The Field: Introduction to complex numbers
|
|
|
- Rosalyn Wiggins
- 6 years ago
- Views:
Transcription
1 [1] The Field
2 The Field: Introduction to complex numbers Solutions to x 2 = 1? Mathematicians invented i to be one solution Guest Week: Bill Amend (excerpt, Can use i to solve other equations, e.g.: Solution is x = 3i x 2 = 9
3 Introduction to complex numbers Numbers such as i, i, 3i, 2.17i are called imaginary numbers. Math Paper (
4 The Field: Introduction to complex numbers Solution to (x 1) 2 = 9? One is x = 1 + 3i. A real number plus an imaginary number is a complex number. A complex number has a real part and an imaginary part. complex number = (real part) + (imaginary part) i
5 The Field: Complex numbers in Python
6 Abstracting over Fields Overloading: Same names (+, etc.) used in Python for operations on real numbers and for operations complex numbers Write procedure solve(a,b,c) to solve ax + b = c: >>> def solve(a,b,c): return (c-b)/a Can now solve equation 10x + 5 = 30: >>> solve(10, 5, 30) 2.5 Can also solve equation (10 + 5i)x + 5 = 20: >>> solve(10+5j, 5, 20) ( j) Same procedure works on complex numbers.
7 Abstracting over Fields Why does procedure works with complex numbers? Correctness based on: / is inverse of * - is inverse of + Similarly, much of linear algebra based just on +, -, *, / and algebraic properties / is inverse of * - is inverse of + addition is commutative: a + b = b + a multiplication distributes over addition: a (b + c) = a b + a c etc. You can plug in any collection of numbers with arithmetic operators +, -, *, / satisfying the algebraic properties and much of linear algebra will still work. Such a collection of numbers with +, -, *, / is called a field. Different fields are like different classes obeying the same interface.
8 Field notation When we want to refer to a field without specifying which field, we will use the notation F.
9 Abstracting over Fields We study three fields: The field R of real numbers The field C of complex numbers The finite field GF (2), which consists of 0 and 1 under mod 2 arithmetic. Reasons for studying the field C of complex numbers: C is similar enough to R to be familiar but different enough to illustrate the idea of a field. Complex numbers are built into Python. Complex numbers are the intellectual ancestors of vectors. In more advanced parts of linear algebra (to be covered in a follow-on course), complex numbers play an important role.
10 Complex numbers as points in the complex plane Can interpret real and imaginary parts of a complex number as x and y coordinates. Thus can interpret a complex number as a point in the plane z.imag z z.real (the complex plane)
11 Playing with C
12 Playing with C: The absolute value of a complex number Absolute value of z = distance from the origin to the point z in the complex plane. z.imag z length z z.real In Mathese, written z. In Python, written abs(z).
13 Playing with C: Adding complex numbers Geometric interpretation of f (z) = z + (1 + 2i)? Increase each real coordinate by 1 and increases each imaginary coordinate by 2. f (z) = z + (1 + 2i) is called a translation.
14 Playing with C: Adding complex numbers Translation in general: f (z) = z + z 0 where z 0 is a complex number. A translation can move the picture anywhere in the complex plane.
15 Playing with C: Adding complex numbers Quiz: The left eye of the list L of complex numbers is located at 2 + 2i. For what complex number z 0 does the translation move the left eye to the origin 0 + 0i? f (z) = z + z 0 Answer: z 0 = 2 2i
16 Playing with C: Adding complex numbers: Complex numbers as arrows Interpret z 0 as representing the translation f (z) = z + z 0. Visualize a complex number z 0 as an arrow. Arrow s tail located an any point z Arrow s head located at z + z 0 Shows an example of what the translation f (z) = z + z 0 does z 0 + z z 0 z
17 Playing with C: Adding complex numbers: Complex numbers as arrows Example: Represent 6 + 5i as an arrow.
18 Playing with C: Adding complex numbers: Composing translations, adding arrows Consider two complex numbers z 1 and z 2. They correspond to translations f 1 (z) = z + z 1 and f 2 (z) = z + z 2 Functional composition: (f 1 f 2 )(z) = z + z 1 + z 2 Represent functional composition by adding arrows. Example: z 1 = 2 + 3i and z 2 = 3 + 1i
19 Playing with C: Multiplying complex numbers by a positive real number f (z) = 0.5 z Multiply each complex number by 0.5 Arrow in same direction but half the length. Scaling
20 Playing with C: Multiplying complex numbers by a negative number f (z) = ( 1) z Multiply each complex number by -1 Arrow in opposite direction Rotation by 180 degrees
21 Playing with C: Multiplying by i: rotation by 90 degrees How to rotate counterclockwise by 90? Need x + y i y + x i Use i(x + yi) = x i + y i 2 = x i y f (z) = i z
22 Playing with C: The unit circle in the complex plane: argument and angle What about rotating by another angle? Definition: Argument of z is the angle in radians between z arrow and 1 + 0i arrow. z z argument of z z argument of z argument of z Rotating a complex number z means increasing its argument.
23 Playing with C: Euler s formula He calculated just as men breathe, as eagles sustain themselves in the air. Said of Leonhard Euler Euler s formula: For any real number θ, e θ i is the point z on the unit circle with argument θ. z = e i 4 = 4 e =
24 Playing with C: Euler s formula Euler s formula: For any real number θ, e θ i is the point z on the unit circle with argument θ. Plug in θ = π... z = e i = 1
25 Playing with C: Euler s formula Plot e 0 2πi 20, e 1 2πi 20, e 2 2πi 20, e 3 2πi 20,..., e 19 2πi 20
26 Playing with C: Rotation by τ radians Back to question of rotation by any angle τ. Every complex number can be written in the form z = re θi r is the absolute value of z θ is the argument of z Need to increase the argument of z Use exponentiation law e a e b = e a+b re θi e τi = re θi+τi = re (θ+τ)i f (z) = z e τi does rotation by angle τ.
27 Playing with C: Rotation by τ radians Rotation by 3π/4
28 Playing with GF (2) Galois Field 2 has just two elements: 0 and 1 Addition is like exclusive-or: Multiplication is like ordinary multiplication Evariste Galois, Usual algebraic laws still hold, e.g. multiplication distributes over addition a (b + c) = a b + a c
29 GF (2) in Python We provide a module GF2 that defines a value one. This value acts like 1 in GF (2): >>> from GF2 import one >>> one + one 0 >>> one * one one >>> one * 0 0 >>> one/one one We will use one in coding with GF (2).
