Theory of Additive Cellular Automata
|
|
|
- Garey Lynch
- 6 years ago
- Views:
Transcription
1 Fundamenta Informaticae XXI (200) IOS Press Theory of Additive Cellular Automata Niloy Ganguly Department of Computer Science and Engineering, Indian Institute of Technology, Waragpur, India Biplab K Sikdar Department of Computer Science & Technology, Bengal Engineering College (DU), Botanic Garden, Howrah,West Bengal, India P Pal Chaudhuri Flat E4, Block H30, BP Township, Calcutta India. Abstract. This paper reports the complete characterization of additive cellular automata (ACA) that employ xor and xnor logic as the next state function. Compared to linear cellular automata (LCA) [3], which employs only xor logic in its next state function, an ACA display much wider varieties of state transition behavior and enhanced computing power. An analytical framework is developed to characterize the cyclic vector subspaces generated by an ACA with reference to LCA. It identifies the conditions on which the state transition behavior of an ACA differs from that of the corresponding LCA and also provides the theoretical analysis of the nature of difference. I. Introduction This work develops the theory of additive cellular automata (ACA). The theoretical framework proposed, provides the complete characterization of the cyclic state space generated by an ACA. An ACA is additive in the sense that it employs affine (also referred to as additive) transformation rather than a linear transformation implemented in a typical linear cellular automata (LCA). The theory of LCA provides the foundation of the proposed characterization of ACA. ACA which employ xor and xnor logic to generate its next state function has been specially popular among researchers. Both ACA and its subset LCA (which employ only xor logic) have been used to develop a lot of applications in V LSI and related fields. They have been used to develop pseudo-random Address for correspondence: Department of Computer Science and Engineering, Indian Institute of Technology, Kharagpur, India 72302
2 002 N. Ganguly, B. K. Sikdar, P. P. Chaudhuri / Theory of Additive Cellular Automata test pattern generators [8, 9], signature analyzers [6], finite state machines F SM [], error correcting codes [5] etc. Moreover, researchers have designed CA based cipher system[5], message authenticators [9], CA based pattern classifier [] with the help of ACA. In the process of developing the applications, there has been several works to characterize the state transition behavior of both LCA and ACA. The analysis of linear CA, has been extensively investigated by Stone [2] as part of the exploration of linear machine. Vector space theoretic analysis of state transition behavior of this class of CA has been reported by Das [8] and subsequently by a number of researchers [3, 6, ]. The partial characterization of ACA, that employs both the xor and xnor logic in its next state function, has been introduced in [3, 5]. However, complete characterization of the cyclic state space generated by such a CA remains untouched. In this background, this paper reports a complete vector space theoretic analysis of ACA. We develop an elegant solution to derive its cycle structure from analysis of the given rules, defining the ACA. An ACA can have both the cyclic and non-cyclic state space. However, in the current work, we only consider the characterization of cyclic state space as the non-cyclic subspace generated by an ACA is isomorphic to that of LCA [3]. We next provide a brief introduction to additive CA along with some important results on linear CA that are relevant for the characterization of ACA in section III. The vector space theoretic analysis targeting complete characterization of ACA, is reported in section III. II. Cellular Automata Characterization Cellular Automata (CA) consist of a number of interconnected cells arranged spatially in a regular manner. In most general case, a CA cell can exhibit s different states and the next state of each cell depends on the present states of its k neighbors including itself. Such a CA is called an s-state k-neighborhood CA. However, Wolfram [2] worked with several features of finite CA known as 3-neighborhood (left, right and self) CA having 2 states for each cell. The state (next state) q {0,} of the i th cell at time (t + ) is denoted as qi t+ = f i (qi t,qt i,qt i+ ), where qi t denotes the state of the ith cell at time t and f i is the next state function called the rule of the automata [22]. Since f is a function of 3 variables, there are 2 23 or 256 possible next state functions. The structure of a 3-neighborhood CA cell is shown in Fig.. Out of total 256 CA rules, 4 rules that can be realized by xor/xnor logic are called additive rules [3]. A CA designed with such rules are called additive CA (ACA). The ACA has been of special interest to researchers, as it can be characterized by matrix algebraic tools. Matrix algebraic tools are used to represent ACA that uses different rules in different cells. In the current work, we concentrate on characterizing such hybrid CA. A brief overview of this model is next outlined [3]. An n-cell -dimensional ACA is characterized by a linear operator [T] n n matrix and an n-dimensional inversion vector F. T is the characteristic matrix of the cellular automata. The i th row of T corresponds to the neighborhood relation of the i th cell, where T[i,j] = {, if the next state of the i th cell depends on the present state of the j th cell 0, otherwise.
3 N. Ganguly, B. K. Sikdar, P. P. Chaudhuri / Theory of Additive Cellular Automata 003 Clock CLK D Flip-flop Q From left neighbor Combinational logic From right neighbor Figure. A 3-neighborhood CA cell Since the CA is restricted to 3-neighborhood dependency, T[i,j] can have non-zero values for j = (i ), i, (i + ). The inversion vector F of an ACA is defined as {, if the next state of the i th cell results from inversion (xnor) F i = 0, otherwise (xor) If s t represents the state of the CA at the t th instant of time, then the next state - that is, the state at the (t + ) th time instant, is given by : s (t+) = T s t + F. Therefore, s (t+p) = T p s t + (I + T + T T p )F, () where s (t+p) is the state of CA at (t + p) th instant of time. For an n-cell CA, F is the n bit inversion vector with its i th (0 i n ) bit as, if xnor rule is applied on the i th cell; whereas 0 implies xor (linear) rules. The operators (., +) follow the rules defined in binary arithmetic for multiplication and addition respectively. As the LCA is a special case of ACA, where the inversion vector F is an all 0s vector, the next state function (eq. ()) for the LCA gets simplified to s t+ = T s t s t+p = T p s t (2) The state transition eqs. () and (2) results in some global state transition behavior of the CA on the basis of which we can classify CA into two categories - group and non-group CA. II.. Group and non-group CA A CA that generates only cyclic states during its state transitions is known as group CA, whereas a CA generating both cyclic and non-cyclic subspaces is the non-group CA. The state transition diagram of an ACA can be characterized from its T matrix and the inversion vector F. However, the characteristic matrix (T ) can directly determine whether the CA is a group or non-group CA - if det(t) =, the CA is a group CA = 0, the CA is a non group CA Henceforth, unless otherwise mentioned, the term ACA and CA are synonymously used.
4 004 N. Ganguly, B. K. Sikdar, P. P. Chaudhuri / Theory of Additive Cellular Automata Rule Configuration of the 5 Cell CA (Note : 204 is a XOR rule while 53, 85, 95 are XNOR Rules.) T = F = (a) T Matrix and Inversion Vector F Characteristic Polynomial = x + x + x + x + x + Minimal Polynomial = Invariant Polynomials = 4 2 x + x + (b) Characteristic Polynomial of Linear Operator T (x + ). (x + ). 2 2 (x + x + ) (c)cycle Structure CS=4(),2(2),4(3),2(6) 24 Figure 2. A 5-cell group CA and its cycle structure [4(),2(2),4(3),2(6)] Note : The LCA formed from the T matrix also have the same cycle structure CS = [4(),2(2),4(3),2(6)] Group CA : For a group CA (Fig. 2), each CA state has a unique predecessor. That is, all the states lie on a disjoint set of cycles. The state transition behavior of a group CA is represented by the cycle structure (CS) = [µ k (k ),µ k2 (k 2 ), µ km (k m )], where k i is the cycle length of the i th cyclic component of CS and µ ki is the number of such components. Fig. 2(c) illustrates the cycle structure of the 5-cell group CA. It has 4 cycles of length, 2 cycles of length 2, 3 cycles of length 3 and 2 cycles of length 6. The complete cycle structure is denoted as CS = [4(), 2(2), 4(3), 2(6)]. Problem Definition :- tackled in this paper. In this work, we analytically compute the CS = [µ k (k ),µ k2 (k 2 ), µ km (k m )] from a given additive CA - that is from a T matrix and the F vector. Computation of CS for a linear CA has been widely studied [3, 6, 7, 20]. We consider those studies as the base while formulating our proposed scheme. The reported analysis show that the cycle structure of LCA and ACA follows some definite relation and can be divided into two distinct categories - () The cycle structure repeated and not the sequence of LCA and ACA are identical (Fig. 2); (2) The cycle structure of LCA and ACA are different (Fig. 3). Details of these two aspects are reported in section III. Scheme to analyze cycle structure for LCA has been developed with the underlying concept of characteristic polynomial, minimal polynomial and invariant polynomials. Characteristic polynomial : The characteristic polynomial f(x) of a CA is det(t + Ix), where T is the characteristic matrix. Minimal polynomial: The minimal polynomial is the minimum degree polynomial which annihilates T. Invariant polynomials (IP): The characteristic polynomial f(x) comprises of polynomials φ i (x) n i invariant to the linear operator T, where φ i (x) is irreducible. The example CA of Fig. 2 illustrates T, its characteristic polynomial, minimal polynomial and the invariant polynomials. If the characteristic polynomial f(x) of a CA is expressed as a product of its invariant polynomials (IP ), then f(x) = x n x n2 x n l φ l+ (x) n l+ φ N (x) n N where φ i (x) is irreducible (i =,2,, N ). The number of IP comprising the characteristic polynomial
5 N. Ganguly, B. K. Sikdar, P. P. Chaudhuri / Theory of Additive Cellular Automata 005 is denoted by N. A factor x n i (i =,2,,l), (l N ), of f(x) represents a non-cyclic subspace whereas φ i (x) n i corresponds to a cyclic subspace. For a group CA, there is not a single x n i components in f(x). That is, for a group CA, the characteristic polynomial is f(x) = φ (x) n φ 2 (x) n2 φ N (x) n N (3) The characterization of LCA state transition behavior is reported in [2, 3, 4, 6, 3, 4]. Some of the fundamental results reported in [3] and [20] are noted below. These results are important while building the analysis scheme for additive CA, described in section III. II.2. Vector Space Theoretic Analysis of LCA The following theorem, noted from [20], is one of the fundamental results reported for the LCA. Theorem. The cycle structure of an LCA can be represented as CS = [() + k i µ 2j k i (2 j k i )] (4) where k i is odd. Example. The cycle structure of the LCA noted in Fig. 2 is CS = [4(), 2(2), 4(3), 2(6)]. We can also represent it as CS = [(), [3(), 2(2)], [4(3), 2(6)]]. Here k i s, the odd cycles, are and 3. Corresponding to each odd cycle (k i ), there is a cycle of length 2 j k i, in this case, j = for both the odd cycles and 3. The above discussion demands definition of the following terminologies - primary cycles, secondary cycles and cycle family that are essential for the analysis of cycle structure of a CA. Definition. Primary and secondary cycles : Each odd cycle (k i ) in the cycle structure is referred to as a primary cycle and the cycles which are of the form 2 j k i (j ) are referred to as secondary cycles. Definition 2. k cycle family : All the cycles of the form 2 j k (j 0), where k is the length of a primary cycle, are the member of a family of cycles referred to as k-cycle family. It is also referred to as primary cycle family. The basic scheme for extracting the cycle structure of an LCA from its characteristic matrix T has been reported in [20]. Further, a more efficient and compact algorithm is presented in []. The execution steps of the algorithm are next illustrated through an example. Example 2. Let the T matrix of a 5-cell LCA is T = []
6 006 N. Ganguly, B. K. Sikdar, P. P. Chaudhuri / Theory of Additive Cellular Automata The following steps are to be executed to find the cycle structure of the LCA from its T matrix. Step : Find out the characteristic polynomial the CA, illustrating each invariant polynomial separately. For the example CA, it is (x + )(x + ) 2 (x 2 + x + ). Step 2 : Find out the cycle structure for each of the invariant polynomials. For the current example, these are CS LCA(x+) = [(), ()], CS LCA(x+) 2 = [(), (), (2)], CS LCA(x 2 +x+) = [(), (3)] Step 3 : Enumerate the complete cycle structure of the CA by successively performing cross product of cycle structures generated by each invariant polynomial [20]. Therefore, the example CA has the following cycle structure CS LCA = [(), ()] [(), (), (2)] [(), (3)] = [4(), 2(2), 4(3), 2(6)]. where represents the cross product operation and is defined as Definition 3. Cross Product ( ) of two cycle structures CS and CS 2, where CS = [() + i = µ ki (k i )] and CS 2 = [() + 2 i 2 = µ ki2 (k i2 )], is the product of each i th term of CS and the i 2 th term of CS 2. The product of µ ki (k i ) and µ k2i2 (k 2i2 ) results in the cyclic component µ k of length k following the equations [20] µ k = µ ki.µ k2i2.gcd(k i,k 2i2 ) and k = lcm(k i,k 2i2 ) (5) Based on the results provided in this section, we report detail analysis of the state transition behavior of ACA that follows. III. Vector Space Theoretic Analysis of Additive CA Complete characterization of the state transition behavior of an ACA is reported in this section. An ACA, as noted in section II, is represented by the characteristic matrix T and the non-zero inversion vector F. The ACA generates more varieties of cycle structure than that of linear CA (LCA). Fig. 3 gives a typical example of cycle structure generated by ACA which is not available from an LCA. This section also highlights the variation of ACA cycle structure with that of its linear counterpart. An ACA - C is a group CA iff its linear counterpart C (represented by the same characteristic matrix T of C with all 0s F Vector) is a group CA [3]. It signifies that the cycle structure of an ACA can be figured out from the analysis of state transition behavior of the corresponding LCA. Moreover, the concept of null space and its relationship with cycle length of an LCA is necessary for further analysis of cycle structure of ACA. These are reproduced from [0, 7].
