Reordering Rule Makes OBDD Proof Systems Stronger
|
|
|
- Scot Morrison
- 5 years ago
- Views:
Transcription
1 Reordering Rule Makes OBDD Proof Systems Stronger Sam Buss University of California, San Diego, La Jolla, CA, USA Dmitry Itsykson St. Petersburg Department of V.A. Steklov Institute of Mathematics of the Russian Academy of Sciences, St. Petersburg, Russia Alexander Knop University of California, San Diego, La Jolla, CA, USA St. Petersburg Department of V.A. Steklov Institute of Mathematics of the Russian Academy of Sciences, St. Petersburg, Russia Dmitry Sokolov KTH Royal Institute of Technology, Stockholm, Sweden St. Petersburg Department of V.A. Steklov Institute of Mathematics of the Russian Academy of Sciences, St. Petersburg, Russia Abstract Atserias, Kolaitis, and Vardi showed that the proof system of Ordered Binary Decision Diagrams with conjunction and weakening, OBDD(, weakening), simulates CP (Cutting Planes with unary coefficients). We show that OBDD(, weakening) can give exponentially shorter proofs than dag-like cutting planes. This is proved by showing that the Clique-Coloring tautologies have polynomial size proofs in the OBDD(, weakening) system. The reordering rule allows changing the variable order for OBDDs. We show that OBDD(, weakening, reordering) is strictly stronger than OBDD(, weakening). This is proved using the Clique-Coloring tautologies, and by transforming tautologies using coded permutations and orification. We also give CNF formulas which have polynomial size OBDD( ) proofs but require superpolynomial (actually, quasipolynomial size) resolution proofs, and thus we partially resolve an open question proposed by Groote and Zantema. Applying dag-like and tree-like lifting techniques to the mentioned results, we completely analyze which of the systems among CP, OBDD( ), OBDD(, reordering), OBDD(, weakening) and OBDD(, weakening, reordering) polynomially simulate each other. For dag-like proof systems, some of our separations are quasipolynomial and some are exponential; for tree-like systems, all of our separations are exponential ACM Subject Classification Theory of computation Computational complexity and cryptography Keywords and phrases Proof complexity, OBDD, Tseitin formulas, the Clique Coloring principle, lifting theorems Digital Object Identifier /LIPIcs.CCC Funding The research was supported by the Russian Science Foundation (project ) Sam Buss, Dmitry Itsykson, Alexander Knop, and Dmitry Sokolov; licensed under Creative Commons License CC-BY 33rd Computational Complexity Conference (CCC 2018). Editor: Rocco A. Servedio; Article No. 16; pp. 16:1 16:24 Leibniz International Proceedings in Informatics Schloss Dagstuhl Leibniz-Zentrum für Informatik, Dagstuhl Publishing, Germany
2 16:2 Reordering Rule Makes OBDD Proof Systems Stronger 1 Introduction An Ordered Binary Decision Diagram (OBDD) is a branching program such that variables are queried in the same order on every path from the source to a sink. OBDDs were defined by Bryant [3] and have been shown to be useful in a variety of domains, such as hardware verification, model checking, and other CAD applications [4, 15]. Perhaps their most important property is that it is possible to carry out operations on OBDDs efficiently, including Boolean operations, projection, and testing satisfiability. OBDDs have been used for several approaches to SAT-solving [17, 22]. The first such algorithms [22] worked by computing an OBDD for bigger and bigger subformulas of the input formula until obtaining an OBDD for the entire input formula, and then testing the resulting OBDD for satisfiability. A more attractive algorithm, called symbolic quantifier elimination, was proposed by Pan and Vardi [17]. Symbolic quantifier elimination loads clauses of the input formula into the current OBDD one by one and applies projection by a variables which do not appear in the remaining clauses. In contrast with DPLL algorithms, symbolic quantifier elimination can solve Tseitin formulas [11] and the pigeonhole principle [6] in polynomial time. Atserias-Kolaitis-Vardi [1] defined a proof system based on OBDDs for proving unsatisfiability of CNFs, which is now called OBDD(, weakening). An OBDD(, weakening) proof is a sequence of π-obdds with the ordering π of the variables held fixed. The initial lines are π-obdds expressing the input clauses; the final line is the constant false. Each step of the proof applies one of the two rules: Join (or ): A conjunction of any two previously derived π-obdds is inferred; Weakening: A π-obdd is inferred that is semantically implied by some earlier derived π-obdd. The correctness of a proof step can be checked in polynomial time; in particular, checking if D 1 is a weakening of D 2 can done by verifying that D 2 D 1 is unsatisfiable. The paper [1] showed that Cutting Planes with unary coefficients (CP ) is simulated by OBDD(, weakening). This was proved by showing that any linear inequality has a short π-obdd representation (under any ordering π) and that addition of two inequalities may be simulated by join and weakening. Hence, OBDD(, weakening) is strictly stronger than resolution; however, Segerlind [19] showed that tree-like OBDD(, weakening) does not simulate (dag-like) resolution. Additionally, [1] showed that any unsatisfiable system of linear equation modulo two has a short refutation in OBDD(, weakening), while it is open, whether linear systems have short CP refutations. It is still open whether CP is strictly stronger than CP, and correspondingly it is open whether OBDD(, weakening) simulates CP. Krajíček [14] proved the first exponential lower bound for OBDD(, weakening). His lower bound consisted of two parts. 1. If a function f is computed by a π-obdd D, the communication complexity of f under a partition Π 0, Π 1 of the variables where the variables in Π 0 precede (in the sense of π) the variables from Π 1 is at most log D +1. Since every proof system that operates with proof lines with small communication complexity admits monotone feasible interpolation [13], there is an ordering π of the variables so that any π-obdd(, weakening) proof of the Clique-Coloring principle has exponential size. (This was already proven by Atserias et al. [1]). 2. Formulas which are hard for OBDD(, weakening) in some order can be transformed into formulas that are hard for OBDD(, weakening) in all orders. This transformation behaves well for constant width formulas.
3 Sam Buss, Dmitry Itsykson, Alexander Knop, and Dmitry Sokolov 16:3 In the paper we use another transformation due to Segerlind [19]; we use it to prove Lemma 1 and Theorem 10. This transformation behaves well for formulas which grow polynomially under orification. Theorem 8, proved in Section 6, gives short (polynomial size) OBDD(, weakening) proofs of the Clique-Coloring principle. Since any CP proof of the Clique-Coloring principle has exponential size [18], it follows that CP does not simulate OBDD(, weakening) and moreover, that OBDD(, weakening) is strictly stronger than CP. The existence of the small proofs of the Clique-Coloring principle implies that OBDD(, weakening) does not have the feasible interpolation property. This is very curious, because the monotone feasible interpolation property nonetheless helps to prove lower bounds for this system. Our short proofs of the Clique-Coloring principles are based on Grigoriev et. al [9], who gave short proofs of Clique-Coloring in LS 4, a proof system that uses inequalities of degree 4. Unfortunately, even inequalities of degree 2 do not have short OBDD representation, in contrast to inequalities of degree 1. Nevertheless, the proof of [9] may be simulated in OBDD(, weakening) in some order over the variables. An interesting subsystem of OBDD(, weakening) is the system OBDD( ) that uses only the join rule; this system is connected with early OBDD algorithms for SAT-solving [22]. Tveretina et al. [21] proved that PHP n+1 n is hard for OBDD( ). Grut and Zantema [10] showed that there is an unsatisfiable formula (not in CNF) such that it has an efficient construction in OBDDs and any resolution proof of its Tseitin transformation has exponential size. Because of the different translations, the question of an actual separation between OBDD( ) and resolution was left open. In Corollary 12 and Lemma 13, we improve their result by giving CNF formulas which have polynomial size OBDD( ) proofs but require superpolynomial (actually, quasipolynomial size) resolution proofs. Järvisalo [12] claimed an exponential separation between tree-like resolution proofs and (dag-like) OBDD( ) proofs. Unfortunately, as is discussed in Section 5, the proof for the last claim was erroneous. We correct the proof and establish an even stronger result: the proof of Theorem 32 shows that there is a formula ψ n such that in some order π any tree-like π-obdd(, weakening) proof of ψ n has exponential size, but there is a short OBDD( ) proof of ψ n in another order. Note that tree-like π-obdd(, weakening) simulates tree-like resolution for any order π. So far, we have only discussed OBDD proof systems for which proofs consists of π-obdds in the same fixed order π. This constraint is somewhat artificial since there is an algorithm to transforms an OBDD in one order into an OBDD in another order which runs in time polynomially bounded by the combined sizes of the input and output OBDDs. Accordingly, Itsykson et al. [11] introduced the proof system OBDD(, reordering). This system includes a reordering rule which allows changing an OBDD to a different variable ordering. It also includes the join ( ) rule, but with the condition that the two conjoined OBDDs use the same variable ordering. They showed that OBDD(, reordering) does not have short proofs of PHP n+1 n or of Tseitin formulas based on expanders. Additionally, they showed that OBDD(, reordering) is strictly stronger than OBDD( ). In Theorem 10, we resolve an open question of [11] by showing that OBDD(, weakening, reordering) is strictly stronger than OBDD(, weakening). Theorem 24 constructs formulas that have tree-like OBDD(, reordering) proofs of small size but require superpolynomially larger size (dag-like) OBDD(, weakening) proofs. The proof uses a result of [7] and formulas that have short OBDD( ) refutations but require superpolynomial size resolution proofs. This method also allows constructing formulas C C C
4 16:4 Reordering Rule Makes OBDD Proof Systems Stronger OBDD(, weakening, reordering) Theorem 10 CP OBDD(, weakening) Theorem 8 Theorem 24, q.p. CP Theorem 23, q.p. [11, Theorem 13] OBDD(, reordering) Res OBDD( ) [11, Theorem 7] Figure 1 C 1 C 2 denotes C 1 p-simulates C 2, and C 1 C 2 denotes C 1 does not p-simulate C 2. The results are for the dag-like versions of the systems. New results are labelled with the relevant theorem. All the separations on the picture are exponential, except the two separations labeled by q.p for quasipolynomial. that are hard for CP but easy for OBDD( ), see Theorem 23. In Theorem 32, we give CNF formulas which have polynomial size tree-like OBDD(, reordering) proofs but require exponential size for tree-like OBDD(, weakening) proofs. A summary of the (non-)simulation results for dag-like systems is shown in Figure 1. There are still a few questions left open about the systems shown there. First, it is a long-standing open problem whether CP simulates CP. Second, it is open whether OBDD(, weakening) simulates CP. Third, we do not know whether resolution is simulated by OBDD(, reordering). In fact, we do not know whether resolution is simulated by OBDD( ). A couple of earlier papers have claimed that resolution is not simulated by OBDD( ), see Theorem 5 of [21] and Corollary 4 of [12], but we have been unable to verify their proofs. 1 All the other missing arrows in Figure 1 follow from the arrows shown. For instance, OBDD( ) does not simulate CP, since OBDD(, reordering) does not simulate CP. 1 The difficult point in the proofs is in Lemma 8 of [21] and in Lemma 4 of [12]. In the former, it is shown that two distinct nodes in an OBDD B(F, ) correspond to two distinct nodes in another OBDD B(F G, ); however, it does not follow from this that n distinct nodes in B(F, ) correspond to n distinct nodes in B(F G, ). A similar technique is implicitly used in the latter paper, and it is possible to give a counterexample to Lemma 4 of [12].
