Revisiting Wiener s Attack New Weak Keys in RSA
|
|
|
- Christine Chase
- 5 years ago
- Views:
Transcription
1 Rvisiting Winr s Attack w Wak Kys in RSA Subhamoy Maitra an Santanu Sarkar Inian Statistical Institut, 0 B T Roa, Kolkata , Inia {subho, santanu r}@isicalacin Abstract In this papr w rvisit Winr s mtho (IEEE-IT 990) of continu fraction (CF) to fin nw waknsss in RSA W consir RSA with = pq, q < p < q, public ncryption xponnt an privat cryption xponnt Our motivation is to fin out whn RSA is inscur givn is O( δ ), whr w ar mostly intrst in th rang 0 δ 05 Givn ( ) is known to th attackr, w show that th RSA kys ar wak whn = δ an δ < γ γ, whr q p 6 This prsnts aitional rsults ovr th work of Wgr (AAECC 00) W also iscuss how th lattic bas ia of Bonh-Durf (IEEE-IT 000) works bttr to fin wak kys byon th boun δ < γ Furthr w show that, th RSA kys ar wak whn < δ an is O( δ ) for δ Using similar tchniqus w also prsnt nw rsults ovr th work of Blömr an May (PKC 004) Kywors: Cryptanalysis, RSA, Factorization, Wak Kys Introuction RSA [4] is on of th most popular cryptosystms in th history of cryptology Hr, w us th stanar notations in RSA as follows: prims p, q, with q < p < q; = pq, φ() = (p )(q );, with, < φ() ar such that = + tφ(), t ; 4, ar availabl in public an th mssag M is ncrypt as C M mo ; 5 th scrt ky is rquir to crypt th mssag as M C mo In this papr w xploit th Winr s mtho [] of continu fraction (CF) to fin nw waknsss in RSA (s [5] for Lgnr s thorm rlat to CF xprssion) Winr [] show that if < 05, thn t < an t (which in turn rvals p, q) coul b stimat in poly(log ) tim from th CF xprssion of th publicly availabl quantity From = + tφ(), it is asy to s that t =, i, t < whnvr φ() φ() φ() < φ() Thus a goo stimation of φ() can b of us whilxploiting CF xprssion It is known that for q < p < q, + < φ() < + In [5, Sction 4], Winr s attack [] has bn xtn stimating φ() as + This is a substantially rvis (with som corrctions an gnralizations) an xtn vrsion of th papr that has bn prsnt in ISC 008, th Information Scurity Confrnc Sptmbr 5-8, 008, Taipi, Taiwan, publish in Pags 8 4, volum 5, Lctur ots in Computr Scinc, Springr, 008 Th introuction of th paramtr is a gnralization in Thorms, 4; in th confrnc vrsion, w hav us = Furthr, Sctions, prsnt aitional matrials that wr not inclu in th confrnc vrsion of this papr
2 Lots of waknsss of RSA hav bn intifi in past thr cas, but still RSA can b scurly us with propr prcautions as a public ky cryptosystm Th scurity of RSA pns on th harnss of factorization Lt us now brifly iscuss som waknsss of RSA RSA is foun to b wak whn th prim factors of ithr p or q ar small [] Similarly, RSA is wak too whn th prim factors of ithr p + or q + ar small [4] In [0], it has bn point out that short public xponnts may caus waknss if sam mssag is broacast to many partis An outstaning survy on th attacks on RSA is availabl in [] For vry rcnt rsults on RSA on may rfr to [7,, 9] an th rfrncs thrin In this papr w stuy th waknsss of RSA whn th scrt cryption xponnt is uppr boun Th work of [] initiats th application of Continu Fraction (CF) xprssion for th attack In th work of [6], important rsults hav bn shown rgaring small solutions to polynomial quations that in turn show vulnrabilitis of low xponnt RSA In [4, 5], th mtho of [6] has bn xploit to show that RSA is inscur if < 09 Th rsults from [6] hav bn us along with th rsults of [] in many paprs [4, 5, 5,, ] to gt th waknsss whn is lss than δ In this papr, w lik to fin out how th ia of CF xprssion from [] can b xploit to fin waknsss of RSA whn is small In [5, Sction 4], som xtnsion of th work [] has bn mntion an it has also bn not that similar xtnsion will work on th rsults of [] Th rsult of [] works for with a fw mor bits longr than 4 In [8], an xtnsion of Lgnr s rsult has bn stui to gt mor wak kys in th irction of [] Howvr, w fin that nw wak kys of RSA can b intifi using th CF tchniqu Ths wak kys hav not bn xplor in th litratur bfor to th bst of our knowlg In [], it has bn shown that RSA is not scur whn < 05 as unr this conition, t < an t can b foun in th CF xprssion of Th knowlg of hlps in gtting p, q immiatly In [9], a ngativ rsult has bn intifi that Winr s attack will work with ngligibl succss for > 4 Thus thr is a p intrst to fin out cass whr th Winr s stratgy [] can b xtn to gt mor wak kys On may asily chck that > t an < t In [], φ() has bn approximat φ() by to gt th rsults A bttr rsult has bn obtain in [5, Sction 4] whr φ() is approximat by + It has bn shown that t < whn δ < β, + 4 whr p q = β an = δ ot that, for β =, th rsult of [5] givs similar boun on as in [], which is of th orr 4 Th improvmnt is obtain whn β crass Only at β =, bcoms of th orr of In [5, Sction 5, 6], th attack of [4, 5] 4 has bn xtn consiring th valu of β, whr p q = β Insta of consiring p q = β, w hr consir q p γ whr to gt aitional rsults 6 Ths rsults ar prsnt in Sction Furthr, in Sction, w also stuy th ia of Bonh an Durf [4, 5] to monstrat that it compars bttr than th ia prsnt in th bginning of Sction which uss th ia of CF xpansion only Furthr, insta of rlating β, 4 β, with = δ, w put th constraint on W fin that RSA is inscur whn is of th orr of δ for δ 05 Th constraint in our cas
3 is on th public xponnt, which is rlat to th iffrnc of th prims W show that our attack works whn δ A+, which can b stimat as O( 5 δ ) in gnral B A+ Hr A = β + 4 an B = Th consrvativ uppr boun on, i, O( 5 δ ), ignors th trm β in A an thus th iffrnc btwn th two prims os not com into th pictur for th attack in gnral Ths rsults ar prsnt in Sction In [], it has bn shown that p, q can b foun in polynomial tim for vry, satisfying x + y 0 mo φ(), with x 4 an y = O( 4 x); furthr som xtnsions consiring th iffrnc p q hav also bn consir Th work of [] also uss th rsult of [6] as wll as th ia of CF xprssion [] in thir proof W also provi aitional rsult ovr []This is prsnt in Sction W hr highlight th contribution of this papr Givn with known to th attackr RSA is inscur whn = δ an δ < γ γ, whr q p an γ Furthr w show that this boun on δ can b 6 xtn using th lattic bas tchniqus < δ an is O( δ ) for δ x + y = mφ() for m > 0, x 7 4, y c 4 x, c an p q c 4 4 x + y = mφ(), for m > 0, 0 < x φ() γ for an y γ x whr 6 φ() 4 q p γ whr γ an is known to th attackr In th confrnc vrsion of this papr, w hav consir =, whras, th cas for = has bn stui [5] Taking in th rang of [, ] gnralizs both ths ias On may ask a qustion that how can b availabl to th attackr In fact, on may try to guss for iffrnt valus (that ar computationally fasibl) to mount th attack Furthr, on may not that th knowlg of most significant bits (MSBs) of p or q can provi som approximation of that may also b us In [], it has also bn stui how a fw MSBs of p or q can b foun from th knowlg of only Our rsult in Thorm shows that can b factoriz from th knowlg of ( not known) whn is O( ) an is O( ) W lik to point out an important rsult [7, Thorm ] that shoul b stat in this contxt, whr it has bn shown that for, with th knowlg of,, th intgr can b factoriz in O(log ) tim In [0], Sun an Yang propos a variant of RSA whr th public ncryption xponnt an th privat cryption xponnt ar such that log + log log + l k, whr l k is a positiv intgr Th main ia was to kp th bit siz as wll as quit lss an th valu of l k is rlat to th scurity of this variant of RSA Though th class of th xponnts in [0] ar not covr by our Thorm, on ns to b cautious whil choosing,, whn both of thm ar rstrict by som uppr boun Bfor procing furthr, lt us xplain th Continu Fraction (CF) xprssion W follow th matrial from [8, Chaptr 5] for this Givn a positiv rational numbr a, a finit b CF xprssion of a can b writtn as q b + or in short [q, q, q, q m ] As an q + q ++ qm
4 xampl, tak th rational numbr 4 On can writ this as follows in th CF xprssion: 99 4 = = 0 + = 0 + = 0 + = 0 + = , an in short [0,,, 0, ] Consir a subsqunc of [0,,, 0, ] as [0,, ] ot that 0 + = =, + 99 which is vry clos to 4, i, a subsqunc of CF will giv an approximation of th rational 99 numbr Givn that a, b ar t bit intgrs, th CF xprssion [q, q, q,, q m ] of a can b b foun in O(poly(t)) tim an can b stor in O(poly(t)) spac Any initial subsqunc of [q, q, q,, q m ], i, [q, q, q,, q r ], whr r m is call th convrgnt of [q, q, q,, q m ] As xampl, [0,, ] is a convrgnt of [0,,, 0, ], i, = is a 99 convrgnt of 4 Also not that if th subsqunc has a at th n thn that may also 99 writtn by aing th to th prvious intgr an rmoving th That is, both [0,, ] an [0, ] provis th sam rational numbr w Wak Kys I It is known that if p q < 4 [7] (s also [5, Sction ]), thn RSA is wak by Frmat s factorization tchniqu Thus w ar intrst in th rang 4 < p q < only Proposition Lt p, q b of sam bit siz, i, q < p < q Thn φ() > B +, whr B = Furthr, if p q = β whr 4 < β <, thn φ() = A +, whr A = β + 4 Proof Sinc (p q)(p q) < 0, w hav + < φ() Also, as p q = β, w hav p β p = 0, putting q = Thus p = β + β +4 So w gt p + q = p + = p p β + β +4 = β + 4 Thn φ() = (p + q) + = A + β +4 + β + In [5], it has bn intifi that if p q = β, thn RSA is wak for = δ whn δ < β In such a cas t coul b foun as a convrgnt in th CF xprssion of 4 + Thus th rsult works bttr whn p, q ar clos As xampl, if p q = 4 +ɛ, thn δ is boun by ɛ As xampl, for ɛ = 005, RSA bcoms inscur if = 044 < 045 Howvr, this improvmnt is not significant whn p q is O( 05 ) Proposition Lt p q γ 6, whr γ < an Thn p+q ( + ) < γ 8 Proof W hav p q γ So 6 p p γ Hnc p p + p γ, 6 6 i, p + γ As + >, w hav p < γ Again p 6 p 6 multiplying q with th inquality p q γ, w hav 6 q q γ So w hav 6 q + γ As, w hav + > Hnc, q < γ q 6 q 6 i, q < γ 6 γ, as ow p+q ( + 6 ) p + q < γ 8
