Approximation Algorithms and Hardness of Approximation. IPM, Jan Mohammad R. Salavatipour Department of Computing Science University of Alberta
|
|
|
- Myra Hardy
- 5 years ago
- Views:
Transcription
1 Approximation Algorithms and Hardness of Approximation IPM, Jan 2006 Mohammad R. Salavatipour Department of Computing Science University of Alberta 1
2 Introduction For NP-hard optimization problems, we want to: 1. find the optimal solution, 2. find the solution fast, often in polynomial time 3. find solutions for any instance Assuming P NP, we cannot have all the above simultaneously. If we 1. relax (3), then we are into study of special cases. 2. relax (2), we will be in the field of integer programming (branch-and-bound, etc). 3. relax (1), we are into study of heuristics and approximation algorithms. We are going to focus on approximation algorithms: finding solutions that are within a guaranteed factor of the optimal solutions, and We want to find this solution fast (i.e. polynomial time). 2
3 Introduction An NP optimization problem, Π, is a minimization (maximization) problem which consists of the following items: Valid instances: each valid instance I is recognizable in polytime; D Π is set of all valid instances. Feasible solutions: Each I D Π has a set S Π (I) of feasible solutions and for each solution s S Π (I), s is polynomial (in I ). Objective function: A polytime computable function f(s, I) that assigns a 0 rational value to each feasible solution. Typically, want a solution whose value is minimized (maximized): it is called the optimal solution. Example: Minimum Spanning Tree (MST): A connected graph G(V, E), each (u, v) E has a weight w(u, v), Goal: find an acyclic connected subset T E whose total weight is minimized. valid instances : a graph with weighted edges. feasible solutions : all the spanning trees of the given weighted graph. objective functions : minimizing the total weight of a spanning tree. 3
4 Introduction Approximation algorithms: An α-approximation algorithm is a polytime algorithm whose solution is always within factor α of optimal solution. For a minimization problem Π, algorithm A has factor α 1 if for its solution s: f(s, I) α( I ) OP T (I). α can be a constant or a function of the size of the instance. Example: Vertex-Cover Problem Input: undirected graph G = (V, E) and a cost function c : V Q + Goal: find a minimum cost vertex cover, i.e. a set V V s.t. every edge has at least one endpoint in V. The special case, in which all vertices are of unit cost: cardinality vertex cover problem. V.C. is NP-hard. Let s look for an approximation 4
5 Vertex Cover Perhaps the most natural greedy algorithm for this problem is: Algorithm VC1: S While E do let v be a vertex of maximum degree in G S S {v} remove v and all its edges from G return S Easy to see that it finds a VC. What about the approximation ratio? It can be shown that the approximation ratio is O(log ), where is the maximum degree in G. The second approximation algorithm V C2 appears to be counter-intuitive at first glance: Algorithm VC2: S While E do let (u, v) E be any edge S S {u, v} delete u,v and all their edges from G return S 5
6 Lemma 1 VC2 returns a vertex cover of G. Vertex Cover Proof: V C2 loops until every edge in G has been covered by some vertex in S. Lemma 2 VC2 is a 2-approximation algorithm. Proof: Let A denote the set of edges selected by V C2. Note that A forms a matching, i.e. no two edges selected share an end-point Therefore, in order to cover the edges of A, any vertex cover must include at least one endpoint of each edge in A. So does any optimal V.C. S, i.e. S A. Since S = 2 A, we have S 2 S. Lemma 3 The analysis of V C2 is tight. A complete bipartite graph K n,n. V C2 picks all the 2n vertices, but optimal picks one part only. Major Open question: Is there a 2 O(1)-approx algorithm for V.C.? 6
7 Set Cover Theorem 4 (Hastad 97) Unless P = NP, there is no approximation algorithm with ratio < 7 6 for Vertex-Cover problem. Set Cover Set-cover is perhaps the single most important (and very well-studied) problem in the field of approximation algorithms. Set-Cover Problem Input U : a universe of n elements e 1,..., e n, S = {S 1, S 2,, S k } a collection of subsets of U, c : S Q + a cost function Goal: find a min cost subcollection of S that covers all the elements of U, i.e. I {1, 2,, k} with min i I c(s i) such that i I S i = U V.C. problem is a special case of Set-Cover: for a graph G(V, E), let U = E, and S i = {e E e is incident within v i } 7
8 Set Cover We will give an (ln n)-approx greedy algorithm for Set Cover. Rather than greedily picking the set which covers maximum number of elements, we have to take the cost into account at the same time. We pick the most cost-effective set and remove the covered elements until all elements are covered. Definition 5 The cost-effectiveness of a set S i is the average cost at which it covers new element, i.e., α = c(s i) S i, where C is the set of elements already C covered. We Define the price of an element to be the cost at which it is covered. Greedy Set-Cover algorithm C, T While C U do choose a S i with the smallest α add S i to T for each element C C {S i } return T e S i C, set price(e) = α when a set S i is picked, its cost is distributed equally among the new elements covered 8
9 Set Cover: Greedy Theorem 6 The Greedy Set-Cover algorithm is an H n factor approximation algorithm for the minimum set cover problem, where H n = n. Note that H n ln n. Proof: Let e 1, e 2,, e n be the order at which the elements are covered It can be seen that: c(s i ) = S i T n price(e k ) k=1 We try to estimate price(e k ) (at this stage, we have covered e 1, e 2,, e k 1, and have n k + 1 uncovered elements). Let T OP T be an opt solution and C OP T be its cost. At any point of time, we can cover the elements in U C at a cost of at most C OP T. Thus among the sets not selected, a set with cost-effectiveness C OP T U C In the iteration in which element e k was covered, U C = n k
10 Set Cover: Greedy Since e k was covered by the most cost-effective set in this iteration: price(e k ) C OP T n k + 1 As the cost of each set picked is distributed among the new elements covered, the total cost of the set cover picked is: n c(s i ) = price(e k ) S i T k=1 C OP T n k=1 = H n C OP T 1 n k + 1 The analysis of this greedy algorithm is tight: Example: each e 1, e 2,, e n by itself is a set, with cost 1 n, 1 n 1,, 1 respectively; one set contains all of U with cost 1 + ɛ for some ɛ > 0. the greedy solution picks n singleton sets; costs 1 n + 1 n = H n. The optimal cover has cost 1 + ɛ. 10
11 Set Cover: Greedy Theorem 7 Based on the results of Lund and Yannakakis 92, Feige 86, Raz 98, Safra 97, Suduan 97: There is a constant 0 < c < 1 such that if there is a (c ln n)-approximation algorithm for Set-Cover problem, then P = NP. For any constant ɛ > 0, if there is a (1 ɛ) ln n- approximation algorithm for Set-Cover then NP DT IME(n O(ln ln n) ). Next we give another algorithm for Set Cover using Linear Programming (LP). First, forumlate Set Cover as an IP. We have one indicator variable x s for every set S: minimize s S c sx s subject to e U : x s {0, 1} s:e S x s 1 Now relax the integrality constraint to obtain the corresponding LP. Although IP is NP-hard, there are polytime algorithms for solving LP. Solution to an LP-relaxation is usually called the fractional solution and is denoted by OP T f. 11
12 Set Cover: Randomized Rounding We give another O(log n)-approximation for Set Cover using a powerful technique called randomized rounding. The general idea is to start with the optimal fractional solution (solution to the LP) and then round the fractional values to 1 with some appropriate probabilities. Randomized Rounding Alg for Set cover: Take the LP relaxation and solve it. For each set S, pick S with probability P s = x s (i.e. round x s up to 1 with probability x s), let s call the integer value ˆx s ), Consider the collection C = {S j ˆx Sj = 1}: E[cost(C)] = S j S Pr[S j is picked] c Sj = x S j c Sj = OP T f Let α be large enough s.t. ( 1 e )α log n 1 4n. (1) Repeat the algorithm above α log n times and let C = α log n i=1 C i be the final solution, where C i is the collection obtained after round i of the algorithm. 12
13 Suppose e j belongs to S 1,...S q. Set Cover: Randomized Rounding By the constraint for e j, in any fractional feasible solution: x S1 + x S x Sq 1 It can be shown that the probability that e j is covered is minimized when x S1 = x S2 =... = x Sq = 1 q Pr[e j is not covered in C i ] (1 1 q )q < 1 e Pr[e j / C ] ( 1 e )α log n 1 4n Sum over all e j : Pr[ e j, e j / C, (i.e. C is not a set cover)] n 1 4n 1 4 Let s call the event C is not a Set Cover, E1. By above: Pr[E 1 ] 1 4. (2) On the other hand, by (1) and by summing over all rounds: E[cost(C )] α log n OP T f 13
14 Set Cover: Randomized Rounding Markov s inequality says for any random variable X: Pr[X t] E[X] t. Define the bad event E 2 to be the event that cost(c ) > 4α log n OP T. Thus: Pr[E 2 ] = Pr[cost(C ) > 4α log n OP T ] α log n OP T f 4α log n OP T f 1 4 The probability that either C is not a set cover (i.e. E 1 happens) or that C is a set cover with large cost (i.e. E 2 happens) is at most: Pr[E 1 ] + Pr[E 2 ] 1 2. Therefore, with probability 1 2, C is a set cover with cost(c ) 4α log n OP T f 4α log n OP T. Repeating this algorithm t times, the probability of failure at all rounds is at most 1 2 t. So, the probability of success for at least one run of the algorithm is t. 14
15 Section 2: Hardness of Approximation 15
