EE 550: Notes on Markov chains, Travel Times, and Opportunistic Routing
|
|
|
- Maurice Chapman
- 5 years ago
- Views:
Transcription
1 EE 550: Notes on Markov chains, Travel Times, and Opportunistic Routing Michael J. Neely University of Southern California mjneely 1 Abstract This collection of notes provides a brief review of Markov chain theory. It focuses attention on expected travel times and applications to opportunistic routing in wireless networks. The exercises are provided for your own interest. I. INTRODUCTION TO EXPECTED TRAVEL TIMES (coffee)' '''''1' 8' 20' (home)' '''''0' 15' 5' (store)' '''''2' (school)' '''''3' 11' Fig. 1. A simple travel time example with four locations. Travel time between the locations is shown. We start at home and want to get to school. There are three different paths we can take, depending on where we go first: Path one: First go to the coffee shop, then go to school. Path two: First go to the store, then go to school. Path three: Go directly to school. Every day we randomly take a path. We want to know the expected time to get to school. To more precisely formulate this problem, represent the four different locations by integers {0, 1, 2, 3}: Location 0: home Location 1: coffee shop Location 2: store Location 3: school The travel times between each location are shown in the graph of Fig. 1. For simplicity, the travel times are assumed to be constant (not random). For example, from Fig. 1, we see that it takes 8 minutes to go from home to the coffee shop. Assume this 8 minutes includes the time spent ordering coffee. From the coffee shop it takes another 20 minutes to get to school. Thus, the total travel time over path one is 28 minutes. Likewise, total travel time for path two is 20 minutes, and the total travel time for path three is 11 minutes. Suppose we decide between paths 1, 2, 3 with probabilities p 1, p 2, p 3, where p 1 + p 2 + p 3 = 1 and p i 0 for i {1, 2, 3}. Let T be the random time required to get to school. By the law of total expectation we have: E [T ] = E [T go to 1 next] p 1 + E [T go to 2 next] p 2 + E [T go to 3 next] }{{}}{{}}{{} For example, if p 1 = p 2 = p 3 = 1/3 then E [T ] = 59/ minutes. p 3
2 2 5' (coffee)' '''''1' 8' 20' (home)' '''''0' 15' 5' (store)' '''''2' (school)' '''''3' 11' Fig. 2. An extended example that adds the possibility of a 5 minute self-transition from home to home. A. An extended problem That was easy. Let s extend the problem by considering the possibility of deciding to linger at home for 5 minutes with probability p 0. So, now assume we have probabilities p 0, p 1, p 2, p 3 that are nonnegative and sum to 1. This can be represented by the picture in Fig. 2, where a self-transition from home to home is drawn. Further, assume that every time we self-transition back to home, our memory is somehow erased and we again independently choose between the four options with probabilities p 0, p 1, p 2, p 3. In particular, we might choose to self-transition to home 32 times before going to the coffee shop, then to school (which would take 32(5) minutes). Again let T be the random time required to get to school. By the same idea as before, we have: E [T ] = E [T go to 0 next] p 0 + E [T go to 1 next] p 1 + E [T go to 2 next] p 2 + E [T go to 3 next] }{{}}{{}}{{} The only remaining question is: What is the value of E [T go to 0 next]? Given that we do a 5-minute self-transition, we know that: E [T go to 0 next] = 5 + E [remaining time starting from 0] Due to our lack of memory, the remaining time starting from 0 is distributed the same as the random time T itself! Thus: Substituting this gives: E [remaining time starting from 0] = E [T ] E [T ] = (5 + E [T ])p 0 + (8 + 20)p 1 + (15 + 5)p p 3 The interesting thing is this: We have written an equation for E [T ] in terms of itself. Of course, once we have this equation, there is no remaining challenge. Using basic algebra to solve for E [T ] gives: E [T ] = 5p p p p 3 1 p 0 For example, if p 0 = p 1 = p 2 = p 3 = 1/4, then E [T ] = 64/ minutes. General problems of this type can be solved via the theory of discrete time Markov chains, as described in the remainder of these notes. p 3 A. Describing a DTMC II. DISCRETE TIME MARKOV CHAINS Let Z(t) be a discrete time Markov chain (DTMC) defined over time slots t {0, 1, 2,...}. Recall that a DTMC Z(t) is characterized by: 1 A state space Z, specifying the set of all possible states. Thus, Z(t) Z for all t {0, 1, 2,...}. Here we assume that Z is a finite or countably infinite set. A transition probability matrix P = (P ij ), where P ij = P r[z(t + 1) = j Z(t) = i] for all i Z and j Z. The transition probabilities have the property that, for all i Z: P ij = 1 j Z 1 This implicitly assumes the DTMC Z(t) is time homogeneous, so that its transition probabilities P ij do not change with time. This is assumed throughout the course unless otherwise stated.
3 3 The Markov property of Z(t) guarantees that the future state is conditionally independent of the past, given the current state: P r[z(t + 1) = j Z(t) = i, Z(t 1) = z(t 1),..., Z(0) = z(0)] = P ij where the above holds for all integers t 0, all i Z, j Z, and all sequences (z(0), z(1),..., z(t 1)) Z t. In order to simulate the DTMC, we must specify either an initial condition Z(0), or a probability distribution on Z(0). B. Evolution of the probabilities Suppose that at time slot t 0 we know the probabilities P r[z(t) = i] for all i Z. This can be used to compute the probabilities for slot t + 1. Indeed, by the law of total probability, we have for all j Z: P r[z(t + 1) = j] = i Z P r[z(t + 1) = j Z(t) = i]p r[z(t) = i] = i Z P ij P r[z(t) = i] (1) where the final equality holds by the Markov chain definition. The equation (1) provides one equation for each j Z. This evolution can be described with vector notation. Let π(t) = (π i (t)) i Z be a row vector that specifies the probability distribution for Z(t), so that for all i Z we have: π i (t) = P r[z(t) = i] The initial probability distribution is given as some probability vector π(0) (with nonnegative entries that sum to 1). If we want Z(0) to be a certain initial state z 0 (with probability 1), we use a probability vector π(0) of the form: π(0) = (0, 0,..., 0, 1, 0,... 0) which is a vector with a single 1 in entry z 0, and with 0s in all other entries. With this vector notation, the equation (1) is written more concisely by multiplying the row vector π(t) by the matrix P. That is, for all slots t 0: π(t + 1) = π(t)p (2) Iterating this equation gives: π(0) is given. π(1) = π(0)p. π(2) = π(1)p = π(0)p 2. π(3) = π(2)p = π(0)p 3. and on. Thus, for all slots t {0, 1, 2,...} we have: π(t) = π(0)p t (3) Exercise 1. Suppose π(0) = π, for some probability vector π that solves the equation π = πp. This equation is called the stationary equation (also called the global balance equation). Prove that π(t) = π for all t {0, 1, 2,...}. Why do you think the equation π = πp is called the stationary equation? Exercise 2. Suppose Z is a finite state space with N states, so P is an N N matrix. Recall that multiplying an N N matrix by another N N matrix requires N 3 multiply-add operations, while multiplying the matrix by a row vector requires N 2 multiply-add operations. The initial probability distribution is π(0). We want to compute π(t ) for some time T > 0. a) How many operations are required to compute π(t ) using equation (3)? That is, P T is computed by T 1 separate multiplications of a square matrix by a square matrix. b) How many operations are required to compute π(t ) using equation (2)? Under what conditions is this approach simpler? c) Suppose T = 2 K for some positive integer K. Develop a technique for computing π(t ) that, for large K, is faster than the answers in both (a) and (b). Consider your answer for K = 20 and N = 50. Exercise 3. This exercise is open-ended. a) Define an N-state Markov chain with a specific N N transition probability matrix P (perhaps with N = 5). Use Matlab to plot π(t) for slots t {0, 1,..., T }, for some specific initial condition and for some finite integer T that produces a meaningful plot (so that both transient and long term behavior can be seen). b) Repeat using a different initial condition. c) Compare to a simulation of the system.