5 Thorm Lt p q γ with, γ an = δ Thn can b factor 6 in O(poly(log())) tim whn δ < γ Proof Sinc p q γ, w hav p + q ( + 6 ) < γ, 8 i, φ() + ( + ) < γ ow, 8 ( + ) + t ( + ) + φ() + φ() t = φ() ( ( + ) + ) φ() ( ( + ) + ) + φ() < φ() ( ( + ) + ) ( ( + ) + ) + φ() < γ 8 assuming ( + ) + > Thus, ) t < γ + ( + Whn γ <, w gt ( + + 4, an φ() > = γ ) + t < Putting = δ in th inquality γ <, w gt δ < γ This givs th proof 4 4 For xprimntal vincs, w work with prims p, q 0 60, i, 0 0 an = So in this cas w stuy th Continu Fraction of + Howvr, th xprimnts whn q p < n 4 may not b of intrst as in that cas th factorization can b on in polynomial tim similar to th argumnt of Frmat s factorization stratgy [7] (s also [5, Sction ]) Thus w consir th scnario whn q p > All th xampls in this papr (apart from th rsults rlat to lattic ruction) involving larg intgrs ar implmnt in LIUX nvironmnt using C with GMP Exampl W choos a ranom prim q [0 60, 0 6 ] Thn w choos a ranom prim p, such that q p > In this xampl, q p < 05 W thn choos th first gratr 6 than or qual to δ for δ such that is coprim to φ() W consir p, q rspctivly as an , which givs as
6 ot that q p > On can chck that φ() is Taking γ = 05, w gt δ < γ = 04 Thus, in this cas for any < 04, RSA will b inscur ow tak 0 < < 04 W consir = (a 04 igit numbr) Th corrsponing is Th valu of t is Hr t coul b foun in th CF xprssion of + Th CF xprssion of + is as follows 0,,,,, 5,,,,, 4,,,,,,,,,,, 8, 0,,,, 6,,,,, 7,, 5,,,,,,,,,,,,,, 4,, 5,, 6,,,, 5, 4,, 7, 4,, 5, 5,,, 45,, 54, 5,, 4,,, 8,,,,,,,,, 6,,,,, 7, 4,,, 5,,,,,, 4,, 0,,,,,, 8,,,,,, 7,,,, 4,, 6,,, 4,, 8, 6,, 4,,,,, 5,,, 7,,,,,, 0,,, 6,,, 5,, 4,,, 7,,,,,,,,, 4,,,,, 4,,, 4,,,,,, 50, 4,,, 4,,,,, 9, 6,,,, 8,,, 0, 6,,,,, 9,, 6,,,,,,,,,, 4,,, 7,,,, 4,,,,,, 4, 5,,,, 4,, 5, 4, 0,,,,,, 0,, 65, 0,,,,, 6,,, 5, 4, 6,, 9,,,,, 0,, 7,,,,,,,,,,,,, 7,,4,,,,, 5, 5, 6,,,,,,,,,,,,, 4,,,, 48,,, 6,, 7,,,, 9, 6, 4,, 4,, 4,,,,,,,,,,,,,,,, 0,, 0, 7,,, 6,,, 5, 5,,, 5,,,,,,,, 8,,,, 75,,, 4,,,, 7,,,, 7,, 5,, 5,,, 6,,, 4,, 4,,, 8, 6, 6,,, 5,,,,,,, 5, 4,, 6,,,,, 4,,,,,,,,, 7,,, 8,,, 8,,,, 8,,,, 47,, 5,, 0,, 9,,,, 8,,,,, 7,, 6, 5,,, 4,,,,,,,,,, 0,,,,, 4,,,,, 4,,,,,,,,,,,,,,, 57,,, 5,,, 0,,,,,, 7,,,,, 4,, 0, 8,, 5,,,, 5,,,,, 4, 4,, 45,,, 60,,,,,, 5, 4,,,,,,, 5, 4,,,,,,,, 0,,, 4,,, 7,,, 4,,,, 5,,,,,,,,,, 8,, 49, 9, 9,, 7, 4,, 5,, 7,, 8,,,, 4, 5,,, 5,, 94,, 6,,,,,,,, 6,,,, 4,,, 4,,, 55,, 7,,,,, 9,, 9,, 6,,,,,,,,, 6,, 4,,, 5,,, 6,, 4,, 8,,,,, 84, Th CF xprssion of t is as follows 0,,,,, 5,,,,, 4,,,,,,,,,,, 8, 0,,,, 6,,,,, 7,, 5,,,,,,,,,,,,,, 4,, 5,, 6,,,, 5, 4,, 7, 4,, 5, 5,,, 45,, 54, 5,, 4,,, 8,,,,,,,,, 6,,,,, 7, 4,,, 5,,,,,, 4,, 0,,,,,, 8,,,,,, 7,,,, 4,, 6,,, 4,, 8, 6,, 4,,,,, 5,,, 7,,,,,, 0,,, 6,,, 5,, 4,,, 7,,,,,,,,, 4,
7 ,,,, 4,,, 4,,,,,, 50, 4,,, 4,,,,, 9, 6,,,, 8,,, 0, 6,,,,, 9,, 6,,,,,,,,,, 4,,, 7,, Th mark in th CF xprssion of + points th trmination of th subsqunc for th CF xprssion of t This xampl corrspons to Thorm In fact, Thorm prsnts a sufficint conition on whn RSA will b wak In Exampl, it is shown that vn for som, gratr than th boun in Thorm, RSA can b inscur bas on som conition on Exampl shows that thr xists som vn gratr than whn RSA is inscur That is prsnt in Sction, whr w try to rmov th constraint on th iffrnc btwn th prims; insta an uppr boun on is consir Extnsion using lattic bas ia In this sction, w xploit lattic bas tchniqus following th ia of [4, Sction 4] This ia has bn us in [5, Sction 5] whn p q is boun W us similar ia whn q p is boun In this sction w rfr to th arlir works an o not xplain th ia rlat to lattics in tails To follow our rsults, on may n to go through th tail ias prsnt in [4, 5, 5,, 6] Lt = δ W assum = as for < on can gt bttr uppr boun on δ [4, Pag 9] W hav = + tφ() = + t( + p q) = + t ( + ( + ) (p + q ( + ) ) ) = + x(a + y), whr x = t < = δ, A = + ( + ), y = (p + q ( + ) ) Using =, w hav, x < δ, y < γ 8 W hav to fin x 0, y 0 such that + x 0 (A + y 0 ) 0 mo, whr x 0 < δ an y 0 < γ So w hav to fin th roots of th polynomial f(x, y) = + x(a + y) Lt X = δ, Y = γ Thn X, Y ar th uppr bouns of x 0, y 0 nglcting th constant trms As th polynomial f(x, y) w hav scrib hr is sam as th polynomial in [6, Thorms, 4, 5], th uppr bouns X, Y of th roots will also sam Hnc, w can us th sam analysis of [6, Thorms, 4, 5] to not that RSA is inscur unr th following conitions: δ < γ + γ(γ + ) ; () γ < δ < γ; () 6γ 4γ + 4 (6γ ) δ < () 5 Th sha rgion in Figur intifis th valus of γ, δ for which w fin that RSA is inscur In th figur, g(γ) = γ+ γ(γ+) (corrsponing to Inquality ), f(γ) = 6γ γ (corrsponing to Inquality ) an h(γ) = 4γ+4 (6γ ) (corrsponing to 5 Inquality ) Th lowr boun of th Inquality, i, γ is mark by a straight lin
8 δ=05 05γ δ=05 δ=09 δ=f(γ) δ=g(γ) δ= γ δ=h(γ) δ γ Fig Th rgion for δ an γ valus for which RSA is inscur Th cas δ = 05 corrspons to th rsult of [], th cas δ = 09 corrspons to th rsult of [5] an th cas δ = 05 05γ corrspons to our Thorm Exampl For lattic bas stratgy, w hav implmnt th program in SAGE 0 ovr Linux Ubuntu 704 on a computr with Dual CORE Intl(R) Pntium(R) D CPU 80GHz, GB RAM an MB Cach Th lattic paramtrs us hr ar m = 7, t = an on may rfr to [6] for scription of ths lattic paramtrs Th attackr knows only, as scrib blow an tris to fin out W consir sam as in Exampl Th public xponnt is Th corrsponing cryption xponnt ( igit numbr) is , which givs δ is 076 Th valu of t is For th cass corrsponing to Inqualitis, an, w gt th lattics of imnsion w = 60, 5 an rspctivly an th rquir tims to fin ar 789, 774 an 409 scons Th ia of continu fraction mtho as xplain in Thorm will not work in this cas as th valu of δ is highr
9 RSA is wak whn is O( ) an is O( ) Lmma Lt < δ, whr 0 < δ Lt A, B b as in Proposition Thn for δ A+, it is possibl to gt z z such that B A+ z t z t < B+ z z whn < δ + z z < whn k < z B+ z an A+ A+ Proof As w hav < t, thr ar two cass with th conition z z > t t z but 0 z t < but 0 t z z < Cas Th conition hr is: t but 0 z z t < Thus, w hav to satisfy 0 z tz z <, i, 0 z +z tφ() tz z < t > Lt < δ, for δ > 0 Thn 0 z +z tφ() tz z < δ implis 0 z +z tφ() tz z < So w n to stimat z z consiring 0 z +z tφ() tz z < δ ow 0 z +z tφ() tz z < iff 0 z δ t z z ( + tφ()) < k + t iff φ() z z < δ +t if B+ z z (i) Proposition, (ii) > A+ δ δ z ( + tφ()) t < δ iff < δ +t if t +tφ() z z < δ + +tφ(), following A+ > δ, an (iii) = + tφ() t = φ() To hav an z z, w n < δ + B+ A+ For th guarant of gtting a rational z z in th intrval [, k + ), on may choos Clarly, < < B+ A+ B + B+ B + Thus, k + n to b satisfi This givs, B B A+ = (B+)+ δ A+ B A+ Cas Th conition hr is: t but 0 t With similar analysis, w gt δ < z B+ z, which again givs th sam uppr boun for A+ z z < Thorm Consir th intrval I such that I = ( δ, δ + ) Lt < δ, whr 0 < δ Thn for B+ A+ δ A+, an z z I, z z t < B A+ z Proof From Lmma w gt that z t < for th intrvals z B+ z < k + an k < z A+ B+ z A+ Sinc, δ < < z B+ A+ B+ z < δ +, it is nough to A+ hav z z in th intrval I = ( δ, δ + ) to gt z B+ A+ z t < for δ < δ A+ B A+
10 A+ B A+ Corollary Lt < δ, whr 0 < δ an δ in poly(log ) tim Proof Th proof follows from Lmma as will b foun in th CF xprssion of CF xprssion of B + < B+ B + < δ + z z whn z z = B + Thus t Thn can b factor Thn t A+ will b foun in th Blow w prsnt th summariz rsult which is a consrvativ on as th uppr boun of is unrstimat This rsult is gnral as it os not rquir th paramtr β for th proof, whr p q = β Thorm Lt = pq, whr p, q ar prims such that q < p < q Thn can b factor in poly(log ) tim from th knowlg of, whn < δ an is O( δ ) for δ Proof W hav, δ ) B = ( δ ( A+) B A+ ( B) A+ A+, whn β is nglct Thus, δ, an this incrass as A incrass Also th lowr boun of A is + + an this is O( δ ) Th rsults givn in Thorms, o not put any constraint on th iffrnc of th prims to gt a bttr boun on, but th constraint is impos on Whn < δ, thn A+ B A+ with incras in th valu of δ, th valu of bcoms uppr boun by δ In [5, Sction 4], CF xprssion of only a spcific valu + to gt t Thus compar to our cas, z z is approximat by Consiring Lmma, if + < b us to gt th prims, but our mtho will work Th xact algorithm for our propos attack is as follows + has bn xploit in [5, Sction 4] B+ δ, thn th approach of [5] may not Input:,, δ Comput th CF xprssion of + For vry convrgnt t of th xprssion abov if th roots of x ( + t )x + = 0 ar positiv intgrs lss than thn rturn th roots as p, q; Rturn ( failur ); Our consrvativ stimat shows that th RSA kys ar wak whn < δ an is O( δ ) For xampl, consiring δ = 0, 04, 045, 05, is boun by O( 09 ), O( 07 ), O( 06 ), O( 05 ) rspctivly
11 Howvr, w lik to point out that this is a consrvativ stimat an actually th uppr boun of is much bttr W hav δ A+ an th attack works for < n δ Thus th attack will work whn B A+ (+) A+ B A+, taking δ = + Exampl Rfr to p, q of Exampl W consir >, which is (a 07 igit numbr) Th corrsponing is (+) ot that, w n to chck A+ B A+ (+) A+ is B A , taking δ = + an th valu of , which is gratr than in Th valu of t is Hr t coul b foun in th CF xprssion of + Th CF xprssion of + is as follows 0, 8878,,, 4,,,,,, 8,, 54,, 7, 0,,, 44,,,, 68,, 9,,,, 8,,,,, 4,,,,, 4,,,,, 9,,,,, 06,,,, 9, 4, 9,,, 86,,,, 6,,,, 5, 4,,, 6,, 4,, 6,,,, 4, 8, 7,, 4,,,, 7,, 65,,, 6,,, 7, 9,,, 5,,,,,, 5,,,,, 4,,,, 4,,,, 4,,,,,,,,,, 5,,, 4, 4,,,, 0,,,,,,,,, 7,,,,,, 0,,,, 4,,,,,,, 69,,,,, 68,,,,, 4, 4,,, 5,, 5, 8, 6,,,,,, 4,,,, 4,,, 8,,,,,,,,,,,,,,,, 5,, 8,,,,,, 7, 4,,,,,, 6,,,, 47,,, 4,,,,,, 0, 4,,, 5,,, 0,,, 4,,,, 0,,,, 5, 9,, 6,,,, 4,, 5,, 457,,,, 9, 5,,,, 9,,,,,, 4, 58,, 4, 6,,,, 5,,,,, 4,,,, 6, 4,, 5,,,, 6, 47, 4,,,,,,,,,,,,, 7,,,, 5,,,,,,, 5,,,,,,, 7,, 0,,,, 5,,,,, 5,,,,, 4,, 9,,, 8,,,,,,, 7,,,,,,,, 0,,,, 4, 5,,,,,, 59,, 0,, 9,, 7, 9,, 7,,,,,, 5,,,,,, 8,,,,, 6,,, 7,, 7,,,, 0,,,,,,,,,,, 4,,, 8,,,,,,, 8,,,,, 6, 4, 9,,, 5,,,, 6, 8,, 6,,,,, 4,, 4,,,, 4,, 4,,,,,,, 5, 4,,,,, 6,,,,, 6,, 5,, 7,,,,,,,,,,,,, 5,, 5,,,, 9,,, 6, 5,,, 6,, 7, 4,,,,,,,, 6, 4,,,,,,, 6,, 7,,,, 8,,,,,,,,,,,, 4,,, 0,,,, 4,,,,,,,, 5,,,,,, 7,, 4, 6,, 5,,, 4,,, 0,,, 6,, 5,,,,, 6, 8,,, 9,,,,,,,,,,,,,,,,,,,, 4,,, 7,,, 4,, 7, 6, 6,, 4,, 4,, 6,, Th CF xprssion of t is as follows 0, 8878,,, 4,,,,,, 8,, 54,, 7, 0,,, 44,,,, 68,, 9,,,, 8,,,,, 4,,,,, 4,,,,, 9,,,,, 06,,,, 9, 4, 9,,, 86,,,, 6,,,, 5, 4,,, 6,, 4,, 6,,,, 4, 8, 7,
