Algebraic approach to exact algorithms, Part III: Polynomials over nite elds of characteristic two
|
|
|
- Christian Hampton
- 5 years ago
- Views:
Transcription
1 Algebraic approach to exact algorithms, Part III: Polynomials over nite elds of characteristic two Šukasz Kowalik University of Warsaw ADFOCS, Saarbrücken, August 2013 Šukasz Kowalik (UW) Algebraic approach... August / 38
2 The Schwartz-Zippel Lemma Lemma [DeMillo and Lipton 1978, Zippel 1979, Schwartz 1980] Let p(x 1, x 2,..., x n ) be a non-zero polynomial of degree at most d over a eld F and let S be a nite subset of F. Sample values a 1, a 2,..., a n from S uniformly at random. Then, A typical application Pr[p(a 1, a 2,..., a n )] = 0] d/ S. We can eciently evaluate a polynomial p of degree d. We want to test whether p is a non-zero polynomial. Then, we pick S so that S 2d and we evaluate p on a random vector x S n. We answer YES i we got p(x) 0. If p is the zero polynomial we always get NO, otherwise we get YES with probability at least 1 2. This is called a Monte-Carlo algorithm with one-sided error. Šukasz Kowalik (UW) Algebraic approach... August / 38
3 The Schwartz-Zippel Lemma: Example Polynomial equality testing Input: Two multivariate polynomials P, Q given as an arithmetic circuit. Question: Does P Q? Note: A polynomial described by an arithmetic circuit of size s can have 2 Ω(s) dierent monomials: (x 1 + x 2 )(x 1 x 3 )(x 2 + x 4 ). Šukasz Kowalik (UW) Algebraic approach... August / 38
4 The Schwartz-Zippel Lemma: Example Polynomial equality testing Input: Two multivariate polynomials P, Q given as an arithmetic circuit. Question: Does P Q? Note: A polynomial described by an arithmetic circuit of size s can have 2 Ω(s) dierent monomials: (x 1 + x 2 )(x 1 x 3 )(x 2 + x 4 ). Solution Test whether the polynomial P Q is non-zero using the Schwartz-Zippel Lemma. Theorem Polynomial equality testing for two polynomials represented by circuits of size at most s can be solved in O(s) time with a Monte Carlo algorithm with one-sided error probability bounded by 1/2. Šukasz Kowalik (UW) Algebraic approach... August / 38
5 Question Question What if the bound of 1/2 for the probability of success is not enough for us? Šukasz Kowalik (UW) Algebraic approach... August / 38
6 Question Question What if the bound of 1/2 for the probability of success is not enough for us? Answer Repeat the algorithm 1000 times and answer YES if there was at least one YES. Then, Note Pr[error] The probability that an earthquake destroys the computer is probably 1 higher than Šukasz Kowalik (UW) Algebraic approach... August / 38
7 Finite elds of characteristic 2 In what follows, we use nite elds of size 2 k. We need to know just three things about such elds: They exist (for every k N), We can perform arithmetic operations fast, in O(k log k log log k) time, They are of characteristic two, i.e = 0. In particular, for any element a, we have a + a = a (1 + 1) = a 0 = 0 Šukasz Kowalik (UW) Algebraic approach... August / 38
8 k-path problem Problem Input: directed/undirected graph G, integer k. Question: Does G contain a path of length k? A few facts NP-complete (why?) Šukasz Kowalik (UW) Algebraic approach... August / 38
9 k-path problem Problem Input: directed/undirected graph G, integer k. Question: Does G contain a path of length k? A few facts NP-complete (why?) even O(f (k)n O(1) )-time algorithm is non-trivial, Šukasz Kowalik (UW) Algebraic approach... August / 38
10 k-path problem Problem Input: directed/undirected graph G, integer k. Question: Does G contain a path of length k? A few facts NP-complete (why?) even O(f (k)n O(1) )-time algorithm is non-trivial, Monien 1985: O(k!n O(1) ) Šukasz Kowalik (UW) Algebraic approach... August / 38
11 k-path problem Problem Input: directed/undirected graph G, integer k. Question: Does G contain a path of length k? A few facts NP-complete (why?) even O(f (k)n O(1) )-time algorithm is non-trivial, Monien 1985: O(k!n O(1) ) Alon, Yuster, Zwick 1994: O((2e) k n O(1) ) Šukasz Kowalik (UW) Algebraic approach... August / 38
12 k-path problem Problem Input: directed/undirected graph G, integer k. Question: Does G contain a path of length k? A few facts NP-complete (why?) even O(f (k)n O(1) )-time algorithm is non-trivial, Monien 1985: O(k!n O(1) ) Alon, Yuster, Zwick 1994: O((2e) k n O(1) ) Kneis, Mölle, Richter, Rossmanith 2006: O(4 k n O(1) ) Šukasz Kowalik (UW) Algebraic approach... August / 38
13 k-path problem Problem Input: directed/undirected graph G, integer k. Question: Does G contain a path of length k? A few facts NP-complete (why?) even O(f (k)n O(1) )-time algorithm is non-trivial, Monien 1985: O(k!n O(1) ) Alon, Yuster, Zwick 1994: O((2e) k n O(1) ) Kneis, Mölle, Richter, Rossmanith 2006: O(4 k n O(1) ) Koutis 2008: O(2 3/2k n O(1) ) Šukasz Kowalik (UW) Algebraic approach... August / 38
14 k-path problem Problem Input: directed/undirected graph G, integer k. Question: Does G contain a path of length k? A few facts NP-complete (why?) even O(f (k)n O(1) )-time algorithm is non-trivial, Monien 1985: O(k!n O(1) ) Alon, Yuster, Zwick 1994: O((2e) k n O(1) ) Kneis, Mölle, Richter, Rossmanith 2006: O(4 k n O(1) ) Koutis 2008: O(2 3/2k n O(1) ) Williams 2009: O(2 k n O(1) ) Šukasz Kowalik (UW) Algebraic approach... August / 38
15 k-path problem Problem Input: directed/undirected graph G, integer k. Question: Does G contain a path of length k? A few facts NP-complete (why?) even O(f (k)n O(1) )-time algorithm is non-trivial, Monien 1985: O(k!n O(1) ) Alon, Yuster, Zwick 1994: O((2e) k n O(1) ) Kneis, Mölle, Richter, Rossmanith 2006: O(4 k n O(1) ) Koutis 2008: O(2 3/2k n O(1) ) Williams 2009: O(2 k n O(1) ) Björklund 2010: O(1.66 n n O(1) ), undirected Hamiltonian cycle (k = n) Šukasz Kowalik (UW) Algebraic approach... August / 38
16 k-path problem Problem Input: directed/undirected graph G, integer k. Question: Does G contain a path of length k? A few facts NP-complete (why?) even O(f (k)n O(1) )-time algorithm is non-trivial, Monien 1985: O(k!n O(1) ) Alon, Yuster, Zwick 1994: O((2e) k n O(1) ) Kneis, Mölle, Richter, Rossmanith 2006: O(4 k n O(1) ) Koutis 2008: O(2 3/2k n O(1) ) Williams 2009: O(2 k n O(1) ) Björklund 2010: O(1.66 n n O(1) ), undirected Hamiltonian cycle (k = n) Björklund, Husfeldt, Kaski, Koivisto 2010: O(1.66 k n O(1) ), undirected Šukasz Kowalik (UW) Algebraic approach... August / 38
17 k-path in O (2 k )-time Šukasz Kowalik (UW) Algebraic approach... August / 38
18 Notation [k] = {1,..., k} Šukasz Kowalik (UW) Algebraic approach... August / 38
19 O (2 k )-time algorithm for k-path Rough idea Want to construct a polynomial P, P 0 i G has a k-path. Šukasz Kowalik (UW) Algebraic approach... August / 38
20 O (2 k )-time algorithm for k-path Rough idea Want to construct a polynomial P, P 0 i G has a k-path. First try: P( ) = monomial(r). k-path R in G Seems good, but how to evaluate it? Šukasz Kowalik (UW) Algebraic approach... August / 38
21 O (2 k )-time algorithm for k-path Rough idea Want to construct a polynomial P, P 0 i G has a k-path. First try: P( ) = monomial(r). k-path R in G Seems good, but how to evaluate it? Second try: P( ) = monomial(w ). k-walk W in G Now we can evaluate it but we may get false positives. Šukasz Kowalik (UW) Algebraic approach... August / 38
22 O (2 k )-time algorithm for k-path Rough idea Want to construct a polynomial P, P 0 i G has a k-path. First try: P( ) = monomial(r). k-path R in G Seems good, but how to evaluate it? Second try: P( ) = monomial(w ). k-walk W in G Now we can evaluate it but we may get false positives. Final try: P( ) = monomial(w, l). k-walk W in G l:[k] [k] l is bijective We still can evaluate it, It turns out that every monomial corresponding to a walk which is not a path appears an even number of times so it cancels-out! Šukasz Kowalik (UW) Algebraic approach... August / 38
23 Our Hero P(x, y) = k 1 walk W = v 1,..., v k l:[k] [k] i=1 l is bijective k x vi,v i+1 y vi,l(i) i=1 } {{ } mon W,l Variables: a variable x e for every e E, a variable y v,l for every v V and l [k]. Šukasz Kowalik (UW) Algebraic approach... August / 38
24 Monomials corresponding to non-path walks cancel-out Let W = v 1,..., v k be a walk, and a bijection l S k. Šukasz Kowalik (UW) Algebraic approach... August / 38
