ROSENA R.X. DU AND HELMUT PRODINGER. Dedicated to Philippe Flajolet ( )
|
|
|
- Gary Leonard
- 5 years ago
- Views:
Transcription
1 ON PROTECTED NODES IN DIGITAL SEARCH TREES ROSENA R.X. DU AND HELMUT PRODINGER Dedicated to Philippe Flajolet (98 2) Abstract. Recently, 2-protected nodes were studied in the context of ordered trees and -trees. These nodes have a distance of at least 2 to each leaf. Here, we study digital search trees, which are binary trees, but with a different probability distribution underlying. Our result says, that grosso modo some 3% of the nodes are 2-protected. Methods include exponential generating functions, contour integration, and some elements from q-analysis.. Introduction Cheon and Shapiro [2] started the study of 2-protected nodes in trees. A node enjoys this property if its distance to any leaf is at least 2. A simpler notion is -protected: exactly the nodes that are not leaves are -protected. In the cited paper, the family of ordered trees was considered, and it was found that asymptotically a proportion of of the nodes is 2-protected. Recently, Mansour [9] complemented these results by 6 studying -ary trees. In the present note, we study the analogous quantity for Digital Search Trees (DSTs), a structure that is important in Computer Science [7]. As trees, they are binary trees, but the (probability) distribution is quite different. From a mathematical point of view, they always lead to interesting and nontrivial considerations, with a flair of q- analysis. Here are a few papers of relevance: [3,, 6, 8, 5] DSTs are constructed as follows. Given a sequence of binary strings, we place the first in the root node; those starting with ( ) are directed to the left (right) subtree of the root, and are constructed recursively by the same procedure but with the removal of their first bits when comparisons are made. See Figure for an illustration. In the following section we will show that the proportion of 2-protected nodes in the DST model is about 3%; a more detailed statement will be given later. We collect here are few notations. These quantities belong to the realm of q-series and can be found in [], although with a slightly different notation: Q m = m = ( 2 ), Q = = ( 2 ), Q(x) = = ( x 2 ). There is a formula that is equivalent to one of Euler s partition identities: Q(t) = m a m+ t m with a m+ = ( )m 2 (m+ 2 ) Q m. Finally, we will use L = log 2.
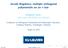
2 2 R.R.X. DU AND H. PRODINGER A : B : C : D : E : F : G : H : I : C B F E A D I G H Figure. A digital search tree with nine nodes, among which A and D are 2-protected. 2. Average number of 2-protected nodes Denote by l n the average number of 2-protected nodes in a random DST, built from n data. By random we mean that whenever a decision has to be made whether to go down to the left or right, a fair coin is tossed, and a direction is chosen with probability. 2 The following recursion follows from the observation that, provided we have n + data, ( go to the left and n go to the right, and such a split happens with probability n ) 2 n. One node goes to the root and is always 2-protected except in the instances = or = n. Therefore n ( n l n+ = = = + 2 n n )2 n ( l + l n + = l n2 n. ) = or n 2 n This recursion is true for n 3, with initial conditions l = l = l 2 =, l 3 =. 2 Our treatment follows [3]. We introduce the exponential generating function L(z) = n l nz n /n! and translate the recursion: z n l n+ n! = z n n! + z n n 2 n l n zn n2 n! n! or z n l n+ n! l z 2 3 2! = n = z n n! + z n n! n which leads after some simple manipulations to n = 2 n l n zn n2 n!, L (z) = e z ze z/2 + z2 + 2ez/2 L( z 2 ).
3 ON PROTECTED NODES IN DIGITAL SEARCH TREES 3 Now we introduce the Poisson generating function M(z) = e z L(z) = n m nz n /n! and rewrite the equation: M (z) + M(z) = ze z/2 e z + z2 e z + 2M( z 2 ). For n, we can read off the coefficients of z n /n!: m n+ = ( 2 n )m n + n( ) n 2 n ( ) n + In order to solve it, we rewrite it as m n+ ( ) n = m n( ) n 2 which can be summed and leads to and eventually to Since m N+ ( ) N Q N = N n=2 N 2 m N = Q N 2 ( ) N l n = n= n =2 + n2 n + n(n ), n2 n + n(n ) (n + )2 n n(n+). m n(n ) ( ) n. we found the following explicit formula that we formulate as a theorem. Theorem. The average number of 2-protected nodes in random DSTs of size N is exactly given by N ( N 2 l N = )( ) (n + )2 n n(n+) Q 2. Q n= n =2 Now we turn to the asymptotic evaluation of l N as N. Again, we follow the approach in [3] and use Rice s integrals, which means that we are able to rewrite l N as a contour integral. Changing the contour of integration and collecting residues produces the asymptotic expansion of interest. Many examples have been described in []. In order to do so, one must extend the function 2 Q 2 n= (n + )2 n n(n+) so that is maes sense for any complex, not just integers. This will be discussed now. We have Q 2 = Q /Q(2 2 ), and this maes sense for any. Now we have, using Euler s identity mentioned in the Introduction, = Q(2 n ) = a m+ 2 nm, Q Q m
4 R.R.X. DU AND H. PRODINGER and this maes sense for any n, since the smallness of the a m s handles all convergence issues. Therefore 2 n= (n + )2 n n(n+) = Q m a m+ 2 n= [ (n + )2 n n(n + ) ] 2 nm. The inner sum (on n) can be explicitly evaluated, but since it is long and ugly, we don t display it here, but the resulting form (that we eep in our Maple calculation) can be used for any C. The integral expression is l N = 2πi C Γ(N + )Γ( z) Γ(N + z) ψ(z)dz, where C encircles the poles 2, 3,..., N and no others. The function ψ(z) is the extension of 2 (n + )2 n n(n+) Q 2 n= as just discussed. Changing the contour, one encounters other poles. They must be subtracted and produce the asymptotic expansion that we need. The main contribution comes from z =. There are also poles at z = + χ, with χ = 2πi, and they L contribute a tiny oscillating function N δ(log 2 N), where the amplitude of δ(x) is typically smaller than 5. In order to eep this note short and crisp, we refrain from computing this function explicitly. It is not difficult, and there are many similar examples in the literature. So we concentrate now on z =, and we will find a simple pole. As a first step, we consider lim Q 2 2 n= [ (n + )2 n This limit can be computed by Maple, with the result b m := B(2 m ) L (2 m ) 3 (2 m 2) 2 n(n + ) ] 2 nm. and B(x) := 6L 8xL + 8x 2 L 6x 3 L 2 + 6x 69x x 3 7x 8x log (x) + 2x 2 log (x) x 3 log (x) + x log (x). Note that b is interpreted as a limit: So we are left with the negative residue of b = 37 2L. Γ(N + )Γ( z) Γ(N + z) at z =, which is just N. Summarizing, we found the asymptotic behaviour.
