Universal Traversal Sequences with Backtracking
|
|
|
- Lora Nelson
- 5 years ago
- Views:
Transcription
1 Universal Traversal Sequences with Backtracking Michal Koucký Department of Computer Science Rutgers University, Piscataway NJ 08854, USA April 9, 001 Abstract In this paper we introduce a new notion of traversal sequences that we call exploration sequences. Exploration sequences share many properties with the traversal sequences defined in [AKL+], but they also exhibit some new properties. In particular, they have an ability to backtrack, and their random properties are robust under choice of the probability distribution on labels. Further, we present extremely simple constructions of polynomial length universal exploration sequences for some previously studied classes of graphs (e.g., -regular graphs, cliques, expanders), and we also present universal exploration sequences for trees. Our constructions beat previously known lower-bounds on the length of universal traversal sequences. 1 Introduction The s-t-connectivity problem has drawn a lot of attention in computer science. One direction of study is aimed at investigating the space complexity of this problem. It is known that the directed version of this problem is complete for nondeterministic log-space (NL), and its undirected version is complete for symmetric log-space (SL), which is defined to be the class of problems logspace reducible to undirected s-t-connectivity. It is conjectured that symmetric log-space is equal to deterministic log-space (SL = L.) The main evidence supporting this conjecture is the existence of short universal traversal sequences, that were introduced by Cook and studied in [A], and [AKL+], and the success of derandomization techniques applied to random walk algorithm putting SL into DSPACE(log 4/3 n), [NSW], [SZ], and [ATWZ]. A traversal sequence is a sequence which guides a walk in a graph. It is known that with high probability a sequence of length O(d n 3 log n) chosen uniformly at random guides a walk in any undirected d-regular connected graph Supported in part by NSF grant CCR
2 in such a way that all vertices are visited. A sequence with this property is called a universal traversal sequence (UTS). If there is a universal traversal sequence constructible in log-space then the s-t-connectivity problem is in logspace, hence, SL = L. Explicit universal traversal sequences for -regular graphs were constructed in [BBK+], [B], [I], [K], for cliques in [KPS], and for expanders in [HW]. The sequences in [BBK+], [B], and [KPS] are of length n O(log n), thus they are not log-space constructible. On the other hand, the sequences constructed in [I], [K], and [HW] are of polynomial length, and they are log-space constructible. However, the construction for expanders in [HW] requires the graph to be labeled consistently. [HW] does not address the question of finding such a labeling in small space, although it is known that this problem can be reduced to finding a perfect matching in a bipartite graph. The only known explicit constructions of UTS s of subexponential length for 3-regular graphs are based on pseudo-random generators for randomized logspace, [BNS], [N], [INW]. The pseudo-random generator presented in [BNS] yields a UTS of length 0( n), and the pseudo-random generators presented in [N] and [INW] yield UTS s of length n O(log n). We introduce a new type of traversal sequences that we call exploration sequences. We show that exploration sequences have the same useful properties as traversal sequences, and moreover, they also exhibit a new property - the ability to backtrack. Using that new ability we construct universal exploration sequences (UXS) for some classes of graphs. These UXS s beat lower-bounds on the length of UTS s for cycles and cliques given by [BBK+], [AAR], [T], and [BT]. Under our definition it can be shown, that a random exploration sequence of length O(d n 3 log n) is a UXS for d-regular graphs with high probability. Thus, constructions of UTS s of length n O(log n) for 3-regular graphs that are based on pseudo-random generators apply to UXS s, too. Also the results of [NSW], and [ATWZ] can be formulated in terms of exploration sequences, as well as other results on random traversal sequences. In particular, the strengthening of the upper-bound on the length of non-uniform UTS s of [KLNS], and [CRR+] apply to UXS s, too. Beside that, random exploration sequences exhibit robustness under the choice of probability distribution on labels. Our definition is motivated by the following. If we are told that we reach a vertex v in a graph following a traversal sequence t, it is impossible in principle to determine where the walk started (or even to tell what vertex was visited immediately previously to v). This ambiguity does not occur if the labeling of the graph is consistent as required for the construction of [HW]. However, in neither of these cases is there a traversal sequence that depends only on t and that brings us back from v to the starting vertex. In contrast, with exploration sequences we can have such a sequence, we can backtrack. That gives us a lot of power.
3 1.1 Definitions, basic properties, and explicit constructions Let G be an undirected graph. A labeling l of G is a map assigning to every vertex v and every edge e incident to v a label l(e, v) {0,..., deg(v) 1}, so that for every two distinct edges e, e incident to v, l(e, v) l(e, v). (A labeling would be consistent if for every vertex v, and every two distinct edges {v, u}, {v, w}, l({v, u}, u) l({v, w}, w).) In our new notion, during a walk on G guided by an exploration sequence t, digits of t will be interpreted as labels relative to the edge by which we got to the vertex. In contrast, in definition of traversal sequences of [AKL+], digits of t are interpreted directly as edge labels. More formally: Let l be a labeling of G. Let e E(G), and v e. We say that i N takes us from the pair (e, v) to a pair (e, v ), if e = {v, v } and l(e, v) = l(e, v) + i mod deg(v). We denote that by (e, v) i (e, v ). (Intuitively, pair (e, v) corresponds to being at v s end of edge e.) The symbol Λ denotes the empty move, i.e., (e, v) Λ (e, v). For t (N {Λ}), we extend the notation to (e, v) t (e, v ) in obvious way. We say that t visits a vertex u starting at (e, v) if there is a prefix t of t and an edge e u incident to u, such that (e, v) t (e u, u). We call sequence t an exploration sequence. (If t contains symbol Λ then it is a general exploration sequence, otherwise it is simple.) Let G be a class of connected undirected graphs. We say that an exploration sequence t is a universal exploration sequence for G, if for every G G and every labeling of G, t visits every vertex in G starting at any pair (e, v), where e E(G) and v e. For comparison, in our terms, the traversal sequences defined in [AKL+] require l(e, v) = i rather than l(e, v) = l(e, v) + i moddeg(v), when choosing where to go next according to i. There is also another minor technical difference that we go from one edge vertex pair to another edge vertex pair whereas, in [AKL+] you go from one vertex to another vertex. Let d > 1 be an integer, and t {0,..., d 1}, where t = t 1 t t k. We define a backtrack t of t to be the sequence t k t k 1 t 1, where t i = (d t i )mod d. We state the following theorem, that is rather a proposition for its simplicity. Theorem 1 (Backtracking Theorem) Let d > 1 be an integer. Let s, t {0,..., d 1}. Then there is an exploration sequence t = 0t0 such that for any d-regular graph G, and any labeling of G the following holds. If e E(G), v e, and (e, v) s (e, v ) then (e, v) stt (e, v ). The proof by induction on the length of t is very simple, and we leave it as an exercise. Note, we defined backtracking only for simple exploration sequences but it can be easily extended to general exploration sequences. The following theorem says that like a random traversal sequence, a random exploration sequence of sufficient length is a UXS. 3
4 Theorem Let d > 1 be an integer, and let n > 1 be an integer. With high probability, a sequence chosen uniformly at random from {0,...,d 1} O(d n 3 log n) is a universal exploration sequence for d-regular graphs on n vertices. This theorem follows from the fact that with high probability, a general exploration sequence of length O(d n 3 log n) chosen uniformly at random is a UXS for d-regular graphs on n vertices. This fact can be proven in exactly the same way as the equivalent theorem for traversal sequences (see [AKL+]), since regardless of whether we are walking using the traversal sequences or the exploration sequences, the next edge is chosen uniformly at random among the incident edges. (Λ guarantees aperiodicity.) (This result can be strengthened using [KLNS], and [CRR+], for example.) Clearly, if we could construct a UXS of polynomial length for 3-regular graphs in log-space, we could conclude SL = L. Unfortunately, we do not have such a construction, yet. Rather, we present simple constructions of UXS s for previously studied classes of graphs. Let us first note, that the constructions of [KPS], and [HW] can be liftedup, and reformulated in the terms of the exploration sequences using the backtracking ability. This reformulation is possible, although technically complicated, so we do not do that. Rather we present new UXS s. Proposition 3 1 n is a UXS for cycles of length n. Proposition 4 (10) n is a UXS for cliques of size n. For expanders, we have to work a little bit harder (for an appropriate definition of expanders see, e.g., [HW].) Define s 0 = 0, and, for h 1, define recursively s h = 1s h 1 1s h 1 1, and t h = s h 1 1s h 1 1s h 1 1. Theorem 5 t O(log n) is a UXS for 3-regular expanders. As in [HW], the expansion factor of the expander is hidden in O(log n). Theorem 5 easily follows from the following more general theorem. Theorem 6 t h is a UXS for 3-regular graphs with maximum distance (diameter) at most h. Both Theorems 5 and 6 can be also formulated for d-regular graphs, where d 3. Define s 0 d = 0, for h 1, define sh d = 1(sh 1 d 1) d 1, and t h d = (sh 1 d 1) d. O(log n) Sequence td is a UXS for d-regular expanders of size n. Note, that the length of t k d is less than dk, hence, the UXS for d-regular expanders is of length n O(log d). The UTS for expanders, which is presented in [HW], is of length n O(d log d). The proof of Theorem 6 uses the following two lemmas. Lemma 7 Let G be a 3-regular graph. For any integer h, and any edge e = {v, u} of G, (e, v) sh (e, u). 4