25 Monomials corresponding to non-path walks cancel-out Let W = v 1,..., v k be a walk, and a bijection l S k. Assume v a = v b for some a < b, if many such pairs take the lexicographically rst. Šukasz Kowalik (UW) Algebraic approach... August / 38
26 Monomials corresponding to non-path walks cancel-out Let W = v 1,..., v k be a walk, and a bijection l S k. Assume v a = v b for some a < b, if many such pairs take the lexicographically rst. We dene l : [k] [k] as follows: l(b) if x = a, l (x) = l(a) if x = b, l(x) otherwise. Šukasz Kowalik (UW) Algebraic approach... August / 38
27 Monomials corresponding to non-path walks cancel-out Let W = v 1,..., v k be a walk, and a bijection l S k. Assume v a = v b for some a < b, if many such pairs take the lexicographically rst. We dene l : [k] [k] as follows: l(b) if x = a, l (x) = l(a) if x = b, l(x) otherwise. (W, l) (W, l ) since l is injective. Šukasz Kowalik (UW) Algebraic approach... August / 38
28 Monomials corresponding to non-path walks cancel-out Let W = v 1,..., v k be a walk, and a bijection l S k. Assume v a = v b for some a < b, if many such pairs take the lexicographically rst. We dene l : [k] [k] as follows: l(b) if x = a, l (x) = l(a) if x = b, l(x) otherwise. (W, l) (W, l ) since l is injective. k 1 k mon W,l = y vi,l(i) = k 1 x vi,v i+1 i=1 i=1 x vi,v i+1 i=1 i [k]\{a,b} y vi,l(i) y va,l(a) }{{} y vb l (b) y vb,l(b) }{{} y val (a) = mon W,l Šukasz Kowalik (UW) Algebraic approach... August / 38
29 Monomials corresponding to non-path walks cancel-out Let W = v 1,..., v k be a walk, and a bijection l S k. Assume v a = v b for some a < b, if many such pairs take the lexicographically rst. We dene l : [k] [k] as follows: l(b) if x = a, l (x) = l(a) if x = b, l(x) otherwise. (W, l) (W, l ) since l is injective. mon W,l = mon W,l Šukasz Kowalik (UW) Algebraic approach... August / 38
30 Monomials corresponding to non-path walks cancel-out Let W = v 1,..., v k be a walk, and a bijection l S k. Assume v a = v b for some a < b, if many such pairs take the lexicographically rst. We dene l : [k] [k] as follows: l(b) if x = a, l (x) = l(a) if x = b, l(x) otherwise. (W, l) (W, l ) since l is injective. mon W,l = mon W,l If we start from (W, l ) and follow the same way of assignment we get (W, l) back. (This is called a xed-point free involution) Šukasz Kowalik (UW) Algebraic approach... August / 38
31 Monomials corresponding to non-path walks cancel-out Let W = v 1,..., v k be a walk, and a bijection l S k. Assume v a = v b for some a < b, if many such pairs take the lexicographically rst. We dene l : [k] [k] as follows: l(b) if x = a, l (x) = l(a) if x = b, l(x) otherwise. (W, l) (W, l ) since l is injective. mon W,l = mon W,l If we start from (W, l ) and follow the same way of assignment we get (W, l) back. (This is called a xed-point free involution) Since the eld is of characteristic 2, mon W,l and mon W,l cancel out! Šukasz Kowalik (UW) Algebraic approach... August / 38
32 Half the way... Corollary If P 0 then there is a k-path. Šukasz Kowalik (UW) Algebraic approach... August / 38
33 The second half Recall: P(x, y) = k 1 walk W = v 1,..., v k l:[k] [k] i=1 l is bijective k x vi,v i+1 y vi,l(i) i=1 } {{ } mon W,l Question Why do we need exactly mon W,l = k 1 i=1 x v i,v i+1 k i=1 y v i,l(i)? What if, say, mon W,l = k i=1 y v i,l(i)? Šukasz Kowalik (UW) Algebraic approach... August / 38
34 The second half Recall: P(x, y) = k 1 walk W = v 1,..., v k l:[k] [k] i=1 l is bijective k x vi,v i+1 y vi,l(i) i=1 } {{ } mon W,l Question Why do we need exactly mon W,l = k 1 i=1 x v i,v i+1 k i=1 y v i,l(i)? What if, say, mon W,l = k i=1 y v i,l(i)? Answer Now, every labelled walk which is a path gets a unique monomial. Šukasz Kowalik (UW) Algebraic approach... August / 38
35 The second half Recall: P(x, y) = k 1 walk W = v 1,..., v k l:[k] [k] i=1 l is bijective k x vi,v i+1 y vi,l(i) i=1 } {{ } mon W,l Question Why do we need exactly mon W,l = k 1 i=1 x v i,v i+1 k i=1 y v i,l(i)? What if, say, mon W,l = k i=1 y v i,l(i)? Answer Now, every labelled walk which is a path gets a unique monomial. Corollary If there is a k-path in G then P 0. Šukasz Kowalik (UW) Algebraic approach... August / 38
36 Where are we? Corollary There is a k-path in G i P 0. The missing element How to evaluate P eciently? (O (2 k ) is eciently enough.) Šukasz Kowalik (UW) Algebraic approach... August / 38
37 Weighted inclusion-exclusion Let A 1,..., A n U, where U is a nite set. Let w : U F be a weight function. For any X U denote w(x ) = x X w(x). Let us also denote i (U A i) = U. Then, w = ( ) ( 1) X w (U A i ). A i i [n] X [n] i X Šukasz Kowalik (UW) Algebraic approach... August / 38
38 Weighted inclusion-exclusion Let A 1,..., A n U, where U is a nite set. Let w : U F be a weight function. For any X U denote w(x ) = x X w(x). Let us also denote i (U A i) = U. Then, w = ( ) ( 1) X w (U A i ). A i i [n] X [n] i X Counting over a eld of characteristic 2 we know that 1 = 1 so we can remove the ( 1) X : w = ( ) w (U A i ). i [n] A i X [n] Šukasz Kowalik (UW) Algebraic approach... August / 38 i X
39 Evaluating P(x, y) = walk W l:[k] [k] l is bijective mon W,l (x, y) Fix a walk W. U = {l : [k] [k]} (all functions) for l U, dene the weight w(l) = mon W,l (x, y). for i = 1,..., k let A i = {l U : l 1 (i) }. Then, mon W,l (x, y) = mon W,l (x, y) = w( l:[k] [k] l is bijective l:[k] [k] l is surjective l:[k] [k] l is surjective By weighted I-E, mon W,l (x, y) = ( ) w (U A i ) = X [k] l:[k] [k]\x mon W,l (x, y) X [k] i X k A i ). Šukasz Kowalik (UW) Algebraic approach... August / 38 i=1
40 Evaluating P(x, y) = walk W l:[k] [k] l is bijective mon W,l (x, y) Fix a walk W. U = {l : [k] [k]} (all functions) for l U, dene the weight w(l) = mon W,l (x, y). for i = 1,..., k let A i = {l U : l 1 (i) }. Then, mon W,l (x, y) = mon W,l (x, y) = w( l:[k] [k] l is bijective l:[k] [k] l is surjective l:[k] [k] l is surjective By weighted I-E, mon W,l (x, y) = ( ) w (U A i ) = X [k] l:[k] X mon W,l (x, y) X [k] i X k A i ). Šukasz Kowalik (UW) Algebraic approach... August / 38 i=1
41 Evaluating P(x, y) = walk W l:[k] [k] l is bijective mon W,l (x, y) We got Hence, l:[k] [k] l is bijective mon W,l (x, y) = X [k] l:[k] X mon W,l (x, y) P(x, y) = walk W X [k] l:[k] X = X [k] walk W l:[k] X mon W,l (x, y) mon W,l (x, y) } {{ } P X (x,y) Šukasz Kowalik (UW) Algebraic approach... August / 38
42 Evaluating P X (x, y) = mon W,l (x, y) in n O(1) walk W l:[k] X of length k We use dynamic programming. (How?) Šukasz Kowalik (UW) Algebraic approach... August / 38
43 Evaluating P X (x, y) = walk W l:[k] X of length k We use dynamic programming. (How?) Fill the 2-dimensional table T, mon W,l (x, y) in n O(1) Then, T [v, d] = walk W = v 1,..., v d v 1 = v d 1 l:[k] X i=1 d x vi,v i+1 y vi,l(i) i=1 y vl when d = 1, l X T [v, d] = y vl x vw T [w, d 1] otherwise. l X (v,w) E Hence, P X (x, y) = s V T [s, k] can be computed in O(k E ) time. Šukasz Kowalik (UW) Algebraic approach... August / 38
44 Conclusion Corollary The k-path problem can be solved by a O (2 k )-time polynomial space one-sided error Monte-Carlo algorithm. Šukasz Kowalik (UW) Algebraic approach... August / 38
45 k-path in undirected bipartite graphs in O (2 k/2 ) time Šukasz Kowalik (UW) Algebraic approach... August / 38
46 k-path in undirected bipartite graphs in O (2 k/2 ) time V 2 V 1 Šukasz Kowalik (UW) Algebraic approach... August / 38
47 A new hero Idea Label vertices of V 1 only. P(x, y) = walk W = v 1,..., v k l:[k/2] [k/2] l is bijective k 1 i=1 k/2 x vi,v i+1 y v2i 1,l(i) i=1 } {{ } mon W,l Variables: a variable x e for every e E (x u v = x v u), a variable y v,l for every v V and l [k/2]. Šukasz Kowalik (UW) Algebraic approach... August / 38
48 Checking the hero P(x, y) = walk W = v 1,..., v k l:[k/2] [k/2] l is bijective k 1 i=1 k/2 x vi,v i+1 y v2i 1,l(i) i=1 } {{ } mon W,l Paths do not cancel-out If there is a k-path with an endpoint in V 1 then P 0. (Proof: We can recover (W, l) from mon W,l as before.) Šukasz Kowalik (UW) Algebraic approach... August / 38
49 Checking the hero P(x, y) = walk W = v 1,..., v k Do non-path walks cancel-out? l:[k/2] [k/2] l is bijective k 1 i=1 k/2 x vi,v i+1 y v2i 1,l(i) i=1 } {{ } mon W,l Consider a non-path labelled walk (W, l), W = v 1,..., v k. Case 1 If exist i, j, i < j s.t. v i = v j, v i V 1 : pick lexicographically rst such pair; both v i and v j have labels so we swap labels as before. Case 2 As in Case 1, but v i V 2 and Case 1 does not occur: reverse the cycle: l 2 l 1 l 2 l 1 mon W,l = mon W,l, W v i = v j W v i = v j from (W, l ) we get (W, l), Does (W, l) (W, l )? Šukasz Kowalik (UW) Algebraic approach... August / 38
