Pacific Symposium on Biocomputing 6: (2001)
|
|
|
- Alfred Stevenson
- 6 years ago
- Views:
Transcription
1 Analyzing sensory systems with the information distortion function Alexander G Dimitrov and John P Miller Center for Computational Biology Montana State University Bozeman, MT falex,jpmg@nervana.montana.edu The nature and information content of neural signals have been discussed extensively in the neuroscience community. They are important ingredients in many theories on neural function, yet there is still no agreement on the details of neural coding. There have been various suggestions about how information is encoded in neural spike trains: by the number of spikes, by temporal correlations, through single spikes, or by spike patterns in one, or across many neurons. The latter scheme is most general and encompasses many others. We present an algorithm which can recover a coarse representation of a pattern coding scheme, through quantization to a reproduction set of smaller size. Among many possible quantizations, we choose one which preserves as much of the informativeness of the original stimulus/response relation as possible, through the use of an information-based distortion function. This method allows us to study coarse but highly informative models of a coding scheme, and then to refine them when more data becomes available. We shall describe a model in which full recovery is possible and present example for cases with partial recovery. 1 Introduction When discussing neural systems, one of the questions we are interested in is how the activity of a set of neurons represents the input to these neurons from other cells or from the environment. The nature and information content of neural signals have been discussed extensively in the neuroscience community. They are important ingredients in many theories on neural function, yet there is still no agreement on the details of neural coding. There have been various hypotheses about how information is encoded in neural spike trains: by the number of spikes, by temporal correlations between spikes, through single spikes, or by complete temporal patterns of spikes from a single neuron or groups of neurons 10. The latter scheme is most general and encompasses many others. The search for pattern codes requires exponentially more data than the search for mean rate or correlation codes 9. We will describe a method that allows us to uncover as much of the details of a coding scheme as is supported by the available data, by quantizing the set of responses to a smaller reproduction set of finite size. To assess the quality of the quantization we use an information-based distortion measure. The quantization is optimized to have minimal distortion for a fixed reproduction size. This method allows us to study coarse models of coding schemes which can be refined as more data becomes available.
2 2 Quantizing neural responses With communication systems, the usual use of information theory is to design a coding scheme given the structure of the communication channel. Our application differs since now we are analyzing an already implemented neural coding scheme (the cricket cercal system in particular 2;5 ). Our goal is to uncover the structure of the the scheme from observations of the stimulus and response properties of a neural system. 2.1 Quantizing the response The basic concepts of information theory are the entropy H(X) and the mutual information I(X,Y) of random sources (X; Y ) 12;1. The information quantities H and I depend only on the underlying probability function and not on the structure of the event space. This allows us to estimate them in cases where more traditional statistical measures (e.g., variance, correlations, etc.) simply do not exist. There is a drawback though, since now we must either model the necessary probabilities or use large amounts of data to estimate them nonparametrically. As pointed out by Johnson et.al. 9, the amount of data needed to support coding schemes which contain long sequences (length T) across multiple neurons (N) grows exponentially with T and N. It is conceivable that for some systems the required data recording time may well exceed the expected lifespan of the system. To resolve this issue we need to sacrifice some detail in the description of the coding scheme in order to obtain robust estimates of a coarser description. This can be achieved through quantization 1;7 of the neural representation Y into a coarser representation in a smaller event space Y N. Y N is referred to as the reproduction of Y. Most of the results in this section are valid for the general case of continuous, ergodic random variables 7. The formulation for the most general case requires special attention to details though. For clarity of the presentation here we shall assume that all random variables are finite and discrete. Quantizers are maps from one probability space to another. They can be deterministic (functions) or stochastic (given through a conditional probability) 11. We shall consider the most general case of a stochastic quantizer q(y N jy) the probability of a response y belonging to an abstract class y N. A deterministic quantizer f : Y! Y N is a special case in which q takes values 0 or 1 only. In both cases, stimulus, response and reproduction form a Markov chain X! Y! Y N. In information theory the quality of a quantization is characterized by a distortion function 6. We shall look for a minimum distortion quantization using an information distortion function and discuss its relationship to the codebook estimation problem.
3 2.2 A distortion measure based on mutual information In engineering applications, the distortion function is usually chosen in a moderately random fashion 1;6, and is the one that introduces structures in the original space, to be preserved by the quantization. We can avoid this arbitrariness since we expect that the neural system is already reflecting pertinent structures of the sensory stimuli and we would like to preserve this in the reproduction. Thus our choice of distortion function is determined by the informativeness of the quantization. The mutual information I(X; Y ) tells us how many different states on the average can be distinguished in X by observing Y. If we quantize Y to Y N (a reproduction with N elements), we can estimate I(X; Y N ) - the mutual information between X and the reproduction Y N. Our information preservation criterion will then require that we choose a quantizer that preserves as much of the mutual information as possible, i.e., the quantizer q(y N jy) which minimizes the difference D I (Y ; Y N )=I(X;Y) I(X;Y N ) (1) (note that D I 0). We use the functional D I as a measure of the average distortion of the quality of a quantization. It can be interpreted as an information distortion measure, hence the symbol D I. The only term that depends on the quantization is I(X; Y N ) so we can reformulate the problem as the maximization of the effective functional D ef f = I(X; Y N ). The average distortion can be rewritten as the expectation of a pointwise distortion function of a rather interesting form. Using the definition of the mutual information and the Markov relation X! Y! Y N between the spaces, we can express D I as the expectation where D I = E p(y;y N ) d(y; y N ) (2) d(y; y N ) KL(q(xjy)jjq(xjy N )) (3) is the Kullback-Leibler directed divergence of the input stimulus conditioned on a response y relative to the stimulus conditioned on a reproduction y N. Intuitively, this measures the similaritybetween the stimulus partition induced by the quantization to the one induced by the sensory system. 2.3 Implementations Using a quantization (deterministic or stochastic) of the output space 7 allows us to control the exponential growth of required data. With this approach we estimate a quantity which isknown to be a lower bound of the actual mutual information. We obtain a biased estimate but control the precision with which
4 it can be estimated. We fix the coarseness of the quantization ( the size of the reproduction, N) and look for a quantization that minimizes the information distortion measure D I = I(X; Y ) I(X; Y N ) described previously. Constrained maximum entropy optimization. The problem of optimal quantization has been formulated for a large class of distortion functions 11 as a maximum entropy problem 8. We cannot use this analysis directly, since in our case the distortion function depends explicitly on the quantizer. The reasoning behind the maximum entropy formulation is that, among all quantizers that satisfy a given set of constraints, the maximum entropy quantizer does not implicitly introduce further restrictions in the problem. We pose the minimum distortion problem as a maximum quantization entropy problem with a distortion constraint: max H(Y N jy ) constrained by (4) q(y N jy) X D I (q(y N jy))» D o and y N q(y N jy) =1 8y2Y This is an ordinary constrained optimization problem that can be solved numerically with standard optimization tools. The P cost function H(Y N jy )is concaveinq(y N jy), and the probability constraints y N q(y N jy) = 1 are linear in q(y N jy) 1. The constraint D I is also concave inq(y N jy), which make the whole problem one of concave maximization. The problem with this formulation is that it relies on knowing D I, which depends on the mutual information between X and Y. We can easily avoid the need for that by using the effective distortion D ef f I(X; Y N ). In this case, the optimization problem is max H(Y N jy ) constrained by (5) q(y N jy) X D ef f I(q(y N jy)) I o and y N q(y N jy) =1 8y2Y The solution to the optimization problem (5) depends on a single parameter I o, which can be interpreted as the informativeness of the quantization. If I o» 0, the distortion constraint is always satisfied and we obtain only the unconstrained maximum entropy solution q(y N jy) =1=N for all pairs (y; y N ). For I o 0 the distortion constraint becomes active and the uniform quantizer
5 is no longer a solution to the optimization problem. Because of the convexity of the problem, the optimal solution will lie on the boundary of the constraint and thus carry I(X; Y N )=I o bits of information. Maximum cost optimization. A standard approach to constrained optimization problems is through the use of Lagrange multipliers. The system (4) can be solved as the unconstrained optimization of y X max q(y N jy) H(Y N jy ) fid ef f (q(y N jy)) + X y y N q(y N jy) The solution depends on the parameters (fi;f y g) which can be found from the constraints X D ef f (q(y N jy)) I o q(y N jy) =18y2Y y N Since fi is a function of I o, which is a free parameter, we can as well discard I o and reformulate the optimization problem as finding the maximum of the cost function max F (q(y N jy)) q(y N jy) max q(y N jy) H(Y N jy )+fid ef f (q(y N jy)) constrained by Py N q(y N jy) =18y2Y: : (6) An implicit solution for the optimal quantizer. Further analysis of the problem uses the simplicity of the linear constraint in (6). Extrema of F can be found by setting its derivatives with respect to the quantizer q(y N jy) to zero. In the subsequent steps we shall explicitly use the assumption that all spaces are finite and discrete. The expressions are thus in a form convenient for programming on a computer. The results for continuous random variables can easily be adapted from this using analogous methods from the calculus of variations. We use Latin indices (i; j; k) to denote members in the original spaces X; Y and Greek indices (μ; ν; ) for elements of the reproduction Y N. With this in mind we solve the Lagrange multiplier problem q(y ν jy k )= (rdeff )νk efi p(y k ) Pν efi (rd eff ) νk p(y k ) : (7)
6 In practice, the expression (7) can be iterated for a fixed value of fi to obtain a solution for the optimization problem, starting from a particular initial state. For small fi, before the first bifurcation 11, the obvious initial condition is the uniform solution q(y N jy) =1=N. The solution for one fi can be used as the initial condition for a subsequent fi because solutions are continuous with respect to the quantizer. 3 Neural Information Processing We shall present a general model of a neural system which can be fully recovered by the quantization procedure described earlier. Sensory stimuli and their neural representation can be quite complex. Information theory suggests a way for dealing with this complexity by extracting the essential parts of the signal while maintaining most of its information content. The method of choice is through typical sequences. We can afford just a brief sketch of the model here. A more complete presentation can be found in an earlier paper Jointly Typical Sequences When analyzing information channels, we deal with two sets of random sequences input and output. In this case it is necessary to consider the combined behavior of the pair (X; Y ). In the current formalism this is achieved by using jointly typical sequences: x n and y n are independently typical and (x n ;y n ) is also typical in the product space 1. All the elements of the jointly typical set are nearly equiprobable, the set has probability close to 1, and the number of elements is about 2 nh(x;y ). Not all pairs of typical x n and typical y n are also jointly typical. The probability that a randomly chosen pair is jointly typical is about 2 ni (X ;Y ). Hence, for a fixed y n ni (X ;Y ), we can consider about 2 such pairs before we are likely to come across a jointly typical pair. This suggests there are about 2 ni (X ;Y ) distinguishable messages in X n that can be communicated through Y n (figure 1). 3.2 Decoding with jointly typical sequences The jointly typical pairs (x n ;y n ) can be used as codewords. Since there are 2 ni (X ;Y ) distinguishable signals and 2 nh(x;y ) codewords, some of the codewords represent the same signals. The redundancy helps to combat noise or is due to projections to a lower dimensional subspace. Sets of codewords representing the same signal form equivalence classes, which we call codeword classes. We shall equate the distinguishable signals with the codeword classes. Within each class, a stimulus in X n invokes a corresponding jointly typical response in Y n with high probability (about 1 2 ni (X ;Y ) ).
