Intersecting curves (variation on an observation of Maxim Kontsevich) by Étienne GHYS
|
|
|
- Reynard O’Brien’
- 5 years ago
- Views:
Transcription
1 Intersecting curves (variation on an observation of Maxim Kontsevich) by Étienne GHYS Abstract Consider the graphs of n distinct polynomials of a real variable intersecting at some point. In the neighborhood of this point, the qualitative picture is described by some permutation of {1,..., n}. We describe the permutations that occur in such a situation. In this note, we shall examine the relative positions of the graphs of several functions in the neighborhood of a point where they intersect. In order to keep the discussion as elementary as possible, we shall restrict ourselves to polynomials in the real variable x f(x) = a 0 + a 1 x a d x d, where the coefficients a i are real numbers. As usual, one says that the valuation of f at 0 is the integer k d such that a 0 = a 1 =... = a k 1 = 0 and a k 0 (and if f = 0). It is well known that the function f changes sign in the neighborhood of the origin if and only if its valuation is odd. Two curves Assume now that the graphs of two distinct polynomials f 1, f 2 intersect in some point, say the origin (0, 0). Then the relative position of the graphs of f 1 and f 2 in the neighborhood of this point is easy to describe. If the valuation of f 1 f 2 is odd, these graphs cross each other. Otherwise they touch without crossing. Figure 1: Two intersecting curves 1
2 Three curves Let us now look at the graphs of three distinct polynomials f 1, f 2, f 3 vanishing at the origin. The relative positions of these graphs are determined by the valuations of the differences f i f j. Looking at small negative values of x, we can rename the polynomials in such a way that f 1 (x) > f 2 (x) > f 3 (x). For small positive numbers x, the ordering of the f i (x) may be different so that the crossing of the three graphs can be described by one of the six permutations of {1, 2, 3}. It is not difficult to show, by way of examples, that all six permutations occur. Here are six examples: (f 1 (x) = x 2 ; f 2 (x) = 0 ; f 3 (x) = x 2 ) (f 1 (x) = x 2 ; f 2 (x) = x 3 ; f 3 (x) = 0) (f 1 (x) = 0 ; f 2 (x) = x 3 ; f 3 (x) = x 2 ) (f 1 (x) = x ; f 2 (x) = x 2 ; f 3 (x) = x 2 ) (f 1 (x) = x ; f 2 (x) = 0 ; f 3 (x) = x) (f 1 (x) = x 2 ; f 2 (x) = x 2 ; f 3 (x) = x) leading to the six permutations as illustrated in Figure 2. Figure 2: Three intersecting curves Four curves Maxim Kontsevich observed that the situation is different when four graphs intersect 1. Not all permutations of {1, 2, 3, 4} occur. The following figure 3 shows four piecewise linear functions which intersect in a way which is not possible for polynomials. Theorem 1. There do not exist four polynomials f 1, f 2, f 3, f 4 such that: 1. they all vanish at the origin, 1 Personal communication (2009). 2
3 Figure 3: An impossible situation for polynomials 2. f 1 (x) > f 2 (x) > f 3 (x) > f 4 (x) for small negative x, 3. f 2 (x) > f 4 (x) > f 1 (x) > f 3 (x) for small positive x. Proof. The proof is by contradiction. Replacing the f i by f i f 4, we can assume that f 4 = 0. Since f 1 and f 3 change sign at the origin, their valuations val(f 1 ), val(f 3 ) are odd. Since f 2 does not change sign, its valuation val(f 2 ) is even. From f 1 (x) > f 2 (x) > f 3 (x) > 0 for small negative x, we deduce that val(f 3 ) val(f 2 ) val(f 1 ). Similarly, from 0 > f 1 (x) > f 3 (x) for small positive x, we deduce val(f 1 ) val(f 3 ). That would force the three valuations to be equal, but two of them are odd and the third is even! This yields a contradiction.. Note that the same proof applies to real analytic functions but does not apply to smooth functions. Indeed the reader will easily find four C functions f i crossing at the origin according to the forbidden permutation (1, 2, 3, 4) (2, 4, 1, 3). Changing orientations along the x-axis, one can see that the inverse permutation (1, 2, 3, 4) (3, 1, 4, 2) is also forbidden. As an exercise, I recommend showing that the remaining 22 permutations of {1, 2, 3, 4} occur for suitable choices of the f i. Many curves Planting trees Let us now analyze the situation when the graphs of n polynomials intersect at the origin. Let us first coin a name. Definition. Let n 2 be some integer and π : {1, 2,..., n} {1, 2,..., n} some permutation. We say that π is an interchange if there exist n polynomials f 1,..., f n vanishing at 0 and such that: 3
4 1. f 1 (x) > f 2 (x) >... > f n (x) for small negative x, and 2. f π(1) (x) > f π(2) (x) >... > f π(n) (x) for small positive x. Our goal is to give a fairly precise description of interchanges. We start with some estimate of the growth of the number of interchanges. Theorem 2. Let a(n) denote the number of interchanges of {1, 2,..., n}. Then 1 log a(n) n converges to log ( ) when n tends to infinity. Note in particular that a(n) is much smaller than the total number n! of permutations. Here is a concrete way of computing a(n). Theorem 3. The number a(n) of interchanges is twice the number of possible ways of parenthesizing a word of length n in a correct way. More precisely, one requires that each pair of opening-closing parenthesis contains at least two letters and that there is a pair containing the full word. Examples. 1. For n = 3, one can parenthesize abc in three different ways: ((ab)c), (a(bc)), (abc). We do not count useless parenthesis, like double (( )), as in (((ab))c) containing a useless pair around ab. 2. For the 4-letters word abcd, there are 11 ways: (abcd), ((ab)cd), (a(bc)d), ((ab(cd)), ((ab)(cd)), ((abc)cd), (a(bcd)), (((ab)c)d), ((a(bc))d), (a((bc)d)), (a(b(cd))). Twice eleven gives twenty-two and we do recover the twenty-two allowable permutations of four graphs. Theorem 4. One can program a computer to answer the question: Is a given permutation π of {1, 2,..., n} an interchange? in such a way that the computing time is bounded by some polynomial in n. Theorem 5. A permutation π of {1, 2,..., n} is an interchange if and only if there does not exist four integers a, b, c, d which are permuted as in the forbidden permutations, i.e., satisfying n a > b > c > d 1 and π(b) > π(d) > π(a) > π(c) or π(c) > π(a) > π(d) > π(b). Actually, we shall not prove these results since they will appear as obvious consequences of the description of interchanges that follows. 4
5 Some arboriculture Let us consider the following eight polynomials, (almost) chosen at random. f1 (x) = x2 x3 + x5 + x6 + x8, f2 (x) = 2x + 2x2 x3 x4 + x5 + x6, f3 (x) = x + x2 + x3 + x4 x5 + x6 + x7 x8, f4 (x) = 2x + x2 + x4 + 2x5 x6, f5 (x) = x2 x3 + 2x4 + x5, f6 (x) = x2 x3 x4 + 2x5 + x6 x7, f7 (x) = x + x2 + x3 + x4 + x5 x6, and f8 (x) = x + x2 + x3 + x4 + x5 2x6. Figure 4 shows their graphs. Figure 4: Eight graphs We are going to analyze their relative positions for small x, positive or negative. Let us consider first the degree 1 terms. One finds only three possibilities. 2x (for f2 and f4 ), 0 (for f1, f5, f6 ), or x (for f3, f7 and f8 ). This corresponds to the fact that if we zoom on the origin, we essentially only see three graphs. Of course, for x > 0, one has x < 0 < 2x, so that we can say that for small positive x, the graph of f3 for instance is below the graph of f2. However, the degree 1 terms do not contain enough information to distinguish between f1 and f5. We picture the situation in Figure 5. 5
6 Figure 5: Degree one terms Figure 6: Degree two terms Let us now consider the degree 2 terms. We have now four possibilities x + x 2, x 2, 2x + x 2, 2x + 2x 2, pictured in Figure 6. The second degree terms enabled us to distinguish between f 2 and f 4 and it will be therefore useless to continue analyzing these two polynomials to higher degrees. However, f 3, f 7, f 8 an f 1, f 5, f 6 are still equally placed. We have to proceed to a finer analysis. Degree 3 is useless, and does not allow us to distinguish between two previously undistinguishable f i as illustrated in Figure 7. We have to go on. The final result us illustrated in Figure 8: we have to wait until the fifth degree to separate all these polynomials. We can therefore encode the situation by a planar tree: at each level the nodes are ordered from left to right. In this paper, we only deal with planar trees and for simplicity we skip the word planar. Let us check that this tree contains enough information to construct the associated interchange. Indeed, here is the recipe. For small x > 0, it should be obvious to the reader, from the tree, that: f 3 (x) < f 8 (x) < f 7 (x) < f 6 (x) < f 1 (x) < f 5 (x) < f 2 (x) < f 4 (x). How should we order the polynomials for small negative x? We have to evaluate the valuations of the f i f j. One should simply determine at which level the two paths 6
