Partitioning Metric Spaces
|
|
|
- Kevin Simmons
- 5 years ago
- Views:
Transcription
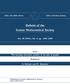
1 Partitioning Metric Spaces Computational and Metric Geometry Instructor: Yury Makarychev 1 Multiway Cut Problem 1.1 Preliminaries Definition 1.1. We are given a graph G = (V, E) and a set of terminals T = {s 1,..., s k } V. We need to partition the graph into k pieces P 1,..., P k such that s i P i. Our goal is to minimize the number of cut edges. When k =, Multiway Cut is just the minimum s t cut problem and can be solved in polynomial-time. However, when k 3 the problem is NP-hard. Exercise 1. Design a combinatorial -approximation algorithm for Multiway Cut. 1. Consider i {1,..., k}. Show how to find a minimum cut (S i, S i ) that separates s i and T \ {s i } (that is, a cut (S, S) such that s i S i and s j S i for j i).. Consider the following algorithm for the Multiway Cut problem. Find sets S 1,..., S k as described above. Remove all edges cut by cuts (S 1, S 1 ),..., (S k, S k ). We get a partition of G into a number of connected components. Let P i be the connected component that contains s i. If a connected component does not contain any terminals, merge it with an arbitrary set P i. Show that this algorithm gives approximation for the problem. We will see how to get a 3/ approximation using linear programming. Consider the following relaxation for the problem. For every vertex u, we introduce k LP variables ū 1,..., ū k and let ū = (ū 1,..., ū k ). Let = {x R d : x x k = 1, x 1 0,..., x k 0}; is a simplex with vertices e 1 = (1, 0,..., 0), e = (0, 1, 0,..., 0),..., e k = (0,..., 0, 1) (see Figure 1). We write the following linear program. minimize 1 ū v 1 subject to (u,v) E s i = e i for every i, ū for every i. 1
2 s 3 e 3 e 3 s 3 s 1 s e 1 e e 1 e s 1 s Figure 1: The figure shows (1) an input graph, () a feasible LP solution, (3) a random partitioning, and (4) the corresponding cut in the graph. Exercise. Show that this program is indeed a linear program. Hint: Introduce additional LP variables y uvi. Write y uvi ū i v i and y uvi v i ū i. Replace each term ū v 1 in the objective function with k y uvi. Show that the obtained program is equivalent to our original program. We denote the value of the optimal solution by OPT, and the value of LP by LP. Claim 1.. The LP is a relaxation of the problem. That is, LP OPT. Proof. Consider the optimal solution P 1,..., P k. Let ū = e i for u P i. Clearly, ū is a feasible LP solution. We compute the value of this solution. Consider an edge e = (u, v). Suppose that u P i and v P j. The contribution of e to the objective function is u v 1 = e i e j 1 = { 1, if i j, 0, if i = j. That is, the contribution of e is 1 if e is cut, and 0, otherwise. Thus the total contribution of all edges equals the number of cut edges. We get that the value of the LP solution ū is OPT. Therefore, LP OPT. 1. Rounding Scheme for k = It is instructive to first consider the case k =. Define d(u, v) = ū v 1 /. Let us choose r uniformly at random from (0, 1). Let P 1 = B r (s 1 ) and P = V \ P 1. Note that (P 1, P ) is a feasible solution to Multiway Cut: Since d(s 1, s 1 ) = 0 < r, we have s 1 B r (s 1 ) = P 1. Since d(s 1, s ) = 1 > r, we have s / B r (s 1 ) = P 1 and thus s P. Let us compute the expected number of cut edges. Consider an edge (u, v). Note that (u, v) is cut if and only if either u B r (s 1 ) and v / B r (s 1 ) or u / B r (s 1 ) and v B r (s 1 ). That is, if and only if d(u, s 1 ) r < d(v, s 1 ) or d(v, s 1 ) r < d(u, s 1 ), or equivalently min(d(u, s 1 ), d(v, s 1 )) r < max(d(u, s 1 ), d(v, s 1 )).
3 Since we sample r from a segment of length 1, the probability that is r [min(d(u, s 1 ), d(v, s 1 )), max(d(u, s 1 ), d(v, s 1 ))) max(d(u, s 1 ), d(v, s 1 ))) min(d(u, s 1 ), d(v, s 1 )) = d(u, s 1 ) d(v, s 1 ) d(u, v). By the linearity of expectation, we get that the expected number of cut edges is at most d(u, v) = LP. e E Pr (e is cut) e E We showed that we get a solution of value at most OPT in expectation Rounding Scheme Now we consider the general case when k 3. We need to partition the graph into k pieces. Let us try to generalize the approach we used for k =. We again choose a random radius, and consider balls B r (s 1 ),..., B r (s k ). Note that now these balls are not necessarily disjoint: the distance between every s i and s j is 1 and so balls B r (s i ) and B r (s j ) might intersect if r > 1/. In general, {B r (s 1 ),..., B r (s k )} is not a partition of V. Exercise 3. One way to deal with this problem is to sample r uniformly at random from (0, 1/). Then sets P 1 = B r (s 1 ),..., P k 1 = B r (s k 1 ), and P k = V \ (P 1... P k 1 ) are disjoint and define a valid partition of V. Show that the expected cost of this partition is at most LP. We resolve this problem as follows. We choose a random permutation π of {1,..., k} and process terminals according to the order defined by π: s π(1), s π(),..., s π(k 1). When we process terminal s i, we add to P i those vertices in B r (s i ) that were not added previously to any set P j. We present the algorithm in Figure. Claim 1.3. The algorithm returns a feasible solution. Proof. The claim follows from the fact that s i B r (s i ) and s i / B r (s j ) for every j i. Now we compute the expected cost of the solution. Consider an edge e = (u, v). Note that Let d(u, s i ) = u e i = (1 ū i) + j i ūj = (1 ū i) + (1 ū i ) A i = min(d(u, s i ), d(v, s i )) and B i = max(d(u, s i ), d(v, s i )). = 1 ū i. 1 In fact, we always get an optimal solution, since we never get a solution better than an optimal solution (there is no such solution), and thus we cannot get a solution which is worse than an optimal if we did the expected value would be worse than OPT. 3
4 Approximation Algorithm for Multiway Cut Input: graph G = (V, E) and a set of terminals T = {s 1,..., s k } V. Output: a partition P 1,..., P k of V such that s i P i. solve the LP relaxation for Multiway Cut. Define d(u, v) = 1 ū v 1. choose a random permutation π of {1,..., k} choose r uniformly at random from (0, 1) let A = for i = π(1), π(),..., π(k 1) do let P i = B r (s i ) \ A let A = A P i let P π(k) = V \ A return partition P 1,..., P k Figure : Approximation algorithm for Multiway Cut We have, B i A i = d(u, s i ) d(v, s i ) = ū i v i. We may assume without loss of generality that A 1 A A k. (1) Let us write i j if π 1 (i) < π 1 (j) (i precedes j in the order defined by π). We say that an index i settles the edge (u, v) if i is the first index w.r.t. π such that u B r (s i ), or v B r (s i ) (or both). In other words, index i settles edge e if A i r and A j > r for all j i. Let E i be the event that i settles (u, v). Note that at most one of the events E i happens. (If no event P i happens than u and v belong to P π(k), and the edge (u, v) is not cut.) When the event E i happens, we add either one or both of the vertices u and v to P i. Note that in the former case, the edge (u, v) is cut since u P i and v / P i ; in the latter case, the edge (u, v) is not cut since u, v P i. We conclude that Pr (e is cut) = Pr (E i and {u, v} B r (s i ) = 1) = Pr (E i and A i r < B i ). We are going to show now that Pr (E i r) 1/ for every i > 1. Consider the event L i that i 1. Event L i happens with probability 1/. We claim that when L i happens E i does not happen and therefore Pr (E i r) 1 Pr (L i r) = 1. Assume to the contrary that both events happen. Then 4
5 r A i and r < A j for every j i, and 1 i, therefore, r A i and r < A 1, and A i < A 1, which contradicts to our assumption (1). We have, Pr (e is cut) = Pr (E i and A i r < B i ) = (B 1 A 1 ) + = ū 1 v 1 + i= B i A i ū i v i E r [Pr (E i r) Pr (A i r < B i r)] = B 1 A 1 + B i A i = ū 1 v 1 + ū v 1. Observe that u v 1 u 1 v 1 + u i i= v i = u 1 v 1 + (1 u 1 ) (1 v 1 ) = u 1 v 1. i= Thus Pr (e is cut) 3 ū v 1 /4. By the linearity of expectation, the expected number of cut edges is at most 3 4 ū v 1 = 3 LP 3 OPT. (u,v) E We proved that our algorithm gives a 3/ approximation. Remark 1.4. Our analysis showed that we find a solution of expected cost 3OPT. Note that this implies that for every ε > 0 with probability at least ε we find a solution of cost at most 3OPT (by Markov s inequality). Hence by running the algorithm polynomially many times (1 ε) and returning the best solution, we can find a solution of cost at most ( ) OPT p(n) with high probability for every fixed polynomial p(n). The results presented in this section are due to Calinescu, Karloff, and Rabani. Multicut Problem Definition.1. We are given a graph G = (V, E) and a set of source-terminal pairs {(s 1, t 1 ),..., (s k, t k )}. We need to cut the graph into pieces such that each (s i, t i ) pair is separated. Our objective is to minimize the number of cut edges. 5