5 Sam Buss, Dmitry Itsykson, Alexander Knop, and Dmitry Sokolov 16:5 Further research Segerlind showed [19] that dag-like resolution does not polynomially simulate tree-like OBDD(, weakening), hence dag-like OBDD(, weakening) is strictly stronger than treelike OBDD(, weakening). It is open whether OBDD( ), OBDD(, reordering) and OBDD(, weakening, reordering) are simulated by their tree-like versions. It is interesting open question, whether resolution quasipolynomially simulates OBDD( ). Any improving of our separation will automatically improve separations between CP vs. OBDD( ) and OBDD(, weakening) vs. OBDD(, reordering). The major open question is to prove a superpolynomial lower bound on the size of OBDD(, weakening, reordering) refutations. 2 Preliminaries 2.1 Ordered Binary Decision Diagrams An ordered binary decision diagram (OBDD) is used to represent a Boolean function [3]. Let Γ = {x 1,..., x n } be a set of propositional variables. A binary decision diagram (BDD) is a directed acyclic graph with one source. Each vertex of the graph is labeled by a variable from Γ or by a constant 0 or 1. If a vertex is labeled by a constant, then it is a sink (has out-degree 0). If a vertex is labeled by a variable, then it has exactly two outgoing edges: one edge is labeled by 0 and the other edge is labeled by 1. Every binary decision diagram defines a Boolean function {0, 1} n {0, 1}. The value of the function for given values of x 1,..., x n is computed as follows: we start a path at the source and at every step follow the edge that corresponds to the value of the variable labelling the current vertex. Every such path reaches a sink, which is labelled either 0 or 1: this constant is the value of the function. Let π be a permutation of the set [n] = {1,..., n}. A π-ordered binary decision diagram (π-obdd) is a binary decision diagram such that on every path from the source to a sink every variable has at most one occurrence and the variable x π(i) can not appear before x π(j) if i > j. An ordered binary decision diagram (OBDD) is a π-ordered binary decision diagram for some permutation π. By convention, every OBDD is associated with a single fixed permutation π. This π puts a total order on all the variables, even if the OBDD does not query all variables. OBDDs have a number of nice properties. Size of an OBDD is the number of vertices in it, and for a fixed ordering π of variables, every Boolean function has a unique minimal π-obdd. Furthermore, the minimal π-obdd of a function f may be constructed in polynomial time from any π-obdd for the same f. There are also polynomial-time algorithms which act on π-obdds and efficiently perform the operations of conjunction, negation, disjunction, and projection [16]. (Projection is the operation that maps a π-obdd D computing the Boolean function f(x, y 1,..., y n ) to a π-obdd D computing the Boolean function x f(x, y 1,..., y n ).) In addition, there is an algorithm running in time polynomial in the combined sizes of the input and the output which takes as input a π-obdd D and a permutation ρ, and returns the minimal ρ-obdd that represents the same function as D [16]. 2.2 Proof Systems Resolution For an unsatisfiable CNF formula ϕ, a resolution refutation of ϕ (often called a resolution proof ) is a sequence of clauses with the following properties: the last clause is an empty clause; and every clause is either a clause of the initial formula ϕ, or can be obtained from C C C
6 16:6 Reordering Rule Makes OBDD Proof Systems Stronger previous ones by the resolution rule. The resolution rule allows inferring a clause (B C) from clauses (x B) and ( x C). The size of a resolution refutation is the number of clauses in it. It is well known that the resolution proof system is sound and complete. Soundness means that if a formula has a resolution refutation then it is unsatisfiable. Completeness means that every unsatisfiable CNF formula has a resolution refutation. If every clause is used as a premise of the inference rule at most once, then the proof is tree-like Cutting Planes Before we give a definition of this proof system let us define the translation of clauses into linear inequalities by the following rule: if C = n x bi i, then L(C) is the following inequality ( 1) 1 bi x i 1 n (1 b i ) where x 0 denotes x and x 1 denotes x. For an unsatisfiable CNF formula ϕ over the variables x 1,..., x n, a Cutting Planes refutation of ϕ is a sequence of inequalities I 1,..., I t of the type n a i x i c (where a i, c Z) such that I t is an inequality 0 1 and every inequality I j either is L(C) where C is some clause of the initial formula ϕ or can be obtained from previous inequalities by the following rules: Linear Combination: I j is an inequality n (α a i +β b i )x i αc+βd where for some α, β > 0 and 1 k, l < j, I k is an inequality n a i x i c and I l is an inequality n b i x i d; Division: I j is an inequality da i x i c. n a i x i c/d, where for some k < j, I k is an inequality The size of such a refutation is the number of inequalities. Additionally, we say that an unsatisfiable CNF formula ϕ has CP refutation of size S iff there is a CP refutation of ϕ such that the sum of absolute values of coefficients in the inequalities in this proof is at most S. 2 We say that an unsatisfiable CNF formula ϕ has a semantic CP refutation (semantic CP refutation) of size S if there is a CP refutation of ϕ of size S such that instead of these rules we allow deriving any semantic implication of at most two previously derived inequalities. Note that semantic CP (semantic CP ) is not a Cook Reckhow proof system since it is NP-hard to check the correctness of the semantic rule. A proof is tree-like if every inequality is used as a premise of an inference at most once OBDD-based Proof Systems Let ϕ be an unsatisfiable CNF formula. An OBDD proof of ϕ is a sequence D 1, D 2,..., D t of OBDDs and permutations π 1,..., π t such that D t is a π t -OBDD that represents the constant false function, and such that each D i is either a π i -OBDD which represents a clause of ϕ or can be obtained from previous OBDDs by one of the following inference rules: Join (or ): D i represents the Boolean function D k D l for 1 l, k < i, where D i, D k, D l have the same order π i = π k = π l ; 2 Many authors define CP differently, by bounding the coefficients by a polynomial of the size of the formula. All the results for CP stated in the present paper hold under both definitions.
7 Sam Buss, Dmitry Itsykson, Alexander Knop, and Dmitry Sokolov 16:7 Weakening: there exists a 1 j < i such that D i and D j have the same order π i = π j, and D j semantically implies D i. The latter means that every assignment that satisfies D j also satisfies D i ; Reordering: D i is a π i -OBDD that is equivalent to a π j -OBDD D j with 1 j < i. Note that although we use terminology OBDD proof, it is actually a refutation of ϕ. By the discussion in the previous section, there is a polynomial time algorithm which recognizes whether a given D 1,..., D t and π 1,..., π t is a valid OBDD proof of a given ϕ. The size of this proof is equal to t D i. We use several different OBDD proof systems with different sets of allowed rules. For example, the OBDD(, weakening) proof system uses conjunction and weakening rules; hence, all OBDDs in such a proof have the same order π. We use the notation π-obdd( ) proof and π-obdd(, weakening) proof to explicitly indicate the ordering. If every D i is used as a premise of the inference rule at most once, then the proof is tree-like. 3 OBDD(, weakening, reordering) is Strictly Stronger Than OBDD(, weakening) This section constructs formulas which are easy for OBDD(, weakening, reordering) and hard for OBDD(, weakening). For this, we construct a transformation T = T (ϕ) such that If a formula ϕ is hard for π-obdd(, weakening) for some order π, then T (ϕ) is hard for OBDD(, weakening); i.e., T (ϕ) is hard for any order. If a formula ϕ is easy for π-obdd(, weakening) for some order π, then T (ϕ) is easy OBDD(, weakening, reordering). Then we construct a formula ϕ such that there are two orders π 1 and π 2 such that ϕ is hard for π 1 -OBDD(, weakening) but easy for π 2 -OBDD(, weakening). As a corollary, we get that T (ϕ) separates OBDD(, weakening, reordering) and OBDD(, weakening). We will apply this transformation to a formula ϕ expressing the Clique-Coloring principle (Clique-Coloring n,m ) that any (m 1)-colorable graph on n vertices does not contain a clique of size m for m n. Atserias, Kolaitis, and Vardi [1] proved (see also Krajíček [14]) that Clique-Coloring n,m is hard for π-obdd(, weakening) for some order π. However, in Section 6 we show that there is an order π such that Clique-Coloring n,m has a π-obdd(, weakening) proof of size polynomially bounded by n and m. 3.1 Construction of T The transformation T is the same as a construction of Segerlind [19]. We develop the definition of T in stages. As a first approximation, we define how to transform a formula ϕ(x 1,..., x n ) into a formula perm Sn (ϕ)(z 1,..., z l, x 1,..., x n ) where l = log(n!). Fix an injective map rep : S n {0, 1} l that maps the set of permutations of [n] into binary strings of length l. The formula perm Sn (ϕ) is defined by: perm Sn (ϕ)(z 1,..., z l, x 1,..., x n ) = σ S n [( l ) z i = rep(σ) i ϕ ( ) ] x σ(1),..., x σ(n) t {0,1} l \rep(s n) (z 1 = t 1 z 2 = t 2 z l = t l ). Note that it is easy to convert perm Sn (ϕ) into a formula in CNF. We just add to each clause of ϕ(x σ(1),..., x σ(n) ) the literals z 1 rep(σ)1 1, z 1 rep(σ)2 1,..., z 1 rep(σ) l, where zi 0 l C C C
8 16:8 Reordering Rule Makes OBDD Proof Systems Stronger denotes z i, and zi 1 denotes z i, and also add the clauses (z 1 = t 1 z 2 = t 2 z l = t l ). It is easy to see that the formula perm Sn (ϕ) is unsatisfiable since if a substitution to variables z 1, z 2,..., z l does not correspond to a representation of some permutation, then this substitution falsifies the constraint (z 1 = t 1 z 2 = t 2 z l = t l ) and if a substitution to the variables z 1, z 2,..., z l corresponds to a permutation σ, then the ( l formula ) z i = rep(σ) i ϕ(x σ(1),..., x σ(n) ) is falsified by this substitution, since ϕ is unsatisfiable. Applying the partial substitution z i := rep(σ) i for all i to perm Sn (ϕ)(z 1,..., z l, x 1,..., x n ) yields the formula ϕ(x σ(1),..., x σ(n) ). This implies that if ϕ requires a π-obdd(, weakening) proof of size S for some order π, then perm Sn (ϕ) requires an OBDD(, weakening) proof of size S in any order. Indeed, let τ be an order on the variables z 1, z 2,..., z l, x 1, x 2,..., x n and let σ be the order on the variables x 1,..., x n induced by τ. The substitution z 1 z 2... z l := rep(πσ 1 ) transforms a τ-obdd(, weakening) proof of perm Sn (ϕ) to a π-obdd(, weakening) proof of ϕ with no increase in size. Hence the size of the minimal OBDD(, weakening) proof of perm Sn (ϕ) is at least S. The problem with the transformation perm Sn is that perm Sn (ϕ) can be exponentially big. So the next idea for a transformation is to consider a small good set of permutations Π S n instead of all of S n. Letting l = log Π and letting rep now be some injective map rep : Π {0, 1} l, we define analogously perm Π (ϕ)(z 1,..., z l, x 1,..., x n ) = [( l ) z i = rep(σ) i ϕ ( ) ] x σ(1),..., x σ(n) σ Π t {0,1} l \rep(π) (z 1 = t 1 z 2 = t 2 z l = t l ). The problem with this is that it is possible that πσ 1 does not belong to Π. To solve this problem we orify variables: each variable x i is replaced by the disjunction of m fresh ( variables y i,1,... y i,m ; i.e., instead of ϕ(x 1, x 2,..., x n ) we consider ϕ m (y 1,1,..., y n,m ) = m ϕ y 1,j,..., m y n,j ). Now let Π S mn and consider perm Π (ϕ m ). As in previous case j=1 j=1 we want to substitute variables to a proof of perm Π (ϕ m ) in some order and get a proof of ϕ in order π. However, in this case we substitute not only for the variables z 1,..., z l, but also for each k [n] we substitute zero for all variables y k,i except one. This increases the number of different permutations of the variables x 1,..., x n that we can obtain. The only problem with this transformation is that for some formulas ϕ, size of ϕ m may be exponentially bigger than size of ϕ. However, if each clause of ϕ there is only O(1) negated literals, then size of ϕ m will be polynomially bounded. Our good set of permutations is a set of pairwise independent permutations. Let t = log(n) and N = 2 t, and F be the field GF(N). Define Π n to be the set of all mappings given by x ax + b with a, b F and a 0. Elements of Π n may be represented by binary strings of length l = 2t such that the first t bits are not all zero. Note that Π n S N so we have to add new variables, x n+1,..., x N and assume that ϕ does not depend on them. Then define perm(ϕ)(z 1,..., z l, x 1,..., x N ) = [( l ) ] t z i = rep(σ) i ϕ(x σ(1),..., x σ(n) ) z i. σ Π n