50 Checking the hero P(x, y) = walk W = v 1,..., v k Do non-path walks cancel-out? l:[k/2] [k/2] l is bijective k 1 i=1 k/2 x vi,v i+1 y v2i 1,l(i) i=1 } {{ } mon W,l Consider a non-path labelled walk (W, l), W = v 1,..., v k. Case 1 If exist i, j, i < j s.t. v i = v j, v i V 1 : pick lexicographically rst such pair; both v i and v j have labels so we swap labels as before. Case 2 As in Case 1, but v i V 2 and Case 1 does not occur: reverse the cycle: W v i = v j W v i = v j mon W,l = mon W,l, from (W, l ) we get (W, l), Does (W, l) (W, l )? NO! Šukasz Kowalik (UW) Algebraic approach... August / 38
51 Fixing the hero Admissible walks Walk v 1,..., v k is admissible if: For every i = 1,..., k 2, if v i V 2 and v i+1 V 1 then v i+2 v i. P(x, y) = walk W = v 1,..., v k W is admissible l:[k/2] [k/2] l is bijective k 1 i=1 k/2 x vi,v i+1 y v2i 1,l(i) i=1 } {{ } mon W,l Šukasz Kowalik (UW) Algebraic approach... August / 38
52 Checking the xed hero P(x, y) = walk W = v 1,..., v k W is admissible Do non-path walks cancel-out? l:[k/2] [k/2] l is bijective k 1 i=1 k/2 x vi,v i+1 y v2i 1,l(i) i=1 } {{ } mon W,l Consider a non-path labelled walk (W, l), W = v 1,..., v k. Case 1 If exist i, j, i < j s.t. v i = v j, v i V 1 : pick lexicographically rst such pair; both v i and v j have labels so we swap labels as before. Case 2 As in Case 1, but v i V 2 and Case 1 does not occur: reverse the cycle: mon W,l = mon W,l l 2 l 1 l, 2 l 1 from (W, l ) we get (W, l), W W (W, l) (W, l ) because W v i = v j v i = v j admissible, W is admissible. Šukasz Kowalik (UW) Algebraic approach... August / 38
53 Evaluating P(x, y) = admissible walk W l:[k/2] [k/2] l is bijective mon W,l (x, y) As before, from inclusion-exclusion principle we can get l:[k/2] [k/2] l is bijective Hence, as before: mon W,l (x, y) = X [k/2] l:[k/2] X mon W,l (x, y) P(x, y) = = admissible walk W X [k/2] l:[k/2] X X [k/2] admissible walk W l:[k/2] X mon W,l (x, y) mon W,l (x, y) } {{ } P X (x,y) Note: Only 2 k/2 polynomials P X to evaluate. Šukasz Kowalik (UW) Algebraic approach... August / 38
54 Evaluating P X (x, y) = Dynamic programming: Then, T [v, w, d] = admissiblel:[k/2] X walk W of length k admissible walk W = v 1,..., v d v 1 = v v 2 = w l:[k/2] X i=1 mon W,l in poly-time k 1 k/2 x vi,v i+1 y v2i 1,l(i) x vw l X y vl when d = 2 and v V 1, x vw l X y wl when d = 2 and v V 2, y vl x vw T [w, u, d 1] when d > 2 and v V 1, T [v, w, d] = l X (w,u) E x vw T [w, u, d 1] when d > 2 and v V 2. (w,u) E u v Šukasz Kowalik (UW) Algebraic approach... August / 38 i=1
55 Conclusion Theorem (Björklund, Husfeldt, Kaski, Koivisto 2010) The k-path problem in undirected bipartite graphs can be solved in O (2 k/2 ) = O (1.42 k ) time and polynomial space. Šukasz Kowalik (UW) Algebraic approach... August / 38
56 Conclusion Theorem (Björklund, Husfeldt, Kaski, Koivisto 2010) The k-path problem in undirected bipartite graphs can be solved in O (2 k/2 ) = O (1.42 k ) time and polynomial space. Šukasz Kowalik (UW) Algebraic approach... August / 38
57 k-path in undirected graphs in 3 O (24 k ) time Šukasz Kowalik (UW) Algebraic approach... August / 38
58 k-path in undirected graphs in O (2 3 4 k ) time Choose a random bipartition V = V 1 V 2, V 1 V 2 1. (V 1 and V 2 need not be independent now.) Where does the bipartite case algorithm fail? W W Then (W, l) = (W, l ). v i = v j v i = v j Šukasz Kowalik (UW) Algebraic approach... August / 38
59 k-path in undirected graphs in O (2 3 4 k ) time Choose a random bipartition V = V 1 V 2, V 1 V 2 1. (V 1 and V 2 need not be independent now.) Where does the bipartite case algorithm fail? W W Then (W, l) = (W, l ). v i = v j v i = v j What if we forbid also? Šukasz Kowalik (UW) Algebraic approach... August / 38
60 k-path in undirected graphs in O (2 3 4 k ) time Choose a random bipartition V = V 1 V 2, V 1 V 2 1. (V 1 and V 2 need not be independent now.) Where does the bipartite case algorithm fail? W W Then (W, l) = (W, l ). v i = v j v i = v j What if we forbid also? Then we run into another trouble: W W W contains the forbidden conguration. Šukasz Kowalik (UW) Algebraic approach... August / 38
61 The solution Forbidden conguration as before: Add more labels: label each V 2 V 2 -edge: W W l 2 l 1 l 2 l 1 Now l l. v i = v j v i = v j Šukasz Kowalik (UW) Algebraic approach... August / 38
62 How many labels do we need now? a dierent label for each i = 1,..., k s.t. v i V 1 a dierent label for each i = 1,..., k s.t. v i v i+1 V 2 Šukasz Kowalik (UW) Algebraic approach... August / 38
63 L-admissible walks Walk W = v 1,..., v k is L-admissible when For every i = 1,..., k 2, if v i V 2 and v i+1 V 1 then v i+2 v i. {i : v i V 1 } + {i : v i v i+1 V 2 } = L Šukasz Kowalik (UW) Algebraic approach... August / 38
64 The ultimate hero P L (x, y) = walk W = v 1,..., v k W is L-admissible l:[l] [L] l is bijective k 1 x vi,v i+1 i=1 i=1 L y f (i),l(i), where f (i) = i-th labeled object (V 1 -vertex or V 2 V 2 -edge) in walk W. f (3) f (5) f (4) f (1) f (2) f (6) P = 3 4 k L=k/2 P L Šukasz Kowalik (UW) Algebraic approach... August / 38
65 Correctness We have checked that: P 0 exists k-path (i.e. non-path walks cancel-out) Šukasz Kowalik (UW) Algebraic approach... August / 38
66 Correctness We have checked that: P 0 exists k-path (i.e. non-path walks cancel-out) The opposite implication not always true! (why?) Šukasz Kowalik (UW) Algebraic approach... August / 38
67 Correctness We have checked that: P 0 exists k-path (i.e. non-path walks cancel-out) The opposite implication not always true! (why?) it may happen that the only (say) solution P is not L-admissible for all L 3 4 k. Šukasz Kowalik (UW) Algebraic approach... August / 38
68 Correctness We have checked that: P 0 exists k-path (i.e. non-path walks cancel-out) The opposite implication not always true! (why?) it may happen that the only (say) solution P is not L-admissible for all L 3 4 k. But... E[ {i : v i V 1 } + {i : v i v i+1 V 2 } ] = k + k 1 = 3k Šukasz Kowalik (UW) Algebraic approach... August / 38
69 Correctness We have checked that: P 0 exists k-path (i.e. non-path walks cancel-out) The opposite implication not always true! (why?) it may happen that the only (say) solution P is not L-admissible for all L 3 4 k. But... E[ {i : v i V 1 } + {i : v i v i+1 V 2 } ] = k + k 1 = 3k So, by Markov inequality Pr[P is not L-admissible for all L 3 (3k 1)/4 4k ] 3 4 k + 1 = 1 1/O(k) Šukasz Kowalik (UW) Algebraic approach... August / 38
70 Correctness We have checked that: P 0 exists k-path (i.e. non-path walks cancel-out) The opposite implication not always true! (why?) it may happen that the only (say) solution P is not L-admissible for all L 3 4 k. But... E[ {i : v i V 1 } + {i : v i v i+1 V 2 } ] = k + k 1 = 3k So, by Markov inequality Pr[P is not L-admissible for all L 3 (3k 1)/4 4k ] 3 4 k + 1 = 1 1/O(k) If we repeat the algorithm k log n times this probability drops to (1 1/O(k)) k log n = (e 1/O(k) ) k log n = e O(log n) = 1/n Ω(1) Šukasz Kowalik (UW) Algebraic approach... August / 38
71 Conclusion Theorem (Björklund, Husfeldt, Kaski, Koivisto 2010) The k-path problem in undirected graphs can be solved in O (2 3k/4 ) = O (1.682 k ) time and polynomial space. Šukasz Kowalik (UW) Algebraic approach... August / 38
72 Conclusion Theorem (Björklund, Husfeldt, Kaski, Koivisto 2010) The k-path problem in undirected graphs can be solved in O (2 3k/4 ) = O (1.682 k ) time and polynomial space. Exercises: tune the algorithm to get O (1.66 k ). Corollary (Björklund 2009) The Hamiltonian Cycle problem in undirected graphs can be solved in O (1.66 k ) time and polynomial space. Šukasz Kowalik (UW) Algebraic approach... August / 38
CPSC 536N: Randomized Algorithms Term 2. Lecture 9
 CPSC 536N: Randomized Algorithms 2011-12 Term 2 Prof. Nick Harvey Lecture 9 University of British Columbia 1 Polynomial Identity Testing In the first lecture we discussed the problem of testing equality
CPSC 536N: Randomized Algorithms 2011-12 Term 2 Prof. Nick Harvey Lecture 9 University of British Columbia 1 Polynomial Identity Testing In the first lecture we discussed the problem of testing equality
(x 1 +x 2 )(x 1 x 2 )+(x 2 +x 3 )(x 2 x 3 )+(x 3 +x 1 )(x 3 x 1 ).
