Ph219/CS219 Problem Set 3
|
|
|
- Elaine Emily Anderson
- 5 years ago
- Views:
Transcription
1 Ph19/CS19 Problem Set 3 Solutions by Hui Khoon Ng December 3, 006 (KSV: Kitaev, Shen, Vyalyi, Classical and Quantum Computation) 3.1 The O(...) notation We can do this problem easily just by knowing the following hierarchy: s (log n) p n q r n (S1) for any constants s, p, q, r greater than 1, and the log can be to any base. The sign stands for the O-relation. Let us transform some of the functions in question: n log n = cn ln n (more precisely, n log a n = n ln n ). Using the = sign for the bidirectional ln a O-relation, we may write n log n = n ln n. One must be careful, though see the next item; (log n) n = (1/ ln ) n (ln n) n. Note that 1/ ln > 1, hence (log n) n > (ln n) n in the O-relation sense; (ln n) n = e (ln ln n)n. This function grows faster than a n = e (ln a)n for any constant a. Indeed f(n) O(g(n)) implies that e f(n) O ( e g(n)). Proof: f O(g) f(n) cg(n) e f(n) e c e g(n) e f(n) (constant)e g(n) ; n n 0, some c n ln n = e (ln n). This function grows faster than any constant power of n, yet not as fast as an exponential function. n! πn ( ) n n using Stirling s formula; e ( ) n n = (n)! 4n (n!) πn ; ln(n!) ln π + 1 ln n + n ln n n ln n; 1
2 ln ( ) n n ln π 1 ln n + n ln 4 n ln 4. Putting all these together, the ordering of the functions is ( ) ( ) n n n = ln < n log n = ln(n!) < n ln n < n < < (ln n) n < (log n n n) n < n!. 3. Programming a Turing Machine (a) We are given the n-digit binary number u written backwards on the tape as x 0 x 1 x... x n 1 = n 1 k=0 k x k, x k {0, 1}, and we want to increment it by 1. To do this, we start with the cell on the left end of the tape containing x 0, if it is 1, change it to 0, and move right by one step; if x 1 is 1, change it to 0 and move right by one step; etc. We repeat this until we see the first 0 or a blank symbol (marking the end of the input) on the tape, we change that to 1 and stop. This procedure is implemented by the rules below, with external alphabet given as A = {0, 1}, internal alphabet S = A { }, and Turing machine (TM) states Q = {α, β}, where α is the initial state of the TM and β will be used as the stop state. Recall the notation: (q, s) (q, t, step) means the current TM state is q, the symbol in the current cell (where the head is) is s, and the transition is to a new state q, the head writes symbol t in current cell, and then moves by step. The rules are as follows: (α, 0) (β, 1, 0) (α, 1) (α, 0, +1) (α, ) (β, 1, 0). The TM stops when it goes into the β state. Note that this TM increments the input by 1 even if the input tape is blank (i.e. u is 0-bit number). (b) We want to duplicate the input binary string bit by bit, i.e. we want to convert x 0 x 1... x n 1 into x 0 x 0 x 1 x 1... x n 1 x n 1. One way to do this is to clear the cell immediately to the right of the symbol we want to duplicate by shifting all symbols to the right by one cell. The external alphabet is given as A = {0, 1}, we will use internal alphabet S = A { }, and the state set Q = {α, r 0, r 1, l 0, l 1, w}. The procedure is as follows (s, t {0, 1}): Step 1: Pick up the symbol in the current cell which we want to duplicate, put a blank symbol in its place to mark the position, and move to the right. Swap the symbol we picked before with the one on the tape and move to the right again. Repeat until we see the end of the input. (α, s) (r s,, +1) (r s, t) (r t, s, +1) (r s, ) (l s, s, 1)
3 Step : Move left until we find a blank symbol the mark we left on Step 1. Put a copy of the symbol we saw last and make two step rightwards. Then return to Step 1. (l s, t) (l t, t, 1) (l s, ) (w, s, +1) (w, s) (α, s, +1) Does this TM stop? After it is done duplicating the input, it will be in state α, but its current cell symbol will be, for which there is no rule defined, so machine stops. (c) The idea is to use a fixed length code based on the symbols in A = {0, 1} to represent the internal alphabet S A. Let us try to understand the details of how this works through an example. Suppose we have a TM that uses the internal alphabet S = A {, }. Instead of using the additional symbol, we can have another TM that carries out the same program with the internal alphabet S = A { } by using the following -bit code to represent all symbols of S: 0 00, 1 11, 01, 10. We have chosen not to use the blank symbol in the encoding but rather reserve it for other purposes (see below). When the input tape is given to the TM, with symbols from the external alphabet A = {0, 1}, the TM first does an encoding of the input, i.e., duplicating all input symbols according to the code so that the input x 0 x 1... x n 1 becomes x 0 x 0 x 1 x 1... x n 1 x n 1. Notice that this is exactly part (b) of this problem, the solution of which used only the internal alphabet consisting of 0, 1, and. Once the TM is done encoding the input, it performs the actual computation using the encoded input and the encoded internal symbols,. Note that the fixed length code allows the TM to recognize the correct internal symbol by reading the cells on the tape two at a time (one after another). When it is done, the TM returns to the left end of the tape and decodes the output back into 0 s and 1 s, i.e and (There is a technical problem here: the definition given in class or in KSV does not allow a TM to see the left end of the tape before crashing into it. To cope with this difficulty, we may insert a blank symbol at the left end of the tape as a cushion. Furthermore, we have to avoid using blanks in our computation, which is the reason for the rule 10. If the machine must move beyond the original encoded region, it will recognize a pair of blanks as an encoded blank, replacing it by the suitable combination of 0 s and 1 s. This way, 0 s and 1 s will always occupy a contiguous region, making it easy to locate the cushion symbol.) A similar procedure can be used for a TM with S consisting of a larger set of symbols, just by using a longer code, with 0 represented as , 1 as , and other symbols represented by other codewords of the same length. The encoding phase can be carried out in a similar fashion as above, using only the internal symbols 0,1 and. 3
4 3.3 The Threshold Function (a) There are a few ways of doing this part, one of which is to think of this as sorting the input string of x 1,..., x n into a string with all the 1 s in front of all the 0 s. Another way of doing this is to start with a string of n 0 s, and shift 1 s rightwards when the input is a 1. The circuit that does this is shown in Fig. 1, where q 0 = is a string of n 0 s, and q k = q k,1 q k,... q k,n is the encoding of y k = k j=1 x j as 1 }.{{.. 1} 0 }.{{.. 0}. In particular, q n y k n y k is the string representing n j=1 x j as required. The k-th bit of q n gives the value of the THRESHOLD function. Figure 1: The circuit for Problem 3 (a). q 0 q k 1 : q k 1,1 q k 1, q k 1,3 q k 1,n x 1 q 1 x k x q q n 1 x n q n q k : q k,1 q k, q k,3 q k,n Each box in this circuit is of size O(n) and constant depth, and we have n boxes in sequence. Therefore, the total circuit size is O(n ) and depth O(n). (b) Recall from class that there exists a circuit of size O(m) and depth O(1) that converts the sum of three m-digit numbers into a sum of two numbers, one of which is an m-digit number and the other an (m + 1)-digit number. (If you want the details of the proof, refer to the lemma in the solution of KSV problem.13.) Using this circuit twice, we can convert a sum of four m-digit numbers into a sum of two (m + 1)-digit numbers. We are going to use this in our algorithm described below. Take n = l for some integer l (if this is not true, append the input data with 0 s). Let us construct a tree, with the n bits of input data x 1, x,..., x n as the leaves, and at each node, we add the values of the two input leaves to the node. At the first level, we do nothing, and just write x j +x j+1 at the node with input leaves x j and x j+1. At the second level, at each node, we convert the sum of four numbers (x j + x j 1 ) + (x j + x j+1 ) to a sum of two numbers using the constant depth circuit mentioned above. We end up with a sum of two -bit numbers at each node. Repeat this procedure for every level of the tree, each time converting the sum of four m-digit numbers at each node into a sum of 4