9 Sam Buss, Dmitry Itsykson, Alexander Knop, and Dmitry Sokolov 16:9 Now we can define the transformation T. Let ϕ be a formula on n variables and m be the least integer such that 2n3 m + n2 mn 1 < 1, so m = O(n3 ). Then T (ϕ) = perm(ϕ m ). The first property of T given at the beginning of Section 2.2 was established by Segerlind [19]: Lemma 1 ([19]). Let ϕ be an unsatisfiable formula in CNF on the variables x 1,..., x n. Suppose there is an OBDD(, weakening) proof (respectively, an OBDD( ) proof) of the formula T (ϕ) of size S. Then for every order π on x 1,..., x n there is a π-obdd(, weakening) proof (respectively, a π-obdd( ) proof) of ϕ of size at most S. The idea of the proof of lemma is as follows. Suppose τ Π n is an order on z 1,..., z l, x 1,..., x N, and let π be an order on x 1,..., x n. Then there are j 1,..., j n such the order τ restricted to y 1,j1,..., y n,jn is the same as the order π on x 1,..., x n. Replacing the variables z i with the constants rep(τ) i, renaming the variables y i,ji to x i, and replacing all other variables y i,j with 0 thus transforms the OBDD(, weakening) or OBDD( ) proof of T (ϕ) into a proof of ϕ. For details, consult Segerlind [19]. The second property of T states that if ϕ is easy for OBDD(, weakening) in some order, then T (ϕ) is easy for OBDD(, weakening, reordering). Its proof consists of two parts: First, Lemma 2 shows that if ϕ is easy for OBDD(, weakening), then perm(ϕ) is easy for OBDD(, weakening, reordering); then Section 3.2 shows that if ϕ is easy for OBDD(, weakening), then ϕ m is easy for OBDD(, weakening). Lemma 2. Let ϕ n (x 1, x 2,..., x n ) be a family of unsatisfiable formulas such that for each n, there is an order τ so that ϕ n has a τ-obdd(, weakening) proof P 1 of size t(n). Then the formula perm(ϕ n ) has an OBDD(, weakening, reordering) proof P 2 of size t(n)poly(n). If P 1 is tree-like, then so is P 2. In addition, if P 1 does not use the weakening rule, then neither does P 2. Proof. Suppose P 1 is a τ-obdd(, weakening) proof of ϕ n (x 1, x 2,..., x n ) of size t(n) using the order τ on x 1, x 2,..., x n. We describe an OBDD(, weakening, reordering) proof P 2 of perm(ϕ n ). For σ a permutation in Π n, let µ σ be the order on z 1, z 2,..., z l, x 1, x 2,..., x n such that x 1, x 2,..., x n are ordered by τσ 1 and follow the variables z 1, z 2,..., z l. In other words, µ σ orders variables as follows: z 1, z 2,..., z l, x τσ 1 (1), x τσ 1 (2),..., x τσ 1 (n). For σ Π n, it is easy to ( transform the proof P 1 into a µ σ -OBDD( ) derivation P 1,σ of a l ) ( diagram that represents z l ) i = rep(σ) i from the CNF formula z i = rep(σ) i ϕ n (x σ(1),..., x σ(n) ). Namely each diagram D of P 1 is replaced by the diagram D σ ( l z i = rep(σ) i ), where D σ is D with the variables x i permuted according to σ. Since the variables ( z 1, z 2,..., z l precede the variables x 1,... x n in the order µ σ, each diagram l ) D σ z i = rep(σ) i has size D + O(l), where D is the size of D. Hence, P 1,σ is t(n) (1 + O(l)). For σ Π n, the hypotheses of P 1,σ are clauses of perm(ϕ n ). Therefore combining the derivations P 1,σ gives immediately a derivation of the diagrams which represent ( l ) z i = rep(σ) i for σ Π n and a diagram encoding l z i. Formally, these diagrams use different orders µ σ but these differ only in how they order the variables x 1,..., x n that do not occur in the derived diagrams. Thus, the reordering rule can be used to change the orders in all of these diagrams to some standard one, without changing the diagrams. Repeatedly applying the conjunction rule to these diagrams yields the constant false diagram since z 1 z 2... z l is equal to rep(σ) for some σ Π n or z 1 = z 2 = = z t = 0. All intermediate diagrams use only l variables and thus have size at most O(2 l ). The overall size of the proof P 2 is Π n t(n)(1 + O(l)) + O(2 l Π n ) = t(n)poly(n) since l = 2t = 2 log n. The construction preserves the tree-like property, and whether the weakening rule is used, so Lemma 2 is proved. C C C
10 16:10 Reordering Rule Makes OBDD Proof Systems Stronger 3.2 Complexity of Composition We now prove that if ϕ has a small OBDD(, weakening) proof, then ϕ m has a small OBDD(, weakening) proof. In fact, we prove more a general statement. Let ϕ be a CNF formula with n variables, and g : {0, 1} k {0, 1} be a Boolean function. Then ϕ g denotes a CNF formula on kn variables that represents ϕ(g( x 1 ), g( x 2 ),..., g( x n )), where x i denotes a vector of k new variables. ϕ g is constructed by applying the substitution to every clause C of ϕ and converting the resulting function C g to CNF in some fixed way. We need the following technical definition. Consider a CNF formula ϕ = m C i. We say ϕ is S-constructible with respect to (w.r.t.) the order π if there is a binary tree with vertices labeled by π-obdds such that: (1) the root is labeled by a π-obdd representation of ϕ, (2) the tree contains m leaves labeled by π-obdd representations of the clauses C i, each clause appears in exactly one leaf, (3) each vertex is labelled by a π-obdd that represents the conjunction of labels of its children, and (4) the size of each label is at most S. Remark. If ϕ is S-constructible CNF w.r.t. the order π, then there is a tree-like π-obdd( ) derivation of size (2m 1)S of a π-obdd that represents ϕ from the clauses of ϕ. Proposition 3. Let F = G 1 G 2, where G 1 and G 2 are Boolean functions that depend on disjoint sets of variables. If the variables of G 1 precede variables of G 2 in the order π, then the smallest size of a π-obdd representation of F is at most the sum of sizes of the smallest π-obdd representations of G 1 and G 2. Proof. This is obvious. The π-obdd for F can be obtained by the identifying the source of the π-obdd for G 2 with the sink of the π-obdd for G 1 labeled by 0. Lemma 4. Let F 1, F 2,..., F k be CNF formulas with disjoint sets of variables, where F j = C i for all j [k]. Let π 1,..., π k be orders such that each F j is S-constructible i I j w.r.t. π j. Define the order π to order the variables of each F i according to π i and so that all the variables of F i precede all the variables of F i+1. Let F be the CNF representation of the k function F 1 F 2 F k, namely, F = C ij. Then F is ks-constructible w.r.t. π. i 1 I 1,...,i k I k j=1 Proof. We prove this lemma by induction on k. The basis case is trivial: if k = 1, then F = F 1, hence F is S-constructible. For the induction hypothesis, let G = F 1 F 2 F k 1. By the induction hypothesis G is (k 1)S-constructible w.r.t. π. For each clause D of G and each i I k, the clause D C i is a clause of F. The formula F k is S-constructible w.r.t. π by a tree T k with I k leaves which are labeled by C i for i I l. We wish to replace each leaf of T k labelled with a C i with a tree for G C i. Since G is (k 1)S-constructible and since the variables of C i are disjoint from those of G, Proposition 3 implies that G C i is ks-constructible w.r.t. π, since we can incorporate the clause C i into all clauses of the tree giving the (k 1)S-constructibility of G. In addition, replace all the diagrams D labelling vertices in the tree T k by D G; by Proposition 3 the size of the updated diagrams is at most ks. This gives a tree witnessing the ks-constructibility of F 1 F k as desired. Theorem 5. Let π be an order on z 1,..., z m. Let f and g be Boolean functions of z 1,..., z m such that f = g and that both f and g have S-constructible CNF representations w.r.t. π. If ϕ(x 1,..., x n ) is a CNF formula that has an OBDD(, weakening) proof of size L, then ϕ g has an OBDD(, weakening) proof of size poly( ϕ g, S, L). The statement is also true for OBDD( ), tree-like OBDD( ), and tree-like OBDD(, weakening).
11 Sam Buss, Dmitry Itsykson, Alexander Knop, and Dmitry Sokolov 16:11 The basic idea of Theorem 5 is that each line of a proof of ϕ can be composed with g to form a proof of ϕ g; Lemma 4 is used to handle initial clauses. Proof. Let ϕ have an OBDD(, weakening) proof of size L using the order σ on x 1,..., x n. Define the order τ on the variables z i,j as follows. The variables are grouped into blocks, the i-th block is z i,1,..., z i,m. The blocks are ordered according to σ so all variables of block i precede those of block j iff x i precedes x j according to σ. Within the i-th block, the variables z i,1,..., z i,m are ordered according to the order π. We construct the desired OBDD(, weakening) proof using the order τ. Lemma 4 implies that, for any clause C, the CNF C g is S C -constructible in order τ. Note that we need that both g and g are S-constructible to apply Lemma 4, since variables can appear both positively and negatively in C. Consider the following τ-obdd(, weakening) proof of ϕ g: First we create τ-obdds that represent the functions C g for each clause C of the formula ϕ. Then we repeat the OBDD(, weakening) proof for ϕ, but we do it for ϕ g. Each a diagram D from the proof of ϕ is replaced by a diagram for D g. It is not hard to see that the definition of τ allows us to replace a splitting over a variable x i in the diagram D by a subdiagram splitting over the value of the function g( z i ), where z i is the vector of the variables z i,1,..., z i,m. This increases the proof size by at most a factor of S. The resulting proof is a correct OBDD(, weakening) proof and its size is at most L S + ϕ g S. The clause m y i and the CNF m y i are both m-constructible, thus we obtain: Corollary 6. If there is a short OBDD(, weakening) proof (tree-like OBDD( ) proof) of a formula ϕ, then there is a short OBDD(, weakening) proof (tree-like OBDD( ) proof) of the formula ϕ m. 3.3 Separation We have shown that if a formula ϕ is hard for OBDD(, weakening) in one order, but is easy for OBDD(, weakening) in another, then T (ϕ) is hard for OBDD(, weakening) but it is easy for OBDD(, weakening, reordering). We will prove this holds for ϕ the Clique-Coloring principle. Definition 7. The Clique-Coloring principle is a formula encoding the statement that it is impossible that a graph both is (m 1)-colorable and has a m-clique. The Clique-Coloring principle uses the variables {p i,j } i j [n], {r i,l } i [n],l [m 1], and {q k,i } k [m],i [n]. Informally p i,j = 1 if there is an edge between vertices i and j, r i,l = 1 if vertex i has color l, and q k,i = 1 if vertex i is the k-th vertex in the clique. More formally, the Clique-Coloring principle is the conjunction of the following statements written as clauses. For technical reasons we also express the clauses as inequalities with integer coefficients: n 1. q k,i ( n q k,i 1) for any k [m]. This states that the clique has a vertex with number k. 2. q k,i q k,j p i,j (q k,i + q k,j p i,j + 1) for all i j [n] and k k [m]. This states that there is an edge between the i-th and j-th vertices of the clique. 3. q k,i q k,j (q k,i + q k,j 1) for any k [m] and i j [n]. This states that at most one element in the clique with number k. C C C
12 16:12 Reordering Rule Makes OBDD Proof Systems Stronger 4. q k,i q k,i (q k,i + q k,i 1) for all i [n] and k k [m]. This states that the n vertices in clique are distinct. r i,l 1) for all i [n]. This states that the i-th vertex has a color. 5. m 1 r i,l l=1 ( m 1 l=1 6. p i,j r i,l r j,l (p i,j + r i,l + r j,l 2) for all i j and l. This states that if vertices i and j have the same color l, there there is no edge between them. Clique-Coloring n,m denotes the Clique-Coloring principle for n and m. This formula has size polynomially bounded by m and n. Note that, usually Clique-Coloring principle is defined without constraints 3. We prove the next theorem in Section 6. Theorem 8. There is an OBDD(, weakening) proof of the Clique-Coloring n,m principle of size polynomial in n and m. An exponential lower bound on the size of proofs of the formula Clique-Coloring n,m has been given by Atserias Kolaitis Vardi and by Krajíček. Their proofs hold even with the addition of the constraints 3. Theorem 9 ([1, 14]). There is an order π such that any OBDD(, weakening) proof of Clique-Coloring n, n has size at least 2 n1/5. These two theorems let us separate the OBDD(, weakening, reordering) and OBDD(, weakening) proof systems. Theorem 10. There are a family of CNF formulas ϕ n and a constant c > 0 such that: ϕ n has size poly(n); there is an OBDD(, weakening, reordering) proof of ϕ n of size poly(n); any OBDD(, weakening) proof of ϕ n has size Ω(2 nc ). Proof. Let us consider ψ n = Clique-Coloring n, n. By Theorem 9 there is an order π such that any π-obdd(, weakening) proof of the formula ψ n has size at least 2 nɛ. Since all clauses of Clique-Coloring n, n that contain a negation have constant width, the CNF encoding of Clique-Coloring m n, has size poly(n, m). By Lemma 1, any OBDD(, weakening) proof of n the formula T (ψ n ) has size 2 nɛ. In the definition of T (ψ n ), we choose m that is polynomially bounded in the number of variables in Clique-Coloring n, n. Hence, by Theorem 8 and Theorem 5, there is an OBDD(, weakening) proof of ψn m of size polynomial in n. As a result, by Lemma 2, there is an OBDD(, weakening, reordering) proof of T (ψ n ) = perm(ψn m ) of size poly(n, m). Thus, we can use the formula T (ψ n ) as ϕ n. 4 Quasipolynomial Separations for Dag-like Case 4.1 Resolution Does Not Polynomially Simulate OBDD( ) In this section we prove that resolution does not polynomially simulate OBDD( ). After that we will apply to this result a lifting technique recently developed by Garg et al. [7] and get as a corollary that Cutting Planes does not polynomially simulate OBDD( ), and that OBDD(, weakening) does not polynomially simulate OBDD(, reordering). A Tseitin formula TS G,c is based on an undirected graph G(V, E) and a labelling function c : V {0, 1}. In this formula for every edge e E there is the corresponding propositional variable p e. For every vertex v V we write down a formula in CNF encoding