 CMPSCI611: Verifying Polynomial Identities Lecture 13 Here is a problem that has a polynomial-time randomized solution, but so far no poly-time deterministic solution. Let F be any field and let Q(x 1,...,
CMPSCI611: Verifying Polynomial Identities Lecture 13 Here is a problem that has a polynomial-time randomized solution, but so far no poly-time deterministic solution. Let F be any field and let Q(x 1,...,
Lecture 04: Secret Sharing Schemes (2) Secret Sharing
 Lecture 04: Schemes (2) Recall: Goal We want to Share a secret s Z p to n parties, such that {1,..., n} Z p, Any two parties can reconstruct the secret s, and No party alone can predict the secret s Recall:
Lecture 04: Schemes (2) Recall: Goal We want to Share a secret s Z p to n parties, such that {1,..., n} Z p, Any two parties can reconstruct the secret s, and No party alone can predict the secret s Recall:
arxiv: v2 [cs.ds] 22 Jan 2014
![arxiv: v2 [cs.ds] 22 Jan 2014 arxiv: v2 [cs.ds] 22 Jan 2014](/thumbs/94/121868880.jpg) On r-simple k-path arxiv:1312.4863v2 [cs.ds] 22 Jan 2014 Hasan Abasi Nader H. Bshouty Ariel Gabizon Elad Haramaty Department of Computer Science Technion, Haifa June 15, 2018 Abstract An r-simple k-path
On r-simple k-path arxiv:1312.4863v2 [cs.ds] 22 Jan 2014 Hasan Abasi Nader H. Bshouty Ariel Gabizon Elad Haramaty Department of Computer Science Technion, Haifa June 15, 2018 Abstract An r-simple k-path
Lecture 7: Schwartz-Zippel Lemma, Perfect Matching. 1.1 Polynomial Identity Testing and Schwartz-Zippel Lemma
 CSE 521: Design and Analysis of Algorithms I Winter 2017 Lecture 7: Schwartz-Zippel Lemma, Perfect Matching Lecturer: Shayan Oveis Gharan 01/30/2017 Scribe: Philip Cho Disclaimer: These notes have not
CSE 521: Design and Analysis of Algorithms I Winter 2017 Lecture 7: Schwartz-Zippel Lemma, Perfect Matching Lecturer: Shayan Oveis Gharan 01/30/2017 Scribe: Philip Cho Disclaimer: These notes have not
Lecture 5 Polynomial Identity Testing
 Lecture 5 Polynomial Identity Testing Michael P. Kim 18 April 2017 1 Outline and Motivation In this lecture we will cover a fundamental problem in complexity theory polynomial identity testing (PIT). We
Lecture 5 Polynomial Identity Testing Michael P. Kim 18 April 2017 1 Outline and Motivation In this lecture we will cover a fundamental problem in complexity theory polynomial identity testing (PIT). We
Lecture 2: January 18
 CS271 Randomness & Computation Spring 2018 Instructor: Alistair Sinclair Lecture 2: January 18 Disclaimer: These notes have not been subjected to the usual scrutiny accorded to formal publications. They
CS271 Randomness & Computation Spring 2018 Instructor: Alistair Sinclair Lecture 2: January 18 Disclaimer: These notes have not been subjected to the usual scrutiny accorded to formal publications. They
Faster Algorithm for Optimum Steiner Trees. Jens Vygen
 Faster Algorithm for Optimum Steiner Trees Jens Vygen University of Bonn Aussois 2010 The Steiner Tree Problem Given an undirected graph G with weights c : E(G) R +, and a terminal set T V (G), The Steiner
Faster Algorithm for Optimum Steiner Trees Jens Vygen University of Bonn Aussois 2010 The Steiner Tree Problem Given an undirected graph G with weights c : E(G) R +, and a terminal set T V (G), The Steiner
Limits and Applications of Group Algebras for Parameterized Problems
 Limits and Applications of Group Algebras for Parameterized Problems Ioannis Koutis Computer Science Department Carnegie Mellon University ioannis.koutis@cs.cmu.edu Ryan Williams School of Mathematics
Limits and Applications of Group Algebras for Parameterized Problems Ioannis Koutis Computer Science Department Carnegie Mellon University ioannis.koutis@cs.cmu.edu Ryan Williams School of Mathematics
Structural Grobner Basis. Bernd Sturmfels and Markus Wiegelmann TR May Department of Mathematics, UC Berkeley.
 I 1947 Center St. Suite 600 Berkeley, California 94704-1198 (510) 643-9153 FAX (510) 643-7684 INTERNATIONAL COMPUTER SCIENCE INSTITUTE Structural Grobner Basis Detection Bernd Sturmfels and Markus Wiegelmann
I 1947 Center St. Suite 600 Berkeley, California 94704-1198 (510) 643-9153 FAX (510) 643-7684 INTERNATIONAL COMPUTER SCIENCE INSTITUTE Structural Grobner Basis Detection Bernd Sturmfels and Markus Wiegelmann
Advanced Combinatorial Optimization Feb 13 and 25, Lectures 4 and 6
 18.438 Advanced Combinatorial Optimization Feb 13 and 25, 2014 Lectures 4 and 6 Lecturer: Michel X. Goemans Scribe: Zhenyu Liao and Michel X. Goemans Today, we will use an algebraic approach to solve the
18.438 Advanced Combinatorial Optimization Feb 13 and 25, 2014 Lectures 4 and 6 Lecturer: Michel X. Goemans Scribe: Zhenyu Liao and Michel X. Goemans Today, we will use an algebraic approach to solve the
arxiv: v3 [cs.ds] 27 Nov 2014
![arxiv: v3 [cs.ds] 27 Nov 2014 arxiv: v3 [cs.ds] 27 Nov 2014](/thumbs/89/98391470.jpg) Representative sets for multisets Ariel Gabizon Daniel Lokshtanov Michal Pilipczuk December 1, 2014 arxiv:1411.6756v3 [cs.ds] 27 Nov 2014 Abstract The notion of a q-representative set for a family of subsets
Representative sets for multisets Ariel Gabizon Daniel Lokshtanov Michal Pilipczuk December 1, 2014 arxiv:1411.6756v3 [cs.ds] 27 Nov 2014 Abstract The notion of a q-representative set for a family of subsets
20.1 2SAT. CS125 Lecture 20 Fall 2016
 CS125 Lecture 20 Fall 2016 20.1 2SAT We show yet another possible way to solve the 2SAT problem. Recall that the input to 2SAT is a logical expression that is the conunction (AND) of a set of clauses,
CS125 Lecture 20 Fall 2016 20.1 2SAT We show yet another possible way to solve the 2SAT problem. Recall that the input to 2SAT is a logical expression that is the conunction (AND) of a set of clauses,
Improved Algorithms for Path, Matching, and Packing Problems
 Improved Algorithms for Path, Matching, and Packing Problems Jianer Chen Songjian Lu Sing-Hoi Sze Fenghui Zhang Abstract Improved randomized and deterministic algorithms are presented for path, matching,
Improved Algorithms for Path, Matching, and Packing Problems Jianer Chen Songjian Lu Sing-Hoi Sze Fenghui Zhang Abstract Improved randomized and deterministic algorithms are presented for path, matching,
Lecture 15 - NP Completeness 1
 CME 305: Discrete Mathematics and Algorithms Instructor: Professor Aaron Sidford (sidford@stanford.edu) February 29, 2018 Lecture 15 - NP Completeness 1 In the last lecture we discussed how to provide
CME 305: Discrete Mathematics and Algorithms Instructor: Professor Aaron Sidford (sidford@stanford.edu) February 29, 2018 Lecture 15 - NP Completeness 1 In the last lecture we discussed how to provide
ACO Comprehensive Exam March 17 and 18, Computability, Complexity and Algorithms
 1. Computability, Complexity and Algorithms (a) Let G(V, E) be an undirected unweighted graph. Let C V be a vertex cover of G. Argue that V \ C is an independent set of G. (b) Minimum cardinality vertex
1. Computability, Complexity and Algorithms (a) Let G(V, E) be an undirected unweighted graph. Let C V be a vertex cover of G. Argue that V \ C is an independent set of G. (b) Minimum cardinality vertex
THE MAXIMAL SUBGROUPS AND THE COMPLEXITY OF THE FLOW SEMIGROUP OF FINITE (DI)GRAPHS
 THE MAXIMAL SUBGROUPS AND THE COMPLEXITY OF THE FLOW SEMIGROUP OF FINITE (DI)GRAPHS GÁBOR HORVÁTH, CHRYSTOPHER L. NEHANIV, AND KÁROLY PODOSKI Dedicated to John Rhodes on the occasion of his 80th birthday.
THE MAXIMAL SUBGROUPS AND THE COMPLEXITY OF THE FLOW SEMIGROUP OF FINITE (DI)GRAPHS GÁBOR HORVÁTH, CHRYSTOPHER L. NEHANIV, AND KÁROLY PODOSKI Dedicated to John Rhodes on the occasion of his 80th birthday.
ACO Comprehensive Exam October 14 and 15, 2013
 1. Computability, Complexity and Algorithms (a) Let G be the complete graph on n vertices, and let c : V (G) V (G) [0, ) be a symmetric cost function. Consider the following closest point heuristic for
1. Computability, Complexity and Algorithms (a) Let G be the complete graph on n vertices, and let c : V (G) V (G) [0, ) be a symmetric cost function. Consider the following closest point heuristic for
Formalizing Randomized Matching Algorithms
 Formalizing Randomized Matching Algorithms Stephen Cook Joint work with Dai Tri Man Lê Department of Computer Science University of Toronto Canada The Banff Workshop on Proof Complexity 2011 1 / 15 Feasible
Formalizing Randomized Matching Algorithms Stephen Cook Joint work with Dai Tri Man Lê Department of Computer Science University of Toronto Canada The Banff Workshop on Proof Complexity 2011 1 / 15 Feasible
Complexity Theory of Polynomial-Time Problems
 Complexity Theory of Polynomial-Time Problems Lecture 11: Nondeterministic SETH Karl Bringmann Complexity Inside P SAT 2 n 3SUM n 2 OV n 2 Colinearity n 2 3SUM-hard APSP n 3 APSP equivalent Radius n 3
Complexity Theory of Polynomial-Time Problems Lecture 11: Nondeterministic SETH Karl Bringmann Complexity Inside P SAT 2 n 3SUM n 2 OV n 2 Colinearity n 2 3SUM-hard APSP n 3 APSP equivalent Radius n 3
Computational Complexity: Problem Set 4
 Computational Complexity: Problem Set 4 Due: Friday January 8, 16, at 3:59 AoE. Submit your solutions as a PDF le by e-mail to jakobn at kth dot se with the subject line Problem set 4: your full name.
