Robin Moser makes Lovász Local Lemma Algorithmic! Notes of Joel Spencer
|
|
|
- Sophia McCarthy
- 5 years ago
- Views:
Transcription
1 Robin Moser makes Lovász Local Lemma Algorithmic! Notes of Joel Spencer 1 Preliminaries The idea in these notes is to explain a new approach of Robin Moser 1 to give an algorithm for the Lovász Local Lemma. This description is of the approach as modified and improved by Gábor Tardos. We don t strive for best possible or most general here. In particular, we stick to what is called the symmetric case. Lets start with a particular and instructive example. Let x i, 1 i n be Boolean variables. Let C j, 1 j m be clauses, each the disjunction of k variables or their negations. For example, with k = 3, x 8 x 19 x 37 would be a typical clause. We say two clauses overlap, and write C i C j, if they have a common variable x k, regardless of whether the variable is negated or not in the clauses. A set of clauses is called mutually satisfiable if there exists a truth assignment of the underlying variables so that each clause is satisfied or, equivalently, if the of the clauses is satisfiable. Theorem 1.1 Assume, using the above notation, that each clause overlaps at most d clauses (including itself). Assume 2 k d d 1 (1) (d 1) d 1 Then the set of clauses is mutually satisfiable. Moreover (and this is the new part) there is an algorithm that finds an assignment for which each clause C j is satisfied that runs in linear time in n, with k,d fixed. Here is a more general setting. Let Ω be a set of size n. For v Ω let X v be independent random variables. For 1 j m let e j Ω and let B j be an event that depends only on the values X v, v e j. We say two events overlap, and write B i B j, if e i e j. Theorem 1.2 Assume, using the above notation, that each event overlaps at most d events (including itself). Assume Pr[B j ] p for all j (2) 1 Moser is a graduate student (!) at ETH, working with Emo Welzl 1
2 and that Then d d p 1 (3) (d 1) d 1 m j=1b j (4) Moreover (and this is the new part) there is an algorithm that finds an assignment of the X i for which each B j holds that runs in linear time in n, with k, d fixed. To say the implication of Theorem 1.1 from Theorem 1.2 consider a random assignment X v of the variables x v. That is, each X v independently takes on the values true, false with probabilities one half. The bad event B j is then that the clause C j is not satisfied, which has probability 2 k. The event that none of the bad events occur is nonempty. By Erdős Magic, there is a point in the probability space, which is precisely an assignment of truth values, such that no bad event occurs, which is precisely that the clauses are all simultaneously satisfied. We will write the proof in the more general form, but the example of Theorem 1.1 is a good one to keep in mind. The time of the algorithm actually will depend on some data structure assumptions which we omit. The Moser-Tardos (ML) Algorithm. 1. Give X v random values from their distributions. 2. WHILE some B j holds. 3. PICK some B j that holds. 4. Reset the X v, v e j, independently 5. END WHILE The selection mechanism for PICK can be arbitrary. For definiteness, we may pick the minimal j for which B j holds, but it doesn t affect the proof. We just need some specified mechanism for PICK. As this is a randomized algorithm, its output may be and will be considered a random variable. Let B t,e t be the event and underlying set in the t-th iteration of the WHILE loop. We shall refer to this as time t in the running of ML. We define the LOG of the running of the algorithm to be the sequence e 1,...,e t,... A priori, there is no reason to believe that this algorithm will actually terminate, and so the LOG might be an infinite sequence. On the other extreme, the initial random assignment might work in which case LOG would be the null sequence. For convenience we let H = {e 1,...,e m } so that the e H are just the possible values of the e t. For e H let COUNT[e] denote the number of times e appears in LOG, that is, the number of times t for which e = e t. A priori this could be infinite. But our main result is: 2
3 Theorem 1.3 E[COUNT[e]] 1 d 1 (5) Given this result, linearity of expectation gives m Theorem 1.4 The expected length of LOG is at most number of events. d 1 where m is the As each event overlaps at most d events, each v Ω can be in at most d events, and so m nd. Theorem 1.4 then gives that the expected length of LOG is linear in the size of Ω. This is why we call the MT algorithm linear time, though in particular instances one would need further assumptions about the data structure. The remainder of the argument is a proof of Theorem 1.3. Given a running of MT with the LOG of size at least t we define TREE[t] to be a rooted tree with vertices labelled by the e H. (Note: Several vertices may have the same label.) The root of TREE[t] is e t. Now we construct the tree by reverse induction from i = t 1 to i = 1. (When t = 1 the tree has only the root e 1.) For a given i we check whether there is a j, i < j t, such that e i,e j overlap and e j has already been placed in the tree. If there is no such j we go on to the next i, that is, we do not put e i in the tree. If there is such a j select that j for which e j is lowest (that is, furthest from the root, this part is important!) and add to the tree by making e i a child of e j. In case of ties, use an arbitrary tiebreaker, for example, pick that j with the smallest index. TREE[t] gives a concise description of those e i that are relevant to e t. It has certain key tautological properties. The TREE[t] are all different. Reason: If s < t and TREE[s],TREE[t] were equal, they would have to have the same root e = e s = e t. In creating TREE[t] each time e i = e for 1 i t there will be another node e in the tree. (When i < t as e i does overlap e t it is placed in the tree.) That is, e appears in the tree precisely the number of times in appears in e 1,...,e t. When e = e s = e t, however, these numbers will be different for T REE[s], T REE[t] as all the copies of e in TREE[s] are in TREE[t] and e t is in TREE[t] but not TREE[s]. The e TREE[t] on the same level of the tree do not overlap. Reason: Suppose r < s and e r,e s TREE[t] and suppose they did overlap. When e r is placed in the tree it is placed as low as possible. Since e s is already in the tree it is placed on the level below e s or even lower. When e r,e s TREE[t] overlap and r < s, e r is lower than e s. Reason: Above. Let v Ω and let f 0,...,f s be the nodes of TREE[t] that contain v. Order these by the depth of the node in the tree with the first being the furthest from the root. (From above there will be no ties.) Then the fs will be in this order in the LOG. Reason: Say 0 i < j s. After f j was placed in TREE[t] the later (in creating TREE) f i overlaps f j and so is placed on the level below f j or even lower. 3
