Bootstrapping. 1 Overview. 2 Problem Setting and Notation. Steven Abney AT&T Laboratories Research 180 Park Avenue Florham Park, NJ, USA, 07932
|
|
|
- Beryl Thomas
- 5 years ago
- Views:
Transcription
1 Bootstrapping Steven Abney AT&T Laboratories Research 180 Park Avenue Florham Park, NJ, USA, Abstract This paper refines the analysis of cotraining, defines and evaluates a new co-training algorithm that has theoretical justification, gives a theoretical justification for the Yarowsky algorithm, and shows that co-training and the Yarowsky algorithm are based on different independence assumptions. 1 Overview The term bootstrapping here refers to a problem setting in which one is given a small set of labeled data and a large set of unlabeled data, and the task is to induce a classifier. The plenitude of unlabeled natural language data, and the paucity of labeled data, have made bootstrapping a topic of interest in computational linguistics. Current work has been spurred by two papers, (Yarowsky, 1995) and (Blum and Mitchell, 1998). Blum and Mitchell propose a conditional independence assumption to account for the efficacy of their algorithm, called co-training, and they give a proof based on that conditional independence assumption. They also give an intuitive explanation of why co-training works, in terms of maximizing agreement on unlabeled data between classifiers based on different views of the data. Finally, they suggest that the Yarowsky algorithm is a special case of the co-training algorithm. The Blum and Mitchell paper has been very influential, but it has some shortcomings. The proof they give does not actually apply directly to the co-training algorithm, nor does it directly justify the intuitive account in terms of classifier agreement on unlabeled data, nor, for that matter, does the co-training algorithm directly seek to find classifiers that agree on unlabeled data. Moreover, the suggestion that the Yarowsky algorithm is a special case of co-training is based on an incidental detail of the particular application that Yarowsky considers, not on the properties of the core algorithm. In recent work, (Dasgupta et al., 2001) prove that a classifier has low generalization error if it agrees on unlabeled data with a second classifier based on a different view of the data. This addresses one of the shortcomings of the original co-training paper: it gives a proof that justifies searching for classifiers that agree on unlabeled data. I extend this work in two ways. First, (Dasgupta et al., 2001) assume the same conditional independence assumption as proposed by Blum and Mitchell. I show that that independence assumption is remarkably powerful, and violated in the data; however, I show that a weaker assumption suffices. Second, I give an algorithm that finds classifiers that agree on unlabeled data, and I report on an implementation and empirical results. Finally, I consider the question of the relation between the co-training algorithm and the Yarowsky algorithm. I suggest that the Yarowsky algorithm is actually based on a different independence assumption, and I show that, if the independence assumption holds, the Yarowsky algorithm is effective at finding a high-precision classifier. 2 Problem Setting and Notation A bootstrapping problem consists of a space of instances X, a set of labels L, a function
2 Y : X L assigning labels to instances, and a space of rules mapping instances to labels. Rules may be partial functions; we write F (x) = if F abstains (that is, makes no prediction) on input x. Classifier is synonymous with rule. It is often useful to think of rules and labels as sets of instances. A binary rule F can be thought of as the characteristic function of the set of instances {x : F (x) = }. Multi-class rules also define useful sets when a particular target class l is understood. For any rule F, we write F l for the set of instances {x : F (x) = l}, or (ambiguously) for that set s characteristic function. We write F l for the complement of F l, either as a set or characteristic function. Note that F l contains instances on which F abstains. We write F l for {x : F (x) l F (x) }. When F does not abstain, F l and F l are identical. Finally, in expressions like Pr[F = Y = ] (with square brackets and Pr ), the functions F (x) and Y (x) are used as random variables. By contrast, in the expression P (F Y ) (with parentheses and P ), F is the set of instances for which F (x) =, and Y is the set of instances for which Y (x) =. 3 View Independence Blum and Mitchell assume that each instance x consists of two views x 1, x 2. We can take this as the assumption of functions X 1 and X 2 such that X 1 (x) = x 1 and X 2 (x) = x 2. They propose that views are conditionally independent given the label. Definition 1 A pair of views x 1, x 2 view independence just in case: satisfy Pr[X 1 = x 1 X 2 = x 2, Y = y] = Pr[X 1 = x 1 Y = y] Pr[X 2 = x 2 X 1 = x 1, Y = y] = Pr[X 2 = x 2 Y = y] A classification problem instance satisfies view independence just in case all pairs x 1, x 2 satisfy view independence. There is a related independence assumption that will prove useful. Let us define H 1 to consist of rules that are functions of X 1 only, and define H 2 to consist of rules that are functions of X 2 only. Definition 2 A pair of rules F H 1, H 2 satisfies rule independence just in case, for all u, v, y: Pr[F = u = v, Y = y] = Pr[F = u Y = y] and similarly for F H 2, H 1. A classification problem instance satisfies rule independence just in case all opposing-view rule pairs satisfy rule independence. If instead of generating H 1 and H 2 from X 1 and X 2, we assume a set of features F (which can be thought of as binary rules), and take H 1 = H 2 = F, rule independence reduces to the Naive Bayes independence assumption. The following theorem is not difficult to prove; we omit the proof. Theorem 1 View independence implies rule independence. 4 Rule Independence and Bootstrapping Blum and Mitchell s paper suggests that rules that agree on unlabelled instances are useful in bootstrapping. Definition 3 The agreement rate between rules F and is Pr[F = F, ] Note that the agreement rate between rules makes no reference to labels; it can be determined from unlabeled data. The algorithm that Blum and Mitchell describe does not explicitly search for rules with good agreement; nor does agreement rate play any direct role in the learnability proof given in the Blum and Mitchell paper. The second lack is emended in (Dasgupta et al., 2001). They show that, if view independence is satisfied, then the agreement rate between opposing-view rules F and upper bounds the error of F (or ). The following statement of the theorem is simplified and assumes non-abstaining binary rules. Theorem 2 For all F H 1, H 2 that satisfy rule independence and are nontrivial predictors in the sense that min u Pr[F = u] > Pr[F
3 ], one of the following inequalities holds: Pr[F Y ] Pr[F ] Pr[ F Y ] Pr[F ] If F agrees with on all but ɛ unlabelled instances, then either F or F predicts Y with error no greater than ɛ. A small amount of labelled data suffices to choose between F and F. I give a geometric proof sketch here; the reader is referred to the original paper for a formal proof. Consider figures 1 and 2. In these diagrams, area represents probability. For example, the leftmost box (in either diagram) represents the instances for which Y =, and the area of its upper left quadrant represents Pr[F =, =, Y = ]. Typically, in such a diagram, either the horizontal or vertical line is broken, as in figure 2. In the special case in which rule independence is satisfied, both horizontal and vertical lines are unbroken, as in figure 1. Theorem 2 states that disagreement upper bounds error. First let us consider a lemma, to wit: disagreement upper bounds minority probabilities. Define the minority value of F given Y = y to be the value u with least probability Pr[F = u Y = y]; the minority probability is the probability of the minority value. (Note that minority probabilities are conditional probabilities, and distinct from the marginal probability min u Pr[F = u] mentioned in the theorem.) In figure 1a, the areas of disagreement are the upper right and lower left quadrants of each box, as marked. The areas of minority values are marked in figure 1b. It should be obvious that the area of disagreement upper bounds the area of minority values. The error values of F are the values opposite to the values of Y : the error value is when Y = and when Y =. When minority values are error values, as in figure 1, disagreement upper bounds error, and theorem 2 follows immediately. However, three other cases are possible. One possibility is that minority values are opposite to error values. In this case, the minority values of F are error values, and disagreement between F and upper bounds the error of F. F Y = Y = (a) Disagreement F Y = Y = (b) Minority Values Figure 1: Disagreement upper-bounds minority probabilities. This case is admitted by theorem 2. In the final two cases, minority values are the same regardless of the value of Y. In these cases, however, the predictors do not satisfy the nontriviality condition of theorem 2, which requires that min u Pr[F = u] be greater than the disagreement between F and. 5 The Unreasonableness of Rule Independence Rule independence is a very strong assumption; one remarkable consequence will show just how strong it is. The precision of a rule F is defined to be Pr[Y = F = ]. (We continue to assume non-abstaining binary rules.) If rule independence holds, knowing the precision of any one rule allows one to exactly compute the precision of every other rule given only unlabeled data and knowledge of the size of the target concept. Let F and be arbitrary rules based on independent views. We first derive an expression for the precision of F in terms of. Note that the second line is derived from the first by rule independence. P (F ) = P (F Y )P (Y ) P (F Ȳ )P (Ȳ ) = P (F Y )P (Y ) P (F Ȳ )P (Ȳ ) P ( F ) = P (Y F )P ( Y ) [1 P (Y F )]P ( Ȳ ) P (Y F ) = P ( F ) P ( Ȳ ) P ( Y ) P ( Ȳ ) To compute the expression on the righthand side of the last line, we require P (Y ), P (Y ), P ( F ), and P (). The first value, the precision of, is assumed known. The second value, P (Y ), is also assumed known; it can at any rate be estimated from a small amount of labeled data. The last two values, P ( F ) and P (), can be computed from unlabeled data.