30 Playing with GF (2): Encryption Alice wants to arrange with Bob to communicate one bit p (the plaintext). To ensure privacy, they use a cryptosystem: Alice and Bob agree beforehand on a secret key k. Alice encrypts the plaintext p using the key k, obtaining the cyphertext c according to the table p k c Q: Can Bob uniquely decrypt the cyphertext? A: Yes: for any value of k and any value of c, there is just one consistent value for p. An eavesdropper, Eve, observes the value of c (but does not know the key k). Question: Does Eve learn anything about the value of p? Simple answer: No: if c = 0, Eve doesn t know if p = 0 or p = 1 (both are consistent with c = 0). if c = 1, Eve doesn t know if p = 0 or p = 1 (both are consistent with c = 1). More sophisticated answer: It depends on how the secret key k is chosen. Suppose k is chosen by flipping a coin: 1
31 Playing with GF (2): One-to-one and onto function and perfect secrecy What is it about this cryptosystem that leads to perfect secrecy? Why does Eve learn nothing from eavesdropping? p k c Define f 0 : GF (2) GF (2) by Define f 1 : GF (2) GF (2) by f 0 (k) =encryption of p = 0 with key k f 1 (k) =encryption of p = 1 with key k According to the first two rows of the table, According to the last two rows of the table, f 0 (0) = 0 and f 0 (1) = 1 f 1 (0) = 1 and f 1 (1) = 0 This function is one-to-one and onto. This function is one-to-one and onto. When key k is chosen uniformly at random When key k is chosen uniformly at random Prob[k = 0] = 1 2, Prob[k = 1] = 1 2 Prob[k = 0] = 1 2, Prob[k = 1] = 1 2 the probability distribution of the output the probability distribution of the output f 0 (k) = p is also uniform: f 1 (k) = p is also uniform: Prob[f 0 (k) = 0] = 1 2, Prob[f 0(k) = 1] = 1 2 Prob[f 1 (k) = 1] = 1 2, Prob[f 1(k) = 0] = 1 2 The probability distribution of the cyphertext does not depend on the plaintext!
32 Perfect secrecy Idea is the basis for cryptosystem: the one-time pad. p k c If each bit is encrypted with its own one-bit key, the cryptosystem is unbreakable In the 1940 s the Soviets started re-using bits of key that had already been used. Unfortunately for them, this was discovered by the US Army s Signal Intelligence Service in the top-secret VENONA project. This led to a tiny but historically significant portion of the Soviet traffic being cracked, including intelligence on spies such as Julius Rosenberg and Donald Maclean, and Soviet espionage on US technology including nuclear weapons. The public only learned of VENONA when it was declassified in 1995.
33 Playing with GF (2): Network coding s Streaming video through a network one customer no problem two customers contention! do computation at intermediate nodes avoids contention Network coding doubles throughput in this example! c d
34 Playing with GF (2): Network coding Streaming video through a network one customer no problem two customers contention! s b 1 b 2 do computation at intermediate nodes avoids contention Network coding doubles throughput in this example! c d
35 Playing with GF (2): Network coding Streaming video through a network one customer no problem two customers contention! do computation at intermediate nodes avoids contention s b 1 b 2 Two bits contend for same link Network coding doubles throughput in this example! c d
36 Playing with GF (2): Network coding Streaming video through a network one customer no problem two customers contention! do computation at intermediate nodes avoids contention s b 1 b 2 b 1 + b 2 Network coding doubles throughput in this example! c d
Playing with C: Reflectingaboutthereal/imaginaryaxis. Reflecting about the real axis: Use complex conjugate z 7! z
 Playing with C: Reflectingaboutthereal/imaginaryaxis Reflecting about the real axis: Use complex conjugate z 7! z Playing with C: Multiplyingcomplexnumbersbyapositiverealnumber f (z) =0.5 z Multiply each
Playing with C: Reflectingaboutthereal/imaginaryaxis Reflecting about the real axis: Use complex conjugate z 7! z Playing with C: Multiplyingcomplexnumbersbyapositiverealnumber f (z) =0.5 z Multiply each
Vector addition: The zero vector. The D-vector whose entries are all zero is the zero vector, written 0 D or just 0
 Vector addition: The zero vector The D-vector whose entries are all zero is the zero vector, written 0 D or just 0 v + 0 = v Vector addition: Vector addition is associative and commutative I Associativity
Vector addition: The zero vector The D-vector whose entries are all zero is the zero vector, written 0 D or just 0 v + 0 = v Vector addition: Vector addition is associative and commutative I Associativity
8 Elliptic Curve Cryptography
 8 Elliptic Curve Cryptography 8.1 Elliptic Curves over a Finite Field For the purposes of cryptography, we want to consider an elliptic curve defined over a finite field F p = Z/pZ for p a prime. Given
8 Elliptic Curve Cryptography 8.1 Elliptic Curves over a Finite Field For the purposes of cryptography, we want to consider an elliptic curve defined over a finite field F p = Z/pZ for p a prime. Given
Solution to Midterm Examination
 YALE UNIVERSITY DEPARTMENT OF COMPUTER SCIENCE CPSC 467a: Cryptography and Computer Security Handout #13 Xueyuan Su November 4, 2008 Instructions: Solution to Midterm Examination This is a closed book
YALE UNIVERSITY DEPARTMENT OF COMPUTER SCIENCE CPSC 467a: Cryptography and Computer Security Handout #13 Xueyuan Su November 4, 2008 Instructions: Solution to Midterm Examination This is a closed book
Historical cryptography. cryptography encryption main applications: military and diplomacy
 Historical cryptography cryptography encryption main applications: military and diplomacy ancient times world war II Historical cryptography All historical cryptosystems badly broken! No clear understanding
Historical cryptography cryptography encryption main applications: military and diplomacy ancient times world war II Historical cryptography All historical cryptosystems badly broken! No clear understanding
PERFECT SECRECY AND ADVERSARIAL INDISTINGUISHABILITY
 PERFECT SECRECY AND ADVERSARIAL INDISTINGUISHABILITY BURTON ROSENBERG UNIVERSITY OF MIAMI Contents 1. Perfect Secrecy 1 1.1. A Perfectly Secret Cipher 2 1.2. Odds Ratio and Bias 3 1.3. Conditions for Perfect
PERFECT SECRECY AND ADVERSARIAL INDISTINGUISHABILITY BURTON ROSENBERG UNIVERSITY OF MIAMI Contents 1. Perfect Secrecy 1 1.1. A Perfectly Secret Cipher 2 1.2. Odds Ratio and Bias 3 1.3. Conditions for Perfect
Cryptography and RSA. Group (1854, Cayley) Upcoming Interview? Outline. Commutative or Abelian Groups
 Great Theoretical Ideas in CS V. Adamchik CS 15-251 Upcoming Interview? Lecture 24 Carnegie Mellon University Cryptography and RSA How the World's Smartest Company Selects the Most Creative Thinkers Groups
Great Theoretical Ideas in CS V. Adamchik CS 15-251 Upcoming Interview? Lecture 24 Carnegie Mellon University Cryptography and RSA How the World's Smartest Company Selects the Most Creative Thinkers Groups
The symmetric group R + :1! 2! 3! 1. R :1! 3! 2! 1.
 Chapter 2 The symmetric group Consider the equilateral triangle. 3 1 2 We want to describe all the symmetries, which are the motions (both rotations and flips) which takes the triangle to itself. First
Chapter 2 The symmetric group Consider the equilateral triangle. 3 1 2 We want to describe all the symmetries, which are the motions (both rotations and flips) which takes the triangle to itself. First
Univ.-Prof. Dr. rer. nat. Rudolf Mathar. Written Examination. Cryptography. Tuesday, August 29, 2017, 01:30 p.m.