7 Figure 7: Degree three terms Figure 8: Final picture starting from the root of the tree and aiming at i and j bifurcate. If this level is odd, the valuation of f i f j is one more, and is hence even: π(i) and π(j) are in the same order as i and j. If the bifurcation level is even, we obtain the contrary. For instance, on Figure 8, in order to go in the tree from f 3 to f 8, one has to go down until level 3, so that the valuation of f 8 f 3 is 4. Since f 8 (x) f 3 (x) > 0 for small positive x, the same is true for small negative x. In our situation, we find for small negative x that: f 2 (x) < f 4 (x) < f 6 (x) < f 1 (x) < f 5 (x) < f 3 (x) < f 7 (x) < f 8 (x). In order to determine the corresponding interchange, we have to rename the f i in such a way that for small negative x the sequence f i (x) is decreasing and then observe the ordering 7
8 for small positive x. One finds (1, 2, 3, 4, 5, 6, 7, 8) (7, 8, 4, 5, 6, 2, 1, 3). One could also say that the permutation is obtained by twisting the tree over at every even level and watching what happens to the leaves. Of course, the convention that we used, looking first at the positions of the graphs for small negative x and then for small positive x, is only one of the possible conventions. One could change the orientation along either axis, but this would not change the definition of interchange. In summary, given the polynomials, on can construct a tree and, given the tree, we can easily order the polynomials for small values of x and deduce the corresponding interchange. Pruning Our trees contain too much information and we shall prune their branches. Let us introduce some vocabulary. Our trees have three kinds of vertices: one root, some nodes, and several leaves (terminal vertices). An edge connecting two vertices will be called a branch. Each vertex lies at some level which is the number of branches connecting it to the root. The two endpoints of a branch are called child and parent, the parent being at a lower level. Suppose two vertices x, y are connected in the tree by some path consisting of an even number of branches. Suppose moreover that all the intermediate vertices between x and y are non-ramified, i.e., that have only one child. Let us cut all these paths. The tree now consists of several trees, one of which contains the initial root. Let us identify the endpoints x, y on each of these paths. This produces a new tree. Of course, in this process, the levels of some vertices have changed, but only by an even number. Figure 9: Pruning Therefore, if one computes the valuation of f i f j in the new tree, the parity did not change and this parity is the only information that matters in order to construct the interchange. Note that the pruned tree has the property that all its nodes have at least two children. In summary, given n polynomials, one can construct a tree such that: 1. the root can have any number of children, 8
9 2. every node has at least two children, 3. there are exactly n leaves, labeled by the n polynomials. Let us say that a tree is pruned if it satisfies these properties. It should be clear that for any pruned tree, one can find n polynomials such that the associated pruned tree is the given one. In particular, the number of interchanges is less than or equal to the number of pruned trees. We shall now show that these two numbers are actually equal. Two lists of polynomials might theoretically give the same interchange but different pruned trees. The issue is to show that one cannot have two different pruned trees giving the same permutation. In other words, we have to show that the interchange determines uniquely the pruned tree. From an interchange to a tree Let T be a pruned tree with n 2 leaves and let π : {1, 2,..., n} {1, 2,..., n} be the associated interchange. From now on, we always label leaves from 1 to n, from left to right. We want to show that π determines T. On our way, we shall produce an algorithm which determines if a given permutation is associated to some pruned tree, i.e., if it is an interchange. Let us say that a (non-empty) subset of {1, 2,..., n} is an interval if it consists of a certain number of consecutive integers. If a is a node, the set D(a) of leaves which are descendants of a is an interval. One easily checks that the interchange π maps each of these intervals D(a) onto some interval. In combinatorics, such permutations are called separable (see for instance [3, section 2.2.5] for references). The root of a pruned tree with n 2 leaves can have one, or at least two children. In the first case, the unique child of the root has at least two children a 1,..., a m. The corresponding consecutive intervals D(a 1 ),..., D(a m ) are invariant by π. Moreover, this decomposition of {1, 2,..., n} is maximal: none of these intervals D(a i ) can be split into two sub-intervals which are invariant by π. In the second case, the children a 1,..., a m of the root define consecutive intervals D(a 1 ),..., D(a m ) which are now invariant by π where π denotes the permutation π followed by the flip i n + 1 i. We therefore have the following algorithm constructing the tree T from its interchange π. If it is possible to decompose {1,..., n} into at least two intervals which are invariant by π, we are in the first case and we conclude that the root of T has only one child. The children of this unique child are indexed by the unique maximal decomposition of {1,..., n} in consecutive intervals invariant by π. By induction, we continue the description of T by looking at the restrictions of π to these invariant intervals. If it is possible to decompose {1,..., n} into at least two intervals which are invariant by π, we are in the second case and we conclude that the root has at least two children. These children are indexed by the unique maximal decomposition of {1,..., n} in consecutive 9
10 intervals invariant by π. By induction, we continue the description of T by looking at the restrictions of π to these intervals. Note that these two situations cannot occur simultaneously, since π 1 (1) < π 1 (n) in the first case and π 1 (1) > π 1 (n) in the second case. This algorithm can be applied to any permutation, without assuming a priori that it is associated to a pruned tree. If, at some stage of the algorithm, it is not possible to split an interval into sub-intervals which are invariant under the permutation or its composition with the flip, we conclude that the permutation is not an interchange and the algorithm stops. We therefore have reached the conclusion that the number of interchanges is equal to the number of pruned trees. Some exercises Exercise 1: Prove theorem 3. Hint: The root of a pruned tree can have one child or at least two children. If it has only one child, one can delete the root and the resulting tree has a new root having at least two children. Conversely, given a pruned tree such that the root has at least two children, on can add a new root, one level below, which will be the parent of the previous root. Figure 10: Deleting the root Hence, the number of pruned trees is twice the number of pruned trees which are such that the root has at least two children. These trees can be interpreted as ways of placing parenthesis on a word. For instance, Figure 11 corresponds to ((ab)c(d(e(f gh)))). Exercise 2: Prove theorem 5. Hint: It is clear that an interchange cannot contain the forbidden permutations. The main content of the theorem is the sufficient condition: if π does not contain those two permutations, it is possible to construct a pruned tree giving rise to π. The proof is by induction. Starting from some permutation π, one orders first π(1), π(2),..., π(n 1). This produces a permutation of {1, 2,..., n 1}, for which you apply the induction hypothesis. You therefore get a pruned tree with n 1 leaves and you still have to show how to place the last leaf. Exercise 3: Prove theorem 4. Is is possible to find some algorithm in linear time in n? 10
11 Figure 11: Parenthesis Let us count! We are going to count the number a(n) of interchanges. Let b(n) be the number of pruned trees with n leaves which are such that the root does not have a single child (hence has no child, if n = 1, and at least two children if n 2). We know that a(n) = 2b(n) for n 2. The first values of b are: 1. b(1) = 1: a tiny tree whose root is also its unique leaf, 2. b(2) = 1: a tiny tree with two branches and two leaves, 3. b(3) = 3. Figure 12: Small trees It is very tempting to establish an recurrence relation for b(n). To do this, start with a pruned tree with n leaves such that the root has at least two children. If one deletes the root and the adjacent branches, one gets a certain number of trees, having a total of n leaves. Conversely, if one starts with at least two pruned trees having n leaves in total, one can add a new root and connect it to the previous roots, in order to construct a pruned tree with n leaves. Therefore, we have the following relation: b(n) = n k=2 i 1 +i i k =n b(i 1 )b(i 2 ) b(i k ). 11