4 Furthermore, there will be no other e in the LOG that contain v and come before f s. Reason: All such e overlaps f s and so would be placed in the TREE. Let T be a rooted tree with vertices labelled by e H and such that when f is a child of e, f,e overlap. For each such T let OCCUR[T] be the event that T = TREE[t] for some t. Let T denote the number of nodes of T. Theorem 1.5 Pr[OCCUR[T]] p T (6) While the proof of Theorem 1.5 is short, it is subtle and we begin with two simple examples. Suppose T consists solely of the root e. Then OCCUR[T] means that at some time t in the running of ML an event B t held and values X i, i e t = e were changed. But it further means that there had been no e s overlapping e before this time. That is, the values X i, i e t = e, were unchanged from their original values. Thus for OCCUR[T] to hold it is necessary that B t holds with the original values of the X i and this occurs with probability at most p. Now suppose T consists solely of the root e and a child f. Suppose f arises at time s and then e arises at time t > s. The subtlety arises with those i Ω lying in both e and f. For these we must distinguish the original value of X i and the revised value after time s. It is necessary that B s hold with the original values of X i and this occurs with probability at most p. It is further necessary that B t holds using the revised values X i for i e f and the original values for the other i e. This also occurs with probability at most p and, more importantly, that probability that both B s and B t hold is at most p 2. This is because in looking at B t we are looking at different coin flips for the values X i. We argue the general case for Theorem 1.5 by preprocessing the randomness. That is, each variable v Ω independently makes a countable number of evaluations of X v, labelled x 0 v,x1 v,... Following this preprocessing ML is deterministic. When v needs to reset X v for the i-th time, it takes the value x i v, x 0 v being the original evaluation. We call i above the evaluation number. Preprocessing is a powerful tool in analyzing random algorithms, though it has no affect on the actual running of the algorithms. While TREE[t] does not determine LOG, or even the precise order of the appearances of the nodes of TREE[t] in the LOG, it does determine the order of appearance of the nodes f 0,...,f s containing any given vertex v. When the ML algorithm reached f i, v had value x i v. That is, for each e TREE[t] and each vertex v e there is an evaluation number i so that when ML reaches e the vertex v had value x i v. Critically, this i is determined by the TREE (even though many values of LOG could yield the same TREE) and the particular node e and vertex v. For OCCUR[T] it is necessary that For each e T REE the associated bad event B occurs where for each v e, v is using the i-th evaluation with i the evaluation number as determined above. 4
5 For each e TREE this occurs with probability at most p as the various evaluations are independent. Moreover, critically, the various events B are mutually independent as for each v one uses different evaluation number for each one. Thus the probability that all the B hold at their various times is at most p T, completing Theorem 1.5. Now we turn to proving Theorem 1.3 by bounding E[COUNT[e]]. As the values T REE[t] are tautologically distinct, no T can be counted more than once in COUNT[e] and so E[COUNT[e]] = T Pr[OCCUR[T]] T p T (7) where the sum is over all finite trees with root e, and the second inequality is from Theorem 1.5. We bound the Right Hand Side of 7 using standard methods from algebraic combinatorics. Let PURE denote the infinite rooted tree in which every node has precisely d children. Let ACTUALbe the infinite tree rooted at e in which f has as children all g which overlap it. Our basic assumption is that each node in ACTUAL will have at most d children and so ACTUALis a subtree of PURE. Hence the sum for subtrees T of ACTUALis at most the sum for subtrees of PURE. Here we have an exact result. Theorem 1.6 Assume (d 1)d 1 p d d (8) Then, taking the sum over all subtrees of PURErooted at the root of PURE, y = T p T (9) is finite, and is that unique y, 0 y 1 d 1, satisfying y = p(1 + y) d (10) Proof: Assumming the sum is finite, we find 10 by considering the terms when there are i children of the root in T. Each subtree then gives a contribution of y and they are independent so the total contribution is y i. Thus y = p d i=0 ( ) d y i = p(1 + y) d (11) i In general let y s be the sum 9 over all T of depth at most s. Then y 0 = p and 11 becomes ( ) d d y s+1 = p ys i i = p(1 + y s) d (12) i=0 and basic analysis shows that this sequence approaches a fixed point y as desired. 5
NEEDLES IN EXPONENTIAL HAYSTACKS II Notes of Joel Spencer Cornell Probability School The Lovász Local Lemma
 NEEDLES IN EXPONENTIAL HAYSTACKS II Notes of Joel Spencer Cornell Probability School 2012 1 The Lovász Local Lemma We here describe the LLL in somewhat different, and somewhat more limited, format that
NEEDLES IN EXPONENTIAL HAYSTACKS II Notes of Joel Spencer Cornell Probability School 2012 1 The Lovász Local Lemma We here describe the LLL in somewhat different, and somewhat more limited, format that
Lecture 10 Algorithmic version of the local lemma
 Lecture 10 Algorithmic version of the local lemma Uriel Feige Department of Computer Science and Applied Mathematics The Weizman Institute Rehovot 76100, Israel uriel.feige@weizmann.ac.il June 9, 2014
Lecture 10 Algorithmic version of the local lemma Uriel Feige Department of Computer Science and Applied Mathematics The Weizman Institute Rehovot 76100, Israel uriel.feige@weizmann.ac.il June 9, 2014
The Lovász Local Lemma : A constructive proof
 The Lovász Local Lemma : A constructive proof Andrew Li 19 May 2016 Abstract The Lovász Local Lemma is a tool used to non-constructively prove existence of combinatorial objects meeting a certain conditions.
The Lovász Local Lemma : A constructive proof Andrew Li 19 May 2016 Abstract The Lovász Local Lemma is a tool used to non-constructively prove existence of combinatorial objects meeting a certain conditions.
An Algorithmic Proof of the Lopsided Lovász Local Lemma (simplified and condensed into lecture notes)
 An Algorithmic Proof of the Lopsided Lovász Local Lemma (simplified and condensed into lecture notes) Nicholas J. A. Harvey University of British Columbia Vancouver, Canada nickhar@cs.ubc.ca Jan Vondrák
An Algorithmic Proof of the Lopsided Lovász Local Lemma (simplified and condensed into lecture notes) Nicholas J. A. Harvey University of British Columbia Vancouver, Canada nickhar@cs.ubc.ca Jan Vondrák
Lecture Notes CS:5360 Randomized Algorithms Lecture 20 and 21: Nov 6th and 8th, 2018 Scribe: Qianhang Sun
 1 Probabilistic Method Lecture Notes CS:5360 Randomized Algorithms Lecture 20 and 21: Nov 6th and 8th, 2018 Scribe: Qianhang Sun Turning the MaxCut proof into an algorithm. { Las Vegas Algorithm Algorithm
1 Probabilistic Method Lecture Notes CS:5360 Randomized Algorithms Lecture 20 and 21: Nov 6th and 8th, 2018 Scribe: Qianhang Sun Turning the MaxCut proof into an algorithm. { Las Vegas Algorithm Algorithm
n Boolean variables: x 1, x 2,...,x n 2 {true,false} conjunctive normal form:
 Advanced Algorithms k-sat n Boolean variables: x 1, x 2,...,x n 2 {true,false} conjunctive normal form: k-cnf = C 1 ^C 2 ^ ^C m Is φ satisfiable? m clauses: C 1,C 2,...,C m each clause C i = `i1 _ `i2
Advanced Algorithms k-sat n Boolean variables: x 1, x 2,...,x n 2 {true,false} conjunctive normal form: k-cnf = C 1 ^C 2 ^ ^C m Is φ satisfiable? m clauses: C 1,C 2,...,C m each clause C i = `i1 _ `i2
An extension of the Moser-Tardos algorithmic local lemma
 An extension of the Moser-Tardos algorithmic local lemma Wesley Pegden January 26, 2013 Abstract A recent theorem of Bissacot, et al. proved using results about the cluster expansion in statistical mechanics
An extension of the Moser-Tardos algorithmic local lemma Wesley Pegden January 26, 2013 Abstract A recent theorem of Bissacot, et al. proved using results about the cluster expansion in statistical mechanics
Induction on Failing Derivations
