A Constraint-Reduced Variant of Mehrotra s Predictor-Corrector Algorithm
|
|
|
- August Thomas
- 5 years ago
- Views:
Transcription
1 A Constraint-Reduced Variant of Mehrotra s Predictor-Corrector Algorithm Luke B. Winternitz, Stacey O. Nicholls, André L. Tits, Dianne P. O Leary September 24, 2007 Abstract Consider linear programs in dual standard form with n constraints and m variables. When typical interior-point algorithms are used for the solution of such problems, updating the iterates, using direct methods for solving the linear systems and assuming a dense constraint matrix A, requires O(nm 2 ) operations. When n m it is often the case that at each iteration most of the constraints are not very relevant for the construction of a good update and could be ignored to achieve computational savings. This idea has been considered in the 1990s by Dantzig and Ye, Tone, Kaliski and Ye, den Hertog et al. and others. More recently, Tits et al. proposed a simple constraint-reduction scheme and proved global and local quadratic convergence for a dual-feasible primal-dual affine-scaling method modified according to that scheme. In the present work, similar convergence results are proved for a dual-feasible constraint-reduced variant of Mehrotra s predictor-corrector algorithm. Some promising numerical results are reported. 1 Introduction Consider the primal and dual standard forms of linear programming (LP): min c T x s.t. Ax = b, x 0, and max b T y s.t. A T y c, where A is an m n matrix with n m, that is, the dual problem has many more inequality constraints than variables. We assume b 0. 1 The dual problem can alternatively be written in the form (with slack variable s) max b T y s.t. A T y + s = c, s 0. (2) Some of the most effective algorithms for solving LPs are the primal-dual interior-point methods (PDIPMs), which apply Newton s method, or variations thereof, to the perturbed Karush-Kuhn-Tucker (KKT) optimality conditions for the primal-dual pair (1): This work was supported by NSF grant DMI and DoE grant DEFG0204ER The work of the first author was supported by NASA under the Goddard Space Flight Center Study Fellowship Program. Any opinions, findings, and conclusions or recommendations expressed in this paper are those of the authors and do not necessarily reflect the views of the National Science Foundation, those of the US Department of Energy, or those of NASA. Department of Electrical and Computer Engineering and the Institute for Systems Research, University of Maryland College Park (lukewinternitz@gmail.com, andre@umd.edu) Applied Mathematics and Scientific Computing Program, University of Maryland College Park (son@math.umd.edu) Department of Computer Science and Institute for Advanced Computer Studies, University of Maryland College Park (oleary@cs.umd.edu) 1 This assumption is benign, since if b = 0 the problem at hand is readily solved: any dual feasible point y 0 (assumed available for the algorithm analyzed in this paper) is dual optimal and x = 0 is primal optimal. (1) 1
2 A T y + s c = 0, Ax b = 0, (3) Xs τe = 0, (x,s) 0, with X = diag(x), S = diag(s), e the vector of all ones, and τ a positive parameter. As τ ranges over (0, ), the unique (if it exists) 2 solution (x,y,s) to this system traces out the primal-dual central path. Newton-type steps for system (3) are obtained by solving one or more linear systems of the form 0 A T I x f A 0 0 y = g, (4) S 0 X s h where f, g, and h are certain vectors of appropriate dimension. System (4) is often solved by first eliminating s, giving the augmented system ( A 0 S XA T )( ) ( ) x g =, (5) y h Xf s = f A T y, or by further eliminating x, giving the normal system AS 1 XA T y = g AS 1 (h Xf), s = f A T y, (6) x = S 1 (h X s). irrelevant? redundant active Figure 1: A view of the y space when m = 2 and n = 12. The arrow indicates the direction of vector b. The two active constraints are critical and define the solution, while the others are redundant or perhaps not very relevant for the formation of good search directions. When n m, a drawback of most interior-point methods is that the computational cost of determining a step is rather high. For example, in the context of PDIPMs, if we choose to solve (6) by a direct method and A is dense, the most expensive computation is forming the normal matrix AS 1 XA T, which costs O(nm 2 ) operations. This computation involves forming the sum AS 1 XA T = n i=1 x i s i a i a T i, (7) 2 System (3) has a unique solution for each τ > 0 (equivalently, for some τ) if there exists (x, y, s) with Ax = b, A T y + s = c and (x, s) > 0 [Wri97, Thm. 2.8, p39]. This is the so called Slater or interior-point condition. 2
3 where a i is the ith column of A and x i and s i are the ith components of x and s respectively, so that each term of the sum corresponds to a particular constraint in the dual problem. Note however that we expect most of the n constraints are redundant or not very relevant for the formation of a good search direction (see Figure 1). In (7), if we were to select a small set of q < n important constraints and compute only the corresponding partial sum, then the work would be reduced to O(qm 2 ) operations. Similar possibilities arise in other interior-point methods: by somehow ignoring most of the constraints, we may hope that a good step can still be computed, at significantly reduced cost. (Such a step may even be better: see [DNPT06] for evidence of potential harm caused by redundant constraints.) This observation is the basis of the present paper. In the sequel we refer to methods that attempt such computations as constraint-reduced. Prior work investigating this question started at least as far back as Dantzig and Ye [DY91], who proposed a build-up variant of a dual affine-scaling algorithm. In their scheme, at each iteration, starting with a small working set of constraints, a dual affine-scaling step is computed. If this step is feasible with respect to the full constraint set, then it is taken. Otherwise, more constraints are added to the working set and the process is repeated. Convergence of this method was shown to follow from prior convergence results on the dual affine-scaling algorithm. At about the same time, Tone [Ton93] developed an active set version of Ye s dual potential-reduction (DPR) algorithm [Ye91]. There, starting with a small working set of constraints, a DPR-type search direction is computed. If a step along this direction gives a sufficient decrease of the potential function, then it is accepted. Otherwise, more constraints are added to the working set and the process is repeated. Convergence and complexity results are essentially inherited from the properties of the DPR algorithm. Kaliski and Ye [KY93] considered a variant of Tone s algorithm and investigated applying the method to large scale transportation problems. Remarkable computational results were obtained. A different approach was used by den Hertog et al. [dhrt94] who proposed a build-up and down path-following algorithm based on a dual logarithmic barrier method. Starting from an interior dual-feasible point, the central path corresponding to a small set of working constraints is followed until it becomes infeasible with respect to the full constraint set, whereupon the working set is appropriately updated and the process restarts from the previous iterate. The authors proved an O( q log 1 ε ) iteration complexity bound for this algorithm, where q is the maximum size of the working constraint set during the iteration. Notably, this suggests that both the computational cost per iteration and the iteration complexity may be reduced. However, it appears that in this algorithm the only sure upper bound on q is n. A common component of [DY91, Ton93, dhrt94] is the backtracking that adds constraints and tries again when the step generated using the working constraint set fails to pass certain acceptability tests. In constrast, no such backtracking is used in [TAW06] where the authors considered constraint reduction for primal-dual algorithms. In particular, they proposed constraint-reduced versions of a primal-dual affinescaling algorithm (rpdas) and of Mehrotra s Predictor-Corrector algorithm (rmpc). As in [DY91, Ton93, dhrt94], at each iteration, rpdas and rmpc use a small working set of constraints to generate a step, but this step is not subjected to acceptability tests; it is simply taken. This has the advantage that the cost per iteration can be guaranteed to be cheaper than when the full constraint set is used; however it may preclude polynomial complexity results, as were obtained in [Ton93] and [dhrt94]. Global and local quadratic convergence of rpdas was proved in [TAW06] (under nondegeneracy assumptions) using a nonlinear programming inspired line of argument [Her82, PTH88] and promising numerical results were reported. To our knowledge, aside from the analysis of rpdas in [TAW06], no attempts have been made to date at analyzing constraint-reduced versions of PDIPMs, the leading class of interior-points methods over the past decade. This observation applies in particular to the current champion, Mehrotra s Predictor Corrector algorithm (MPC, [Meh92]), which combines an adaptive choice of the perturbation parameter τ in (3), a second order correction to the Newton direction, and several ingenious heuristics which together have proven to be extremely effective. Investigations of the convergence properties of variants of MPC are reported in [Meh92, ZZ95, ZZ96, SPT05, ST05, Car04]. In the present paper, we follow the line of analysis of [Her82, PTH88, TAW06] to analyze a proposed dual-feasible constraint-reduced version of MPC, inspired from rmpc of [TAW06], which we term rmpc*. The main contribution is this analysis, and also a somewhat different, and perhaps more natural, perspective on the notion of constraint reduction than was put forth in [TAW06] (see Remark 2.1 below). We prove global and local quadratic convergence of rmpc under certain nondegeneracy assumptions. We also report 3
4 on numerical experiments investigating the performance of rmpc on randomly generated LPs and on LPs arising from the discretization of a class of semi-infinite linear programming problems. Various rules for choosing the working constraint set are proposed and investigated numerically. The notation in this paper is mostly standard. We use to denote the 2-norm or its induced operator norm. Given a vector x R n, we let X = diag(x) denote the diagonal n n matrix with x on its main diagonal. We define n := {1,2,...n} and given any index set n, we use A to denote the m (where is the cardinality of ) matrix obtained from A by deleting all columns a i with i. Similarly, we use x and s to denote the vectors of size obtained from x and s by deleting all entries x i and s i with i. We define e to be the column vector of ones, with length determined by context. For a vector v, [v] is defined by ([v] ) i := min{v i,0}. Further, we define the dual feasible, dual strictly feasible, and dual solution sets, respectively, as The active set at y F is F := {y R m A T y c}, F o := {y R m A T y < c}, F := {y F b T y b T w for all w F }. I(y) := {i n a T i y = c i }. We term a vector y R m stationary if A T y c and there exists x R n with Ax = b and X(c A T y) = 0. Such an x is called a multiplier associated to the stationary point y. (A stationary vector y belongs to F if and only if x 0.) Lowercase k always indicates an iteration count, and limits of the form y k y are meant as k. Uppercase K generally refers to an infinite index set and the qualification on K is synonymous with for k K. In particular, y k y on K means y k y as k, k K. Finally we define and J(G,u,v) := G GT I diag(v) 0 diag(u) ( G 0 J a (G,u,v) := diag(v) diag(u)g T for any matrix G and vectors u and v of compatible dimensions (cf. systems (4) and (5)). (8) The rest of the paper is structured as follows. Section 2 contains the definition and discussion of algorithm rmpc. Sections 3 and 4 contain the global and local convergence analyses, respectively. Some numerical results are presented in section 5, and conclusions are drawn in section 6. 2 A Constraint-Reduced MPC Algorithm 2.1 A convergent variant of MPC Our proposed algorithm, rmpc, is based on the implementation of MPC discussed in [Wri97, Ch. 10], which we state here for ease of reference. Iteration MPC [Meh92, Wri97]. Parameter. β (0,1). Data. y R m, s R n with s > 0, x R n with x > 0, µ := x T s/n. Step 1. Compute the affine scaling direction, i.e., solve 0 AT I x a A 0 0 y a = c AT y s b Ax (10) S 0 X s a Xs ) (9) 4