12 Figure 13: Recurrence We now use the classical method of generating series (see for instance [1]). Define the formal power series H by: Let us square H: H(t) = b(n)t n = t + t 2 + 3t n=1 H(t) 2 = t 2 + 2t 3 + 4t The coefficient of t n in this new series is i 1 +i 2 =n b(i 1 )b(i 2 ), which is equal to the number of pruned trees with n leaves such that the root has exactly two children. Using H(t) 3, we would count the number of trees whose root has three children, etc. The infinite series G(t) = H(t) 2 + H(t) counts therefore all trees, except the only one which has a single leaf. Hence, this infinite sum is H(t) t. We have proved that, Summing the geometric series, we get, or which yields, G(t) = H(t) t = H(t) 2 + H(t) H(t) t = H(t)2 1 H(t) 2H(t) 2 (1 + t)h(t) + t = 0, H(t) = b(n)t n = (1 + t 1 6t + t 2 )/4. n=1 As a function of a complex variable, (1 + t + 1 6t + t 2 )/4 is well defined and holomorphic in the disc of center 0 whose radius is the smallest of the two roots of 1 6t + t 2 = 0, i.e., t = The radius of convergence of H(t) is therefore (3 2 2). In other words lim sup n 1 n log a(n) = log( ). This is theorem 2. Not quite..., but the reader will easily show that the lim sup can be replaced by a lim. 12
13 Visiting Sloane s website The On-Line Encyclopedia of integer sequences [5], is a very powerful tool. In our example, we know that a(1) = 1, a(2) = 2, a(3) = 6, a(4) = 22. Let us type 1, 2, 6, 22 in the main window of this website, and we get immediately a page fully devoted to the Schröder sequence. Indeed the sequence a(n) is not a newcomer in mathematics. It has already appeared in many different contexts, long time ago, and the bibliography on this topic is huge. In Sloane s site, one finds many recurrence relations, many equivalent definitions of a(n), a numerical table of a(n), and much more. For instance, one finds a refined description of the asymptotic growth of a(n): a(n) ( ) n ( n 2πn ( ) ) n +... Or, this recurrence relation, enabling a quick computation: (n + 1)a(n + 1) 3(2n 1)a(n) (n 2)a(n 1) = 0. Prove this relation as an exercise! The trick is to find a second order differential equation satisfied by H(t). From the bibliography in this website, one can easily trace the history of this sequence. According to Plutarch, it seems that Hipparchus, (second century BC), proved that b(10) = What was his motivation? Which method did he use? See [2, 6] for some interesting historical comments. However, Ernst Schröder made the first systematic study of a(n) in 1870 [4]. His motivation was not related to the behavior of intersecting curves. If you like counting trees, you will probably enjoy this paper [7]. A slightly different French version of this note appeared online References [1] Camina, A. & Lewis, B.: An introduction to enumeration. Springer Undergraduate Mathematics Series. Springer-Verlag London, Ltd., London, xii+235 pp. [2] Habsieger, L., Kazarian, M. & Lando, S.: On the second number of Plutarch. Amer. Math. Monthly 105 (1998), 446. [3] Kitaev, S.: Patterns in permutations and words, Springer Verlag (EATCS monographs in Theoretical Computer Science book series)
14 [4] Schröder, E.: Vier combinatorische Probleme. Z. Math. Physik 15, (1870), [5] Sloane, N.: On-Line Encyclopedia of integer sequences, [6] Stanley, R.: Hipparchus, Plutarch, Schröder, and Hough. Amer. Math. Monthly 104 (1997), [7] Stanley, R.: Catalan addendum, math.mit.edu/~rstan/ec/catadd.pdf. Étienne Ghys Unité de Mathématiques Pures et Appliquées de l École normale supérieure de Lyon U.M.R du CNRS 46, Allée d Italie Lyon Cedex 07- France etienne.ghys@ens-lyon.fr October 14,
Modular Periodicity of the Euler Numbers and a Sequence by Arnold
 Arnold Math J. (2018) 3:519 524 https://doi.org/10.1007/s40598-018-0079-0 PROBLEM CONTRIBUTION Modular Periodicity of the Euler Numbers and a Sequence by Arnold Sanjay Ramassamy 1 Received: 19 November
Arnold Math J. (2018) 3:519 524 https://doi.org/10.1007/s40598-018-0079-0 PROBLEM CONTRIBUTION Modular Periodicity of the Euler Numbers and a Sequence by Arnold Sanjay Ramassamy 1 Received: 19 November
Sequences that satisfy a(n a(n)) = 0
 Sequences that satisfy a(n a(n)) = 0 Nate Kube Frank Ruskey October 13, 2005 Abstract We explore the properties of some sequences for which a(n a(n)) = 0. Under the natural restriction that a(n) < n the
Sequences that satisfy a(n a(n)) = 0 Nate Kube Frank Ruskey October 13, 2005 Abstract We explore the properties of some sequences for which a(n a(n)) = 0. Under the natural restriction that a(n) < n the
Generating Permutations and Combinations
 Generating Permutations and Combinations March 0, 005 Generating Permutations We have learned that there are n! permutations of {,,, n} It is important in many instances to generate a list of such permutations
Generating Permutations and Combinations March 0, 005 Generating Permutations We have learned that there are n! permutations of {,,, n} It is important in many instances to generate a list of such permutations
On improving matchings in trees, via bounded-length augmentations 1
 On improving matchings in trees, via bounded-length augmentations 1 Julien Bensmail a, Valentin Garnero a, Nicolas Nisse a a Université Côte d Azur, CNRS, Inria, I3S, France Abstract Due to a classical
On improving matchings in trees, via bounded-length augmentations 1 Julien Bensmail a, Valentin Garnero a, Nicolas Nisse a a Université Côte d Azur, CNRS, Inria, I3S, France Abstract Due to a classical
HW Graph Theory SOLUTIONS (hbovik) - Q
 1, Diestel 3.5: Deduce the k = 2 case of Menger s theorem (3.3.1) from Proposition 3.1.1. Let G be 2-connected, and let A and B be 2-sets. We handle some special cases (thus later in the induction if these
1, Diestel 3.5: Deduce the k = 2 case of Menger s theorem (3.3.1) from Proposition 3.1.1. Let G be 2-connected, and let A and B be 2-sets. We handle some special cases (thus later in the induction if these
k-protected VERTICES IN BINARY SEARCH TREES
 k-protected VERTICES IN BINARY SEARCH TREES MIKLÓS BÓNA Abstract. We show that for every k, the probability that a randomly selected vertex of a random binary search tree on n nodes is at distance k from
k-protected VERTICES IN BINARY SEARCH TREES MIKLÓS BÓNA Abstract. We show that for every k, the probability that a randomly selected vertex of a random binary search tree on n nodes is at distance k from
PRIMES Math Problem Set
 PRIMES Math Problem Set PRIMES 017 Due December 1, 01 Dear PRIMES applicant: This is the PRIMES 017 Math Problem Set. Please send us your solutions as part of your PRIMES application by December 1, 01.
PRIMES Math Problem Set PRIMES 017 Due December 1, 01 Dear PRIMES applicant: This is the PRIMES 017 Math Problem Set. Please send us your solutions as part of your PRIMES application by December 1, 01.
Fibonacci numbers. Chapter The Fibonacci sequence. The Fibonacci numbers F n are defined recursively by
 Chapter Fibonacci numbers The Fibonacci sequence The Fibonacci numbers F n are defined recursively by F n+ = F n + F n, F 0 = 0, F = The first few Fibonacci numbers are n 0 5 6 7 8 9 0 F n 0 5 8 55 89
Chapter Fibonacci numbers The Fibonacci sequence The Fibonacci numbers F n are defined recursively by F n+ = F n + F n, F 0 = 0, F = The first few Fibonacci numbers are n 0 5 6 7 8 9 0 F n 0 5 8 55 89
THE FUNDAMENTAL THEOREM OF ALGEBRA VIA PROPER MAPS
 THE FUNDAMENTAL THEOREM OF ALGEBRA VIA PROPER MAPS KEITH CONRAD 1. Introduction The Fundamental Theorem of Algebra says every nonconstant polynomial with complex coefficients can be factored into linear
THE FUNDAMENTAL THEOREM OF ALGEBRA VIA PROPER MAPS KEITH CONRAD 1. Introduction The Fundamental Theorem of Algebra says every nonconstant polynomial with complex coefficients can be factored into linear
A BIJECTION BETWEEN WELL-LABELLED POSITIVE PATHS AND MATCHINGS
 Séminaire Lotharingien de Combinatoire 63 (0), Article B63e A BJECTON BETWEEN WELL-LABELLED POSTVE PATHS AND MATCHNGS OLVER BERNARD, BERTRAND DUPLANTER, AND PHLPPE NADEAU Abstract. A well-labelled positive
Séminaire Lotharingien de Combinatoire 63 (0), Article B63e A BJECTON BETWEEN WELL-LABELLED POSTVE PATHS AND MATCHNGS OLVER BERNARD, BERTRAND DUPLANTER, AND PHLPPE NADEAU Abstract. A well-labelled positive
1 Sequences and Summation
 1 Sequences and Summation A sequence is a function whose domain is either all the integers between two given integers or all the integers greater than or equal to a given integer. For example, a m, a m+1,...,
1 Sequences and Summation A sequence is a function whose domain is either all the integers between two given integers or all the integers greater than or equal to a given integer. For example, a m, a m+1,...,
On the parity of the Wiener index
 On the parity of the Wiener index Stephan Wagner Department of Mathematical Sciences, Stellenbosch University, Stellenbosch 7602, South Africa Hua Wang Department of Mathematics, University of Florida,
On the parity of the Wiener index Stephan Wagner Department of Mathematical Sciences, Stellenbosch University, Stellenbosch 7602, South Africa Hua Wang Department of Mathematics, University of Florida,
A singular mathematical promenade by Étienne Ghys ENS Éditions, Lyon, 2017 viii+ 302 pp. ISBN: REVIEWED BY SERGEI TABACHNIKOV
 A singular mathematical promenade by Étienne Ghys ENS Éditions, Lyon, 07 viii+ 0 pp. ISBN: 978--84788-99-0 REVIEWED BY SERGEI TABACHNIKOV Consider two graphs of real polynomials that pass through the origin.