6 We use the following LP relaxation for Multicut. minimize d(u, v) subject to (u,v) E d(s i, t i ) = 1 for every i d(, ) is a semi-metric on V. Question 1. Why do not we write an l 1 -relaxation similar to the relaxation for Multiway Cut? Answer: We do not know which terminals are separated and which terminals are not separated. Say, we cannot require that s i = e i and s j = e j since s i and s j possibly lie in one piece of the optimal cut; similarly, we cannot require that s i = e k and s j = e k since s i and s j possibly lie in different pieces of the cut. Finally, we cannot just require that s i t i 1 = 1 since this constraint is not a linear constraint. Let P be the optimal solution. Denote the piece that u belongs to by P(u). The intended LP solution corresponding to P is { 1, if P(u) P(v), d(u, v) = 0, otherwise. Solution d(, ) is a feasible LP solution since (1) P(s i ) P(t i ) and so d(s i, t i ) = 1 and () d(, ) is a semi-metric. Therefore, LP OPT. Consider the following algorithm for the problem. Approximation Algorithm for Multicut Input: graph G = (V, E) and a set of source-terminal pairs {(s 1, t 1 ),..., (s k, t k )}. Output: a partition P of V such that each pair (s i, t i ) is separated by P. solve the LP relaxation for Multicut choose a random permutation π of {1,..., k} choose r uniformly at random from (0, 1/) let A = for i = π(1), π(),..., π(k) do let P i = B r (s i ) \ A let A = A P i let P k+1 = V \ A return partition {P i } //some sets in the partition may be empty The algorithm is very similar to the algorithm for Multiway Cut. Essentially, the only difference is that we choose r uniformly at random from (0, 1/) rather than from (0, 1). Note that vertex s i does not necessarily lies in P i ; it might lie in some P j for j i. 6
7 Lemma.. The algorithm always finds a feasible solution. Proof. We need to prove that s i and t i belong to different pieces of the cut for every i. Let P j = P(s i ) be the piece s i belongs to. Note that either j = i or j i. In particular, j k + 1. For every u, v P j, d(u, v) d(u, s j ) + d(s j, v) r < 1. Since d(s i, t i ) = 1, terminal t i cannot belong to P j. We now prove that the algorithm gives O(log k) approximation. Lemma.3. Partition P cuts at most O(log k OPT) edges in expectation. Proof. Consider an edge e = (u, v). Define A i = min(d(u, s i ), d(v, s i )) and B i = max(d(u, s i ), d(v, s i )). Assume without loss of generality that A 1 A A k. We say that an index i settles (u, v) if i is the first index w.r.t. π such that u B r (s i ) or v B r (s i ) or both; i.e., index i settles edge e if A i r and A j > r for all j i. Let E i be the event that i settles (u, v). Note that at most one of the events E i happens. We have, Pr (e is cut) = Pr (E i and A i r < B i ). We prove that Pr (E i r) 1/i. Consider the set I = {j : A i r}. This set depends only on r and not on the permutation π. Note that the first index in I w.r.t. π settles (u, v). Each element of I is the first index w.r.t. π with the same probability 1/ I. If i I then also 1,..., i 1 I since A 1 A i 1 A i. Therefore, Pr (E i r) 1 i Pr (i I) + 0 Pr (i / I) 1/i. We have, Pr (e is cut) Pr (A i r < B i ) i d(u, v) i = O(log k) d(u, v). We conclude that the expected number of cut edges is O(log k) d(u, v) O(log k) LP O(log k) OPT. (u,v) E The first O(log n) approximation algorithm for Multicut was designed by Garg, Vazirani, and Yannakakis. The algorithm presented in this section is due to Calinescu, Karloff, and Rabani. 7
8 3 Padded Decomposition I We have successfully used essentially the same algorithm to solve two different problems. In this section, we again use this algorithm; this time we apply it to an arbitrary metric space (X, d) on n points and get a padded bounded stochastic decomposition of X. Definition 3.1. Let (X, d) be a metric space on n points. An (α, ) padded decomposition of X is a probabilistic distribution of partitions P of X such that The diameter of each cluster C P is at most, d(u, v) for every u, v C. The probability that u and v are separated is at most α d(u, v)/. Remark 3.. Some authors call this decomposition an α separating -bounded stochastic decomposition of X and call the decomposition that we define later in Theorem 5.1 a padded -bounded stochastic decomposition. Padded Decomposition Input: a finite metric space (X, d) and a parameter. Output: a (O(log X ), ) padded decomposition P of X. choose a random ordering π : {1,..., n} X of X choose r uniformly at random from (0, /) let A = for i = 1,..., n do let C i = B r (π(i)) \ A let A = A C i return partition P = {C i } //some clusters in the partition may be empty Alternatively, we can formulate the algorithm as follows. We choose a random threshold r (0, /) and random ordering π on X. For each point u, consider the ball B r (u), find the first vertex in B r (u) w.r.t. to the order defined by π, i = min{j : π(j) B r (u)}, and assign u to C i (see the right diagram in Figure 3). It is immediate that every set in partition has diameter at most. The same argument as we used to prove that our algorithm for Multicut gives an O(log k) approximation shows that the probability that u and v are separated is at most α d(u, v)/ where α = O(log n). We proved he following theorem. Theorem 3.3. For every metric space (X, d) and every > 0, there is an (O(log n), ) padded decomposition of X (where n = X ). Moreover, there is a polynomial time randomized algorithm that finds a (O(log n), ) padded decomposition. 8
9 Figure 3: Padded Decomposition. Vertices are listed w.r.t. random ordering π. The left diagram shows how the algorithm works. The right diagram shows that each vertex u is assigned to the cluster C i with i = min{j : π(j) B r (u)}. For example, the ball around vertex 5 consists of vertices 3, 5 and 7; thus vertex 5 is assigned to the cluster C 3. 4 Hierarchically Well-Separated Trees Let T be a tree on V with positive edge lengths. Recall that the tree metric d T (, ) is the shortest metric on T. Tree metrics are much simpler than general metrics, and many problems that cannot be solved on arbitrary metrics can be solved on tree metrics. This observation leads to a natural question, can an arbitrary metric be well-approximated with a tree metric? An arbitrary metric may be very far from being a tree metric, but as we will show every metric can be approximated with a distribution of tree metrics. Definition 4.1. Let us say that a metric space (X, d) embeds into a distribution of (dominating) trees with distortion α if there is a probabilistic distribution of tree metrics d T on X X such that for every u, v X: d(u, v) d T (u, v) and E T [d T (u, v)] αd(u, v). Question. We showed that every metric space embeds into a distribution of cut metrics with distortion O(log n). Every cut metric trivially is a tree metric. Is an embedding in a distribution of cuts an embedding into a distribution of dominating trees? Why? We show that every metric space embeds into a distribution of trees. Theorem 4.. Let (X, d) be a metric space on n points. Assume that d(u, v) 1 for every u, v V. Let 0 = diam(x) = max u,v X d(u, v) be the diameter of X. Then there is an embedding of X into a distribution of dominating trees with distortion O(log n (log 0 + 1)) Proof. We find a padded decomposition P 1 of X with = 0 /, then find a subpartition of each cluster of P 1 with = 0 /4 and so on. At level i + 1 of recursion, we partition each cluster obtained at level i with paramter = 0 / i+1. We recurse until / i < 1. We obtain a hierarchical decomposition of X. Consider the corresponding decomposition tree T : 9
10 level 0 level 1 clusters level clusters points of X X C C C C... C k 0 / 0 /4 0 /8. Figure 4: Hierarchically Well-Separated Tree There is a vertex in T for each cluster in the hierarchical decomposition (including the top level cluster X); we denote the vertex for C by v C. The tree is rooted at v X. v A is a child of v B if A is a cluster in the partition of B. The level level(v C ) of a vertex v C is the depth of v C in the tree (the number of edges on the path from the root to v C ); the level of cluster C is level(v C ). All edges between vertices at levels i and i + 1 have length 0 / i+1. We identify leaf vertices with elements of X. Specifically, for each leaf vertex v C, we have diam(c) < 1 and thus C contains a single point. We identify v C with the single element of C. It may happen that a partitioning of some cluster C is trivial: the only sub-cluster of C is C. In this case, we keep two vertices v C (one is at level i; the other is at level i + 1). Formally, we use procedure FindHST(X, 0 /), presented in Figure 4, to find T. Let us say that two vertices u and v are separated at level i, if u and v lie in the same cluster at level i 1 but in different clusters at level i + 1. Claim 4.3. T is a dominating tree; that is, d T (u, v) d(u, v) for every u, v X. Proof. Let u, v X. Suppose that u and v are separated at level i. Then both u and v lie in one cluster C at level i 1, but lie in different clusters, A and B, at level i. Then d T (u, v) d T (v A, v B ) = d T (v A, v C ) + d T (v B, v C ) = 0 / i diam(c) d(u, v). Claim 4.4. E T [d T (u, v)] O(α (h + 1)), where α = O(log n) and h = log 0 is the depth of T. 10