13 Sam Buss, Dmitry Itsykson, Alexander Knop, and Dmitry Sokolov 16:13 p (u,v) c(v) (mod 2). The conjunction of the formulas described above is u V :(u,v) E,u v called a Tseitin formula. If c(v) 1 (mod 2) for some connected component U V, v U then the Tseitin formula is unsatisfiable. Indeed, if we sum up (modulo 2) all equalities corresponding to the vertices from U we get 0 1 (mod 2) since each variable has exactly 2 occurrences. If c(v) 0 (mod 2) for every connected component U, then the Tseitin v U formula is satisfiable ([23, Lemma 4.1]). Tseitin formulas based on constant degree expanders are known to be hard for resolution [23]. Itsykson et al. [11] showed that they are also hard for OBDD(, reordering) by giving a 2 Ω( V ) lower bound. There are, of course, resolution refutations of size O(2 E ) since there are E many variables. Accordingly, we consider Tseitin formulas based on the complete graph K log n on log n vertices, so as to have V = o( E ). By the definition of a Tseitin formula, TS Klogn,c is a system of log n linear equations and every equation depends on log n 1 variables. Hence, TS Klogn,c is a ( log n 1)-CNF formula with O(log 2 n) variables and O(n log n) clauses. Lemma 11. Let F be a canonical CNF representation of an unsatisfiable linear system A over F 2 that contains m equations and n variables. Then for every order of variables, F has a tree-like OBDD( ) proof of size at most 8m F 2 + mn2 m + 2m. Proof. First of all, for every linear equation of A we deduce an OBDD representing this equation. Assume that a linear equation contains r variables, then its canonical CNF representation contains 2 r 1 clauses, hence F 2 r 1. We deduce an OBDD representation of the equation by joining all the clauses that represent this equation. The conjunction of several clauses that represent the equation is a Boolean function from r variables, hence it has an OBDD representation of size at most 2 r (this is the size of an OBDD that corresponds to the complete decision tree). Hence, the size of the derivation is at most 8 F 2. And the size of the derivation of all OBDDs for all equations is at most 8m F 2. Finally, we join all OBDDs representing linear equations one by one and we get the constant false OBDD. The size of the described derivation may be estimated using the following claim. Claim. For any order over the variables there is an OBDD of size at most n2 m + 2 that represents the system of m linear equations over F 2 with n variables. Let us fix some order on the variables. The described OBDD will have n levels. Nodes on the i-th level are labeled with i-th variable in the chosen order. Assume that we already tested the values of the first i 1 variables. For every equation we compute the sum modulo 2 of the values of these i 1 variables that occur in the equation. So we will have a vector of m parities. The i-th level of the OBDD contains 2 m nodes corresponding to all the possible values of the vector of parities that we get after the reading of the first i 1 edges. Each node on the i-th level has two outgoing edges to nodes on the (i + 1)-th level corresponding to the way how values of variables change the partial sum. The node on the first level corresponding to all zero values of parities is the source of the OBDD (all nodes that are not reachable from the source should be removed). Outgoing edges for every node on the last level lead to a sink labelled 1 or 0 depending whether or not all the equations are satisfied. This proves the claim, and hence Lemma 11. Corollary 12. If TS Klogn,c is unsatisfiable Tseitin formula, then there is a tree-like OBDD( ) proof of TS Klogn,c of size at most poly(n). C C C
14 16:14 Reordering Rule Makes OBDD Proof Systems Stronger Lemma 13. Every resolution proof of TS Klogn,c has size at least 2 Ω(log2 n). The proof of Lemma 13 is based on the width based lower bound by Ben-Sasson and Wigderson [2]. The width of a clause is the number of literals in it. For a CNF formula ϕ, the width w(ϕ) of ϕ is the maximum width of its clauses. The width of a resolution refutation is a width of the largest used clause. w( ϕ) denotes the minimum width of any resolution proof of ϕ. Theorem 14 ([2]). The size of the shortest resolution refutation of any CNF formula ϕ with n variables is at least 2 Ω((w( ϕ) w(ϕ))2 /n). Theorem 15 ([2]). The minimal width of a resolution proof of a Tseitin formula based on a graph G(V, E) is at least e(g), where e(g) is the minimal number of edges between U and V \ U over all set of vertices U of size between V /3 and 2 V /3. Corollary 16. If TS Klog n,c is an unsatisfiable Tseitin formula, then w( TS Klog n,c) = Ω(log 2 n). Proof. It is straightforward that e(k log n ) = Ω(log 2 n). So by Theorem 13, w( TS Klog n,c) = Ω(log 2 n). Proof of Lemma 13. It is easy to see that w(ts Klog n,c) = O(log n) and TS Klog n,f contains O(log 2 n) variables. Thus, by Theorem 14 and by Corollary 16, size of the shortest resolution proof of TS Klog n,f is at least 2 Ω(log2 n). Corollary 12 and Lemma 13 give a superpolynomial separation between resolution and tree-like OBDD( ). The next sections describe how to lift this to separate cutting planes and tree-like OBDD( ). 4.2 Lifting from Resolution Width This subsection briefly describes the results by Garg et al. [7] that allows maping formulas with large resolution width to formulas that are hard for several stronger proof systems. Let G be a family of functions {0, 1} n {0, 1} and ϕ be an unsatisfiable formula over n variables. The G-refutation of ϕ is a directed acyclic graph of fan-out at most 2 with each node v labeled by a function g v G such that the following constraints are satisfied. Source: There is a distinguished source node r with fan-in 0, and g r is constant 0 function. Non-sinks: For each non-sink node v with children u 1 and u 2, we have gv 1 (0) gu 1 1 (0) gu 1 2 (0). And if v has only one child u, then gv 1 (0) gu 1 (0). (0) C 1 (0) (i.e. every assignment that satisfies C also satisfies g v ). The size of a G-refutation is the size of the graph. The notion of G-refutation extends several proof systems including resolution (if functions from G are represented by clauses), Cutting Planes (if functions from G are represented by linear inequalities) and OBDD(, weakening) (if functions from G are represented by OBDDs). G-refutations are commonly called semantic refutations. Let Π = (X, Y ) be a partition of [n] into two disjoint parts. We say that G is Π- rectangular if for every function g G, the set g 1 (0) is a rectangle, i.e. g 1 (0) = A B, where A {0, 1} X and B {0, 1} Y. We say that G has Π-communication complexity at most c iff for every g G the communication complexity of g with respect to the partition Π is at most c. Notice that if G is Π-rectangular, then it has Π-communication complexity at most 2. Sinks: Each sink node v is labeled by a clause C of ϕ such that g 1 v
15 Sam Buss, Dmitry Itsykson, Alexander Knop, and Dmitry Sokolov 16:15 Lemma 17 ([20]). Let ϕ be an unsatisfiable CNF formula with n variables and Π = (X, Y ) be a partition of [n] into two disjoint parts. Assume that π has a G-refutation of size S and G has Π-communication complexity at most c. Then there is a Π-rectangular set G such that ϕ has a G -refutation of size at most 2 3c S. Notice that the set of all clauses is Π-rectangular for every partition Π. The set of π-obdds of size S has Π-communication complexity log S + 1 for partitions Π = (X, Y ) where the variables of X precede the variables of Y in the order π. In order to capture Cutting Planes we say that G is Π-triangular if for every g G there are functions a : {0, 1} X R and b : {0, 1} Y R such that g 1 (0) = {x {0, 1} X, y {0, 1} y a(x) < b(y)}. Note that the set of all linear inequalities with integer coefficients over Boolean variables is Π-triangular for every partition Π. Let Ind m : {0, 1} log m {0, 1} m {0, 1} be a Boolean function such that Ind m (z 1,..., z log m, y 1,..., y m ) = y b, where b is the integer with binary representation z 1... z log m. Theorem 18 ([7]). Let ϕ be an unsatisfiable CNF formula ϕ with n variables. Let m = n δ, where δ is some global constant. Let Π = (X, Y ) be the following partition of variables of ϕ Ind m : all z-variables go to X, all y-variables go to Y. If G is Π-rectangular or G is Π-triangular, then every G-refutation of ϕ Ind m has size at least n Ω(w( ϕ)). Corollary 19. Under the conditions of Theorem 18, if G has Π-communication complexity at most c, then every G-refutation of ϕ Ind m has size at least 2 3c n Ω(w( ϕ)). Proof. By Lemma 17, if there is a G-refutation of ϕ Ind m of size S, there exists a G - refutation of ϕ Ind m of size at most 2 3c S such that G is Π-rectangular. By Theorem 18, 2 3c S n Ω(w( ϕ)), hence S 2 3c n Ω(w( ϕ)). Corollary 20. Under the conditions of Theorem 18, every Cutting Planes proof of ϕ Ind m has size at least n Ω(w( ϕ)). Proof. The statement follows from Theorem 18, since the set of linear inequalities is Π- triangular for every partition Π. 4.3 Cutting Planes Does Not Polynomially Simulates OBDD( ) Lemma 21. Both functions Ind m and Ind m have poly(m)-constructible CNF representations. Proof. Let us consider the following formula for Ind m, m (bin(z 1,..., z log m ) = i) y i, where bin(z 1,..., z log m ) = i is the conjunction of literals stating that z 1,..., z log m is the binary representation of i. For l [m], let ϕ l be the formula l (bin(z 1,..., z log m ) = i) y i, and let ϕ m = Ind m. We claim that for all l [m] the formula ϕ l has an OBDD representation of size poly(m) in the order z 1,..., z log m, y 1,..., y m. Indeed, such an OBDD has the following structure: it starts with the complete decision tree over all the variables z i ; consider a leaf of this decision tree that corresponds to a number i. If i l, then we add to this leaf a node of OBDD labeled with y i and the outgoing edge labeled with 0 going to the C C C
16 16:16 Reordering Rule Makes OBDD Proof Systems Stronger 0-sink and the outgoing edge labeled with 1 going to the 1-sink. If i > l, then we identify this leaf with 1-sink. Hence, there is a poly(m)-constructible CNF representation of Ind m. The same argument works also for Ind m, since Ind m (z 1,..., z log m, y 1, y 2,..., y m ) = Ind m (z 1,..., z log m, y 1, y 2,..., y m ). Lemma 22. The formula TS Klogn,c Ind m has at most m O(log n) clauses of size O(log n log m) and O(m log 2 n) variables. Proof. Each clause of TS Klogn,c consists of log n 1 literals and by Lemma 21 there is CNF representations of Ind m and Ind m with m clauses. Hence, for each clause C of TS Klogn,c, the formula C Ind m has m log n 1 clauses each of length ( log n 1)( log m + 1). Theorem 23. Let TS Klogn,c be unsatisfiable Tseitin formula based on a complete graph K log n on log n vertices. Let m = (log n) 2δ, where δ is the constant from Theorem 18. Then 1. TS Klogn,c Ind m has a tree-like OBDD( ) proof of size (log n) O(log n) and 2. every Cutting Planes proof of TS Klogn,c Ind m has size at least (log n) Ω(log2 n). Proof. 1. By Lemma 21, both Ind m and Ind m are poly(m)-constructible. By Corollary 12, there is a tree-like OBDD( ) refutation of TS Klogn,c of size poly(n). By Lemma 22, the size of the formula TS Klogn,c Ind m is at most m O(log n). Hence, by Theorem 5, there is a treelike OBDD( ) refutation of TS Klogn,c Ind m of size poly(poly(n), m O(log n), poly(n)) = (log n) O(log n). 2. By Corollary 16, w( TS Klog n,c) = Ω(log 2 n). Hence, by Corollary 20, every Cutting Planes proof of TS Klog n,c Ind m has size at least (log 2 n) Ω(log2 n) = (log n) Ω(log2 n). 4.4 OBDD(, weakening) Does Not Polynomially Simulate OBDD(, reordering) Theorem 24. There is a family of formulas ϕ n such that: the size of ϕ n is (log n) O(log n log log n) and number of variables in ϕ n is poly(log n); there is a tree-like OBDD(, reordering) proof of ϕ n of size (log n) O(log n log log n) ; every OBDD(, weakening) proof of ϕ n has size at least (log n) Ω(log2 n). Lemma 25. Let TS Klog n,c be an unsatisfiable Tseitin formula. Let m = (log n) 2δ, where δ is the constant from Theorem 18. There is a family of orders {π n } n N over the variables of the formulas TS Klog n,c Ind m such that every π n -OBDD(, weakening) proof of TS Klog n,c Ind m has size at least (log n) Ω(log2 n). Proof. Let π n be an order on variables of TS Klog n,c Ind m, where all z-variables precedes all y-variables. Consider some π n -OBDD(, weakening) proof of TS Klog n,c Ind m ; let S denote its total size. Hence, the number of proof lines and sizes of all OBDDs are at most S. Consider a partition Π = (X, Y ) of the variables of TS Klog n,c Ind m such that X contains all z-variables and Y contains all y-variables. The communication complexity of computing an OBDD of size S w.r.t. the partition Π is at most log S + 1. Therefore, the π n -OBDD(, weakening) proof can be viewed as a G-refutation, where G has Π-communication complexity at most log S + 1. Hence, by Corollary 19, S 2 3 log S 3 (log 2 n) Ω(log2 n). Thus, S (log 2 n) Ω(log2 n) = (log n) Ω(log2 n).