4 4 III. EXPECTED TRAVEL TIMES FOR A MARKOV CHAIN This section considers expected travel times in Markov chains, with applications to opportunistic routing in wireless networks. A. Computing expected travel times For simplicity, assume a finite state space Z = {1, 2,..., N} for some positive integer N 2. Fix state N as a destination state. We are interested in the amount of time required to travel to state N. For each i {1,..., N 1}, define T i as the random time required to travel from state i to state N in one particular simulation of the DTMC (assuming initial condition Z(0) = i). Define T i = if the simulation never reaches state N. Define T N = 0. If Z(0) = i and the DTMC eventually reaches state N, its path from i to N has an integer number of hops. Thus, for all i {1, 2,..., N 1}, the value T i is either a positive integer (since it takes at least one slot to travel to the destination) or is equal to. Fix i {1,..., N 1}. Then: 1 + T 1 with probability P i1 1 + T i = T 2 with probability P i2 (4) 1 + T N with probability P in where T j is defined as the random remaining time to travel to the destination state N, given that the first hop took us from state i to state j. The random variable T j is only defined when the path from i to the destination visits state j on its first hop (which happens with probability P ij ). Each random variable T j has the same probability distribution as T j. There is a subtlety here. Why do we introduce additional notation T j, instead of just using T j itself? The reason is that the random variable T j was defined from a particular instance of a simulation that starts in state j and ends in state N. This particular instance might be different than the simulation associated with T j. Indeed, the simulation for T j is a portion of the same simulation that defines T i. This distinction is particularly important if we travel from state i back to state i on the first hop (which happens with probability P ii ). In this case, the correct equation is T i = 1 + T i (with probability P ii ). In particular, the conditional distribution of T i, given that the first hop travels back to state i, is different from the a-priori distribution of T i. Without the T i notation, one might be tempted to write the confusing (and incorrect) equation T i = 1 + T i (with probability P ii ). Given that T j exists, it has the same distribution as the a-priori distribution of T j. Thus, we can write E Tj = E [T j ] for all j {1,..., N}, and so from (4) we have (using E TN = E [T N ] = 0): N 1 E [T i ] = 1 + P ij E [T j ] i {1,..., N 1} (5) j=1 The equation (5) says that the expected time to travel from state i to the destination is equal to 1 (for the first hop) plus the expected residual time after the first hop. Indeed, one can define T i = 1 + R, where R is the residual time, and so E [T i ] = 1 + E [R]. The expected residual time can be computed via the law of total expectation: E [R] = N E [R first hop takes us to state j] P ij = j=1 N 1 j=1 E [T j ] P ij Adding 1 to the above expression for E [R] gives an alternative derivation of equation (5). Note that (5) specifies N 1 linear equations for the N 1 unknowns E [T 1 ], E [T 2 ],..., E [T N 1 ]. The equations (5) can be written in vector form. Let E T = (E [T 1 ],..., E [T N 1 ]) be a column vector. The equations become: E T = 1 + P E T where P is a truncation of P that removes the last row and column (producing an (N 1) (N 1) matrix), and where 1 is an (N 1) 1 column vector of all 1s. Let I be the (N 1) (N 1) identity matrix. If I P is invertible, the unique solution to (6) is: E T = (I P ) 1 1 It can be shown that (I P ) is invertible if and only if the DTMC has a path of nonzero probability from each state to the destination N (see Exercise 5). Exercise 4. Devise a method for computing travel time variances V ar(t i ) for i {1,..., N 1}. Exercise 5. Show (I P )(I + P + P P n ) = I P n+1. Argue that if lim n P n = (0), then (I P ) is invertible and (I P ) 1 = i=0 P i. (see related proof in Appendix) (6)
5 5 Exercise 6. There are five computers, labeled {1, 2, 3, 4, 5}. A single file is randomly transferred between computers according to a transition probability matrix (P ij ). It takes time S ij to shift a file from computer i to computer j over link (i, j). The (P ij ) and (S ij ) matrices are given below: (P ij ) = 0 1/3 1/3 1/3 0 1/2 0 1/4 1/4 0 1/ /5 1/5 1/4 1/4 1/4 0 1/ , (S ij) = For example, starting at computer 1, the file can take a route , and this route has total time and total probability (1/3)(1/5)(1/3)(1/4). a) For each i {1, 2, 3, 4, 5}, define E [T i ] as the expected time to reach computer 5, given the file starts in computer i. Note that E [T 5 ] = 0. Write recursive equations for E [T i ] using E [T i ] = 5 j=1 E [T i next hop to j] P ij. b) Compute E [T 1 ]. Exercise 7. Consider a 5-state DTMC with transition probability matrix P = (P ij ) as given in Exercise 6. We start in state 1. a) What is the probability that we visit state 4 before state 5? Hint: For i {1, 2, 3, 4, 5} define q i as the probability we visit state 4 before state 5, given we start in state i. Note that q 4 = 1 and q 5 = 0. Write linear equations for q 1, q 2, q 3. b) As a function of the matrix P, what is the probability that after 10 steps we are still not in state 5? B. Applications to opportunistic routing Consider a wireless network with N nodes. The network operates in discrete time with slots t {0, 1, 2,...}. Assume we have a single packet at node 1 that must be transmitted over the network to eventually reach the destination node N. Each transmission from a node i can be overheard by multiple other nodes. Let q ij be the probability that a packet transmitted at node i is successfully received at node j. For simplicity, assume the receptions are independent at each node and across time. Thus, if node 1 transmits, the probability that both nodes 2 and 3 successfully receive is q 12 q 13. It is convenient to assume that q ii = 1 for all i {1,..., N}. Thus, if a node i transmits and no other nodes successfully receive the transmission, then node i must try again on the next slot. Assume that all nodes provide ACK/NACK feedback at the end of each transmission (absence of an ACK is considered to be a NACK). At the end of each time slot, the transmitting node observes the successful receivers and makes an opportunistic routing decision about who takes the packet next. It can either choose itself (so that it tries again on the next slot) or can pass responsibility to one other node that successfully received on that slot. Once responsibility is shifted, the new node becomes the transmitter, makes a transmission, and then makes similar decisions. Thus, there is one and only one node responsible for the packet at any given time. The packet completes its travel once it reaches the destination node N. Exercise 8. This exercise is open-ended. There are several types of questions that can be asked in this framework, such as: a) Suppose the routing decision is made according to the closest-to-destination metric (as in the GeRaF heuristic of [1]). Compute the expected travel time. b) Give an example network for which the closest-to-destination metric gives infinite average travel time, while another simple algorithm would give finite average travel time. c) Introduce average energy into the picture. d) Try to develop an algorithm with optimal average travel time [2][3][4][5] (see also heuristics in [6][7] and optimal treatment of multi-packet flows in [8]). APPENDIX Lemma 1. Let A be a square matrix. Let {B n } n=1 be a sequence of square matrices (the same size as A) such that lim n AB n = I, where I is the identity matrix. Then A is invertible, B n has a limit, and lim n B n = A 1. Proof. Suppose A is not invertible (we reach a contradiction). Then there is a nonzero row vector v such that va = 0. Thus, for all n {1, 2, 3,...}: vab n = 0B n = 0 Hence, vab n = 0 for all n. Taking a limit as n gives vi = 0, and so v = 0 (a contradiction). Thus, A is invertible. It follows that B n = A 1 (AB n ) for all n. Taking a limit gives lim n B n = A 1.
6 6 REFERENCES [1] M. Zorzi and R. Rao. Geographic random forwarding (GeRaF) for ad hoc and sensor networks: Multihop performance. IEEE Trans. on Mobile Computing, vol. 2, no. 4, Oct.-Dec [2] C. Lott and D. Teneketzis. Stochastic routing in ad-hoc networks. IEEE Trans. on Automatic Control, vol. 51, no. 1, pp , Jan [3] T. Javidi and D. Teneketzis. Sensitivity analysis for optimal routing in wireless ad hoc networks in presence of error in channel quality estimation. IEEE Trans. on Automatic Control, vol. 49, no. 8, Aug [4] F. Baccelli, B. Blaszczyszyn, and P. Muhlethaler. An aloha protocol for multihop mobile wireless networks. IEEE Transactions on Information Theory, [5] R. Laufer, H. Dubois-Ferrière, and L. Kleinrock. Multirate anypath routing in wireless mesh networks. Proc. IEEE INFOCOM, [6] S. Biswas and R. Morris. ExOR: Opportunistic multi-hop routing for wireless networks. Proc. of Sigcomm, [7] P. Larsson and N. Johansson. Multiuser diversity forwarding in multihop packet radio networks. IEEE Proc. WCNC, [8] M. J. Neely and R. Urgaonkar. Optimal backpressure routing in wireless networks with multi-receiver diversity. Ad Hoc Networks (Elsevier), vol. 7, no. 5, pp , July 2009.
