This research was partially supported by the Faculty Research and Development Fund of the University of North Carolina at Wilmington
|
|
|
- Kristina Welch
- 5 years ago
- Views:
Transcription
1 LARGE SCALE GEOMETRIC PROGRAMMING: AN APPLICATION IN CODING THEORY Yaw O. Chang and John K. Karlof Mathematical Sciences Department The University of North Carolina at Wilmington This research was partially supported by the Faculty Research and Development Fund of the University of North Carolina at Wilmington
2 SCOPE AND PURPOSE Geometric programming is an optimization technique originally developed for solving a class of nonlinear optimization problems found in engineering and design. Previous applications have generally been small scale and highly nonlinear. In a geometric programming problem all the constraints as well as the objective function are posynomials. The Gaussian channel is a communications model in which messages are represented by vectors in R n. The transmitter has a finite set of messages available and these messages are transmitted over a noisy channel to a receiver. The received message equals the sent vector perturbed by a Gaussian noise vector. The receiver must decide which of the messages was sent. We use groups of orthogonal matrices to generate the message set and the result is called a group code. The problem of finding the best code generated by a particular group is called the initial vector problem. Previous attempts to find a general solution to this problem have been unsuccessful. Although, it has been solved in several special cases. We write this problem as a nonlinear programming problem, transform it to a generalized geometric programming problem, and use the double condensation technique developed by Avriel, Dembo, and Passy and modified by Burns to develop an algorithm for its solution. We apply this algorithm to groups in which the resulting initial vector problem has close to 50,000 constraints. 2
3 ABSTRACT An algorithm is presented that solves the initial vector problem for group codes for the Gaussian channel. The Gaussian channel is a communications model in which messages are represented by vectors in R n and transmitted over a noisy channel. In this paper, the set of messages, called a code, is generated by a group of permutation matrices and the problem of finding the code with the largest minimum distance between codewords for a particular permutation group is called the initial vector problem. This problem is an especially large scale nonlinear programming problem. We transform it to a generalized geometric programming problem and use the double condensation method to develop an algorithm for its solution. 3
4 1. INTRODUCTION Geometric programming is an optimization technique originally developed for solving a class of nonlinear optimization problems found in engineering design [14, 15]. In a geometric programming problem all the constraints as well as the objective function are posynomials (sum of terms having a positive real coefficient multiplied by a product of variables where each variable is raised to an arbitrary real constant power) and all the variables are strictly positive. That is, a function of the form: m n P (x) = c i x a ij j i=1 j=1 where c i > 0 and a ij R. In a generalized geometric programming problem, the coefficients may be arbitrary real numbers. Avriel, Dembo, and Passy [1] describe a technique called double condensation that solves a generalized geometric programming problem by solving a series of linear programming problems. This technique was later modified by Burns [4] to apply to problems with equality constraints. The Gaussian channel is a communications model in which messages are represented by vectors in R n and transmitted over a noisy channel. We generate the set of messages by groups of permutation matrices and the resulting message set is called a permutation code. Given an arbitrary permutation group, the problem of finding an optimal code generated by that group may be written as a nonlinear programming problem [10]. The resulting problem is called the initial vector problem and in it each group element together with its inverse create a constraint. Since we will be considering groups as large as 95,000 elements, the associated nonlinear programming problem is especially large scale. In this paper, we transform this large scale nonlinear 1
5 programming problem to a generalized geometric programming problem and use the double condensation method to develop an algorithm for its solution. Previous applications of geometric programming have been highly nonlinear problems with few constraints and variables [9, for survey article]. In section 2, we describe the Gaussian channel, permutation codes, and present some previous results on solving the initial vector problem. In section 3 we describe the double condensation technique and present our specialized algorithm. Section 4 contains a numerical example and in section 6 we present computational results. 2
6 2. GROUP CODES FOR THE GAUSSIAN CHANNEL The Gaussian channel is a communications model introduced by Shannon in 1948 in which messages are represented by vectors in R n and transmitted over a noisy channel. We assume the transmitter has a finite set of messages available and sends one every T seconds. When the vector x is transmitted, the received signal is represented by a vector y = x + z which consists of the sent vector and a Gaussian noise vector z whose components are statistically independent Gaussian random variables of mean zero and variance N. Upon receiving y, the receiver must decide, presumably in some optimum manner, which of the messages was sent. The set of vectors representing the messages is called a code and the process of deciding is called decoding. In this paper, we consider codes generated by groups of orthogonal n by n matrices (a real matrix, A, is orthogonal if A t = A 1 ) and more specifically by groups of permutation matrices (A is a permutation matrix if exactly one entry in each row and column is equal to one, and all other entries are zero). Group codes were first defined by Slepian [12] in Definition 2.1 A set X of M n-dimensional unit vectors is an (M,n) group code if there exists a group G of orthogonal n by n matrices and a unit vector x such that X = {gx : g G}. The code X is said to be generated by the group G and the initial vector x. If G is a group of permutation matrices then X is called a permutation code. If the set of vectors available to the transmitter is an (M,n) group code where each codeword has the same a priori probability of transmission, then the decoding criteria for the receiver that minimizes the average error probability is maximum likelihood [3, section 6.2]. That is, the optimum receiver 3
7 decodes y as the codeword g x that minimizes the set of Euclidean distances {d(y, gx) : g G}. One advantage of using a group code is that all the codewords are on an equal footing; each has the same error probability and the same disposition of codeword neighbors. Thus, the best group codes are those with a large nearest neighbor distance between codewords. This is formulated in the following problem. Initial Vector Problem: Given a group G of orthogonal n by n matrices, find an initial vector that maximizes the minimum distance between the codewords of all codes generated by G, i.e., find a unit vector x in R n such that min{d(x, gx)} = max min{d(z, gz)} where the maximum is taken over all unit vectors z in R n and the minimum is taken over all nonidentity elements g in G. The vector x is called an optimal initial vector for G and the associated code is called an optimal code generated by G. Previous attempts to provide a general solution to this problem have not been successful, although it has been solved in some special cases [2, 7, 8, 13]. The evidence so far is that is a very difficult problem and it does not have a closed-form solution. Suppose G is a group of orthogonal n by n matrices and V G = {y R n : gy = y, g G}. Let (, ) denote the ordinary inner product and define V G = {y R n : (y, z) = 0, z V G }. Karlof [10] has shown that if V G {0}, any optimal initial vector for G must lie in VG. Karlof [10] presented a numerical algorithm for the initial vector problem that incorporates this fact. This algorithm is a two phase method. Phase I is a modification of Topkis and Veinott s feasible directions method that identifies a set of active constraints and a starting point for phase II. Phase II uses a Newton- Raphson technique on the equations formed by the active constraints, the 4
8 equations defining VG (if V G {0}), and the equation x 2 i = 1. Karlof has applied this algorithm to many permutation groups, the largest one being the Mathieu group of degree 11 and order It is also shown in [10] that if G is a doubly transitive permutation group, then VG = {y : y i = 0}. Let G be a doubly transitive permutation group. Now, since d 2 (gx, x) = 2 2(gx, x) and (gx, x) = (g 1 x, x), an equivalent formulation of the initial vector problem(ivp) is min z n+1 n z i = 0 i=1 n zi 2 = 1 i=1 (gz, z) z n+1 g S z = (z 1,..., z n ) R n, z n+1 R where S is a complete list of the group elements excluding inverses and the identity. We now let M denote the cardinality of S. Note that this formulation of problem (IVP) is a geometric programming problem except the variables are unrestricted. It can be transformed to a generalized geometric programming problem by replacing z i = z i + zi and restricting z i ± ρ for some ρ > 0. We present an algorithm that uses the double condensation methods to solve this transformed formulation of the initial vector problem. We apply this algorithm to permutation groups as large as 95,040. 5