4 Thus, given the precision of an arbitrary rule, we can compute the precision of any otherview rule F. Then we can compute the precision of rules based on the same view as by using the precision of some other-view rule F. Hence we can compute the precision of every rule given the precision of any one. 6 Some Data The empirical investigations described here and below use the data set of (Collins and Singer, 1999). The task is to classify names in text as person, location, or organization. There is an unlabeled training set containing 89,305 instances, and a labeled test set containing 289 persons, 186 locations, 402 organizations, and 123 other, for a total of 1,000 instances. Instances are represented as lists of features. Intrinsic features are the words making up the name, and contextual features are features of the syntactic context in which the name occurs. For example, consider Bruce Kaplan, president of Metals Inc. This text snippet contains two instances. The first has intrinsic features N:Bruce-Kaplan, C:Bruce, and C:Kaplan ( N for the complete name, C for contains ), and contextual feature M:president ( M for modified by ). The second instance has intrinsic features N:Metals-Inc, C:Metals, C:Inc, and contextual feature X:president-of ( X for in the context of ). Let us define Y (x) = if x is a location instance, and Y (x) = otherwise. We can estimate P (Y ) from the test sample; it contains 186/1000 location instances, giving P (Y ) =.186. Let us treat each feature F as a rule predicting when F is present and otherwise. The precision of F is P (Y F ). The internal feature N:New-York has precision 1. This permits us to compute the precision of various contextual features, as shown in the Co-training column of Table 1. We note that the numbers do not even look like probabilities. The cause is the failure of view independence to hold in the data, combined with the instability of the estimator. (The Yarowsky column uses a seed rule to estimate F Co-training Yarowsky Truth M:chairman X:Company-of X:court-in X:Company-in X:firm-in X:%-in X:meeting-in F Y = Table 1: Some data Y = (a) Positive correlation F Y = Y = (b) Negative correlation Figure 2: Deviation from conditional independence. P (Y F ), as is done in the Yarowsky algorithm, and the Truth column shows the true value of P (Y F ).) 7 Relaxing the Assumption Nonetheless, the unreasonableness of view independence does not mean we must abandon theorem 2. In this section, we introduce a weaker assumption, one that is satisfied by the data, and we show that theorem 2 holds under this weaker assumption. There are two ways in which the data can diverge from conditional independence: the rules may either be positively or negatively correlated, given the class value. Figure 2a illustrates positive correlation, and figure 2b illustrates negative correlation. If the rules are negatively correlated, then their disagreement (shaded in figure 2) is larger than if they are conditionally independent, and the conclusion of theorem 2 is maintained a fortiori. Unfortunately, in the data, they are positively correlated, so the theorem does not apply. Let us quantify the amount of deviation from conditional independence. We define the conditional dependence of F and given Y = y to
5 be d y = 1 2 Pr[ = v Y = y, F = u] Pr[ = v Y = y] u,v If F and are conditionally independent, then d y = 0. This permits us to state a weaker version of rule independence: Definition 4 Rules F and satisfy weak rule dependence just in case, for y {, }: d y p 2 q 1 p 1 2p 1 q 1 where p 1 = min u Pr[F = u Y = y], p 2 = min u Pr[ = u Y = y], and q 1 = 1 p 1. By definition, p 1 and p 2 cannot exceed 0.5. If p 1 = 0.5, then weak rule dependence reduces to independence: if p 1 = 0.5 and weak rule dependence is satisfied, then d y must be 0, which is to say, F and must be conditionally independent. However, as p 1 decreases, the permissible amount of conditional dependence increases. We can now state a generalized version of theorem 2: Theorem 3 For all F H 1, H 2 that satisfy weak rule dependence and are nontrivial predictors in the sense that min u Pr[F = u] > Pr[F ], one of the following inequalities holds: Pr[F Y ] Pr[F ] Pr[ F Y ] Pr[F ] Consider figure 3. This illustrates the most relevant case, in which F and are positively correlated given Y. (Only the case Y = is shown; the case Y = is similar.) We assume that the minority values of F are error values; the other cases are handled as in the discussion of theorem 2. Let u be the minority value of when Y =. In figure 3, a is the probability that = u when F takes its minority value, and b is the probability that = u when F takes its majority value. The value r = a b is the difference. Note that r = 0 if F and are conditionally independent given Y =. In fact, we can show q 1 D q 2 1 B p r C a A p 2 Figure 3: Positive correlation, Y =. that r is exactly our measure d y of conditional dependence: 2d y = a p 2 b p 2 (1 a) (1 p 2 ) (1 b) (1 p 2 ) = a b a b = 2r Hence, in particular, we may write d y = a b. Observe further that p 2, the minority probability of when Y =, is a weighted average of a and b, namely, p 2 = p 1 aq 1 b. Combining this with the equation d y = a b allows us to express a and b in terms of the remaining variables, to wit: a = p 2 q 1 d y and b = p 2 p 1 d y. In order to prove theorem 3, we need to show that the area of disagreement (B C) upper bounds the area of the minority value of F (A B). This is true just in case C is larger than A, which is to say, if bq 1 ap 1. Substituting our expressions for a and b into this inequality and solving for d y yields: d y p 2 q 1 p 1 2p 1 q 1 In short, disagreement upper bounds the minority probability just in case weak rule dependence is satisfied, proving the theorem. 8 The reedy Agreement Algorithm Dasgupta, Littman, and McAllester suggest a possible algorithm at the end of their paper, but they give only the briefest suggestion, and do not implement or evaluate it. I give here an algorithm, the reedy Agreement Algorithm, b
6 Input: seed rules F, loop for each atomic rule H = H evaluate cost of (F, ) keep lowest-cost if is worse than, quit swap F, Figure 4: The reedy Agreement Algorithm Precision that constructs paired rules that agree on unlabeled data, and I examine its performance. The algorithm is given in figure 4. It begins with two seed rules, one for each view. At each iteration, each possible extension to one of the rules is considered and scored. The best one is kept, and attention shifts to the other rule. A complex rule (or classifier) is a list of atomic rules H, each associating a single feature h with a label l. H(x) = l if x has feature h, and H(x) = otherwise. A given atomic rule is permitted to appear multiple times in the list. Each atomic rule occurrence gets one vote, and the classifier s prediction is the label that receives the most votes. In case of a tie, there is no prediction. The cost of a classifier pair (F, ) is based on a more general version of theorem 2, that admits abstaining rules. The following theorem is based on (Dasgupta et al., 2001). Theorem 4 If view independence is satisfied, and if F and are rules based on different views, then one of the following holds: Pr[F Y F ] Pr[ F Y F ] δ µ δ δ µ δ where δ = Pr[F F, ], and µ = min u Pr[F = u F ]. In other words, for a given binary rule F, a pessimistic estimate of the number of errors made by F is δ/(µ δ) times the number of instances labeled by F, plus the number of instances left unlabeled by F. Finally, we note that the cost of F is sensitive to the choice of, but the cost of F with respect to is not necessarily the same as the cost of with respect to F. To get an overall cost, we average the cost of F with respect to and with respect to F Recall Figure 5: Performance of the greedy agreement algorithm Figure 5 shows the performance of the greedy agreement algorithm after each iteration. Because not all test instances are labeled (some are neither persons nor locations nor organizations), and because classifiers do not label all instances, we show precision and recall rather than a single error rate. The contour lines show levels of the F-measure (the harmonic mean of precision and recall). The algorithm is run to convergence, that is, until no atomic rule can be found that decreases cost. It is interesting to note that there is no significant overtraining with respect to F-measure. The final values are 89.2/80.4/84.5 recall/precision/f-measure, which compare favorably with the performance of the Yarowsky algorithm (83.3/84.6/84.0). (Collins and Singer, 1999) add a special final round to boost recall, yielding 91.2/80.0/85.2 for the Yarowsky algorithm and 91.3/80.1/85.3 for their version of the original co-training algorithm. All four algorithms essentially perform equally well; the advantage of the greedy agreement algorithm is that we have an explanation for why it performs well. 9 The Yarowsky Algorithm For Yarowsky s algorithm, a classifier again consists of a list of atomic rules. The prediction of the classifier is the prediction of the first rule in the list that applies. The algorithm constructs a
7 classifier iteratively, beginning with a seed rule. In the variant we consider here, one atomic rule is added at each iteration. An atomic rule F l is chosen only if its precision, Pr[ l = F l = ] (as measured using the labels assigned by the current classifier ), exceeds a fixed threshold θ. 1 Yarowsky does not give an explicit justification for the algorithm. I show here that the algorithm can be justified on the basis of two independence assumptions. In what follows, F represents an atomic rule under consideration, and represents the current classifier. Recall that Y l is the set of instances whose true label is l, and l is the set of instances {x : (x) = l}. We write for the set of instances labeled by the current classifier, that is, {x : (x) }. The first assumption is precision independence. Definition 5 Candidate rule F l and classifier satisfy precision independence just in case P (Y l F l, ) = P (Y l F l ) A bootstrapping problem instance satisfies precision independence just in case all rules and all atomic rules F l that nontrivially overlap with (both F l and F l are nonempty) satisfy precision independence. Precision independence is stated here so that it looks like a conditional independence assumption, to emphasize the similarity to the analysis of co-training. In fact, it is only half an independence assumption for precision independence, it is not necessary that P (Y l F l, ) = P (Y l F l ). The second assumption is that classifiers make balanced errors. That is: P (Y l, l F l ) = P (Y l, l F l ) Let us first consider a concrete (but hypothetical) example. Suppose the initial classifier correctly labels 100 out of 1000 instances, and makes no mistakes. Then the initial precision is 1 (Yarowsky, 1995), citing (Yarowsky, 1994), actually uses a superficially different score that is, however, a monotone transform of precision, hence equivalent to precision, since it is used only for sorting. 1 and recall is 0.1. Suppose further that we add an atomic rule that correctly labels 19 new instances, and incorrectly labels one new instance. The rule s precision is The precision of the new classifier (the old classifier plus the new atomic rule) is 119/120 = Note that the new precision lies between the old precision and the precision of the rule. We will show that this is always the case, given precision independence and balanced errors. We need to consider several quantities: the precision of the current classifier, P (Y l l ); the precision of the rule under consideration, P (Y l F l ); the precision of the rule on the current labeled set, P (Y l F l ); and the precision of the rule as measured using estimated labels, P ( l F l ). The assumption of balanced errors implies that measured precision equals true precision on labeled instances, as follows. (We assume here that all instances have true labels, hence that Ȳ l = Y l.) P (F l l Ȳ l ) = P (F l ly l ) P (F l l Y l ) P (F l l Ȳ l ) = P (Y l F l l ) P (F l ly l ) P (F l l ) = P (Y l F l ) P ( l F l ) = P (Y l F l ) This, combined with precision independence, implies that the precision of F l as measured on the labeled set is equal to its true precision P (Y l F l ). Now consider the precision of the old and new classifiers at predicting l. Of the instances that the old classifier labels l, let A be the number that are correctly labeled and B be the number that are incorrectly labeled. Defining N t = A B, the precision of the old classifier is Q t = A/N t. Let A be the number of new instances that the rule under consideration correctly labels, and let B be the number that it incorrectly labels. Defining n = A B, the precision of the rule is q = A/n. The precision of the new classifier is Q t1 = (A A)/N t1, which can be written as: Q t1 = N t Q t n q N t1 N t1 That is, the precision of the new classifier is a weighted average of the precision of the old classifier and the precision of the new rule.