Cooperative HARQ with Poisson Interference and Opportunistic Routing
 Cooperative HARQ with Poisson Interference and Opportunistic Routing Amogh Rajanna & Mostafa Kaveh Department of Electrical and Computer Engineering University of Minnesota, Minneapolis, MN USA. Outline
Cooperative HARQ with Poisson Interference and Opportunistic Routing Amogh Rajanna & Mostafa Kaveh Department of Electrical and Computer Engineering University of Minnesota, Minneapolis, MN USA. Outline
Information in Aloha Networks
 Achieving Proportional Fairness using Local Information in Aloha Networks Koushik Kar, Saswati Sarkar, Leandros Tassiulas Abstract We address the problem of attaining proportionally fair rates using Aloha
Achieving Proportional Fairness using Local Information in Aloha Networks Koushik Kar, Saswati Sarkar, Leandros Tassiulas Abstract We address the problem of attaining proportionally fair rates using Aloha
IEOR 6711: Professor Whitt. Introduction to Markov Chains
 IEOR 6711: Professor Whitt Introduction to Markov Chains 1. Markov Mouse: The Closed Maze We start by considering how to model a mouse moving around in a maze. The maze is a closed space containing nine
IEOR 6711: Professor Whitt Introduction to Markov Chains 1. Markov Mouse: The Closed Maze We start by considering how to model a mouse moving around in a maze. The maze is a closed space containing nine
Channel Allocation Using Pricing in Satellite Networks
 Channel Allocation Using Pricing in Satellite Networks Jun Sun and Eytan Modiano Laboratory for Information and Decision Systems Massachusetts Institute of Technology {junsun, modiano}@mitedu Abstract
Channel Allocation Using Pricing in Satellite Networks Jun Sun and Eytan Modiano Laboratory for Information and Decision Systems Massachusetts Institute of Technology {junsun, modiano}@mitedu Abstract
P e = 0.1. P e = 0.01
 23 10 0 10-2 P e = 0.1 Deadline Failure Probability 10-4 10-6 10-8 P e = 0.01 10-10 P e = 0.001 10-12 10 11 12 13 14 15 16 Number of Slots in a Frame Fig. 10. The deadline failure probability as a function
23 10 0 10-2 P e = 0.1 Deadline Failure Probability 10-4 10-6 10-8 P e = 0.01 10-10 P e = 0.001 10-12 10 11 12 13 14 15 16 Number of Slots in a Frame Fig. 10. The deadline failure probability as a function
Markov Chain Model for ALOHA protocol
 Markov Chain Model for ALOHA protocol Laila Daniel and Krishnan Narayanan April 22, 2012 Outline of the talk A Markov chain (MC) model for Slotted ALOHA Basic properties of Discrete-time Markov Chain Stability
Markov Chain Model for ALOHA protocol Laila Daniel and Krishnan Narayanan April 22, 2012 Outline of the talk A Markov chain (MC) model for Slotted ALOHA Basic properties of Discrete-time Markov Chain Stability
Markov Chains Handout for Stat 110
 Markov Chains Handout for Stat 0 Prof. Joe Blitzstein (Harvard Statistics Department) Introduction Markov chains were first introduced in 906 by Andrey Markov, with the goal of showing that the Law of
Markov Chains Handout for Stat 0 Prof. Joe Blitzstein (Harvard Statistics Department) Introduction Markov chains were first introduced in 906 by Andrey Markov, with the goal of showing that the Law of
Stochastic processes. MAS275 Probability Modelling. Introduction and Markov chains. Continuous time. Markov property
 Chapter 1: and Markov chains Stochastic processes We study stochastic processes, which are families of random variables describing the evolution of a quantity with time. In some situations, we can treat
Chapter 1: and Markov chains Stochastic processes We study stochastic processes, which are families of random variables describing the evolution of a quantity with time. In some situations, we can treat
MATH 56A: STOCHASTIC PROCESSES CHAPTER 1
 MATH 56A: STOCHASTIC PROCESSES CHAPTER. Finite Markov chains For the sake of completeness of these notes I decided to write a summary of the basic concepts of finite Markov chains. The topics in this chapter
MATH 56A: STOCHASTIC PROCESSES CHAPTER. Finite Markov chains For the sake of completeness of these notes I decided to write a summary of the basic concepts of finite Markov chains. The topics in this chapter
Decodability Analysis of Finite Memory Random Linear Coding in Line Networks
 Decodability Analysis of Finite Memory Random Linear Coding in Line Networks Nima Torabkhani, Faramarz Fekri School of Electrical and Computer Engineering Georgia Institute of Technology, Atlanta GA 30332,
Decodability Analysis of Finite Memory Random Linear Coding in Line Networks Nima Torabkhani, Faramarz Fekri School of Electrical and Computer Engineering Georgia Institute of Technology, Atlanta GA 30332,
Analysis of Uncoordinated Opportunistic Two-Hop Wireless Ad Hoc Systems
 Analysis of Uncoordinated Opportunistic Two-Hop Wireless Ad Hoc Systems Radha Krishna Ganti and Martin Haenggi Department of Electrical Engineering University of Notre Dame Notre Dame, IN 46556, USA {rganti,mhaenggi}@nd.edu
Analysis of Uncoordinated Opportunistic Two-Hop Wireless Ad Hoc Systems Radha Krishna Ganti and Martin Haenggi Department of Electrical Engineering University of Notre Dame Notre Dame, IN 46556, USA {rganti,mhaenggi}@nd.edu
Lecture 20 : Markov Chains
 CSCI 3560 Probability and Computing Instructor: Bogdan Chlebus Lecture 0 : Markov Chains We consider stochastic processes. A process represents a system that evolves through incremental changes called
CSCI 3560 Probability and Computing Instructor: Bogdan Chlebus Lecture 0 : Markov Chains We consider stochastic processes. A process represents a system that evolves through incremental changes called
Message Delivery Probability of Two-Hop Relay with Erasure Coding in MANETs
 01 7th International ICST Conference on Communications and Networking in China (CHINACOM) Message Delivery Probability of Two-Hop Relay with Erasure Coding in MANETs Jiajia Liu Tohoku University Sendai,
01 7th International ICST Conference on Communications and Networking in China (CHINACOM) Message Delivery Probability of Two-Hop Relay with Erasure Coding in MANETs Jiajia Liu Tohoku University Sendai,
TRANSMISSION STRATEGIES FOR SINGLE-DESTINATION WIRELESS NETWORKS
 The 20 Military Communications Conference - Track - Waveforms and Signal Processing TRANSMISSION STRATEGIES FOR SINGLE-DESTINATION WIRELESS NETWORKS Gam D. Nguyen, Jeffrey E. Wieselthier 2, Sastry Kompella,
The 20 Military Communications Conference - Track - Waveforms and Signal Processing TRANSMISSION STRATEGIES FOR SINGLE-DESTINATION WIRELESS NETWORKS Gam D. Nguyen, Jeffrey E. Wieselthier 2, Sastry Kompella,
LECTURE 3. Last time:
 LECTURE 3 Last time: Mutual Information. Convexity and concavity Jensen s inequality Information Inequality Data processing theorem Fano s Inequality Lecture outline Stochastic processes, Entropy rate
LECTURE 3 Last time: Mutual Information. Convexity and concavity Jensen s inequality Information Inequality Data processing theorem Fano s Inequality Lecture outline Stochastic processes, Entropy rate
Power Allocation over Two Identical Gilbert-Elliott Channels
 Power Allocation over Two Identical Gilbert-Elliott Channels Junhua Tang School of Electronic Information and Electrical Engineering Shanghai Jiao Tong University, China Email: junhuatang@sjtu.edu.cn Parisa
Power Allocation over Two Identical Gilbert-Elliott Channels Junhua Tang School of Electronic Information and Electrical Engineering Shanghai Jiao Tong University, China Email: junhuatang@sjtu.edu.cn Parisa
A POMDP Framework for Cognitive MAC Based on Primary Feedback Exploitation
 A POMDP Framework for Cognitive MAC Based on Primary Feedback Exploitation Karim G. Seddik and Amr A. El-Sherif 2 Electronics and Communications Engineering Department, American University in Cairo, New