16 Hardness of Approximation We are familiar with the theory of NP-completeness. When we prove that a problem is NP-hard it implies that, assuming P NP there is no polynomail time algorithm that solves the problem (exactly). For example, for SAT, deciding between Yes/No is hard (again assuming P NP). We would like to show that even deciding between those instances that are (almost) satisfiable and those that are far from being satisfiable is also hard. In other words, create a gap between Yes instances and No instances. These kinds of gaps imply hardness of approximation for optimization version of NP-hard problems. As SAT is the canonical problem for NP-hardness, Max-SAT is the canonical problem for hardness of approximation: Max-SAT: Input: A boolean formula Φ over variables x 1,..., x n in CNF which has clauses C 1,..., C M. Question: Find a truth assignment to maximizes the number of satisfied clauses. 16
17 Hardness of Approximation The PCP theorem implies that Max-SAT is NPhard to approximate within a factor of (1 ɛ 0 ), for some fixed ɛ 0 > 0. For proving a hardness of approximation, for example for vertex cover, we prove a reduction like the following: Given a formula ϕ for Max-SAT, we build a graph G(V, E) in polytime such that: if ϕ is a yes-instance, then G has a vertex cover of size 2 V ; 3 if ϕ is a no-instance, then every vertex cover of G has a size > α 2 V for some fixed α > 1. 3 Corollary 8 The vertex cover problem cannot be approximated with a factor of α unless P = NP. In this reduction we have created a gap of size α between yes/no instances. 17
18 Hardness of Approximation Suppose L is NP-complete and π is a minimization problem. Let g be a function computable in polytime that maps Yes-instances of L into a set S 1 of instances of π and No-instances of L into a set S 2. Assume that there is a polytime computable function h such that: for every Yes-instance x of L: OP T (g(x)) h(g(x)); for every No-instance x of L: OP T (g(x)) > αh(g(x)). Then g is called a gap-introducing reduction from L to π and α is the size of the gap. This implies π is hard to approximate within factor α. 18
19 Max-SNP and PCP Many problems, such as Bin Packing and Knapsack, have PTAS s, i.e. a (1 + ɛ)-approximation for any constant ɛ > 0. A major open question was: does Max-3SAT have a PTAS? A significant result on this line was by Papadimitriou and M. Yannakakis ( 92); they defined the class Max-SNP. All problems in Max-SNP have constant approximation algorithms. They also defined the notion of completeness for this class and showed if a Max-SNP-complete problem has a PTAS then every Max-SNP problem has a PTAS. Several well-known problems including Max-3SAT and TSP are Max-SNP-complete. The celeberated PCP theorem states that there is no PTAS for Max-SNP problems. It also give another characterization of NP. 19
20 PCP Definition 9 A language L NP if and only if there is a deterministic polynomial time verifier (i.e. algorithm) V that takes an input x and a proof y with y = x c for a constant c > 0 and it satisfies the following: Completeness: if x L y s.t. V (x, y) = 1. Soundness: if x / L y, V (x, y) = 0. Definition 10 An (r(n), b(n))-restricted verifier is a randomized verifier that uses at most r(n) random bits. It runs in probabilistic polynomial time and reads/queries at most b(n) bits of the proof. Definition 11 For 0 s < c 1, a language L PCP c,s (r(n), b(n)) if and only if there is a (r(n), b(n))- restricted verifier V such that given an input x with length x = n and a proof π, it satisfies the following: Completeness: if x L a proof π such that Pr[V (x, π) = 1] C. Soundness: if x / L π, Pr[V (x, π) = 1] S. 20
21 PCP The probabilities in completeness and soundness given in definition above are typically C = 1 and S = 1 2, respectively. From the definition, for any 0 s < c 1: NP PCP c,s (0, poly(n)) PCP c,s (O(log n), poly(n)). Lemma 12 PCP c,s (O(log n), poly(n)) NP Proof: Let L be a language in PCP c,s (O(log n), poly(n)) with a verifier V. We construct a non-deterministic polytime Turing machine M for L. Starting with an input x, M guesses a proof π and simulates V on all 2 O(log n) = poly(n) possible random strings. M accepts if at least a fraction c of all these runs accept, rejects otherwise. 21
22 PCP Theorem Thus: if x L V (x, π) accepts with probability at least c; thus at least a fraction c of random strings cause the verifier V and therefore M to accept. if x L then the verifier accepts with probability at most s which is smaller than c; thus for only a fraction of < c of random strings verifier V accepts; M rejects. Since there are O(poly(n)) random strings of length O(log n) and each simulation takes polytime, the running time of M is polytime. This lemma and the observation before it implies that PCP c,s (O(log n), poly(n)) = NP. The remarkable PCP theorem, proved by Arora/Safra [92] and Arora/Lund/Motwani/Sudan/Szegedy[92] states: Theorem 13 (PCP Theorem) NP = PCP 1, 1(O(log n), O(1)) 2 22
23 PCP to Max-3SAT The original proof of PCP theorem was extremely difficult. There is a new a much simpler proof of PCP theorem using a different technique by Dinur [2005]. Basically, the PCP theorem says that for every problem in NP there is a verifier that queries only a constant number of bits of the proof (regardless of the length of the proof) and with sufficiently high probability gives a correct answer. Starting from the PCP theorem, we show that approximating Max-3SAT within some constant factor is NP-hard. Before that note that there is a trivial 7 8 -approximation for Max-3SAT. Given a 3SAT formula Φ for Max-3SAT with 3-clauses C 1,..., C m and variables x 1,..., x n, assign each x i True/False u.r. with probability 1 2. This is a 7 -approximation for Max-3SAT: 8 23
24 Max-3SAT For each clause C i = (x 5 x 1 x 3 ), the probability that C i is not satisfied is: Pr[x 5 = F ] Pr[x 1 = T ] Pr[x 3 = F ] = 1 8 Thus each clause C i is satisfied with probability 7 8 ; so the expected number of satisfied clauses is at least 7 m (this can be easily de-randomized). 8 Theorem 14 For some absolute constant ɛ > 0, there is a gap-introducing reduction from SAT to Max-3SAT such that it transforms a boolean formula φ for SAT to a boolean formula ψ with m clauses for Max-3SAT such that: if φ is satisfiable, then OP T (ψ) = m. if φ is a NO-instance, then OP T (ψ) (1 ɛ)m. Corollary 15 Approximating Max-3SAT with a factor better then (1 ɛ) is NP-hard for some constant ɛ > 0. 24
25 Max-3SAT Proof of Theorem 14: By PCP theorem, SAT has a P CP 1, 1(O(log n), O(1)) 2 verifier V. Let us assume that it is P CP 1, 1(d log n, k) 2 where d and k are some constants. Let r 1,..., r n d be all the possible random bits (of length d log n) that can be given as seed to V. We will construct a formula f i for every possible random bit r i. Thus we will have formulas f 1,..., f n d. For any particular choice of random bits, the verifier reads k positions of the proof; each of these positions is determined by the value read in previous position and the random bits. So it can be considered to evaluate a boolean binary decision tree of height at most k; where the decision to go left or right is based on the value read from the proof. 25
26 Max-3SAT X_j 0 1 X_k X_l Reject Accept Reject Accept Here suppose k = 2 and we have a fixed random bit string. Based on the first random bit the position we read is x j, if it returns 0 we get the second random bit and based on that we read position x k, else if x j was 1 we read position x l. So we can use four variables x j, x k, x j, x l to form a formula encoding this tree 26
27 In general, this decision tree can be encoded as a boolean formula with at most 2 k variables and 2 k clauses each of length k. Think of every node as a variable and every path from root to leaf forms a clause. It is easy to see that the formula is satisfied if and only if the path that the verifier traverses on the tree ends at an accept leaf. Any truth assignment to the variables i.e. any proof, will give a unique path for each decision tree. If for a fixed random bit string and a proof (truth assignment) the path ends in an accept it means that the verifier accepts the proof, otherwise it rejects the proof. If φ is a YES-instance, there is a truth assignment that works/accpets with probability of 1 (i.e., for any random bits it will accept) the corresponding truth assignment will give a path from root to an accept leaf in every decision tree (corresponding to a random bit string); so it satisfies all formulas f 1,..., f n d.
28 PCP and Max-3SAT If φ is a NO-instance for any proof (truth assignment) V accepts with probability 1 (this is from 2 the P CP definition) for at least half of the decision trees, the truth assignment will give a root to leaf path that ends in reject, i.e. the formula is not satisfied. Therefore, among all n d them are not satisfied. formulas, at least nd 2 of Now on we can transform all formulas f 1,..., f n d into 3-CNF formulas f 1,..., f n such that that f d i is satisfiable if and only if f i is. This theorem showed that PCP theorem implies a gap-introducing reduction from SAT to Max-3SAT. The oposite is also true; i.e. assuming the existence of a gap-introducing reduction from SAT to Max- 3SAT we can prove the PCP theorem, as follows. Suppose that for each L NP there is a polytime computable g from L to instances of MAX-3SAT, such that for Yes-instance y L, all 3-clauses in g(y) can be satisfied; 27
29 for No-instance y L, at most 1 2 of g(y) can be satisfied. of the 3-clauses Define a proof that y L to be a truth assignment satisfying g(y). We define a randomized verifier V for L. V runs in polynomial time and takes y and the new proof π; accept iff π satisfies a 3-clause selected uniformly and randomly from g(y). If y L then there is a proof (truth assignment) such that all the 3-clauses in g(y) can be satisfied. For that proof Verifier V (y, π) accepts with probability 1. If y L then every truth assignment satisfies no more than 1 of clauses in g(y). So verifier V (y, π) 2 will reject with probability at least 1 2. This, together with Theorem 14 implies that the PCP theorem is in fact equivalent to: There is no PTAS for Max-3SAT.