 Induction on Failing Derivations Technical Report PL-Sep13 September 2013, with addenda from Spring 2016 ay Ligatti Department of Computer Science and Engineering University of South Florida Abstract A
Induction on Failing Derivations Technical Report PL-Sep13 September 2013, with addenda from Spring 2016 ay Ligatti Department of Computer Science and Engineering University of South Florida Abstract A
Propositional Logic: Models and Proofs
 Propositional Logic: Models and Proofs C. R. Ramakrishnan CSE 505 1 Syntax 2 Model Theory 3 Proof Theory and Resolution Compiled at 11:51 on 2016/11/02 Computing with Logic Propositional Logic CSE 505
Propositional Logic: Models and Proofs C. R. Ramakrishnan CSE 505 1 Syntax 2 Model Theory 3 Proof Theory and Resolution Compiled at 11:51 on 2016/11/02 Computing with Logic Propositional Logic CSE 505
3 Propositional Logic
 3 Propositional Logic 3.1 Syntax 3.2 Semantics 3.3 Equivalence and Normal Forms 3.4 Proof Procedures 3.5 Properties Propositional Logic (25th October 2007) 1 3.1 Syntax Definition 3.0 An alphabet Σ consists
3 Propositional Logic 3.1 Syntax 3.2 Semantics 3.3 Equivalence and Normal Forms 3.4 Proof Procedures 3.5 Properties Propositional Logic (25th October 2007) 1 3.1 Syntax Definition 3.0 An alphabet Σ consists
Lecture 2: Proof of Switching Lemma
 Lecture 2: oof of Switching Lemma Yuan Li June 25, 2014 1 Decision Tree Instead of bounding the probability that f can be written as some s-dnf, we estimate the probability that f can be computed by a
Lecture 2: oof of Switching Lemma Yuan Li June 25, 2014 1 Decision Tree Instead of bounding the probability that f can be written as some s-dnf, we estimate the probability that f can be computed by a
Size and degree anti-ramsey numbers
 Size and degree anti-ramsey numbers Noga Alon Abstract A copy of a graph H in an edge colored graph G is called rainbow if all edges of H have distinct colors. The size anti-ramsey number of H, denoted
Size and degree anti-ramsey numbers Noga Alon Abstract A copy of a graph H in an edge colored graph G is called rainbow if all edges of H have distinct colors. The size anti-ramsey number of H, denoted
On the Effectiveness of Symmetry Breaking
 On the Effectiveness of Symmetry Breaking Russell Miller 1, Reed Solomon 2, and Rebecca M Steiner 3 1 Queens College and the Graduate Center of the City University of New York Flushing NY 11367 2 University
On the Effectiveness of Symmetry Breaking Russell Miller 1, Reed Solomon 2, and Rebecca M Steiner 3 1 Queens College and the Graduate Center of the City University of New York Flushing NY 11367 2 University
Lecture 24: April 12
 CS271 Randomness & Computation Spring 2018 Instructor: Alistair Sinclair Lecture 24: April 12 Disclaimer: These notes have not been subjected to the usual scrutiny accorded to formal publications. They
CS271 Randomness & Computation Spring 2018 Instructor: Alistair Sinclair Lecture 24: April 12 Disclaimer: These notes have not been subjected to the usual scrutiny accorded to formal publications. They
A An Overview of Complexity Theory for the Algorithm Designer
 A An Overview of Complexity Theory for the Algorithm Designer A.1 Certificates and the class NP A decision problem is one whose answer is either yes or no. Two examples are: SAT: Given a Boolean formula
A An Overview of Complexity Theory for the Algorithm Designer A.1 Certificates and the class NP A decision problem is one whose answer is either yes or no. Two examples are: SAT: Given a Boolean formula
Notes on the Matrix-Tree theorem and Cayley s tree enumerator
 Notes on the Matrix-Tree theorem and Cayley s tree enumerator 1 Cayley s tree enumerator Recall that the degree of a vertex in a tree (or in any graph) is the number of edges emanating from it We will
Notes on the Matrix-Tree theorem and Cayley s tree enumerator 1 Cayley s tree enumerator Recall that the degree of a vertex in a tree (or in any graph) is the number of edges emanating from it We will
Propositional and Predicate Logic - V
 Propositional and Predicate Logic - V Petr Gregor KTIML MFF UK WS 2016/2017 Petr Gregor (KTIML MFF UK) Propositional and Predicate Logic - V WS 2016/2017 1 / 21 Formal proof systems Hilbert s calculus
Propositional and Predicate Logic - V Petr Gregor KTIML MFF UK WS 2016/2017 Petr Gregor (KTIML MFF UK) Propositional and Predicate Logic - V WS 2016/2017 1 / 21 Formal proof systems Hilbert s calculus
The Probabilistic Method
 The Probabilistic Method Janabel Xia and Tejas Gopalakrishna MIT PRIMES Reading Group, mentors Gwen McKinley and Jake Wellens December 7th, 2018 Janabel Xia and Tejas Gopalakrishna Probabilistic Method
The Probabilistic Method Janabel Xia and Tejas Gopalakrishna MIT PRIMES Reading Group, mentors Gwen McKinley and Jake Wellens December 7th, 2018 Janabel Xia and Tejas Gopalakrishna Probabilistic Method
FIRST ORDER SENTENCES ON G(n, p), ZERO-ONE LAWS, ALMOST SURE AND COMPLETE THEORIES ON SPARSE RANDOM GRAPHS
 FIRST ORDER SENTENCES ON G(n, p), ZERO-ONE LAWS, ALMOST SURE AND COMPLETE THEORIES ON SPARSE RANDOM GRAPHS MOUMANTI PODDER 1. First order theory on G(n, p) We start with a very simple property of G(n,
FIRST ORDER SENTENCES ON G(n, p), ZERO-ONE LAWS, ALMOST SURE AND COMPLETE THEORIES ON SPARSE RANDOM GRAPHS MOUMANTI PODDER 1. First order theory on G(n, p) We start with a very simple property of G(n,
Propositional and Predicate Logic - II
 Propositional and Predicate Logic - II Petr Gregor KTIML MFF UK WS 2016/2017 Petr Gregor (KTIML MFF UK) Propositional and Predicate Logic - II WS 2016/2017 1 / 16 Basic syntax Language Propositional logic
Propositional and Predicate Logic - II Petr Gregor KTIML MFF UK WS 2016/2017 Petr Gregor (KTIML MFF UK) Propositional and Predicate Logic - II WS 2016/2017 1 / 16 Basic syntax Language Propositional logic
Basing Decisions on Sentences in Decision Diagrams
 Proceedings of the Twenty-Sixth AAAI Conference on Artificial Intelligence Basing Decisions on Sentences in Decision Diagrams Yexiang Xue Department of Computer Science Cornell University yexiang@cs.cornell.edu
Proceedings of the Twenty-Sixth AAAI Conference on Artificial Intelligence Basing Decisions on Sentences in Decision Diagrams Yexiang Xue Department of Computer Science Cornell University yexiang@cs.cornell.edu
Advanced Algorithms 南京大学 尹一通
 Advanced Algorithms 南京大学 尹一通 Constraint Satisfaction Problem variables: (CSP) X = {x 1, x2,..., xn} each variable ranges over a finite domain Ω an assignment σ ΩX assigns each variable a value in Ω constraints:
Advanced Algorithms 南京大学 尹一通 Constraint Satisfaction Problem variables: (CSP) X = {x 1, x2,..., xn} each variable ranges over a finite domain Ω an assignment σ ΩX assigns each variable a value in Ω constraints:
Bayesian Networks Factor Graphs the Case-Factor Algorithm and the Junction Tree Algorithm
 Bayesian Networks Factor Graphs the Case-Factor Algorithm and the Junction Tree Algorithm 1 Bayesian Networks We will use capital letters for random variables and lower case letters for values of those
Bayesian Networks Factor Graphs the Case-Factor Algorithm and the Junction Tree Algorithm 1 Bayesian Networks We will use capital letters for random variables and lower case letters for values of those
Conjunctive Normal Form and SAT
 Notes on Satisfiability-Based Problem Solving Conjunctive Normal Form and SAT David Mitchell mitchell@cs.sfu.ca October 4, 2015 These notes are a preliminary draft. Please use freely, but do not re-distribute