A POMDP Framework for Cognitive MAC Based on Primary Feedback Exploitation Karim G. Seddik and Amr A. El-Sherif 2 Electronics and Communications Engineering Department, American University in Cairo, New
Network Optimization: Notes and Exercises
 SPRING 2016 1 Network Optimization: Notes and Exercises Michael J. Neely University of Southern California http://www-bcf.usc.edu/ mjneely Abstract These notes provide a tutorial treatment of topics of
SPRING 2016 1 Network Optimization: Notes and Exercises Michael J. Neely University of Southern California http://www-bcf.usc.edu/ mjneely Abstract These notes provide a tutorial treatment of topics of
Finite-Horizon Statistics for Markov chains
 Analyzing FSDT Markov chains Friday, September 30, 2011 2:03 PM Simulating FSDT Markov chains, as we have said is very straightforward, either by using probability transition matrix or stochastic update
Analyzing FSDT Markov chains Friday, September 30, 2011 2:03 PM Simulating FSDT Markov chains, as we have said is very straightforward, either by using probability transition matrix or stochastic update
Lecture 10: Powers of Matrices, Difference Equations
 Lecture 10: Powers of Matrices, Difference Equations Difference Equations A difference equation, also sometimes called a recurrence equation is an equation that defines a sequence recursively, i.e. each
Lecture 10: Powers of Matrices, Difference Equations Difference Equations A difference equation, also sometimes called a recurrence equation is an equation that defines a sequence recursively, i.e. each
Classification of Countable State Markov Chains
 Classification of Countable State Markov Chains Friday, March 21, 2014 2:01 PM How can we determine whether a communication class in a countable state Markov chain is: transient null recurrent positive
Classification of Countable State Markov Chains Friday, March 21, 2014 2:01 PM How can we determine whether a communication class in a countable state Markov chain is: transient null recurrent positive
Markov Processes Hamid R. Rabiee
 Markov Processes Hamid R. Rabiee Overview Markov Property Markov Chains Definition Stationary Property Paths in Markov Chains Classification of States Steady States in MCs. 2 Markov Property A discrete
Markov Processes Hamid R. Rabiee Overview Markov Property Markov Chains Definition Stationary Property Paths in Markov Chains Classification of States Steady States in MCs. 2 Markov Property A discrete
12. Perturbed Matrices
 MAT334 : Applied Linear Algebra Mike Newman, winter 208 2. Perturbed Matrices motivation We want to solve a system Ax = b in a context where A and b are not known exactly. There might be experimental errors,
MAT334 : Applied Linear Algebra Mike Newman, winter 208 2. Perturbed Matrices motivation We want to solve a system Ax = b in a context where A and b are not known exactly. There might be experimental errors,
4.7.1 Computing a stationary distribution
 At a high-level our interest in the rest of this section will be to understand the limiting distribution, when it exists and how to compute it To compute it, we will try to reason about when the limiting
At a high-level our interest in the rest of this section will be to understand the limiting distribution, when it exists and how to compute it To compute it, we will try to reason about when the limiting
Channel Selection in Cognitive Radio Networks with Opportunistic RF Energy Harvesting
 1 Channel Selection in Cognitive Radio Networks with Opportunistic RF Energy Harvesting Dusit Niyato 1, Ping Wang 1, and Dong In Kim 2 1 School of Computer Engineering, Nanyang Technological University
1 Channel Selection in Cognitive Radio Networks with Opportunistic RF Energy Harvesting Dusit Niyato 1, Ping Wang 1, and Dong In Kim 2 1 School of Computer Engineering, Nanyang Technological University
Outlines. Discrete Time Markov Chain (DTMC) Continuous Time Markov Chain (CTMC)
 Markov Chains (2) Outlines Discrete Time Markov Chain (DTMC) Continuous Time Markov Chain (CTMC) 2 pj ( n) denotes the pmf of the random variable p ( n) P( X j) j We will only be concerned with homogenous
Markov Chains (2) Outlines Discrete Time Markov Chain (DTMC) Continuous Time Markov Chain (CTMC) 2 pj ( n) denotes the pmf of the random variable p ( n) P( X j) j We will only be concerned with homogenous
LIMITING PROBABILITY TRANSITION MATRIX OF A CONDENSED FIBONACCI TREE
 International Journal of Applied Mathematics Volume 31 No. 18, 41-49 ISSN: 1311-178 (printed version); ISSN: 1314-86 (on-line version) doi: http://dx.doi.org/1.173/ijam.v31i.6 LIMITING PROBABILITY TRANSITION
International Journal of Applied Mathematics Volume 31 No. 18, 41-49 ISSN: 1311-178 (printed version); ISSN: 1314-86 (on-line version) doi: http://dx.doi.org/1.173/ijam.v31i.6 LIMITING PROBABILITY TRANSITION
Lecture notes for Analysis of Algorithms : Markov decision processes
 Lecture notes for Analysis of Algorithms : Markov decision processes Lecturer: Thomas Dueholm Hansen June 6, 013 Abstract We give an introduction to infinite-horizon Markov decision processes (MDPs) with
Lecture notes for Analysis of Algorithms : Markov decision processes Lecturer: Thomas Dueholm Hansen June 6, 013 Abstract We give an introduction to infinite-horizon Markov decision processes (MDPs) with
Distributed Power Control for Time Varying Wireless Networks: Optimality and Convergence
 Distributed Power Control for Time Varying Wireless Networks: Optimality and Convergence Tim Holliday, Nick Bambos, Peter Glynn, Andrea Goldsmith Stanford University Abstract This paper presents a new
Distributed Power Control for Time Varying Wireless Networks: Optimality and Convergence Tim Holliday, Nick Bambos, Peter Glynn, Andrea Goldsmith Stanford University Abstract This paper presents a new
Dynamic Power Allocation and Routing for Time Varying Wireless Networks
 Dynamic Power Allocation and Routing for Time Varying Wireless Networks X 14 (t) X 12 (t) 1 3 4 k a P ak () t P a tot X 21 (t) 2 N X 2N (t) X N4 (t) µ ab () rate µ ab µ ab (p, S 3 ) µ ab µ ac () µ ab (p,
Dynamic Power Allocation and Routing for Time Varying Wireless Networks X 14 (t) X 12 (t) 1 3 4 k a P ak () t P a tot X 21 (t) 2 N X 2N (t) X N4 (t) µ ab () rate µ ab µ ab (p, S 3 ) µ ab µ ac () µ ab (p,
2. Transience and Recurrence
 Virtual Laboratories > 15. Markov Chains > 1 2 3 4 5 6 7 8 9 10 11 12 2. Transience and Recurrence The study of Markov chains, particularly the limiting behavior, depends critically on the random times
Virtual Laboratories > 15. Markov Chains > 1 2 3 4 5 6 7 8 9 10 11 12 2. Transience and Recurrence The study of Markov chains, particularly the limiting behavior, depends critically on the random times
Asymptotics, asynchrony, and asymmetry in distributed consensus
 DANCES Seminar 1 / Asymptotics, asynchrony, and asymmetry in distributed consensus Anand D. Information Theory and Applications Center University of California, San Diego 9 March 011 Joint work with Alex
DANCES Seminar 1 / Asymptotics, asynchrony, and asymmetry in distributed consensus Anand D. Information Theory and Applications Center University of California, San Diego 9 March 011 Joint work with Alex
The Factor: Inferring Protocol Performance Using Inter-link Reception Correlation
 The Factor: Inferring Protocol Performance Using Inter-link Reception Correlation Kannan Srinivasan, Mayank Jain, Jung Il Choi, Tahir Azim, Edward S Kim, Philip Levis and Bhaskar Krishnamachari MobiCom
The Factor: Inferring Protocol Performance Using Inter-link Reception Correlation Kannan Srinivasan, Mayank Jain, Jung Il Choi, Tahir Azim, Edward S Kim, Philip Levis and Bhaskar Krishnamachari MobiCom
Definition A finite Markov chain is a memoryless homogeneous discrete stochastic process with a finite number of states.