5 for ( x a, y a, s a ) and set Step 2. Compute the centering parameter where µ a := (x + t a p x a ) T (s + t a d sa )/n. t a p := arg max{t [0,1] x + t x a 0}, (11) t a d := arg max{t [0,1] s + t s a 0}. (12) σ:=(µ a /µ) 3, (13) Step 3. Compute the centering/corrector direction, i.e., solve 0 A T I x c 0 A 0 0 y c = 0 (14) S 0 X s c σµe X a s a for ( x c, y c, s c ). Step 4. Form the total search direction and set Step 5. Update the variables: set set and compute ( x m, y m, s m ):=( x a, y a, s a ) + ( x c, y c, s c ), (15) t m p := arg max{t [0,1] x + t x m 0}, (16) t m d := arg max{t [0,1] s + t s m 0}. (17) t m p :=β t m p, t m d :=β t m d, (18) (x +,y +,s + ):=(x,y,s) + (t m p x m, t m d y m, t m d s m ), (19) µ + := (x+ ) T (s + ). (20) n Algorithm MPC is of the infeasible type, in that it does not require the availability of a feasible initial point. 3 In contrast, the global convergence analysis for Algorithm rmpc (see section 3 below) critically relies on the monotonic increase of the dual objective b T y from iteration to iteration, and for this we do need a dual feasible initial point. As stated, Iteration MPC has no known convergence guarantees. Previous approaches to providing such guarantees involve introducing certain safeguards or modifications [Meh92, ZZ95, ZZ96, SPT05, ST05, Car04]. We do this here as well. Specifically, aside from the constraint-reduction mechanism (to be discussed in section 2.2), Iteration rmpc proposed below has four differences from Iteration MPC, all motivated by the structure of the convergence analysis adapted from [Her82, PTH88, TZ94, TAW06]. These differences, which occur in Steps 2, 4, and 5, are discussed next. Numerical experience suggests that they do not negatively affect the performance of the algorithm. The first difference, in Step 2, is the formula for the centering parameter σ. Instead of using (13), we set σ := (1 t a ) λ, 3 In MPC and rmpc (and most PDIPMs for that matter), dual (primal) feasibility of the initial iterate implies dual (primal) feasibility of all subsequent iterates. 5
6 where t a := min{t a p, t a d } and λ 2 is a scalar algorithm parameter. This formula agrees with (13) when λ = 3, (x,y,s) is primal and dual feasible, and t a = t a p = t a d. In general, both formulas result in similar empirical performance, while the new formula simplifies our analysis. The second difference is in Step 4, where we introduce a mixing parameter γ (0,1] and replace (15) with ( x m, y m, s m ):=( x a, y a, s a ) + γ( x c, y c, s c ). (21) Nominally we want γ = 1, but we reduce γ as needed to enforce three properties of our algorithm that are essential for the analysis. The first such property is the monotonic increase of b T y mentioned previously. While, given dual feasibility, it is readily verified that y a is an ascent direction for b T y (i.e., b T y a > 0), this may not be the case for y m, defined in (15). To enforce monotonicity we choose γ γ 1 where γ 1 is the largest number in [0,1] such that b T ( y a + γ 1 y c ) θb T y a, with θ (0,1) an algorithm parameter. It is easily verified that γ 1 is given by { 1 b T y c 0, γ 1 = min { 1, (1 θ) bt y a b T y } b T y c < 0. c The second essential property addressed via the mixing parameter is that (22) y a small implies y m and γσµ are also small. This smallness property is enforced (along with the first property) by requiring γ γ 0, where { } γ 0 := min γ 1,ψ ya y c,ψ ya, (23) σµ and ψ > 0 is another algorithm parameter. The final property enforced by γ is that t m d ζt a d, (24) where ζ (0,1) is a third algorithm parameter and t m d depends on γ via (17) and (21). We could choose γ to be the largest number in [0,γ 0 ] such that (24) holds, but this would seem to require a potentially expensive iterative procedure. Instead, rmpc sets where γ := { γ 0 t m d,0 ζta d γ 0 (1 ζ) t m d,0 (1 ζ) t m d,0 +(ζta d t m d,0 ) t m d,0 < ζta d (25) t m d,0 := arg max{t [0,1] s + t( s a + γ 0 s c ) 0}. (26) Geometrically, if t m d,0 ζta d then γ = γ 0, but otherwise γ [0,γ 0 ) and is selected in such a way that the search direction s m = s a +γ s c goes through the intersection of the line segment connecting s+ζt a d sa and s + ζt a d ( sa + γ 0 s c ) with the feasible line segment connecting s + t a d sa and s + t m d,0 ( sa + γ 0 s c ). See Figure 2. Since the intersection point s + ζt a d ( sa + γ s c ) is feasible, (24) will hold. In spite of these three requirements on γ, it is typical that γ = 1 in practice (with appropriate choice of algorithm parameters, as in section 5), except when aggressive constraint reduction is used (i.e., very few constraints are retained at each iteration). The remaining two differences between rmpc and MPC (aside from constraint reduction) are in Step 5. First, (18) is replaced by t m p := max{β t m p, t m p y a } (27) and similarly for t m d, to allow for local quadratic convergence. Second, the primal update is replaced by a componentwise clipped (from above and below) version of the primal update in (19). Namely, defining ˆx := x + t m p x m and x a := x + x a, for all i n, we update x i to x + i := min{max{ˆx i, min{ξ max, y a ν + [ x a ] ν }}, ξ}, (28) 6
7 s + t a d sa s + ζt a d sa s + t m d ( sa + γ s c ) s 0 s + ζt a d ( sa + γ s c ) s + t m d,0 ( sa + γ 0 s c ) s + ζt a d ( sa + γ 0 s c ) Figure 2: Enforcing t m d ζt a d with γ. The positive orthant here represents the feasible region s 0 in twodimensional slack space. The top arrow shows the step taken from some s > 0 along the affine scaling direction s a. The bottom arrow is the step along the MPC step with mixing parameter γ 0. In this picture, the damping factor t m d,0 is less than ζt a d, so we do not choose γ = γ 0. Rather, we take a step along the direction from s that passes through the intersection of two lines: the line consisting of points of the form s + ζt a d( s a + γ s c ) with γ [0, γ 0] and the feasible line connecting s + t a d s a and s + t m d,0( s a + γ 0 s c ). The maximum feasible step along this direction has length t m d ζt a d. where ν 2, ξ max (small) and ξ (large) are positive algorithm parameters. Formula (28) is adapted from [TAW06]. The lower bound, min{ξ max, y a ν + [ x a ] ν }, ensures that the components of x remain bounded away from zero away from KKT points (which is crucial to the global convergence analysis), while allowing for local quadratic convergence. Parameter ξ max, the maximum value of the lower bound, is not needed in our convergence analysis, but is important in practice; if ξ max is set sufficiently small, then normally x + = ˆx and the resulting iteration emulates the behavior of Iteration MPC. The upper bound parameter ξ ensures boundedness of the primal sequence, which is needed in the analysis; in practice performance is unaffected even if we set ξ = A constraint reduction mechanism Given a working set of constraints and a dual-feasible point (x,y,s), we compute an MPC-type direction for the reduced primal-dual pair min c T x s.t. A x = b, x 0, and max b T y s.t. A T y + s = c, s 0. To that effect, we first compute the reduced affine-scaling direction by solving 0 AT I x a 0 A 0 0 y a = b A x (30) S 0 X s a X s and then the reduced centering-corrector direction by solving 0 AT I x c 0 A 0 0 y c = 0, (31) S 0 X s c σµ e X s a a where µ := (x ) T (s )/. As discussed above, we combine these components using the mixing parameter γ to get our primal and dual search directions: ( x m, y m, s m ):=( x a, y a, s a ) + γ( x c, y c, s c ). (32) (29) 7
8 This leaves the search direction in the n \ components of x m and s m unspecified. However, using an update of the form (19) and requiring dual feasibility from iteration to iteration requires that we set s a n\:= A T n\ y a and s c n\:= A T n\ y c. Thus, we augment (32) accordingly, yielding the search direction for x, y, and s, ( x m, y m, s m ) = ( x a, y a, s a ) + γ( x c, y c, s c ). (33) However, we do not update x n\ by taking a step along a computed direction. Rather, inspired by an idea in [Ton93], we first consider the update x + i :=µ+ s + i i n \, with µ + := (x + ) T (s + )/. This makes (x + n\,s + n\) perfectly centered. Indeed, µ + = (x+ ) T (s + ) n = (x+ ) T (s + ) + (x + n\) T (s + n\) n = n µ+ + i n\ x + i s+ i n = n µ+ + n µ + = µ + n, and hence x + i s+ i = µ + for all i n \. However, since the analysis requires that the primal iterates remain bounded, we use instead, for i n \, ˆx i := µ+ s +, x + i := min{ˆx i,ξ}. (34) i Like the upper bound in (28), bound ξ in (34) was never active in numerical tests (when chosen appropriately large). Remark 2.1. A somewhat different approach to constraint-reduction, where the motivating idea of ignoring irrelevant constraints is less prominent, is used in [TAW06]. There, instead of the reduced systems, (30)- (31), full systems of equations of the form (4) are solved via the corresponding normal systems (6), only with the normal matrix AS 1 XA T replaced by the reduced normal matrix A S 1 X A T. Possible benefits of the approach taken here in rmpc are: 1) the [TAW06] approach is essentially tied to the normal equations, whereas our approach is not, 2) if we do solve the normal equations (62) (below) there is a (mild) computational savings over algorithm rmpc of [TAW06] and 3) initial computational experiments suggest that rmpc is at least as efficient as rmpc in practice. Before formally defining Iteration rmpc, we define the set of admissible s. Here we follow [TAW06] in requiring that contain m most nearly active constraints. 4 However, we depart from [TAW06] in that we also require to satisfy rank(a ) = m. (In [TAW06] this rank condition is still needed, but is enforced differently, through a rather strong assumption on A.) Specifically, we require that be selected from the set (y) := { n rank(a ) = m,, = m, and (c A T y) i (c A T y) j i,j / }. (35) In words, A must have full rank and must contain m most nearly active constraints. We are now ready to state Iteration rmpc. Iteration rmpc. Parameters. β (0,1), θ (0,1), ψ > 0, ζ (0,1), λ 2, ν 2, ξ max > 0, and ξ > 0. Data. y R m, s R n, such that A T y + s = c and s > 0, x R n such that x > 0, (y), µ := (x ) T (s )/. 4 Of course, nearness to activity can be measured in different ways. Here by most active constraints, we mean those having the smallest slack values. When the columns of A are normalized to unit 2-norm, the slack in a constraint is just the Euclidean distance to the constraint boundary. Also see Remark 2.3 below on invariance under scaling. 8
9 Step 1. Compute the affine scaling direction, i.e., solve (30) for ( x a, y a, s a ), set s a n\ = A T n\ y a, and set Step 2. Compute the centering parameter t a p := arg max{t [0,1] x + t x a 0}, (36) t a d := arg max{t [0,1] s + t s a 0}, (37) t a := min{t a p,t a d}. (38) σ:= (1 t a ) λ. (39) Step 3. Compute the centering/corrector direction, i.e., solve (31) for ( x c, y c, s c ) and set s c n\ := A T n\ y c. Step 4. Form the total search direction ( x m, y m, s m ):=( x a, y a, s a ) + γ( x c, y c, s c ), (40) where γ is as in (25), with µ (in (23)) replaced by µ. Set t m p := arg max{t [0,1] x + t x m 0}, (41) t m d := arg max{t [0,1] s + t s m 0}. (42) Step 5. Update the variables: set t m p := max{β t m p, t m p y a }, (43) t m d := max{β t m d, t m d ya }, (44) and set (ˆx,y +,s + ):=(x,y,s) + (t m p x m, t m d y m, t m d s m ). (45) For each i, set x + i := min{max{ˆx i, min{ξ max, y a ν + [ x a ] ν }}, ξ}, (46) where x a is defined by Set and, for each i n \, set { x a xi + x i:= a i i, 0 i n \. µ + := (x+ ) T (s + ) (47) (48) ˆx i := µ+ s +, i (49) x + i := min{ˆx i,ξ}. (50) Step 6. Choose a new set of constraints + (y + ) and compute µ + := (x+ ) T (s + ) (51) 9
10 In the convergence analysis, we will also make use of the quantities x m, s a, and s m defined by the following expressions: { x m xi + x i := m i i, (52) 0 i n \, s a := s + s a, (53) s m := s + s m. (54) Remark 2.2. As in iteration MPC, rmpc uses separate step sizes for the primal and dual variables. In practice, this has been observed by many to be preferable to using a common step size. However, often in convergence analysis of MPC-type algorithms a common step size is assumed. We found that using separate step sizes simplified our analysis and was, in fact, necessary for proving a critical result (Proposition 4.4). Remark 2.3. While rmpc as stated fails to retain the remarkable invariance properties of MPC, invariance under diagonal scaling in the primal space and under Euclidean transformations and uniform diagonal scaling in the dual space can be readily recovered (without affecting the theoretical properties of the algorithm) by modifying iteration rmpc along lines similar to those discussed in section 5 of [TAW06]. In closing this section, we note a few immediate results to be used in the remainder of the paper. First, the following identities are valid for j {a,m}: { { }} t j x i p = min 1,min x j i, x j i < 0, (55) i { }} t j d {1,min = min s i s j s j i < 0. (56) i Next, the following are direct consequences of equations (30)-(31) and Steps 1 and 3 of Iteration rmpc : and, for i, s j = A T y j for j {a,c,m}, (57) s i s i x a i + x i s a i = x i s i, (58) x i s a = x i i x a and i x a = s i i s a, (59) i s i x m i + x i s m i = x i s i + γ(σµ x a i s a i). (60) Further, system (30) can alternatively be solved in augmented system form ( )( ) ( ) A 0 x a S X A T b A x y a =, (61) X s or in normal equations form s a = A T y a, A S 1 X A T y a = b, (62a) s a = A T y a, (62b) x a = x S 1 X s a. (62c) Similarly, (31) can be solved in augmented system form ( )( ) ( ) A 0 x c S X A T 0 y c = σµ e X s a a, (63) s c = A T y c, 10