5 Proof: The proof is by induction on h. For h = 0, the lemma is trivial. Assume h > 0. s h = 1s h 1 1s h 1 1 and G is 3-regular, so by the induction hypothesis we get (e, v) 1 (e 1, v 1 ) sh 1 (e 1, v) 1 (e, v ) sh 1 (e, v) 1 (e, u), where e 1 = {v, v 1 }, and e = {v, v } for some vertices v 1 and v. Lemma 8 Let G be a 3-regular graph. Let T be a rooted binary spanning subtree of G with root r, and let the edge incident with r that does not belong to T be e r. Let the depth of T be h 0. Then for all h h 0, s h visits all vertices of T starting at (e r, r), and (e r, r) sh (e r, r ), where e r = {r, r }. Proof: From the previous lemma it follows, that (e r, r) sh (e r, r ), hence, we only need to verify that all vertices in T are visited. We prove it by induction on h 0. For h 0 = 0, the lemma is trivial, so consider h 0 > 0. Let h h 0 be arbitrary. Let e 1 = {r, v 1 }, and e = {r, v }, so that (e, r) 1 (e 1, v 1 ) and (e 1, r) 1 (e, v ). Clearly, (e, r) 1 (e r, r ). By the previous lemma, (e r, r) 1 (e 1, v 1 ) sh 1 (e 1, r) 1 (e, v ) sh 1 (e, r) 1 (e r, r ). By the induction hypothesis, the first s h 1 visits all vertices in the subtree of T rooted in v 1 starting at (e 1, v 1 ), and the other s h 1 visits all vertices in the subtree of T rooted in v starting at (e, v ). (These subtrees may be actually empty.) Hence, all vertices in T are visited. Proof of Theorem 6: Let G be any 3-regular graph with a diameter at most h, let e E(G), and v e. We need to show that t h visits all vertices in G starting at (e, v). G has diameter at most h, hence it contains a spanning tree T of depth at most h rooted in v (e.g., a breadth first search tree.) T can be partitioned into three subtrees each of them rooted in a distinct neighbor of v, plus a single vertex v. Each of the subtrees is of depth at most h 1, so by the previous lemma, it is completely traversed by s h 1 starting at the edge connecting v with the root of the subtree. It easily follows that all vertices of G are visited by t h. Further, we present a polynomial length UXS for trees. Note, there is no known explicit polynomial length UTS for trees. Proposition 9 1 n is a UTS for trees of size n. Note, Propositions 3 and 4 in conjunction with known super-linear lowerbounds on the length of universal traversal sequences for cycles and cliques suggest that exploration sequences are most likely substantially more powerful than traversal sequences. Notice, the UXS s constructed in this section are sequences from {0, 1}. Theorems of the following section show that we can restrict the alphabet of exploration sequences for traversal of any graph. 5
6 1. Unbalanced probability distributions on labels In this section we show that random exploration sequences are robust under the choice of the probability distribution on labels. That implies that we can use a biased source of randomness for randomized s-t-connectivity algorithm. Let us first show that the traversal sequences are not robust under the choice of the probability distribution on labels. Consider a labeled graph G in Figure 1. It is a 3-regular undirected graph on n vertices v u Figure 1. Consider a random walk on G, where at every step of the walk the edge labeled by 0 is chosen with probability 1/, the edge labeled by 1 is chosen with probability 1/4, and the edge labeled by is chosen with probability 1/4. Such a distribution is naturally obtained by a transformation of two independent uniformly distributed random bits r i and r i+1 into a number from {0, 1, } using formula (r i + r i+1 )mod 3. It is straightforward to verify that the stationary distribution of the random walk is not uniform. Moreover, the probability of being at vertex v is exponentially small. (If p i denotes the probability of being at the top i-th vertex (or the bottom one, the graph is symmetric) then p = p 1 /3, p n = p n 1 /3, and for 1 < i < n, p i = p i 1 /.) Hence, the expected recurrence time of v is exponential in n. We claim that the following cannot happen: there is a polynomial p(n) and a constant k > 0, such that for any n > 1 and any G on n vertices, the probability of visiting v by a random walk of length p(n) starting at any vertex of G different from v is at least 1/n k. Suppose on contrary that this may happen. Then by amplification, there is a polynomial p (n), such that a random walk of length p (n) visits v starting from any vertex of G different from v with probability at least 1/. But that would imply that the recurrence time of v would be O(p (n)), in contradiction to the fact that the recurrence time of v is exponential in n. To see this, note that a random walk starting from v revisits v with probability at least 1/ within the first p (n)+1 steps, within the next p (n) steps it revisits v with probability at least 1/4 if it was not revisited before, and so on. Thus, the standard randomized log-space algorithm for s-t-connectivity, that performs a polynomial length random walk on a graph, will produce incorrect answers using the biased distribution on labels. The following theorem asserts that this is not the case if we perform the random walk using relative labeling. 6
7 Theorem 10 Let d be an integer. Let D be a probability distribution on {0,..., d 1}, such that there exist 0 r < q < d, for which G.C.D.(q r, d) = 1, and r and q occur with positive probabilities under D. Then there is a constant c > 0 such that for any integer n > 1, for every connected d-regular graph G on n vertices, and every labeling of G, the following holds. If e E(G) and v e, then with probability at least 1/, a random walk of length cd n 3 starting at (e, v), where at every step of the walk the next relative label is chosen according to D, visits all vertices of G. Note, the constant c depends on D. To establish the theorem we need the following lemma which assures that all vertices are reachable under D. Lemma 11 Let d, and let integers 0 r < q < d satisfy that G.C.D.(q r, d) = 1. Let G be any connected d-regular graph, and let l be its labeling. Then e, e E(G), v e, and v e, there exists t {r, q} E(G) such that (e, v) t (e, v ). Proof: Let r, q and G be given. Fix a pair (e, v). We want to show that any other pair (e, v ) is reachable by a sequence consisting of only r s and q s. (Note, if it is reachable then it is also reachable by an exploration sequence of length at most E(G).) For u V (G), define the in-degree and out-degree of u as follows: and d + (u) = {{u, w} E(G); t {1, } ; (e, v) t ({u, w}, u)}, d (u) = {{u, w} E(G); t {1, } ; (e, v) t ({u, w}, w)}. We claim that for any u V (G), d + (u) d (u). Moreover, d + (u) < d (u), unless d + (u) = d (u) = d. We prove this claim. Fix u V (G), and define the sets of incoming and outgoing edge labels: and L + (u) = {l({u, w}, u); {u, w} E(G); t {1, } ; (e, v) t ({u, w}, u)}, L (u) = {l({u, w}, u); {u, w} E(G); t {1, } ; (e, v) t ({u, w}, w)}. Observe, d + (u) = L + (u), and d (u) = L (u). Clearly, x L + (u), x + r L (u), where the arithmetic is done modulo d. Hence, L + (u) L (u), which implies that d + (u) d (u). For the second part of the claim: L + (u) = L (u) x L + (u), y L + (u) such that x + q = y + r x L + (u), y L + (u) such that y = x + q r a {0,...,d 1} such that {a + (q r)b; b {0,...,d 1}} L + (u), where all arithmetic is done modulo d. If G.C.D.(q r, d) = 1, then {a + (q r)b; b {0,...,d 1}} = 7
8 {0,..., d 1}. Hence, d + (u) = d (u) implies that L + (u) = {0,..., d 1} and d + (u) = d (u) = d, which establishes the claim. Clearly, u V d +(u) = u V d (u). Hence, if there were a vertex w such that d + (w) < d, then there would have to be a vertex w such that d + (w ) > d (w ), which would be a contradiction. Thus, for all v V (G), d + (v ) = d, which means that all pairs (e, v ) are reachable from (e, v). Note, the key property in the previous lemma is that for every u V (G), G.C.D.(q r, deg u) = 1. Hence, if q = r + 1 then the lemma holds for any graph, not only for d-regular. Proof of Theorem 10: Let D, n, G, e, v be given. Instead of considering a traversal of G by a random simple exploration sequence, we consider a traversal of G by a random general exploration sequence, i.e., we allow also Λ to be chosen. We define a probability distribution D ǫ on {Λ, 0,..., d 1} as follows: Pr x Dǫ [x = Λ] = ǫ, and for every i {0,..., d 1}, Pr x Dǫ [x = i] = (1 ǫ)pr x D [x = i], where we set ǫ = 1/4. Let us consider a random walk on G during which distribution D ǫ is used for choosing a label at every step of the walk. This random walk corresponds to a Markov chain with the set of states S = {(e, v); e E(G), v e}. The previous lemma implies that this Markov chain is irreducible, and the non-zero probability of Λ implies that the chain is aperiodic. Hence, it has a stationary distribution. It is easy to verify that this stationary distribution is uniform. Thus for every i S, the expected recurrence time T i,i = S = E(G). (For background on Markov chains see [IM] or [AF].) The previous lemma implies that there is t {r, q} of length m E(G) V (G), such that t visits all vertices in G starting at (e, v). Let t = t 1 t t m, where t 1, t,...,t m {q, r}. Let i 0, i 1,...,i m S be such that (e, v) = i 0 t1 i 1 t i tm i m. We want to upper bound the expected time of a walk that visits i 1, i,..., i m in this order starting from i 0 and ending at i m. (Some i j s may be the same.) We use the following two lemmas. Lemma 1 Let i 0, i 1,..., i m be a sequence of states of a finite state, irreducible, aperiodic Markov chain M. Then the expected time ET of visiting states i 1, i,...,i m in this order starting from i 0 satisfies: ET = j=0 T ij,i j+1, where T ij,i j+1 is the expected time of the first visit to state i j+1 starting from i j. A variation of this lemma can be found in [AF]. We give the proof of this lemma in the appendix. Lemma 13 Let i and j be states of a finite state, irreducible, aperiodic Markov chain M. Let p i,j > 0 be the transition probability of going from i to j. Then the expected time T i,j of the first visit to j starting from i satisfies: T i,j T i,i /p i,j, where T i,i is the recurrence time of i. 8