8 Precision Recall Figure 6: Performance of the Yarowsky algorithm An immediate consequence is that, if we only accept rules whose precision exceeds a given threshold θ, then the precision of the new classifier exceeds θ. Since measured precision equals true precision under our previous assumptions, it follows that the true precision of the final classifier exceeds θ if the measured precision of every accepted rule exceeds θ. Moreover, observe that recall can be written as: A = N t Q t N l N l where N l is the number of instances whose true label is l. If Q t > θ, then recall is bounded below by N t θ/n l, which grows as N t grows. Hence we have proven the following theorem. Theorem 5 If the assumptions of precision independence and balanced errors are satisfied, then the Yarowsky algorithm with threshold θ obtains a final classifier whose precision is at least θ. Moreover, recall is bounded below by N t θ/n l, a quantity which increases at each round. Intuitively, the Yarowsky algorithm increases recall while holding precision above a threshold that represents the desired precision of the final classifier. The empirical behavior of the algorithm, as shown in figure 6, is in accordance with this analysis. We have seen, then, that the Yarowsky algorithm, like the co-training algorithm, can be justified on the basis of an independence assumption, precision independence. It is important to note, however, that the Yarowsky algorithm is not a special case of co-training. Precision independence and view independence are distinct assumptions; neither implies the other Conclusion To sum up, we have refined previous work on the analysis of co-training, and given a new cotraining algorithm that is theoretically justified and has good empirical performance. We have also given a theoretical analysis of the Yarowsky algorithm for the first time, and shown that it can be justified by an independence assumption that is quite distinct from the independence assumption that co-training is based on. References A. Blum and T. Mitchell Combining labeled and unlabeled data with co-training. In COLT: Proceedings of the Workshop on Computational Learning Theory. Morgan Kaufmann Publishers. Michael Collins and Yoram Singer Unsupervised models for named entity classification. In EMNLP. Sanjoy Dasgupta, Michael Littman, and David McAllester PAC generalization bounds for co-training. In Proceedings of NIPS. David Yarowsky Decision lists for lexical ambiguity resolution. In Proceedings ACL 32. David Yarowsky Unsupervised word sense disambiguation rivaling supervised methods. In Proceedings of the 33rd Annual Meeting of the Association for Computational Linguistics, pages To see that view independence does not imply precision indepence, consider an example in which = Y always. This is compatible with rule independence, but it implies that P (Y F ) = 1 and P (Y F Ḡ) = 0, violating precision independence.
PAC Generalization Bounds for Co-training
 PAC Generalization Bounds for Co-training Sanjoy Dasgupta AT&T Labs Research dasgupta@research.att.com Michael L. Littman AT&T Labs Research mlittman@research.att.com David McAllester AT&T Labs Research
PAC Generalization Bounds for Co-training Sanjoy Dasgupta AT&T Labs Research dasgupta@research.att.com Michael L. Littman AT&T Labs Research mlittman@research.att.com David McAllester AT&T Labs Research
Co-Training and Expansion: Towards Bridging Theory and Practice
 Co-Training and Expansion: Towards Bridging Theory and Practice Maria-Florina Balcan Computer Science Dept. Carnegie Mellon Univ. Pittsburgh, PA 53 ninamf@cs.cmu.edu Avrim Blum Computer Science Dept. Carnegie
Co-Training and Expansion: Towards Bridging Theory and Practice Maria-Florina Balcan Computer Science Dept. Carnegie Mellon Univ. Pittsburgh, PA 53 ninamf@cs.cmu.edu Avrim Blum Computer Science Dept. Carnegie
Expectation Maximization, and Learning from Partly Unobserved Data (part 2)
 Expectation Maximization, and Learning from Partly Unobserved Data (part 2) Machine Learning 10-701 April 2005 Tom M. Mitchell Carnegie Mellon University Clustering Outline K means EM: Mixture of Gaussians
Expectation Maximization, and Learning from Partly Unobserved Data (part 2) Machine Learning 10-701 April 2005 Tom M. Mitchell Carnegie Mellon University Clustering Outline K means EM: Mixture of Gaussians
Co-training and Learning with Noise
 Co-training and Learning with Noise Wee Sun Lee LEEWS@COMP.NUS.EDU.SG Department of Computer Science and Singapore-MIT Alliance, National University of Singapore, Singapore 117543, Republic of Singapore
Co-training and Learning with Noise Wee Sun Lee LEEWS@COMP.NUS.EDU.SG Department of Computer Science and Singapore-MIT Alliance, National University of Singapore, Singapore 117543, Republic of Singapore
Discriminative Learning can Succeed where Generative Learning Fails
 Discriminative Learning can Succeed where Generative Learning Fails Philip M. Long, a Rocco A. Servedio, b,,1 Hans Ulrich Simon c a Google, Mountain View, CA, USA b Columbia University, New York, New York,
Discriminative Learning can Succeed where Generative Learning Fails Philip M. Long, a Rocco A. Servedio, b,,1 Hans Ulrich Simon c a Google, Mountain View, CA, USA b Columbia University, New York, New York,
Understanding the Yarowsky Algorithm
 Understanding the Yarowsy Algorithm Steven Abney University of Michigan Many problems in computational linguistics are well suited for bootstrapping (semi-supervised learning) techniques. The Yarowsy algorithm
Understanding the Yarowsy Algorithm Steven Abney University of Michigan Many problems in computational linguistics are well suited for bootstrapping (semi-supervised learning) techniques. The Yarowsy algorithm
Understanding the Yarowsky Algorithm
 Understanding the Yarowsky Algorithm Steven Abney University of Michigan Many problems in computational linguistics are well suited for bootstrapping (semisupervised learning) techniques. The Yarowsky
Understanding the Yarowsky Algorithm Steven Abney University of Michigan Many problems in computational linguistics are well suited for bootstrapping (semisupervised learning) techniques. The Yarowsky
Efficient Semi-supervised and Active Learning of Disjunctions
 Maria-Florina Balcan ninamf@cc.gatech.edu Christopher Berlind cberlind@gatech.edu Steven Ehrlich sehrlich@cc.gatech.edu Yingyu Liang yliang39@gatech.edu School of Computer Science, College of Computing,
Maria-Florina Balcan ninamf@cc.gatech.edu Christopher Berlind cberlind@gatech.edu Steven Ehrlich sehrlich@cc.gatech.edu Yingyu Liang yliang39@gatech.edu School of Computer Science, College of Computing,
CS446: Machine Learning Fall Final Exam. December 6 th, 2016
 CS446: Machine Learning Fall 2016 Final Exam December 6 th, 2016 This is a closed book exam. Everything you need in order to solve the problems is supplied in the body of this exam. This exam booklet contains
CS446: Machine Learning Fall 2016 Final Exam December 6 th, 2016 This is a closed book exam. Everything you need in order to solve the problems is supplied in the body of this exam. This exam booklet contains
Learning Features from Co-occurrences: A Theoretical Analysis
 Learning Features from Co-occurrences: A Theoretical Analysis Yanpeng Li IBM T. J. Watson Research Center Yorktown Heights, New York 10598 liyanpeng.lyp@gmail.com Abstract Representing a word by its co-occurrences
Learning Features from Co-occurrences: A Theoretical Analysis Yanpeng Li IBM T. J. Watson Research Center Yorktown Heights, New York 10598 liyanpeng.lyp@gmail.com Abstract Representing a word by its co-occurrences
Understanding the Yarowsky Algorithm
 Understanding the Yarowsy Algorithm Steven Abney August, 2003 Introduction Bootstrapping, or semi-supervised learning, has become an important topic in computational linguistics. For many language-processing
Understanding the Yarowsy Algorithm Steven Abney August, 2003 Introduction Bootstrapping, or semi-supervised learning, has become an important topic in computational linguistics. For many language-processing
From Batch to Transductive Online Learning
 From Batch to Transductive Online Learning Sham Kakade Toyota Technological Institute Chicago, IL 60637 sham@tti-c.org Adam Tauman Kalai Toyota Technological Institute Chicago, IL 60637 kalai@tti-c.org
From Batch to Transductive Online Learning Sham Kakade Toyota Technological Institute Chicago, IL 60637 sham@tti-c.org Adam Tauman Kalai Toyota Technological Institute Chicago, IL 60637 kalai@tti-c.org
Does Unlabeled Data Help?