11 or in normal equations form A S 1 X A T y c = A S 1 (σµ X s a a ), (64a) s c = A T y c, (64b) x c = S 1 X s c + S 1 (σµ X s a a ). (64c) Finally, as an immediate consequence of the definition (21) of the rmpc search direction in Step 4 of Iteration rmpc and the expressions (23) and (25) (in particular (23)), we have γ y c ψ y a, γσµ ψ y a. (65) 3 Global Convergence Analysis The analysis given here follows the line of argument used in [TAW06] for the rpdas algorithm. We first list the assumptions we use in the global convergence analysis. Each result to follow will state explicitly which, if any, of these assumptions it relies on. Assumption 1. A has full row rank. Assumption 2. The dual solution set F is nonempty and bounded. Assumption 3. For all y F, {a i : i I(y)} is a linearly independent set. Note that the first assumption ensures that (y) is always nonempty. The next two lemmas are taken (almost) verbatim from [TAW06, Lemmas 1 and 2]. Lemma 3.1. J a (A,x,s) is nonsingular if and only if J(A,x,s) is. Further suppose x 0 and s 0. Then J(A,x,s) is nonsingular if and only if (i) x i + s i > 0 for all i, (ii) {a i : s i = 0} is linearly independent, and (iii) {a i : x i 0} spans R m. Lemma 3.2. Let x > 0, s > 0, and (y) for some y R m. Then A X S 1 A T is positive definite. The following proposition, which builds on [TAW06, Prop. 3], shows that Iteration rmpc is well defined and that the dual objective strictly increases. Proposition 3.3. Let x > 0, s > 0, and (y) for some y R m. Then the following hold: (i) b T y a > 0, (ii) b T y m θb T y a, and (iii) t m p > 0, t m d > 0, y+ F o, s + = c A T y + > 0, and x + > 0. Proof. Claim (i) follows directly from Lemma 3.2, (62) and b 0, which imply For claim (ii), if b T y c 0, then, by claim (i), b T y a = b T (A S 1 X A T ) 1 b > 0. b T y m = b T y a + γb T y c b T y a θb T y a, and from step 4 of Iteration rmpc, if b T y c < 0 then, using claim (i) and since γ γ 1, b T y m b T y a + γ 1 b T y c b T y a + (1 θ) bt y a Finally, claim (iii) follows from steps 4-5 of Iteration rmpc. b T y c bt y c = b T y a (1 θ)b T y a = θb T y a. Hence, under Assumption 1 (which ensures that (y) is always nonempty), Iteration rmpc can be executed repeatedly to generate an infinite sequence of iterates. From here on we attach an iteration index k to the quantities generated. In view of Proposition 3.3, the sequence of dual objective values {b T y k } is monotonically increasing. As in [TAW06, Lemma 5], under Assumption 2 and in view of Proposition 3.3, this implies boundedness of {y k }. 11
12 Lemma 3.4. Suppose Assumptions 1 and 2 hold. Then {y k } is bounded. Our global convergence analysis critically relies on the fact (see Lemma 3.6 below) that if y a,k is small then y k is close to a stationary point and x a,k is close to the corresponding multiplier. An essential property of our working set selection strategy, to be used repeatedly in the global and local convergence analyses is that, under Assumptions 1 and 3, k eventually includes the indices of all critical constraints. Specifically the following holds. Lemma 3.5. Suppose Assumptions 1 and 3 hold and for some y R m, y k y on an infinite index set K. Then I(y ) k for all sufficiently large k K. Proof. Assumption 3 implies I(y ) m, and in view of the definition (35) of (y k ), the claim follows by convergence of {y k } k K to y. The next step in the global convergence analysis is to establish that, if { y a,k } goes to zero on a subsequence, then, on the same subsequence, {y k } tends to a stationary point, and both { x a,k } and { x m,k } converge to the associated multiplier (c.f. [TAW06, Lemma 6]). Lemma 3.6. Suppose Assumptions 1 and 3 hold and for some y R m, y k y on an infinite index set K. If y a,k 0 on K, then y is stationary and both { x a,k } k K and { x m,k } k K converge to x, where x is the multiplier associated with y. Proof. The second block equation in (30) yields, for all k, and (58) yields for all k and all i k, A k x a,k k b = 0 (66) s k i x a,k i Now, let s := c A T y, and suppose y a,k 0 on K. sufficiently large. We claim that for all i n \ I(y ), + x k i s a,k i = 0, (67) Lemma 3.5 implies I(y ) k for k K x a,k i 0 on K. (68) Suppose it is not the case. Then for some i n \ I(y ), and an infinite index set K K, inf k K x a,k i > 0. This implies that i k for all k K since x a,k i := 0 for all i n \ k. Thus in view of (67), since s a,k i 0 on K (by (57)) and {x k } is bounded (by construction), we must have s k i 0 on K, so s i = 0, but this contradicts i n \ I(y ). From (66) and (68) it follows that A I(y ) x a,k I(y ) b 0 on K. Next, Assumption 3 implies that the columns of A I(y ) are linearly independent which, in view of (68), implies that x a,k x on K, for some x. Taking limits in (66) and (67) as k, k K gives Ax = A I(y )x I(y ) = b and X s = 0; i.e., y is stationary with multiplier x. Finally we turn to { x m,k } k K. The second block equations of (30) and (31), together with (40), yield, for all k and (60) yields for all k and all i k, s k i x m,k i + x k i s m,k i A k x m,k k b = 0, (69) = γ k (σ k µ k k xa,k i s a,k i ). (70) Convergence of { x a,k } k K and boundedness of {x k } imply boundedness of { x a,k k } k K since x a,k k = x a,k k x k k. In addition, y a,k 0 on K and relations (65) give γ k σ k µ k k 0 on K and γ k y c,k 0 on K which, in turn, implies γ k s c,k = γ k A T y c,k 0 on K by (57). So, in view of (40), (57), and (65), we see that the subsequence { s m,k } k K and the entire right-hand side of (70) converge to zero on K. With these facts, the same argument as above yields the remaining portion of the claim. 12
13 Hence, when y a,k becomes small on a subsequence, a stationary point is approached, as desired. Could it be however that y a,k does not become small, while y k converges on a subsequence to some limit point? The next result, which will used in Lemma 3.9 below as part of a contradiction argument, shows that a KKT point must then be approached on the previous subsequence (cf. [TAW06, Lemma 7]). Lemma 3.7. Suppose Assumptions 1, 2 and 3 hold. If K is an infinite index set such that then y a,k 0 on K. inf{ y a,k 1 ν + [ x a,k 1 ] ν k K} > 0, (71) Proof. We proceed by contradiction. Suppose the claim does not hold; that is, suppose (71) holds but y a,k 0 on K. Then for some infinite index set, K K, inf{ y a,k > 0 k K } > 0. Since {y k } (see Lemma 3.4) and {x k } (by construction) are bounded, assume without loss of generality that they converge on K to y and x respectively. Since k is selected from a finite set, we may also assume without loss of generality that, for some fixed n, k = for all k K. In view of Lemma 3.5, we may further assume that I(y ). Also, note that (71) and (46) imply that for each i, {x k i } k K is bounded away from zero and positive and hence x > 0. The idea in the remainder of the proof is to show that, under the contradiction hypothesis, the dual objective increases by a constant amount infinitely many times, i.e., there exists δ > 0 such that b T y k+1 > b T y k + δ for all k K. This implies by monotonicity (Proposition 3.3) that {y k } is unbounded, which contradicts Lemma 3.4. First, by dual feasibility, s k = c A T y k for all k, hence {s k } converges to s := c A T y on K. The three conditions of Lemma 3.1 are satisfied at (A,x,s ), since (i) x > 0 and s 0, (ii) {a i i I(y )} is a linearly independent set by Assumption 3, and (iii) {a i i, x i 0} = {a i i } spans R m since (y k ) implies rank(a ) = m by (35). Therefore J a (A,x,s ) is nonsingular. Since, from (9) and (61), ) ) ( y J a (A,x k,s k a,k ) x a,k = ( b A x k X k s k and the right hand side converges on K, it follows that the steps converge on K : y a,k y a, and x a,k x a,, for some y a, and x a,. Also, since inf k K { y a,k } > 0, we have y a, 0 which implies s a, := A T y a, 0 since, again, (y k ) implies rank(a ) = m by (35). Next, we have by Step 5 of rmpc and Proposition 3.3 (ii) that, for all k, (72) b T y k+1 = b T (y k + t m,k d y m,k ) b T y k + t m,k d θb T y a,k. (73) Also, from (62a) and using s a,k = A T y a,k (by (57)), we have for all k, b T y a,k = ( y a,k ) T A (S) k 1 XA k T y a,k = ( s a,k ) T (S) k 1 X s k a,k = x k i s k ( s a,k i ) 2. i i The terms of this sum are all nonnegative and, as noted above, for at least one i, s a,k i tends to a nonzero limit s a, i on K. Therefore, since x k x > 0 on K and {s k i } k K is bounded (since it converges), we conclude that b T y a, > 0. So there exists a δ > 0 such that for all k K with k large enough, b T y a,k > δ > 0. In view of (73), establishing a positive lower bound on t m,k d for k K will complete the proof. By (44) and since Step 4 of Iteration rmpc ensures (24), we have t m,k d β t m,k d βζt a,k d. Therefore, it suffices to bound t a,k d away from zero. From (37), either t a,k d = 1 or, for some such that s a,k < 0, we have t a,k d = sk s a,k. (74) 13
14 If n \ ( n \ I(y ), since we assumed, without loss of generality, that I(y ) ) then, by Assumption 3, s k is bounded away from zero on K (since it converges to s > 0) and since s a,k = A T y a,k is bounded on K, we do get a positive lower bound for t a,k t a,k d d. On the other hand, if, using (74) and (59) we obtain = x k / x a,k, which is positive and bounded away from zero on K since x k is bounded away from zero on is bounded on K. This completes the proof. K and x a,k As in [TAW06, Lemmas 8 and 9] (with an identical proof using the appropriate modified lemmas) convergence to a stationary point readily follows. We include the next two results with proof for completeness and ease of reference. Lemma 3.8. Suppose Assumptions 1, 2 and 3 hold, and suppose there exists an infinite index set K on which y k is bounded away from F. Then y a,k 0 on K. Proof. Suppose the claim does not hold. Then Lemma 3.7 implies that { y a,k 1 } k K and {[ x a,k 1 ] } k K both converge to zero. Since {y k } is bounded (Lemma 3.4), there exists a vector y and an infinite index set K K such that {y k 1 } k K y. Lemma 3.6 implies that y is stationary and that { x a,k 1 } k K x, where x is the associated multiplier. However {[ x a,k 1 ] } k K 0 implies x 0 and so y F, a contradiction. Lemma 3.9. Suppose Assumptions 1, 2 and 3 hold. Then {y k } converges to the set of stationary points of (1). Proof. Suppose the claim does not hold. By boundedness of {y k }, there exists an infinite index set K on which y k y, with y non-stationary, hence {y k } k K is bounded away from F. Lemma 3.8 then implies y a,k 0 on K, which contradicts Lemma 3.6. This result is then used together with a technical lemma, proved in [TAW06, Lemmas 10 and 11], to show (using a modification of the proof of [TAW06, Theorem 12]) that in fact {y k } must converge to the dual solution set F (see Theorem 3.11 below). Lemma Suppose Assumptions 1, 2 and 3 hold. If {y k } is bounded away from F, then all limit (stationary) points of {y k } have the same multiplier. Theorem Suppose Assumptions 1, 2 and 3 hold. Then {y k } converges to F, the dual solution set. Proof. Suppose the claim does not hold. Monotonicity of {b T y k } implies that all limit points of y k have the same objective value. Therefore, since {y k } converges to its set of limit points (by boundedness), it must be bounded away from F. Lemma 3.8 then implies that y a,k 0. Let x be the unique (by Lemma 3.10) multiplier associated with all limit points of {y k }. We claim that x a,k x and x m,k x. We use another (nested) contradiction argument to prove this claim. Thus, suppose x a,k x, and let K be an infinite index set such that x a,k is bounded away from x on K. Let ŷ be such that y k ŷ on some infinite index set K K. Since y a,k 0 (on K in particular), Lemma 3.6 implies x a,k x on K, a contradiction. The same argument with x m,k in place of x a,k gives x m,k x. Now let y be an arbitrary limit point of {y k }, and let K be an infinite index set such that y k y on K, so that also s k := c A T y k c A T y =:s on K. Lemma 3.9 and the contradiction assumption imply that y is a non-kkt stationary point and hence for at least one i n, say i =, we have x < 0. This implies that x a,k < 0 and x m,k < 0 for all k sufficiently large. Complementarity implies s = 0, i.e., I(y ), so that by Lemma 3.5, k for all sufficiently large k K. Hence, for all large enough k, by (58), which implies s a,k that x a,k s a,k s k x a,k < 0. Since x a,k + x k s a,k = 0, (75) < 0 and x k > 0 also imply that x a,k > 0 since x a,k < 0. Therefore, since σ k µ k 0 and γ k 0, using (60) we get k s k x m,k + x k s m,k which, since x m,k < 0, implies that s m,k contradicts the fact that s = 0. < 0, it follows = γ k (σ k µ k k xa,k s a,k ) 0 (76) > 0 for all k large enough, say k k 0. Thus s k s k0 > 0, which 14
15 4 Local Convergence Analysis In this section we show, under additional Assumptions 4 and 5 (see below), that the iteration sequence z k := (x k,y k ) converges q-quadratically to the solution z :=(x,y ). We will first show that the iteration sequence converges to the solution, viz. z k z (Proposition 4.4), and then that it does so with a q-quadratic rate (Theorem 4.12). The following assumption supersedes Assumption 2. Assumption 4. The dual solution set is a singleton, F = {y }. Of course under this assumption, Theorem 3.11 implies y k y and s k := c A T y k c A T y =: s. Let x be the (unique by Assumption 3) multiplier associated to the stationary point y. The following result is a slight extension of [TAW06, Lemma 13]. Lemma 4.1. Under Assumptions 1, 3, and 4, the sequence {y k } generated by Iteration rmpc converges to y, the unique dual solution, and (x,s ) satisfy strict complementary slackness, i.e., x + s > 0. Further, for any x R n, x 0 such that x + s > 0, (in particular for x = x ) and any such that I(y ), J(A,x,s ) and J a (A,x,s ) are nonsingular. Proof. Assumption 4 and the Goldman-Tucker theorem, (e.g. see [Wri97, p.28]) imply strict complementary slackness for the pair (x,s ). Assumption 4 also implies that {a i i I(y )} = {a i x i 0} consists of exactly m linearly independent vectors. Hence, the three conditions for Lemma 3.1 are satisfied, and the non-singularity claim follows. The following technical lemma, that relates quantities generated by rmpc, is called upon below (in Lemmas 4.3 and 4.10) to show that the damping coefficients t m p and t m d converge to one and, moreover, that the convergence is fast enough for quadratic convergence of {z k } to take place. Lemma 4.2. Suppose Assumptions 1, 3, and 4 hold. Let (x,y,s) satisfy A T y + s = c, s > 0, and x > 0 and let (y), with I(y ). Let x a, s a, x a, s a, x m, and s m be generated by Iteration rmpc. If x m i > 0 for all i I(y ) and s m i > 0 for all i n \ I(y ), then t m p min { 1, min i \I(y ) { t m d min 1, min i I(y ) { si s a i, s i s m i { xi x a i, x i x m i sa i s m i xa i x m i }}, (77) }}. (78) Proof. First consider (77). With reference to (55), we see that either t m p = 1, in which case (77) is verified, or for some with x m < 0, we have t m p = x x m < 1. (79) Suppose I(y )( ). Since x m < 0, and x i0 > 0 and in view of the definition (52) of x m, the inequality x m > 0, which holds by assumption, implies x i0 /( x m ) 1, contradicting (79). Thus we must have \ I(y ). To complete the proof of (77), we consider two possibilities. If then, using (59) we have x a x m, t m p = x x m x x a = s s a, (80) and (77) is again verified. Alternately, if x a < x m, then using (60) and rearranging terms, we get (see below for explanation of the inequalities) t m p = x x m = s s m + γσµ x m s m + γ xa s a x m s m s s m γ xa s a x m s m s s m sa s m, 15