7 Figure 1: The structure of the jointly typical set. There are about 2nH (X ) typical x sequences, 2 nh (Y ) typical y sequences but only 2 nh (X;Y ) jointly typical sequences. This suggests there are about 2nI (X ;Y ) distinguishable equivalence classes C i of (x n ;y n ) pairs. The number of output sequences in each class is about jc i jß2 nh (Y jx ). We define the codebook of this system as the map F : x n! y n. The codebook is stochastic on individual elements, so it is better represented through association probabilities q(y n jx n ). When considered on codeword classes though, the map is almost bijective, that is, with probability close to 1 elements of Y n are assigned to an elements of X n in the same codeword class. We shall decode an output y n as (any of) the inputs that belong to the same codeword class. Similarly, we shall consider the representation of an input x n to be any ofthe outputs in the same codeword class. 3.3 Resolving the decoding problem The minimal information distortion quantization can help us resolve the neural decoding problem. We quantize the neural response by fixing the size of the reproduction to N. This bounds our estimate of D ef f to be no more than log N bits. In the ideal case, max D ef f max I(X; Y N ) ß log N but in general it will be lower. Due to the Markov relation, I(X; Y N )» I(X; Y )aswell. Since log N increases with N and I(X; Y ) is a constant, these two independent bounds intersect for some N = N c at which point adding more elements to Y N does not improve the distortion measure. If I(X; Y N ) increases with N until N = N c and then levels off, we can identify the correct N c by looking at the behavior of the expected distortion (or, equivalently, D ef f I(X; Y N )) as a function of N, given sufficient data. The elements of Y N are then representa-
8 tives of the original equivalence classes whichwewanted to find. The quantizer q(y N jy) gives the probability of a response y belonging to an equivalence class y N. As mentioned in 11, the optimal quantizer for low distortions (high fi) is deterministic (or effectively deterministic, in case of duplicate classes) and so we recover an almost complete reproduction of the model. If there is not enough data to support a complete recovery, the algorithm has to stop earlier. The criterion we use in such a case is that the estimate of D ef f does not change with N within its error bounds (obtained analytically or by statistical re-estimation methods like bootstrap, or jack-knife). Then N < N c and the quantized mutual information is at most log N. We can recover at most N classes and some of the original classes will be combined. The quantizer may also not be deterministic due to lack of enough data to resolve uncertainties. Thus we can recover a somewhat impoverished picture of the actual input/output relationship which can be refined as more data becomes available. 4 Results We shall discuss the application of the method described so far to a few test cases of synthetic data. Applying it to physiological data from a sensory system involves additional difficulties associated with the estimates of D I for complex input stimuli, which are dealt with elsewhere 4; Random Clusters We present the analysis of data drawn from the probability shown in figure 2a. This model was chosen to resemble the picture of decoding with jointly typical sequences (figure 1). The mutual information between the two sequences is about 1.8 bits, which is comparable to the mutual information of single neurons in the cricket cercal system 2. In this case we assume the original relation between X and Y is known (the joint probability p(x; y) is used explicitly). The results can be seen in figure 2b. The algorithm recovers an incomplete representation when two classes are forced (b.1). This is improved for the 3 class version (b.2). The next refinement (b.3) separates all the classes correctly and recovers most of the mutual information. Further refinements (b.4) fail to split the classes and are effectively identical to b.3 (note that classes 4 and 5 in b.4 are almost evenly populated and the class membership there is close to a uniform 1/2). The quantized mutual information (c) increases with the number of classes until it recovers about 90% of the original mutual information (N = 4) at which point itlevels off. The behavior of D ef f as a function of the annealing parameter fi is shown in figure 3. One can observe the bifurcations of the optimal solution (1 through 5) and the corresponding transitions of the effective distortion. The abrupt
9 Figure 2: A joint probability for the relation between two random variables X and Y with 52 elements each (a) with optimal quantizers q(y N jy) (b) for different number of classes. The behavior of the mutual information with increasing N can be seen in (c). Figure 3: Behavior of D eff (top) and the optimal quantizer q(y N jy) (bottom) as a function of the annealing parameter fi.
10 Figure 4: A joint probability for a linear relation between two random variables X and Y (a) with optimal quantization (b) for different number of classes. The behavior of the mutual information with increasing N can be seen in (c). transitions (1! 2, 2! 3) are similar to the ones described in 11 for an arbitrary distortion function. We also observe transitions (4! 5) which appear to be smooth in D ef f even though the solution for the optimal quantizer undergoes a bifurcation. A random permutation of the rows and columns of the joint probability in figure 2a has the same channel structure. The quantization is identical to the case presented in figure 2 after applying the inverse permutation and fully recovers the permuted classes (the quantization is contravariant with respect to the action of the permutation group). 4.2 Linear encoding We also applied the algorithm to a case which, unlike the previous cases, does not have clearly defined clusters. This model tries to simulate the process of a physical measurement where X is the physical system and Y is the measurement. In this example we model a linear relation between X and Y and Gaussian measurement noise, that is Y = kx + where 2N(0;ff) is drawn from a normal distribution with zero mean and variance ff 2. The particular relation we used (figure 4a) contains about 2 bits of mutual information. The results can be seen in figure 4. The algorithm recovers a series of representations (b.1 b.4), where each is a refinement of the previous one. The reproduction classes were permuted to roughly follow the original linear
11 relation. There isn't a natural stopping point and so the quantized mutual information I(X; Y N ) approaches a constant. This is in contrast to the previous two cases where I(X; Y N ) abruptly stopped changing after some N. 5 Conclusions We presented a method for recovering the structure of a neural coding scheme from observations. We choose to recover an impoverished description of the coding scheme by quantizing the responses to a reproduction set of a few variables. To assess the quality of the reproduction, we defined the information distortion D I = I(X; Y ) I(X; Y N ) which measures how much information is lost in the quantization process. For a fixed reproduction size N we pose the optimization problem of finding the quantization with smallest distortion, as the one which preserves most of the information present in the original relation between X and Y. Refining the reproduction by increasing N was shown to decrease the distortion. We showed empirically on a set of synthetic problems that, if the original relation contains almost disjoint clusters, a sufficiently fine optimal quantization recovers them completely. If the quantization is too coarse, then some of the clusters will be combined, but in such away that a large fraction of the original information is still preserved. It is interesting to note that, although we had neural systems in mind while developing the information distortion method, the ensuing analysis is in no way limited to nervous systems. Indeed, the constraints on the two signals we analyze are so general that they can represent almost any pair of interacting physical systems. In this case, finding a minimal information distortion reproduction allows us to recover certain aspects of the interaction between the two physical systems, which may improve considerably any subsequent analysis performed on them. It is also possible to analyze parts of the structure of a single physical system Y, if X is a system with known properties (e.g., a signal generator, controlled by a researcher) and is used to perturb Y. These cases point to the exciting possibility of obtaining a more automated approach for succinct descriptions of arbitrary physical systems through the use of minimal information distortion quantizers. Acknowledgments This research was supported in part by NIH grants MH12159 (AGD) and MH57179 (JPM). The authors are indebted to Penio Penev (Rockefeller U), Tomá»s Gedeon, Zane Aldworth and Kay Kirkpatrick (Montana State U) for numerous discussions which helped shape this paper.