RESOLUTION OVER LINEAR EQUATIONS AND MULTILINEAR PROOFS
 RESOLUTION OVER LINEAR EQUATIONS AND MULTILINEAR PROOFS RAN RAZ AND IDDO TZAMERET Abstract. We develop and study the complexity of propositional proof systems of varying strength extending resolution by
RESOLUTION OVER LINEAR EQUATIONS AND MULTILINEAR PROOFS RAN RAZ AND IDDO TZAMERET Abstract. We develop and study the complexity of propositional proof systems of varying strength extending resolution by
Comp487/587 - Boolean Formulas
 Comp487/587 - Boolean Formulas 1 Logic and SAT 1.1 What is a Boolean Formula Logic is a way through which we can analyze and reason about simple or complicated events. In particular, we are interested
Comp487/587 - Boolean Formulas 1 Logic and SAT 1.1 What is a Boolean Formula Logic is a way through which we can analyze and reason about simple or complicated events. In particular, we are interested
arxiv: v1 [cs.cc] 10 Aug 2007
![arxiv: v1 [cs.cc] 10 Aug 2007 arxiv: v1 [cs.cc] 10 Aug 2007](/thumbs/95/123522020.jpg) RESOLUTION OVER LINEAR EQUATIONS AND MULTILINEAR PROOFS RAN RAZ AND IDDO TZAMERET arxiv:0708.1529v1 [cs.cc] 10 Aug 2007 Abstract. We develop and study the complexity of propositional proof systems of varying
RESOLUTION OVER LINEAR EQUATIONS AND MULTILINEAR PROOFS RAN RAZ AND IDDO TZAMERET arxiv:0708.1529v1 [cs.cc] 10 Aug 2007 Abstract. We develop and study the complexity of propositional proof systems of varying
Resolution and the Weak Pigeonhole Principle
 Resolution and the Weak Pigeonhole Principle Sam Buss 1 and Toniann Pitassi 2 1 Departments of Mathematics and Computer Science University of California, San Diego, La Jolla, CA 92093-0112. 2 Department
Resolution and the Weak Pigeonhole Principle Sam Buss 1 and Toniann Pitassi 2 1 Departments of Mathematics and Computer Science University of California, San Diego, La Jolla, CA 92093-0112. 2 Department
Regular Resolution Lower Bounds for the Weak Pigeonhole Principle
 Regular Resolution Lower Bounds for the Weak Pigeonhole Principle Toniann Pitassi Department of Computer Science University of Toronto toni@cs.toronto.edu Ran Raz Department of Computer Science Weizmann
Regular Resolution Lower Bounds for the Weak Pigeonhole Principle Toniann Pitassi Department of Computer Science University of Toronto toni@cs.toronto.edu Ran Raz Department of Computer Science Weizmann
ALGEBRAIC PROOFS OVER NONCOMMUTATIVE FORMULAS
 Electronic Colloquium on Computational Complexity, Report No. 97 (2010) ALGEBRAIC PROOFS OVER NONCOMMUTATIVE FORMULAS IDDO TZAMERET Abstract. We study possible formulations of algebraic propositional proof
Electronic Colloquium on Computational Complexity, Report No. 97 (2010) ALGEBRAIC PROOFS OVER NONCOMMUTATIVE FORMULAS IDDO TZAMERET Abstract. We study possible formulations of algebraic propositional proof
The Strength of Multilinear Proofs
 The Strength of Multilinear Proofs Ran Raz Iddo Tzameret December 19, 2006 Abstract We introduce an algebraic proof system that manipulates multilinear arithmetic formulas. We show that this proof system
The Strength of Multilinear Proofs Ran Raz Iddo Tzameret December 19, 2006 Abstract We introduce an algebraic proof system that manipulates multilinear arithmetic formulas. We show that this proof system
Space complexity of cutting planes refutations
 Space complexity of cutting planes refutations Nicola Galesi, Pavel Pudlák, Neil Thapen Nicola Galesi Sapienza - University of Rome June 19, 2015 () June 19, 2015 1 / 32 Cutting planes proofs A refutational
Space complexity of cutting planes refutations Nicola Galesi, Pavel Pudlák, Neil Thapen Nicola Galesi Sapienza - University of Rome June 19, 2015 () June 19, 2015 1 / 32 Cutting planes proofs A refutational
INSTITUTE OF MATHEMATICS THE CZECH ACADEMY OF SCIENCES. A trade-off between length and width in resolution. Neil Thapen
 INSTITUTE OF MATHEMATICS THE CZECH ACADEMY OF SCIENCES A trade-off between length and width in resolution Neil Thapen Preprint No. 59-2015 PRAHA 2015 A trade-off between length and width in resolution
INSTITUTE OF MATHEMATICS THE CZECH ACADEMY OF SCIENCES A trade-off between length and width in resolution Neil Thapen Preprint No. 59-2015 PRAHA 2015 A trade-off between length and width in resolution
A New 3-CNF Transformation by Parallel-Serial Graphs 1
 A New 3-CNF Transformation by Parallel-Serial Graphs 1 Uwe Bubeck, Hans Kleine Büning University of Paderborn, Computer Science Institute, 33098 Paderborn, Germany Abstract For propositional formulas we
A New 3-CNF Transformation by Parallel-Serial Graphs 1 Uwe Bubeck, Hans Kleine Büning University of Paderborn, Computer Science Institute, 33098 Paderborn, Germany Abstract For propositional formulas we
Resolution Lower Bounds for the Weak Pigeonhole Principle
 Electronic Colloquium on Computational Complexity, Report No. 21 (2001) Resolution Lower Bounds for the Weak Pigeonhole Principle Ran Raz Weizmann Institute, and The Institute for Advanced Study ranraz@wisdom.weizmann.ac.il
Electronic Colloquium on Computational Complexity, Report No. 21 (2001) Resolution Lower Bounds for the Weak Pigeonhole Principle Ran Raz Weizmann Institute, and The Institute for Advanced Study ranraz@wisdom.weizmann.ac.il
On the Automatizability of Resolution and Related Propositional Proof Systems
 On the Automatizability of Resolution and Related Propositional Proof Systems Albert Atserias and María Luisa Bonet Departament de Llenguatges i Sistemes Informàtics Universitat Politècnica de Catalunya
On the Automatizability of Resolution and Related Propositional Proof Systems Albert Atserias and María Luisa Bonet Departament de Llenguatges i Sistemes Informàtics Universitat Politècnica de Catalunya
An Introduction to Proof Complexity, Part II.
 An Introduction to Proof Complexity, Part II. Pavel Pudlák Mathematical Institute, Academy of Sciences, Prague and Charles University, Prague Computability in Europe 2009, Heidelberg 2 Overview Part I.
An Introduction to Proof Complexity, Part II. Pavel Pudlák Mathematical Institute, Academy of Sciences, Prague and Charles University, Prague Computability in Europe 2009, Heidelberg 2 Overview Part I.
Warm-Up Problem. Is the following true or false? 1/35
 Warm-Up Problem Is the following true or false? 1/35 Propositional Logic: Resolution Carmen Bruni Lecture 6 Based on work by J Buss, A Gao, L Kari, A Lubiw, B Bonakdarpour, D Maftuleac, C Roberts, R Trefler,
Warm-Up Problem Is the following true or false? 1/35 Propositional Logic: Resolution Carmen Bruni Lecture 6 Based on work by J Buss, A Gao, L Kari, A Lubiw, B Bonakdarpour, D Maftuleac, C Roberts, R Trefler,
Propositional Logic: Models and Proofs
 Propositional Logic: Models and Proofs C. R. Ramakrishnan CSE 505 1 Syntax 2 Model Theory 3 Proof Theory and Resolution Compiled at 11:51 on 2016/11/02 Computing with Logic Propositional Logic CSE 505
Propositional Logic: Models and Proofs C. R. Ramakrishnan CSE 505 1 Syntax 2 Model Theory 3 Proof Theory and Resolution Compiled at 11:51 on 2016/11/02 Computing with Logic Propositional Logic CSE 505
The NP-hardness of finding a directed acyclic graph for regular resolution
 The NP-hardness of finding a directed acyclic graph for regular resolution Samuel R. Buss Department of Mathematics University of California, San Diego La Jolla, CA 92093-0112, USA sbuss@math.ucsd.edu
The NP-hardness of finding a directed acyclic graph for regular resolution Samuel R. Buss Department of Mathematics University of California, San Diego La Jolla, CA 92093-0112, USA sbuss@math.ucsd.edu
On the Relative Efficiency of DPLL and OBDDs with Axiom and Join
 On the Relative Efficiency of DPLL and OBDDs with Axiom and Join Matti Järvisalo University of Helsinki, Finland September 16, 2011 @ CP M. Järvisalo (U. Helsinki) DPLL and OBDDs September 16, 2011 @ CP
On the Relative Efficiency of DPLL and OBDDs with Axiom and Join Matti Järvisalo University of Helsinki, Finland September 16, 2011 @ CP M. Järvisalo (U. Helsinki) DPLL and OBDDs September 16, 2011 @ CP
Upper and Lower Bounds for Tree-like. Cutting Planes Proofs. Abstract. In this paper we study the complexity of Cutting Planes (CP) refutations, and
 Upper and Lower Bounds for Tree-like Cutting Planes Proofs Russell Impagliazzo Toniann Pitassi y Alasdair Urquhart z UCSD UCSD and U. of Pittsburgh University of Toronto Abstract In this paper we study
Upper and Lower Bounds for Tree-like Cutting Planes Proofs Russell Impagliazzo Toniann Pitassi y Alasdair Urquhart z UCSD UCSD and U. of Pittsburgh University of Toronto Abstract In this paper we study
Computational Logic. Davide Martinenghi. Spring Free University of Bozen-Bolzano. Computational Logic Davide Martinenghi (1/30)
 Computational Logic Davide Martinenghi Free University of Bozen-Bolzano Spring 2010 Computational Logic Davide Martinenghi (1/30) Propositional Logic - sequent calculus To overcome the problems of natural
Computational Logic Davide Martinenghi Free University of Bozen-Bolzano Spring 2010 Computational Logic Davide Martinenghi (1/30) Propositional Logic - sequent calculus To overcome the problems of natural
Critical Reading of Optimization Methods for Logical Inference [1]
![Critical Reading of Optimization Methods for Logical Inference [1] Critical Reading of Optimization Methods for Logical Inference [1]](/thumbs/95/124347829.jpg) Critical Reading of Optimization Methods for Logical Inference [1] Undergraduate Research Internship Department of Management Sciences Fall 2007 Supervisor: Dr. Miguel Anjos UNIVERSITY OF WATERLOO Rajesh
Critical Reading of Optimization Methods for Logical Inference [1] Undergraduate Research Internship Department of Management Sciences Fall 2007 Supervisor: Dr. Miguel Anjos UNIVERSITY OF WATERLOO Rajesh
On extracting computations from propositional proofs (a survey)
 On extracting computations from propositional proofs (a survey) Pavel Pudlák September 16, 2010 Abstract This paper describes a project that aims at showing that propositional proofs of certain tautologies
On extracting computations from propositional proofs (a survey) Pavel Pudlák September 16, 2010 Abstract This paper describes a project that aims at showing that propositional proofs of certain tautologies
Propositional Logic Language
 Propositional Logic Language A logic consists of: an alphabet A, a language L, i.e., a set of formulas, and a binary relation = between a set of formulas and a formula. An alphabet A consists of a finite
Propositional Logic Language A logic consists of: an alphabet A, a language L, i.e., a set of formulas, and a binary relation = between a set of formulas and a formula. An alphabet A consists of a finite
Bounded-width QBF is PSPACE-complete
 Bounded-width QBF is PSPACE-complete Albert Atserias Universitat Politècnica de Catalunya Barcelona, Spain atserias@lsi.upc.edu Sergi Oliva Universitat Politècnica de Catalunya Barcelona, Spain oliva@lsi.upc.edu
Bounded-width QBF is PSPACE-complete Albert Atserias Universitat Politècnica de Catalunya Barcelona, Spain atserias@lsi.upc.edu Sergi Oliva Universitat Politècnica de Catalunya Barcelona, Spain oliva@lsi.upc.edu
Algorithms for Satisfiability beyond Resolution.
 Algorithms for Satisfiability beyond Resolution. Maria Luisa Bonet UPC, Barcelona, Spain Oaxaca, August, 2018 Co-Authors: Sam Buss, Alexey Ignatiev, Joao Marques-Silva, Antonio Morgado. Motivation. Satisfiability
Algorithms for Satisfiability beyond Resolution. Maria Luisa Bonet UPC, Barcelona, Spain Oaxaca, August, 2018 Co-Authors: Sam Buss, Alexey Ignatiev, Joao Marques-Silva, Antonio Morgado. Motivation. Satisfiability
Organization. Informal introduction and Overview Informal introductions to P,NP,co-NP and themes from and relationships with Proof complexity
 15-16/08/2009 Nicola Galesi 1 Organization Informal introduction and Overview Informal introductions to P,NP,co-NP and themes from and relationships with Proof complexity First Steps in Proof Complexity
15-16/08/2009 Nicola Galesi 1 Organization Informal introduction and Overview Informal introductions to P,NP,co-NP and themes from and relationships with Proof complexity First Steps in Proof Complexity
On Transformations of Constant Depth Propositional Proofs
 On Transformations of Constant Depth Propositional Proofs Submitted for publication. Feedback appreciated. Arnold Beckmann Department of Computer Science College of Science Swansea University Swansea SA2
On Transformations of Constant Depth Propositional Proofs Submitted for publication. Feedback appreciated. Arnold Beckmann Department of Computer Science College of Science Swansea University Swansea SA2
Lecture #14: NP-Completeness (Chapter 34 Old Edition Chapter 36) Discussion here is from the old edition.