30 Section 3: Improved Hardness results 28
31 Improved PCP s Recall that PCP theorem says: NP = P CP 1, 1(O(log n), O(1)). 2 Goal: reduce the number of query bits and also decrease the the probability of failure. Theorem 16 For some s < 1 : NP = P CP 1,s (O(log n), 3). Proof: Let L NP be an arbitrary language; y be an instance of L. By PCP, we can construct a 3CNF formula F such that: if y L = a truth assignment for F s.t. all clauses of F are satisfied. if y / L = for any truth assignment for F at most (1 ɛ) fractions of clauses are satisfied. We assume that the proof π given for y is the truth assignment to formula F above. 29
32 Improved PCP s Verifier V given y and proof π, computes F in polytime, then uses O(log n) bits to pick a random clause of F and query the truth assignment to its 3 variables. The verifier accepts if and only if the clause is satisfied. It is easy to see that: If y L then there is a proof π s.t. V accepts with probability 1. If y L then for any proof π, V accepts with probability at most 1 ɛ. Theorem 17 (Guruswami,Sudan,Lewin,Trevisan 93) For all ɛ > 0 NP = P CP 1, 1 2 +ɛ (O(log n), 3). Note that the 3 bits of the proof are selected by the verifier adaptively. Theorem 18 (Karloff/Zwick, 97) P = P CP 1, 1(O(log n), 3). 2 30
33 Improved PCP s Theorem 19 (Hástad 97) NP = P CP 1 ɛ, 1 2 +ɛ (O(log n), 3) where the verifier selects the 3 bits of the proof a priori. That is, the verifier uses O(log n) random bits to choose 3 positions, i 1, i 2, i 3 of the proof and a bit b and accepts if and only if π(i 1 ) π(i 2 ) π(i 3 ) = b. Corollary 20 For any ɛ > 0, it is NP-hard to approximate: Max-3SAT within a factor of ( ɛ), Vertex cover within a factor of ( ɛ), Recall that the simple algorithm we gave for Max- 3SAT has approximation factor 7 8. The best Hardness factor for VC is
34 Hardness of Clique Definition 21 (MAX-CLIQUE) Given a graph with n vertices, find a maximum size clique in it, i.e. a complete subgraph of maximum size. The best known algorithm has a factor of O( n log log2 n ). log 3 n Clique and Max-3SAT are both NP-hard, but why the approximation for clique is so bad? Hástad: for any ɛ > 0 there is no polytime approximation algorithm for clique with factor n 1 ɛ 2 (if P NP) or n 1 ɛ (if ZPP NP). Our goal is to prove a polynomial hardness for clique. We start with a constant hardness result for Clique. Then show that it is hard to approximate Clique within any constant factor. Finally, we show how to improve this to a polynomial. 32
35 Hardness of Clique Consider a PCP 1, 1(d log n, q) verifier F for SAT, where 2 d and q are constants (V exists by PCP). Let r 1, r 2,..., r n d strings to F. be the set of all possible random Given an instance φ of SAT, we construct a graph G from F and φ which will be an instance of Clique. G has one vertex v ri,σ for each pair (i, σ), where r i is one of the the random strings r i and σ is a truth assignment to q variables. G has n d 2 q vertices. An accepting transcript for F on φ with random string r i is q pairs (p 1, a 1 ),..., (p q, a q ) s.t. for every truth assignment that has values a 1,..., a q for variables p 1,..., p q, verifier F given r i checks positions p 1,..., p q in that order and accepts. Once we have φ, r i, a 1,..., a q it is easy to compute p 1,..., p q. For each transcript we have a vertex. Two vertices (i, σ) and (i, σ ) are adjacent iff σ, σ don t assign different values to same variable, i.e. they are consistent, and both are accepting. 33
36 Hardness of Clique If φ is a yes instance then there is a proof (truth assignment) π such that F accepts (given π) on all random strings. For each r i, there is a corresponding σ (which has the same answers as in π) and is an accepting transcript. We have n d random strings and therefore there are n d vertices of G (corresponding to those). They form a clique because they come from the same truth assignment and so are consistent; Therefore G has a clique of size n d. For the case φ is a no instance we want to show that every clique in G has size at most nd 2. By way of contradiction suppose we have a clique C of size c > nd 2. Assume that (i 1, σ 1 )...(i c, σ c ) are the vertices in this clique. Therefore the transcripts σ 1...σ c (partial truth assignments) are all consistent. We can extend this truth assignment to a whole proof (truth assignment) such that on random strings i 1,..., i c, verifier V accepts. 34
37 Hardness of Clique Therefore the verifier accepts for more than nd 2 strings, which contradicts the assumption that φ is a no instance. So it is NP-hard to decide whether: G has a clique of size n d G every clique of G has size < nd 2 Note that the gap created here is exactly the soundness probability of the verifier; so the the smaller S is, the larger gap we get. By simulating a PCP 1, 1(d log n, q) verifier V for k 2 times and accepting iff all of those simulations accept, we get a PCP (k d log n, k q) verifier V 1, 1. 2 k Note that in this case the size of the construction G is n kd 2 kq, which is polynomial as long as k is constant. This will show a hardness of 2 k, which is a constant. Corollary 22 For any constant S, it is NP-hard to approximation clique within a factor of S (say S = 1/2 k in the above). 35
38 Hardness of Clique To get an n δ gap, we need S to be polynomially small, and for that we need to repeat k = Ω(log n) times. Therefore, k q = O(log n) which is Ok. But the length of random string becomes k log n = Ω(log 2 n), and the size of G becomes 2 Ω(log2 n), which is superpolynomial. To get a polynomial hardness we need a verifier. PCP 1, 1(O(log n), O(log n)) n The trick here is to start with only O(log n) random bits and use random walks on expander graphs to generate O(log n) random strings, each of length about log n. Definition 23 (Expander Graph) Every vertex has the same constant degree, say d, and for every nonempty set S V, E(S, S) min{ S, S }. 36
39 Hardness of Clique There are explicit construction of expander graphs. Let H be an expander graph with n d nodes. To each node we assign a label which is a binary string of length d log n. We can generate a random walk in H using only O(log n) random bits: need d log n bits to choose the first vertex, and need constant number of random bits to choose one neighbor at every step. Therefore, to have a random walk of length O(log n) in H we need only O(log n) bits. Theorem 24 For any set S of vertices of H with < nd vertices, there is a constant k such that the 2 probability that a random walk of length k log n lies entirely in S is < 1 n. Proof outline: By definition, if you have a set S of vertices, we expect a constant fraction of edges out of the vertices of S be going into S. Therefore, if you start a random walk from a vertex in S, at every step, there is a constant probability that this walk jumps into S. 37
40 Hardness of Clique So the probability that a random walk of length Ω(log n) stays entirely within S is polynomially small. Theorem 25 PCP 1, 1(d log n, q) PCP 2 1, 1(O(log n), O(log n)). n Proof: Let L PCP 1, 1(d log n, q) and F be a verifier 2 for L. We give a PCP 1, 1(O(log n), O(log n)) verifier F for n L. F builds the expander graph H of Theorem 24, then creates a random walk of length k log n using only O(log n) bits for some constant k This random walk yields k log n random string of length d log n each, which are the labels of the vertices of the walk. Then F simulates F on each of these strings and accepts if and only if all these simulations accept. If y L is a yes instance, then there is a proof π s.t. F accepts with probability 1 given π; so F accepts. 38
41 If y L is a no instance, then F accepts on at most nd of the random strings. 2 Let S be the set of vertices of H with those labels. Note that S nd 2. This means that F accepts (wrongly) y only if the entire random walk is inside S. Now, based on Theorem 24 the probability that a random walk remains entirely in S is at most 1 n Therefore, the probability that F most 1 n. accepts y is at This completes the proof of PCP 1, 1(d log n, q) PCP 2 1, 1(O(log n), O(log n)). n
42 Max-3SAT Theorem 26 For some δ > 0, it is NP-hard to approximate clique within a factor of Ω(n δ ). Proof: Given a SAT formula φ, let F be a PCP 1, 1(d log n, q log n) verifier for it for some constants d and n q. Construct the graph G from F in the same manner as we did earlier for the constant factor hardness. So the size of G is n d 2 q log n = n d+q and the gap created is equal to soundness probability, i.e. 1 n. we have: If φ is a yes instance then G has a clique of size n d. If φ is a no instance then every clique of G has size at most n d 1. This creates a gap of n δ with δ = 1 d+q. 39
43 Section 4: Hardness of Set Cover 40
44 Hardness of Set Cover Hardness of Set Cover Our final lecture is the outline of the proof of a hardness of O(log n) for Set cover. We need to define another problem: Label Cover. This is a graph theoric representation of another proof system for NP (2 prover 1 round proof system). An instance of label cover consists of the followings: G(V W, E) is a bipartite graph. [N] = {1...N}, [M] = {1...M} are 2 sets of labels, [N] for the vertices in V and [M] for the vertices in W. {Π v,w } (v,w) E denotes a (partial) function on every edge (v, w) such that Π v,w : [M] [N] A labeling l : V [N], W [M] is said to cover edge (v, w) if Π v,w (l(w)) = l(v). Goal: Given an instance of label cover, find a labeling that covers maximum fraction of the edge. 41
45 It follows from PCP theorem that: Hardness of Set Cover: Label cover Theorem 27 There is an absolute ɛ > 0 s.t. given an instance L(G, M = 7, N = 2, {Π v,w }) it is NPhard to decide if opt(l) = 1, or opt(l) 1 ɛ From an instance L(G(V, W, E), [M], [N ], {Π vw }), we obtain the k-power as following. we build L k (G (V, W, E ), [M ], [N ], {Π vw }) where: V = V k (k-tuples of V ) W = W k [M] = [M] k [N] = [N] k (V, W ) E (v ij, w ij ) E, i, j 1 j k (V = (v i1,..., v ik ), W = (w i1,..., w ik )) Π vw(b 1,..., b k ) = Π vi1,w i1 (b 1 ), Π vi2,w i2 (b 2 ),..., Π vik,w ik (b k ) 42
46 Hardness of Set Cover: Label cover Theorem 27, together with a strong result of Raz 98 implies the following: Theorem 28 There is a reduction from SAT to an instance L(G(V, W, E), [7 k ], [2 k ], {Π vw }) of label cover such that: if φ is a yes instance OPT(L) = 1 if φ is a no instance OPT(L) = 2 ck for some constant c < 1 and L = n O(k) We need one more definition. A set-system with parameters m and l consists of: U a universe (of elements) C 1,..., C m, C 1,..., C m are subsets of U For any set of l subsets from C i s and C i s that does not include a C j s and C j together, the union does not cover U. Theorem 29 Given m, l there are explicit constructions for a set system with U = O(l log m 2 l ). 43
47 Hardness of Set Cover Consider a label cover instance L(G(V, W, E), M = [7 k ], N = [2 k ], {Π v,w }). Let s assume V = W. set cover S such that: We build an instance of If opt(l) = 1, then opt(s) V + W. If opt(l) < 2, then opt(s) > l ( V + W ). l 2 16 Consider a set system with m = N = 2 k and l to be specified later. For every e = (v, w) G, we have a (disjoint) (m, l)- set system with universe U e. Let C vw 1,, Cvw N=m be the subsets of U e. The union of all U es (for all the edges e) is the universe of the set cover instance, denoted as U = U vw. w:(v,w) E (v,w) G Now we define the subsets. For every v V (w W ) and every label i [2 k ] (j [7 k ]), we have a set S v,i = Ci vw S w,j = v:(v,w) E C vw Π vw (j) 44
48 This completes the construction of S from L. Lemma 30 If opt(l) = 1, then opt(s) V + W. Proof: Consider an optimal labeling l : V [2 k ], W [7 k ] for L. Because it is covering every edge (v, w) E, Π vw (l(w)) = l(v). This labeling defines a label for every vertex and every pair of vertex/label corresponds to a set in S. From C vw l(v) S v,l(v) and C vw l(v) = Cvw Π vw (l(w)) S w,l(w): S v,l(v) S w,l(w) U vw. Because all U e s for e E are covered, U is covered. So we have a set cover of size V + W. Lemma 31 if opt(s) l ( V + W ), then 16 opt(l) 2. l 2 Proof: From the set cover solution, we assign labels (maybe more than one label) to the vertices. If S v,i is in the solution, v gets label i.