12 , 4,,,, 7,, 65,,, 6,,, 7, 9,,, 5,,,,,, 5,,,,, 4,,,, 4,,,, 4,,,,,,,,,, 5,,, 4, 4,,,, 0,,,,,,,,, 7,,,,,, 0,,,, 4,,,,,,, 69,,,,, 68,,,,, 4, 4,,, 5,, 5, 8, 6,,,,,, 4,,,, 4 Th mark in th CF xprssion of + points th trmination of th subsqunc for th CF xprssion of t ) This xampl corrspons to Corollary On may chck that t will not b foun in th continu fraction xprssion of (Winr s rsult []) or (Wgr s rsult [5, Sction 4]) in Exampl In this + xampl, 65 Actually, th boun 5 in Thorm is a consrvativ approximation of th rsult in Corollary In practic, w may gt rsults whn is gratr than 5 In [5, Sctions 5, 6], th approach of [4] has bn us to slightly improv th bouns of [5, Sctions 4] Th improvmnt in that cas is not vint whn p q approachs an it os not covr our rsults In Exampl, < p q < Thus, for p q = β, β > For β = 04995, w gt δ < β = 096 Thus th mtho of [5, Sction 6] will work for < 096 Our xampl consirs > an hnc not contain in th wak kys prsnt in [5, Sction 6] ow w prsnt anothr xampl Exampl 4 Rfr to p, q of Exampl W consir > Lt = (a 07 igit numbr) Th corrsponing is (+) ow th valu of A+ is B A , which is smallr than an thus th conition in Corollary is not satisfi Th valu of t is Th CF xprssion of + is as follows 0, 4,, 6, 49,, 6, 0, 74,,,,,,,, 4,,,,,,,,4,,, 4,,,, 9,,,,,, 6,,,,, 9,,,,,, 7,, 5,,,, 4,,,,, 88,,, 5,,,,, 6,,,,,, 9,,,,, 4,,,,,,,,,,,,,, 4,,, 5,,, 7,,, 6,,,, 7,,,,,, 8, 9,, 5,, 4,,, 6,,,, 5,, 4,,,, 5,,,,,,,,, 6,,,,,,,,, 8,,,, 5,, 4, 4, 0,,,,,,,, 9, 6,,,,,,,,,, 5, 5,, 4,, 7,,,,,,, 5,,,,, 7, 7,,,, 7,,, 6,,,,, 4, 5,,, 9,,,,,, 5,,, 5,,,,, 6,,, 7, 0,,, 7, 4, 7,,, 5,, 4,,,,
13 ,, 5,,,,,,, 6, 6,, 0,,,, 6,,,,,,,,,,,, 8,, 9,,,, 6,, 5,,, 0, 9,, 4,, 9,,,, 4, 6, 0,,, 5, 0, 4,,,, 4, 9,,,,,,, 4,,,,,,, 5, 4,, 5,,, 4,, 6, 4, 8,, 8, 47, 0,,,, 7,,,,,,, 0,,,, 9, 440,,,, 6,,,,,,,,,,,, 48, 6,, 5,,, 4,,, 4, 4, 9, 50,, 8,,,,,,, 4,,, 5, 9, 7,,,,,,, 8,, 6,,, 4,, 4,, 6,,, 4, 6,,, 6, 7, 6,, 4, 8,,,,,,,,, 8,,,,,,,,, 4, 5,, 5,,, 4,,, 78,,,,,,,,, 4, 6,,,,,,,, 6,, 76,,,,,,,,,, 5,,,,,, 6,,,,, 5,, 9,, 40,,,, 7,,,, 4,, 5,, 4,,,,,,,, 5,, 9,,, 5,,,,,,, 9,,, 7,,,,,, 5,,, 4, 4,,,,, 7,, 5,,, 8,,,,,,,,,,,, 6,,,, 6,,,,,, 6,,,,, 6,,,,, 5, 5,,,,, 4,,,,,,, 9,,, 9,,, 5,,,, 9,,,,,,, 8,,,,,, 4,,,,, 6,,,,, 4,,,, 4,, 0,,,, 8, 9,,,,,,, 44, 7868,,, Th CF xprssion of t is as follows 0, 4,, 6, 49,, 6, 0, 74,,,,,,,, 4,,,,,,,, 4,,, 4,,,, 9,,,,,, 6,,,,, 9,,,,,, 7,, 5,,,, 4,,,,, 88,,, 5,,,,, 6,,,,,, 9,,,,, 4,,,,,,,,,,,,,, 4,,, 5,,, 7,,, 6,,,, 7,,,,,, 8, 9,, 5,, 4,,, 6,,,, 5,, 4,,,, 5,,,,,,,,, 6,,,,,,,,, 8,,,, 5,, 4, 4, 0,,,,,,,, 9, 6,,,,,,,,,, 5, 5,, 4,, 7,,,,,,, 5,,,,, 7, 7,,,, 7,,, 6,,,,, 4, 5,,, 9,,,,,, 5,,, 0 ot that th CF xprssion of t coul not b foun (last thr placs o not match) in th CF xprssion of + Rmark W prsnt Exampl 4 to show th ffcts of th uppr boun on in Thorm as wll as th uppr bouns on, in Corollary ot that of Exampl < of Exampl 4 < of Exampl For th of Exampl 4, t cannot b foun in th CF xprssion of + Th of Exampl 4 os not satisfy th conition givn in Thorm On th othr han, though of Exampl 4 < of Exampl, th boun on corrsponing to Corollary is not satisfi in Exampl 4 On may not that in Exampl 4, th CF xprssion of t os not match only in thr placs at th n with th initial subsqunc of th CF xprssion of + Thus, th ia of sarch in th lin of [] will actually provi th xact rsult with som xtra ffort w Wak Kys II Lt us rstat th rsult of [, Thorm ], whr it was prov that p, q can b foun in polynomial tim for vry, satisfying x + y 0 mo φ(), with x 4 an y = O( 4 x) Consir that x + y 0 mo φ() an th intrst is on th nontrivial cass Thus x+y = m( p q +) This givs m = m(p+q )+y If m = m(p+q )+y <, x x x x x thn th fraction m appars among th convrgnts of Thus on ns to fin out th x
14 conitions such that m(p + q ) + y < is satisfi Calculation shows that for y = x O( 4 x), on gts x 4 ot that insta of trying to fin m among th convrgnts of, a bttr attmpt will x b to fin m among th convrgnts of, whr x φ () φ () is a bttr stimat than for φ() Following th ia of [5], φ () has bn takn as (i, th uppr boun of φ()) an th CF xprssion of has bn consir to stimat m in [, Sction x 4] It has bn prov in [, Thorm 4, Sction 4] that p, q can b foun in polynomial tim for vry, satisfying x + y 0 mo φ(), with x φ() 4 an y p q x p q φ() 4 ow w start with th following Lmma Lmma Lt x + y = mφ() for m > 0 Thn whn y c 4 x, whr c an p q c Proof Lt us list th following obsrvations + m < for x 7 x x 4 4 From Proposition, w hav + < φ() < +, which givs, ( ) < p+q < 0 Thus, ( ) > p+q, i, ( ) > p + q Also not that y c 4 x, which givs y < x 4 as < an c From [, Proof of Thorm ], x m 5 x 4 φ() 4 φ() ow, This givs, + m x = m( p q+ ) y x( +) + m x < m(( ow, m(( ) )+ y x( +) < x if 5 4 if 5 4 x(( ) )+x 4 x( +) < x (as if ( +) < ) )+ y x( +) using itm x φ() (( ) )+x 4 x( +) < x (using itms, ) φ() < ) iff 5 4 (( ) )+ 4 ( +) < x x (as < 0 an 5 4 ( ) ) + 4 < for larg ) iff 5 0x < + if x < 076 (for larg ) if x 75 4 This shows that th class of wak kys intifi in [, Thorm ] can b xtn by, i, by mor than 5 tims 4 In th improv rsult of [, Thorm 4, Sction 4], it has bn shown that p, q can b foun in polynomial tim for vry, satisfying x + y = 0 mo φ(), with 0 < x φ() 4 p q an y p q φ() 4 x Our rsult in Lmma provis nw wak kys which ar not covr by th rsult of [, Thorm 4, Sction 4] in crtain cass as follows
15 Lt p q = c As, q < p < q, w hav p q < Thus, c < In [, Thorm 4, Sction 4], it is givn that x φ() 4 Putting p q = c, w fin x φ() 4 p q c Thus our rsult in Lmma provis xtra wak kys than [, Thorm 4, Sction 4] whn c φ() 4 < 7 4, which is tru for > ( ) 4 4 φ() c As < φ(), 4 <, which givs c Thus th rsult our Lmma prsnts nw wak kys ovr In [, Thorm 4, Sction c > 4 4] whn > ( ) 4 φ() c for 4 < c < xt w us our ia of consiring q p (as prsnt in Proposition ) insta of p q Thorm 4 Lt q p γ whr an γ Suppos satisfis th quation x+y = mφ(), for m > 0 Thn can b factor in O(poly(log())) tim whn 0 < x φ() γ an y q p x 6 φ() 4 Proof W hav m = x+y Using th boun on y, w gt m x φ() ( ) m = x m ( + ) ) + ( ) + x ( + ( = m ( x ( m ( x ( ( + ) p q ( + ) + ( + ) p q x φ() ( + ) + q p (+ φ() ) 4 th uppr ( boun of y) )( = φ() < φ() x ( q p (+ φ() 4 ) x ( + ) + ) y ) (putting x = y + mφ()) ) + y ) )( ) ( + ) p q + q p φ() 4 x ( + ) + ( + ) p q)+ q p φ() 4 ( ( + ) + γ + γ γ 4 ( + ) + < γ φ() ( + ) + ) ( φ() + q p ) ow, φ() 4 ) (putting th uppr boun on m an using (Using q p γ an + ) p q < γ ) < 8 γ (Assum ( + φ() ) + > ) 6 So w gt m via CF xpansion of x < φ() x i, x < 6 Givn, φ() γ ( + ) if + ( + ) m <, can b factoriz using [, Algorithm Gnraliz + x x Winr Attack II] Th rsult of [, Thorm 4, Sction 4] stats that p, q can b foun in polynomial tim for vry, satisfying x+y 0 mo φ(), with 0 < x φ() 4 p q an y p q φ()n 4 x
16 In our rsult p q is rplac by q p whr is known to th attackr Thus th rsults of this sction prsnt nw wak kys othr than thos prsnt in [] Th rsult of [, Thorm 4, Sction 4] works fficintly whn p q is uppr boun an our work givs bttr rsults whn q p is uppr boun A Practical Exampl an Enumration of Wak Kys Exampl 5 W consir sam (065-bit intgr) as in Exampl an tak = Hr public xponnt is 050-bit intgr Using th convrgnts of CF xprssion, w fin x as an m as As, + x = p + q + y, with th knowlg of,, x, m on can gt a goo m m approximation of p + q whn y is in th spcifi boun (in this cas, y is in insi th boun having th valu 498) Thn using th ia of [6], th valus of factors p, q can b known in O(poly(log())) tim In this xampl, is 06-bit intgr ow w lik to point out that th wak ky of Exampl 5 is not covr by th works of [, 5, ] In this cas, th cryption xponnt is a 0-igit intgr ( > 099 ) an hnc th boun of [] that < 4 will not work hr Hr p q > 049 an accoring to [5, Sction 6] on can consir β = 049 If = δ, thn accoring to [5, Sction 6] th boun of δ will b 4β < δ < β for RSA to b inscur Putting β = 049, on can gt 004 < δ < 0 In Exampl 5, > 099 an hnc th wak kys of [5] os not covr our rsult In [, Thorm 4, Sction 4], it has bn shown that p, q can b foun in polynomial tim for vry, satisfying x + y = mφ(), with 0 < x Accoring to [], convrgnts of th CF xprssion of φ() 4 p q an y p q φ() 4 x will provi m For th x φ() 4 p q paramtrs in Exampl 5, w calculat all th convrgnts with x an w fin that for ach such m, x, x mφ() > p q x As y = x mφ(), th boun on φ() 4
17 y is not satisfi Thus th wak ky prsnt in Exampl 5 is not covr by th work of [] To stimat th numbr of wak kys, w us th sam approach as in [] W first us th following xisting rsult Lmma [, Lmma 6] Lt f(, ), g(, ) b functions such that f (, )g(, ) < φ(), f(, ) an g(, ) f(, ) Th numbr of public kys Zφ(), φ() 4 that satisfy an quation x + y 0 mo φ() for x f(, ) an y g(, )x is at last f (, )g(, ) 8 log log ( ) O(f (, ) ɛ ), whr ɛ > 0 is arbitrarily small for suitably larg ow w prsnt our stimat using similar analysis as in [, Thorm 7] First lt us prsnt th finition of th class of wak kys as prsnt in [, Dfinition 5] Dfinition Lt C b a class of RSA public kys (, ) Th siz of th class C is fin by siz C () = { Zφ() (, ) C C is call wak if siz C () = Ω( γ ) for som γ > 0 Thr xists a probabilistic algorithm which on vry input (, ) C outputs th factorization of in O(poly(log )) tim Thorm 5 Lt q p = 4 +γ with 0 < γ Furthr, lt C b th wak class that is 4 givn by th public ky tupls (, ) fin in th Thorm 4 with th aitional rstrictions that Zφ() φ() an Thn siz 4 C () = Ω( 4 ) Proof Hr f(, ) = φ(), an g(, ) = q p Clarly f(, ) Also, 6 q p φ() 4 f (, )g(, ) < φ() Again g(, ) f(, ) Hnc, w can apply Lmma Sinc g(, ) = Ω( γ ), th trm f (, )g(, ) 8 log log ( ) ominats th rror trm O(f (, ) ɛ ) Using f (, )g(, ) = Ω( 4 ), w gt th stimat 4 Conclusion In this papr w stuy th wll known mtho of Continu Fraction (CF) xprssion to monstrat nw wak kys of RSA Th ia is to factoriz using th knowlg of an som stimat of φ() On may not that in most of th cass t can b foun in th CF xprssion of This ia was first propos in [], whr th CF xprssion has bn φ()