 Lecture #14: 0.0.1 NP-Completeness (Chapter 34 Old Edition Chapter 36) Discussion here is from the old edition. 0.0.2 Preliminaries: Definition 1 n abstract problem Q is a binary relations on a set I of
Lecture #14: 0.0.1 NP-Completeness (Chapter 34 Old Edition Chapter 36) Discussion here is from the old edition. 0.0.2 Preliminaries: Definition 1 n abstract problem Q is a binary relations on a set I of
CSC 2429 Approaches to the P vs. NP Question and Related Complexity Questions Lecture 2: Switching Lemma, AC 0 Circuit Lower Bounds
 CSC 2429 Approaches to the P vs. NP Question and Related Complexity Questions Lecture 2: Switching Lemma, AC 0 Circuit Lower Bounds Lecturer: Toniann Pitassi Scribe: Robert Robere Winter 2014 1 Switching
CSC 2429 Approaches to the P vs. NP Question and Related Complexity Questions Lecture 2: Switching Lemma, AC 0 Circuit Lower Bounds Lecturer: Toniann Pitassi Scribe: Robert Robere Winter 2014 1 Switching
Part 1: Propositional Logic
 Part 1: Propositional Logic Literature (also for first-order logic) Schöning: Logik für Informatiker, Spektrum Fitting: First-Order Logic and Automated Theorem Proving, Springer 1 Last time 1.1 Syntax
Part 1: Propositional Logic Literature (also for first-order logic) Schöning: Logik für Informatiker, Spektrum Fitting: First-Order Logic and Automated Theorem Proving, Springer 1 Last time 1.1 Syntax
Resolution and Pebbling Games
 Resolution and Pebbling Games Nicola Galesi and Neil Thapen Abstract. We define a collection of Prover-Delayer games to characterise some subsystems of propositional resolution. We give some natural criteria
Resolution and Pebbling Games Nicola Galesi and Neil Thapen Abstract. We define a collection of Prover-Delayer games to characterise some subsystems of propositional resolution. We give some natural criteria
Complexity Theory VU , SS The Polynomial Hierarchy. Reinhard Pichler
 Complexity Theory Complexity Theory VU 181.142, SS 2018 6. The Polynomial Hierarchy Reinhard Pichler Institut für Informationssysteme Arbeitsbereich DBAI Technische Universität Wien 15 May, 2018 Reinhard
Complexity Theory Complexity Theory VU 181.142, SS 2018 6. The Polynomial Hierarchy Reinhard Pichler Institut für Informationssysteme Arbeitsbereich DBAI Technische Universität Wien 15 May, 2018 Reinhard
Outline. Complexity Theory EXACT TSP. The Class DP. Definition. Problem EXACT TSP. Complexity of EXACT TSP. Proposition VU 181.
 Complexity Theory Complexity Theory Outline Complexity Theory VU 181.142, SS 2018 6. The Polynomial Hierarchy Reinhard Pichler Institut für Informationssysteme Arbeitsbereich DBAI Technische Universität
Complexity Theory Complexity Theory Outline Complexity Theory VU 181.142, SS 2018 6. The Polynomial Hierarchy Reinhard Pichler Institut für Informationssysteme Arbeitsbereich DBAI Technische Universität
A Collection of Problems in Propositional Logic
 A Collection of Problems in Propositional Logic Hans Kleine Büning SS 2016 Problem 1: SAT (respectively SAT) Instance: A propositional formula α (for SAT in CNF). Question: Is α satisfiable? The problems
A Collection of Problems in Propositional Logic Hans Kleine Büning SS 2016 Problem 1: SAT (respectively SAT) Instance: A propositional formula α (for SAT in CNF). Question: Is α satisfiable? The problems
LOGIC PROPOSITIONAL REASONING
 LOGIC PROPOSITIONAL REASONING WS 2017/2018 (342.208) Armin Biere Martina Seidl biere@jku.at martina.seidl@jku.at Institute for Formal Models and Verification Johannes Kepler Universität Linz Version 2018.1
LOGIC PROPOSITIONAL REASONING WS 2017/2018 (342.208) Armin Biere Martina Seidl biere@jku.at martina.seidl@jku.at Institute for Formal Models and Verification Johannes Kepler Universität Linz Version 2018.1
CS Introduction to Complexity Theory. Lecture #11: Dec 8th, 2015
 CS 2401 - Introduction to Complexity Theory Lecture #11: Dec 8th, 2015 Lecturer: Toniann Pitassi Scribe Notes by: Xu Zhao 1 Communication Complexity Applications Communication Complexity (CC) has many
CS 2401 - Introduction to Complexity Theory Lecture #11: Dec 8th, 2015 Lecturer: Toniann Pitassi Scribe Notes by: Xu Zhao 1 Communication Complexity Applications Communication Complexity (CC) has many
Reduced Ordered Binary Decision Diagrams
 Reduced Ordered Binary Decision Diagrams Lecture #12 of Advanced Model Checking Joost-Pieter Katoen Lehrstuhl 2: Software Modeling & Verification E-mail: katoen@cs.rwth-aachen.de December 13, 2016 c JPK
Reduced Ordered Binary Decision Diagrams Lecture #12 of Advanced Model Checking Joost-Pieter Katoen Lehrstuhl 2: Software Modeling & Verification E-mail: katoen@cs.rwth-aachen.de December 13, 2016 c JPK
A Resolution Method for Modal Logic S5
 EPiC Series in Computer Science Volume 36, 2015, Pages 252 262 GCAI 2015. Global Conference on Artificial Intelligence A Resolution Method for Modal Logic S5 Yakoub Salhi and Michael Sioutis Université
EPiC Series in Computer Science Volume 36, 2015, Pages 252 262 GCAI 2015. Global Conference on Artificial Intelligence A Resolution Method for Modal Logic S5 Yakoub Salhi and Michael Sioutis Université
Show that the following problems are NP-complete
 Show that the following problems are NP-complete April 7, 2018 Below is a list of 30 exercises in which you are asked to prove that some problem is NP-complete. The goal is to better understand the theory
Show that the following problems are NP-complete April 7, 2018 Below is a list of 30 exercises in which you are asked to prove that some problem is NP-complete. The goal is to better understand the theory
NP-COMPLETE PROBLEMS. 1. Characterizing NP. Proof
 T-79.5103 / Autumn 2006 NP-complete problems 1 NP-COMPLETE PROBLEMS Characterizing NP Variants of satisfiability Graph-theoretic problems Coloring problems Sets and numbers Pseudopolynomial algorithms
T-79.5103 / Autumn 2006 NP-complete problems 1 NP-COMPLETE PROBLEMS Characterizing NP Variants of satisfiability Graph-theoretic problems Coloring problems Sets and numbers Pseudopolynomial algorithms
PROPOSITIONAL LOGIC. VL Logik: WS 2018/19
 PROPOSITIONAL LOGIC VL Logik: WS 2018/19 (Version 2018.2) Martina Seidl (martina.seidl@jku.at), Armin Biere (biere@jku.at) Institut für Formale Modelle und Verifikation BOX Game: Rules 1. The game board
PROPOSITIONAL LOGIC VL Logik: WS 2018/19 (Version 2018.2) Martina Seidl (martina.seidl@jku.at), Armin Biere (biere@jku.at) Institut für Formale Modelle und Verifikation BOX Game: Rules 1. The game board
Complexity of propositional proofs: Some theory and examples
 Complexity of propositional proofs: Some theory and examples Univ. of California, San Diego Barcelona April 27, 2015 Frege proofs Introduction Frege proofs Pigeonhole principle Frege proofs are the usual
Complexity of propositional proofs: Some theory and examples Univ. of California, San Diego Barcelona April 27, 2015 Frege proofs Introduction Frege proofs Pigeonhole principle Frege proofs are the usual
Lower Bounds for Cutting Planes Proofs. with Small Coecients. Abstract. We consider small-weight Cutting Planes (CP ) proofs; that is,
 Lower Bounds for Cutting Planes Proofs with Small Coecients Maria Bonet y Toniann Pitassi z Ran Raz x Abstract We consider small-weight Cutting Planes (CP ) proofs; that is, Cutting Planes (CP ) proofs
Lower Bounds for Cutting Planes Proofs with Small Coecients Maria Bonet y Toniann Pitassi z Ran Raz x Abstract We consider small-weight Cutting Planes (CP ) proofs; that is, Cutting Planes (CP ) proofs
Tecniche di Verifica. Introduction to Propositional Logic
 Tecniche di Verifica Introduction to Propositional Logic 1 Logic A formal logic is defined by its syntax and semantics. Syntax An alphabet is a set of symbols. A finite sequence of these symbols is called
Tecniche di Verifica Introduction to Propositional Logic 1 Logic A formal logic is defined by its syntax and semantics. Syntax An alphabet is a set of symbols. A finite sequence of these symbols is called
Basing Decisions on Sentences in Decision Diagrams
 Proceedings of the Twenty-Sixth AAAI Conference on Artificial Intelligence Basing Decisions on Sentences in Decision Diagrams Yexiang Xue Department of Computer Science Cornell University yexiang@cs.cornell.edu
Proceedings of the Twenty-Sixth AAAI Conference on Artificial Intelligence Basing Decisions on Sentences in Decision Diagrams Yexiang Xue Department of Computer Science Cornell University yexiang@cs.cornell.edu
Propositional and Predicate Logic - V
 Propositional and Predicate Logic - V Petr Gregor KTIML MFF UK WS 2016/2017 Petr Gregor (KTIML MFF UK) Propositional and Predicate Logic - V WS 2016/2017 1 / 21 Formal proof systems Hilbert s calculus
Propositional and Predicate Logic - V Petr Gregor KTIML MFF UK WS 2016/2017 Petr Gregor (KTIML MFF UK) Propositional and Predicate Logic - V WS 2016/2017 1 / 21 Formal proof systems Hilbert s calculus
On the Complexity of the Reflected Logic of Proofs
 On the Complexity of the Reflected Logic of Proofs Nikolai V. Krupski Department of Math. Logic and the Theory of Algorithms, Faculty of Mechanics and Mathematics, Moscow State University, Moscow 119899,
On the Complexity of the Reflected Logic of Proofs Nikolai V. Krupski Department of Math. Logic and the Theory of Algorithms, Faculty of Mechanics and Mathematics, Moscow State University, Moscow 119899,
A note on monotone real circuits
 A note on monotone real circuits Pavel Hrubeš and Pavel Pudlák March 14, 2017 Abstract We show that if a Boolean function f : {0, 1} n {0, 1} can be computed by a monotone real circuit of size s using
A note on monotone real circuits Pavel Hrubeš and Pavel Pudlák March 14, 2017 Abstract We show that if a Boolean function f : {0, 1} n {0, 1} can be computed by a monotone real circuit of size s using
Solvers for the Problem of Boolean Satisfiability (SAT) Will Klieber Aug 31, 2011
 Solvers for the Problem of Boolean Satisfiability (SAT) Will Klieber 15-414 Aug 31, 2011 Why study SAT solvers? Many problems reduce to SAT. Formal verification CAD, VLSI Optimization AI, planning, automated
Solvers for the Problem of Boolean Satisfiability (SAT) Will Klieber 15-414 Aug 31, 2011 Why study SAT solvers? Many problems reduce to SAT. Formal verification CAD, VLSI Optimization AI, planning, automated
Propositional Logic: Evaluating the Formulas
 Institute for Formal Models and Verification Johannes Kepler University Linz VL Logik (LVA-Nr. 342208) Winter Semester 2015/2016 Propositional Logic: Evaluating the Formulas Version 2015.2 Armin Biere
Institute for Formal Models and Verification Johannes Kepler University Linz VL Logik (LVA-Nr. 342208) Winter Semester 2015/2016 Propositional Logic: Evaluating the Formulas Version 2015.2 Armin Biere
Essential facts about NP-completeness:
 CMPSCI611: NP Completeness Lecture 17 Essential facts about NP-completeness: Any NP-complete problem can be solved by a simple, but exponentially slow algorithm. We don t have polynomial-time solutions
CMPSCI611: NP Completeness Lecture 17 Essential facts about NP-completeness: Any NP-complete problem can be solved by a simple, but exponentially slow algorithm. We don t have polynomial-time solutions
Reckhow s Theorem. Yuval Filmus. November 2010
 Reckhow s Theorem Yuval Filmus November 2010 1 Introduction In 5.3.1 of his thesis [2], Reckhow showed that any two Frege systems p-simulate each other. One of the difficulties involves translation of
Reckhow s Theorem Yuval Filmus November 2010 1 Introduction In 5.3.1 of his thesis [2], Reckhow showed that any two Frege systems p-simulate each other. One of the difficulties involves translation of
Propositional Logic. Methods & Tools for Software Engineering (MTSE) Fall Prof. Arie Gurfinkel
 Propositional Logic Methods & Tools for Software Engineering (MTSE) Fall 2017 Prof. Arie Gurfinkel References Chpater 1 of Logic for Computer Scientists http://www.springerlink.com/content/978-0-8176-4762-9/
Propositional Logic Methods & Tools for Software Engineering (MTSE) Fall 2017 Prof. Arie Gurfinkel References Chpater 1 of Logic for Computer Scientists http://www.springerlink.com/content/978-0-8176-4762-9/
PCPs and Inapproximability Gap-producing and Gap-Preserving Reductions. My T. Thai
 PCPs and Inapproximability Gap-producing and Gap-Preserving Reductions My T. Thai 1 1 Hardness of Approximation Consider a maximization problem Π such as MAX-E3SAT. To show that it is NP-hard to approximation
PCPs and Inapproximability Gap-producing and Gap-Preserving Reductions My T. Thai 1 1 Hardness of Approximation Consider a maximization problem Π such as MAX-E3SAT. To show that it is NP-hard to approximation
Chapter 2. Reductions and NP. 2.1 Reductions Continued The Satisfiability Problem (SAT) SAT 3SAT. CS 573: Algorithms, Fall 2013 August 29, 2013
 Chapter 2 Reductions and NP CS 573: Algorithms, Fall 2013 August 29, 2013 2.1 Reductions Continued 2.1.1 The Satisfiability Problem SAT 2.1.1.1 Propositional Formulas Definition 2.1.1. Consider a set of
Chapter 2 Reductions and NP CS 573: Algorithms, Fall 2013 August 29, 2013 2.1 Reductions Continued 2.1.1 The Satisfiability Problem SAT 2.1.1.1 Propositional Formulas Definition 2.1.1. Consider a set of
Propositional Logic. Testing, Quality Assurance, and Maintenance Winter Prof. Arie Gurfinkel
 Propositional Logic Testing, Quality Assurance, and Maintenance Winter 2018 Prof. Arie Gurfinkel References Chpater 1 of Logic for Computer Scientists http://www.springerlink.com/content/978-0-8176-4762-9/
Propositional Logic Testing, Quality Assurance, and Maintenance Winter 2018 Prof. Arie Gurfinkel References Chpater 1 of Logic for Computer Scientists http://www.springerlink.com/content/978-0-8176-4762-9/
NP and NP-Completeness
 CSC 364S Notes University of Toronto, Spring, 2003 NP NP and NP-Completeness NP is a class of languages that contains all of P, but which most people think also contains many languages that aren t in P.