5 ON PROTECTED NODES IN DIGITAL SEARCH TREES 5 Theorem 2. The average number l N of 2-protected nodes in random DSTs of size N admits the asymptotic expansion l N = N Q m a m+ b m + N δ(log 2 N) + O(), where the numerical constant evaluates to The tiny periodic function δ(x) has a Fourier expansion that could be computed in principle. The remainder term O() stems from the next pole at z =. For example, l 5 /5 = Remar. Flajolet and Sedgewic in [3] solved an open problem of Knuth [7], and considered the number of endnodes. They found this to be on average as β N, with β = Again, there are tiny oscillations. The quantity ( β)n is (asymptotically) the number of -protected nodes. So, there are roughly 63% - protected nodes, and our new results say that there are about 3% 2-protected nodes. Acnowledgement. The first author is partially supported by the National Science Foundation of China under Grant 853, and the Shanghai Rising-Star Program (No. QA9). The second author is supported by an International Science and Technology Agreement (Grant 6725) from the NRF (South Africa). References [] George E. Andrews. The theory of partitions. Addison-Wesley Publishing Co., Reading, Mass.- London-Amsterdam, 976. Encyclopedia of Mathematics and its Applications, Vol. 2. [2] Gi-Sang Cheon and Louis W. Shapiro. Protected points in ordered trees. Appl. Math. Lett., 2(5):56 52, 28. [3] Philippe Flajolet and Robert Sedgewic. Digital search trees revisited. SIAM J. Comput., 5(3):78 767, 986. [] Philippe Flajolet and Robert Sedgewic. Mellin transforms and asymptotics: finite differences and Rice s integrals. Theoret. Comput. Sci., (-2): 2, 995. Special volume on mathematical analysis of algorithms. [5] Hsien-Kuei Hwang, Michael Fuchs, and Vytas Zacharovas. Asymptotic variance of random symmetric digital search trees. Discrete Math. Theor. Comput. Sci., 2(2):3 65, 2. [6] Peter Kirschenhofer and Helmut Prodinger. Eine Anwendung der Theorie der Modulfuntionen in der Informati. Österreich. Aad. Wiss. Math.-Natur. Kl. Sitzungsber. II, 97(-7): , 988. [7] Donald E. Knuth. The Art of Computer Programming, volume 3: Sorting and Searching. Addison- Wesley, 973. Second edition, 998. [8] Guy Louchard and Helmut Prodinger. Asymptotics of the moments of extreme-value related distribution functions. Algorithmica, 6(3-):3 67, 26. [9] Toufi Mansour. Protected points in -ary trees. Appl. Math. Lett., 2():78 8, 2. [] Helmut Prodinger. External internal nodes in digital search trees via Mellin transforms. SIAM J. Comput., 2(6):8 83, 992.
6 6 R.R.X. DU AND H. PRODINGER Rosena R.X. Du, Department of Mathematics, East China Normal University, 5 Dongchuan Road, Shanghai, 22, P. R. China. address: rxdu@math.ecnu.edu.cn Helmut Prodinger, Mathematics Department, Stellenbosch University, 762 Stellenbosch, South Africa. address: hproding@sun.ac.za
Forty years of tree enumeration
 October 24, 206 Canada John Moon (Alberta) Counting labelled trees Canadian mathematical monographs What is our subject? Asymptotic enumeration or Probabilistic combinatorics? What is our subject? Asymptotic
October 24, 206 Canada John Moon (Alberta) Counting labelled trees Canadian mathematical monographs What is our subject? Asymptotic enumeration or Probabilistic combinatorics? What is our subject? Asymptotic
Asymptotic and Exact Poissonized Variance in the Analysis of Random Digital Trees (joint with Hsien-Kuei Hwang and Vytas Zacharovas)
 Asymptotic and Exact Poissonized Variance in the Analysis of Random Digital Trees (joint with Hsien-Kuei Hwang and Vytas Zacharovas) Michael Fuchs Institute of Applied Mathematics National Chiao Tung University
Asymptotic and Exact Poissonized Variance in the Analysis of Random Digital Trees (joint with Hsien-Kuei Hwang and Vytas Zacharovas) Michael Fuchs Institute of Applied Mathematics National Chiao Tung University
Approximate Counting via the Poisson-Laplace-Mellin Method (joint with Chung-Kuei Lee and Helmut Prodinger)
 Approximate Counting via the Poisson-Laplace-Mellin Method (joint with Chung-Kuei Lee and Helmut Prodinger) Michael Fuchs Department of Applied Mathematics National Chiao Tung University Hsinchu, Taiwan
Approximate Counting via the Poisson-Laplace-Mellin Method (joint with Chung-Kuei Lee and Helmut Prodinger) Michael Fuchs Department of Applied Mathematics National Chiao Tung University Hsinchu, Taiwan
Asymptotic results for silent elimination
 Discrete Mathematics and Theoretical Computer Science DMTCS vol. subm., by the authors, 1 1 Asymptotic results for silent elimination Guy Louchard 1 and Helmut Prodinger 2 1 Université Libre de Bruxelles,
Discrete Mathematics and Theoretical Computer Science DMTCS vol. subm., by the authors, 1 1 Asymptotic results for silent elimination Guy Louchard 1 and Helmut Prodinger 2 1 Université Libre de Bruxelles,
k-protected VERTICES IN BINARY SEARCH TREES
 k-protected VERTICES IN BINARY SEARCH TREES MIKLÓS BÓNA Abstract. We show that for every k, the probability that a randomly selected vertex of a random binary search tree on n nodes is at distance k from
k-protected VERTICES IN BINARY SEARCH TREES MIKLÓS BÓNA Abstract. We show that for every k, the probability that a randomly selected vertex of a random binary search tree on n nodes is at distance k from
Counting Palindromes According to r-runs of Ones Using Generating Functions
 3 47 6 3 Journal of Integer Sequences, Vol. 7 (04), Article 4.6. Counting Palindromes According to r-runs of Ones Using Generating Functions Helmut Prodinger Department of Mathematics Stellenbosch University
3 47 6 3 Journal of Integer Sequences, Vol. 7 (04), Article 4.6. Counting Palindromes According to r-runs of Ones Using Generating Functions Helmut Prodinger Department of Mathematics Stellenbosch University
Counting Palindromes According to r-runs of Ones Using Generating Functions
 Counting Palindromes According to r-runs of Ones Using Generating Functions Helmut Prodinger Department of Mathematics Stellenbosch University 7602 Stellenbosch South Africa hproding@sun.ac.za Abstract
Counting Palindromes According to r-runs of Ones Using Generating Functions Helmut Prodinger Department of Mathematics Stellenbosch University 7602 Stellenbosch South Africa hproding@sun.ac.za Abstract
arxiv: v1 [math.co] 1 Aug 2018
![arxiv: v1 [math.co] 1 Aug 2018 arxiv: v1 [math.co] 1 Aug 2018](/thumbs/83/88788887.jpg) REDUCING SIMPLY GENERATED TREES BY ITERATIVE LEAF CUTTING BENJAMIN HACKL, CLEMENS HEUBERGER, AND STEPHAN WAGNER arxiv:1808.00363v1 [math.co] 1 Aug 2018 ABSTRACT. We consider a procedure to reduce simply
REDUCING SIMPLY GENERATED TREES BY ITERATIVE LEAF CUTTING BENJAMIN HACKL, CLEMENS HEUBERGER, AND STEPHAN WAGNER arxiv:1808.00363v1 [math.co] 1 Aug 2018 ABSTRACT. We consider a procedure to reduce simply
How often do we reject a superior value? (Extended abstract)
 How often do we reject a superior value? (Extended abstract) Kamilla Oliver, Helmut Prodinger To cite this version: Kamilla Oliver, Helmut Prodinger. How often do we reject a superior value? (Extended
How often do we reject a superior value? (Extended abstract) Kamilla Oliver, Helmut Prodinger To cite this version: Kamilla Oliver, Helmut Prodinger. How often do we reject a superior value? (Extended
The Moments of the Profile in Random Binary Digital Trees
 Journal of mathematics and computer science 6(2013)176-190 The Moments of the Profile in Random Binary Digital Trees Ramin Kazemi and Saeid Delavar Department of Statistics, Imam Khomeini International
Journal of mathematics and computer science 6(2013)176-190 The Moments of the Profile in Random Binary Digital Trees Ramin Kazemi and Saeid Delavar Department of Statistics, Imam Khomeini International
PROTECTED NODES AND FRINGE SUBTREES IN SOME RANDOM TREES
 PROTECTED NODES AND FRINGE SUBTREES IN SOME RANDOM TREES LUC DEVROYE AND SVANTE JANSON Abstract. We study protected nodes in various classes of random rooted trees by putting them in the general context
PROTECTED NODES AND FRINGE SUBTREES IN SOME RANDOM TREES LUC DEVROYE AND SVANTE JANSON Abstract. We study protected nodes in various classes of random rooted trees by putting them in the general context
New Multiple Harmonic Sum Identities
 New Multiple Harmonic Sum Identities Helmut Prodinger Department of Mathematics University of Stellenbosch 760 Stellenbosch, South Africa hproding@sun.ac.za Roberto Tauraso Dipartimento di Matematica Università
New Multiple Harmonic Sum Identities Helmut Prodinger Department of Mathematics University of Stellenbosch 760 Stellenbosch, South Africa hproding@sun.ac.za Roberto Tauraso Dipartimento di Matematica Università
The Number of Inversions in Permutations: A Saddle Point Approach
 1 2 3 47 6 23 11 Journal of Integer Sequences, Vol. 6 (23), Article 3.2.8 The Number of Inversions in Permutations: A Saddle Point Approach Guy Louchard Département d Informatique CP 212, Boulevard du
1 2 3 47 6 23 11 Journal of Integer Sequences, Vol. 6 (23), Article 3.2.8 The Number of Inversions in Permutations: A Saddle Point Approach Guy Louchard Département d Informatique CP 212, Boulevard du
Compositions and samples of geometric random variables with constrained multiplicities
 FPSAC 2010, San Francisco, USA DMTCS proc. AN, 2010, 317 328 Compositions and samples of geometric random variables with constrained multiplicities Margaret Archibald 1 and Arnold Knopfmacher 2 and Toufik
FPSAC 2010, San Francisco, USA DMTCS proc. AN, 2010, 317 328 Compositions and samples of geometric random variables with constrained multiplicities Margaret Archibald 1 and Arnold Knopfmacher 2 and Toufik
Probabilistic analysis of the asymmetric digital search trees
 Int. J. Nonlinear Anal. Appl. 6 2015 No. 2, 161-173 ISSN: 2008-6822 electronic http://dx.doi.org/10.22075/ijnaa.2015.266 Probabilistic analysis of the asymmetric digital search trees R. Kazemi a,, M. Q.