7 N. Ganguly, B. K. Sikdar, P. P. Chaudhuri / Theory of Additive Cellular Automata 007 T = F = Figure 3. Additive CA and its state transition behavior. The cycle structure is CS = 2(8). The cycle structure of the corresponding LCA is CS = [2(), (2), 3(4)] Definition 4. Null space : The null space of a matrix (T ) consists of all such vectors that are transformed to the all-zero vector when premultiplied by the matrix. Theorem III.. [6] If an LCA represented by T has a cycle of length k, then the cardinality of the null space of (T k + I) denotes the number of states forming cycles of length k or sub-multiple of k. Theorem III.2. [0] If an LCA is represented by T and for any state χ 0, g(t) χ = 0, then g(x) and the characteristic polynomial f(x) have some common factor h(x). The analysis of ACA state transition behavior is done with the solutions of following issues : A. To check whether a particular cycle length (k) is present in the cycle structure of an ACA. B. To find the special class of ACA (C ) having the cycle structure as that of its linear counterpart C irrespective of its inversion vector F. C. To identify the class of C whose cycle structure differs from that of C, and the properties of F vectors which impart this difference. D. To enumerate the cycle structure and depth of C. III.. The following subsections report the analysis and results of above four issues. Identification of a cycle of length (k) in ACA cycle structure The following theorem enables us to determine whether a cycle of length k exists in an ACA or not. Theorem 2. [6] In an ACA with characteristic matrix T and the inversion vector F, a cycle of length k exists if rank([t k + I]) = rank([t k + I, F]), where F = [I + T + T T k ]F Proof: Let χ be a state in a cycle of length k in an ACA C. Hence, as per eq. () in section II, It can be written as χ = [I + T + T T k ]F + T k χ [T k + I] χ = F, where F = [I + T + T T k ]F (6)
8 008 N. Ganguly, B. K. Sikdar, P. P. Chaudhuri / Theory of Additive Cellular Automata If a cycle of length k is to exist in C, eq. (6) should be consistent. The condition for consistency is rank([t k + I]) = rank([t k + I, F]) (7) Hence the proof. III.2. Class of ACA with the cycle structure identical to corresponding linear CA Theorem 2 is utilized to explore a special class of C (ACA) that has cycle structure identical to that of C (LCA) irrespective of the inversion vector F. The following theorem defines such a class of C. Theorem 3. The cycle structures of C (ACA) and C (LCA) are identical if the characteristic polynomial f(x) of the T matrix does not have a factor (x + ). Proof: Let k be the length of a cycle of the linear CA - C with characteristic matrix T ; characteristic polynomial f(x) of which does not have a factor (x + ). To have a cycle of length k in the corresponding ACA - C, eq. (7) has to be satisfied. The number of vectors, forming a cycle of length k or sub-multiple of k, in the ACA/LCA are derived from the enumeration of null space of α = (T k + I) [7]. Let (x k + ) = g(x) φ c (x); φ c (x) is the largest factor of the characteristic polynomial f(x) that divides (x k + ). Therefore g(x) and f(x) don t have any common factor. Hence for each state χ, where (T k + I) χ = 0, there is a corresponding unique state χ, where φ c (T) χ = 0 (from theorem III.2). Hence, the cardinality of null space of α 2 = φ c (T) is same as α. Since f(x) does not have a factor (x + ) and x k + = (x + ) ( + x + x x k ), therefore similarly the cardinality of the null space of α 3 = [I + T + T 2 T k ] = α = α 2. Hence, that is, rank(t k + I) = rank(t k + I,I + T + T 2 T k ) rank(t k + I) = rank(t k + I, F) directly follows for any F. Therefore, all the cycle lengths of C also exist in C. Since the number of vectors forming each cycle length is same for the both (directly derived from the cardinality of null space), the cycle structures for both the CA are identical. Hence the proof. The following example illustrates the result of theorem 3. Example 3. Let consider a 5-cell ACA with characteristic matrix T and the inversion vector F 0, where T =
9 N. Ganguly, B. K. Sikdar, P. P. Chaudhuri / Theory of Additive Cellular Automata 009 The characteristic polynomial of T is (x 3 +x+)(x 2 +x+). The cycle structure of the corresponding LCA is [(),(3),(7),(2)]. The ACA, as per theorem 3, has the identical cycle structure as that of the LCA, irrespective of F. Let us consider a particular cycle of length 7. As per the theorem, we enumerate α = T 7 + I, α 2 = T 3 + T + and α 3 = T 6 + T 5 + T 4 + T 3 + T 2 + T + I, where T 7 + I = , T 3 + T + = T 6 + T 5 + T 4 + T 3 + T 2 + T + I = , and All the three matrices with 3 rd, 4 th & 5 th rows as all zeros, have cardinality of null space as 8. Therefore, rank(α ) = rank(α 2,α 3 ) and rank(α ) = rank(α 2,F); F=(I + T + T 2 + T 3 + T 4 + T 5 + T 6 ) F. That is, both the C and C have cycles of length 7. The number of states having cycle length 7 or submultiple of 7 (here it is ) is 8. Therefore, the CA cyclic components of cycle length 7 = (8 ) 7 = (as one state forms a self loop). The complete cycle structure of C can be shown as CS = [(), (3), (7), (2)], which is same as that of C. III.3. Class of ACA with cycle structure different from that of LCA From theorem 3, it is obvious that the cycle structure of the linear CA - C and the ACA - C can differ only if the characteristic polynomial of the CA has a factor of (x + ). The study of the role of (x + ) factor helps identification of the class of ACA for which the cycle structure differs from that of the corresponding LCA. Let us concentrate on the LCA/ACA having a single invariant polynomial as (x + ) n. The generalization follows subsequently. The following terminologies are defined relating the cycle structure of LCA/ACA. C(x + ) n : The LCA with characteristic matrix T, the characteristic & minimal polynomial as (x + ) n has the cycle structure [3] CS = [() + m µ 2 j(2 j )], where m = log 2 (n), (8) rank of (T + I) = n, and rank of (T + I) i = n i. (9) The Cφ(x) and C φ(x) represent the LCA and ACA respectively with characteristic polynomial φ(x).
10 00 N. Ganguly, B. K. Sikdar, P. P. Chaudhuri / Theory of Additive Cellular Automata [F k ] : The set of inversion vectors which annihilates only (x + ) k - that is, (T + I) k χ = 0, where (T + I) k χ 0 and k < k & χ [F k ]. (0) Car[F k ] : Cardinality of the set F k. Based on the results of the theorem 2, we next identify the condition responsible for the difference in cycle structure of C(x + ) n and C (x + ) n. Theorem 4. The ACA C (x+) n, characterized by T and the inversion vector F, and LCA C(x+) n have the identical cycle structure if rank(t + I) = rank((t + I),F) () Proof: In order to test whether the cycle structure of LCA C(x + ) n and ACA C (x + ) n are identical, the consistency of eq. (6) is checked for the existence of a cycle of length k in C. The LCA C has cycle(s) of length k, where from eq. (8), k = 2 j, j = (0,,2,,m), m = log 2 (n). Since the cycle length (k) of C(x + ) n is of the form 2 j, the relation for consistency (eq. (6)) can be rewritten as (T 2j + I) χ = (I + T + T T 2j )F (2) where j = (0,, 2,, m) and m = log 2 (n). The relation has to be consistent j to establish the equivalence of cycle structures of C & C. Since (T 2j + I) = (T + I) 2j and (I + T + T T 2j ) = (T + I) 2j, eq. (2) can be rewritten as It implies (T + I) 2j χ = (T + I) 2j F (T + I) 2j [(T + I) χ = F] (3) (T + I) χ = F (4) is to be consistent. That is, it should satisfy rank(t + I) = rank((t + I), F ). Hence the proof. Eq. () characterizes the F vector responsible for imparting the difference in cycle structure between LCA and ACA. The following theorem notes the characterization of F vectors. Theorem 5. The cycle structure of ACA C (x + ) n differs from that of its linear counterpart C(x+) n if and only if the inversion vector F of ACA [F n ].
11 N. Ganguly, B. K. Sikdar, P. P. Chaudhuri / Theory of Additive Cellular Automata 0 Proof: In order to prove the theorem, the consistency of eq. (4) is checked for inversion vector () F [F n ], where n < n, and (2) F [F n ]. Comment: The proof establishes the fact that in the first case both C and C have the same cycle structure while in the second case the cycle structure of C differs from that of C. The proof is established by checking consistency for every cycle length (k = 2 j, j = {0,,2,,m}) Case : Inversion vector F [F n ], where n < n. consistent iff χ [F n + ]. If χ [F n + ], then We show that eq. 4 ((T + I) χ = F ) is (T + I) n + χ = 0 (T + I) n [(T + I) χ] = 0 (5) As per the definition of [F n + ] (noted in page 00), the constituent vectors become zero only when premultiplied by (T + I) n + and higher factors. Therefore, (T + I) χ 0 and the vector y is formed by enumerating the equation Moreover, eq. (5) can be rewritten as (T + I) χ = y (6) (T + I) n y = 0 y [F n ] i.e. (T + I) n y 0 n < n (7) Since rank of (T + I) is (n -), χ i ( i =, 2 and χ, χ 2 [F n + ]), while premultiplied with (T + I) generates the same y in eq. (6). That is, (T + I) χ = (T + I) χ 2 = y Hence, exploiting the all possible pairs of χ, we obtain the set of y having cardinality Car(F n + ) 2, where the cardinality of [F n + ] is denoted as Car(F n + ). Since rank of (T + I) n + is one less than that of (T + I) n (eq. (9)), therefore Car(F n + ) = 2 Car(F n ) Therefore, Car(y) = Car(F n ) - that is, the full set of (F n ) is represented by y. It implies, the relation (T + I) χ = F is consistent for all values of F [F n ] and consequently, eq. (3) is consistent for all F [F n ], n < n. Case 2 : Checking consistency of cycle length for ACA C (x + ) n with inversion vector F [F n ] : In this case, it is shown that eq. (4) is inconsistent for all cycle length 2 j n. Multiplying either side of eq. (4) with (T + I) n we obtain (T + I) n χ = (T + I) n F. (8) It is inconsistent since the lef t hand side (LHS) = 0 while right hand side (RHS) 0.