Computational Complexity: Problem Set 4 Due: Friday January 8, 16, at 3:59 AoE. Submit your solutions as a PDF le by e-mail to jakobn at kth dot se with the subject line Problem set 4: your full name.
10. Noether Normalization and Hilbert s Nullstellensatz
 10. Noether Normalization and Hilbert s Nullstellensatz 91 10. Noether Normalization and Hilbert s Nullstellensatz In the last chapter we have gained much understanding for integral and finite ring extensions.
10. Noether Normalization and Hilbert s Nullstellensatz 91 10. Noether Normalization and Hilbert s Nullstellensatz In the last chapter we have gained much understanding for integral and finite ring extensions.
List of Theorems. Mat 416, Introduction to Graph Theory. Theorem 1 The numbers R(p, q) exist and for p, q 2,
 List of Theorems Mat 416, Introduction to Graph Theory 1. Ramsey s Theorem for graphs 8.3.11. Theorem 1 The numbers R(p, q) exist and for p, q 2, R(p, q) R(p 1, q) + R(p, q 1). If both summands on the
List of Theorems Mat 416, Introduction to Graph Theory 1. Ramsey s Theorem for graphs 8.3.11. Theorem 1 The numbers R(p, q) exist and for p, q 2, R(p, q) R(p 1, q) + R(p, q 1). If both summands on the
Theory of Computer Science to Msc Students, Spring Lecture 2
 Theory of Computer Science to Msc Students, Spring 2007 Lecture 2 Lecturer: Dorit Aharonov Scribe: Bar Shalem and Amitai Gilad Revised: Shahar Dobzinski, March 2007 1 BPP and NP The theory of computer
Theory of Computer Science to Msc Students, Spring 2007 Lecture 2 Lecturer: Dorit Aharonov Scribe: Bar Shalem and Amitai Gilad Revised: Shahar Dobzinski, March 2007 1 BPP and NP The theory of computer
Fine Grained Counting Complexity I
 Fine Grained Counting Complexity I Holger Dell Saarland University and Cluster of Excellence (MMCI) & Simons Institute for the Theory of Computing 1 50 Shades of Fine-Grained #W[1] W[1] fixed-parameter
Fine Grained Counting Complexity I Holger Dell Saarland University and Cluster of Excellence (MMCI) & Simons Institute for the Theory of Computing 1 50 Shades of Fine-Grained #W[1] W[1] fixed-parameter
Homework 1 Solutions ECEn 670, Fall 2013
 Homework Solutions ECEn 670, Fall 03 A.. Use the rst seven relations to prove relations (A.0, (A.3, and (A.6. Prove (F G c F c G c (A.0. (F G c ((F c G c c c by A.6. (F G c F c G c by A.4 Prove F (F G
Homework Solutions ECEn 670, Fall 03 A.. Use the rst seven relations to prove relations (A.0, (A.3, and (A.6. Prove (F G c F c G c (A.0. (F G c ((F c G c c c by A.6. (F G c F c G c by A.4 Prove F (F G
Combinatorial Optimisation, Problems I, Solutions Term /2015
 /0/205 Combinatorial Optimisation, Problems I, Solutions Term 2 204/205 Tomasz Tkocz, t (dot) tkocz (at) warwick (dot) ac (dot) uk 3. By Problem 2, any tree which is not a single vertex has at least 2
/0/205 Combinatorial Optimisation, Problems I, Solutions Term 2 204/205 Tomasz Tkocz, t (dot) tkocz (at) warwick (dot) ac (dot) uk 3. By Problem 2, any tree which is not a single vertex has at least 2
Lecture 15: Expanders
 CS 710: Complexity Theory 10/7/011 Lecture 15: Expanders Instructor: Dieter van Melkebeek Scribe: Li-Hsiang Kuo In the last lecture we introduced randomized computation in terms of machines that have access
CS 710: Complexity Theory 10/7/011 Lecture 15: Expanders Instructor: Dieter van Melkebeek Scribe: Li-Hsiang Kuo In the last lecture we introduced randomized computation in terms of machines that have access
Probability & Computing
 Probability & Computing Stochastic Process time t {X t t 2 T } state space Ω X t 2 state x 2 discrete time: T is countable T = {0,, 2,...} discrete space: Ω is finite or countably infinite X 0,X,X 2,...
Probability & Computing Stochastic Process time t {X t t 2 T } state space Ω X t 2 state x 2 discrete time: T is countable T = {0,, 2,...} discrete space: Ω is finite or countably infinite X 0,X,X 2,...
A note on the Isomorphism Problem for Monomial Digraphs
 A note on the Isomorphism Problem for Monomial Digraphs Aleksandr Kodess Department of Mathematics University of Rhode Island kodess@uri.edu Felix Lazebnik Department of Mathematical Sciences University
A note on the Isomorphism Problem for Monomial Digraphs Aleksandr Kodess Department of Mathematics University of Rhode Island kodess@uri.edu Felix Lazebnik Department of Mathematical Sciences University
Approximation Algorithms for the k-set Packing Problem
 Approximation Algorithms for the k-set Packing Problem Marek Cygan Institute of Informatics University of Warsaw 20th October 2016, Warszawa Marek Cygan Approximation Algorithms for the k-set Packing Problem
Approximation Algorithms for the k-set Packing Problem Marek Cygan Institute of Informatics University of Warsaw 20th October 2016, Warszawa Marek Cygan Approximation Algorithms for the k-set Packing Problem
Problem Set 2. Assigned: Mon. November. 23, 2015
 Pseudorandomness Prof. Salil Vadhan Problem Set 2 Assigned: Mon. November. 23, 2015 Chi-Ning Chou Index Problem Progress 1 SchwartzZippel lemma 1/1 2 Robustness of the model 1/1 3 Zero error versus 1-sided
Pseudorandomness Prof. Salil Vadhan Problem Set 2 Assigned: Mon. November. 23, 2015 Chi-Ning Chou Index Problem Progress 1 SchwartzZippel lemma 1/1 2 Robustness of the model 1/1 3 Zero error versus 1-sided
Analysis on Graphs. Alexander Grigoryan Lecture Notes. University of Bielefeld, WS 2011/12
 Analysis on Graphs Alexander Grigoryan Lecture Notes University of Bielefeld, WS 0/ Contents The Laplace operator on graphs 5. The notion of a graph............................. 5. Cayley graphs..................................
Analysis on Graphs Alexander Grigoryan Lecture Notes University of Bielefeld, WS 0/ Contents The Laplace operator on graphs 5. The notion of a graph............................. 5. Cayley graphs..................................
Name (print): Question 4. exercise 1.24 (compute the union, then the intersection of two sets)
 MTH299 - Homework 1 Question 1. exercise 1.10 (compute the cardinality of a handful of finite sets) Solution. Write your answer here. Question 2. exercise 1.20 (compute the union of two sets) Question
MTH299 - Homework 1 Question 1. exercise 1.10 (compute the cardinality of a handful of finite sets) Solution. Write your answer here. Question 2. exercise 1.20 (compute the union of two sets) Question
Essentials of Intermediate Algebra
 Essentials of Intermediate Algebra BY Tom K. Kim, Ph.D. Peninsula College, WA Randy Anderson, M.S. Peninsula College, WA 9/24/2012 Contents 1 Review 1 2 Rules of Exponents 2 2.1 Multiplying Two Exponentials
Essentials of Intermediate Algebra BY Tom K. Kim, Ph.D. Peninsula College, WA Randy Anderson, M.S. Peninsula College, WA 9/24/2012 Contents 1 Review 1 2 Rules of Exponents 2 2.1 Multiplying Two Exponentials
(K2) For sum of the potential differences around any cycle is equal to zero. r uv resistance of {u, v}. [In other words, V ir.]
![(K2) For sum of the potential differences around any cycle is equal to zero. r uv resistance of {u, v}. [In other words, V ir.] (K2) For sum of the potential differences around any cycle is equal to zero. r uv resistance of {u, v}. [In other words, V ir.]](/thumbs/88/116126474.jpg) Lectures 16-17: Random walks on graphs CSE 525, Winter 2015 Instructor: James R. Lee 1 Random walks Let G V, E) be an undirected graph. The random walk on G is a Markov chain on V that, at each time step,
Lectures 16-17: Random walks on graphs CSE 525, Winter 2015 Instructor: James R. Lee 1 Random walks Let G V, E) be an undirected graph. The random walk on G is a Markov chain on V that, at each time step,
Lecture 10. Sublinear Time Algorithms (contd) CSC2420 Allan Borodin & Nisarg Shah 1
 Lecture 10 Sublinear Time Algorithms (contd) CSC2420 Allan Borodin & Nisarg Shah 1 Recap Sublinear time algorithms Deterministic + exact: binary search Deterministic + inexact: estimating diameter in a
Lecture 10 Sublinear Time Algorithms (contd) CSC2420 Allan Borodin & Nisarg Shah 1 Recap Sublinear time algorithms Deterministic + exact: binary search Deterministic + inexact: estimating diameter in a
Lecture 24 Nov. 20, 2014
 CS 224: Advanced Algorithms Fall 2014 Prof. Jelani Nelson Lecture 24 Nov. 20, 2014 Scribe: Xiaoyu He Overview Today we will move to a new topic: another way to deal with NP-hard problems. We have already
CS 224: Advanced Algorithms Fall 2014 Prof. Jelani Nelson Lecture 24 Nov. 20, 2014 Scribe: Xiaoyu He Overview Today we will move to a new topic: another way to deal with NP-hard problems. We have already
Representative Sets of Product Families
 Representative Sets of Product Families Fedor V. Fomin Daniel Lokshtanov Fahad Panolan Saket Saurabh Abstract A subfamily F of a set family F is said to q-represent F if for every A F and B of size q such
Representative Sets of Product Families Fedor V. Fomin Daniel Lokshtanov Fahad Panolan Saket Saurabh Abstract A subfamily F of a set family F is said to q-represent F if for every A F and B of size q such
Chapter 1 : The language of mathematics.