49 l Since there are ( V + W ) sets and V + W 16 vertices, the average number of labels per vertex is l 16. We discard vertices with > l 2 labels. V vertices from each of V and W are discarded. 4 Let V and W be the vertices remaining. so V > 3 4 V and W > 3 W. 4 Pick an edge e = (v, w) from G randomly. Pr[v V and w W ] 1 ( ) = 1 2. so 1 2 edges of G are between V and W. Define T v = {S v,i : i is a label of v} T w = {S w,j : j is a label of w}. We have T v l 2 and T w l 2.
50 Note that sets in T v T w cover U vw, i.e. Hardness of Set Cover X 1 = {Ci vw : i is a label of v} X 2 = {CΠ vw vw : j is a label of w} (j) covers universe U vw Since X 1 l 2 and X 2 l, a set Cvw 2 i CΠ vw vw (j) X 2 that are in X 1 X 2. X 1 and Because we pick labels of v and w randomly, with probability ( 2 l )2 = 4 we have set C vw l 2 i for v and Cj vw for w i.e. the labels i for v and j for w cover edge e E. Thus the expected fraction of edges between V and W that are covered is 4 l 2. Therefore, at least a fraction of 2 l covered. 2 of edges of G are This lemma is equivalent to saying that if opt(l) < 2 l 2 then opt(s) > l ( V + W ). 16 Thus we have: 45
51 If opt(l) = 1, then opt(s) V + W. If opt(l) < 2, then opt(s) > l ( V + W ). l 2 16 Let l Θ(2 δk 2 ). Then, l 2 Θ(2 δk ). We get a hardness of Ω(l) for S. The size of S is n O(k) O(l log m 2 l ). If k = c log log n for sufficiently large c, l = O(2 O(log log n) ) log n log log n. Thus log S = O(log log n log n+log l+log log log n+ l) = Θ(l). We have the following hardness result for set cover: Theorem 32 Unless NP DT IME(n O(log log n) ), set cover has no o(log n)-approximation algorithm.
PCPs and Inapproximability Gap-producing and Gap-Preserving Reductions. My T. Thai
 PCPs and Inapproximability Gap-producing and Gap-Preserving Reductions My T. Thai 1 1 Hardness of Approximation Consider a maximization problem Π such as MAX-E3SAT. To show that it is NP-hard to approximation
PCPs and Inapproximability Gap-producing and Gap-Preserving Reductions My T. Thai 1 1 Hardness of Approximation Consider a maximization problem Π such as MAX-E3SAT. To show that it is NP-hard to approximation
Notes for Lecture 2. Statement of the PCP Theorem and Constraint Satisfaction
 U.C. Berkeley Handout N2 CS294: PCP and Hardness of Approximation January 23, 2006 Professor Luca Trevisan Scribe: Luca Trevisan Notes for Lecture 2 These notes are based on my survey paper [5]. L.T. Statement
U.C. Berkeley Handout N2 CS294: PCP and Hardness of Approximation January 23, 2006 Professor Luca Trevisan Scribe: Luca Trevisan Notes for Lecture 2 These notes are based on my survey paper [5]. L.T. Statement
Lecture 18: PCP Theorem and Hardness of Approximation I
 Lecture 18: and Hardness of Approximation I Arijit Bishnu 26.04.2010 Outline 1 Introduction to Approximation Algorithm 2 Outline 1 Introduction to Approximation Algorithm 2 Approximation Algorithm Approximation
Lecture 18: and Hardness of Approximation I Arijit Bishnu 26.04.2010 Outline 1 Introduction to Approximation Algorithm 2 Outline 1 Introduction to Approximation Algorithm 2 Approximation Algorithm Approximation
A An Overview of Complexity Theory for the Algorithm Designer
 A An Overview of Complexity Theory for the Algorithm Designer A.1 Certificates and the class NP A decision problem is one whose answer is either yes or no. Two examples are: SAT: Given a Boolean formula
A An Overview of Complexity Theory for the Algorithm Designer A.1 Certificates and the class NP A decision problem is one whose answer is either yes or no. Two examples are: SAT: Given a Boolean formula
CS151 Complexity Theory. Lecture 15 May 22, 2017
 CS151 Complexity Theory Lecture 15 New topic(s) Optimization problems, Approximation Algorithms, and Probabilistically Checkable Proofs Optimization Problems many hard problems (especially NP-hard) are
CS151 Complexity Theory Lecture 15 New topic(s) Optimization problems, Approximation Algorithms, and Probabilistically Checkable Proofs Optimization Problems many hard problems (especially NP-hard) are
Limits to Approximability: When Algorithms Won't Help You. Note: Contents of today s lecture won t be on the exam
 Limits to Approximability: When Algorithms Won't Help You Note: Contents of today s lecture won t be on the exam Outline Limits to Approximability: basic results Detour: Provers, verifiers, and NP Graph
Limits to Approximability: When Algorithms Won't Help You Note: Contents of today s lecture won t be on the exam Outline Limits to Approximability: basic results Detour: Provers, verifiers, and NP Graph
Approximation Algorithms
 Approximation Algorithms What do you do when a problem is NP-complete? or, when the polynomial time solution is impractically slow? assume input is random, do expected performance. Eg, Hamiltonian path
Approximation Algorithms What do you do when a problem is NP-complete? or, when the polynomial time solution is impractically slow? assume input is random, do expected performance. Eg, Hamiltonian path
Approximation algorithm for Max Cut with unit weights
 Definition Max Cut Definition: Given an undirected graph G=(V, E), find a partition of V into two subsets A, B so as to maximize the number of edges having one endpoint in A and the other in B. Definition:
Definition Max Cut Definition: Given an undirected graph G=(V, E), find a partition of V into two subsets A, B so as to maximize the number of edges having one endpoint in A and the other in B. Definition:
Non-Approximability Results (2 nd part) 1/19
 Non-Approximability Results (2 nd part) 1/19 Summary - The PCP theorem - Application: Non-approximability of MAXIMUM 3-SAT 2/19 Non deterministic TM - A TM where it is possible to associate more than one
Non-Approximability Results (2 nd part) 1/19 Summary - The PCP theorem - Application: Non-approximability of MAXIMUM 3-SAT 2/19 Non deterministic TM - A TM where it is possible to associate more than one
NP Completeness and Approximation Algorithms
 Chapter 10 NP Completeness and Approximation Algorithms Let C() be a class of problems defined by some property. We are interested in characterizing the hardest problems in the class, so that if we can
Chapter 10 NP Completeness and Approximation Algorithms Let C() be a class of problems defined by some property. We are interested in characterizing the hardest problems in the class, so that if we can
NP-Completeness. Andreas Klappenecker. [based on slides by Prof. Welch]
![NP-Completeness. Andreas Klappenecker. [based on slides by Prof. Welch] NP-Completeness. Andreas Klappenecker. [based on slides by Prof. Welch]](/thumbs/79/79291182.jpg) NP-Completeness Andreas Klappenecker [based on slides by Prof. Welch] 1 Prelude: Informal Discussion (Incidentally, we will never get very formal in this course) 2 Polynomial Time Algorithms Most of the
NP-Completeness Andreas Klappenecker [based on slides by Prof. Welch] 1 Prelude: Informal Discussion (Incidentally, we will never get very formal in this course) 2 Polynomial Time Algorithms Most of the
Hardness of Directed Routing with Congestion
 Hardness of Directed Routing with Congestion Julia Chuzhoy Sanjeev Khanna August 28, 2006 Abstract Given a graph G and a collection of source-sink pairs in G, what is the least integer c such that each
Hardness of Directed Routing with Congestion Julia Chuzhoy Sanjeev Khanna August 28, 2006 Abstract Given a graph G and a collection of source-sink pairs in G, what is the least integer c such that each
Complexity Theory VU , SS The Polynomial Hierarchy. Reinhard Pichler
 Complexity Theory Complexity Theory VU 181.142, SS 2018 6. The Polynomial Hierarchy Reinhard Pichler Institut für Informationssysteme Arbeitsbereich DBAI Technische Universität Wien 15 May, 2018 Reinhard
Complexity Theory Complexity Theory VU 181.142, SS 2018 6. The Polynomial Hierarchy Reinhard Pichler Institut für Informationssysteme Arbeitsbereich DBAI Technische Universität Wien 15 May, 2018 Reinhard
Outline. Complexity Theory EXACT TSP. The Class DP. Definition. Problem EXACT TSP. Complexity of EXACT TSP. Proposition VU 181.
 Complexity Theory Complexity Theory Outline Complexity Theory VU 181.142, SS 2018 6. The Polynomial Hierarchy Reinhard Pichler Institut für Informationssysteme Arbeitsbereich DBAI Technische Universität
Complexity Theory Complexity Theory Outline Complexity Theory VU 181.142, SS 2018 6. The Polynomial Hierarchy Reinhard Pichler Institut für Informationssysteme Arbeitsbereich DBAI Technische Universität
Chapter 11. Approximation Algorithms. Slides by Kevin Wayne Pearson-Addison Wesley. All rights reserved.
 Chapter 11 Approximation Algorithms Slides by Kevin Wayne. Copyright @ 2005 Pearson-Addison Wesley. All rights reserved. 1 P and NP P: The family of problems that can be solved quickly in polynomial time.
Chapter 11 Approximation Algorithms Slides by Kevin Wayne. Copyright @ 2005 Pearson-Addison Wesley. All rights reserved. 1 P and NP P: The family of problems that can be solved quickly in polynomial time.