12 References 1. T. Cover and J. Thomas. Elements of Information Theory. Wiley Series in Communication, New York, A. G. Dimitrov and J. P. Miller. Natural time scales for neural encoding. Neurocomputing, 32-33: , A. G. Dimitrov and J. P. Miller. Neural coding and decoding: joint typicality and quantization. Network: Computation in Neural Systems, submitted. 4. A. G. Dimitrov, J. P. Miller, and Z. Aldworth. The fine structure of neural codes. In preparation, A. G. Dimitrov, J. P. Miller, and Z. Aldworth. Non-uniform quantization of neural spike sequences through an information distortion measure. In J. Bower, editor, Computational Neuroscience: Trends in Research (to appear). 6. A. Gersho and R. M. Gray. Vector Quantization and Signal Compression. Kluwer Academic Publishers, R. M. Gray. Entropy and Information Theory. Springer-Verlag, E. T. Jaynes. On the rationale of maximum-entropy methods. Proc. IEEE, 70: , D. H. Johnson, C. M. Gruner, K. Baggerly, and C. Seshagiri. Information-theoretic analysis of the neural code. J. Comp. Neurosci., under review. 10. F. Rieke, D. Warland, R. R. de Ruyter van Steveninck, and W. Bialek. Spikes: Exploring the neural code. The MIT Press, K. Rose. Deteministic annealing for clustering, compression, classification, regerssion, and related optimization problems. Proceedings of the IEEE, 86(11): , C. E. Shannon. A mathematical theory of communication. Bell Sys. Tech. J., 27: , 1948.
Neural coding and decoding: communication channels and quantization
 INSTITUTE OF PHSICS PUBLISHING Network: Comput. Neural Syst. (00) 7 NETWORK: COMPUTATION IN NEURAL SSTEMS PII: S095-898X(0)5-8 Neural coding and decoding: communication channels and quantization Alexander
INSTITUTE OF PHSICS PUBLISHING Network: Comput. Neural Syst. (00) 7 NETWORK: COMPUTATION IN NEURAL SSTEMS PII: S095-898X(0)5-8 Neural coding and decoding: communication channels and quantization Alexander
Analysis of neural coding through quantization with an information-based distortion measure
 Submitted to: Network: Comput. Neural Syst. Analysis of neural coding through quantization with an information-based distortion measure Alexander G. Dimitrov, John P. Miller, Tomáš Gedeon, Zane Aldworth
Submitted to: Network: Comput. Neural Syst. Analysis of neural coding through quantization with an information-based distortion measure Alexander G. Dimitrov, John P. Miller, Tomáš Gedeon, Zane Aldworth
Estimation of information-theoretic quantities
 Estimation of information-theoretic quantities Liam Paninski Gatsby Computational Neuroscience Unit University College London http://www.gatsby.ucl.ac.uk/ liam liam@gatsby.ucl.ac.uk November 16, 2004 Some
Estimation of information-theoretic quantities Liam Paninski Gatsby Computational Neuroscience Unit University College London http://www.gatsby.ucl.ac.uk/ liam liam@gatsby.ucl.ac.uk November 16, 2004 Some
arxiv:physics/ v1 [physics.data-an] 24 Apr 2000 Naftali Tishby, 1,2 Fernando C. Pereira, 3 and William Bialek 1
![arxiv:physics/ v1 [physics.data-an] 24 Apr 2000 Naftali Tishby, 1,2 Fernando C. Pereira, 3 and William Bialek 1 arxiv:physics/ v1 [physics.data-an] 24 Apr 2000 Naftali Tishby, 1,2 Fernando C. Pereira, 3 and William Bialek 1](/thumbs/74/70237419.jpg) The information bottleneck method arxiv:physics/0004057v1 [physics.data-an] 24 Apr 2000 Naftali Tishby, 1,2 Fernando C. Pereira, 3 and William Bialek 1 1 NEC Research Institute, 4 Independence Way Princeton,
The information bottleneck method arxiv:physics/0004057v1 [physics.data-an] 24 Apr 2000 Naftali Tishby, 1,2 Fernando C. Pereira, 3 and William Bialek 1 1 NEC Research Institute, 4 Independence Way Princeton,
SYMMETRY BREAKING BIFURCATIONS OF THE INFORMATION DISTORTION. Albert Edward Parker III
 SYMMETRY BREAKING BIFURCATIONS OF THE INFORMATION DISTORTION by Albert Edward Parker III A dissertation submitted in partial fulfillment of the requirements for the degree of Doctor of Philosophy in Mathematics
SYMMETRY BREAKING BIFURCATIONS OF THE INFORMATION DISTORTION by Albert Edward Parker III A dissertation submitted in partial fulfillment of the requirements for the degree of Doctor of Philosophy in Mathematics
3. If a choice is broken down into two successive choices, the original H should be the weighted sum of the individual values of H.
 Appendix A Information Theory A.1 Entropy Shannon (Shanon, 1948) developed the concept of entropy to measure the uncertainty of a discrete random variable. Suppose X is a discrete random variable that
Appendix A Information Theory A.1 Entropy Shannon (Shanon, 1948) developed the concept of entropy to measure the uncertainty of a discrete random variable. Suppose X is a discrete random variable that
Information Theory. Mark van Rossum. January 24, School of Informatics, University of Edinburgh 1 / 35
 1 / 35 Information Theory Mark van Rossum School of Informatics, University of Edinburgh January 24, 2018 0 Version: January 24, 2018 Why information theory 2 / 35 Understanding the neural code. Encoding
1 / 35 Information Theory Mark van Rossum School of Informatics, University of Edinburgh January 24, 2018 0 Version: January 24, 2018 Why information theory 2 / 35 Understanding the neural code. Encoding
(Classical) Information Theory III: Noisy channel coding
 (Classical) Information Theory III: Noisy channel coding Sibasish Ghosh The Institute of Mathematical Sciences CIT Campus, Taramani, Chennai 600 113, India. p. 1 Abstract What is the best possible way
(Classical) Information Theory III: Noisy channel coding Sibasish Ghosh The Institute of Mathematical Sciences CIT Campus, Taramani, Chennai 600 113, India. p. 1 Abstract What is the best possible way
Chapter 4. Data Transmission and Channel Capacity. Po-Ning Chen, Professor. Department of Communications Engineering. National Chiao Tung University
 Chapter 4 Data Transmission and Channel Capacity Po-Ning Chen, Professor Department of Communications Engineering National Chiao Tung University Hsin Chu, Taiwan 30050, R.O.C. Principle of Data Transmission
Chapter 4 Data Transmission and Channel Capacity Po-Ning Chen, Professor Department of Communications Engineering National Chiao Tung University Hsin Chu, Taiwan 30050, R.O.C. Principle of Data Transmission
Neural coding Ecological approach to sensory coding: efficient adaptation to the natural environment
 Neural coding Ecological approach to sensory coding: efficient adaptation to the natural environment Jean-Pierre Nadal CNRS & EHESS Laboratoire de Physique Statistique (LPS, UMR 8550 CNRS - ENS UPMC Univ.
Neural coding Ecological approach to sensory coding: efficient adaptation to the natural environment Jean-Pierre Nadal CNRS & EHESS Laboratoire de Physique Statistique (LPS, UMR 8550 CNRS - ENS UPMC Univ.