 MAT 200, Logic, Language and Proof, Fall 2015 Summary Chapter 1 : The language of mathematics. Definition. A proposition is a sentence which is either true or false. Truth table for the connective or :
MAT 200, Logic, Language and Proof, Fall 2015 Summary Chapter 1 : The language of mathematics. Definition. A proposition is a sentence which is either true or false. Truth table for the connective or :
Lecture 14 - P v.s. NP 1
 CME 305: Discrete Mathematics and Algorithms Instructor: Professor Aaron Sidford (sidford@stanford.edu) February 27, 2018 Lecture 14 - P v.s. NP 1 In this lecture we start Unit 3 on NP-hardness and approximation
CME 305: Discrete Mathematics and Algorithms Instructor: Professor Aaron Sidford (sidford@stanford.edu) February 27, 2018 Lecture 14 - P v.s. NP 1 In this lecture we start Unit 3 on NP-hardness and approximation
1. Decide for each of the following expressions: Is it a function? If so, f is a function. (i) Domain: R. Codomain: R. Range: R. (iii) Yes surjective.
 Homework 2 2/14/2018 SOLUTIONS Exercise 6. 1. Decide for each of the following expressions: Is it a function? If so, (i) what is its domain, codomain, and image? (iii) is it surjective? (ii) is it injective?
Homework 2 2/14/2018 SOLUTIONS Exercise 6. 1. Decide for each of the following expressions: Is it a function? If so, (i) what is its domain, codomain, and image? (iii) is it surjective? (ii) is it injective?
ZEROS OF SPARSE POLYNOMIALS OVER LOCAL FIELDS OF CHARACTERISTIC p
 ZEROS OF SPARSE POLYNOMIALS OVER LOCAL FIELDS OF CHARACTERISTIC p BJORN POONEN 1. Statement of results Let K be a field of characteristic p > 0 equipped with a valuation v : K G taking values in an ordered
ZEROS OF SPARSE POLYNOMIALS OVER LOCAL FIELDS OF CHARACTERISTIC p BJORN POONEN 1. Statement of results Let K be a field of characteristic p > 0 equipped with a valuation v : K G taking values in an ordered
Functions If (x, y 1 ), (x, y 2 ) S, then y 1 = y 2
 Functions 4-3-2008 Definition. A function f from a set X to a set Y is a subset S of the product X Y such that if (, y 1 ), (, y 2 ) S, then y 1 = y 2. Instead of writing (, y) S, you usually write f()
Functions 4-3-2008 Definition. A function f from a set X to a set Y is a subset S of the product X Y such that if (, y 1 ), (, y 2 ) S, then y 1 = y 2. Instead of writing (, y) S, you usually write f()
The Bipartite Swapping Trick on Graph Homomorphisms
 The Bipartite Swapping Trick on Graph Homomorphisms Yufei Zhao Massachusetts Institute of Technology yufei.zhao@gmail.com June 11, 2011 Abstract We provide an upper bound to the number of graph homomorphisms
The Bipartite Swapping Trick on Graph Homomorphisms Yufei Zhao Massachusetts Institute of Technology yufei.zhao@gmail.com June 11, 2011 Abstract We provide an upper bound to the number of graph homomorphisms
NEW CLASSES OF SET-THEORETIC COMPLETE INTERSECTION MONOMIAL IDEALS
 NEW CLASSES OF SET-THEORETIC COMPLETE INTERSECTION MONOMIAL IDEALS M. R. POURNAKI, S. A. SEYED FAKHARI, AND S. YASSEMI Abstract. Let be a simplicial complex and χ be an s-coloring of. Biermann and Van
NEW CLASSES OF SET-THEORETIC COMPLETE INTERSECTION MONOMIAL IDEALS M. R. POURNAKI, S. A. SEYED FAKHARI, AND S. YASSEMI Abstract. Let be a simplicial complex and χ be an s-coloring of. Biermann and Van
Deterministic APSP, Orthogonal Vectors, and More:
 Deterministic APSP, Orthogonal Vectors, and More: Quickly Derandomizing Razborov Smolensky Timothy Chan U of Waterloo Ryan Williams Stanford Problem 1: All-Pairs Shortest Paths (APSP) Given real-weighted
Deterministic APSP, Orthogonal Vectors, and More: Quickly Derandomizing Razborov Smolensky Timothy Chan U of Waterloo Ryan Williams Stanford Problem 1: All-Pairs Shortest Paths (APSP) Given real-weighted
Observation 4.1 G has a proper separation of order 0 if and only if G is disconnected.
 4 Connectivity 2-connectivity Separation: A separation of G of order k is a pair of subgraphs (H 1, H 2 ) so that H 1 H 2 = G E(H 1 ) E(H 2 ) = V (H 1 ) V (H 2 ) = k Such a separation is proper if V (H
4 Connectivity 2-connectivity Separation: A separation of G of order k is a pair of subgraphs (H 1, H 2 ) so that H 1 H 2 = G E(H 1 ) E(H 2 ) = V (H 1 ) V (H 2 ) = k Such a separation is proper if V (H
University of Chicago Autumn 2003 CS Markov Chain Monte Carlo Methods
 University of Chicago Autumn 2003 CS37101-1 Markov Chain Monte Carlo Methods Lecture 4: October 21, 2003 Bounding the mixing time via coupling Eric Vigoda 4.1 Introduction In this lecture we ll use the
University of Chicago Autumn 2003 CS37101-1 Markov Chain Monte Carlo Methods Lecture 4: October 21, 2003 Bounding the mixing time via coupling Eric Vigoda 4.1 Introduction In this lecture we ll use the
9. Integral Ring Extensions
 80 Andreas Gathmann 9. Integral ing Extensions In this chapter we want to discuss a concept in commutative algebra that has its original motivation in algebra, but turns out to have surprisingly many applications
80 Andreas Gathmann 9. Integral ing Extensions In this chapter we want to discuss a concept in commutative algebra that has its original motivation in algebra, but turns out to have surprisingly many applications
Randomized Algorithms
 Randomized Algorithms Prof. Tapio Elomaa tapio.elomaa@tut.fi Course Basics A new 4 credit unit course Part of Theoretical Computer Science courses at the Department of Mathematics There will be 4 hours
Randomized Algorithms Prof. Tapio Elomaa tapio.elomaa@tut.fi Course Basics A new 4 credit unit course Part of Theoretical Computer Science courses at the Department of Mathematics There will be 4 hours
15-251: Great Theoretical Ideas In Computer Science Recitation 9 : Randomized Algorithms and Communication Complexity Solutions
 15-251: Great Theoretical Ideas In Computer Science Recitation 9 : Randomized Algorithms and Communication Complexity Solutions Definitions We say a (deterministic) protocol P computes f if (x, y) {0,
15-251: Great Theoretical Ideas In Computer Science Recitation 9 : Randomized Algorithms and Communication Complexity Solutions Definitions We say a (deterministic) protocol P computes f if (x, y) {0,
Siegel s theorem, edge coloring, and a holant dichotomy
 Siegel s theorem, edge coloring, and a holant dichotomy Tyson Williams (University of Wisconsin-Madison) Joint with: Jin-Yi Cai and Heng Guo (University of Wisconsin-Madison) Appeared at FOCS 2014 1 /
Siegel s theorem, edge coloring, and a holant dichotomy Tyson Williams (University of Wisconsin-Madison) Joint with: Jin-Yi Cai and Heng Guo (University of Wisconsin-Madison) Appeared at FOCS 2014 1 /
The Markov Chain Monte Carlo Method
 The Markov Chain Monte Carlo Method Idea: define an ergodic Markov chain whose stationary distribution is the desired probability distribution. Let X 0, X 1, X 2,..., X n be the run of the chain. The Markov
The Markov Chain Monte Carlo Method Idea: define an ergodic Markov chain whose stationary distribution is the desired probability distribution. Let X 0, X 1, X 2,..., X n be the run of the chain. The Markov
Random Walks on graphs
 November 2007 UW Probability Seminar 1 Random Walks on graphs Random walk on G: Simple to analyze: satisfying some natural properties Mixes quickly to stationary distribution. efficient sampling of the
November 2007 UW Probability Seminar 1 Random Walks on graphs Random walk on G: Simple to analyze: satisfying some natural properties Mixes quickly to stationary distribution. efficient sampling of the
Randomness. What next?
 Randomness What next? Random Walk Attribution These slides were prepared for the New Jersey Governor s School course The Math Behind the Machine taught in the summer of 2012 by Grant Schoenebeck Large
Randomness What next? Random Walk Attribution These slides were prepared for the New Jersey Governor s School course The Math Behind the Machine taught in the summer of 2012 by Grant Schoenebeck Large
Circuit depth relative to a random oracle. Peter Bro Miltersen. Aarhus University, Computer Science Department
 Circuit depth relative to a random oracle Peter Bro Miltersen Aarhus University, Computer Science Department Ny Munkegade, DK 8000 Aarhus C, Denmark. pbmiltersen@daimi.aau.dk Keywords: Computational complexity,
Circuit depth relative to a random oracle Peter Bro Miltersen Aarhus University, Computer Science Department Ny Munkegade, DK 8000 Aarhus C, Denmark. pbmiltersen@daimi.aau.dk Keywords: Computational complexity,
(1) Which of the following are propositions? If it is a proposition, determine its truth value: A propositional function, but not a proposition.