Lecture Hardness of Set Cover
 PCPs and Inapproxiability CIS 6930 October 5, 2009 Lecture Hardness of Set Cover Lecturer: Dr. My T. Thai Scribe: Ying Xuan 1 Preliminaries 1.1 Two-Prover-One-Round Proof System A new PCP model 2P1R Think
PCPs and Inapproxiability CIS 6930 October 5, 2009 Lecture Hardness of Set Cover Lecturer: Dr. My T. Thai Scribe: Ying Xuan 1 Preliminaries 1.1 Two-Prover-One-Round Proof System A new PCP model 2P1R Think
PCP Theorem and Hardness of Approximation
 PCP Theorem and Hardness of Approximation An Introduction Lee Carraher and Ryan McGovern Department of Computer Science University of Cincinnati October 27, 2003 Introduction Assuming NP P, there are many
PCP Theorem and Hardness of Approximation An Introduction Lee Carraher and Ryan McGovern Department of Computer Science University of Cincinnati October 27, 2003 Introduction Assuming NP P, there are many
P, NP, NP-Complete, and NPhard
 P, NP, NP-Complete, and NPhard Problems Zhenjiang Li 21/09/2011 Outline Algorithm time complicity P and NP problems NP-Complete and NP-Hard problems Algorithm time complicity Outline What is this course
P, NP, NP-Complete, and NPhard Problems Zhenjiang Li 21/09/2011 Outline Algorithm time complicity P and NP problems NP-Complete and NP-Hard problems Algorithm time complicity Outline What is this course
Topics in Theoretical Computer Science April 08, Lecture 8
 Topics in Theoretical Computer Science April 08, 204 Lecture 8 Lecturer: Ola Svensson Scribes: David Leydier and Samuel Grütter Introduction In this lecture we will introduce Linear Programming. It was
Topics in Theoretical Computer Science April 08, 204 Lecture 8 Lecturer: Ola Svensson Scribes: David Leydier and Samuel Grütter Introduction In this lecture we will introduce Linear Programming. It was
Lecture 20: LP Relaxation and Approximation Algorithms. 1 Introduction. 2 Vertex Cover problem. CSCI-B609: A Theorist s Toolkit, Fall 2016 Nov 8
 CSCI-B609: A Theorist s Toolkit, Fall 2016 Nov 8 Lecture 20: LP Relaxation and Approximation Algorithms Lecturer: Yuan Zhou Scribe: Syed Mahbub Hafiz 1 Introduction When variables of constraints of an
CSCI-B609: A Theorist s Toolkit, Fall 2016 Nov 8 Lecture 20: LP Relaxation and Approximation Algorithms Lecturer: Yuan Zhou Scribe: Syed Mahbub Hafiz 1 Introduction When variables of constraints of an
Advanced Algorithms (XIII) Yijia Chen Fudan University
 Advanced Algorithms (XIII) Yijia Chen Fudan University The PCP Theorem Theorem NP = PCP(log n, 1). Motivation Approximate solutions Definition (Approximation of MAX-3SAT) For every 3CNF formula ϕ, the
Advanced Algorithms (XIII) Yijia Chen Fudan University The PCP Theorem Theorem NP = PCP(log n, 1). Motivation Approximate solutions Definition (Approximation of MAX-3SAT) For every 3CNF formula ϕ, the
Lecture 15: A Brief Look at PCP
 IAS/PCMI Summer Session 2000 Clay Mathematics Undergraduate Program Basic Course on Computational Complexity Lecture 15: A Brief Look at PCP David Mix Barrington and Alexis Maciel August 4, 2000 1. Overview
IAS/PCMI Summer Session 2000 Clay Mathematics Undergraduate Program Basic Course on Computational Complexity Lecture 15: A Brief Look at PCP David Mix Barrington and Alexis Maciel August 4, 2000 1. Overview
Essential facts about NP-completeness:
 CMPSCI611: NP Completeness Lecture 17 Essential facts about NP-completeness: Any NP-complete problem can be solved by a simple, but exponentially slow algorithm. We don t have polynomial-time solutions
CMPSCI611: NP Completeness Lecture 17 Essential facts about NP-completeness: Any NP-complete problem can be solved by a simple, but exponentially slow algorithm. We don t have polynomial-time solutions
Complexity Theory. Jörg Kreiker. Summer term Chair for Theoretical Computer Science Prof. Esparza TU München
 Complexity Theory Jörg Kreiker Chair for Theoretical Computer Science Prof. Esparza TU München Summer term 2010 Lecture 19 Hardness of Approximation 3 Recap Recap: optimization many decision problems we
Complexity Theory Jörg Kreiker Chair for Theoretical Computer Science Prof. Esparza TU München Summer term 2010 Lecture 19 Hardness of Approximation 3 Recap Recap: optimization many decision problems we
Lecture 18: More NP-Complete Problems
 6.045 Lecture 18: More NP-Complete Problems 1 The Clique Problem a d f c b e g Given a graph G and positive k, does G contain a complete subgraph on k nodes? CLIQUE = { (G,k) G is an undirected graph with
6.045 Lecture 18: More NP-Complete Problems 1 The Clique Problem a d f c b e g Given a graph G and positive k, does G contain a complete subgraph on k nodes? CLIQUE = { (G,k) G is an undirected graph with
Lecture 6,7 (Sept 27 and 29, 2011 ): Bin Packing, MAX-SAT
 ,7 CMPUT 675: Approximation Algorithms Fall 2011 Lecture 6,7 (Sept 27 and 29, 2011 ): Bin Pacing, MAX-SAT Lecturer: Mohammad R. Salavatipour Scribe: Weitian Tong 6.1 Bin Pacing Problem Recall the bin pacing
,7 CMPUT 675: Approximation Algorithms Fall 2011 Lecture 6,7 (Sept 27 and 29, 2011 ): Bin Pacing, MAX-SAT Lecturer: Mohammad R. Salavatipour Scribe: Weitian Tong 6.1 Bin Pacing Problem Recall the bin pacing
Intro to Theory of Computation
 Intro to Theory of Computation LECTURE 25 Last time Class NP Today Polynomial-time reductions Adam Smith; Sofya Raskhodnikova 4/18/2016 L25.1 The classes P and NP P is the class of languages decidable
Intro to Theory of Computation LECTURE 25 Last time Class NP Today Polynomial-time reductions Adam Smith; Sofya Raskhodnikova 4/18/2016 L25.1 The classes P and NP P is the class of languages decidable
Chapter 11. Approximation Algorithms. Slides by Kevin Wayne Pearson-Addison Wesley. All rights reserved.
 Chapter 11 Approximation Algorithms Slides by Kevin Wayne. Copyright @ 2005 Pearson-Addison Wesley. All rights reserved. 1 Approximation Algorithms Q. Suppose I need to solve an NP-hard problem. What should
Chapter 11 Approximation Algorithms Slides by Kevin Wayne. Copyright @ 2005 Pearson-Addison Wesley. All rights reserved. 1 Approximation Algorithms Q. Suppose I need to solve an NP-hard problem. What should
Lecture 20: conp and Friends, Oracles in Complexity Theory
 6.045 Lecture 20: conp and Friends, Oracles in Complexity Theory 1 Definition: conp = { L L NP } What does a conp computation look like? In NP algorithms, we can use a guess instruction in pseudocode:
6.045 Lecture 20: conp and Friends, Oracles in Complexity Theory 1 Definition: conp = { L L NP } What does a conp computation look like? In NP algorithms, we can use a guess instruction in pseudocode:
Complexity Classes IV
 Complexity Classes IV NP Optimization Problems and Probabilistically Checkable Proofs Eric Rachlin 1 Decision vs. Optimization Most complexity classes are defined in terms of Yes/No questions. In the case
Complexity Classes IV NP Optimization Problems and Probabilistically Checkable Proofs Eric Rachlin 1 Decision vs. Optimization Most complexity classes are defined in terms of Yes/No questions. In the case
Geometric Steiner Trees
 Geometric Steiner Trees From the book: Optimal Interconnection Trees in the Plane By Marcus Brazil and Martin Zachariasen Part 3: Computational Complexity and the Steiner Tree Problem Marcus Brazil 2015
Geometric Steiner Trees From the book: Optimal Interconnection Trees in the Plane By Marcus Brazil and Martin Zachariasen Part 3: Computational Complexity and the Steiner Tree Problem Marcus Brazil 2015
Probabilistically Checkable Proofs. 1 Introduction to Probabilistically Checkable Proofs
 Course Proofs and Computers, JASS 06 Probabilistically Checkable Proofs Lukas Bulwahn May 21, 2006 1 Introduction to Probabilistically Checkable Proofs 1.1 History of Inapproximability Results Before introducing
Course Proofs and Computers, JASS 06 Probabilistically Checkable Proofs Lukas Bulwahn May 21, 2006 1 Introduction to Probabilistically Checkable Proofs 1.1 History of Inapproximability Results Before introducing
Limitations of Algorithm Power
 Limitations of Algorithm Power Objectives We now move into the third and final major theme for this course. 1. Tools for analyzing algorithms. 2. Design strategies for designing algorithms. 3. Identifying
Limitations of Algorithm Power Objectives We now move into the third and final major theme for this course. 1. Tools for analyzing algorithms. 2. Design strategies for designing algorithms. 3. Identifying
PROBABILISTIC CHECKING OF PROOFS AND HARDNESS OF APPROXIMATION
 PROBABILISTIC CHECKING OF PROOFS AND HARDNESS OF APPROXIMATION YOUNG KUN KO Abstract. This paper introduces basic notions of classic computational complexity theory and probabilistically checkable proof.
PROBABILISTIC CHECKING OF PROOFS AND HARDNESS OF APPROXIMATION YOUNG KUN KO Abstract. This paper introduces basic notions of classic computational complexity theory and probabilistically checkable proof.
CS154, Lecture 13: P vs NP
 CS154, Lecture 13: P vs NP The EXTENDED Church-Turing Thesis Everyone s Intuitive Notion of Efficient Algorithms Polynomial-Time Turing Machines More generally: TM can simulate every reasonable model of
CS154, Lecture 13: P vs NP The EXTENDED Church-Turing Thesis Everyone s Intuitive Notion of Efficient Algorithms Polynomial-Time Turing Machines More generally: TM can simulate every reasonable model of
Easy Problems vs. Hard Problems. CSE 421 Introduction to Algorithms Winter Is P a good definition of efficient? The class P
 Easy Problems vs. Hard Problems CSE 421 Introduction to Algorithms Winter 2000 NP-Completeness (Chapter 11) Easy - problems whose worst case running time is bounded by some polynomial in the size of the
Easy Problems vs. Hard Problems CSE 421 Introduction to Algorithms Winter 2000 NP-Completeness (Chapter 11) Easy - problems whose worst case running time is bounded by some polynomial in the size of the
Lecture 59 : Instance Compression and Succinct PCP s for NP
 IITM-CS6840: Advanced Complexity Theory March 31, 2012 Lecture 59 : Instance Compression and Succinct PCP s for NP Lecturer: Sivaramakrishnan N.R. Scribe: Prashant Vasudevan 1 Introduction Classical Complexity
IITM-CS6840: Advanced Complexity Theory March 31, 2012 Lecture 59 : Instance Compression and Succinct PCP s for NP Lecturer: Sivaramakrishnan N.R. Scribe: Prashant Vasudevan 1 Introduction Classical Complexity
1 Agenda. 2 History. 3 Probabilistically Checkable Proofs (PCPs). Lecture Notes Definitions. PCPs. Approximation Algorithms.