 Does Unlabeled Data Help? Worst-case Analysis of the Sample Complexity of Semi-supervised Learning. Ben-David, Lu and Pal; COLT, 2008. Presentation by Ashish Rastogi Courant Machine Learning Seminar. Outline
Does Unlabeled Data Help? Worst-case Analysis of the Sample Complexity of Semi-supervised Learning. Ben-David, Lu and Pal; COLT, 2008. Presentation by Ashish Rastogi Courant Machine Learning Seminar. Outline
Machine Learning Ensemble Learning I Hamid R. Rabiee Jafar Muhammadi, Alireza Ghasemi Spring /
 Machine Learning Ensemble Learning I Hamid R. Rabiee Jafar Muhammadi, Alireza Ghasemi Spring 2015 http://ce.sharif.edu/courses/93-94/2/ce717-1 / Agenda Combining Classifiers Empirical view Theoretical
Machine Learning Ensemble Learning I Hamid R. Rabiee Jafar Muhammadi, Alireza Ghasemi Spring 2015 http://ce.sharif.edu/courses/93-94/2/ce717-1 / Agenda Combining Classifiers Empirical view Theoretical
A Bound on the Label Complexity of Agnostic Active Learning
 A Bound on the Label Complexity of Agnostic Active Learning Steve Hanneke March 2007 CMU-ML-07-103 School of Computer Science Carnegie Mellon University Pittsburgh, PA 15213 Machine Learning Department,
A Bound on the Label Complexity of Agnostic Active Learning Steve Hanneke March 2007 CMU-ML-07-103 School of Computer Science Carnegie Mellon University Pittsburgh, PA 15213 Machine Learning Department,
CSCI-567: Machine Learning (Spring 2019)
 CSCI-567: Machine Learning (Spring 2019) Prof. Victor Adamchik U of Southern California Mar. 19, 2019 March 19, 2019 1 / 43 Administration March 19, 2019 2 / 43 Administration TA3 is due this week March
CSCI-567: Machine Learning (Spring 2019) Prof. Victor Adamchik U of Southern California Mar. 19, 2019 March 19, 2019 1 / 43 Administration March 19, 2019 2 / 43 Administration TA3 is due this week March
Minimax risk bounds for linear threshold functions
 CS281B/Stat241B (Spring 2008) Statistical Learning Theory Lecture: 3 Minimax risk bounds for linear threshold functions Lecturer: Peter Bartlett Scribe: Hao Zhang 1 Review We assume that there is a probability
CS281B/Stat241B (Spring 2008) Statistical Learning Theory Lecture: 3 Minimax risk bounds for linear threshold functions Lecturer: Peter Bartlett Scribe: Hao Zhang 1 Review We assume that there is a probability
1 Active Learning Foundations of Machine Learning and Data Science. Lecturer: Maria-Florina Balcan Lecture 20 & 21: November 16 & 18, 2015
 10-806 Foundations of Machine Learning and Data Science Lecturer: Maria-Florina Balcan Lecture 20 & 21: November 16 & 18, 2015 1 Active Learning Most classic machine learning methods and the formal learning
10-806 Foundations of Machine Learning and Data Science Lecturer: Maria-Florina Balcan Lecture 20 & 21: November 16 & 18, 2015 1 Active Learning Most classic machine learning methods and the formal learning
Machine Learning, Midterm Exam: Spring 2008 SOLUTIONS. Q Topic Max. Score Score. 1 Short answer questions 20.
 10-601 Machine Learning, Midterm Exam: Spring 2008 Please put your name on this cover sheet If you need more room to work out your answer to a question, use the back of the page and clearly mark on the
10-601 Machine Learning, Midterm Exam: Spring 2008 Please put your name on this cover sheet If you need more room to work out your answer to a question, use the back of the page and clearly mark on the
Unsupervised Learning with Permuted Data
 Unsupervised Learning with Permuted Data Sergey Kirshner skirshne@ics.uci.edu Sridevi Parise sparise@ics.uci.edu Padhraic Smyth smyth@ics.uci.edu School of Information and Computer Science, University
Unsupervised Learning with Permuted Data Sergey Kirshner skirshne@ics.uci.edu Sridevi Parise sparise@ics.uci.edu Padhraic Smyth smyth@ics.uci.edu School of Information and Computer Science, University
Lecture Learning infinite hypothesis class via VC-dimension and Rademacher complexity;
 CSCI699: Topics in Learning and Game Theory Lecture 2 Lecturer: Ilias Diakonikolas Scribes: Li Han Today we will cover the following 2 topics: 1. Learning infinite hypothesis class via VC-dimension and
CSCI699: Topics in Learning and Game Theory Lecture 2 Lecturer: Ilias Diakonikolas Scribes: Li Han Today we will cover the following 2 topics: 1. Learning infinite hypothesis class via VC-dimension and
Algorithm Independent Topics Lecture 6
 Algorithm Independent Topics Lecture 6 Jason Corso SUNY at Buffalo Feb. 23 2009 J. Corso (SUNY at Buffalo) Algorithm Independent Topics Lecture 6 Feb. 23 2009 1 / 45 Introduction Now that we ve built an
Algorithm Independent Topics Lecture 6 Jason Corso SUNY at Buffalo Feb. 23 2009 J. Corso (SUNY at Buffalo) Algorithm Independent Topics Lecture 6 Feb. 23 2009 1 / 45 Introduction Now that we ve built an
Introduction to Algorithms / Algorithms I Lecturer: Michael Dinitz Topic: Intro to Learning Theory Date: 12/8/16
 600.463 Introduction to Algorithms / Algorithms I Lecturer: Michael Dinitz Topic: Intro to Learning Theory Date: 12/8/16 25.1 Introduction Today we re going to talk about machine learning, but from an
600.463 Introduction to Algorithms / Algorithms I Lecturer: Michael Dinitz Topic: Intro to Learning Theory Date: 12/8/16 25.1 Introduction Today we re going to talk about machine learning, but from an
Learning with multiple models. Boosting.