9 We give the proof of this lemma in the appendix, too. Thus in our setting, for all j {0,..., m 1}, T ij,i j+1 T ij,i j /p ij,i j+1, where T ij,i j = E(G). Let γ ǫ = min{pr x Dǫ [x = r], Pr x Dǫ [x = q]}. Clearly, p ij,i j+1 γ ǫ. Hence by Lemma 1, the expected time to visit all states i 1, i,..., i m in this order starting at i 0 is at most γǫ 1 E(G) m 4γǫ 1 d n 3. Set c = 8γǫ 1. By the Markov inequality, with probability at least 1/, a random walk starting at (e, v) of length l = cd n 3 visits all vertices of G. This is a random walk according to D ǫ. It is easy to observe that with at least the same probability, a random walk according to D starting at (e, v) visits all vertices of G. (1/ Pr t D l ǫ [t visits all vertices of G] = l i=0 ( l i) ǫ i (1 ǫ) l i Pr t D l i[t visits all vertices of G]. The result follows by noting that for any j l, Pr t D j[t visits all vertices of G] Pr t D l[t visits all vertices of G].) By the same argument as in [AKL+], Theorem 10 implies, that for l = cd 3 n 4 log n, an exploration sequence, that is chosen randomly from {0,...,d 1} l according to distribution D l, is a UXS for d-regular graphs, with high probability. The following theorem can also be viewed as an unbalanced probability distribution on labels. Theorem 14 Let r 0 and n > 1 be integers. With high probability, a sequence chosen uniformly at random from {r, r + 1} O(n7 log n) is a universal exploration sequence for graphs on n vertices. This theorem is a consequence of the next theorem which can be viewed as a generalization of Theorem 10 for all graphs. The proof of that theorem is similar to the proof of Theorem 10, hence the proof is omitted. Theorem 15 Let r 0 be an integer. Then there is a constant c > 0 such that for any integer n > 1, for every connected graph G on n vertices, and every labeling of G, the following holds. If e E(G) and v e, then with probability at least 1/, a random walk of length cn 5 starting at (e, v), where at every step of the walk the next relative label is chosen uniformly at random from {r, r + 1}, visits all vertices of G. Note, the last theorem can be further generalized for r and r + 1 to have different probabilities. Conclusion We have shown that properly defined traversal sequences may have surprising computational power, in particular, they can backtrack. Can they compute something more? In particular, can we convert any s-t-connectivity algorithm into a universal exploration sequence, e.g., the one of [ATWZ] running in space O(log 4/3 n)? (Such a possibility could allow us to further optimize the existing connectivity algorithms.) At this point, we don t know the answer. 9
10 3 Acknowledgments I would like to thank to Eric Allender, Navin Goyal, Jeff Kahn, János Komlós, Sachin Lodha, Dieter van Melkebeek, Mike Saks, and Venkatesh Srinivasan for helpful discussions. I am grateful to Eric Allender for comments on preliminary versions of this paper and for proposing the term exploration sequences. I would like to thank also to the anonymous referee for valuable comments. References [AF] D. Aldous, and J. A. Fill, Reversible Markov Chains and Random Walks on Graphs, manuscript, users/aldous/book.html. [A] R. Aleliunas, A simple graph traversing problem, Master s Thesis, University of Toronto, 1978 (Technical Report 0). [AKL+] R. Aleliunas, R. M. Karp, R. J. Lipton, L. Lovász, and C. Rackoff, Random walks, universal traversal sequences, and the complexity of maze problems, FOCS 0, pp. 18-3, [AAR] N. Alon, Y. Azar, and Y. Ravid, Universal sequences for complete graphs, Discrete Appl. Math, 7, pp. 5-8, [ATWZ] R. Armoni, A. Ta-Shma, A. Wigderson, and S. Zhou, SL L 4/3, STOC 9, pp , [BNS] L. Babai, N. Nisan, and M. Szegedy, Multiparty Protocols and Logspacehard Pseudorandom Sequences (Extended Abstract), STOC 1, pp. 1-11, [BBK+] A. Bar-Noy, A. Borodin, M. Karchmer, N. Linial, and M. Werman, Bounds on universal sequences, SIAM J. Comput., 18(), pp , [BRT] A. Borodin, W. L. Ruzzo, and M. Tompa, Lower bounds on the length of traversal sequences, J. of Comp. and Syst. Sci., 45(), pp , 199. [B] M. F. Bridgland, Universal traversal sequences for paths and cycles, J. of Alg., 8(3), pp , [BT] J. Buss, and M. Tompa, Lower bounds on universal traversal sequences based on chains of length five, Inf. and Comp., 10(), pp , [CRR+] A. K. Chandra, P. Raghavan, W. L. Ruzzo, R. Smolensky, and P. Tiwari, The electrical resistance of a graph captures its commute and cover times, STOC 1, pp , [HW] S. Hoory, and A. Wigderson, Universal traversal sequences for expander graphs, Inf. Proc. Letters, 46(), pp ,
11 [INW] R. Impagliazzo, N. Nisan, and A. Wigderson, Pseudorandomness for Network Algorithms, STOC 6, pp , [IM] Isaacson, D. L., and Madsen, R. W., Markov chains, theory and applications, Wiley, [I] S. Istrail, Polynomial universal traversing sequences for cycles are constructible (extended abstract), STOC 0, pp , [KLNS] J. D. Kahn, N. Linial, N. Nisan, and M. E. Saks, On the cover time of random walks on graphs, J. of Theor. Probab., (1), pp , [KPS] H. J. Karloff, R. Paturi, and J, Simon, Universal traversal sequences of length n O(logn) for cliques. Inf. Proc. Letters, 8(5), pp , [K] M. Koucký, Log-space constructible universal traversal sequences for cycles of length O(n 4.03 ), ECCC-TR01-13, 001. [N] N. Nisan, Pseudorandom Generators for Space-bounded Computation, Combinatorica, 1(4), pp , 199. [NSW] N. Nisan, E. Szemerédi, and A. Wigderson, Undirected Connectivity in O(log 1.5 n) Space, FOCS 33, pp. 4-9, 199. [SZ] M. Saks, and S. Zhou, RSPACE(S) DSPACE(S 3/ ), FOCS 36, pp , [T] M. Tompa, Lower bounds on universal traversal sequences for cycles and other low degree graphs, SIAM J. Comput., 1(6), pp ,
12 A Appendix Lemma 1 Let i 0, i 1,..., i m be a sequence of states of a finite state, irreducible, aperiodic Markov chain M. Then the expected time ET of visiting states i 1, i,...,i m in this order starting from i 0 satisfies: ET = j=0 T ij,i j+1, where T ij,i j+1 is the expected time of the first visit to state i j+1 starting from i j. A variation of this lemma can be found in [AF]. Proof: Note, all states of a finite state, irreducible, aperiodic Markov chain M are positive persistent, so k>0 f(k) i,j = 1, where i, j are states of M, and f (k) i,j is the probability of first visit to j starting from i at time k. In the following we use Fubini-like theorems for manipulating with infinite sums. They are applicable because all values that we are working with are non-negative. Let b 0, b 1, b,..., b l be states of M. Then: f (a1) b 0,b 1 f (a) b 1,b f (a l) b l 1,b l = (a 1,a,...,a l ) N l f (a1) b 0,b 1 Now: a 1 N a N f (a) b 1,b a l N f (a l) b l 1,b l = 1. ET = m (a 1 + a + + a m ) f (a d) a N m d=1 = m (a a ) f (a d) + a N m d=1 = = = a m N + f (am) i,i m ( a N d=1 a N j=1 a j f (a d) ) a m N (a a ) a N d=1 (a a ) a N d=1 d=1 m a m a N m d=1 f (a d) a m f (am) i,i m = = T i0,i 1 + T i1,i + + T i,i m. f (a d) + a m N f (a d) + T i,i m f (a d) a m f (am) i,i m 1
13 Lemma 13 Let i and j be states of a finite state, irreducible, aperiodic Markov chain M. Let p i,j > 0 be the transition probability of going from i to j. Then the expected time T i,j of the first visit to j starting from i satisfies: T i,j T i,i /p i,j, where T i,i is the recurrence time of i. Proof: Let S be the set of states of Markov chain M. Let p s,t denote the transition probability from s to t in M, and let T s,t denote the expected time of the first visit to t starting from s. Let us modify Markov chain M by adding an extra state j, i.e., S = S {j }, and defining the transition probabilities p s,t to be the same as in M but p i,j = p i,j, p i,j = 0, p s,j = 0, for all s S {j } {i}, and p j,s = p j,s, for all s S. Denote this new Markov chain by M. It is easy to verify that M is irreducible and aperiodic, too. (We assume here that p s,j > 0, for some s i. If that is not the case, we use similar argument as below for M = M. In our setting, it is always true that p s,j > 0 for some s i.) Let π be the stationary distribution of M, and let π be the stationary distribution of M. It is straightforward to verify, that for all s S {j}, π (s) = π(s), π (j ) = p i,j π(i), and π (j) = π(j) p i,j π(i). Hence, the recurrence time of j in M satisfies T j,j = 1/p i,jπ(i) = T i,i /p i,j. It is easy to verify that T j,j = T i,j + T j,i thus, T i,i/p i,j is an upper bound on T i,j. T i,j exactly corresponds to the expected time of first reaching j using the transition from i to j starting the walk from i in M. Hence, T i,j is an upper bound on T i,j. Thus, T i,j T i,j T i,i/p i,j. 13
Universal Traversal Sequences for Expander Graphs
 Universal Traversal Sequences for Expander Graphs Shlomo Hoory Avi Wigderson Hebrew University, Jerusalem Keywords: Universal traversal sequence, space-bounded computation, explicit construction, connectivity,
Universal Traversal Sequences for Expander Graphs Shlomo Hoory Avi Wigderson Hebrew University, Jerusalem Keywords: Universal traversal sequence, space-bounded computation, explicit construction, connectivity,
Randomized Time Space Tradeoffs for Directed Graph Connectivity
 Randomized Time Space Tradeoffs for Directed Graph Connectivity Parikshit Gopalan, Richard Lipton, and Aranyak Mehta College of Computing, Georgia Institute of Technology, Atlanta GA 30309, USA. Email:
Randomized Time Space Tradeoffs for Directed Graph Connectivity Parikshit Gopalan, Richard Lipton, and Aranyak Mehta College of Computing, Georgia Institute of Technology, Atlanta GA 30309, USA. Email:
Pseudorandom Generators for Regular Branching Programs
 Pseudorandom Generators for Regular Branching Programs Mark Braverman Anup Rao Ran Raz Amir Yehudayoff Abstract We give new pseudorandom generators for regular read-once branching programs of small width.