Int. J. Nonlinear Anal. Appl. 6 2015 No. 2, 161-173 ISSN: 2008-6822 electronic http://dx.doi.org/10.22075/ijnaa.2015.266 Probabilistic analysis of the asymmetric digital search trees R. Kazemi a,, M. Q.
Permutations with Inversions
 1 2 3 47 6 23 11 Journal of Integer Sequences, Vol. 4 2001, Article 01.2.4 Permutations with Inversions Barbara H. Margolius Cleveland State University Cleveland, Ohio 44115 Email address: b.margolius@csuohio.edu
1 2 3 47 6 23 11 Journal of Integer Sequences, Vol. 4 2001, Article 01.2.4 Permutations with Inversions Barbara H. Margolius Cleveland State University Cleveland, Ohio 44115 Email address: b.margolius@csuohio.edu
Growing and Destroying Catalan Stanley Trees
 Discrete Mathematics and Theoretical Computer Science DMTCS vol. 20:1, 2018, #11 Growing and Destroying Catalan Stanley Trees Benjamin Hackl 1 Helmut Prodinger 2 arxiv:1704.03734v3 [math.co] 26 Feb 2018
Discrete Mathematics and Theoretical Computer Science DMTCS vol. 20:1, 2018, #11 Growing and Destroying Catalan Stanley Trees Benjamin Hackl 1 Helmut Prodinger 2 arxiv:1704.03734v3 [math.co] 26 Feb 2018
Digital search trees JASS
 Digital search trees Analysis of different digital trees with Rice s integrals. JASS Nicolai v. Hoyningen-Huene 28.3.2004 28.3.2004 JASS 04 - Digital search trees 1 content Tree Digital search tree: Definition
Digital search trees Analysis of different digital trees with Rice s integrals. JASS Nicolai v. Hoyningen-Huene 28.3.2004 28.3.2004 JASS 04 - Digital search trees 1 content Tree Digital search tree: Definition
The number of inversions in permutations: A saddle point approach
 The number of inversions in permutations: A saddle point approach Guy Louchard and Helmut Prodinger November 4, 22 Abstract Using the saddle point method, we obtain from the generating function of the
The number of inversions in permutations: A saddle point approach Guy Louchard and Helmut Prodinger November 4, 22 Abstract Using the saddle point method, we obtain from the generating function of the
Dependence between Path Lengths and Size in Random Trees (joint with H.-H. Chern, H.-K. Hwang and R. Neininger)
 Dependence between Path Lengths and Size in Random Trees (joint with H.-H. Chern, H.-K. Hwang and R. Neininger) Michael Fuchs Institute of Applied Mathematics National Chiao Tung University Hsinchu, Taiwan
Dependence between Path Lengths and Size in Random Trees (joint with H.-H. Chern, H.-K. Hwang and R. Neininger) Michael Fuchs Institute of Applied Mathematics National Chiao Tung University Hsinchu, Taiwan
Additive irreducibles in α-expansions
 Publ. Math. Debrecen Manuscript Additive irreducibles in α-expansions By Peter J. Grabner and Helmut Prodinger * Abstract. The Bergman number system uses the base α = + 5 2, the digits 0 and, and the condition
Publ. Math. Debrecen Manuscript Additive irreducibles in α-expansions By Peter J. Grabner and Helmut Prodinger * Abstract. The Bergman number system uses the base α = + 5 2, the digits 0 and, and the condition
Protected nodes and fringe subtrees in some random trees
 Electron. Commun. Probab. 19 (214), no. 6, 1 1. DOI: 1.1214/ECP.v19-348 ISSN: 183-589X ELECTRONIC COMMUNICATIONS in PROBABILITY Protected nodes and fringe subtrees in some random trees Luc Devroye Svante
Electron. Commun. Probab. 19 (214), no. 6, 1 1. DOI: 1.1214/ECP.v19-348 ISSN: 183-589X ELECTRONIC COMMUNICATIONS in PROBABILITY Protected nodes and fringe subtrees in some random trees Luc Devroye Svante
PARTITIONS WITH FIXED DIFFERENCES BETWEEN LARGEST AND SMALLEST PARTS
 PARTITIONS WITH FIXED DIFFERENCES BETWEEN LARGEST AND SMALLEST PARTS GEORGE E. ANDREWS, MATTHIAS BECK, AND NEVILLE ROBBINS Abstract. We study the number p(n, t) of partitions of n with difference t between
PARTITIONS WITH FIXED DIFFERENCES BETWEEN LARGEST AND SMALLEST PARTS GEORGE E. ANDREWS, MATTHIAS BECK, AND NEVILLE ROBBINS Abstract. We study the number p(n, t) of partitions of n with difference t between
Partial Match Queries in Relaxed Multidimensional Search Trees 1
 Algorithmica 2001 29: 181 204 DOI: 10.1007/s004530010065 Algorithmica 2001 Springer-Verlag New York Inc. Partial Match Queries in Relaxed Multidimensional Search Trees 1 C. Martínez, 2 A. Panholzer, 3
Algorithmica 2001 29: 181 204 DOI: 10.1007/s004530010065 Algorithmica 2001 Springer-Verlag New York Inc. Partial Match Queries in Relaxed Multidimensional Search Trees 1 C. Martínez, 2 A. Panholzer, 3
ON THE COEFFICIENTS OF AN ASYMPTOTIC EXPANSION RELATED TO SOMOS QUADRATIC RECURRENCE CONSTANT
 Applicable Analysis and Discrete Mathematics available online at http://pefmath.etf.bg.ac.yu Appl. Anal. Discrete Math. x (xxxx), xxx xxx. doi:10.2298/aadmxxxxxxxx ON THE COEFFICIENTS OF AN ASYMPTOTIC
Applicable Analysis and Discrete Mathematics available online at http://pefmath.etf.bg.ac.yu Appl. Anal. Discrete Math. x (xxxx), xxx xxx. doi:10.2298/aadmxxxxxxxx ON THE COEFFICIENTS OF AN ASYMPTOTIC
Almost all trees have an even number of independent sets
 Almost all trees have an even number of independent sets Stephan G. Wagner Department of Mathematical Sciences Stellenbosch University Private Bag X1, Matieland 7602, South Africa swagner@sun.ac.za Submitted:
Almost all trees have an even number of independent sets Stephan G. Wagner Department of Mathematical Sciences Stellenbosch University Private Bag X1, Matieland 7602, South Africa swagner@sun.ac.za Submitted:
The variance for partial match retrievals in k-dimensional bucket digital trees
 The variance for partial match retrievals in k-dimensional ucket digital trees Michael FUCHS Department of Applied Mathematics National Chiao Tung University January 12, 21 Astract The variance of partial
The variance for partial match retrievals in k-dimensional ucket digital trees Michael FUCHS Department of Applied Mathematics National Chiao Tung University January 12, 21 Astract The variance of partial
SORTING ALGORITHMS FOR BROADCAST COMMUNICATIONS: MATHEMATICAL ANALYSIS
 SORTING ALGORITHMS FOR BROADCAST COMMUNICATIONS: MATHEMATICAL ANALYSIS PETER J. GRABNER AND HELMUT PRODINGER Abstract. Assume that n persons communicate via a channel; to each person a certain number is
SORTING ALGORITHMS FOR BROADCAST COMMUNICATIONS: MATHEMATICAL ANALYSIS PETER J. GRABNER AND HELMUT PRODINGER Abstract. Assume that n persons communicate via a channel; to each person a certain number is
arxiv: v1 [math.pr] 21 Mar 2014
![arxiv: v1 [math.pr] 21 Mar 2014 arxiv: v1 [math.pr] 21 Mar 2014](/thumbs/80/81662484.jpg) Asymptotic distribution of two-protected nodes in ternary search trees Cecilia Holmgren Svante Janson March 2, 24 arxiv:4.557v [math.pr] 2 Mar 24 Abstract We study protected nodes in m-ary search trees,