5 two m + 1-digit numbers. We end up with two (log n)-digit numbers at the root of the tree. This tree is shown in Figure. Level 0: Figure : x1 x x 3 x 4 x 5 x 6 x 7 x 8 x n 1 x n Level 1: x 1 + x x + 3 x x x 6 x 7 + x x 8 n 1 + x n Level : (x 1+ x ) +(x 3 + x 4 ) u 1 + u (x 5+ x 6 ) +(x 7 + x 8 ) u 3 + u 4 Level 3: v 1 + v Level (log n): z 1 + z 1 Let us figure out the circuit complexity of this tree. At level 1, we do nothing, so the circuit size and depth are both constant. At level, we have n/ nodes, at each of which, we convert four 1-bit numbers into two -bit numbers, so the size is n/ O(), and depth is constant. At level k, we have n/ k 1 nodes, at each of which, we convert four (k 1)-bit numbers into two k-bit numbers, so the size is n/ k 1 O(k) and depth is still constant. We have log n levels in total, hence, size = log n k=1 ( log n 1 no(k) = O n k 1 k=0 ) ( k O n k k=0 ) k = O(n), k since the series k k=0 converges. The depth is O(log n). k At the root of the tree, we have two (log n)-digit numbers denoted as z 1 and z. We want a binary output at the end of the procedure, so we still have to do the actual binary sum of z 1 and z, which can be done with the parallel addition circuit with depth O(log log n) and size O(log n). Altogether then, the circuit complexity is: size = O(n) + O(log n) = O(n), depth = O(log n) + O(log log n) = O(log n). better than the problem asks for! 5
6 To get the value of the THRESHOLD function, we need to compute the difference n j=1 x j k and compare the result with 0. To do this, we write the difference as n j=1 x j + ( k) and use the complementary code to represent k in binary. (Google two s complement if you are not familiar with this. Briefly, to represent negative numbers for m-digit numbers, we use an (m + 1)-digit binary string, with the first bit being the sign bit, i.e. it is 0 if the number is non-negative, 1 if negative. To read the complementary code when the sign bit is 1, we flip all the bits in the (m + 1)-bit string and add 1. The number represented is then the negative of the resulting string.) Then, do the binary sum of n j=1 x j and k, which we can do with size O(log n) and depth O(log log n) since both are O(log n)-digit numbers, and the value of the THRESHOLD function is the value of the sign bit of the result. 3.4 Measurement Decoding We are given n readings s 0, s 1,..., s n 1 {0, 1,..., 7} from n meters differing in rotation speeds by a factor of, with the s 0 meter being the slowest. We are promised that these ( readings ) are consistent estimates of a number x between 0 and 1 such that j sj 1 x(mod 1), s j+1. Let 8 8 us define β j := s j, then, 8 ( j x β j ) mod 1 1 < for j = 0, 1,..., n 1. 8 The problem is to combine the overlapping information from the n readings to get an estimate y of x such that (x y) mod 1 < (n+). First, a simple fact that we will use: suppose (a.b 1 b b 3...) mod 1 < δ < 1, then exactly one of the following is true: either ( a.0b 1 b... ) < δ/ mod 1 or ( a.1b 1 b... ) mod 1 < δ/. (S) For each j, let us write β j :=.b j1 b j b j3 (note that we only need three digits since β j = integer/8). Given ( j x β j ) mod 1 < 1/8, using (S), we also know that either ( j 1 x.0b j1 b j b j3 ) mod 1 < 1/16 or ( j 1 x.1b j1 b j b j3 ) mod 1 < 1/16. Repeating this procedure, we eventually get j possible regions, each of length (j+), in which x can lie which are consistent with the given value of β j. Since the data are consistent, there will be a finite region contained in the intersection of the sets of regions from the different j values. This region is of length (n+1) and contains x. If we take y as the midpoint of this region, then (x y) mod 1 < (n+). Let us look at a specific example. Consider x = , which we know just to check our results. Take n = 3. Then, we can have the data s 0 = 4, s 1 = 7, s = 7. We can check that this 6
7 Figure 3: s 0 meter, pointer indicates value of x set of data satisfies the required conditions: ( x s ) 0 = = 1 8 mod = 3 64 < 1 8, ( x s ) 1 = = 8 mod 1 64 < 1 8, ( x s ) = = 1 8 mod = 1 16 < 1 8. Using (S) repeatedly, from s, we get four possible regions in which x can lie, each of length 1/16 (see Fig. 3), from s 1, two regions, each of length 1/8, and from s 0, one region of length 1/4. The shaded region (of length 1/16 as constrained by the region coming from s ) corresponds to the overlap between all the different s j values. As can be seen from the diagram, x indeed lies in this region, and we get the desired precision if we take y as the midpoint of the shaded region. (a) How do we get the correct value of y with circuit size O(n)? The problem is, of course, that there are exponentially many regions. Fortunately, we do not need to list all of them. 1 Let 1 A subtle point to note is that there is more than one possible set of values for {s j } that is consistent with a given x. For instance, in the example above, s 0 could have been 3 instead of 4, and we would still get the same shaded region. This causes the following seemingly plausible strategy to fail to give the correct y: write each β j in the binary fraction representation β j =.b j1 b j b j3 and take y =.b 01 b 11 b 1... b n,1 b n 1,1 b n 1, b n 1,3, i.e. start with β n 1 =.b n 1,1 b n 1, b n 1,3, and prepend with the first digit of β n, β n 3,..., β 0. In our example, if the data is given as s 0 = 3, s 1 = 7, s = 7, this strategy gives y = which is within 1/16 of the value of x. However, if the data is given as s 0 = 4, s 1 = 7, s = 7, we get y =.11111, which is not within the desired precision. It is easy to see that this strategy only works if we are given s j values that are the nearest tick marks counterclockwise from the pointer for j x on the respective meters. 7
8 us go back to our original argument. The inequalities ( j 1 x.0b j1 b j b j3 ) mod 1 < 1/16 and ( j 1 x.1b j1 b j b j3 ) mod 1 < 1/16 define two arcs of length 1/8 on opposite sides of the circle. Only one of the arcs can overlap with the region defined by the inequality ( j 1 x β j 1 ) mod 1 < 1/8 because the length of this region (1/4) is smaller than the gaps between the arcs (3/8). Therefore, we can select the right arc before further multiplying the number of choices. This observation suggest the following algorithm, in which we work out the bits of y right to left. Let us start with the binary representation of β n 1 :=.y n y n+1 y n+. Now, sequentially pick y k, k = n 1, n,..., 1 such that { ( ) 0 if.0yk+1 β k 1 y k = 1 if ( ) {, 1, 0, mod } 1,.1y k+1 β k 1 {, 1, 0, } 1 (S3) mod (Note that exactly one of these two conditions holds.) Then, take y =.y 1 y... y n y n+1 y n+. We need to check that y found this way gives the required precision for x, i.e., (x y) mod 1 < (n+). We prove this using induction on the statement: (.y k y k+1... y n+ k 1 x ) mod 1 < δ k, where δ k = (n+3 k). (S4) Base case. If k = n then (.y n y n+1 y n+ n 1 x ) mod 1 = (βn 1 n 1 x) mod 1 < 3 = δ n. Induction step. Assume that equation (S4) is true for some k; we need to prove it for k = k 1. The inductive assumption implies that (.uy k y k+1... y n+ k x ) δ k mod 1 < = δ k 1 (S5) for u = 0 or u = 1. We just need to check that (S3) gives the correct value for y k 1, i.e., y k 1 = u. To see this, notice that 0.uy k y k+1... y n+.uy k n+4 k j=3 j = 1/4 δ k 1. (S6) Using (S5) and (S6) together with the data consistency condition, ( k x β k ) mod 1 1/8, we get: δ k 1 (1/4 δ k 1 ) 1/8 < (.uy k β k ) mod 1 < δ k /8. Hence as required. (.uy k β k ) mod 1 { /8, 1/8, 0, 1/8} (S7) 8
9 Figure 4: O(n) circuit as a finite-state automaton. β 0 β n 3 β n F (y, y 3 ) (y n 1, y n) (y n, y n+1 )... F F y 1 y n y n 1 In this algorithm, y k depends only on β k and y k+1. Proving the correctness by induction is somewhat tricky, though. The proof may be easier to carry out if we replace condition (S3) by, say, this inequality: ( ).y k y k+1 y k+ 1 β k 1 < 1/4. (S8) mod 1 In this case, y k depends on β k, y k+1, and y k+. However, the overall structure of the algorithm remains the same. It can be viewed as a finite-state automaton F : (β, q) (y, q) (where β {0, 1}, y {0, 1}, and q = (y, y ) {0, 1} denotes the state of the automaton) defined as: F (β k 1, (y k+1, y k+ )) = (y k, (y k, y k+1 )) with y k given by (S8). This is represented schematically in Fig. 4. The initial state of the automaton is computed from β n 1 (which can be done with a constant size circuit). Notice that F is computable by a fixed size circuit, but we need to repeat it n times in sequence, so the circuit complexity is given by size = O(n) depth = O(n). (b) From part (a), we know that our algorithm can be viewed as a finite-state automaton operating n times in sequence. This point of view makes it very easy to see how to parallelize the circuit, just by analogy with the parallelization of addition discussed in class. Recall that in parallelizing addition, we compute all the carry-bits with depth O(log n) by first computing the composition of functions given the input in the form of a tree of depth O(log n). Here, the automaton state q k := (y k+1, y k+ ) plays the role of the carry bit, which we need to compute the next value of y k. We carry out the exact same procedure as in the case of parallelizing addition. We first compute all compositions of the functions F βk : Q Q in the form of a tree. This tree is of depth O(log n), with O(n) nodes, each node corresponding to a composition of two fixed size functions (and hence computable by a circuit with constant size and depth). Hence this composition process has circuit size O(n) and depth O(log n). Having gotten all these composition functions, we need to compute q k k. This can be done in O(log n) steps, just like in the 9