A singular mathematical promenade by Étienne Ghys ENS Éditions, Lyon, 07 viii+ 0 pp. ISBN: 978--84788-99-0 REVIEWED BY SERGEI TABACHNIKOV Consider two graphs of real polynomials that pass through the origin.
Alpha-Beta Pruning: Algorithm and Analysis
 Alpha-Beta Pruning: Algorithm and Analysis Tsan-sheng Hsu tshsu@iis.sinica.edu.tw http://www.iis.sinica.edu.tw/~tshsu 1 Introduction Alpha-beta pruning is the standard searching procedure used for solving
Alpha-Beta Pruning: Algorithm and Analysis Tsan-sheng Hsu tshsu@iis.sinica.edu.tw http://www.iis.sinica.edu.tw/~tshsu 1 Introduction Alpha-beta pruning is the standard searching procedure used for solving
Notes by Zvi Rosen. Thanks to Alyssa Palfreyman for supplements.
 Lecture: Hélène Barcelo Analytic Combinatorics ECCO 202, Bogotá Notes by Zvi Rosen. Thanks to Alyssa Palfreyman for supplements.. Tuesday, June 2, 202 Combinatorics is the study of finite structures that
Lecture: Hélène Barcelo Analytic Combinatorics ECCO 202, Bogotá Notes by Zvi Rosen. Thanks to Alyssa Palfreyman for supplements.. Tuesday, June 2, 202 Combinatorics is the study of finite structures that
α-acyclic Joins Jef Wijsen May 4, 2017
 α-acyclic Joins Jef Wijsen May 4, 2017 1 Motivation Joins in a Distributed Environment Assume the following relations. 1 M[NN, Field of Study, Year] stores data about students of UMONS. For example, (19950423158,
α-acyclic Joins Jef Wijsen May 4, 2017 1 Motivation Joins in a Distributed Environment Assume the following relations. 1 M[NN, Field of Study, Year] stores data about students of UMONS. For example, (19950423158,
Notes on Complex Analysis
 Michael Papadimitrakis Notes on Complex Analysis Department of Mathematics University of Crete Contents The complex plane.. The complex plane...................................2 Argument and polar representation.........................
Michael Papadimitrakis Notes on Complex Analysis Department of Mathematics University of Crete Contents The complex plane.. The complex plane...................................2 Argument and polar representation.........................
are the q-versions of n, n! and . The falling factorial is (x) k = x(x 1)(x 2)... (x k + 1).
 Lecture A jacques@ucsd.edu Notation: N, R, Z, F, C naturals, reals, integers, a field, complex numbers. p(n), S n,, b(n), s n, partition numbers, Stirling of the second ind, Bell numbers, Stirling of the
Lecture A jacques@ucsd.edu Notation: N, R, Z, F, C naturals, reals, integers, a field, complex numbers. p(n), S n,, b(n), s n, partition numbers, Stirling of the second ind, Bell numbers, Stirling of the
Week 4-5: Generating Permutations and Combinations
 Week 4-5: Generating Permutations and Combinations February 27, 2017 1 Generating Permutations We have learned that there are n! permutations of {1, 2,...,n}. It is important in many instances to generate
Week 4-5: Generating Permutations and Combinations February 27, 2017 1 Generating Permutations We have learned that there are n! permutations of {1, 2,...,n}. It is important in many instances to generate
Matching Polynomials of Graphs
 Spectral Graph Theory Lecture 25 Matching Polynomials of Graphs Daniel A Spielman December 7, 2015 Disclaimer These notes are not necessarily an accurate representation of what happened in class The notes
Spectral Graph Theory Lecture 25 Matching Polynomials of Graphs Daniel A Spielman December 7, 2015 Disclaimer These notes are not necessarily an accurate representation of what happened in class The notes
Isomorphisms between pattern classes
 Journal of Combinatorics olume 0, Number 0, 1 8, 0000 Isomorphisms between pattern classes M. H. Albert, M. D. Atkinson and Anders Claesson Isomorphisms φ : A B between pattern classes are considered.
Journal of Combinatorics olume 0, Number 0, 1 8, 0000 Isomorphisms between pattern classes M. H. Albert, M. D. Atkinson and Anders Claesson Isomorphisms φ : A B between pattern classes are considered.
Greedy Trees, Caterpillars, and Wiener-Type Graph Invariants
 Georgia Southern University Digital Commons@Georgia Southern Mathematical Sciences Faculty Publications Mathematical Sciences, Department of 2012 Greedy Trees, Caterpillars, and Wiener-Type Graph Invariants
Georgia Southern University Digital Commons@Georgia Southern Mathematical Sciences Faculty Publications Mathematical Sciences, Department of 2012 Greedy Trees, Caterpillars, and Wiener-Type Graph Invariants
Uniform Star-factors of Graphs with Girth Three
 Uniform Star-factors of Graphs with Girth Three Yunjian Wu 1 and Qinglin Yu 1,2 1 Center for Combinatorics, LPMC Nankai University, Tianjin, 300071, China 2 Department of Mathematics and Statistics Thompson
Uniform Star-factors of Graphs with Girth Three Yunjian Wu 1 and Qinglin Yu 1,2 1 Center for Combinatorics, LPMC Nankai University, Tianjin, 300071, China 2 Department of Mathematics and Statistics Thompson
Notes on Paths, Trees and Lagrange Inversion
 Notes on Paths, Trees and Lagrange Inversion Today we are going to start with a problem that may seem somewhat unmotivated, and solve it in two ways. From there, we will proceed to discuss applications
Notes on Paths, Trees and Lagrange Inversion Today we are going to start with a problem that may seem somewhat unmotivated, and solve it in two ways. From there, we will proceed to discuss applications
FRACTIONAL PACKING OF T-JOINS. 1. Introduction
 FRACTIONAL PACKING OF T-JOINS FRANCISCO BARAHONA Abstract Given a graph with nonnegative capacities on its edges, it is well known that the capacity of a minimum T -cut is equal to the value of a maximum
FRACTIONAL PACKING OF T-JOINS FRANCISCO BARAHONA Abstract Given a graph with nonnegative capacities on its edges, it is well known that the capacity of a minimum T -cut is equal to the value of a maximum
ANSWER TO A QUESTION BY BURR AND ERDŐS ON RESTRICTED ADDITION, AND RELATED RESULTS Mathematics Subject Classification: 11B05, 11B13, 11P99
 ANSWER TO A QUESTION BY BURR AND ERDŐS ON RESTRICTED ADDITION, AND RELATED RESULTS N. HEGYVÁRI, F. HENNECART AND A. PLAGNE Abstract. We study the gaps in the sequence of sums of h pairwise distinct elements
ANSWER TO A QUESTION BY BURR AND ERDŐS ON RESTRICTED ADDITION, AND RELATED RESULTS N. HEGYVÁRI, F. HENNECART AND A. PLAGNE Abstract. We study the gaps in the sequence of sums of h pairwise distinct elements
Caspar David Friedrich Wanderer above the sea of fog (1818)
 ii Caspar David Friedrich Wanderer above the sea of fog (1818) ÉTIENNE GHYS A SINGULAR MATHEMATICAL PROMENADE iv Étienne Ghys CNRS-ENS Lyon, UMPA 46 Allée d Italie 69364 Lyon France etienne.ghys@ens-lyon.fr
ii Caspar David Friedrich Wanderer above the sea of fog (1818) ÉTIENNE GHYS A SINGULAR MATHEMATICAL PROMENADE iv Étienne Ghys CNRS-ENS Lyon, UMPA 46 Allée d Italie 69364 Lyon France etienne.ghys@ens-lyon.fr
H2 MATHS SET D PAPER 1
 H Maths Set D Paper H MATHS Exam papers with worked solutions SET D PAPER Compiled by THE MATHS CAFE P a g e b The curve y ax c x 3 points, and, H Maths Set D Paper has a stationary point at x 3. It also
H Maths Set D Paper H MATHS Exam papers with worked solutions SET D PAPER Compiled by THE MATHS CAFE P a g e b The curve y ax c x 3 points, and, H Maths Set D Paper has a stationary point at x 3. It also
Introduction to Combinatorial Mathematics
 Introduction to Combinatorial Mathematics George Voutsadakis 1 1 Mathematics and Computer Science Lake Superior State University LSSU Math 300 George Voutsadakis (LSSU) Combinatorics April 2016 1 / 57
Introduction to Combinatorial Mathematics George Voutsadakis 1 1 Mathematics and Computer Science Lake Superior State University LSSU Math 300 George Voutsadakis (LSSU) Combinatorics April 2016 1 / 57
An Application of Catalan Numbers on Cayley Tree of Order 2: Single Polygon Counting
 BULLETIN of the Malaysian Mathematical Sciences Society http://math.usm.my/bulletin Bull. Malays. Math. Sci. Soc. (2) 31(2) (2008), 175 183 An Application of Catalan Numbers on Cayley Tree of Order 2:
BULLETIN of the Malaysian Mathematical Sciences Society http://math.usm.my/bulletin Bull. Malays. Math. Sci. Soc. (2) 31(2) (2008), 175 183 An Application of Catalan Numbers on Cayley Tree of Order 2:
Classical Complexity and Fixed-Parameter Tractability of Simultaneous Consecutive Ones Submatrix & Editing Problems
 Classical Complexity and Fixed-Parameter Tractability of Simultaneous Consecutive Ones Submatrix & Editing Problems Rani M. R, Mohith Jagalmohanan, R. Subashini Binary matrices having simultaneous consecutive
Classical Complexity and Fixed-Parameter Tractability of Simultaneous Consecutive Ones Submatrix & Editing Problems Rani M. R, Mohith Jagalmohanan, R. Subashini Binary matrices having simultaneous consecutive
Locating-Total Dominating Sets in Twin-Free Graphs: a Conjecture
 Locating-Total Dominating Sets in Twin-Free Graphs: a Conjecture Florent Foucaud Michael A. Henning Department of Pure and Applied Mathematics University of Johannesburg Auckland Park, 2006, South Africa
Locating-Total Dominating Sets in Twin-Free Graphs: a Conjecture Florent Foucaud Michael A. Henning Department of Pure and Applied Mathematics University of Johannesburg Auckland Park, 2006, South Africa
Laplacian Integral Graphs with Maximum Degree 3
 Laplacian Integral Graphs with Maximum Degree Steve Kirkland Department of Mathematics and Statistics University of Regina Regina, Saskatchewan, Canada S4S 0A kirkland@math.uregina.ca Submitted: Nov 5,
Laplacian Integral Graphs with Maximum Degree Steve Kirkland Department of Mathematics and Statistics University of Regina Regina, Saskatchewan, Canada S4S 0A kirkland@math.uregina.ca Submitted: Nov 5,
The theory of numbers
 1 AXIOMS FOR THE INTEGERS 1 The theory of numbers UCU Foundations of Mathematics course 2017 Author: F. Beukers 1 Axioms for the integers Roughly speaking, number theory is the mathematics of the integers.