Asymptotic distribution of two-protected nodes in ternary search trees Cecilia Holmgren Svante Janson March 2, 24 arxiv:4.557v [math.pr] 2 Mar 24 Abstract We study protected nodes in m-ary search trees,
Mergesort, File: msfinal6.tex Date: (678) BOTTOM-UP MERGESORT y. A Detailed Analysis
 BOTTOM-UP MERGESORT y A Detailed Analysis W. PANNY 1 and H. PRODINGER 1 Department of Computer Science, University of Economics, Augasse {6, A-1090 Vienna, Austria. E-mail: wolfgang.panny@wu-wien.ac.at
BOTTOM-UP MERGESORT y A Detailed Analysis W. PANNY 1 and H. PRODINGER 1 Department of Computer Science, University of Economics, Augasse {6, A-1090 Vienna, Austria. E-mail: wolfgang.panny@wu-wien.ac.at
Asymptotic variance of random symmetric digital search trees
 Discrete Mathematics and Theoretical Computer Science DMTCS vol. :,, 3 66 Asymptotic variance of random symmetric digital search trees Hsien-Kuei Hwang, Michael Fuchs and Vytas Zacharovas Institute of
Discrete Mathematics and Theoretical Computer Science DMTCS vol. :,, 3 66 Asymptotic variance of random symmetric digital search trees Hsien-Kuei Hwang, Michael Fuchs and Vytas Zacharovas Institute of
Notes by Zvi Rosen. Thanks to Alyssa Palfreyman for supplements.
 Lecture: Hélène Barcelo Analytic Combinatorics ECCO 202, Bogotá Notes by Zvi Rosen. Thanks to Alyssa Palfreyman for supplements.. Tuesday, June 2, 202 Combinatorics is the study of finite structures that
Lecture: Hélène Barcelo Analytic Combinatorics ECCO 202, Bogotá Notes by Zvi Rosen. Thanks to Alyssa Palfreyman for supplements.. Tuesday, June 2, 202 Combinatorics is the study of finite structures that
Asymptotic distribution of two-protected nodes in ternary search trees
 Asymptotic distribution of two-protected nodes in ternary search trees Cecilia Holmgren Svante Janson March 2, 204; revised October 5, 204 Abstract We study protected nodes in m-ary search trees, by putting
Asymptotic distribution of two-protected nodes in ternary search trees Cecilia Holmgren Svante Janson March 2, 204; revised October 5, 204 Abstract We study protected nodes in m-ary search trees, by putting
PROBABILISTIC BEHAVIOR OF ASYMMETRIC LEVEL COMPRESSED TRIES
 PROBABILISTIC BEAVIOR OF ASYMMETRIC LEVEL COMPRESSED TRIES Luc Devroye Wojcieh Szpankowski School of Computer Science Department of Computer Sciences McGill University Purdue University 3450 University
PROBABILISTIC BEAVIOR OF ASYMMETRIC LEVEL COMPRESSED TRIES Luc Devroye Wojcieh Szpankowski School of Computer Science Department of Computer Sciences McGill University Purdue University 3450 University
The distribution of run lengths in integer compositions
 The distribution of run lengths in integer compositions Herbert S Wilf University of Pennsylvania Philadelphia PA 19104-6395, USA wilf@mathupennedu Submitted: Mar 7, 2010; Accepted: Oct 9, 2011; Published:
The distribution of run lengths in integer compositions Herbert S Wilf University of Pennsylvania Philadelphia PA 19104-6395, USA wilf@mathupennedu Submitted: Mar 7, 2010; Accepted: Oct 9, 2011; Published:
ON THE SLACK EULER PAIR FOR VECTOR PARTITION
 #A7 INTEGERS 18 (2018 ON THE SLACK EULER PAIR FOR VECTOR PARTITION Shishuo Fu College of Mathematics and Statistics, Chongqing University, Huxi Campus, Chongqing, P.R. China. fsshuo@cqu.edu.cn Ting Hua
#A7 INTEGERS 18 (2018 ON THE SLACK EULER PAIR FOR VECTOR PARTITION Shishuo Fu College of Mathematics and Statistics, Chongqing University, Huxi Campus, Chongqing, P.R. China. fsshuo@cqu.edu.cn Ting Hua
ABSTRACT 1. INTRODUCTION
 THE FIBONACCI NUMBER OF GENERALIZED PETERSEN GRAPHS Stephan G. Wagner Department of Mathematics, Graz University of Technology, Steyrergasse 30, A-8010 Graz, Austria e-mail: wagner@finanz.math.tu-graz.ac.at
THE FIBONACCI NUMBER OF GENERALIZED PETERSEN GRAPHS Stephan G. Wagner Department of Mathematics, Graz University of Technology, Steyrergasse 30, A-8010 Graz, Austria e-mail: wagner@finanz.math.tu-graz.ac.at
On the number of matchings of a tree.
 On the number of matchings of a tree. Stephan G. Wagner Department of Mathematics, Graz University of Technology, Steyrergasse 30, A-800 Graz, Austria Abstract In a paper of Klazar, several counting examples
On the number of matchings of a tree. Stephan G. Wagner Department of Mathematics, Graz University of Technology, Steyrergasse 30, A-800 Graz, Austria Abstract In a paper of Klazar, several counting examples
The Subtree Size Profile of Plane-oriented Recursive Trees
 The Subtree Size Profile of Plane-oriented Recursive Trees Michael Fuchs Department of Applied Mathematics National Chiao Tung University Hsinchu, Taiwan ANALCO11, January 22nd, 2011 Michael Fuchs (NCTU)
The Subtree Size Profile of Plane-oriented Recursive Trees Michael Fuchs Department of Applied Mathematics National Chiao Tung University Hsinchu, Taiwan ANALCO11, January 22nd, 2011 Michael Fuchs (NCTU)
Everything You Always Wanted to Know about Quicksort, but Were Afraid to Ask. Marianne Durand
 Algorithms Seminar 200 2002, F. Chyzak (ed., INRIA, (2003, pp. 57 62. Available online at the URL http://algo.inria.fr/seminars/. Everything You Always Wanted to Know about Quicksort, but Were Afraid to
Algorithms Seminar 200 2002, F. Chyzak (ed., INRIA, (2003, pp. 57 62. Available online at the URL http://algo.inria.fr/seminars/. Everything You Always Wanted to Know about Quicksort, but Were Afraid to
The Largest Missing Value in a Composition of an Integer and Some Allouche-Shallit-Type Identities
 1 3 47 6 3 11 Journal of Integer Sequences, Vol. 16 13, Article 13.. The Largest Missing Value in a Composition of an Integer and Some Allouche-Shallit-Type Identities Guy Louchard Université Libre de
1 3 47 6 3 11 Journal of Integer Sequences, Vol. 16 13, Article 13.. The Largest Missing Value in a Composition of an Integer and Some Allouche-Shallit-Type Identities Guy Louchard Université Libre de
Applications of Analytic Combinatorics in Mathematical Biology (joint with H. Chang, M. Drmota, E. Y. Jin, and Y.-W. Lee)
 Applications of Analytic Combinatorics in Mathematical Biology (joint with H. Chang, M. Drmota, E. Y. Jin, and Y.-W. Lee) Michael Fuchs Department of Applied Mathematics National Chiao Tung University
Applications of Analytic Combinatorics in Mathematical Biology (joint with H. Chang, M. Drmota, E. Y. Jin, and Y.-W. Lee) Michael Fuchs Department of Applied Mathematics National Chiao Tung University
A Note on a Problem Posed by D. E. Knuth on a Satisfiability Recurrence
 A Note on a Problem Posed by D. E. Knuth on a Satisfiability Recurrence Dedicated to Philippe Flajolet 1948-2011 July 4, 2013 Philippe Jacquet Charles Knessl 1 Wojciech Szpankowski 2 Bell Labs Dept. Math.