9 3. ALGORITHM A generalized geometric programming problem is of the form: min P 0 (x) Q 0 (x) P k (x) Q k (x) = 0, k = 1, 2,..., M P k (x) Q k (x) 0, k = M + 1, M + 2,..., N (3.1) 0 < x LB j x j x UB j j = 1,..., n where P k (x) and Q k (x) are posynomials of the general form: P k (x) = I k i=1 L k u ik (x) = Q k (x) = v lk (x) = l=1 I k n c ik i=1 j=1 L k n d lk l=1 j=1 and c ik > 0, for all i, k, and d lk > 0 for all l, k. x a jik j, x b jlk j, Before we give the description of the double condensation method [4] for solving problem IVP, we describe the condensation technique. The classical arithmetic-geometric inequality stating that the weighted arithmetic mean of positive numbers a 1, a 2,..., a n is greater than or equal to the geometric mean may be written as follows: n n ( ) ai wi a i (3.2) i=1 i=1 w i where w i = 1, and w i > 0 for all i. Equality holds in (3.2) if and only if a 1 w 1 = a 2 w 2 =... = a n w n. 6
10 Let p(x) 1 be a functional constraint where p(x) is a posynomial of the form I n p(x) = c i x a ij j, c i > 0; i=1 j=1 and x > 0 be given. Define w i = c nj=1 i x a ij j, i = 1,..., I. p(x ) Then w i > 0 and I i=1 w i = 1. Therefore, as a direct consequence of (3.2) we have where p(x, x ) = p(x, x ) p(x) 1, (3.3) I i=1 ( ci nj=1 x a ij j w i ) wi. The monomial p(x, x ) is the condensed form of p(x), and equals the original posynomial at the point of condensation x. Note that (3.3) implies that any x that satisfies p(x) 1 will also satisfy p(x, x ) 1, but not vice versa. We convert problem IVP to a generalized geometric programming problem by writing the variables z i = z + i z i (i = 1,..., n) and restricting z + i, z i ρ > 0. It is no loss of generality to restrict z n+1 > 0 since the maximum inner product is always positive. Thus, this generalized geometric programming problem has 2n + 1 variables: min z n+1 n n z i + zi = 0 i=1 i=1 n n (z i +2 + zi 2 ) 2 z i + zi = 1 i=1 i=1 (gz +, z + ) + (gz, z ) [(gz +, z ) + (gz, z + )] z n+1 g S (3.4) 7
11 where z ± = (z ± 1, z ± 2,..., z ± n ). An equivalent version of (3.4) is: ρ z + i, z i, 0 < z n+1 min z n+1 ni=1 z + i ni=1 z i ni=1 z i +2 + zi n i=1 z i + zi (gz +, z + ) + (gz, z ) z n+1 + (gz +, z ) + (gz, z + ) = 1 = 1 1 (3.5) ρ z + i, z i, 0 < z n+1. We now describe how to solve (3.5) by solving a serie of linear programming problems via the double condensation method. Let z R 2n+1 be a feasible solution of (3.5). Using the condensation technique described above, the denominators of (3.5) can be condensed to monomials and (3.5) becomes a posynomial geometric programming problem. Now we perform another condensation on the new posynomial geometric programming problem at z to obtain a the following monomial programming problem. We let z = (z 1 +, z1, z 2 +, z2,..., z n +, zn, z n+1 ). min z n+1 C k (z) = 1, k = 1, 2. C k (z) 1, k = 3,..., M + 2, 8
12 ρ z i +, zi, 0 < z n+1. where C k (z) is a monomial. The natural logarithm function ln y is monotonicly increasing and is defined for y > 0. Therefore, (3.6) can be transformed to a linear programing problem through a change of variables: y j ± = ln z j ±, j = 1,..., n and y n+1 = ln(z n+1 + 1). Also, we set ρ = 1 so that y j ± 0. Problem LP(z): max y n+1 f 1 y = b 1 f 2 y = b 2 Ay B 0 y + i, y i ln 2 0 y n+1 where f 1, f 2, and b 1, b 2 are the left side and right side respectively obtained from the two equality constraints of problem (3.6), A is an M by 2n+1 matrix and B is an M dimensional column vector obtained from the inequality constraints of problem (3.6). We restrict 0 y i ± ln 2 so that 1 z i ± 2 and then 0 z i 1. Since y n+1 is restricted 0 in problem LP(z), z n+1 = e y n+1 1. This linear programming problem has M + 2 constraints and 2n+1 variables. The algorithm will be applied to groups with M as large as 50,000 and n as large as 20. Thus, in this case, the problem would have on the order 9
13 of 50,000 constraints and, after adding slacks, on the order of 50,000 variables. However, the dual of the problem has only 2n+1 constraints all of type greater than or equal to. The right hand side values of these constraints are all zero except for the last constraint where the value is minus one. Since the primal has two equalities, M inequalities, and 2n upper bound constraints, the dual has 2 unrestricted and M + 2n restricted variables. We multiply all the constraints of the dual by minus one, add slack variables, write each of the two unrestricted variables as the difference of two restricted variables and obtain a linear programming problem in standard form with 2n+1 equality constraints and M + 4n + 5 variables. This is a great improvement over the number of constraints in the primal. Solving the dual has other advantages. We may take the slack variables as our beginning basis. The double condensation algorithm of [4] involves condensing the most violated inequality constraint of the original problem, transforming it to linear form, adding it to the primal problem, and resolving the new linear programming problem. But adding a constraint to the primal is equivalent to adding a variable to the dual. So when solving the dual problem with the new variable added, we may use our current optimal solution as our starting basic feasible solution and pivot on the new variable. We incorporate the above observations in the following algorithm which employs the double condensation algorithm of [4] to solve the initial vector problem. STEP 0: Form problem IVP. Let z 0 be a feasible solution of problem IVP. Set K=0 and OBJ= z n+1 0 and choose ɛ > 0. STEP 1: Apply the double condensation technique and linearization procedure to form linear program LP( z K ). Form the dual DL( z K ) of linear 10
14 program LP( z K ). Solve DL( z K ) using the slack variables as the beginning basic feasible solution. Let x K+1 be the optimal basic feasible solution to DL( z K ). Compute the corresponding solution z K+1 to problem IVP. STEP 2: Evaluate the inequality constraints in problem IVP at z K+1. If z K+1 satisfies all the inequality constraints, then go to step 5. STEP 3: Recondense the most violated constraint at z K+1, transform it to linear form, and append it to DL( z K ) as a new variable. STEP 4: Solve the appended problem DL( z K ) using x K+1 as the beginning basic feasible solution and pivot on the new variable. Let x K+1 be the optimal basic feasible solution to the appended problem DL( z K ). Compute the corresponding solution z K+1 to problem IVP. Go to step 2. STEP 5: If z K+1 n+1 OBJ < ɛ, then stop. The solution is z K+1. Otherwise, Remarks set K=K+1, OBJ = z K n+1 and go to step Steps 2 thru 4 form a method to obtain an optimal solution to the posynomial geometric programming problem. When a solution z K+1 passes the test in STEP 3, it is a global optimum to the posynomial goemetric programming problem. The linear constraint generated in STEP 4 reduces the feasible region of LP (z K ) so that z K+1 no longer belongs to it but all the feasible solutions of the posynomial geometric programming problem still remain a subset of this new feasible region. The new linear constraint is generally referred to as a cut. 11
15 2. This algorithm is not guaranted to converge to a global optimum of the original problem. Avriel, Dembo, and Passy [1] prove only convergence to a Kuhn-Tucker point for a generalized geometric programming problem without equality constraints. 3. The equality constraints are not involved in the calculations of STEP 3 and do not change during each major interation. 12
16 4. EXAMPLE In this section, we present an example of the algorithm described in section 3 applied to a small permutation group of degree 4. The group is the alternating group on four elements, A 4 = {(1), (1,2)(3,4), (1,3)(2,4), (1,4)(2,3), (1,2,3), (1,3,2), (1,3,4), (1,4,3), (2,3,4), (2,4,3), (1,2,4), (1,4,2)}. Problem IVP from section 2 is: min z 5 z 1 + z 2 + z 3 + z 4 = 0 z1 2 + z2 2 + z3 2 + z4 2 = 1 z 1 z 2 + z 2 z 1 + z 3 z 4 + z 4 z 3 z 5 z 1 z 3 + z 2 z 4 + z 3 z 1 + z 4 z 2 z 5 z 1 z 4 + z 2 z 3 + z 3 z 2 + z 4 z 1 z 5 z 1 z 3 + z 2 z 2 + z 3 z 4 + z 4 z 1 z 5 z 1 z 4 + z 2 z 1 + z 3 z 3 + z 4 z 2 z 5 z 1 z 1 + z 2 z 4 + z 3 z 2 + z 4 z 3 z 5 z 1 z 2 + z 2 z 3 + z 3 z 1 + z 4 z 4 z 5 z R 5 To change problem IVP to a generalized geometic programming problem, we write z i = z i + zi (i = 1,..., 4) and restrict z i +, zi 1. Then the problem has 9 constraints and 9 variables. STEP 0: Choose z 0 = (.4082,.4082,.8165, 0.0,.8333) then OBJ= z 0 n+1 = Set K=0 and ɛ =
17 STEP 1: After applying the double condensation technique, problem LP( z 0 ) is formed: f 1 = (.094,.067,.094,.067,.133,.242,.000,.000,.000) b 1 =.209 f 2 = (.292,.208,.292,.208,.208,.377,.208,.208,.000) b 2 = A = B = (.029,.051,.051,.011,.080,.011,.037) T. The dual, DL( z 0 ), of the above problem is formed. After putting it in standard form, it has 9 constraints and 28 variables. After 8 pivots, the optimal basic feasible solution is x 1 with basic variables x 1 2 = 4.690, x 1 3 =.0010, x 1 5 = 2.246, x 1 9 = 4.898, x 1 10 =.0011, x 1 21 =.0331, x 1 23 =.0334, x 1 24 =.0281, x 1 26 = The corresponding solution to LP( z 0 ) is y = (.692,.000,.0621,.000,.000,.570,.000,.147,.519) T and to problem IVP is z 1 = (.999,.064,.768,.159,.680) where z 1± i = e y± i for i = 1,..., 4, z 1 i = z 1+ i z 1 i and z 1 5 = e y