10 Figure 5: Computing q values for n=8. q 7 q 3 q 1 q 0 q q 4 q 5 q 6 q q q q q q q q case of computing the carry bits in the parallel addition algorithm (see Figure 5 for an example for n = 8). Finally, we compute in parallel, all the y k values given the q k values. Altogether then, the circuit complexity is: size = O(n), depth = O(log n). Note that all finite-state automaton algorithms of the above form can be parallelized in the same way to reduce the depth from O(n) to O(log n). For further reference, see the solution to KSV problem.11 (for simplicity, you can take the parameter k in that problem to be a constant). 10
Theory of Computation
 Theory of Computation Dr. Sarmad Abbasi Dr. Sarmad Abbasi () Theory of Computation 1 / 33 Lecture 20: Overview Incompressible strings Minimal Length Descriptions Descriptive Complexity Dr. Sarmad Abbasi
Theory of Computation Dr. Sarmad Abbasi Dr. Sarmad Abbasi () Theory of Computation 1 / 33 Lecture 20: Overview Incompressible strings Minimal Length Descriptions Descriptive Complexity Dr. Sarmad Abbasi
Q = Set of states, IE661: Scheduling Theory (Fall 2003) Primer to Complexity Theory Satyaki Ghosh Dastidar
 IE661: Scheduling Theory (Fall 2003) Primer to Complexity Theory Satyaki Ghosh Dastidar Turing Machine A Turing machine is an abstract representation of a computing device. It consists of a read/write
IE661: Scheduling Theory (Fall 2003) Primer to Complexity Theory Satyaki Ghosh Dastidar Turing Machine A Turing machine is an abstract representation of a computing device. It consists of a read/write
COMPUTATIONAL COMPLEXITY
 ATHEATICS: CONCEPTS, AND FOUNDATIONS Vol. III - Computational Complexity - Osamu Watanabe COPUTATIONAL COPLEXITY Osamu Watanabe Tokyo Institute of Technology, Tokyo, Japan Keywords: {deterministic, randomized,
ATHEATICS: CONCEPTS, AND FOUNDATIONS Vol. III - Computational Complexity - Osamu Watanabe COPUTATIONAL COPLEXITY Osamu Watanabe Tokyo Institute of Technology, Tokyo, Japan Keywords: {deterministic, randomized,
Theory of Computation
 Theory of Computation Dr. Sarmad Abbasi Dr. Sarmad Abbasi () Theory of Computation 1 / 38 Lecture 21: Overview Big-Oh notation. Little-o notation. Time Complexity Classes Non-deterministic TMs The Class
Theory of Computation Dr. Sarmad Abbasi Dr. Sarmad Abbasi () Theory of Computation 1 / 38 Lecture 21: Overview Big-Oh notation. Little-o notation. Time Complexity Classes Non-deterministic TMs The Class
CMPT 710/407 - Complexity Theory Lecture 4: Complexity Classes, Completeness, Linear Speedup, and Hierarchy Theorems
 CMPT 710/407 - Complexity Theory Lecture 4: Complexity Classes, Completeness, Linear Speedup, and Hierarchy Theorems Valentine Kabanets September 13, 2007 1 Complexity Classes Unless explicitly stated,
CMPT 710/407 - Complexity Theory Lecture 4: Complexity Classes, Completeness, Linear Speedup, and Hierarchy Theorems Valentine Kabanets September 13, 2007 1 Complexity Classes Unless explicitly stated,
Quantum Computing Lecture 8. Quantum Automata and Complexity
 Quantum Computing Lecture 8 Quantum Automata and Complexity Maris Ozols Computational models and complexity Shor s algorithm solves, in polynomial time, a problem for which no classical polynomial time
Quantum Computing Lecture 8 Quantum Automata and Complexity Maris Ozols Computational models and complexity Shor s algorithm solves, in polynomial time, a problem for which no classical polynomial time
Homework Assignment 6 Answers
 Homework Assignment 6 Answers CSCI 2670 Introduction to Theory of Computing, Fall 2016 December 2, 2016 This homework assignment is about Turing machines, decidable languages, Turing recognizable languages,
Homework Assignment 6 Answers CSCI 2670 Introduction to Theory of Computing, Fall 2016 December 2, 2016 This homework assignment is about Turing machines, decidable languages, Turing recognizable languages,
Turing Machine Variants. Sipser pages
 Turing Machine Variants Sipser pages 148-154 Marking symbols It is often convenient to have the Turing machine leave a symbol on the tape but to mark it in some way 1 1 0 2 B B B B B B B State = 1 1 1
Turing Machine Variants Sipser pages 148-154 Marking symbols It is often convenient to have the Turing machine leave a symbol on the tape but to mark it in some way 1 1 0 2 B B B B B B B State = 1 1 1
Sample Project: Simulation of Turing Machines by Machines with only Two Tape Symbols
 Sample Project: Simulation of Turing Machines by Machines with only Two Tape Symbols The purpose of this document is to illustrate what a completed project should look like. I have chosen a problem that
Sample Project: Simulation of Turing Machines by Machines with only Two Tape Symbols The purpose of this document is to illustrate what a completed project should look like. I have chosen a problem that
CSCI3390-Assignment 2 Solutions
 CSCI3390-Assignment 2 Solutions due February 3, 2016 1 TMs for Deciding Languages Write the specification of a Turing machine recognizing one of the following three languages. Do one of these problems.
CSCI3390-Assignment 2 Solutions due February 3, 2016 1 TMs for Deciding Languages Write the specification of a Turing machine recognizing one of the following three languages. Do one of these problems.
Further discussion of Turing machines
 Further discussion of Turing machines In this lecture we will discuss various aspects of decidable and Turing-recognizable languages that were not mentioned in previous lectures. In particular, we will
Further discussion of Turing machines In this lecture we will discuss various aspects of decidable and Turing-recognizable languages that were not mentioned in previous lectures. In particular, we will
Time Complexity (1) CSCI Spring Original Slides were written by Dr. Frederick W Maier. CSCI 2670 Time Complexity (1)
 Time Complexity (1) CSCI 2670 Original Slides were written by Dr. Frederick W Maier Spring 2014 Time Complexity So far we ve dealt with determining whether or not a problem is decidable. But even if it
Time Complexity (1) CSCI 2670 Original Slides were written by Dr. Frederick W Maier Spring 2014 Time Complexity So far we ve dealt with determining whether or not a problem is decidable. But even if it
Lecture 1 : Data Compression and Entropy
 CPS290: Algorithmic Foundations of Data Science January 8, 207 Lecture : Data Compression and Entropy Lecturer: Kamesh Munagala Scribe: Kamesh Munagala In this lecture, we will study a simple model for
CPS290: Algorithmic Foundations of Data Science January 8, 207 Lecture : Data Compression and Entropy Lecturer: Kamesh Munagala Scribe: Kamesh Munagala In this lecture, we will study a simple model for
CHAPTER 5. Interactive Turing Machines
 CHAPTER 5 Interactive Turing Machines The interactive Turing machine, which was introduced by Van Leeuwen and Wiedermann[28, 30], is an extension of the classical Turing machine model. It attempts to model
CHAPTER 5 Interactive Turing Machines The interactive Turing machine, which was introduced by Van Leeuwen and Wiedermann[28, 30], is an extension of the classical Turing machine model. It attempts to model
Universal Turing Machine. Lecture 20
 Universal Turing Machine Lecture 20 1 Turing Machine move the head left or right by one cell read write sequentially accessed infinite memory finite memory (state) next-action look-up table Variants don
Universal Turing Machine Lecture 20 1 Turing Machine move the head left or right by one cell read write sequentially accessed infinite memory finite memory (state) next-action look-up table Variants don
Complexity Theory Part I
 Complexity Theory Part I Problem Problem Set Set 77 due due right right now now using using a late late period period The Limits of Computability EQ TM EQ TM co-re R RE L D ADD L D HALT A TM HALT A TM
Complexity Theory Part I Problem Problem Set Set 77 due due right right now now using using a late late period period The Limits of Computability EQ TM EQ TM co-re R RE L D ADD L D HALT A TM HALT A TM
Great Theoretical Ideas in Computer Science. Lecture 7: Introduction to Computational Complexity
 15-251 Great Theoretical Ideas in Computer Science Lecture 7: Introduction to Computational Complexity September 20th, 2016 What have we done so far? What will we do next? What have we done so far? > Introduction
15-251 Great Theoretical Ideas in Computer Science Lecture 7: Introduction to Computational Complexity September 20th, 2016 What have we done so far? What will we do next? What have we done so far? > Introduction
Compute the Fourier transform on the first register to get x {0,1} n x 0.