11 procedure FindHST(Y, ) Input: a finite metric space (Y, d) and a parameter. Output: a rooted dominating tree T on Y Y ; points of Y are leaves of T. if < 1 return a tree on the single vertex of Y find a random (α, ) padded decomposition P of Y. for each cluster C in P T C = FindHST(C, /) create a new vertex v Y let v Y be the root of T connect v Y with roots v C of trees T C by edges of length return the obtained tree T Figure 5: Procedure FindHST(Y, ) generates a random dominating tree for Y. Proof. The probability that u and v are separated at level i is at most α d(u,v) 0 / i = i α/ 0. If u and v are separated at level i, the distance between them is h 0 / j = O( 0 / i ). j=i Thus the expected distance between u and v in T is at most h ( ( 0 / i ) (α i d(u, v)/ 0 ) ) ( h ) = O αd(u, v) = O (α (h + 1) d(u, v)). i=0 This concludes the proof of Theorem 4.. We obtained an embedding into distribution of dominating trees with distortion i=0 O(log n(log 0 + 1)). Note that every tree in the distribution satisfies the following properties: points of X are leaves of the tree, all leaves are at the same level, all edges between levels i and i + 1 have the same length (for a given i). We call a tree that satisfies these properties a hierarchically well-separated tree (HST). Results presented in this section are due to Bartal. 11
12 5 Padded Decomposition II Our bound on the distortion depends on the depth of the decomposition tree. That happens because we first show that each level contributes at most αd(u, v) and then add up contributions of all h + 1 levels. We now show how to improve the distortion to O(log n). To this end, we get a padded decomposition with stronger guarantees. Theorem 5.1. Let (X, d) be a metric space on n points, and > 0. There is a probabilistic distribution of partitions P of X that satisfies the following properties. Each cluster C in P has diameter at most. For every x X and ρ > 0, where α(x) = O(log B (x) B /8 (x) ). Pr (B ρ (x) P(x)) α(x) ρ, Remark 5.. The decomposition P is an (α, ) padded decomposition. Indeed for every x and y, Pr (P(x) P(x)) = Pr (y / P(x)) Pr ( B d(x,y) (x) P ) (x) α(x)d(x, y)/, where α(x) = O(log B(x, ) ) = O(log n). B(x, /8) Proof. We slightly change the algorithm that computes the padded decomposition. Padded Decomposition II Input: a finite metric space (X, d) and a parameter. Output: a padded decomposition P of X. choose a random ordering π : {1,..., n} X of X choose r uniformly at random from ( /4, /) let A = for i = 1,..., n do let C i = B r (π(i)) \ A let A = A C i return partition P = {C i } //some clusters in the partition may be empty The analysis of this algorithm is very similar to the one in Section 3. We may assume that ρ < /8 (as otherwise, our guarantee is trivial). Consider a point x. Sort vertices of X by their distance to x; denote them by u 1,..., u n. Let A i = d(u i, x) ρ and B i = d(u i, x) + ρ for every i {1,..., n}. Then A 1 A A n and B 1 B B n. 1
13 If x B r (u i ) but B ρ (x) B r (u i ), then r [A i, B i ). Let E i be the event that i is the first index w.r.t. π such that r A i. Note that if E i and r B i then B ρ (x) P(x). Indeed, on one hand no vertex of B ρ (x) belongs to P(u j ) for j i because r < A j ; on the other hand, B ρ (x) B r (u i ) since B i r. Thus Pr (B ρ (u) P(x)) n Pr (E i and A i r < B i ). Note that Pr (E i r) 1/i and Pr (A i r < B i ) B i A i /4 = 8ρ/. Moreover, if / < A i then r < A i and thus E i cannot happen. Therefore, if i > B (x) then i / B (x) (since all vertices u i are sorted according to their distance to x) and hence A i = d(u i, x) ρ ρ > /, and hence Pr (E i ) = 0. Additionally, if /4 > B i then r > B i and Pr (A i r < B i ) = 0. Therefore, if i B /8 (x) then i B /8 (x) and B i = d(x, u i ) + ρ /8 + ρ < /4 and hence Pr (A i r < B i ) = 0. We conclude that Pr (B ρ (u) P(x)) B (x) i= B /8 (x) 1 i 8ρ ( = O log B (x) B /8 (x) ρ ). We use this decomposition to construct a distribution of HSTs. We get that the probability that u and v are separated at level i is at most ( O log B ) (u) B /8 (u) d(u, v) i. 0 If u and v are separated at level i, the distance between them is O( 0 / i ). Thus the expected distance between u and v is at most O(1) h i=0 log B (u) d(u, v) d(u, v) = O(log n). B /8 (u) 0 0 Remark 5.3. Give another proof of Bourgain s theorem using embeddings into distributions of dominating trees. Prove a lower bound of Ω(log n) on the distortion of embeddings into distributions of trees. The results presented in this section are due to Fakcharoenphol, Rao and Talwar. 13
14 6 k-median There are many applications of padded decompositions and HSTs in theoretical computer science. We will not have time to discuss these applications in detail. We show below only one application of HSTs to demonstrate the general approach. Definition 6.1. We are given a metric space (X, d). The k-median problem is to find a set S of k points in X so as to minimize u X d(u, S). The problem can be solved exactly on tree metrics using dynamic-programming. Exercise 4. Design a polynomial-time algorithm that solves the problem on trees. Consider an instance of the k-median problem. Let S be its optimal solution Compute an embedding of X in a distribution of dominating trees T with distortion α = O(log n). Exercise 5. Show that we may assume that T is a tree on X. Compute an optimal solution S for k-median on (X, d T ). We always have, d T (u, S ). u X d(u, S ) u X d T (u, S ) u X We also have, ] E T [ u X d T (u, S ) α u X d(u, S ) = α OPT. Therefore, S is an α approximate solution in expectation. Remark 6.. This algorithm is due to Bartal. It was the first approximation algorithm for k-median. Later Charikar, Guha, Tardos, and Shmoys gave a constant factor approximation algorithm for the problem. The best currently known algorithm for the problem is due to Li and Svensson. 14
Cuts & Metrics: Multiway Cut
 Cuts & Metrics: Multiway Cut Barna Saha April 21, 2015 Cuts and Metrics Multiway Cut Probabilistic Approximation of Metrics by Tree Metric Cuts & Metrics Metric Space: A metric (V, d) on a set of vertices
Cuts & Metrics: Multiway Cut Barna Saha April 21, 2015 Cuts and Metrics Multiway Cut Probabilistic Approximation of Metrics by Tree Metric Cuts & Metrics Metric Space: A metric (V, d) on a set of vertices
An Improved Approximation Algorithm for Requirement Cut
 An Improved Approximation Algorithm for Requirement Cut Anupam Gupta Viswanath Nagarajan R. Ravi Abstract This note presents improved approximation guarantees for the requirement cut problem: given an
An Improved Approximation Algorithm for Requirement Cut Anupam Gupta Viswanath Nagarajan R. Ravi Abstract This note presents improved approximation guarantees for the requirement cut problem: given an
Finite Metric Spaces & Their Embeddings: Introduction and Basic Tools
 Finite Metric Spaces & Their Embeddings: Introduction and Basic Tools Manor Mendel, CMI, Caltech 1 Finite Metric Spaces Definition of (semi) metric. (M, ρ): M a (finite) set of points. ρ a distance function
Finite Metric Spaces & Their Embeddings: Introduction and Basic Tools Manor Mendel, CMI, Caltech 1 Finite Metric Spaces Definition of (semi) metric. (M, ρ): M a (finite) set of points. ρ a distance function
15-854: Approximation Algorithms Lecturer: Anupam Gupta Topic: Approximating Metrics by Tree Metrics Date: 10/19/2005 Scribe: Roy Liu
 15-854: Approximation Algorithms Lecturer: Anupam Gupta Topic: Approximating Metrics by Tree Metrics Date: 10/19/2005 Scribe: Roy Liu 121 Introduction In this lecture, we show how to embed metric weighted
15-854: Approximation Algorithms Lecturer: Anupam Gupta Topic: Approximating Metrics by Tree Metrics Date: 10/19/2005 Scribe: Roy Liu 121 Introduction In this lecture, we show how to embed metric weighted
arxiv:cs/ v1 [cs.cc] 7 Sep 2006
![arxiv:cs/ v1 [cs.cc] 7 Sep 2006 arxiv:cs/ v1 [cs.cc] 7 Sep 2006](/thumbs/76/74366214.jpg) Approximation Algorithms for the Bipartite Multi-cut problem arxiv:cs/0609031v1 [cs.cc] 7 Sep 2006 Sreyash Kenkre Sundar Vishwanathan Department Of Computer Science & Engineering, IIT Bombay, Powai-00076,
Approximation Algorithms for the Bipartite Multi-cut problem arxiv:cs/0609031v1 [cs.cc] 7 Sep 2006 Sreyash Kenkre Sundar Vishwanathan Department Of Computer Science & Engineering, IIT Bombay, Powai-00076,
Lecture 10: Bourgain s Theorem
 princeton u. sp 0 cos 598B: algorithms and complexity Lecture 10: Bourgain s Theorem Lecturer: Sanjeev Arora Scribe:Daniel J. Peng The goal of this week s lecture is to prove the l version of Bourgain
princeton u. sp 0 cos 598B: algorithms and complexity Lecture 10: Bourgain s Theorem Lecturer: Sanjeev Arora Scribe:Daniel J. Peng The goal of this week s lecture is to prove the l version of Bourgain
On Stochastic Decompositions of Metric Spaces
 On Stochastic Decompositions of Metric Spaces Scribe of a talk given at the fall school Metric Embeddings : Constructions and Obstructions. 3-7 November 204, Paris, France Ofer Neiman Abstract In this
On Stochastic Decompositions of Metric Spaces Scribe of a talk given at the fall school Metric Embeddings : Constructions and Obstructions. 3-7 November 204, Paris, France Ofer Neiman Abstract In this
Topic: Balanced Cut, Sparsest Cut, and Metric Embeddings Date: 3/21/2007
 CS880: Approximations Algorithms Scribe: Tom Watson Lecturer: Shuchi Chawla Topic: Balanced Cut, Sparsest Cut, and Metric Embeddings Date: 3/21/2007 In the last lecture, we described an O(log k log D)-approximation