18 us to stimat t, i, has bn us as an stimat of φ() Latr to that, + (an uppr boun of φ()) has bn us as an stimat of φ() in many works, g, [5, ] In this papr w hav stui both th uppr an lowr bouns of φ() carfully an us ( + ) + as an stimat of φ() W xtnsivly stuy th cass whn t can b foun in th CF xprssion of ( + ) Our rsults provi nw wak kys ovr + th work of [5, ] an to th bst of our knowlg th wak kys intifi in our papr hav not bn prsnt arlir Acknowlgmnts: Th authors lik to thank Prof Bnn Wgr for his tail commnts on an initial vrsion of this papr post at on -Jul- 008 Motivat by that, w hav introuc th paramtr in this papr Prof Wgr has also point out that th paramtr τ (in th sai vrsion of this papr) cannot b consir small Bas on ths, w hav moifi Thorms an 4 in this vrsion W also thank th anonymous rviwrs of this papr for thir commnts that improv th tchnical as wll as itorial quality of this papr Th scon author liks to acknowlg th Council of Scintific an Inustrial Rsarch (CSIR), Inia for supporting his rsarch fllowship Rfrncs J Blömr an A May Low scrt xponnt RSA rvisit CaLC 00, LCS 46, pp 4 9, 00 J Blömr an A May A gnraliz Winr attack on RSA PKC 004, LCS 947, pp, 004 D Bonh Twnty Yars of Attacks on th RSA Cryptosystm otics of th AMS, 46():0, Fbruary, D Bonh an G Durf Cryptanalysis of RSA with privat ky lss than 09 Eurocrypt 999, LCS 59, pp, D Bonh an G Durf Cryptanalysis of RSA with privat ky lss than 09 IEEE Trans on Information Thory, 46(4):9 49, D Coppprsmith Small solutions to polynomial quations an low xponnt vulnrabilitis Journal of Cryptology, 0(4): 60, J -S Coron an A May Dtrministic Polynomial-Tim Equivalnc of Computing th RSA Scrt Ky an Factoring J Cryptology 0():9 50 (007) 8 A Dujlla Continu fractions an RSA with small scrt xponnt Tatra Mt Math Publ, vol 9, pp 0, E Jochmsz Cryptanalysis of RSA variants using small roots of polynomials Ph D thsis, Tchnisch Univrsitit Einhovn, J Hasta On using RSA with low xponnt in public ky ntwork Lctur ots in Computr Scinc, Avancs in Cryplogy-CRYPTO 85 Procings w York: Springr-Vrlag, pp D Ibrahim, H M Bahig, A Bhry an S S Daou A nw RSA vulnrability using continu fractions In th 6th ACS/IEEE Intrnational Confrnc on Computr Systms an Applications (AICCSA 008), March April 4, 008, Doha, Qatar E Jochmsz an A May A Polynomial Tim Attack on RSA with Privat CRT-Exponnts Smallr Than 007 CRYPTO 007, LCS 46, pp 95 4 J M Pollar Thorms on factorization an primality tsting Proc of Combrig Philos Soc, vol 76, pp 5 58, R L Rivst, A Shamir an L Alman A mtho for obtaining igital signaturs an public ky cryptosystms Communications of ACM, ():58 64, Fb K H Rosn Elmntary umbr Thory Aison-Wsly, Raing Mass, 984
19 6 S Sarkar, S Maitra an S Sarkar RSA Cryptanalysis with Incras Bouns on th Scrt Exponnt using Lss Lattic Dimnsion Cryptology Print Archiv: Rport 008/5, Availabl at 7 R D Silvrman Fast gnration of ranom, strong RSA prims Cryptobyts, ():9, D R Stinson Cryptography Thory an Practic n Eition, Chapman & Hall/CRC, 00 9 R Stinfl, S Contini, J Piprzyk an H Wang Convrs rsults to th Winr attack on RSA PKC 005, LCS 86, pp 84 98, H -M Sun an C -T Tang RSA with Balanc Short Exponnts an Its Application to Entity Authntication PKC 005, LCS 86, pp 99 5, 005 H -M Sun, M -E Wu an Y -H Chn Estimating th prim-factors of an RSA moulus an an xtnsion of th Winr attack ACS 007, LCS 45, pp 6 8, 007 E R Vrhul an H C A van Tilborg Cryptanalysis of lss short RSA scrt xponnts Applicabl Algbra in Enginring, Communication an Computing, vol 8, pp 45 45, 997 M Winr Cryptanalysis of short RSA scrt xponnts IEEE Transactions on Information Thory, 6():55 558, H C Williams A p + mtho of factoring Mathmatics of Computation, 9(59):5 4, July 98 5 B Wgr Cryptanalysis of RSA with small prim iffrnc Applicabl Algbra in Enginring, Communication an Computing, ():7 8, 00
A generalized attack on RSA type cryptosystems
 A gnralizd attack on RSA typ cryptosystms Martin Bundr, Abdrrahman Nitaj, Willy Susilo, Josph Tonin Abstract Lt N = pq b an RSA modulus with unknown factorization. Som variants of th RSA cryptosystm, such
A gnralizd attack on RSA typ cryptosystms Martin Bundr, Abdrrahman Nitaj, Willy Susilo, Josph Tonin Abstract Lt N = pq b an RSA modulus with unknown factorization. Som variants of th RSA cryptosystm, such
BINOMIAL COEFFICIENTS INVOLVING INFINITE POWERS OF PRIMES
 BINOMIAL COEFFICIENTS INVOLVING INFINITE POWERS OF PRIMES DONALD M. DAVIS Abstract. If p is a prim (implicit in notation and n a positiv intgr, lt ν(n dnot th xponnt of p in n, and U(n n/p ν(n, th unit
BINOMIAL COEFFICIENTS INVOLVING INFINITE POWERS OF PRIMES DONALD M. DAVIS Abstract. If p is a prim (implicit in notation and n a positiv intgr, lt ν(n dnot th xponnt of p in n, and U(n n/p ν(n, th unit
BINOMIAL COEFFICIENTS INVOLVING INFINITE POWERS OF PRIMES. 1. Statement of results
 BINOMIAL COEFFICIENTS INVOLVING INFINITE POWERS OF PRIMES DONALD M. DAVIS Abstract. If p is a prim and n a positiv intgr, lt ν p (n dnot th xponnt of p in n, and u p (n n/p νp(n th unit part of n. If α
BINOMIAL COEFFICIENTS INVOLVING INFINITE POWERS OF PRIMES DONALD M. DAVIS Abstract. If p is a prim and n a positiv intgr, lt ν p (n dnot th xponnt of p in n, and u p (n n/p νp(n th unit part of n. If α
The second condition says that a node α of the tree has exactly n children if the arity of its label is n.
 CS 6110 S14 Hanout 2 Proof of Conflunc 27 January 2014 In this supplmntary lctur w prov that th λ-calculus is conflunt. This is rsult is u to lonzo Church (1903 1995) an J. arkly Rossr (1907 1989) an is
CS 6110 S14 Hanout 2 Proof of Conflunc 27 January 2014 In this supplmntary lctur w prov that th λ-calculus is conflunt. This is rsult is u to lonzo Church (1903 1995) an J. arkly Rossr (1907 1989) an is
Derangements and Applications
 2 3 47 6 23 Journal of Intgr Squncs, Vol. 6 (2003), Articl 03..2 Drangmnts and Applications Mhdi Hassani Dpartmnt of Mathmatics Institut for Advancd Studis in Basic Scincs Zanjan, Iran mhassani@iasbs.ac.ir
2 3 47 6 23 Journal of Intgr Squncs, Vol. 6 (2003), Articl 03..2 Drangmnts and Applications Mhdi Hassani Dpartmnt of Mathmatics Institut for Advancd Studis in Basic Scincs Zanjan, Iran mhassani@iasbs.ac.ir
Introduction to Arithmetic Geometry Fall 2013 Lecture #20 11/14/2013
 18.782 Introduction to Arithmtic Gomtry Fall 2013 Lctur #20 11/14/2013 20.1 Dgr thorm for morphisms of curvs Lt us rstat th thorm givn at th nd of th last lctur, which w will now prov. Thorm 20.1. Lt φ:
18.782 Introduction to Arithmtic Gomtry Fall 2013 Lctur #20 11/14/2013 20.1 Dgr thorm for morphisms of curvs Lt us rstat th thorm givn at th nd of th last lctur, which w will now prov. Thorm 20.1. Lt φ:
First order differential equation Linear equation; Method of integrating factors
 First orr iffrntial quation Linar quation; Mtho of intgrating factors Exampl 1: Rwrit th lft han si as th rivativ of th prouct of y an som function by prouct rul irctly. Solving th first orr iffrntial
First orr iffrntial quation Linar quation; Mtho of intgrating factors Exampl 1: Rwrit th lft han si as th rivativ of th prouct of y an som function by prouct rul irctly. Solving th first orr iffrntial
10. EXTENDING TRACTABILITY
 Coping with NP-compltnss 0. EXTENDING TRACTABILITY ining small vrtx covrs solving NP-har problms on trs circular arc covrings vrtx covr in bipartit graphs Q. Suppos I n to solv an NP-complt problm. What
Coping with NP-compltnss 0. EXTENDING TRACTABILITY ining small vrtx covrs solving NP-har problms on trs circular arc covrings vrtx covr in bipartit graphs Q. Suppos I n to solv an NP-complt problm. What
Recall that by Theorems 10.3 and 10.4 together provide us the estimate o(n2 ), S(q) q 9, q=1
 Chaptr 11 Th singular sris Rcall that by Thorms 10 and 104 togthr provid us th stimat 9 4 n 2 111 Rn = SnΓ 2 + on2, whr th singular sris Sn was dfind in Chaptr 10 as Sn = q=1 Sq q 9, with Sq = 1 a q gcda,q=1
Chaptr 11 Th singular sris Rcall that by Thorms 10 and 104 togthr provid us th stimat 9 4 n 2 111 Rn = SnΓ 2 + on2, whr th singular sris Sn was dfind in Chaptr 10 as Sn = q=1 Sq q 9, with Sq = 1 a q gcda,q=1
(Upside-Down o Direct Rotation) β - Numbers
 Amrican Journal of Mathmatics and Statistics 014, 4(): 58-64 DOI: 10593/jajms0140400 (Upsid-Down o Dirct Rotation) β - Numbrs Ammar Sddiq Mahmood 1, Shukriyah Sabir Ali,* 1 Dpartmnt of Mathmatics, Collg
Amrican Journal of Mathmatics and Statistics 014, 4(): 58-64 DOI: 10593/jajms0140400 (Upsid-Down o Dirct Rotation) β - Numbrs Ammar Sddiq Mahmood 1, Shukriyah Sabir Ali,* 1 Dpartmnt of Mathmatics, Collg
New Attacks on RSA with Modulus N = p 2 q Using Continued Fractions
 Journal of Physics: Confrnc Sris PAPER OPEN ACCESS Nw Attacks on RSA with Modulus N = p q Using Continud Fractions To cit this articl: M A Asbullah and M R K Ariffin 015 J. Phys.: Conf. Sr. 6 01019 Viw
Journal of Physics: Confrnc Sris PAPER OPEN ACCESS Nw Attacks on RSA with Modulus N = p q Using Continud Fractions To cit this articl: M A Asbullah and M R K Ariffin 015 J. Phys.: Conf. Sr. 6 01019 Viw
The Matrix Exponential
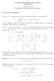 Th Matrix Exponntial (with xrciss) by D. Klain Vrsion 207.0.05 Corrctions and commnts ar wlcom. Th Matrix Exponntial For ach n n complx matrix A, dfin th xponntial of A to b th matrix A A k I + A + k!