 CS 94 Recursive Fourier Sampling, Simon s Algorithm /5/009 Spring 009 Lecture 3 1 Review Recall that we can write any classical circuit x f(x) as a reversible circuit R f. We can view R f as a unitary
CS 94 Recursive Fourier Sampling, Simon s Algorithm /5/009 Spring 009 Lecture 3 1 Review Recall that we can write any classical circuit x f(x) as a reversible circuit R f. We can view R f as a unitary
Week 2: Defining Computation
 Computational Complexity Theory Summer HSSP 2018 Week 2: Defining Computation Dylan Hendrickson MIT Educational Studies Program 2.1 Turing Machines Turing machines provide a simple, clearly defined way
Computational Complexity Theory Summer HSSP 2018 Week 2: Defining Computation Dylan Hendrickson MIT Educational Studies Program 2.1 Turing Machines Turing machines provide a simple, clearly defined way
5 + 9(10) + 3(100) + 0(1000) + 2(10000) =
 Chapter 5 Analyzing Algorithms So far we have been proving statements about databases, mathematics and arithmetic, or sequences of numbers. Though these types of statements are common in computer science,
Chapter 5 Analyzing Algorithms So far we have been proving statements about databases, mathematics and arithmetic, or sequences of numbers. Though these types of statements are common in computer science,
UCSD CSE 21, Spring 2014 [Section B00] Mathematics for Algorithm and System Analysis
![UCSD CSE 21, Spring 2014 [Section B00] Mathematics for Algorithm and System Analysis UCSD CSE 21, Spring 2014 [Section B00] Mathematics for Algorithm and System Analysis](/thumbs/89/98802725.jpg) UCSD CSE 21, Spring 2014 [Section B00] Mathematics for Algorithm and System Analysis Lecture 14 Class URL: http://vlsicad.ucsd.edu/courses/cse21-s14/ Lecture 14 Notes Goals for this week Big-O complexity
UCSD CSE 21, Spring 2014 [Section B00] Mathematics for Algorithm and System Analysis Lecture 14 Class URL: http://vlsicad.ucsd.edu/courses/cse21-s14/ Lecture 14 Notes Goals for this week Big-O complexity
ECE 695 Numerical Simulations Lecture 2: Computability and NPhardness. Prof. Peter Bermel January 11, 2017
 ECE 695 Numerical Simulations Lecture 2: Computability and NPhardness Prof. Peter Bermel January 11, 2017 Outline Overview Definitions Computing Machines Church-Turing Thesis Polynomial Time (Class P)
ECE 695 Numerical Simulations Lecture 2: Computability and NPhardness Prof. Peter Bermel January 11, 2017 Outline Overview Definitions Computing Machines Church-Turing Thesis Polynomial Time (Class P)
CP405 Theory of Computation
 CP405 Theory of Computation BB(3) q 0 q 1 q 2 0 q 1 1R q 2 0R q 2 1L 1 H1R q 1 1R q 0 1L Growing Fast BB(3) = 6 BB(4) = 13 BB(5) = 4098 BB(6) = 3.515 x 10 18267 (known) (known) (possible) (possible) Language:
CP405 Theory of Computation BB(3) q 0 q 1 q 2 0 q 1 1R q 2 0R q 2 1L 1 H1R q 1 1R q 0 1L Growing Fast BB(3) = 6 BB(4) = 13 BB(5) = 4098 BB(6) = 3.515 x 10 18267 (known) (known) (possible) (possible) Language:
Module 1: Analyzing the Efficiency of Algorithms
 Module 1: Analyzing the Efficiency of Algorithms Dr. Natarajan Meghanathan Professor of Computer Science Jackson State University Jackson, MS 39217 E-mail: natarajan.meghanathan@jsums.edu What is an Algorithm?
Module 1: Analyzing the Efficiency of Algorithms Dr. Natarajan Meghanathan Professor of Computer Science Jackson State University Jackson, MS 39217 E-mail: natarajan.meghanathan@jsums.edu What is an Algorithm?
CS 361 Meeting 26 11/10/17
 CS 361 Meeting 26 11/10/17 1. Homework 8 due Announcements A Recognizable, but Undecidable Language 1. Last class, I presented a brief, somewhat inscrutable proof that the language A BT M = { M w M is
CS 361 Meeting 26 11/10/17 1. Homework 8 due Announcements A Recognizable, but Undecidable Language 1. Last class, I presented a brief, somewhat inscrutable proof that the language A BT M = { M w M is
P, NP, NP-Complete, and NPhard
 P, NP, NP-Complete, and NPhard Problems Zhenjiang Li 21/09/2011 Outline Algorithm time complicity P and NP problems NP-Complete and NP-Hard problems Algorithm time complicity Outline What is this course
P, NP, NP-Complete, and NPhard Problems Zhenjiang Li 21/09/2011 Outline Algorithm time complicity P and NP problems NP-Complete and NP-Hard problems Algorithm time complicity Outline What is this course
Theory of Computation Time Complexity
 Theory of Computation Time Complexity Bow-Yaw Wang Academia Sinica Spring 2012 Bow-Yaw Wang (Academia Sinica) Time Complexity Spring 2012 1 / 59 Time for Deciding a Language Let us consider A = {0 n 1
Theory of Computation Time Complexity Bow-Yaw Wang Academia Sinica Spring 2012 Bow-Yaw Wang (Academia Sinica) Time Complexity Spring 2012 1 / 59 Time for Deciding a Language Let us consider A = {0 n 1
CSC173 Workshop: 13 Sept. Notes
 CSC173 Workshop: 13 Sept. Notes Frank Ferraro Department of Computer Science University of Rochester September 14, 2010 1 Regular Languages and Equivalent Forms A language can be thought of a set L of
CSC173 Workshop: 13 Sept. Notes Frank Ferraro Department of Computer Science University of Rochester September 14, 2010 1 Regular Languages and Equivalent Forms A language can be thought of a set L of
MA008/MIIZ01 Design and Analysis of Algorithms Lecture Notes 3
 MA008 p.1/37 MA008/MIIZ01 Design and Analysis of Algorithms Lecture Notes 3 Dr. Markus Hagenbuchner markus@uow.edu.au. MA008 p.2/37 Exercise 1 (from LN 2) Asymptotic Notation When constants appear in exponents
MA008 p.1/37 MA008/MIIZ01 Design and Analysis of Algorithms Lecture Notes 3 Dr. Markus Hagenbuchner markus@uow.edu.au. MA008 p.2/37 Exercise 1 (from LN 2) Asymptotic Notation When constants appear in exponents
A non-turing-recognizable language
 CS 360: Introduction to the Theory of Computing John Watrous, University of Waterloo A non-turing-recognizable language 1 OVERVIEW Thus far in the course we have seen many examples of decidable languages
CS 360: Introduction to the Theory of Computing John Watrous, University of Waterloo A non-turing-recognizable language 1 OVERVIEW Thus far in the course we have seen many examples of decidable languages
Lecture 1: September 25, A quick reminder about random variables and convexity
 Information and Coding Theory Autumn 207 Lecturer: Madhur Tulsiani Lecture : September 25, 207 Administrivia This course will cover some basic concepts in information and coding theory, and their applications
Information and Coding Theory Autumn 207 Lecturer: Madhur Tulsiani Lecture : September 25, 207 Administrivia This course will cover some basic concepts in information and coding theory, and their applications
SE 3310b Theoretical Foundations of Software Engineering. Turing Machines. Aleksander Essex
 SE 3310b Theoretical Foundations of Software Engineering Turing Machines Aleksander Essex 1 / 1 Turing Machines 2 / 1 Introduction We ve finally arrived at a complete model of computation: Turing machines.