Shannon s noisy-channel theorem
 Shannon s noisy-channel theorem Information theory Amon Elders Korteweg de Vries Institute for Mathematics University of Amsterdam. Tuesday, 26th of Januari Amon Elders (Korteweg de Vries Institute for
Shannon s noisy-channel theorem Information theory Amon Elders Korteweg de Vries Institute for Mathematics University of Amsterdam. Tuesday, 26th of Januari Amon Elders (Korteweg de Vries Institute for
Lecture 11: Continuous-valued signals and differential entropy
 Lecture 11: Continuous-valued signals and differential entropy Biology 429 Carl Bergstrom September 20, 2008 Sources: Parts of today s lecture follow Chapter 8 from Cover and Thomas (2007). Some components
Lecture 11: Continuous-valued signals and differential entropy Biology 429 Carl Bergstrom September 20, 2008 Sources: Parts of today s lecture follow Chapter 8 from Cover and Thomas (2007). Some components
ELEC546 Review of Information Theory
 ELEC546 Review of Information Theory Vincent Lau 1/1/004 1 Review of Information Theory Entropy: Measure of uncertainty of a random variable X. The entropy of X, H(X), is given by: If X is a discrete random
ELEC546 Review of Information Theory Vincent Lau 1/1/004 1 Review of Information Theory Entropy: Measure of uncertainty of a random variable X. The entropy of X, H(X), is given by: If X is a discrete random
EE368B Image and Video Compression
 EE368B Image and Video Compression Homework Set #2 due Friday, October 20, 2000, 9 a.m. Introduction The Lloyd-Max quantizer is a scalar quantizer which can be seen as a special case of a vector quantizer
EE368B Image and Video Compression Homework Set #2 due Friday, October 20, 2000, 9 a.m. Introduction The Lloyd-Max quantizer is a scalar quantizer which can be seen as a special case of a vector quantizer
Lecture 4 Noisy Channel Coding
 Lecture 4 Noisy Channel Coding I-Hsiang Wang Department of Electrical Engineering National Taiwan University ihwang@ntu.edu.tw October 9, 2015 1 / 56 I-Hsiang Wang IT Lecture 4 The Channel Coding Problem
Lecture 4 Noisy Channel Coding I-Hsiang Wang Department of Electrical Engineering National Taiwan University ihwang@ntu.edu.tw October 9, 2015 1 / 56 I-Hsiang Wang IT Lecture 4 The Channel Coding Problem
Superposition Encoding and Partial Decoding Is Optimal for a Class of Z-interference Channels
 Superposition Encoding and Partial Decoding Is Optimal for a Class of Z-interference Channels Nan Liu and Andrea Goldsmith Department of Electrical Engineering Stanford University, Stanford CA 94305 Email:
Superposition Encoding and Partial Decoding Is Optimal for a Class of Z-interference Channels Nan Liu and Andrea Goldsmith Department of Electrical Engineering Stanford University, Stanford CA 94305 Email:
+ + ( + ) = Linear recurrent networks. Simpler, much more amenable to analytic treatment E.g. by choosing
 Linear recurrent networks Simpler, much more amenable to analytic treatment E.g. by choosing + ( + ) = Firing rates can be negative Approximates dynamics around fixed point Approximation often reasonable
Linear recurrent networks Simpler, much more amenable to analytic treatment E.g. by choosing + ( + ) = Firing rates can be negative Approximates dynamics around fixed point Approximation often reasonable
Introduction to Information Theory. Uncertainty. Entropy. Surprisal. Joint entropy. Conditional entropy. Mutual information.
 L65 Dept. of Linguistics, Indiana University Fall 205 Information theory answers two fundamental questions in communication theory: What is the ultimate data compression? What is the transmission rate
L65 Dept. of Linguistics, Indiana University Fall 205 Information theory answers two fundamental questions in communication theory: What is the ultimate data compression? What is the transmission rate
Dept. of Linguistics, Indiana University Fall 2015
 L645 Dept. of Linguistics, Indiana University Fall 2015 1 / 28 Information theory answers two fundamental questions in communication theory: What is the ultimate data compression? What is the transmission
L645 Dept. of Linguistics, Indiana University Fall 2015 1 / 28 Information theory answers two fundamental questions in communication theory: What is the ultimate data compression? What is the transmission
Chapter 2 Review of Classical Information Theory
 Chapter 2 Review of Classical Information Theory Abstract This chapter presents a review of the classical information theory which plays a crucial role in this thesis. We introduce the various types of
Chapter 2 Review of Classical Information Theory Abstract This chapter presents a review of the classical information theory which plays a crucial role in this thesis. We introduce the various types of
Lecture 22: Final Review
 Lecture 22: Final Review Nuts and bolts Fundamental questions and limits Tools Practical algorithms Future topics Dr Yao Xie, ECE587, Information Theory, Duke University Basics Dr Yao Xie, ECE587, Information
Lecture 22: Final Review Nuts and bolts Fundamental questions and limits Tools Practical algorithms Future topics Dr Yao Xie, ECE587, Information Theory, Duke University Basics Dr Yao Xie, ECE587, Information
When does interval coding occur?
 When does interval coding occur? Don H. Johnson Λ and Raymon M. Glantz y Λ Department of Electrical & Computer Engineering, MS 366 y Department of Biochemistry and Cell Biology Rice University 6 Main Street
When does interval coding occur? Don H. Johnson Λ and Raymon M. Glantz y Λ Department of Electrical & Computer Engineering, MS 366 y Department of Biochemistry and Cell Biology Rice University 6 Main Street
Entropies & Information Theory
 Entropies & Information Theory LECTURE I Nilanjana Datta University of Cambridge,U.K. See lecture notes on: http://www.qi.damtp.cam.ac.uk/node/223 Quantum Information Theory Born out of Classical Information
Entropies & Information Theory LECTURE I Nilanjana Datta University of Cambridge,U.K. See lecture notes on: http://www.qi.damtp.cam.ac.uk/node/223 Quantum Information Theory Born out of Classical Information
Chapter 2: Entropy and Mutual Information. University of Illinois at Chicago ECE 534, Natasha Devroye
 Chapter 2: Entropy and Mutual Information Chapter 2 outline Definitions Entropy Joint entropy, conditional entropy Relative entropy, mutual information Chain rules Jensen s inequality Log-sum inequality
Chapter 2: Entropy and Mutual Information Chapter 2 outline Definitions Entropy Joint entropy, conditional entropy Relative entropy, mutual information Chain rules Jensen s inequality Log-sum inequality
EE 4TM4: Digital Communications II. Channel Capacity
 EE 4TM4: Digital Communications II 1 Channel Capacity I. CHANNEL CODING THEOREM Definition 1: A rater is said to be achievable if there exists a sequence of(2 nr,n) codes such thatlim n P (n) e (C) = 0.
EE 4TM4: Digital Communications II 1 Channel Capacity I. CHANNEL CODING THEOREM Definition 1: A rater is said to be achievable if there exists a sequence of(2 nr,n) codes such thatlim n P (n) e (C) = 0.