1 AXIOMS FOR THE INTEGERS 1 The theory of numbers UCU Foundations of Mathematics course 2017 Author: F. Beukers 1 Axioms for the integers Roughly speaking, number theory is the mathematics of the integers.
Graphs with few total dominating sets
 Graphs with few total dominating sets Marcin Krzywkowski marcin.krzywkowski@gmail.com Stephan Wagner swagner@sun.ac.za Abstract We give a lower bound for the number of total dominating sets of a graph
Graphs with few total dominating sets Marcin Krzywkowski marcin.krzywkowski@gmail.com Stephan Wagner swagner@sun.ac.za Abstract We give a lower bound for the number of total dominating sets of a graph
Dominating Set Counting in Graph Classes
 Dominating Set Counting in Graph Classes Shuji Kijima 1, Yoshio Okamoto 2, and Takeaki Uno 3 1 Graduate School of Information Science and Electrical Engineering, Kyushu University, Japan kijima@inf.kyushu-u.ac.jp
Dominating Set Counting in Graph Classes Shuji Kijima 1, Yoshio Okamoto 2, and Takeaki Uno 3 1 Graduate School of Information Science and Electrical Engineering, Kyushu University, Japan kijima@inf.kyushu-u.ac.jp
Notes on uniform convergence
 Notes on uniform convergence Erik Wahlén erik.wahlen@math.lu.se January 17, 2012 1 Numerical sequences We begin by recalling some properties of numerical sequences. By a numerical sequence we simply mean
Notes on uniform convergence Erik Wahlén erik.wahlen@math.lu.se January 17, 2012 1 Numerical sequences We begin by recalling some properties of numerical sequences. By a numerical sequence we simply mean
Alpha-Beta Pruning: Algorithm and Analysis
 Alpha-Beta Pruning: Algorithm and Analysis Tsan-sheng Hsu tshsu@iis.sinica.edu.tw http://www.iis.sinica.edu.tw/~tshsu 1 Introduction Alpha-beta pruning is the standard searching procedure used for 2-person
Alpha-Beta Pruning: Algorithm and Analysis Tsan-sheng Hsu tshsu@iis.sinica.edu.tw http://www.iis.sinica.edu.tw/~tshsu 1 Introduction Alpha-beta pruning is the standard searching procedure used for 2-person
( ) 0. Section 3.3 Graphs of Polynomial Functions. Chapter 3
 76 Chapter 3 Section 3.3 Graphs of Polynomial Functions In the previous section we explored the short run behavior of quadratics, a special case of polynomials. In this section we will explore the short
76 Chapter 3 Section 3.3 Graphs of Polynomial Functions In the previous section we explored the short run behavior of quadratics, a special case of polynomials. In this section we will explore the short
Chapter 1 The Real Numbers
 Chapter 1 The Real Numbers In a beginning course in calculus, the emphasis is on introducing the techniques of the subject;i.e., differentiation and integration and their applications. An advanced calculus
Chapter 1 The Real Numbers In a beginning course in calculus, the emphasis is on introducing the techniques of the subject;i.e., differentiation and integration and their applications. An advanced calculus
What can you prove by induction?
 MEI CONFERENCE 013 What can you prove by induction? Martyn Parker M.J.Parker@keele.ac.uk Contents Contents iii 1 Splitting Coins.................................................. 1 Convex Polygons................................................
MEI CONFERENCE 013 What can you prove by induction? Martyn Parker M.J.Parker@keele.ac.uk Contents Contents iii 1 Splitting Coins.................................................. 1 Convex Polygons................................................
Constructions with ruler and compass.
 Constructions with ruler and compass. Semyon Alesker. 1 Introduction. Let us assume that we have a ruler and a compass. Let us also assume that we have a segment of length one. Using these tools we can
Constructions with ruler and compass. Semyon Alesker. 1 Introduction. Let us assume that we have a ruler and a compass. Let us also assume that we have a segment of length one. Using these tools we can
Eigenvectors Via Graph Theory
 Eigenvectors Via Graph Theory Jennifer Harris Advisor: Dr. David Garth October 3, 2009 Introduction There is no problem in all mathematics that cannot be solved by direct counting. -Ernst Mach The goal
Eigenvectors Via Graph Theory Jennifer Harris Advisor: Dr. David Garth October 3, 2009 Introduction There is no problem in all mathematics that cannot be solved by direct counting. -Ernst Mach The goal
Alpha-Beta Pruning: Algorithm and Analysis
 Alpha-Beta Pruning: Algorithm and Analysis Tsan-sheng Hsu tshsu@iis.sinica.edu.tw http://www.iis.sinica.edu.tw/~tshsu 1 Introduction Alpha-beta pruning is the standard searching procedure used for 2-person
Alpha-Beta Pruning: Algorithm and Analysis Tsan-sheng Hsu tshsu@iis.sinica.edu.tw http://www.iis.sinica.edu.tw/~tshsu 1 Introduction Alpha-beta pruning is the standard searching procedure used for 2-person
On the minimum neighborhood of independent sets in the n-cube
 Matemática Contemporânea, Vol. 44, 1 10 c 2015, Sociedade Brasileira de Matemática On the minimum neighborhood of independent sets in the n-cube Moysés da S. Sampaio Júnior Fabiano de S. Oliveira Luérbio
Matemática Contemporânea, Vol. 44, 1 10 c 2015, Sociedade Brasileira de Matemática On the minimum neighborhood of independent sets in the n-cube Moysés da S. Sampaio Júnior Fabiano de S. Oliveira Luérbio
5.1 Polynomial Functions
 5.1 Polynomial Functions In this section, we will study the following topics: Identifying polynomial functions and their degree Determining end behavior of polynomial graphs Finding real zeros of polynomial
5.1 Polynomial Functions In this section, we will study the following topics: Identifying polynomial functions and their degree Determining end behavior of polynomial graphs Finding real zeros of polynomial
Partitioning a graph into highly connected subgraphs
 Partitioning a graph into highly connected subgraphs Valentin Borozan 1,5, Michael Ferrara, Shinya Fujita 3 Michitaka Furuya 4, Yannis Manoussakis 5, Narayanan N 6 and Derrick Stolee 7 Abstract Given k
Partitioning a graph into highly connected subgraphs Valentin Borozan 1,5, Michael Ferrara, Shinya Fujita 3 Michitaka Furuya 4, Yannis Manoussakis 5, Narayanan N 6 and Derrick Stolee 7 Abstract Given k
Connectivity of addable graph classes
 Connectivity of addable graph classes Paul Balister Béla Bollobás Stefanie Gerke July 6, 008 A non-empty class A of labelled graphs is weakly addable if for each graph G A and any two distinct components
Connectivity of addable graph classes Paul Balister Béla Bollobás Stefanie Gerke July 6, 008 A non-empty class A of labelled graphs is weakly addable if for each graph G A and any two distinct components
Morse functions statistics
 P H A S I S Journal Program F U N C T I O N A L A N A L Y S I S and Other Mathematics, 006, 11, 97 103 Morse functions statistics Liviu I. Nicolaescu Abstract. We prove a conjecture of V. I. Arnold concerning