CS880: Approximations Algorithms Scribe: Tom Watson Lecturer: Shuchi Chawla Topic: Balanced Cut, Sparsest Cut, and Metric Embeddings Date: 3/21/2007 In the last lecture, we described an O(log k log D)-approximation
Local Global Tradeoffs in Metric Embeddings
 Local Global Tradeoffs in Metric Embeddings Moses Charikar Konstantin Makarychev Yury Makarychev Preprint Abstract Suppose that every k points in a n point metric space X are D-distortion embeddable into
Local Global Tradeoffs in Metric Embeddings Moses Charikar Konstantin Makarychev Yury Makarychev Preprint Abstract Suppose that every k points in a n point metric space X are D-distortion embeddable into
16.1 Min-Cut as an LP
 600.469 / 600.669 Approximation Algorithms Lecturer: Michael Dinitz Topic: LPs as Metrics: Min Cut and Multiway Cut Date: 4//5 Scribe: Gabriel Kaptchuk 6. Min-Cut as an LP We recall the basic definition
600.469 / 600.669 Approximation Algorithms Lecturer: Michael Dinitz Topic: LPs as Metrics: Min Cut and Multiway Cut Date: 4//5 Scribe: Gabriel Kaptchuk 6. Min-Cut as an LP We recall the basic definition
arxiv: v1 [cs.ds] 20 Nov 2016
![arxiv: v1 [cs.ds] 20 Nov 2016 arxiv: v1 [cs.ds] 20 Nov 2016](/thumbs/85/91372723.jpg) Algorithmic and Hardness Results for the Hub Labeling Problem Haris Angelidakis 1, Yury Makarychev 1 and Vsevolod Oparin 2 1 Toyota Technological Institute at Chicago 2 Saint Petersburg Academic University
Algorithmic and Hardness Results for the Hub Labeling Problem Haris Angelidakis 1, Yury Makarychev 1 and Vsevolod Oparin 2 1 Toyota Technological Institute at Chicago 2 Saint Petersburg Academic University
Basic Properties of Metric and Normed Spaces
 Basic Properties of Metric and Normed Spaces Computational and Metric Geometry Instructor: Yury Makarychev The second part of this course is about metric geometry. We will study metric spaces, low distortion
Basic Properties of Metric and Normed Spaces Computational and Metric Geometry Instructor: Yury Makarychev The second part of this course is about metric geometry. We will study metric spaces, low distortion
Key words. sparsification, approximation algorithm, graph partitioning, routing, metric space
 VERTEX SPARSIFICATION AND OBLIVIOUS REDUCTIONS ANKUR MOITRA Abstract. Given an undirected, capacitated graph G = (V, E) and a set K V of terminals of size k, we construct an undirected, capacitated graph
VERTEX SPARSIFICATION AND OBLIVIOUS REDUCTIONS ANKUR MOITRA Abstract. Given an undirected, capacitated graph G = (V, E) and a set K V of terminals of size k, we construct an undirected, capacitated graph
Hardness of Embedding Metric Spaces of Equal Size
 Hardness of Embedding Metric Spaces of Equal Size Subhash Khot and Rishi Saket Georgia Institute of Technology {khot,saket}@cc.gatech.edu Abstract. We study the problem embedding an n-point metric space
Hardness of Embedding Metric Spaces of Equal Size Subhash Khot and Rishi Saket Georgia Institute of Technology {khot,saket}@cc.gatech.edu Abstract. We study the problem embedding an n-point metric space
Metric decomposition, smooth measures, and clustering
 Metric decomposition, smooth measures, and clustering James R. Lee U.C. Berkeley jrl@cs.berkeley.edu Assaf Naor Microsoft Research anaor@microsoft.com Abstract In recent years, randomized decompositions
Metric decomposition, smooth measures, and clustering James R. Lee U.C. Berkeley jrl@cs.berkeley.edu Assaf Naor Microsoft Research anaor@microsoft.com Abstract In recent years, randomized decompositions
Ramsey partitions and proximity data structures
 Ramsey partitions and proximity data structures Manor Mendel Assaf Naor Abstract This paper addresses two problems lying at the intersection of geometric analysis and theoretical computer science: The
Ramsey partitions and proximity data structures Manor Mendel Assaf Naor Abstract This paper addresses two problems lying at the intersection of geometric analysis and theoretical computer science: The
CMPUT 675: Approximation Algorithms Fall 2014
 CMPUT 675: Approximation Algorithms Fall 204 Lecture 25 (Nov 3 & 5): Group Steiner Tree Lecturer: Zachary Friggstad Scribe: Zachary Friggstad 25. Group Steiner Tree In this problem, we are given a graph
CMPUT 675: Approximation Algorithms Fall 204 Lecture 25 (Nov 3 & 5): Group Steiner Tree Lecturer: Zachary Friggstad Scribe: Zachary Friggstad 25. Group Steiner Tree In this problem, we are given a graph
25 Minimum bandwidth: Approximation via volume respecting embeddings
 25 Minimum bandwidth: Approximation via volume respecting embeddings We continue the study of Volume respecting embeddings. In the last lecture, we motivated the use of volume respecting embeddings by
25 Minimum bandwidth: Approximation via volume respecting embeddings We continue the study of Volume respecting embeddings. In the last lecture, we motivated the use of volume respecting embeddings by
Integer Linear Programs
 Lecture 2: Review, Linear Programming Relaxations Today we will talk about expressing combinatorial problems as mathematical programs, specifically Integer Linear Programs (ILPs). We then see what happens
Lecture 2: Review, Linear Programming Relaxations Today we will talk about expressing combinatorial problems as mathematical programs, specifically Integer Linear Programs (ILPs). We then see what happens
Ramsey partitions and proximity data structures
 Ramsey partitions and proximity data structures Manor Mendel The Open University of Israel Assaf Naor Microsoft Research Abstract This paper addresses two problems lying at the intersection of geometric
Ramsey partitions and proximity data structures Manor Mendel The Open University of Israel Assaf Naor Microsoft Research Abstract This paper addresses two problems lying at the intersection of geometric
Lecture 18: March 15
 CS71 Randomness & Computation Spring 018 Instructor: Alistair Sinclair Lecture 18: March 15 Disclaimer: These notes have not been subjected to the usual scrutiny accorded to formal publications. They may
CS71 Randomness & Computation Spring 018 Instructor: Alistair Sinclair Lecture 18: March 15 Disclaimer: These notes have not been subjected to the usual scrutiny accorded to formal publications. They may
Approximation Algorithms for Min-Sum k-clustering and Balanced k-median
 Approximation Algorithms for Min-Sum k-clustering and Balanced k-median Babak Behsaz Zachary Friggstad Mohammad R. Salavatipour Rohit Sivakumar Department of Computing Science University of Alberta Edmonton,
Approximation Algorithms for Min-Sum k-clustering and Balanced k-median Babak Behsaz Zachary Friggstad Mohammad R. Salavatipour Rohit Sivakumar Department of Computing Science University of Alberta Edmonton,
ORIE 6334 Spectral Graph Theory November 22, Lecture 25
 ORIE 64 Spectral Graph Theory November 22, 206 Lecture 25 Lecturer: David P. Williamson Scribe: Pu Yang In the remaining three lectures, we will cover a prominent result by Arora, Rao, and Vazirani for
ORIE 64 Spectral Graph Theory November 22, 206 Lecture 25 Lecturer: David P. Williamson Scribe: Pu Yang In the remaining three lectures, we will cover a prominent result by Arora, Rao, and Vazirani for
Topics in Theoretical Computer Science April 08, Lecture 8
 Topics in Theoretical Computer Science April 08, 204 Lecture 8 Lecturer: Ola Svensson Scribes: David Leydier and Samuel Grütter Introduction In this lecture we will introduce Linear Programming. It was
Topics in Theoretical Computer Science April 08, 204 Lecture 8 Lecturer: Ola Svensson Scribes: David Leydier and Samuel Grütter Introduction In this lecture we will introduce Linear Programming. It was
Algorithms, Geometry and Learning. Reading group Paris Syminelakis
 Algorithms, Geometry and Learning Reading group Paris Syminelakis October 11, 2016 2 Contents 1 Local Dimensionality Reduction 5 1 Introduction.................................... 5 2 Definitions and Results..............................
Algorithms, Geometry and Learning Reading group Paris Syminelakis October 11, 2016 2 Contents 1 Local Dimensionality Reduction 5 1 Introduction.................................... 5 2 Definitions and Results..............................
Hierarchical Clustering via Spreading Metrics
 Journal of Machine Learning Research 18 2017) 1-35 Submitted 2/17; Revised 5/17; Published 8/17 Hierarchical Clustering via Spreading Metrics Aurko Roy College of Computing Georgia Institute of Technology
Journal of Machine Learning Research 18 2017) 1-35 Submitted 2/17; Revised 5/17; Published 8/17 Hierarchical Clustering via Spreading Metrics Aurko Roy College of Computing Georgia Institute of Technology
The Steiner k-cut Problem
 The Steiner k-cut Problem Chandra Chekuri Sudipto Guha Joseph (Seffi) Naor September 23, 2005 Abstract We consider the Steiner k-cut problem which generalizes both the k-cut problem and the multiway cut
The Steiner k-cut Problem Chandra Chekuri Sudipto Guha Joseph (Seffi) Naor September 23, 2005 Abstract We consider the Steiner k-cut problem which generalizes both the k-cut problem and the multiway cut
Chapter 11. Approximation Algorithms. Slides by Kevin Wayne Pearson-Addison Wesley. All rights reserved.