12 02 N. Ganguly, B. K. Sikdar, P. P. Chaudhuri / Theory of Additive Cellular Automata Theorem 5 leads to the following corollary that specifies the cycle structure of C (x + ) n. Corollary III.. The cycle structure of C (x + ) n with F F n is CS = µ (2 M ); µ = 2 n M and M = log 2 (n) + (9) where the cycle structure of C(x + ) (eq. (8), page 009) is m CS = [() + µ 2 j(2 j )] where m = log 2 (n). Proof: Since the characteristic and minimal polynomial of C is (x + ) n - that is, (T + I) n is always = 0. Therefore, eq. (4) becomes consistent (LHS = RHS = 0), when we premultiply both sides by (T +I) n. Consequently, eq. (3) is consistent if 2 j n - that is, cycles of length 2 j exist in C if 2 j n. The minimum value of j for which the equation becomes consistent is represented by M, where 2 M n < 2 M.. If n = 2 log 2n, then n is of the form 2 j ; where j is an integer. Therefore, log 2 n = log 2 n = log 2 n. In that case, M= log 2 n If n < 2 log 2n, then M = log 2 n = log 2 n +. Considering () and (2), it can be found that M = log 2 n +. Since all the states fall in the null space of (T +I) 2M, as per theorem III., the ACA can have cycles only of length 2 M and the number of cyclic components (µ ) is 2 n /2 M = 2 n M. The M is denoted as the minimum additive factor. The following example illustrates the results of theorem 5 and corollary III.. Example 4. Let us consider the following T matrix and two inversion vectors F and F 2 of the 4-cell ACA - T = F = F 2 = 0. The characteristic polynomial and minimal polynomial of the T is (x + ) 4. The cycle structure of the LCA counterpart with characteristic matrix T is CS = [2(),(2),3(4)]. The inversion vector F annihilates (T + I) 4. The ACA with characteristic matrix T and the inversion vector F has the cycle structure [2(8)] (Fig. 3). However, F 2 cannot annihilate (T +I) 4. The ACA with characteristic matrix T and the inversion vector F 2 has its cycle structure CS identical to CS generated by the LCA.
13 N. Ganguly, B. K. Sikdar, P. P. Chaudhuri / Theory of Additive Cellular Automata 03 Theorem 5 & corollary III. can be extended to a more generalized class of LCA/ACA. As per theorem 3, it is noted that the cycle structure of ACA - C can differ from C only if the characteristic polynomial of C/C contains a factor of (x+). That is, the characteristic polynomial can be represented as f(x) = (x + ) n (x + ) n l φ l+ (x) n l+ φ N (x) n N where (i) each φ i (x) n i is an invariant polynomial and (ii) the irreducible factor of the first l invariant polynomials is (x + ). The following theorem states the nature of cycle structure of such LCA and ACA. Theorem III.3. The cycle structure of LCA, with characteristic matrix T and a factor (x + ) in the characteristic polynomial, is CS = [() + k i µ 2j k i (2 j k i )]; k = ; (20) whereas the cycle structure of ACA, with the characteristic matrix T & inversion vector F and having the largest (x + )-invariant polynomial annihilated by F as (x + ) n i, is CS = k i j=m µ 2 j k i (2 j k i ), k = (2) where M (µ 2 j.k i 2 j k i ) + µ for k = 2 M k i = 2 M.k i M µ 2j k i 2 j k i 2 M k otherwise i and µ 2 j k i = µ 2j k i j > M, M = log 2 n i +. Proof: The proof is developed with the assumption that the (x + ) n i is the only factor annihilated by F. The generalization can be done where (x + ) n i is the largest factor annihilated by F. The characteristic polynomial f(x) of such a CA is denoted as f(x) = (x + ) n i φ(x); φ(x) = φ (x) n φ i (x) n i φ i+ (x) n i+ φ N (x) n N The cycle structure CS φ(x) corresponding to φ(x) is same for both the LCA and ACA. Let F be the inversion vector which annihilates the factor (x + ) n i. As per the theorem 5, the cycle structures generated due to the factor (x + ) n i differ in C & C and these are CS (x + ) n i and CS(x + ) n i (from corollary III.). From the eqs. (9) & (8), we have CS (x + ) n i = µ (2 M ), µ = 2 n i M & M = log 2 (n i ) +
14 04 N. Ganguly, B. K. Sikdar, P. P. Chaudhuri / Theory of Additive Cellular Automata m and CS(x + ) n i = [() + µ 2 j(2 j )], where m = log 2 (n i ). The cycle structure of C φ(x) follows from eq. (4) and forms a linear cycle structure CS φ(x) = [() + k i (2 j k i )] Therefore, the cycle structures CS and CS are represented as CS = CS φ(x) CS(x + ) ni = [() + k i m ki m (2 j k i )] [() + µ 2 j(2 j )] (22) CS = CS φ(x) CS (x + ) ni = [() + k i (2 j k i )] [µ (2 M )] (23) The above two cross products 2 produce CS and CS specified in the eqs. (20) and (2) respectively. The results of theorem III.3 are illustrated below. Example 5. Let us consider the T matrix of the 5-cell CA of Fig. 2 as shown below T = Consider the three ACA with the characteristic matrix as T having these inversion vectors 0 0 F =, F 2 =, and F 3 = The characteristic polynomial f(x) of the example LCA/ACA, in invariant polynomial form, is f(x) = (x + )(x + ) 2 (x 2 + x + ). The inversion vector F = [000] annihilates only (x + ) 2. Therefore, M = log 2 (2) + = 2 (corollary III.). For this case, 2 note the appendix for details
15 N. Ganguly, B. K. Sikdar, P. P. Chaudhuri / Theory of Additive Cellular Automata 05 f(x) can be expressed as φ(x) (x + ) 2, where φ(x) = ( + x) (x 2 + x + ). The cycle structure CS φ(x) = CS( + x) CS(x 2 + x + ) = [(),()] [(), (3)] = [2(),2(3)]. The cycle structure CS( + x) 2 = [(),(),(2)], whereas CS ( + x) 2 = [(4)]. The resultant cycle structure CS = CS φ(x) CS(+x) 2 = [[4(),2(2)], [4(3),2(6)]] while CS = CS φ(x) CS ( + x) 2 = [2(4),2(2)]. Similarly, F 2 = [00] annihilates both the invariant polynomials (x + ) and (x + ) 2. This is, the case where (x + ) 2 is the largest factor annihilated by F 2. Therefore, CS = CS (x + ) CS (x + ) 2 CS(x 2 + x + ) = [(4)] [(2)] [(),(3)] = [2(4),2(2)]. It is same as that of the cycle structure generated by F. The changes in cycle structure of each cycle family k i in CS and CS respectively are as per eq. (2) of theorem III.3. For example, 2(4) where k = and 2 M = 4, the corresponding cycle structure in C which have got merged in C is [4(),2(2)]. The cyclic component of µ 22 has been formed as per eq. 2. Here µ 22 = = 2. Consider F 3 = [0000]. It doesn t annihilate either (x + ) or (x + ) 2. Therefore, the cycle structure of C and C are the same - [4(), 2(2), 4(3), 2(6)]. Theorem III.3 and the earlier example identify the nature of cycle structure of ACA. The complete algorithm to compute cycle structure of an ACA is described next. III.4. Enumerating cycle structure of an ACA The scheme to enumerate cycle structure of an ACA is developed based on the theory reported in the earlier subsections. Theorem 3 reports that the cycle structures of ACA and the corresponding LCA are identical if the characteristic polynomial of the linear operator T doesn t contain the factor (x + ). On the other hand, if the characteristic polynomial is having the factor (x + ), then the cycle structure of the ACA is to be computed from eq. (2). However, it requires evaluation of M - the minimum additive factor. Definition 5. The least cycle length of any primary cycle (k) in CS (cycle structure of ACA) is given by 2 M k; where M is denoted as minimum additive factor. The value of M can be deduced from theorem 2. The rank of [T k +I] and [T k +I, F] is successively compared for all k = 2 m k, m 0, until the ranks become equal. The value of k at which both the ranks become equal provides the value of M. The algorithm to deduce M is next elaborated. Algorithm. Enum M(T, F ) Input : T matrix, F Vector Output : M M = - I, F] do {
16 06 N. Ganguly, B. K. Sikdar, P. P. Chaudhuri / Theory of Additive Cellular Automata M = M + Evaluate F = [I + T + T T 2M ]F Evaluate R = rank[t 2M + ] and R2 = rank[t 2M + I, F] }while ( R < R2) return M Once the M is enumerated, the cycle structure of ACA - C for each k i -cycle family constituting CS is evaluated from the CS of LCA - C (theorem III.3). Algorithm 2. Enum CS of ACA(T,F, CS ) Input : Characteristic matrix T and inversion vector F Output : The cycle structure of ACA - C Enumerate cycle structure CS of LCA, where CS = [() + k i µ 2j k i (2 j k i )]; k i is odd and [CL] is the set of odd cycles of length k i. If characteristic polynomial of T doesn t have a factor of (x + ), then Output the cycle structure CS of C as CS of C. else M = Enum M(T,F) for each k i [CL] { Evaluate µ 2 M k i for each k i following eq. (2) µ 2 j k i = µ 2j k i for j > M } Output CS = k i j=m µ 2j k i (2 j k i ), k = The next example illustrates the execution steps of the algorithm. The ACA is represented by its T matrix and F vector; the T matrix of this example is the one used in the example 2. Example 6. Let the T matrix of a 5-cell ACA be [] T = and F = The matrix [T k + I, F] is referred to as augmented matrix. Step & 2 : Finding characteristic polynomial and cycle structure - Characteristic polynomial f(x) = (x + ) 3 (x 2 + x + ) The cycle structure of the LCA having the characteristic polynomial f(x) is [4(), 2(2), 4(3), 2(6)]. Step 3 : Finding the values of M.