Notes on Satisfiability-Based Problem Solving Conjunctive Normal Form and SAT David Mitchell mitchell@cs.sfu.ca October 4, 2015 These notes are a preliminary draft. Please use freely, but do not re-distribute
20.1 2SAT. CS125 Lecture 20 Fall 2016
 CS125 Lecture 20 Fall 2016 20.1 2SAT We show yet another possible way to solve the 2SAT problem. Recall that the input to 2SAT is a logical expression that is the conunction (AND) of a set of clauses,
CS125 Lecture 20 Fall 2016 20.1 2SAT We show yet another possible way to solve the 2SAT problem. Recall that the input to 2SAT is a logical expression that is the conunction (AND) of a set of clauses,
Graph coloring, perfect graphs
 Lecture 5 (05.04.2013) Graph coloring, perfect graphs Scribe: Tomasz Kociumaka Lecturer: Marcin Pilipczuk 1 Introduction to graph coloring Definition 1. Let G be a simple undirected graph and k a positive
Lecture 5 (05.04.2013) Graph coloring, perfect graphs Scribe: Tomasz Kociumaka Lecturer: Marcin Pilipczuk 1 Introduction to graph coloring Definition 1. Let G be a simple undirected graph and k a positive
1 Basic Definitions. 2 Proof By Contradiction. 3 Exchange Argument
 1 Basic Definitions A Problem is a relation from input to acceptable output. For example, INPUT: A list of integers x 1,..., x n OUTPUT: One of the three smallest numbers in the list An algorithm A solves
1 Basic Definitions A Problem is a relation from input to acceptable output. For example, INPUT: A list of integers x 1,..., x n OUTPUT: One of the three smallest numbers in the list An algorithm A solves
REU 2007 Transfinite Combinatorics Lecture 9
 REU 2007 Transfinite Combinatorics Lecture 9 Instructor: László Babai Scribe: Travis Schedler August 10, 2007. Revised by instructor. Last updated August 11, 3:40pm Note: All (0, 1)-measures will be assumed
REU 2007 Transfinite Combinatorics Lecture 9 Instructor: László Babai Scribe: Travis Schedler August 10, 2007. Revised by instructor. Last updated August 11, 3:40pm Note: All (0, 1)-measures will be assumed
Part V. Intractable Problems
 Part V Intractable Problems 507 Chapter 16 N P-Completeness Up to now, we have focused on developing efficient algorithms for solving problems. The word efficient is somewhat subjective, and the degree
Part V Intractable Problems 507 Chapter 16 N P-Completeness Up to now, we have focused on developing efficient algorithms for solving problems. The word efficient is somewhat subjective, and the degree
CSCE 222 Discrete Structures for Computing. Propositional Logic. Dr. Hyunyoung Lee. !!!!!! Based on slides by Andreas Klappenecker
 CSCE 222 Discrete Structures for Computing Propositional Logic Dr. Hyunyoung Lee Based on slides by Andreas Klappenecker 1 Propositions A proposition is a declarative sentence that is either true or false
CSCE 222 Discrete Structures for Computing Propositional Logic Dr. Hyunyoung Lee Based on slides by Andreas Klappenecker 1 Propositions A proposition is a declarative sentence that is either true or false
Lecture 11: Generalized Lovász Local Lemma. Lovász Local Lemma
 Lecture 11: Generalized Recall We design an experiment with independent random variables X 1,..., X m We define bad events A 1,..., A n where) the bad event A i depends on the variables (X k1,..., X kni
Lecture 11: Generalized Recall We design an experiment with independent random variables X 1,..., X m We define bad events A 1,..., A n where) the bad event A i depends on the variables (X k1,..., X kni
Allocation of multiple processors to lazy boolean function trees justification of the magic number 2/3
 Allocation of multiple processors to lazy boolean function trees justification of the magic number 2/3 Alan Dix Computer Science Department University of York, York, YO1 5DD, U.K. alan@uk.ac.york.minster
Allocation of multiple processors to lazy boolean function trees justification of the magic number 2/3 Alan Dix Computer Science Department University of York, York, YO1 5DD, U.K. alan@uk.ac.york.minster
Semantic Metatheory of SL: Mathematical Induction
 Semantic Metatheory of SL: Mathematical Induction Preliminary matters: why and when do we need Mathematical Induction? We need it when we want prove that a certain claim (n) holds for all n N (0, 1, 2,
Semantic Metatheory of SL: Mathematical Induction Preliminary matters: why and when do we need Mathematical Induction? We need it when we want prove that a certain claim (n) holds for all n N (0, 1, 2,
Countable Menger s theorem with finitary matroid constraints on the ingoing edges
 Countable Menger s theorem with finitary matroid constraints on the ingoing edges Attila Joó Alfréd Rényi Institute of Mathematics, MTA-ELTE Egerváry Research Group. Budapest, Hungary jooattila@renyi.hu
Countable Menger s theorem with finitary matroid constraints on the ingoing edges Attila Joó Alfréd Rényi Institute of Mathematics, MTA-ELTE Egerváry Research Group. Budapest, Hungary jooattila@renyi.hu
REVIEW QUESTIONS. Chapter 1: Foundations: Sets, Logic, and Algorithms
 REVIEW QUESTIONS Chapter 1: Foundations: Sets, Logic, and Algorithms 1. Why can t a Venn diagram be used to prove a statement about sets? 2. Suppose S is a set with n elements. Explain why the power set
REVIEW QUESTIONS Chapter 1: Foundations: Sets, Logic, and Algorithms 1. Why can t a Venn diagram be used to prove a statement about sets? 2. Suppose S is a set with n elements. Explain why the power set
CSC 2429 Approaches to the P vs. NP Question and Related Complexity Questions Lecture 2: Switching Lemma, AC 0 Circuit Lower Bounds
 CSC 2429 Approaches to the P vs. NP Question and Related Complexity Questions Lecture 2: Switching Lemma, AC 0 Circuit Lower Bounds Lecturer: Toniann Pitassi Scribe: Robert Robere Winter 2014 1 Switching
CSC 2429 Approaches to the P vs. NP Question and Related Complexity Questions Lecture 2: Switching Lemma, AC 0 Circuit Lower Bounds Lecturer: Toniann Pitassi Scribe: Robert Robere Winter 2014 1 Switching
Classes of Boolean Functions
 Classes of Boolean Functions Nader H. Bshouty Eyal Kushilevitz Abstract Here we give classes of Boolean functions that considered in COLT. Classes of Functions Here we introduce the basic classes of functions
Classes of Boolean Functions Nader H. Bshouty Eyal Kushilevitz Abstract Here we give classes of Boolean functions that considered in COLT. Classes of Functions Here we introduce the basic classes of functions
On the Structure and the Number of Prime Implicants of 2-CNFs
 On the Structure and the Number of Prime Implicants of 2-CNFs Navid Talebanfard Department of Mathematical and Computing Sciences, Tokyo Institute of Technology, Meguro-ku Ookayama 2-12-1, Japan 152-8552
On the Structure and the Number of Prime Implicants of 2-CNFs Navid Talebanfard Department of Mathematical and Computing Sciences, Tokyo Institute of Technology, Meguro-ku Ookayama 2-12-1, Japan 152-8552
Asymptotic Polynomial-Time Approximation (APTAS) and Randomized Approximation Algorithms
 Approximation Algorithms Asymptotic Polynomial-Time Approximation (APTAS) and Randomized Approximation Algorithms Jens Egeblad November 29th, 2006 Agenda First lesson (Asymptotic Approximation): Bin-Packing
Approximation Algorithms Asymptotic Polynomial-Time Approximation (APTAS) and Randomized Approximation Algorithms Jens Egeblad November 29th, 2006 Agenda First lesson (Asymptotic Approximation): Bin-Packing
U.C. Berkeley CS294: Beyond Worst-Case Analysis Handout 3 Luca Trevisan August 31, 2017
 U.C. Berkeley CS294: Beyond Worst-Case Analysis Handout 3 Luca Trevisan August 3, 207 Scribed by Keyhan Vakil Lecture 3 In which we complete the study of Independent Set and Max Cut in G n,p random graphs.