18 STEPS 2 and 3: We evaluate problem IVP at z 1. The most violated inequality constraint is the sixth one. It is recondensed at z 1 and appended to DL( z 0 ) as a new variable. The new coefficient in the objective function is.101 and the new column is (.275,.150,.077,.062,.011,.005,.055,.053,.122) T. STEP 4: The appended problem is solved using x 1 as the beginning basic feasible solution and pivoting on the new variable. An optimal solution is obtained after 2 pivots. The corresponding solution (again denoted by z 1 ) to problem IVP is z 1 = (.849,.150,.768,.159,.680) and we return to step 2. STEPS 2, 3, and 4: The sixth constraint is again the most violated inequality and is recondensed at z 1 and appended to DL( z 0 ) as a new variable. The appended problem is solved after 2 pivots and the corresponding solution to problem IVP is z 1 = (.839,.157,.768,.159,.680). STEP 2: z 1 satisfies all the inequality constraints of problem IVP. STEP 5: z 5 1 OBJ = > Set K = 1, OBJ =.680 and return to step 1. REMARK: The algorithm converges after 3 more iterations with z 2 = ( ) z 3 = ( ) z 4 = ( ) 15
19 5. COMPUTATIONAL RESULTS In this section, we present the results of some computational experiments in which the algorithm of section 3 was used to calculate the optimal initial vectors of several well-known permutation groups. The groups were generated using a table of generators in [11] and group algorithms from [5]. The computations were done on a VAX 6420 at the University of North Carolina at Wilmington and a CRAY Y-MP at the North Carolina Supercomputer Center. Recall from the discussion of section 3, the linear programming problem DL(z K ) has a very special structure. The right hand side values of the constraints are all zero except for the last constraint. As a consequence, DL(z K ) is highly degenerate which can cause computational problems. To avoid this situation, we employ a perturbation method found in [6]. We found that this perturbation results in a substantial decrease in the number of pivots. In Table 5.1, we compare the number of pivots with perturbation and without perturbation required at the beginning of each major iteration (i.e., everytime DL(z K ) was formed in STEP 1) for the numerical example of the permutation group A 4 presented in section 4. We can see the number of pivots decreased significantly even for such a small group. We also compare the total number of pivots required of the entire calculations for the groups A 4, M 11, and P SL(4, 2). The group M 11 eventually encounters cycling without perturbation and the calculation could not be finished. These results are shown in Table 5.2. We tested the proposed algorithm on five large permutation groups: they are the symmetric group S 8, the Mathieu groups M 11 and M 12, the projective unimodular group P SL(4, 2), and a group of order 40,320 and degree 16 16
20 which we call P 16. The initial starting solutions were generated randomly by IMSL subroutine RNUN. See Table 5.3 for the results, and note the following nomenclature: G : order of the permutation group, M: number of less than or equal to constraints in problem (IVP), n: degree of the permutation group, INT: number of major iterations, MIN DIS: minimum distance of optimal code. Table 5.1: Comparison for group A4. iteration No. of pivots without perturbation No. of pivots with perturbation
21 Table 5.2: Comparison of total number of pivots for three groups Group Total No. of pivots without pertur. Total No. of pivots with pertur. A M P SL(4, 2) 28,309 1,892 Table 5.3: Computational results for 5 large groups Group G M n INT MIN DIS S 8 40,320 20, M 11 7,920 4, M 12 95,040 47, P SL(4, 2) 20,160 10, P 16 40,320 20, CONCLUSIONS The algorithm developed to solve the initial vector problem in this paper differs from the previous method [10] in several respects. In [10], Karlof employed a two phase algorithm. Phase I was a modification of Topkis and Veinott s feasible directions method and was used to identify a set of active constraints. Phase II used a Newton-Raphson technique on the equations formed by the active constraints. Phase I failed to converge for large groups. The largest group solved was of order 7,920. Convergence of phase I was 18
22 also sensitive to the choice of the starting point. On the other hand, the algorithm developed in this paper never failed to converge and the starting points were choosen randomly. The largest group solved in this paper was of order 95,040. This was the largest group we were able to generate. We believe this algorithm has the potential to handle much larger groups. 19
23 References [1] M. Avriel, R. Dembo and U. Passy, Solution of generalized geometric programs, Int. J. Numer. Methods Engrg., 9, (1975). [2] I. Blake, Distance properties of group codes for the Gaussian channel, SIAM J. Appl. Math., 23, No. 3, , (1972). [3] I. Blake and R. Mullin, The Mathematical Theory of Coding, Academic Press, New York (1975). [4] S. A. Burns, Generalized geometric programming with many equality constraints, Int. J. Numer. Methods Engrg., 24, (1987). [5] J. Cannon, The basis of a computer system for modern algebra, SYMAC 81, Proc ACM Symp. Symbolic and Algebraic Computation, (1981). [6] A. Charnes, Optimality and degeneracy in linear programming, Econometrica, 20, , (1952). [7] D. Djokovic and I. Blake, An optimization problem for unitary and orthogonal representations of finite groups, Trans. Amer. Math. Soc., 164, , (1972). [8] C. Downey and J. Karlof, The analysis of optimal [M,3] group codes for the Gaussian channel, Util. Math., 18, 51-70, (1980). [9] J. Ecker, Geometric progamming: methods, computations, and applications, SIAM Review, 22, No. 3, , (1980). 20
24 [10] J. Karlof, Permutation codes for the gaussian channel, IEEE Trans. on Inform. Theory. IT-35, No. 4, , (1989). [11] C. Sims, Computational methods for permutation groups, in Computational Problems in Abstract Algebra. Oxford, UK:Pergamon (1970). [12] D. Slepian, Group codes for the Gaussian channel, Bell Syst. Tech. J., 17, , (1968). [13], Permutation modulation, Proc. IEEE, 53, , (1965). [14] C. Zener, A mathematical aid in optimizing engineering design, Proc. Nat. Acad. Sci. U.S.A., 47, ,(1961). [15], A further mathematical aid in optimizing engineering design, Ibid., 48, , (1962). 21
Representing Group Codes as Permutation Codes
 Representing Group Codes as Permutation Codes Ezio Biglieri John K. Karlof Emanuele Viterbo November 19, 001 Abstract Given an abstract group G, an N dimensional orthogonal matrix representation G of G,
Representing Group Codes as Permutation Codes Ezio Biglieri John K. Karlof Emanuele Viterbo November 19, 001 Abstract Given an abstract group G, an N dimensional orthogonal matrix representation G of G,
Complex Reflection Group Coding
 Complex Reflection Group Coding Hye Jung Kim Thesis Committee: Dr. J.B. Nation, Adviser Dr. Ralph Freese Graduate Committee: Dr. Michelle Manes Dr. Monique Chyba Dr. Robert Little 1 Acknowledgements I
Complex Reflection Group Coding Hye Jung Kim Thesis Committee: Dr. J.B. Nation, Adviser Dr. Ralph Freese Graduate Committee: Dr. Michelle Manes Dr. Monique Chyba Dr. Robert Little 1 Acknowledgements I
Slack Variable. Max Z= 3x 1 + 4x 2 + 5X 3. Subject to: X 1 + X 2 + X x 1 + 4x 2 + X X 1 + X 2 + 4X 3 10 X 1 0, X 2 0, X 3 0
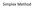 Simplex Method Slack Variable Max Z= 3x 1 + 4x 2 + 5X 3 Subject to: X 1 + X 2 + X 3 20 3x 1 + 4x 2 + X 3 15 2X 1 + X 2 + 4X 3 10 X 1 0, X 2 0, X 3 0 Standard Form Max Z= 3x 1 +4x 2 +5X 3 + 0S 1 + 0S 2
Simplex Method Slack Variable Max Z= 3x 1 + 4x 2 + 5X 3 Subject to: X 1 + X 2 + X 3 20 3x 1 + 4x 2 + X 3 15 2X 1 + X 2 + 4X 3 10 X 1 0, X 2 0, X 3 0 Standard Form Max Z= 3x 1 +4x 2 +5X 3 + 0S 1 + 0S 2
3. Coding theory 3.1. Basic concepts
 3. CODING THEORY 1 3. Coding theory 3.1. Basic concepts In this chapter we will discuss briefly some aspects of error correcting codes. The main problem is that if information is sent via a noisy channel,
3. CODING THEORY 1 3. Coding theory 3.1. Basic concepts In this chapter we will discuss briefly some aspects of error correcting codes. The main problem is that if information is sent via a noisy channel,
i.e., into a monomial, using the Arithmetic-Geometric Mean Inequality, the result will be a posynomial approximation!
 Dennis L. Bricker Dept of Mechanical & Industrial Engineering The University of Iowa i.e., 1 1 1 Minimize X X X subject to XX 4 X 1 0.5X 1 Minimize X X X X 1X X s.t. 4 1 1 1 1 4X X 1 1 1 1 0.5X X X 1 1
Dennis L. Bricker Dept of Mechanical & Industrial Engineering The University of Iowa i.e., 1 1 1 Minimize X X X subject to XX 4 X 1 0.5X 1 Minimize X X X X 1X X s.t. 4 1 1 1 1 4X X 1 1 1 1 0.5X X X 1 1
Optimization in Information Theory
 Optimization in Information Theory Dawei Shen November 11, 2005 Abstract This tutorial introduces the application of optimization techniques in information theory. We revisit channel capacity problem from
Optimization in Information Theory Dawei Shen November 11, 2005 Abstract This tutorial introduces the application of optimization techniques in information theory. We revisit channel capacity problem from
Understanding the Simplex algorithm. Standard Optimization Problems.