17 N. Ganguly, B. K. Sikdar, P. P. Chaudhuri / Theory of Additive Cellular Automata 07 Rank of (T + I) is 3, while the rank of the augmented matrix is 4. Hence, cycle of length does not exist. Rank of (T 2 + I) is 2, while the rank of the augmented matrix is 3. Hence, cycle of length 2 also does not exist in the ACA. Rank of (T 4 + I) is 2, while the rank of the augmented matrix is 2. So, the value of M is 2. Step 4 : Finding the components. k i = µ 22 = = k i =3 µ 22 3 = = 2. Hence, the cycle structure becomes [2(4), 2(2)]. IV. Conclusion This paper presents the complete scheme to compute the cycle structure of additive cellular automata (ACA). The similarities between the cycle structure of an LCA and the cycle structure produced by the ACA is explored. An analytical scheme has been devised to extract the similarities for enumeration of the cycle structure of ACA. The scheme can be used further to efficiently utilize ACA for different purposes in the future. Appendix Elaboration of the steps to obtain the cross product of eq. (23) The cycle structure (CS) of an LCA is evaluated from the expression referred in eq. (22). The expressions for CS noted in eq. (22) is reproduced below along with the final result noted in eq. (20). The intermediate computation steps are not shown as it can be directly obtained through simple cross product [20]. CS = CS φ(x) CS(x + ) ni = [() + k i = [() + k i µ 2j k i (2 j k i )]; k = ; (2 j k i )] [() + The cycle structure (CS ) of ACA is evaluated through eq. (23) reproduced below. m µ 2 j(2 j )] CS = CS φ(x) CS (x + ) n i = [() + k i (2 j k i )] [µ (2 M )] The cross product of eq. (23) produces eq. (2) (page 03). As can be seen from eq. (2), the cyclic components of CS, µ 2 j k i has some relationship with µ 2j k i - the cyclic components of CS. This section establishes the relationship defined in eq. (2). The relationship between µ 2j k i and µ 2 j k i comprises of two parts - (a) where j > M and (b) where j M
18 08 N. Ganguly, B. K. Sikdar, P. P. Chaudhuri / Theory of Additive Cellular Automata Let us consider a particular cycle family k i. We () first show that the number of states encompassed by a the family is same for both CS and CS. (2) Then we show µ 2j k i = µ 2 j k i for j > M and finally (3) establish the relation between µ 2 M k i and µ 2j k i for j M.. Computing the number of states in a family k i. From eq. (5), product of µ ki (k i ) and µ k2i2 (k 2i2 ) results in the cyclic component µ k of length k, where µ k = µ ki.µ k2i2.gcd(k i,k 2i2 ) and k = lcm(k i,k 2i2 ). Therefore, the number of states involved in forming the cycle is given by µ k = (µ ki.µ k2i2.gcd(k i,k 2i2 )) (lcm(k i,k 2i2 )) = µ ki.µ k2i2.k i.k 2i2 (24) The above result can be applied to compute the number of states of a particular family k i in CS and CS. Let refer cycle structure of k i family as CS(k i ) and CS (k i ) for LCA and ACA respectively. The number of states covered are considered as S(k i ) and S (k i ) respectively in CS(k i ) and CS (k i ). Therefore, CS(k i ) = m m ki m (2 j k i ) [() + µ 2 j(2 j )] S(k i ) = ( 2 j k i [ + ( µ 2 j 2 j )]) Similarly, CS (k i ) = ˆµ 2j k i (2 j k i ) [µ (2 M )] S (k i )] = (ˆµ 2j k i 2 j k i µ 2 M ) From the eqs. (9) & (8), we have Therefore, S(k i ) = S (k i ) Result (). 2. The µ 2j k i = µ 2 j k i for j > M. µ 2 M = + m µ 2 j(2 j ) (25) CS = CS φ(x) CS(x + ) ni = [() + m ki m (2 j k i )] [() + µ 2 j(2 j )] k i m = [() + µ 2 j(2 j ) + m ki m ( (2 j k i ) [() + µ 2 j(2 j )])] k i = [() + m µ 2 j(2 j ) + M ( k i (2 j k i ) [() + m µ 2 j(2 j )] + (i) Considering 2 j = 2 j k i, where k = & since m M (eqs. (9) & ( 8)) CS = [() + M ( µ 2j k i (2 j k i ) + k i j=m+ [() + j=m+ (2 j k i ) [() + m µ 2 j(2 j )](2 j k i ))] m µ 2 j(2 j )])]
19 N. Ganguly, B. K. Sikdar, P. P. Chaudhuri / Theory of Additive Cellular Automata 09 CS = CS φ(x) CS (x + ) ni = [() + k i = [µ (2 M )] + [ ˆµ 2j k i (2 j k i ) µ (2 M )] k i = [µ (2 M )] + M [( (2 j k i ) µ (2 M )) + ( k i (ii) Considering 2 M = 2 M k i, where k =. CS = M [( (µ 2M k i (2 M k i )) + k i j=m+ (2 j k i )] [µ (2 M )] j=m+ (2 j k i ) µ (2 M ))] µ 2 M ˆµ 2j k i (2 j k i )] For j > M µ 2j k i = [ + m µ 2 j(2 j )] µ 2 j k i = µ 2 M Therefore, µ 2j k i = µ 2 j k i for j > M (eq. (25)) Result (2). 3. Computation of µ 2 M k i Combining the results () and (2), the number of states covered by the cycles of length 2 M k i are same for both LCA and ACA. The states covered by ACA are µ 2 M k i 2 M k i. M Similarly, the states covered by an LCA for any k i are µ 2j k i 2 j k i Therefore, µ 2 M k i = M µ 2j k i 2 j k i 2 M k i ; k i M However, the states covered by the LCA for k i = are (µ 2j k i 2 j k i ) + and, therefore, µ 2 M k i = M + µ 2j k i 2 j k i 2 M k i ; k i =
20 020 N. Ganguly, B. K. Sikdar, P. P. Chaudhuri / Theory of Additive Cellular Automata References [] Chakraborty, S., Chowdhury, D. R., Chaudhuri, P. P.: Theory and Application of Non-Group Cellular Automata for Synthesis of Easily Testable Finite State Machines, IEEE Trans. on Computers, 45(7), July 996, [2] Chattopadhyay, S.: Some Studies on Theory and Applications of Additive Cellular Automata, Ph.D. Thesis, I.I.T. Kharagpur, India, 996. [3] Chaudhuri, P. P., Chowdhury, D. R., Nandi, S., Chatterjee, S.: Additive Cellular Automata Theory and Applications, vol., IEEE Computer Society Press, CA, USA, ISBN , 997. [4] Chowdhury, D. R.: Theory and Applications of Additive Cellular Automata for Reliable and Testable VLSI Circuit Design, Ph.D. Thesis, I.I.T. Kharagpur, India, 992. [5] Chowdhury, D. R., Basu, S., Gupta, I. S., Chaudhuri, P. P.: Design of CAECC Cellular Automata Based Error Correcting Code, IEEE Trans. on Computers, 43(6), June 994, [6] Das, A. K.: Additive Cellular Automata : Theory and Application as a Built-in Self-test Structure, Ph.D. Thesis, I.I.T. Kharagpur, India, 990. [7] Das, A. K., Chaudhuri, P. P.: Efficient Characterization of Cellular Automata, Proc. IEE (Part E), 37(), January 990, [8] Das, A. K., Chaudhuri, P. P.: Vector Space Theoretic Analysis of Additive Cellular Automata and Its Applications for Pseudo-Exhaustive Test Pattern Generation, IEEE Trans. on Computers, 42(3), March 993, [9] Dasgupta, P., Chattopadhyay, S., Sengupta, I.: Theory and Application of Nongroup Cellular Automata for Message Authentification, Journal of Systems Architecture, 47(7), July 200, [0] Datta, K. B..: Matrix and Linear Algebra, BPB Publications, 993. [] Ganguly, N.: Cellular Automata Evolution: Theory and Applications in Pattern Classification, Ph.D. Thesis, B. E. College (Deemed University), [2] Martin, O., Odlyzko, A. M., Wolfram, S.: Algebraic Properties of Cellular Automata, Comm. Math. Phys., 93, 984, [3] Misra, S.: Theory and Application of Additive Cellular Automata for Easily Testable VLSI Circuit Design, Ph.D. Thesis, I.I.T. Kharagpur, India, 992. [4] Nandi, S.: Additive Cellular Automata : Theory and Application for Testable Circuit Design and Data Encryption, Ph.D. Thesis, I.I.T. Kharagpur, India, 994. [5] Nandi, S., Kar, B. K., Chaudhuri, P. P.: Theory and Application of Cellular Automata in Cryptography, IEEE Trans. on Computers, 43(2), December 994, [6] Paul, K.: Theory and Application of GF(2 p ) Cellular Automata, Ph.D. Thesis, B. E. College, (Deemed University), Howrah, India, [7] Paul, K., Chowdhury, D. R., Chaudhuri, P. P.: Theory of Extended Linear Machines, IEEE Trans. on Computers, 5(9), 2002, [8] Serra, M., Chen, G. L.: Pseudo-Random Pattern Generation and Fault Coverage of Delay Faults with Non Linear Finite State Machines with High Entropy, Proc. IEEE On-Line Testing Workshop,Crete, Greece, 997. [9] Sikdar, B. K., Ganguly, N., Chaudhuri, P. P.: Design of Test Pattern Generator without Prohibited Pattern Set, IEEE Trans on Computer Aided Design, 23, Dec 2004,
21 N. Ganguly, B. K. Sikdar, P. P. Chaudhuri / Theory of Additive Cellular Automata 02 [20] Stone, H.: Linear Machines, Princeton Univ. Press, 965. [2] Stone, H.: Discrete Mathematical Structures and Their Applications, Science Research Associates Inc., 973. [22] Wolfram, S.: Statistical Mechanics of Cellular Automata, Rev. Mod. Phys., 55(3), July 983,
Cellular Automata-Based Recursive Pseudoexhaustive Test Pattern Generator
 IEEE TRANSACTIONS ON COMPUTERS, VOL, NO, FEBRUARY Cellular Automata-Based Recursive Pseudoexhaustive Test Pattern Generator Prabir Dasgupta, Santanu Chattopadhyay, P Pal Chaudhuri, and Indranil Sengupta
IEEE TRANSACTIONS ON COMPUTERS, VOL, NO, FEBRUARY Cellular Automata-Based Recursive Pseudoexhaustive Test Pattern Generator Prabir Dasgupta, Santanu Chattopadhyay, P Pal Chaudhuri, and Indranil Sengupta
Optimization of 1D and 2D Cellular Automata for Pseudo Random Number Generator.
 IOSR Journal of VLSI and Signal Processing (IOSR-JVSP) Volume 4, Issue 6, Ver. I (Nov - Dec. 2014), PP 28-33 e-issn: 2319 4200, p-issn No. : 2319 4197 Optimization of 1D and 2D Cellular Automata for Pseudo
IOSR Journal of VLSI and Signal Processing (IOSR-JVSP) Volume 4, Issue 6, Ver. I (Nov - Dec. 2014), PP 28-33 e-issn: 2319 4200, p-issn No. : 2319 4197 Optimization of 1D and 2D Cellular Automata for Pseudo
Cryptographically Robust Large Boolean Functions. Debdeep Mukhopadhyay CSE, IIT Kharagpur
 Cryptographically Robust Large Boolean Functions Debdeep Mukhopadhyay CSE, IIT Kharagpur Outline of the Talk Importance of Boolean functions in Cryptography Important Cryptographic properties Proposed
Cryptographically Robust Large Boolean Functions Debdeep Mukhopadhyay CSE, IIT Kharagpur Outline of the Talk Importance of Boolean functions in Cryptography Important Cryptographic properties Proposed
One-Dimensional Linear Hybrid Cellular Automata: Their Synthesis, Properties and Applications to Digital Circuits Testing
 One-Dimensional Linear Hybrid Cellular Automata: Their Synthesis, Properties and Applications to Digital Circuits Testing M. Serra, K. Cattell, S. Zhang, J.C. Muzio, D.M. Miller Dept. of Computer Science
One-Dimensional Linear Hybrid Cellular Automata: Their Synthesis, Properties and Applications to Digital Circuits Testing M. Serra, K. Cattell, S. Zhang, J.C. Muzio, D.M. Miller Dept. of Computer Science
Designing Cellular Automata Structures using Quantum-dot Cellular Automata
 Designing Cellular Automata Structures using Quantum-dot Cellular Automata Mayur Bubna, Subhra Mazumdar, Sudip Roy and Rajib Mall Department of Computer Sc. & Engineering Indian Institute of Technology,
Designing Cellular Automata Structures using Quantum-dot Cellular Automata Mayur Bubna, Subhra Mazumdar, Sudip Roy and Rajib Mall Department of Computer Sc. & Engineering Indian Institute of Technology,
An Explicit Similarity Transform between Cellular Automata and LFSR Matrices*
 FINITE FIELDS AND THEIR APPLICATIONS 4, 239 251 (1998) ARTICLE NO FF980212 An Explicit Similarity Transform between Cellular Automata and LFSR Matrices* Kevin Cattell and Jon C Muzio Department of Computer