U.C. Berkeley CS294: Beyond Worst-Case Analysis Handout 3 Luca Trevisan August 3, 207 Scribed by Keyhan Vakil Lecture 3 In which we complete the study of Independent Set and Max Cut in G n,p random graphs.
Logic as a Tool Chapter 1: Understanding Propositional Logic 1.1 Propositions and logical connectives. Truth tables and tautologies
 Logic as a Tool Chapter 1: Understanding Propositional Logic 1.1 Propositions and logical connectives. Truth tables and tautologies Valentin Stockholm University September 2016 Propositions Proposition:
Logic as a Tool Chapter 1: Understanding Propositional Logic 1.1 Propositions and logical connectives. Truth tables and tautologies Valentin Stockholm University September 2016 Propositions Proposition:
The Local Lemma is asymptotically tight for SAT
 The Local Lemma is asymptotically tight for SAT H. Gebauer, T. Szabó, G. Tardos Abstract The Local Lemma is a fundamental tool of probabilistic combinatorics and theoretical computer science, yet there
The Local Lemma is asymptotically tight for SAT H. Gebauer, T. Szabó, G. Tardos Abstract The Local Lemma is a fundamental tool of probabilistic combinatorics and theoretical computer science, yet there
Madhavan Mukund Chennai Mathematical Institute
 AN INTRODUCTION TO LOGIC Madhavan Mukund Chennai Mathematical Institute E-mail: madhavan@cmiacin Abstract ese are lecture notes for an introductory course on logic aimed at graduate students in Computer
AN INTRODUCTION TO LOGIC Madhavan Mukund Chennai Mathematical Institute E-mail: madhavan@cmiacin Abstract ese are lecture notes for an introductory course on logic aimed at graduate students in Computer
Greedy Trees, Caterpillars, and Wiener-Type Graph Invariants
 Georgia Southern University Digital Commons@Georgia Southern Mathematical Sciences Faculty Publications Mathematical Sciences, Department of 2012 Greedy Trees, Caterpillars, and Wiener-Type Graph Invariants
Georgia Southern University Digital Commons@Georgia Southern Mathematical Sciences Faculty Publications Mathematical Sciences, Department of 2012 Greedy Trees, Caterpillars, and Wiener-Type Graph Invariants
Lecture 20: PSPACE. November 15, 2016 CS 1010 Theory of Computation
 Lecture 20: PSPACE November 15, 2016 CS 1010 Theory of Computation Recall that PSPACE = k=1 SPACE(nk ). We will see that a relationship between time and space complexity is given by: P NP PSPACE = NPSPACE
Lecture 20: PSPACE November 15, 2016 CS 1010 Theory of Computation Recall that PSPACE = k=1 SPACE(nk ). We will see that a relationship between time and space complexity is given by: P NP PSPACE = NPSPACE
Notes on induction proofs and recursive definitions
 Notes on induction proofs and recursive definitions James Aspnes December 13, 2010 1 Simple induction Most of the proof techniques we ve talked about so far are only really useful for proving a property
Notes on induction proofs and recursive definitions James Aspnes December 13, 2010 1 Simple induction Most of the proof techniques we ve talked about so far are only really useful for proving a property
Mathematical Logic Propositional Logic - Tableaux*
 Mathematical Logic Propositional Logic - Tableaux* Fausto Giunchiglia and Mattia Fumagalli University of Trento *Originally by Luciano Serafini and Chiara Ghidini Modified by Fausto Giunchiglia and Mattia
Mathematical Logic Propositional Logic - Tableaux* Fausto Giunchiglia and Mattia Fumagalli University of Trento *Originally by Luciano Serafini and Chiara Ghidini Modified by Fausto Giunchiglia and Mattia
Good Triangulations. Jean-Daniel Boissonnat DataShape, INRIA
 Good Triangulations Jean-Daniel Boissonnat DataShape, INRIA http://www-sop.inria.fr/geometrica Algorithmic Geometry Good Triangulations J-D. Boissonnat 1 / 29 Definition and existence of nets Definition
Good Triangulations Jean-Daniel Boissonnat DataShape, INRIA http://www-sop.inria.fr/geometrica Algorithmic Geometry Good Triangulations J-D. Boissonnat 1 / 29 Definition and existence of nets Definition
The simplex algorithm
 The simplex algorithm The simplex algorithm is the classical method for solving linear programs. Its running time is not polynomial in the worst case. It does yield insight into linear programs, however,
The simplex algorithm The simplex algorithm is the classical method for solving linear programs. Its running time is not polynomial in the worst case. It does yield insight into linear programs, however,
CS 173: Induction. Madhusudan Parthasarathy University of Illinois at Urbana-Champaign. February 7, 2016
 CS 173: Induction Madhusudan Parthasarathy University of Illinois at Urbana-Champaign 1 Induction February 7, 016 This chapter covers mathematical induction, and is an alternative resource to the one in
CS 173: Induction Madhusudan Parthasarathy University of Illinois at Urbana-Champaign 1 Induction February 7, 016 This chapter covers mathematical induction, and is an alternative resource to the one in
First order logic on Galton-Watson trees
 First order logic on Galton-Watson trees Moumanti Podder Georgia Institute of Technology Joint work with Joel Spencer January 9, 2018 Mathematics Seminar, Indian Institute of Science, Bangalore 1 / 20
First order logic on Galton-Watson trees Moumanti Podder Georgia Institute of Technology Joint work with Joel Spencer January 9, 2018 Mathematics Seminar, Indian Institute of Science, Bangalore 1 / 20
arxiv: v1 [math.co] 22 Jan 2013
![arxiv: v1 [math.co] 22 Jan 2013 arxiv: v1 [math.co] 22 Jan 2013](/thumbs/85/92098505.jpg) NESTED RECURSIONS, SIMULTANEOUS PARAMETERS AND TREE SUPERPOSITIONS ABRAHAM ISGUR, VITALY KUZNETSOV, MUSTAZEE RAHMAN, AND STEPHEN TANNY arxiv:1301.5055v1 [math.co] 22 Jan 2013 Abstract. We apply a tree-based
NESTED RECURSIONS, SIMULTANEOUS PARAMETERS AND TREE SUPERPOSITIONS ABRAHAM ISGUR, VITALY KUZNETSOV, MUSTAZEE RAHMAN, AND STEPHEN TANNY arxiv:1301.5055v1 [math.co] 22 Jan 2013 Abstract. We apply a tree-based
Discrete Mathematics. Benny George K. September 22, 2011
 Discrete Mathematics Benny George K Department of Computer Science and Engineering Indian Institute of Technology Guwahati ben@iitg.ernet.in September 22, 2011 Set Theory Elementary Concepts Let A and
Discrete Mathematics Benny George K Department of Computer Science and Engineering Indian Institute of Technology Guwahati ben@iitg.ernet.in September 22, 2011 Set Theory Elementary Concepts Let A and
Solutions to Sample Problems for Midterm
 Solutions to Sample Problems for Midterm Problem 1. The dual of a proposition is defined for which contains only,,. It is For a compound proposition that only uses,, as operators, we obtained the dual
Solutions to Sample Problems for Midterm Problem 1. The dual of a proposition is defined for which contains only,,. It is For a compound proposition that only uses,, as operators, we obtained the dual
Conjunctive Normal Form and SAT
 Notes on Satisfiability-Based Problem Solving Conjunctive Normal Form and SAT David Mitchell mitchell@cs.sfu.ca September 10, 2014 These notes are a preliminary draft. Please use freely, but do not re-distribute
Notes on Satisfiability-Based Problem Solving Conjunctive Normal Form and SAT David Mitchell mitchell@cs.sfu.ca September 10, 2014 These notes are a preliminary draft. Please use freely, but do not re-distribute
Markov Decision Processes
 Markov Decision Processes Lecture notes for the course Games on Graphs B. Srivathsan Chennai Mathematical Institute, India 1 Markov Chains We will define Markov chains in a manner that will be useful to
Markov Decision Processes Lecture notes for the course Games on Graphs B. Srivathsan Chennai Mathematical Institute, India 1 Markov Chains We will define Markov chains in a manner that will be useful to
CS1800: Mathematical Induction. Professor Kevin Gold
 CS1800: Mathematical Induction Professor Kevin Gold Induction: Used to Prove Patterns Just Keep Going For an algorithm, we may want to prove that it just keeps working, no matter how big the input size
CS1800: Mathematical Induction Professor Kevin Gold Induction: Used to Prove Patterns Just Keep Going For an algorithm, we may want to prove that it just keeps working, no matter how big the input size
Petri nets. s 1 s 2. s 3 s 4. directed arcs.
