The Small-World Phenomenon: An Algorithmic Perspective
|
|
|
- Ralf Watson
- 6 years ago
- Views:
Transcription
1 The Small-World Phenomenon: An Algorithmic Perspective Jon Kleinberg Abstract Long a matter of folklore, the small-world phenomenon the principle that we are all linked by short chains of acquaintances was inaugurated as an area of experimental study in the social sciences through the pioneering work of Stanley Milgram in the 1960 s. This work was among the first to make the phenomenon quantitative, allowing people to speak of the six degrees of separation between any two people in the United States. Since then, a number of network models have been proposed as frameworks in which to study the problem analytically. One of the most refined of these models was formulated in recent work of Watts and Strogatz; their framework provided compelling evidence that the small-world phenomenon is pervasive in a range of networks arising in nature and technology, and a fundamental ingredient in the evolution of the World Wide Web. But existing models are insufficient to explain the striking algorithmic component of Milgram s original findings: that individuals using local information are collectively very effective at actually constructing short paths between two points in a social network. Although recently proposed network models are rich in short paths, we prove that no decentralized algorithm, operating with local information only, can construct short paths in these networks with non-negligible probability. We then define an infinite family of network models that naturally generalizes the Watts-Strogatz model, and show that for one of these models, there is a decentralized algorithm capable of finding short paths with high probability. More generally, we provide a strong characterization of this family of network models, showing that there is in fact a unique model within the family for which decentralized algorithms are effective. A version of this work appears as Cornell Computer Science Technical Report (October 1999). Department of Computer Science, Cornell University, Ithaca NY kleinber@cs.cornell.edu. Supported in part by a David and Lucile Packard Foundation Fellowship, an Alfred P. Sloan Research Fellowship, an ONR Young Investigator Award, and NSF Faculty Early Career Development Award CCR
2 1 Introduction The Small-World Phenomenon. A social network exhibits the small-world phenomenon if, roughly speaking, any two individuals in the network are likely to be connected through a short sequence of intermediate acquaintances. This has long been the subject of anecdotal observation and folklore; often we meet a stranger and discover that we have an acquaintance in common. It has since grown into a significant area of study in the social sciences, in large part through a series of striking experiments conducted by Stanley Milgram and his co-workers in the 1960 s [13, 18, 12]. Recent work has suggested that the phenomenon is pervasive in networks arising in nature and technology, and a fundamental ingredient in the structural evolution of the World Wide Web [17, 19, 2]. Milgram s basic small-world experiment remains one of the most compelling ways to think about the problem. The goal of the experiment was to find short chains of acquaintances linking pairs of people in the United States who did not know one another. In a typical instance of the experiment, a source person in Nebraska would be given a letter to deliver to a target person in Massachusetts. The source would initially be told basic information about the target, including his address and occupation; the source would then be instructed to send the letter to someone she knew on a first-name basis in an effort to transmit the letter to the target as efficaciously as possible. Anyone subsequently receiving the letter would be given the same instructions, and the chain of communication would continue until the target was reached. Over many trials, the average number of intermediate steps in a successful chain was found to lie between five and six, a quantity that has since entered popular culture as the six degrees of separation principle [7]. Modeling the Phenomenon. Naturally, the empirical validation of the phenomenon has led to a rash of analytical work aimed at answering the following general question: ( ) Why should there exist short chains of acquaintances linking together arbitrary pairs of strangers? Most of the early work on this issue, beginning with analysis of Pool and Kochen that pre-dated Milgram s experiments [16], was based on versions of the following explanation: random networks have low diameter. (See for example the book of surveys edited by Kochen [11].) That is, if every individual in the United States were to have a small number of acquaintances selected uniformly at random from the population and if acquaintanceship were symmetric then two random individuals would be linked by a short chain with high probability. Even this early work recognized the limitations of a uniform random model; if A and B are two individuals with a common friend, it is much more likely that they themselves are friends. But at the same time, a network of acquaintanceships that is too clustered will not have the low diameter that Milgram s experiments indicated. Recently, Watts and Strogatz proposed a model for the small-world phenomenon based on a class of random networks that interpolates between these two extremes, in which the edges of the network are divided into local and long-range contacts [19]. The paradigmatic example they studied was a re-wired ring lattice, constructed roughly as follows. One starts with a set V of n points spaced uniformly on a circle, and joins each point by an edge 2
3 to each of its k nearest neighbors, for a small constant k. These are the local contacts in the network. One then introduces a small number of edges in which the endpoints are chosen uniformly at random from V the long-range contacts. Watts and Strogatz argued that such a model captures two crucial parameters of social networks: there is a simple underlying structure that explains the presence of most edges, but a few edges are produced by a random process that does not respect this structure. Their networks thus have low diameter (like uniform random networks), but also have the property that many of the neighbors of a node u are themselves neighbors (unlike uniform random networks). They showed that a number of naturally arising networks exhibit this pair of properties (including the connections among neurons in the nematode species C. elegans, and the power grid of the Western U.S.); and their approach has been applied to the analysis of the hyperlink graph of the World Wide Web as well [1]. Networks that are formed from a superposition of a structured subgraph and a random subgraph have been investigated in the area of probabilistic combinatorics. In a fundamental instance of such an approach, Bollobás and Chung [5] gave bounds on the diameter of the random graph obtained by adding a random matching to the nodes of a cycle. (See also [6].) The Present Work. Let us return to Milgram s experiment. We claim that it really contains two fundamentally surprising discoveries: first, that such short chains should exist in the network of acquaintanceships; and second, that people should be able to find these chains knowing so little about the target individual. From an analytical point of view, the first of these discoveries is existential in nature, the second algorithmic it reveals that individuals who know only the locations of their direct acquaintances can still, collectively, construct a short path between two points in the network. We therefore propose to study the following natural companion to Question ( ) above: ( ) Why should arbitrary pairs of strangers be able to find short chains of acquaintances that link them together? It is important to note that Question ( ) raises issues that lie truly beyond the scope of Question ( ): one can imagine networks in which short chains exist, but no mechanism based on purely local information is able to find them. The success of Milgram s experiment suggests a source of latent navigational cues embedded in the underlying social network, by which a message could implicitly be guided quickly from source to target. It is natural to ask what properties a social network must possess in order for it to exhibit such cues, and enable its members to find short chains through it. In this work, we study decentralized algorithms by which individuals, knowing only the locations of their direct acquaintances, attempt to transmit a message from a source to a target along a short path. Our central findings are the following. First, we show that existing models are insufficient to explain the success of such decentralized algorithms in finding short paths through a social network. In a class of networks generated according to the model of Watts and Strogatz, we prove that there is no decentralized algorithm capable of constructing paths of small expected length (relative to the diameter of the underlying network). 3
4 A) B) v w u Figure 1: (A) A two-dimensional grid network with n = 6, p = 1, and q = 0. (B) The contacts of a node u with p = 1 and q = 2. v and w are the two long-range contacts. We then define an infinite family of random network models that naturally generalizes the Watts-Strogatz model. We show that for one of these models, there is a decentralized algorithm capable of finding short paths with high probability. Finally, we prove the stronger statement that there is in fact a unique model within the family for which decentralized algorithms are effective. The Model: Networks and Decentralized Algorithms. We now give precise definitions for our network model and our notion of a decentralized algorithm; we then provide formal statements of the main results. In designing our network model, we seek a simple framework that encapsulates the paradigm of Watts and Strogatz rich in local connections, with a few long-range connections. Rather than using a ring as the basic structure, however, we begin from a twodimensional grid and allow for edges to be directed. Thus, we begin with a set of nodes (representing individuals in the social network) that are identified with the set of lattice points in an n n square, {(i, j) : i {1, 2,..., n}, j {1, 2,..., n}}, and we define the lattice distance between two nodes (i, j) and (k, l) to be the number of lattice steps separating them: d((i, j), (k, l)) = k i + l j. For a universal constant p 1, the node u has a directed edge to every other node within lattice distance p these are its local contacts. For universal constants q 0 and r 0, we also construct directed edges from u to q other nodes (the long-range contacts) using independent random trials; the i th directed edge from u has endpoint v with probability proportional to [d(u, v)] r. (To obtain a probability distribution, we divide this quantity by the appropriate normalizing constant v[d(u, v)] r ; we will call this the inverse r th -power distribution.) This model has a simple geographic interpretation: individuals live on a grid and know their neighbors for some number of steps in all directions; they also have some number of acquaintances distributed more broadly across the grid. Viewing p and q as fixed constants, we obtain a one-parameter family of network models by tuning the value of the exponent r. When r = 0, we have the uniform distribution over long-range contacts, the distribution 4