 Cryptography Univ.-Prof. Dr. rer. nat. Rudolf Mathar 1 2 3 4 15 15 15 15 60 Written Examination Cryptography Tuesday, August 29, 2017, 01:30 p.m. Name: Matr.-No.: Field of study: Please pay attention to
Cryptography Univ.-Prof. Dr. rer. nat. Rudolf Mathar 1 2 3 4 15 15 15 15 60 Written Examination Cryptography Tuesday, August 29, 2017, 01:30 p.m. Name: Matr.-No.: Field of study: Please pay attention to
Algebra for Cryptology
 Algebra for Cryptology Arkadii Slinko Department of Mathematics The University of Auckland Auckland, 6 April, 2013 What is cryptology? Cryptology is about communication in the presence of adversaries or
Algebra for Cryptology Arkadii Slinko Department of Mathematics The University of Auckland Auckland, 6 April, 2013 What is cryptology? Cryptology is about communication in the presence of adversaries or
Outline. CPSC 418/MATH 318 Introduction to Cryptography. Information Theory. Partial Information. Perfect Secrecy, One-Time Pad
 Outline CPSC 418/MATH 318 Introduction to Cryptography, One-Time Pad Renate Scheidler Department of Mathematics & Statistics Department of Computer Science University of Calgary Based in part on slides
Outline CPSC 418/MATH 318 Introduction to Cryptography, One-Time Pad Renate Scheidler Department of Mathematics & Statistics Department of Computer Science University of Calgary Based in part on slides
Cryptography. Lecture 2: Perfect Secrecy and its Limitations. Gil Segev
 Cryptography Lecture 2: Perfect Secrecy and its Limitations Gil Segev Last Week Symmetric-key encryption (KeyGen, Enc, Dec) Historical ciphers that are completely broken The basic principles of modern
Cryptography Lecture 2: Perfect Secrecy and its Limitations Gil Segev Last Week Symmetric-key encryption (KeyGen, Enc, Dec) Historical ciphers that are completely broken The basic principles of modern
Lecture Notes, Week 6
 YALE UNIVERSITY DEPARTMENT OF COMPUTER SCIENCE CPSC 467b: Cryptography and Computer Security Week 6 (rev. 3) Professor M. J. Fischer February 15 & 17, 2005 1 RSA Security Lecture Notes, Week 6 Several
YALE UNIVERSITY DEPARTMENT OF COMPUTER SCIENCE CPSC 467b: Cryptography and Computer Security Week 6 (rev. 3) Professor M. J. Fischer February 15 & 17, 2005 1 RSA Security Lecture Notes, Week 6 Several
CSE 311 Lecture 11: Modular Arithmetic. Emina Torlak and Kevin Zatloukal
 CSE 311 Lecture 11: Modular Arithmetic Emina Torlak and Kevin Zatloukal 1 Topics Sets and set operations A quick wrap-up of Lecture 10. Modular arithmetic basics Arithmetic over a finite domain (a.k.a
CSE 311 Lecture 11: Modular Arithmetic Emina Torlak and Kevin Zatloukal 1 Topics Sets and set operations A quick wrap-up of Lecture 10. Modular arithmetic basics Arithmetic over a finite domain (a.k.a
Cryptography 2017 Lecture 2
 Cryptography 2017 Lecture 2 One Time Pad - Perfect Secrecy Stream Ciphers November 3, 2017 1 / 39 What have seen? What are we discussing today? Lecture 1 Course Intro Historical Ciphers Lecture 2 One Time
Cryptography 2017 Lecture 2 One Time Pad - Perfect Secrecy Stream Ciphers November 3, 2017 1 / 39 What have seen? What are we discussing today? Lecture 1 Course Intro Historical Ciphers Lecture 2 One Time
3 Vectors. 18 October 2018 PHY101 Physics I Dr.Cem Özdoğan
 Chapter 3 Vectors 3 Vectors 18 October 2018 PHY101 Physics I Dr.Cem Özdoğan 2 3 3-2 Vectors and Scalars Physics deals with many quantities that have both size and direction. It needs a special mathematical
Chapter 3 Vectors 3 Vectors 18 October 2018 PHY101 Physics I Dr.Cem Özdoğan 2 3 3-2 Vectors and Scalars Physics deals with many quantities that have both size and direction. It needs a special mathematical
CPSC 467b: Cryptography and Computer Security
 CPSC 467b: Cryptography and Computer Security Michael J. Fischer Lecture 3 January 22, 2013 CPSC 467b, Lecture 3 1/35 Perfect secrecy Caesar cipher Loss of perfection Classical ciphers One-time pad Affine
CPSC 467b: Cryptography and Computer Security Michael J. Fischer Lecture 3 January 22, 2013 CPSC 467b, Lecture 3 1/35 Perfect secrecy Caesar cipher Loss of perfection Classical ciphers One-time pad Affine
Bits. Chapter 1. Information can be learned through observation, experiment, or measurement.
 Chapter 1 Bits Information is measured in bits, just as length is measured in meters and time is measured in seconds. Of course knowing the amount of information is not the same as knowing the information
Chapter 1 Bits Information is measured in bits, just as length is measured in meters and time is measured in seconds. Of course knowing the amount of information is not the same as knowing the information
Solutions for week 1, Cryptography Course - TDA 352/DIT 250
 Solutions for week, Cryptography Course - TDA 352/DIT 250 In this weekly exercise sheet: you will use some historical ciphers, the OTP, the definition of semantic security and some combinatorial problems.
Solutions for week, Cryptography Course - TDA 352/DIT 250 In this weekly exercise sheet: you will use some historical ciphers, the OTP, the definition of semantic security and some combinatorial problems.
Vectors Picturing vectors Properties of vectors Linear combination Span. Vectors. Math 4A Scharlemann. 9 January /31
 1/31 Vectors Math 4A Scharlemann 9 January 2015 2/31 CELL PHONES OFF 3/31 An m-vector [column vector, vector in R m ] is an m 1 matrix: a 1 a 2 a = a 3. a m 3/31 An m-vector [column vector, vector in R
1/31 Vectors Math 4A Scharlemann 9 January 2015 2/31 CELL PHONES OFF 3/31 An m-vector [column vector, vector in R m ] is an m 1 matrix: a 1 a 2 a = a 3. a m 3/31 An m-vector [column vector, vector in R
3 What You Should Know About Complex Numbers
 3 What You Should Know About Complex Numbers Life is complex it has a real part, and an imaginary part Andrew Koenig. Complex numbers are an extension of the more familiar world of real numbers that make
3 What You Should Know About Complex Numbers Life is complex it has a real part, and an imaginary part Andrew Koenig. Complex numbers are an extension of the more familiar world of real numbers that make
Perfectly-Secret Encryption
 Perfectly-Secret Encryption CSE 5351: Introduction to Cryptography Reading assignment: Read Chapter 2 You may sip proofs, but are encouraged to read some of them. 1 Outline Definition of encryption schemes
Perfectly-Secret Encryption CSE 5351: Introduction to Cryptography Reading assignment: Read Chapter 2 You may sip proofs, but are encouraged to read some of them. 1 Outline Definition of encryption schemes
CPSC 467b: Cryptography and Computer Security
 CPSC 467b: Cryptography and Computer Security Michael J. Fischer Lecture 11 February 21, 2013 CPSC 467b, Lecture 11 1/27 Discrete Logarithm Diffie-Hellman Key Exchange ElGamal Key Agreement Primitive Roots
CPSC 467b: Cryptography and Computer Security Michael J. Fischer Lecture 11 February 21, 2013 CPSC 467b, Lecture 11 1/27 Discrete Logarithm Diffie-Hellman Key Exchange ElGamal Key Agreement Primitive Roots
Quantum Cryptography
 Quantum Cryptography (Notes for Course on Quantum Computation and Information Theory. Sec. 13) Robert B. Griffiths Version of 26 March 2003 References: Gisin = N. Gisin et al., Rev. Mod. Phys. 74, 145
Quantum Cryptography (Notes for Course on Quantum Computation and Information Theory. Sec. 13) Robert B. Griffiths Version of 26 March 2003 References: Gisin = N. Gisin et al., Rev. Mod. Phys. 74, 145
Topics. Probability Theory. Perfect Secrecy. Information Theory
 Topics Probability Theory Perfect Secrecy Information Theory Some Terms (P,C,K,E,D) Computational Security Computational effort required to break cryptosystem Provable Security Relative to another, difficult
Topics Probability Theory Perfect Secrecy Information Theory Some Terms (P,C,K,E,D) Computational Security Computational effort required to break cryptosystem Provable Security Relative to another, difficult
Number theory (Chapter 4)
 EECS 203 Spring 2016 Lecture 12 Page 1 of 8 Number theory (Chapter 4) Review Compute 6 11 mod 13 in an efficient way What is the prime factorization of 100? 138? What is gcd(100, 138)? What is lcm(100,138)?