 Petri nets Petri nets Petri nets are a basic model of parallel and distributed systems (named after Carl Adam Petri). The basic idea is to describe state changes in a system with transitions. @ @R s 1
Petri nets Petri nets Petri nets are a basic model of parallel and distributed systems (named after Carl Adam Petri). The basic idea is to describe state changes in a system with transitions. @ @R s 1
1. Prove: A full m- ary tree with i internal vertices contains n = mi + 1 vertices.
 1. Prove: A full m- ary tree with i internal vertices contains n = mi + 1 vertices. Proof: Every vertex, except the root, is the child of an internal vertex. Since there are i internal vertices, each of
1. Prove: A full m- ary tree with i internal vertices contains n = mi + 1 vertices. Proof: Every vertex, except the root, is the child of an internal vertex. Since there are i internal vertices, each of
Reading 11 : Relations and Functions
 CS/Math 240: Introduction to Discrete Mathematics Fall 2015 Reading 11 : Relations and Functions Instructor: Beck Hasti and Gautam Prakriya In reading 3, we described a correspondence between predicates
CS/Math 240: Introduction to Discrete Mathematics Fall 2015 Reading 11 : Relations and Functions Instructor: Beck Hasti and Gautam Prakriya In reading 3, we described a correspondence between predicates
1 Hamiltonian properties
 1 Hamiltonian properties 1.1 Hamiltonian Cycles Last time we saw this generalization of Dirac s result, which we shall prove now. Proposition 1 (Ore 60). For a graph G with nonadjacent vertices u and v
1 Hamiltonian properties 1.1 Hamiltonian Cycles Last time we saw this generalization of Dirac s result, which we shall prove now. Proposition 1 (Ore 60). For a graph G with nonadjacent vertices u and v
Lecture Notes on Software Model Checking
 15-414: Bug Catching: Automated Program Verification Lecture Notes on Software Model Checking Matt Fredrikson André Platzer Carnegie Mellon University Lecture 19 1 Introduction So far we ve focused on
15-414: Bug Catching: Automated Program Verification Lecture Notes on Software Model Checking Matt Fredrikson André Platzer Carnegie Mellon University Lecture 19 1 Introduction So far we ve focused on
Exercises 1 - Solutions
 Exercises 1 - Solutions SAV 2013 1 PL validity For each of the following propositional logic formulae determine whether it is valid or not. If it is valid prove it, otherwise give a counterexample. Note
Exercises 1 - Solutions SAV 2013 1 PL validity For each of the following propositional logic formulae determine whether it is valid or not. If it is valid prove it, otherwise give a counterexample. Note
Trivial, Tractable, Hard. A Not So Sudden Complexity Jump in Neighborhood Restricted CNF Formulas
 Trivial, Tractable, Hard. A Not So Sudden Complexity Jump in Neighborhood Restricted CNF Formulas Dominik Scheder Aarhus University Abstract. For a CNF formula F we define its 1-conflict graph as follows:
Trivial, Tractable, Hard. A Not So Sudden Complexity Jump in Neighborhood Restricted CNF Formulas Dominik Scheder Aarhus University Abstract. For a CNF formula F we define its 1-conflict graph as follows:
Propositional Logic. Methods & Tools for Software Engineering (MTSE) Fall Prof. Arie Gurfinkel
 Propositional Logic Methods & Tools for Software Engineering (MTSE) Fall 2017 Prof. Arie Gurfinkel References Chpater 1 of Logic for Computer Scientists http://www.springerlink.com/content/978-0-8176-4762-9/
Propositional Logic Methods & Tools for Software Engineering (MTSE) Fall 2017 Prof. Arie Gurfinkel References Chpater 1 of Logic for Computer Scientists http://www.springerlink.com/content/978-0-8176-4762-9/
6.841/18.405J: Advanced Complexity Wednesday, February 12, Lecture Lecture 3
 6.841/18.405J: Advanced Complexity Wednesday, February 12, 2003 Lecture Lecture 3 Instructor: Madhu Sudan Scribe: Bobby Kleinberg 1 The language MinDNF At the end of the last lecture, we introduced the
6.841/18.405J: Advanced Complexity Wednesday, February 12, 2003 Lecture Lecture 3 Instructor: Madhu Sudan Scribe: Bobby Kleinberg 1 The language MinDNF At the end of the last lecture, we introduced the
Problem. Problem Given a dictionary and a word. Which page (if any) contains the given word? 3 / 26
 Binary Search Introduction Problem Problem Given a dictionary and a word. Which page (if any) contains the given word? 3 / 26 Strategy 1: Random Search Randomly select a page until the page containing
Binary Search Introduction Problem Problem Given a dictionary and a word. Which page (if any) contains the given word? 3 / 26 Strategy 1: Random Search Randomly select a page until the page containing
CMPSCI 611 Advanced Algorithms Midterm Exam Fall 2015
 NAME: CMPSCI 611 Advanced Algorithms Midterm Exam Fall 015 A. McGregor 1 October 015 DIRECTIONS: Do not turn over the page until you are told to do so. This is a closed book exam. No communicating with
NAME: CMPSCI 611 Advanced Algorithms Midterm Exam Fall 015 A. McGregor 1 October 015 DIRECTIONS: Do not turn over the page until you are told to do so. This is a closed book exam. No communicating with
Answers to the CSCE 551 Final Exam, April 30, 2008
 Answers to the CSCE 55 Final Exam, April 3, 28. (5 points) Use the Pumping Lemma to show that the language L = {x {, } the number of s and s in x differ (in either direction) by at most 28} is not regular.
Answers to the CSCE 55 Final Exam, April 3, 28. (5 points) Use the Pumping Lemma to show that the language L = {x {, } the number of s and s in x differ (in either direction) by at most 28} is not regular.