Th Matrix Exponntial (with xrciss) by D. Klain Vrsion 207.0.05 Corrctions and commnts ar wlcom. Th Matrix Exponntial For ach n n complx matrix A, dfin th xponntial of A to b th matrix A A k I + A + k!
LINEAR DELAY DIFFERENTIAL EQUATION WITH A POSITIVE AND A NEGATIVE TERM
 Elctronic Journal of Diffrntial Equations, Vol. 2003(2003), No. 92, pp. 1 6. ISSN: 1072-6691. URL: http://jd.math.swt.du or http://jd.math.unt.du ftp jd.math.swt.du (login: ftp) LINEAR DELAY DIFFERENTIAL
Elctronic Journal of Diffrntial Equations, Vol. 2003(2003), No. 92, pp. 1 6. ISSN: 1072-6691. URL: http://jd.math.swt.du or http://jd.math.unt.du ftp jd.math.swt.du (login: ftp) LINEAR DELAY DIFFERENTIAL
Construction of asymmetric orthogonal arrays of strength three via a replacement method
 isid/ms/26/2 Fbruary, 26 http://www.isid.ac.in/ statmath/indx.php?modul=prprint Construction of asymmtric orthogonal arrays of strngth thr via a rplacmnt mthod Tian-fang Zhang, Qiaoling Dng and Alok Dy
isid/ms/26/2 Fbruary, 26 http://www.isid.ac.in/ statmath/indx.php?modul=prprint Construction of asymmtric orthogonal arrays of strngth thr via a rplacmnt mthod Tian-fang Zhang, Qiaoling Dng and Alok Dy
Cryptanalysis of Improved Liaw s Broadcasting Cryptosystem *
 JOURNAL OF INFORMATION SCIENCE AND ENGINEERING 22, 391-399 (26) Cryptanalysis of Improv Liaw s Broacasting Cryptosystm * J. MUÑOZ MASQUÉ AND A. PEINADO ** Dpartamnto Trataminto la Informacióny Coificación
JOURNAL OF INFORMATION SCIENCE AND ENGINEERING 22, 391-399 (26) Cryptanalysis of Improv Liaw s Broacasting Cryptosystm * J. MUÑOZ MASQUÉ AND A. PEINADO ** Dpartamnto Trataminto la Informacióny Coificación
The Matrix Exponential
 Th Matrix Exponntial (with xrciss) by Dan Klain Vrsion 28928 Corrctions and commnts ar wlcom Th Matrix Exponntial For ach n n complx matrix A, dfin th xponntial of A to b th matrix () A A k I + A + k!
Th Matrix Exponntial (with xrciss) by Dan Klain Vrsion 28928 Corrctions and commnts ar wlcom Th Matrix Exponntial For ach n n complx matrix A, dfin th xponntial of A to b th matrix () A A k I + A + k!
1 Minimum Cut Problem
 CS 6 Lctur 6 Min Cut and argr s Algorithm Scribs: Png Hui How (05), Virginia Dat: May 4, 06 Minimum Cut Problm Today, w introduc th minimum cut problm. This problm has many motivations, on of which coms
CS 6 Lctur 6 Min Cut and argr s Algorithm Scribs: Png Hui How (05), Virginia Dat: May 4, 06 Minimum Cut Problm Today, w introduc th minimum cut problm. This problm has many motivations, on of which coms
Chapter 10. The singular integral Introducing S(n) and J(n)
 Chaptr Th singular intgral Our aim in this chaptr is to rplac th functions S (n) and J (n) by mor convnint xprssions; ths will b calld th singular sris S(n) and th singular intgral J(n). This will b don
Chaptr Th singular intgral Our aim in this chaptr is to rplac th functions S (n) and J (n) by mor convnint xprssions; ths will b calld th singular sris S(n) and th singular intgral J(n). This will b don
Multiple Short Term Infusion Homework # 5 PHA 5127
 Multipl Short rm Infusion Homwork # 5 PHA 527 A rug is aministr as a short trm infusion. h avrag pharmacokintic paramtrs for this rug ar: k 0.40 hr - V 28 L his rug follows a on-compartmnt boy mol. A 300
Multipl Short rm Infusion Homwork # 5 PHA 527 A rug is aministr as a short trm infusion. h avrag pharmacokintic paramtrs for this rug ar: k 0.40 hr - V 28 L his rug follows a on-compartmnt boy mol. A 300
The Equitable Dominating Graph
 Intrnational Journal of Enginring Rsarch and Tchnology. ISSN 0974-3154 Volum 8, Numbr 1 (015), pp. 35-4 Intrnational Rsarch Publication Hous http://www.irphous.com Th Equitabl Dominating Graph P.N. Vinay
Intrnational Journal of Enginring Rsarch and Tchnology. ISSN 0974-3154 Volum 8, Numbr 1 (015), pp. 35-4 Intrnational Rsarch Publication Hous http://www.irphous.com Th Equitabl Dominating Graph P.N. Vinay
cycle that does not cross any edges (including its own), then it has at least
 W prov th following thorm: Thorm If a K n is drawn in th plan in such a way that it has a hamiltonian cycl that dos not cross any dgs (including its own, thn it has at last n ( 4 48 π + O(n crossings Th
W prov th following thorm: Thorm If a K n is drawn in th plan in such a way that it has a hamiltonian cycl that dos not cross any dgs (including its own, thn it has at last n ( 4 48 π + O(n crossings Th
On the irreducibility of some polynomials in two variables
 ACTA ARITHMETICA LXXXII.3 (1997) On th irrducibility of som polynomials in two variabls by B. Brindza and Á. Pintér (Dbrcn) To th mmory of Paul Erdős Lt f(x) and g(y ) b polynomials with intgral cofficints
ACTA ARITHMETICA LXXXII.3 (1997) On th irrducibility of som polynomials in two variabls by B. Brindza and Á. Pintér (Dbrcn) To th mmory of Paul Erdős Lt f(x) and g(y ) b polynomials with intgral cofficints
Case Study 4 PHA 5127 Aminoglycosides Answers provided by Jeffrey Stark Graduate Student
 Cas Stuy 4 PHA 527 Aminoglycosis Answrs provi by Jffry Stark Grauat Stunt Backgroun Gntamicin is us to trat a wi varity of infctions. Howvr, u to its toxicity, its us must b rstrict to th thrapy of lif-thratning
Cas Stuy 4 PHA 527 Aminoglycosis Answrs provi by Jffry Stark Grauat Stunt Backgroun Gntamicin is us to trat a wi varity of infctions. Howvr, u to its toxicity, its us must b rstrict to th thrapy of lif-thratning
That is, we start with a general matrix: And end with a simpler matrix:
 DIAGON ALIZATION OF THE STR ESS TEN SOR INTRO DUCTIO N By th us of Cauchy s thorm w ar abl to rduc th numbr of strss componnts in th strss tnsor to only nin valus. An additional simplification of th strss
DIAGON ALIZATION OF THE STR ESS TEN SOR INTRO DUCTIO N By th us of Cauchy s thorm w ar abl to rduc th numbr of strss componnts in th strss tnsor to only nin valus. An additional simplification of th strss
Where k is either given or determined from the data and c is an arbitrary constant.
 Exponntial growth and dcay applications W wish to solv an quation that has a drivativ. dy ky k > dx This quation says that th rat of chang of th function is proportional to th function. Th solution is
Exponntial growth and dcay applications W wish to solv an quation that has a drivativ. dy ky k > dx This quation says that th rat of chang of th function is proportional to th function. Th solution is
Brief Introduction to Statistical Mechanics
 Brif Introduction to Statistical Mchanics. Purpos: Ths nots ar intndd to provid a vry quick introduction to Statistical Mchanics. Th fild is of cours far mor vast than could b containd in ths fw pags.
Brif Introduction to Statistical Mchanics. Purpos: Ths nots ar intndd to provid a vry quick introduction to Statistical Mchanics. Th fild is of cours far mor vast than could b containd in ths fw pags.
Research Article On the Improvement of Wiener Attack on RSA with Small Private Exponent
 Scintific World Journal, Articl ID 650537, 9 pags http://dx.doi.org/10.1155/014/650537 Rsarch Articl On th Improvmnt of Winr Attack on RSA with Small Privat Exponnt Mu-En Wu, 1 Chin-Ming Chn,,3 Yu-Hsun
Scintific World Journal, Articl ID 650537, 9 pags http://dx.doi.org/10.1155/014/650537 Rsarch Articl On th Improvmnt of Winr Attack on RSA with Small Privat Exponnt Mu-En Wu, 1 Chin-Ming Chn,,3 Yu-Hsun
Mathematics 1110H Calculus I: Limits, derivatives, and Integrals Trent University, Summer 2018 Solutions to the Actual Final Examination
 Mathmatics H Calculus I: Limits, rivativs, an Intgrals Trnt Univrsity, Summr 8 Solutions to th Actual Final Eamination Tim-spac: 9:-: in FPHL 7. Brought to you by Stfan B lan k. Instructions: Do parts
Mathmatics H Calculus I: Limits, rivativs, an Intgrals Trnt Univrsity, Summr 8 Solutions to th Actual Final Eamination Tim-spac: 9:-: in FPHL 7. Brought to you by Stfan B lan k. Instructions: Do parts
Search sequence databases 3 10/25/2016
 Sarch squnc databass 3 10/25/2016 Etrm valu distribution Ø Suppos X is a random variabl with probability dnsity function p(, w sampl a larg numbr S of indpndnt valus of X from this distribution for an
Sarch squnc databass 3 10/25/2016 Etrm valu distribution Ø Suppos X is a random variabl with probability dnsity function p(, w sampl a larg numbr S of indpndnt valus of X from this distribution for an
Function Spaces. a x 3. (Letting x = 1 =)) a(0) + b + c (1) = 0. Row reducing the matrix. b 1. e 4 3. e 9. >: (x = 1 =)) a(0) + b + c (1) = 0
 unction Spacs Prrquisit: Sction 4.7, Coordinatization n this sction, w apply th tchniqus of Chaptr 4 to vctor spacs whos lmnts ar functions. Th vctor spacs P n and P ar familiar xampls of such spacs. Othr
unction Spacs Prrquisit: Sction 4.7, Coordinatization n this sction, w apply th tchniqus of Chaptr 4 to vctor spacs whos lmnts ar functions. Th vctor spacs P n and P ar familiar xampls of such spacs. Othr
A Prey-Predator Model with an Alternative Food for the Predator, Harvesting of Both the Species and with A Gestation Period for Interaction
 Int. J. Opn Problms Compt. Math., Vol., o., Jun 008 A Pry-Prdator Modl with an Altrnativ Food for th Prdator, Harvsting of Both th Spcis and with A Gstation Priod for Intraction K. L. arayan and. CH. P.
Int. J. Opn Problms Compt. Math., Vol., o., Jun 008 A Pry-Prdator Modl with an Altrnativ Food for th Prdator, Harvsting of Both th Spcis and with A Gstation Priod for Intraction K. L. arayan and. CH. P.