5 used in the basic network model of Watts and Strogatz one s long-range contacts are chosen independently of their position on the grid. As r increases, the long-range contacts of a node become more and more clustered in its vicinity on the grid. Thus, r serves as a basic structural parameter measuring how widely networked the underlying society of nodes is. The algorithmic component of the model is based on Milgram s experiment. We start with two arbitrary nodes in the network, denoted s and t; the goal is to transmit a message from s to t in as few steps as possible. We study decentralized algorithms, mechanisms whereby the message is passed sequentially from a current message holder to one of its (local or long-range) contacts, using only local information. In particular, the message holder u in a given step has knowledge of (i) the set of local contacts among all nodes (i.e. the underlying grid structure); (ii) the location, on the lattice, of the target t; and (iii) the locations and long-range contacts of all nodes that have come in contact with the message. Crucially, u does not have knowledge of the long-range contacts of nodes that have not touched the message. Given this, u must choose one of its contacts v, and forward the message to this contact. The expected delivery time of a decentralized algorithm a primary figure of merit in our analysis is the expected number of steps taken by the algorithm to deliver the message over a network generated according to an inverse r th -power distribution, from a source to a target chosen uniformly at random from the set of nodes. Of course, constraining the algorithm to use only local information is crucial to our model; if one had full global knowledge of the local and long-range contacts of all nodes in the network, the shortest chain between two nodes could be computed simply by breadth-first search. The reader may worry that assumption (iii) above gives a decentralized algorithm too much power. However, it only strengthens our results: our lower bounds will hold even for algorithms that are given this knowledge, while our upper bounds make use of decentralized algorithms that only require assumptions (i) and (ii). Statement of Results. Our results explore the way in which the structure of the network affects the ability of a decentralized algorithm to construct a short path. When r = 0 the uniform distribution over long-range contacts standard results from random graph theory can be used to show that with high probability there exist paths between every pair of nodes whose lengths are bounded by a polynomial in log n, exponentially smaller than the total number of nodes. However, there is no way for a decentralized algorithm to find these chains: Theorem 1 There is a constant α 0, depending on p and q but independent of n, so that when r = 0, the expected delivery time of any decentralized algorithm is at least α 0 n 2/3. (Hence exponential in the expected minimum path length.) As the parameter r increases, a decentralized algorithm can take more advantage of the geographic structure implicit in the long-range contacts; at the same time, long-range 5
6 contacts become less useful in moving the message a large distance. There is a value of r where this trade-off can be best exploited algorithmically; this is r = 2, the inverse-square distribution. Theorem 2 There is a decentralized algorithm A and a constant α 2, independent of n, so that when r = 2 and p = q = 1, the expected delivery time of A is at most α 2 (log n) 2. This pair of theorems reflects a fundamental consequence of our model. When long-range contacts are formed independently of the geometry of the grid, short chains will exist but the nodes, operating at a local level, will not be able to find them. When long-range contacts are formed by a process that is related to the geometry of the grid in a specific way, however, then short chains will still form and nodes operating with local knowledge will be able to construct them. We now comment on the ideas underlying the proofs of these results; the full details are given in the subsequent sections. The decentralized algorithm A that achieves the bound of Theorem 2 is the following simple rule: in each step, the current message-holder u chooses a contact that is as close to the target t as possible, in the sense of lattice distance. Note that algorithm A makes use of even less information than is allowed by our general model: the current message holder does not need to know anything about the set of previous message holders. To analyze an execution of algorithm A, we say that it is in phase j if the lattice distance from the current message holder to the target is between 2 j and 2 j+1. We show that in phase j, the expected time before the current message holder has a long-range contact within lattice distance 2 j of t is bounded proportionally to log n; at this point, phase j will come to an end. As there are at most 1 + log n phases, a bound proportional to (log n) 2 follows. Interestingly, the analysis matches our intuition, and Milgram s description, of how a short chain is found in real life: The geographic movement of the [message] from Nebraska to Massachusetts is striking. There is a progressive closing in on the target area as each new person is added to the chain [13]. The impossibility result of Theorem 1 is based, fundamentally, on the fact that the uniform distribution prevents a decentralized algorithm from using any clues provided by the geometry of the grid. Roughly, we consider the set U of all nodes within lattice distance n 2/3 of t. With high probability, the source s will lie outside of U, and if the message is never passed from a node to a long-range contact in U, the number of steps needed to reach t will be at least proportional to n 2/3. But the probability that any message holder has a long-range contact in U is roughly n 2/3, so the expected number of steps before a long-range contact in U is found is at least proportional to n 2/3 as well. More generally, we can show a strong characterization theorem for this family of models: r = 2 is the only value for which there is a decentralized algorithm capable of producing chains whose length is a polynomial in log n: Theorem 3 (a) Let 0 r < 2. There is a constant α r, depending on p, q, r, but independent of n, so that the expected delivery time of any decentralized algorithm is at least α r n (2 r)/3. (b) Let r > 2. There is a constant α r, depending on p, q, r, but independent of n, so that the expected delivery time of any decentralized algorithm is at least α r n (r 2)/(r 1). 6
7 .8 lower bound T on delivery time (given as log T) n clustering exponent r Figure 2: The lower bound implied by Theorem 3. The x-axis is the value of r; the y-axis is the resulting exponent on n. The complete proof of this theorem is given in Section 3. The proof of (a) is analogous to that of Theorem 1. The proof of (b), on the other hand, exposes a dual obstacle for decentralized algorithms: with a large value of r, it takes a significant amount of time before the message reaches a node with a long-range contact that is far away in lattice distance. This effectively limits the speed at which the message can travel from s to t. Although we have focused on the two-dimensional grid, our analysis can be applied more broadly. We can generalize our results to k-dimensional lattice networks, for constant values of k, as well as less structured graphs with analogous scaling properties. In the k-dimensional case, a decentralized algorithm can construct paths of length polynomial in log n if and only if r = k. The results suggest a fundamental network property, distinct from diameter, that helps to explain the success of small-world experiments. One could think of it as the transmission rate of a class of networks: the minimum expected delivery time of any decentralized algorithm operating in a random network drawn from this class. Thus we see that minimizing the transmission rate of a network is not necessarily the same as minimizing its diameter. This may seem counter-intuitive at first, but in fact it formalizes a notion raised initially in addition to having short paths, a network should contain latent structural cues that can be used to guide a message towards a target. The dependence of long-range connections on the geometry of the lattice is providing precisely such implicit information. Indeed, the proofs of the theorems reveal a general structural property that implies the optimality of the exponent r = 2 for the two-dimensional lattice: it is the unique exponent at which a node s long-range contacts are nearly uniformly distributed over all distance scales. Specifically, given any node u, we can partition the remaining nodes of the lattice 7
8 into sets A 0, A 1, A 2,..., A log n, where A j consists of all nodes whose lattice distance to u is between 2 j and 2 j+1. These sets naturally correspond to different levels of resolution as we move away from u; all nodes in each A j are at approximately the same distance (to within a factor of 2) from u. At exponent r = 2, each long-range contact of u is nearly equally likely to belong to any of the sets A j ; when r < 2, there is a bias toward sets A j at greater distances, and when r > 2, there is a bias toward sets A j at nearer distances. Other Related Work. There has been work aimed at modeling the way in which individuals in Milgram s experiments chose recipients for their letters. Some of this work is related in spirit to what we do here, though using very different perspectives and models. Killworth and Bernard [10], in their reverse small-world experiments, asked a set of respondents to explain how they chose to send letters in a run of the small-world experiment, and used this information to look for common principles at an empirical level. At an analytical level, White [20] investigated the probability that a chain would die out through an individual s failure to participate, and Hunter and Shotland [8] studied the passage of a chain through different social categories. In the context of a referral system for the World Wide Web, Kautz, Selman, and Shah [17] ran simulations of communication in an abstract social network in which each individual was given pre-defined accuracy and responsiveness parameters. The distinction between the mere existence of short paths linking points on the World Wide Web, and the ability of agents to find them, has also been raised recently in work of Albert, Jeong, and Barabasi [2, 9]. 2 Upper Bound for the Inverse-Square Distribution We now present proofs of the theorems discussed in the previous section. When we analyze a decentralized algorithm, we can adopt the following equivalent formulation of the model, which will make the exposition easier. Although our model considers all long-range contacts as being generated initially, at random, we invoke the Principle of Deferred Decisions a common mechanism for analyzing randomized algorithms [14] and assume that the long-range contacts of a node v are generated only when the message first reaches v. Since a decentralized algorithm does not learn the long-range contacts of v until the message reaches v, this formulation is equivalent for the purposes of analysis. A comment on the notation: log n denotes the logarithm base 2, while ln n denotes the natural logarithm, base e. Proof of Theorem 2. Since p = q = 1, we have a network in which each node u is connected to its four nearest neighbors in the lattice (two or three neighbors in the case of nodes on the boundary), and has a single long-range contact v. The probability that u chooses v as its long-range contact is d(u, v) 2 / v u d(u, v) 2, and we have d(u, v) 2 v u 2n 2 j=1 (4j)(j 2 ) 8