NP-Hardness reductions
 NP-Hardness reductions Definition: P is the class of problems that can be solved in polynomial time, that is n c for a constant c Roughly, if a problem is in P then it's easy, and if it's not in P then
NP-Hardness reductions Definition: P is the class of problems that can be solved in polynomial time, that is n c for a constant c Roughly, if a problem is in P then it's easy, and if it's not in P then
2.2: Logical Equivalence: The Laws of Logic
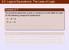 Example (2.7) For primitive statement p and q, construct a truth table for each of the following compound statements. a) p q b) p q Here we see that the corresponding truth tables for two statement p q
Example (2.7) For primitive statement p and q, construct a truth table for each of the following compound statements. a) p q b) p q Here we see that the corresponding truth tables for two statement p q
Gap Embedding for Well-Quasi-Orderings 1
 WoLLIC 2003 Preliminary Version Gap Embedding for Well-Quasi-Orderings 1 Nachum Dershowitz 2 and Iddo Tzameret 3 School of Computer Science, Tel-Aviv University, Tel-Aviv 69978, Israel Abstract Given a
WoLLIC 2003 Preliminary Version Gap Embedding for Well-Quasi-Orderings 1 Nachum Dershowitz 2 and Iddo Tzameret 3 School of Computer Science, Tel-Aviv University, Tel-Aviv 69978, Israel Abstract Given a
Finding Satisfying Assignments by Random Walk
 Ferienakademie, Sarntal 2010 Finding Satisfying Assignments by Random Walk Rolf Wanka, Erlangen Overview Preliminaries A Randomized Polynomial-time Algorithm for 2-SAT A Randomized O(2 n )-time Algorithm
Ferienakademie, Sarntal 2010 Finding Satisfying Assignments by Random Walk Rolf Wanka, Erlangen Overview Preliminaries A Randomized Polynomial-time Algorithm for 2-SAT A Randomized O(2 n )-time Algorithm
Lecture 3: Lower Bounds for Bandit Algorithms
 CMSC 858G: Bandits, Experts and Games 09/19/16 Lecture 3: Lower Bounds for Bandit Algorithms Instructor: Alex Slivkins Scribed by: Soham De & Karthik A Sankararaman 1 Lower Bounds In this lecture (and
CMSC 858G: Bandits, Experts and Games 09/19/16 Lecture 3: Lower Bounds for Bandit Algorithms Instructor: Alex Slivkins Scribed by: Soham De & Karthik A Sankararaman 1 Lower Bounds In this lecture (and
Announcements. Friday Four Square! Problem Set 8 due right now. Problem Set 9 out, due next Friday at 2:15PM. Did you lose a phone in my office?
 N P NP Completeness Announcements Friday Four Square! Today at 4:15PM, outside Gates. Problem Set 8 due right now. Problem Set 9 out, due next Friday at 2:15PM. Explore P, NP, and their connection. Did
N P NP Completeness Announcements Friday Four Square! Today at 4:15PM, outside Gates. Problem Set 8 due right now. Problem Set 9 out, due next Friday at 2:15PM. Explore P, NP, and their connection. Did
CSC 411 Lecture 3: Decision Trees
 CSC 411 Lecture 3: Decision Trees Roger Grosse, Amir-massoud Farahmand, and Juan Carrasquilla University of Toronto UofT CSC 411: 03-Decision Trees 1 / 33 Today Decision Trees Simple but powerful learning
CSC 411 Lecture 3: Decision Trees Roger Grosse, Amir-massoud Farahmand, and Juan Carrasquilla University of Toronto UofT CSC 411: 03-Decision Trees 1 / 33 Today Decision Trees Simple but powerful learning
CSE 555 HW 5 SAMPLE SOLUTION. Question 1.
 CSE 555 HW 5 SAMPLE SOLUTION Question 1. Show that if L is PSPACE-complete, then L is NP-hard. Show that the converse is not true. If L is PSPACE-complete, then for all A PSPACE, A P L. We know SAT PSPACE
CSE 555 HW 5 SAMPLE SOLUTION Question 1. Show that if L is PSPACE-complete, then L is NP-hard. Show that the converse is not true. If L is PSPACE-complete, then for all A PSPACE, A P L. We know SAT PSPACE
10 Propositional logic
 10 The study of how the truth value of compound statements depends on those of simple statements. A reminder of truth-tables. and A B A B F T F F F F or A B A B T F T F T T F F F not A A T F F T material
10 The study of how the truth value of compound statements depends on those of simple statements. A reminder of truth-tables. and A B A B F T F F F F or A B A B T F T F T T F F F not A A T F F T material
SMT 2013 Power Round Solutions February 2, 2013
 Introduction This Power Round is an exploration of numerical semigroups, mathematical structures which appear very naturally out of answers to simple questions. For example, suppose McDonald s sells Chicken
Introduction This Power Round is an exploration of numerical semigroups, mathematical structures which appear very naturally out of answers to simple questions. For example, suppose McDonald s sells Chicken
Computational Logic. Davide Martinenghi. Spring Free University of Bozen-Bolzano. Computational Logic Davide Martinenghi (1/30)
 Computational Logic Davide Martinenghi Free University of Bozen-Bolzano Spring 2010 Computational Logic Davide Martinenghi (1/30) Propositional Logic - sequent calculus To overcome the problems of natural
Computational Logic Davide Martinenghi Free University of Bozen-Bolzano Spring 2010 Computational Logic Davide Martinenghi (1/30) Propositional Logic - sequent calculus To overcome the problems of natural
Language of Propositional Logic
 Logic A logic has: 1. An alphabet that contains all the symbols of the language of the logic. 2. A syntax giving the rules that define the well formed expressions of the language of the logic (often called
Logic A logic has: 1. An alphabet that contains all the symbols of the language of the logic. 2. A syntax giving the rules that define the well formed expressions of the language of the logic (often called
NATIONAL UNIVERSITY OF SINGAPORE CS3230 DESIGN AND ANALYSIS OF ALGORITHMS SEMESTER II: Time Allowed 2 Hours
 NATIONAL UNIVERSITY OF SINGAPORE CS3230 DESIGN AND ANALYSIS OF ALGORITHMS SEMESTER II: 2017 2018 Time Allowed 2 Hours INSTRUCTIONS TO STUDENTS 1. This assessment consists of Eight (8) questions and comprises
NATIONAL UNIVERSITY OF SINGAPORE CS3230 DESIGN AND ANALYSIS OF ALGORITHMS SEMESTER II: 2017 2018 Time Allowed 2 Hours INSTRUCTIONS TO STUDENTS 1. This assessment consists of Eight (8) questions and comprises
Propositional Calculus - Semantics (3/3) Moonzoo Kim CS Dept. KAIST
 Propositional Calculus - Semantics (3/3) Moonzoo Kim CS Dept. KAIST moonzoo@cs.kaist.ac.kr 1 Overview 2.1 Boolean operators 2.2 Propositional formulas 2.3 Interpretations 2.4 Logical Equivalence and substitution
Propositional Calculus - Semantics (3/3) Moonzoo Kim CS Dept. KAIST moonzoo@cs.kaist.ac.kr 1 Overview 2.1 Boolean operators 2.2 Propositional formulas 2.3 Interpretations 2.4 Logical Equivalence and substitution
Computation and Logic Definitions
 Computation and Logic Definitions True and False Also called Boolean truth values, True and False represent the two values or states an atom can assume. We can use any two distinct objects to represent
Computation and Logic Definitions True and False Also called Boolean truth values, True and False represent the two values or states an atom can assume. We can use any two distinct objects to represent
Math 105A HW 1 Solutions
 Sect. 1.1.3: # 2, 3 (Page 7-8 Math 105A HW 1 Solutions 2(a ( Statement: Each positive integers has a unique prime factorization. n N: n = 1 or ( R N, p 1,..., p R P such that n = p 1 p R and ( n, R, S
Sect. 1.1.3: # 2, 3 (Page 7-8 Math 105A HW 1 Solutions 2(a ( Statement: Each positive integers has a unique prime factorization. n N: n = 1 or ( R N, p 1,..., p R P such that n = p 1 p R and ( n, R, S
The semantics of propositional logic
 The semantics of propositional logic Readings: Sections 1.3 and 1.4 of Huth and Ryan. In this module, we will nail down the formal definition of a logical formula, and describe the semantics of propositional
The semantics of propositional logic Readings: Sections 1.3 and 1.4 of Huth and Ryan. In this module, we will nail down the formal definition of a logical formula, and describe the semantics of propositional
The Generalised Randić Index of Trees
 The Generalised Randić Index of Trees Paul Balister Béla Bollobás Stefanie Gerke December 10, 2006 Abstract The Generalised Randić index R α (T ) of a tree T is the sum over the edges uv of T of (d(u)d(v))
The Generalised Randić Index of Trees Paul Balister Béla Bollobás Stefanie Gerke December 10, 2006 Abstract The Generalised Randić index R α (T ) of a tree T is the sum over the edges uv of T of (d(u)d(v))
1 More finite deterministic automata
 CS 125 Section #6 Finite automata October 18, 2016 1 More finite deterministic automata Exercise. Consider the following game with two players: Repeatedly flip a coin. On heads, player 1 gets a point.