Problem Set 6 Solutions
 6.04/18.06J Mathmatics for Computr Scinc March 15, 005 Srini Dvadas and Eric Lhman Problm St 6 Solutions Du: Monday, March 8 at 9 PM in Room 3-044 Problm 1. Sammy th Shark is a financial srvic providr
6.04/18.06J Mathmatics for Computr Scinc March 15, 005 Srini Dvadas and Eric Lhman Problm St 6 Solutions Du: Monday, March 8 at 9 PM in Room 3-044 Problm 1. Sammy th Shark is a financial srvic providr
Efficient encryption and decryption
 ECE646 Lctur RSA Implmntation: Efficint ncryption, dcryption & ky gnration Rquird Rading W. Stallings, "Cryptography and twork-scurity, Chaptr 9. Th RSA Algorithm Chaptr 8. Tsting for Primality A. Mnzs,
ECE646 Lctur RSA Implmntation: Efficint ncryption, dcryption & ky gnration Rquird Rading W. Stallings, "Cryptography and twork-scurity, Chaptr 9. Th RSA Algorithm Chaptr 8. Tsting for Primality A. Mnzs,
First derivative analysis
 Robrto s Nots on Dirntial Calculus Chaptr 8: Graphical analysis Sction First drivativ analysis What you nd to know alrady: How to us drivativs to idntiy th critical valus o a unction and its trm points
Robrto s Nots on Dirntial Calculus Chaptr 8: Graphical analysis Sction First drivativ analysis What you nd to know alrady: How to us drivativs to idntiy th critical valus o a unction and its trm points
u x v x dx u x v x v x u x dx d u x v x u x v x dx u x v x dx Integration by Parts Formula
 7. Intgration by Parts Each drivativ formula givs ris to a corrsponding intgral formula, as w v sn many tims. Th drivativ product rul yilds a vry usful intgration tchniqu calld intgration by parts. Starting
7. Intgration by Parts Each drivativ formula givs ris to a corrsponding intgral formula, as w v sn many tims. Th drivativ product rul yilds a vry usful intgration tchniqu calld intgration by parts. Starting
Higher order derivatives
 Robrto s Nots on Diffrntial Calculus Chaptr 4: Basic diffrntiation ruls Sction 7 Highr ordr drivativs What you nd to know alrady: Basic diffrntiation ruls. What you can larn hr: How to rpat th procss of
Robrto s Nots on Diffrntial Calculus Chaptr 4: Basic diffrntiation ruls Sction 7 Highr ordr drivativs What you nd to know alrady: Basic diffrntiation ruls. What you can larn hr: How to rpat th procss of
Y 0. Standing Wave Interference between the incident & reflected waves Standing wave. A string with one end fixed on a wall
 Staning Wav Intrfrnc btwn th incint & rflct wavs Staning wav A string with on n fix on a wall Incint: y, t) Y cos( t ) 1( Y 1 ( ) Y (St th incint wav s phas to b, i.., Y + ral & positiv.) Rflct: y, t)
Staning Wav Intrfrnc btwn th incint & rflct wavs Staning wav A string with on n fix on a wall Incint: y, t) Y cos( t ) 1( Y 1 ( ) Y (St th incint wav s phas to b, i.., Y + ral & positiv.) Rflct: y, t)
Einstein Equations for Tetrad Fields
 Apiron, Vol 13, No, Octobr 006 6 Einstin Equations for Ttrad Filds Ali Rıza ŞAHİN, R T L Istanbul (Turky) Evry mtric tnsor can b xprssd by th innr product of ttrad filds W prov that Einstin quations for
Apiron, Vol 13, No, Octobr 006 6 Einstin Equations for Ttrad Filds Ali Rıza ŞAHİN, R T L Istanbul (Turky) Evry mtric tnsor can b xprssd by th innr product of ttrad filds W prov that Einstin quations for
Thomas Whitham Sixth Form
 Thomas Whitham Sith Form Pur Mathmatics Cor rvision gui Pag Algbra Moulus functions graphs, quations an inqualitis Graph of f () Draw f () an rflct an part of th curv blow th ais in th ais. f () f () f
Thomas Whitham Sith Form Pur Mathmatics Cor rvision gui Pag Algbra Moulus functions graphs, quations an inqualitis Graph of f () Draw f () an rflct an part of th curv blow th ais in th ais. f () f () f
Indeterminate Forms and L Hôpital s Rule. Indeterminate Forms
 SECTION 87 Intrminat Forms an L Hôpital s Rul 567 Sction 87 Intrminat Forms an L Hôpital s Rul Rcogniz its that prouc intrminat forms Apply L Hôpital s Rul to valuat a it Intrminat Forms Rcall from Chaptrs
SECTION 87 Intrminat Forms an L Hôpital s Rul 567 Sction 87 Intrminat Forms an L Hôpital s Rul Rcogniz its that prouc intrminat forms Apply L Hôpital s Rul to valuat a it Intrminat Forms Rcall from Chaptrs
Thomas Whitham Sixth Form
 Thomas Whitham Sith Form Pur Mathmatics Unit C Algbra Trigonomtr Gomtr Calculus Vctor gomtr Pag Algbra Molus functions graphs, quations an inqualitis Graph of f () Draw f () an rflct an part of th curv
Thomas Whitham Sith Form Pur Mathmatics Unit C Algbra Trigonomtr Gomtr Calculus Vctor gomtr Pag Algbra Molus functions graphs, quations an inqualitis Graph of f () Draw f () an rflct an part of th curv
Chapter Finding Small Vertex Covers. Extending the Limits of Tractability. Coping With NP-Completeness. Vertex Cover
 Coping With NP-Compltnss Chaptr 0 Extning th Limits o Tractability Q. Suppos I n to solv an NP-complt problm. What shoul I o? A. Thory says you'r unlikly to in poly-tim algorithm. Must sacriic on o thr
Coping With NP-Compltnss Chaptr 0 Extning th Limits o Tractability Q. Suppos I n to solv an NP-complt problm. What shoul I o? A. Thory says you'r unlikly to in poly-tim algorithm. Must sacriic on o thr
A. Limits and Horizontal Asymptotes ( ) f x f x. f x. x "±# ( ).
 A. Limits and Horizontal Asymptots What you ar finding: You can b askd to find lim x "a H.A.) problm is asking you find lim x "# and lim x "$#. or lim x "±#. Typically, a horizontal asymptot algbraically,
A. Limits and Horizontal Asymptots What you ar finding: You can b askd to find lim x "a H.A.) problm is asking you find lim x "# and lim x "$#. or lim x "±#. Typically, a horizontal asymptot algbraically,
Computing and Communications -- Network Coding
 89 90 98 00 Computing and Communications -- Ntwork Coding Dr. Zhiyong Chn Institut of Wirlss Communications Tchnology Shanghai Jiao Tong Univrsity China Lctur 5- Nov. 05 0 Classical Information Thory Sourc
89 90 98 00 Computing and Communications -- Ntwork Coding Dr. Zhiyong Chn Institut of Wirlss Communications Tchnology Shanghai Jiao Tong Univrsity China Lctur 5- Nov. 05 0 Classical Information Thory Sourc
Estimation of apparent fraction defective: A mathematical approach
 Availabl onlin at www.plagiarsarchlibrary.com Plagia Rsarch Library Advancs in Applid Scinc Rsarch, 011, (): 84-89 ISSN: 0976-8610 CODEN (USA): AASRFC Estimation of apparnt fraction dfctiv: A mathmatical
Availabl onlin at www.plagiarsarchlibrary.com Plagia Rsarch Library Advancs in Applid Scinc Rsarch, 011, (): 84-89 ISSN: 0976-8610 CODEN (USA): AASRFC Estimation of apparnt fraction dfctiv: A mathmatical
Online Supplement: Advance Selling in a Supply Chain under Uncertain Supply and Demand
 Onlin Supplmnt Avanc Slling in a Supply Cain unr Uncrtain Supply an Dman. Proos o Analytical sults Proo o Lmma. Using a = minl 0 ; x g; w can rwrit () as ollows (x ; w ; x ; w ) = a +(m0 w )a +( +" x w
Onlin Supplmnt Avanc Slling in a Supply Cain unr Uncrtain Supply an Dman. Proos o Analytical sults Proo o Lmma. Using a = minl 0 ; x g; w can rwrit () as ollows (x ; w ; x ; w ) = a +(m0 w )a +( +" x w
Ch. 24 Molecular Reaction Dynamics 1. Collision Theory
 Ch. 4 Molcular Raction Dynamics 1. Collision Thory Lctur 16. Diffusion-Controlld Raction 3. Th Matrial Balanc Equation 4. Transition Stat Thory: Th Eyring Equation 5. Transition Stat Thory: Thrmodynamic
Ch. 4 Molcular Raction Dynamics 1. Collision Thory Lctur 16. Diffusion-Controlld Raction 3. Th Matrial Balanc Equation 4. Transition Stat Thory: Th Eyring Equation 5. Transition Stat Thory: Thrmodynamic
A Propagating Wave Packet Group Velocity Dispersion
 Lctur 8 Phys 375 A Propagating Wav Packt Group Vlocity Disprsion Ovrviw and Motivation: In th last lctur w lookd at a localizd solution t) to th 1D fr-particl Schrödingr quation (SE) that corrsponds to
Lctur 8 Phys 375 A Propagating Wav Packt Group Vlocity Disprsion Ovrviw and Motivation: In th last lctur w lookd at a localizd solution t) to th 1D fr-particl Schrödingr quation (SE) that corrsponds to
Examples and applications on SSSP and MST
 Exampls an applications on SSSP an MST Dan (Doris) H & Junhao Gan ITEE Univrsity of Qunslan COMP3506/7505, Uni of Qunslan Exampls an applications on SSSP an MST Dijkstra s Algorithm Th algorithm solvs
Exampls an applications on SSSP an MST Dan (Doris) H & Junhao Gan ITEE Univrsity of Qunslan COMP3506/7505, Uni of Qunslan Exampls an applications on SSSP an MST Dijkstra s Algorithm Th algorithm solvs
Limiting value of higher Mahler measure
 Limiting valu of highr Mahlr masur Arunabha Biswas a, Chris Monico a, a Dpartmnt of Mathmatics & Statistics, Txas Tch Univrsity, Lubbock, TX 7949, USA Abstract W considr th k-highr Mahlr masur m k P )
Limiting valu of highr Mahlr masur Arunabha Biswas a, Chris Monico a, a Dpartmnt of Mathmatics & Statistics, Txas Tch Univrsity, Lubbock, TX 7949, USA Abstract W considr th k-highr Mahlr masur m k P )
Basic Polyhedral theory
 Basic Polyhdral thory Th st P = { A b} is calld a polyhdron. Lmma 1. Eithr th systm A = b, b 0, 0 has a solution or thr is a vctorπ such that π A 0, πb < 0 Thr cass, if solution in top row dos not ist
Basic Polyhdral thory Th st P = { A b} is calld a polyhdron. Lmma 1. Eithr th systm A = b, b 0, 0 has a solution or thr is a vctorπ such that π A 0, πb < 0 Thr cass, if solution in top row dos not ist
Case Study Vancomycin Answers Provided by Jeffrey Stark, Graduate Student
 Cas Stuy Vancomycin Answrs Provi by Jffry Stark, Grauat Stunt h antibiotic Vancomycin is liminat almost ntirly by glomrular filtration. For a patint with normal rnal function, th half-lif is about 6 hours.
Cas Stuy Vancomycin Answrs Provi by Jffry Stark, Grauat Stunt h antibiotic Vancomycin is liminat almost ntirly by glomrular filtration. For a patint with normal rnal function, th half-lif is about 6 hours.
On spanning trees and cycles of multicolored point sets with few intersections
 On spanning trs and cycls of multicolord point sts with fw intrsctions M. Kano, C. Mrino, and J. Urrutia April, 00 Abstract Lt P 1,..., P k b a collction of disjoint point sts in R in gnral position. W
On spanning trs and cycls of multicolord point sts with fw intrsctions M. Kano, C. Mrino, and J. Urrutia April, 00 Abstract Lt P 1,..., P k b a collction of disjoint point sts in R in gnral position. W
1973 AP Calculus AB: Section I
 97 AP Calculus AB: Sction I 9 Minuts No Calculator Not: In this amination, ln dnots th natural logarithm of (that is, logarithm to th bas ).. ( ) d= + C 6 + C + C + C + C. If f ( ) = + + + and ( ), g=
97 AP Calculus AB: Sction I 9 Minuts No Calculator Not: In this amination, ln dnots th natural logarithm of (that is, logarithm to th bas ).. ( ) d= + C 6 + C + C + C + C. If f ( ) = + + + and ( ), g=
Minimum Spanning Trees
 Yufi Tao ITEE Univrsity of Qunslan In tis lctur, w will stuy anotr classic prolm: finin a minimum spannin tr of an unirct wit rap. Intrstinly, vn tou t prolm appars ratr iffrnt from SSSP (sinl sourc sortst
Yufi Tao ITEE Univrsity of Qunslan In tis lctur, w will stuy anotr classic prolm: finin a minimum spannin tr of an unirct wit rap. Intrstinly, vn tou t prolm appars ratr iffrnt from SSSP (sinl sourc sortst
SECTION where P (cos θ, sin θ) and Q(cos θ, sin θ) are polynomials in cos θ and sin θ, provided Q is never equal to zero.
 SETION 6. 57 6. Evaluation of Dfinit Intgrals Exampl 6.6 W hav usd dfinit intgrals to valuat contour intgrals. It may com as a surpris to larn that contour intgrals and rsidus can b usd to valuat crtain
SETION 6. 57 6. Evaluation of Dfinit Intgrals Exampl 6.6 W hav usd dfinit intgrals to valuat contour intgrals. It may com as a surpris to larn that contour intgrals and rsidus can b usd to valuat crtain
What are those βs anyway? Understanding Design Matrix & Odds ratios
 Ral paramtr stimat WILD 750 - Wildlif Population Analysis of 6 What ar thos βs anyway? Undrsting Dsign Matrix & Odds ratios Rfrncs Hosmr D.W.. Lmshow. 000. Applid logistic rgrssion. John Wily & ons Inc.