FINITE FIELDS AND THEIR APPLICATIONS 4, 239 251 (1998) ARTICLE NO FF980212 An Explicit Similarity Transform between Cellular Automata and LFSR Matrices* Kevin Cattell and Jon C Muzio Department of Computer
Cellular Automata Evolution for Pattern Recognition
 Cellular Automata Evolution for Pattern Recognition Pradipta Maji Center for Soft Computing Research Indian Statistical Institute, Kolkata, 700 108, INDIA Under the supervision of Prof. P Pal Chaudhuri
Cellular Automata Evolution for Pattern Recognition Pradipta Maji Center for Soft Computing Research Indian Statistical Institute, Kolkata, 700 108, INDIA Under the supervision of Prof. P Pal Chaudhuri
Error Correcting Capability of Cellular Automata Based Associative Memory
 466 IEEE TRANSACTIONS ON SYSTEMS, MAN, AND CYBERNETICS PART A: SYSTEMS AND HUMANS, VOL. 33, NO. 4, JULY 2003 Error Correcting Capability of Cellular Automata Based Associative Memory Pradipta Maji, Niloy
466 IEEE TRANSACTIONS ON SYSTEMS, MAN, AND CYBERNETICS PART A: SYSTEMS AND HUMANS, VOL. 33, NO. 4, JULY 2003 Error Correcting Capability of Cellular Automata Based Associative Memory Pradipta Maji, Niloy
Subquadratic Space Complexity Multiplication over Binary Fields with Dickson Polynomial Representation
 Subquadratic Space Complexity Multiplication over Binary Fields with Dickson Polynomial Representation M A Hasan and C Negre Abstract We study Dickson bases for binary field representation Such representation
Subquadratic Space Complexity Multiplication over Binary Fields with Dickson Polynomial Representation M A Hasan and C Negre Abstract We study Dickson bases for binary field representation Such representation
Inadmissible Class of Boolean Functions under Stuck-at Faults
 Inadmissible Class of Boolean Functions under Stuck-at Faults Debesh K. Das 1, Debabani Chowdhury 1, Bhargab B. Bhattacharya 2, Tsutomu Sasao 3 1 Computer Sc. & Engg. Dept., Jadavpur University, Kolkata
Inadmissible Class of Boolean Functions under Stuck-at Faults Debesh K. Das 1, Debabani Chowdhury 1, Bhargab B. Bhattacharya 2, Tsutomu Sasao 3 1 Computer Sc. & Engg. Dept., Jadavpur University, Kolkata
Subquadratic space complexity multiplier for a class of binary fields using Toeplitz matrix approach
 Subquadratic space complexity multiplier for a class of binary fields using Toeplitz matrix approach M A Hasan 1 and C Negre 2 1 ECE Department and CACR, University of Waterloo, Ontario, Canada 2 Team
Subquadratic space complexity multiplier for a class of binary fields using Toeplitz matrix approach M A Hasan 1 and C Negre 2 1 ECE Department and CACR, University of Waterloo, Ontario, Canada 2 Team
Linear Cellular Automata as Discrete Models for Generating Cryptographic Sequences
 Linear Cellular Automata as Discrete Models for Generating Cryptographic Sequences A Fúster-Sabater P Caballero-Gil 2 Institute of Applied Physics, CSIC Serrano 44, 286 Madrid, Spain Email: amparo@ieccsices
Linear Cellular Automata as Discrete Models for Generating Cryptographic Sequences A Fúster-Sabater P Caballero-Gil 2 Institute of Applied Physics, CSIC Serrano 44, 286 Madrid, Spain Email: amparo@ieccsices
Transition Faults Detection in Bit Parallel Multipliers over GF(2 m )
 Transition Faults Detection in Bit Parallel Multipliers over GF( m ) Hafizur Rahaman Bengal Engineering & Science University, Shibpur Howrah-73, India rahaman_h@it.becs.ac.in Jimson Mathew Computer Science
Transition Faults Detection in Bit Parallel Multipliers over GF( m ) Hafizur Rahaman Bengal Engineering & Science University, Shibpur Howrah-73, India rahaman_h@it.becs.ac.in Jimson Mathew Computer Science
PARALLEL MULTIPLICATION IN F 2
 PARALLEL MULTIPLICATION IN F 2 n USING CONDENSED MATRIX REPRESENTATION Christophe Negre Équipe DALI, LP2A, Université de Perpignan avenue P Alduy, 66 000 Perpignan, France christophenegre@univ-perpfr Keywords:
PARALLEL MULTIPLICATION IN F 2 n USING CONDENSED MATRIX REPRESENTATION Christophe Negre Équipe DALI, LP2A, Université de Perpignan avenue P Alduy, 66 000 Perpignan, France christophenegre@univ-perpfr Keywords:
Representations of Sp(6,R) and SU(3) carried by homogeneous polynomials
 Representations of Sp(6,R) and SU(3) carried by homogeneous polynomials Govindan Rangarajan a) Department of Mathematics and Centre for Theoretical Studies, Indian Institute of Science, Bangalore 560 012,
Representations of Sp(6,R) and SU(3) carried by homogeneous polynomials Govindan Rangarajan a) Department of Mathematics and Centre for Theoretical Studies, Indian Institute of Science, Bangalore 560 012,
Counting Two-State Transition-Tour Sequences
 Counting Two-State Transition-Tour Sequences Nirmal R. Saxena & Edward J. McCluskey Center for Reliable Computing, ERL 460 Department of Electrical Engineering, Stanford University, Stanford, CA 94305
Counting Two-State Transition-Tour Sequences Nirmal R. Saxena & Edward J. McCluskey Center for Reliable Computing, ERL 460 Department of Electrical Engineering, Stanford University, Stanford, CA 94305
BP -HOMOLOGY AND AN IMPLICATION FOR SYMMETRIC POLYNOMIALS. 1. Introduction and results
 BP -HOMOLOGY AND AN IMPLICATION FOR SYMMETRIC POLYNOMIALS DONALD M. DAVIS Abstract. We determine the BP -module structure, mod higher filtration, of the main part of the BP -homology of elementary 2- groups.
BP -HOMOLOGY AND AN IMPLICATION FOR SYMMETRIC POLYNOMIALS DONALD M. DAVIS Abstract. We determine the BP -module structure, mod higher filtration, of the main part of the BP -homology of elementary 2- groups.
New Algebraic Decoding of (17,9,5) Quadratic Residue Code by using Inverse Free Berlekamp-Massey Algorithm (IFBM)
 International Journal of Computational Intelligence Research (IJCIR). ISSN: 097-87 Volume, Number 8 (207), pp. 205 2027 Research India Publications http://www.ripublication.com/ijcir.htm New Algebraic
International Journal of Computational Intelligence Research (IJCIR). ISSN: 097-87 Volume, Number 8 (207), pp. 205 2027 Research India Publications http://www.ripublication.com/ijcir.htm New Algebraic
Finite Fields. Mike Reiter
 1 Finite Fields Mike Reiter reiter@cs.unc.edu Based on Chapter 4 of: W. Stallings. Cryptography and Network Security, Principles and Practices. 3 rd Edition, 2003. Groups 2 A group G, is a set G of elements
1 Finite Fields Mike Reiter reiter@cs.unc.edu Based on Chapter 4 of: W. Stallings. Cryptography and Network Security, Principles and Practices. 3 rd Edition, 2003. Groups 2 A group G, is a set G of elements
Theory of Rule 6 and it s Application to Round Robin Tournament
 Theory of Rule 6 and it s Application to Round Robin Tournament Pabitra Pal Choudhury, Sk. Sarif Hassan Applied Statistics Unit, Indian Statistical Institute, Kolkata, 78, INDIA Email: pabitrapalchoudhury@gmail.com
Theory of Rule 6 and it s Application to Round Robin Tournament Pabitra Pal Choudhury, Sk. Sarif Hassan Applied Statistics Unit, Indian Statistical Institute, Kolkata, 78, INDIA Email: pabitrapalchoudhury@gmail.com
Introduction to Modern Cryptography. (1) Finite Groups, Rings and Fields. (2) AES - Advanced Encryption Standard
 Introduction to Modern Cryptography Lecture 3 (1) Finite Groups, Rings and Fields (2) AES - Advanced Encryption Standard +,0, and -a are only notations! Review - Groups Def (group): A set G with a binary
Introduction to Modern Cryptography Lecture 3 (1) Finite Groups, Rings and Fields (2) AES - Advanced Encryption Standard +,0, and -a are only notations! Review - Groups Def (group): A set G with a binary
Subquadratic Computational Complexity Schemes for Extended Binary Field Multiplication Using Optimal Normal Bases
 1 Subquadratic Computational Complexity Schemes for Extended Binary Field Multiplication Using Optimal Normal Bases H. Fan and M. A. Hasan March 31, 2007 Abstract Based on a recently proposed Toeplitz
1 Subquadratic Computational Complexity Schemes for Extended Binary Field Multiplication Using Optimal Normal Bases H. Fan and M. A. Hasan March 31, 2007 Abstract Based on a recently proposed Toeplitz
Dynamics of finite linear cellular automata over Z N
 Dynamics of finite linear cellular automata over Z N F. Mendivil, D. Patterson September 9, 2009 Abstract We investigate the behaviour of linear cellular automata with state space Z N and only finitely
Dynamics of finite linear cellular automata over Z N F. Mendivil, D. Patterson September 9, 2009 Abstract We investigate the behaviour of linear cellular automata with state space Z N and only finitely
XOR - XNOR Gates. The graphic symbol and truth table of XOR gate is shown in the figure.
 XOR - XNOR Gates Lesson Objectives: In addition to AND, OR, NOT, NAND and NOR gates, exclusive-or (XOR) and exclusive-nor (XNOR) gates are also used in the design of digital circuits. These have special
XOR - XNOR Gates Lesson Objectives: In addition to AND, OR, NOT, NAND and NOR gates, exclusive-or (XOR) and exclusive-nor (XNOR) gates are also used in the design of digital circuits. These have special
EECS Components and Design Techniques for Digital Systems. Lec 26 CRCs, LFSRs (and a little power)
 EECS 150 - Components and esign Techniques for igital Systems Lec 26 CRCs, LFSRs (and a little power) avid Culler Electrical Engineering and Computer Sciences University of California, Berkeley http://www.eecs.berkeley.edu/~culler
EECS 150 - Components and esign Techniques for igital Systems Lec 26 CRCs, LFSRs (and a little power) avid Culler Electrical Engineering and Computer Sciences University of California, Berkeley http://www.eecs.berkeley.edu/~culler
Highly Efficient GF(2 8 ) Inversion Circuit Based on Redundant GF Arithmetic and Its Application to AES Design
 Saint-Malo, September 13th, 2015 Cryptographic Hardware and Embedded Systems Highly Efficient GF(2 8 ) Inversion Circuit Based on Redundant GF Arithmetic and Its Application to AES Design Rei Ueno 1, Naofumi
Saint-Malo, September 13th, 2015 Cryptographic Hardware and Embedded Systems Highly Efficient GF(2 8 ) Inversion Circuit Based on Redundant GF Arithmetic and Its Application to AES Design Rei Ueno 1, Naofumi
Cellular Automata in Cryptography" Information Security Group,Royal Holloway, Abstract The cipher systems based on Cellular Automata proposed by Nandi
 Comments on \Theory and Applications of Cellular Automata in Cryptography" S.R. Blackburn, S. Murphy y and K.G. Paterson z Information Security Group,Royal Holloway, University of London, Surrey TW20 0EX,
Comments on \Theory and Applications of Cellular Automata in Cryptography" S.R. Blackburn, S. Murphy y and K.G. Paterson z Information Security Group,Royal Holloway, University of London, Surrey TW20 0EX,
A GENERAL POLYNOMIAL SIEVE
 A GENERAL POLYNOMIAL SIEVE SHUHONG GAO AND JASON HOWELL Abstract. An important component of the index calculus methods for finding discrete logarithms is the acquisition of smooth polynomial relations.
A GENERAL POLYNOMIAL SIEVE SHUHONG GAO AND JASON HOWELL Abstract. An important component of the index calculus methods for finding discrete logarithms is the acquisition of smooth polynomial relations.