16 where γ, σ, and µ are as generated by Iteration rmpc. The first inequality follows because the second term is nonnegative: the numerator is nonegative, x m > 0 by assumption, and s m > 0 also by assumption. The second inequality follows since x a < x m and γ 1. So, once again, (77) is verified. Finally, inequality (78) is proved by a very similar argument that flips the roles of x and s. Since by construction x k i ξ for all i and k, where ξ is set arbitrarily by the user, the sequence {x k} cannot be expected in general to converge to x. The best we can hope for is that it converges to x #, where x # i := min{x i,ξ}. (81) This, together with appropriate convergence of other quantities, is established in Proposition 4.4 below, whose proof makes use of the following lemma. Lemma 4.3. Suppose Assumptions 1, 3, and 4 hold. If there exists an infinite index set K on which y a,k 0, then ˆx k x and x k+1 x #, both as k, k K. Proof. Since y k y, in view of Lemma 3.5, we may assume without loss of generality that I(y ) k for all k K. Now, since y a,k 0 on K and y k y, (57) implies that s a,k 0 on K, and Lemma 3.6 implies that x a,k x on K and x m,k x on K, in particular, that [ x a,k ] 0 on K. Further, by (65), and (40), y m,k 0 on K which implies, again by (57), that s m,k 0 on K. We first show that ˆx k x 0 on K. 5 We have for all k, using the triangle inequality, (52), and k k (45), ˆx k k x k ˆxk k xm,k + x m,k x k k k 1 tm,k p x m,k k + x m,k x. (82) Since x m,k x on K and { x m,k } k k K is bounded (since {x k } and { x m,k } k K are both bounded), we need only show t m,k p 1 on K. Now, since I(y ) k, x m,k x on K, and s m,k s on K (by y k y, (57), (40), (65), and (54)) all hold, strict complementarity (Lemma 4.1) implies that, for all k K large enough, x m,k i > 0 for i I(y ) and s m,k i > 0 for i n \ I(y ). Thus, without loss of generality, we assume it holds for all k K. Therefore, the hypothesis of Lemma 4.2 is verified for all k K, and in view of (77), since s a,k 0 on K and {s k } k K, { s a,k } k K and { s m,k } k K all converge to s, we have t m,k p 1 on K (since s i > 0 for all i n \ I(y )). Further, by (43) and since y m,k 0 on K, we also have t m,k p 1 on K. So indeed, ˆx k x 0 on k k K. Next, we show that x k+1 x # 0 on K. Let i I(y ) ( k for all k K). We have already k k established that y a,k ν + [ x a,k ] ν 0 on K and ˆx k i x i > 0 on K (positivity is by strict complementary slackness). This implies, by (46), that for sufficiently large k K we have x k+1 i = min{ˆx k i,ξ}, so that x k+1 i x # i on K. Now consider i n \ I(y ), where x i = 0, and consider the set K i K defined by K i := {k K i k }. If K i is finite, then this i is irrelevant to the limit of x k+1 x #. If it is infinite k k however, then since y a,k ν + [ x a,k ] ν 0 on K i and ˆx k i x i = 0 on K i, we have from (46) that x k+1 i 0 = x # i = x i on K i. Thus we have shown that x k+1 x # 0 on K. This fact, taken together k k with the complementarity of (x #,s ) (which follows from complementarity of (s,x ) and the definition (81) of x # ), then implies that µ k+1 0 on K. k Let K be the subset of K on which n \ k is nonempty. If K is finite, then the proof of the lemma is already complete. Otherwise, to complete the proof, we show that ˆx k x = ˆx k 0 on n\ k n\ k n\ k K and x k+1 x # = x k+1 0 on K. For this, we consider i n \ I(y ) and the set K n\ k n\ k n\ k i K defined by K i := {k K i n \ k }. As before, if K i is finite then this index i is irrelevant to the limits we are interested in. If it is infinite, then by (49) we get ˆx k i = µk+1 /s k+1 k bounded away from zero (since i n \ I(y ) ) and µ k+1 k i on K i, and since {s k+1 i } is 0 on K (as shown in the previous paragraph), we have ˆx k i x i = 0 on K i. In view of (50), this implies x k+1 i x # i = x i = 0 on K i. Thus, the proof is complete. 5 Note that the dimension of ˆx k k x k, i.e., k, may vary with k. 16
17 Proposition 4.4. Suppose Assumptions 1, 3 and 4 hold. Then we have (i) y a,k 0 and y m,k 0, (ii) x a,k x and x m,k x,(iii) ˆx k x and x k x #, and (iv) if x i ξ for all i n, then xk x, x a,k 0 and x m,k 0. k k Proof. First we show that y a,k 0. Supposing it is not so, take an infinite index set K with inf k K y a,k > 0. Lemma 3.7 then implies that there exists an infinite index set K K on which { y a,k 1 } k K and {[ x a,k 1 ] } k K converge to zero. We assume without loss of generality that k =, a constant set, for all k K (since k is selected from a finite set). Lemma 4.3 implies x k x # on K and since s k s (on K in particular), we have J(A,x k,s k ) J(A,x #,s ) on K. Further, by strict complementarity of (x #,s ) (which follows from strict complementarity of (s,x ) and the definition (81) of x # ) and Assumption 4, and since I(y ), Lemma 4.1 implies that J(A,x #,s ) is nonsingular. Using these facts and noting that (30) and the inclusion I(y ) imply J(A,x k,s k ) x a,k y a,k s a,k 0 = b on K and J(A,x #,s ) 0 x = b, (83) 0 we see that y a,k 0 on K. This gives the desired contradiction and proves that the entire sequence { y a,k } converges to zero. In view of (65) and definition (40) of y m, the proof of claim (i) is complete. In view of Lemma 3.6 and Lemma 4.3, claims (ii) and (iii) are immediate consequences of claim (i). Claim (iv) follows directly from claims (ii) and (iii) and the definition (81) of x #. The dual sequence {y k } was shown to converge to the dual optimal set F under Assumptions 1, 2, and 3. Adding Assumption 4 allowed us to show that the surrogate primal sequence {ˆx k } converges to the optimal multiplier x. Under the further assumption that x i ξ for all i n, the primal sequence itself was shown to converge to the optimal multiplier. An ever-so-slightly strengthened version of this latter assumption, which we state next, guarantees local quadratic convergence of the primal-dual sequence {z k } = {(x k,y k )}. Assumption 5. x i < ξ, i n. From here forward, we focus on the {z k } sequence. To prove quadratic convergence, we show that there exist constants c 0, and ρ > 0 (independent of z = (x,y) and ) such that for all z B(z,ρ) G o and all (y), Here z + (z,) z c z z 2. (84) B(z,ρ) := {z R m+n z z ρ}, G o := {(x,y) R n R m x > 0, y F o }, and z + (z,) is the update to z with the dependence of z + on z and made explicit. We will use this explicit notation for all quantities that depend on (z,) from now on, e.g. z a (z,), x m (z,), etc. Notice that the set of (z,) such that z B(z,ρ) G o and (y) is precisely the domain of definition of the mappings defined by Iteration rmpc : z + (, ), z a (, ), etc. We also introduce the (somewhat abusive) notation z := (x,y), z := ( x, y). The following lemma gives a neighborhood of z on which we will prove that the quadratic rate inequality (84) holds. In particular, several useful bounds that simplify the remaining analysis are proven on this neighborhood. We first define a quantity which is guaranteed to be positive when strict complementarity holds: ε := min{1, min i n (s i + x i )}. (85) 17
18 Lemma 4.5. Suppose Assumptions 1, 3, 4 and 5 hold and let β > 0 and ξ > 0. Then there exists ρ > 0 and R > 0 such that for all z B(z,ρ) G o and (y) the following hold: (i) I(y ) and J a (A,x,s ) 1 R, (86) (ii) max{ z(z,), a z m (z,), s a (z,), s m (z,) } < ε /2, (87) (iii) min{x i, x a i(z,), x m i (z,)} > ε /2, i I(y ), (88) max{s i, s a i (z,), s m i (z,)} < ε /2, i I(y ), (89) max{x i, x a i(z,), x m i (z,)} < ε /2, i n \ I(y ), (90) min{s i, s a i(z,), s m i (z,)} > ε /2, i n \ I(y ), (91) (iv) β t m p (z,) < t m p (z,) y a (z,), (92) β t m d (z,) < t m d (z,) y a (z,) (93) (v) ˆx i (z,) < ξ, i. (94) Proof. Let s := c A T y. (Note that, through y, s varies with z.) Consider the (finite) set := { n I(y ) }. We first note that for all y sufficiently close to y, we must have I(y ) (y), and hence (y). Indeed, Assumption 3 implies that, for i I(y ), s i (y ) = 0 is among the m smallest slack values at y, and thus that, for i I(y ), s i (y) is among the m smallest slack values at y, for all y close enough to y ; rule (35) for selecting then implies the claim. (In fact, under Assumptions 3 and 4, (y) = for all y close enough to y.) To prove the lemma, it suffices to show that we can find ρ > 0 and R > 0 to establish claims (i)-(v) for any fixed and all z B(z,ρ ). Indeed, given this, in view of the finiteness of, the claims are easily seen to hold for all and z B(z,ρ 0 ) (e.g. take ρ 0 := min ρ and R := max R ). Then by the argument of the first paragraph, we can find a sufficiently small ρ (0,ρ 0 ] so that (y) for all z = (x,y) B(z,ρ) and the proof would be complete. Thus, we now fix and seek appropriate ρ and R. For claim (i), since, we have I(y ) and so Lemma 4.1 implies that J a (A,x,s ) is nonsingular. Since J a (A,x,s ) depends continuously on z, we can find ρ > 0 and R > 0 such that J a (A,x,s ) 1 R, for all z B(z,ρ ). For claim (ii), since the right hand sides of (30) and (31) vanish at z and are continuous in z, and since J a (A,x,s ) 1 is bounded on B(z,ρ ), by further tightening ρ if needed, we can also make z(z,), a z(z,), c and hence z m (z,) as small as desired on B(z,ρ ) G o. Equation (57) implies that s a (z,) and s m (z,) can also be made small by controlling z a (z,) and z m (z,) respectively. Consider now claim (iii). By complementarity and the definition (85) of ε, it is clear that x i > ε /2, s i < ε /2 for i I(y ) and x i < ε /2, s i > ε /2 for i n \ I(y ) can be made to hold for all z B(z,ρ ) G o by further reducing ρ if needed. Further, since x n\ = 0 (since I(y ) ) and in view of (47), x a n\(z,) = 0 also, using the triangle inequality we have x a i(z,) x i x a (z,) x x a (z,) + x x, (95) for all i n and for all z B(z,ρ ) G o. Thus, in view of (87) (note the inequality in there is strict), by further tightening ρ if needed (since x x can thus be made arbitrarily small), the right hand side of (95) can be made less than ε /2 for all z B(z,ρ ) G o. Hence, for i n \ I(y ) (since x i = 0), x a i (z,) < ε /2 and for i I(y ) (since x i ε ), x a i (z,) > ε /2. Similar arguments apply for x m i (z,), s a i (z,), and sm i (z,). 18
A Constraint-Reduced Variant of Mehrotra s Predictor-Corrector Algorithm
 A Constraint-Reduced Variant of Mehrotra s Predictor-Corrector Algorithm Luke B. Winternitz, Stacey O. Nicholls, André L. Tits, Dianne P. O Leary September 7, 2010 Abstract Consider linear programs in
A Constraint-Reduced Variant of Mehrotra s Predictor-Corrector Algorithm Luke B. Winternitz, Stacey O. Nicholls, André L. Tits, Dianne P. O Leary September 7, 2010 Abstract Consider linear programs in
Constraint Reduction for Linear Programs with Many Constraints
 Constraint Reduction for Linear Programs with Many Constraints André L. Tits Institute for Systems Research and Department of Electrical and Computer Engineering University of Maryland, College Park Pierre-Antoine
Constraint Reduction for Linear Programs with Many Constraints André L. Tits Institute for Systems Research and Department of Electrical and Computer Engineering University of Maryland, College Park Pierre-Antoine
A Constraint-Reduced MPC Algorithm for Convex Quadratic Programming, with a Modified Active-Set Identification Scheme
 A Constraint-Reduced MPC Algorithm for Convex Quadratic Programming, with a Modified Active-Set Identification Scheme M. Paul Laiu 1 and (presenter) André L. Tits 2 1 Oak Ridge National Laboratory laiump@ornl.gov
A Constraint-Reduced MPC Algorithm for Convex Quadratic Programming, with a Modified Active-Set Identification Scheme M. Paul Laiu 1 and (presenter) André L. Tits 2 1 Oak Ridge National Laboratory laiump@ornl.gov
Constraint Reduction for Linear Programs with Many Inequality Constraints
 SIOPT 63342, compiled November 7, 25 Constraint Reduction for Linear Programs with Many Inequality Constraints André L. Tits Department of Electrical and Computer Engineering and Institute for Systems
SIOPT 63342, compiled November 7, 25 Constraint Reduction for Linear Programs with Many Inequality Constraints André L. Tits Department of Electrical and Computer Engineering and Institute for Systems
ABSTRACT. linear and convex quadratic programs with many more inequality constraints than
 ABSTRACT Title of dissertation: INFEASIBLE-START CONSTRAINT-REDUCED METHODS FOR LINEAR AND CONVEX QUADRATIC OPTIMIZATION Meiyun He, Doctor of Philosophy, 211 Dissertation directed by: Professor André L.