Block 2: Introduction to Information Theory
 Block 2: Introduction to Information Theory Francisco J. Escribano April 26, 2015 Francisco J. Escribano Block 2: Introduction to Information Theory April 26, 2015 1 / 51 Table of contents 1 Motivation
Block 2: Introduction to Information Theory Francisco J. Escribano April 26, 2015 Francisco J. Escribano Block 2: Introduction to Information Theory April 26, 2015 1 / 51 Table of contents 1 Motivation
DEEP LEARNING CHAPTER 3 PROBABILITY & INFORMATION THEORY
 DEEP LEARNING CHAPTER 3 PROBABILITY & INFORMATION THEORY OUTLINE 3.1 Why Probability? 3.2 Random Variables 3.3 Probability Distributions 3.4 Marginal Probability 3.5 Conditional Probability 3.6 The Chain
DEEP LEARNING CHAPTER 3 PROBABILITY & INFORMATION THEORY OUTLINE 3.1 Why Probability? 3.2 Random Variables 3.3 Probability Distributions 3.4 Marginal Probability 3.5 Conditional Probability 3.6 The Chain
Hands-On Learning Theory Fall 2016, Lecture 3
 Hands-On Learning Theory Fall 016, Lecture 3 Jean Honorio jhonorio@purdue.edu 1 Information Theory First, we provide some information theory background. Definition 3.1 (Entropy). The entropy of a discrete
Hands-On Learning Theory Fall 016, Lecture 3 Jean Honorio jhonorio@purdue.edu 1 Information Theory First, we provide some information theory background. Definition 3.1 (Entropy). The entropy of a discrete
Lecture 5 Channel Coding over Continuous Channels
 Lecture 5 Channel Coding over Continuous Channels I-Hsiang Wang Department of Electrical Engineering National Taiwan University ihwang@ntu.edu.tw November 14, 2014 1 / 34 I-Hsiang Wang NIT Lecture 5 From
Lecture 5 Channel Coding over Continuous Channels I-Hsiang Wang Department of Electrical Engineering National Taiwan University ihwang@ntu.edu.tw November 14, 2014 1 / 34 I-Hsiang Wang NIT Lecture 5 From
Information Theory CHAPTER. 5.1 Introduction. 5.2 Entropy
 Haykin_ch05_pp3.fm Page 207 Monday, November 26, 202 2:44 PM CHAPTER 5 Information Theory 5. Introduction As mentioned in Chapter and reiterated along the way, the purpose of a communication system is
Haykin_ch05_pp3.fm Page 207 Monday, November 26, 202 2:44 PM CHAPTER 5 Information Theory 5. Introduction As mentioned in Chapter and reiterated along the way, the purpose of a communication system is
Information Theory. Coding and Information Theory. Information Theory Textbooks. Entropy
 Coding and Information Theory Chris Williams, School of Informatics, University of Edinburgh Overview What is information theory? Entropy Coding Information Theory Shannon (1948): Information theory is
Coding and Information Theory Chris Williams, School of Informatics, University of Edinburgh Overview What is information theory? Entropy Coding Information Theory Shannon (1948): Information theory is
Lecture 6 I. CHANNEL CODING. X n (m) P Y X
 6- Introduction to Information Theory Lecture 6 Lecturer: Haim Permuter Scribe: Yoav Eisenberg and Yakov Miron I. CHANNEL CODING We consider the following channel coding problem: m = {,2,..,2 nr} Encoder
6- Introduction to Information Theory Lecture 6 Lecturer: Haim Permuter Scribe: Yoav Eisenberg and Yakov Miron I. CHANNEL CODING We consider the following channel coding problem: m = {,2,..,2 nr} Encoder
5 Mutual Information and Channel Capacity
 5 Mutual Information and Channel Capacity In Section 2, we have seen the use of a quantity called entropy to measure the amount of randomness in a random variable. In this section, we introduce several
5 Mutual Information and Channel Capacity In Section 2, we have seen the use of a quantity called entropy to measure the amount of randomness in a random variable. In this section, we introduce several
SOURCE CODING WITH SIDE INFORMATION AT THE DECODER (WYNER-ZIV CODING) FEB 13, 2003
 SOURCE CODING WITH SIDE INFORMATION AT THE DECODER (WYNER-ZIV CODING) FEB 13, 2003 SLEPIAN-WOLF RESULT { X i} RATE R x ENCODER 1 DECODER X i V i {, } { V i} ENCODER 0 RATE R v Problem: Determine R, the
SOURCE CODING WITH SIDE INFORMATION AT THE DECODER (WYNER-ZIV CODING) FEB 13, 2003 SLEPIAN-WOLF RESULT { X i} RATE R x ENCODER 1 DECODER X i V i {, } { V i} ENCODER 0 RATE R v Problem: Determine R, the
EE376A: Homework #3 Due by 11:59pm Saturday, February 10th, 2018
 Please submit the solutions on Gradescope. EE376A: Homework #3 Due by 11:59pm Saturday, February 10th, 2018 1. Optimal codeword lengths. Although the codeword lengths of an optimal variable length code
Please submit the solutions on Gradescope. EE376A: Homework #3 Due by 11:59pm Saturday, February 10th, 2018 1. Optimal codeword lengths. Although the codeword lengths of an optimal variable length code
Chapter 9 Fundamental Limits in Information Theory
 Chapter 9 Fundamental Limits in Information Theory Information Theory is the fundamental theory behind information manipulation, including data compression and data transmission. 9.1 Introduction o For
Chapter 9 Fundamental Limits in Information Theory Information Theory is the fundamental theory behind information manipulation, including data compression and data transmission. 9.1 Introduction o For
Information Theory, Statistics, and Decision Trees
 Information Theory, Statistics, and Decision Trees Léon Bottou COS 424 4/6/2010 Summary 1. Basic information theory. 2. Decision trees. 3. Information theory and statistics. Léon Bottou 2/31 COS 424 4/6/2010
Information Theory, Statistics, and Decision Trees Léon Bottou COS 424 4/6/2010 Summary 1. Basic information theory. 2. Decision trees. 3. Information theory and statistics. Léon Bottou 2/31 COS 424 4/6/2010
Lecture 15: Conditional and Joint Typicaility
 EE376A Information Theory Lecture 1-02/26/2015 Lecture 15: Conditional and Joint Typicaility Lecturer: Kartik Venkat Scribe: Max Zimet, Brian Wai, Sepehr Nezami 1 Notation We always write a sequence of
EE376A Information Theory Lecture 1-02/26/2015 Lecture 15: Conditional and Joint Typicaility Lecturer: Kartik Venkat Scribe: Max Zimet, Brian Wai, Sepehr Nezami 1 Notation We always write a sequence of
ECE 4400:693 - Information Theory
 ECE 4400:693 - Information Theory Dr. Nghi Tran Lecture 8: Differential Entropy Dr. Nghi Tran (ECE-University of Akron) ECE 4400:693 Lecture 1 / 43 Outline 1 Review: Entropy of discrete RVs 2 Differential
ECE 4400:693 - Information Theory Dr. Nghi Tran Lecture 8: Differential Entropy Dr. Nghi Tran (ECE-University of Akron) ECE 4400:693 Lecture 1 / 43 Outline 1 Review: Entropy of discrete RVs 2 Differential
Lecture 1: Introduction, Entropy and ML estimation
 0-704: Information Processing and Learning Spring 202 Lecture : Introduction, Entropy and ML estimation Lecturer: Aarti Singh Scribes: Min Xu Disclaimer: These notes have not been subjected to the usual
0-704: Information Processing and Learning Spring 202 Lecture : Introduction, Entropy and ML estimation Lecturer: Aarti Singh Scribes: Min Xu Disclaimer: These notes have not been subjected to the usual
Capacity of a channel Shannon s second theorem. Information Theory 1/33
 Capacity of a channel Shannon s second theorem Information Theory 1/33 Outline 1. Memoryless channels, examples ; 2. Capacity ; 3. Symmetric channels ; 4. Channel Coding ; 5. Shannon s second theorem,
Capacity of a channel Shannon s second theorem Information Theory 1/33 Outline 1. Memoryless channels, examples ; 2. Capacity ; 3. Symmetric channels ; 4. Channel Coding ; 5. Shannon s second theorem,
Generalized Writing on Dirty Paper
 Generalized Writing on Dirty Paper Aaron S. Cohen acohen@mit.edu MIT, 36-689 77 Massachusetts Ave. Cambridge, MA 02139-4307 Amos Lapidoth lapidoth@isi.ee.ethz.ch ETF E107 ETH-Zentrum CH-8092 Zürich, Switzerland
Generalized Writing on Dirty Paper Aaron S. Cohen acohen@mit.edu MIT, 36-689 77 Massachusetts Ave. Cambridge, MA 02139-4307 Amos Lapidoth lapidoth@isi.ee.ethz.ch ETF E107 ETH-Zentrum CH-8092 Zürich, Switzerland
Lecture 14 February 28
 EE/Stats 376A: Information Theory Winter 07 Lecture 4 February 8 Lecturer: David Tse Scribe: Sagnik M, Vivek B 4 Outline Gaussian channel and capacity Information measures for continuous random variables