9 2n 2 = 4 j=1 j ln(2n 2) 4 ln(6n). Thus, the probability that v is chosen is at least [4 ln(6n)d(u, v) 2 ] 1. The decentralized algorithm A is defined as follows: in each step, the current messageholder u chooses a contact that is as close to the target t as possible, in the sense of lattice distance. For j > 0, we say that the execution of A is in phase j when the lattice distance from the current node to t is greater than 2 j and at most 2 j+1. We say A is in phase 0 when the lattice distance to t is at most 2. Thus, the initial value of j is at most log n. Now, because the distance from the message to the target decreases strictly in each step, each node that becomes the message holder has not touched the message before; thus, we may assume that the long-range contact from the message holder is generated at this moment. Suppose we are in phase j, log(log n) j < log n, and the current message holder is u. What is the probability that phase j will end in this step? This requires the message to enter the set B j of nodes within lattice distance 2 j of t. There are at least 2 j 1 + i = j j + 1 > 2 2j 1 i=1 nodes in B j, each is within lattice distance 2 j j < 2 j+2 of u, and hence each has a probability of at least (4 ln(6n)2 2j+4 ) 1 of being the long-range contact of u. If any of these nodes is the long-range contact of u, it will be u s closest neighbor to t; thus the message enters B j with probability at least 2 2j 1 4 ln(6n)2 = 1 2j ln(6n). Let X j denote total number of steps spent in phase j, log(log n) j < log n. We have EX j = Pr [X j i] i=1 ( ) i i=1 128 ln(6n) = 128 ln(6n). An analogous set of bounds shows that EX j 128 ln(6n) for j = log n as well. Finally, if 0 j log(log n), then EX j 128 ln(6n) holds for the simple reason that the algorithm can spend at most log n steps in phase j even if all nodes pass the message to a local contact. Now, if X denotes the total number of steps spent by the algorithm, we have X = log n j=0 and so by linearity of expectation we have EX (1 + log n)(128 ln(6n)) α 2 (log n) 2 for a suitable choice of α 2. 9 X j,
10 3 Lower Bounds for Other Distributions We first expand our model of a decentralized algorithm slightly; it will correspondingly strengthen the result to show a lower bound for this new model. An algorithm initially has knowledge of the grid structure, all the local contacts, and the locations of s and t. In step i, some set S i of nodes has touched the message. At this point, the algorithm has knowledge of all long-range contacts of all nodes in S i. (Following our style of analysis, the long-range contacts of other nodes will be constructed only as the message reaches them.) Based on this information, it chooses any contact v of any node in S i that has not yet received the message v need not be a contact of the current message holder and it sends the message to v. The set S i+1 thus contains one element more than S i, and the algorithm iterates. This is the same as our initial model of a decentralized algorithm, except that we do not count steps in which the algorithm backtracks by sending the message through a node that has already received it. For technical reasons, we will add one additional feature to the algorithms we consider. An algorithm will run for an infinite sequence of steps; initially it behaves as above, and once the message reaches t, the message remains at t in all subsequent steps. Thus, when we consider the i th step of a given algorithm, we need not worry that it has already terminated by this step. We now prove the two parts of Theorem 3; note that part (a) implies Theorem 1 by setting r = 0. As in Section 2, we will invoke the Principle of Deferred Decisions [14] in the analysis. Proof of Theorem 3a. We consider an arbitrary decentralized algorithm of the type described above, and consider the expected number of steps required for the message to travel from s to t, for nodes s and t generated uniformly at random from the grid. Note that because we have the freedom to choose the constant α r, we may also assume that n is at least as large as some fixed absolute constant n 0. The probability that a node u chooses v as its i th out of q long-range contacts is d(u, v) r / v u d(u, v) r, and we have d(u, v) r v u = n/2 j=1 (j)(j r ) n/2 j 1 r j=1 n/2 1 x 1 r dx (2 r) 1 ((n/2) 2 r 1) 1 (2 r)2 3 r n2 r, where the last line follows if we assume n 2 r 2 3 r. Let δ = (2 r)/3. 10
11 Let U denote the set of nodes within lattice distance pn δ of t. Note that pn δ U 1 + 4j 4p 2 n 2δ, j=1 where we assume n is large enough that pn δ 2. Define λ = (2 8 r qp 2 ) 1. Let E be the event that within λn δ steps, the message reaches a node other than t with a long-range contact in U. Let E i be the event that in step i, the message reaches a node other than t with a long-range contact in U; thus E = E i. Now, the node reached at step i has q long-range iλn δ contacts that are generated at random when it is encountered; so we have Pr [E i] 1 (2 r)2 3 r q U n 2 r (2 r)23 r q 4p 2 n 2δ n 2 r = (2 r)25 r qp 2 n 2δ n 2 r. Since the probability of a union of events is bounded by the sum of their probabilities, Pr [E ] iλn δ Pr [E i ] (2 r)25 r λqp 2 n 3δ n 2 r = (2 r)2 5 r λqp We now define two further events. Let F denote the event that the chosen source s and target t are separated by a lattice distance of at least n/4. One can verify that Pr [F] 1. 2 Since Pr [ F E ] 1 + 1, Pr [ ] F E Finally, let X denote the random variable equal to the number of steps taken for the message to reach t, and let E denote the event that the message reaches t within λn δ steps. We claim that if F occurs and E does not occur, then E cannot occur. For suppose it does. Since d(s, t) n/4 > pλn δ, in any s-t path of at most λn δ steps, the message must be passed at least once from a node to a long-range contact. Moreover, the final time this happens, the long-range contact must lie in U. This contradicts our assumption that E does not occur. Thus, Pr [ ] [ E F E = 0, hence E X F E ] λn δ. Since part (a) of the theorem follows. EX E [ ] [ ] 1 X F E Pr F E 4 λnδ, Proof of Theorem 3b. We now turn to part (b) of the theorem, when r > 2. Again we consider an arbitrary decentralized algorithm; and again, as necessary, we may assume that 11
12 n is larger than some fixed absolute constant n 0. We write ε = r 2. Consider a node u, and let v be a randomly generated long-range contact of v. The normalizing constant for the inverse r th -power distribution is at least 1, and so for any m, we have Pr [d(u, v) > m] = 4 2n 2 j=m+1 (4j)(j r ) 2n 2 j 1 r j=m+1 m x 1 r dx (r 2) 1 m 2 r = ε 1 m ε. We set β = ε, γ = 1, and 1+ε 1+ε λ = min(ε,1). We will assume n has been chosen large 8q enough that n γ p. Let E i be the event that in step i, the message reaches a node u t that has a long-range contact v satisfying d(u, v) > n γ. Let E = be the event that this happens in the first λ n β steps. We have Pr [E ] iλ n β Pr [E i ] λ n β qε 1 n εγ = λ qε iλ n β E i As in part (a), we define F to be the event that s and t are separated by a lattice distance of at least n/4. Observe that Pr [ ] F E 1. Let X denote the random variable equal to 4 the number of steps taken for the message to reach t, and let E denote the event that the message reaches t within λ n β steps. We claim that if F occurs and E does not occur, then E cannot occur. For if E does not occur, then the message can move a lattice distance of at most n γ in each of its first λ n β steps. This is a total lattice distance of at most λ n β+γ = λ n < n/4, and so the message will not reach t given that F occurs. Thus E [ X F E ] λ n β. Since part (b) of the theorem follows. 4 Conclusion EX E [ ] [ ] 1 X F E Pr F E 4 λ n β, Algorithmic work in different settings has considered the problem of routing with local information; see for example the problem of designing compact routing tables for communication 12
13 networks [15] and the problem of robot navigation in an unknown environment [3]. Our results are technically quite different from these; but they share the general goal of identifying qualitative properties of networks that makes routing with local information tractable, and offering a model for reasoning about effective routing schemes in such networks. While we have deliberately focused on a very clean model, we believe that a more general conclusion can be drawn for small-world networks: that the correlation between local structure and long-range connections provides fundamental cues for finding paths through the network. When this correlation is near a critical threshold, the structure of the long-range connections forms a type of gradient that allows individuals to guide a message efficiently toward a target. As the correlation drops below this critical value and the social network becomes more homogeneous, these cues begin to disappear; in the limit, when long-range connections are generated uniformly at random, our model describes a world in which short chains exist but individuals, faced with a disorienting array of social contacts, are unable to find them. Acknowledgements. topic. We thank Steve Strogatz for many valuable discussions on this References [1] L. Adamic, The small world Web, Proceedings of the European Conf. on Digital Libraries, [2] R. Albert, H. Jeong, A.-L. Barabasi, The diameter of the World Wide Web, Nature 401, 130 (1999). [3] P. Berman, On-line searching and navigation, On-Line Algorithms: The State of the Art, A. Fiat and G. Woeginger, Eds., Springer, [4] B. Bollobás, Random Graphs (Academic Press, London, 1985). [5] B. Bollobás, F.R.K. Chung, The diameter of a cycle plus a random matching, SIAM J. Discrete Math. 1, 328 (1988). [6] F.R.K. Chung, M.R. Garey, Diameter bounds for altered graphs, J. Graph Theory 8, 511 (1984). [7] J. Guare, Six Degrees of Separation: A Play (Vintage Books, New York, 1990). [8] J. Hunter and R. Shotland, Treating data collected by the small world method as a Markov process, Social Forces 52, 321 (1974). [9] J. Kaiser, Ed., It s a small Web after all, Science 285, 1815 (1999). [10] P. Killworth and H. Bernard, Reverse small world experiment, Social Networks 1, 159 (1978). [11] M. Kochen, Ed., The Small World (Ablex, Norwood, 1989). 13
14 [12] C. Korte and S. Milgram, Acquaintance networks between racial groups: Application of the small world method, J. Personality and Social Psych., 15, 101 (1978). [13] S. Milgram, The small world problem, Psychology Today 1, 61 (1967). [14] R. Motwani and P. Raghavan, Randomized Algorithms (Cambridge University Press, Cambridge, 1995). [15] D. Peleg, E. Upfal, A trade-off between size and efficiency for routing tables, Journal of the ACM 36(1989). [16] I. de Sola Pool and M. Kochen, Contacts and influence, Social Networks 1, 5 (1978). [17] H. Kautz, B. Selman, M. Shah, ReferralWeb: Combining Social Networks and Collaborative Filtering, Communications of the ACM, 30, 3 (March 1997). [18] J. Travers and S. Milgram, An experimental study of the small world problem, Sociometry 32, 425 (1969). [19] D. Watts and S. Strogatz, Collective dynamics of small-world networks, Nature 393, 440 (1998). [20] H. White, Search parameters for the small world problem, Social Forces 49, 259 (1970). 14
6.207/14.15: Networks Lecture 7: Search on Networks: Navigation and Web Search
 6.207/14.15: Networks Lecture 7: Search on Networks: Navigation and Web Search Daron Acemoglu and Asu Ozdaglar MIT September 30, 2009 1 Networks: Lecture 7 Outline Navigation (or decentralized search)
6.207/14.15: Networks Lecture 7: Search on Networks: Navigation and Web Search Daron Acemoglu and Asu Ozdaglar MIT September 30, 2009 1 Networks: Lecture 7 Outline Navigation (or decentralized search)
Efficient routing in Poisson small-world networks
 Efficient routing in Poisson small-world networks M. Draief and A. Ganesh Abstract In recent work, Jon Kleinberg considered a small-world network model consisting of a d-dimensional lattice augmented with
Efficient routing in Poisson small-world networks M. Draief and A. Ganesh Abstract In recent work, Jon Kleinberg considered a small-world network model consisting of a d-dimensional lattice augmented with
Social Networks. Chapter 9
 Chapter 9 Social Networks Distributed computing is applicable in various contexts. This lecture exemplarily studies one of these contexts, social networks, an area of study whose origins date back a century.
Chapter 9 Social Networks Distributed computing is applicable in various contexts. This lecture exemplarily studies one of these contexts, social networks, an area of study whose origins date back a century.