 Understanding the Simplex algorithm. Ma 162 Spring 2011 Ma 162 Spring 2011 February 28, 2011 Standard Optimization Problems. A standard maximization problem can be conveniently described in matrix form
Understanding the Simplex algorithm. Ma 162 Spring 2011 Ma 162 Spring 2011 February 28, 2011 Standard Optimization Problems. A standard maximization problem can be conveniently described in matrix form
The Nearest Doubly Stochastic Matrix to a Real Matrix with the same First Moment
 he Nearest Doubly Stochastic Matrix to a Real Matrix with the same First Moment William Glunt 1, homas L. Hayden 2 and Robert Reams 2 1 Department of Mathematics and Computer Science, Austin Peay State
he Nearest Doubly Stochastic Matrix to a Real Matrix with the same First Moment William Glunt 1, homas L. Hayden 2 and Robert Reams 2 1 Department of Mathematics and Computer Science, Austin Peay State
Cooperative Communication with Feedback via Stochastic Approximation
 Cooperative Communication with Feedback via Stochastic Approximation Utsaw Kumar J Nicholas Laneman and Vijay Gupta Department of Electrical Engineering University of Notre Dame Email: {ukumar jnl vgupta}@ndedu
Cooperative Communication with Feedback via Stochastic Approximation Utsaw Kumar J Nicholas Laneman and Vijay Gupta Department of Electrical Engineering University of Notre Dame Email: {ukumar jnl vgupta}@ndedu
1 The independent set problem
 ORF 523 Lecture 11 Spring 2016, Princeton University Instructor: A.A. Ahmadi Scribe: G. Hall Tuesday, March 29, 2016 When in doubt on the accuracy of these notes, please cross chec with the instructor
ORF 523 Lecture 11 Spring 2016, Princeton University Instructor: A.A. Ahmadi Scribe: G. Hall Tuesday, March 29, 2016 When in doubt on the accuracy of these notes, please cross chec with the instructor
Some Results in Duality
 Int. J. Contemp. Math. Sciences, Vol. 4, 2009, no. 30, 1493-1501 Some Results in Duality Vanita Ben Dhagat and Savita Tiwari Jai Narain college of Technology Bairasia Road, Bhopal M.P., India vanita1_dhagat@yahoo.co.in
Int. J. Contemp. Math. Sciences, Vol. 4, 2009, no. 30, 1493-1501 Some Results in Duality Vanita Ben Dhagat and Savita Tiwari Jai Narain college of Technology Bairasia Road, Bhopal M.P., India vanita1_dhagat@yahoo.co.in
MATH32031: Coding Theory Part 15: Summary
 MATH32031: Coding Theory Part 15: Summary 1 The initial problem The main goal of coding theory is to develop techniques which permit the detection of errors in the transmission of information and, if necessary,
MATH32031: Coding Theory Part 15: Summary 1 The initial problem The main goal of coding theory is to develop techniques which permit the detection of errors in the transmission of information and, if necessary,
1 Number Systems and Errors 1
 Contents 1 Number Systems and Errors 1 1.1 Introduction................................ 1 1.2 Number Representation and Base of Numbers............. 1 1.2.1 Normalized Floating-point Representation...........
Contents 1 Number Systems and Errors 1 1.1 Introduction................................ 1 1.2 Number Representation and Base of Numbers............. 1 1.2.1 Normalized Floating-point Representation...........
3 The Simplex Method. 3.1 Basic Solutions
 3 The Simplex Method 3.1 Basic Solutions In the LP of Example 2.3, the optimal solution happened to lie at an extreme point of the feasible set. This was not a coincidence. Consider an LP in general form,
3 The Simplex Method 3.1 Basic Solutions In the LP of Example 2.3, the optimal solution happened to lie at an extreme point of the feasible set. This was not a coincidence. Consider an LP in general form,
THE SNOWFLAKE DECODING ALGORITHM
 THE SNOWFLAKE DECODING ALGORITHM J. B. NATION AND CATHERINE WALKER Abstract. This paper describes an automated algorithm for generating a group code using any unitary group, initial vector, and generating
THE SNOWFLAKE DECODING ALGORITHM J. B. NATION AND CATHERINE WALKER Abstract. This paper describes an automated algorithm for generating a group code using any unitary group, initial vector, and generating
In Chapters 3 and 4 we introduced linear programming
 SUPPLEMENT The Simplex Method CD3 In Chapters 3 and 4 we introduced linear programming and showed how models with two variables can be solved graphically. We relied on computer programs (WINQSB, Excel,
SUPPLEMENT The Simplex Method CD3 In Chapters 3 and 4 we introduced linear programming and showed how models with two variables can be solved graphically. We relied on computer programs (WINQSB, Excel,
Part 1. The Review of Linear Programming
 In the name of God Part 1. The Review of Linear Programming 1.2. Spring 2010 Instructor: Dr. Masoud Yaghini Outline Introduction Basic Feasible Solutions Key to the Algebra of the The Simplex Algorithm
In the name of God Part 1. The Review of Linear Programming 1.2. Spring 2010 Instructor: Dr. Masoud Yaghini Outline Introduction Basic Feasible Solutions Key to the Algebra of the The Simplex Algorithm
On the Block Error Probability of LP Decoding of LDPC Codes
 On the Block Error Probability of LP Decoding of LDPC Codes Ralf Koetter CSL and Dept. of ECE University of Illinois at Urbana-Champaign Urbana, IL 680, USA koetter@uiuc.edu Pascal O. Vontobel Dept. of
On the Block Error Probability of LP Decoding of LDPC Codes Ralf Koetter CSL and Dept. of ECE University of Illinois at Urbana-Champaign Urbana, IL 680, USA koetter@uiuc.edu Pascal O. Vontobel Dept. of
The Simplex Algorithm
 8.433 Combinatorial Optimization The Simplex Algorithm October 6, 8 Lecturer: Santosh Vempala We proved the following: Lemma (Farkas). Let A R m n, b R m. Exactly one of the following conditions is true:.
8.433 Combinatorial Optimization The Simplex Algorithm October 6, 8 Lecturer: Santosh Vempala We proved the following: Lemma (Farkas). Let A R m n, b R m. Exactly one of the following conditions is true:.
Lecture Notes 1: Vector spaces
 Optimization-based data analysis Fall 2017 Lecture Notes 1: Vector spaces In this chapter we review certain basic concepts of linear algebra, highlighting their application to signal processing. 1 Vector
Optimization-based data analysis Fall 2017 Lecture Notes 1: Vector spaces In this chapter we review certain basic concepts of linear algebra, highlighting their application to signal processing. 1 Vector
Introduction to Applied Linear Algebra with MATLAB
 Sigam Series in Applied Mathematics Volume 7 Rizwan Butt Introduction to Applied Linear Algebra with MATLAB Heldermann Verlag Contents Number Systems and Errors 1 1.1 Introduction 1 1.2 Number Representation
Sigam Series in Applied Mathematics Volume 7 Rizwan Butt Introduction to Applied Linear Algebra with MATLAB Heldermann Verlag Contents Number Systems and Errors 1 1.1 Introduction 1 1.2 Number Representation
Adaptive Cut Generation for Improved Linear Programming Decoding of Binary Linear Codes
 Adaptive Cut Generation for Improved Linear Programming Decoding of Binary Linear Codes Xiaojie Zhang and Paul H. Siegel University of California, San Diego, La Jolla, CA 9093, U Email:{ericzhang, psiegel}@ucsd.edu
Adaptive Cut Generation for Improved Linear Programming Decoding of Binary Linear Codes Xiaojie Zhang and Paul H. Siegel University of California, San Diego, La Jolla, CA 9093, U Email:{ericzhang, psiegel}@ucsd.edu
MATRICES. a m,1 a m,n A =
 MATRICES Matrices are rectangular arrays of real or complex numbers With them, we define arithmetic operations that are generalizations of those for real and complex numbers The general form a matrix of
MATRICES Matrices are rectangular arrays of real or complex numbers With them, we define arithmetic operations that are generalizations of those for real and complex numbers The general form a matrix of
CSC Linear Programming and Combinatorial Optimization Lecture 10: Semidefinite Programming
 CSC2411 - Linear Programming and Combinatorial Optimization Lecture 10: Semidefinite Programming Notes taken by Mike Jamieson March 28, 2005 Summary: In this lecture, we introduce semidefinite programming
CSC2411 - Linear Programming and Combinatorial Optimization Lecture 10: Semidefinite Programming Notes taken by Mike Jamieson March 28, 2005 Summary: In this lecture, we introduce semidefinite programming
Chapter 1: Linear Programming
 Chapter 1: Linear Programming Math 368 c Copyright 2013 R Clark Robinson May 22, 2013 Chapter 1: Linear Programming 1 Max and Min For f : D R n R, f (D) = {f (x) : x D } is set of attainable values of
Chapter 1: Linear Programming Math 368 c Copyright 2013 R Clark Robinson May 22, 2013 Chapter 1: Linear Programming 1 Max and Min For f : D R n R, f (D) = {f (x) : x D } is set of attainable values of
Chapter 2. Error Correcting Codes. 2.1 Basic Notions
 Chapter 2 Error Correcting Codes The identification number schemes we discussed in the previous chapter give us the ability to determine if an error has been made in recording or transmitting information.
Chapter 2 Error Correcting Codes The identification number schemes we discussed in the previous chapter give us the ability to determine if an error has been made in recording or transmitting information.