SE 3310b Theoretical Foundations of Software Engineering Turing Machines Aleksander Essex 1 / 1 Turing Machines 2 / 1 Introduction We ve finally arrived at a complete model of computation: Turing machines.
Harvard CS 121 and CSCI E-121 Lecture 20: Polynomial Time
 Harvard CS 121 and CSCI E-121 Lecture 20: Polynomial Time Harry Lewis November 12, 20123 Review of Asymptotic Notation For f, g : N R + f = O(g): c > 0 s.t. f(n) c g(n) for all sufficiently large n. f
Harvard CS 121 and CSCI E-121 Lecture 20: Polynomial Time Harry Lewis November 12, 20123 Review of Asymptotic Notation For f, g : N R + f = O(g): c > 0 s.t. f(n) c g(n) for all sufficiently large n. f
Computational Models Lecture 11, Spring 2009
 Slides modified by Benny Chor, based on original slides by Maurice Herlihy, Brown University. p. 1 Computational Models Lecture 11, Spring 2009 Deterministic Time Classes NonDeterministic Time Classes
Slides modified by Benny Chor, based on original slides by Maurice Herlihy, Brown University. p. 1 Computational Models Lecture 11, Spring 2009 Deterministic Time Classes NonDeterministic Time Classes
Announcements. Problem Set 6 due next Monday, February 25, at 12:50PM. Midterm graded, will be returned at end of lecture.
 Turing Machines Hello Hello Condensed Slide Slide Readers! Readers! This This lecture lecture is is almost almost entirely entirely animations that that show show how how each each Turing Turing machine
Turing Machines Hello Hello Condensed Slide Slide Readers! Readers! This This lecture lecture is is almost almost entirely entirely animations that that show show how how each each Turing Turing machine
Theory of computation: initial remarks (Chapter 11)
 Theory of computation: initial remarks (Chapter 11) For many purposes, computation is elegantly modeled with simple mathematical objects: Turing machines, finite automata, pushdown automata, and such.
Theory of computation: initial remarks (Chapter 11) For many purposes, computation is elegantly modeled with simple mathematical objects: Turing machines, finite automata, pushdown automata, and such.
TURING MAHINES
 15-453 TURING MAHINES TURING MACHINE FINITE STATE q 10 CONTROL AI N P U T INFINITE TAPE read write move 0 0, R, R q accept, R q reject 0 0, R 0 0, R, L read write move 0 0, R, R q accept, R 0 0, R 0 0,
15-453 TURING MAHINES TURING MACHINE FINITE STATE q 10 CONTROL AI N P U T INFINITE TAPE read write move 0 0, R, R q accept, R q reject 0 0, R 0 0, R, L read write move 0 0, R, R q accept, R 0 0, R 0 0,
Lecture 17: Trees and Merge Sort 10:00 AM, Oct 15, 2018
 CS17 Integrated Introduction to Computer Science Klein Contents Lecture 17: Trees and Merge Sort 10:00 AM, Oct 15, 2018 1 Tree definitions 1 2 Analysis of mergesort using a binary tree 1 3 Analysis of
CS17 Integrated Introduction to Computer Science Klein Contents Lecture 17: Trees and Merge Sort 10:00 AM, Oct 15, 2018 1 Tree definitions 1 2 Analysis of mergesort using a binary tree 1 3 Analysis of
On the Space Complexity of Parameterized Problems
 On the Space Complexity of Parameterized Problems Michael Elberfeld Christoph Stockhusen Till Tantau Institute for Theoretical Computer Science Universität zu Lübeck D-23538 Lübeck, Germany {elberfeld,stockhus,tantau}@tcs.uni-luebeck.de
On the Space Complexity of Parameterized Problems Michael Elberfeld Christoph Stockhusen Till Tantau Institute for Theoretical Computer Science Universität zu Lübeck D-23538 Lübeck, Germany {elberfeld,stockhus,tantau}@tcs.uni-luebeck.de
Part I: Definitions and Properties
 Turing Machines Part I: Definitions and Properties Finite State Automata Deterministic Automata (DFSA) M = {Q, Σ, δ, q 0, F} -- Σ = Symbols -- Q = States -- q 0 = Initial State -- F = Accepting States
Turing Machines Part I: Definitions and Properties Finite State Automata Deterministic Automata (DFSA) M = {Q, Σ, δ, q 0, F} -- Σ = Symbols -- Q = States -- q 0 = Initial State -- F = Accepting States
Lecture 16: Time Complexity and P vs NP
 6.045 Lecture 16: Time Complexity and P vs NP 1 Time-Bounded Complexity Classes Definition: TIME(t(n)) = { L there is a Turing machine M with time complexity O(t(n)) so that L = L(M) } = { L L is a language
6.045 Lecture 16: Time Complexity and P vs NP 1 Time-Bounded Complexity Classes Definition: TIME(t(n)) = { L there is a Turing machine M with time complexity O(t(n)) so that L = L(M) } = { L L is a language
MTAT Complexity Theory October 13th-14th, Lecture 6
 MTAT.07.004 Complexity Theory October 13th-14th, 2011 Lecturer: Peeter Laud Lecture 6 Scribe(s): Riivo Talviste 1 Logarithmic memory Turing machines working in logarithmic space become interesting when
MTAT.07.004 Complexity Theory October 13th-14th, 2011 Lecturer: Peeter Laud Lecture 6 Scribe(s): Riivo Talviste 1 Logarithmic memory Turing machines working in logarithmic space become interesting when
Deterministic Finite Automata (DFAs)
 Algorithms & Models of Computation CS/ECE 374, Fall 27 Deterministic Finite Automata (DFAs) Lecture 3 Tuesday, September 5, 27 Sariel Har-Peled (UIUC) CS374 Fall 27 / 36 Part I DFA Introduction Sariel
Algorithms & Models of Computation CS/ECE 374, Fall 27 Deterministic Finite Automata (DFAs) Lecture 3 Tuesday, September 5, 27 Sariel Har-Peled (UIUC) CS374 Fall 27 / 36 Part I DFA Introduction Sariel
Deterministic Finite Automata (DFAs)
 Algorithms & Models of Computation CS/ECE 374, Spring 29 Deterministic Finite Automata (DFAs) Lecture 3 Tuesday, January 22, 29 L A TEXed: December 27, 28 8:25 Chan, Har-Peled, Hassanieh (UIUC) CS374 Spring
Algorithms & Models of Computation CS/ECE 374, Spring 29 Deterministic Finite Automata (DFAs) Lecture 3 Tuesday, January 22, 29 L A TEXed: December 27, 28 8:25 Chan, Har-Peled, Hassanieh (UIUC) CS374 Spring
Computational complexity
 COMS11700 Computational complexity Department of Computer Science, University of Bristol Bristol, UK 2 May 2014 COMS11700: Computational complexity Slide 1/23 Introduction If we can prove that a language
COMS11700 Computational complexity Department of Computer Science, University of Bristol Bristol, UK 2 May 2014 COMS11700: Computational complexity Slide 1/23 Introduction If we can prove that a language
Intro to Theory of Computation
 Intro to Theory of Computation LECTURE 22 Last time Review Today: Finish recursion theorem Complexity theory Exam 2 solutions out Homework 9 out Sofya Raskhodnikova L22.1 I-clicker question (frequency:
Intro to Theory of Computation LECTURE 22 Last time Review Today: Finish recursion theorem Complexity theory Exam 2 solutions out Homework 9 out Sofya Raskhodnikova L22.1 I-clicker question (frequency:
IV. Turing Machine. Yuxi Fu. BASICS, Shanghai Jiao Tong University
 IV. Turing Machine Yuxi Fu BASICS, Shanghai Jiao Tong University Alan Turing Alan Turing (23Jun.1912-7Jun.1954), an English student of Church, introduced a machine model for effective calculation in On
IV. Turing Machine Yuxi Fu BASICS, Shanghai Jiao Tong University Alan Turing Alan Turing (23Jun.1912-7Jun.1954), an English student of Church, introduced a machine model for effective calculation in On
M. Smith. 6 September 2016 / GSAC
 , Complexity, and Department of Mathematics University of Utah 6 September 2016 / GSAC Outline 1 2 3 4 Outline 1 2 3 4 Motivation The clock puzzle is an infamous part of the video game XIII-2 (2011). Most
, Complexity, and Department of Mathematics University of Utah 6 September 2016 / GSAC Outline 1 2 3 4 Outline 1 2 3 4 Motivation The clock puzzle is an infamous part of the video game XIII-2 (2011). Most
Lecture notes on Turing machines
 Lecture notes on Turing machines Ivano Ciardelli 1 Introduction Turing machines, introduced by Alan Turing in 1936, are one of the earliest and perhaps the best known model of computation. The importance
Lecture notes on Turing machines Ivano Ciardelli 1 Introduction Turing machines, introduced by Alan Turing in 1936, are one of the earliest and perhaps the best known model of computation. The importance
Proving languages to be nonregular
 Proving languages to be nonregular We already know that there exist languages A Σ that are nonregular, for any choice of an alphabet Σ. This is because there are uncountably many languages in total and
Proving languages to be nonregular We already know that there exist languages A Σ that are nonregular, for any choice of an alphabet Σ. This is because there are uncountably many languages in total and
CS 310 Advanced Data Structures and Algorithms
 CS 310 Advanced Data Structures and Algorithms Runtime Analysis May 31, 2017 Tong Wang UMass Boston CS 310 May 31, 2017 1 / 37 Topics Weiss chapter 5 What is algorithm analysis Big O, big, big notations
CS 310 Advanced Data Structures and Algorithms Runtime Analysis May 31, 2017 Tong Wang UMass Boston CS 310 May 31, 2017 1 / 37 Topics Weiss chapter 5 What is algorithm analysis Big O, big, big notations
Turing machines and linear bounded automata
 and linear bounded automata Informatics 2A: Lecture 29 John Longley School of Informatics University of Edinburgh jrl@inf.ed.ac.uk 25 November, 2011 1 / 13 1 The Chomsky hierarchy: summary 2 3 4 2 / 13
and linear bounded automata Informatics 2A: Lecture 29 John Longley School of Informatics University of Edinburgh jrl@inf.ed.ac.uk 25 November, 2011 1 / 13 1 The Chomsky hierarchy: summary 2 3 4 2 / 13
Exercise Sheet #1 Solutions, Computer Science, A M. Hallett, K. Smith a k n b k = n b + k. a k n b k c 1 n b k. a k n b.