 Chapter 8 Finite Markov Chains A discrete system is characterized by a set V of states and transitions between the states. V is referred to as the state space. We think of the transitions as occurring
Chapter 8 Finite Markov Chains A discrete system is characterized by a set V of states and transitions between the states. V is referred to as the state space. We think of the transitions as occurring
STOCHASTIC PROCESSES Basic notions
 J. Virtamo 38.3143 Queueing Theory / Stochastic processes 1 STOCHASTIC PROCESSES Basic notions Often the systems we consider evolve in time and we are interested in their dynamic behaviour, usually involving
J. Virtamo 38.3143 Queueing Theory / Stochastic processes 1 STOCHASTIC PROCESSES Basic notions Often the systems we consider evolve in time and we are interested in their dynamic behaviour, usually involving
Markov Model. Model representing the different resident states of a system, and the transitions between the different states
 Markov Model Model representing the different resident states of a system, and the transitions between the different states (applicable to repairable, as well as non-repairable systems) System behavior
Markov Model Model representing the different resident states of a system, and the transitions between the different states (applicable to repairable, as well as non-repairable systems) System behavior
Eigenvalues and Eigenvectors
 Eigenvalues and Eigenvectors MAT 67L, Laboratory III Contents Instructions (1) Read this document. (2) The questions labeled Experiments are not graded, and should not be turned in. They are designed for
Eigenvalues and Eigenvectors MAT 67L, Laboratory III Contents Instructions (1) Read this document. (2) The questions labeled Experiments are not graded, and should not be turned in. They are designed for
Channel Probing in Communication Systems: Myopic Policies Are Not Always Optimal
 Channel Probing in Communication Systems: Myopic Policies Are Not Always Optimal Matthew Johnston, Eytan Modiano Laboratory for Information and Decision Systems Massachusetts Institute of Technology Cambridge,
Channel Probing in Communication Systems: Myopic Policies Are Not Always Optimal Matthew Johnston, Eytan Modiano Laboratory for Information and Decision Systems Massachusetts Institute of Technology Cambridge,
Markov Chain Monte Carlo The Metropolis-Hastings Algorithm
 Markov Chain Monte Carlo The Metropolis-Hastings Algorithm Anthony Trubiano April 11th, 2018 1 Introduction Markov Chain Monte Carlo (MCMC) methods are a class of algorithms for sampling from a probability
Markov Chain Monte Carlo The Metropolis-Hastings Algorithm Anthony Trubiano April 11th, 2018 1 Introduction Markov Chain Monte Carlo (MCMC) methods are a class of algorithms for sampling from a probability
Definition and Examples of DTMCs
 Definition and Examples of DTMCs Natarajan Gautam Department of Industrial and Systems Engineering Texas A&M University 235A Zachry, College Station, TX 77843-3131 Email: gautam@tamuedu Phone: 979-845-5458
Definition and Examples of DTMCs Natarajan Gautam Department of Industrial and Systems Engineering Texas A&M University 235A Zachry, College Station, TX 77843-3131 Email: gautam@tamuedu Phone: 979-845-5458
Modular numbers and Error Correcting Codes. Introduction. Modular Arithmetic.
 Modular numbers and Error Correcting Codes Introduction Modular Arithmetic Finite fields n-space over a finite field Error correcting codes Exercises Introduction. Data transmission is not normally perfect;
Modular numbers and Error Correcting Codes Introduction Modular Arithmetic Finite fields n-space over a finite field Error correcting codes Exercises Introduction. Data transmission is not normally perfect;
On the exact bit error probability for Viterbi decoding of convolutional codes
 On the exact bit error probability for Viterbi decoding of convolutional codes Irina E. Bocharova, Florian Hug, Rolf Johannesson, and Boris D. Kudryashov Dept. of Information Systems Dept. of Electrical
On the exact bit error probability for Viterbi decoding of convolutional codes Irina E. Bocharova, Florian Hug, Rolf Johannesson, and Boris D. Kudryashov Dept. of Information Systems Dept. of Electrical
Delay-Based Connectivity of Wireless Networks
 Delay-Based Connectivity of Wireless Networks Martin Haenggi Abstract Interference in wireless networks causes intricate dependencies between the formation of links. In current graph models of wireless
Delay-Based Connectivity of Wireless Networks Martin Haenggi Abstract Interference in wireless networks causes intricate dependencies between the formation of links. In current graph models of wireless
Lecture: Local Spectral Methods (1 of 4)
 Stat260/CS294: Spectral Graph Methods Lecture 18-03/31/2015 Lecture: Local Spectral Methods (1 of 4) Lecturer: Michael Mahoney Scribe: Michael Mahoney Warning: these notes are still very rough. They provide
Stat260/CS294: Spectral Graph Methods Lecture 18-03/31/2015 Lecture: Local Spectral Methods (1 of 4) Lecturer: Michael Mahoney Scribe: Michael Mahoney Warning: these notes are still very rough. They provide
Generalized Two-Hop Relay for Flexible Delay Control in MANETs
 Generalized Two-Hop Relay for Flexible Delay Control in MANETs 12 IEEE. Personal use of this material is permitted. Permission from IEEE must be obtained for all other uses, in any current or future media,
Generalized Two-Hop Relay for Flexible Delay Control in MANETs 12 IEEE. Personal use of this material is permitted. Permission from IEEE must be obtained for all other uses, in any current or future media,
IN this paper, we consider the capacity of sticky channels, a
 72 IEEE TRANSACTIONS ON INFORMATION THEORY, VOL. 54, NO. 1, JANUARY 2008 Capacity Bounds for Sticky Channels Michael Mitzenmacher, Member, IEEE Abstract The capacity of sticky channels, a subclass of insertion
72 IEEE TRANSACTIONS ON INFORMATION THEORY, VOL. 54, NO. 1, JANUARY 2008 Capacity Bounds for Sticky Channels Michael Mitzenmacher, Member, IEEE Abstract The capacity of sticky channels, a subclass of insertion
Distributed Optimization over Networks Gossip-Based Algorithms
 Distributed Optimization over Networks Gossip-Based Algorithms Angelia Nedić angelia@illinois.edu ISE Department and Coordinated Science Laboratory University of Illinois at Urbana-Champaign Outline Random
Distributed Optimization over Networks Gossip-Based Algorithms Angelia Nedić angelia@illinois.edu ISE Department and Coordinated Science Laboratory University of Illinois at Urbana-Champaign Outline Random
Energy Optimal Control for Time Varying Wireless Networks. Michael J. Neely University of Southern California
 Energy Optimal Control for Time Varying Wireless Networks Michael J. Neely University of Southern California http://www-rcf.usc.edu/~mjneely Part 1: A single wireless downlink (L links) L 2 1 S={Totally
Energy Optimal Control for Time Varying Wireless Networks Michael J. Neely University of Southern California http://www-rcf.usc.edu/~mjneely Part 1: A single wireless downlink (L links) L 2 1 S={Totally
Optimal Link Adaptation in Wideband CDMA Systems
 Optimal Link Adaptation in Wideband CDMA Systems Tim Holliday, Andrea Goldsmith, and Peter Glynn Stanford University Abstract We develop a general framework for optimizing link adaptation for multiuser
Optimal Link Adaptation in Wideband CDMA Systems Tim Holliday, Andrea Goldsmith, and Peter Glynn Stanford University Abstract We develop a general framework for optimizing link adaptation for multiuser
Markov chains. Randomness and Computation. Markov chains. Markov processes
 Markov chains Randomness and Computation or, Randomized Algorithms Mary Cryan School of Informatics University of Edinburgh Definition (Definition 7) A discrete-time stochastic process on the state space
Markov chains Randomness and Computation or, Randomized Algorithms Mary Cryan School of Informatics University of Edinburgh Definition (Definition 7) A discrete-time stochastic process on the state space
16:330:543 Communication Networks I Midterm Exam November 7, 2005
 l l l l l l l l 1 3 np n = ρ 1 ρ = λ µ λ. n= T = E[N] = 1 λ µ λ = 1 µ 1. 16:33:543 Communication Networks I Midterm Exam November 7, 5 You have 16 minutes to complete this four problem exam. If you know
l l l l l l l l 1 3 np n = ρ 1 ρ = λ µ λ. n= T = E[N] = 1 λ µ λ = 1 µ 1. 16:33:543 Communication Networks I Midterm Exam November 7, 5 You have 16 minutes to complete this four problem exam. If you know
The Basis. [5] The Basis
![The Basis. [5] The Basis The Basis. [5] The Basis](/thumbs/90/103470138.jpg) The Basis [5] The Basis René Descartes Born 1596. After studying law in college,... I entirely abandoned the study of letters. Resolving to seek no knowledge other than that of which could be found in
The Basis [5] The Basis René Descartes Born 1596. After studying law in college,... I entirely abandoned the study of letters. Resolving to seek no knowledge other than that of which could be found in
Session-Based Queueing Systems
 Session-Based Queueing Systems Modelling, Simulation, and Approximation Jeroen Horters Supervisor VU: Sandjai Bhulai Executive Summary Companies often offer services that require multiple steps on the
Session-Based Queueing Systems Modelling, Simulation, and Approximation Jeroen Horters Supervisor VU: Sandjai Bhulai Executive Summary Companies often offer services that require multiple steps on the
Markov Chains. As part of Interdisciplinary Mathematical Modeling, By Warren Weckesser Copyright c 2006.