 CS 221: Computational Complexity Prof. Salil Vadhan Lecture Notes 20 April 12, 2010 Scribe: Jonathan Pines 1 Agenda. PCPs. Approximation Algorithms. PCPs = Inapproximability. 2 History. First, some history
CS 221: Computational Complexity Prof. Salil Vadhan Lecture Notes 20 April 12, 2010 Scribe: Jonathan Pines 1 Agenda. PCPs. Approximation Algorithms. PCPs = Inapproximability. 2 History. First, some history
CS154, Lecture 15: Cook-Levin Theorem SAT, 3SAT
 CS154, Lecture 15: Cook-Levin Theorem SAT, 3SAT Definition: A language B is NP-complete if: 1. B NP 2. Every A in NP is poly-time reducible to B That is, A P B When this is true, we say B is NP-hard On
CS154, Lecture 15: Cook-Levin Theorem SAT, 3SAT Definition: A language B is NP-complete if: 1. B NP 2. Every A in NP is poly-time reducible to B That is, A P B When this is true, we say B is NP-hard On
Lecture 19: Interactive Proofs and the PCP Theorem
 Lecture 19: Interactive Proofs and the PCP Theorem Valentine Kabanets November 29, 2016 1 Interactive Proofs In this model, we have an all-powerful Prover (with unlimited computational prover) and a polytime
Lecture 19: Interactive Proofs and the PCP Theorem Valentine Kabanets November 29, 2016 1 Interactive Proofs In this model, we have an all-powerful Prover (with unlimited computational prover) and a polytime
CS154, Lecture 13: P vs NP
 CS154, Lecture 13: P vs NP The EXTENDED Church-Turing Thesis Everyone s Intuitive Notion of Efficient Algorithms Polynomial-Time Turing Machines More generally: TM can simulate every reasonable model of
CS154, Lecture 13: P vs NP The EXTENDED Church-Turing Thesis Everyone s Intuitive Notion of Efficient Algorithms Polynomial-Time Turing Machines More generally: TM can simulate every reasonable model of
Chapter 2. Reductions and NP. 2.1 Reductions Continued The Satisfiability Problem (SAT) SAT 3SAT. CS 573: Algorithms, Fall 2013 August 29, 2013
 Chapter 2 Reductions and NP CS 573: Algorithms, Fall 2013 August 29, 2013 2.1 Reductions Continued 2.1.1 The Satisfiability Problem SAT 2.1.1.1 Propositional Formulas Definition 2.1.1. Consider a set of
Chapter 2 Reductions and NP CS 573: Algorithms, Fall 2013 August 29, 2013 2.1 Reductions Continued 2.1.1 The Satisfiability Problem SAT 2.1.1.1 Propositional Formulas Definition 2.1.1. Consider a set of
Some Algebra Problems (Algorithmic) CSE 417 Introduction to Algorithms Winter Some Problems. A Brief History of Ideas
 Some Algebra Problems (Algorithmic) CSE 417 Introduction to Algorithms Winter 2006 NP-Completeness (Chapter 8) Given positive integers a, b, c Question 1: does there exist a positive integer x such that
Some Algebra Problems (Algorithmic) CSE 417 Introduction to Algorithms Winter 2006 NP-Completeness (Chapter 8) Given positive integers a, b, c Question 1: does there exist a positive integer x such that
Lecture 18: P & NP. Revised, May 1, CLRS, pp
 Lecture 18: P & NP Revised, May 1, 2003 CLRS, pp.966-982 The course so far: techniques for designing efficient algorithms, e.g., divide-and-conquer, dynamic-programming, greedy-algorithms. What happens
Lecture 18: P & NP Revised, May 1, 2003 CLRS, pp.966-982 The course so far: techniques for designing efficient algorithms, e.g., divide-and-conquer, dynamic-programming, greedy-algorithms. What happens
Approximation Basics
 Approximation Basics, Concepts, and Examples Xiaofeng Gao Department of Computer Science and Engineering Shanghai Jiao Tong University, P.R.China Fall 2012 Special thanks is given to Dr. Guoqiang Li for
Approximation Basics, Concepts, and Examples Xiaofeng Gao Department of Computer Science and Engineering Shanghai Jiao Tong University, P.R.China Fall 2012 Special thanks is given to Dr. Guoqiang Li for
A Threshold of ln(n) for approximating set cover
 A Threshold of ln(n) for approximating set cover October 20, 2009 1 The k-prover proof system There is a single verifier V and k provers P 1, P 2,..., P k. Binary code with k codewords, each of length
A Threshold of ln(n) for approximating set cover October 20, 2009 1 The k-prover proof system There is a single verifier V and k provers P 1, P 2,..., P k. Binary code with k codewords, each of length
i times p(p(... (p( n))...) = n ki.
 Chapter 7 NP Completeness Exercise 7.1 Show that an algorithm that makes at most a constant number of calls to polynomial-time subroutines runs in polynomial time, but that a polynomial number of calls
Chapter 7 NP Completeness Exercise 7.1 Show that an algorithm that makes at most a constant number of calls to polynomial-time subroutines runs in polynomial time, but that a polynomial number of calls
P,NP, NP-Hard and NP-Complete
 P,NP, NP-Hard and NP-Complete We can categorize the problem space into two parts Solvable Problems Unsolvable problems 7/11/2011 1 Halting Problem Given a description of a program and a finite input, decide
P,NP, NP-Hard and NP-Complete We can categorize the problem space into two parts Solvable Problems Unsolvable problems 7/11/2011 1 Halting Problem Given a description of a program and a finite input, decide
Lecturer: Shuchi Chawla Topic: Inapproximability Date: 4/27/2007
 CS880: Approximations Algorithms Scribe: Tom Watson Lecturer: Shuchi Chawla Topic: Inapproximability Date: 4/27/2007 So far in this course, we have been proving upper bounds on the approximation factors
CS880: Approximations Algorithms Scribe: Tom Watson Lecturer: Shuchi Chawla Topic: Inapproximability Date: 4/27/2007 So far in this course, we have been proving upper bounds on the approximation factors
NP-Complete Problems. More reductions
 NP-Complete Problems More reductions Definitions P: problems that can be solved in polynomial time (typically in n, size of input) on a deterministic Turing machine Any normal computer simulates a DTM
NP-Complete Problems More reductions Definitions P: problems that can be solved in polynomial time (typically in n, size of input) on a deterministic Turing machine Any normal computer simulates a DTM
CS 151 Complexity Theory Spring Solution Set 5
 CS 151 Complexity Theory Spring 2017 Solution Set 5 Posted: May 17 Chris Umans 1. We are given a Boolean circuit C on n variables x 1, x 2,..., x n with m, and gates. Our 3-CNF formula will have m auxiliary
CS 151 Complexity Theory Spring 2017 Solution Set 5 Posted: May 17 Chris Umans 1. We are given a Boolean circuit C on n variables x 1, x 2,..., x n with m, and gates. Our 3-CNF formula will have m auxiliary
Almost transparent short proofs for NP R
 Brandenburgische Technische Universität, Cottbus, Germany From Dynamics to Complexity: A conference celebrating the work of Mike Shub Toronto, May 10, 2012 Supported by DFG under GZ:ME 1424/7-1 Outline
Brandenburgische Technische Universität, Cottbus, Germany From Dynamics to Complexity: A conference celebrating the work of Mike Shub Toronto, May 10, 2012 Supported by DFG under GZ:ME 1424/7-1 Outline
2 Completing the Hardness of approximation of Set Cover
 CSE 533: The PCP Theorem and Hardness of Approximation (Autumn 2005) Lecture 15: Set Cover hardness and testing Long Codes Nov. 21, 2005 Lecturer: Venkat Guruswami Scribe: Atri Rudra 1 Recap We will first
CSE 533: The PCP Theorem and Hardness of Approximation (Autumn 2005) Lecture 15: Set Cover hardness and testing Long Codes Nov. 21, 2005 Lecturer: Venkat Guruswami Scribe: Atri Rudra 1 Recap We will first
CMPUT 675: Approximation Algorithms Fall 2014
 CMPUT 675: Approximation Algorithms Fall 204 Lecture 25 (Nov 3 & 5): Group Steiner Tree Lecturer: Zachary Friggstad Scribe: Zachary Friggstad 25. Group Steiner Tree In this problem, we are given a graph
CMPUT 675: Approximation Algorithms Fall 204 Lecture 25 (Nov 3 & 5): Group Steiner Tree Lecturer: Zachary Friggstad Scribe: Zachary Friggstad 25. Group Steiner Tree In this problem, we are given a graph
Lecture 10: Hardness of approximating clique, FGLSS graph
 CSE 533: The PCP Theorem and Hardness of Approximation (Autumn 2005) Lecture 10: Hardness of approximating clique, FGLSS graph Nov. 2, 2005 Lecturer: Venkat Guruswami and Ryan O Donnell Scribe: Ioannis
CSE 533: The PCP Theorem and Hardness of Approximation (Autumn 2005) Lecture 10: Hardness of approximating clique, FGLSS graph Nov. 2, 2005 Lecturer: Venkat Guruswami and Ryan O Donnell Scribe: Ioannis
1 Computational Problems
 Stanford University CS254: Computational Complexity Handout 2 Luca Trevisan March 31, 2010 Last revised 4/29/2010 In this lecture we define NP, we state the P versus NP problem, we prove that its formulation
Stanford University CS254: Computational Complexity Handout 2 Luca Trevisan March 31, 2010 Last revised 4/29/2010 In this lecture we define NP, we state the P versus NP problem, we prove that its formulation
BBM402-Lecture 11: The Class NP
 BBM402-Lecture 11: The Class NP Lecturer: Lale Özkahya Resources for the presentation: http://ocw.mit.edu/courses/electrical-engineering-andcomputer-science/6-045j-automata-computability-andcomplexity-spring-2011/syllabus/
BBM402-Lecture 11: The Class NP Lecturer: Lale Özkahya Resources for the presentation: http://ocw.mit.edu/courses/electrical-engineering-andcomputer-science/6-045j-automata-computability-andcomplexity-spring-2011/syllabus/
Umans Complexity Theory Lectures
 New topic(s) Umans Complexity Theory Lectures Lecture 15: Approximation Algorithms and Probabilistically Checable Proos (PCPs) Optimization problems,, and Probabilistically Checable Proos 2 Optimization
New topic(s) Umans Complexity Theory Lectures Lecture 15: Approximation Algorithms and Probabilistically Checable Proos (PCPs) Optimization problems,, and Probabilistically Checable Proos 2 Optimization
NP-COMPLETE PROBLEMS. 1. Characterizing NP. Proof
 T-79.5103 / Autumn 2006 NP-complete problems 1 NP-COMPLETE PROBLEMS Characterizing NP Variants of satisfiability Graph-theoretic problems Coloring problems Sets and numbers Pseudopolynomial algorithms
T-79.5103 / Autumn 2006 NP-complete problems 1 NP-COMPLETE PROBLEMS Characterizing NP Variants of satisfiability Graph-theoretic problems Coloring problems Sets and numbers Pseudopolynomial algorithms
Approximation Preserving Reductions
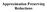 Approximation Preserving Reductions - Memo Summary - AP-reducibility - L-reduction technique - Complete problems - Examples: MAXIMUM CLIQUE, MAXIMUM INDEPENDENT SET, MAXIMUM 2-SAT, MAXIMUM NAE 3-SAT, MAXIMUM
Approximation Preserving Reductions - Memo Summary - AP-reducibility - L-reduction technique - Complete problems - Examples: MAXIMUM CLIQUE, MAXIMUM INDEPENDENT SET, MAXIMUM 2-SAT, MAXIMUM NAE 3-SAT, MAXIMUM
Increasing the Span of Stars
 Increasing the Span of Stars Ning Chen Roee Engelberg C. Thach Nguyen Prasad Raghavendra Atri Rudra Gynanit Singh Department of Computer Science and Engineering, University of Washington, Seattle, WA.