A Note on a Problem Posed by D. E. Knuth on a Satisfiability Recurrence Dedicated to Philippe Flajolet 1948-2011 July 4, 2013 Philippe Jacquet Charles Knessl 1 Wojciech Szpankowski 2 Bell Labs Dept. Math.
A REMARK ON THE BOROS-MOLL SEQUENCE
 #A49 INTEGERS 11 (2011) A REMARK ON THE BOROS-MOLL SEQUENCE J.-P. Allouche CNRS, Institut de Math., Équipe Combinatoire et Optimisation Université Pierre et Marie Curie, Paris, France allouche@math.jussieu.fr
#A49 INTEGERS 11 (2011) A REMARK ON THE BOROS-MOLL SEQUENCE J.-P. Allouche CNRS, Institut de Math., Équipe Combinatoire et Optimisation Université Pierre et Marie Curie, Paris, France allouche@math.jussieu.fr
Math 259: Introduction to Analytic Number Theory More about the Gamma function
 Math 59: Introduction to Analytic Number Theory More about the Gamma function We collect some more facts about Γs as a function of a complex variable that will figure in our treatment of ζs and Ls, χ.
Math 59: Introduction to Analytic Number Theory More about the Gamma function We collect some more facts about Γs as a function of a complex variable that will figure in our treatment of ζs and Ls, χ.
The register function for lattice paths
 Fifth Colloquium on Mathematics and Computer Science DMTCS proc. AI, 2008, 35 48 The register function for lattice paths Guy Louchard and Helmut Prodinger 2 Université Libre de Bruxelles, Département d
Fifth Colloquium on Mathematics and Computer Science DMTCS proc. AI, 2008, 35 48 The register function for lattice paths Guy Louchard and Helmut Prodinger 2 Université Libre de Bruxelles, Département d
COMPOSITIONS WITH A FIXED NUMBER OF INVERSIONS
 COMPOSITIONS WITH A FIXED NUMBER OF INVERSIONS A. KNOPFMACHER, M. E. MAYS, AND S. WAGNER Abstract. A composition of the positive integer n is a representation of n as an ordered sum of positive integers
COMPOSITIONS WITH A FIXED NUMBER OF INVERSIONS A. KNOPFMACHER, M. E. MAYS, AND S. WAGNER Abstract. A composition of the positive integer n is a representation of n as an ordered sum of positive integers
HYPERGEOMETRIC BERNOULLI POLYNOMIALS AND APPELL SEQUENCES
 HYPERGEOMETRIC BERNOULLI POLYNOMIALS AND APPELL SEQUENCES ABDUL HASSEN AND HIEU D. NGUYEN Abstract. There are two analytic approaches to Bernoulli polynomials B n(x): either by way of the generating function
HYPERGEOMETRIC BERNOULLI POLYNOMIALS AND APPELL SEQUENCES ABDUL HASSEN AND HIEU D. NGUYEN Abstract. There are two analytic approaches to Bernoulli polynomials B n(x): either by way of the generating function
Average Case Analysis of QuickSort and Insertion Tree Height using Incompressibility
 Average Case Analysis of QuickSort and Insertion Tree Height using Incompressibility Tao Jiang, Ming Li, Brendan Lucier September 26, 2005 Abstract In this paper we study the Kolmogorov Complexity of a
Average Case Analysis of QuickSort and Insertion Tree Height using Incompressibility Tao Jiang, Ming Li, Brendan Lucier September 26, 2005 Abstract In this paper we study the Kolmogorov Complexity of a
Combinatorial/probabilistic analysis of a class of search-tree functionals
 Combinatorial/probabilistic analysis of a class of search-tree functionals Jim Fill jimfill@jhu.edu http://www.mts.jhu.edu/ fill/ Mathematical Sciences The Johns Hopkins University Joint Statistical Meetings;
Combinatorial/probabilistic analysis of a class of search-tree functionals Jim Fill jimfill@jhu.edu http://www.mts.jhu.edu/ fill/ Mathematical Sciences The Johns Hopkins University Joint Statistical Meetings;
EXPECTED WORST-CASE PARTIAL MATCH IN RANDOM QUADTRIES
 EXPECTED WORST-CASE PARTIAL MATCH IN RANDOM QUADTRIES Luc Devroye School of Computer Science McGill University Montreal, Canada H3A 2K6 luc@csmcgillca Carlos Zamora-Cura Instituto de Matemáticas Universidad
EXPECTED WORST-CASE PARTIAL MATCH IN RANDOM QUADTRIES Luc Devroye School of Computer Science McGill University Montreal, Canada H3A 2K6 luc@csmcgillca Carlos Zamora-Cura Instituto de Matemáticas Universidad
GENERALIZED STIRLING PERMUTATIONS, FAMILIES OF INCREASING TREES AND URN MODELS
 GENERALIZED STIRLING PERMUTATIONS, FAMILIES OF INCREASING TREES AND URN MODELS SVANTE JANSON, MARKUS KUBA, AND ALOIS PANHOLZER ABSTRACT. Bona [6] studied the distribution of ascents, plateaux and descents
GENERALIZED STIRLING PERMUTATIONS, FAMILIES OF INCREASING TREES AND URN MODELS SVANTE JANSON, MARKUS KUBA, AND ALOIS PANHOLZER ABSTRACT. Bona [6] studied the distribution of ascents, plateaux and descents
GENERATING SERIES FOR IRREDUCIBLE POLYNOMIALS OVER FINITE FIELDS
 GENERATING SERIES FOR IRREDUCIBLE POLYNOMIALS OVER FINITE FIELDS ARNAUD BODIN Abstract. We count the number of irreducible polynomials in several variables of a given degree over a finite field. The results
GENERATING SERIES FOR IRREDUCIBLE POLYNOMIALS OVER FINITE FIELDS ARNAUD BODIN Abstract. We count the number of irreducible polynomials in several variables of a given degree over a finite field. The results
A REFINED ENUMERATION OF p-ary LABELED TREES
 Korean J. Math. 21 (2013), No. 4, pp. 495 502 http://dx.doi.org/10.11568/kjm.2013.21.4.495 A REFINED ENUMERATION OF p-ary LABELED TREES Seunghyun Seo and Heesung Shin Abstract. Let T n (p) be the set of
Korean J. Math. 21 (2013), No. 4, pp. 495 502 http://dx.doi.org/10.11568/kjm.2013.21.4.495 A REFINED ENUMERATION OF p-ary LABELED TREES Seunghyun Seo and Heesung Shin Abstract. Let T n (p) be the set of
7 Asymptotics for Meromorphic Functions
 Lecture G jacques@ucsd.edu 7 Asymptotics for Meromorphic Functions Hadamard s Theorem gives a broad description of the exponential growth of coefficients in power series, but the notion of exponential
Lecture G jacques@ucsd.edu 7 Asymptotics for Meromorphic Functions Hadamard s Theorem gives a broad description of the exponential growth of coefficients in power series, but the notion of exponential
WAITING FOR A BAT TO FLY BY (IN POLYNOMIAL TIME)
 WAITING FOR A BAT TO FLY BY (IN POLYNOMIAL TIME ITAI BENJAMINI, GADY KOZMA, LÁSZLÓ LOVÁSZ, DAN ROMIK, AND GÁBOR TARDOS Abstract. We observe returns of a simple random wal on a finite graph to a fixed node,