EECS 203 Spring 2016 Lecture 12 Page 1 of 8 Number theory (Chapter 4) Review Compute 6 11 mod 13 in an efficient way What is the prime factorization of 100? 138? What is gcd(100, 138)? What is lcm(100,138)?
MODULAR ARITHMETIC KEITH CONRAD
 MODULAR ARITHMETIC KEITH CONRAD. Introduction We will define the notion of congruent integers (with respect to a modulus) and develop some basic ideas of modular arithmetic. Applications of modular arithmetic
MODULAR ARITHMETIC KEITH CONRAD. Introduction We will define the notion of congruent integers (with respect to a modulus) and develop some basic ideas of modular arithmetic. Applications of modular arithmetic
Slides by Kent Seamons and Tim van der Horst Last Updated: Oct 1, 2013
 RSA Slides by Kent Seamons and Tim van der Horst Last Updated: Oct 1, 2013 Recap Recap Number theory o What is a prime number? o What is prime factorization? o What is a GCD? o What does relatively prime
RSA Slides by Kent Seamons and Tim van der Horst Last Updated: Oct 1, 2013 Recap Recap Number theory o What is a prime number? o What is prime factorization? o What is a GCD? o What does relatively prime
MATH.2720 Introduction to Programming with MATLAB Vector and Matrix Algebra
 MATH.2720 Introduction to Programming with MATLAB Vector and Matrix Algebra A. Vectors A vector is a quantity that has both magnitude and direction, like velocity. The location of a vector is irrelevant;
MATH.2720 Introduction to Programming with MATLAB Vector and Matrix Algebra A. Vectors A vector is a quantity that has both magnitude and direction, like velocity. The location of a vector is irrelevant;
Solution of Exercise Sheet 6
 Foundations of Cybersecurity (Winter 16/17) Prof. Dr. Michael Backes CISPA / Saarland University saarland university computer science Solution of Exercise Sheet 6 1 Perfect Secrecy Answer the following
Foundations of Cybersecurity (Winter 16/17) Prof. Dr. Michael Backes CISPA / Saarland University saarland university computer science Solution of Exercise Sheet 6 1 Perfect Secrecy Answer the following
CS 282A/MATH 209A: Foundations of Cryptography Prof. Rafail Ostrosky. Lecture 4
 CS 282A/MATH 209A: Foundations of Cryptography Prof. Rafail Ostrosky Lecture 4 Lecture date: January 26, 2005 Scribe: Paul Ray, Mike Welch, Fernando Pereira 1 Private Key Encryption Consider a game between
CS 282A/MATH 209A: Foundations of Cryptography Prof. Rafail Ostrosky Lecture 4 Lecture date: January 26, 2005 Scribe: Paul Ray, Mike Welch, Fernando Pereira 1 Private Key Encryption Consider a game between
Final Exam Math 105: Topics in Mathematics Cryptology, the Science of Secret Writing Rhodes College Tuesday, 30 April :30 11:00 a.m.
 Final Exam Math 10: Topics in Mathematics Cryptology, the Science of Secret Writing Rhodes College Tuesday, 0 April 2002 :0 11:00 a.m. Instructions: Please be as neat as possible (use a pencil), and show
Final Exam Math 10: Topics in Mathematics Cryptology, the Science of Secret Writing Rhodes College Tuesday, 0 April 2002 :0 11:00 a.m. Instructions: Please be as neat as possible (use a pencil), and show
VECTORS. 3-1 What is Physics? 3-2 Vectors and Scalars CHAPTER
 CHAPTER 3 VECTORS 3-1 What is Physics? Physics deals with a great many quantities that have both size and direction, and it needs a special mathematical language the language of vectors to describe those
CHAPTER 3 VECTORS 3-1 What is Physics? Physics deals with a great many quantities that have both size and direction, and it needs a special mathematical language the language of vectors to describe those
Math 416, Spring 2010 More on Algebraic and Geometric Properties January 21, 2010 MORE ON ALGEBRAIC AND GEOMETRIC PROPERTIES
 Math 46, Spring 2 More on Algebraic and Geometric Properties January 2, 2 MORE ON ALGEBRAIC AND GEOMETRIC PROPERTIES Algebraic properties Algebraic properties of matrix/vector multiplication Last time
Math 46, Spring 2 More on Algebraic and Geometric Properties January 2, 2 MORE ON ALGEBRAIC AND GEOMETRIC PROPERTIES Algebraic properties Algebraic properties of matrix/vector multiplication Last time
C. Complex Numbers. 1. Complex arithmetic.
 C. Complex Numbers. Complex arithmetic. Most people think that complex numbers arose from attempts to solve quadratic equations, but actually it was in connection with cubic equations they first appeared.
C. Complex Numbers. Complex arithmetic. Most people think that complex numbers arose from attempts to solve quadratic equations, but actually it was in connection with cubic equations they first appeared.