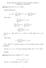 Exercise Sheet #1 Solutions, Computer Science, 308-251A M. Hallett, K. Smith 2002 Question 1.1: Prove (n + a) b = Θ(n b ). Binomial Expansion: Show O(n b ): (n + a) b = For any c 1 > b = O(n b ). Show
Exercise Sheet #1 Solutions, Computer Science, 308-251A M. Hallett, K. Smith 2002 Question 1.1: Prove (n + a) b = Θ(n b ). Binomial Expansion: Show O(n b ): (n + a) b = For any c 1 > b = O(n b ). Show
Theory of Computation Lecture Notes. Problems and Algorithms. Class Information
 Theory of Computation Lecture Notes Prof. Yuh-Dauh Lyuu Dept. Computer Science & Information Engineering and Department of Finance National Taiwan University Problems and Algorithms c 2004 Prof. Yuh-Dauh
Theory of Computation Lecture Notes Prof. Yuh-Dauh Lyuu Dept. Computer Science & Information Engineering and Department of Finance National Taiwan University Problems and Algorithms c 2004 Prof. Yuh-Dauh
Chapter 3 Source Coding. 3.1 An Introduction to Source Coding 3.2 Optimal Source Codes 3.3 Shannon-Fano Code 3.4 Huffman Code
 Chapter 3 Source Coding 3. An Introduction to Source Coding 3.2 Optimal Source Codes 3.3 Shannon-Fano Code 3.4 Huffman Code 3. An Introduction to Source Coding Entropy (in bits per symbol) implies in average
Chapter 3 Source Coding 3. An Introduction to Source Coding 3.2 Optimal Source Codes 3.3 Shannon-Fano Code 3.4 Huffman Code 3. An Introduction to Source Coding Entropy (in bits per symbol) implies in average
CS 4104 Data and Algorithm Analysis. Recurrence Relations. Modeling Recursive Function Cost. Solving Recurrences. Clifford A. Shaffer.
 Department of Computer Science Virginia Tech Blacksburg, Virginia Copyright c 2010,2017 by Clifford A. Shaffer Data and Algorithm Analysis Title page Data and Algorithm Analysis Clifford A. Shaffer Spring
Department of Computer Science Virginia Tech Blacksburg, Virginia Copyright c 2010,2017 by Clifford A. Shaffer Data and Algorithm Analysis Title page Data and Algorithm Analysis Clifford A. Shaffer Spring
Asymptotic Analysis. Slides by Carl Kingsford. Jan. 27, AD Chapter 2
 Asymptotic Analysis Slides by Carl Kingsford Jan. 27, 2014 AD Chapter 2 Independent Set Definition (Independent Set). Given a graph G = (V, E) an independent set is a set S V if no two nodes in S are joined
Asymptotic Analysis Slides by Carl Kingsford Jan. 27, 2014 AD Chapter 2 Independent Set Definition (Independent Set). Given a graph G = (V, E) an independent set is a set S V if no two nodes in S are joined
Please give details of your answer. A direct answer without explanation is not counted.
 Please give details of your answer. A direct answer without explanation is not counted. Your answers must be in English. Please carefully read problem statements. During the exam you are not allowed to
Please give details of your answer. A direct answer without explanation is not counted. Your answers must be in English. Please carefully read problem statements. During the exam you are not allowed to
Complexity (Pre Lecture)
 Complexity (Pre Lecture) Dr. Neil T. Dantam CSCI-561, Colorado School of Mines Fall 2018 Dantam (Mines CSCI-561) Complexity (Pre Lecture) Fall 2018 1 / 70 Why? What can we always compute efficiently? What
Complexity (Pre Lecture) Dr. Neil T. Dantam CSCI-561, Colorado School of Mines Fall 2018 Dantam (Mines CSCI-561) Complexity (Pre Lecture) Fall 2018 1 / 70 Why? What can we always compute efficiently? What
Finish K-Complexity, Start Time Complexity
 6.045 Finish K-Complexity, Start Time Complexity 1 Kolmogorov Complexity Definition: The shortest description of x, denoted as d(x), is the lexicographically shortest string such that M(w) halts
6.045 Finish K-Complexity, Start Time Complexity 1 Kolmogorov Complexity Definition: The shortest description of x, denoted as d(x), is the lexicographically shortest string such that M(w) halts
1 Circuit Complexity. CS 6743 Lecture 15 1 Fall Definitions
 CS 6743 Lecture 15 1 Fall 2007 1 Circuit Complexity 1.1 Definitions A Boolean circuit C on n inputs x 1,..., x n is a directed acyclic graph (DAG) with n nodes of in-degree 0 (the inputs x 1,..., x n ),
CS 6743 Lecture 15 1 Fall 2007 1 Circuit Complexity 1.1 Definitions A Boolean circuit C on n inputs x 1,..., x n is a directed acyclic graph (DAG) with n nodes of in-degree 0 (the inputs x 1,..., x n ),
An analogy from Calculus: limits
 COMP 250 Fall 2018 35 - big O Nov. 30, 2018 We have seen several algorithms in the course, and we have loosely characterized their runtimes in terms of the size n of the input. We say that the algorithm
COMP 250 Fall 2018 35 - big O Nov. 30, 2018 We have seen several algorithms in the course, and we have loosely characterized their runtimes in terms of the size n of the input. We say that the algorithm
Lecture Notes on Inductive Definitions
 Lecture Notes on Inductive Definitions 15-312: Foundations of Programming Languages Frank Pfenning Lecture 2 September 2, 2004 These supplementary notes review the notion of an inductive definition and
Lecture Notes on Inductive Definitions 15-312: Foundations of Programming Languages Frank Pfenning Lecture 2 September 2, 2004 These supplementary notes review the notion of an inductive definition and
Lecture 16. Error-free variable length schemes (contd.): Shannon-Fano-Elias code, Huffman code
 Lecture 16 Agenda for the lecture Error-free variable length schemes (contd.): Shannon-Fano-Elias code, Huffman code Variable-length source codes with error 16.1 Error-free coding schemes 16.1.1 The Shannon-Fano-Elias
Lecture 16 Agenda for the lecture Error-free variable length schemes (contd.): Shannon-Fano-Elias code, Huffman code Variable-length source codes with error 16.1 Error-free coding schemes 16.1.1 The Shannon-Fano-Elias
Lecture 10: Synchronous Sequential Circuits Design
 Lecture 0: Synchronous Sequential Circuits Design. General Form Input Combinational Flip-flops Combinational Output Circuit Circuit Clock.. Moore type has outputs dependent only on the state, e.g. ripple
Lecture 0: Synchronous Sequential Circuits Design. General Form Input Combinational Flip-flops Combinational Output Circuit Circuit Clock.. Moore type has outputs dependent only on the state, e.g. ripple
T (s, xa) = T (T (s, x), a). The language recognized by M, denoted L(M), is the set of strings accepted by M. That is,
 Recall A deterministic finite automaton is a five-tuple where S is a finite set of states, M = (S, Σ, T, s 0, F ) Σ is an alphabet the input alphabet, T : S Σ S is the transition function, s 0 S is the
Recall A deterministic finite automaton is a five-tuple where S is a finite set of states, M = (S, Σ, T, s 0, F ) Σ is an alphabet the input alphabet, T : S Σ S is the transition function, s 0 S is the
Automata Theory CS S-12 Turing Machine Modifications
 Automata Theory CS411-2015S-12 Turing Machine Modifications David Galles Department of Computer Science University of San Francisco 12-0: Extending Turing Machines When we added a stack to NFA to get a
Automata Theory CS411-2015S-12 Turing Machine Modifications David Galles Department of Computer Science University of San Francisco 12-0: Extending Turing Machines When we added a stack to NFA to get a
Lecture 4. 1 Circuit Complexity. Notes on Complexity Theory: Fall 2005 Last updated: September, Jonathan Katz
 Notes on Complexity Theory: Fall 2005 Last updated: September, 2005 Jonathan Katz Lecture 4 1 Circuit Complexity Circuits are directed, acyclic graphs where nodes are called gates and edges are called
Notes on Complexity Theory: Fall 2005 Last updated: September, 2005 Jonathan Katz Lecture 4 1 Circuit Complexity Circuits are directed, acyclic graphs where nodes are called gates and edges are called
CS 125 Section #10 (Un)decidability and Probability November 1, 2016