Feedback Capacity of the First-Order Moving Average Gaussian Channel
 Feedback Capacity of the First-Order Moving Average Gaussian Channel Young-Han Kim* Information Systems Laboratory, Stanford University, Stanford, CA 94305, USA Email: yhk@stanford.edu Abstract The feedback
Feedback Capacity of the First-Order Moving Average Gaussian Channel Young-Han Kim* Information Systems Laboratory, Stanford University, Stanford, CA 94305, USA Email: yhk@stanford.edu Abstract The feedback
18.310A Final exam practice questions
 18.310A Final exam practice questions This is a collection of practice questions, gathered randomly from previous exams and quizzes. They may not be representative of what will be on the final. In particular,
18.310A Final exam practice questions This is a collection of practice questions, gathered randomly from previous exams and quizzes. They may not be representative of what will be on the final. In particular,
1 The linear algebra of linear programs (March 15 and 22, 2015)
 1 The linear algebra of linear programs (March 15 and 22, 2015) Many optimization problems can be formulated as linear programs. The main features of a linear program are the following: Variables are real
1 The linear algebra of linear programs (March 15 and 22, 2015) Many optimization problems can be formulated as linear programs. The main features of a linear program are the following: Variables are real
Performance Analysis and Code Optimization of Low Density Parity-Check Codes on Rayleigh Fading Channels
 Performance Analysis and Code Optimization of Low Density Parity-Check Codes on Rayleigh Fading Channels Jilei Hou, Paul H. Siegel and Laurence B. Milstein Department of Electrical and Computer Engineering
Performance Analysis and Code Optimization of Low Density Parity-Check Codes on Rayleigh Fading Channels Jilei Hou, Paul H. Siegel and Laurence B. Milstein Department of Electrical and Computer Engineering
On the Classification of Splitting (v, u c, ) BIBDs
 BULGARIAN ACADEMY OF SCIENCES CYBERNETICS AND INFORMATION TECHNOLOGIES Volume 18, No 5 Special Thematic Issue on Optimal Codes and Related Topics Sofia 2018 Print ISSN: 1311-9702; Online ISSN: 1314-4081
BULGARIAN ACADEMY OF SCIENCES CYBERNETICS AND INFORMATION TECHNOLOGIES Volume 18, No 5 Special Thematic Issue on Optimal Codes and Related Topics Sofia 2018 Print ISSN: 1311-9702; Online ISSN: 1314-4081
MATH2070 Optimisation
 MATH2070 Optimisation Linear Programming Semester 2, 2012 Lecturer: I.W. Guo Lecture slides courtesy of J.R. Wishart Review The standard Linear Programming (LP) Problem Graphical method of solving LP problem
MATH2070 Optimisation Linear Programming Semester 2, 2012 Lecturer: I.W. Guo Lecture slides courtesy of J.R. Wishart Review The standard Linear Programming (LP) Problem Graphical method of solving LP problem
OPERATIONS RESEARCH. Linear Programming Problem
 OPERATIONS RESEARCH Chapter 1 Linear Programming Problem Prof. Bibhas C. Giri Department of Mathematics Jadavpur University Kolkata, India Email: bcgiri.jumath@gmail.com MODULE - 2: Simplex Method for
OPERATIONS RESEARCH Chapter 1 Linear Programming Problem Prof. Bibhas C. Giri Department of Mathematics Jadavpur University Kolkata, India Email: bcgiri.jumath@gmail.com MODULE - 2: Simplex Method for
Coding Theory and Applications. Linear Codes. Enes Pasalic University of Primorska Koper, 2013
 Coding Theory and Applications Linear Codes Enes Pasalic University of Primorska Koper, 2013 2 Contents 1 Preface 5 2 Shannon theory and coding 7 3 Coding theory 31 4 Decoding of linear codes and MacWilliams
Coding Theory and Applications Linear Codes Enes Pasalic University of Primorska Koper, 2013 2 Contents 1 Preface 5 2 Shannon theory and coding 7 3 Coding theory 31 4 Decoding of linear codes and MacWilliams
MATH Examination for the Module MATH-3152 (May 2009) Coding Theory. Time allowed: 2 hours. S = q
 MATH-315201 This question paper consists of 6 printed pages, each of which is identified by the reference MATH-3152 Only approved basic scientific calculators may be used. c UNIVERSITY OF LEEDS Examination
MATH-315201 This question paper consists of 6 printed pages, each of which is identified by the reference MATH-3152 Only approved basic scientific calculators may be used. c UNIVERSITY OF LEEDS Examination
4488 IEEE TRANSACTIONS ON INFORMATION THEORY, VOL. 54, NO. 10, OCTOBER /$ IEEE
 4488 IEEE TRANSACTIONS ON INFORMATION THEORY, VOL. 54, NO. 10, OCTOBER 2008 List Decoding of Biorthogonal Codes the Hadamard Transform With Linear Complexity Ilya Dumer, Fellow, IEEE, Grigory Kabatiansky,
4488 IEEE TRANSACTIONS ON INFORMATION THEORY, VOL. 54, NO. 10, OCTOBER 2008 List Decoding of Biorthogonal Codes the Hadamard Transform With Linear Complexity Ilya Dumer, Fellow, IEEE, Grigory Kabatiansky,
CO 250 Final Exam Guide
 Spring 2017 CO 250 Final Exam Guide TABLE OF CONTENTS richardwu.ca CO 250 Final Exam Guide Introduction to Optimization Kanstantsin Pashkovich Spring 2017 University of Waterloo Last Revision: March 4,
Spring 2017 CO 250 Final Exam Guide TABLE OF CONTENTS richardwu.ca CO 250 Final Exam Guide Introduction to Optimization Kanstantsin Pashkovich Spring 2017 University of Waterloo Last Revision: March 4,
Data representation and classification
 Representation and classification of data January 25, 2016 Outline Lecture 1: Data Representation 1 Lecture 1: Data Representation Data representation The phrase data representation usually refers to the
Representation and classification of data January 25, 2016 Outline Lecture 1: Data Representation 1 Lecture 1: Data Representation Data representation The phrase data representation usually refers to the
The simplex algorithm
 The simplex algorithm The simplex algorithm is the classical method for solving linear programs. Its running time is not polynomial in the worst case. It does yield insight into linear programs, however,
The simplex algorithm The simplex algorithm is the classical method for solving linear programs. Its running time is not polynomial in the worst case. It does yield insight into linear programs, however,
PROCESSING AND TRANSMISSION OF INFORMATION*
 IX. PROCESSING AND TRANSMISSION OF INFORMATION* Prof. P. Elias E. Ferretti E. T. Schoen Prof. R. M. Fano K. Joannou F. F. Tung Prof. D. A. Huffman R. M. Lerner S. H. Unger Prof. C. E. Shannon J. B. O'Loughlin
IX. PROCESSING AND TRANSMISSION OF INFORMATION* Prof. P. Elias E. Ferretti E. T. Schoen Prof. R. M. Fano K. Joannou F. F. Tung Prof. D. A. Huffman R. M. Lerner S. H. Unger Prof. C. E. Shannon J. B. O'Loughlin
Secure Degrees of Freedom of the MIMO Multiple Access Wiretap Channel
 Secure Degrees of Freedom of the MIMO Multiple Access Wiretap Channel Pritam Mukherjee Sennur Ulukus Department of Electrical and Computer Engineering University of Maryland, College Park, MD 074 pritamm@umd.edu
Secure Degrees of Freedom of the MIMO Multiple Access Wiretap Channel Pritam Mukherjee Sennur Ulukus Department of Electrical and Computer Engineering University of Maryland, College Park, MD 074 pritamm@umd.edu
Matrices: 2.1 Operations with Matrices
 Goals In this chapter and section we study matrix operations: Define matrix addition Define multiplication of matrix by a scalar, to be called scalar multiplication. Define multiplication of two matrices,
Goals In this chapter and section we study matrix operations: Define matrix addition Define multiplication of matrix by a scalar, to be called scalar multiplication. Define multiplication of two matrices,
Dual Basic Solutions. Observation 5.7. Consider LP in standard form with A 2 R m n,rank(a) =m, and dual LP:
 Dual Basic Solutions Consider LP in standard form with A 2 R m n,rank(a) =m, and dual LP: Observation 5.7. AbasisB yields min c T x max p T b s.t. A x = b s.t. p T A apple c T x 0 aprimalbasicsolutiongivenbyx
Dual Basic Solutions Consider LP in standard form with A 2 R m n,rank(a) =m, and dual LP: Observation 5.7. AbasisB yields min c T x max p T b s.t. A x = b s.t. p T A apple c T x 0 aprimalbasicsolutiongivenbyx
Shannon s noisy-channel theorem
 Shannon s noisy-channel theorem Information theory Amon Elders Korteweg de Vries Institute for Mathematics University of Amsterdam. Tuesday, 26th of Januari Amon Elders (Korteweg de Vries Institute for
Shannon s noisy-channel theorem Information theory Amon Elders Korteweg de Vries Institute for Mathematics University of Amsterdam. Tuesday, 26th of Januari Amon Elders (Korteweg de Vries Institute for