 Chapter 11 Approximation Algorithms Slides by Kevin Wayne. Copyright @ 2005 Pearson-Addison Wesley. All rights reserved. 1 Approximation Algorithms Q. Suppose I need to solve an NP-hard problem. What should
Chapter 11 Approximation Algorithms Slides by Kevin Wayne. Copyright @ 2005 Pearson-Addison Wesley. All rights reserved. 1 Approximation Algorithms Q. Suppose I need to solve an NP-hard problem. What should
Algorithms for Stable and Perturbation-Resilient Problems
 Algorithms for Stable and Perturbation-Resilient Problems ABSTRACT Haris Angelidais TTIC Chicago, IL, USA We study the notion of stability and perturbation resilience introduced by Bilu and Linial 2010)
Algorithms for Stable and Perturbation-Resilient Problems ABSTRACT Haris Angelidais TTIC Chicago, IL, USA We study the notion of stability and perturbation resilience introduced by Bilu and Linial 2010)
Improving Christofides Algorithm for the s-t Path TSP
 Cornell University May 21, 2012 Joint work with Bobby Kleinberg and David Shmoys Metric TSP Metric (circuit) TSP Given a weighted graph G = (V, E) (c : E R + ), find a minimum Hamiltonian circuit Triangle
Cornell University May 21, 2012 Joint work with Bobby Kleinberg and David Shmoys Metric TSP Metric (circuit) TSP Given a weighted graph G = (V, E) (c : E R + ), find a minimum Hamiltonian circuit Triangle
Approximating Multicut and the Demand Graph
 Approximating Multicut and the Demand Graph Chandra Chekuri Vivek Madan November 2, 2016 Abstract In the minimum Multicut problem, the input is an edgeweighted supply graph G (V, E) and a demand graph
Approximating Multicut and the Demand Graph Chandra Chekuri Vivek Madan November 2, 2016 Abstract In the minimum Multicut problem, the input is an edgeweighted supply graph G (V, E) and a demand graph
arxiv: v4 [cs.ds] 28 Dec 2018
![arxiv: v4 [cs.ds] 28 Dec 2018 arxiv: v4 [cs.ds] 28 Dec 2018](/thumbs/92/110889366.jpg) k-center Clustering under Perturbation Resilience Maria-Florina Balcan Nika Haghtalab Colin White arxiv:1505.03924v4 [cs.ds] 28 Dec 2018 Abstract The k-center problem is a canonical and long-studied facility
k-center Clustering under Perturbation Resilience Maria-Florina Balcan Nika Haghtalab Colin White arxiv:1505.03924v4 [cs.ds] 28 Dec 2018 Abstract The k-center problem is a canonical and long-studied facility
An LP Formulation and Approximation Algorithms for the Metric Labeling Problem
 An LP Formulation and Approximation Algorithms for the Metric Labeling Problem C. Chekuri y S. Khanna z J. Naor x L. Zosin { August 4, 2004 Abstract We consider approximation algorithms for the metric
An LP Formulation and Approximation Algorithms for the Metric Labeling Problem C. Chekuri y S. Khanna z J. Naor x L. Zosin { August 4, 2004 Abstract We consider approximation algorithms for the metric
Lecture notes for Analysis of Algorithms : Markov decision processes
 Lecture notes for Analysis of Algorithms : Markov decision processes Lecturer: Thomas Dueholm Hansen June 6, 013 Abstract We give an introduction to infinite-horizon Markov decision processes (MDPs) with
Lecture notes for Analysis of Algorithms : Markov decision processes Lecturer: Thomas Dueholm Hansen June 6, 013 Abstract We give an introduction to infinite-horizon Markov decision processes (MDPs) with
Cographs; chordal graphs and tree decompositions
 Cographs; chordal graphs and tree decompositions Zdeněk Dvořák September 14, 2015 Let us now proceed with some more interesting graph classes closed on induced subgraphs. 1 Cographs The class of cographs
Cographs; chordal graphs and tree decompositions Zdeněk Dvořák September 14, 2015 Let us now proceed with some more interesting graph classes closed on induced subgraphs. 1 Cographs The class of cographs
Small distortion and volume preserving embedding for Planar and Euclidian metrics Satish Rao
 Small distortion and volume preserving embedding for Planar and Euclidian metrics Satish Rao presented by Fjóla Rún Björnsdóttir CSE 254 - Metric Embeddings Winter 2007 CSE 254 - Metric Embeddings - Winter
Small distortion and volume preserving embedding for Planar and Euclidian metrics Satish Rao presented by Fjóla Rún Björnsdóttir CSE 254 - Metric Embeddings Winter 2007 CSE 254 - Metric Embeddings - Winter
Fréchet embeddings of negative type metrics
 Fréchet embeddings of negative type metrics Sanjeev Arora James R Lee Assaf Naor Abstract We show that every n-point metric of negative type (in particular, every n-point subset of L 1 ) admits a Fréchet
Fréchet embeddings of negative type metrics Sanjeev Arora James R Lee Assaf Naor Abstract We show that every n-point metric of negative type (in particular, every n-point subset of L 1 ) admits a Fréchet
Algorithms for 2-Route Cut Problems
 Algorithms for 2-Route Cut Problems Chandra Chekuri 1 and Sanjeev Khanna 2 1 Dept. of Computer Science, University of Illinois, Urbana, IL 61801. chekuri@cs.uiuc.edu 2 Dept. of CIS, Univ. of Pennsylvania,
Algorithms for 2-Route Cut Problems Chandra Chekuri 1 and Sanjeev Khanna 2 1 Dept. of Computer Science, University of Illinois, Urbana, IL 61801. chekuri@cs.uiuc.edu 2 Dept. of CIS, Univ. of Pennsylvania,
SCALE-OBLIVIOUS METRIC FRAGMENTATION AND THE NONLINEAR DVORETZKY THEOREM
 SCALE-OBLIVIOUS METRIC FRAGMENTATION AN THE NONLINEAR VORETZKY THEOREM ASSAF NAOR AN TERENCE TAO Abstract. We introduce a randomized iterative fragmentation procedure for finite metric spaces, which is
SCALE-OBLIVIOUS METRIC FRAGMENTATION AN THE NONLINEAR VORETZKY THEOREM ASSAF NAOR AN TERENCE TAO Abstract. We introduce a randomized iterative fragmentation procedure for finite metric spaces, which is
Metric Approximations (Embeddings) M M 1 2 f M 1, M 2 metric spaces. f injective mapping from M 1 to M 2. M 2 dominates M 1 under f if d M1 (u; v) d M
 Approximating a nite metric by a small number of tree metrics Moses Charikar Chandra Chekuri Ashish Goel Sudipto Guha Serge Plotkin Metric Approximations (Embeddings) M M 1 2 f M 1, M 2 metric spaces.
Approximating a nite metric by a small number of tree metrics Moses Charikar Chandra Chekuri Ashish Goel Sudipto Guha Serge Plotkin Metric Approximations (Embeddings) M M 1 2 f M 1, M 2 metric spaces.
Partitioning Algorithms that Combine Spectral and Flow Methods
 CS369M: Algorithms for Modern Massive Data Set Analysis Lecture 15-11/11/2009 Partitioning Algorithms that Combine Spectral and Flow Methods Lecturer: Michael Mahoney Scribes: Kshipra Bhawalkar and Deyan
CS369M: Algorithms for Modern Massive Data Set Analysis Lecture 15-11/11/2009 Partitioning Algorithms that Combine Spectral and Flow Methods Lecturer: Michael Mahoney Scribes: Kshipra Bhawalkar and Deyan
Minmax Tree Cover in the Euclidean Space
 Journal of Graph Algorithms and Applications http://jgaa.info/ vol. 15, no. 3, pp. 345 371 (2011) Minmax Tree Cover in the Euclidean Space Seigo Karakawa 1 Ehab Morsy 1 Hiroshi Nagamochi 1 1 Department
Journal of Graph Algorithms and Applications http://jgaa.info/ vol. 15, no. 3, pp. 345 371 (2011) Minmax Tree Cover in the Euclidean Space Seigo Karakawa 1 Ehab Morsy 1 Hiroshi Nagamochi 1 1 Department
- Well-characterized problems, min-max relations, approximate certificates. - LP problems in the standard form, primal and dual linear programs
 LP-Duality ( Approximation Algorithms by V. Vazirani, Chapter 12) - Well-characterized problems, min-max relations, approximate certificates - LP problems in the standard form, primal and dual linear programs
LP-Duality ( Approximation Algorithms by V. Vazirani, Chapter 12) - Well-characterized problems, min-max relations, approximate certificates - LP problems in the standard form, primal and dual linear programs
A Polynomial-Time Approximation Scheme for Euclidean Steiner Forest
 A Polynomial-Time Approximation Scheme for Euclidean Steiner Forest Borradaile, G., Klein, P. N., & Mathieu, C. (25). A polynomial-time approximation scheme for Euclidean Steiner forest. ACM Transactions
A Polynomial-Time Approximation Scheme for Euclidean Steiner Forest Borradaile, G., Klein, P. N., & Mathieu, C. (25). A polynomial-time approximation scheme for Euclidean Steiner forest. ACM Transactions
Approximation Algorithms for Asymmetric TSP by Decomposing Directed Regular Multigraphs
 Approximation Algorithms for Asymmetric TSP by Decomposing Directed Regular Multigraphs Haim Kaplan Tel-Aviv University, Israel haimk@post.tau.ac.il Nira Shafrir Tel-Aviv University, Israel shafrirn@post.tau.ac.il
Approximation Algorithms for Asymmetric TSP by Decomposing Directed Regular Multigraphs Haim Kaplan Tel-Aviv University, Israel haimk@post.tau.ac.il Nira Shafrir Tel-Aviv University, Israel shafrirn@post.tau.ac.il
Approximation slides 1. Cut problems. The character flaw of of Michael Myers, Freddy Kruger and Jason Voorhees: Cut problems
 Approximation slides 1 Cut problems The character flaw of of Michael Myers, Freddy Kruger and Jason Voorhees: Cut problems Approximation slides 2 The directed multicut problem S j T j S 1 Figure 1: The
Approximation slides 1 Cut problems The character flaw of of Michael Myers, Freddy Kruger and Jason Voorhees: Cut problems Approximation slides 2 The directed multicut problem S j T j S 1 Figure 1: The
Bourgain s Theorem. Computational and Metric Geometry. Instructor: Yury Makarychev. d(s 1, s 2 ).