Pseudorandom Generators for Regular Branching Programs Mark Braverman Anup Rao Ran Raz Amir Yehudayoff Abstract We give new pseudorandom generators for regular read-once branching programs of small width.
The power and weakness of randomness (when you are short on time) Avi Wigderson Institute for Advanced Study
 The power and weakness of randomness (when you are short on time) Avi Wigderson Institute for Advanced Study Plan of the talk Computational complexity -- efficient algorithms, hard and easy problems, P
The power and weakness of randomness (when you are short on time) Avi Wigderson Institute for Advanced Study Plan of the talk Computational complexity -- efficient algorithms, hard and easy problems, P
Generating random spanning trees. Andrei Broder. DEC - Systems Research Center 130 Lytton Ave., Palo Alto, CA
 Generating random spanning trees Andrei Broder DEC - Systems Research Center 30 Lytton Ave., Palo Alto, CA 9430 Extended abstract Abstract. This paper describes a probabilistic algorithm that, given a
Generating random spanning trees Andrei Broder DEC - Systems Research Center 30 Lytton Ave., Palo Alto, CA 9430 Extended abstract Abstract. This paper describes a probabilistic algorithm that, given a
Probability & Computing
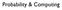 Probability & Computing Stochastic Process time t {X t t 2 T } state space Ω X t 2 state x 2 discrete time: T is countable T = {0,, 2,...} discrete space: Ω is finite or countably infinite X 0,X,X 2,...
Probability & Computing Stochastic Process time t {X t t 2 T } state space Ω X t 2 state x 2 discrete time: T is countable T = {0,, 2,...} discrete space: Ω is finite or countably infinite X 0,X,X 2,...
Pseudorandom Generators for Regular Branching Programs
 Pseudorandom Generators for Regular Branching Programs Mark Braverman Anup Rao Ran Raz Amir Yehudayoff Abstract We give new pseudorandom generators for regular read-once branching programs of small width.
Pseudorandom Generators for Regular Branching Programs Mark Braverman Anup Rao Ran Raz Amir Yehudayoff Abstract We give new pseudorandom generators for regular read-once branching programs of small width.
Notes on Space-Bounded Complexity
 U.C. Berkeley CS172: Automata, Computability and Complexity Handout 6 Professor Luca Trevisan 4/13/2004 Notes on Space-Bounded Complexity These are notes for CS278, Computational Complexity, scribed by
U.C. Berkeley CS172: Automata, Computability and Complexity Handout 6 Professor Luca Trevisan 4/13/2004 Notes on Space-Bounded Complexity These are notes for CS278, Computational Complexity, scribed by
Notes on Space-Bounded Complexity
 U.C. Berkeley CS172: Automata, Computability and Complexity Handout 7 Professor Luca Trevisan April 14, 2015 Notes on Space-Bounded Complexity These are notes for CS278, Computational Complexity, scribed
U.C. Berkeley CS172: Automata, Computability and Complexity Handout 7 Professor Luca Trevisan April 14, 2015 Notes on Space-Bounded Complexity These are notes for CS278, Computational Complexity, scribed
Deterministic approximation for the cover time of trees
 Deterministic approximation for the cover time of trees Uriel Feige Ofer Zeitouni September 10, 2009 Abstract We present a deterministic algorithm that given a tree T with n vertices, a starting vertex
Deterministic approximation for the cover time of trees Uriel Feige Ofer Zeitouni September 10, 2009 Abstract We present a deterministic algorithm that given a tree T with n vertices, a starting vertex
PRGs for space-bounded computation: INW, Nisan
 0368-4283: Space-Bounded Computation 15/5/2018 Lecture 9 PRGs for space-bounded computation: INW, Nisan Amnon Ta-Shma and Dean Doron 1 PRGs Definition 1. Let C be a collection of functions C : Σ n {0,
0368-4283: Space-Bounded Computation 15/5/2018 Lecture 9 PRGs for space-bounded computation: INW, Nisan Amnon Ta-Shma and Dean Doron 1 PRGs Definition 1. Let C be a collection of functions C : Σ n {0,
U.C. Berkeley CS278: Computational Complexity Professor Luca Trevisan 9/6/2004. Notes for Lecture 3
 U.C. Berkeley CS278: Computational Complexity Handout N3 Professor Luca Trevisan 9/6/2004 Notes for Lecture 3 Revised 10/6/04 1 Space-Bounded Complexity Classes A machine solves a problem using space s(
U.C. Berkeley CS278: Computational Complexity Handout N3 Professor Luca Trevisan 9/6/2004 Notes for Lecture 3 Revised 10/6/04 1 Space-Bounded Complexity Classes A machine solves a problem using space s(
1 Random Walks and Electrical Networks
 CME 305: Discrete Mathematics and Algorithms Random Walks and Electrical Networks Random walks are widely used tools in algorithm design and probabilistic analysis and they have numerous applications.
CME 305: Discrete Mathematics and Algorithms Random Walks and Electrical Networks Random walks are widely used tools in algorithm design and probabilistic analysis and they have numerous applications.
Powerful tool for sampling from complicated distributions. Many use Markov chains to model events that arise in nature.
 Markov Chains Markov chains: 2SAT: Powerful tool for sampling from complicated distributions rely only on local moves to explore state space. Many use Markov chains to model events that arise in nature.
Markov Chains Markov chains: 2SAT: Powerful tool for sampling from complicated distributions rely only on local moves to explore state space. Many use Markov chains to model events that arise in nature.
There are no zero-hard problems in multiparty communication complexity
 There are no zero-hard problems in multiparty communication complexity László Babai and Denis Pankratov University of Chicago DRAFT: 2015-04-29 7:00pm Abstract We study the feasibility of generalizing
There are no zero-hard problems in multiparty communication complexity László Babai and Denis Pankratov University of Chicago DRAFT: 2015-04-29 7:00pm Abstract We study the feasibility of generalizing
Random Walks on Graphs. One Concrete Example of a random walk Motivation applications
 Random Walks on Graphs Outline One Concrete Example of a random walk Motivation applications shuffling cards universal traverse sequence self stabilizing token management scheme random sampling enumeration
Random Walks on Graphs Outline One Concrete Example of a random walk Motivation applications shuffling cards universal traverse sequence self stabilizing token management scheme random sampling enumeration
CSC 2429 Approaches to the P vs. NP Question and Related Complexity Questions Lecture 2: Switching Lemma, AC 0 Circuit Lower Bounds
 CSC 2429 Approaches to the P vs. NP Question and Related Complexity Questions Lecture 2: Switching Lemma, AC 0 Circuit Lower Bounds Lecturer: Toniann Pitassi Scribe: Robert Robere Winter 2014 1 Switching
CSC 2429 Approaches to the P vs. NP Question and Related Complexity Questions Lecture 2: Switching Lemma, AC 0 Circuit Lower Bounds Lecturer: Toniann Pitassi Scribe: Robert Robere Winter 2014 1 Switching
PCPs and Inapproximability Gap-producing and Gap-Preserving Reductions. My T. Thai
 PCPs and Inapproximability Gap-producing and Gap-Preserving Reductions My T. Thai 1 1 Hardness of Approximation Consider a maximization problem Π such as MAX-E3SAT. To show that it is NP-hard to approximation
PCPs and Inapproximability Gap-producing and Gap-Preserving Reductions My T. Thai 1 1 Hardness of Approximation Consider a maximization problem Π such as MAX-E3SAT. To show that it is NP-hard to approximation
A note on monotone real circuits
 A note on monotone real circuits Pavel Hrubeš and Pavel Pudlák March 14, 2017 Abstract We show that if a Boolean function f : {0, 1} n {0, 1} can be computed by a monotone real circuit of size s using
A note on monotone real circuits Pavel Hrubeš and Pavel Pudlák March 14, 2017 Abstract We show that if a Boolean function f : {0, 1} n {0, 1} can be computed by a monotone real circuit of size s using
Multi-Linear Formulas for Permanent and Determinant are of Super-Polynomial Size
 Multi-Linear Formulas for Permanent and Determinant are of Super-Polynomial Size Ran Raz Weizmann Institute ranraz@wisdom.weizmann.ac.il Abstract An arithmetic formula is multi-linear if the polynomial
Multi-Linear Formulas for Permanent and Determinant are of Super-Polynomial Size Ran Raz Weizmann Institute ranraz@wisdom.weizmann.ac.il Abstract An arithmetic formula is multi-linear if the polynomial
ON TRAVERSAL SEQUENCES, EXPLORATION SEQUENCES AND COMPLETENESS OF KOLMOGOROV RANDOM STRINGS
 ON TRAVERSAL SEQUENCES, EXPLORATION SEQUENCES AND COMPLETENESS OF KOLMOGOROV RANDOM STRINGS BY MICHAL KOUCKÝ A dissertation submitted to the Graduate School New Brunswick Rutgers, The State University
ON TRAVERSAL SEQUENCES, EXPLORATION SEQUENCES AND COMPLETENESS OF KOLMOGOROV RANDOM STRINGS BY MICHAL KOUCKÝ A dissertation submitted to the Graduate School New Brunswick Rutgers, The State University
EECS 495: Randomized Algorithms Lecture 14 Random Walks. j p ij = 1. Pr[X t+1 = j X 0 = i 0,..., X t 1 = i t 1, X t = i] = Pr[X t+
![EECS 495: Randomized Algorithms Lecture 14 Random Walks. j p ij = 1. Pr[X t+1 = j X 0 = i 0,..., X t 1 = i t 1, X t = i] = Pr[X t+ EECS 495: Randomized Algorithms Lecture 14 Random Walks. j p ij = 1. Pr[X t+1 = j X 0 = i 0,..., X t 1 = i t 1, X t = i] = Pr[X t+](/thumbs/89/98539575.jpg) EECS 495: Randomized Algorithms Lecture 14 Random Walks Reading: Motwani-Raghavan Chapter 6 Powerful tool for sampling complicated distributions since use only local moves Given: to explore state space.