Increasing the Span of Stars Ning Chen Roee Engelberg C. Thach Nguyen Prasad Raghavendra Atri Rudra Gynanit Singh Department of Computer Science and Engineering, University of Washington, Seattle, WA.
CS151 Complexity Theory. Lecture 6 April 19, 2017
 CS151 Complexity Theory Lecture 6 Shannon s counting argument frustrating fact: almost all functions require huge circuits Theorem (Shannon): With probability at least 1 o(1), a random function f:{0,1}
CS151 Complexity Theory Lecture 6 Shannon s counting argument frustrating fact: almost all functions require huge circuits Theorem (Shannon): With probability at least 1 o(1), a random function f:{0,1}
Lecture 8 (Notes) 1. The book Computational Complexity: A Modern Approach by Sanjeev Arora and Boaz Barak;
 Topics in Theoretical Computer Science April 18, 2016 Lecturer: Ola Svensson Lecture 8 (Notes) Scribes: Ola Svensson Disclaimer: These notes were written for the lecturer only and may contain inconsistent
Topics in Theoretical Computer Science April 18, 2016 Lecturer: Ola Svensson Lecture 8 (Notes) Scribes: Ola Svensson Disclaimer: These notes were written for the lecturer only and may contain inconsistent
Complexity Classes V. More PCPs. Eric Rachlin
 Complexity Classes V More PCPs Eric Rachlin 1 Recall from last time Nondeterminism is equivalent to having access to a certificate. If a valid certificate exists, the machine accepts. We see that problems
Complexity Classes V More PCPs Eric Rachlin 1 Recall from last time Nondeterminism is equivalent to having access to a certificate. If a valid certificate exists, the machine accepts. We see that problems
PCP Theorem And Hardness Of Approximation For MAX-SATISFY Over Finite Fields
 MM Research Preprints KLMM, AMSS, Academia Sinica Vol. 7, 1 15, July, 008 1 PCP Theorem And Hardness Of Approximation For MAX-SATISFY Over Finite Fields Shangwei Zhao Key Laboratory of Mathematics Mechanization
MM Research Preprints KLMM, AMSS, Academia Sinica Vol. 7, 1 15, July, 008 1 PCP Theorem And Hardness Of Approximation For MAX-SATISFY Over Finite Fields Shangwei Zhao Key Laboratory of Mathematics Mechanization
Notes for Lecture Notes 2
 Stanford University CS254: Computational Complexity Notes 2 Luca Trevisan January 11, 2012 Notes for Lecture Notes 2 In this lecture we define NP, we state the P versus NP problem, we prove that its formulation
Stanford University CS254: Computational Complexity Notes 2 Luca Trevisan January 11, 2012 Notes for Lecture Notes 2 In this lecture we define NP, we state the P versus NP problem, we prove that its formulation
Design and Analysis of Algorithms
 Design and Analysis of Algorithms CSE 5311 Lecture 25 NP Completeness Junzhou Huang, Ph.D. Department of Computer Science and Engineering CSE5311 Design and Analysis of Algorithms 1 NP-Completeness Some
Design and Analysis of Algorithms CSE 5311 Lecture 25 NP Completeness Junzhou Huang, Ph.D. Department of Computer Science and Engineering CSE5311 Design and Analysis of Algorithms 1 NP-Completeness Some
Polynomial kernels for constant-factor approximable problems
 1 Polynomial kernels for constant-factor approximable problems Stefan Kratsch November 11, 2010 2 What do these problems have in common? Cluster Edge Deletion, Cluster Edge Editing, Edge Dominating Set,
1 Polynomial kernels for constant-factor approximable problems Stefan Kratsch November 11, 2010 2 What do these problems have in common? Cluster Edge Deletion, Cluster Edge Editing, Edge Dominating Set,
CS 350 Algorithms and Complexity
 1 CS 350 Algorithms and Complexity Fall 2015 Lecture 15: Limitations of Algorithmic Power Introduction to complexity theory Andrew P. Black Department of Computer Science Portland State University Lower
1 CS 350 Algorithms and Complexity Fall 2015 Lecture 15: Limitations of Algorithmic Power Introduction to complexity theory Andrew P. Black Department of Computer Science Portland State University Lower
1 Randomized Computation
 CS 6743 Lecture 17 1 Fall 2007 1 Randomized Computation Why is randomness useful? Imagine you have a stack of bank notes, with very few counterfeit ones. You want to choose a genuine bank note to pay at
CS 6743 Lecture 17 1 Fall 2007 1 Randomized Computation Why is randomness useful? Imagine you have a stack of bank notes, with very few counterfeit ones. You want to choose a genuine bank note to pay at
Lecture 11 October 7, 2013
 CS 4: Advanced Algorithms Fall 03 Prof. Jelani Nelson Lecture October 7, 03 Scribe: David Ding Overview In the last lecture we talked about set cover: Sets S,..., S m {,..., n}. S has cost c S. Goal: Cover
CS 4: Advanced Algorithms Fall 03 Prof. Jelani Nelson Lecture October 7, 03 Scribe: David Ding Overview In the last lecture we talked about set cover: Sets S,..., S m {,..., n}. S has cost c S. Goal: Cover
On the efficient approximability of constraint satisfaction problems
 On the efficient approximability of constraint satisfaction problems July 13, 2007 My world Max-CSP Efficient computation. P Polynomial time BPP Probabilistic Polynomial time (still efficient) NP Non-deterministic
On the efficient approximability of constraint satisfaction problems July 13, 2007 My world Max-CSP Efficient computation. P Polynomial time BPP Probabilistic Polynomial time (still efficient) NP Non-deterministic
ACO Comprehensive Exam October 14 and 15, 2013
 1. Computability, Complexity and Algorithms (a) Let G be the complete graph on n vertices, and let c : V (G) V (G) [0, ) be a symmetric cost function. Consider the following closest point heuristic for
1. Computability, Complexity and Algorithms (a) Let G be the complete graph on n vertices, and let c : V (G) V (G) [0, ) be a symmetric cost function. Consider the following closest point heuristic for
NP-Complete Reductions 2
 x 1 x 1 x 2 x 2 x 3 x 3 x 4 x 4 12 22 32 CS 447 11 13 21 23 31 33 Algorithms NP-Complete Reductions 2 Prof. Gregory Provan Department of Computer Science University College Cork 1 Lecture Outline NP-Complete
x 1 x 1 x 2 x 2 x 3 x 3 x 4 x 4 12 22 32 CS 447 11 13 21 23 31 33 Algorithms NP-Complete Reductions 2 Prof. Gregory Provan Department of Computer Science University College Cork 1 Lecture Outline NP-Complete
HW11. Due: December 6, 2018
 CSCI 1010 Theory of Computation HW11 Due: December 6, 2018 Attach a fully filled-in cover sheet to the front of your printed homework. Your name should not appear anywhere; the cover sheet and each individual
CSCI 1010 Theory of Computation HW11 Due: December 6, 2018 Attach a fully filled-in cover sheet to the front of your printed homework. Your name should not appear anywhere; the cover sheet and each individual
1 Primals and Duals: Zero Sum Games
 CS 124 Section #11 Zero Sum Games; NP Completeness 4/15/17 1 Primals and Duals: Zero Sum Games We can represent various situations of conflict in life in terms of matrix games. For example, the game shown
CS 124 Section #11 Zero Sum Games; NP Completeness 4/15/17 1 Primals and Duals: Zero Sum Games We can represent various situations of conflict in life in terms of matrix games. For example, the game shown
Lecture 4: An FPTAS for Knapsack, and K-Center
 Comp 260: Advanced Algorithms Tufts University, Spring 2016 Prof. Lenore Cowen Scribe: Eric Bailey Lecture 4: An FPTAS for Knapsack, and K-Center 1 Introduction Definition 1.0.1. The Knapsack problem (restated)
Comp 260: Advanced Algorithms Tufts University, Spring 2016 Prof. Lenore Cowen Scribe: Eric Bailey Lecture 4: An FPTAS for Knapsack, and K-Center 1 Introduction Definition 1.0.1. The Knapsack problem (restated)
NP-completeness. Chapter 34. Sergey Bereg
 NP-completeness Chapter 34 Sergey Bereg Oct 2017 Examples Some problems admit polynomial time algorithms, i.e. O(n k ) running time where n is the input size. We will study a class of NP-complete problems
NP-completeness Chapter 34 Sergey Bereg Oct 2017 Examples Some problems admit polynomial time algorithms, i.e. O(n k ) running time where n is the input size. We will study a class of NP-complete problems
P is the class of problems for which there are algorithms that solve the problem in time O(n k ) for some constant k.