ABSTRACT Title of dissertation: INFEASIBLE-START CONSTRAINT-REDUCED METHODS FOR LINEAR AND CONVEX QUADRATIC OPTIMIZATION Meiyun He, Doctor of Philosophy, 211 Dissertation directed by: Professor André L.
Interior-Point Methods for Linear Optimization
 Interior-Point Methods for Linear Optimization Robert M. Freund and Jorge Vera March, 204 c 204 Robert M. Freund and Jorge Vera. All rights reserved. Linear Optimization with a Logarithmic Barrier Function
Interior-Point Methods for Linear Optimization Robert M. Freund and Jorge Vera March, 204 c 204 Robert M. Freund and Jorge Vera. All rights reserved. Linear Optimization with a Logarithmic Barrier Function
A full-newton step infeasible interior-point algorithm for linear programming based on a kernel function
 A full-newton step infeasible interior-point algorithm for linear programming based on a kernel function Zhongyi Liu, Wenyu Sun Abstract This paper proposes an infeasible interior-point algorithm with
A full-newton step infeasible interior-point algorithm for linear programming based on a kernel function Zhongyi Liu, Wenyu Sun Abstract This paper proposes an infeasible interior-point algorithm with
A Constraint-Reduced MPC Algorithm for Convex Quadratic Programming, with a Modified Active Set Identification Scheme
 Noname manuscript No. (will be inserted by the editor) A Constraint-Reduced MPC Algorithm for Convex Quadratic Programming, with a Modified Active Set Identification Scheme M. Paul Laiu André L. Tits February
Noname manuscript No. (will be inserted by the editor) A Constraint-Reduced MPC Algorithm for Convex Quadratic Programming, with a Modified Active Set Identification Scheme M. Paul Laiu André L. Tits February
Enlarging neighborhoods of interior-point algorithms for linear programming via least values of proximity measure functions
 Enlarging neighborhoods of interior-point algorithms for linear programming via least values of proximity measure functions Y B Zhao Abstract It is well known that a wide-neighborhood interior-point algorithm
Enlarging neighborhoods of interior-point algorithms for linear programming via least values of proximity measure functions Y B Zhao Abstract It is well known that a wide-neighborhood interior-point algorithm
Primal-Dual Interior-Point Methods for Linear Programming based on Newton s Method
 Primal-Dual Interior-Point Methods for Linear Programming based on Newton s Method Robert M. Freund March, 2004 2004 Massachusetts Institute of Technology. The Problem The logarithmic barrier approach
Primal-Dual Interior-Point Methods for Linear Programming based on Newton s Method Robert M. Freund March, 2004 2004 Massachusetts Institute of Technology. The Problem The logarithmic barrier approach
Extreme Abridgment of Boyd and Vandenberghe s Convex Optimization
 Extreme Abridgment of Boyd and Vandenberghe s Convex Optimization Compiled by David Rosenberg Abstract Boyd and Vandenberghe s Convex Optimization book is very well-written and a pleasure to read. The
Extreme Abridgment of Boyd and Vandenberghe s Convex Optimization Compiled by David Rosenberg Abstract Boyd and Vandenberghe s Convex Optimization book is very well-written and a pleasure to read. The
CONVERGENCE ANALYSIS OF AN INTERIOR-POINT METHOD FOR NONCONVEX NONLINEAR PROGRAMMING
 CONVERGENCE ANALYSIS OF AN INTERIOR-POINT METHOD FOR NONCONVEX NONLINEAR PROGRAMMING HANDE Y. BENSON, ARUN SEN, AND DAVID F. SHANNO Abstract. In this paper, we present global and local convergence results
CONVERGENCE ANALYSIS OF AN INTERIOR-POINT METHOD FOR NONCONVEX NONLINEAR PROGRAMMING HANDE Y. BENSON, ARUN SEN, AND DAVID F. SHANNO Abstract. In this paper, we present global and local convergence results
Lecture: Algorithms for LP, SOCP and SDP
 1/53 Lecture: Algorithms for LP, SOCP and SDP Zaiwen Wen Beijing International Center For Mathematical Research Peking University http://bicmr.pku.edu.cn/~wenzw/bigdata2018.html wenzw@pku.edu.cn Acknowledgement:
1/53 Lecture: Algorithms for LP, SOCP and SDP Zaiwen Wen Beijing International Center For Mathematical Research Peking University http://bicmr.pku.edu.cn/~wenzw/bigdata2018.html wenzw@pku.edu.cn Acknowledgement:
Interior Point Methods for LP
 11.1 Interior Point Methods for LP Katta G. Murty, IOE 510, LP, U. Of Michigan, Ann Arbor, Winter 1997. Simplex Method - A Boundary Method: Starting at an extreme point of the feasible set, the simplex
11.1 Interior Point Methods for LP Katta G. Murty, IOE 510, LP, U. Of Michigan, Ann Arbor, Winter 1997. Simplex Method - A Boundary Method: Starting at an extreme point of the feasible set, the simplex
5 Handling Constraints
 5 Handling Constraints Engineering design optimization problems are very rarely unconstrained. Moreover, the constraints that appear in these problems are typically nonlinear. This motivates our interest
5 Handling Constraints Engineering design optimization problems are very rarely unconstrained. Moreover, the constraints that appear in these problems are typically nonlinear. This motivates our interest
A FULL-NEWTON STEP INFEASIBLE-INTERIOR-POINT ALGORITHM COMPLEMENTARITY PROBLEMS
 Yugoslav Journal of Operations Research 25 (205), Number, 57 72 DOI: 0.2298/YJOR3055034A A FULL-NEWTON STEP INFEASIBLE-INTERIOR-POINT ALGORITHM FOR P (κ)-horizontal LINEAR COMPLEMENTARITY PROBLEMS Soodabeh
Yugoslav Journal of Operations Research 25 (205), Number, 57 72 DOI: 0.2298/YJOR3055034A A FULL-NEWTON STEP INFEASIBLE-INTERIOR-POINT ALGORITHM FOR P (κ)-horizontal LINEAR COMPLEMENTARITY PROBLEMS Soodabeh
DS-GA 1002 Lecture notes 0 Fall Linear Algebra. These notes provide a review of basic concepts in linear algebra.
 DS-GA 1002 Lecture notes 0 Fall 2016 Linear Algebra These notes provide a review of basic concepts in linear algebra. 1 Vector spaces You are no doubt familiar with vectors in R 2 or R 3, i.e. [ ] 1.1
DS-GA 1002 Lecture notes 0 Fall 2016 Linear Algebra These notes provide a review of basic concepts in linear algebra. 1 Vector spaces You are no doubt familiar with vectors in R 2 or R 3, i.e. [ ] 1.1
An Infeasible Interior-Point Algorithm with full-newton Step for Linear Optimization
 An Infeasible Interior-Point Algorithm with full-newton Step for Linear Optimization H. Mansouri M. Zangiabadi Y. Bai C. Roos Department of Mathematical Science, Shahrekord University, P.O. Box 115, Shahrekord,
An Infeasible Interior-Point Algorithm with full-newton Step for Linear Optimization H. Mansouri M. Zangiabadi Y. Bai C. Roos Department of Mathematical Science, Shahrekord University, P.O. Box 115, Shahrekord,
Meiyun Y. He a & Andréé L. Tits a a Department of Electrical and Computer Engineering and. Available online: 14 Sep 2011
 This article was downloaded by: [University Of Maryland], [Andre Tits] On: 14 September 2011, At: 15:41 Publisher: Taylor & Francis Informa Ltd Registered in England and Wales Registered Number: 1072954
This article was downloaded by: [University Of Maryland], [Andre Tits] On: 14 September 2011, At: 15:41 Publisher: Taylor & Francis Informa Ltd Registered in England and Wales Registered Number: 1072954
MODIFYING SQP FOR DEGENERATE PROBLEMS
 PREPRINT ANL/MCS-P699-1097, OCTOBER, 1997, (REVISED JUNE, 2000; MARCH, 2002), MATHEMATICS AND COMPUTER SCIENCE DIVISION, ARGONNE NATIONAL LABORATORY MODIFYING SQP FOR DEGENERATE PROBLEMS STEPHEN J. WRIGHT
PREPRINT ANL/MCS-P699-1097, OCTOBER, 1997, (REVISED JUNE, 2000; MARCH, 2002), MATHEMATICS AND COMPUTER SCIENCE DIVISION, ARGONNE NATIONAL LABORATORY MODIFYING SQP FOR DEGENERATE PROBLEMS STEPHEN J. WRIGHT
SVM May 2007 DOE-PI Dianne P. O Leary c 2007
 SVM May 2007 DOE-PI Dianne P. O Leary c 2007 1 Speeding the Training of Support Vector Machines and Solution of Quadratic Programs Dianne P. O Leary Computer Science Dept. and Institute for Advanced Computer
SVM May 2007 DOE-PI Dianne P. O Leary c 2007 1 Speeding the Training of Support Vector Machines and Solution of Quadratic Programs Dianne P. O Leary Computer Science Dept. and Institute for Advanced Computer
Introduction to Real Analysis Alternative Chapter 1
 Christopher Heil Introduction to Real Analysis Alternative Chapter 1 A Primer on Norms and Banach Spaces Last Updated: March 10, 2018 c 2018 by Christopher Heil Chapter 1 A Primer on Norms and Banach Spaces
Christopher Heil Introduction to Real Analysis Alternative Chapter 1 A Primer on Norms and Banach Spaces Last Updated: March 10, 2018 c 2018 by Christopher Heil Chapter 1 A Primer on Norms and Banach Spaces
Key words. linear complementarity problem, non-interior-point algorithm, Tikhonov regularization, P 0 matrix, regularized central path
 A GLOBALLY AND LOCALLY SUPERLINEARLY CONVERGENT NON-INTERIOR-POINT ALGORITHM FOR P 0 LCPS YUN-BIN ZHAO AND DUAN LI Abstract Based on the concept of the regularized central path, a new non-interior-point
A GLOBALLY AND LOCALLY SUPERLINEARLY CONVERGENT NON-INTERIOR-POINT ALGORITHM FOR P 0 LCPS YUN-BIN ZHAO AND DUAN LI Abstract Based on the concept of the regularized central path, a new non-interior-point
1 Lyapunov theory of stability
 M.Kawski, APM 581 Diff Equns Intro to Lyapunov theory. November 15, 29 1 1 Lyapunov theory of stability Introduction. Lyapunov s second (or direct) method provides tools for studying (asymptotic) stability
M.Kawski, APM 581 Diff Equns Intro to Lyapunov theory. November 15, 29 1 1 Lyapunov theory of stability Introduction. Lyapunov s second (or direct) method provides tools for studying (asymptotic) stability
Convex Optimization M2
 Convex Optimization M2 Lecture 3 A. d Aspremont. Convex Optimization M2. 1/49 Duality A. d Aspremont. Convex Optimization M2. 2/49 DMs DM par email: dm.daspremont@gmail.com A. d Aspremont. Convex Optimization
Convex Optimization M2 Lecture 3 A. d Aspremont. Convex Optimization M2. 1/49 Duality A. d Aspremont. Convex Optimization M2. 2/49 DMs DM par email: dm.daspremont@gmail.com A. d Aspremont. Convex Optimization
Optimality, Duality, Complementarity for Constrained Optimization
 Optimality, Duality, Complementarity for Constrained Optimization Stephen Wright University of Wisconsin-Madison May 2014 Wright (UW-Madison) Optimality, Duality, Complementarity May 2014 1 / 41 Linear
Optimality, Duality, Complementarity for Constrained Optimization Stephen Wright University of Wisconsin-Madison May 2014 Wright (UW-Madison) Optimality, Duality, Complementarity May 2014 1 / 41 Linear
I.3. LMI DUALITY. Didier HENRION EECI Graduate School on Control Supélec - Spring 2010
 I.3. LMI DUALITY Didier HENRION henrion@laas.fr EECI Graduate School on Control Supélec - Spring 2010 Primal and dual For primal problem p = inf x g 0 (x) s.t. g i (x) 0 define Lagrangian L(x, z) = g 0
I.3. LMI DUALITY Didier HENRION henrion@laas.fr EECI Graduate School on Control Supélec - Spring 2010 Primal and dual For primal problem p = inf x g 0 (x) s.t. g i (x) 0 define Lagrangian L(x, z) = g 0
Chapter 1. Preliminaries
 Introduction This dissertation is a reading of chapter 4 in part I of the book : Integer and Combinatorial Optimization by George L. Nemhauser & Laurence A. Wolsey. The chapter elaborates links between
Introduction This dissertation is a reading of chapter 4 in part I of the book : Integer and Combinatorial Optimization by George L. Nemhauser & Laurence A. Wolsey. The chapter elaborates links between
Penalty and Barrier Methods. So we again build on our unconstrained algorithms, but in a different way.