WAITING FOR A BAT TO FLY BY (IN POLYNOMIAL TIME ITAI BENJAMINI, GADY KOZMA, LÁSZLÓ LOVÁSZ, DAN ROMIK, AND GÁBOR TARDOS Abstract. We observe returns of a simple random wal on a finite graph to a fixed node,
ALGEBRA II CURRICULUM MAP
 2017-2018 MATHEMATICS ALGEBRA II CURRICULUM MAP Department of Curriculum and Instruction RCCSD Common Core Major Emphasis Clusters The Real Number System Extend the properties of exponents to rational
2017-2018 MATHEMATICS ALGEBRA II CURRICULUM MAP Department of Curriculum and Instruction RCCSD Common Core Major Emphasis Clusters The Real Number System Extend the properties of exponents to rational
Polyexponentials. Khristo N. Boyadzhiev Ohio Northern University Departnment of Mathematics Ada, OH
 Polyexponentials Khristo N. Boyadzhiev Ohio Northern University Departnment of Mathematics Ada, OH 45810 k-boyadzhiev@onu.edu 1. Introduction. The polylogarithmic function [15] (1.1) and the more general
Polyexponentials Khristo N. Boyadzhiev Ohio Northern University Departnment of Mathematics Ada, OH 45810 k-boyadzhiev@onu.edu 1. Introduction. The polylogarithmic function [15] (1.1) and the more general
On the Sequence A and Its Combinatorial Interpretations
 1 2 47 6 2 11 Journal of Integer Sequences, Vol. 9 (2006), Article 06..1 On the Sequence A079500 and Its Combinatorial Interpretations A. Frosini and S. Rinaldi Università di Siena Dipartimento di Scienze
1 2 47 6 2 11 Journal of Integer Sequences, Vol. 9 (2006), Article 06..1 On the Sequence A079500 and Its Combinatorial Interpretations A. Frosini and S. Rinaldi Università di Siena Dipartimento di Scienze
ASYMPTOTICS OF THE EULERIAN NUMBERS REVISITED: A LARGE DEVIATION ANALYSIS
 ASYMPTOTICS OF THE EULERIAN NUMBERS REVISITED: A LARGE DEVIATION ANALYSIS GUY LOUCHARD ABSTRACT Using the Saddle point method and multiseries expansions we obtain from the generating function of the Eulerian
ASYMPTOTICS OF THE EULERIAN NUMBERS REVISITED: A LARGE DEVIATION ANALYSIS GUY LOUCHARD ABSTRACT Using the Saddle point method and multiseries expansions we obtain from the generating function of the Eulerian
Algebra 2 Mississippi College- and Career- Readiness Standards for Mathematics RCSD Unit 1 Data Relationships 1st Nine Weeks
 1 st Nine Weeks Algebra 2 Mississippi College- and Career- Readiness Standards for Mathematics Unit 1 Data Relationships Level 4: I can interpret key features of graphs and tables in terms of the quantities.
1 st Nine Weeks Algebra 2 Mississippi College- and Career- Readiness Standards for Mathematics Unit 1 Data Relationships Level 4: I can interpret key features of graphs and tables in terms of the quantities.
arxiv: v1 [cs.dm] 15 Jul 2016
![arxiv: v1 [cs.dm] 15 Jul 2016 arxiv: v1 [cs.dm] 15 Jul 2016](/thumbs/94/119552316.jpg) Best-case Analysis of MergeSort with an Application to the Sum of Digits Problem A manuscript (MS) intended for future journal publication arxiv:1607.04604v1 [cs.dm] 15 Jul 016 MAREK A. SUCHENEK California
Best-case Analysis of MergeSort with an Application to the Sum of Digits Problem A manuscript (MS) intended for future journal publication arxiv:1607.04604v1 [cs.dm] 15 Jul 016 MAREK A. SUCHENEK California
ANALYSIS OF LINEAR COMBINATION ALGORITHMS IN CRYPTOGRAPHY
 ANALYSIS OF LINEAR COMBINATION ALGORITHMS IN CRYPTOGRAPHY PETER J. GRABNER, CLEMENS HEUBERGER, HELMUT PRODINGER, AND JÖRG M. THUSWALDNER Abstract. Several cryptosystems rely on fast calculations of linear
ANALYSIS OF LINEAR COMBINATION ALGORITHMS IN CRYPTOGRAPHY PETER J. GRABNER, CLEMENS HEUBERGER, HELMUT PRODINGER, AND JÖRG M. THUSWALDNER Abstract. Several cryptosystems rely on fast calculations of linear
Math 213br HW 1 solutions
 Math 213br HW 1 solutions February 26, 2014 Problem 1 Let P (x) be a polynomial of degree d > 1 with P (x) > 0 for all x 0. For what values of α R does the integral I(α) = 0 x α P (x) dx converge? Give
Math 213br HW 1 solutions February 26, 2014 Problem 1 Let P (x) be a polynomial of degree d > 1 with P (x) > 0 for all x 0. For what values of α R does the integral I(α) = 0 x α P (x) dx converge? Give
RENEWAL THEORY IN ANALYSIS OF TRIES AND STRINGS: EXTENDED ABSTRACT
 RENEWAL THEORY IN ANALYSIS OF TRIES AND STRINGS: EXTENDED ABSTRACT SVANTE JANSON Abstract. We give a survey of a number of simple applications of renewal theory to problems on random strings, in particular
RENEWAL THEORY IN ANALYSIS OF TRIES AND STRINGS: EXTENDED ABSTRACT SVANTE JANSON Abstract. We give a survey of a number of simple applications of renewal theory to problems on random strings, in particular
From the Discrete to the Continuous, and Back... Philippe Flajolet INRIA, France
 From the Discrete to the Continuous, and Back... Philippe Flajolet INRIA, France 1 Discrete structures in... Combinatorial mathematics Computer science: data structures & algorithms Information and communication
From the Discrete to the Continuous, and Back... Philippe Flajolet INRIA, France 1 Discrete structures in... Combinatorial mathematics Computer science: data structures & algorithms Information and communication
Data Structures and Algorithms
 Data Structures and Algorithms Spring 2017-2018 Outline 1 Sorting Algorithms (contd.) Outline Sorting Algorithms (contd.) 1 Sorting Algorithms (contd.) Analysis of Quicksort Time to sort array of length
Data Structures and Algorithms Spring 2017-2018 Outline 1 Sorting Algorithms (contd.) Outline Sorting Algorithms (contd.) 1 Sorting Algorithms (contd.) Analysis of Quicksort Time to sort array of length
Enumerating connected labelled graphs
 Enumerating connected labelled graphs Keith Briggs Keith.Briggs@bt.com more.btexact.com/people/briggsk2/ 2004 August 17 conn-lab-graphs.tex typeset 2004 August 17 10:40 in pdflatex on a linux system Enumerating
Enumerating connected labelled graphs Keith Briggs Keith.Briggs@bt.com more.btexact.com/people/briggsk2/ 2004 August 17 conn-lab-graphs.tex typeset 2004 August 17 10:40 in pdflatex on a linux system Enumerating
A.CED.1.4. Rearrange formulas to highlight a quantity of interest, using the same reasoning as in solving equations.