P H A S I S Journal Program F U N C T I O N A L A N A L Y S I S and Other Mathematics, 006, 11, 97 103 Morse functions statistics Liviu I. Nicolaescu Abstract. We prove a conjecture of V. I. Arnold concerning
MATH10040: Numbers and Functions Homework 1: Solutions
 MATH10040: Numbers and Functions Homework 1: Solutions 1. Prove that a Z and if 3 divides into a then 3 divides a. Solution: The statement to be proved is equivalent to the statement: For any a N, if 3
MATH10040: Numbers and Functions Homework 1: Solutions 1. Prove that a Z and if 3 divides into a then 3 divides a. Solution: The statement to be proved is equivalent to the statement: For any a N, if 3
Graceful Tree Conjecture for Infinite Trees
 Graceful Tree Conjecture for Infinite Trees Tsz Lung Chan Department of Mathematics The University of Hong Kong, Pokfulam, Hong Kong h0592107@graduate.hku.hk Wai Shun Cheung Department of Mathematics The
Graceful Tree Conjecture for Infinite Trees Tsz Lung Chan Department of Mathematics The University of Hong Kong, Pokfulam, Hong Kong h0592107@graduate.hku.hk Wai Shun Cheung Department of Mathematics The
SUMS PROBLEM COMPETITION, 2000
 SUMS ROBLEM COMETITION, 2000 SOLUTIONS 1 The result is well known, and called Morley s Theorem Many proofs are known See for example HSM Coxeter, Introduction to Geometry, page 23 2 If the number of vertices,
SUMS ROBLEM COMETITION, 2000 SOLUTIONS 1 The result is well known, and called Morley s Theorem Many proofs are known See for example HSM Coxeter, Introduction to Geometry, page 23 2 If the number of vertices,
4 CONNECTED PROJECTIVE-PLANAR GRAPHS ARE HAMILTONIAN. Robin Thomas* Xingxing Yu**
 4 CONNECTED PROJECTIVE-PLANAR GRAPHS ARE HAMILTONIAN Robin Thomas* Xingxing Yu** School of Mathematics Georgia Institute of Technology Atlanta, Georgia 30332, USA May 1991, revised 23 October 1993. Published
4 CONNECTED PROJECTIVE-PLANAR GRAPHS ARE HAMILTONIAN Robin Thomas* Xingxing Yu** School of Mathematics Georgia Institute of Technology Atlanta, Georgia 30332, USA May 1991, revised 23 October 1993. Published
CSE 321 Solutions to Practice Problems
 CSE 321 Solutions to Practice Problems Instructions: Feel free NOT to multiply out binomial coefficients, factorials, etc, and feel free to leave answers in the form of a sum. No calculators, books or
CSE 321 Solutions to Practice Problems Instructions: Feel free NOT to multiply out binomial coefficients, factorials, etc, and feel free to leave answers in the form of a sum. No calculators, books or
Even Cycles in Hypergraphs.
 Even Cycles in Hypergraphs. Alexandr Kostochka Jacques Verstraëte Abstract A cycle in a hypergraph A is an alternating cyclic sequence A 0, v 0, A 1, v 1,..., A k 1, v k 1, A 0 of distinct edges A i and
Even Cycles in Hypergraphs. Alexandr Kostochka Jacques Verstraëte Abstract A cycle in a hypergraph A is an alternating cyclic sequence A 0, v 0, A 1, v 1,..., A k 1, v k 1, A 0 of distinct edges A i and
A basis for the non-crossing partition lattice top homology
 J Algebr Comb (2006) 23: 231 242 DOI 10.1007/s10801-006-7395-5 A basis for the non-crossing partition lattice top homology Eliana Zoque Received: July 31, 2003 / Revised: September 14, 2005 / Accepted:
J Algebr Comb (2006) 23: 231 242 DOI 10.1007/s10801-006-7395-5 A basis for the non-crossing partition lattice top homology Eliana Zoque Received: July 31, 2003 / Revised: September 14, 2005 / Accepted:
Generating p-extremal graphs
 Generating p-extremal graphs Derrick Stolee Department of Mathematics Department of Computer Science University of Nebraska Lincoln s-dstolee1@math.unl.edu August 2, 2011 Abstract Let f(n, p be the maximum
Generating p-extremal graphs Derrick Stolee Department of Mathematics Department of Computer Science University of Nebraska Lincoln s-dstolee1@math.unl.edu August 2, 2011 Abstract Let f(n, p be the maximum
Tree sets. Reinhard Diestel
 1 Tree sets Reinhard Diestel Abstract We study an abstract notion of tree structure which generalizes treedecompositions of graphs and matroids. Unlike tree-decompositions, which are too closely linked
1 Tree sets Reinhard Diestel Abstract We study an abstract notion of tree structure which generalizes treedecompositions of graphs and matroids. Unlike tree-decompositions, which are too closely linked
Bounds on parameters of minimally non-linear patterns
 Bounds on parameters of minimally non-linear patterns P.A. CrowdMath Department of Mathematics Massachusetts Institute of Technology Massachusetts, U.S.A. crowdmath@artofproblemsolving.com Submitted: Jan
Bounds on parameters of minimally non-linear patterns P.A. CrowdMath Department of Mathematics Massachusetts Institute of Technology Massachusetts, U.S.A. crowdmath@artofproblemsolving.com Submitted: Jan
Combinatorial Interpretations of a Generalization of the Genocchi Numbers
 1 2 3 47 6 23 11 Journal of Integer Sequences, Vol. 7 (2004), Article 04.3.6 Combinatorial Interpretations of a Generalization of the Genocchi Numbers Michael Domaratzki Jodrey School of Computer Science
1 2 3 47 6 23 11 Journal of Integer Sequences, Vol. 7 (2004), Article 04.3.6 Combinatorial Interpretations of a Generalization of the Genocchi Numbers Michael Domaratzki Jodrey School of Computer Science
SEPARABILITY AND COMPLETENESS FOR THE WASSERSTEIN DISTANCE
 SEPARABILITY AND COMPLETENESS FOR THE WASSERSTEIN DISTANCE FRANÇOIS BOLLEY Abstract. In this note we prove in an elementary way that the Wasserstein distances, which play a basic role in optimal transportation
SEPARABILITY AND COMPLETENESS FOR THE WASSERSTEIN DISTANCE FRANÇOIS BOLLEY Abstract. In this note we prove in an elementary way that the Wasserstein distances, which play a basic role in optimal transportation
Models of Computation. by Costas Busch, LSU
 Models of Computation by Costas Busch, LSU 1 Computation CPU memory 2 temporary memory input memory CPU output memory Program memory 3 Example: f ( x) x 3 temporary memory input memory Program memory compute
Models of Computation by Costas Busch, LSU 1 Computation CPU memory 2 temporary memory input memory CPU output memory Program memory 3 Example: f ( x) x 3 temporary memory input memory Program memory compute
Enumeration Schemes for Words Avoiding Permutations
 Enumeration Schemes for Words Avoiding Permutations Lara Pudwell November 27, 2007 Abstract The enumeration of permutation classes has been accomplished with a variety of techniques. One wide-reaching
Enumeration Schemes for Words Avoiding Permutations Lara Pudwell November 27, 2007 Abstract The enumeration of permutation classes has been accomplished with a variety of techniques. One wide-reaching
Math 564 Homework 1. Solutions.