An Intuitive Introduction to Motivic Homotopy Theory Vladimir Voevodsky
 What follows is Vladimir Voevodsky s snapshot of his Fields Medal work on motivic homotopy, plus a little philosophy and from my point of view the main fun of doing mathematics Voevodsky (2002). Voevodsky
What follows is Vladimir Voevodsky s snapshot of his Fields Medal work on motivic homotopy, plus a little philosophy and from my point of view the main fun of doing mathematics Voevodsky (2002). Voevodsky
MATH3302 Cryptography Problem Set 2
 MATH3302 Cryptography Problem Set 2 These questions are based on the material in Section 4: Shannon s Theory, Section 5: Modern Cryptography, Section 6: The Data Encryption Standard, Section 7: International
MATH3302 Cryptography Problem Set 2 These questions are based on the material in Section 4: Shannon s Theory, Section 5: Modern Cryptography, Section 6: The Data Encryption Standard, Section 7: International
Definition: For a positive integer n, if 0<a<n and gcd(a,n)=1, a is relatively prime to n. Ahmet Burak Can Hacettepe University
 Number Theory, Public Key Cryptography, RSA Ahmet Burak Can Hacettepe University abc@hacettepe.edu.tr The Euler Phi Function For a positive integer n, if 0
Number Theory, Public Key Cryptography, RSA Ahmet Burak Can Hacettepe University abc@hacettepe.edu.tr The Euler Phi Function For a positive integer n, if 0
Cosc 412: Cryptography and complexity Lecture 7 (22/8/2018) Knapsacks and attacks
 1 Cosc 412: Cryptography and complexity Lecture 7 (22/8/2018) Knapsacks and attacks Michael Albert michael.albert@cs.otago.ac.nz 2 This week Arithmetic Knapsack cryptosystems Attacks on knapsacks Some
1 Cosc 412: Cryptography and complexity Lecture 7 (22/8/2018) Knapsacks and attacks Michael Albert michael.albert@cs.otago.ac.nz 2 This week Arithmetic Knapsack cryptosystems Attacks on knapsacks Some
Outline. Computer Science 418. Number of Keys in the Sum. More on Perfect Secrecy, One-Time Pad, Entropy. Mike Jacobson. Week 3
 Outline Computer Science 48 More on Perfect Secrecy, One-Time Pad, Mike Jacobson Department of Computer Science University of Calgary Week 3 2 3 Mike Jacobson (University of Calgary) Computer Science 48
Outline Computer Science 48 More on Perfect Secrecy, One-Time Pad, Mike Jacobson Department of Computer Science University of Calgary Week 3 2 3 Mike Jacobson (University of Calgary) Computer Science 48
Vector Basics, with Exercises
 Math 230 Spring 09 Vector Basics, with Exercises This sheet is designed to follow the GeoGebra Introduction to Vectors. It includes a summary of some of the properties of vectors, as well as homework exercises.
Math 230 Spring 09 Vector Basics, with Exercises This sheet is designed to follow the GeoGebra Introduction to Vectors. It includes a summary of some of the properties of vectors, as well as homework exercises.
Elliptic Curve Cryptography
 Elliptic Curve Cryptography Elliptic Curves An elliptic curve is a cubic equation of the form: y + axy + by = x 3 + cx + dx + e where a, b, c, d and e are real numbers. A special addition operation is
Elliptic Curve Cryptography Elliptic Curves An elliptic curve is a cubic equation of the form: y + axy + by = x 3 + cx + dx + e where a, b, c, d and e are real numbers. A special addition operation is
Notes 10: Public-key cryptography
 MTH6115 Cryptography Notes 10: Public-key cryptography In this section we look at two other schemes that have been proposed for publickey ciphers. The first is interesting because it was the earliest such
MTH6115 Cryptography Notes 10: Public-key cryptography In this section we look at two other schemes that have been proposed for publickey ciphers. The first is interesting because it was the earliest such
MATH 158 FINAL EXAM 20 DECEMBER 2016
 MATH 158 FINAL EXAM 20 DECEMBER 2016 Name : The exam is double-sided. Make sure to read both sides of each page. The time limit is three hours. No calculators are permitted. You are permitted one page
MATH 158 FINAL EXAM 20 DECEMBER 2016 Name : The exam is double-sided. Make sure to read both sides of each page. The time limit is three hours. No calculators are permitted. You are permitted one page
Alternative Approaches: Bounded Storage Model
 Alternative Approaches: Bounded Storage Model A. Würfl 17th April 2005 1 Motivation Description of the Randomized Cipher 2 Motivation Motivation Description of the Randomized Cipher Common practice in
Alternative Approaches: Bounded Storage Model A. Würfl 17th April 2005 1 Motivation Description of the Randomized Cipher 2 Motivation Motivation Description of the Randomized Cipher Common practice in
5-9. Complex Numbers. Key Concept. Square Root of a Negative Real Number. Key Concept. Complex Numbers VOCABULARY TEKS FOCUS ESSENTIAL UNDERSTANDING
 TEKS FOCUS 5-9 Complex Numbers VOCABULARY TEKS (7)(A) Add, subtract, and multiply complex TEKS (1)(F) Analyze mathematical relationships to connect and communicate mathematical ideas. Additional TEKS (1)(D),
TEKS FOCUS 5-9 Complex Numbers VOCABULARY TEKS (7)(A) Add, subtract, and multiply complex TEKS (1)(F) Analyze mathematical relationships to connect and communicate mathematical ideas. Additional TEKS (1)(D),
Chapter 2 : Perfectly-Secret Encryption
 COMP547 Claude Crépeau INTRODUCTION TO MODERN CRYPTOGRAPHY _ Second Edition _ Jonathan Katz Yehuda Lindell Chapter 2 : Perfectly-Secret Encryption 1 2.1 Definitions and Basic Properties We refer to probability
COMP547 Claude Crépeau INTRODUCTION TO MODERN CRYPTOGRAPHY _ Second Edition _ Jonathan Katz Yehuda Lindell Chapter 2 : Perfectly-Secret Encryption 1 2.1 Definitions and Basic Properties We refer to probability
Think about systems of linear equations, their solutions, and how they might be represented with matrices.
 Think About This Situation Unit 4 Lesson 3 Investigation 1 Name: Think about systems of linear equations, their solutions, and how they might be represented with matrices. a Consider a system of two linear
Think About This Situation Unit 4 Lesson 3 Investigation 1 Name: Think about systems of linear equations, their solutions, and how they might be represented with matrices. a Consider a system of two linear
Lecture Notes 15 : Voting, Homomorphic Encryption
 6.857 Computer and Network Security October 29, 2002 Lecture Notes 15 : Voting, Homomorphic Encryption Lecturer: Ron Rivest Scribe: Ledlie/Ortiz/Paskalev/Zhao 1 Introduction The big picture and where we
6.857 Computer and Network Security October 29, 2002 Lecture Notes 15 : Voting, Homomorphic Encryption Lecturer: Ron Rivest Scribe: Ledlie/Ortiz/Paskalev/Zhao 1 Introduction The big picture and where we
3 + 4i 2 + 3i. 3 4i Fig 1b
 The introduction of complex numbers in the 16th century was a natural step in a sequence of extensions of the positive integers, starting with the introduction of negative numbers (to solve equations of
The introduction of complex numbers in the 16th century was a natural step in a sequence of extensions of the positive integers, starting with the introduction of negative numbers (to solve equations of
Notes for Lecture 17
 U.C. Berkeley CS276: Cryptography Handout N17 Luca Trevisan March 17, 2009 Notes for Lecture 17 Scribed by Matt Finifter, posted April 8, 2009 Summary Today we begin to talk about public-key cryptography,
U.C. Berkeley CS276: Cryptography Handout N17 Luca Trevisan March 17, 2009 Notes for Lecture 17 Scribed by Matt Finifter, posted April 8, 2009 Summary Today we begin to talk about public-key cryptography,
Chapter 2 - Vector Algebra
 A spatial vector, or simply vector, is a concept characterized by a magnitude and a direction, and which sums with other vectors according to the Parallelogram Law. A vector can be thought of as an arrow
A spatial vector, or simply vector, is a concept characterized by a magnitude and a direction, and which sums with other vectors according to the Parallelogram Law. A vector can be thought of as an arrow
Cryptography: A Fairy Tale for Mathematicians and Starring Mathematicians!