 CS 2750 Machine Learning Lecture 21 Learning with multiple models. Boosting. Milos Hauskrecht milos@cs.pitt.edu 5329 Sennott Square Learning with multiple models: Approach 2 Approach 2: use multiple models
CS 2750 Machine Learning Lecture 21 Learning with multiple models. Boosting. Milos Hauskrecht milos@cs.pitt.edu 5329 Sennott Square Learning with multiple models: Approach 2 Approach 2: use multiple models
Lecture 8. Instructor: Haipeng Luo
 Lecture 8 Instructor: Haipeng Luo Boosting and AdaBoost In this lecture we discuss the connection between boosting and online learning. Boosting is not only one of the most fundamental theories in machine
Lecture 8 Instructor: Haipeng Luo Boosting and AdaBoost In this lecture we discuss the connection between boosting and online learning. Boosting is not only one of the most fundamental theories in machine
On the errors introduced by the naive Bayes independence assumption
 On the errors introduced by the naive Bayes independence assumption Author Matthijs de Wachter 3671100 Utrecht University Master Thesis Artificial Intelligence Supervisor Dr. Silja Renooij Department of
On the errors introduced by the naive Bayes independence assumption Author Matthijs de Wachter 3671100 Utrecht University Master Thesis Artificial Intelligence Supervisor Dr. Silja Renooij Department of
arxiv: v1 [cs.lg] 15 Aug 2017
![arxiv: v1 [cs.lg] 15 Aug 2017 arxiv: v1 [cs.lg] 15 Aug 2017](/thumbs/76/73518315.jpg) Theoretical Foundation of Co-Training and Disagreement-Based Algorithms arxiv:1708.04403v1 [cs.lg] 15 Aug 017 Abstract Wei Wang, Zhi-Hua Zhou National Key Laboratory for Novel Software Technology, Nanjing
Theoretical Foundation of Co-Training and Disagreement-Based Algorithms arxiv:1708.04403v1 [cs.lg] 15 Aug 017 Abstract Wei Wang, Zhi-Hua Zhou National Key Laboratory for Novel Software Technology, Nanjing
Testing Problems with Sub-Learning Sample Complexity
 Testing Problems with Sub-Learning Sample Complexity Michael Kearns AT&T Labs Research 180 Park Avenue Florham Park, NJ, 07932 mkearns@researchattcom Dana Ron Laboratory for Computer Science, MIT 545 Technology
Testing Problems with Sub-Learning Sample Complexity Michael Kearns AT&T Labs Research 180 Park Avenue Florham Park, NJ, 07932 mkearns@researchattcom Dana Ron Laboratory for Computer Science, MIT 545 Technology
COMS 4771 Introduction to Machine Learning. Nakul Verma
 COMS 4771 Introduction to Machine Learning Nakul Verma Announcements HW1 due next lecture Project details are available decide on the group and topic by Thursday Last time Generative vs. Discriminative
COMS 4771 Introduction to Machine Learning Nakul Verma Announcements HW1 due next lecture Project details are available decide on the group and topic by Thursday Last time Generative vs. Discriminative
Algorithm-Independent Learning Issues
 Algorithm-Independent Learning Issues Selim Aksoy Department of Computer Engineering Bilkent University saksoy@cs.bilkent.edu.tr CS 551, Spring 2007 c 2007, Selim Aksoy Introduction We have seen many learning
Algorithm-Independent Learning Issues Selim Aksoy Department of Computer Engineering Bilkent University saksoy@cs.bilkent.edu.tr CS 551, Spring 2007 c 2007, Selim Aksoy Introduction We have seen many learning
Learning with Rejection
 Learning with Rejection Corinna Cortes 1, Giulia DeSalvo 2, and Mehryar Mohri 2,1 1 Google Research, 111 8th Avenue, New York, NY 2 Courant Institute of Mathematical Sciences, 251 Mercer Street, New York,
Learning with Rejection Corinna Cortes 1, Giulia DeSalvo 2, and Mehryar Mohri 2,1 1 Google Research, 111 8th Avenue, New York, NY 2 Courant Institute of Mathematical Sciences, 251 Mercer Street, New York,
Essential Question: What is a complex number, and how can you add, subtract, and multiply complex numbers? Explore Exploring Operations Involving
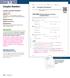 Locker LESSON 3. Complex Numbers Name Class Date 3. Complex Numbers Common Core Math Standards The student is expected to: N-CN. Use the relation i = 1 and the commutative, associative, and distributive
Locker LESSON 3. Complex Numbers Name Class Date 3. Complex Numbers Common Core Math Standards The student is expected to: N-CN. Use the relation i = 1 and the commutative, associative, and distributive
Generalization bounds
 Advanced Course in Machine Learning pring 200 Generalization bounds Handouts are jointly prepared by hie Mannor and hai halev-hwartz he problem of characterizing learnability is the most basic question
Advanced Course in Machine Learning pring 200 Generalization bounds Handouts are jointly prepared by hie Mannor and hai halev-hwartz he problem of characterizing learnability is the most basic question
CS229 Supplemental Lecture notes
 CS229 Supplemental Lecture notes John Duchi 1 Boosting We have seen so far how to solve classification (and other) problems when we have a data representation already chosen. We now talk about a procedure,
CS229 Supplemental Lecture notes John Duchi 1 Boosting We have seen so far how to solve classification (and other) problems when we have a data representation already chosen. We now talk about a procedure,
Chapter 2 The Naïve Bayes Model in the Context of Word Sense Disambiguation
 Chapter 2 The Naïve Bayes Model in the Context of Word Sense Disambiguation Abstract This chapter discusses the Naïve Bayes model strictly in the context of word sense disambiguation. The theoretical model
Chapter 2 The Naïve Bayes Model in the Context of Word Sense Disambiguation Abstract This chapter discusses the Naïve Bayes model strictly in the context of word sense disambiguation. The theoretical model
Support Vector Machines
 Support Vector Machines Jordan Boyd-Graber University of Colorado Boulder LECTURE 7 Slides adapted from Tom Mitchell, Eric Xing, and Lauren Hannah Jordan Boyd-Graber Boulder Support Vector Machines 1 of
Support Vector Machines Jordan Boyd-Graber University of Colorado Boulder LECTURE 7 Slides adapted from Tom Mitchell, Eric Xing, and Lauren Hannah Jordan Boyd-Graber Boulder Support Vector Machines 1 of
Machine Learning: Chenhao Tan University of Colorado Boulder LECTURE 9
 Machine Learning: Chenhao Tan University of Colorado Boulder LECTURE 9 Slides adapted from Jordan Boyd-Graber Machine Learning: Chenhao Tan Boulder 1 of 39 Recap Supervised learning Previously: KNN, naïve
Machine Learning: Chenhao Tan University of Colorado Boulder LECTURE 9 Slides adapted from Jordan Boyd-Graber Machine Learning: Chenhao Tan Boulder 1 of 39 Recap Supervised learning Previously: KNN, naïve
10.1 The Formal Model
 67577 Intro. to Machine Learning Fall semester, 2008/9 Lecture 10: The Formal (PAC) Learning Model Lecturer: Amnon Shashua Scribe: Amnon Shashua 1 We have see so far algorithms that explicitly estimate
67577 Intro. to Machine Learning Fall semester, 2008/9 Lecture 10: The Formal (PAC) Learning Model Lecturer: Amnon Shashua Scribe: Amnon Shashua 1 We have see so far algorithms that explicitly estimate
Linear Classifiers. Michael Collins. January 18, 2012
 Linear Classifiers Michael Collins January 18, 2012 Today s Lecture Binary classification problems Linear classifiers The perceptron algorithm Classification Problems: An Example Goal: build a system that
Linear Classifiers Michael Collins January 18, 2012 Today s Lecture Binary classification problems Linear classifiers The perceptron algorithm Classification Problems: An Example Goal: build a system that
Lecture 29: Computational Learning Theory
 CS 710: Complexity Theory 5/4/2010 Lecture 29: Computational Learning Theory Instructor: Dieter van Melkebeek Scribe: Dmitri Svetlov and Jake Rosin Today we will provide a brief introduction to computational
CS 710: Complexity Theory 5/4/2010 Lecture 29: Computational Learning Theory Instructor: Dieter van Melkebeek Scribe: Dmitri Svetlov and Jake Rosin Today we will provide a brief introduction to computational
Machine Learning for NLP
 Machine Learning for NLP Uppsala University Department of Linguistics and Philology Slides borrowed from Ryan McDonald, Google Research Machine Learning for NLP 1(50) Introduction Linear Classifiers Classifiers
Machine Learning for NLP Uppsala University Department of Linguistics and Philology Slides borrowed from Ryan McDonald, Google Research Machine Learning for NLP 1(50) Introduction Linear Classifiers Classifiers
1 Overview. 2 Learning from Experts. 2.1 Defining a meaningful benchmark. AM 221: Advanced Optimization Spring 2016
 AM 1: Advanced Optimization Spring 016 Prof. Yaron Singer Lecture 11 March 3rd 1 Overview In this lecture we will introduce the notion of online convex optimization. This is an extremely useful framework
AM 1: Advanced Optimization Spring 016 Prof. Yaron Singer Lecture 11 March 3rd 1 Overview In this lecture we will introduce the notion of online convex optimization. This is an extremely useful framework
Boosting with decision stumps and binary features
 Boosting with decision stumps and binary features Jason Rennie jrennie@ai.mit.edu April 10, 2003 1 Introduction A special case of boosting is when features are binary and the base learner is a decision
Boosting with decision stumps and binary features Jason Rennie jrennie@ai.mit.edu April 10, 2003 1 Introduction A special case of boosting is when features are binary and the base learner is a decision
Lecture 4. 1 Learning Non-Linear Classifiers. 2 The Kernel Trick. CS-621 Theory Gems September 27, 2012