 CS 125 Section #10 (Un)decidability and Probability November 1, 2016 1 Countability Recall that a set S is countable (either finite or countably infinite) if and only if there exists a surjective mapping
CS 125 Section #10 (Un)decidability and Probability November 1, 2016 1 Countability Recall that a set S is countable (either finite or countably infinite) if and only if there exists a surjective mapping
MATH 521, WEEK 2: Rational and Real Numbers, Ordered Sets, Countable Sets
 MATH 521, WEEK 2: Rational and Real Numbers, Ordered Sets, Countable Sets 1 Rational and Real Numbers Recall that a number is rational if it can be written in the form a/b where a, b Z and b 0, and a number
MATH 521, WEEK 2: Rational and Real Numbers, Ordered Sets, Countable Sets 1 Rational and Real Numbers Recall that a number is rational if it can be written in the form a/b where a, b Z and b 0, and a number
Theory of Computation Prof. Kamala Krithivasan Department of Computer Science and Engineering Indian Institute Of Technology, Madras
 Theory of Computation Prof. Kamala Krithivasan Department of Computer Science and Engineering Indian Institute Of Technology, Madras Lecture No. # 25 Problems and Solutions (Refer Slide Time: 00:16) Today,
Theory of Computation Prof. Kamala Krithivasan Department of Computer Science and Engineering Indian Institute Of Technology, Madras Lecture No. # 25 Problems and Solutions (Refer Slide Time: 00:16) Today,
Turing Machines, diagonalization, the halting problem, reducibility
 Notes on Computer Theory Last updated: September, 015 Turing Machines, diagonalization, the halting problem, reducibility 1 Turing Machines A Turing machine is a state machine, similar to the ones we have
Notes on Computer Theory Last updated: September, 015 Turing Machines, diagonalization, the halting problem, reducibility 1 Turing Machines A Turing machine is a state machine, similar to the ones we have
Deterministic Finite Automata (DFAs)
 CS/ECE 374: Algorithms & Models of Computation, Fall 28 Deterministic Finite Automata (DFAs) Lecture 3 September 4, 28 Chandra Chekuri (UIUC) CS/ECE 374 Fall 28 / 33 Part I DFA Introduction Chandra Chekuri
CS/ECE 374: Algorithms & Models of Computation, Fall 28 Deterministic Finite Automata (DFAs) Lecture 3 September 4, 28 Chandra Chekuri (UIUC) CS/ECE 374 Fall 28 / 33 Part I DFA Introduction Chandra Chekuri
Theory of Computing Tamás Herendi
 Theory of Computing Tamás Herendi Theory of Computing Tamás Herendi Publication date 2014 Table of Contents 1 Preface 1 2 Formal languages 2 3 Order of growth rate 9 4 Turing machines 16 1 The definition
Theory of Computing Tamás Herendi Theory of Computing Tamás Herendi Publication date 2014 Table of Contents 1 Preface 1 2 Formal languages 2 3 Order of growth rate 9 4 Turing machines 16 1 The definition
Turing Machine Variants
 CS311 Computational Structures Turing Machine Variants Lecture 12 Andrew Black Andrew Tolmach 1 The Church-Turing Thesis The problems that can be decided by an algorithm are exactly those that can be decided
CS311 Computational Structures Turing Machine Variants Lecture 12 Andrew Black Andrew Tolmach 1 The Church-Turing Thesis The problems that can be decided by an algorithm are exactly those that can be decided
Theory of Computation
 Theory of Computation Unit 4-6: Turing Machines and Computability Decidability and Encoding Turing Machines Complexity and NP Completeness Syedur Rahman syedurrahman@gmail.com Turing Machines Q The set
Theory of Computation Unit 4-6: Turing Machines and Computability Decidability and Encoding Turing Machines Complexity and NP Completeness Syedur Rahman syedurrahman@gmail.com Turing Machines Q The set
CPSC 421: Tutorial #1
 CPSC 421: Tutorial #1 October 14, 2016 Set Theory. 1. Let A be an arbitrary set, and let B = {x A : x / x}. That is, B contains all sets in A that do not contain themselves: For all y, ( ) y B if and only
CPSC 421: Tutorial #1 October 14, 2016 Set Theory. 1. Let A be an arbitrary set, and let B = {x A : x / x}. That is, B contains all sets in A that do not contain themselves: For all y, ( ) y B if and only
CpSc 421 Final Exam December 15, 2006
 CpSc 421 Final Exam December 15, 2006 Do problem zero and six of problems 1 through 9. If you write down solutions for more that six problems, clearly indicate those that you want graded. Note that problems
CpSc 421 Final Exam December 15, 2006 Do problem zero and six of problems 1 through 9. If you write down solutions for more that six problems, clearly indicate those that you want graded. Note that problems
ACS2: Decidability Decidability
 Decidability Bernhard Nebel and Christian Becker-Asano 1 Overview An investigation into the solvable/decidable Decidable languages The halting problem (undecidable) 2 Decidable problems? Acceptance problem
Decidability Bernhard Nebel and Christian Becker-Asano 1 Overview An investigation into the solvable/decidable Decidable languages The halting problem (undecidable) 2 Decidable problems? Acceptance problem
CS151 Complexity Theory. Lecture 1 April 3, 2017
 CS151 Complexity Theory Lecture 1 April 3, 2017 Complexity Theory Classify problems according to the computational resources required running time storage space parallelism randomness rounds of interaction,
CS151 Complexity Theory Lecture 1 April 3, 2017 Complexity Theory Classify problems according to the computational resources required running time storage space parallelism randomness rounds of interaction,
Advanced topic: Space complexity
 Advanced topic: Space complexity CSCI 3130 Formal Languages and Automata Theory Siu On CHAN Chinese University of Hong Kong Fall 2016 1/28 Review: time complexity We have looked at how long it takes to
Advanced topic: Space complexity CSCI 3130 Formal Languages and Automata Theory Siu On CHAN Chinese University of Hong Kong Fall 2016 1/28 Review: time complexity We have looked at how long it takes to
Theory of Computation
 Theory of Computation Lecture #6 Sarmad Abbasi Virtual University Sarmad Abbasi (Virtual University) Theory of Computation 1 / 39 Lecture 6: Overview Prove the equivalence of enumerators and TMs. Dovetailing
Theory of Computation Lecture #6 Sarmad Abbasi Virtual University Sarmad Abbasi (Virtual University) Theory of Computation 1 / 39 Lecture 6: Overview Prove the equivalence of enumerators and TMs. Dovetailing
6.045: Automata, Computability, and Complexity Or, Great Ideas in Theoretical Computer Science Spring, Class 8 Nancy Lynch
 6.045: Automata, Computability, and Complexity Or, Great Ideas in Theoretical Computer Science Spring, 2010 Class 8 Nancy Lynch Today More undecidable problems: About Turing machines: Emptiness, etc. About
6.045: Automata, Computability, and Complexity Or, Great Ideas in Theoretical Computer Science Spring, 2010 Class 8 Nancy Lynch Today More undecidable problems: About Turing machines: Emptiness, etc. About
UNIT-VIII COMPUTABILITY THEORY
 CONTEXT SENSITIVE LANGUAGE UNIT-VIII COMPUTABILITY THEORY A Context Sensitive Grammar is a 4-tuple, G = (N, Σ P, S) where: N Set of non terminal symbols Σ Set of terminal symbols S Start symbol of the
CONTEXT SENSITIVE LANGUAGE UNIT-VIII COMPUTABILITY THEORY A Context Sensitive Grammar is a 4-tuple, G = (N, Σ P, S) where: N Set of non terminal symbols Σ Set of terminal symbols S Start symbol of the
Algorithms, Design and Analysis. Order of growth. Table 2.1. Big-oh. Asymptotic growth rate. Types of formulas for basic operation count
 Types of formulas for basic operation count Exact formula e.g., C(n) = n(n-1)/2 Algorithms, Design and Analysis Big-Oh analysis, Brute Force, Divide and conquer intro Formula indicating order of growth
Types of formulas for basic operation count Exact formula e.g., C(n) = n(n-1)/2 Algorithms, Design and Analysis Big-Oh analysis, Brute Force, Divide and conquer intro Formula indicating order of growth
Emphasize physical realizability.