Greedy Search in Social Networks
 Greedy Search in Social Networks David Liben-Nowell Carleton College dlibenno@carleton.edu Joint work with Ravi Kumar, Jasmine Novak, Prabhakar Raghavan, and Andrew Tomkins. IPAM, Los Angeles 8 May 2007
Greedy Search in Social Networks David Liben-Nowell Carleton College dlibenno@carleton.edu Joint work with Ravi Kumar, Jasmine Novak, Prabhakar Raghavan, and Andrew Tomkins. IPAM, Los Angeles 8 May 2007
Deterministic Decentralized Search in Random Graphs
 Deterministic Decentralized Search in Random Graphs Esteban Arcaute 1,, Ning Chen 2,, Ravi Kumar 3, David Liben-Nowell 4,, Mohammad Mahdian 3, Hamid Nazerzadeh 1,, and Ying Xu 1, 1 Stanford University.
Deterministic Decentralized Search in Random Graphs Esteban Arcaute 1,, Ning Chen 2,, Ravi Kumar 3, David Liben-Nowell 4,, Mohammad Mahdian 3, Hamid Nazerzadeh 1,, and Ying Xu 1, 1 Stanford University.
SMALL-WORLD NAVIGABILITY. Alexandru Seminar in Distributed Computing
 SMALL-WORLD NAVIGABILITY Talk about a small world 2 Zurich, CH Hunedoara, RO From cliché to social networks 3 Milgram s Experiment and The Small World Hypothesis Omaha, NE Boston, MA Wichita, KS Human
SMALL-WORLD NAVIGABILITY Talk about a small world 2 Zurich, CH Hunedoara, RO From cliché to social networks 3 Milgram s Experiment and The Small World Hypothesis Omaha, NE Boston, MA Wichita, KS Human
Exact solution of site and bond percolation. on small-world networks. Abstract
 Exact solution of site and bond percolation on small-world networks Cristopher Moore 1,2 and M. E. J. Newman 2 1 Departments of Computer Science and Physics, University of New Mexico, Albuquerque, New
Exact solution of site and bond percolation on small-world networks Cristopher Moore 1,2 and M. E. J. Newman 2 1 Departments of Computer Science and Physics, University of New Mexico, Albuquerque, New
6.207/14.15: Networks Lecture 12: Generalized Random Graphs
 6.207/14.15: Networks Lecture 12: Generalized Random Graphs 1 Outline Small-world model Growing random networks Power-law degree distributions: Rich-Get-Richer effects Models: Uniform attachment model
6.207/14.15: Networks Lecture 12: Generalized Random Graphs 1 Outline Small-world model Growing random networks Power-law degree distributions: Rich-Get-Richer effects Models: Uniform attachment model
MAE 298, Lecture 8 Feb 4, Web search and decentralized search on small-worlds
 MAE 298, Lecture 8 Feb 4, 2008 Web search and decentralized search on small-worlds Search for information Assume some resource of interest is stored at the vertices of a network: Web pages Files in a file-sharing
MAE 298, Lecture 8 Feb 4, 2008 Web search and decentralized search on small-worlds Search for information Assume some resource of interest is stored at the vertices of a network: Web pages Files in a file-sharing
EFFICIENT ROUTEING IN POISSON SMALL-WORLD NETWORKS
 J. Appl. Prob. 43, 678 686 (2006) Printed in Israel Applied Probability Trust 2006 EFFICIENT ROUTEING IN POISSON SMALL-WORLD NETWORKS M. DRAIEF, University of Cambridge A. GANESH, Microsoft Research Abstract
J. Appl. Prob. 43, 678 686 (2006) Printed in Israel Applied Probability Trust 2006 EFFICIENT ROUTEING IN POISSON SMALL-WORLD NETWORKS M. DRAIEF, University of Cambridge A. GANESH, Microsoft Research Abstract
CS 781 Lecture 9 March 10, 2011 Topics: Local Search and Optimization Metropolis Algorithm Greedy Optimization Hopfield Networks Max Cut Problem Nash
 CS 781 Lecture 9 March 10, 2011 Topics: Local Search and Optimization Metropolis Algorithm Greedy Optimization Hopfield Networks Max Cut Problem Nash Equilibrium Price of Stability Coping With NP-Hardness
CS 781 Lecture 9 March 10, 2011 Topics: Local Search and Optimization Metropolis Algorithm Greedy Optimization Hopfield Networks Max Cut Problem Nash Equilibrium Price of Stability Coping With NP-Hardness
1 Complex Networks - A Brief Overview
 Power-law Degree Distributions 1 Complex Networks - A Brief Overview Complex networks occur in many social, technological and scientific settings. Examples of complex networks include World Wide Web, Internet,
Power-law Degree Distributions 1 Complex Networks - A Brief Overview Complex networks occur in many social, technological and scientific settings. Examples of complex networks include World Wide Web, Internet,
Adventures in random graphs: Models, structures and algorithms
 BCAM January 2011 1 Adventures in random graphs: Models, structures and algorithms Armand M. Makowski ECE & ISR/HyNet University of Maryland at College Park armand@isr.umd.edu BCAM January 2011 2 LECTURE
BCAM January 2011 1 Adventures in random graphs: Models, structures and algorithms Armand M. Makowski ECE & ISR/HyNet University of Maryland at College Park armand@isr.umd.edu BCAM January 2011 2 LECTURE
The Beginning of Graph Theory. Theory and Applications of Complex Networks. Eulerian paths. Graph Theory. Class Three. College of the Atlantic
 Theory and Applications of Complex Networs 1 Theory and Applications of Complex Networs 2 Theory and Applications of Complex Networs Class Three The Beginning of Graph Theory Leonhard Euler wonders, can
Theory and Applications of Complex Networs 1 Theory and Applications of Complex Networs 2 Theory and Applications of Complex Networs Class Three The Beginning of Graph Theory Leonhard Euler wonders, can
Conservative Belief and Rationality
 Conservative Belief and Rationality Joseph Y. Halpern and Rafael Pass Department of Computer Science Cornell University Ithaca, NY, 14853, U.S.A. e-mail: halpern@cs.cornell.edu, rafael@cs.cornell.edu January
Conservative Belief and Rationality Joseph Y. Halpern and Rafael Pass Department of Computer Science Cornell University Ithaca, NY, 14853, U.S.A. e-mail: halpern@cs.cornell.edu, rafael@cs.cornell.edu January
Lower Bounds for Testing Bipartiteness in Dense Graphs
 Lower Bounds for Testing Bipartiteness in Dense Graphs Andrej Bogdanov Luca Trevisan Abstract We consider the problem of testing bipartiteness in the adjacency matrix model. The best known algorithm, due
Lower Bounds for Testing Bipartiteness in Dense Graphs Andrej Bogdanov Luca Trevisan Abstract We consider the problem of testing bipartiteness in the adjacency matrix model. The best known algorithm, due
Spatial Gossip and Resource Location Protocols
 Spatial Gossip and Resource Location Protocols David Kempe, Jon Kleinberg, and Alan Demers Dept. of Computer Science Cornell University, Ithaca NY 14853 email: {kempe,kleinber,ademers}@cs.cornell.edu September
Spatial Gossip and Resource Location Protocols David Kempe, Jon Kleinberg, and Alan Demers Dept. of Computer Science Cornell University, Ithaca NY 14853 email: {kempe,kleinber,ademers}@cs.cornell.edu September
Complex Networks, Course 303A, Spring, Prof. Peter Dodds
 Complex Networks, Course 303A, Spring, 2009 Prof. Peter Dodds Department of Mathematics & Statistics University of Vermont Licensed under the Creative Commons Attribution-NonCommercial-ShareAlike 3.0 License.
Complex Networks, Course 303A, Spring, 2009 Prof. Peter Dodds Department of Mathematics & Statistics University of Vermont Licensed under the Creative Commons Attribution-NonCommercial-ShareAlike 3.0 License.