 Math 564 Homework 1. Solutions. Problem 1. Prove Proposition 0.2.2. A guide to this problem: start with the open set S = (a, b), for example. First assume that a >, and show that the number a has the properties
Math 564 Homework 1. Solutions. Problem 1. Prove Proposition 0.2.2. A guide to this problem: start with the open set S = (a, b), for example. First assume that a >, and show that the number a has the properties
Paul-Eugène Parent. March 12th, Department of Mathematics and Statistics University of Ottawa. MAT 3121: Complex Analysis I
 Paul-Eugène Parent Department of Mathematics and Statistics University of Ottawa March 12th, 2014 Outline 1 Holomorphic power Series Proposition Let f (z) = a n (z z o ) n be the holomorphic function defined
Paul-Eugène Parent Department of Mathematics and Statistics University of Ottawa March 12th, 2014 Outline 1 Holomorphic power Series Proposition Let f (z) = a n (z z o ) n be the holomorphic function defined
besides your solutions of these problems. 1 1 We note, however, that there will be many factors in the admission decision
 The PRIMES 2015 Math Problem Set Dear PRIMES applicant! This is the PRIMES 2015 Math Problem Set. Please send us your solutions as part of your PRIMES application by December 1, 2015. For complete rules,
The PRIMES 2015 Math Problem Set Dear PRIMES applicant! This is the PRIMES 2015 Math Problem Set. Please send us your solutions as part of your PRIMES application by December 1, 2015. For complete rules,
The domination game played on unions of graphs
 The domination game played on unions of graphs Paul Dorbec 1,2 Gašper Košmrlj 3 Gabriel Renault 1,2 1 Univ. Bordeaux, LaBRI, UMR5800, F-33405 Talence 2 CNRS, LaBRI, UMR5800, F-33405 Talence Email: dorbec@labri.fr,
The domination game played on unions of graphs Paul Dorbec 1,2 Gašper Košmrlj 3 Gabriel Renault 1,2 1 Univ. Bordeaux, LaBRI, UMR5800, F-33405 Talence 2 CNRS, LaBRI, UMR5800, F-33405 Talence Email: dorbec@labri.fr,
UNC Charlotte 2004 Algebra with solutions
 with solutions March 8, 2004 1. Let z denote the real number solution to of the digits of z? (A) 13 (B) 14 (C) 15 (D) 16 (E) 17 3 + x 1 = 5. What is the sum Solution: E. Square both sides twice to get
with solutions March 8, 2004 1. Let z denote the real number solution to of the digits of z? (A) 13 (B) 14 (C) 15 (D) 16 (E) 17 3 + x 1 = 5. What is the sum Solution: E. Square both sides twice to get
Monomial transformations of the projective space
 Monomial transformations of the projective space Olivier Debarre and Bodo Lass Abstract We prove that, over any field, the dimension of the indeterminacy locus of a rational map f : P n P n defined by
Monomial transformations of the projective space Olivier Debarre and Bodo Lass Abstract We prove that, over any field, the dimension of the indeterminacy locus of a rational map f : P n P n defined by
Counting Methods. CSE 191, Class Note 05: Counting Methods Computer Sci & Eng Dept SUNY Buffalo
 Counting Methods CSE 191, Class Note 05: Counting Methods Computer Sci & Eng Dept SUNY Buffalo c Xin He (University at Buffalo) CSE 191 Discrete Structures 1 / 48 Need for Counting The problem of counting
Counting Methods CSE 191, Class Note 05: Counting Methods Computer Sci & Eng Dept SUNY Buffalo c Xin He (University at Buffalo) CSE 191 Discrete Structures 1 / 48 Need for Counting The problem of counting
Caspar David Friedrich Wanderer above the sea of fog (1818)
 ii Caspar David Friedrich Wanderer above the sea of fog (1818) ÉTIENNE GHYS A SINGULAR MATHEMATICAL PROMENADE iv Étienne Ghys CNRS-ENS Lyon, UMPA 46 Allée d Italie 69364 Lyon France http://perso.ens-lyon.fr/ghys
ii Caspar David Friedrich Wanderer above the sea of fog (1818) ÉTIENNE GHYS A SINGULAR MATHEMATICAL PROMENADE iv Étienne Ghys CNRS-ENS Lyon, UMPA 46 Allée d Italie 69364 Lyon France http://perso.ens-lyon.fr/ghys
HMMT February 2018 February 10, 2018
 HMMT February 018 February 10, 018 Algebra and Number Theory 1. For some real number c, the graphs of the equation y = x 0 + x + 18 and the line y = x + c intersect at exactly one point. What is c? 18
HMMT February 018 February 10, 018 Algebra and Number Theory 1. For some real number c, the graphs of the equation y = x 0 + x + 18 and the line y = x + c intersect at exactly one point. What is c? 18
Standard forms for writing numbers
 Standard forms for writing numbers In order to relate the abstract mathematical descriptions of familiar number systems to the everyday descriptions of numbers by decimal expansions and similar means,
Standard forms for writing numbers In order to relate the abstract mathematical descriptions of familiar number systems to the everyday descriptions of numbers by decimal expansions and similar means,
Lecture 4 October 18th
 Directed and undirected graphical models Fall 2017 Lecture 4 October 18th Lecturer: Guillaume Obozinski Scribe: In this lecture, we will assume that all random variables are discrete, to keep notations
Directed and undirected graphical models Fall 2017 Lecture 4 October 18th Lecturer: Guillaume Obozinski Scribe: In this lecture, we will assume that all random variables are discrete, to keep notations
Department of Mathematics, University of California, Berkeley. GRADUATE PRELIMINARY EXAMINATION, Part A Fall Semester 2014
 Department of Mathematics, University of California, Berkeley YOUR 1 OR 2 DIGIT EXAM NUMBER GRADUATE PRELIMINARY EXAMINATION, Part A Fall Semester 2014 1. Please write your 1- or 2-digit exam number on
Department of Mathematics, University of California, Berkeley YOUR 1 OR 2 DIGIT EXAM NUMBER GRADUATE PRELIMINARY EXAMINATION, Part A Fall Semester 2014 1. Please write your 1- or 2-digit exam number on
5.5 Deeper Properties of Continuous Functions
 5.5. DEEPER PROPERTIES OF CONTINUOUS FUNCTIONS 195 5.5 Deeper Properties of Continuous Functions 5.5.1 Intermediate Value Theorem and Consequences When one studies a function, one is usually interested
5.5. DEEPER PROPERTIES OF CONTINUOUS FUNCTIONS 195 5.5 Deeper Properties of Continuous Functions 5.5.1 Intermediate Value Theorem and Consequences When one studies a function, one is usually interested
UNDERSTANDING RULER AND COMPASS CONSTRUCTIONS WITH FIELD THEORY
 UNDERSTANDING RULER AND COMPASS CONSTRUCTIONS WITH FIELD THEORY ISAAC M. DAVIS Abstract. By associating a subfield of R to a set of points P 0 R 2, geometric properties of ruler and compass constructions
UNDERSTANDING RULER AND COMPASS CONSTRUCTIONS WITH FIELD THEORY ISAAC M. DAVIS Abstract. By associating a subfield of R to a set of points P 0 R 2, geometric properties of ruler and compass constructions
Universal convex coverings
 Bull. London Math. Soc. 41 (2009) 987 992 C 2009 London Mathematical Society doi:10.1112/blms/bdp076 Universal convex coverings Roland Bacher Abstract In every dimension d 1, we establish the existence
Bull. London Math. Soc. 41 (2009) 987 992 C 2009 London Mathematical Society doi:10.1112/blms/bdp076 Universal convex coverings Roland Bacher Abstract In every dimension d 1, we establish the existence
Real Analysis Math 131AH Rudin, Chapter #1. Dominique Abdi
 Real Analysis Math 3AH Rudin, Chapter # Dominique Abdi.. If r is rational (r 0) and x is irrational, prove that r + x and rx are irrational. Solution. Assume the contrary, that r+x and rx are rational.
Real Analysis Math 3AH Rudin, Chapter # Dominique Abdi.. If r is rational (r 0) and x is irrational, prove that r + x and rx are irrational. Solution. Assume the contrary, that r+x and rx are rational.
MATH 722, COMPLEX ANALYSIS, SPRING 2009 PART 5
 MATH 722, COMPLEX ANALYSIS, SPRING 2009 PART 5.. The Arzela-Ascoli Theorem.. The Riemann mapping theorem Let X be a metric space, and let F be a family of continuous complex-valued functions on X. We have
MATH 722, COMPLEX ANALYSIS, SPRING 2009 PART 5.. The Arzela-Ascoli Theorem.. The Riemann mapping theorem Let X be a metric space, and let F be a family of continuous complex-valued functions on X. We have
Math 259: Introduction to Analytic Number Theory Functions of finite order: product formula and logarithmic derivative
 Math 259: Introduction to Analytic Number Theory Functions of finite order: product formula and logarithmic derivative This chapter is another review of standard material in complex analysis. See for instance
Math 259: Introduction to Analytic Number Theory Functions of finite order: product formula and logarithmic derivative This chapter is another review of standard material in complex analysis. See for instance
Some Examples of Lexicographic Order Algorithms and some Open Combinatorial Problems
 Some Examples of Lexicographic Order Algorithms and some Open Combinatorial Problems Dimitar Vandev A general reasoning based on the lexicographic order is studied. It helps to create algorithms for generation
Some Examples of Lexicographic Order Algorithms and some Open Combinatorial Problems Dimitar Vandev A general reasoning based on the lexicographic order is studied. It helps to create algorithms for generation
Section 1: Sets and Interval Notation
 PART 1 From Sets to Functions Section 1: Sets and Interval Notation Introduction Set concepts offer the means for understanding many different aspects of mathematics and its applications to other branches
PART 1 From Sets to Functions Section 1: Sets and Interval Notation Introduction Set concepts offer the means for understanding many different aspects of mathematics and its applications to other branches
CMSC Discrete Mathematics SOLUTIONS TO FIRST MIDTERM EXAM October 18, 2005 posted Nov 2, 2005
 CMSC-37110 Discrete Mathematics SOLUTIONS TO FIRST MIDTERM EXAM October 18, 2005 posted Nov 2, 2005 Instructor: László Babai Ryerson 164 e-mail: laci@cs This exam contributes 20% to your course grade.