 Bourgain s Theorem Computationa and Metric Geometry Instructor: Yury Makarychev 1 Notation Given a metric space (X, d) and S X, the distance from x X to S equas d(x, S) = inf d(x, s). s S The distance
Bourgain s Theorem Computationa and Metric Geometry Instructor: Yury Makarychev 1 Notation Given a metric space (X, d) and S X, the distance from x X to S equas d(x, S) = inf d(x, s). s S The distance
On-line embeddings. Piotr Indyk Avner Magen Anastasios Sidiropoulos Anastasios Zouzias
 On-line embeddings Piotr Indyk Avner Magen Anastasios Sidiropoulos Anastasios Zouzias Abstract We initiate the study of on-line metric embeddings. In such an embedding we are given a sequence of n points
On-line embeddings Piotr Indyk Avner Magen Anastasios Sidiropoulos Anastasios Zouzias Abstract We initiate the study of on-line metric embeddings. In such an embedding we are given a sequence of n points
Algorithms for instance-stable and perturbation-resilient problems
 Midwest Theory Day, Indiana U., April 16, 2017 Algorithms for instance-stable and perturbation-resilient problems Haris Angelidakis, TTIC Konstantin Makarychev, Northwestern Yury Makarychev, TTIC Motivation
Midwest Theory Day, Indiana U., April 16, 2017 Algorithms for instance-stable and perturbation-resilient problems Haris Angelidakis, TTIC Konstantin Makarychev, Northwestern Yury Makarychev, TTIC Motivation
A Union of Euclidean Spaces is Euclidean. Konstantin Makarychev, Northwestern Yury Makarychev, TTIC
 Union of Euclidean Spaces is Euclidean Konstantin Makarychev, Northwestern Yury Makarychev, TTIC MS Meeting, New York, May 7, 2017 Problem by ssaf Naor Suppose that metric space (X, d) is a union of two
Union of Euclidean Spaces is Euclidean Konstantin Makarychev, Northwestern Yury Makarychev, TTIC MS Meeting, New York, May 7, 2017 Problem by ssaf Naor Suppose that metric space (X, d) is a union of two
Thus, X is connected by Problem 4. Case 3: X = (a, b]. This case is analogous to Case 2. Case 4: X = (a, b). Choose ε < b a
![Thus, X is connected by Problem 4. Case 3: X = (a, b]. This case is analogous to Case 2. Case 4: X = (a, b). Choose ε < b a Thus, X is connected by Problem 4. Case 3: X = (a, b]. This case is analogous to Case 2. Case 4: X = (a, b). Choose ε < b a](/thumbs/93/112528193.jpg) Solutions to Homework #6 1. Complete the proof of the backwards direction of Theorem 12.2 from class (which asserts the any interval in R is connected). Solution: Let X R be a closed interval. Case 1:
Solutions to Homework #6 1. Complete the proof of the backwards direction of Theorem 12.2 from class (which asserts the any interval in R is connected). Solution: Let X R be a closed interval. Case 1:
Santa Claus Schedules Jobs on Unrelated Machines
 Santa Claus Schedules Jobs on Unrelated Machines Ola Svensson (osven@kth.se) Royal Institute of Technology - KTH Stockholm, Sweden March 22, 2011 arxiv:1011.1168v2 [cs.ds] 21 Mar 2011 Abstract One of the
Santa Claus Schedules Jobs on Unrelated Machines Ola Svensson (osven@kth.se) Royal Institute of Technology - KTH Stockholm, Sweden March 22, 2011 arxiv:1011.1168v2 [cs.ds] 21 Mar 2011 Abstract One of the
Multi-Embedding and Path Approximation of Metric Spaces
 Multi-Embedding and Path Approximation of Metric Spaces Yair Bartal and Manor Mendel mendelma@cshujiacil The Hebrew University Multi-Embedding and Path Approximation of Metric Spaces p1/4 Metric Embedding
Multi-Embedding and Path Approximation of Metric Spaces Yair Bartal and Manor Mendel mendelma@cshujiacil The Hebrew University Multi-Embedding and Path Approximation of Metric Spaces p1/4 Metric Embedding
U.C. Berkeley CS294: Spectral Methods and Expanders Handout 11 Luca Trevisan February 29, 2016
 U.C. Berkeley CS294: Spectral Methods and Expanders Handout Luca Trevisan February 29, 206 Lecture : ARV In which we introduce semi-definite programming and a semi-definite programming relaxation of sparsest
U.C. Berkeley CS294: Spectral Methods and Expanders Handout Luca Trevisan February 29, 206 Lecture : ARV In which we introduce semi-definite programming and a semi-definite programming relaxation of sparsest
11.1 Set Cover ILP formulation of set cover Deterministic rounding
 CS787: Advanced Algorithms Lecture 11: Randomized Rounding, Concentration Bounds In this lecture we will see some more examples of approximation algorithms based on LP relaxations. This time we will use
CS787: Advanced Algorithms Lecture 11: Randomized Rounding, Concentration Bounds In this lecture we will see some more examples of approximation algorithms based on LP relaxations. This time we will use
On the Competitive Ratio for Online Facility Location
 On the Competitive Ratio for Online Facility Location Dimitris Fotakis Max-Planck-Institut für Informatik Stuhlsatzenhausweg 85, 6613 Saarbrücken, Germany Email: fotakis@mpi-sb.mpg.de Abstract. We consider
On the Competitive Ratio for Online Facility Location Dimitris Fotakis Max-Planck-Institut für Informatik Stuhlsatzenhausweg 85, 6613 Saarbrücken, Germany Email: fotakis@mpi-sb.mpg.de Abstract. We consider
Solutions to Exercises
 1/13 Solutions to Exercises The exercises referred to as WS 1.1(a), and so forth, are from the course book: Williamson and Shmoys, The Design of Approximation Algorithms, Cambridge University Press, 2011,
1/13 Solutions to Exercises The exercises referred to as WS 1.1(a), and so forth, are from the course book: Williamson and Shmoys, The Design of Approximation Algorithms, Cambridge University Press, 2011,
Extensions and limits to vertex sparsification
 Extensions and limits to vertex sparsification The MIT Faculty has made this article openly available. Please share how this access benefits you. Your story matters. Citation As Published Publisher F.
Extensions and limits to vertex sparsification The MIT Faculty has made this article openly available. Please share how this access benefits you. Your story matters. Citation As Published Publisher F.
Topics in Approximation Algorithms Solution for Homework 3
 Topics in Approximation Algorithms Solution for Homework 3 Problem 1 We show that any solution {U t } can be modified to satisfy U τ L τ as follows. Suppose U τ L τ, so there is a vertex v U τ but v L
Topics in Approximation Algorithms Solution for Homework 3 Problem 1 We show that any solution {U t } can be modified to satisfy U τ L τ as follows. Suppose U τ L τ, so there is a vertex v U τ but v L
Non-Uniform Graph Partitioning
 Robert Seffi Roy Kunal Krauthgamer Naor Schwartz Talwar Weizmann Institute Technion Microsoft Research Microsoft Research Problem Definition Introduction Definitions Related Work Our Result Input: G =
Robert Seffi Roy Kunal Krauthgamer Naor Schwartz Talwar Weizmann Institute Technion Microsoft Research Microsoft Research Problem Definition Introduction Definitions Related Work Our Result Input: G =
Minimum d-dimensional arrangement with fixed points
 Abstract Minimum d-dimensional arrangement with fixed points Anupam Gupta Anastasios Sidiropoulos October 8, 2013 In the Minimum d-dimensional Arrangement Problem d-dimap) we are given a graph with edge
Abstract Minimum d-dimensional arrangement with fixed points Anupam Gupta Anastasios Sidiropoulos October 8, 2013 In the Minimum d-dimensional Arrangement Problem d-dimap) we are given a graph with edge
Flows. Chapter Circulations
 Chapter 4 Flows For a directed graph D = (V,A), we define δ + (U) := {(u,v) A : u U,v / U} as the arcs leaving U and δ (U) := {(u,v) A u / U,v U} as the arcs entering U. 4. Circulations In a directed graph
Chapter 4 Flows For a directed graph D = (V,A), we define δ + (U) := {(u,v) A : u U,v / U} as the arcs leaving U and δ (U) := {(u,v) A u / U,v U} as the arcs entering U. 4. Circulations In a directed graph
A better approximation ratio for the Vertex Cover problem
 A better approximation ratio for the Vertex Cover problem George Karakostas Dept. of Computing and Software McMaster University October 5, 004 Abstract We reduce the approximation factor for Vertex Cover
A better approximation ratio for the Vertex Cover problem George Karakostas Dept. of Computing and Software McMaster University October 5, 004 Abstract We reduce the approximation factor for Vertex Cover
On Fixed Cost k-flow Problems
 On Fixed Cost k-flow Problems MohammadTaghi Hajiaghayi 1, Rohit Khandekar 2, Guy Kortsarz 3, and Zeev Nutov 4 1 University of Maryland, College Park, MD. hajiagha@cs.umd.edu. 2 Knight Capital Group, Jersey
On Fixed Cost k-flow Problems MohammadTaghi Hajiaghayi 1, Rohit Khandekar 2, Guy Kortsarz 3, and Zeev Nutov 4 1 University of Maryland, College Park, MD. hajiagha@cs.umd.edu. 2 Knight Capital Group, Jersey
Chapter 11. Approximation Algorithms. Slides by Kevin Wayne Pearson-Addison Wesley. All rights reserved.