EE/Stats 376A: Information Theory Winter 07 Lecture 4 February 8 Lecturer: David Tse Scribe: Sagnik M, Vivek B 4 Outline Gaussian channel and capacity Information measures for continuous random variables
The Method of Types and Its Application to Information Hiding
 The Method of Types and Its Application to Information Hiding Pierre Moulin University of Illinois at Urbana-Champaign www.ifp.uiuc.edu/ moulin/talks/eusipco05-slides.pdf EUSIPCO Antalya, September 7,
The Method of Types and Its Application to Information Hiding Pierre Moulin University of Illinois at Urbana-Champaign www.ifp.uiuc.edu/ moulin/talks/eusipco05-slides.pdf EUSIPCO Antalya, September 7,
CUSUM(t) D data. Supplementary Figure 1: Examples of changes in linear trend and CUSUM. (a) The existence of
 Supplementary Figures a b a(t) a(t) c t d t d(t) d(t) t t e f CUSUM(t) D data t CUSUM(t) D data t Supplementary Figure 1: Examples of changes in linear trend and CUSUM. (a) The existence of an abrupt jump
Supplementary Figures a b a(t) a(t) c t d t d(t) d(t) t t e f CUSUM(t) D data t CUSUM(t) D data t Supplementary Figure 1: Examples of changes in linear trend and CUSUM. (a) The existence of an abrupt jump
Lecture 2: August 31
 0-704: Information Processing and Learning Fall 206 Lecturer: Aarti Singh Lecture 2: August 3 Note: These notes are based on scribed notes from Spring5 offering of this course. LaTeX template courtesy
0-704: Information Processing and Learning Fall 206 Lecturer: Aarti Singh Lecture 2: August 3 Note: These notes are based on scribed notes from Spring5 offering of this course. LaTeX template courtesy
Lecture 5 - Information theory
 Lecture 5 - Information theory Jan Bouda FI MU May 18, 2012 Jan Bouda (FI MU) Lecture 5 - Information theory May 18, 2012 1 / 42 Part I Uncertainty and entropy Jan Bouda (FI MU) Lecture 5 - Information
Lecture 5 - Information theory Jan Bouda FI MU May 18, 2012 Jan Bouda (FI MU) Lecture 5 - Information theory May 18, 2012 1 / 42 Part I Uncertainty and entropy Jan Bouda (FI MU) Lecture 5 - Information
Computational Systems Biology: Biology X
 Bud Mishra Room 1002, 715 Broadway, Courant Institute, NYU, New York, USA L#8:(November-08-2010) Cancer and Signals Outline 1 Bayesian Interpretation of Probabilities Information Theory Outline Bayesian
Bud Mishra Room 1002, 715 Broadway, Courant Institute, NYU, New York, USA L#8:(November-08-2010) Cancer and Signals Outline 1 Bayesian Interpretation of Probabilities Information Theory Outline Bayesian
Bioinformatics: Biology X
 Bud Mishra Room 1002, 715 Broadway, Courant Institute, NYU, New York, USA Model Building/Checking, Reverse Engineering, Causality Outline 1 Bayesian Interpretation of Probabilities 2 Where (or of what)
Bud Mishra Room 1002, 715 Broadway, Courant Institute, NYU, New York, USA Model Building/Checking, Reverse Engineering, Causality Outline 1 Bayesian Interpretation of Probabilities 2 Where (or of what)
1 Introduction to information theory
 1 Introduction to information theory 1.1 Introduction In this chapter we present some of the basic concepts of information theory. The situations we have in mind involve the exchange of information through
1 Introduction to information theory 1.1 Introduction In this chapter we present some of the basic concepts of information theory. The situations we have in mind involve the exchange of information through
On Optimal Coding of Hidden Markov Sources
 2014 Data Compression Conference On Optimal Coding of Hidden Markov Sources Mehdi Salehifar, Emrah Akyol, Kumar Viswanatha, and Kenneth Rose Department of Electrical and Computer Engineering University
2014 Data Compression Conference On Optimal Coding of Hidden Markov Sources Mehdi Salehifar, Emrah Akyol, Kumar Viswanatha, and Kenneth Rose Department of Electrical and Computer Engineering University
arxiv: v1 [cs.it] 5 Sep 2008
![arxiv: v1 [cs.it] 5 Sep 2008 arxiv: v1 [cs.it] 5 Sep 2008](/thumbs/81/82638715.jpg) 1 arxiv:0809.1043v1 [cs.it] 5 Sep 2008 On Unique Decodability Marco Dalai, Riccardo Leonardi Abstract In this paper we propose a revisitation of the topic of unique decodability and of some fundamental
1 arxiv:0809.1043v1 [cs.it] 5 Sep 2008 On Unique Decodability Marco Dalai, Riccardo Leonardi Abstract In this paper we propose a revisitation of the topic of unique decodability and of some fundamental
Noisy-Channel Coding
 Copyright Cambridge University Press 2003. On-screen viewing permitted. Printing not permitted. http://www.cambridge.org/05264298 Part II Noisy-Channel Coding Copyright Cambridge University Press 2003.
Copyright Cambridge University Press 2003. On-screen viewing permitted. Printing not permitted. http://www.cambridge.org/05264298 Part II Noisy-Channel Coding Copyright Cambridge University Press 2003.
Information-theoretic foundations of differential privacy
 Information-theoretic foundations of differential privacy Darakhshan J. Mir Rutgers University, Piscataway NJ 08854, USA, mir@cs.rutgers.edu Abstract. We examine the information-theoretic foundations of
Information-theoretic foundations of differential privacy Darakhshan J. Mir Rutgers University, Piscataway NJ 08854, USA, mir@cs.rutgers.edu Abstract. We examine the information-theoretic foundations of
Soft-Output Trellis Waveform Coding
 Soft-Output Trellis Waveform Coding Tariq Haddad and Abbas Yongaçoḡlu School of Information Technology and Engineering, University of Ottawa Ottawa, Ontario, K1N 6N5, Canada Fax: +1 (613) 562 5175 thaddad@site.uottawa.ca
Soft-Output Trellis Waveform Coding Tariq Haddad and Abbas Yongaçoḡlu School of Information Technology and Engineering, University of Ottawa Ottawa, Ontario, K1N 6N5, Canada Fax: +1 (613) 562 5175 thaddad@site.uottawa.ca
Design of Optimal Quantizers for Distributed Source Coding
 Design of Optimal Quantizers for Distributed Source Coding David Rebollo-Monedero, Rui Zhang and Bernd Girod Information Systems Laboratory, Electrical Eng. Dept. Stanford University, Stanford, CA 94305
Design of Optimal Quantizers for Distributed Source Coding David Rebollo-Monedero, Rui Zhang and Bernd Girod Information Systems Laboratory, Electrical Eng. Dept. Stanford University, Stanford, CA 94305
Annealing and the Normalized N-Cut
 Annealing and the Normalized N-Cut Tomáš Gedeon a,1 Albert E. Parker a Collette Campion a a Department of Mathematical Sciences, Montana State University, Bozeman, MT 59715, USA Zane Aldworth b b Center
Annealing and the Normalized N-Cut Tomáš Gedeon a,1 Albert E. Parker a Collette Campion a a Department of Mathematical Sciences, Montana State University, Bozeman, MT 59715, USA Zane Aldworth b b Center
Encoding or decoding
 Encoding or decoding Decoding How well can we learn what the stimulus is by looking at the neural responses? We will discuss two approaches: devise and evaluate explicit algorithms for extracting a stimulus
Encoding or decoding Decoding How well can we learn what the stimulus is by looking at the neural responses? We will discuss two approaches: devise and evaluate explicit algorithms for extracting a stimulus
Information Theory in Intelligent Decision Making
 Information Theory in Intelligent Decision Making Adaptive Systems and Algorithms Research Groups School of Computer Science University of Hertfordshire, United Kingdom June 7, 2015 Information Theory
Information Theory in Intelligent Decision Making Adaptive Systems and Algorithms Research Groups School of Computer Science University of Hertfordshire, United Kingdom June 7, 2015 Information Theory
Lecture 3: Channel Capacity
 Lecture 3: Channel Capacity 1 Definitions Channel capacity is a measure of maximum information per channel usage one can get through a channel. This one of the fundamental concepts in information theory.
Lecture 3: Channel Capacity 1 Definitions Channel capacity is a measure of maximum information per channel usage one can get through a channel. This one of the fundamental concepts in information theory.