CS 125 Section #6 Finite automata October 18, 2016 1 More finite deterministic automata Exercise. Consider the following game with two players: Repeatedly flip a coin. On heads, player 1 gets a point.
On the size of minimal unsatisfiable formulas
 On the size of minimal unsatisfiable formulas Choongbum Lee Submitted: 2008; Accepted: 2008; Published: XX Mathematics Subject Classification: 05D99(Primary); 05C15, 68R10(Secondary) Abstract An unsatisfiable
On the size of minimal unsatisfiable formulas Choongbum Lee Submitted: 2008; Accepted: 2008; Published: XX Mathematics Subject Classification: 05D99(Primary); 05C15, 68R10(Secondary) Abstract An unsatisfiable
CMPUT 675: Approximation Algorithms Fall 2014
 CMPUT 675: Approximation Algorithms Fall 204 Lecture 25 (Nov 3 & 5): Group Steiner Tree Lecturer: Zachary Friggstad Scribe: Zachary Friggstad 25. Group Steiner Tree In this problem, we are given a graph
CMPUT 675: Approximation Algorithms Fall 204 Lecture 25 (Nov 3 & 5): Group Steiner Tree Lecturer: Zachary Friggstad Scribe: Zachary Friggstad 25. Group Steiner Tree In this problem, we are given a graph
Formalizing Probability. Choosing the Sample Space. Probability Measures
 Formalizing Probability Choosing the Sample Space What do we assign probability to? Intuitively, we assign them to possible events (things that might happen, outcomes of an experiment) Formally, we take
Formalizing Probability Choosing the Sample Space What do we assign probability to? Intuitively, we assign them to possible events (things that might happen, outcomes of an experiment) Formally, we take
Finitely generated free Heyting algebras; the well-founded initial segment
 Finitely generated free Heyting algebras; the well-founded initial segment R. Elageili and J.K. Truss Department of Pure Mathematics, University of Leeds, Leeds LS2 9JT, UK e-mail yazid98rajab@yahoo.com,
Finitely generated free Heyting algebras; the well-founded initial segment R. Elageili and J.K. Truss Department of Pure Mathematics, University of Leeds, Leeds LS2 9JT, UK e-mail yazid98rajab@yahoo.com,
Essential facts about NP-completeness:
 CMPSCI611: NP Completeness Lecture 17 Essential facts about NP-completeness: Any NP-complete problem can be solved by a simple, but exponentially slow algorithm. We don t have polynomial-time solutions
CMPSCI611: NP Completeness Lecture 17 Essential facts about NP-completeness: Any NP-complete problem can be solved by a simple, but exponentially slow algorithm. We don t have polynomial-time solutions
Chapter 4: Classical Propositional Semantics
 Chapter 4: Classical Propositional Semantics Language : L {,,, }. Classical Semantics assumptions: TWO VALUES: there are only two logical values: truth (T) and false (F), and EXTENSIONALITY: the logical
Chapter 4: Classical Propositional Semantics Language : L {,,, }. Classical Semantics assumptions: TWO VALUES: there are only two logical values: truth (T) and false (F), and EXTENSIONALITY: the logical
SOME TRANSFINITE INDUCTION DEDUCTIONS
 SOME TRANSFINITE INDUCTION DEDUCTIONS SYLVIA DURIAN Abstract. This paper develops the ordinal numbers and transfinite induction, then demonstrates some interesting applications of transfinite induction.
SOME TRANSFINITE INDUCTION DEDUCTIONS SYLVIA DURIAN Abstract. This paper develops the ordinal numbers and transfinite induction, then demonstrates some interesting applications of transfinite induction.
Computing the Independence Polynomial: from the Tree Threshold Down to the Roots
 1 / 16 Computing the Independence Polynomial: from the Tree Threshold Down to the Roots Nick Harvey 1 Piyush Srivastava 2 Jan Vondrák 3 1 UBC 2 Tata Institute 3 Stanford SODA 2018 The Lovász Local Lemma
1 / 16 Computing the Independence Polynomial: from the Tree Threshold Down to the Roots Nick Harvey 1 Piyush Srivastava 2 Jan Vondrák 3 1 UBC 2 Tata Institute 3 Stanford SODA 2018 The Lovász Local Lemma
Math Introduction to Logic Final Exam
 Math 2283 - Introduction to Logic Final Exam Assigned: 2018.11.26 Due: 2018.12.10 at 08:00 Instructions: Work on this by yourself, the only person you may contact in any way to discuss or ask questions
Math 2283 - Introduction to Logic Final Exam Assigned: 2018.11.26 Due: 2018.12.10 at 08:00 Instructions: Work on this by yourself, the only person you may contact in any way to discuss or ask questions
Conjunctive Normal Form and SAT
 Notes on Satisfiability-Based Problem Solving Conjunctive Normal Form and SAT David Mitchell mitchell@cs.sfu.ca September 19, 2013 This is a preliminary draft of these notes. Please do not distribute without
Notes on Satisfiability-Based Problem Solving Conjunctive Normal Form and SAT David Mitchell mitchell@cs.sfu.ca September 19, 2013 This is a preliminary draft of these notes. Please do not distribute without
PHIL 422 Advanced Logic Inductive Proof
 PHIL 422 Advanced Logic Inductive Proof 1. Preamble: One of the most powerful tools in your meta-logical toolkit will be proof by induction. Just about every significant meta-logical result relies upon
PHIL 422 Advanced Logic Inductive Proof 1. Preamble: One of the most powerful tools in your meta-logical toolkit will be proof by induction. Just about every significant meta-logical result relies upon
Proof Techniques (Review of Math 271)
 Chapter 2 Proof Techniques (Review of Math 271) 2.1 Overview This chapter reviews proof techniques that were probably introduced in Math 271 and that may also have been used in a different way in Phil
Chapter 2 Proof Techniques (Review of Math 271) 2.1 Overview This chapter reviews proof techniques that were probably introduced in Math 271 and that may also have been used in a different way in Phil