EECS 495: Randomized Algorithms Lecture 14 Random Walks Reading: Motwani-Raghavan Chapter 6 Powerful tool for sampling complicated distributions since use only local moves Given: to explore state space.
20.1 2SAT. CS125 Lecture 20 Fall 2016
 CS125 Lecture 20 Fall 2016 20.1 2SAT We show yet another possible way to solve the 2SAT problem. Recall that the input to 2SAT is a logical expression that is the conunction (AND) of a set of clauses,
CS125 Lecture 20 Fall 2016 20.1 2SAT We show yet another possible way to solve the 2SAT problem. Recall that the input to 2SAT is a logical expression that is the conunction (AND) of a set of clauses,
Approximating Longest Directed Path
 Electronic Colloquium on Computational Complexity, Report No. 3 (003) Approximating Longest Directed Path Andreas Björklund Thore Husfeldt Sanjeev Khanna April 6, 003 Abstract We investigate the hardness
Electronic Colloquium on Computational Complexity, Report No. 3 (003) Approximating Longest Directed Path Andreas Björklund Thore Husfeldt Sanjeev Khanna April 6, 003 Abstract We investigate the hardness
Expander Construction in VNC 1
 Expander Construction in VNC 1 Sam Buss joint work with Valentine Kabanets, Antonina Kolokolova & Michal Koucký Prague Workshop on Bounded Arithmetic November 2-3, 2017 Talk outline I. Combinatorial construction
Expander Construction in VNC 1 Sam Buss joint work with Valentine Kabanets, Antonina Kolokolova & Michal Koucký Prague Workshop on Bounded Arithmetic November 2-3, 2017 Talk outline I. Combinatorial construction
The cocycle lattice of binary matroids
 Published in: Europ. J. Comb. 14 (1993), 241 250. The cocycle lattice of binary matroids László Lovász Eötvös University, Budapest, Hungary, H-1088 Princeton University, Princeton, NJ 08544 Ákos Seress*
Published in: Europ. J. Comb. 14 (1993), 241 250. The cocycle lattice of binary matroids László Lovász Eötvös University, Budapest, Hungary, H-1088 Princeton University, Princeton, NJ 08544 Ákos Seress*
Cycle lengths in sparse graphs
 Cycle lengths in sparse graphs Benny Sudakov Jacques Verstraëte Abstract Let C(G) denote the set of lengths of cycles in a graph G. In the first part of this paper, we study the minimum possible value
Cycle lengths in sparse graphs Benny Sudakov Jacques Verstraëte Abstract Let C(G) denote the set of lengths of cycles in a graph G. In the first part of this paper, we study the minimum possible value
Limiting Negations in Non-Deterministic Circuits
 Limiting Negations in Non-Deterministic Circuits Hiroki Morizumi Graduate School of Information Sciences, Tohoku University, Sendai 980-8579, Japan morizumi@ecei.tohoku.ac.jp Abstract The minimum number
Limiting Negations in Non-Deterministic Circuits Hiroki Morizumi Graduate School of Information Sciences, Tohoku University, Sendai 980-8579, Japan morizumi@ecei.tohoku.ac.jp Abstract The minimum number
Pseudorandom Generators
 8 Pseudorandom Generators Great Ideas in Theoretical Computer Science Saarland University, Summer 2014 andomness is one of the fundamental computational resources and appears everywhere. In computer science,
8 Pseudorandom Generators Great Ideas in Theoretical Computer Science Saarland University, Summer 2014 andomness is one of the fundamental computational resources and appears everywhere. In computer science,
Algorithms: COMP3121/3821/9101/9801
 NEW SOUTH WALES Algorithms: COMP3121/3821/9101/9801 Aleks Ignjatović School of Computer Science and Engineering University of New South Wales LECTURE 9: INTRACTABILITY COMP3121/3821/9101/9801 1 / 29 Feasibility
NEW SOUTH WALES Algorithms: COMP3121/3821/9101/9801 Aleks Ignjatović School of Computer Science and Engineering University of New South Wales LECTURE 9: INTRACTABILITY COMP3121/3821/9101/9801 1 / 29 Feasibility
Graph coloring, perfect graphs
 Lecture 5 (05.04.2013) Graph coloring, perfect graphs Scribe: Tomasz Kociumaka Lecturer: Marcin Pilipczuk 1 Introduction to graph coloring Definition 1. Let G be a simple undirected graph and k a positive
Lecture 5 (05.04.2013) Graph coloring, perfect graphs Scribe: Tomasz Kociumaka Lecturer: Marcin Pilipczuk 1 Introduction to graph coloring Definition 1. Let G be a simple undirected graph and k a positive
Counting independent sets up to the tree threshold
 Counting independent sets up to the tree threshold Dror Weitz March 16, 2006 Abstract We consider the problem of approximately counting/sampling weighted independent sets of a graph G with activity λ,
Counting independent sets up to the tree threshold Dror Weitz March 16, 2006 Abstract We consider the problem of approximately counting/sampling weighted independent sets of a graph G with activity λ,
Testing Equality in Communication Graphs
 Electronic Colloquium on Computational Complexity, Report No. 86 (2016) Testing Equality in Communication Graphs Noga Alon Klim Efremenko Benny Sudakov Abstract Let G = (V, E) be a connected undirected
Electronic Colloquium on Computational Complexity, Report No. 86 (2016) Testing Equality in Communication Graphs Noga Alon Klim Efremenko Benny Sudakov Abstract Let G = (V, E) be a connected undirected
Bounded Arithmetic, Expanders, and Monotone Propositional Proofs
 Bounded Arithmetic, Expanders, and Monotone Propositional Proofs joint work with Valentine Kabanets, Antonina Kolokolova & Michal Koucký Takeuti Symposium on Advances in Logic Kobe, Japan September 20,
Bounded Arithmetic, Expanders, and Monotone Propositional Proofs joint work with Valentine Kabanets, Antonina Kolokolova & Michal Koucký Takeuti Symposium on Advances in Logic Kobe, Japan September 20,
Reductions to Graph Isomorphism
 Reductions to raph Isomorphism Jacobo Torán Institut für Theoretische Informatik Universität Ulm D-89069 Ulm, ermany jacobo.toran@uni-ulm.de June 13, 2008 Keywords: Computational complexity, reducibilities,
Reductions to raph Isomorphism Jacobo Torán Institut für Theoretische Informatik Universität Ulm D-89069 Ulm, ermany jacobo.toran@uni-ulm.de June 13, 2008 Keywords: Computational complexity, reducibilities,
Meta-Algorithms vs. Circuit Lower Bounds Valentine Kabanets
 Meta-Algorithms vs. Circuit Lower Bounds Valentine Kabanets Tokyo Institute of Technology & Simon Fraser University Understanding Efficiency Better understanding of Efficient Computation Good Algorithms
Meta-Algorithms vs. Circuit Lower Bounds Valentine Kabanets Tokyo Institute of Technology & Simon Fraser University Understanding Efficiency Better understanding of Efficient Computation Good Algorithms
AALBORG UNIVERSITY. Total domination in partitioned graphs. Allan Frendrup, Preben Dahl Vestergaard and Anders Yeo
 AALBORG UNIVERSITY Total domination in partitioned graphs by Allan Frendrup, Preben Dahl Vestergaard and Anders Yeo R-2007-08 February 2007 Department of Mathematical Sciences Aalborg University Fredrik
AALBORG UNIVERSITY Total domination in partitioned graphs by Allan Frendrup, Preben Dahl Vestergaard and Anders Yeo R-2007-08 February 2007 Department of Mathematical Sciences Aalborg University Fredrik
Show that the following problems are NP-complete
 Show that the following problems are NP-complete April 7, 2018 Below is a list of 30 exercises in which you are asked to prove that some problem is NP-complete. The goal is to better understand the theory
Show that the following problems are NP-complete April 7, 2018 Below is a list of 30 exercises in which you are asked to prove that some problem is NP-complete. The goal is to better understand the theory
P is the class of problems for which there are algorithms that solve the problem in time O(n k ) for some constant k.
 Complexity Theory Problems are divided into complexity classes. Informally: So far in this course, almost all algorithms had polynomial running time, i.e., on inputs of size n, worst-case running time
Complexity Theory Problems are divided into complexity classes. Informally: So far in this course, almost all algorithms had polynomial running time, i.e., on inputs of size n, worst-case running time
Lecture 7: More Arithmetic and Fun With Primes
 IAS/PCMI Summer Session 2000 Clay Mathematics Undergraduate Program Advanced Course on Computational Complexity Lecture 7: More Arithmetic and Fun With Primes David Mix Barrington and Alexis Maciel July
IAS/PCMI Summer Session 2000 Clay Mathematics Undergraduate Program Advanced Course on Computational Complexity Lecture 7: More Arithmetic and Fun With Primes David Mix Barrington and Alexis Maciel July
CSC 5170: Theory of Computational Complexity Lecture 4 The Chinese University of Hong Kong 1 February 2010
 CSC 5170: Theory of Computational Complexity Lecture 4 The Chinese University of Hong Kong 1 February 2010 Computational complexity studies the amount of resources necessary to perform given computations.
CSC 5170: Theory of Computational Complexity Lecture 4 The Chinese University of Hong Kong 1 February 2010 Computational complexity studies the amount of resources necessary to perform given computations.