Ral paramtr stimat WILD 750 - Wildlif Population Analysis of 6 What ar thos βs anyway? Undrsting Dsign Matrix & Odds ratios Rfrncs Hosmr D.W.. Lmshow. 000. Applid logistic rgrssion. John Wily & ons Inc.
COUNTING TAMELY RAMIFIED EXTENSIONS OF LOCAL FIELDS UP TO ISOMORPHISM
 COUNTING TAMELY RAMIFIED EXTENSIONS OF LOCAL FIELDS UP TO ISOMORPHISM Jim Brown Dpartmnt of Mathmatical Scincs, Clmson Univrsity, Clmson, SC 9634, USA jimlb@g.clmson.du Robrt Cass Dpartmnt of Mathmatics,
COUNTING TAMELY RAMIFIED EXTENSIONS OF LOCAL FIELDS UP TO ISOMORPHISM Jim Brown Dpartmnt of Mathmatical Scincs, Clmson Univrsity, Clmson, SC 9634, USA jimlb@g.clmson.du Robrt Cass Dpartmnt of Mathmatics,
PROBLEM SET Problem 1.
 PROLEM SET 1 PROFESSOR PETER JOHNSTONE 1. Problm 1. 1.1. Th catgory Mat L. OK, I m not amiliar with th trminology o partially orr sts, so lt s go ovr that irst. Dinition 1.1. partial orr is a binary rlation
PROLEM SET 1 PROFESSOR PETER JOHNSTONE 1. Problm 1. 1.1. Th catgory Mat L. OK, I m not amiliar with th trminology o partially orr sts, so lt s go ovr that irst. Dinition 1.1. partial orr is a binary rlation
CPSC 665 : An Algorithmist s Toolkit Lecture 4 : 21 Jan Linear Programming
 CPSC 665 : An Algorithmist s Toolkit Lctur 4 : 21 Jan 2015 Lcturr: Sushant Sachdva Linar Programming Scrib: Rasmus Kyng 1. Introduction An optimization problm rquirs us to find th minimum or maximum) of
CPSC 665 : An Algorithmist s Toolkit Lctur 4 : 21 Jan 2015 Lcturr: Sushant Sachdva Linar Programming Scrib: Rasmus Kyng 1. Introduction An optimization problm rquirs us to find th minimum or maximum) of
Quasi-Classical States of the Simple Harmonic Oscillator
 Quasi-Classical Stats of th Simpl Harmonic Oscillator (Draft Vrsion) Introduction: Why Look for Eignstats of th Annihilation Oprator? Excpt for th ground stat, th corrspondnc btwn th quantum nrgy ignstats
Quasi-Classical Stats of th Simpl Harmonic Oscillator (Draft Vrsion) Introduction: Why Look for Eignstats of th Annihilation Oprator? Excpt for th ground stat, th corrspondnc btwn th quantum nrgy ignstats
Homotopy perturbation technique
 Comput. Mthods Appl. Mch. Engrg. 178 (1999) 257±262 www.lsvir.com/locat/cma Homotopy prturbation tchniqu Ji-Huan H 1 Shanghai Univrsity, Shanghai Institut of Applid Mathmatics and Mchanics, Shanghai 272,
Comput. Mthods Appl. Mch. Engrg. 178 (1999) 257±262 www.lsvir.com/locat/cma Homotopy prturbation tchniqu Ji-Huan H 1 Shanghai Univrsity, Shanghai Institut of Applid Mathmatics and Mchanics, Shanghai 272,
EEO 401 Digital Signal Processing Prof. Mark Fowler
 EEO 401 Digital Signal Procssing Prof. Mark Fowlr ot St #18 Introduction to DFT (via th DTFT) Rading Assignmnt: Sct. 7.1 of Proakis & Manolakis 1/24 Discrt Fourir Transform (DFT) W v sn that th DTFT is
EEO 401 Digital Signal Procssing Prof. Mark Fowlr ot St #18 Introduction to DFT (via th DTFT) Rading Assignmnt: Sct. 7.1 of Proakis & Manolakis 1/24 Discrt Fourir Transform (DFT) W v sn that th DTFT is
The Transfer Function. The Transfer Function. The Transfer Function. The Transfer Function. The Transfer Function. The Transfer Function
 A gnraliation of th frquncy rsons function Th convolution sum scrition of an LTI iscrt-tim systm with an imuls rsons h[n] is givn by h y [ n] [ ] x[ n ] Taing th -transforms of both sis w gt n n h n n
A gnraliation of th frquncy rsons function Th convolution sum scrition of an LTI iscrt-tim systm with an imuls rsons h[n] is givn by h y [ n] [ ] x[ n ] Taing th -transforms of both sis w gt n n h n n
EXST Regression Techniques Page 1
 EXST704 - Rgrssion Tchniqus Pag 1 Masurmnt rrors in X W hav assumd that all variation is in Y. Masurmnt rror in this variabl will not ffct th rsults, as long as thy ar uncorrlatd and unbiasd, sinc thy
EXST704 - Rgrssion Tchniqus Pag 1 Masurmnt rrors in X W hav assumd that all variation is in Y. Masurmnt rror in this variabl will not ffct th rsults, as long as thy ar uncorrlatd and unbiasd, sinc thy
Supplementary Materials
 6 Supplmntary Matrials APPENDIX A PHYSICAL INTERPRETATION OF FUEL-RATE-SPEED FUNCTION A truck running on a road with grad/slop θ positiv if moving up and ngativ if moving down facs thr rsistancs: arodynamic
6 Supplmntary Matrials APPENDIX A PHYSICAL INTERPRETATION OF FUEL-RATE-SPEED FUNCTION A truck running on a road with grad/slop θ positiv if moving up and ngativ if moving down facs thr rsistancs: arodynamic
Differential Equations
 Prfac Hr ar m onlin nots for m diffrntial quations cours that I tach hr at Lamar Univrsit. Dspit th fact that ths ar m class nots, th should b accssibl to anon wanting to larn how to solv diffrntial quations
Prfac Hr ar m onlin nots for m diffrntial quations cours that I tach hr at Lamar Univrsit. Dspit th fact that ths ar m class nots, th should b accssibl to anon wanting to larn how to solv diffrntial quations
SCHUR S THEOREM REU SUMMER 2005
 SCHUR S THEOREM REU SUMMER 2005 1. Combinatorial aroach Prhas th first rsult in th subjct blongs to I. Schur and dats back to 1916. On of his motivation was to study th local vrsion of th famous quation
SCHUR S THEOREM REU SUMMER 2005 1. Combinatorial aroach Prhas th first rsult in th subjct blongs to I. Schur and dats back to 1916. On of his motivation was to study th local vrsion of th famous quation
Equidistribution and Weyl s criterion
 Euidistribution and Wyl s critrion by Brad Hannigan-Daly W introduc th ida of a sunc of numbrs bing uidistributd (mod ), and w stat and prov a thorm of Hrmann Wyl which charactrizs such suncs. W also discuss
Euidistribution and Wyl s critrion by Brad Hannigan-Daly W introduc th ida of a sunc of numbrs bing uidistributd (mod ), and w stat and prov a thorm of Hrmann Wyl which charactrizs such suncs. W also discuss
y = 2xe x + x 2 e x at (0, 3). solution: Since y is implicitly related to x we have to use implicit differentiation: 3 6y = 0 y = 1 2 x ln(b) ln(b)
 4. y = y = + 5. Find th quation of th tangnt lin for th function y = ( + ) 3 whn = 0. solution: First not that whn = 0, y = (1 + 1) 3 = 8, so th lin gos through (0, 8) and thrfor its y-intrcpt is 8. y
4. y = y = + 5. Find th quation of th tangnt lin for th function y = ( + ) 3 whn = 0. solution: First not that whn = 0, y = (1 + 1) 3 = 8, so th lin gos through (0, 8) and thrfor its y-intrcpt is 8. y
PROOF OF FIRST STANDARD FORM OF NONELEMENTARY FUNCTIONS
 Intrnational Journal Of Advanc Rsarch In Scinc And Enginring http://www.ijars.com IJARSE, Vol. No., Issu No., Fbruary, 013 ISSN-319-8354(E) PROOF OF FIRST STANDARD FORM OF NONELEMENTARY FUNCTIONS 1 Dharmndra
Intrnational Journal Of Advanc Rsarch In Scinc And Enginring http://www.ijars.com IJARSE, Vol. No., Issu No., Fbruary, 013 ISSN-319-8354(E) PROOF OF FIRST STANDARD FORM OF NONELEMENTARY FUNCTIONS 1 Dharmndra
Exiting from QE. Fumio Hayashi and Junko Koeda. for presentation at SF Fed Conference. March 28, 2014
 Fumio Hayashi an Junko Koa Exiting from QE March 28, 214, 1 / 29 Exiting from QE Fumio Hayashi an Junko Koa for prsntation at SF F Confrnc March 28, 214 To gt start... h^ : Fumio Hayashi an Junko Koa Exiting
Fumio Hayashi an Junko Koa Exiting from QE March 28, 214, 1 / 29 Exiting from QE Fumio Hayashi an Junko Koa for prsntation at SF F Confrnc March 28, 214 To gt start... h^ : Fumio Hayashi an Junko Koa Exiting
Math 34A. Final Review
 Math A Final Rviw 1) Us th graph of y10 to find approimat valus: a) 50 0. b) y (0.65) solution for part a) first writ an quation: 50 0. now tak th logarithm of both sids: log() log(50 0. ) pand th right
Math A Final Rviw 1) Us th graph of y10 to find approimat valus: a) 50 0. b) y (0.65) solution for part a) first writ an quation: 50 0. now tak th logarithm of both sids: log() log(50 0. ) pand th right
Combinatorial Networks Week 1, March 11-12
 1 Nots on March 11 Combinatorial Ntwors W 1, March 11-1 11 Th Pigonhol Principl Th Pigonhol Principl If n objcts ar placd in hols, whr n >, thr xists a box with mor than on objcts 11 Thorm Givn a simpl
1 Nots on March 11 Combinatorial Ntwors W 1, March 11-1 11 Th Pigonhol Principl Th Pigonhol Principl If n objcts ar placd in hols, whr n >, thr xists a box with mor than on objcts 11 Thorm Givn a simpl
SPH4U Electric Charges and Electric Fields Mr. LoRusso
 SPH4U lctric Chargs an lctric Fils Mr. LoRusso lctricity is th flow of lctric charg. Th Grks first obsrv lctrical forcs whn arly scintists rubb ambr with fur. Th notic thy coul attract small bits of straw
SPH4U lctric Chargs an lctric Fils Mr. LoRusso lctricity is th flow of lctric charg. Th Grks first obsrv lctrical forcs whn arly scintists rubb ambr with fur. Th notic thy coul attract small bits of straw
6.1 Integration by Parts and Present Value. Copyright Cengage Learning. All rights reserved.
 6.1 Intgration by Parts and Prsnt Valu Copyright Cngag Larning. All rights rsrvd. Warm-Up: Find f () 1. F() = ln(+1). F() = 3 3. F() =. F() = ln ( 1) 5. F() = 6. F() = - Objctivs, Day #1 Studnts will b
6.1 Intgration by Parts and Prsnt Valu Copyright Cngag Larning. All rights rsrvd. Warm-Up: Find f () 1. F() = ln(+1). F() = 3 3. F() =. F() = ln ( 1) 5. F() = 6. F() = - Objctivs, Day #1 Studnts will b
Cramér-Rao Inequality: Let f(x; θ) be a probability density function with continuous parameter
 WHEN THE CRAMÉR-RAO INEQUALITY PROVIDES NO INFORMATION STEVEN J. MILLER Abstract. W invstigat a on-paramtr family of probability dnsitis (rlatd to th Parto distribution, which dscribs many natural phnomna)
WHEN THE CRAMÉR-RAO INEQUALITY PROVIDES NO INFORMATION STEVEN J. MILLER Abstract. W invstigat a on-paramtr family of probability dnsitis (rlatd to th Parto distribution, which dscribs many natural phnomna)
y cos x = cos xdx = sin x + c y = tan x + c sec x But, y = 1 when x = 0 giving c = 1. y = tan x + sec x (A1) (C4) OR y cos x = sin x + 1 [8]
![y cos x = cos xdx = sin x + c y = tan x + c sec x But, y = 1 when x = 0 giving c = 1. y = tan x + sec x (A1) (C4) OR y cos x = sin x + 1 [8] y cos x = cos xdx = sin x + c y = tan x + c sec x But, y = 1 when x = 0 giving c = 1. y = tan x + sec x (A1) (C4) OR y cos x = sin x + 1 [8]](/thumbs/88/115680282.jpg) DIFF EQ - OPTION. Sol th iffrntial quation tan +, 0
DIFF EQ - OPTION. Sol th iffrntial quation tan +, 0
1 Isoparametric Concept
 UNIVERSITY OF CALIFORNIA BERKELEY Dpartmnt of Civil Enginring Spring 06 Structural Enginring, Mchanics and Matrials Profssor: S. Govindj Nots on D isoparamtric lmnts Isoparamtric Concpt Th isoparamtric
UNIVERSITY OF CALIFORNIA BERKELEY Dpartmnt of Civil Enginring Spring 06 Structural Enginring, Mchanics and Matrials Profssor: S. Govindj Nots on D isoparamtric lmnts Isoparamtric Concpt Th isoparamtric
22/ Breakdown of the Born-Oppenheimer approximation. Selection rules for rotational-vibrational transitions. P, R branches.