 AMSC 607 / CMSC 878o Advanced Numerical Optimization Fall 2008 UNIT 3: Constrained Optimization PART 3: Penalty and Barrier Methods Dianne P. O Leary c 2008 Reference: N&S Chapter 16 Penalty and Barrier
AMSC 607 / CMSC 878o Advanced Numerical Optimization Fall 2008 UNIT 3: Constrained Optimization PART 3: Penalty and Barrier Methods Dianne P. O Leary c 2008 Reference: N&S Chapter 16 Penalty and Barrier
On Generalized Primal-Dual Interior-Point Methods with Non-uniform Complementarity Perturbations for Quadratic Programming
 On Generalized Primal-Dual Interior-Point Methods with Non-uniform Complementarity Perturbations for Quadratic Programming Altuğ Bitlislioğlu and Colin N. Jones Abstract This technical note discusses convergence
On Generalized Primal-Dual Interior-Point Methods with Non-uniform Complementarity Perturbations for Quadratic Programming Altuğ Bitlislioğlu and Colin N. Jones Abstract This technical note discusses convergence
A Brief Review on Convex Optimization
 A Brief Review on Convex Optimization 1 Convex set S R n is convex if x,y S, λ,µ 0, λ+µ = 1 λx+µy S geometrically: x,y S line segment through x,y S examples (one convex, two nonconvex sets): A Brief Review
A Brief Review on Convex Optimization 1 Convex set S R n is convex if x,y S, λ,µ 0, λ+µ = 1 λx+µy S geometrically: x,y S line segment through x,y S examples (one convex, two nonconvex sets): A Brief Review
Interior-Point Methods
 Interior-Point Methods Stephen Wright University of Wisconsin-Madison Simons, Berkeley, August, 2017 Wright (UW-Madison) Interior-Point Methods August 2017 1 / 48 Outline Introduction: Problems and Fundamentals
Interior-Point Methods Stephen Wright University of Wisconsin-Madison Simons, Berkeley, August, 2017 Wright (UW-Madison) Interior-Point Methods August 2017 1 / 48 Outline Introduction: Problems and Fundamentals
On Superlinear Convergence of Infeasible Interior-Point Algorithms for Linearly Constrained Convex Programs *
 Computational Optimization and Applications, 8, 245 262 (1997) c 1997 Kluwer Academic Publishers. Manufactured in The Netherlands. On Superlinear Convergence of Infeasible Interior-Point Algorithms for
Computational Optimization and Applications, 8, 245 262 (1997) c 1997 Kluwer Academic Publishers. Manufactured in The Netherlands. On Superlinear Convergence of Infeasible Interior-Point Algorithms for
2.098/6.255/ Optimization Methods Practice True/False Questions
 2.098/6.255/15.093 Optimization Methods Practice True/False Questions December 11, 2009 Part I For each one of the statements below, state whether it is true or false. Include a 1-3 line supporting sentence
2.098/6.255/15.093 Optimization Methods Practice True/False Questions December 11, 2009 Part I For each one of the statements below, state whether it is true or false. Include a 1-3 line supporting sentence
INTERIOR-POINT METHODS FOR NONCONVEX NONLINEAR PROGRAMMING: CONVERGENCE ANALYSIS AND COMPUTATIONAL PERFORMANCE
 INTERIOR-POINT METHODS FOR NONCONVEX NONLINEAR PROGRAMMING: CONVERGENCE ANALYSIS AND COMPUTATIONAL PERFORMANCE HANDE Y. BENSON, ARUN SEN, AND DAVID F. SHANNO Abstract. In this paper, we present global
INTERIOR-POINT METHODS FOR NONCONVEX NONLINEAR PROGRAMMING: CONVERGENCE ANALYSIS AND COMPUTATIONAL PERFORMANCE HANDE Y. BENSON, ARUN SEN, AND DAVID F. SHANNO Abstract. In this paper, we present global
5. Duality. Lagrangian
 5. Duality Convex Optimization Boyd & Vandenberghe Lagrange dual problem weak and strong duality geometric interpretation optimality conditions perturbation and sensitivity analysis examples generalized
5. Duality Convex Optimization Boyd & Vandenberghe Lagrange dual problem weak and strong duality geometric interpretation optimality conditions perturbation and sensitivity analysis examples generalized
CSCI : Optimization and Control of Networks. Review on Convex Optimization
 CSCI7000-016: Optimization and Control of Networks Review on Convex Optimization 1 Convex set S R n is convex if x,y S, λ,µ 0, λ+µ = 1 λx+µy S geometrically: x,y S line segment through x,y S examples (one
CSCI7000-016: Optimization and Control of Networks Review on Convex Optimization 1 Convex set S R n is convex if x,y S, λ,µ 0, λ+µ = 1 λx+µy S geometrically: x,y S line segment through x,y S examples (one
A Second Full-Newton Step O(n) Infeasible Interior-Point Algorithm for Linear Optimization
 A Second Full-Newton Step On Infeasible Interior-Point Algorithm for Linear Optimization H. Mansouri C. Roos August 1, 005 July 1, 005 Department of Electrical Engineering, Mathematics and Computer Science,
A Second Full-Newton Step On Infeasible Interior-Point Algorithm for Linear Optimization H. Mansouri C. Roos August 1, 005 July 1, 005 Department of Electrical Engineering, Mathematics and Computer Science,
3. Linear Programming and Polyhedral Combinatorics
 Massachusetts Institute of Technology 18.433: Combinatorial Optimization Michel X. Goemans February 28th, 2013 3. Linear Programming and Polyhedral Combinatorics Summary of what was seen in the introductory
Massachusetts Institute of Technology 18.433: Combinatorial Optimization Michel X. Goemans February 28th, 2013 3. Linear Programming and Polyhedral Combinatorics Summary of what was seen in the introductory
Elements of Convex Optimization Theory
 Elements of Convex Optimization Theory Costis Skiadas August 2015 This is a revised and extended version of Appendix A of Skiadas (2009), providing a self-contained overview of elements of convex optimization
Elements of Convex Optimization Theory Costis Skiadas August 2015 This is a revised and extended version of Appendix A of Skiadas (2009), providing a self-contained overview of elements of convex optimization
Contents. 1 Vectors, Lines and Planes 1. 2 Gaussian Elimination Matrices Vector Spaces and Subspaces 124
 Matrices Math 220 Copyright 2016 Pinaki Das This document is freely redistributable under the terms of the GNU Free Documentation License For more information, visit http://wwwgnuorg/copyleft/fdlhtml Contents
Matrices Math 220 Copyright 2016 Pinaki Das This document is freely redistributable under the terms of the GNU Free Documentation License For more information, visit http://wwwgnuorg/copyleft/fdlhtml Contents
A PREDICTOR-CORRECTOR PATH-FOLLOWING ALGORITHM FOR SYMMETRIC OPTIMIZATION BASED ON DARVAY'S TECHNIQUE
 Yugoslav Journal of Operations Research 24 (2014) Number 1, 35-51 DOI: 10.2298/YJOR120904016K A PREDICTOR-CORRECTOR PATH-FOLLOWING ALGORITHM FOR SYMMETRIC OPTIMIZATION BASED ON DARVAY'S TECHNIQUE BEHROUZ
Yugoslav Journal of Operations Research 24 (2014) Number 1, 35-51 DOI: 10.2298/YJOR120904016K A PREDICTOR-CORRECTOR PATH-FOLLOWING ALGORITHM FOR SYMMETRIC OPTIMIZATION BASED ON DARVAY'S TECHNIQUE BEHROUZ
A Distributed Newton Method for Network Utility Maximization, II: Convergence
 A Distributed Newton Method for Network Utility Maximization, II: Convergence Ermin Wei, Asuman Ozdaglar, and Ali Jadbabaie October 31, 2012 Abstract The existing distributed algorithms for Network Utility
A Distributed Newton Method for Network Utility Maximization, II: Convergence Ermin Wei, Asuman Ozdaglar, and Ali Jadbabaie October 31, 2012 Abstract The existing distributed algorithms for Network Utility
Convex Optimization. Newton s method. ENSAE: Optimisation 1/44
 Convex Optimization Newton s method ENSAE: Optimisation 1/44 Unconstrained minimization minimize f(x) f convex, twice continuously differentiable (hence dom f open) we assume optimal value p = inf x f(x)
Convex Optimization Newton s method ENSAE: Optimisation 1/44 Unconstrained minimization minimize f(x) f convex, twice continuously differentiable (hence dom f open) we assume optimal value p = inf x f(x)
Appendix PRELIMINARIES 1. THEOREMS OF ALTERNATIVES FOR SYSTEMS OF LINEAR CONSTRAINTS
 Appendix PRELIMINARIES 1. THEOREMS OF ALTERNATIVES FOR SYSTEMS OF LINEAR CONSTRAINTS Here we consider systems of linear constraints, consisting of equations or inequalities or both. A feasible solution
Appendix PRELIMINARIES 1. THEOREMS OF ALTERNATIVES FOR SYSTEMS OF LINEAR CONSTRAINTS Here we consider systems of linear constraints, consisting of equations or inequalities or both. A feasible solution
UNDERGROUND LECTURE NOTES 1: Optimality Conditions for Constrained Optimization Problems
 UNDERGROUND LECTURE NOTES 1: Optimality Conditions for Constrained Optimization Problems Robert M. Freund February 2016 c 2016 Massachusetts Institute of Technology. All rights reserved. 1 1 Introduction
UNDERGROUND LECTURE NOTES 1: Optimality Conditions for Constrained Optimization Problems Robert M. Freund February 2016 c 2016 Massachusetts Institute of Technology. All rights reserved. 1 1 Introduction
A SHIFTED PRIMAL-DUAL PENALTY-BARRIER METHOD FOR NONLINEAR OPTIMIZATION
 A SHIFTED PRIMAL-DUAL PENALTY-BARRIER METHOD FOR NONLINEAR OPTIMIZATION Philip E. Gill Vyacheslav Kungurtsev Daniel P. Robinson UCSD Center for Computational Mathematics Technical Report CCoM-19-3 March
A SHIFTED PRIMAL-DUAL PENALTY-BARRIER METHOD FOR NONLINEAR OPTIMIZATION Philip E. Gill Vyacheslav Kungurtsev Daniel P. Robinson UCSD Center for Computational Mathematics Technical Report CCoM-19-3 March
Optimality Conditions for Constrained Optimization
 72 CHAPTER 7 Optimality Conditions for Constrained Optimization 1. First Order Conditions In this section we consider first order optimality conditions for the constrained problem P : minimize f 0 (x)
72 CHAPTER 7 Optimality Conditions for Constrained Optimization 1. First Order Conditions In this section we consider first order optimality conditions for the constrained problem P : minimize f 0 (x)
Lecture 8 Plus properties, merit functions and gap functions. September 28, 2008
 Lecture 8 Plus properties, merit functions and gap functions September 28, 2008 Outline Plus-properties and F-uniqueness Equation reformulations of VI/CPs Merit functions Gap merit functions FP-I book:
Lecture 8 Plus properties, merit functions and gap functions September 28, 2008 Outline Plus-properties and F-uniqueness Equation reformulations of VI/CPs Merit functions Gap merit functions FP-I book:
Solving Dual Problems
 Lecture 20 Solving Dual Problems We consider a constrained problem where, in addition to the constraint set X, there are also inequality and linear equality constraints. Specifically the minimization problem
Lecture 20 Solving Dual Problems We consider a constrained problem where, in addition to the constraint set X, there are also inequality and linear equality constraints. Specifically the minimization problem