Low-Depth Witnesses are Easy to Find
 Low-Depth Witnesses are Easy to Find Luis Antunes U. Porto Lance Fortnow U. Chicago Alexandre Pinto U. Porto André Souto U. Porto Abstract Antunes, Fortnow, van Melkebeek and Vinodchandran captured the
Low-Depth Witnesses are Easy to Find Luis Antunes U. Porto Lance Fortnow U. Chicago Alexandre Pinto U. Porto André Souto U. Porto Abstract Antunes, Fortnow, van Melkebeek and Vinodchandran captured the
Lecture 22: Derandomization Implies Circuit Lower Bounds
 Advanced Complexity Theory Spring 2016 Lecture 22: Derandomization Implies Circuit Lower Bounds Prof. Dana Moshkovitz 1 Overview In the last lecture we saw a proof presented by Madhu Sudan that E SIZE(2
Advanced Complexity Theory Spring 2016 Lecture 22: Derandomization Implies Circuit Lower Bounds Prof. Dana Moshkovitz 1 Overview In the last lecture we saw a proof presented by Madhu Sudan that E SIZE(2
Lecture 6: Random Walks versus Independent Sampling
 Spectral Graph Theory and Applications WS 011/01 Lecture 6: Random Walks versus Independent Sampling Lecturer: Thomas Sauerwald & He Sun For many problems it is necessary to draw samples from some distribution
Spectral Graph Theory and Applications WS 011/01 Lecture 6: Random Walks versus Independent Sampling Lecturer: Thomas Sauerwald & He Sun For many problems it is necessary to draw samples from some distribution
Lecture 2: January 18
 CS271 Randomness & Computation Spring 2018 Instructor: Alistair Sinclair Lecture 2: January 18 Disclaimer: These notes have not been subjected to the usual scrutiny accorded to formal publications. They
CS271 Randomness & Computation Spring 2018 Instructor: Alistair Sinclair Lecture 2: January 18 Disclaimer: These notes have not been subjected to the usual scrutiny accorded to formal publications. They
Lecture 5: Derandomization (Part II)
 CS369E: Expanders May 1, 005 Lecture 5: Derandomization (Part II) Lecturer: Prahladh Harsha Scribe: Adam Barth Today we will use expanders to derandomize the algorithm for linearity test. Before presenting
CS369E: Expanders May 1, 005 Lecture 5: Derandomization (Part II) Lecturer: Prahladh Harsha Scribe: Adam Barth Today we will use expanders to derandomize the algorithm for linearity test. Before presenting
Decomposing oriented graphs into transitive tournaments
 Decomposing oriented graphs into transitive tournaments Raphael Yuster Department of Mathematics University of Haifa Haifa 39105, Israel Abstract For an oriented graph G with n vertices, let f(g) denote
Decomposing oriented graphs into transitive tournaments Raphael Yuster Department of Mathematics University of Haifa Haifa 39105, Israel Abstract For an oriented graph G with n vertices, let f(g) denote
IITM-CS6845: Theory Toolkit February 3, 2012
 IITM-CS6845: Theory Toolkit February 3, 2012 Lecture 4 : Derandomizing the logspace algorithm for s-t connectivity Lecturer: N S Narayanaswamy Scribe: Mrinal Kumar Lecture Plan:In this lecture, we will
IITM-CS6845: Theory Toolkit February 3, 2012 Lecture 4 : Derandomizing the logspace algorithm for s-t connectivity Lecturer: N S Narayanaswamy Scribe: Mrinal Kumar Lecture Plan:In this lecture, we will
On Aperiodic Subtraction Games with Bounded Nim Sequence
 On Aperiodic Subtraction Games with Bounded Nim Sequence Nathan Fox arxiv:1407.2823v1 [math.co] 10 Jul 2014 Abstract Subtraction games are a class of impartial combinatorial games whose positions correspond
On Aperiodic Subtraction Games with Bounded Nim Sequence Nathan Fox arxiv:1407.2823v1 [math.co] 10 Jul 2014 Abstract Subtraction games are a class of impartial combinatorial games whose positions correspond
Rounds in Communication Complexity Revisited
 Rounds in Communication Complexity Revisited Noam Nisan Hebrew University Avi Widgerson Hebrew University and Princeton University Abstract The k-round two-party communication complexity was studied in
Rounds in Communication Complexity Revisited Noam Nisan Hebrew University Avi Widgerson Hebrew University and Princeton University Abstract The k-round two-party communication complexity was studied in
Pseudorandom Generators for Group Products
 Pseudorandom Generators for Group Products preliminary version Michal Koucký, Prajakta Nimbhorkar and Pavel Pudlák July 16, 2010 Abstract We prove that the pseudorandom generator introduced in [INW94]
Pseudorandom Generators for Group Products preliminary version Michal Koucký, Prajakta Nimbhorkar and Pavel Pudlák July 16, 2010 Abstract We prove that the pseudorandom generator introduced in [INW94]
Testing the Expansion of a Graph
 Testing the Expansion of a Graph Asaf Nachmias Asaf Shapira Abstract We study the problem of testing the expansion of graphs with bounded degree d in sublinear time. A graph is said to be an α- expander
Testing the Expansion of a Graph Asaf Nachmias Asaf Shapira Abstract We study the problem of testing the expansion of graphs with bounded degree d in sublinear time. A graph is said to be an α- expander
Lecture 24: April 12
 CS271 Randomness & Computation Spring 2018 Instructor: Alistair Sinclair Lecture 24: April 12 Disclaimer: These notes have not been subjected to the usual scrutiny accorded to formal publications. They
CS271 Randomness & Computation Spring 2018 Instructor: Alistair Sinclair Lecture 24: April 12 Disclaimer: These notes have not been subjected to the usual scrutiny accorded to formal publications. They
Perfect matchings in highly cyclically connected regular graphs
 Perfect matchings in highly cyclically connected regular graphs arxiv:1709.08891v1 [math.co] 6 Sep 017 Robert Lukot ka Comenius University, Bratislava lukotka@dcs.fmph.uniba.sk Edita Rollová University
Perfect matchings in highly cyclically connected regular graphs arxiv:1709.08891v1 [math.co] 6 Sep 017 Robert Lukot ka Comenius University, Bratislava lukotka@dcs.fmph.uniba.sk Edita Rollová University
/633 Introduction to Algorithms Lecturer: Michael Dinitz Topic: Dynamic Programming II Date: 10/12/17
 601.433/633 Introduction to Algorithms Lecturer: Michael Dinitz Topic: Dynamic Programming II Date: 10/12/17 12.1 Introduction Today we re going to do a couple more examples of dynamic programming. While
601.433/633 Introduction to Algorithms Lecturer: Michael Dinitz Topic: Dynamic Programming II Date: 10/12/17 12.1 Introduction Today we re going to do a couple more examples of dynamic programming. While
Lecture 3: Randomness in Computation
 Great Ideas in Theoretical Computer Science Summer 2013 Lecture 3: Randomness in Computation Lecturer: Kurt Mehlhorn & He Sun Randomness is one of basic resources and appears everywhere. In computer science,
Great Ideas in Theoretical Computer Science Summer 2013 Lecture 3: Randomness in Computation Lecturer: Kurt Mehlhorn & He Sun Randomness is one of basic resources and appears everywhere. In computer science,
With Question/Answer Animations
 Chapter 5 With Question/Answer Animations Copyright McGraw-Hill Education. All rights reserved. No reproduction or distribution without the prior written consent of McGraw-Hill Education. Chapter Summary
Chapter 5 With Question/Answer Animations Copyright McGraw-Hill Education. All rights reserved. No reproduction or distribution without the prior written consent of McGraw-Hill Education. Chapter Summary
c 1998 Society for Industrial and Applied Mathematics Vol. 27, No. 4, pp , August
 SIAM J COMPUT c 1998 Society for Industrial and Applied Mathematics Vol 27, No 4, pp 173 182, August 1998 8 SEPARATING EXPONENTIALLY AMBIGUOUS FINITE AUTOMATA FROM POLYNOMIALLY AMBIGUOUS FINITE AUTOMATA
SIAM J COMPUT c 1998 Society for Industrial and Applied Mathematics Vol 27, No 4, pp 173 182, August 1998 8 SEPARATING EXPONENTIALLY AMBIGUOUS FINITE AUTOMATA FROM POLYNOMIALLY AMBIGUOUS FINITE AUTOMATA
University of Chicago Autumn 2003 CS Markov Chain Monte Carlo Methods
 University of Chicago Autumn 2003 CS37101-1 Markov Chain Monte Carlo Methods Lecture 4: October 21, 2003 Bounding the mixing time via coupling Eric Vigoda 4.1 Introduction In this lecture we ll use the
University of Chicago Autumn 2003 CS37101-1 Markov Chain Monte Carlo Methods Lecture 4: October 21, 2003 Bounding the mixing time via coupling Eric Vigoda 4.1 Introduction In this lecture we ll use the
Probabilistic Proofs of Existence of Rare Events. Noga Alon
 Probabilistic Proofs of Existence of Rare Events Noga Alon Department of Mathematics Sackler Faculty of Exact Sciences Tel Aviv University Ramat-Aviv, Tel Aviv 69978 ISRAEL 1. The Local Lemma In a typical
Probabilistic Proofs of Existence of Rare Events Noga Alon Department of Mathematics Sackler Faculty of Exact Sciences Tel Aviv University Ramat-Aviv, Tel Aviv 69978 ISRAEL 1. The Local Lemma In a typical
On the Structure and the Number of Prime Implicants of 2-CNFs
 On the Structure and the Number of Prime Implicants of 2-CNFs Navid Talebanfard Department of Mathematical and Computing Sciences, Tokyo Institute of Technology, Meguro-ku Ookayama 2-12-1, Japan 152-8552
On the Structure and the Number of Prime Implicants of 2-CNFs Navid Talebanfard Department of Mathematical and Computing Sciences, Tokyo Institute of Technology, Meguro-ku Ookayama 2-12-1, Japan 152-8552
LIMITING PROBABILITY TRANSITION MATRIX OF A CONDENSED FIBONACCI TREE
 International Journal of Applied Mathematics Volume 31 No. 18, 41-49 ISSN: 1311-178 (printed version); ISSN: 1314-86 (on-line version) doi: http://dx.doi.org/1.173/ijam.v31i.6 LIMITING PROBABILITY TRANSITION
International Journal of Applied Mathematics Volume 31 No. 18, 41-49 ISSN: 1311-178 (printed version); ISSN: 1314-86 (on-line version) doi: http://dx.doi.org/1.173/ijam.v31i.6 LIMITING PROBABILITY TRANSITION
Downloaded 07/22/13 to Redistribution subject to SIAM license or copyright; see
 SIAM J. COMPUT. Vol. 28, No. 3, pp. 1051 1072 c 1999 Society for Industrial and Applied Mathematics A TIME-SPACE TRADEOFF FOR UNDIRECTED GRAPH TRAVERSAL BY WALKING AUTOMATA PAUL BEAME, ALLAN BORODIN, PRABHAKAR
SIAM J. COMPUT. Vol. 28, No. 3, pp. 1051 1072 c 1999 Society for Industrial and Applied Mathematics A TIME-SPACE TRADEOFF FOR UNDIRECTED GRAPH TRAVERSAL BY WALKING AUTOMATA PAUL BEAME, ALLAN BORODIN, PRABHAKAR
A Proof of the Lucas-Lehmer Test and its Variations by Using a Singular Cubic Curve
 1 47 6 11 Journal of Integer Sequences, Vol. 1 (018), Article 18.6. A Proof of the Lucas-Lehmer Test and its Variations by Using a Singular Cubic Curve Ömer Küçüksakallı Mathematics Department Middle East