 CS-62 Theory Gems September 27, 22 Lecture 4 Lecturer: Aleksander Mądry Scribes: Alhussein Fawzi Learning Non-Linear Classifiers In the previous lectures, we have focused on finding linear classifiers,
CS-62 Theory Gems September 27, 22 Lecture 4 Lecturer: Aleksander Mądry Scribes: Alhussein Fawzi Learning Non-Linear Classifiers In the previous lectures, we have focused on finding linear classifiers,
Active Learning: Disagreement Coefficient
 Advanced Course in Machine Learning Spring 2010 Active Learning: Disagreement Coefficient Handouts are jointly prepared by Shie Mannor and Shai Shalev-Shwartz In previous lectures we saw examples in which
Advanced Course in Machine Learning Spring 2010 Active Learning: Disagreement Coefficient Handouts are jointly prepared by Shie Mannor and Shai Shalev-Shwartz In previous lectures we saw examples in which
10701/15781 Machine Learning, Spring 2007: Homework 2
 070/578 Machine Learning, Spring 2007: Homework 2 Due: Wednesday, February 2, beginning of the class Instructions There are 4 questions on this assignment The second question involves coding Do not attach
070/578 Machine Learning, Spring 2007: Homework 2 Due: Wednesday, February 2, beginning of the class Instructions There are 4 questions on this assignment The second question involves coding Do not attach
CS6999 Probabilistic Methods in Integer Programming Randomized Rounding Andrew D. Smith April 2003
 CS6999 Probabilistic Methods in Integer Programming Randomized Rounding April 2003 Overview 2 Background Randomized Rounding Handling Feasibility Derandomization Advanced Techniques Integer Programming
CS6999 Probabilistic Methods in Integer Programming Randomized Rounding April 2003 Overview 2 Background Randomized Rounding Handling Feasibility Derandomization Advanced Techniques Integer Programming
Click Prediction and Preference Ranking of RSS Feeds
 Click Prediction and Preference Ranking of RSS Feeds 1 Introduction December 11, 2009 Steven Wu RSS (Really Simple Syndication) is a family of data formats used to publish frequently updated works. RSS
Click Prediction and Preference Ranking of RSS Feeds 1 Introduction December 11, 2009 Steven Wu RSS (Really Simple Syndication) is a family of data formats used to publish frequently updated works. RSS
Multiclass Classification-1
 CS 446 Machine Learning Fall 2016 Oct 27, 2016 Multiclass Classification Professor: Dan Roth Scribe: C. Cheng Overview Binary to multiclass Multiclass SVM Constraint classification 1 Introduction Multiclass
CS 446 Machine Learning Fall 2016 Oct 27, 2016 Multiclass Classification Professor: Dan Roth Scribe: C. Cheng Overview Binary to multiclass Multiclass SVM Constraint classification 1 Introduction Multiclass
Online Learning, Mistake Bounds, Perceptron Algorithm
 Online Learning, Mistake Bounds, Perceptron Algorithm 1 Online Learning So far the focus of the course has been on batch learning, where algorithms are presented with a sample of training data, from which
Online Learning, Mistake Bounds, Perceptron Algorithm 1 Online Learning So far the focus of the course has been on batch learning, where algorithms are presented with a sample of training data, from which
COMPUTATIONAL LEARNING THEORY
 COMPUTATIONAL LEARNING THEORY XIAOXU LI Abstract. This paper starts with basic concepts of computational learning theory and moves on with examples in monomials and learning rays to the final discussion
COMPUTATIONAL LEARNING THEORY XIAOXU LI Abstract. This paper starts with basic concepts of computational learning theory and moves on with examples in monomials and learning rays to the final discussion
1 A Lower Bound on Sample Complexity
 COS 511: Theoretical Machine Learning Lecturer: Rob Schapire Lecture #7 Scribe: Chee Wei Tan February 25, 2008 1 A Lower Bound on Sample Complexity In the last lecture, we stopped at the lower bound on
COS 511: Theoretical Machine Learning Lecturer: Rob Schapire Lecture #7 Scribe: Chee Wei Tan February 25, 2008 1 A Lower Bound on Sample Complexity In the last lecture, we stopped at the lower bound on
Practical Agnostic Active Learning
 Practical Agnostic Active Learning Alina Beygelzimer Yahoo Research based on joint work with Sanjoy Dasgupta, Daniel Hsu, John Langford, Francesco Orabona, Chicheng Zhang, and Tong Zhang * * introductory
Practical Agnostic Active Learning Alina Beygelzimer Yahoo Research based on joint work with Sanjoy Dasgupta, Daniel Hsu, John Langford, Francesco Orabona, Chicheng Zhang, and Tong Zhang * * introductory
Improved Algorithms for Confidence-Rated Prediction with Error Guarantees
 Improved Algorithms for Confidence-Rated Prediction with Error Guarantees Kamalika Chaudhuri Chicheng Zhang Department of Computer Science and Engineering University of California, San Diego 95 Gilman
Improved Algorithms for Confidence-Rated Prediction with Error Guarantees Kamalika Chaudhuri Chicheng Zhang Department of Computer Science and Engineering University of California, San Diego 95 Gilman
An adaptive version of the boost by majority algorithm
 An adaptive version of the boost by majority algorithm Yoav Freund AT&T Labs 180 Park Avenue Florham Park NJ 092 USA October 2 2000 Abstract We propose a new boosting algorithm This boosting algorithm
An adaptive version of the boost by majority algorithm Yoav Freund AT&T Labs 180 Park Avenue Florham Park NJ 092 USA October 2 2000 Abstract We propose a new boosting algorithm This boosting algorithm
Bayesian Co-Training
 Bayesian Co-Training Shipeng Yu, Balai Krishnapuram, Rómer Rosales, Harald Steck, R. Bharat Rao CAD & Knowledge Solutions, Siemens Medical Solutions USA, Inc. firstname.lastname@siemens.com Abstract We
Bayesian Co-Training Shipeng Yu, Balai Krishnapuram, Rómer Rosales, Harald Steck, R. Bharat Rao CAD & Knowledge Solutions, Siemens Medical Solutions USA, Inc. firstname.lastname@siemens.com Abstract We
Logistic regression and linear classifiers COMS 4771
 Logistic regression and linear classifiers COMS 4771 1. Prediction functions (again) Learning prediction functions IID model for supervised learning: (X 1, Y 1),..., (X n, Y n), (X, Y ) are iid random
Logistic regression and linear classifiers COMS 4771 1. Prediction functions (again) Learning prediction functions IID model for supervised learning: (X 1, Y 1),..., (X n, Y n), (X, Y ) are iid random
The Perceptron algorithm
 The Perceptron algorithm Tirgul 3 November 2016 Agnostic PAC Learnability A hypothesis class H is agnostic PAC learnable if there exists a function m H : 0,1 2 N and a learning algorithm with the following
The Perceptron algorithm Tirgul 3 November 2016 Agnostic PAC Learnability A hypothesis class H is agnostic PAC learnable if there exists a function m H : 0,1 2 N and a learning algorithm with the following
Part of the slides are adapted from Ziko Kolter
 Part of the slides are adapted from Ziko Kolter OUTLINE 1 Supervised learning: classification........................................................ 2 2 Non-linear regression/classification, overfitting,
Part of the slides are adapted from Ziko Kolter OUTLINE 1 Supervised learning: classification........................................................ 2 2 Non-linear regression/classification, overfitting,
Tuning as Linear Regression
 Tuning as Linear Regression Marzieh Bazrafshan, Tagyoung Chung and Daniel Gildea Department of Computer Science University of Rochester Rochester, NY 14627 Abstract We propose a tuning method for statistical
Tuning as Linear Regression Marzieh Bazrafshan, Tagyoung Chung and Daniel Gildea Department of Computer Science University of Rochester Rochester, NY 14627 Abstract We propose a tuning method for statistical
PAC Learning. prof. dr Arno Siebes. Algorithmic Data Analysis Group Department of Information and Computing Sciences Universiteit Utrecht
 PAC Learning prof. dr Arno Siebes Algorithmic Data Analysis Group Department of Information and Computing Sciences Universiteit Utrecht Recall: PAC Learning (Version 1) A hypothesis class H is PAC learnable
PAC Learning prof. dr Arno Siebes Algorithmic Data Analysis Group Department of Information and Computing Sciences Universiteit Utrecht Recall: PAC Learning (Version 1) A hypothesis class H is PAC learnable
Learning From Crowds. Presented by: Bei Peng 03/24/15
 Learning From Crowds Presented by: Bei Peng 03/24/15 1 Supervised Learning Given labeled training data, learn to generalize well on unseen data Binary classification ( ) Multi-class classification ( y
Learning From Crowds Presented by: Bei Peng 03/24/15 1 Supervised Learning Given labeled training data, learn to generalize well on unseen data Binary classification ( ) Multi-class classification ( y
MIRA, SVM, k-nn. Lirong Xia
 MIRA, SVM, k-nn Lirong Xia Linear Classifiers (perceptrons) Inputs are feature values Each feature has a weight Sum is the activation activation w If the activation is: Positive: output +1 Negative, output
MIRA, SVM, k-nn Lirong Xia Linear Classifiers (perceptrons) Inputs are feature values Each feature has a weight Sum is the activation activation w If the activation is: Positive: output +1 Negative, output
Lecture 25 of 42. PAC Learning, VC Dimension, and Mistake Bounds
 Lecture 25 of 42 PAC Learning, VC Dimension, and Mistake Bounds Thursday, 15 March 2007 William H. Hsu, KSU http://www.kddresearch.org/courses/spring2007/cis732 Readings: Sections 7.4.17.4.3, 7.5.17.5.3,
Lecture 25 of 42 PAC Learning, VC Dimension, and Mistake Bounds Thursday, 15 March 2007 William H. Hsu, KSU http://www.kddresearch.org/courses/spring2007/cis732 Readings: Sections 7.4.17.4.3, 7.5.17.5.3,