AN AUGMENTED LAGRANGIAN AFFINE SCALING METHOD FOR NONLINEAR PROGRAMMING
 AN AUGMENTED LAGRANGIAN AFFINE SCALING METHOD FOR NONLINEAR PROGRAMMING XIAO WANG AND HONGCHAO ZHANG Abstract. In this paper, we propose an Augmented Lagrangian Affine Scaling (ALAS) algorithm for general
AN AUGMENTED LAGRANGIAN AFFINE SCALING METHOD FOR NONLINEAR PROGRAMMING XIAO WANG AND HONGCHAO ZHANG Abstract. In this paper, we propose an Augmented Lagrangian Affine Scaling (ALAS) algorithm for general
Linear Programming: Simplex
 Linear Programming: Simplex Stephen J. Wright 1 2 Computer Sciences Department, University of Wisconsin-Madison. IMA, August 2016 Stephen Wright (UW-Madison) Linear Programming: Simplex IMA, August 2016
Linear Programming: Simplex Stephen J. Wright 1 2 Computer Sciences Department, University of Wisconsin-Madison. IMA, August 2016 Stephen Wright (UW-Madison) Linear Programming: Simplex IMA, August 2016
Interior Point Methods for Nonlinear Optimization
 Interior Point Methods for Nonlinear Optimization Imre Pólik 1 and Tamás Terlaky 2 1 School of Computational Engineering and Science, McMaster University, Hamilton, Ontario, Canada, imre@polik.net 2 School
Interior Point Methods for Nonlinear Optimization Imre Pólik 1 and Tamás Terlaky 2 1 School of Computational Engineering and Science, McMaster University, Hamilton, Ontario, Canada, imre@polik.net 2 School
Interior Point Methods for Linear Programming: Motivation & Theory
 School of Mathematics T H E U N I V E R S I T Y O H F E D I N B U R G Interior Point Methods for Linear Programming: Motivation & Theory Jacek Gondzio Email: J.Gondzio@ed.ac.uk URL: http://www.maths.ed.ac.uk/~gondzio
School of Mathematics T H E U N I V E R S I T Y O H F E D I N B U R G Interior Point Methods for Linear Programming: Motivation & Theory Jacek Gondzio Email: J.Gondzio@ed.ac.uk URL: http://www.maths.ed.ac.uk/~gondzio
4TE3/6TE3. Algorithms for. Continuous Optimization
 4TE3/6TE3 Algorithms for Continuous Optimization (Duality in Nonlinear Optimization ) Tamás TERLAKY Computing and Software McMaster University Hamilton, January 2004 terlaky@mcmaster.ca Tel: 27780 Optimality
4TE3/6TE3 Algorithms for Continuous Optimization (Duality in Nonlinear Optimization ) Tamás TERLAKY Computing and Software McMaster University Hamilton, January 2004 terlaky@mcmaster.ca Tel: 27780 Optimality
Lecture 3: Lagrangian duality and algorithms for the Lagrangian dual problem
 Lecture 3: Lagrangian duality and algorithms for the Lagrangian dual problem Michael Patriksson 0-0 The Relaxation Theorem 1 Problem: find f := infimum f(x), x subject to x S, (1a) (1b) where f : R n R
Lecture 3: Lagrangian duality and algorithms for the Lagrangian dual problem Michael Patriksson 0-0 The Relaxation Theorem 1 Problem: find f := infimum f(x), x subject to x S, (1a) (1b) where f : R n R
Interior Point Methods in Mathematical Programming
 Interior Point Methods in Mathematical Programming Clóvis C. Gonzaga Federal University of Santa Catarina, Brazil Journées en l honneur de Pierre Huard Paris, novembre 2008 01 00 11 00 000 000 000 000
Interior Point Methods in Mathematical Programming Clóvis C. Gonzaga Federal University of Santa Catarina, Brazil Journées en l honneur de Pierre Huard Paris, novembre 2008 01 00 11 00 000 000 000 000
Lagrange Duality. Daniel P. Palomar. Hong Kong University of Science and Technology (HKUST)
 Lagrange Duality Daniel P. Palomar Hong Kong University of Science and Technology (HKUST) ELEC5470 - Convex Optimization Fall 2017-18, HKUST, Hong Kong Outline of Lecture Lagrangian Dual function Dual
Lagrange Duality Daniel P. Palomar Hong Kong University of Science and Technology (HKUST) ELEC5470 - Convex Optimization Fall 2017-18, HKUST, Hong Kong Outline of Lecture Lagrangian Dual function Dual
A priori bounds on the condition numbers in interior-point methods
 A priori bounds on the condition numbers in interior-point methods Florian Jarre, Mathematisches Institut, Heinrich-Heine Universität Düsseldorf, Germany. Abstract Interior-point methods are known to be
A priori bounds on the condition numbers in interior-point methods Florian Jarre, Mathematisches Institut, Heinrich-Heine Universität Düsseldorf, Germany. Abstract Interior-point methods are known to be
10 Numerical methods for constrained problems
 10 Numerical methods for constrained problems min s.t. f(x) h(x) = 0 (l), g(x) 0 (m), x X The algorithms can be roughly divided the following way: ˆ primal methods: find descent direction keeping inside
10 Numerical methods for constrained problems min s.t. f(x) h(x) = 0 (l), g(x) 0 (m), x X The algorithms can be roughly divided the following way: ˆ primal methods: find descent direction keeping inside
6-1 The Positivstellensatz P. Parrilo and S. Lall, ECC
 6-1 The Positivstellensatz P. Parrilo and S. Lall, ECC 2003 2003.09.02.10 6. The Positivstellensatz Basic semialgebraic sets Semialgebraic sets Tarski-Seidenberg and quantifier elimination Feasibility
6-1 The Positivstellensatz P. Parrilo and S. Lall, ECC 2003 2003.09.02.10 6. The Positivstellensatz Basic semialgebraic sets Semialgebraic sets Tarski-Seidenberg and quantifier elimination Feasibility
Lecture 5. Theorems of Alternatives and Self-Dual Embedding
 IE 8534 1 Lecture 5. Theorems of Alternatives and Self-Dual Embedding IE 8534 2 A system of linear equations may not have a solution. It is well known that either Ax = c has a solution, or A T y = 0, c
IE 8534 1 Lecture 5. Theorems of Alternatives and Self-Dual Embedding IE 8534 2 A system of linear equations may not have a solution. It is well known that either Ax = c has a solution, or A T y = 0, c
A Simple Primal-Dual Feasible Interior-Point Method for Nonlinear Programming with Monotone Descent
 A Simple Primal-Dual Feasible Interior-Point Method for Nonlinear Programming with Monotone Descent Sasan Bahtiari André L. Tits Department of Electrical and Computer Engineering and Institute for Systems
A Simple Primal-Dual Feasible Interior-Point Method for Nonlinear Programming with Monotone Descent Sasan Bahtiari André L. Tits Department of Electrical and Computer Engineering and Institute for Systems
An interior-point gradient method for large-scale totally nonnegative least squares problems
 An interior-point gradient method for large-scale totally nonnegative least squares problems Michael Merritt and Yin Zhang Technical Report TR04-08 Department of Computational and Applied Mathematics Rice
An interior-point gradient method for large-scale totally nonnegative least squares problems Michael Merritt and Yin Zhang Technical Report TR04-08 Department of Computational and Applied Mathematics Rice
Chapter 1: Linear Programming
 Chapter 1: Linear Programming Math 368 c Copyright 2013 R Clark Robinson May 22, 2013 Chapter 1: Linear Programming 1 Max and Min For f : D R n R, f (D) = {f (x) : x D } is set of attainable values of
Chapter 1: Linear Programming Math 368 c Copyright 2013 R Clark Robinson May 22, 2013 Chapter 1: Linear Programming 1 Max and Min For f : D R n R, f (D) = {f (x) : x D } is set of attainable values of
Linear Programming Redux
 Linear Programming Redux Jim Bremer May 12, 2008 The purpose of these notes is to review the basics of linear programming and the simplex method in a clear, concise, and comprehensive way. The book contains
Linear Programming Redux Jim Bremer May 12, 2008 The purpose of these notes is to review the basics of linear programming and the simplex method in a clear, concise, and comprehensive way. The book contains
Nonlinear Programming 3rd Edition. Theoretical Solutions Manual Chapter 6
 Nonlinear Programming 3rd Edition Theoretical Solutions Manual Chapter 6 Dimitri P. Bertsekas Massachusetts Institute of Technology Athena Scientific, Belmont, Massachusetts 1 NOTE This manual contains
Nonlinear Programming 3rd Edition Theoretical Solutions Manual Chapter 6 Dimitri P. Bertsekas Massachusetts Institute of Technology Athena Scientific, Belmont, Massachusetts 1 NOTE This manual contains
(Linear Programming program, Linear, Theorem on Alternative, Linear Programming duality)
 Lecture 2 Theory of Linear Programming (Linear Programming program, Linear, Theorem on Alternative, Linear Programming duality) 2.1 Linear Programming: basic notions A Linear Programming (LP) program is
Lecture 2 Theory of Linear Programming (Linear Programming program, Linear, Theorem on Alternative, Linear Programming duality) 2.1 Linear Programming: basic notions A Linear Programming (LP) program is
Lecture 1. 1 Conic programming. MA 796S: Convex Optimization and Interior Point Methods October 8, Consider the conic program. min.
 MA 796S: Convex Optimization and Interior Point Methods October 8, 2007 Lecture 1 Lecturer: Kartik Sivaramakrishnan Scribe: Kartik Sivaramakrishnan 1 Conic programming Consider the conic program min s.t.
MA 796S: Convex Optimization and Interior Point Methods October 8, 2007 Lecture 1 Lecturer: Kartik Sivaramakrishnan Scribe: Kartik Sivaramakrishnan 1 Conic programming Consider the conic program min s.t.
A Primal-Dual Interior-Point Method for Nonlinear Programming with Strong Global and Local Convergence Properties
 A Primal-Dual Interior-Point Method for Nonlinear Programming with Strong Global and Local Convergence Properties André L. Tits Andreas Wächter Sasan Bahtiari Thomas J. Urban Craig T. Lawrence ISR Technical
A Primal-Dual Interior-Point Method for Nonlinear Programming with Strong Global and Local Convergence Properties André L. Tits Andreas Wächter Sasan Bahtiari Thomas J. Urban Craig T. Lawrence ISR Technical
A QUADRATIC CONE RELAXATION-BASED ALGORITHM FOR LINEAR PROGRAMMING
 A QUADRATIC CONE RELAXATION-BASED ALGORITHM FOR LINEAR PROGRAMMING A Dissertation Presented to the Faculty of the Graduate School of Cornell University in Partial Fulfillment of the Requirements for the
A QUADRATIC CONE RELAXATION-BASED ALGORITHM FOR LINEAR PROGRAMMING A Dissertation Presented to the Faculty of the Graduate School of Cornell University in Partial Fulfillment of the Requirements for the
3. THE SIMPLEX ALGORITHM
 Optimization. THE SIMPLEX ALGORITHM DPK Easter Term. Introduction We know that, if a linear programming problem has a finite optimal solution, it has an optimal solution at a basic feasible solution (b.f.s.).
Optimization. THE SIMPLEX ALGORITHM DPK Easter Term. Introduction We know that, if a linear programming problem has a finite optimal solution, it has an optimal solution at a basic feasible solution (b.f.s.).