CSC 364S Notes University of Toronto, Spring, 2003 NP NP and NP-Completeness NP is a class of languages that contains all of P, but which most people think also contains many languages that aren t in P.
MINI-TUTORIAL ON SEMI-ALGEBRAIC PROOF SYSTEMS. Albert Atserias Universitat Politècnica de Catalunya Barcelona
 MINI-TUTORIAL ON SEMI-ALGEBRAIC PROOF SYSTEMS Albert Atserias Universitat Politècnica de Catalunya Barcelona Part I CONVEX POLYTOPES Convex polytopes as linear inequalities Polytope: P = {x R n : Ax b}
MINI-TUTORIAL ON SEMI-ALGEBRAIC PROOF SYSTEMS Albert Atserias Universitat Politècnica de Catalunya Barcelona Part I CONVEX POLYTOPES Convex polytopes as linear inequalities Polytope: P = {x R n : Ax b}
Proof Complexity of Intuitionistic Propositional Logic
 Proof Complexity of Intuitionistic Propositional Logic Alexander Hertel & Alasdair Urquhart November 29, 2006 Abstract We explore the proof complexity of intuitionistic propositional logic (IP L) The problem
Proof Complexity of Intuitionistic Propositional Logic Alexander Hertel & Alasdair Urquhart November 29, 2006 Abstract We explore the proof complexity of intuitionistic propositional logic (IP L) The problem
COMPLEXITY OF SEMIALGEBRAIC PROOFS
 MOSCOW MATHEMATICAL JOURNAL Volume 2, Number 4, October December 2002, Pages 647 679 COMPLEXITY OF SEMIALGEBRAIC PROOFS DIMA GRIGORIEV, EDWARD A. HIRSCH, AND DMITRII V. PASECHNIK Dedicated to Yuri I. Manin
MOSCOW MATHEMATICAL JOURNAL Volume 2, Number 4, October December 2002, Pages 647 679 COMPLEXITY OF SEMIALGEBRAIC PROOFS DIMA GRIGORIEV, EDWARD A. HIRSCH, AND DMITRII V. PASECHNIK Dedicated to Yuri I. Manin
Chapter 3 Deterministic planning
 Chapter 3 Deterministic planning In this chapter we describe a number of algorithms for solving the historically most important and most basic type of planning problem. Two rather strong simplifying assumptions
Chapter 3 Deterministic planning In this chapter we describe a number of algorithms for solving the historically most important and most basic type of planning problem. Two rather strong simplifying assumptions
Representations of Monotone Boolean Functions by Linear Programs
 Electronic Colloquium on Computational Complexity, Report No. 106 (2017) Representations of Monotone Boolean Functions by Linear Programs Mateus de Oliveira Oliveira and Pavel Pudlák April 10, 2017 Abstract
Electronic Colloquium on Computational Complexity, Report No. 106 (2017) Representations of Monotone Boolean Functions by Linear Programs Mateus de Oliveira Oliveira and Pavel Pudlák April 10, 2017 Abstract
1 Circuit Complexity. CS 6743 Lecture 15 1 Fall Definitions
 CS 6743 Lecture 15 1 Fall 2007 1 Circuit Complexity 1.1 Definitions A Boolean circuit C on n inputs x 1,..., x n is a directed acyclic graph (DAG) with n nodes of in-degree 0 (the inputs x 1,..., x n ),
CS 6743 Lecture 15 1 Fall 2007 1 Circuit Complexity 1.1 Definitions A Boolean circuit C on n inputs x 1,..., x n is a directed acyclic graph (DAG) with n nodes of in-degree 0 (the inputs x 1,..., x n ),
From Small Space to Small Width in Resolution
 From Small Space to Small Width in Resolution Yuval Filmus 1, Massimo Lauria 2, Mladen Mikša 2, Jakob Nordström 2, and Marc Vinyals 2 1 Simons Institute for the Theory of Computing, University of California,
From Small Space to Small Width in Resolution Yuval Filmus 1, Massimo Lauria 2, Mladen Mikša 2, Jakob Nordström 2, and Marc Vinyals 2 1 Simons Institute for the Theory of Computing, University of California,
Introduction. 1 Partially supported by a grant from The John Templeton Foundation
 Nisan-Wigderson generators in proof systems with forms of interpolation Ján Pich 1 Faculty of Mathematics and Physics Charles University in Prague March, 2010 We prove that the Nisan-Wigderson generators
Nisan-Wigderson generators in proof systems with forms of interpolation Ján Pich 1 Faculty of Mathematics and Physics Charles University in Prague March, 2010 We prove that the Nisan-Wigderson generators
Conjunctive Normal Form and SAT
 Notes on Satisfiability-Based Problem Solving Conjunctive Normal Form and SAT David Mitchell mitchell@cs.sfu.ca October 4, 2015 These notes are a preliminary draft. Please use freely, but do not re-distribute
Notes on Satisfiability-Based Problem Solving Conjunctive Normal Form and SAT David Mitchell mitchell@cs.sfu.ca October 4, 2015 These notes are a preliminary draft. Please use freely, but do not re-distribute
Learning implicitly in reasoning in PAC-Semantics
 Learning implicitly in reasoning in PAC-Semantics Brendan Juba MIT CSAIL and Harvard SEAS bjuba@alum.mit.edu Abstract We consider the problem of answering queries about formulas of propositional logic
Learning implicitly in reasoning in PAC-Semantics Brendan Juba MIT CSAIL and Harvard SEAS bjuba@alum.mit.edu Abstract We consider the problem of answering queries about formulas of propositional logic
1 Efficient Transformation to CNF Formulas
 1 Efficient Transformation to CNF Formulas We discuss an algorithm, due to Tseitin [?], which efficiently transforms an arbitrary Boolean formula φ to a CNF formula ψ such that ψ has a model if and only
1 Efficient Transformation to CNF Formulas We discuss an algorithm, due to Tseitin [?], which efficiently transforms an arbitrary Boolean formula φ to a CNF formula ψ such that ψ has a model if and only
Decision Procedures for Satisfiability and Validity in Propositional Logic
 Decision Procedures for Satisfiability and Validity in Propositional Logic Meghdad Ghari Institute for Research in Fundamental Sciences (IPM) School of Mathematics-Isfahan Branch Logic Group http://math.ipm.ac.ir/isfahan/logic-group.htm
Decision Procedures for Satisfiability and Validity in Propositional Logic Meghdad Ghari Institute for Research in Fundamental Sciences (IPM) School of Mathematics-Isfahan Branch Logic Group http://math.ipm.ac.ir/isfahan/logic-group.htm
INSTITUTE OF MATHEMATICS THE CZECH ACADEMY OF SCIENCES. Random resolution refutations. Pavel Pudlák Neil Thapen
 INSTITUTE OF MATHEMATICS THE CZECH ACADEMY OF SCIENCES Random resolution refutations Pavel Pudlák Neil Thapen Preprint No. 40-2016 PRAHA 2016 Random resolution refutations Pavel Pudlák and Neil Thapen
INSTITUTE OF MATHEMATICS THE CZECH ACADEMY OF SCIENCES Random resolution refutations Pavel Pudlák Neil Thapen Preprint No. 40-2016 PRAHA 2016 Random resolution refutations Pavel Pudlák and Neil Thapen
Branching. Teppo Niinimäki. Helsinki October 14, 2011 Seminar: Exact Exponential Algorithms UNIVERSITY OF HELSINKI Department of Computer Science
 Branching Teppo Niinimäki Helsinki October 14, 2011 Seminar: Exact Exponential Algorithms UNIVERSITY OF HELSINKI Department of Computer Science 1 For a large number of important computational problems
Branching Teppo Niinimäki Helsinki October 14, 2011 Seminar: Exact Exponential Algorithms UNIVERSITY OF HELSINKI Department of Computer Science 1 For a large number of important computational problems
Part V. Intractable Problems
 Part V Intractable Problems 507 Chapter 16 N P-Completeness Up to now, we have focused on developing efficient algorithms for solving problems. The word efficient is somewhat subjective, and the degree
Part V Intractable Problems 507 Chapter 16 N P-Completeness Up to now, we have focused on developing efficient algorithms for solving problems. The word efficient is somewhat subjective, and the degree
THE RESOLUTION COMPLEXITY OF INDEPENDENT SETS AND VERTEX COVERS IN RANDOM GRAPHS
 THE RESOLUTION COMPLEXITY OF INDEPENDENT SETS AND VERTEX COVERS IN RANDOM GRAPHS Paul Beame, Russell Impagliazzo, and Ashish Sabharwal Abstract. We consider the problem of providing a resolution proof
THE RESOLUTION COMPLEXITY OF INDEPENDENT SETS AND VERTEX COVERS IN RANDOM GRAPHS Paul Beame, Russell Impagliazzo, and Ashish Sabharwal Abstract. We consider the problem of providing a resolution proof
Propositional and Predicate Logic - II
 Propositional and Predicate Logic - II Petr Gregor KTIML MFF UK WS 2016/2017 Petr Gregor (KTIML MFF UK) Propositional and Predicate Logic - II WS 2016/2017 1 / 16 Basic syntax Language Propositional logic
Propositional and Predicate Logic - II Petr Gregor KTIML MFF UK WS 2016/2017 Petr Gregor (KTIML MFF UK) Propositional and Predicate Logic - II WS 2016/2017 1 / 16 Basic syntax Language Propositional logic
Quantified Boolean Formulas: Complexity and Expressiveness
 Dagstuhl SAT Interactions 2012 Quantified Boolean Formulas: Complexity and Expressiveness Uwe Bubeck University of Paderborn 20.11.2012 Outline Introduction Free Variables and Equivalence Complexity Expressiveness
Dagstuhl SAT Interactions 2012 Quantified Boolean Formulas: Complexity and Expressiveness Uwe Bubeck University of Paderborn 20.11.2012 Outline Introduction Free Variables and Equivalence Complexity Expressiveness
3 Propositional Logic
 3 Propositional Logic 3.1 Syntax 3.2 Semantics 3.3 Equivalence and Normal Forms 3.4 Proof Procedures 3.5 Properties Propositional Logic (25th October 2007) 1 3.1 Syntax Definition 3.0 An alphabet Σ consists
3 Propositional Logic 3.1 Syntax 3.2 Semantics 3.3 Equivalence and Normal Forms 3.4 Proof Procedures 3.5 Properties Propositional Logic (25th October 2007) 1 3.1 Syntax Definition 3.0 An alphabet Σ consists
Toda s theorem in bounded arithmetic with parity quantifiers and bounded depth proof systems with parity gates
 1 / 17 Toda s theorem in bounded arithmetic with parity quantifiers and bounded depth proof systems with parity gates Leszek Kołodziejczyk University of Warsaw/UCSD (joint work with Sam Buss and Konrad
1 / 17 Toda s theorem in bounded arithmetic with parity quantifiers and bounded depth proof systems with parity gates Leszek Kołodziejczyk University of Warsaw/UCSD (joint work with Sam Buss and Konrad
SAT Solvers: Theory and Practice
 Summer School on Verification Technology, Systems & Applications, September 17, 2008 p. 1/98 SAT Solvers: Theory and Practice Clark Barrett barrett@cs.nyu.edu New York University Summer School on Verification
Summer School on Verification Technology, Systems & Applications, September 17, 2008 p. 1/98 SAT Solvers: Theory and Practice Clark Barrett barrett@cs.nyu.edu New York University Summer School on Verification
Propositional and Predicate Logic. jean/gbooks/logic.html
 CMSC 630 February 10, 2009 1 Propositional and Predicate Logic Sources J. Gallier. Logic for Computer Science, John Wiley and Sons, Hoboken NJ, 1986. 2003 revised edition available on line at http://www.cis.upenn.edu/
CMSC 630 February 10, 2009 1 Propositional and Predicate Logic Sources J. Gallier. Logic for Computer Science, John Wiley and Sons, Hoboken NJ, 1986. 2003 revised edition available on line at http://www.cis.upenn.edu/
CS6840: Advanced Complexity Theory Mar 29, Lecturer: Jayalal Sarma M.N. Scribe: Dinesh K.