 Algebra 2 Curriculum Map (including Honors) 2014-2015 First Nine Weeks 42 days Mathematics Florida Standards Student Performance Objectives by Benchmark Number and Quantity Quantities Reason quantitatively
Algebra 2 Curriculum Map (including Honors) 2014-2015 First Nine Weeks 42 days Mathematics Florida Standards Student Performance Objectives by Benchmark Number and Quantity Quantities Reason quantitatively
A class of trees and its Wiener index.
 A class of trees and its Wiener index. Stephan G. Wagner Department of Mathematics Graz University of Technology Steyrergasse 3, A-81 Graz, Austria wagner@finanz.math.tu-graz.ac.at Abstract In this paper,
A class of trees and its Wiener index. Stephan G. Wagner Department of Mathematics Graz University of Technology Steyrergasse 3, A-81 Graz, Austria wagner@finanz.math.tu-graz.ac.at Abstract In this paper,
A Note about the Pochhammer Symbol
 Mathematica Moravica Vol. 12-1 (2008), 37 42 A Note about the Pochhammer Symbol Aleksandar Petoević Abstract. In this paper we give elementary proofs of the generating functions for the Pochhammer symbol
Mathematica Moravica Vol. 12-1 (2008), 37 42 A Note about the Pochhammer Symbol Aleksandar Petoević Abstract. In this paper we give elementary proofs of the generating functions for the Pochhammer symbol
Two-stage allocations and the double Q-function
 Two-stage allocations and the double Q-function Sergey Agievich National Research Center for Applied Problems of Mathematics and Informatics Belarusian State University Fr. Skorina av. 4, 220050 Minsk,
Two-stage allocations and the double Q-function Sergey Agievich National Research Center for Applied Problems of Mathematics and Informatics Belarusian State University Fr. Skorina av. 4, 220050 Minsk,
Toufik Mansour 1. Department of Mathematics, Chalmers University of Technology, S Göteborg, Sweden
 COUNTING OCCURRENCES OF 32 IN AN EVEN PERMUTATION Toufik Mansour Department of Mathematics, Chalmers University of Technology, S-4296 Göteborg, Sweden toufik@mathchalmersse Abstract We study the generating
COUNTING OCCURRENCES OF 32 IN AN EVEN PERMUTATION Toufik Mansour Department of Mathematics, Chalmers University of Technology, S-4296 Göteborg, Sweden toufik@mathchalmersse Abstract We study the generating
The Subtree Size Profile of Bucket Recursive Trees
 Iranian Journal of Mathematical Sciences and Informatics Vol., No. (206, pp - DOI: 0.7508/ijmsi.206.0.00 The Subtree Size Profile of Bucket Recursive Trees Ramin Kazemi Department of Statistics, Imam Khomeini
Iranian Journal of Mathematical Sciences and Informatics Vol., No. (206, pp - DOI: 0.7508/ijmsi.206.0.00 The Subtree Size Profile of Bucket Recursive Trees Ramin Kazemi Department of Statistics, Imam Khomeini
Fourier transforms, Generalised functions and Greens functions
 Fourier transforms, Generalised functions and Greens functions T. Johnson 2015-01-23 Electromagnetic Processes In Dispersive Media, Lecture 2 - T. Johnson 1 Motivation A big part of this course concerns
Fourier transforms, Generalised functions and Greens functions T. Johnson 2015-01-23 Electromagnetic Processes In Dispersive Media, Lecture 2 - T. Johnson 1 Motivation A big part of this course concerns
CPSC 518 Introduction to Computer Algebra Schönhage and Strassen s Algorithm for Integer Multiplication
 CPSC 518 Introduction to Computer Algebra Schönhage and Strassen s Algorithm for Integer Multiplication March, 2006 1 Introduction We have now seen that the Fast Fourier Transform can be applied to perform
CPSC 518 Introduction to Computer Algebra Schönhage and Strassen s Algorithm for Integer Multiplication March, 2006 1 Introduction We have now seen that the Fast Fourier Transform can be applied to perform
On the mean connected induced subgraph order of cographs
 AUSTRALASIAN JOURNAL OF COMBINATORICS Volume 71(1) (018), Pages 161 183 On the mean connected induced subgraph order of cographs Matthew E Kroeker Lucas Mol Ortrud R Oellermann University of Winnipeg Winnipeg,
AUSTRALASIAN JOURNAL OF COMBINATORICS Volume 71(1) (018), Pages 161 183 On the mean connected induced subgraph order of cographs Matthew E Kroeker Lucas Mol Ortrud R Oellermann University of Winnipeg Winnipeg,
Conway s RATS Sequences in Base 3
 3 47 6 3 Journal of Integer Sequences, Vol. 5 (0), Article.9. Conway s RATS Sequences in Base 3 Johann Thiel Department of Mathematical Sciences United States Military Academy West Point, NY 0996 USA johann.thiel@usma.edu
3 47 6 3 Journal of Integer Sequences, Vol. 5 (0), Article.9. Conway s RATS Sequences in Base 3 Johann Thiel Department of Mathematical Sciences United States Military Academy West Point, NY 0996 USA johann.thiel@usma.edu
Algebraic aspects of some Riordan arrays related to binary words avoiding a pattern
 Algebraic aspects of some Riordan arrays related to binary words avoiding a pattern D. Merlini and R. Sprugnoli Dipartimento di Sistemi e Informatica viale Morgagni 65, 5034, Firenze, Italia merlini@dsi.unifi.it,
Algebraic aspects of some Riordan arrays related to binary words avoiding a pattern D. Merlini and R. Sprugnoli Dipartimento di Sistemi e Informatica viale Morgagni 65, 5034, Firenze, Italia merlini@dsi.unifi.it,
Hamming Weight of the Non-Adjacent-Form under Various Input Statistics. Clemens Heuberger and Helmut Prodinger
 FoSP Algorithmen & mathematische Modellierung FoSP Forschungsschwerpunkt Algorithmen und mathematische Modellierung Hamming Weight of the Non-Adjacent-Form under Various Input Statistics Clemens Heuberger
FoSP Algorithmen & mathematische Modellierung FoSP Forschungsschwerpunkt Algorithmen und mathematische Modellierung Hamming Weight of the Non-Adjacent-Form under Various Input Statistics Clemens Heuberger
Summations in Bernoulli s Triangles via Generating Functions
 2 3 47 6 23 Journal of Integer Sequences, Vol 20 (207, Article 73 Summations in Bernoulli s Triangles via Generating Functions Kamilla Oliver 9 Stellenberg Road 730 Somerset West Sout Africa olikamilla@gmailcom
2 3 47 6 23 Journal of Integer Sequences, Vol 20 (207, Article 73 Summations in Bernoulli s Triangles via Generating Functions Kamilla Oliver 9 Stellenberg Road 730 Somerset West Sout Africa olikamilla@gmailcom
Investigating Geometric and Exponential Polynomials with Euler-Seidel Matrices
 1 2 3 47 6 23 11 Journal of Integer Sequences, Vol. 14 (2011), Article 11.4.6 Investigating Geometric and Exponential Polynomials with Euler-Seidel Matrices Ayhan Dil and Veli Kurt Department of Mathematics
1 2 3 47 6 23 11 Journal of Integer Sequences, Vol. 14 (2011), Article 11.4.6 Investigating Geometric and Exponential Polynomials with Euler-Seidel Matrices Ayhan Dil and Veli Kurt Department of Mathematics
A General Lower Bound on the I/O-Complexity of Comparison-based Algorithms
 A General Lower ound on the I/O-Complexity of Comparison-based Algorithms Lars Arge Mikael Knudsen Kirsten Larsent Aarhus University, Computer Science Department Ny Munkegade, DK-8000 Aarhus C. August
A General Lower ound on the I/O-Complexity of Comparison-based Algorithms Lars Arge Mikael Knudsen Kirsten Larsent Aarhus University, Computer Science Department Ny Munkegade, DK-8000 Aarhus C. August
Stat 134 Fall 2011: Notes on generating functions
 Stat 3 Fall 0: Notes on generating functions Michael Lugo October, 0 Definitions Given a random variable X which always takes on a positive integer value, we define the probability generating function
Stat 3 Fall 0: Notes on generating functions Michael Lugo October, 0 Definitions Given a random variable X which always takes on a positive integer value, we define the probability generating function