TRANSPORTATION PROBLEMS
 Chapter 6 TRANSPORTATION PROBLEMS 61 Transportation Model Transportation models deal with the determination of a minimum-cost plan for transporting a commodity from a number of sources to a number of destinations
Chapter 6 TRANSPORTATION PROBLEMS 61 Transportation Model Transportation models deal with the determination of a minimum-cost plan for transporting a commodity from a number of sources to a number of destinations
TMA 4180 Optimeringsteori KARUSH-KUHN-TUCKER THEOREM
 TMA 4180 Optimeringsteori KARUSH-KUHN-TUCKER THEOREM H. E. Krogstad, IMF, Spring 2012 Karush-Kuhn-Tucker (KKT) Theorem is the most central theorem in constrained optimization, and since the proof is scattered
TMA 4180 Optimeringsteori KARUSH-KUHN-TUCKER THEOREM H. E. Krogstad, IMF, Spring 2012 Karush-Kuhn-Tucker (KKT) Theorem is the most central theorem in constrained optimization, and since the proof is scattered
Convex Optimization & Lagrange Duality
 Convex Optimization & Lagrange Duality Chee Wei Tan CS 8292 : Advanced Topics in Convex Optimization and its Applications Fall 2010 Outline Convex optimization Optimality condition Lagrange duality KKT
Convex Optimization & Lagrange Duality Chee Wei Tan CS 8292 : Advanced Topics in Convex Optimization and its Applications Fall 2010 Outline Convex optimization Optimality condition Lagrange duality KKT
Lecture 7 Monotonicity. September 21, 2008
 Lecture 7 Monotonicity September 21, 2008 Outline Introduce several monotonicity properties of vector functions Are satisfied immediately by gradient maps of convex functions In a sense, role of monotonicity
Lecture 7 Monotonicity September 21, 2008 Outline Introduce several monotonicity properties of vector functions Are satisfied immediately by gradient maps of convex functions In a sense, role of monotonicity
CO 250 Final Exam Guide
 Spring 2017 CO 250 Final Exam Guide TABLE OF CONTENTS richardwu.ca CO 250 Final Exam Guide Introduction to Optimization Kanstantsin Pashkovich Spring 2017 University of Waterloo Last Revision: March 4,
Spring 2017 CO 250 Final Exam Guide TABLE OF CONTENTS richardwu.ca CO 250 Final Exam Guide Introduction to Optimization Kanstantsin Pashkovich Spring 2017 University of Waterloo Last Revision: March 4,
Interior Point Methods. We ll discuss linear programming first, followed by three nonlinear problems. Algorithms for Linear Programming Problems
 AMSC 607 / CMSC 764 Advanced Numerical Optimization Fall 2008 UNIT 3: Constrained Optimization PART 4: Introduction to Interior Point Methods Dianne P. O Leary c 2008 Interior Point Methods We ll discuss
AMSC 607 / CMSC 764 Advanced Numerical Optimization Fall 2008 UNIT 3: Constrained Optimization PART 4: Introduction to Interior Point Methods Dianne P. O Leary c 2008 Interior Point Methods We ll discuss
Preprint ANL/MCS-P , Dec 2002 (Revised Nov 2003, Mar 2004) Mathematics and Computer Science Division Argonne National Laboratory
 Preprint ANL/MCS-P1015-1202, Dec 2002 (Revised Nov 2003, Mar 2004) Mathematics and Computer Science Division Argonne National Laboratory A GLOBALLY CONVERGENT LINEARLY CONSTRAINED LAGRANGIAN METHOD FOR
Preprint ANL/MCS-P1015-1202, Dec 2002 (Revised Nov 2003, Mar 2004) Mathematics and Computer Science Division Argonne National Laboratory A GLOBALLY CONVERGENT LINEARLY CONSTRAINED LAGRANGIAN METHOD FOR
Research Note. A New Infeasible Interior-Point Algorithm with Full Nesterov-Todd Step for Semi-Definite Optimization
 Iranian Journal of Operations Research Vol. 4, No. 1, 2013, pp. 88-107 Research Note A New Infeasible Interior-Point Algorithm with Full Nesterov-Todd Step for Semi-Definite Optimization B. Kheirfam We
Iranian Journal of Operations Research Vol. 4, No. 1, 2013, pp. 88-107 Research Note A New Infeasible Interior-Point Algorithm with Full Nesterov-Todd Step for Semi-Definite Optimization B. Kheirfam We
Convex Optimization Boyd & Vandenberghe. 5. Duality
 5. Duality Convex Optimization Boyd & Vandenberghe Lagrange dual problem weak and strong duality geometric interpretation optimality conditions perturbation and sensitivity analysis examples generalized
5. Duality Convex Optimization Boyd & Vandenberghe Lagrange dual problem weak and strong duality geometric interpretation optimality conditions perturbation and sensitivity analysis examples generalized
Lecture: Duality of LP, SOCP and SDP
 1/33 Lecture: Duality of LP, SOCP and SDP Zaiwen Wen Beijing International Center For Mathematical Research Peking University http://bicmr.pku.edu.cn/~wenzw/bigdata2017.html wenzw@pku.edu.cn Acknowledgement:
1/33 Lecture: Duality of LP, SOCP and SDP Zaiwen Wen Beijing International Center For Mathematical Research Peking University http://bicmr.pku.edu.cn/~wenzw/bigdata2017.html wenzw@pku.edu.cn Acknowledgement:
6.254 : Game Theory with Engineering Applications Lecture 7: Supermodular Games
 6.254 : Game Theory with Engineering Applications Lecture 7: Asu Ozdaglar MIT February 25, 2010 1 Introduction Outline Uniqueness of a Pure Nash Equilibrium for Continuous Games Reading: Rosen J.B., Existence
6.254 : Game Theory with Engineering Applications Lecture 7: Asu Ozdaglar MIT February 25, 2010 1 Introduction Outline Uniqueness of a Pure Nash Equilibrium for Continuous Games Reading: Rosen J.B., Existence
SHIFTED BARRIER METHODS FOR LINEAR PROGRAMMING
 SHIFTED BARRIER METHODS FOR LINEAR PROGRAMMING Philip E. GILL Department of Mathematics University of California, San Diego La Jolla, California 92093 Walter MURRAY, Michael A. SAUNDERS Systems Optimization
SHIFTED BARRIER METHODS FOR LINEAR PROGRAMMING Philip E. GILL Department of Mathematics University of California, San Diego La Jolla, California 92093 Walter MURRAY, Michael A. SAUNDERS Systems Optimization
4TE3/6TE3. Algorithms for. Continuous Optimization
 4TE3/6TE3 Algorithms for Continuous Optimization (Algorithms for Constrained Nonlinear Optimization Problems) Tamás TERLAKY Computing and Software McMaster University Hamilton, November 2005 terlaky@mcmaster.ca
4TE3/6TE3 Algorithms for Continuous Optimization (Algorithms for Constrained Nonlinear Optimization Problems) Tamás TERLAKY Computing and Software McMaster University Hamilton, November 2005 terlaky@mcmaster.ca
Constrained Optimization and Lagrangian Duality
 CIS 520: Machine Learning Oct 02, 2017 Constrained Optimization and Lagrangian Duality Lecturer: Shivani Agarwal Disclaimer: These notes are designed to be a supplement to the lecture. They may or may
CIS 520: Machine Learning Oct 02, 2017 Constrained Optimization and Lagrangian Duality Lecturer: Shivani Agarwal Disclaimer: These notes are designed to be a supplement to the lecture. They may or may
Elementary linear algebra
 Chapter 1 Elementary linear algebra 1.1 Vector spaces Vector spaces owe their importance to the fact that so many models arising in the solutions of specific problems turn out to be vector spaces. The
Chapter 1 Elementary linear algebra 1.1 Vector spaces Vector spaces owe their importance to the fact that so many models arising in the solutions of specific problems turn out to be vector spaces. The
Lecture: Duality.
 Lecture: Duality http://bicmr.pku.edu.cn/~wenzw/opt-2016-fall.html Acknowledgement: this slides is based on Prof. Lieven Vandenberghe s lecture notes Introduction 2/35 Lagrange dual problem weak and strong
Lecture: Duality http://bicmr.pku.edu.cn/~wenzw/opt-2016-fall.html Acknowledgement: this slides is based on Prof. Lieven Vandenberghe s lecture notes Introduction 2/35 Lagrange dual problem weak and strong
Course Notes for EE227C (Spring 2018): Convex Optimization and Approximation
 Course Notes for EE227C (Spring 2018): Convex Optimization and Approximation Instructor: Moritz Hardt Email: hardt+ee227c@berkeley.edu Graduate Instructor: Max Simchowitz Email: msimchow+ee227c@berkeley.edu
Course Notes for EE227C (Spring 2018): Convex Optimization and Approximation Instructor: Moritz Hardt Email: hardt+ee227c@berkeley.edu Graduate Instructor: Max Simchowitz Email: msimchow+ee227c@berkeley.edu
Copositive Plus Matrices
 Copositive Plus Matrices Willemieke van Vliet Master Thesis in Applied Mathematics October 2011 Copositive Plus Matrices Summary In this report we discuss the set of copositive plus matrices and their
Copositive Plus Matrices Willemieke van Vliet Master Thesis in Applied Mathematics October 2011 Copositive Plus Matrices Summary In this report we discuss the set of copositive plus matrices and their
ABSTRACT. Primal-dual interior-point methods (IPMs) are distinguished for their exceptional
 ABSTRACT Title of dissertation: COLUMN GENERATION IN INFEASIBLE PREDICTOR-CORRECTOR METHODS FOR SOLVING LINEAR PROGRAMS Stacey O. Nicholls, Doctor of Philosophy, 2009 Dissertation directed by: Professor
ABSTRACT Title of dissertation: COLUMN GENERATION IN INFEASIBLE PREDICTOR-CORRECTOR METHODS FOR SOLVING LINEAR PROGRAMS Stacey O. Nicholls, Doctor of Philosophy, 2009 Dissertation directed by: Professor
Machine Learning. Support Vector Machines. Manfred Huber
 Machine Learning Support Vector Machines Manfred Huber 2015 1 Support Vector Machines Both logistic regression and linear discriminant analysis learn a linear discriminant function to separate the data
Machine Learning Support Vector Machines Manfred Huber 2015 1 Support Vector Machines Both logistic regression and linear discriminant analysis learn a linear discriminant function to separate the data
CS-E4830 Kernel Methods in Machine Learning
 CS-E4830 Kernel Methods in Machine Learning Lecture 3: Convex optimization and duality Juho Rousu 27. September, 2017 Juho Rousu 27. September, 2017 1 / 45 Convex optimization Convex optimisation This
CS-E4830 Kernel Methods in Machine Learning Lecture 3: Convex optimization and duality Juho Rousu 27. September, 2017 Juho Rousu 27. September, 2017 1 / 45 Convex optimization Convex optimisation This
Lecture 8: Semidefinite programs for fidelity and optimal measurements
 CS 766/QIC 80 Theory of Quantum Information (Fall 0) Lecture 8: Semidefinite programs for fidelity and optimal measurements This lecture is devoted to two examples of semidefinite programs: one is for
CS 766/QIC 80 Theory of Quantum Information (Fall 0) Lecture 8: Semidefinite programs for fidelity and optimal measurements This lecture is devoted to two examples of semidefinite programs: one is for
c 2005 Society for Industrial and Applied Mathematics
 SIAM J. OPTIM. Vol. 15, No. 4, pp. 1147 1154 c 2005 Society for Industrial and Applied Mathematics A NOTE ON THE LOCAL CONVERGENCE OF A PREDICTOR-CORRECTOR INTERIOR-POINT ALGORITHM FOR THE SEMIDEFINITE
SIAM J. OPTIM. Vol. 15, No. 4, pp. 1147 1154 c 2005 Society for Industrial and Applied Mathematics A NOTE ON THE LOCAL CONVERGENCE OF A PREDICTOR-CORRECTOR INTERIOR-POINT ALGORITHM FOR THE SEMIDEFINITE
CMSC 451: Lecture 7 Greedy Algorithms for Scheduling Tuesday, Sep 19, 2017
 CMSC CMSC : Lecture Greedy Algorithms for Scheduling Tuesday, Sep 9, 0 Reading: Sects.. and. of KT. (Not covered in DPV.) Interval Scheduling: We continue our discussion of greedy algorithms with a number
CMSC CMSC : Lecture Greedy Algorithms for Scheduling Tuesday, Sep 9, 0 Reading: Sects.. and. of KT. (Not covered in DPV.) Interval Scheduling: We continue our discussion of greedy algorithms with a number
A strongly polynomial algorithm for linear systems having a binary solution
 A strongly polynomial algorithm for linear systems having a binary solution Sergei Chubanov Institute of Information Systems at the University of Siegen, Germany e-mail: sergei.chubanov@uni-siegen.de 7th
A strongly polynomial algorithm for linear systems having a binary solution Sergei Chubanov Institute of Information Systems at the University of Siegen, Germany e-mail: sergei.chubanov@uni-siegen.de 7th
EE/AA 578, Univ of Washington, Fall Duality
 7. Duality EE/AA 578, Univ of Washington, Fall 2016 Lagrange dual problem weak and strong duality geometric interpretation optimality conditions perturbation and sensitivity analysis examples generalized
7. Duality EE/AA 578, Univ of Washington, Fall 2016 Lagrange dual problem weak and strong duality geometric interpretation optimality conditions perturbation and sensitivity analysis examples generalized
14. Duality. ˆ Upper and lower bounds. ˆ General duality. ˆ Constraint qualifications. ˆ Counterexample. ˆ Complementary slackness.
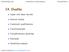 CS/ECE/ISyE 524 Introduction to Optimization Spring 2016 17 14. Duality ˆ Upper and lower bounds ˆ General duality ˆ Constraint qualifications ˆ Counterexample ˆ Complementary slackness ˆ Examples ˆ Sensitivity
CS/ECE/ISyE 524 Introduction to Optimization Spring 2016 17 14. Duality ˆ Upper and lower bounds ˆ General duality ˆ Constraint qualifications ˆ Counterexample ˆ Complementary slackness ˆ Examples ˆ Sensitivity
12. Interior-point methods
 12. Interior-point methods Convex Optimization Boyd & Vandenberghe inequality constrained minimization logarithmic barrier function and central path barrier method feasibility and phase I methods complexity
12. Interior-point methods Convex Optimization Boyd & Vandenberghe inequality constrained minimization logarithmic barrier function and central path barrier method feasibility and phase I methods complexity