Duality, Achievable Rates, and Sum-Rate Capacity of Gaussian MIMO Broadcast Channels
 2658 IEEE TRANSACTIONS ON INFORMATION THEORY, VOL 49, NO 10, OCTOBER 2003 Duality, Achievable Rates, and Sum-Rate Capacity of Gaussian MIMO Broadcast Channels Sriram Vishwanath, Student Member, IEEE, Nihar
2658 IEEE TRANSACTIONS ON INFORMATION THEORY, VOL 49, NO 10, OCTOBER 2003 Duality, Achievable Rates, and Sum-Rate Capacity of Gaussian MIMO Broadcast Channels Sriram Vishwanath, Student Member, IEEE, Nihar
Standard Form An LP is in standard form when: All variables are non-negativenegative All constraints are equalities Putting an LP formulation into sta
 Chapter 4 Linear Programming: The Simplex Method An Overview of the Simplex Method Standard Form Tableau Form Setting Up the Initial Simplex Tableau Improving the Solution Calculating the Next Tableau
Chapter 4 Linear Programming: The Simplex Method An Overview of the Simplex Method Standard Form Tableau Form Setting Up the Initial Simplex Tableau Improving the Solution Calculating the Next Tableau
F 1 F 2 Daily Requirement Cost N N N
 Chapter 5 DUALITY 5. The Dual Problems Every linear programming problem has associated with it another linear programming problem and that the two problems have such a close relationship that whenever
Chapter 5 DUALITY 5. The Dual Problems Every linear programming problem has associated with it another linear programming problem and that the two problems have such a close relationship that whenever
Learning Module 1 - Basic Algebra Review (Appendix A)
 Learning Module 1 - Basic Algebra Review (Appendix A) Element 1 Real Numbers and Operations on Polynomials (A.1, A.2) Use the properties of real numbers and work with subsets of the real numbers Determine
Learning Module 1 - Basic Algebra Review (Appendix A) Element 1 Real Numbers and Operations on Polynomials (A.1, A.2) Use the properties of real numbers and work with subsets of the real numbers Determine
2.098/6.255/ Optimization Methods Practice True/False Questions
 2.098/6.255/15.093 Optimization Methods Practice True/False Questions December 11, 2009 Part I For each one of the statements below, state whether it is true or false. Include a 1-3 line supporting sentence
2.098/6.255/15.093 Optimization Methods Practice True/False Questions December 11, 2009 Part I For each one of the statements below, state whether it is true or false. Include a 1-3 line supporting sentence
Lecture 11 Linear programming : The Revised Simplex Method
 Lecture 11 Linear programming : The Revised Simplex Method 11.1 The Revised Simplex Method While solving linear programming problem on a digital computer by regular simplex method, it requires storing
Lecture 11 Linear programming : The Revised Simplex Method 11.1 The Revised Simplex Method While solving linear programming problem on a digital computer by regular simplex method, it requires storing
GROUP CODES WITH COMPLEX PERMUTATION GROUPS
 GROUP CODES WITH COMPLEX PERMUTATION GROUPS HYE JUNG KIM, J. B. NATION AND ANNE SHEPLER In memory of Wes Peterson. Abstract. Group codes that use certain complex matrix groups are analyzed. These groups
GROUP CODES WITH COMPLEX PERMUTATION GROUPS HYE JUNG KIM, J. B. NATION AND ANNE SHEPLER In memory of Wes Peterson. Abstract. Group codes that use certain complex matrix groups are analyzed. These groups
1 Review Session. 1.1 Lecture 2
 1 Review Session Note: The following lists give an overview of the material that was covered in the lectures and sections. Your TF will go through these lists. If anything is unclear or you have questions
1 Review Session Note: The following lists give an overview of the material that was covered in the lectures and sections. Your TF will go through these lists. If anything is unclear or you have questions
Homework Assignment 4 Solutions
 MTAT.03.86: Advanced Methods in Algorithms Homework Assignment 4 Solutions University of Tartu 1 Probabilistic algorithm Let S = {x 1, x,, x n } be a set of binary variables of size n 1, x i {0, 1}. Consider
MTAT.03.86: Advanced Methods in Algorithms Homework Assignment 4 Solutions University of Tartu 1 Probabilistic algorithm Let S = {x 1, x,, x n } be a set of binary variables of size n 1, x i {0, 1}. Consider
A Proof of the Converse for the Capacity of Gaussian MIMO Broadcast Channels
 A Proof of the Converse for the Capacity of Gaussian MIMO Broadcast Channels Mehdi Mohseni Department of Electrical Engineering Stanford University Stanford, CA 94305, USA Email: mmohseni@stanford.edu
A Proof of the Converse for the Capacity of Gaussian MIMO Broadcast Channels Mehdi Mohseni Department of Electrical Engineering Stanford University Stanford, CA 94305, USA Email: mmohseni@stanford.edu
Berlekamp-Massey decoding of RS code
 IERG60 Coding for Distributed Storage Systems Lecture - 05//06 Berlekamp-Massey decoding of RS code Lecturer: Kenneth Shum Scribe: Bowen Zhang Berlekamp-Massey algorithm We recall some notations from lecture
IERG60 Coding for Distributed Storage Systems Lecture - 05//06 Berlekamp-Massey decoding of RS code Lecturer: Kenneth Shum Scribe: Bowen Zhang Berlekamp-Massey algorithm We recall some notations from lecture
15-780: LinearProgramming
 15-780: LinearProgramming J. Zico Kolter February 1-3, 2016 1 Outline Introduction Some linear algebra review Linear programming Simplex algorithm Duality and dual simplex 2 Outline Introduction Some linear
15-780: LinearProgramming J. Zico Kolter February 1-3, 2016 1 Outline Introduction Some linear algebra review Linear programming Simplex algorithm Duality and dual simplex 2 Outline Introduction Some linear
 Penalty and Barrier Methods General classical constrained minimization problem minimize f(x) subject to g(x) 0 h(x) =0 Penalty methods are motivated by the desire to use unconstrained optimization techniques
Penalty and Barrier Methods General classical constrained minimization problem minimize f(x) subject to g(x) 0 h(x) =0 Penalty methods are motivated by the desire to use unconstrained optimization techniques
"SYMMETRIC" PRIMAL-DUAL PAIR
 "SYMMETRIC" PRIMAL-DUAL PAIR PRIMAL Minimize cx DUAL Maximize y T b st Ax b st A T y c T x y Here c 1 n, x n 1, b m 1, A m n, y m 1, WITH THE PRIMAL IN STANDARD FORM... Minimize cx Maximize y T b st Ax
"SYMMETRIC" PRIMAL-DUAL PAIR PRIMAL Minimize cx DUAL Maximize y T b st Ax b st A T y c T x y Here c 1 n, x n 1, b m 1, A m n, y m 1, WITH THE PRIMAL IN STANDARD FORM... Minimize cx Maximize y T b st Ax
Week_4: simplex method II
 Week_4: simplex method II 1 1.introduction LPs in which all the constraints are ( ) with nonnegative right-hand sides offer a convenient all-slack starting basic feasible solution. Models involving (=)
Week_4: simplex method II 1 1.introduction LPs in which all the constraints are ( ) with nonnegative right-hand sides offer a convenient all-slack starting basic feasible solution. Models involving (=)
A Parametric Simplex Algorithm for Linear Vector Optimization Problems
 A Parametric Simplex Algorithm for Linear Vector Optimization Problems Birgit Rudloff Firdevs Ulus Robert Vanderbei July 9, 2015 Abstract In this paper, a parametric simplex algorithm for solving linear
A Parametric Simplex Algorithm for Linear Vector Optimization Problems Birgit Rudloff Firdevs Ulus Robert Vanderbei July 9, 2015 Abstract In this paper, a parametric simplex algorithm for solving linear
CSCI5654 (Linear Programming, Fall 2013) Lecture-8. Lecture 8 Slide# 1
 CSCI5654 (Linear Programming, Fall 2013) Lecture-8 Lecture 8 Slide# 1 Today s Lecture 1. Recap of dual variables and strong duality. 2. Complementary Slackness Theorem. 3. Interpretation of dual variables.
CSCI5654 (Linear Programming, Fall 2013) Lecture-8 Lecture 8 Slide# 1 Today s Lecture 1. Recap of dual variables and strong duality. 2. Complementary Slackness Theorem. 3. Interpretation of dual variables.
3. THE SIMPLEX ALGORITHM
 Optimization. THE SIMPLEX ALGORITHM DPK Easter Term. Introduction We know that, if a linear programming problem has a finite optimal solution, it has an optimal solution at a basic feasible solution (b.f.s.).
Optimization. THE SIMPLEX ALGORITHM DPK Easter Term. Introduction We know that, if a linear programming problem has a finite optimal solution, it has an optimal solution at a basic feasible solution (b.f.s.).