Nonlinear Dynamical Behavior in BS Evolution Model Based on Small-World Network Added with Nonlinear Preference
 Commun. Theor. Phys. (Beijing, China) 48 (2007) pp. 137 142 c International Academic Publishers Vol. 48, No. 1, July 15, 2007 Nonlinear Dynamical Behavior in BS Evolution Model Based on Small-World Network
Commun. Theor. Phys. (Beijing, China) 48 (2007) pp. 137 142 c International Academic Publishers Vol. 48, No. 1, July 15, 2007 Nonlinear Dynamical Behavior in BS Evolution Model Based on Small-World Network
arxiv:cond-mat/ v2 [cond-mat.stat-mech] 7 Jan 2000
![arxiv:cond-mat/ v2 [cond-mat.stat-mech] 7 Jan 2000 arxiv:cond-mat/ v2 [cond-mat.stat-mech] 7 Jan 2000](/thumbs/88/116231555.jpg) Epidemics and percolation in small-world networks Cristopher Moore 1,2 and M. E. J. Newman 1 1 Santa Fe Institute, 1399 Hyde Park Road, Santa Fe, New Mexico 87501 2 Departments of Computer Science and
Epidemics and percolation in small-world networks Cristopher Moore 1,2 and M. E. J. Newman 1 1 Santa Fe Institute, 1399 Hyde Park Road, Santa Fe, New Mexico 87501 2 Departments of Computer Science and
BOSTON UNIVERSITY GRADUATE SCHOOL OF ARTS AND SCIENCES. Dissertation TRANSPORT AND PERCOLATION IN COMPLEX NETWORKS GUANLIANG LI
 BOSTON UNIVERSITY GRADUATE SCHOOL OF ARTS AND SCIENCES Dissertation TRANSPORT AND PERCOLATION IN COMPLEX NETWORKS by GUANLIANG LI B.S., University of Science and Technology of China, 2003 Submitted in
BOSTON UNIVERSITY GRADUATE SCHOOL OF ARTS AND SCIENCES Dissertation TRANSPORT AND PERCOLATION IN COMPLEX NETWORKS by GUANLIANG LI B.S., University of Science and Technology of China, 2003 Submitted in
Spatial and Temporal Behaviors in a Modified Evolution Model Based on Small World Network
 Commun. Theor. Phys. (Beijing, China) 42 (2004) pp. 242 246 c International Academic Publishers Vol. 42, No. 2, August 15, 2004 Spatial and Temporal Behaviors in a Modified Evolution Model Based on Small
Commun. Theor. Phys. (Beijing, China) 42 (2004) pp. 242 246 c International Academic Publishers Vol. 42, No. 2, August 15, 2004 Spatial and Temporal Behaviors in a Modified Evolution Model Based on Small
The diameter of a long-range percolation graph
 The diameter of a long-range percolation graph Don Coppersmith David Gamarnik Maxim Sviridenko Abstract We consider the following long-range percolation model: an undirected graph with the node set {0,,...,
The diameter of a long-range percolation graph Don Coppersmith David Gamarnik Maxim Sviridenko Abstract We consider the following long-range percolation model: an undirected graph with the node set {0,,...,
CORRECTNESS OF A GOSSIP BASED MEMBERSHIP PROTOCOL BY (ANDRÉ ALLAVENA, ALAN DEMERS, JOHN E. HOPCROFT ) PRATIK TIMALSENA UNIVERSITY OF OSLO
 CORRECTNESS OF A GOSSIP BASED MEMBERSHIP PROTOCOL BY (ANDRÉ ALLAVENA, ALAN DEMERS, JOHN E. HOPCROFT ) PRATIK TIMALSENA UNIVERSITY OF OSLO OUTLINE q Contribution of the paper q Gossip algorithm q The corrected
CORRECTNESS OF A GOSSIP BASED MEMBERSHIP PROTOCOL BY (ANDRÉ ALLAVENA, ALAN DEMERS, JOHN E. HOPCROFT ) PRATIK TIMALSENA UNIVERSITY OF OSLO OUTLINE q Contribution of the paper q Gossip algorithm q The corrected
Using Markov Chains To Model Human Migration in a Network Equilibrium Framework
 Using Markov Chains To Model Human Migration in a Network Equilibrium Framework Jie Pan Department of Mathematics and Computer Science Saint Joseph s University Philadelphia, PA 19131 Anna Nagurney School
Using Markov Chains To Model Human Migration in a Network Equilibrium Framework Jie Pan Department of Mathematics and Computer Science Saint Joseph s University Philadelphia, PA 19131 Anna Nagurney School
arxiv: v1 [physics.soc-ph] 15 Dec 2009
![arxiv: v1 [physics.soc-ph] 15 Dec 2009 arxiv: v1 [physics.soc-ph] 15 Dec 2009](/thumbs/96/128729428.jpg) Power laws of the in-degree and out-degree distributions of complex networks arxiv:0912.2793v1 [physics.soc-ph] 15 Dec 2009 Shinji Tanimoto Department of Mathematics, Kochi Joshi University, Kochi 780-8515,
Power laws of the in-degree and out-degree distributions of complex networks arxiv:0912.2793v1 [physics.soc-ph] 15 Dec 2009 Shinji Tanimoto Department of Mathematics, Kochi Joshi University, Kochi 780-8515,
Testing Problems with Sub-Learning Sample Complexity
 Testing Problems with Sub-Learning Sample Complexity Michael Kearns AT&T Labs Research 180 Park Avenue Florham Park, NJ, 07932 mkearns@researchattcom Dana Ron Laboratory for Computer Science, MIT 545 Technology
Testing Problems with Sub-Learning Sample Complexity Michael Kearns AT&T Labs Research 180 Park Avenue Florham Park, NJ, 07932 mkearns@researchattcom Dana Ron Laboratory for Computer Science, MIT 545 Technology
12. LOCAL SEARCH. gradient descent Metropolis algorithm Hopfield neural networks maximum cut Nash equilibria
 12. LOCAL SEARCH gradient descent Metropolis algorithm Hopfield neural networks maximum cut Nash equilibria Lecture slides by Kevin Wayne Copyright 2005 Pearson-Addison Wesley h ttp://www.cs.princeton.edu/~wayne/kleinberg-tardos
12. LOCAL SEARCH gradient descent Metropolis algorithm Hopfield neural networks maximum cut Nash equilibria Lecture slides by Kevin Wayne Copyright 2005 Pearson-Addison Wesley h ttp://www.cs.princeton.edu/~wayne/kleinberg-tardos
COMPLEXITY OF LATTICE PROBLEMS A Cryptographic Perspective
 COMPLEXITY OF LATTICE PROBLEMS A Cryptographic Perspective THE KLUWER INTERNATIONAL SERIES IN ENGINEERING AND COMPUTER SCIENCE COMPLEXITY OF LATTICE PROBLEMS A Cryptographic Perspective Daniele Micciancio
COMPLEXITY OF LATTICE PROBLEMS A Cryptographic Perspective THE KLUWER INTERNATIONAL SERIES IN ENGINEERING AND COMPUTER SCIENCE COMPLEXITY OF LATTICE PROBLEMS A Cryptographic Perspective Daniele Micciancio
Cultural Dissemination using a Quantum Model
 Cultural Dissemination using a Quantum Model Scott Christley schristl@nd.edu Greg Madey gmadey@nd.edu Abstract Axelrod s [Axelrod, 1997] cultural dissemination model introduces an agent-based simulation
Cultural Dissemination using a Quantum Model Scott Christley schristl@nd.edu Greg Madey gmadey@nd.edu Abstract Axelrod s [Axelrod, 1997] cultural dissemination model introduces an agent-based simulation
6. APPLICATION TO THE TRAVELING SALESMAN PROBLEM
 6. Application to the Traveling Salesman Problem 92 6. APPLICATION TO THE TRAVELING SALESMAN PROBLEM The properties that have the most significant influence on the maps constructed by Kohonen s algorithm
6. Application to the Traveling Salesman Problem 92 6. APPLICATION TO THE TRAVELING SALESMAN PROBLEM The properties that have the most significant influence on the maps constructed by Kohonen s algorithm
arxiv:cond-mat/ v1 [cond-mat.dis-nn] 4 May 2000
![arxiv:cond-mat/ v1 [cond-mat.dis-nn] 4 May 2000 arxiv:cond-mat/ v1 [cond-mat.dis-nn] 4 May 2000](/thumbs/76/73443926.jpg) Topology of evolving networks: local events and universality arxiv:cond-mat/0005085v1 [cond-mat.dis-nn] 4 May 2000 Réka Albert and Albert-László Barabási Department of Physics, University of Notre-Dame,
Topology of evolving networks: local events and universality arxiv:cond-mat/0005085v1 [cond-mat.dis-nn] 4 May 2000 Réka Albert and Albert-László Barabási Department of Physics, University of Notre-Dame,
Detecting a Network Failure
 Detecting a Network Failure Jon Kleinberg Abstract Measuring the properties of a large, unstructed network can be difficult: one may not have full knowledge of the network topology, and detailed global
Detecting a Network Failure Jon Kleinberg Abstract Measuring the properties of a large, unstructed network can be difficult: one may not have full knowledge of the network topology, and detailed global
k-protected VERTICES IN BINARY SEARCH TREES
 k-protected VERTICES IN BINARY SEARCH TREES MIKLÓS BÓNA Abstract. We show that for every k, the probability that a randomly selected vertex of a random binary search tree on n nodes is at distance k from
k-protected VERTICES IN BINARY SEARCH TREES MIKLÓS BÓNA Abstract. We show that for every k, the probability that a randomly selected vertex of a random binary search tree on n nodes is at distance k from
CS224W Project Writeup: On Navigability in Small-World Networks
 CS224W Project Writeup: On Navigability in Small-World Networks Danny Goodman 12/11/2011 1 Introduction Graphs are called navigable one can find short paths through them using only local knowledge [2].
CS224W Project Writeup: On Navigability in Small-World Networks Danny Goodman 12/11/2011 1 Introduction Graphs are called navigable one can find short paths through them using only local knowledge [2].