Ensemble Methods. NLP ML Web! Fall 2013! Andrew Rosenberg! TA/Grader: David Guy Brizan
 Ensemble Methods NLP ML Web! Fall 2013! Andrew Rosenberg! TA/Grader: David Guy Brizan How do you make a decision? What do you want for lunch today?! What did you have last night?! What are your favorite
Ensemble Methods NLP ML Web! Fall 2013! Andrew Rosenberg! TA/Grader: David Guy Brizan How do you make a decision? What do you want for lunch today?! What did you have last night?! What are your favorite
CMSC 451: Lecture 7 Greedy Algorithms for Scheduling Tuesday, Sep 19, 2017
 CMSC CMSC : Lecture Greedy Algorithms for Scheduling Tuesday, Sep 9, 0 Reading: Sects.. and. of KT. (Not covered in DPV.) Interval Scheduling: We continue our discussion of greedy algorithms with a number
CMSC CMSC : Lecture Greedy Algorithms for Scheduling Tuesday, Sep 9, 0 Reading: Sects.. and. of KT. (Not covered in DPV.) Interval Scheduling: We continue our discussion of greedy algorithms with a number
Computational Learning Theory. Definitions
 Computational Learning Theory Computational learning theory is interested in theoretical analyses of the following issues. What is needed to learn effectively? Sample complexity. How many examples? Computational
Computational Learning Theory Computational learning theory is interested in theoretical analyses of the following issues. What is needed to learn effectively? Sample complexity. How many examples? Computational
Data Mining: Concepts and Techniques. (3 rd ed.) Chapter 8. Chapter 8. Classification: Basic Concepts
 Data Mining: Concepts and Techniques (3 rd ed.) Chapter 8 1 Chapter 8. Classification: Basic Concepts Classification: Basic Concepts Decision Tree Induction Bayes Classification Methods Rule-Based Classification
Data Mining: Concepts and Techniques (3 rd ed.) Chapter 8 1 Chapter 8. Classification: Basic Concepts Classification: Basic Concepts Decision Tree Induction Bayes Classification Methods Rule-Based Classification
10-810: Advanced Algorithms and Models for Computational Biology. Optimal leaf ordering and classification
 10-810: Advanced Algorithms and Models for Computational Biology Optimal leaf ordering and classification Hierarchical clustering As we mentioned, its one of the most popular methods for clustering gene
10-810: Advanced Algorithms and Models for Computational Biology Optimal leaf ordering and classification Hierarchical clustering As we mentioned, its one of the most popular methods for clustering gene
Computational and Statistical Learning theory
 Computational and Statistical Learning theory Problem set 2 Due: January 31st Email solutions to : karthik at ttic dot edu Notation : Input space : X Label space : Y = {±1} Sample : (x 1, y 1,..., (x n,
Computational and Statistical Learning theory Problem set 2 Due: January 31st Email solutions to : karthik at ttic dot edu Notation : Input space : X Label space : Y = {±1} Sample : (x 1, y 1,..., (x n,
Lecture 3 Classification, Logistic Regression
 Lecture 3 Classification, Logistic Regression Fredrik Lindsten Division of Systems and Control Department of Information Technology Uppsala University. Email: fredrik.lindsten@it.uu.se F. Lindsten Summary
Lecture 3 Classification, Logistic Regression Fredrik Lindsten Division of Systems and Control Department of Information Technology Uppsala University. Email: fredrik.lindsten@it.uu.se F. Lindsten Summary
A Course in Machine Learning
 A Course in Machine Learning Hal Daumé III 10 LEARNING THEORY For nothing ought to be posited without a reason given, unless it is self-evident or known by experience or proved by the authority of Sacred
A Course in Machine Learning Hal Daumé III 10 LEARNING THEORY For nothing ought to be posited without a reason given, unless it is self-evident or known by experience or proved by the authority of Sacred
CSE 546 Final Exam, Autumn 2013
 CSE 546 Final Exam, Autumn 0. Personal info: Name: Student ID: E-mail address:. There should be 5 numbered pages in this exam (including this cover sheet).. You can use any material you brought: any book,
CSE 546 Final Exam, Autumn 0. Personal info: Name: Student ID: E-mail address:. There should be 5 numbered pages in this exam (including this cover sheet).. You can use any material you brought: any book,
COMS F18 Homework 3 (due October 29, 2018)
 COMS 477-2 F8 Homework 3 (due October 29, 208) Instructions Submit your write-up on Gradescope as a neatly typeset (not scanned nor handwritten) PDF document by :59 PM of the due date. On Gradescope, be
COMS 477-2 F8 Homework 3 (due October 29, 208) Instructions Submit your write-up on Gradescope as a neatly typeset (not scanned nor handwritten) PDF document by :59 PM of the due date. On Gradescope, be
Final Exam. December 11 th, This exam booklet contains five problems, out of which you are expected to answer four problems of your choice.
 CS446: Machine Learning Fall 2012 Final Exam December 11 th, 2012 This is a closed book exam. Everything you need in order to solve the problems is supplied in the body of this exam. Note that there is
CS446: Machine Learning Fall 2012 Final Exam December 11 th, 2012 This is a closed book exam. Everything you need in order to solve the problems is supplied in the body of this exam. Note that there is
IEOR E4703: Monte-Carlo Simulation
 IEOR E4703: Monte-Carlo Simulation Output Analysis for Monte-Carlo Martin Haugh Department of Industrial Engineering and Operations Research Columbia University Email: martin.b.haugh@gmail.com Output Analysis
IEOR E4703: Monte-Carlo Simulation Output Analysis for Monte-Carlo Martin Haugh Department of Industrial Engineering and Operations Research Columbia University Email: martin.b.haugh@gmail.com Output Analysis
Introduction to Machine Learning
 Introduction to Machine Learning Machine Learning: Jordan Boyd-Graber University of Maryland SUPPORT VECTOR MACHINES Slides adapted from Tom Mitchell, Eric Xing, and Lauren Hannah Machine Learning: Jordan
Introduction to Machine Learning Machine Learning: Jordan Boyd-Graber University of Maryland SUPPORT VECTOR MACHINES Slides adapted from Tom Mitchell, Eric Xing, and Lauren Hannah Machine Learning: Jordan
Final Exam, Fall 2002
 15-781 Final Exam, Fall 22 1. Write your name and your andrew email address below. Name: Andrew ID: 2. There should be 17 pages in this exam (excluding this cover sheet). 3. If you need more room to work
15-781 Final Exam, Fall 22 1. Write your name and your andrew email address below. Name: Andrew ID: 2. There should be 17 pages in this exam (excluding this cover sheet). 3. If you need more room to work
Propositions and Proofs
 Chapter 2 Propositions and Proofs The goal of this chapter is to develop the two principal notions of logic, namely propositions and proofs There is no universal agreement about the proper foundations
Chapter 2 Propositions and Proofs The goal of this chapter is to develop the two principal notions of logic, namely propositions and proofs There is no universal agreement about the proper foundations
Modern Information Retrieval
 Modern Information Retrieval Chapter 8 Text Classification Introduction A Characterization of Text Classification Unsupervised Algorithms Supervised Algorithms Feature Selection or Dimensionality Reduction
Modern Information Retrieval Chapter 8 Text Classification Introduction A Characterization of Text Classification Unsupervised Algorithms Supervised Algorithms Feature Selection or Dimensionality Reduction
Pattern Recognition and Machine Learning. Learning and Evaluation of Pattern Recognition Processes
 Pattern Recognition and Machine Learning James L. Crowley ENSIMAG 3 - MMIS Fall Semester 2016 Lesson 1 5 October 2016 Learning and Evaluation of Pattern Recognition Processes Outline Notation...2 1. The
Pattern Recognition and Machine Learning James L. Crowley ENSIMAG 3 - MMIS Fall Semester 2016 Lesson 1 5 October 2016 Learning and Evaluation of Pattern Recognition Processes Outline Notation...2 1. The
6.867 Machine learning: lecture 2. Tommi S. Jaakkola MIT CSAIL
 6.867 Machine learning: lecture 2 Tommi S. Jaakkola MIT CSAIL tommi@csail.mit.edu Topics The learning problem hypothesis class, estimation algorithm loss and estimation criterion sampling, empirical and
6.867 Machine learning: lecture 2 Tommi S. Jaakkola MIT CSAIL tommi@csail.mit.edu Topics The learning problem hypothesis class, estimation algorithm loss and estimation criterion sampling, empirical and
Tree sets. Reinhard Diestel
 1 Tree sets Reinhard Diestel Abstract We study an abstract notion of tree structure which generalizes treedecompositions of graphs and matroids. Unlike tree-decompositions, which are too closely linked
1 Tree sets Reinhard Diestel Abstract We study an abstract notion of tree structure which generalizes treedecompositions of graphs and matroids. Unlike tree-decompositions, which are too closely linked
12. Structural Risk Minimization. ECE 830 & CS 761, Spring 2016
 12. Structural Risk Minimization ECE 830 & CS 761, Spring 2016 1 / 23 General setup for statistical learning theory We observe training examples {x i, y i } n i=1 x i = features X y i = labels / responses
12. Structural Risk Minimization ECE 830 & CS 761, Spring 2016 1 / 23 General setup for statistical learning theory We observe training examples {x i, y i } n i=1 x i = features X y i = labels / responses
Knowledge Discovery in Data: Overview. Naïve Bayesian Classification. .. Spring 2009 CSC 466: Knowledge Discovery from Data Alexander Dekhtyar..