UNIT-4 Chapter6 Linear Programming
 UNIT-4 Chapter6 Linear Programming Linear Programming 6.1 Introduction Operations Research is a scientific approach to problem solving for executive management. It came into existence in England during
UNIT-4 Chapter6 Linear Programming Linear Programming 6.1 Introduction Operations Research is a scientific approach to problem solving for executive management. It came into existence in England during
Lecture 7. Union bound for reducing M-ary to binary hypothesis testing
 Lecture 7 Agenda for the lecture M-ary hypothesis testing and the MAP rule Union bound for reducing M-ary to binary hypothesis testing Introduction of the channel coding problem 7.1 M-ary hypothesis testing
Lecture 7 Agenda for the lecture M-ary hypothesis testing and the MAP rule Union bound for reducing M-ary to binary hypothesis testing Introduction of the channel coding problem 7.1 M-ary hypothesis testing
On the complexity of maximizing the minimum Shannon capacity in wireless networks by joint channel assignment and power allocation
 On the complexity of maximizing the minimum Shannon capacity in wireless networks by joint channel assignment and power allocation Mikael Fallgren Royal Institute of Technology December, 2009 Abstract
On the complexity of maximizing the minimum Shannon capacity in wireless networks by joint channel assignment and power allocation Mikael Fallgren Royal Institute of Technology December, 2009 Abstract
1. Algebraic and geometric treatments Consider an LP problem in the standard form. x 0. Solutions to the system of linear equations
 The Simplex Method Most textbooks in mathematical optimization, especially linear programming, deal with the simplex method. In this note we study the simplex method. It requires basically elementary linear
The Simplex Method Most textbooks in mathematical optimization, especially linear programming, deal with the simplex method. In this note we study the simplex method. It requires basically elementary linear
Example Problem. Linear Program (standard form) CSCI5654 (Linear Programming, Fall 2013) Lecture-7. Duality
 CSCI5654 (Linear Programming, Fall 013) Lecture-7 Duality Lecture 7 Slide# 1 Lecture 7 Slide# Linear Program (standard form) Example Problem maximize c 1 x 1 + + c n x n s.t. a j1 x 1 + + a jn x n b j
CSCI5654 (Linear Programming, Fall 013) Lecture-7 Duality Lecture 7 Slide# 1 Lecture 7 Slide# Linear Program (standard form) Example Problem maximize c 1 x 1 + + c n x n s.t. a j1 x 1 + + a jn x n b j
Vector spaces. DS-GA 1013 / MATH-GA 2824 Optimization-based Data Analysis.
 Vector spaces DS-GA 1013 / MATH-GA 2824 Optimization-based Data Analysis http://www.cims.nyu.edu/~cfgranda/pages/obda_fall17/index.html Carlos Fernandez-Granda Vector space Consists of: A set V A scalar
Vector spaces DS-GA 1013 / MATH-GA 2824 Optimization-based Data Analysis http://www.cims.nyu.edu/~cfgranda/pages/obda_fall17/index.html Carlos Fernandez-Granda Vector space Consists of: A set V A scalar
5 Handling Constraints
 5 Handling Constraints Engineering design optimization problems are very rarely unconstrained. Moreover, the constraints that appear in these problems are typically nonlinear. This motivates our interest
5 Handling Constraints Engineering design optimization problems are very rarely unconstrained. Moreover, the constraints that appear in these problems are typically nonlinear. This motivates our interest
12. Interior-point methods
 12. Interior-point methods Convex Optimization Boyd & Vandenberghe inequality constrained minimization logarithmic barrier function and central path barrier method feasibility and phase I methods complexity
12. Interior-point methods Convex Optimization Boyd & Vandenberghe inequality constrained minimization logarithmic barrier function and central path barrier method feasibility and phase I methods complexity
Benders Decomposition
 Benders Decomposition Yuping Huang, Dr. Qipeng Phil Zheng Department of Industrial and Management Systems Engineering West Virginia University IENG 593G Nonlinear Programg, Spring 2012 Yuping Huang (IMSE@WVU)
Benders Decomposition Yuping Huang, Dr. Qipeng Phil Zheng Department of Industrial and Management Systems Engineering West Virginia University IENG 593G Nonlinear Programg, Spring 2012 Yuping Huang (IMSE@WVU)
A Review of Linear Programming
 A Review of Linear Programming Instructor: Farid Alizadeh IEOR 4600y Spring 2001 February 14, 2001 1 Overview In this note we review the basic properties of linear programming including the primal simplex
A Review of Linear Programming Instructor: Farid Alizadeh IEOR 4600y Spring 2001 February 14, 2001 1 Overview In this note we review the basic properties of linear programming including the primal simplex
4.6 Linear Programming duality
 4.6 Linear Programming duality To any minimization (maximization) LP we can associate a closely related maximization (minimization) LP Different spaces and objective functions but in general same optimal
4.6 Linear Programming duality To any minimization (maximization) LP we can associate a closely related maximization (minimization) LP Different spaces and objective functions but in general same optimal
Applications of Linear Programming
 Applications of Linear Programming lecturer: András London University of Szeged Institute of Informatics Department of Computational Optimization Lecture 9 Non-linear programming In case of LP, the goal
Applications of Linear Programming lecturer: András London University of Szeged Institute of Informatics Department of Computational Optimization Lecture 9 Non-linear programming In case of LP, the goal
The Hamming Codes and Delsarte s Linear Programming Bound
 The Hamming Codes and Delsarte s Linear Programming Bound by Sky McKinley Under the Astute Tutelage of Professor John S. Caughman, IV A thesis submitted in partial fulfillment of the requirements for the
The Hamming Codes and Delsarte s Linear Programming Bound by Sky McKinley Under the Astute Tutelage of Professor John S. Caughman, IV A thesis submitted in partial fulfillment of the requirements for the
Lecture: Algorithms for LP, SOCP and SDP
 1/53 Lecture: Algorithms for LP, SOCP and SDP Zaiwen Wen Beijing International Center For Mathematical Research Peking University http://bicmr.pku.edu.cn/~wenzw/bigdata2018.html wenzw@pku.edu.cn Acknowledgement:
1/53 Lecture: Algorithms for LP, SOCP and SDP Zaiwen Wen Beijing International Center For Mathematical Research Peking University http://bicmr.pku.edu.cn/~wenzw/bigdata2018.html wenzw@pku.edu.cn Acknowledgement:
An introduction to basic information theory. Hampus Wessman
 An introduction to basic information theory Hampus Wessman Abstract We give a short and simple introduction to basic information theory, by stripping away all the non-essentials. Theoretical bounds on
An introduction to basic information theory Hampus Wessman Abstract We give a short and simple introduction to basic information theory, by stripping away all the non-essentials. Theoretical bounds on
Answers to problems. Chapter 1. Chapter (0, 0) (3.5,0) (0,4.5) (2, 3) 2.1(a) Last tableau. (b) Last tableau /2 -3/ /4 3/4 1/4 2.
 Answers to problems Chapter 1 1.1. (0, 0) (3.5,0) (0,4.5) (, 3) Chapter.1(a) Last tableau X4 X3 B /5 7/5 x -3/5 /5 Xl 4/5-1/5 8 3 Xl =,X =3,B=8 (b) Last tableau c Xl -19/ X3-3/ -7 3/4 1/4 4.5 5/4-1/4.5
Answers to problems Chapter 1 1.1. (0, 0) (3.5,0) (0,4.5) (, 3) Chapter.1(a) Last tableau X4 X3 B /5 7/5 x -3/5 /5 Xl 4/5-1/5 8 3 Xl =,X =3,B=8 (b) Last tableau c Xl -19/ X3-3/ -7 3/4 1/4 4.5 5/4-1/4.5
Upper Bounds on the Capacity of Binary Intermittent Communication
 Upper Bounds on the Capacity of Binary Intermittent Communication Mostafa Khoshnevisan and J. Nicholas Laneman Department of Electrical Engineering University of Notre Dame Notre Dame, Indiana 46556 Email:{mhoshne,
Upper Bounds on the Capacity of Binary Intermittent Communication Mostafa Khoshnevisan and J. Nicholas Laneman Department of Electrical Engineering University of Notre Dame Notre Dame, Indiana 46556 Email:{mhoshne,
[Invited Paper] An Efficient Algorithm for Finding All DC Solutions of Nonlinear Circuits
![[Invited Paper] An Efficient Algorithm for Finding All DC Solutions of Nonlinear Circuits [Invited Paper] An Efficient Algorithm for Finding All DC Solutions of Nonlinear Circuits](/thumbs/83/87694416.jpg) [Invited Paper] An Efficient Algorithm for Finding All DC Solutions of Nonlinear Circuits KIYOTAKA YAMAMURA, KOKI SUDA, and WATARU KUROKI Department of Electrical, Electronic, and Communication Engineering
[Invited Paper] An Efficient Algorithm for Finding All DC Solutions of Nonlinear Circuits KIYOTAKA YAMAMURA, KOKI SUDA, and WATARU KUROKI Department of Electrical, Electronic, and Communication Engineering
MATH3302. Coding and Cryptography. Coding Theory
 MATH3302 Coding and Cryptography Coding Theory 2010 Contents 1 Introduction to coding theory 2 1.1 Introduction.......................................... 2 1.2 Basic definitions and assumptions..............................
MATH3302 Coding and Cryptography Coding Theory 2010 Contents 1 Introduction to coding theory 2 1.1 Introduction.......................................... 2 1.2 Basic definitions and assumptions..............................