 Cryptography: A Fairy Tale for Mathematicians and Starring Mathematicians! University of California, Berkeley Mathematics Undergraduate Student Association October 27, 2014 Why Crypto? So why on earth
Cryptography: A Fairy Tale for Mathematicians and Starring Mathematicians! University of California, Berkeley Mathematics Undergraduate Student Association October 27, 2014 Why Crypto? So why on earth
THE UNIVERSITY OF CALGARY FACULTY OF SCIENCE DEPARTMENT OF COMPUTER SCIENCE DEPARTMENT OF MATHEMATICS & STATISTICS MIDTERM EXAMINATION 1 FALL 2018
 THE UNIVERSITY OF CALGARY FACULTY OF SCIENCE DEPARTMENT OF COMPUTER SCIENCE DEPARTMENT OF MATHEMATICS & STATISTICS MIDTERM EXAMINATION 1 FALL 2018 CPSC 418/MATH 318 L01 October 17, 2018 Time: 50 minutes
THE UNIVERSITY OF CALGARY FACULTY OF SCIENCE DEPARTMENT OF COMPUTER SCIENCE DEPARTMENT OF MATHEMATICS & STATISTICS MIDTERM EXAMINATION 1 FALL 2018 CPSC 418/MATH 318 L01 October 17, 2018 Time: 50 minutes
Circuit Complexity. Circuit complexity is based on boolean circuits instead of Turing machines.
 Circuit Complexity Circuit complexity is based on boolean circuits instead of Turing machines. A boolean circuit with n inputs computes a boolean function of n variables. Now, identify true/1 with yes
Circuit Complexity Circuit complexity is based on boolean circuits instead of Turing machines. A boolean circuit with n inputs computes a boolean function of n variables. Now, identify true/1 with yes
MEETING 6 - MODULAR ARITHMETIC AND INTRODUCTORY CRYPTOGRAPHY
 MEETING 6 - MODULAR ARITHMETIC AND INTRODUCTORY CRYPTOGRAPHY In this meeting we go through the foundations of modular arithmetic. Before the meeting it is assumed that you have watched the videos and worked
MEETING 6 - MODULAR ARITHMETIC AND INTRODUCTORY CRYPTOGRAPHY In this meeting we go through the foundations of modular arithmetic. Before the meeting it is assumed that you have watched the videos and worked
CHAPTER 1 REVIEW Section 1 - Algebraic Expressions
 CHAPTER 1 REVIEW Section 1 - Algebraic Expressions A variable is a symbol used to represent one or more numbers. The numbers are called the values of the variable. The terms of an expression are the parts
CHAPTER 1 REVIEW Section 1 - Algebraic Expressions A variable is a symbol used to represent one or more numbers. The numbers are called the values of the variable. The terms of an expression are the parts
Number Theory & Modern Cryptography
 Number Theory & Modern Cryptography Week 12 Stallings: Ch 4, 8, 9, 10 CNT-4403: 2.April.2015 1 Introduction Increasing importance in cryptography Public Key Crypto and Signatures Concern operations on
Number Theory & Modern Cryptography Week 12 Stallings: Ch 4, 8, 9, 10 CNT-4403: 2.April.2015 1 Introduction Increasing importance in cryptography Public Key Crypto and Signatures Concern operations on
Carmen s Core Concepts (Math 135)
 Carmen s Core Concepts (Math 135) Carmen Bruni University of Waterloo Week 8 1 The following are equivalent (TFAE) 2 Inverses 3 More on Multiplicative Inverses 4 Linear Congruence Theorem 2 [LCT2] 5 Fermat
Carmen s Core Concepts (Math 135) Carmen Bruni University of Waterloo Week 8 1 The following are equivalent (TFAE) 2 Inverses 3 More on Multiplicative Inverses 4 Linear Congruence Theorem 2 [LCT2] 5 Fermat
19. Coding for Secrecy
 19. Coding for Secrecy 19.1 Introduction Protecting sensitive information from the prying eyes and ears of others is an important issue today as much as it has been for thousands of years. Government secrets,
19. Coding for Secrecy 19.1 Introduction Protecting sensitive information from the prying eyes and ears of others is an important issue today as much as it has been for thousands of years. Government secrets,
3F1: Signals and Systems INFORMATION THEORY Examples Paper Solutions
 Engineering Tripos Part IIA THIRD YEAR 3F: Signals and Systems INFORMATION THEORY Examples Paper Solutions. Let the joint probability mass function of two binary random variables X and Y be given in the
Engineering Tripos Part IIA THIRD YEAR 3F: Signals and Systems INFORMATION THEORY Examples Paper Solutions. Let the joint probability mass function of two binary random variables X and Y be given in the
The Two Time Pad Encryption System
 Hardware Random Number Generators This document describe the use and function of a one-time-pad style encryption system for field and educational use. You may download sheets free from www.randomserver.dyndns.org/client/random.php
Hardware Random Number Generators This document describe the use and function of a one-time-pad style encryption system for field and educational use. You may download sheets free from www.randomserver.dyndns.org/client/random.php
Latin squares. Clock arithmetic. Modular arithmetic. Binary operations 18/09/2013. Members only an introduction to groups
 Members only an introduction to groups Sue de Pomerai MEI (FMSP Deputy rogramme Leader) 1 2 4 2 4 1 4 1 2 4 1 2 Latin squares A Latin square is an n n table filled with n different symbols in such a way
Members only an introduction to groups Sue de Pomerai MEI (FMSP Deputy rogramme Leader) 1 2 4 2 4 1 4 1 2 4 1 2 Latin squares A Latin square is an n n table filled with n different symbols in such a way
The RSA public encryption scheme: How I learned to stop worrying and love buying stuff online
 The RSA public encryption scheme: How I learned to stop worrying and love buying stuff online Anthony Várilly-Alvarado Rice University Mathematics Leadership Institute, June 2010 Our Goal Today I will
The RSA public encryption scheme: How I learned to stop worrying and love buying stuff online Anthony Várilly-Alvarado Rice University Mathematics Leadership Institute, June 2010 Our Goal Today I will
Announcements Monday, September 25
 Announcements Monday, September 25 The midterm will be returned in recitation on Friday. You can pick it up from me in office hours before then. Keep tabs on your grades on Canvas. WeBWorK 1.7 is due Friday
Announcements Monday, September 25 The midterm will be returned in recitation on Friday. You can pick it up from me in office hours before then. Keep tabs on your grades on Canvas. WeBWorK 1.7 is due Friday
CPSC 467: Cryptography and Computer Security
 CPSC 467: Cryptography and Computer Security Michael J. Fischer 1 Lecture 13 October 16, 2017 (notes revised 10/23/17) 1 Derived from lecture notes by Ewa Syta. CPSC 467, Lecture 13 1/57 Elliptic Curves
CPSC 467: Cryptography and Computer Security Michael J. Fischer 1 Lecture 13 October 16, 2017 (notes revised 10/23/17) 1 Derived from lecture notes by Ewa Syta. CPSC 467, Lecture 13 1/57 Elliptic Curves
Sums of Squares (FNS 195-S) Fall 2014
 Sums of Squares (FNS 195-S) Fall 014 Record of What We Did Drew Armstrong Vectors When we tried to apply Cartesian coordinates in 3 dimensions we ran into some difficulty tryiing to describe lines and
Sums of Squares (FNS 195-S) Fall 014 Record of What We Did Drew Armstrong Vectors When we tried to apply Cartesian coordinates in 3 dimensions we ran into some difficulty tryiing to describe lines and
Notes on Mathematics Groups
 EPGY Singapore Quantum Mechanics: 2007 Notes on Mathematics Groups A group, G, is defined is a set of elements G and a binary operation on G; one of the elements of G has particularly special properties