Conquering Edge Faults in a Butterfly with Automorphisms
 International Conference on Theoretical and Mathematical Foundations of Computer Science (TMFCS-0) Conquering Edge Faults in a Butterfly with Automorphisms Meghanad D. Wagh and Khadidja Bendjilali Department
International Conference on Theoretical and Mathematical Foundations of Computer Science (TMFCS-0) Conquering Edge Faults in a Butterfly with Automorphisms Meghanad D. Wagh and Khadidja Bendjilali Department
Division Property: a New Attack Against Block Ciphers
 Division Property: a New Attack Against Block Ciphers Christina Boura (joint on-going work with Anne Canteaut) Séminaire du groupe Algèbre et Géometrie, LMV November 24, 2015 1 / 50 Symmetric-key encryption
Division Property: a New Attack Against Block Ciphers Christina Boura (joint on-going work with Anne Canteaut) Séminaire du groupe Algèbre et Géometrie, LMV November 24, 2015 1 / 50 Symmetric-key encryption
Low complexity bit-parallel GF (2 m ) multiplier for all-one polynomials
 Low complexity bit-parallel GF (2 m ) multiplier for all-one polynomials Yin Li 1, Gong-liang Chen 2, and Xiao-ning Xie 1 Xinyang local taxation bureau, Henan, China. Email:yunfeiyangli@gmail.com, 2 School
Low complexity bit-parallel GF (2 m ) multiplier for all-one polynomials Yin Li 1, Gong-liang Chen 2, and Xiao-ning Xie 1 Xinyang local taxation bureau, Henan, China. Email:yunfeiyangli@gmail.com, 2 School
Repeated-Root Self-Dual Negacyclic Codes over Finite Fields
 Journal of Mathematical Research with Applications May, 2016, Vol. 36, No. 3, pp. 275 284 DOI:10.3770/j.issn:2095-2651.2016.03.004 Http://jmre.dlut.edu.cn Repeated-Root Self-Dual Negacyclic Codes over
Journal of Mathematical Research with Applications May, 2016, Vol. 36, No. 3, pp. 275 284 DOI:10.3770/j.issn:2095-2651.2016.03.004 Http://jmre.dlut.edu.cn Repeated-Root Self-Dual Negacyclic Codes over
Revisiting Finite Field Multiplication Using Dickson Bases
 Revisiting Finite Field Multiplication Using Dickson Bases Bijan Ansari and M. Anwar Hasan Department of Electrical and Computer Engineering University of Waterloo, Waterloo, Ontario, Canada {bansari,
Revisiting Finite Field Multiplication Using Dickson Bases Bijan Ansari and M. Anwar Hasan Department of Electrical and Computer Engineering University of Waterloo, Waterloo, Ontario, Canada {bansari,
Generalized hyper-bent functions over GF(p)
 Discrete Applied Mathematics 55 2007) 066 070 Note Generalized hyper-bent functions over GFp) A.M. Youssef Concordia Institute for Information Systems Engineering, Concordia University, Montreal, QC, H3G
Discrete Applied Mathematics 55 2007) 066 070 Note Generalized hyper-bent functions over GFp) A.M. Youssef Concordia Institute for Information Systems Engineering, Concordia University, Montreal, QC, H3G
Cyclic codes: overview
 Cyclic codes: overview EE 387, Notes 14, Handout #22 A linear block code is cyclic if the cyclic shift of a codeword is a codeword. Cyclic codes have many advantages. Elegant algebraic descriptions: c(x)
Cyclic codes: overview EE 387, Notes 14, Handout #22 A linear block code is cyclic if the cyclic shift of a codeword is a codeword. Cyclic codes have many advantages. Elegant algebraic descriptions: c(x)
Probabilistic Analysis of Cellular Automata Rules and its Application in Pseudo Random Pattern Generation
 Probabilistic Analysis of Cellular Automata Rules and its Application in Pseudo Random Pattern Generation Abhishek Seth, S. Bandyopadhyay, U. Maulik. Abstract The present work is an extension of the work
Probabilistic Analysis of Cellular Automata Rules and its Application in Pseudo Random Pattern Generation Abhishek Seth, S. Bandyopadhyay, U. Maulik. Abstract The present work is an extension of the work
The decomposability of simple orthogonal arrays on 3 symbols having t + 1 rows and strength t
 The decomposability of simple orthogonal arrays on 3 symbols having t + 1 rows and strength t Wiebke S. Diestelkamp Department of Mathematics University of Dayton Dayton, OH 45469-2316 USA wiebke@udayton.edu
The decomposability of simple orthogonal arrays on 3 symbols having t + 1 rows and strength t Wiebke S. Diestelkamp Department of Mathematics University of Dayton Dayton, OH 45469-2316 USA wiebke@udayton.edu
Chapter 4 Mathematics of Cryptography
 Chapter 4 Mathematics of Cryptography Part II: Algebraic Structures Copyright The McGraw-Hill Companies, Inc. Permission required for reproduction or display. 4.1 Chapter 4 Objectives To review the concept
Chapter 4 Mathematics of Cryptography Part II: Algebraic Structures Copyright The McGraw-Hill Companies, Inc. Permission required for reproduction or display. 4.1 Chapter 4 Objectives To review the concept
Montgomery Multiplier and Squarer in GF(2 m )
 Montgomery Multiplier and Squarer in GF( m ) Huapeng Wu The Centre for Applied Cryptographic Research Department of Combinatorics and Optimization University of Waterloo, Waterloo, Canada h3wu@cacrmathuwaterlooca
Montgomery Multiplier and Squarer in GF( m ) Huapeng Wu The Centre for Applied Cryptographic Research Department of Combinatorics and Optimization University of Waterloo, Waterloo, Canada h3wu@cacrmathuwaterlooca
PARITY BASED FAULT DETECTION TECHNIQUES FOR S-BOX/ INV S-BOX ADVANCED ENCRYPTION SYSTEM
 PARITY BASED FAULT DETECTION TECHNIQUES FOR S-BOX/ INV S-BOX ADVANCED ENCRYPTION SYSTEM Nabihah Ahmad Department of Electronic Engineering, Faculty of Electrical and Electronic Engineering, Universiti
PARITY BASED FAULT DETECTION TECHNIQUES FOR S-BOX/ INV S-BOX ADVANCED ENCRYPTION SYSTEM Nabihah Ahmad Department of Electronic Engineering, Faculty of Electrical and Electronic Engineering, Universiti
Error Correcting Index Codes and Matroids
 Error Correcting Index Codes and Matroids Anoop Thomas and B Sundar Rajan Dept of ECE, IISc, Bangalore 5612, India, Email: {anoopt,bsrajan}@eceiiscernetin arxiv:15156v1 [csit 21 Jan 215 Abstract The connection
Error Correcting Index Codes and Matroids Anoop Thomas and B Sundar Rajan Dept of ECE, IISc, Bangalore 5612, India, Email: {anoopt,bsrajan}@eceiiscernetin arxiv:15156v1 [csit 21 Jan 215 Abstract The connection
COMPUTER ARITHMETIC. 13/05/2010 cryptography - math background pp. 1 / 162
 COMPUTER ARITHMETIC 13/05/2010 cryptography - math background pp. 1 / 162 RECALL OF COMPUTER ARITHMETIC computers implement some types of arithmetic for instance, addition, subtratction, multiplication
COMPUTER ARITHMETIC 13/05/2010 cryptography - math background pp. 1 / 162 RECALL OF COMPUTER ARITHMETIC computers implement some types of arithmetic for instance, addition, subtratction, multiplication
1 The Algebraic Normal Form
 1 The Algebraic Normal Form Boolean maps can be expressed by polynomials this is the algebraic normal form (ANF). The degree as a polynomial is a first obvious measure of nonlinearity linear (or affine)
1 The Algebraic Normal Form Boolean maps can be expressed by polynomials this is the algebraic normal form (ANF). The degree as a polynomial is a first obvious measure of nonlinearity linear (or affine)
Finite Fields. SOLUTIONS Network Coding - Prof. Frank H.P. Fitzek
 Finite Fields In practice most finite field applications e.g. cryptography and error correcting codes utilizes a specific type of finite fields, namely the binary extension fields. The following exercises
Finite Fields In practice most finite field applications e.g. cryptography and error correcting codes utilizes a specific type of finite fields, namely the binary extension fields. The following exercises
University of Toronto Faculty of Applied Science and Engineering Edward S. Rogers Sr. Department of Electrical and Computer Engineering
 University of Toronto Faculty of Applied Science and Engineering Edward S. Rogers Sr. Department of Electrical and Computer Engineering Final Examination ECE 241F - Digital Systems Examiners: S. Brown,
University of Toronto Faculty of Applied Science and Engineering Edward S. Rogers Sr. Department of Electrical and Computer Engineering Final Examination ECE 241F - Digital Systems Examiners: S. Brown,
Fault Tolerance & Reliability CDA Chapter 2 Cyclic Polynomial Codes
 Fault Tolerance & Reliability CDA 5140 Chapter 2 Cyclic Polynomial Codes - cylic code: special type of parity check code such that every cyclic shift of codeword is a codeword - for example, if (c n-1,
Fault Tolerance & Reliability CDA 5140 Chapter 2 Cyclic Polynomial Codes - cylic code: special type of parity check code such that every cyclic shift of codeword is a codeword - for example, if (c n-1,
Cryptanalysis of a Multistage Encryption System
 Cryptanalysis of a Multistage Encryption System Chengqing Li, Xinxiao Li, Shujun Li and Guanrong Chen Department of Mathematics, Zhejiang University, Hangzhou, Zhejiang 310027, China Software Engineering
Cryptanalysis of a Multistage Encryption System Chengqing Li, Xinxiao Li, Shujun Li and Guanrong Chen Department of Mathematics, Zhejiang University, Hangzhou, Zhejiang 310027, China Software Engineering
High Performance GHASH Function for Long Messages
 High Performance GHASH Function for Long Messages Nicolas Méloni 1, Christophe Négre 2 and M. Anwar Hasan 1 1 Department of Electrical and Computer Engineering University of Waterloo, Canada 2 Team DALI/ELIAUS
High Performance GHASH Function for Long Messages Nicolas Méloni 1, Christophe Négre 2 and M. Anwar Hasan 1 1 Department of Electrical and Computer Engineering University of Waterloo, Canada 2 Team DALI/ELIAUS
FResCA: A Fault-Resistant Cellular Automata Based Stream Cipher
 FResCA: A Fault-Resistant Cellular Automata Based Stream Cipher Jimmy Jose 1,2 Dipanwita Roy Chowdhury 1 1 Crypto Research Laboratory, Department of Computer Science and Engineering, Indian Institute of
FResCA: A Fault-Resistant Cellular Automata Based Stream Cipher Jimmy Jose 1,2 Dipanwita Roy Chowdhury 1 1 Crypto Research Laboratory, Department of Computer Science and Engineering, Indian Institute of
 Twitter: @Owen134866 www.mathsfreeresourcelibrary.com Prior Knowledge Check 1) Simplify: a) 3x 2 5x 5 b) 5x3 y 2 15x 7 2) Factorise: a) x 2 2x 24 b) 3x 2 17x + 20 15x 2 y 3 3) Use long division to calculate:
Twitter: @Owen134866 www.mathsfreeresourcelibrary.com Prior Knowledge Check 1) Simplify: a) 3x 2 5x 5 b) 5x3 y 2 15x 7 2) Factorise: a) x 2 2x 24 b) 3x 2 17x + 20 15x 2 y 3 3) Use long division to calculate:
The cycle polynomial of a permutation group
 The cycle polynomial of a permutation group Peter J. Cameron School of Mathematics and Statistics University of St Andrews North Haugh St Andrews, Fife, U.K. pjc0@st-andrews.ac.uk Jason Semeraro Department
The cycle polynomial of a permutation group Peter J. Cameron School of Mathematics and Statistics University of St Andrews North Haugh St Andrews, Fife, U.K. pjc0@st-andrews.ac.uk Jason Semeraro Department
New Possibilities for Cellular Automata in Cryptography
 New Possibilities for Cellular Automata in Cryptography Mauro Tardivo Filho Marco A. A. Henriques Faculty of Electrical and Computer Engineering University of Campinas Sao Paulo - Brazil Overview 1. History
New Possibilities for Cellular Automata in Cryptography Mauro Tardivo Filho Marco A. A. Henriques Faculty of Electrical and Computer Engineering University of Campinas Sao Paulo - Brazil Overview 1. History
A collection of topological Ramsey spaces of trees and their application to profinite graph theory
 A collection of topological Ramsey spaces of trees and their application to profinite graph theory Yuan Yuan Zheng Abstract We construct a collection of new topological Ramsey spaces of trees. It is based
A collection of topological Ramsey spaces of trees and their application to profinite graph theory Yuan Yuan Zheng Abstract We construct a collection of new topological Ramsey spaces of trees. It is based