 Chapter 11 Approximation Algorithms Slides by Kevin Wayne. Copyright @ 2005 Pearson-Addison Wesley. All rights reserved. 1 P and NP P: The family of problems that can be solved quickly in polynomial time.
Chapter 11 Approximation Algorithms Slides by Kevin Wayne. Copyright @ 2005 Pearson-Addison Wesley. All rights reserved. 1 P and NP P: The family of problems that can be solved quickly in polynomial time.
Local Search Based Approximation Algorithms. Vinayaka Pandit. IBM India Research Laboratory
 Local Search Based Approximation Algorithms The k-median problem Vinayaka Pandit IBM India Research Laboratory joint work with Naveen Garg, Rohit Khandekar, and Vijay Arya The 2011 School on Approximability,
Local Search Based Approximation Algorithms The k-median problem Vinayaka Pandit IBM India Research Laboratory joint work with Naveen Garg, Rohit Khandekar, and Vijay Arya The 2011 School on Approximability,
Ring Sums, Bridges and Fundamental Sets
 1 Ring Sums Definition 1 Given two graphs G 1 = (V 1, E 1 ) and G 2 = (V 2, E 2 ) we define the ring sum G 1 G 2 = (V 1 V 2, (E 1 E 2 ) (E 1 E 2 )) with isolated points dropped. So an edge is in G 1 G
1 Ring Sums Definition 1 Given two graphs G 1 = (V 1, E 1 ) and G 2 = (V 2, E 2 ) we define the ring sum G 1 G 2 = (V 1 V 2, (E 1 E 2 ) (E 1 E 2 )) with isolated points dropped. So an edge is in G 1 G
Embeddings of finite metric spaces in Euclidean space: a probabilistic view
 Embeddings of finite metric spaces in Euclidean space: a probabilistic view Yuval Peres May 11, 2006 Talk based on work joint with: Assaf Naor, Oded Schramm and Scott Sheffield Definition: An invertible
Embeddings of finite metric spaces in Euclidean space: a probabilistic view Yuval Peres May 11, 2006 Talk based on work joint with: Assaf Naor, Oded Schramm and Scott Sheffield Definition: An invertible
Discrete Geometry. Problem 1. Austin Mohr. April 26, 2012
 Discrete Geometry Austin Mohr April 26, 2012 Problem 1 Theorem 1 (Linear Programming Duality). Suppose x, y, b, c R n and A R n n, Ax b, x 0, A T y c, and y 0. If x maximizes c T x and y minimizes b T
Discrete Geometry Austin Mohr April 26, 2012 Problem 1 Theorem 1 (Linear Programming Duality). Suppose x, y, b, c R n and A R n n, Ax b, x 0, A T y c, and y 0. If x maximizes c T x and y minimizes b T
Topic: Primal-Dual Algorithms Date: We finished our discussion of randomized rounding and began talking about LP Duality.
 CS787: Advanced Algorithms Scribe: Amanda Burton, Leah Kluegel Lecturer: Shuchi Chawla Topic: Primal-Dual Algorithms Date: 10-17-07 14.1 Last Time We finished our discussion of randomized rounding and
CS787: Advanced Algorithms Scribe: Amanda Burton, Leah Kluegel Lecturer: Shuchi Chawla Topic: Primal-Dual Algorithms Date: 10-17-07 14.1 Last Time We finished our discussion of randomized rounding and
The Lefthanded Local Lemma characterizes chordal dependency graphs
 The Lefthanded Local Lemma characterizes chordal dependency graphs Wesley Pegden March 30, 2012 Abstract Shearer gave a general theorem characterizing the family L of dependency graphs labeled with probabilities
The Lefthanded Local Lemma characterizes chordal dependency graphs Wesley Pegden March 30, 2012 Abstract Shearer gave a general theorem characterizing the family L of dependency graphs labeled with probabilities
On Allocating Goods to Maximize Fairness
 On Allocating Goods to Maximize Fairness Deeparnab Chakrabarty Julia Chuzhoy Sanjeev Khanna February 24, 2012 Abstract We consider the Max-Min Allocation problem: given a set A of m agents and a set I
On Allocating Goods to Maximize Fairness Deeparnab Chakrabarty Julia Chuzhoy Sanjeev Khanna February 24, 2012 Abstract We consider the Max-Min Allocation problem: given a set A of m agents and a set I
HAMILTON CYCLES IN RANDOM REGULAR DIGRAPHS
 HAMILTON CYCLES IN RANDOM REGULAR DIGRAPHS Colin Cooper School of Mathematical Sciences, Polytechnic of North London, London, U.K. and Alan Frieze and Michael Molloy Department of Mathematics, Carnegie-Mellon
HAMILTON CYCLES IN RANDOM REGULAR DIGRAPHS Colin Cooper School of Mathematical Sciences, Polytechnic of North London, London, U.K. and Alan Frieze and Michael Molloy Department of Mathematics, Carnegie-Mellon
On Allocating Goods to Maximize Fairness
 On Allocating Goods to Maximize Fairness Deeparnab Chakrabarty Julia Chuzhoy Sanjeev Khanna September 23, 2009 Abstract We consider the Max-Min Allocation problem: given a set A of m agents and a set I
On Allocating Goods to Maximize Fairness Deeparnab Chakrabarty Julia Chuzhoy Sanjeev Khanna September 23, 2009 Abstract We consider the Max-Min Allocation problem: given a set A of m agents and a set I
Partial cubes: structures, characterizations, and constructions
 Partial cubes: structures, characterizations, and constructions Sergei Ovchinnikov San Francisco State University, Mathematics Department, 1600 Holloway Ave., San Francisco, CA 94132 Abstract Partial cubes
Partial cubes: structures, characterizations, and constructions Sergei Ovchinnikov San Francisco State University, Mathematics Department, 1600 Holloway Ave., San Francisco, CA 94132 Abstract Partial cubes
Label Cover Algorithms via the Log-Density Threshold
 Label Cover Algorithms via the Log-Density Threshold Jimmy Wu jimmyjwu@stanford.edu June 13, 2017 1 Introduction Since the discovery of the PCP Theorem and its implications for approximation algorithms,
Label Cover Algorithms via the Log-Density Threshold Jimmy Wu jimmyjwu@stanford.edu June 13, 2017 1 Introduction Since the discovery of the PCP Theorem and its implications for approximation algorithms,
Lecture 2: Scheduling on Parallel Machines
 Lecture 2: Scheduling on Parallel Machines Loris Marchal October 17, 2012 Parallel environment alpha in Graham s notation): P parallel identical Q uniform machines: each machine has a given speed speed
Lecture 2: Scheduling on Parallel Machines Loris Marchal October 17, 2012 Parallel environment alpha in Graham s notation): P parallel identical Q uniform machines: each machine has a given speed speed
Randomized algorithm
 Tutorial 4 Joyce 2009-11-24 Outline Solution to Midterm Question 1 Question 2 Question 1 Question 2 Question 3 Question 4 Question 5 Solution to Midterm Solution to Midterm Solution to Midterm Question
Tutorial 4 Joyce 2009-11-24 Outline Solution to Midterm Question 1 Question 2 Question 1 Question 2 Question 3 Question 4 Question 5 Solution to Midterm Solution to Midterm Solution to Midterm Question
The 2-valued case of makespan minimization with assignment constraints
 The 2-valued case of maespan minimization with assignment constraints Stavros G. Kolliopoulos Yannis Moysoglou Abstract We consider the following special case of minimizing maespan. A set of jobs J and
The 2-valued case of maespan minimization with assignment constraints Stavros G. Kolliopoulos Yannis Moysoglou Abstract We consider the following special case of minimizing maespan. A set of jobs J and
Hardness of Submodular Cost Allocation: Lattice Matching and a Simplex Coloring Conjecture
 Hardness of Submodular Cost Allocation: Lattice Matching and a Simplex Coloring Conjecture Alina Ene,2 and Jan Vondrák 3 Center for Computational Intractability, Princeton University 2 Department of Computer
Hardness of Submodular Cost Allocation: Lattice Matching and a Simplex Coloring Conjecture Alina Ene,2 and Jan Vondrák 3 Center for Computational Intractability, Princeton University 2 Department of Computer
Distributed Distance-Bounded Network Design Through Distributed Convex Programming
 Distributed Distance-Bounded Network Design Through Distributed Convex Programming OPODIS 2017 Michael Dinitz, Yasamin Nazari Johns Hopkins University December 18, 2017 Distance Bounded Network Design
Distributed Distance-Bounded Network Design Through Distributed Convex Programming OPODIS 2017 Michael Dinitz, Yasamin Nazari Johns Hopkins University December 18, 2017 Distance Bounded Network Design
Project in Computational Game Theory: Communities in Social Networks
 Project in Computational Game Theory: Communities in Social Networks Eldad Rubinstein November 11, 2012 1 Presentation of the Original Paper 1.1 Introduction In this section I present the article [1].