 Math 231 Exam Practice Problem Solutions WARNING: This is not a sample test. Problems on the exams may or may not be similar to these problems. These problems are just intended to focus your study of the
Math 231 Exam Practice Problem Solutions WARNING: This is not a sample test. Problems on the exams may or may not be similar to these problems. These problems are just intended to focus your study of the
Strongly chordal and chordal bipartite graphs are sandwich monotone
 Strongly chordal and chordal bipartite graphs are sandwich monotone Pinar Heggernes Federico Mancini Charis Papadopoulos R. Sritharan Abstract A graph class is sandwich monotone if, for every pair of its
Strongly chordal and chordal bipartite graphs are sandwich monotone Pinar Heggernes Federico Mancini Charis Papadopoulos R. Sritharan Abstract A graph class is sandwich monotone if, for every pair of its
MATH 2200 Final Review
 MATH 00 Final Review Thomas Goller December 7, 01 1 Exam Format The final exam will consist of 8-10 proofs It will take place on Tuesday, December 11, from 10:30 AM - 1:30 PM, in the usual room Topics
MATH 00 Final Review Thomas Goller December 7, 01 1 Exam Format The final exam will consist of 8-10 proofs It will take place on Tuesday, December 11, from 10:30 AM - 1:30 PM, in the usual room Topics
Classes of Problems. CS 461, Lecture 23. NP-Hard. Today s Outline. We can characterize many problems into three classes:
 Classes of Problems We can characterize many problems into three classes: CS 461, Lecture 23 Jared Saia University of New Mexico P is the set of yes/no problems that can be solved in polynomial time. Intuitively
Classes of Problems We can characterize many problems into three classes: CS 461, Lecture 23 Jared Saia University of New Mexico P is the set of yes/no problems that can be solved in polynomial time. Intuitively
Mathematical Induction
 Mathematical Induction Let s motivate our discussion by considering an example first. What happens when we add the first n positive odd integers? The table below shows what results for the first few values
Mathematical Induction Let s motivate our discussion by considering an example first. What happens when we add the first n positive odd integers? The table below shows what results for the first few values
Holger Dell Saarland University and Cluster of Excellence (MMCI) Simons Institute for the Theory of Computing
 Fine-Grained Complexity Classification of Counting Problems Holger Dell Saarland University and Cluster of Excellence (MMCI) Simons Institute for the Theory of Computing 1 In P or not in P? Exact counting
Fine-Grained Complexity Classification of Counting Problems Holger Dell Saarland University and Cluster of Excellence (MMCI) Simons Institute for the Theory of Computing 1 In P or not in P? Exact counting
Lecture 8 - Algebraic Methods for Matching 1
 CME 305: Discrete Mathematics and Algorithms Instructor: Professor Aaron Sidford (sidford@stanford.edu) February 1, 2018 Lecture 8 - Algebraic Methods for Matching 1 In the last lecture we showed that
CME 305: Discrete Mathematics and Algorithms Instructor: Professor Aaron Sidford (sidford@stanford.edu) February 1, 2018 Lecture 8 - Algebraic Methods for Matching 1 In the last lecture we showed that
Exponential-Time Approximation of Weighted Set Cover
 Exponential-Time Approximation of Weighted Set Cover Marek Cygan, Lukasz Kowalik and Mateusz Wykurz Institute of Informatics, University of Warsaw, Poland. cygan@mimuw.edu.pl, kowalik@mimuw.edu.pl, wykurz@gmail.com.
Exponential-Time Approximation of Weighted Set Cover Marek Cygan, Lukasz Kowalik and Mateusz Wykurz Institute of Informatics, University of Warsaw, Poland. cygan@mimuw.edu.pl, kowalik@mimuw.edu.pl, wykurz@gmail.com.
Counting Strategies: Inclusion-Exclusion, Categories
 Counting Strategies: Inclusion-Exclusion, Categories Russell Impagliazzo and Miles Jones Thanks to Janine Tiefenbruck http://cseweb.ucsd.edu/classes/sp16/cse21-bd/ May 4, 2016 A scheduling problem In one
Counting Strategies: Inclusion-Exclusion, Categories Russell Impagliazzo and Miles Jones Thanks to Janine Tiefenbruck http://cseweb.ucsd.edu/classes/sp16/cse21-bd/ May 4, 2016 A scheduling problem In one
MATH 829: Introduction to Data Mining and Analysis Graphical Models I
 MATH 829: Introduction to Data Mining and Analysis Graphical Models I Dominique Guillot Departments of Mathematical Sciences University of Delaware May 2, 2016 1/12 Independence and conditional independence:
MATH 829: Introduction to Data Mining and Analysis Graphical Models I Dominique Guillot Departments of Mathematical Sciences University of Delaware May 2, 2016 1/12 Independence and conditional independence:
Binomial Ideals from Graphs
 Binomial Ideals from Graphs Danielle Farrar University of Washington Yolanda Manzano St. Mary s University Juan Manuel Torres-Acevedo University of Puerto Rico Humacao August 10, 2000 Abstract This paper
Binomial Ideals from Graphs Danielle Farrar University of Washington Yolanda Manzano St. Mary s University Juan Manuel Torres-Acevedo University of Puerto Rico Humacao August 10, 2000 Abstract This paper
Algebraic Fingerprints for faster algorithms
 Algebraic Fingerprints for faster algorithms Ioannis Koutis Computer Science Dept. U of Puerto Rico-Rio Piedras ioannis.koutis@upr.edu Ryan Williams Computer Science Dept. Stanford University rrw@cs.stanford.edu
Algebraic Fingerprints for faster algorithms Ioannis Koutis Computer Science Dept. U of Puerto Rico-Rio Piedras ioannis.koutis@upr.edu Ryan Williams Computer Science Dept. Stanford University rrw@cs.stanford.edu
Notes for Math 290 using Introduction to Mathematical Proofs by Charles E. Roberts, Jr.
 Notes for Math 290 using Introduction to Mathematical Proofs by Charles E. Roberts, Jr. Chapter : Logic Topics:. Statements, Negation, and Compound Statements.2 Truth Tables and Logical Equivalences.3
Notes for Math 290 using Introduction to Mathematical Proofs by Charles E. Roberts, Jr. Chapter : Logic Topics:. Statements, Negation, and Compound Statements.2 Truth Tables and Logical Equivalences.3
Linear Algebra, 4th day, Thursday 7/1/04 REU Info:
 Linear Algebra, 4th day, Thursday 7/1/04 REU 004. Info http//people.cs.uchicago.edu/laci/reu04. Instructor Laszlo Babai Scribe Nick Gurski 1 Linear maps We shall study the notion of maps between vector
Linear Algebra, 4th day, Thursday 7/1/04 REU 004. Info http//people.cs.uchicago.edu/laci/reu04. Instructor Laszlo Babai Scribe Nick Gurski 1 Linear maps We shall study the notion of maps between vector
Algebraic function fields
 Algebraic function fields 1 Places Definition An algebraic function field F/K of one variable over K is an extension field F K such that F is a finite algebraic extension of K(x) for some element x F which
Algebraic function fields 1 Places Definition An algebraic function field F/K of one variable over K is an extension field F K such that F is a finite algebraic extension of K(x) for some element x F which
NP-Hardness reductions
 NP-Hardness reductions Definition: P is the class of problems that can be solved in polynomial time, that is n c for a constant c Roughly, if a problem is in P then it's easy, and if it's not in P then
NP-Hardness reductions Definition: P is the class of problems that can be solved in polynomial time, that is n c for a constant c Roughly, if a problem is in P then it's easy, and if it's not in P then
Admin NP-COMPLETE PROBLEMS. Run-time analysis. Tractable vs. intractable problems 5/2/13. What is a tractable problem?
 Admin Two more assignments No office hours on tomorrow NP-COMPLETE PROBLEMS Run-time analysis Tractable vs. intractable problems We ve spent a lot of time in this class putting algorithms into specific
Admin Two more assignments No office hours on tomorrow NP-COMPLETE PROBLEMS Run-time analysis Tractable vs. intractable problems We ve spent a lot of time in this class putting algorithms into specific
The complexity of acyclic subhypergraph problems
 The complexity of acyclic subhypergraph problems David Duris and Yann Strozecki Équipe de Logique Mathématique (FRE 3233) - Université Paris Diderot-Paris 7 {duris,strozecki}@logique.jussieu.fr Abstract.
The complexity of acyclic subhypergraph problems David Duris and Yann Strozecki Équipe de Logique Mathématique (FRE 3233) - Université Paris Diderot-Paris 7 {duris,strozecki}@logique.jussieu.fr Abstract.
Chain Minors are FPT. B Marcin Kamiński. 1 Introduction. Jarosław Błasiok 1 Marcin Kamiński 1
 Algorithmica (2017) 79:698 707 DOI 10.1007/s00453-016-0220-1 Chain Minors are FPT Jarosław Błasiok 1 Marcin Kamiński 1 Received: 21 March 2014 / Accepted: 21 September 2016 / Published online: 20 October
Algorithmica (2017) 79:698 707 DOI 10.1007/s00453-016-0220-1 Chain Minors are FPT Jarosław Błasiok 1 Marcin Kamiński 1 Received: 21 March 2014 / Accepted: 21 September 2016 / Published online: 20 October
NP-Complete problems
 NP-Complete problems NP-complete problems (NPC): A subset of NP. If any NP-complete problem can be solved in polynomial time, then every problem in NP has a polynomial time solution. NP-complete languages
NP-Complete problems NP-complete problems (NPC): A subset of NP. If any NP-complete problem can be solved in polynomial time, then every problem in NP has a polynomial time solution. NP-complete languages
4.1 Notation and probability review
 Directed and undirected graphical models Fall 2015 Lecture 4 October 21st Lecturer: Simon Lacoste-Julien Scribe: Jaime Roquero, JieYing Wu 4.1 Notation and probability review 4.1.1 Notations Let us recall
Directed and undirected graphical models Fall 2015 Lecture 4 October 21st Lecturer: Simon Lacoste-Julien Scribe: Jaime Roquero, JieYing Wu 4.1 Notation and probability review 4.1.1 Notations Let us recall
Chapter 1 Divide and Conquer Algorithm Theory WS 2016/17 Fabian Kuhn
 Chapter 1 Divide and Conquer Algorithm Theory WS 2016/17 Fabian Kuhn Formulation of the D&C principle Divide-and-conquer method for solving a problem instance of size n: 1. Divide n c: Solve the problem
Chapter 1 Divide and Conquer Algorithm Theory WS 2016/17 Fabian Kuhn Formulation of the D&C principle Divide-and-conquer method for solving a problem instance of size n: 1. Divide n c: Solve the problem
Symbolic Variable Elimination in Discrete and Continuous Graphical Models. Scott Sanner Ehsan Abbasnejad
 Symbolic Variable Elimination in Discrete and Continuous Graphical Models Scott Sanner Ehsan Abbasnejad Inference for Dynamic Tracking No one previously did this inference exactly in closed-form! Exact
Symbolic Variable Elimination in Discrete and Continuous Graphical Models Scott Sanner Ehsan Abbasnejad Inference for Dynamic Tracking No one previously did this inference exactly in closed-form! Exact
On the rank of Directed Hamiltonicity and beyond
 Utrecht University Faculty of Science Department of Information and Computing Sciences On the rank of Directed Hamiltonicity and beyond Author: Ioannis Katsikarelis Supervisors: Dr. Hans L. Bodlaender
Utrecht University Faculty of Science Department of Information and Computing Sciences On the rank of Directed Hamiltonicity and beyond Author: Ioannis Katsikarelis Supervisors: Dr. Hans L. Bodlaender
Observation 4.1 G has a proper separation of order 0 if and only if G is disconnected.