Novel Implementation of Finite Field Multipliers over GF(2m) for Emerging Cryptographic Applications
 Wright State University CORE Scholar Browse all Theses and Dissertations Theses and Dissertations 2017 Novel Implementation of Finite Field Multipliers over GF(2m) for Emerging Cryptographic Applications
Wright State University CORE Scholar Browse all Theses and Dissertations Theses and Dissertations 2017 Novel Implementation of Finite Field Multipliers over GF(2m) for Emerging Cryptographic Applications
Frequency Domain Finite Field Arithmetic for Elliptic Curve Cryptography
 Frequency Domain Finite Field Arithmetic for Elliptic Curve Cryptography Selçuk Baktır, Berk Sunar {selcuk,sunar}@wpi.edu Department of Electrical & Computer Engineering Worcester Polytechnic Institute
Frequency Domain Finite Field Arithmetic for Elliptic Curve Cryptography Selçuk Baktır, Berk Sunar {selcuk,sunar}@wpi.edu Department of Electrical & Computer Engineering Worcester Polytechnic Institute
A Digit-Serial Systolic Multiplier for Finite Fields GF(2 m )
 A Digit-Serial Systolic Multiplier for Finite Fields GF( m ) Chang Hoon Kim, Sang Duk Han, and Chun Pyo Hong Department of Computer and Information Engineering Taegu University 5 Naeri, Jinryang, Kyungsan,
A Digit-Serial Systolic Multiplier for Finite Fields GF( m ) Chang Hoon Kim, Sang Duk Han, and Chun Pyo Hong Department of Computer and Information Engineering Taegu University 5 Naeri, Jinryang, Kyungsan,
Primary classes of compositions of numbers
 Annales Mathematicae et Informaticae 41 (2013) pp. 193 204 Proceedings of the 15 th International Conference on Fibonacci Numbers and Their Applications Institute of Mathematics and Informatics, Eszterházy
Annales Mathematicae et Informaticae 41 (2013) pp. 193 204 Proceedings of the 15 th International Conference on Fibonacci Numbers and Their Applications Institute of Mathematics and Informatics, Eszterházy
Computing Higher Dimensional Digital Homotopy Groups
 Appl. Math. Inf. Sci. 8, No. 5, 2417-2425 (2014) 2417 Applied Mathematics & Information Sciences An International Journal http://dx.doi.org/10.12785/amis/080537 Computing Higher Dimensional Digital Homotopy
Appl. Math. Inf. Sci. 8, No. 5, 2417-2425 (2014) 2417 Applied Mathematics & Information Sciences An International Journal http://dx.doi.org/10.12785/amis/080537 Computing Higher Dimensional Digital Homotopy
Decomposing Bent Functions
 2004 IEEE TRANSACTIONS ON INFORMATION THEORY, VOL. 49, NO. 8, AUGUST 2003 Decomposing Bent Functions Anne Canteaut and Pascale Charpin Abstract In a recent paper [1], it is shown that the restrictions
2004 IEEE TRANSACTIONS ON INFORMATION THEORY, VOL. 49, NO. 8, AUGUST 2003 Decomposing Bent Functions Anne Canteaut and Pascale Charpin Abstract In a recent paper [1], it is shown that the restrictions
Linear Finite State Machines 1. X. Sun E. Kontopidi M. Serra J. Muzio. Abstract
 The Concatenation and Partitioning of Linear Finite State Machines 1 X. Sun E. Kontopidi M. Serra J. Muzio Dept. of Electrical Engineering University of Alberta Edmonton, AB T6G 2G7 Dept. of Comp. Science
The Concatenation and Partitioning of Linear Finite State Machines 1 X. Sun E. Kontopidi M. Serra J. Muzio Dept. of Electrical Engineering University of Alberta Edmonton, AB T6G 2G7 Dept. of Comp. Science
Design for Testability
 Design for Testability Outline Ad Hoc Design for Testability Techniques Method of test points Multiplexing and demultiplexing of test points Time sharing of I/O for normal working and testing modes Partitioning
Design for Testability Outline Ad Hoc Design for Testability Techniques Method of test points Multiplexing and demultiplexing of test points Time sharing of I/O for normal working and testing modes Partitioning
Research Article Characterization of the Evolution of Nonlinear Uniform Cellular Automata in the Light of Deviant States
 Hindawi Publishing Corporation International Journal of Mathematics and Mathematical Sciences Volume 2011, Article ID 605098, 16 pages doi:101155/2011/605098 Research Article Characterization of the Evolution
Hindawi Publishing Corporation International Journal of Mathematics and Mathematical Sciences Volume 2011, Article ID 605098, 16 pages doi:101155/2011/605098 Research Article Characterization of the Evolution
Construction of quasi-cyclic self-dual codes
 Construction of quasi-cyclic self-dual codes Sunghyu Han, Jon-Lark Kim, Heisook Lee, and Yoonjin Lee December 17, 2011 Abstract There is a one-to-one correspondence between l-quasi-cyclic codes over a
Construction of quasi-cyclic self-dual codes Sunghyu Han, Jon-Lark Kim, Heisook Lee, and Yoonjin Lee December 17, 2011 Abstract There is a one-to-one correspondence between l-quasi-cyclic codes over a
Design of Low Power Optimized MixColumn/Inverse MixColumn Architecture for AES
 Design of Low Power Optimized MixColumn/Inverse MixColumn Architecture for AES Rajasekar P Assistant Professor, Department of Electronics and Communication Engineering, Kathir College of Engineering, Neelambur,
Design of Low Power Optimized MixColumn/Inverse MixColumn Architecture for AES Rajasekar P Assistant Professor, Department of Electronics and Communication Engineering, Kathir College of Engineering, Neelambur,
A New Multiple Weight Set Calculation Algorithm
 A New Multiple Weight Set Calculation Algorithm Hong-Sik Kim Jin-kyue Lee Sungho Kang hskim@dopey.yonsei.ac.kr jklee@cowboys.yonsei.ac.kr shkang@yonsei.ac.kr Dept. of Electrical Eng. Yonsei Univ. Shinchon-dong
A New Multiple Weight Set Calculation Algorithm Hong-Sik Kim Jin-kyue Lee Sungho Kang hskim@dopey.yonsei.ac.kr jklee@cowboys.yonsei.ac.kr shkang@yonsei.ac.kr Dept. of Electrical Eng. Yonsei Univ. Shinchon-dong
Linear Cellular Automata as Discrete Models for Generating Cryptographic Sequences
 Linear Cellular Automata as Discrete Models for Generating Cryptographic Sequences Pino Caballero-Gil Faculty of Mathematics. University of La Laguna 38271. La Laguna, Tenerife, Spain. pcaballe@ull.es
Linear Cellular Automata as Discrete Models for Generating Cryptographic Sequences Pino Caballero-Gil Faculty of Mathematics. University of La Laguna 38271. La Laguna, Tenerife, Spain. pcaballe@ull.es
Interesting Examples on Maximal Irreducible Goppa Codes
 Interesting Examples on Maximal Irreducible Goppa Codes Marta Giorgetti Dipartimento di Fisica e Matematica, Universita dell Insubria Abstract. In this paper a full categorization of irreducible classical
Interesting Examples on Maximal Irreducible Goppa Codes Marta Giorgetti Dipartimento di Fisica e Matematica, Universita dell Insubria Abstract. In this paper a full categorization of irreducible classical
Formal Design of Composite Physically Unclonable Function
 Formal Design of Composite Physically Unclonable Function Durga Prasad Sahoo Debdeep Mukhopadhyay Rajat Subhra Chakraborty Computer Science and Engineering Indian Institute of Technology, Kharagpur, India
Formal Design of Composite Physically Unclonable Function Durga Prasad Sahoo Debdeep Mukhopadhyay Rajat Subhra Chakraborty Computer Science and Engineering Indian Institute of Technology, Kharagpur, India
Logic BIST. Sungho Kang Yonsei University
 Logic BIST Sungho Kang Yonsei University Outline Introduction Basics Issues Weighted Random Pattern Generation BIST Architectures Deterministic BIST Conclusion 2 Built In Self Test Test/ Normal Input Pattern
Logic BIST Sungho Kang Yonsei University Outline Introduction Basics Issues Weighted Random Pattern Generation BIST Architectures Deterministic BIST Conclusion 2 Built In Self Test Test/ Normal Input Pattern
Ir O D = D = ( ) Section 2.6 Example 1. (Bottom of page 119) dim(v ) = dim(l(v, W )) = dim(v ) dim(f ) = dim(v )
 Section 3.2 Theorem 3.6. Let A be an m n matrix of rank r. Then r m, r n, and, by means of a finite number of elementary row and column operations, A can be transformed into the matrix ( ) Ir O D = 1 O
Section 3.2 Theorem 3.6. Let A be an m n matrix of rank r. Then r m, r n, and, by means of a finite number of elementary row and column operations, A can be transformed into the matrix ( ) Ir O D = 1 O
CSCI 1590 Intro to Computational Complexity
 CSCI 59 Intro to Computational Complexity Overview of the Course John E. Savage Brown University January 2, 29 John E. Savage (Brown University) CSCI 59 Intro to Computational Complexity January 2, 29
CSCI 59 Intro to Computational Complexity Overview of the Course John E. Savage Brown University January 2, 29 John E. Savage (Brown University) CSCI 59 Intro to Computational Complexity January 2, 29
Fundamentals of Digital Design
 Fundamentals of Digital Design Digital Radiation Measurement and Spectroscopy NE/RHP 537 1 Binary Number System The binary numeral system, or base-2 number system, is a numeral system that represents numeric
Fundamentals of Digital Design Digital Radiation Measurement and Spectroscopy NE/RHP 537 1 Binary Number System The binary numeral system, or base-2 number system, is a numeral system that represents numeric
Golomb-Lempel Construction of Costas Arrays Revisited
 International Journal of Mathematics and Computer Science, 10(2015), no. 2, 239 249 M CS Golomb-Lempel Construction of Costas Arrays Revisited Ishani Barua University of Engineering & Management Jaipur,
International Journal of Mathematics and Computer Science, 10(2015), no. 2, 239 249 M CS Golomb-Lempel Construction of Costas Arrays Revisited Ishani Barua University of Engineering & Management Jaipur,
CS151 Complexity Theory. Lecture 13 May 15, 2017
 CS151 Complexity Theory Lecture 13 May 15, 2017 Relationship to other classes To compare to classes of decision problems, usually consider P #P which is a decision class easy: NP, conp P #P easy: P #P
CS151 Complexity Theory Lecture 13 May 15, 2017 Relationship to other classes To compare to classes of decision problems, usually consider P #P which is a decision class easy: NP, conp P #P easy: P #P
Math 353, Practice Midterm 1
 Math 353, Practice Midterm Name: This exam consists of 8 pages including this front page Ground Rules No calculator is allowed 2 Show your work for every problem unless otherwise stated Score 2 2 3 5 4
Math 353, Practice Midterm Name: This exam consists of 8 pages including this front page Ground Rules No calculator is allowed 2 Show your work for every problem unless otherwise stated Score 2 2 3 5 4
Implementation of Quantum dot Cellular Automata based Novel Full Adder and Full Subtractor
 Implementation of Quantum dot Cellular Automata based Novel Full Adder and Full Subtractor Peer Zahoor Ahmad 1, Firdous Ahmad 2, b, Syed Muzaffar Ahmad 3, Dr. Rafiq Ahmad Khan 4 1 Department of Computer
Implementation of Quantum dot Cellular Automata based Novel Full Adder and Full Subtractor Peer Zahoor Ahmad 1, Firdous Ahmad 2, b, Syed Muzaffar Ahmad 3, Dr. Rafiq Ahmad Khan 4 1 Department of Computer
Research Article Complex Dynamic Behaviors in Cellular Automata Rule 14
 Discrete Dynamics in Nature and Society Volume, Article ID 5839, pages doi:.55//5839 Research Article Complex Dynamic Behaviors in Cellular Automata Rule 4 Qi Han, Xiaofeng Liao, and Chuandong Li State
Discrete Dynamics in Nature and Society Volume, Article ID 5839, pages doi:.55//5839 Research Article Complex Dynamic Behaviors in Cellular Automata Rule 4 Qi Han, Xiaofeng Liao, and Chuandong Li State
Novel Modulo 2 n +1Multipliers
 Novel Modulo Multipliers H. T. Vergos Computer Engineering and Informatics Dept., University of Patras, 26500 Patras, Greece. vergos@ceid.upatras.gr C. Efstathiou Informatics Dept.,TEI of Athens, 12210
Novel Modulo Multipliers H. T. Vergos Computer Engineering and Informatics Dept., University of Patras, 26500 Patras, Greece. vergos@ceid.upatras.gr C. Efstathiou Informatics Dept.,TEI of Athens, 12210
Outline. EECS Components and Design Techniques for Digital Systems. Lec 18 Error Coding. In the real world. Our beautiful digital world.