 Spring 2009 CSC 466: Knowledge Discovery from Data Alexander Dekhtyar Knowledge Discovery in Data: Naïve Bayes Overview Naïve Bayes methodology refers to a probabilistic approach to information discovery
Spring 2009 CSC 466: Knowledge Discovery from Data Alexander Dekhtyar Knowledge Discovery in Data: Naïve Bayes Overview Naïve Bayes methodology refers to a probabilistic approach to information discovery
Machine Learning for NLP
 Machine Learning for NLP Linear Models Joakim Nivre Uppsala University Department of Linguistics and Philology Slides adapted from Ryan McDonald, Google Research Machine Learning for NLP 1(26) Outline
Machine Learning for NLP Linear Models Joakim Nivre Uppsala University Department of Linguistics and Philology Slides adapted from Ryan McDonald, Google Research Machine Learning for NLP 1(26) Outline
Boosting & Deep Learning
 Boosting & Deep Learning Ensemble Learning n So far learning methods that learn a single hypothesis, chosen form a hypothesis space that is used to make predictions n Ensemble learning à select a collection
Boosting & Deep Learning Ensemble Learning n So far learning methods that learn a single hypothesis, chosen form a hypothesis space that is used to make predictions n Ensemble learning à select a collection
Natural Language Processing (CSEP 517): Text Classification
 Natural Language Processing (CSEP 517): Text Classification Noah Smith c 2017 University of Washington nasmith@cs.washington.edu April 10, 2017 1 / 71 To-Do List Online quiz: due Sunday Read: Jurafsky
Natural Language Processing (CSEP 517): Text Classification Noah Smith c 2017 University of Washington nasmith@cs.washington.edu April 10, 2017 1 / 71 To-Do List Online quiz: due Sunday Read: Jurafsky
Binary Classification, Multi-label Classification and Ranking: A Decision-theoretic Approach
 Binary Classification, Multi-label Classification and Ranking: A Decision-theoretic Approach Krzysztof Dembczyński and Wojciech Kot lowski Intelligent Decision Support Systems Laboratory (IDSS) Poznań
Binary Classification, Multi-label Classification and Ranking: A Decision-theoretic Approach Krzysztof Dembczyński and Wojciech Kot lowski Intelligent Decision Support Systems Laboratory (IDSS) Poznań
Solving Classification Problems By Knowledge Sets
 Solving Classification Problems By Knowledge Sets Marcin Orchel a, a Department of Computer Science, AGH University of Science and Technology, Al. A. Mickiewicza 30, 30-059 Kraków, Poland Abstract We propose
Solving Classification Problems By Knowledge Sets Marcin Orchel a, a Department of Computer Science, AGH University of Science and Technology, Al. A. Mickiewicza 30, 30-059 Kraków, Poland Abstract We propose
The sample complexity of agnostic learning with deterministic labels
 The sample complexity of agnostic learning with deterministic labels Shai Ben-David Cheriton School of Computer Science University of Waterloo Waterloo, ON, N2L 3G CANADA shai@uwaterloo.ca Ruth Urner College
The sample complexity of agnostic learning with deterministic labels Shai Ben-David Cheriton School of Computer Science University of Waterloo Waterloo, ON, N2L 3G CANADA shai@uwaterloo.ca Ruth Urner College
CS446: Machine Learning Spring Problem Set 4
 CS446: Machine Learning Spring 2017 Problem Set 4 Handed Out: February 27 th, 2017 Due: March 11 th, 2017 Feel free to talk to other members of the class in doing the homework. I am more concerned that
CS446: Machine Learning Spring 2017 Problem Set 4 Handed Out: February 27 th, 2017 Due: March 11 th, 2017 Feel free to talk to other members of the class in doing the homework. I am more concerned that
I D I A P. Online Policy Adaptation for Ensemble Classifiers R E S E A R C H R E P O R T. Samy Bengio b. Christos Dimitrakakis a IDIAP RR 03-69
 R E S E A R C H R E P O R T Online Policy Adaptation for Ensemble Classifiers Christos Dimitrakakis a IDIAP RR 03-69 Samy Bengio b I D I A P December 2003 D a l l e M o l l e I n s t i t u t e for Perceptual
R E S E A R C H R E P O R T Online Policy Adaptation for Ensemble Classifiers Christos Dimitrakakis a IDIAP RR 03-69 Samy Bengio b I D I A P December 2003 D a l l e M o l l e I n s t i t u t e for Perceptual
Introduction to Machine Learning Spring 2018 Note 18
 CS 189 Introduction to Machine Learning Spring 2018 Note 18 1 Gaussian Discriminant Analysis Recall the idea of generative models: we classify an arbitrary datapoint x with the class label that maximizes
CS 189 Introduction to Machine Learning Spring 2018 Note 18 1 Gaussian Discriminant Analysis Recall the idea of generative models: we classify an arbitrary datapoint x with the class label that maximizes
Relationship between Least Squares Approximation and Maximum Likelihood Hypotheses
 Relationship between Least Squares Approximation and Maximum Likelihood Hypotheses Steven Bergner, Chris Demwell Lecture notes for Cmpt 882 Machine Learning February 19, 2004 Abstract In these notes, a
Relationship between Least Squares Approximation and Maximum Likelihood Hypotheses Steven Bergner, Chris Demwell Lecture notes for Cmpt 882 Machine Learning February 19, 2004 Abstract In these notes, a
Machine Learning : Support Vector Machines
 Machine Learning Support Vector Machines 05/01/2014 Machine Learning : Support Vector Machines Linear Classifiers (recap) A building block for almost all a mapping, a partitioning of the input space into
Machine Learning Support Vector Machines 05/01/2014 Machine Learning : Support Vector Machines Linear Classifiers (recap) A building block for almost all a mapping, a partitioning of the input space into
Selective Prediction. Binary classifications. Rong Zhou November 8, 2017
 Selective Prediction Binary classifications Rong Zhou November 8, 2017 Table of contents 1. What are selective classifiers? 2. The Realizable Setting 3. The Noisy Setting 1 What are selective classifiers?
Selective Prediction Binary classifications Rong Zhou November 8, 2017 Table of contents 1. What are selective classifiers? 2. The Realizable Setting 3. The Noisy Setting 1 What are selective classifiers?
Computational Learning Theory
 09s1: COMP9417 Machine Learning and Data Mining Computational Learning Theory May 20, 2009 Acknowledgement: Material derived from slides for the book Machine Learning, Tom M. Mitchell, McGraw-Hill, 1997
09s1: COMP9417 Machine Learning and Data Mining Computational Learning Theory May 20, 2009 Acknowledgement: Material derived from slides for the book Machine Learning, Tom M. Mitchell, McGraw-Hill, 1997
New bounds on the price of bandit feedback for mistake-bounded online multiclass learning
 Journal of Machine Learning Research 1 8, 2017 Algorithmic Learning Theory 2017 New bounds on the price of bandit feedback for mistake-bounded online multiclass learning Philip M. Long Google, 1600 Amphitheatre
Journal of Machine Learning Research 1 8, 2017 Algorithmic Learning Theory 2017 New bounds on the price of bandit feedback for mistake-bounded online multiclass learning Philip M. Long Google, 1600 Amphitheatre
On the Problem of Error Propagation in Classifier Chains for Multi-Label Classification
 On the Problem of Error Propagation in Classifier Chains for Multi-Label Classification Robin Senge, Juan José del Coz and Eyke Hüllermeier Draft version of a paper to appear in: L. Schmidt-Thieme and
On the Problem of Error Propagation in Classifier Chains for Multi-Label Classification Robin Senge, Juan José del Coz and Eyke Hüllermeier Draft version of a paper to appear in: L. Schmidt-Thieme and