EPGY Singapore Quantum Mechanics: 2007 Notes on Mathematics Groups A group, G, is defined is a set of elements G and a binary operation on G; one of the elements of G has particularly special properties
Cryptography and Network Security Prof. D. Mukhopadhyay Department of Computer Science and Engineering Indian Institute of Technology, Kharagpur
 Cryptography and Network Security Prof. D. Mukhopadhyay Department of Computer Science and Engineering Indian Institute of Technology, Kharagpur Module No. # 01 Lecture No. # 33 The Diffie-Hellman Problem
Cryptography and Network Security Prof. D. Mukhopadhyay Department of Computer Science and Engineering Indian Institute of Technology, Kharagpur Module No. # 01 Lecture No. # 33 The Diffie-Hellman Problem
Announcements August 31
 Announcements August 31 Homeworks 1.1 and 1.2 are due Friday. The first quiz is on Friday, during recitation. Quizzes mostly test your understanding of the homework. There will generally be a quiz every
Announcements August 31 Homeworks 1.1 and 1.2 are due Friday. The first quiz is on Friday, during recitation. Quizzes mostly test your understanding of the homework. There will generally be a quiz every
Solving Quadratic Equations
 Solving Quadratic Equations MATH 101 College Algebra J. Robert Buchanan Department of Mathematics Summer 2012 Objectives In this lesson we will learn to: solve quadratic equations by factoring, solve quadratic
Solving Quadratic Equations MATH 101 College Algebra J. Robert Buchanan Department of Mathematics Summer 2012 Objectives In this lesson we will learn to: solve quadratic equations by factoring, solve quadratic
What are vectors. Adding Vectors
 Vectors Introduction What are vectors Each vector is defined by two pieces of information: Direction and Magnitude. Often vectors are described by a picture representation or by ordered pairs which describe
Vectors Introduction What are vectors Each vector is defined by two pieces of information: Direction and Magnitude. Often vectors are described by a picture representation or by ordered pairs which describe
CPSC 467b: Cryptography and Computer Security
 CPSC 467b: Cryptography and Computer Security Instructor: Michael Fischer Lecture by Ewa Syta Lecture 13 March 3, 2013 CPSC 467b, Lecture 13 1/52 Elliptic Curves Basics Elliptic Curve Cryptography CPSC
CPSC 467b: Cryptography and Computer Security Instructor: Michael Fischer Lecture by Ewa Syta Lecture 13 March 3, 2013 CPSC 467b, Lecture 13 1/52 Elliptic Curves Basics Elliptic Curve Cryptography CPSC
Commutative Rings and Fields
 Commutative Rings and Fields 1-22-2017 Different algebraic systems are used in linear algebra. The most important are commutative rings with identity and fields. Definition. A ring is a set R with two
Commutative Rings and Fields 1-22-2017 Different algebraic systems are used in linear algebra. The most important are commutative rings with identity and fields. Definition. A ring is a set R with two
and Other Fun Stuff James L. Massey
 Lectures in Cryptology 10-14 October 2005 School of Engineering and Science International University Bremen Lecture 3: Public-Key Cryptography and Other Fun Stuff James L. Massey [Prof.-em. ETH Zürich,
Lectures in Cryptology 10-14 October 2005 School of Engineering and Science International University Bremen Lecture 3: Public-Key Cryptography and Other Fun Stuff James L. Massey [Prof.-em. ETH Zürich,
Great Theoretical Ideas in Computer Science
 15-251 Great Theoretical Ideas in Computer Science Lecture 22: Cryptography November 12th, 2015 What is cryptography about? Adversary Eavesdropper I will cut your throat I will cut your throat What is
15-251 Great Theoretical Ideas in Computer Science Lecture 22: Cryptography November 12th, 2015 What is cryptography about? Adversary Eavesdropper I will cut your throat I will cut your throat What is
Introduction to Group Theory
 Chapter 10 Introduction to Group Theory Since symmetries described by groups play such an important role in modern physics, we will take a little time to introduce the basic structure (as seen by a physicist)
Chapter 10 Introduction to Group Theory Since symmetries described by groups play such an important role in modern physics, we will take a little time to introduce the basic structure (as seen by a physicist)
MATH 135: COMPLEX NUMBERS
 MATH 135: COMPLEX NUMBERS (WINTER, 010) The complex numbers C are important in just about every branch of mathematics. These notes 1 present some basic facts about them. 1. The Complex Plane A complex
MATH 135: COMPLEX NUMBERS (WINTER, 010) The complex numbers C are important in just about every branch of mathematics. These notes 1 present some basic facts about them. 1. The Complex Plane A complex
Discrete Mathematics and Probability Theory Fall 2014 Anant Sahai Note 7
 EECS 70 Discrete Mathematics and Probability Theory Fall 2014 Anant Sahai Note 7 Polynomials Polynomials constitute a rich class of functions which are both easy to describe and widely applicable in topics
EECS 70 Discrete Mathematics and Probability Theory Fall 2014 Anant Sahai Note 7 Polynomials Polynomials constitute a rich class of functions which are both easy to describe and widely applicable in topics
Mathematics of Cryptography
 UNIT - III Mathematics of Cryptography Part III: Primes and Related Congruence Equations 1 Objectives To introduce prime numbers and their applications in cryptography. To discuss some primality test algorithms
UNIT - III Mathematics of Cryptography Part III: Primes and Related Congruence Equations 1 Objectives To introduce prime numbers and their applications in cryptography. To discuss some primality test algorithms
Vectors. Vectors. Vectors. Reminder: Scalars and Vectors. Vector Practice Problems: Odd-numbered problems from
 Vectors Vector Practice Problems: Odd-numbered problems from 3.1-3.21 Reminder: Scalars and Vectors Vector: Scalar: A number (magnitude) with a direction. Just a number. I have continually asked you, which
Vectors Vector Practice Problems: Odd-numbered problems from 3.1-3.21 Reminder: Scalars and Vectors Vector: Scalar: A number (magnitude) with a direction. Just a number. I have continually asked you, which
Math 126: Course Summary
 Math 126: Course Summary Rich Schwartz August 19, 2009 General Information: Math 126 is a course on complex analysis. You might say that complex analysis is the study of what happens when you combine calculus
Math 126: Course Summary Rich Schwartz August 19, 2009 General Information: Math 126 is a course on complex analysis. You might say that complex analysis is the study of what happens when you combine calculus
Chapter 8. Rigid transformations
 Chapter 8. Rigid transformations We are about to start drawing figures in 3D. There are no built-in routines for this purpose in PostScript, and we shall have to start more or less from scratch in extending
Chapter 8. Rigid transformations We are about to start drawing figures in 3D. There are no built-in routines for this purpose in PostScript, and we shall have to start more or less from scratch in extending
I&C 6N. Computational Linear Algebra
 I&C 6N Computational Linear Algebra 1 Lecture 1: Scalars and Vectors What is a scalar? Computer representation of a scalar Scalar Equality Scalar Operations Addition and Multiplication What is a vector?