 Outline EECS 150 - Components and esign Techniques for igital Systems Lec 18 Error Coding Errors and error models Parity and Hamming Codes (SECE) Errors in Communications LFSRs Cyclic Redundancy Check
Outline EECS 150 - Components and esign Techniques for igital Systems Lec 18 Error Coding Errors and error models Parity and Hamming Codes (SECE) Errors in Communications LFSRs Cyclic Redundancy Check
New algebraic decoding method for the (41, 21,9) quadratic residue code
 New algebraic decoding method for the (41, 21,9) quadratic residue code Mohammed M. Al-Ashker a, Ramez Al.Shorbassi b a Department of Mathematics Islamic University of Gaza, Palestine b Ministry of education,
New algebraic decoding method for the (41, 21,9) quadratic residue code Mohammed M. Al-Ashker a, Ramez Al.Shorbassi b a Department of Mathematics Islamic University of Gaza, Palestine b Ministry of education,
Stream Ciphers. Çetin Kaya Koç Winter / 20
 Çetin Kaya Koç http://koclab.cs.ucsb.edu Winter 2016 1 / 20 Linear Congruential Generators A linear congruential generator produces a sequence of integers x i for i = 1,2,... starting with the given initial
Çetin Kaya Koç http://koclab.cs.ucsb.edu Winter 2016 1 / 20 Linear Congruential Generators A linear congruential generator produces a sequence of integers x i for i = 1,2,... starting with the given initial
Chapter 4 Finite Fields
 Chapter 4 Finite Fields Introduction will now introduce finite fields of increasing importance in cryptography AES, Elliptic Curve, IDEA, Public Key concern operations on numbers what constitutes a number
Chapter 4 Finite Fields Introduction will now introduce finite fields of increasing importance in cryptography AES, Elliptic Curve, IDEA, Public Key concern operations on numbers what constitutes a number
CS1800 Discrete Structures Fall 2017 October, CS1800 Discrete Structures Midterm Version A
 CS1800 Discrete Structures Fall 2017 October, 2017 CS1800 Discrete Structures Midterm Version A Instructions: 1. The exam is closed book and closed notes. You may not use a calculator or any other electronic
CS1800 Discrete Structures Fall 2017 October, 2017 CS1800 Discrete Structures Midterm Version A Instructions: 1. The exam is closed book and closed notes. You may not use a calculator or any other electronic
PAPER A Low-Complexity Step-by-Step Decoding Algorithm for Binary BCH Codes
 359 PAPER A Low-Complexity Step-by-Step Decoding Algorithm for Binary BCH Codes Ching-Lung CHR a),szu-linsu, Members, and Shao-Wei WU, Nonmember SUMMARY A low-complexity step-by-step decoding algorithm
359 PAPER A Low-Complexity Step-by-Step Decoding Algorithm for Binary BCH Codes Ching-Lung CHR a),szu-linsu, Members, and Shao-Wei WU, Nonmember SUMMARY A low-complexity step-by-step decoding algorithm
CONSTRUCTING Boolean functions on odd number of variables n having nonlinearity greater than the bent
 Patterson-Wiedemann type functions on 21 variables with Nonlinearity greater than Bent Concatenation bound Selçuk Kavut and Subhamoy Maitra 1 Abstract Nonlinearity is one of the most challenging combinatorial
Patterson-Wiedemann type functions on 21 variables with Nonlinearity greater than Bent Concatenation bound Selçuk Kavut and Subhamoy Maitra 1 Abstract Nonlinearity is one of the most challenging combinatorial
Can You Hear Me Now?
 Can You Hear Me Now? An Introduction to Coding Theory William J. Turner Department of Mathematics & Computer Science Wabash College Crawfordsville, IN 47933 19 October 2004 W. J. Turner (Wabash College)
Can You Hear Me Now? An Introduction to Coding Theory William J. Turner Department of Mathematics & Computer Science Wabash College Crawfordsville, IN 47933 19 October 2004 W. J. Turner (Wabash College)
Homotopy and homology groups of the n-dimensional Hawaiian earring
 F U N D A M E N T A MATHEMATICAE 165 (2000) Homotopy and homology groups of the n-dimensional Hawaiian earring by Katsuya E d a (Tokyo) and Kazuhiro K a w a m u r a (Tsukuba) Abstract. For the n-dimensional
F U N D A M E N T A MATHEMATICAE 165 (2000) Homotopy and homology groups of the n-dimensional Hawaiian earring by Katsuya E d a (Tokyo) and Kazuhiro K a w a m u r a (Tsukuba) Abstract. For the n-dimensional
ELG 5372 Error Control Coding. Lecture 12: Ideals in Rings and Algebraic Description of Cyclic Codes
 ELG 5372 Error Control Coding Lecture 12: Ideals in Rings and Algebraic Description of Cyclic Codes Quotient Ring Example + Quotient Ring Example Quotient Ring Recall the quotient ring R={,,, }, where
ELG 5372 Error Control Coding Lecture 12: Ideals in Rings and Algebraic Description of Cyclic Codes Quotient Ring Example + Quotient Ring Example Quotient Ring Recall the quotient ring R={,,, }, where
EECS150 - Digital Design Lecture 26 Error Correction Codes, Linear Feedback Shift Registers (LFSRs)
 EECS150 - igital esign Lecture 26 Error Correction Codes, Linear Feedback Shift Registers (LFSRs) Nov 21, 2002 John Wawrzynek Fall 2002 EECS150 Lec26-ECC Page 1 Outline Error detection using parity Hamming
EECS150 - igital esign Lecture 26 Error Correction Codes, Linear Feedback Shift Registers (LFSRs) Nov 21, 2002 John Wawrzynek Fall 2002 EECS150 Lec26-ECC Page 1 Outline Error detection using parity Hamming
Information redundancy
 Information redundancy Information redundancy add information to date to tolerate faults error detecting codes error correcting codes data applications communication memory p. 2 - Design of Fault Tolerant
Information redundancy Information redundancy add information to date to tolerate faults error detecting codes error correcting codes data applications communication memory p. 2 - Design of Fault Tolerant
THE MEASURE-THEORETIC ENTROPY OF LINEAR CELLULAR AUTOMATA WITH RESPECT TO A MARKOV MEASURE. 1. Introduction
 THE MEASURE-THEORETIC ENTROPY OF LINEAR CELLULAR AUTOMATA WITH RESPECT TO A MARKOV MEASURE HASAN AKIN Abstract. The purpose of this short paper is to compute the measure-theoretic entropy of the onedimensional
THE MEASURE-THEORETIC ENTROPY OF LINEAR CELLULAR AUTOMATA WITH RESPECT TO A MARKOV MEASURE HASAN AKIN Abstract. The purpose of this short paper is to compute the measure-theoretic entropy of the onedimensional
Correlation of Binary Sequence Families Derived from Multiplicative Character of Finite Fields
 Correlation of Binary Sequence Families Derived from Multiplicative Character of Finite Fields Zilong Wang and Guang Gong Department of Electrical and Computer Engineering, University of Waterloo Waterloo,
Correlation of Binary Sequence Families Derived from Multiplicative Character of Finite Fields Zilong Wang and Guang Gong Department of Electrical and Computer Engineering, University of Waterloo Waterloo,
Math 512 Syllabus Spring 2017, LIU Post
 Week Class Date Material Math 512 Syllabus Spring 2017, LIU Post 1 1/23 ISBN, error-detecting codes HW: Exercises 1.1, 1.3, 1.5, 1.8, 1.14, 1.15 If x, y satisfy ISBN-10 check, then so does x + y. 2 1/30
Week Class Date Material Math 512 Syllabus Spring 2017, LIU Post 1 1/23 ISBN, error-detecting codes HW: Exercises 1.1, 1.3, 1.5, 1.8, 1.14, 1.15 If x, y satisfy ISBN-10 check, then so does x + y. 2 1/30
BASIC NOTIONS. x + y = 1 3, 3x 5y + z = A + 3B,C + 2D, DC are not defined. A + C =
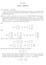 CHAPTER I BASIC NOTIONS (a) 8666 and 8833 (b) a =6,a =4 will work in the first case, but there are no possible such weightings to produce the second case, since Student and Student 3 have to end up with
CHAPTER I BASIC NOTIONS (a) 8666 and 8833 (b) a =6,a =4 will work in the first case, but there are no possible such weightings to produce the second case, since Student and Student 3 have to end up with
CS61C : Machine Structures
 CS 61C L15 Blocks (1) inst.eecs.berkeley.edu/~cs61c/su05 CS61C : Machine Structures Lecture #15: Combinational Logic Blocks Outline CL Blocks Latches & Flip Flops A Closer Look 2005-07-14 Andy Carle CS
CS 61C L15 Blocks (1) inst.eecs.berkeley.edu/~cs61c/su05 CS61C : Machine Structures Lecture #15: Combinational Logic Blocks Outline CL Blocks Latches & Flip Flops A Closer Look 2005-07-14 Andy Carle CS
K Anup Kumar et al,int.j.comp.tech.appl,vol 3 (1), 23-31
 K Anup Kumar et al,int.j.comp.tech.appl,vol 3 (1), 23-31 A Modified Feistel Cipher involving a key as a multiplicant on both the sides of the Plaintext matrix and supplemented with Mixing Permutation and
K Anup Kumar et al,int.j.comp.tech.appl,vol 3 (1), 23-31 A Modified Feistel Cipher involving a key as a multiplicant on both the sides of the Plaintext matrix and supplemented with Mixing Permutation and
GENERALIZED NONLINEARITY OF S-BOXES. Sugata Gangopadhyay
 Volume X, No. 0X, 0xx, X XX doi:0.3934/amc.xx.xx.xx GENERALIZED NONLINEARITY OF -BOXE ugata Gangopadhyay Department of Computer cience and Engineering, Indian Institute of Technology Roorkee, Roorkee 47667,
Volume X, No. 0X, 0xx, X XX doi:0.3934/amc.xx.xx.xx GENERALIZED NONLINEARITY OF -BOXE ugata Gangopadhyay Department of Computer cience and Engineering, Indian Institute of Technology Roorkee, Roorkee 47667,
On the invertibility of the XOR of rotations of a binary word
 On the invertibility of the XOR of rotations of a binary word Ronald L. Rivest November 10, 2009 Abstract We prove the following result regarding operations on a binary word whose length is a power of
On the invertibility of the XOR of rotations of a binary word Ronald L. Rivest November 10, 2009 Abstract We prove the following result regarding operations on a binary word whose length is a power of
Substrictly Cyclic Operators
 Substrictly Cyclic Operators Ben Mathes dbmathes@colby.edu April 29, 2008 Dedicated to Don Hadwin Abstract We initiate the study of substrictly cyclic operators and algebras. As an application of this
Substrictly Cyclic Operators Ben Mathes dbmathes@colby.edu April 29, 2008 Dedicated to Don Hadwin Abstract We initiate the study of substrictly cyclic operators and algebras. As an application of this
Design and Optimization of Parity Generator and Parity Checker Based On Quantum-dot Cellular Automata Santanu Santra, Utpal Roy
 Design and Optimization of Parity Generator and Parity Checker Based On Quantum-dot Cellular Automata Santanu Santra, Utpal Roy Abstract Quantum-dot Cellular Automata (QCA) is one of the most substitute
Design and Optimization of Parity Generator and Parity Checker Based On Quantum-dot Cellular Automata Santanu Santra, Utpal Roy Abstract Quantum-dot Cellular Automata (QCA) is one of the most substitute