CMSC-37110 Discrete Mathematics SOLUTIONS TO FIRST MIDTERM EXAM October 18, 2005 posted Nov 2, 2005 Instructor: László Babai Ryerson 164 e-mail: laci@cs This exam contributes 20% to your course grade.
Given any simple graph G = (V, E), not necessarily finite, and a ground set X, a set-indexer
 Chapter 2 Topogenic Graphs Given any simple graph G = (V, E), not necessarily finite, and a ground set X, a set-indexer of G is an injective set-valued function f : V (G) 2 X such that the induced edge
Chapter 2 Topogenic Graphs Given any simple graph G = (V, E), not necessarily finite, and a ground set X, a set-indexer of G is an injective set-valued function f : V (G) 2 X such that the induced edge
CS1800 Discrete Structures Final Version A
 CS1800 Discrete Structures Fall 2017 Profs. Aslam, Gold, & Pavlu December 11, 2017 CS1800 Discrete Structures Final Version A Instructions: 1. The exam is closed book and closed notes. You may not use
CS1800 Discrete Structures Fall 2017 Profs. Aslam, Gold, & Pavlu December 11, 2017 CS1800 Discrete Structures Final Version A Instructions: 1. The exam is closed book and closed notes. You may not use
Math 259: Introduction to Analytic Number Theory Functions of finite order: product formula and logarithmic derivative
 Math 259: Introduction to Analytic Number Theory Functions of finite order: product formula and logarithmic derivative This chapter is another review of standard material in complex analysis. See for instance
Math 259: Introduction to Analytic Number Theory Functions of finite order: product formula and logarithmic derivative This chapter is another review of standard material in complex analysis. See for instance
ON THE POSSIBLE QUANTITIES OF FIBONACCI NUMBERS THAT OCCUR IN SOME TYPES OF INTERVALS
 Acta Math. Univ. Comenianae Vol. LXXXVII, 2 (2018), pp. 291 299 291 ON THE POSSIBLE QUANTITIES OF FIBONACCI NUMBERS THAT OCCUR IN SOME TYPES OF INTERVALS B. FARHI Abstract. In this paper, we show that
Acta Math. Univ. Comenianae Vol. LXXXVII, 2 (2018), pp. 291 299 291 ON THE POSSIBLE QUANTITIES OF FIBONACCI NUMBERS THAT OCCUR IN SOME TYPES OF INTERVALS B. FARHI Abstract. In this paper, we show that
On representable graphs
 On representable graphs Sergey Kitaev and Artem Pyatkin 3rd November 2005 Abstract A graph G = (V, E) is representable if there exists a word W over the alphabet V such that letters x and y alternate in
On representable graphs Sergey Kitaev and Artem Pyatkin 3rd November 2005 Abstract A graph G = (V, E) is representable if there exists a word W over the alphabet V such that letters x and y alternate in
Game Theory and Algorithms Lecture 7: PPAD and Fixed-Point Theorems
 Game Theory and Algorithms Lecture 7: PPAD and Fixed-Point Theorems March 17, 2011 Summary: The ultimate goal of this lecture is to finally prove Nash s theorem. First, we introduce and prove Sperner s
Game Theory and Algorithms Lecture 7: PPAD and Fixed-Point Theorems March 17, 2011 Summary: The ultimate goal of this lecture is to finally prove Nash s theorem. First, we introduce and prove Sperner s
1 Basic Combinatorics
 1 Basic Combinatorics 1.1 Sets and sequences Sets. A set is an unordered collection of distinct objects. The objects are called elements of the set. We use braces to denote a set, for example, the set
1 Basic Combinatorics 1.1 Sets and sequences Sets. A set is an unordered collection of distinct objects. The objects are called elements of the set. We use braces to denote a set, for example, the set
MATH 802: ENUMERATIVE COMBINATORICS ASSIGNMENT 2
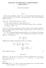 MATH 80: ENUMERATIVE COMBINATORICS ASSIGNMENT KANNAPPAN SAMPATH Facts Recall that, the Stirling number S(, n of the second ind is defined as the number of partitions of a [] into n non-empty blocs. We
MATH 80: ENUMERATIVE COMBINATORICS ASSIGNMENT KANNAPPAN SAMPATH Facts Recall that, the Stirling number S(, n of the second ind is defined as the number of partitions of a [] into n non-empty blocs. We
Graphs of Polynomial Functions
 Graphs of Polynomial Functions By: OpenStaxCollege The revenue in millions of dollars for a fictional cable company from 2006 through 2013 is shown in [link]. Year 2006 2007 2008 2009 2010 2011 2012 2013
Graphs of Polynomial Functions By: OpenStaxCollege The revenue in millions of dollars for a fictional cable company from 2006 through 2013 is shown in [link]. Year 2006 2007 2008 2009 2010 2011 2012 2013
CHAPTER 7. Connectedness
 CHAPTER 7 Connectedness 7.1. Connected topological spaces Definition 7.1. A topological space (X, T X ) is said to be connected if there is no continuous surjection f : X {0, 1} where the two point set
CHAPTER 7 Connectedness 7.1. Connected topological spaces Definition 7.1. A topological space (X, T X ) is said to be connected if there is no continuous surjection f : X {0, 1} where the two point set
Algorithms: Lecture 12. Chalmers University of Technology
 Algorithms: Lecture 1 Chalmers University of Technology Today s Topics Shortest Paths Network Flow Algorithms Shortest Path in a Graph Shortest Path Problem Shortest path network. Directed graph G = (V,
Algorithms: Lecture 1 Chalmers University of Technology Today s Topics Shortest Paths Network Flow Algorithms Shortest Path in a Graph Shortest Path Problem Shortest path network. Directed graph G = (V,
Part III. 10 Topological Space Basics. Topological Spaces
 Part III 10 Topological Space Basics Topological Spaces Using the metric space results above as motivation we will axiomatize the notion of being an open set to more general settings. Definition 10.1.
Part III 10 Topological Space Basics Topological Spaces Using the metric space results above as motivation we will axiomatize the notion of being an open set to more general settings. Definition 10.1.
Topics in Algorithms. 1 Generation of Basic Combinatorial Objects. Exercises. 1.1 Generation of Subsets. 1. Consider the sum:
 Topics in Algorithms Exercises 1 Generation of Basic Combinatorial Objects 1.1 Generation of Subsets 1. Consider the sum: (ε 1,...,ε n) {0,1} n f(ε 1,..., ε n ) (a) Show that it may be calculated in O(n)
Topics in Algorithms Exercises 1 Generation of Basic Combinatorial Objects 1.1 Generation of Subsets 1. Consider the sum: (ε 1,...,ε n) {0,1} n f(ε 1,..., ε n ) (a) Show that it may be calculated in O(n)
7 Asymptotics for Meromorphic Functions
 Lecture G jacques@ucsd.edu 7 Asymptotics for Meromorphic Functions Hadamard s Theorem gives a broad description of the exponential growth of coefficients in power series, but the notion of exponential
Lecture G jacques@ucsd.edu 7 Asymptotics for Meromorphic Functions Hadamard s Theorem gives a broad description of the exponential growth of coefficients in power series, but the notion of exponential
1. Introduction
 Séminaire Lotharingien de Combinatoire 49 (2002), Article B49a AVOIDING 2-LETTER SIGNED PATTERNS T. MANSOUR A AND J. WEST B A LaBRI (UMR 5800), Université Bordeaux, 35 cours de la Libération, 33405 Talence
Séminaire Lotharingien de Combinatoire 49 (2002), Article B49a AVOIDING 2-LETTER SIGNED PATTERNS T. MANSOUR A AND J. WEST B A LaBRI (UMR 5800), Université Bordeaux, 35 cours de la Libération, 33405 Talence
QUADRANT MARKED MESH PATTERNS IN 132-AVOIDING PERMUTATIONS III
 #A39 INTEGERS 5 (05) QUADRANT MARKED MESH PATTERNS IN 3-AVOIDING PERMUTATIONS III Sergey Kitaev Department of Computer and Information Sciences, University of Strathclyde, Glasgow, United Kingdom sergey.kitaev@cis.strath.ac.uk
#A39 INTEGERS 5 (05) QUADRANT MARKED MESH PATTERNS IN 3-AVOIDING PERMUTATIONS III Sergey Kitaev Department of Computer and Information Sciences, University of Strathclyde, Glasgow, United Kingdom sergey.kitaev@cis.strath.ac.uk