I&C 6N Computational Linear Algebra 1 Lecture 1: Scalars and Vectors What is a scalar? Computer representation of a scalar Scalar Equality Scalar Operations Addition and Multiplication What is a vector?
Secrecy and the Quantum
 Secrecy and the Quantum Benjamin Schumacher Department of Physics Kenyon College Bright Horizons 35 (July, 2018) Keeping secrets Communication Alice sound waves, photons, electrical signals, paper and
Secrecy and the Quantum Benjamin Schumacher Department of Physics Kenyon College Bright Horizons 35 (July, 2018) Keeping secrets Communication Alice sound waves, photons, electrical signals, paper and
Chapter 2. Matrix Arithmetic. Chapter 2
 Matrix Arithmetic Matrix Addition and Subtraction Addition and subtraction act element-wise on matrices. In order for the addition/subtraction (A B) to be possible, the two matrices A and B must have the
Matrix Arithmetic Matrix Addition and Subtraction Addition and subtraction act element-wise on matrices. In order for the addition/subtraction (A B) to be possible, the two matrices A and B must have the
Computational security & Private key encryption
 Computational security & Private key encryption Emma Arfelt Stud. BSc. Software Development Frederik Madsen Stud. MSc. Software Development March 2017 Recap Perfect Secrecy Perfect indistinguishability
Computational security & Private key encryption Emma Arfelt Stud. BSc. Software Development Frederik Madsen Stud. MSc. Software Development March 2017 Recap Perfect Secrecy Perfect indistinguishability
Relationships Between Quantities
 Algebra 1 Relationships Between Quantities Relationships Between Quantities Everyone loves math until there are letters (known as variables) in problems!! Do students complain about reading when they come
Algebra 1 Relationships Between Quantities Relationships Between Quantities Everyone loves math until there are letters (known as variables) in problems!! Do students complain about reading when they come
Simple Math: Cryptography
 1 Introduction Simple Math: Cryptography This section develops some mathematics before getting to the application. The mathematics that I use involves simple facts from number theory. Number theory is
1 Introduction Simple Math: Cryptography This section develops some mathematics before getting to the application. The mathematics that I use involves simple facts from number theory. Number theory is
Introduction to Cryptology Dr. Sugata Gangopadhyay Department of Computer Science and Engineering Indian Institute of Technology, Roorkee
 Introduction to Cryptology Dr. Sugata Gangopadhyay Department of Computer Science and Engineering Indian Institute of Technology, Roorkee Lecture 05 Problem discussion on Affine cipher and perfect secrecy
Introduction to Cryptology Dr. Sugata Gangopadhyay Department of Computer Science and Engineering Indian Institute of Technology, Roorkee Lecture 05 Problem discussion on Affine cipher and perfect secrecy
Theme : Cryptography. Instructor : Prof. C Pandu Rangan. Speaker : Arun Moorthy CS
 1 C Theme : Cryptography Instructor : Prof. C Pandu Rangan Speaker : Arun Moorthy 93115 CS 2 RSA Cryptosystem Outline of the Talk! Introduction to RSA! Working of the RSA system and associated terminology!
1 C Theme : Cryptography Instructor : Prof. C Pandu Rangan Speaker : Arun Moorthy 93115 CS 2 RSA Cryptosystem Outline of the Talk! Introduction to RSA! Working of the RSA system and associated terminology!
Review of Coordinate Systems
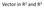 Vector in 2 R and 3 R Review of Coordinate Systems Used to describe the position of a point in space Common coordinate systems are: Cartesian Polar Cartesian Coordinate System Also called rectangular coordinate
Vector in 2 R and 3 R Review of Coordinate Systems Used to describe the position of a point in space Common coordinate systems are: Cartesian Polar Cartesian Coordinate System Also called rectangular coordinate
10.1 Complex Arithmetic Argand Diagrams and the Polar Form The Exponential Form of a Complex Number De Moivre s Theorem 29
 10 Contents Complex Numbers 10.1 Complex Arithmetic 2 10.2 Argand Diagrams and the Polar Form 12 10.3 The Exponential Form of a Complex Number 20 10.4 De Moivre s Theorem 29 Learning outcomes In this Workbook
10 Contents Complex Numbers 10.1 Complex Arithmetic 2 10.2 Argand Diagrams and the Polar Form 12 10.3 The Exponential Form of a Complex Number 20 10.4 De Moivre s Theorem 29 Learning outcomes In this Workbook
9.4 Radical Expressions
 Section 9.4 Radical Expressions 95 9.4 Radical Expressions In the previous two sections, we learned how to multiply and divide square roots. Specifically, we are now armed with the following two properties.
Section 9.4 Radical Expressions 95 9.4 Radical Expressions In the previous two sections, we learned how to multiply and divide square roots. Specifically, we are now armed with the following two properties.
Encryption: The RSA Public Key Cipher
 Encryption: The RSA Public Key Cipher Michael Brockway March 5, 2018 Overview Transport-layer security employs an asymmetric public cryptosystem to allow two parties (usually a client application and a
Encryption: The RSA Public Key Cipher Michael Brockway March 5, 2018 Overview Transport-layer security employs an asymmetric public cryptosystem to allow two parties (usually a client application and a
Vectors a vector is a quantity that has both a magnitude (size) and a direction
 Vectors In physics, a vector is a quantity that has both a magnitude (size) and a direction. Familiar examples of vectors include velocity, force, and electric field. For any applications beyond one dimension,
Vectors In physics, a vector is a quantity that has both a magnitude (size) and a direction. Familiar examples of vectors include velocity, force, and electric field. For any applications beyond one dimension,
10 Public Key Cryptography : RSA
 10 Public Key Cryptography : RSA 10.1 Introduction The idea behind a public-key system is that it might be possible to find a cryptosystem where it is computationally infeasible to determine d K even if
10 Public Key Cryptography : RSA 10.1 Introduction The idea behind a public-key system is that it might be possible to find a cryptosystem where it is computationally infeasible to determine d K even if
Topic 4 Notes Jeremy Orloff
 Topic 4 Notes Jeremy Orloff 4 Complex numbers and exponentials 4.1 Goals 1. Do arithmetic with complex numbers.. Define and compute: magnitude, argument and complex conjugate of a complex number. 3. Euler
Topic 4 Notes Jeremy Orloff 4 Complex numbers and exponentials 4.1 Goals 1. Do arithmetic with complex numbers.. Define and compute: magnitude, argument and complex conjugate of a complex number. 3. Euler
Welcome to IB Math - Standard Level Year 2
 Welcome to IB Math - Standard Level Year 2 Why math? Not So Some things to know: Good HW Good HW Good HW www.aleimath.blogspot.com Example 1. Lots of info at Example Example 2. HW yup. You know you love
Welcome to IB Math - Standard Level Year 2 Why math? Not So Some things to know: Good HW Good HW Good HW www.aleimath.blogspot.com Example 1. Lots of info at Example Example 2. HW yup. You know you love
Canonical Forms Some questions to be explored by high school investigators William J. Martin, WPI
 MME 529 June 2017 Canonical Forms Some questions to be explored by high school investigators William J. Martin, WPI Here are some exercises based on various ideas of canonical form in mathematics. Perhaps
MME 529 June 2017 Canonical Forms Some questions to be explored by high school investigators William J. Martin, WPI Here are some exercises based on various ideas of canonical form in mathematics. Perhaps