8 Laws of large numbers
 8 Laws of large numbers 8.1 Introduction We first start with the idea of standardizing a random variable. Let X be a random variable with mean µ and variance σ 2. Then Z = (X µ)/σ will be a random variable
8 Laws of large numbers 8.1 Introduction We first start with the idea of standardizing a random variable. Let X be a random variable with mean µ and variance σ 2. Then Z = (X µ)/σ will be a random variable
Jacobi-Angelesco multiple orthogonal polynomials on an r-star
 M. Leurs Jacobi-Angelesco m.o.p. 1/19 Jacobi-Angelesco multiple orthogonal polynomials on an r-star Marjolein Leurs, (joint work with Walter Van Assche) Conference on Orthogonal Polynomials and Holomorphic
M. Leurs Jacobi-Angelesco m.o.p. 1/19 Jacobi-Angelesco multiple orthogonal polynomials on an r-star Marjolein Leurs, (joint work with Walter Van Assche) Conference on Orthogonal Polynomials and Holomorphic
Asymptotics of the Eulerian numbers revisited: a large deviation analysis
 Asymptotics of the Eulerian numbers revisited: a large deviation analysis Guy Louchard November 204 Abstract Using the Saddle point method and multiseries expansions we obtain from the generating function
Asymptotics of the Eulerian numbers revisited: a large deviation analysis Guy Louchard November 204 Abstract Using the Saddle point method and multiseries expansions we obtain from the generating function
Exact solution of site and bond percolation. on small-world networks. Abstract
 Exact solution of site and bond percolation on small-world networks Cristopher Moore 1,2 and M. E. J. Newman 2 1 Departments of Computer Science and Physics, University of New Mexico, Albuquerque, New
Exact solution of site and bond percolation on small-world networks Cristopher Moore 1,2 and M. E. J. Newman 2 1 Departments of Computer Science and Physics, University of New Mexico, Albuquerque, New
LAWS OF LARGE NUMBERS AND TAIL INEQUALITIES FOR RANDOM TRIES AND PATRICIA TREES
 LAWS OF LARGE NUMBERS AND TAIL INEQUALITIES FOR RANDOM TRIES AND PATRICIA TREES Luc Devroye School of Computer Science McGill University Montreal, Canada H3A 2K6 luc@csmcgillca June 25, 2001 Abstract We
LAWS OF LARGE NUMBERS AND TAIL INEQUALITIES FOR RANDOM TRIES AND PATRICIA TREES Luc Devroye School of Computer Science McGill University Montreal, Canada H3A 2K6 luc@csmcgillca June 25, 2001 Abstract We
An Entropy Bound for Random Number Generation
 244 An Entropy Bound for Random Number Generation Sung-il Pae, Hongik University, Seoul, Korea Summary Many computer applications use random numbers as an important computational resource, and they often
244 An Entropy Bound for Random Number Generation Sung-il Pae, Hongik University, Seoul, Korea Summary Many computer applications use random numbers as an important computational resource, and they often
On Buffon Machines & Numbers
 On Buffon Machines & Numbers Philippe Flajolet, Maryse Pelletier, Michèle Soria AofA 09, Fréjus --- June 2009 [INRIA-Rocquencourt & LIP6, Paris] 1 1733: Countess Buffon drops her knitting kit on the floor.
On Buffon Machines & Numbers Philippe Flajolet, Maryse Pelletier, Michèle Soria AofA 09, Fréjus --- June 2009 [INRIA-Rocquencourt & LIP6, Paris] 1 1733: Countess Buffon drops her knitting kit on the floor.
Regular Languages and Finite Automata
 Regular Languages and Finite Automata 1 Introduction Hing Leung Department of Computer Science New Mexico State University In 1943, McCulloch and Pitts [4] published a pioneering work on a model for studying
Regular Languages and Finite Automata 1 Introduction Hing Leung Department of Computer Science New Mexico State University In 1943, McCulloch and Pitts [4] published a pioneering work on a model for studying
CS6375: Machine Learning Gautam Kunapuli. Decision Trees
 Gautam Kunapuli Example: Restaurant Recommendation Example: Develop a model to recommend restaurants to users depending on their past dining experiences. Here, the features are cost (x ) and the user s
Gautam Kunapuli Example: Restaurant Recommendation Example: Develop a model to recommend restaurants to users depending on their past dining experiences. Here, the features are cost (x ) and the user s
Math 3 Unit 5: Polynomial and Rational Representations and Modeling
 Approximate Time Frame: 5-6 weeks Connections to Previous Learning: In Math 1 and 2, students worked with one-variable equations. They studied linear, exponential and quadratic functions and compared them
Approximate Time Frame: 5-6 weeks Connections to Previous Learning: In Math 1 and 2, students worked with one-variable equations. They studied linear, exponential and quadratic functions and compared them
APPROXIMATING CONTINUOUS FUNCTIONS: WEIERSTRASS, BERNSTEIN, AND RUNGE
 APPROXIMATING CONTINUOUS FUNCTIONS: WEIERSTRASS, BERNSTEIN, AND RUNGE WILLIE WAI-YEUNG WONG. Introduction This set of notes is meant to describe some aspects of polynomial approximations to continuous
APPROXIMATING CONTINUOUS FUNCTIONS: WEIERSTRASS, BERNSTEIN, AND RUNGE WILLIE WAI-YEUNG WONG. Introduction This set of notes is meant to describe some aspects of polynomial approximations to continuous
A Master Theorem for Discrete Divide and Conquer Recurrences. Dedicated to PHILIPPE FLAJOLET
 A Master Theorem for Discrete Divide and Conquer Recurrences Wojciech Szpankowski Department of Computer Science Purdue University U.S.A. September 6, 2012 Uniwersytet Jagieloński, Kraków, 2012 Dedicated
A Master Theorem for Discrete Divide and Conquer Recurrences Wojciech Szpankowski Department of Computer Science Purdue University U.S.A. September 6, 2012 Uniwersytet Jagieloński, Kraków, 2012 Dedicated
On the number of heaps and the cost of heap construction
 On the number of heaps and the cost of heap construction Hsien-Kuei Hwang Institute of Statistical Science Academia Sinica Taipei 5 Taiwan Jean-Marc Steyaert LIX École Polytechnique 928 Palaiseau France
On the number of heaps and the cost of heap construction Hsien-Kuei Hwang Institute of Statistical Science Academia Sinica Taipei 5 Taiwan Jean-Marc Steyaert LIX École Polytechnique 928 Palaiseau France
Asymptotic Notation. such that t(n) cf(n) for all n n 0. for some positive real constant c and integer threshold n 0
 Asymptotic Notation Asymptotic notation deals with the behaviour of a function in the limit, that is, for sufficiently large values of its parameter. Often, when analysing the run time of an algorithm,
Asymptotic Notation Asymptotic notation deals with the behaviour of a function in the limit, that is, for sufficiently large values of its parameter. Often, when analysing the run time of an algorithm,
On the Average Path Length of Complete m-ary Trees
 1 2 3 47 6 23 11 Journal of Integer Sequences, Vol. 17 2014, Article 14.6.3 On the Average Path Length of Complete m-ary Trees M. A. Nyblom School of Mathematics and Geospatial Science RMIT University
1 2 3 47 6 23 11 Journal of Integer Sequences, Vol. 17 2014, Article 14.6.3 On the Average Path Length of Complete m-ary Trees M. A. Nyblom School of Mathematics and Geospatial Science RMIT University
On the parity of the Wiener index
 On the parity of the Wiener index Stephan Wagner Department of Mathematical Sciences, Stellenbosch University, Stellenbosch 7602, South Africa Hua Wang Department of Mathematics, University of Florida,
On the parity of the Wiener index Stephan Wagner Department of Mathematical Sciences, Stellenbosch University, Stellenbosch 7602, South Africa Hua Wang Department of Mathematics, University of Florida,