1 47 6 11 Journal of Integer Sequences, Vol. 1 (018), Article 18.6. A Proof of the Lucas-Lehmer Test and its Variations by Using a Singular Cubic Curve Ömer Küçüksakallı Mathematics Department Middle East
1 Randomized Computation
 CS 6743 Lecture 17 1 Fall 2007 1 Randomized Computation Why is randomness useful? Imagine you have a stack of bank notes, with very few counterfeit ones. You want to choose a genuine bank note to pay at
CS 6743 Lecture 17 1 Fall 2007 1 Randomized Computation Why is randomness useful? Imagine you have a stack of bank notes, with very few counterfeit ones. You want to choose a genuine bank note to pay at
Flows and Cuts. 1 Concepts. CS 787: Advanced Algorithms. Instructor: Dieter van Melkebeek
 CS 787: Advanced Algorithms Flows and Cuts Instructor: Dieter van Melkebeek This lecture covers the construction of optimal flows and cuts in networks, their relationship, and some applications. It paves
CS 787: Advanced Algorithms Flows and Cuts Instructor: Dieter van Melkebeek This lecture covers the construction of optimal flows and cuts in networks, their relationship, and some applications. It paves
arxiv: v1 [math.co] 13 May 2016
![arxiv: v1 [math.co] 13 May 2016 arxiv: v1 [math.co] 13 May 2016](/thumbs/94/118742815.jpg) GENERALISED RAMSEY NUMBERS FOR TWO SETS OF CYCLES MIKAEL HANSSON arxiv:1605.04301v1 [math.co] 13 May 2016 Abstract. We determine several generalised Ramsey numbers for two sets Γ 1 and Γ 2 of cycles, in
GENERALISED RAMSEY NUMBERS FOR TWO SETS OF CYCLES MIKAEL HANSSON arxiv:1605.04301v1 [math.co] 13 May 2016 Abstract. We determine several generalised Ramsey numbers for two sets Γ 1 and Γ 2 of cycles, in
Testing Expansion in Bounded-Degree Graphs
 Testing Expansion in Bounded-Degree Graphs Artur Czumaj Department of Computer Science University of Warwick Coventry CV4 7AL, UK czumaj@dcs.warwick.ac.uk Christian Sohler Department of Computer Science
Testing Expansion in Bounded-Degree Graphs Artur Czumaj Department of Computer Science University of Warwick Coventry CV4 7AL, UK czumaj@dcs.warwick.ac.uk Christian Sohler Department of Computer Science
A lower bound for the Laplacian eigenvalues of a graph proof of a conjecture by Guo
 A lower bound for the Laplacian eigenvalues of a graph proof of a conjecture by Guo A. E. Brouwer & W. H. Haemers 2008-02-28 Abstract We show that if µ j is the j-th largest Laplacian eigenvalue, and d
A lower bound for the Laplacian eigenvalues of a graph proof of a conjecture by Guo A. E. Brouwer & W. H. Haemers 2008-02-28 Abstract We show that if µ j is the j-th largest Laplacian eigenvalue, and d
On the mean connected induced subgraph order of cographs
 AUSTRALASIAN JOURNAL OF COMBINATORICS Volume 71(1) (018), Pages 161 183 On the mean connected induced subgraph order of cographs Matthew E Kroeker Lucas Mol Ortrud R Oellermann University of Winnipeg Winnipeg,
AUSTRALASIAN JOURNAL OF COMBINATORICS Volume 71(1) (018), Pages 161 183 On the mean connected induced subgraph order of cographs Matthew E Kroeker Lucas Mol Ortrud R Oellermann University of Winnipeg Winnipeg,
ON SENSITIVITY OF k-uniform HYPERGRAPH PROPERTIES
 ON SENSITIVITY OF k-uniform HYPERGRAPH PROPERTIES JOSHUA BIDERMAN, KEVIN CUDDY, ANG LI, MIN JAE SONG Abstract. In this paper we present a graph property with sensitivity Θ( n), where n = ( v 2) is the
ON SENSITIVITY OF k-uniform HYPERGRAPH PROPERTIES JOSHUA BIDERMAN, KEVIN CUDDY, ANG LI, MIN JAE SONG Abstract. In this paper we present a graph property with sensitivity Θ( n), where n = ( v 2) is the
Randomness and non-uniformity
 Randomness and non-uniformity JASS 2006 Course 1: Proofs and Computers Felix Weninger TU München April 2006 Outline Randomized computation 1 Randomized computation 2 Computation with advice Non-uniform
Randomness and non-uniformity JASS 2006 Course 1: Proofs and Computers Felix Weninger TU München April 2006 Outline Randomized computation 1 Randomized computation 2 Computation with advice Non-uniform
Tree-width and planar minors
 Tree-width and planar minors Alexander Leaf and Paul Seymour 1 Princeton University, Princeton, NJ 08544 May 22, 2012; revised March 18, 2014 1 Supported by ONR grant N00014-10-1-0680 and NSF grant DMS-0901075.
Tree-width and planar minors Alexander Leaf and Paul Seymour 1 Princeton University, Princeton, NJ 08544 May 22, 2012; revised March 18, 2014 1 Supported by ONR grant N00014-10-1-0680 and NSF grant DMS-0901075.
VC-DENSITY FOR TREES
 VC-DENSITY FOR TREES ANTON BOBKOV Abstract. We show that for the theory of infinite trees we have vc(n) = n for all n. VC density was introduced in [1] by Aschenbrenner, Dolich, Haskell, MacPherson, and
VC-DENSITY FOR TREES ANTON BOBKOV Abstract. We show that for the theory of infinite trees we have vc(n) = n for all n. VC density was introduced in [1] by Aschenbrenner, Dolich, Haskell, MacPherson, and
NP Completeness and Approximation Algorithms
 Chapter 10 NP Completeness and Approximation Algorithms Let C() be a class of problems defined by some property. We are interested in characterizing the hardest problems in the class, so that if we can
Chapter 10 NP Completeness and Approximation Algorithms Let C() be a class of problems defined by some property. We are interested in characterizing the hardest problems in the class, so that if we can
arxiv: v1 [math.co] 28 Oct 2016
![arxiv: v1 [math.co] 28 Oct 2016 arxiv: v1 [math.co] 28 Oct 2016](/thumbs/92/108819504.jpg) More on foxes arxiv:1610.09093v1 [math.co] 8 Oct 016 Matthias Kriesell Abstract Jens M. Schmidt An edge in a k-connected graph G is called k-contractible if the graph G/e obtained from G by contracting
More on foxes arxiv:1610.09093v1 [math.co] 8 Oct 016 Matthias Kriesell Abstract Jens M. Schmidt An edge in a k-connected graph G is called k-contractible if the graph G/e obtained from G by contracting
Notes for Lecture 2. Statement of the PCP Theorem and Constraint Satisfaction
 U.C. Berkeley Handout N2 CS294: PCP and Hardness of Approximation January 23, 2006 Professor Luca Trevisan Scribe: Luca Trevisan Notes for Lecture 2 These notes are based on my survey paper [5]. L.T. Statement
U.C. Berkeley Handout N2 CS294: PCP and Hardness of Approximation January 23, 2006 Professor Luca Trevisan Scribe: Luca Trevisan Notes for Lecture 2 These notes are based on my survey paper [5]. L.T. Statement
Matchings in hypergraphs of large minimum degree
 Matchings in hypergraphs of large minimum degree Daniela Kühn Deryk Osthus Abstract It is well known that every bipartite graph with vertex classes of size n whose minimum degree is at least n/2 contains
Matchings in hypergraphs of large minimum degree Daniela Kühn Deryk Osthus Abstract It is well known that every bipartite graph with vertex classes of size n whose minimum degree is at least n/2 contains
arxiv: v3 [cs.fl] 2 Jul 2018
![arxiv: v3 [cs.fl] 2 Jul 2018 arxiv: v3 [cs.fl] 2 Jul 2018](/thumbs/93/111950553.jpg) COMPLEXITY OF PREIMAGE PROBLEMS FOR DETERMINISTIC FINITE AUTOMATA MIKHAIL V. BERLINKOV arxiv:1704.08233v3 [cs.fl] 2 Jul 2018 Institute of Natural Sciences and Mathematics, Ural Federal University, Ekaterinburg,
COMPLEXITY OF PREIMAGE PROBLEMS FOR DETERMINISTIC FINITE AUTOMATA MIKHAIL V. BERLINKOV arxiv:1704.08233v3 [cs.fl] 2 Jul 2018 Institute of Natural Sciences and Mathematics, Ural Federal University, Ekaterinburg,
On Recycling the Randomness of the States in Space Bounded Computation
 On Recycling the Randomness of the States in Space Bounded Computation Preliminary Version Ran Raz Omer Reingold Abstract Let M be a logarithmic space Turing machine (or a polynomial width branching program)
On Recycling the Randomness of the States in Space Bounded Computation Preliminary Version Ran Raz Omer Reingold Abstract Let M be a logarithmic space Turing machine (or a polynomial width branching program)
Communication is bounded by root of rank
 Electronic Colloquium on Computational Complexity, Report No. 84 (2013) Communication is bounded by root of rank Shachar Lovett June 7, 2013 Abstract We prove that any total boolean function of rank r
Electronic Colloquium on Computational Complexity, Report No. 84 (2013) Communication is bounded by root of rank Shachar Lovett June 7, 2013 Abstract We prove that any total boolean function of rank r
Szemerédi s regularity lemma revisited. Lewis Memorial Lecture March 14, Terence Tao (UCLA)
 Szemerédi s regularity lemma revisited Lewis Memorial Lecture March 14, 2008 Terence Tao (UCLA) 1 Finding models of large dense graphs Suppose we are given a large dense graph G = (V, E), where V is a
Szemerédi s regularity lemma revisited Lewis Memorial Lecture March 14, 2008 Terence Tao (UCLA) 1 Finding models of large dense graphs Suppose we are given a large dense graph G = (V, E), where V is a
Lecture 20 : Markov Chains
 CSCI 3560 Probability and Computing Instructor: Bogdan Chlebus Lecture 0 : Markov Chains We consider stochastic processes. A process represents a system that evolves through incremental changes called
CSCI 3560 Probability and Computing Instructor: Bogdan Chlebus Lecture 0 : Markov Chains We consider stochastic processes. A process represents a system that evolves through incremental changes called
MINIMALLY NON-PFAFFIAN GRAPHS
 MINIMALLY NON-PFAFFIAN GRAPHS SERGUEI NORINE AND ROBIN THOMAS Abstract. We consider the question of characterizing Pfaffian graphs. We exhibit an infinite family of non-pfaffian graphs minimal with respect
MINIMALLY NON-PFAFFIAN GRAPHS SERGUEI NORINE AND ROBIN THOMAS Abstract. We consider the question of characterizing Pfaffian graphs. We exhibit an infinite family of non-pfaffian graphs minimal with respect
Lecture 12: Randomness Continued
 CS 710: Complexity Theory 2/25/2010 Lecture 12: Randomness Continued Instructor: Dieter van Melkebeek Scribe: Beth Skubak & Nathan Collins In the last lecture we introduced randomized computation in terms
CS 710: Complexity Theory 2/25/2010 Lecture 12: Randomness Continued Instructor: Dieter van Melkebeek Scribe: Beth Skubak & Nathan Collins In the last lecture we introduced randomized computation in terms
Out-colourings of Digraphs
 Out-colourings of Digraphs N. Alon J. Bang-Jensen S. Bessy July 13, 2017 Abstract We study vertex colourings of digraphs so that no out-neighbourhood is monochromatic and call such a colouring an out-colouring.