 Markov Chains As part of Interdisciplinary Mathematical Modeling, By Warren Weckesser Copyright c 2006 1 Introduction A (finite) Markov chain is a process with a finite number of states (or outcomes, or
Markov Chains As part of Interdisciplinary Mathematical Modeling, By Warren Weckesser Copyright c 2006 1 Introduction A (finite) Markov chain is a process with a finite number of states (or outcomes, or
PageRank: The Math-y Version (Or, What To Do When You Can t Tear Up Little Pieces of Paper)
 PageRank: The Math-y Version (Or, What To Do When You Can t Tear Up Little Pieces of Paper) In class, we saw this graph, with each node representing people who are following each other on Twitter: Our
PageRank: The Math-y Version (Or, What To Do When You Can t Tear Up Little Pieces of Paper) In class, we saw this graph, with each node representing people who are following each other on Twitter: Our
Question Points Score Total: 70
 The University of British Columbia Final Examination - April 204 Mathematics 303 Dr. D. Brydges Time: 2.5 hours Last Name First Signature Student Number Special Instructions: Closed book exam, no calculators.
The University of British Columbia Final Examination - April 204 Mathematics 303 Dr. D. Brydges Time: 2.5 hours Last Name First Signature Student Number Special Instructions: Closed book exam, no calculators.
Randomized Algorithms
 Randomized Algorithms Prof. Tapio Elomaa tapio.elomaa@tut.fi Course Basics A new 4 credit unit course Part of Theoretical Computer Science courses at the Department of Mathematics There will be 4 hours
Randomized Algorithms Prof. Tapio Elomaa tapio.elomaa@tut.fi Course Basics A new 4 credit unit course Part of Theoretical Computer Science courses at the Department of Mathematics There will be 4 hours
MARKOV PROCESSES. Valerio Di Valerio
 MARKOV PROCESSES Valerio Di Valerio Stochastic Process Definition: a stochastic process is a collection of random variables {X(t)} indexed by time t T Each X(t) X is a random variable that satisfy some
MARKOV PROCESSES Valerio Di Valerio Stochastic Process Definition: a stochastic process is a collection of random variables {X(t)} indexed by time t T Each X(t) X is a random variable that satisfy some
No class on Thursday, October 1. No office hours on Tuesday, September 29 and Thursday, October 1.
 Stationary Distributions Monday, September 28, 2015 2:02 PM No class on Thursday, October 1. No office hours on Tuesday, September 29 and Thursday, October 1. Homework 1 due Friday, October 2 at 5 PM strongly
Stationary Distributions Monday, September 28, 2015 2:02 PM No class on Thursday, October 1. No office hours on Tuesday, September 29 and Thursday, October 1. Homework 1 due Friday, October 2 at 5 PM strongly
HDR - A Hysteresis-Driven Routing Algorithm for Energy Harvesting Tag Networks
 HDR - A Hysteresis-Driven Routing Algorithm for Energy Harvesting Tag Networks Adrian Segall arxiv:1512.06997v1 [cs.ni] 22 Dec 2015 March 12, 2018 Abstract The work contains a first attempt to treat the
HDR - A Hysteresis-Driven Routing Algorithm for Energy Harvesting Tag Networks Adrian Segall arxiv:1512.06997v1 [cs.ni] 22 Dec 2015 March 12, 2018 Abstract The work contains a first attempt to treat the
Section 29: What s an Inverse?
 Section 29: What s an Inverse? Our investigations in the last section showed that all of the matrix operations had an identity element. The identity element for addition is, for obvious reasons, called
Section 29: What s an Inverse? Our investigations in the last section showed that all of the matrix operations had an identity element. The identity element for addition is, for obvious reasons, called
Markov Chains and Stochastic Sampling
 Part I Markov Chains and Stochastic Sampling 1 Markov Chains and Random Walks on Graphs 1.1 Structure of Finite Markov Chains We shall only consider Markov chains with a finite, but usually very large,
Part I Markov Chains and Stochastic Sampling 1 Markov Chains and Random Walks on Graphs 1.1 Structure of Finite Markov Chains We shall only consider Markov chains with a finite, but usually very large,
Math 304 Handout: Linear algebra, graphs, and networks.
 Math 30 Handout: Linear algebra, graphs, and networks. December, 006. GRAPHS AND ADJACENCY MATRICES. Definition. A graph is a collection of vertices connected by edges. A directed graph is a graph all
Math 30 Handout: Linear algebra, graphs, and networks. December, 006. GRAPHS AND ADJACENCY MATRICES. Definition. A graph is a collection of vertices connected by edges. A directed graph is a graph all
Iterative Methods for Solving A x = b
 Iterative Methods for Solving A x = b A good (free) online source for iterative methods for solving A x = b is given in the description of a set of iterative solvers called templates found at netlib: http
Iterative Methods for Solving A x = b A good (free) online source for iterative methods for solving A x = b is given in the description of a set of iterative solvers called templates found at netlib: http
Discrete time Markov chains. Discrete Time Markov Chains, Limiting. Limiting Distribution and Classification. Regular Transition Probability Matrices
 Discrete time Markov chains Discrete Time Markov Chains, Limiting Distribution and Classification DTU Informatics 02407 Stochastic Processes 3, September 9 207 Today: Discrete time Markov chains - invariant
Discrete time Markov chains Discrete Time Markov Chains, Limiting Distribution and Classification DTU Informatics 02407 Stochastic Processes 3, September 9 207 Today: Discrete time Markov chains - invariant
Solutions to Homework Discrete Stochastic Processes MIT, Spring 2011
 Exercise 6.5: Solutions to Homework 0 6.262 Discrete Stochastic Processes MIT, Spring 20 Consider the Markov process illustrated below. The transitions are labelled by the rate q ij at which those transitions
Exercise 6.5: Solutions to Homework 0 6.262 Discrete Stochastic Processes MIT, Spring 20 Consider the Markov process illustrated below. The transitions are labelled by the rate q ij at which those transitions
1646 IEEE TRANSACTIONS ON COMMUNICATIONS, VOL. 64, NO. 4, APRIL 2016
 646 IEEE TRANSACTIONS ON COMMUNICATIONS, VOL. 64, NO. 4, APRIL 6 On the Throughput Capacity Study for Aloha Mobile Ad Hoc Networks Yin Chen, Member, IEEE, Yulong Shen, Member, IEEE, Jinxiao Zhu, Xiaohong
646 IEEE TRANSACTIONS ON COMMUNICATIONS, VOL. 64, NO. 4, APRIL 6 On the Throughput Capacity Study for Aloha Mobile Ad Hoc Networks Yin Chen, Member, IEEE, Yulong Shen, Member, IEEE, Jinxiao Zhu, Xiaohong
Crossing Over the Bounded Domain: From Exponential To Power-law Intermeeting
 Crossing Over the Bounded Domain: From Exponential To Power-law Intermeeting time in MANET Han Cai, Do Young Eun Department of Electrical and Computer Engineering North Carolina State University Motivation
Crossing Over the Bounded Domain: From Exponential To Power-law Intermeeting time in MANET Han Cai, Do Young Eun Department of Electrical and Computer Engineering North Carolina State University Motivation
Online Social Networks and Media. Link Analysis and Web Search
 Online Social Networks and Media Link Analysis and Web Search How to Organize the Web First try: Human curated Web directories Yahoo, DMOZ, LookSmart How to organize the web Second try: Web Search Information
Online Social Networks and Media Link Analysis and Web Search How to Organize the Web First try: Human curated Web directories Yahoo, DMOZ, LookSmart How to organize the web Second try: Web Search Information
ANALYTICAL MODEL OF A VIRTUAL BACKBONE STABILITY IN MOBILE ENVIRONMENT
 (The 4th New York Metro Area Networking Workshop, New York City, Sept. 2004) ANALYTICAL MODEL OF A VIRTUAL BACKBONE STABILITY IN MOBILE ENVIRONMENT Ibrahim Hökelek 1, Mariusz A. Fecko 2, M. Ümit Uyar 1
(The 4th New York Metro Area Networking Workshop, New York City, Sept. 2004) ANALYTICAL MODEL OF A VIRTUAL BACKBONE STABILITY IN MOBILE ENVIRONMENT Ibrahim Hökelek 1, Mariusz A. Fecko 2, M. Ümit Uyar 1
Continuous-Model Communication Complexity with Application in Distributed Resource Allocation in Wireless Ad hoc Networks
 Continuous-Model Communication Complexity with Application in Distributed Resource Allocation in Wireless Ad hoc Networks Husheng Li 1 and Huaiyu Dai 2 1 Department of Electrical Engineering and Computer
Continuous-Model Communication Complexity with Application in Distributed Resource Allocation in Wireless Ad hoc Networks Husheng Li 1 and Huaiyu Dai 2 1 Department of Electrical Engineering and Computer
Lecture 6 & 7. Shuanglin Shao. September 16th and 18th, 2013
 Lecture 6 & 7 Shuanglin Shao September 16th and 18th, 2013 1 Elementary matrices 2 Equivalence Theorem 3 A method of inverting matrices Def An n n matrice is called an elementary matrix if it can be obtained
Lecture 6 & 7 Shuanglin Shao September 16th and 18th, 2013 1 Elementary matrices 2 Equivalence Theorem 3 A method of inverting matrices Def An n n matrice is called an elementary matrix if it can be obtained
Jim Lambers MAT 610 Summer Session Lecture 2 Notes
 Jim Lambers MAT 610 Summer Session 2009-10 Lecture 2 Notes These notes correspond to Sections 2.2-2.4 in the text. Vector Norms Given vectors x and y of length one, which are simply scalars x and y, the
Jim Lambers MAT 610 Summer Session 2009-10 Lecture 2 Notes These notes correspond to Sections 2.2-2.4 in the text. Vector Norms Given vectors x and y of length one, which are simply scalars x and y, the
DS-GA 1002 Lecture notes 0 Fall Linear Algebra. These notes provide a review of basic concepts in linear algebra.