 CS6304 / Analog and Digital Communication UNIT IV - SOURCE AND ERROR CONTROL CODING PART A 1. What is the use of error control coding? The main use of error control coding is to reduce the overall probability
CS6304 / Analog and Digital Communication UNIT IV - SOURCE AND ERROR CONTROL CODING PART A 1. What is the use of error control coding? The main use of error control coding is to reduce the overall probability
Scalar and Vector Quantization. National Chiao Tung University Chun-Jen Tsai 11/06/2014
 Scalar and Vector Quantization National Chiao Tung University Chun-Jen Tsai 11/06/014 Basic Concept of Quantization Quantization is the process of representing a large, possibly infinite, set of values
Scalar and Vector Quantization National Chiao Tung University Chun-Jen Tsai 11/06/014 Basic Concept of Quantization Quantization is the process of representing a large, possibly infinite, set of values
Constellation Shaping for Communication Channels with Quantized Outputs
 Constellation Shaping for Communication Channels with Quantized Outputs Chandana Nannapaneni, Matthew C. Valenti, and Xingyu Xiang Lane Department of Computer Science and Electrical Engineering West Virginia
Constellation Shaping for Communication Channels with Quantized Outputs Chandana Nannapaneni, Matthew C. Valenti, and Xingyu Xiang Lane Department of Computer Science and Electrical Engineering West Virginia
Notes 3: Stochastic channels and noisy coding theorem bound. 1 Model of information communication and noisy channel
 Introduction to Coding Theory CMU: Spring 2010 Notes 3: Stochastic channels and noisy coding theorem bound January 2010 Lecturer: Venkatesan Guruswami Scribe: Venkatesan Guruswami We now turn to the basic
Introduction to Coding Theory CMU: Spring 2010 Notes 3: Stochastic channels and noisy coding theorem bound January 2010 Lecturer: Venkatesan Guruswami Scribe: Venkatesan Guruswami We now turn to the basic
On Scalable Coding in the Presence of Decoder Side Information
 On Scalable Coding in the Presence of Decoder Side Information Emrah Akyol, Urbashi Mitra Dep. of Electrical Eng. USC, CA, US Email: {eakyol, ubli}@usc.edu Ertem Tuncel Dep. of Electrical Eng. UC Riverside,
On Scalable Coding in the Presence of Decoder Side Information Emrah Akyol, Urbashi Mitra Dep. of Electrical Eng. USC, CA, US Email: {eakyol, ubli}@usc.edu Ertem Tuncel Dep. of Electrical Eng. UC Riverside,
DATA MINING LECTURE 9. Minimum Description Length Information Theory Co-Clustering
 DATA MINING LECTURE 9 Minimum Description Length Information Theory Co-Clustering MINIMUM DESCRIPTION LENGTH Occam s razor Most data mining tasks can be described as creating a model for the data E.g.,
DATA MINING LECTURE 9 Minimum Description Length Information Theory Co-Clustering MINIMUM DESCRIPTION LENGTH Occam s razor Most data mining tasks can be described as creating a model for the data E.g.,
g(x,y) = c. For instance (see Figure 1 on the right), consider the optimization problem maximize subject to
 1 of 11 11/29/2010 10:39 AM From Wikipedia, the free encyclopedia In mathematical optimization, the method of Lagrange multipliers (named after Joseph Louis Lagrange) provides a strategy for finding the
1 of 11 11/29/2010 10:39 AM From Wikipedia, the free encyclopedia In mathematical optimization, the method of Lagrange multipliers (named after Joseph Louis Lagrange) provides a strategy for finding the
Lecture 2. Capacity of the Gaussian channel
 Spring, 207 5237S, Wireless Communications II 2. Lecture 2 Capacity of the Gaussian channel Review on basic concepts in inf. theory ( Cover&Thomas: Elements of Inf. Theory, Tse&Viswanath: Appendix B) AWGN
Spring, 207 5237S, Wireless Communications II 2. Lecture 2 Capacity of the Gaussian channel Review on basic concepts in inf. theory ( Cover&Thomas: Elements of Inf. Theory, Tse&Viswanath: Appendix B) AWGN
Upper Bounds on the Capacity of Binary Intermittent Communication
 Upper Bounds on the Capacity of Binary Intermittent Communication Mostafa Khoshnevisan and J. Nicholas Laneman Department of Electrical Engineering University of Notre Dame Notre Dame, Indiana 46556 Email:{mhoshne,
Upper Bounds on the Capacity of Binary Intermittent Communication Mostafa Khoshnevisan and J. Nicholas Laneman Department of Electrical Engineering University of Notre Dame Notre Dame, Indiana 46556 Email:{mhoshne,
An instantaneous code (prefix code, tree code) with the codeword lengths l 1,..., l N exists if and only if. 2 l i. i=1
 Kraft s inequality An instantaneous code (prefix code, tree code) with the codeword lengths l 1,..., l N exists if and only if N 2 l i 1 Proof: Suppose that we have a tree code. Let l max = max{l 1,...,
Kraft s inequality An instantaneous code (prefix code, tree code) with the codeword lengths l 1,..., l N exists if and only if N 2 l i 1 Proof: Suppose that we have a tree code. Let l max = max{l 1,...,
Capacity of the Discrete Memoryless Energy Harvesting Channel with Side Information
 204 IEEE International Symposium on Information Theory Capacity of the Discrete Memoryless Energy Harvesting Channel with Side Information Omur Ozel, Kaya Tutuncuoglu 2, Sennur Ulukus, and Aylin Yener
204 IEEE International Symposium on Information Theory Capacity of the Discrete Memoryless Energy Harvesting Channel with Side Information Omur Ozel, Kaya Tutuncuoglu 2, Sennur Ulukus, and Aylin Yener
Kyle Reing University of Southern California April 18, 2018
 Renormalization Group and Information Theory Kyle Reing University of Southern California April 18, 2018 Overview Renormalization Group Overview Information Theoretic Preliminaries Real Space Mutual Information
Renormalization Group and Information Theory Kyle Reing University of Southern California April 18, 2018 Overview Renormalization Group Overview Information Theoretic Preliminaries Real Space Mutual Information
FuncICA for time series pattern discovery
 FuncICA for time series pattern discovery Nishant Mehta and Alexander Gray Georgia Institute of Technology The problem Given a set of inherently continuous time series (e.g. EEG) Find a set of patterns
FuncICA for time series pattern discovery Nishant Mehta and Alexander Gray Georgia Institute of Technology The problem Given a set of inherently continuous time series (e.g. EEG) Find a set of patterns
Efficient Coding. Odelia Schwartz 2017
 Efficient Coding Odelia Schwartz 2017 1 Levels of modeling Descriptive (what) Mechanistic (how) Interpretive (why) 2 Levels of modeling Fitting a receptive field model to experimental data (e.g., using
Efficient Coding Odelia Schwartz 2017 1 Levels of modeling Descriptive (what) Mechanistic (how) Interpretive (why) 2 Levels of modeling Fitting a receptive field model to experimental data (e.g., using
Lecture 8: Channel and source-channel coding theorems; BEC & linear codes. 1 Intuitive justification for upper bound on channel capacity
 5-859: Information Theory and Applications in TCS CMU: Spring 23 Lecture 8: Channel and source-channel coding theorems; BEC & linear codes February 7, 23 Lecturer: Venkatesan Guruswami Scribe: Dan Stahlke
5-859: Information Theory and Applications in TCS CMU: Spring 23 Lecture 8: Channel and source-channel coding theorems; BEC & linear codes February 7, 23 Lecturer: Venkatesan Guruswami Scribe: Dan Stahlke
the Information Bottleneck
 the Information Bottleneck Daniel Moyer December 10, 2017 Imaging Genetics Center/Information Science Institute University of Southern California Sorry, no Neuroimaging! (at least not presented) 0 Instead,
the Information Bottleneck Daniel Moyer December 10, 2017 Imaging Genetics Center/Information Science Institute University of Southern California Sorry, no Neuroimaging! (at least not presented) 0 Instead,
Capacity of AWGN channels
 Chapter 3 Capacity of AWGN channels In this chapter we prove that the capacity of an AWGN channel with bandwidth W and signal-tonoise ratio SNR is W log 2 (1+SNR) bits per second (b/s). The proof that
Chapter 3 Capacity of AWGN channels In this chapter we prove that the capacity of an AWGN channel with bandwidth W and signal-tonoise ratio SNR is W log 2 (1+SNR) bits per second (b/s). The proof that
Machine Learning Srihari. Information Theory. Sargur N. Srihari
 Information Theory Sargur N. Srihari 1 Topics 1. Entropy as an Information Measure 1. Discrete variable definition Relationship to Code Length 2. Continuous Variable Differential Entropy 2. Maximum Entropy
Information Theory Sargur N. Srihari 1 Topics 1. Entropy as an Information Measure 1. Discrete variable definition Relationship to Code Length 2. Continuous Variable Differential Entropy 2. Maximum Entropy
Membrane equation. VCl. dv dt + V = V Na G Na + V K G K + V Cl G Cl. G total. C m. G total = G Na + G K + G Cl
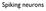 Spiking neurons Membrane equation V GNa GK GCl Cm VNa VK VCl dv dt + V = V Na G Na + V K G K + V Cl G Cl G total G total = G Na + G K + G Cl = C m G total Membrane with synaptic inputs V Gleak GNa GK
Spiking neurons Membrane equation V GNa GK GCl Cm VNa VK VCl dv dt + V = V Na G Na + V K G K + V Cl G Cl G total G total = G Na + G K + G Cl = C m G total Membrane with synaptic inputs V Gleak GNa GK
18.2 Continuous Alphabet (discrete-time, memoryless) Channel
 0-704: Information Processing and Learning Spring 0 Lecture 8: Gaussian channel, Parallel channels and Rate-distortion theory Lecturer: Aarti Singh Scribe: Danai Koutra Disclaimer: These notes have not
0-704: Information Processing and Learning Spring 0 Lecture 8: Gaussian channel, Parallel channels and Rate-distortion theory Lecturer: Aarti Singh Scribe: Danai Koutra Disclaimer: These notes have not