Efficient Decoding of Permutation Codes Obtained from Distance Preserving Maps
 2012 IEEE International Symposium on Information Theory Proceedings Efficient Decoding of Permutation Codes Obtained from Distance Preserving Maps Yeow Meng Chee and Punarbasu Purkayastha Division of Mathematical
2012 IEEE International Symposium on Information Theory Proceedings Efficient Decoding of Permutation Codes Obtained from Distance Preserving Maps Yeow Meng Chee and Punarbasu Purkayastha Division of Mathematical
Applications of Lattices in Telecommunications
 Applications of Lattices in Telecommunications Dept of Electrical and Computer Systems Engineering Monash University amin.sakzad@monash.edu Oct. 2013 1 Sphere Decoder Algorithm Rotated Signal Constellations
Applications of Lattices in Telecommunications Dept of Electrical and Computer Systems Engineering Monash University amin.sakzad@monash.edu Oct. 2013 1 Sphere Decoder Algorithm Rotated Signal Constellations
Error Exponent Region for Gaussian Broadcast Channels
 Error Exponent Region for Gaussian Broadcast Channels Lihua Weng, S. Sandeep Pradhan, and Achilleas Anastasopoulos Electrical Engineering and Computer Science Dept. University of Michigan, Ann Arbor, MI
Error Exponent Region for Gaussian Broadcast Channels Lihua Weng, S. Sandeep Pradhan, and Achilleas Anastasopoulos Electrical Engineering and Computer Science Dept. University of Michigan, Ann Arbor, MI
TRANSPORTATION PROBLEMS
 Chapter 6 TRANSPORTATION PROBLEMS 61 Transportation Model Transportation models deal with the determination of a minimum-cost plan for transporting a commodity from a number of sources to a number of destinations
Chapter 6 TRANSPORTATION PROBLEMS 61 Transportation Model Transportation models deal with the determination of a minimum-cost plan for transporting a commodity from a number of sources to a number of destinations
Lecture 7: Convex Optimizations
 Lecture 7: Convex Optimizations Radu Balan, David Levermore March 29, 2018 Convex Sets. Convex Functions A set S R n is called a convex set if for any points x, y S the line segment [x, y] := {tx + (1
Lecture 7: Convex Optimizations Radu Balan, David Levermore March 29, 2018 Convex Sets. Convex Functions A set S R n is called a convex set if for any points x, y S the line segment [x, y] := {tx + (1
4. Duality Duality 4.1 Duality of LPs and the duality theorem. min c T x x R n, c R n. s.t. ai Tx = b i i M a i R n
 2 4. Duality of LPs and the duality theorem... 22 4.2 Complementary slackness... 23 4.3 The shortest path problem and its dual... 24 4.4 Farkas' Lemma... 25 4.5 Dual information in the tableau... 26 4.6
2 4. Duality of LPs and the duality theorem... 22 4.2 Complementary slackness... 23 4.3 The shortest path problem and its dual... 24 4.4 Farkas' Lemma... 25 4.5 Dual information in the tableau... 26 4.6
 CS6304 / Analog and Digital Communication UNIT IV - SOURCE AND ERROR CONTROL CODING PART A 1. What is the use of error control coding? The main use of error control coding is to reduce the overall probability
CS6304 / Analog and Digital Communication UNIT IV - SOURCE AND ERROR CONTROL CODING PART A 1. What is the use of error control coding? The main use of error control coding is to reduce the overall probability
Chapter 2. Solving Systems of Equations. 2.1 Gaussian elimination
 Chapter 2 Solving Systems of Equations A large number of real life applications which are resolved through mathematical modeling will end up taking the form of the following very simple looking matrix
Chapter 2 Solving Systems of Equations A large number of real life applications which are resolved through mathematical modeling will end up taking the form of the following very simple looking matrix
Linear & nonlinear classifiers
 Linear & nonlinear classifiers Machine Learning Hamid Beigy Sharif University of Technology Fall 1394 Hamid Beigy (Sharif University of Technology) Linear & nonlinear classifiers Fall 1394 1 / 34 Table
Linear & nonlinear classifiers Machine Learning Hamid Beigy Sharif University of Technology Fall 1394 Hamid Beigy (Sharif University of Technology) Linear & nonlinear classifiers Fall 1394 1 / 34 Table
Binary Linear Codes G = = [ I 3 B ] , G 4 = None of these matrices are in standard form. Note that the matrix 1 0 0
![Binary Linear Codes G = = [ I 3 B ] , G 4 = None of these matrices are in standard form. Note that the matrix 1 0 0 Binary Linear Codes G = = [ I 3 B ] , G 4 = None of these matrices are in standard form. Note that the matrix 1 0 0](/thumbs/71/65851982.jpg) Coding Theory Massoud Malek Binary Linear Codes Generator and Parity-Check Matrices. A subset C of IK n is called a linear code, if C is a subspace of IK n (i.e., C is closed under addition). A linear
Coding Theory Massoud Malek Binary Linear Codes Generator and Parity-Check Matrices. A subset C of IK n is called a linear code, if C is a subspace of IK n (i.e., C is closed under addition). A linear
Math 273a: Optimization The Simplex method
 Math 273a: Optimization The Simplex method Instructor: Wotao Yin Department of Mathematics, UCLA Fall 2015 material taken from the textbook Chong-Zak, 4th Ed. Overview: idea and approach If a standard-form
Math 273a: Optimization The Simplex method Instructor: Wotao Yin Department of Mathematics, UCLA Fall 2015 material taken from the textbook Chong-Zak, 4th Ed. Overview: idea and approach If a standard-form
Delsarte s linear programming bound
 15-859 Coding Theory, Fall 14 December 5, 2014 Introduction For all n, q, and d, Delsarte s linear program establishes a series of linear constraints that every code in F n q with distance d must satisfy.
15-859 Coding Theory, Fall 14 December 5, 2014 Introduction For all n, q, and d, Delsarte s linear program establishes a series of linear constraints that every code in F n q with distance d must satisfy.
392D: Coding for the AWGN Channel Wednesday, January 24, 2007 Stanford, Winter 2007 Handout #6. Problem Set 2 Solutions
 392D: Coding for the AWGN Channel Wednesday, January 24, 2007 Stanford, Winter 2007 Handout #6 Problem Set 2 Solutions Problem 2.1 (Cartesian-product constellations) (a) Show that if A is a K-fold Cartesian
392D: Coding for the AWGN Channel Wednesday, January 24, 2007 Stanford, Winter 2007 Handout #6 Problem Set 2 Solutions Problem 2.1 (Cartesian-product constellations) (a) Show that if A is a K-fold Cartesian
Optimum Power Allocation in Fading MIMO Multiple Access Channels with Partial CSI at the Transmitters
 Optimum Power Allocation in Fading MIMO Multiple Access Channels with Partial CSI at the Transmitters Alkan Soysal Sennur Ulukus Department of Electrical and Computer Engineering University of Maryland,
Optimum Power Allocation in Fading MIMO Multiple Access Channels with Partial CSI at the Transmitters Alkan Soysal Sennur Ulukus Department of Electrical and Computer Engineering University of Maryland,
Graph-based codes for flash memory
 1/28 Graph-based codes for flash memory Discrete Mathematics Seminar September 3, 2013 Katie Haymaker Joint work with Professor Christine Kelley University of Nebraska-Lincoln 2/28 Outline 1 Background
1/28 Graph-based codes for flash memory Discrete Mathematics Seminar September 3, 2013 Katie Haymaker Joint work with Professor Christine Kelley University of Nebraska-Lincoln 2/28 Outline 1 Background
On the Duality of Gaussian Multiple-Access and Broadcast Channels
 On the Duality of Gaussian ultiple-access and Broadcast Channels Xiaowei Jin I. INTODUCTION Although T. Cover has been pointed out in [] that one would have expected a duality between the broadcast channel(bc)
On the Duality of Gaussian ultiple-access and Broadcast Channels Xiaowei Jin I. INTODUCTION Although T. Cover has been pointed out in [] that one would have expected a duality between the broadcast channel(bc)
15.083J/6.859J Integer Optimization. Lecture 10: Solving Relaxations
 15.083J/6.859J Integer Optimization Lecture 10: Solving Relaxations 1 Outline The key geometric result behind the ellipsoid method Slide 1 The ellipsoid method for the feasibility problem The ellipsoid
15.083J/6.859J Integer Optimization Lecture 10: Solving Relaxations 1 Outline The key geometric result behind the ellipsoid method Slide 1 The ellipsoid method for the feasibility problem The ellipsoid
Linear Codes, Target Function Classes, and Network Computing Capacity
 Linear Codes, Target Function Classes, and Network Computing Capacity Rathinakumar Appuswamy, Massimo Franceschetti, Nikhil Karamchandani, and Kenneth Zeger IEEE Transactions on Information Theory Submitted:
Linear Codes, Target Function Classes, and Network Computing Capacity Rathinakumar Appuswamy, Massimo Franceschetti, Nikhil Karamchandani, and Kenneth Zeger IEEE Transactions on Information Theory Submitted:
Optimal Power Control in Decentralized Gaussian Multiple Access Channels
 1 Optimal Power Control in Decentralized Gaussian Multiple Access Channels Kamal Singh Department of Electrical Engineering Indian Institute of Technology Bombay. arxiv:1711.08272v1 [eess.sp] 21 Nov 2017
1 Optimal Power Control in Decentralized Gaussian Multiple Access Channels Kamal Singh Department of Electrical Engineering Indian Institute of Technology Bombay. arxiv:1711.08272v1 [eess.sp] 21 Nov 2017