 CS684: Advanced Complexity Theory Mar 29, 22 Lecture 46 : Size lower bounds for AC circuits computing Parity Lecturer: Jayalal Sarma M.N. Scribe: Dinesh K. Theme: Circuit Complexity Lecture Plan: Proof
CS684: Advanced Complexity Theory Mar 29, 22 Lecture 46 : Size lower bounds for AC circuits computing Parity Lecturer: Jayalal Sarma M.N. Scribe: Dinesh K. Theme: Circuit Complexity Lecture Plan: Proof
Critical Reading of Optimization Methods for Logical Inference [1]
![Critical Reading of Optimization Methods for Logical Inference [1] Critical Reading of Optimization Methods for Logical Inference [1]](/thumbs/95/124347778.jpg) Critical Reading of Optimization Methods for Logical Inference [1] Undergraduate Research Internship Department of Management Sciences Winter 2008 Supervisor: Dr. Miguel Anjos UNIVERSITY OF WATERLOO Rajesh
Critical Reading of Optimization Methods for Logical Inference [1] Undergraduate Research Internship Department of Management Sciences Winter 2008 Supervisor: Dr. Miguel Anjos UNIVERSITY OF WATERLOO Rajesh
Expander Construction in VNC 1
 Expander Construction in VNC 1 Sam Buss joint work with Valentine Kabanets, Antonina Kolokolova & Michal Koucký Prague Workshop on Bounded Arithmetic November 2-3, 2017 Talk outline I. Combinatorial construction
Expander Construction in VNC 1 Sam Buss joint work with Valentine Kabanets, Antonina Kolokolova & Michal Koucký Prague Workshop on Bounded Arithmetic November 2-3, 2017 Talk outline I. Combinatorial construction
Semantic versus syntactic cutting planes
 Semantic versus syntactic cutting planes Yuval Filmus 1, Pavel Hrubeš 2, and Massimo Lauria 3 1 Institute for Advanced Study Princeton, NJ yfilmus@ias.edu 2 Institute of Mathematics of ASCR Prague, Czech
Semantic versus syntactic cutting planes Yuval Filmus 1, Pavel Hrubeš 2, and Massimo Lauria 3 1 Institute for Advanced Study Princeton, NJ yfilmus@ias.edu 2 Institute of Mathematics of ASCR Prague, Czech
Lower bounds for width-restricted clause learning on small width formulas
 Electronic Colloquium on Computational Complexity, Report No. 85 (2010) Lower bounds for width-restricted clause learning on small width formulas Eli Ben-Sasson 1 and Jan Johannsen 2 1 Computer Science
Electronic Colloquium on Computational Complexity, Report No. 85 (2010) Lower bounds for width-restricted clause learning on small width formulas Eli Ben-Sasson 1 and Jan Johannsen 2 1 Computer Science
CSE200: Computability and complexity Space Complexity
 CSE200: Computability and complexity Space Complexity Shachar Lovett January 29, 2018 1 Space complexity We would like to discuss languages that may be determined in sub-linear space. Lets first recall
CSE200: Computability and complexity Space Complexity Shachar Lovett January 29, 2018 1 Space complexity We would like to discuss languages that may be determined in sub-linear space. Lets first recall
I. Introduction to NP Functions and Local Search
 I. Introduction to NP Functions and Local Search (UCSD) sbuss@math.ucsd.edu Prague, September 2009 NP Functions TFNP [JPY 88, Papadimitriou 94]. Definition TFNP, the class of Total NP Functions is the
I. Introduction to NP Functions and Local Search (UCSD) sbuss@math.ucsd.edu Prague, September 2009 NP Functions TFNP [JPY 88, Papadimitriou 94]. Definition TFNP, the class of Total NP Functions is the
Clause/Term Resolution and Learning in the Evaluation of Quantified Boolean Formulas
 Journal of Artificial Intelligence Research 1 (1993) 1-15 Submitted 6/91; published 9/91 Clause/Term Resolution and Learning in the Evaluation of Quantified Boolean Formulas Enrico Giunchiglia Massimo
Journal of Artificial Intelligence Research 1 (1993) 1-15 Submitted 6/91; published 9/91 Clause/Term Resolution and Learning in the Evaluation of Quantified Boolean Formulas Enrico Giunchiglia Massimo
Resolution for mixed Post logic
 Resolution for mixed Post logic Vladimir Komendantsky Institute of Philosophy of Russian Academy of Science, Volkhonka 14, 119992 Moscow, Russia vycom@pochtamt.ru Abstract. In this paper we present a resolution
Resolution for mixed Post logic Vladimir Komendantsky Institute of Philosophy of Russian Academy of Science, Volkhonka 14, 119992 Moscow, Russia vycom@pochtamt.ru Abstract. In this paper we present a resolution
A brief introduction to Logic. (slides from
 A brief introduction to Logic (slides from http://www.decision-procedures.org/) 1 A Brief Introduction to Logic - Outline Propositional Logic :Syntax Propositional Logic :Semantics Satisfiability and validity
A brief introduction to Logic (slides from http://www.decision-procedures.org/) 1 A Brief Introduction to Logic - Outline Propositional Logic :Syntax Propositional Logic :Semantics Satisfiability and validity
Tuples of Disjoint NP-Sets
 Tuples of Disjoint NP-Sets (Extended Abstract) Olaf Beyersdorff Institut für Informatik, Humboldt-Universität zu Berlin, 10099 Berlin, Germany beyersdo@informatik.hu-berlin.de Abstract. Disjoint NP-pairs
Tuples of Disjoint NP-Sets (Extended Abstract) Olaf Beyersdorff Institut für Informatik, Humboldt-Universität zu Berlin, 10099 Berlin, Germany beyersdo@informatik.hu-berlin.de Abstract. Disjoint NP-pairs
UC Berkeley CS 170: Efficient Algorithms and Intractable Problems Handout 22 Lecturer: David Wagner April 24, Notes 22 for CS 170
 UC Berkeley CS 170: Efficient Algorithms and Intractable Problems Handout 22 Lecturer: David Wagner April 24, 2003 Notes 22 for CS 170 1 NP-completeness of Circuit-SAT We will prove that the circuit satisfiability
UC Berkeley CS 170: Efficient Algorithms and Intractable Problems Handout 22 Lecturer: David Wagner April 24, 2003 Notes 22 for CS 170 1 NP-completeness of Circuit-SAT We will prove that the circuit satisfiability
CS 512, Spring 2017, Handout 10 Propositional Logic: Conjunctive Normal Forms, Disjunctive Normal Forms, Horn Formulas, and other special forms
 CS 512, Spring 2017, Handout 10 Propositional Logic: Conjunctive Normal Forms, Disjunctive Normal Forms, Horn Formulas, and other special forms Assaf Kfoury 5 February 2017 Assaf Kfoury, CS 512, Spring
CS 512, Spring 2017, Handout 10 Propositional Logic: Conjunctive Normal Forms, Disjunctive Normal Forms, Horn Formulas, and other special forms Assaf Kfoury 5 February 2017 Assaf Kfoury, CS 512, Spring
Boolean decision diagrams and SAT-based representations
 Boolean decision diagrams and SAT-based representations 4th July 200 So far we have seen Kripke Structures 2 Temporal logics (and their semantics over Kripke structures) 3 Model checking of these structures
Boolean decision diagrams and SAT-based representations 4th July 200 So far we have seen Kripke Structures 2 Temporal logics (and their semantics over Kripke structures) 3 Model checking of these structures
A New Look at BDDs for Pseudo-Boolean Constraints
 Journal of Artificial Intelligence Research 45 (22) 443-48 Submitted 3/2; published /2 A New Look at BDDs for Pseudo-Boolean Constraints Ignasi Abío Robert Nieuwenhuis Albert Oliveras Enric Rodríguez-Carbonell
Journal of Artificial Intelligence Research 45 (22) 443-48 Submitted 3/2; published /2 A New Look at BDDs for Pseudo-Boolean Constraints Ignasi Abío Robert Nieuwenhuis Albert Oliveras Enric Rodríguez-Carbonell
The Complexity of Computing the Behaviour of Lattice Automata on Infinite Trees
 The Complexity of Computing the Behaviour of Lattice Automata on Infinite Trees Karsten Lehmann a, Rafael Peñaloza b a Optimisation Research Group, NICTA Artificial Intelligence Group, Australian National
The Complexity of Computing the Behaviour of Lattice Automata on Infinite Trees Karsten Lehmann a, Rafael Peñaloza b a Optimisation Research Group, NICTA Artificial Intelligence Group, Australian National
Chapter 11: Automated Proof Systems (1)
 Chapter 11: Automated Proof Systems (1) SYSTEM RS OVERVIEW Hilbert style systems are easy to define and admit a simple proof of the Completeness Theorem but they are difficult to use. Automated systems
Chapter 11: Automated Proof Systems (1) SYSTEM RS OVERVIEW Hilbert style systems are easy to define and admit a simple proof of the Completeness Theorem but they are difficult to use. Automated systems
Random Resolution Refutations
 [1] Random Resolution Refutations Pavel Pudlák and Neil Thapen 1 Mathematical Institute, Academy of Sciences, Prague Riga, 6.7.17 1 the authors are supported by the ERC grant FEALORA [2] History and Motivation
[1] Random Resolution Refutations Pavel Pudlák and Neil Thapen 1 Mathematical Institute, Academy of Sciences, Prague Riga, 6.7.17 1 the authors are supported by the ERC grant FEALORA [2] History and Motivation
Interpolation theorems, lower bounds for proof. systems, and independence results for bounded. arithmetic. Jan Krajcek
 Interpolation theorems, lower bounds for proof systems, and independence results for bounded arithmetic Jan Krajcek Mathematical Institute of the Academy of Sciences Zitna 25, Praha 1, 115 67, Czech Republic
Interpolation theorems, lower bounds for proof systems, and independence results for bounded arithmetic Jan Krajcek Mathematical Institute of the Academy of Sciences Zitna 25, Praha 1, 115 67, Czech Republic
Computability and Complexity Theory: An Introduction
 Computability and Complexity Theory: An Introduction meena@imsc.res.in http://www.imsc.res.in/ meena IMI-IISc, 20 July 2006 p. 1 Understanding Computation Kinds of questions we seek answers to: Is a given
Computability and Complexity Theory: An Introduction meena@imsc.res.in http://www.imsc.res.in/ meena IMI-IISc, 20 July 2006 p. 1 Understanding Computation Kinds of questions we seek answers to: Is a given
Clique is hard on average for regular resolution
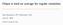 Clique is hard on average for regular resolution Ilario Bonacina, UPC Barcelona Tech July 27, 2018 Oxford Complexity Day Talk based on a joint work with: A. Atserias S. de Rezende J. Nordstro m M. Lauria
Clique is hard on average for regular resolution Ilario Bonacina, UPC Barcelona Tech July 27, 2018 Oxford Complexity Day Talk based on a joint work with: A. Atserias S. de Rezende J. Nordstro m M. Lauria
Lecture 4: NP and computational intractability
 Chapter 4 Lecture 4: NP and computational intractability Listen to: Find the longest path, Daniel Barret What do we do today: polynomial time reduction NP, co-np and NP complete problems some examples
Chapter 4 Lecture 4: NP and computational intractability Listen to: Find the longest path, Daniel Barret What do we do today: polynomial time reduction NP, co-np and NP complete problems some examples