 Emphasize physical realizability. The conventional approach is to measure complexity via SPACE & TIME, which are inherently unbounded by their nature. An alternative approach is to count the MATTER & ENERGY
Emphasize physical realizability. The conventional approach is to measure complexity via SPACE & TIME, which are inherently unbounded by their nature. An alternative approach is to count the MATTER & ENERGY
Algorithms (II) Yu Yu. Shanghai Jiaotong University
 Algorithms (II) Yu Yu Shanghai Jiaotong University Chapter 1. Algorithms with Numbers Two seemingly similar problems Factoring: Given a number N, express it as a product of its prime factors. Primality:
Algorithms (II) Yu Yu Shanghai Jiaotong University Chapter 1. Algorithms with Numbers Two seemingly similar problems Factoring: Given a number N, express it as a product of its prime factors. Primality:
2.2 Asymptotic Order of Growth. definitions and notation (2.2) examples (2.4) properties (2.2)
 2.2 Asymptotic Order of Growth definitions and notation (2.2) examples (2.4) properties (2.2) Asymptotic Order of Growth Upper bounds. T(n) is O(f(n)) if there exist constants c > 0 and n 0 0 such that
2.2 Asymptotic Order of Growth definitions and notation (2.2) examples (2.4) properties (2.2) Asymptotic Order of Growth Upper bounds. T(n) is O(f(n)) if there exist constants c > 0 and n 0 0 such that
Data Structures and Algorithms Running time and growth functions January 18, 2018
 Data Structures and Algorithms Running time and growth functions January 18, 2018 Measuring Running Time of Algorithms One way to measure the running time of an algorithm is to implement it and then study
Data Structures and Algorithms Running time and growth functions January 18, 2018 Measuring Running Time of Algorithms One way to measure the running time of an algorithm is to implement it and then study
This chapter covers asymptotic analysis of function growth and big-o notation.
 Chapter 14 Big-O This chapter covers asymptotic analysis of function growth and big-o notation. 14.1 Running times of programs An important aspect of designing a computer programs is figuring out how well
Chapter 14 Big-O This chapter covers asymptotic analysis of function growth and big-o notation. 14.1 Running times of programs An important aspect of designing a computer programs is figuring out how well
5 3 Watson-Crick Automata with Several Runs
 5 3 Watson-Crick Automata with Several Runs Peter Leupold Department of Mathematics, Faculty of Science Kyoto Sangyo University, Japan Joint work with Benedek Nagy (Debrecen) Presentation at NCMA 2009
5 3 Watson-Crick Automata with Several Runs Peter Leupold Department of Mathematics, Faculty of Science Kyoto Sangyo University, Japan Joint work with Benedek Nagy (Debrecen) Presentation at NCMA 2009
Asymptotic Analysis. Thomas A. Anastasio. January 7, 2004
 Asymptotic Analysis Thomas A. Anastasio January 7, 004 1 Introduction As a programmer, you often have a choice of data structures and algorithms. Choosing the best one for a particular job involves, among
Asymptotic Analysis Thomas A. Anastasio January 7, 004 1 Introduction As a programmer, you often have a choice of data structures and algorithms. Choosing the best one for a particular job involves, among
CISC 4090 Theory of Computation
 CISC 4090 Theory of Computation Complexity Professor Daniel Leeds dleeds@fordham.edu JMH 332 Computability Are we guaranteed to get an answer? Complexity How long do we have to wait for an answer? (Ch7)
CISC 4090 Theory of Computation Complexity Professor Daniel Leeds dleeds@fordham.edu JMH 332 Computability Are we guaranteed to get an answer? Complexity How long do we have to wait for an answer? (Ch7)
1 Introduction to information theory
 1 Introduction to information theory 1.1 Introduction In this chapter we present some of the basic concepts of information theory. The situations we have in mind involve the exchange of information through
1 Introduction to information theory 1.1 Introduction In this chapter we present some of the basic concepts of information theory. The situations we have in mind involve the exchange of information through
Error Detection and Correction: Hamming Code; Reed-Muller Code
 Error Detection and Correction: Hamming Code; Reed-Muller Code Greg Plaxton Theory in Programming Practice, Spring 2005 Department of Computer Science University of Texas at Austin Hamming Code: Motivation
Error Detection and Correction: Hamming Code; Reed-Muller Code Greg Plaxton Theory in Programming Practice, Spring 2005 Department of Computer Science University of Texas at Austin Hamming Code: Motivation
CS6901: review of Theory of Computation and Algorithms
 CS6901: review of Theory of Computation and Algorithms Any mechanically (automatically) discretely computation of problem solving contains at least three components: - problem description - computational
CS6901: review of Theory of Computation and Algorithms Any mechanically (automatically) discretely computation of problem solving contains at least three components: - problem description - computational
Design at the Register Transfer Level
 Week-7 Design at the Register Transfer Level Algorithmic State Machines Algorithmic State Machine (ASM) q Our design methodologies do not scale well to real-world problems. q 232 - Logic Design / Algorithmic
Week-7 Design at the Register Transfer Level Algorithmic State Machines Algorithmic State Machine (ASM) q Our design methodologies do not scale well to real-world problems. q 232 - Logic Design / Algorithmic
Lecture 23 : Nondeterministic Finite Automata DRAFT Connection between Regular Expressions and Finite Automata
 CS/Math 24: Introduction to Discrete Mathematics 4/2/2 Lecture 23 : Nondeterministic Finite Automata Instructor: Dieter van Melkebeek Scribe: Dalibor Zelený DRAFT Last time we designed finite state automata
CS/Math 24: Introduction to Discrete Mathematics 4/2/2 Lecture 23 : Nondeterministic Finite Automata Instructor: Dieter van Melkebeek Scribe: Dalibor Zelený DRAFT Last time we designed finite state automata
CS 525 Proof of Theorems 3.13 and 3.15
 Eric Rock CS 525 (Winter 2015) Presentation 1 (Week 4) Equivalence of Single-Tape and Multi-Tape Turing Machines 1/30/2015 1 Turing Machine (Definition 3.3) Formal Definition: (Q, Σ, Γ, δ, q 0, q accept,
Eric Rock CS 525 (Winter 2015) Presentation 1 (Week 4) Equivalence of Single-Tape and Multi-Tape Turing Machines 1/30/2015 1 Turing Machine (Definition 3.3) Formal Definition: (Q, Σ, Γ, δ, q 0, q accept,
Confusion of Memory. Lawrence S. Moss. Department of Mathematics Indiana University Bloomington, IN USA February 14, 2008
 Confusion of Memory Lawrence S. Moss Department of Mathematics Indiana University Bloomington, IN 47405 USA February 14, 2008 Abstract It is a truism that for a machine to have a useful access to memory
Confusion of Memory Lawrence S. Moss Department of Mathematics Indiana University Bloomington, IN 47405 USA February 14, 2008 Abstract It is a truism that for a machine to have a useful access to memory