 DS-GA 1002 Lecture notes 0 Fall 2016 Linear Algebra These notes provide a review of basic concepts in linear algebra. 1 Vector spaces You are no doubt familiar with vectors in R 2 or R 3, i.e. [ ] 1.1
DS-GA 1002 Lecture notes 0 Fall 2016 Linear Algebra These notes provide a review of basic concepts in linear algebra. 1 Vector spaces You are no doubt familiar with vectors in R 2 or R 3, i.e. [ ] 1.1
Stochastic modelling of epidemic spread
 Stochastic modelling of epidemic spread Julien Arino Centre for Research on Inner City Health St Michael s Hospital Toronto On leave from Department of Mathematics University of Manitoba Julien Arino@umanitoba.ca
Stochastic modelling of epidemic spread Julien Arino Centre for Research on Inner City Health St Michael s Hospital Toronto On leave from Department of Mathematics University of Manitoba Julien Arino@umanitoba.ca
EE263 Midterm Exam. This is a 24 hour take-home midterm. Please turn it in at Bytes Cafe in the Packard building, 24 hours after you pick it up.
 EE263 Midterm Exam This is a 24 hour take-home midterm. Please turn it in at Bytes Cafe in the Packard building, 24 hours after you pick it up. You may use any books, notes, or computer programs (e.g.,
EE263 Midterm Exam This is a 24 hour take-home midterm. Please turn it in at Bytes Cafe in the Packard building, 24 hours after you pick it up. You may use any books, notes, or computer programs (e.g.,
STABILITY OF FINITE-USER SLOTTED ALOHA UNDER PARTIAL INTERFERENCE IN WIRELESS MESH NETWORKS
 The 8th Annual IEEE International Symposium on Personal, Indoor and Mobile Radio Communications (PIMRC 7) STABILITY OF FINITE-USER SLOTTED ALOHA UNDER PARTIAL INTERFERENCE IN WIRELESS MESH NETWORKS Ka-Hung
The 8th Annual IEEE International Symposium on Personal, Indoor and Mobile Radio Communications (PIMRC 7) STABILITY OF FINITE-USER SLOTTED ALOHA UNDER PARTIAL INTERFERENCE IN WIRELESS MESH NETWORKS Ka-Hung
SIGNAL STRENGTH LOCALIZATION BOUNDS IN AD HOC & SENSOR NETWORKS WHEN TRANSMIT POWERS ARE RANDOM. Neal Patwari and Alfred O.
 SIGNAL STRENGTH LOCALIZATION BOUNDS IN AD HOC & SENSOR NETWORKS WHEN TRANSMIT POWERS ARE RANDOM Neal Patwari and Alfred O. Hero III Department of Electrical Engineering & Computer Science University of
SIGNAL STRENGTH LOCALIZATION BOUNDS IN AD HOC & SENSOR NETWORKS WHEN TRANSMIT POWERS ARE RANDOM Neal Patwari and Alfred O. Hero III Department of Electrical Engineering & Computer Science University of
On the Throughput, Capacity and Stability Regions of Random Multiple Access over Standard Multi-Packet Reception Channels
 On the Throughput, Capacity and Stability Regions of Random Multiple Access over Standard Multi-Packet Reception Channels Jie Luo, Anthony Ephremides ECE Dept. Univ. of Maryland College Park, MD 20742
On the Throughput, Capacity and Stability Regions of Random Multiple Access over Standard Multi-Packet Reception Channels Jie Luo, Anthony Ephremides ECE Dept. Univ. of Maryland College Park, MD 20742
Simplified Analysis of HARQ Cooperative Networks Using Finite-State Markov Chains
 Simplified Analysis of HARQ Cooperative Networks Using Finite-State Markov Chains Faton Maliqi, Francesca Bassi, Pierre Duhamel, Ilir Limani L2S CNRS-CentraleSupelec-Université Paris-Sud, Gif-sur-Yvette,
Simplified Analysis of HARQ Cooperative Networks Using Finite-State Markov Chains Faton Maliqi, Francesca Bassi, Pierre Duhamel, Ilir Limani L2S CNRS-CentraleSupelec-Université Paris-Sud, Gif-sur-Yvette,
Exact Probability of Erasure and a Decoding Algorithm for Convolutional Codes on the Binary Erasure Channel
 Exact Probability of Erasure and a Decoding Algorithm for Convolutional Codes on the Binary Erasure Channel Brian M. Kurkoski, Paul H. Siegel, and Jack K. Wolf Department of Electrical and Computer Engineering
Exact Probability of Erasure and a Decoding Algorithm for Convolutional Codes on the Binary Erasure Channel Brian M. Kurkoski, Paul H. Siegel, and Jack K. Wolf Department of Electrical and Computer Engineering
On the Optimality of Myopic Sensing. in Multi-channel Opportunistic Access: the Case of Sensing Multiple Channels
 On the Optimality of Myopic Sensing 1 in Multi-channel Opportunistic Access: the Case of Sensing Multiple Channels Kehao Wang, Lin Chen arxiv:1103.1784v1 [cs.it] 9 Mar 2011 Abstract Recent works ([1],
On the Optimality of Myopic Sensing 1 in Multi-channel Opportunistic Access: the Case of Sensing Multiple Channels Kehao Wang, Lin Chen arxiv:1103.1784v1 [cs.it] 9 Mar 2011 Abstract Recent works ([1],
Let (Ω, F) be a measureable space. A filtration in discrete time is a sequence of. F s F t
 2.2 Filtrations Let (Ω, F) be a measureable space. A filtration in discrete time is a sequence of σ algebras {F t } such that F t F and F t F t+1 for all t = 0, 1,.... In continuous time, the second condition
2.2 Filtrations Let (Ω, F) be a measureable space. A filtration in discrete time is a sequence of σ algebras {F t } such that F t F and F t F t+1 for all t = 0, 1,.... In continuous time, the second condition
Quiz 1 EE 549 Wednesday, Feb. 27, 2008
 UNIVERSITY OF SOUTHERN CALIFORNIA, SPRING 2008 1 Quiz 1 EE 549 Wednesday, Feb. 27, 2008 INSTRUCTIONS This quiz lasts for 85 minutes. This quiz is closed book and closed notes. No Calculators or laptops
UNIVERSITY OF SOUTHERN CALIFORNIA, SPRING 2008 1 Quiz 1 EE 549 Wednesday, Feb. 27, 2008 INSTRUCTIONS This quiz lasts for 85 minutes. This quiz is closed book and closed notes. No Calculators or laptops
 http://www.math.uah.edu/stat/markov/.xhtml 1 of 9 7/16/2009 7:20 AM Virtual Laboratories > 16. Markov Chains > 1 2 3 4 5 6 7 8 9 10 11 12 1. A Markov process is a random process in which the future is
http://www.math.uah.edu/stat/markov/.xhtml 1 of 9 7/16/2009 7:20 AM Virtual Laboratories > 16. Markov Chains > 1 2 3 4 5 6 7 8 9 10 11 12 1. A Markov process is a random process in which the future is
Transience: Whereas a finite closed communication class must be recurrent, an infinite closed communication class can be transient:
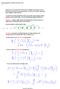 Stochastic2010 Page 1 Long-Time Properties of Countable-State Markov Chains Tuesday, March 23, 2010 2:14 PM Homework 2: if you turn it in by 5 PM on 03/25, I'll grade it by 03/26, but you can turn it in
Stochastic2010 Page 1 Long-Time Properties of Countable-State Markov Chains Tuesday, March 23, 2010 2:14 PM Homework 2: if you turn it in by 5 PM on 03/25, I'll grade it by 03/26, but you can turn it in
1/2 1/2 1/4 1/4 8 1/2 1/2 1/2 1/2 8 1/2 6 P =