Networks as vectors of their motif frequencies and 2-norm distance as a measure of similarity
 Networks as vectors of their motif frequencies and 2-norm distance as a measure of similarity CS322 Project Writeup Semih Salihoglu Stanford University 353 Serra Street Stanford, CA semih@stanford.edu
Networks as vectors of their motif frequencies and 2-norm distance as a measure of similarity CS322 Project Writeup Semih Salihoglu Stanford University 353 Serra Street Stanford, CA semih@stanford.edu
Spatial Gossip and Resource Location Protocols
 Spatial Gossip and Resource Location Protocols David Kempe Jon Kleinberg Alan Demers Abstract The dynamic behavior of a network in which information is changing continuously over time requires robust and
Spatial Gossip and Resource Location Protocols David Kempe Jon Kleinberg Alan Demers Abstract The dynamic behavior of a network in which information is changing continuously over time requires robust and
Lecture 5: January 30
 CS71 Randomness & Computation Spring 018 Instructor: Alistair Sinclair Lecture 5: January 30 Disclaimer: These notes have not been subjected to the usual scrutiny accorded to formal publications. They
CS71 Randomness & Computation Spring 018 Instructor: Alistair Sinclair Lecture 5: January 30 Disclaimer: These notes have not been subjected to the usual scrutiny accorded to formal publications. They
Randomized Algorithms
 Randomized Algorithms Prof. Tapio Elomaa tapio.elomaa@tut.fi Course Basics A new 4 credit unit course Part of Theoretical Computer Science courses at the Department of Mathematics There will be 4 hours
Randomized Algorithms Prof. Tapio Elomaa tapio.elomaa@tut.fi Course Basics A new 4 credit unit course Part of Theoretical Computer Science courses at the Department of Mathematics There will be 4 hours
Lecture 5: Efficient PAC Learning. 1 Consistent Learning: a Bound on Sample Complexity
 Universität zu Lübeck Institut für Theoretische Informatik Lecture notes on Knowledge-Based and Learning Systems by Maciej Liśkiewicz Lecture 5: Efficient PAC Learning 1 Consistent Learning: a Bound on
Universität zu Lübeck Institut für Theoretische Informatik Lecture notes on Knowledge-Based and Learning Systems by Maciej Liśkiewicz Lecture 5: Efficient PAC Learning 1 Consistent Learning: a Bound on
Lecture 5: The Principle of Deferred Decisions. Chernoff Bounds
 Randomized Algorithms Lecture 5: The Principle of Deferred Decisions. Chernoff Bounds Sotiris Nikoletseas Associate Professor CEID - ETY Course 2013-2014 Sotiris Nikoletseas, Associate Professor Randomized
Randomized Algorithms Lecture 5: The Principle of Deferred Decisions. Chernoff Bounds Sotiris Nikoletseas Associate Professor CEID - ETY Course 2013-2014 Sotiris Nikoletseas, Associate Professor Randomized
Improving Dense Packings of Equal Disks in a Square
 Improving Dense Packings of Equal Disks in a Square David W. Boll Jerry Donovan Ronald L. Graham Boris D. Lubachevsky Hewlett-Packard Hewlett-Packard University of California Lucent Technologies 00 st
Improving Dense Packings of Equal Disks in a Square David W. Boll Jerry Donovan Ronald L. Graham Boris D. Lubachevsky Hewlett-Packard Hewlett-Packard University of California Lucent Technologies 00 st
CS 277: Data Mining. Mining Web Link Structure. CS 277: Data Mining Lectures Analyzing Web Link Structure Padhraic Smyth, UC Irvine
 CS 277: Data Mining Mining Web Link Structure Class Presentations In-class, Tuesday and Thursday next week 2-person teams: 6 minutes, up to 6 slides, 3 minutes/slides each person 1-person teams 4 minutes,
CS 277: Data Mining Mining Web Link Structure Class Presentations In-class, Tuesday and Thursday next week 2-person teams: 6 minutes, up to 6 slides, 3 minutes/slides each person 1-person teams 4 minutes,
Optimism in the Face of Uncertainty Should be Refutable
 Optimism in the Face of Uncertainty Should be Refutable Ronald ORTNER Montanuniversität Leoben Department Mathematik und Informationstechnolgie Franz-Josef-Strasse 18, 8700 Leoben, Austria, Phone number:
Optimism in the Face of Uncertainty Should be Refutable Ronald ORTNER Montanuniversität Leoben Department Mathematik und Informationstechnolgie Franz-Josef-Strasse 18, 8700 Leoben, Austria, Phone number:
Theorem 1.7 [Bayes' Law]: Assume that,,, are mutually disjoint events in the sample space s.t.. Then Pr( )
![Theorem 1.7 [Bayes' Law]: Assume that,,, are mutually disjoint events in the sample space s.t.. Then Pr( ) Theorem 1.7 [Bayes' Law]: Assume that,,, are mutually disjoint events in the sample space s.t.. Then Pr( )](/thumbs/95/125074181.jpg) Theorem 1.7 [Bayes' Law]: Assume that,,, are mutually disjoint events in the sample space s.t.. Then Pr Pr = Pr Pr Pr() Pr Pr. We are given three coins and are told that two of the coins are fair and the
Theorem 1.7 [Bayes' Law]: Assume that,,, are mutually disjoint events in the sample space s.t.. Then Pr Pr = Pr Pr Pr() Pr Pr. We are given three coins and are told that two of the coins are fair and the
Introduction to Algorithms / Algorithms I Lecturer: Michael Dinitz Topic: Intro to Learning Theory Date: 12/8/16
 600.463 Introduction to Algorithms / Algorithms I Lecturer: Michael Dinitz Topic: Intro to Learning Theory Date: 12/8/16 25.1 Introduction Today we re going to talk about machine learning, but from an
600.463 Introduction to Algorithms / Algorithms I Lecturer: Michael Dinitz Topic: Intro to Learning Theory Date: 12/8/16 25.1 Introduction Today we re going to talk about machine learning, but from an
CS 6820 Fall 2014 Lectures, October 3-20, 2014
 Analysis of Algorithms Linear Programming Notes CS 6820 Fall 2014 Lectures, October 3-20, 2014 1 Linear programming The linear programming (LP) problem is the following optimization problem. We are given
Analysis of Algorithms Linear Programming Notes CS 6820 Fall 2014 Lectures, October 3-20, 2014 1 Linear programming The linear programming (LP) problem is the following optimization problem. We are given
Selecting Efficient Correlated Equilibria Through Distributed Learning. Jason R. Marden
 1 Selecting Efficient Correlated Equilibria Through Distributed Learning Jason R. Marden Abstract A learning rule is completely uncoupled if each player s behavior is conditioned only on his own realized
1 Selecting Efficient Correlated Equilibria Through Distributed Learning Jason R. Marden Abstract A learning rule is completely uncoupled if each player s behavior is conditioned only on his own realized
On a Form of Coordinate Percolation
 On a Form of Coordinate Percolation Elizabeth R. Moseman and Peter Winkler July 31, 008 Abstract Let a i, b i, i = 0, 1,,... be drawn uniformly and independently from the unit interval, and let t be a
On a Form of Coordinate Percolation Elizabeth R. Moseman and Peter Winkler July 31, 008 Abstract Let a i, b i, i = 0, 1,,... be drawn uniformly and independently from the unit interval, and let t be a
Chapter 11. Min Cut Min Cut Problem Definition Some Definitions. By Sariel Har-Peled, December 10, Version: 1.
 Chapter 11 Min Cut By Sariel Har-Peled, December 10, 013 1 Version: 1.0 I built on the sand And it tumbled down, I built on a rock And it tumbled down. Now when I build, I shall begin With the smoke from
Chapter 11 Min Cut By Sariel Har-Peled, December 10, 013 1 Version: 1.0 I built on the sand And it tumbled down, I built on a rock And it tumbled down. Now when I build, I shall begin With the smoke from
! 1.1 Definitions and Terminology
 ! 1.1 Definitions and Terminology 1. Introduction: At times, mathematics aims to describe a physical phenomenon (take the population of bacteria in a petri dish for example). We want to find a function
! 1.1 Definitions and Terminology 1. Introduction: At times, mathematics aims to describe a physical phenomenon (take the population of bacteria in a petri dish for example). We want to find a function
Growing a Network on a Given Substrate
 Growing a Network on a Given Substrate 1 Babak Fotouhi and Michael G. Rabbat Department of Electrical and Computer Engineering McGill University, Montréal, Québec, Canada Email: babak.fotouhi@mail.mcgill.ca,
Growing a Network on a Given Substrate 1 Babak Fotouhi and Michael G. Rabbat Department of Electrical and Computer Engineering McGill University, Montréal, Québec, Canada Email: babak.fotouhi@mail.mcgill.ca,
The concentration of the chromatic number of random graphs
 The concentration of the chromatic number of random graphs Noga Alon Michael Krivelevich Abstract We prove that for every constant δ > 0 the chromatic number of the random graph G(n, p) with p = n 1/2
The concentration of the chromatic number of random graphs Noga Alon Michael Krivelevich Abstract We prove that for every constant δ > 0 the chromatic number of the random graph G(n, p) with p = n 1/2
Spectral Analysis of Directed Complex Networks. Tetsuro Murai
 MASTER THESIS Spectral Analysis of Directed Complex Networks Tetsuro Murai Department of Physics, Graduate School of Science and Engineering, Aoyama Gakuin University Supervisors: Naomichi Hatano and Kenn
MASTER THESIS Spectral Analysis of Directed Complex Networks Tetsuro Murai Department of Physics, Graduate School of Science and Engineering, Aoyama Gakuin University Supervisors: Naomichi Hatano and Kenn
Notes 6 : First and second moment methods
 Notes 6 : First and second moment methods Math 733-734: Theory of Probability Lecturer: Sebastien Roch References: [Roc, Sections 2.1-2.3]. Recall: THM 6.1 (Markov s inequality) Let X be a non-negative
Notes 6 : First and second moment methods Math 733-734: Theory of Probability Lecturer: Sebastien Roch References: [Roc, Sections 2.1-2.3]. Recall: THM 6.1 (Markov s inequality) Let X be a non-negative
CS264: Beyond Worst-Case Analysis Lecture #18: Smoothed Complexity and Pseudopolynomial-Time Algorithms
 CS264: Beyond Worst-Case Analysis Lecture #18: Smoothed Complexity and Pseudopolynomial-Time Algorithms Tim Roughgarden March 9, 2017 1 Preamble Our first lecture on smoothed analysis sought a better theoretical
CS264: Beyond Worst-Case Analysis Lecture #18: Smoothed Complexity and Pseudopolynomial-Time Algorithms Tim Roughgarden March 9, 2017 1 Preamble Our first lecture on smoothed analysis sought a better theoretical
A Note on the Existence of Ratifiable Acts
 A Note on the Existence of Ratifiable Acts Joseph Y. Halpern Cornell University Computer Science Department Ithaca, NY 14853 halpern@cs.cornell.edu http://www.cs.cornell.edu/home/halpern August 15, 2018
A Note on the Existence of Ratifiable Acts Joseph Y. Halpern Cornell University Computer Science Department Ithaca, NY 14853 halpern@cs.cornell.edu http://www.cs.cornell.edu/home/halpern August 15, 2018
Quantum Percolation: Electrons in a Maze. Brianna Dillon-Thomas, PhD 2016
 Quantum Percolation: Electrons in a Maze Brianna Dillon-Thomas, PhD 2016 Physicists, especially theoretical physicists, love to make models of the world to help us understand it. We weigh various effects
Quantum Percolation: Electrons in a Maze Brianna Dillon-Thomas, PhD 2016 Physicists, especially theoretical physicists, love to make models of the world to help us understand it. We weigh various effects
1 Indistinguishability for multiple encryptions
 CSCI 5440: Cryptography Lecture 3 The Chinese University of Hong Kong 26 September 2012 1 Indistinguishability for multiple encryptions We now have a reasonable encryption scheme, which we proved is message
CSCI 5440: Cryptography Lecture 3 The Chinese University of Hong Kong 26 September 2012 1 Indistinguishability for multiple encryptions We now have a reasonable encryption scheme, which we proved is message
Geographic Routing in Social Networks
 Geographic Routing in Social Networks David Liben-Nowell Department of Computer Science, Carleton College dlibenno@carleton.edu Ravi Kumar Yahoo! Research Labs ravikumar@yahoo-inc.com Prabhakar Raghavan
Geographic Routing in Social Networks David Liben-Nowell Department of Computer Science, Carleton College dlibenno@carleton.edu Ravi Kumar Yahoo! Research Labs ravikumar@yahoo-inc.com Prabhakar Raghavan
Project in Computational Game Theory: Communities in Social Networks
 Project in Computational Game Theory: Communities in Social Networks Eldad Rubinstein November 11, 2012 1 Presentation of the Original Paper 1.1 Introduction In this section I present the article [1].
