING PAIRWISE AND POSITIONAL ELECTION OUTCOMES
 CONNECTING PAIRWISE AND POSITIONAL ELECTION OUTCOMES DONALD G SAARI AND TOMAS J MCINTEE INSTITUTE FOR MATHEMATICAL BEHAVIORAL SCIENCE UNIVERSITY OF CALIFORNIA, IRVINE, CA 9697-5100 Abstract General conclusions
CONNECTING PAIRWISE AND POSITIONAL ELECTION OUTCOMES DONALD G SAARI AND TOMAS J MCINTEE INSTITUTE FOR MATHEMATICAL BEHAVIORAL SCIENCE UNIVERSITY OF CALIFORNIA, IRVINE, CA 9697-5100 Abstract General conclusions
14.770: Introduction to Political Economy Lectures 1 and 2: Collective Choice and Voting
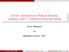 14.770: Introduction to Political Economy Lectures 1 and 2: Collective Choice and Voting Daron Acemoglu MIT September 6 and 11, 2017. Daron Acemoglu (MIT) Political Economy Lectures 1 and 2 September 6
14.770: Introduction to Political Economy Lectures 1 and 2: Collective Choice and Voting Daron Acemoglu MIT September 6 and 11, 2017. Daron Acemoglu (MIT) Political Economy Lectures 1 and 2 September 6
Maximin Share Allocations on Cycles
 Maximin Share Allocations on Cycles Zbigniew Lonc 1, Miroslaw Truszczynski 2 1 Warsaw University of Technology, Poland 2 University of Kentucky, USA zblonc@mini.pw.edu.pl, mirek@cs.uky.edu Abstract The
Maximin Share Allocations on Cycles Zbigniew Lonc 1, Miroslaw Truszczynski 2 1 Warsaw University of Technology, Poland 2 University of Kentucky, USA zblonc@mini.pw.edu.pl, mirek@cs.uky.edu Abstract The
Anyone But Them: The Complexity Challenge for A Resolute Election Controller
 Anyone But Them: The Complexity Challenge for A Resolute Election Controller Yongjie Yang 1 School of Information Science and Engineering Central South University, Changsha, China 2 Chair of Economic Theory
Anyone But Them: The Complexity Challenge for A Resolute Election Controller Yongjie Yang 1 School of Information Science and Engineering Central South University, Changsha, China 2 Chair of Economic Theory
Normal-form games. Vincent Conitzer
 Normal-form games Vincent Conitzer conitzer@cs.duke.edu 2/3 of the average game Everyone writes down a number between 0 and 100 Person closest to 2/3 of the average wins Example: A says 50 B says 10 C
Normal-form games Vincent Conitzer conitzer@cs.duke.edu 2/3 of the average game Everyone writes down a number between 0 and 100 Person closest to 2/3 of the average wins Example: A says 50 B says 10 C
NASH IMPLEMENTATION USING SIMPLE MECHANISMS WITHOUT UNDESIRABLE MIXED-STRATEGY EQUILIBRIA
 NASH IMPLEMENTATION USING SIMPLE MECHANISMS WITHOUT UNDESIRABLE MIXED-STRATEGY EQUILIBRIA MARIA GOLTSMAN Abstract. This note shows that, in separable environments, any monotonic social choice function
NASH IMPLEMENTATION USING SIMPLE MECHANISMS WITHOUT UNDESIRABLE MIXED-STRATEGY EQUILIBRIA MARIA GOLTSMAN Abstract. This note shows that, in separable environments, any monotonic social choice function
Antonio Quesada Universidad de Murcia. Abstract
 From social choice functions to dictatorial social welfare functions Antonio Quesada Universidad de Murcia Abstract A procedure to construct a social welfare function from a social choice function is suggested
From social choice functions to dictatorial social welfare functions Antonio Quesada Universidad de Murcia Abstract A procedure to construct a social welfare function from a social choice function is suggested
Matching. Terence Johnson. April 17, University of Notre Dame. Terence Johnson (ND) Matching April 17, / 41
 Matching Terence Johnson University of Notre Dame April 17, 2018 Terence Johnson (ND) Matching April 17, 2018 1 / 41 Markets without money What do you do when you can t use money to solve your problems?
Matching Terence Johnson University of Notre Dame April 17, 2018 Terence Johnson (ND) Matching April 17, 2018 1 / 41 Markets without money What do you do when you can t use money to solve your problems?