 4 Connectivity 2-connectivity Separation: A separation of G of order k is a pair of subgraphs (H, K) with H K = G and E(H K) = and V (H) V (K) = k. Such a separation is proper if V (H) \ V (K) and V (K)
4 Connectivity 2-connectivity Separation: A separation of G of order k is a pair of subgraphs (H, K) with H K = G and E(H K) = and V (H) V (K) = k. Such a separation is proper if V (H) \ V (K) and V (K)
Dynamic Programming on Trees. Example: Independent Set on T = (V, E) rooted at r V.
 Dynamic Programming on Trees Example: Independent Set on T = (V, E) rooted at r V. For v V let T v denote the subtree rooted at v. Let f + (v) be the size of a maximum independent set for T v that contains
Dynamic Programming on Trees Example: Independent Set on T = (V, E) rooted at r V. For v V let T v denote the subtree rooted at v. Let f + (v) be the size of a maximum independent set for T v that contains
ANALYSIS I. (i) For every ordered pair of real numbers a, b we can associate a third one written a + b called their sum
 1 The real number system 1.1 What are the reals? ANALYSIS I What are the real numbers? For the moment this is too hard a question! We can give various answers, but for the moment we prefer just to agree
1 The real number system 1.1 What are the reals? ANALYSIS I What are the real numbers? For the moment this is too hard a question! We can give various answers, but for the moment we prefer just to agree
5 Banach Algebras. 5.1 Invertibility and the Spectrum. Robert Oeckl FA NOTES 5 19/05/2010 1
 Robert Oeckl FA NOTES 5 19/05/2010 1 5 Banach Algebras 5.1 Invertibility and the Spectrum Suppose X is a Banach space. Then we are often interested in (continuous) operators on this space, i.e, elements
Robert Oeckl FA NOTES 5 19/05/2010 1 5 Banach Algebras 5.1 Invertibility and the Spectrum Suppose X is a Banach space. Then we are often interested in (continuous) operators on this space, i.e, elements
C -algebras generated by mappings with an inverse semigroup of monomials
 C -algebras generated by mappings with an inverse semigroup of monomials A. Kuznetsova Kazan Federal University 09.09.2016 C -algebra generated by mapping The starting point is a selfmapping ϕ : X X on
C -algebras generated by mappings with an inverse semigroup of monomials A. Kuznetsova Kazan Federal University 09.09.2016 C -algebra generated by mapping The starting point is a selfmapping ϕ : X X on
k-degenerate Graphs Allan Bickle Date Western Michigan University
 k-degenerate Graphs Western Michigan University Date Basics Denition The k-core of a graph G is the maximal induced subgraph H G such that δ (H) k. The core number of a vertex, C (v), is the largest value
k-degenerate Graphs Western Michigan University Date Basics Denition The k-core of a graph G is the maximal induced subgraph H G such that δ (H) k. The core number of a vertex, C (v), is the largest value
17 Galois Fields Introduction Primitive Elements Roots of Polynomials... 8
 Contents 17 Galois Fields 2 17.1 Introduction............................... 2 17.2 Irreducible Polynomials, Construction of GF(q m )... 3 17.3 Primitive Elements... 6 17.4 Roots of Polynomials..........................
Contents 17 Galois Fields 2 17.1 Introduction............................... 2 17.2 Irreducible Polynomials, Construction of GF(q m )... 3 17.3 Primitive Elements... 6 17.4 Roots of Polynomials..........................
7.1 Coupling from the Past
 Georgia Tech Fall 2006 Markov Chain Monte Carlo Methods Lecture 7: September 12, 2006 Coupling from the Past Eric Vigoda 7.1 Coupling from the Past 7.1.1 Introduction We saw in the last lecture how Markov
Georgia Tech Fall 2006 Markov Chain Monte Carlo Methods Lecture 7: September 12, 2006 Coupling from the Past Eric Vigoda 7.1 Coupling from the Past 7.1.1 Introduction We saw in the last lecture how Markov
Order of Operations. Real numbers
 Order of Operations When simplifying algebraic expressions we use the following order: 1. Perform operations within a parenthesis. 2. Evaluate exponents. 3. Multiply and divide from left to right. 4. Add
Order of Operations When simplifying algebraic expressions we use the following order: 1. Perform operations within a parenthesis. 2. Evaluate exponents. 3. Multiply and divide from left to right. 4. Add
2-Distance Problems. Combinatorics, 2016 Fall, USTC Week 16, Dec 20&22. Theorem 1. (Frankl-Wilson, 1981) If F is an L-intersecting family in 2 [n],
![2-Distance Problems. Combinatorics, 2016 Fall, USTC Week 16, Dec 20&22. Theorem 1. (Frankl-Wilson, 1981) If F is an L-intersecting family in 2 [n], 2-Distance Problems. Combinatorics, 2016 Fall, USTC Week 16, Dec 20&22. Theorem 1. (Frankl-Wilson, 1981) If F is an L-intersecting family in 2 [n],](/thumbs/94/121628976.jpg) Combinatorics, 206 Fall, USTC Week 6, Dec 20&22 2-Distance Problems Theorem (Frankl-Wilson, 98 If F is an L-intersecting family in 2 [n], then F L k=0 ( n k Proof Let F = {A, A 2,, A m } where A A 2 A
Combinatorics, 206 Fall, USTC Week 6, Dec 20&22 2-Distance Problems Theorem (Frankl-Wilson, 98 If F is an L-intersecting family in 2 [n], then F L k=0 ( n k Proof Let F = {A, A 2,, A m } where A A 2 A
4.1 Real-valued functions of a real variable
 Chapter 4 Functions When introducing relations from a set A to a set B we drew an analogy with co-ordinates in the x-y plane. Instead of coming from R, the first component of an ordered pair comes from
Chapter 4 Functions When introducing relations from a set A to a set B we drew an analogy with co-ordinates in the x-y plane. Instead of coming from R, the first component of an ordered pair comes from
Cardinality of sets. Cardinality of sets
 Cardinality of sets Two sets A and B have the same size, or cardinality, if and only if there is a bijection f : A Ñ B. Example: We know that set ta, b, cu has elements because we can count them: 1: a
Cardinality of sets Two sets A and B have the same size, or cardinality, if and only if there is a bijection f : A Ñ B. Example: We know that set ta, b, cu has elements because we can count them: 1: a
Restricted b-matchings in degree-bounded graphs
 Egerváry Research Group on Combinatorial Optimization Technical reports TR-009-1. Published by the Egerváry Research Group, Pázmány P. sétány 1/C, H1117, Budapest, Hungary. Web site: www.cs.elte.hu/egres.
Egerváry Research Group on Combinatorial Optimization Technical reports TR-009-1. Published by the Egerváry Research Group, Pázmány P. sétány 1/C, H1117, Budapest, Hungary. Web site: www.cs.elte.hu/egres.
1 Randomized Computation
 CS 6743 Lecture 17 1 Fall 2007 1 Randomized Computation Why is randomness useful? Imagine you have a stack of bank notes, with very few counterfeit ones. You want to choose a genuine bank note to pay at
CS 6743 Lecture 17 1 Fall 2007 1 Randomized Computation Why is randomness useful? Imagine you have a stack of bank notes, with very few counterfeit ones. You want to choose a genuine bank note to pay at
MATH 3300 Test 1. Name: Student Id:
 Name: Student Id: There are nine problems (check that you have 9 pages). Solutions are expected to be short. In the case of proofs, one or two short paragraphs should be the average length. Write your
Name: Student Id: There are nine problems (check that you have 9 pages). Solutions are expected to be short. In the case of proofs, one or two short paragraphs should be the average length. Write your
Topics on Computing and Mathematical Sciences I Graph Theory (6) Coloring I
 Topics on Computing and Mathematical Sciences I Graph Theory (6) Coloring I Yoshio Okamoto Tokyo Institute of Technology May, 008 Last updated: Wed May 6: 008 Y. Okamoto (Tokyo Tech) TCMSI Graph Theory
Topics on Computing and Mathematical Sciences I Graph Theory (6) Coloring I Yoshio Okamoto Tokyo Institute of Technology May, 008 Last updated: Wed May 6: 008 Y. Okamoto (Tokyo Tech) TCMSI Graph Theory
1 Adjacency matrix and eigenvalues
 CSC 5170: Theory of Computational Complexity Lecture 7 The Chinese University of Hong Kong 1 March 2010 Our objective of study today is the random walk algorithm for deciding if two vertices in an undirected
CSC 5170: Theory of Computational Complexity Lecture 7 The Chinese University of Hong Kong 1 March 2010 Our objective of study today is the random walk algorithm for deciding if two vertices in an undirected
Discrete Mathematics Fall 2018 Midterm Exam Prof. Callahan. Section: NetID: Multiple Choice Question (30 questions in total, 4 points each)
 Discrete Mathematics Fall 2018 Midterm Exam Prof. Callahan Section: NetID: Name: Multiple Choice Question (30 questions in total, 4 points each) 1 Consider the following propositions: f: The student got
Discrete Mathematics Fall 2018 Midterm Exam Prof. Callahan Section: NetID: Name: Multiple Choice Question (30 questions in total, 4 points each) 1 Consider the following propositions: f: The student got
Limits of Functions (a, L)
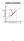 Limits of Functions f(x) (a, L) L f(x) x a x x 20 Informal Definition: If the values of can be made as close to as we like by taking values of sufficiently close to [but not equal to ] then we write or
Limits of Functions f(x) (a, L) L f(x) x a x x 20 Informal Definition: If the values of can be made as close to as we like by taking values of sufficiently close to [but not equal to ] then we write or