Project in Computational Game Theory: Communities in Social Networks Eldad Rubinstein November 11, 2012 1 Presentation of the Original Paper 1.1 Introduction In this section I present the article [1].
6.080 / Great Ideas in Theoretical Computer Science Spring 2008
 MIT OpenCourseWare http://ocw.mit.edu 6.080 / 6.089 Great Ideas in Theoretical Computer Science Spring 2008 For information about citing these materials or our Terms of Use, visit: http://ocw.mit.edu/terms.
MIT OpenCourseWare http://ocw.mit.edu 6.080 / 6.089 Great Ideas in Theoretical Computer Science Spring 2008 For information about citing these materials or our Terms of Use, visit: http://ocw.mit.edu/terms.
z-test, t-test Kenneth A. Ribet Math 10A November 28, 2017
 Math 10A November 28, 2017 Welcome back, Bears! This is the last week of classes. RRR Week December 4 8: This class will meet in this room on December 5, 7 for structured reviews by T. Zhu and crew. Final
Math 10A November 28, 2017 Welcome back, Bears! This is the last week of classes. RRR Week December 4 8: This class will meet in this room on December 5, 7 for structured reviews by T. Zhu and crew. Final
The Lefthanded Local Lemma characterizes chordal dependency graphs
 The Lefthanded Local Lemma characterizes chordal dependency graphs Wesley Pegden March 30, 2012 Abstract Shearer gave a general theorem characterizing the family L of dependency graphs labeled with probabilities
The Lefthanded Local Lemma characterizes chordal dependency graphs Wesley Pegden March 30, 2012 Abstract Shearer gave a general theorem characterizing the family L of dependency graphs labeled with probabilities
Communication Engineering Prof. Surendra Prasad Department of Electrical Engineering Indian Institute of Technology, Delhi
 Communication Engineering Prof. Surendra Prasad Department of Electrical Engineering Indian Institute of Technology, Delhi Lecture - 41 Pulse Code Modulation (PCM) So, if you remember we have been talking
Communication Engineering Prof. Surendra Prasad Department of Electrical Engineering Indian Institute of Technology, Delhi Lecture - 41 Pulse Code Modulation (PCM) So, if you remember we have been talking
Decision Making and Social Networks
 Decision Making and Social Networks Lecture 4: Models of Network Growth Umberto Grandi Summer 2013 Overview In the previous lecture: We got acquainted with graphs and networks We saw lots of definitions:
Decision Making and Social Networks Lecture 4: Models of Network Growth Umberto Grandi Summer 2013 Overview In the previous lecture: We got acquainted with graphs and networks We saw lots of definitions:
On the Impossibility of Black-Box Truthfulness Without Priors
 On the Impossibility of Black-Box Truthfulness Without Priors Nicole Immorlica Brendan Lucier Abstract We consider the problem of converting an arbitrary approximation algorithm for a singleparameter social
On the Impossibility of Black-Box Truthfulness Without Priors Nicole Immorlica Brendan Lucier Abstract We consider the problem of converting an arbitrary approximation algorithm for a singleparameter social
About the relationship between formal logic and complexity classes
 About the relationship between formal logic and complexity classes Working paper Comments welcome; my email: armandobcm@yahoo.com Armando B. Matos October 20, 2013 1 Introduction We analyze a particular
About the relationship between formal logic and complexity classes Working paper Comments welcome; my email: armandobcm@yahoo.com Armando B. Matos October 20, 2013 1 Introduction We analyze a particular
Chaos, Complexity, and Inference (36-462)
 Chaos, Complexity, and Inference (36-462) Lecture 21: More Networks: Models and Origin Myths Cosma Shalizi 31 March 2009 New Assignment: Implement Butterfly Mode in R Real Agenda: Models of Networks, with
Chaos, Complexity, and Inference (36-462) Lecture 21: More Networks: Models and Origin Myths Cosma Shalizi 31 March 2009 New Assignment: Implement Butterfly Mode in R Real Agenda: Models of Networks, with
Notes on Complexity Theory Last updated: November, Lecture 10
 Notes on Complexity Theory Last updated: November, 2015 Lecture 10 Notes by Jonathan Katz, lightly edited by Dov Gordon. 1 Randomized Time Complexity 1.1 How Large is BPP? We know that P ZPP = RP corp
Notes on Complexity Theory Last updated: November, 2015 Lecture 10 Notes by Jonathan Katz, lightly edited by Dov Gordon. 1 Randomized Time Complexity 1.1 How Large is BPP? We know that P ZPP = RP corp
Topic: Balanced Cut, Sparsest Cut, and Metric Embeddings Date: 3/21/2007
 CS880: Approximations Algorithms Scribe: Tom Watson Lecturer: Shuchi Chawla Topic: Balanced Cut, Sparsest Cut, and Metric Embeddings Date: 3/21/2007 In the last lecture, we described an O(log k log D)-approximation
CS880: Approximations Algorithms Scribe: Tom Watson Lecturer: Shuchi Chawla Topic: Balanced Cut, Sparsest Cut, and Metric Embeddings Date: 3/21/2007 In the last lecture, we described an O(log k log D)-approximation
FCE 3900 EDUCATIONAL RESEARCH LECTURE 8 P O P U L A T I O N A N D S A M P L I N G T E C H N I Q U E
 FCE 3900 EDUCATIONAL RESEARCH LECTURE 8 P O P U L A T I O N A N D S A M P L I N G T E C H N I Q U E OBJECTIVE COURSE Understand the concept of population and sampling in the research. Identify the type
FCE 3900 EDUCATIONAL RESEARCH LECTURE 8 P O P U L A T I O N A N D S A M P L I N G T E C H N I Q U E OBJECTIVE COURSE Understand the concept of population and sampling in the research. Identify the type
Topic 5 Notes Jeremy Orloff. 5 Homogeneous, linear, constant coefficient differential equations
 Topic 5 Notes Jeremy Orloff 5 Homogeneous, linear, constant coefficient differential equations 5.1 Goals 1. Be able to solve homogeneous constant coefficient linear differential equations using the method
Topic 5 Notes Jeremy Orloff 5 Homogeneous, linear, constant coefficient differential equations 5.1 Goals 1. Be able to solve homogeneous constant coefficient linear differential equations using the method
Social Networks- Stanley Milgram (1967)
 Complex Networs Networ is a structure of N nodes and 2M lins (or M edges) Called also graph in Mathematics Many examples of networs Internet: nodes represent computers lins the connecting cables Social
Complex Networs Networ is a structure of N nodes and 2M lins (or M edges) Called also graph in Mathematics Many examples of networs Internet: nodes represent computers lins the connecting cables Social
Chaos, Complexity, and Inference (36-462)
 Chaos, Complexity, and Inference (36-462) Lecture 21 Cosma Shalizi 3 April 2008 Models of Networks, with Origin Myths Erdős-Rényi Encore Erdős-Rényi with Node Types Watts-Strogatz Small World Graphs Exponential-Family
Chaos, Complexity, and Inference (36-462) Lecture 21 Cosma Shalizi 3 April 2008 Models of Networks, with Origin Myths Erdős-Rényi Encore Erdős-Rényi with Node Types Watts-Strogatz Small World Graphs Exponential-Family
Planning With Information States: A Survey Term Project for cs397sml Spring 2002
 Planning With Information States: A Survey Term Project for cs397sml Spring 2002 Jason O Kane jokane@uiuc.edu April 18, 2003 1 Introduction Classical planning generally depends on the assumption that the
Planning With Information States: A Survey Term Project for cs397sml Spring 2002 Jason O Kane jokane@uiuc.edu April 18, 2003 1 Introduction Classical planning generally depends on the assumption that the
A Modified Earthquake Model Based on Generalized Barabási Albert Scale-Free
 Commun. Theor. Phys. (Beijing, China) 46 (2006) pp. 1011 1016 c International Academic Publishers Vol. 46, No. 6, December 15, 2006 A Modified Earthquake Model Based on Generalized Barabási Albert Scale-Free
Commun. Theor. Phys. (Beijing, China) 46 (2006) pp. 1011 1016 c International Academic Publishers Vol. 46, No. 6, December 15, 2006 A Modified Earthquake Model Based on Generalized Barabási Albert Scale-Free
Lecture 04: Balls and Bins: Birthday Paradox. Birthday Paradox
 Lecture 04: Balls and Bins: Overview In today s lecture we will start our study of balls-and-bins problems We shall consider a fundamental problem known as the Recall: Inequalities I Lemma Before we begin,
Lecture 04: Balls and Bins: Overview In today s lecture we will start our study of balls-and-bins problems We shall consider a fundamental problem known as the Recall: Inequalities I Lemma Before we begin,
Dominating a family of graphs with small connected subgraphs
 Dominating a family of graphs with small connected subgraphs Yair Caro Raphael Yuster Abstract Let F = {G 1,..., G t } be a family of n-vertex graphs defined on the same vertex-set V, and let k be a positive
Dominating a family of graphs with small connected subgraphs Yair Caro Raphael Yuster Abstract Let F = {G 1,..., G t } be a family of n-vertex graphs defined on the same vertex-set V, and let k be a positive
Class Note #20. In today s class, the following four concepts were introduced: decision
 Class Note #20 Date: 03/29/2006 [Overall Information] In today s class, the following four concepts were introduced: decision version of a problem, formal language, P and NP. We also discussed the relationship
Class Note #20 Date: 03/29/2006 [Overall Information] In today s class, the following four concepts were introduced: decision version of a problem, formal language, P and NP. We also discussed the relationship