Out-colourings of Digraphs N. Alon J. Bang-Jensen S. Bessy July 13, 2017 Abstract We study vertex colourings of digraphs so that no out-neighbourhood is monochromatic and call such a colouring an out-colouring.
Random Permutations using Switching Networks
 Random Permutations using Switching Networks Artur Czumaj Department of Computer Science Centre for Discrete Mathematics and its Applications (DIMAP) University of Warwick A.Czumaj@warwick.ac.uk ABSTRACT
Random Permutations using Switching Networks Artur Czumaj Department of Computer Science Centre for Discrete Mathematics and its Applications (DIMAP) University of Warwick A.Czumaj@warwick.ac.uk ABSTRACT
CSCI3390-Second Test with Solutions
 CSCI3390-Second Test with Solutions April 26, 2016 Each of the 15 parts of the problems below is worth 10 points, except for the more involved 4(d), which is worth 20. A perfect score is 100: if your score
CSCI3390-Second Test with Solutions April 26, 2016 Each of the 15 parts of the problems below is worth 10 points, except for the more involved 4(d), which is worth 20. A perfect score is 100: if your score
Lecture 1 : Probabilistic Method
 IITM-CS6845: Theory Jan 04, 01 Lecturer: N.S.Narayanaswamy Lecture 1 : Probabilistic Method Scribe: R.Krithika The probabilistic method is a technique to deal with combinatorial problems by introducing
IITM-CS6845: Theory Jan 04, 01 Lecturer: N.S.Narayanaswamy Lecture 1 : Probabilistic Method Scribe: R.Krithika The probabilistic method is a technique to deal with combinatorial problems by introducing
arxiv: v2 [cs.ds] 3 Oct 2017
![arxiv: v2 [cs.ds] 3 Oct 2017 arxiv: v2 [cs.ds] 3 Oct 2017](/thumbs/84/90870651.jpg) Orthogonal Vectors Indexing Isaac Goldstein 1, Moshe Lewenstein 1, and Ely Porat 1 1 Bar-Ilan University, Ramat Gan, Israel {goldshi,moshe,porately}@cs.biu.ac.il arxiv:1710.00586v2 [cs.ds] 3 Oct 2017 Abstract
Orthogonal Vectors Indexing Isaac Goldstein 1, Moshe Lewenstein 1, and Ely Porat 1 1 Bar-Ilan University, Ramat Gan, Israel {goldshi,moshe,porately}@cs.biu.ac.il arxiv:1710.00586v2 [cs.ds] 3 Oct 2017 Abstract
Two Comments on Targeted Canonical Derandomizers
 Two Comments on Targeted Canonical Derandomizers Oded Goldreich Department of Computer Science Weizmann Institute of Science Rehovot, Israel. oded.goldreich@weizmann.ac.il April 8, 2011 Abstract We revisit
Two Comments on Targeted Canonical Derandomizers Oded Goldreich Department of Computer Science Weizmann Institute of Science Rehovot, Israel. oded.goldreich@weizmann.ac.il April 8, 2011 Abstract We revisit
Lecture 17: D-Stable Polynomials and Lee-Yang Theorems
 Counting and Sampling Fall 2017 Lecture 17: D-Stable Polynomials and Lee-Yang Theorems Lecturer: Shayan Oveis Gharan November 29th Disclaimer: These notes have not been subjected to the usual scrutiny
Counting and Sampling Fall 2017 Lecture 17: D-Stable Polynomials and Lee-Yang Theorems Lecturer: Shayan Oveis Gharan November 29th Disclaimer: These notes have not been subjected to the usual scrutiny
Time-Space Trade-Os. For Undirected ST -Connectivity. on a JAG
 Time-Space Trade-Os For Undirected ST -Connectivity on a JAG Abstract Undirected st-connectivity is an important problem in computing. There are algorithms for this problem that use O (n) time and ones
Time-Space Trade-Os For Undirected ST -Connectivity on a JAG Abstract Undirected st-connectivity is an important problem in computing. There are algorithms for this problem that use O (n) time and ones
Chapter Summary. Mathematical Induction Strong Induction Well-Ordering Recursive Definitions Structural Induction Recursive Algorithms
 1 Chapter Summary Mathematical Induction Strong Induction Well-Ordering Recursive Definitions Structural Induction Recursive Algorithms 2 Section 5.1 3 Section Summary Mathematical Induction Examples of
1 Chapter Summary Mathematical Induction Strong Induction Well-Ordering Recursive Definitions Structural Induction Recursive Algorithms 2 Section 5.1 3 Section Summary Mathematical Induction Examples of
Learning convex bodies is hard
 Learning convex bodies is hard Navin Goyal Microsoft Research India navingo@microsoft.com Luis Rademacher Georgia Tech lrademac@cc.gatech.edu Abstract We show that learning a convex body in R d, given
Learning convex bodies is hard Navin Goyal Microsoft Research India navingo@microsoft.com Luis Rademacher Georgia Tech lrademac@cc.gatech.edu Abstract We show that learning a convex body in R d, given
25.1 Markov Chain Monte Carlo (MCMC)
 CS880: Approximations Algorithms Scribe: Dave Andrzejewski Lecturer: Shuchi Chawla Topic: Approx counting/sampling, MCMC methods Date: 4/4/07 The previous lecture showed that, for self-reducible problems,
CS880: Approximations Algorithms Scribe: Dave Andrzejewski Lecturer: Shuchi Chawla Topic: Approx counting/sampling, MCMC methods Date: 4/4/07 The previous lecture showed that, for self-reducible problems,
Pseudorandomness for permutation and regular branching programs
 Pseudorandomness for permutation and regular branching programs Anindya De March 6, 2013 Abstract In this paper, we prove the following two results about the INW pseudorandom generator It fools constant
Pseudorandomness for permutation and regular branching programs Anindya De March 6, 2013 Abstract In this paper, we prove the following two results about the INW pseudorandom generator It fools constant
fsat We next show that if sat P, then fsat has a polynomial-time algorithm. c 2010 Prof. Yuh-Dauh Lyuu, National Taiwan University Page 425
 fsat fsat is this function problem: Let φ(x 1, x 2,..., x n ) be a boolean expression. If φ is satisfiable, then return a satisfying truth assignment. Otherwise, return no. We next show that if sat P,
fsat fsat is this function problem: Let φ(x 1, x 2,..., x n ) be a boolean expression. If φ is satisfiable, then return a satisfying truth assignment. Otherwise, return no. We next show that if sat P,
Algebraic Problems in Computational Complexity
 Algebraic Problems in Computational Complexity Pranab Sen School of Technology and Computer Science, Tata Institute of Fundamental Research, Mumbai 400005, India pranab@tcs.tifr.res.in Guide: Prof. R.
Algebraic Problems in Computational Complexity Pranab Sen School of Technology and Computer Science, Tata Institute of Fundamental Research, Mumbai 400005, India pranab@tcs.tifr.res.in Guide: Prof. R.
Chromatic number, clique subdivisions, and the conjectures of Hajós and Erdős-Fajtlowicz
 Chromatic number, clique subdivisions, and the conjectures of Hajós and Erdős-Fajtlowicz Jacob Fox Choongbum Lee Benny Sudakov Abstract For a graph G, let χ(g) denote its chromatic number and σ(g) denote
Chromatic number, clique subdivisions, and the conjectures of Hajós and Erdős-Fajtlowicz Jacob Fox Choongbum Lee Benny Sudakov Abstract For a graph G, let χ(g) denote its chromatic number and σ(g) denote