Encoder Decoder Design for Feedback Control over the Binary Symmetric Channel
 Encoder Decoder Design for Feedback Control over the Binary Symmetric Channel Lei Bao, Mikael Skoglund and Karl Henrik Johansson School of Electrical Engineering, Royal Institute of Technology, Stockholm,
Encoder Decoder Design for Feedback Control over the Binary Symmetric Channel Lei Bao, Mikael Skoglund and Karl Henrik Johansson School of Electrical Engineering, Royal Institute of Technology, Stockholm,
A COLLABORATIVE 20 QUESTIONS MODEL FOR TARGET SEARCH WITH HUMAN-MACHINE INTERACTION
 A COLLABORATIVE 20 QUESTIONS MODEL FOR TARGET SEARCH WITH HUMAN-MACHINE INTERACTION Theodoros Tsiligkaridis, Brian M Sadler and Alfred O Hero III, University of Michigan, EECS Dept and Dept Statistics,
A COLLABORATIVE 20 QUESTIONS MODEL FOR TARGET SEARCH WITH HUMAN-MACHINE INTERACTION Theodoros Tsiligkaridis, Brian M Sadler and Alfred O Hero III, University of Michigan, EECS Dept and Dept Statistics,
Solutions to Homework Set #1 Sanov s Theorem, Rate distortion
 st Semester 00/ Solutions to Homework Set # Sanov s Theorem, Rate distortion. Sanov s theorem: Prove the simple version of Sanov s theorem for the binary random variables, i.e., let X,X,...,X n be a sequence
st Semester 00/ Solutions to Homework Set # Sanov s Theorem, Rate distortion. Sanov s theorem: Prove the simple version of Sanov s theorem for the binary random variables, i.e., let X,X,...,X n be a sequence
Entropy and Ergodic Theory Lecture 4: Conditional entropy and mutual information
 Entropy and Ergodic Theory Lecture 4: Conditional entropy and mutual information 1 Conditional entropy Let (Ω, F, P) be a probability space, let X be a RV taking values in some finite set A. In this lecture
Entropy and Ergodic Theory Lecture 4: Conditional entropy and mutual information 1 Conditional entropy Let (Ω, F, P) be a probability space, let X be a RV taking values in some finite set A. In this lecture
4F5: Advanced Communications and Coding Handout 2: The Typical Set, Compression, Mutual Information
 4F5: Advanced Communications and Coding Handout 2: The Typical Set, Compression, Mutual Information Ramji Venkataramanan Signal Processing and Communications Lab Department of Engineering ramji.v@eng.cam.ac.uk
4F5: Advanced Communications and Coding Handout 2: The Typical Set, Compression, Mutual Information Ramji Venkataramanan Signal Processing and Communications Lab Department of Engineering ramji.v@eng.cam.ac.uk
Gaussian processes. Chuong B. Do (updated by Honglak Lee) November 22, 2008
 Gaussian processes Chuong B Do (updated by Honglak Lee) November 22, 2008 Many of the classical machine learning algorithms that we talked about during the first half of this course fit the following pattern:
Gaussian processes Chuong B Do (updated by Honglak Lee) November 22, 2008 Many of the classical machine learning algorithms that we talked about during the first half of this course fit the following pattern:
Shannon s Noisy-Channel Coding Theorem
 Shannon s Noisy-Channel Coding Theorem Lucas Slot Sebastian Zur February 13, 2015 Lucas Slot, Sebastian Zur Shannon s Noisy-Channel Coding Theorem February 13, 2015 1 / 29 Outline 1 Definitions and Terminology
Shannon s Noisy-Channel Coding Theorem Lucas Slot Sebastian Zur February 13, 2015 Lucas Slot, Sebastian Zur Shannon s Noisy-Channel Coding Theorem February 13, 2015 1 / 29 Outline 1 Definitions and Terminology
CS 630 Basic Probability and Information Theory. Tim Campbell
 CS 630 Basic Probability and Information Theory Tim Campbell 21 January 2003 Probability Theory Probability Theory is the study of how best to predict outcomes of events. An experiment (or trial or event)
CS 630 Basic Probability and Information Theory Tim Campbell 21 January 2003 Probability Theory Probability Theory is the study of how best to predict outcomes of events. An experiment (or trial or event)
TWO METHODS FOR ESTIMATING OVERCOMPLETE INDEPENDENT COMPONENT BASES. Mika Inki and Aapo Hyvärinen
 TWO METHODS FOR ESTIMATING OVERCOMPLETE INDEPENDENT COMPONENT BASES Mika Inki and Aapo Hyvärinen Neural Networks Research Centre Helsinki University of Technology P.O. Box 54, FIN-215 HUT, Finland ABSTRACT
TWO METHODS FOR ESTIMATING OVERCOMPLETE INDEPENDENT COMPONENT BASES Mika Inki and Aapo Hyvärinen Neural Networks Research Centre Helsinki University of Technology P.O. Box 54, FIN-215 HUT, Finland ABSTRACT
EE376A: Homework #2 Solutions Due by 11:59pm Thursday, February 1st, 2018
 Please submit the solutions on Gradescope. Some definitions that may be useful: EE376A: Homework #2 Solutions Due by 11:59pm Thursday, February 1st, 2018 Definition 1: A sequence of random variables X
Please submit the solutions on Gradescope. Some definitions that may be useful: EE376A: Homework #2 Solutions Due by 11:59pm Thursday, February 1st, 2018 Definition 1: A sequence of random variables X
Lecture 6: Gaussian Channels. Copyright G. Caire (Sample Lectures) 157
 Lecture 6: Gaussian Channels Copyright G. Caire (Sample Lectures) 157 Differential entropy (1) Definition 18. The (joint) differential entropy of a continuous random vector X n p X n(x) over R is: Z h(x
Lecture 6: Gaussian Channels Copyright G. Caire (Sample Lectures) 157 Differential entropy (1) Definition 18. The (joint) differential entropy of a continuous random vector X n p X n(x) over R is: Z h(x
Linear Regression and Its Applications
 Linear Regression and Its Applications Predrag Radivojac October 13, 2014 Given a data set D = {(x i, y i )} n the objective is to learn the relationship between features and the target. We usually start
Linear Regression and Its Applications Predrag Radivojac October 13, 2014 Given a data set D = {(x i, y i )} n the objective is to learn the relationship between features and the target. We usually start
Chapter 11. Stochastic Methods Rooted in Statistical Mechanics
 Chapter 11. Stochastic Methods Rooted in Statistical Mechanics Neural Networks and Learning Machines (Haykin) Lecture Notes on Self-learning Neural Algorithms Byoung-Tak Zhang School of Computer Science
Chapter 11. Stochastic Methods Rooted in Statistical Mechanics Neural Networks and Learning Machines (Haykin) Lecture Notes on Self-learning Neural Algorithms Byoung-Tak Zhang School of Computer Science
Shannon s Noisy-Channel Coding Theorem
 Shannon s Noisy-Channel Coding Theorem Lucas Slot Sebastian Zur February 2015 Abstract In information theory, Shannon s Noisy-Channel Coding Theorem states that it is possible to communicate over a noisy
Shannon s Noisy-Channel Coding Theorem Lucas Slot Sebastian Zur February 2015 Abstract In information theory, Shannon s Noisy-Channel Coding Theorem states that it is possible to communicate over a noisy
The memory centre IMUJ PREPRINT 2012/03. P. Spurek
 The memory centre IMUJ PREPRINT 202/03 P. Spurek Faculty of Mathematics and Computer Science, Jagiellonian University, Łojasiewicza 6, 30-348 Kraków, Poland J. Tabor Faculty of Mathematics and Computer
The memory centre IMUJ PREPRINT 202/03 P. Spurek Faculty of Mathematics and Computer Science, Jagiellonian University, Łojasiewicza 6, 30-348 Kraków, Poland J. Tabor Faculty of Mathematics and Computer
Information Theory Primer:
 Information Theory Primer: Entropy, KL Divergence, Mutual Information, Jensen s inequality Seungjin Choi Department of Computer Science and Engineering Pohang University of Science and Technology 77 Cheongam-ro,
Information Theory Primer: Entropy, KL Divergence, Mutual Information, Jensen s inequality Seungjin Choi Department of Computer Science and Engineering Pohang University of Science and Technology 77 Cheongam-ro,
QUANTIZATION FOR DISTRIBUTED ESTIMATION IN LARGE SCALE SENSOR NETWORKS
 QUANTIZATION FOR DISTRIBUTED ESTIMATION IN LARGE SCALE SENSOR NETWORKS Parvathinathan Venkitasubramaniam, Gökhan Mergen, Lang Tong and Ananthram Swami ABSTRACT We study the problem of quantization for
QUANTIZATION FOR DISTRIBUTED ESTIMATION IN LARGE SCALE SENSOR NETWORKS Parvathinathan Venkitasubramaniam, Gökhan Mergen, Lang Tong and Ananthram Swami ABSTRACT We study the problem of quantization for
Introduction to Information Theory
 Introduction to Information Theory Gurinder Singh Mickey Atwal atwal@cshl.edu Center for Quantitative Biology Kullback-Leibler Divergence Summary Shannon s coding theorems Entropy Mutual Information Multi-information
Introduction to Information Theory Gurinder Singh Mickey Atwal atwal@cshl.edu Center for Quantitative Biology Kullback-Leibler Divergence Summary Shannon s coding theorems Entropy Mutual Information Multi-information
The binary entropy function
 ECE 7680 Lecture 2 Definitions and Basic Facts Objective: To learn a bunch of definitions about entropy and information measures that will be useful through the quarter, and to present some simple but
ECE 7680 Lecture 2 Definitions and Basic Facts Objective: To learn a bunch of definitions about entropy and information measures that will be useful through the quarter, and to present some simple but
Information maximization in a network of linear neurons
 Information maximization in a network of linear neurons Holger Arnold May 30, 005 1 Introduction It is known since the work of Hubel and Wiesel [3], that many cells in the early visual areas of mammals
Information maximization in a network of linear neurons Holger Arnold May 30, 005 1 Introduction It is known since the work of Hubel and Wiesel [3], that many cells in the early visual areas of mammals