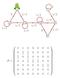 / 7 8 / / / /4 4 5 / /4 / 8 / 6 P = 0 0 0 0 0 0 0 0 0 0 4 0 0 0 0 0 0 0 0 4 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 Andrei Andreevich Markov (856 9) In Example. 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 P (n) = 0
/ 7 8 / / / /4 4 5 / /4 / 8 / 6 P = 0 0 0 0 0 0 0 0 0 0 4 0 0 0 0 0 0 0 0 4 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 Andrei Andreevich Markov (856 9) In Example. 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 P (n) = 0
Week 5: Markov chains Random access in communication networks Solutions
 Week 5: Markov chains Random access in communication networks Solutions A Markov chain model. The model described in the homework defines the following probabilities: P [a terminal receives a packet in
Week 5: Markov chains Random access in communication networks Solutions A Markov chain model. The model described in the homework defines the following probabilities: P [a terminal receives a packet in
SIGNAL STRENGTH LOCALIZATION BOUNDS IN AD HOC & SENSOR NETWORKS WHEN TRANSMIT POWERS ARE RANDOM. Neal Patwari and Alfred O.
 SIGNAL STRENGTH LOCALIZATION BOUNDS IN AD HOC & SENSOR NETWORKS WHEN TRANSMIT POWERS ARE RANDOM Neal Patwari and Alfred O. Hero III Department of Electrical Engineering & Computer Science University of
SIGNAL STRENGTH LOCALIZATION BOUNDS IN AD HOC & SENSOR NETWORKS WHEN TRANSMIT POWERS ARE RANDOM Neal Patwari and Alfred O. Hero III Department of Electrical Engineering & Computer Science University of
DATA MINING LECTURE 13. Link Analysis Ranking PageRank -- Random walks HITS
 DATA MINING LECTURE 3 Link Analysis Ranking PageRank -- Random walks HITS How to organize the web First try: Manually curated Web Directories How to organize the web Second try: Web Search Information
DATA MINING LECTURE 3 Link Analysis Ranking PageRank -- Random walks HITS How to organize the web First try: Manually curated Web Directories How to organize the web Second try: Web Search Information
Radio Network Clustering from Scratch
 Radio Network Clustering from Scratch Fabian Kuhn, Thomas Moscibroda, Roger Wattenhofer {kuhn,moscitho,wattenhofer}@inf.ethz.ch Department of Computer Science, ETH Zurich, 8092 Zurich, Switzerland Abstract.
Radio Network Clustering from Scratch Fabian Kuhn, Thomas Moscibroda, Roger Wattenhofer {kuhn,moscitho,wattenhofer}@inf.ethz.ch Department of Computer Science, ETH Zurich, 8092 Zurich, Switzerland Abstract.
Distributed Scheduling Algorithms for Optimizing Information Freshness in Wireless Networks
 Distributed Scheduling Algorithms for Optimizing Information Freshness in Wireless Networks Rajat Talak, Sertac Karaman, and Eytan Modiano arxiv:803.06469v [cs.it] 7 Mar 208 Abstract Age of Information
Distributed Scheduling Algorithms for Optimizing Information Freshness in Wireless Networks Rajat Talak, Sertac Karaman, and Eytan Modiano arxiv:803.06469v [cs.it] 7 Mar 208 Abstract Age of Information
Multiaccess Communication
 Information Networks p. 1 Multiaccess Communication Satellite systems, radio networks (WLAN), Ethernet segment The received signal is the sum of attenuated transmitted signals from a set of other nodes,
Information Networks p. 1 Multiaccess Communication Satellite systems, radio networks (WLAN), Ethernet segment The received signal is the sum of attenuated transmitted signals from a set of other nodes,
Cognitive Spectrum Access Control Based on Intrinsic Primary ARQ Information
 Cognitive Spectrum Access Control Based on Intrinsic Primary ARQ Information Fabio E. Lapiccirella, Zhi Ding and Xin Liu Electrical and Computer Engineering University of California, Davis, California
Cognitive Spectrum Access Control Based on Intrinsic Primary ARQ Information Fabio E. Lapiccirella, Zhi Ding and Xin Liu Electrical and Computer Engineering University of California, Davis, California
Stochastic2010 Page 1
 Stochastic2010 Page 1 Extinction Probability for Branching Processes Friday, April 02, 2010 2:03 PM Long-time properties for branching processes Clearly state 0 is an absorbing state, forming its own recurrent
Stochastic2010 Page 1 Extinction Probability for Branching Processes Friday, April 02, 2010 2:03 PM Long-time properties for branching processes Clearly state 0 is an absorbing state, forming its own recurrent
Lecture Notes 7 Random Processes. Markov Processes Markov Chains. Random Processes
 Lecture Notes 7 Random Processes Definition IID Processes Bernoulli Process Binomial Counting Process Interarrival Time Process Markov Processes Markov Chains Classification of States Steady State Probabilities
Lecture Notes 7 Random Processes Definition IID Processes Bernoulli Process Binomial Counting Process Interarrival Time Process Markov Processes Markov Chains Classification of States Steady State Probabilities
4452 Mathematical Modeling Lecture 16: Markov Processes
 Math Modeling Lecture 16: Markov Processes Page 1 4452 Mathematical Modeling Lecture 16: Markov Processes Introduction A stochastic model is one in which random effects are incorporated into the model.
Math Modeling Lecture 16: Markov Processes Page 1 4452 Mathematical Modeling Lecture 16: Markov Processes Introduction A stochastic model is one in which random effects are incorporated into the model.
MATH3200, Lecture 31: Applications of Eigenvectors. Markov Chains and Chemical Reaction Systems
 Lecture 31: Some Applications of Eigenvectors: Markov Chains and Chemical Reaction Systems Winfried Just Department of Mathematics, Ohio University April 9 11, 2018 Review: Eigenvectors and left eigenvectors
Lecture 31: Some Applications of Eigenvectors: Markov Chains and Chemical Reaction Systems Winfried Just Department of Mathematics, Ohio University April 9 11, 2018 Review: Eigenvectors and left eigenvectors
Chapter 16 focused on decision making in the face of uncertainty about one future
 9 C H A P T E R Markov Chains Chapter 6 focused on decision making in the face of uncertainty about one future event (learning the true state of nature). However, some decisions need to take into account
9 C H A P T E R Markov Chains Chapter 6 focused on decision making in the face of uncertainty about one future event (learning the true state of nature). However, some decisions need to take into account
TCP over Cognitive Radio Channels
 1/43 TCP over Cognitive Radio Channels Sudheer Poojary Department of ECE, Indian Institute of Science, Bangalore IEEE-IISc I-YES seminar 19 May 2016 2/43 Acknowledgments The work presented here was done
1/43 TCP over Cognitive Radio Channels Sudheer Poojary Department of ECE, Indian Institute of Science, Bangalore IEEE-IISc I-YES seminar 19 May 2016 2/43 Acknowledgments The work presented here was done