 Complexity Theory Problems are divided into complexity classes. Informally: So far in this course, almost all algorithms had polynomial running time, i.e., on inputs of size n, worst-case running time
Complexity Theory Problems are divided into complexity classes. Informally: So far in this course, almost all algorithms had polynomial running time, i.e., on inputs of size n, worst-case running time
NP-Completeness. Subhash Suri. May 15, 2018
 NP-Completeness Subhash Suri May 15, 2018 1 Computational Intractability The classical reference for this topic is the book Computers and Intractability: A guide to the theory of NP-Completeness by Michael
NP-Completeness Subhash Suri May 15, 2018 1 Computational Intractability The classical reference for this topic is the book Computers and Intractability: A guide to the theory of NP-Completeness by Michael
CS151 Complexity Theory
 Introduction CS151 Complexity Theory Lecture 5 April 13, 2004 Power from an unexpected source? we know PEXP, which implies no polytime algorithm for Succinct CVAL poly-size Boolean circuits for Succinct
Introduction CS151 Complexity Theory Lecture 5 April 13, 2004 Power from an unexpected source? we know PEXP, which implies no polytime algorithm for Succinct CVAL poly-size Boolean circuits for Succinct
CS5314 Randomized Algorithms. Lecture 18: Probabilistic Method (De-randomization, Sample-and-Modify)
 CS5314 Randomized Algorithms Lecture 18: Probabilistic Method (De-randomization, Sample-and-Modify) 1 Introduce two topics: De-randomize by conditional expectation provides a deterministic way to construct
CS5314 Randomized Algorithms Lecture 18: Probabilistic Method (De-randomization, Sample-and-Modify) 1 Introduce two topics: De-randomize by conditional expectation provides a deterministic way to construct
Asymptotic Polynomial-Time Approximation (APTAS) and Randomized Approximation Algorithms
 Approximation Algorithms Asymptotic Polynomial-Time Approximation (APTAS) and Randomized Approximation Algorithms Jens Egeblad November 29th, 2006 Agenda First lesson (Asymptotic Approximation): Bin-Packing
Approximation Algorithms Asymptotic Polynomial-Time Approximation (APTAS) and Randomized Approximation Algorithms Jens Egeblad November 29th, 2006 Agenda First lesson (Asymptotic Approximation): Bin-Packing
CS 583: Algorithms. NP Completeness Ch 34. Intractability
 CS 583: Algorithms NP Completeness Ch 34 Intractability Some problems are intractable: as they grow large, we are unable to solve them in reasonable time What constitutes reasonable time? Standard working
CS 583: Algorithms NP Completeness Ch 34 Intractability Some problems are intractable: as they grow large, we are unable to solve them in reasonable time What constitutes reasonable time? Standard working
Lecture 15 - NP Completeness 1
 CME 305: Discrete Mathematics and Algorithms Instructor: Professor Aaron Sidford (sidford@stanford.edu) February 29, 2018 Lecture 15 - NP Completeness 1 In the last lecture we discussed how to provide
CME 305: Discrete Mathematics and Algorithms Instructor: Professor Aaron Sidford (sidford@stanford.edu) February 29, 2018 Lecture 15 - NP Completeness 1 In the last lecture we discussed how to provide
DD2446 Complexity Theory: Problem Set 4
 DD2446 Complexity Theory: Problem Set 4 Due: Friday November 8, 2013, at 23:59. Submit your solutions as a PDF le by e-mail to jakobn at kth dot se with the subject line Problem set 4: your full name.
DD2446 Complexity Theory: Problem Set 4 Due: Friday November 8, 2013, at 23:59. Submit your solutions as a PDF le by e-mail to jakobn at kth dot se with the subject line Problem set 4: your full name.
Some Algebra Problems (Algorithmic) CSE 417 Introduction to Algorithms Winter Some Problems. A Brief History of Ideas
 CSE 417 Introduction to Algorithms Winter 2007 Some Algebra Problems (Algorithmic) Given positive integers a, b, c Question 1: does there exist a positive integer x such that ax = c? NP-Completeness (Chapter
CSE 417 Introduction to Algorithms Winter 2007 Some Algebra Problems (Algorithmic) Given positive integers a, b, c Question 1: does there exist a positive integer x such that ax = c? NP-Completeness (Chapter
DRAFT. PCP and Hardness of Approximation. Chapter 19
 Chapter 19 PCP and Hardness of Approximation...most problem reductions do not create or preserve such gaps...to create such a gap in the generic reduction (cf. Cook)...also seems doubtful. The intuitive
Chapter 19 PCP and Hardness of Approximation...most problem reductions do not create or preserve such gaps...to create such a gap in the generic reduction (cf. Cook)...also seems doubtful. The intuitive
Dual fitting approximation for Set Cover, and Primal Dual approximation for Set Cover
 duality 1 Dual fitting approximation for Set Cover, and Primal Dual approximation for Set Cover Guy Kortsarz duality 2 The set cover problem with uniform costs Input: A universe U and a collection of subsets
duality 1 Dual fitting approximation for Set Cover, and Primal Dual approximation for Set Cover Guy Kortsarz duality 2 The set cover problem with uniform costs Input: A universe U and a collection of subsets
Efficient Approximation for Restricted Biclique Cover Problems
 algorithms Article Efficient Approximation for Restricted Biclique Cover Problems Alessandro Epasto 1, *, and Eli Upfal 2 ID 1 Google Research, New York, NY 10011, USA 2 Department of Computer Science,
algorithms Article Efficient Approximation for Restricted Biclique Cover Problems Alessandro Epasto 1, *, and Eli Upfal 2 ID 1 Google Research, New York, NY 10011, USA 2 Department of Computer Science,
More on NP and Reductions
 Indian Institute of Information Technology Design and Manufacturing, Kancheepuram Chennai 600 127, India An Autonomous Institute under MHRD, Govt of India http://www.iiitdm.ac.in COM 501 Advanced Data
Indian Institute of Information Technology Design and Manufacturing, Kancheepuram Chennai 600 127, India An Autonomous Institute under MHRD, Govt of India http://www.iiitdm.ac.in COM 501 Advanced Data
Algorithms: COMP3121/3821/9101/9801
 NEW SOUTH WALES Algorithms: COMP3121/3821/9101/9801 Aleks Ignjatović School of Computer Science and Engineering University of New South Wales LECTURE 9: INTRACTABILITY COMP3121/3821/9101/9801 1 / 29 Feasibility
NEW SOUTH WALES Algorithms: COMP3121/3821/9101/9801 Aleks Ignjatović School of Computer Science and Engineering University of New South Wales LECTURE 9: INTRACTABILITY COMP3121/3821/9101/9801 1 / 29 Feasibility
Show that the following problems are NP-complete
 Show that the following problems are NP-complete April 7, 2018 Below is a list of 30 exercises in which you are asked to prove that some problem is NP-complete. The goal is to better understand the theory
Show that the following problems are NP-complete April 7, 2018 Below is a list of 30 exercises in which you are asked to prove that some problem is NP-complete. The goal is to better understand the theory
Lecture 12: Interactive Proofs
 princeton university cos 522: computational complexity Lecture 12: Interactive Proofs Lecturer: Sanjeev Arora Scribe:Carl Kingsford Recall the certificate definition of NP. We can think of this characterization
princeton university cos 522: computational complexity Lecture 12: Interactive Proofs Lecturer: Sanjeev Arora Scribe:Carl Kingsford Recall the certificate definition of NP. We can think of this characterization
Graduate Algorithms CS F-21 NP & Approximation Algorithms
 Graduate Algorithms CS673-2016F-21 NP & Approximation Algorithms David Galles Department of Computer Science University of San Francisco 21-0: Classes of Problems Consider three problem classes: Polynomial
Graduate Algorithms CS673-2016F-21 NP & Approximation Algorithms David Galles Department of Computer Science University of San Francisco 21-0: Classes of Problems Consider three problem classes: Polynomial
Discrete Optimization 2010 Lecture 10 P, N P, and N PCompleteness
 Discrete Optimization 2010 Lecture 10 P, N P, and N PCompleteness Marc Uetz University of Twente m.uetz@utwente.nl Lecture 9: sheet 1 / 31 Marc Uetz Discrete Optimization Outline 1 N P and co-n P 2 N P-completeness
Discrete Optimization 2010 Lecture 10 P, N P, and N PCompleteness Marc Uetz University of Twente m.uetz@utwente.nl Lecture 9: sheet 1 / 31 Marc Uetz Discrete Optimization Outline 1 N P and co-n P 2 N P-completeness
1 PSPACE-Completeness
 CS 6743 Lecture 14 1 Fall 2007 1 PSPACE-Completeness Recall the NP-complete problem SAT: Is a given Boolean formula φ(x 1,..., x n ) satisfiable? The same question can be stated equivalently as: Is the
CS 6743 Lecture 14 1 Fall 2007 1 PSPACE-Completeness Recall the NP-complete problem SAT: Is a given Boolean formula φ(x 1,..., x n ) satisfiable? The same question can be stated equivalently as: Is the
CS 5114: Theory of Algorithms. Tractable Problems. Tractable Problems (cont) Decision Problems. Clifford A. Shaffer. Spring 2014
 Department of Computer Science Virginia Tech Blacksburg, Virginia Copyright c 2014 by Clifford A. Shaffer : Theory of Algorithms Title page : Theory of Algorithms Clifford A. Shaffer Spring 2014 Clifford
Department of Computer Science Virginia Tech Blacksburg, Virginia Copyright c 2014 by Clifford A. Shaffer : Theory of Algorithms Title page : Theory of Algorithms Clifford A. Shaffer Spring 2014 Clifford
Fundamentals of optimization problems
 Fundamentals of optimization problems Dmitriy Serdyuk Ferienakademie in Sarntal 2012 FAU Erlangen-Nürnberg, TU München, Uni Stuttgart September 2012 Overview 1 Introduction Optimization problems PO and
Fundamentals of optimization problems Dmitriy Serdyuk Ferienakademie in Sarntal 2012 FAU Erlangen-Nürnberg, TU München, Uni Stuttgart September 2012 Overview 1 Introduction Optimization problems PO and