12. LOCAL SEARCH. gradient descent Metropolis algorithm Hopfield neural networks maximum cut Nash equilibria
 Coping With NP-hardness Q. Suppose I need to solve an NP-hard problem. What should I do? A. Theory says you re unlikely to find poly-time algorithm. Must sacrifice one of three desired features. Solve
Coping With NP-hardness Q. Suppose I need to solve an NP-hard problem. What should I do? A. Theory says you re unlikely to find poly-time algorithm. Must sacrifice one of three desired features. Solve
Session-Based Queueing Systems
 Session-Based Queueing Systems Modelling, Simulation, and Approximation Jeroen Horters Supervisor VU: Sandjai Bhulai Executive Summary Companies often offer services that require multiple steps on the
Session-Based Queueing Systems Modelling, Simulation, and Approximation Jeroen Horters Supervisor VU: Sandjai Bhulai Executive Summary Companies often offer services that require multiple steps on the
Lecture 3: Randomness in Computation
 Great Ideas in Theoretical Computer Science Summer 2013 Lecture 3: Randomness in Computation Lecturer: Kurt Mehlhorn & He Sun Randomness is one of basic resources and appears everywhere. In computer science,
Great Ideas in Theoretical Computer Science Summer 2013 Lecture 3: Randomness in Computation Lecturer: Kurt Mehlhorn & He Sun Randomness is one of basic resources and appears everywhere. In computer science,
CHAPTER 1: Functions
 CHAPTER 1: Functions 1.1: Functions 1.2: Graphs of Functions 1.3: Basic Graphs and Symmetry 1.4: Transformations 1.5: Piecewise-Defined Functions; Limits and Continuity in Calculus 1.6: Combining Functions
CHAPTER 1: Functions 1.1: Functions 1.2: Graphs of Functions 1.3: Basic Graphs and Symmetry 1.4: Transformations 1.5: Piecewise-Defined Functions; Limits and Continuity in Calculus 1.6: Combining Functions
A multiplicative deformation of the Möbius function for the poset of partitions of a multiset
 Contemporary Mathematics A multiplicative deformation of the Möbius function for the poset of partitions of a multiset Patricia Hersh and Robert Kleinberg Abstract. The Möbius function of a partially ordered
Contemporary Mathematics A multiplicative deformation of the Möbius function for the poset of partitions of a multiset Patricia Hersh and Robert Kleinberg Abstract. The Möbius function of a partially ordered
CS264: Beyond Worst-Case Analysis Lecture #15: Smoothed Complexity and Pseudopolynomial-Time Algorithms
 CS264: Beyond Worst-Case Analysis Lecture #15: Smoothed Complexity and Pseudopolynomial-Time Algorithms Tim Roughgarden November 5, 2014 1 Preamble Previous lectures on smoothed analysis sought a better
CS264: Beyond Worst-Case Analysis Lecture #15: Smoothed Complexity and Pseudopolynomial-Time Algorithms Tim Roughgarden November 5, 2014 1 Preamble Previous lectures on smoothed analysis sought a better
All instruction should be three-dimensional. Page 1 of 11
 High School Modified Domains Model Course II - Physics Bundle 4: How Do We Use Energy to Communicate with Each Other? This is the fourth bundle of the High School Domains Model Course II - Physics. Each
High School Modified Domains Model Course II - Physics Bundle 4: How Do We Use Energy to Communicate with Each Other? This is the fourth bundle of the High School Domains Model Course II - Physics. Each
Introduction. Introductory Remarks
 Introductory Remarks This is probably your first real course in quantum mechanics. To be sure, it is understood that you have encountered an introduction to some of the basic concepts, phenomenology, history,
Introductory Remarks This is probably your first real course in quantum mechanics. To be sure, it is understood that you have encountered an introduction to some of the basic concepts, phenomenology, history,
Network Science (overview, part 1)
 Network Science (overview, part 1) Ralucca Gera, Applied Mathematics Dept. Naval Postgraduate School Monterey, California rgera@nps.edu Excellence Through Knowledge Overview Current research Section 1:
Network Science (overview, part 1) Ralucca Gera, Applied Mathematics Dept. Naval Postgraduate School Monterey, California rgera@nps.edu Excellence Through Knowledge Overview Current research Section 1:
27 : Distributed Monte Carlo Markov Chain. 1 Recap of MCMC and Naive Parallel Gibbs Sampling
 10-708: Probabilistic Graphical Models 10-708, Spring 2014 27 : Distributed Monte Carlo Markov Chain Lecturer: Eric P. Xing Scribes: Pengtao Xie, Khoa Luu In this scribe, we are going to review the Parallel
10-708: Probabilistic Graphical Models 10-708, Spring 2014 27 : Distributed Monte Carlo Markov Chain Lecturer: Eric P. Xing Scribes: Pengtao Xie, Khoa Luu In this scribe, we are going to review the Parallel
Not all counting problems are efficiently approximable. We open with a simple example.
 Chapter 7 Inapproximability Not all counting problems are efficiently approximable. We open with a simple example. Fact 7.1. Unless RP = NP there can be no FPRAS for the number of Hamilton cycles in a
Chapter 7 Inapproximability Not all counting problems are efficiently approximable. We open with a simple example. Fact 7.1. Unless RP = NP there can be no FPRAS for the number of Hamilton cycles in a
On a Conjecture of Thomassen
 On a Conjecture of Thomassen Michelle Delcourt Department of Mathematics University of Illinois Urbana, Illinois 61801, U.S.A. delcour2@illinois.edu Asaf Ferber Department of Mathematics Yale University,
On a Conjecture of Thomassen Michelle Delcourt Department of Mathematics University of Illinois Urbana, Illinois 61801, U.S.A. delcour2@illinois.edu Asaf Ferber Department of Mathematics Yale University,
Small subgraphs of random regular graphs
 Discrete Mathematics 307 (2007 1961 1967 Note Small subgraphs of random regular graphs Jeong Han Kim a,b, Benny Sudakov c,1,vanvu d,2 a Theory Group, Microsoft Research, Redmond, WA 98052, USA b Department
Discrete Mathematics 307 (2007 1961 1967 Note Small subgraphs of random regular graphs Jeong Han Kim a,b, Benny Sudakov c,1,vanvu d,2 a Theory Group, Microsoft Research, Redmond, WA 98052, USA b Department
CS264: Beyond Worst-Case Analysis Lecture #11: LP Decoding
 CS264: Beyond Worst-Case Analysis Lecture #11: LP Decoding Tim Roughgarden October 29, 2014 1 Preamble This lecture covers our final subtopic within the exact and approximate recovery part of the course.
CS264: Beyond Worst-Case Analysis Lecture #11: LP Decoding Tim Roughgarden October 29, 2014 1 Preamble This lecture covers our final subtopic within the exact and approximate recovery part of the course.
Lecture 1 and 2: Introduction and Graph theory basics. Spring EE 194, Networked estimation and control (Prof. Khan) January 23, 2012
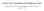 Lecture 1 and 2: Introduction and Graph theory basics Spring 2012 - EE 194, Networked estimation and control (Prof. Khan) January 23, 2012 Spring 2012: EE-194-02 Networked estimation and control Schedule
Lecture 1 and 2: Introduction and Graph theory basics Spring 2012 - EE 194, Networked estimation and control (Prof. Khan) January 23, 2012 Spring 2012: EE-194-02 Networked estimation and control Schedule
Predicting AGI: What can we say when we know so little?
 Predicting AGI: What can we say when we know so little? Fallenstein, Benja Mennen, Alex December 2, 2013 (Working Paper) 1 Time to taxi Our situation now looks fairly similar to our situation 20 years
Predicting AGI: What can we say when we know so little? Fallenstein, Benja Mennen, Alex December 2, 2013 (Working Paper) 1 Time to taxi Our situation now looks fairly similar to our situation 20 years
AN APPLICATION OF LINEAR ALGEBRA TO NETWORKS
 AN APPLICATION OF LINEAR ALGEBRA TO NETWORKS K. N. RAGHAVAN 1. Statement of the problem Imagine that between two nodes there is a network of electrical connections, as for example in the following picture
AN APPLICATION OF LINEAR ALGEBRA TO NETWORKS K. N. RAGHAVAN 1. Statement of the problem Imagine that between two nodes there is a network of electrical connections, as for example in the following picture
Mathematics: applications and interpretation SL
 Mathematics: applications and interpretation SL Chapter 1: Approximations and error A Rounding numbers B Approximations C Errors in measurement D Absolute and percentage error The first two sections of
Mathematics: applications and interpretation SL Chapter 1: Approximations and error A Rounding numbers B Approximations C Errors in measurement D Absolute and percentage error The first two sections of
Modeling of Growing Networks with Directional Attachment and Communities
 Modeling of Growing Networks with Directional Attachment and Communities Masahiro KIMURA, Kazumi SAITO, Naonori UEDA NTT Communication Science Laboratories 2-4 Hikaridai, Seika-cho, Kyoto 619-0237, Japan
Modeling of Growing Networks with Directional Attachment and Communities Masahiro KIMURA, Kazumi SAITO, Naonori UEDA NTT Communication Science Laboratories 2-4 Hikaridai, Seika-cho, Kyoto 619-0237, Japan
A Mathematical Theory of Communication
 A Mathematical Theory of Communication Ben Eggers Abstract This paper defines information-theoretic entropy and proves some elementary results about it. Notably, we prove that given a few basic assumptions
A Mathematical Theory of Communication Ben Eggers Abstract This paper defines information-theoretic entropy and proves some elementary results about it. Notably, we prove that given a few basic assumptions