Project in Computational Game Theory: Communities in Social Networks Eldad Rubinstein November 11, 2012 1 Presentation of the Original Paper 1.1 Introduction In this section I present the article [1].
Lower-Stretch Spanning Trees
 Lower-Stretch Spanning Trees Michael Elkin Ben-Gurion University Joint work with Yuval Emek, Weizmann Institute Dan Spielman, Yale University Shang-Hua Teng, Boston University + 1 The Setting G = (V, E,
Lower-Stretch Spanning Trees Michael Elkin Ben-Gurion University Joint work with Yuval Emek, Weizmann Institute Dan Spielman, Yale University Shang-Hua Teng, Boston University + 1 The Setting G = (V, E,
A necessary and sufficient condition for the existence of a spanning tree with specified vertices having large degrees
 A necessary and sufficient condition for the existence of a spanning tree with specified vertices having large degrees Yoshimi Egawa Department of Mathematical Information Science, Tokyo University of
A necessary and sufficient condition for the existence of a spanning tree with specified vertices having large degrees Yoshimi Egawa Department of Mathematical Information Science, Tokyo University of
Bulletin of the Iranian Mathematical Society
 ISSN: 117-6X (Print) ISSN: 1735-8515 (Online) Bulletin of the Iranian Mathematical Society Vol. 4 (14), No. 6, pp. 1491 154. Title: The locating chromatic number of the join of graphs Author(s): A. Behtoei
ISSN: 117-6X (Print) ISSN: 1735-8515 (Online) Bulletin of the Iranian Mathematical Society Vol. 4 (14), No. 6, pp. 1491 154. Title: The locating chromatic number of the join of graphs Author(s): A. Behtoei
Chapter 2 Metric Spaces
 Chapter 2 Metric Spaces The purpose of this chapter is to present a summary of some basic properties of metric and topological spaces that play an important role in the main body of the book. 2.1 Metrics
Chapter 2 Metric Spaces The purpose of this chapter is to present a summary of some basic properties of metric and topological spaces that play an important role in the main body of the book. 2.1 Metrics
Containment restrictions
 Containment restrictions Tibor Szabó Extremal Combinatorics, FU Berlin, WiSe 207 8 In this chapter we switch from studying constraints on the set operation intersection, to constraints on the set relation
Containment restrictions Tibor Szabó Extremal Combinatorics, FU Berlin, WiSe 207 8 In this chapter we switch from studying constraints on the set operation intersection, to constraints on the set relation
Approximate Voronoi Diagrams
 CS468, Mon. Oct. 30 th, 2006 Approximate Voronoi Diagrams Presentation by Maks Ovsjanikov S. Har-Peled s notes, Chapters 6 and 7 1-1 Outline Preliminaries Problem Statement ANN using PLEB } Bounds and
CS468, Mon. Oct. 30 th, 2006 Approximate Voronoi Diagrams Presentation by Maks Ovsjanikov S. Har-Peled s notes, Chapters 6 and 7 1-1 Outline Preliminaries Problem Statement ANN using PLEB } Bounds and
Approximating maximum satisfiable subsystems of linear equations of bounded width
 Approximating maximum satisfiable subsystems of linear equations of bounded width Zeev Nutov The Open University of Israel Daniel Reichman The Open University of Israel Abstract We consider the problem
Approximating maximum satisfiable subsystems of linear equations of bounded width Zeev Nutov The Open University of Israel Daniel Reichman The Open University of Israel Abstract We consider the problem
Lecture: Flow-based Methods for Partitioning Graphs (1 of 2)
 Stat260/CS294: Spectral Graph Methods Lecture 10-02/24/2015 Lecture: Flow-based Methods for Partitioning Graphs (1 of 2) Lecturer: Michael Mahoney Scribe: Michael Mahoney Warning: these notes are still
Stat260/CS294: Spectral Graph Methods Lecture 10-02/24/2015 Lecture: Flow-based Methods for Partitioning Graphs (1 of 2) Lecturer: Michael Mahoney Scribe: Michael Mahoney Warning: these notes are still
Lecture 4 October 18th
 Directed and undirected graphical models Fall 2017 Lecture 4 October 18th Lecturer: Guillaume Obozinski Scribe: In this lecture, we will assume that all random variables are discrete, to keep notations
Directed and undirected graphical models Fall 2017 Lecture 4 October 18th Lecturer: Guillaume Obozinski Scribe: In this lecture, we will assume that all random variables are discrete, to keep notations
1 Ordinary Load Balancing
 Comp 260: Advanced Algorithms Prof. Lenore Cowen Tufts University, Spring 208 Scribe: Emily Davis Lecture 8: Scheduling Ordinary Load Balancing Suppose we have a set of jobs each with their own finite
Comp 260: Advanced Algorithms Prof. Lenore Cowen Tufts University, Spring 208 Scribe: Emily Davis Lecture 8: Scheduling Ordinary Load Balancing Suppose we have a set of jobs each with their own finite
A PTAS for TSP with Fat Weakly Disjoint Neighborhoods in Doubling Metrics
 A PTAS for TSP with Fat Weakly Disjoint Neighborhoods in Doubling Metrics T-H. Hubert Chan Shaofeng H.-C. Jiang Abstract We consider the Traveling Salesman Problem with Neighborhoods (TSPN) in doubling
A PTAS for TSP with Fat Weakly Disjoint Neighborhoods in Doubling Metrics T-H. Hubert Chan Shaofeng H.-C. Jiang Abstract We consider the Traveling Salesman Problem with Neighborhoods (TSPN) in doubling
Metric Embeddings with Relaxed Guarantees
 Metric Embeddings with Relaxed Guarantees Ittai Abraham Yair Bartal T-H. Hubert Chan Kedar Dhamdhere Anupam Gupta Jon Kleinberg Ofer Neiman Aleksandrs Slivkins Abstract We consider the problem of embedding
Metric Embeddings with Relaxed Guarantees Ittai Abraham Yair Bartal T-H. Hubert Chan Kedar Dhamdhere Anupam Gupta Jon Kleinberg Ofer Neiman Aleksandrs Slivkins Abstract We consider the problem of embedding
Improved Approximating Algorithms for Directed Steiner Forest
 Improved Approximating Algorithms for Directed Steiner Forest Moran Feldman Guy Kortsarz Zeev Nutov Abstract We consider the k-directed Steiner Forest (k-dsf) problem: Given a directed graph G = (V, E)
Improved Approximating Algorithms for Directed Steiner Forest Moran Feldman Guy Kortsarz Zeev Nutov Abstract We consider the k-directed Steiner Forest (k-dsf) problem: Given a directed graph G = (V, E)
3.7 Cutting plane methods
 3.7 Cutting plane methods Generic ILP problem min{ c t x : x X = {x Z n + : Ax b} } with m n matrix A and n 1 vector b of rationals. According to Meyer s theorem: There exists an ideal formulation: conv(x
3.7 Cutting plane methods Generic ILP problem min{ c t x : x X = {x Z n + : Ax b} } with m n matrix A and n 1 vector b of rationals. According to Meyer s theorem: There exists an ideal formulation: conv(x
Routing in Networks with Low Doubling Dimension
 Routing in Networks with Low Doubling Dimension Ittai Abraham 1 Cyril Gavoille 2 Andrew V. Goldberg 3 Dahlia Malkhi 4 December 2005 Technical Report MSR-TR-2005-175 Microsoft Research Microsoft Corporation
Routing in Networks with Low Doubling Dimension Ittai Abraham 1 Cyril Gavoille 2 Andrew V. Goldberg 3 Dahlia Malkhi 4 December 2005 Technical Report MSR-TR-2005-175 Microsoft Research Microsoft Corporation
Combinatorial Optimization
 Combinatorial Optimization 2017-2018 1 Maximum matching on bipartite graphs Given a graph G = (V, E), find a maximum cardinal matching. 1.1 Direct algorithms Theorem 1.1 (Petersen, 1891) A matching M is
Combinatorial Optimization 2017-2018 1 Maximum matching on bipartite graphs Given a graph G = (V, E), find a maximum cardinal matching. 1.1 Direct algorithms Theorem 1.1 (Petersen, 1891) A matching M is
New algorithms for Disjoint Paths and Routing Problems
 New algorithms for Disjoint Paths and Routing Problems Chandra Chekuri Dept. of Computer Science Univ. of Illinois (UIUC) Menger s Theorem Theorem: The maximum number of s-t edgedisjoint paths in a graph
New algorithms for Disjoint Paths and Routing Problems Chandra Chekuri Dept. of Computer Science Univ. of Illinois (UIUC) Menger s Theorem Theorem: The maximum number of s-t edgedisjoint paths in a graph
Notes on Gaussian processes and majorizing measures
 Notes on Gaussian processes and majorizing measures James R. Lee 1 Gaussian processes Consider a Gaussian process {X t } for some index set T. This is a collection of jointly Gaussian random variables,
Notes on Gaussian processes and majorizing measures James R. Lee 1 Gaussian processes Consider a Gaussian process {X t } for some index set T. This is a collection of jointly Gaussian random variables,