 Subjct Chmistry Papr No and Titl Modul No and Titl Modul Tag 8/ Physical Spctroscopy / Brakdown of th Born-Oppnhimr approximation. Slction ruls for rotational-vibrational transitions. P, R branchs. CHE_P8_M
Subjct Chmistry Papr No and Titl Modul No and Titl Modul Tag 8/ Physical Spctroscopy / Brakdown of th Born-Oppnhimr approximation. Slction ruls for rotational-vibrational transitions. P, R branchs. CHE_P8_M
Section 6.1. Question: 2. Let H be a subgroup of a group G. Then H operates on G by left multiplication. Describe the orbits for this operation.
 MAT 444 H Barclo Spring 004 Homwork 6 Solutions Sction 6 Lt H b a subgroup of a group G Thn H oprats on G by lft multiplication Dscrib th orbits for this opration Th orbits of G ar th right costs of H
MAT 444 H Barclo Spring 004 Homwork 6 Solutions Sction 6 Lt H b a subgroup of a group G Thn H oprats on G by lft multiplication Dscrib th orbits for this opration Th orbits of G ar th right costs of H
Bifurcation Theory. , a stationary point, depends on the value of α. At certain values
 Dnamic Macroconomic Thor Prof. Thomas Lux Bifurcation Thor Bifurcation: qualitativ chang in th natur of th solution occurs if a paramtr passs through a critical point bifurcation or branch valu. Local
Dnamic Macroconomic Thor Prof. Thomas Lux Bifurcation Thor Bifurcation: qualitativ chang in th natur of th solution occurs if a paramtr passs through a critical point bifurcation or branch valu. Local
4. Money cannot be neutral in the short-run the neutrality of money is exclusively a medium run phenomenon.
 PART I TRUE/FALSE/UNCERTAIN (5 points ach) 1. Lik xpansionary montary policy, xpansionary fiscal policy rturns output in th mdium run to its natural lvl, and incrass prics. Thrfor, fiscal policy is also
PART I TRUE/FALSE/UNCERTAIN (5 points ach) 1. Lik xpansionary montary policy, xpansionary fiscal policy rturns output in th mdium run to its natural lvl, and incrass prics. Thrfor, fiscal policy is also
 Mor Tutorial at www.dumblittldoctor.com Work th problms without a calculator, but us a calculator to chck rsults. And try diffrntiating your answrs in part III as a usful chck. I. Applications of Intgration
Mor Tutorial at www.dumblittldoctor.com Work th problms without a calculator, but us a calculator to chck rsults. And try diffrntiating your answrs in part III as a usful chck. I. Applications of Intgration
CS 491 G Combinatorial Optimization
 CS 49 G Cobinatorial Optiization Lctur Nots Junhui Jia. Maiu Flow Probls Now lt us iscuss or tails on aiu low probls. Thor. A asibl low is aiu i an only i thr is no -augnting path. Proo: Lt P = A asibl
CS 49 G Cobinatorial Optiization Lctur Nots Junhui Jia. Maiu Flow Probls Now lt us iscuss or tails on aiu low probls. Thor. A asibl low is aiu i an only i thr is no -augnting path. Proo: Lt P = A asibl
Deift/Zhou Steepest descent, Part I
 Lctur 9 Dift/Zhou Stpst dscnt, Part I W now focus on th cas of orthogonal polynomials for th wight w(x) = NV (x), V (x) = t x2 2 + x4 4. Sinc th wight dpnds on th paramtr N N w will writ π n,n, a n,n,
Lctur 9 Dift/Zhou Stpst dscnt, Part I W now focus on th cas of orthogonal polynomials for th wight w(x) = NV (x), V (x) = t x2 2 + x4 4. Sinc th wight dpnds on th paramtr N N w will writ π n,n, a n,n,
Additional Math (4047) Paper 2 (100 marks) y x. 2 d. d d
 Aitional Math (07) Prpar b Mr Ang, Nov 07 Fin th valu of th constant k for which is a solution of th quation k. [7] Givn that, Givn that k, Thrfor, k Topic : Papr (00 marks) Tim : hours 0 mins Nam : Aitional
Aitional Math (07) Prpar b Mr Ang, Nov 07 Fin th valu of th constant k for which is a solution of th quation k. [7] Givn that, Givn that k, Thrfor, k Topic : Papr (00 marks) Tim : hours 0 mins Nam : Aitional
Random Access Techniques: ALOHA (cont.)
 Random Accss Tchniqus: ALOHA (cont.) 1 Exampl [ Aloha avoiding collision ] A pur ALOHA ntwork transmits a 200-bit fram on a shard channl Of 200 kbps at tim. What is th rquirmnt to mak this fram collision
Random Accss Tchniqus: ALOHA (cont.) 1 Exampl [ Aloha avoiding collision ] A pur ALOHA ntwork transmits a 200-bit fram on a shard channl Of 200 kbps at tim. What is th rquirmnt to mak this fram collision
(1) Then we could wave our hands over this and it would become:
 MAT* K285 Spring 28 Anthony Bnoit 4/17/28 Wk 12: Laplac Tranform Rading: Kohlr & Johnon, Chaptr 5 to p. 35 HW: 5.1: 3, 7, 1*, 19 5.2: 1, 5*, 13*, 19, 45* 5.3: 1, 11*, 19 * Pla writ-up th problm natly and
MAT* K285 Spring 28 Anthony Bnoit 4/17/28 Wk 12: Laplac Tranform Rading: Kohlr & Johnon, Chaptr 5 to p. 35 HW: 5.1: 3, 7, 1*, 19 5.2: 1, 5*, 13*, 19, 45* 5.3: 1, 11*, 19 * Pla writ-up th problm natly and
High Energy Physics. Lecture 5 The Passage of Particles through Matter
 High Enrgy Physics Lctur 5 Th Passag of Particls through Mattr 1 Introduction In prvious lcturs w hav sn xampls of tracks lft by chargd particls in passing through mattr. Such tracks provid som of th most
High Enrgy Physics Lctur 5 Th Passag of Particls through Mattr 1 Introduction In prvious lcturs w hav sn xampls of tracks lft by chargd particls in passing through mattr. Such tracks provid som of th most
EECE 301 Signals & Systems Prof. Mark Fowler
 EECE 301 Signals & Systms Prof. Mark Fowlr ot St #21 D-T Signals: Rlation btwn DFT, DTFT, & CTFT 1/16 W can us th DFT to implmnt numrical FT procssing This nabls us to numrically analyz a signal to find
EECE 301 Signals & Systms Prof. Mark Fowlr ot St #21 D-T Signals: Rlation btwn DFT, DTFT, & CTFT 1/16 W can us th DFT to implmnt numrical FT procssing This nabls us to numrically analyz a signal to find
Sundials and Linear Algebra
 Sundials and Linar Algbra M. Scot Swan July 2, 25 Most txts on crating sundials ar dirctd towards thos who ar solly intrstd in making and using sundials and usually assums minimal mathmatical background.
Sundials and Linar Algbra M. Scot Swan July 2, 25 Most txts on crating sundials ar dirctd towards thos who ar solly intrstd in making and using sundials and usually assums minimal mathmatical background.
Answer Homework 5 PHA5127 Fall 1999 Jeff Stark
 Answr omwork 5 PA527 Fall 999 Jff Stark A patint is bing tratd with Drug X in a clinical stting. Upon admiion, an IV bolus dos of 000mg was givn which yildd an initial concntration of 5.56 µg/ml. A fw
Answr omwork 5 PA527 Fall 999 Jff Stark A patint is bing tratd with Drug X in a clinical stting. Upon admiion, an IV bolus dos of 000mg was givn which yildd an initial concntration of 5.56 µg/ml. A fw
INCOMPLETE KLOOSTERMAN SUMS AND MULTIPLICATIVE INVERSES IN SHORT INTERVALS. xy 1 (mod p), (x, y) I (j)
 INCOMPLETE KLOOSTERMAN SUMS AND MULTIPLICATIVE INVERSES IN SHORT INTERVALS T D BROWNING AND A HAYNES Abstract W invstigat th solubility of th congrunc xy (mod ), whr is a rim and x, y ar rstrictd to li
INCOMPLETE KLOOSTERMAN SUMS AND MULTIPLICATIVE INVERSES IN SHORT INTERVALS T D BROWNING AND A HAYNES Abstract W invstigat th solubility of th congrunc xy (mod ), whr is a rim and x, y ar rstrictd to li
3) Use the average steady-state equation to determine the dose. Note that only 100 mg tablets of aminophylline are available here.
 PHA 5127 Dsigning A Dosing Rgimn Answrs provi by Jry Stark Mr. JM is to b start on aminophyllin or th tratmnt o asthma. H is a non-smokr an wighs 60 kg. Dsign an oral osing rgimn or this patint such that
PHA 5127 Dsigning A Dosing Rgimn Answrs provi by Jry Stark Mr. JM is to b start on aminophyllin or th tratmnt o asthma. H is a non-smokr an wighs 60 kg. Dsign an oral osing rgimn or this patint such that
Abstract Interpretation: concrete and abstract semantics
 Abstract Intrprtation: concrt and abstract smantics Concrt smantics W considr a vry tiny languag that manags arithmtic oprations on intgrs valus. Th (concrt) smantics of th languags cab b dfind by th funzcion
Abstract Intrprtation: concrt and abstract smantics Concrt smantics W considr a vry tiny languag that manags arithmtic oprations on intgrs valus. Th (concrt) smantics of th languags cab b dfind by th funzcion
Research Article Measuring Loss-Based Process Capability Index L e and Its Generation L e. with Fuzzy Numbers
 Mathmatical Problms in Enginring Volum 015, Articl ID 17406, 8 pags http://x.oi.org/10.1155/015/17406 Rsarch Articl Masuring Loss-Bas Procss Capability Inx L an Its Gnration L with Fuzzy Numbrs Mohamma
Mathmatical Problms in Enginring Volum 015, Articl ID 17406, 8 pags http://x.oi.org/10.1155/015/17406 Rsarch Articl Masuring Loss-Bas Procss Capability Inx L an Its Gnration L with Fuzzy Numbrs Mohamma
ON RIGHT(LEFT) DUO PO-SEMIGROUPS. S. K. Lee and K. Y. Park
 Kangwon-Kyungki Math. Jour. 11 (2003), No. 2, pp. 147 153 ON RIGHT(LEFT) DUO PO-SEMIGROUPS S. K. L and K. Y. Park Abstract. W invstigat som proprtis on right(rsp. lft) duo po-smigroups. 1. Introduction
Kangwon-Kyungki Math. Jour. 11 (2003), No. 2, pp. 147 153 ON RIGHT(LEFT) DUO PO-SEMIGROUPS S. K. L and K. Y. Park Abstract. W invstigat som proprtis on right(rsp. lft) duo po-smigroups. 1. Introduction
Note If the candidate believes that e x = 0 solves to x = 0 or gives an extra solution of x = 0, then withhold the final accuracy mark.
 . (a) Eithr y = or ( 0, ) (b) Whn =, y = ( 0 + ) = 0 = 0 ( + ) = 0 ( )( ) = 0 Eithr = (for possibly abov) or = A 3. Not If th candidat blivs that = 0 solvs to = 0 or givs an tra solution of = 0, thn withhold
. (a) Eithr y = or ( 0, ) (b) Whn =, y = ( 0 + ) = 0 = 0 ( + ) = 0 ( )( ) = 0 Eithr = (for possibly abov) or = A 3. Not If th candidat blivs that = 0 solvs to = 0 or givs an tra solution of = 0, thn withhold
Hardy-Littlewood Conjecture and Exceptional real Zero. JinHua Fei. ChangLing Company of Electronic Technology Baoji Shannxi P.R.
 Hardy-Littlwood Conjctur and Excptional ral Zro JinHua Fi ChangLing Company of Elctronic Tchnology Baoji Shannxi P.R.China E-mail: fijinhuayoujian@msn.com Abstract. In this papr, w assum that Hardy-Littlwood
Hardy-Littlwood Conjctur and Excptional ral Zro JinHua Fi ChangLing Company of Elctronic Tchnology Baoji Shannxi P.R.China E-mail: fijinhuayoujian@msn.com Abstract. In this papr, w assum that Hardy-Littlwood