We set up the basic model of two-sided, one-to-one matching
 Econ 805 Advanced Micro Theory I Dan Quint Fall 2009 Lecture 18 To recap Tuesday: We set up the basic model of two-sided, one-to-one matching Two finite populations, call them Men and Women, who want to
Econ 805 Advanced Micro Theory I Dan Quint Fall 2009 Lecture 18 To recap Tuesday: We set up the basic model of two-sided, one-to-one matching Two finite populations, call them Men and Women, who want to
Strategy-Proofness on the Condorcet Domain
 College of William and Mary W&M ScholarWorks Undergraduate Honors Theses Theses, Dissertations, & Master Projects 5-2008 Strategy-Proofness on the Condorcet Domain Lauren Nicole Merrill College of William
College of William and Mary W&M ScholarWorks Undergraduate Honors Theses Theses, Dissertations, & Master Projects 5-2008 Strategy-Proofness on the Condorcet Domain Lauren Nicole Merrill College of William
Points-based rules respecting a pairwise-change-symmetric ordering
 Points-based rules respecting a pairwise-change-symmetric ordering AMS Special Session on Voting Theory Karl-Dieter Crisman, Gordon College January 7th, 2008 A simple idea Our usual representations of
Points-based rules respecting a pairwise-change-symmetric ordering AMS Special Session on Voting Theory Karl-Dieter Crisman, Gordon College January 7th, 2008 A simple idea Our usual representations of
Non-Manipulable Domains for the Borda Count
 Non-Manipulable Domains for the Borda Count Martin Barbie, Clemens Puppe * Department of Economics, University of Karlsruhe D 76128 Karlsruhe, Germany and Attila Tasnádi ** Department of Mathematics, Budapest
Non-Manipulable Domains for the Borda Count Martin Barbie, Clemens Puppe * Department of Economics, University of Karlsruhe D 76128 Karlsruhe, Germany and Attila Tasnádi ** Department of Mathematics, Budapest
arxiv: v1 [cs.gt] 1 May 2017
![arxiv: v1 [cs.gt] 1 May 2017 arxiv: v1 [cs.gt] 1 May 2017](/thumbs/86/93671889.jpg) Rank Maximal Equal Contribution: a Probabilistic Social Choice Function Haris Aziz and Pang Luo and Christine Rizkallah arxiv:1705.00544v1 [cs.gt] 1 May 2017 1 Data61, CSIRO and UNSW, Sydney, NSW 2033,
Rank Maximal Equal Contribution: a Probabilistic Social Choice Function Haris Aziz and Pang Luo and Christine Rizkallah arxiv:1705.00544v1 [cs.gt] 1 May 2017 1 Data61, CSIRO and UNSW, Sydney, NSW 2033,
arxiv: v1 [cs.gt] 10 Apr 2018
![arxiv: v1 [cs.gt] 10 Apr 2018 arxiv: v1 [cs.gt] 10 Apr 2018](/thumbs/95/125856574.jpg) Individual and Group Stability in Neutral Restrictions of Hedonic Games Warut Suksompong Department of Computer Science, Stanford University 353 Serra Mall, Stanford, CA 94305, USA warut@cs.stanford.edu
Individual and Group Stability in Neutral Restrictions of Hedonic Games Warut Suksompong Department of Computer Science, Stanford University 353 Serra Mall, Stanford, CA 94305, USA warut@cs.stanford.edu
Arrow s Paradox. Prerna Nadathur. January 1, 2010
 Arrow s Paradox Prerna Nadathur January 1, 2010 Abstract In this paper, we examine the problem of a ranked voting system and introduce Kenneth Arrow s impossibility theorem (1951). We provide a proof sketch
Arrow s Paradox Prerna Nadathur January 1, 2010 Abstract In this paper, we examine the problem of a ranked voting system and introduce Kenneth Arrow s impossibility theorem (1951). We provide a proof sketch
Facility Location with Variable and Dynamic Populations
 Facility Location with Variable and Dynamic Populations Yuho Wada, Tomohiro Ono, Taiki Todo, and Makoto Yokoo Dept. Informatics, Kyushu University Fukuoka, Japan {wada@agent., ono@agent., todo@, yokoo@}inf.kyushu-u.ac.jp
Facility Location with Variable and Dynamic Populations Yuho Wada, Tomohiro Ono, Taiki Todo, and Makoto Yokoo Dept. Informatics, Kyushu University Fukuoka, Japan {wada@agent., ono@agent., todo@, yokoo@}inf.kyushu-u.ac.jp
